Patents
Literature
728 results about "File attribute" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
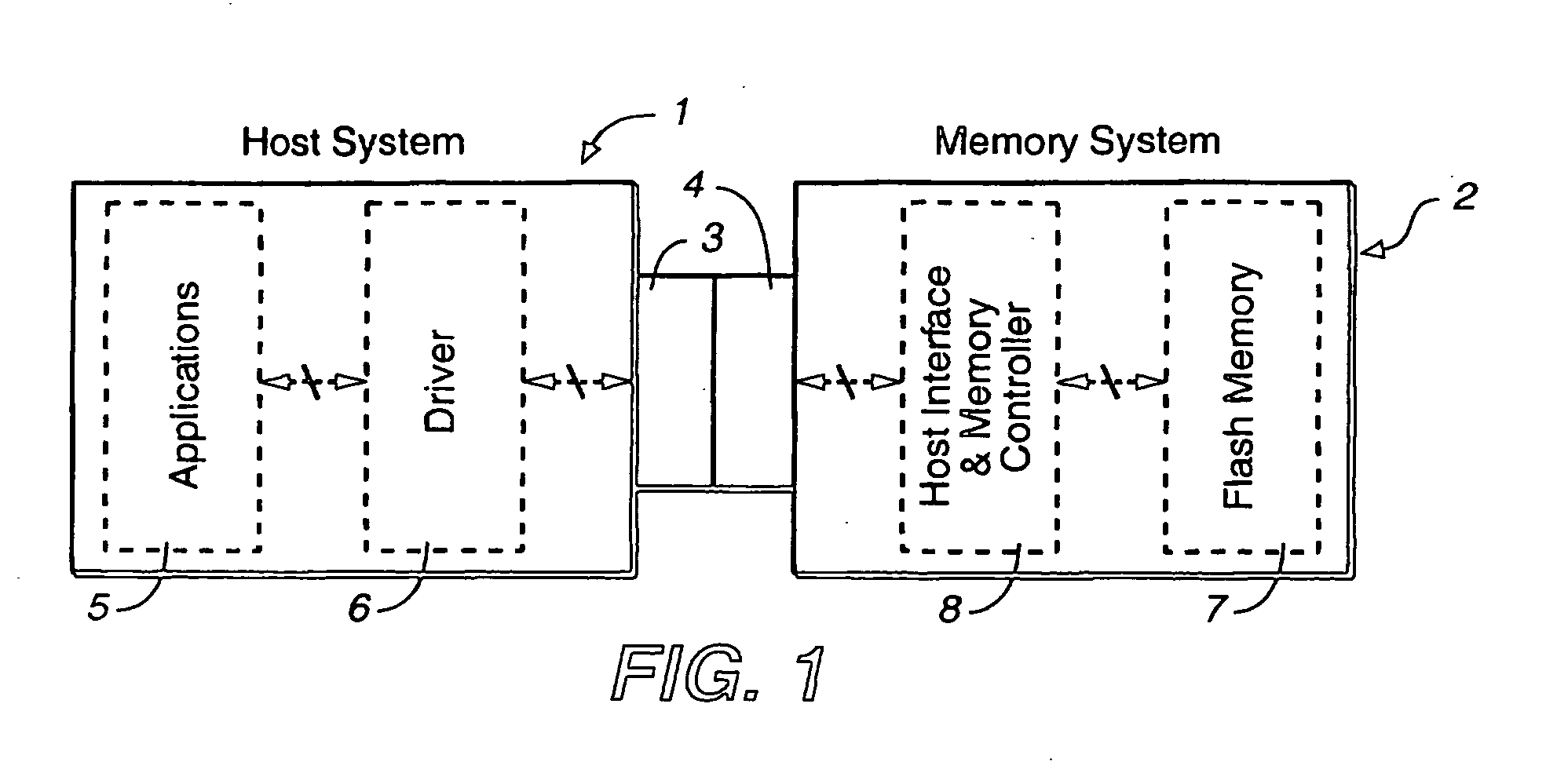
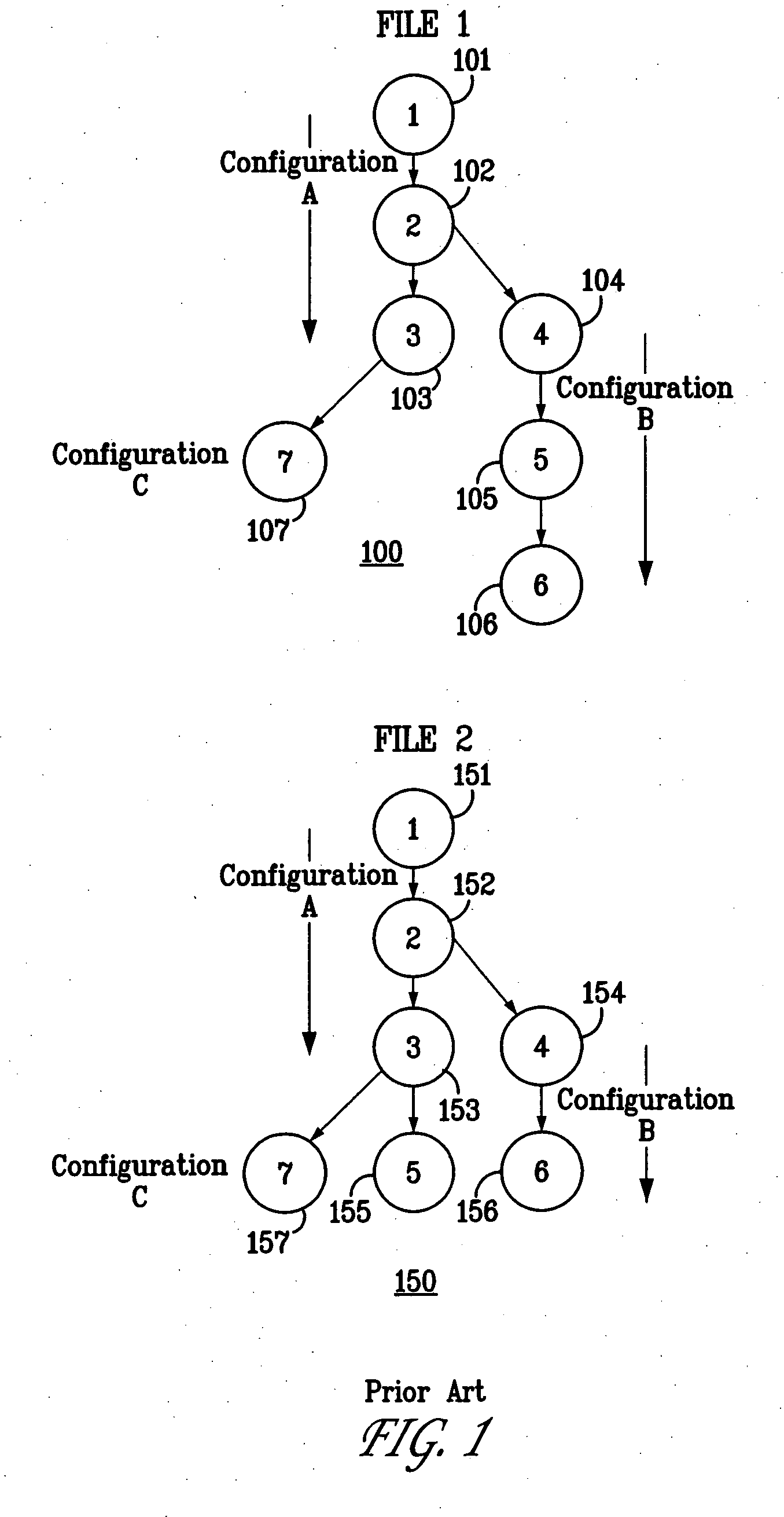
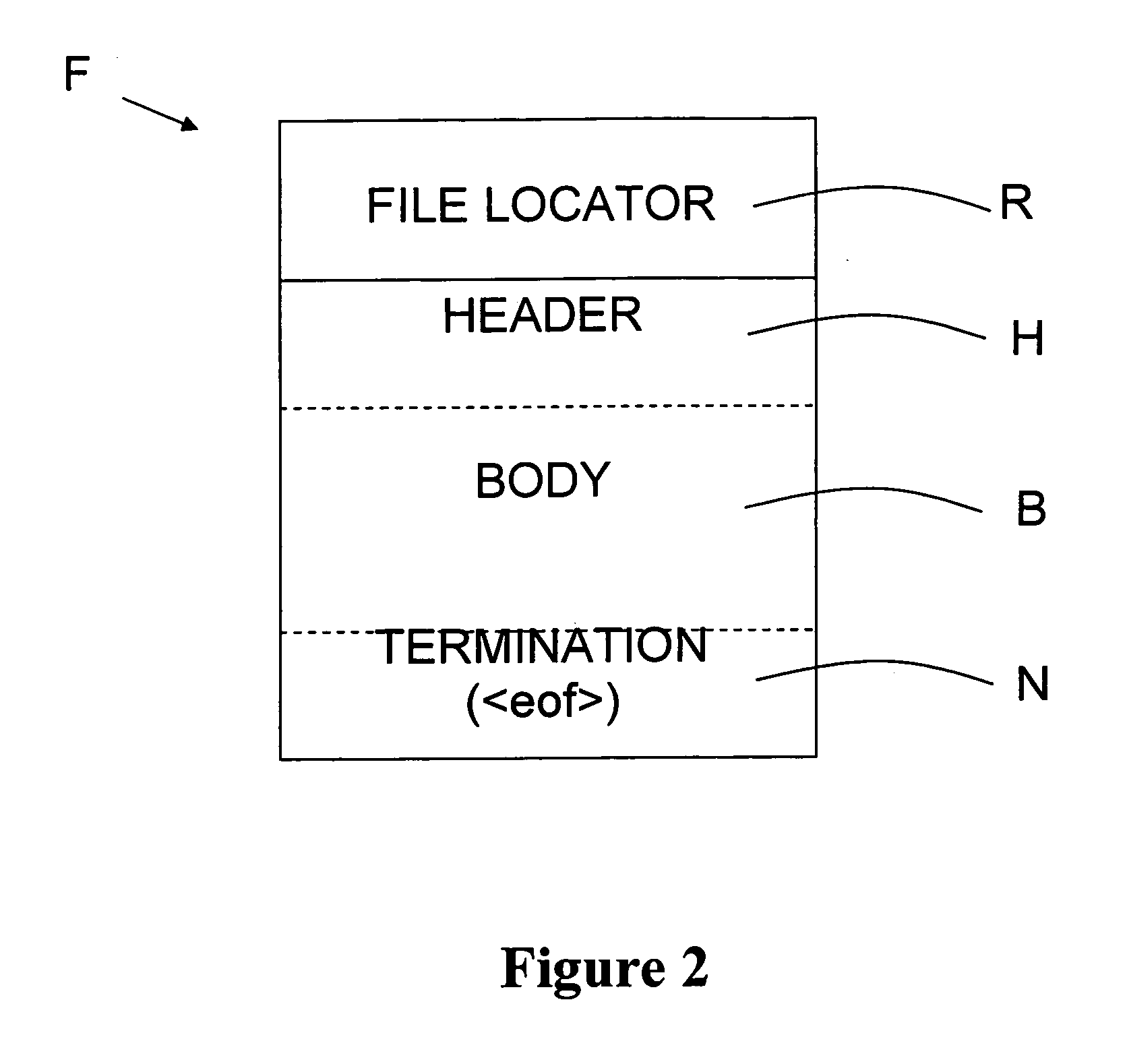
File attributes are metadata associated with computer files that define file system behavior. Each attribute can have one of two states: set and cleared. Attributes are considered distinct from other metadata, such as dates and times, filename extensions or file system permissions. In addition to files, folders, volumes and other file system objects may have attributes.
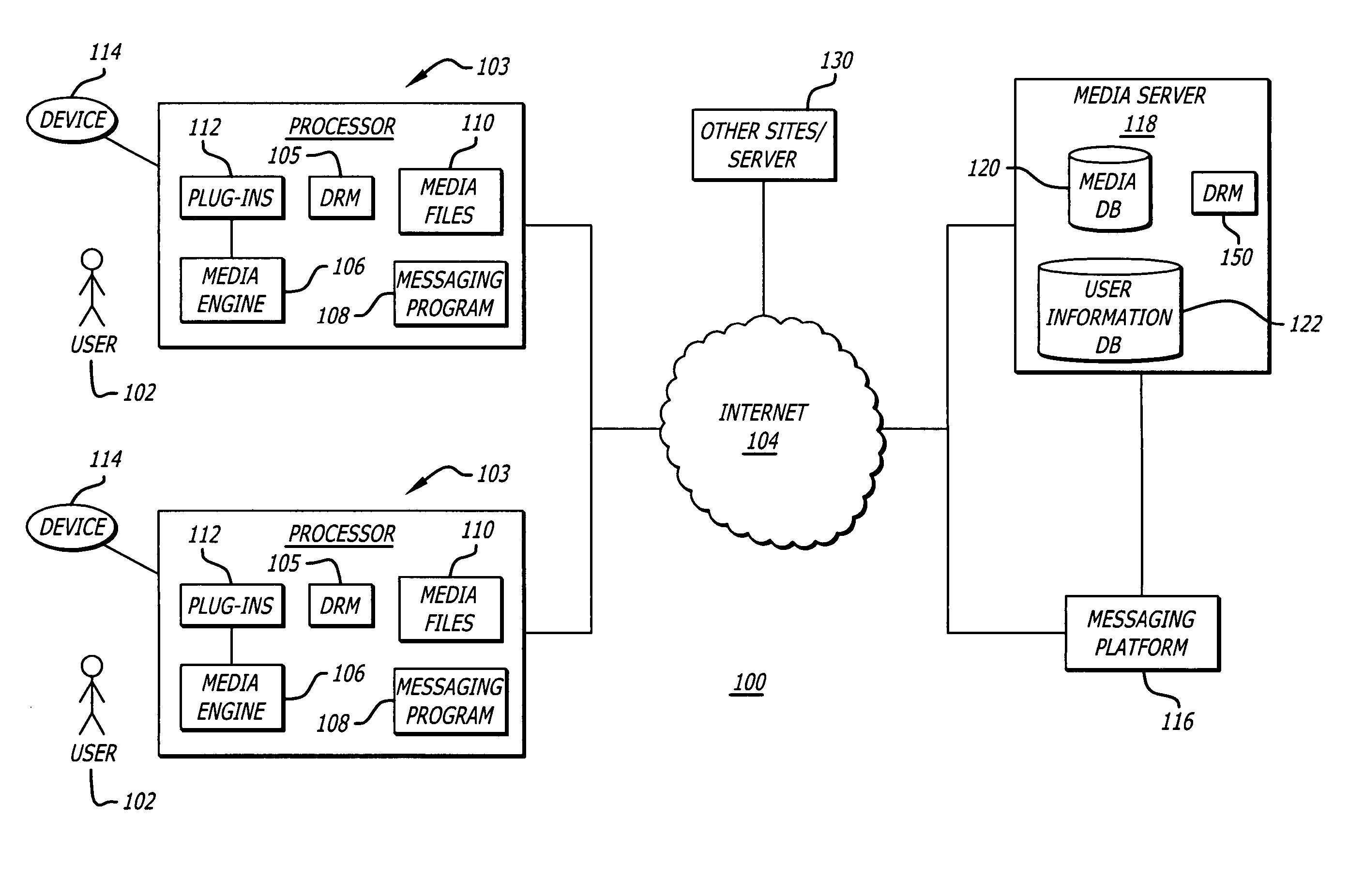
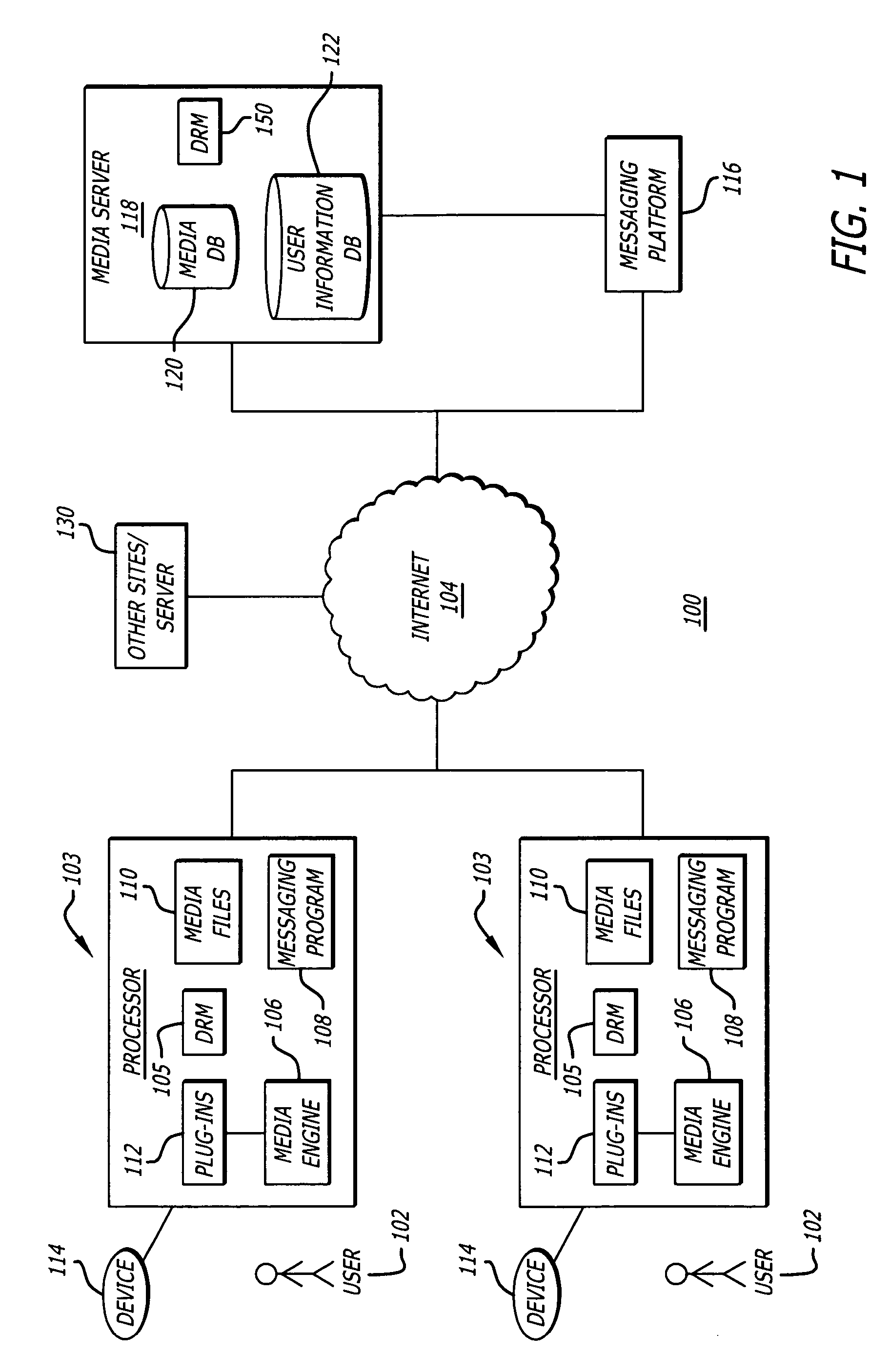
Method and system for generating affinity based playlists
ActiveUS20060195516A1Record information storageMultiple digital computer combinationsRating scoreFile attribute
A system and method of generating a playlist of affinity related media files using affinity relationship data. In one aspect the relationship affinity data is based upon a user rating score obtained from a population of user's ratings associated with media file attributes. In one aspect, a media file attribute which can include an artist, album, title, and genre information associated with a media file is received from a user, indicating the user's desire to create an affinity playlist of media files having an affinity relationship based upon the selected media file attribute.
Owner:HUAWEI TECH CO LTD
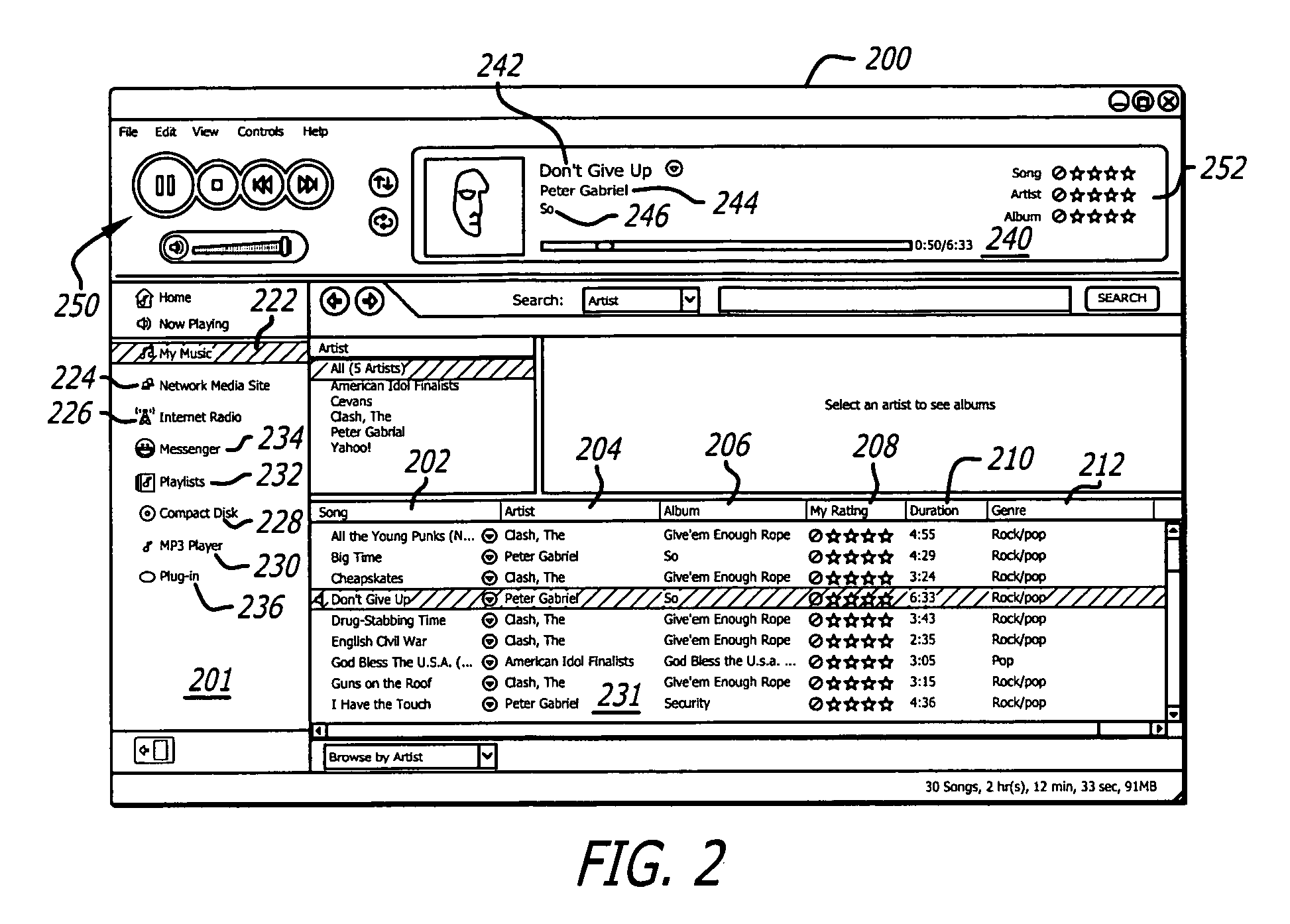
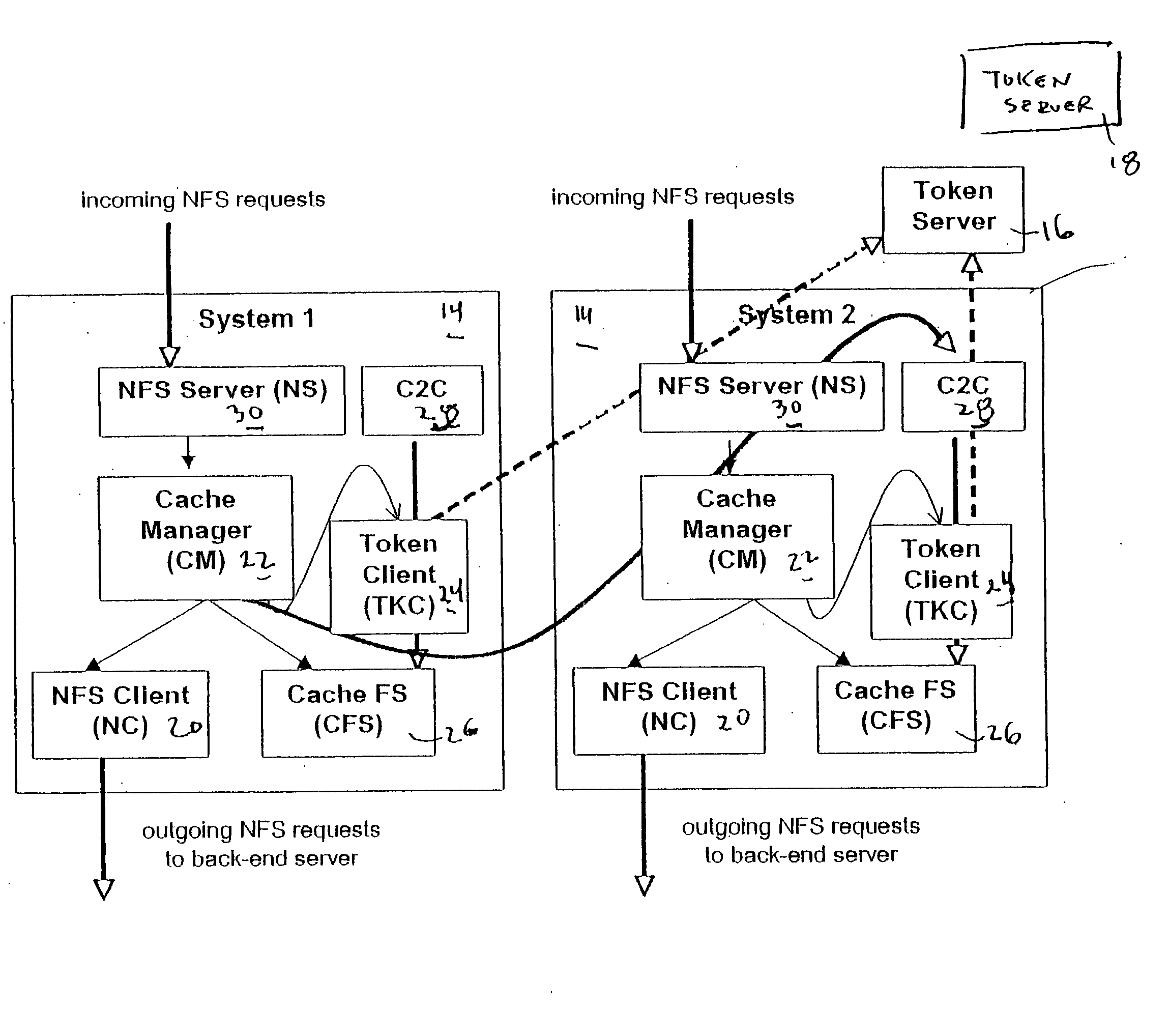
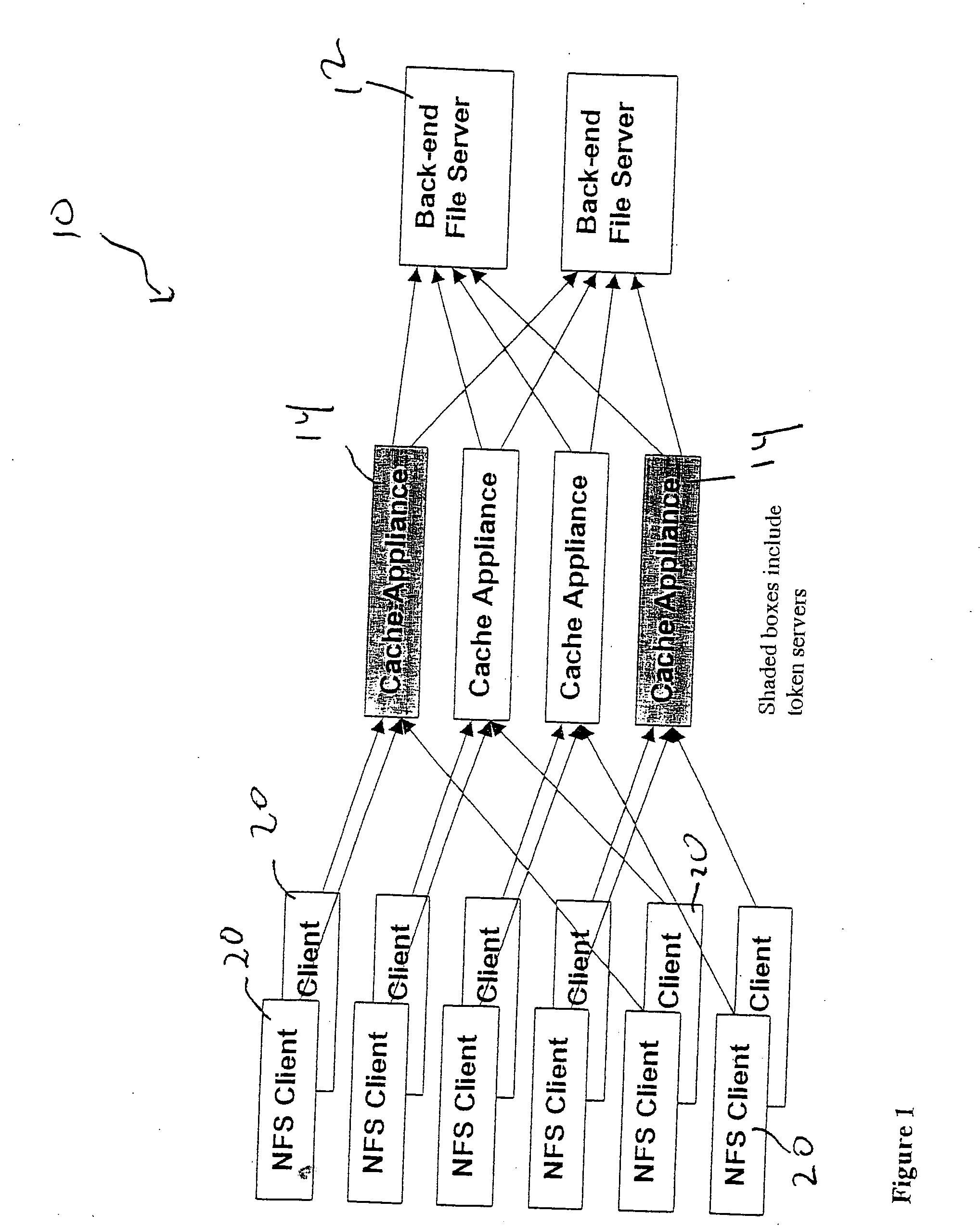
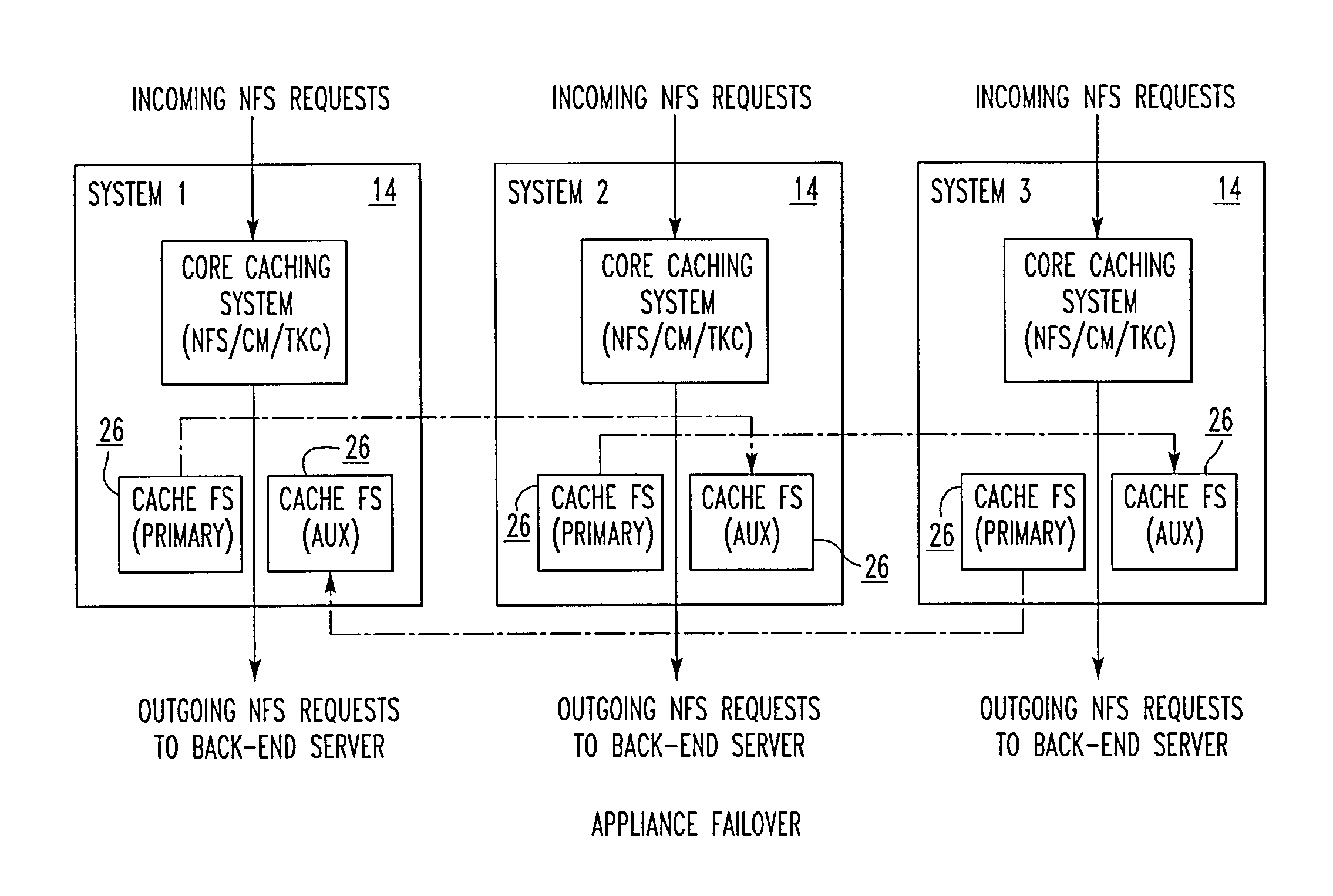
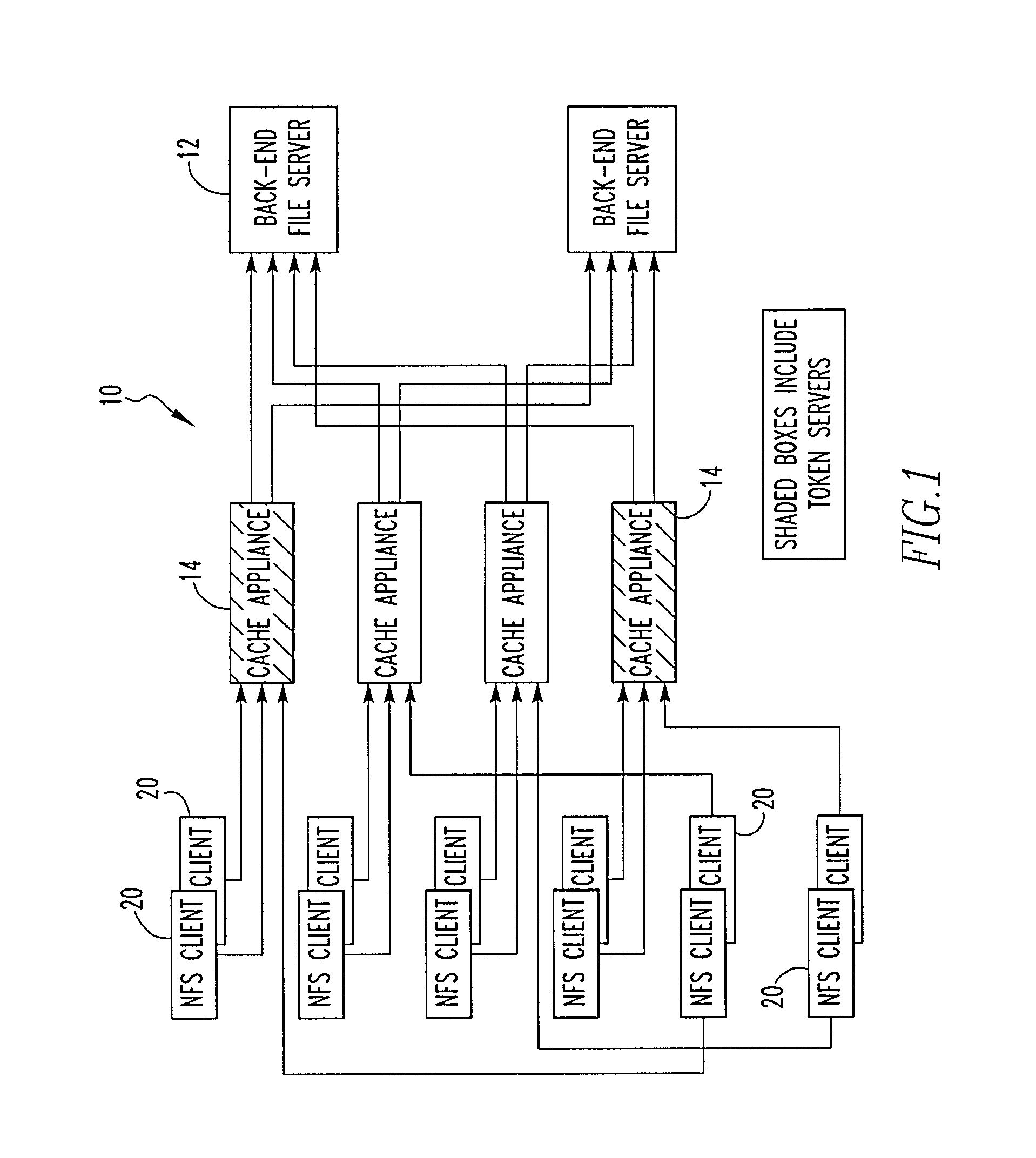
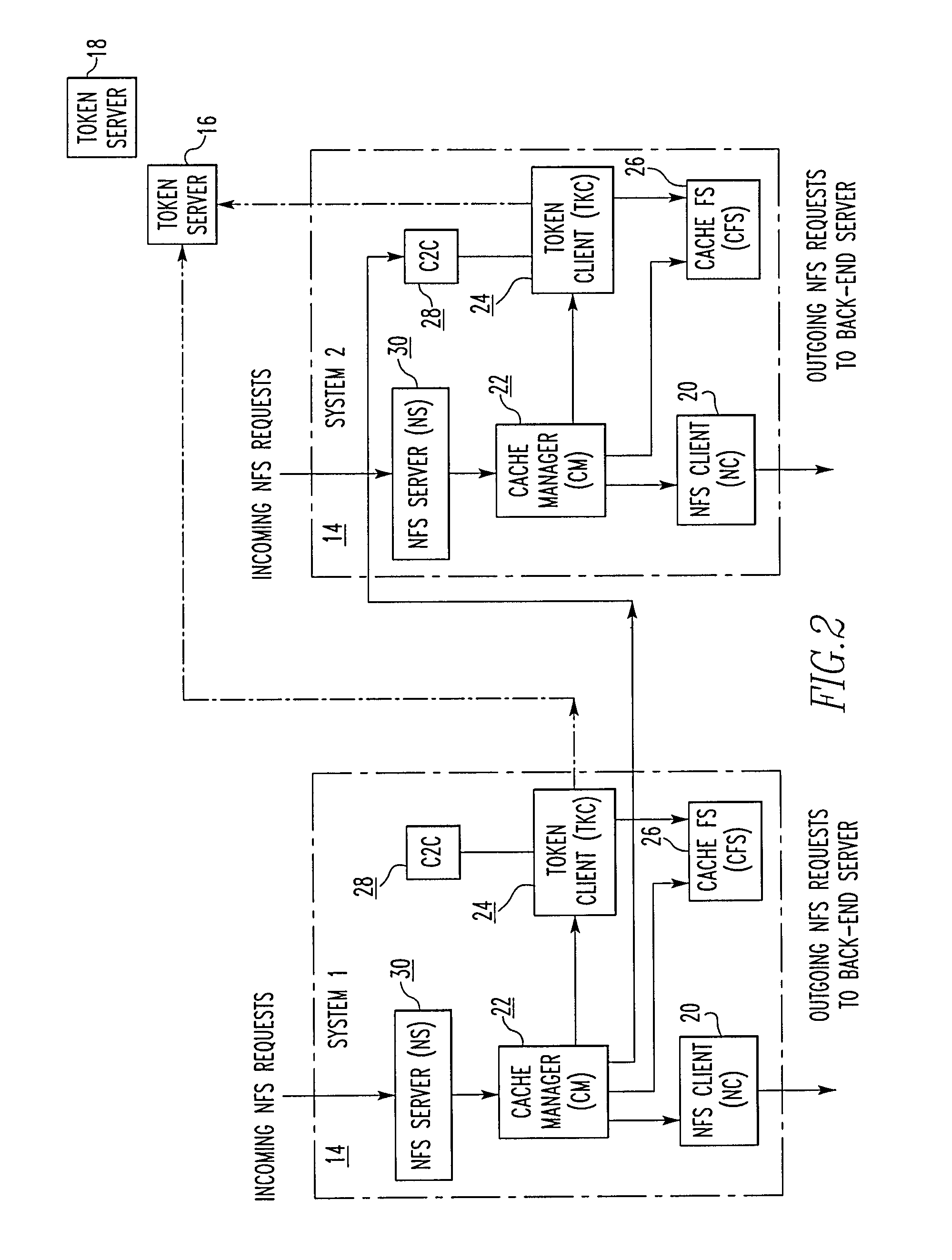
File storage system, cache appliance, and method
ActiveUS20100094806A1Increase profitLow costMemory architecture accessing/allocationDigital data processing detailsFile systemBack end server
A file storage system for storing data of a file received from a client includes a back-end file server in which the data is stored. The system includes a cache appliance in communication with the file server, such that the appliance stores portions of the data or attributes of the file, and uses the stored data or attributes to process file system requests received from the client, and which reads and writes data and attributes to the back-end file server independently. A system for responding to a file system protocol request in regard to a back-end server includes a token server. The system includes a plurality of cache appliances in communication with the token server, each of which receives tokens from the token server to synchronize access to data and attributes caches of the cache appliances, and reading and writing data and attributes to the back-end servers when tokens are revoked, the cache appliance having persistent storage in which data are stored, and the token server having persistent storage in which tokens are stored. A storage system includes a plurality of backend servers. The system includes a token server which grants permission to read and write file attributes and data system, and includes a plurality of cache appliances in communication with at least one of the backend servers and the token server for processing an incoming NFS request to the one backend server. Each cache appliance comprises an NFS server which converts incoming NFS requests into cache manager operations; a token client module in communication with the token server having a cache of tokens obtained from the token server; a cache manager that caches data and attributes and uses tokens from the token client module to ensure that the cached data or attributes are the most recent data or attributes, and an NFS client which sends outgoing NFS requests to the back-end file server. Methods for storing data of a file received from a client.
Owner:MICROSOFT TECH LICENSING LLC
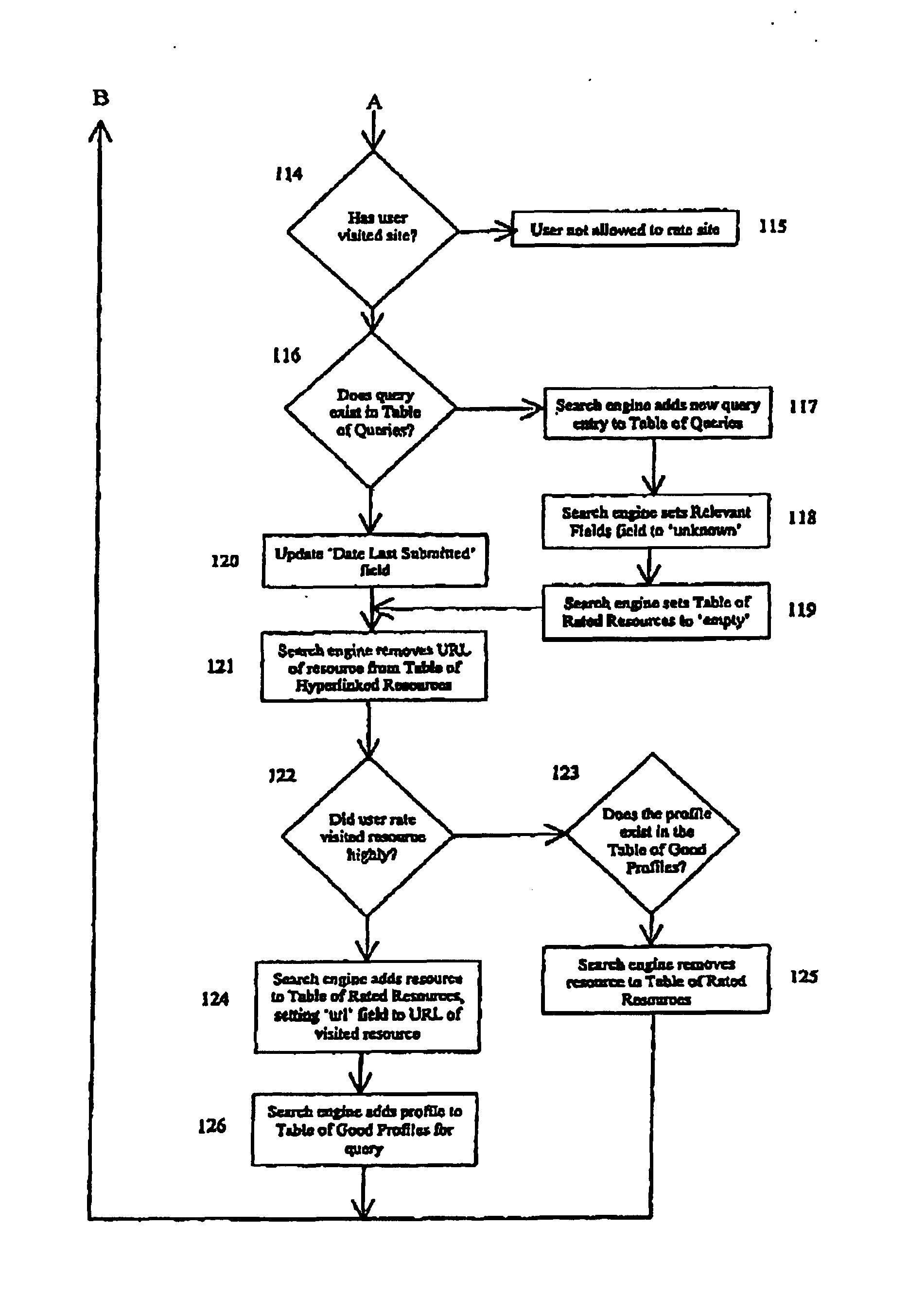
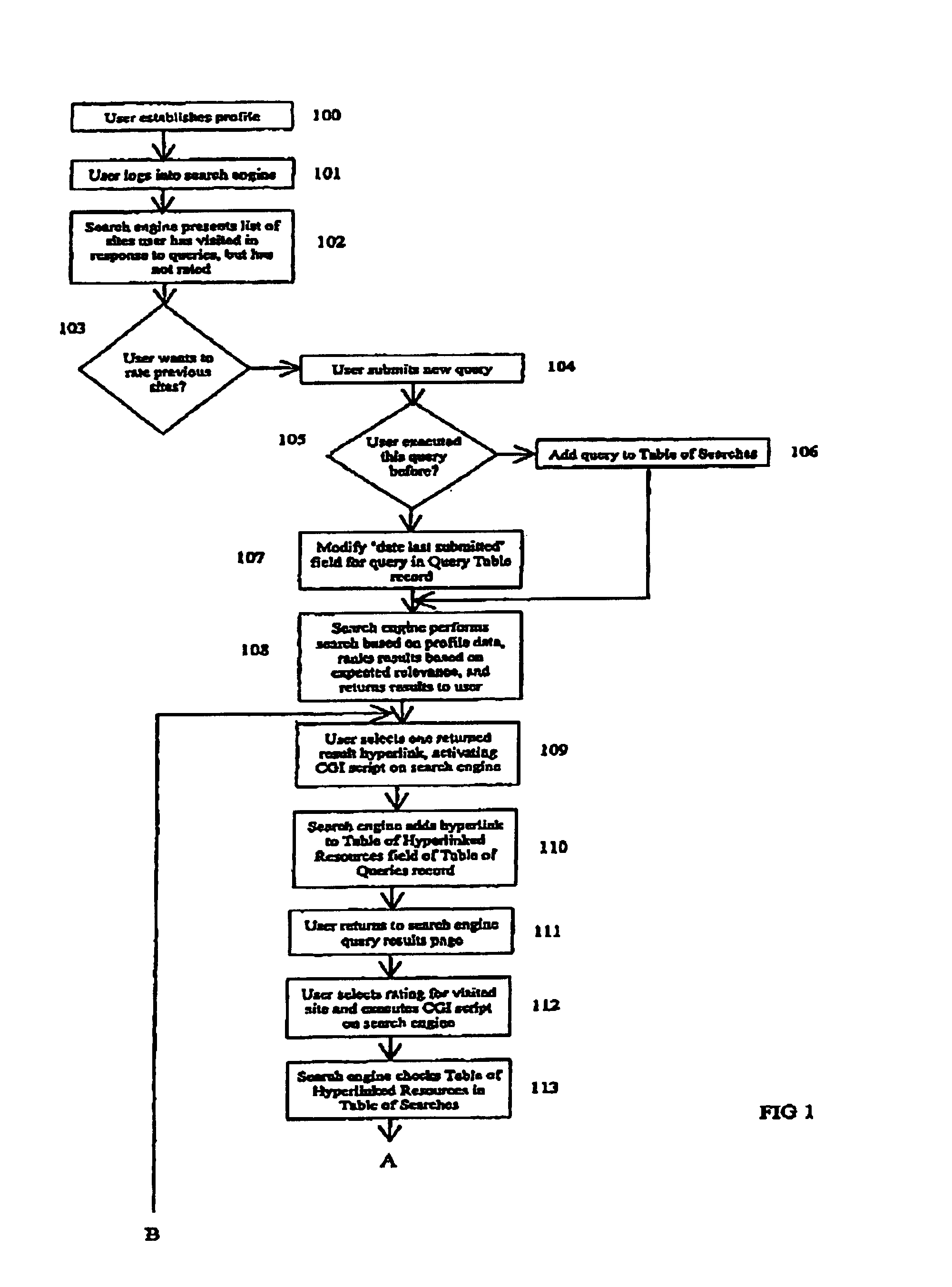
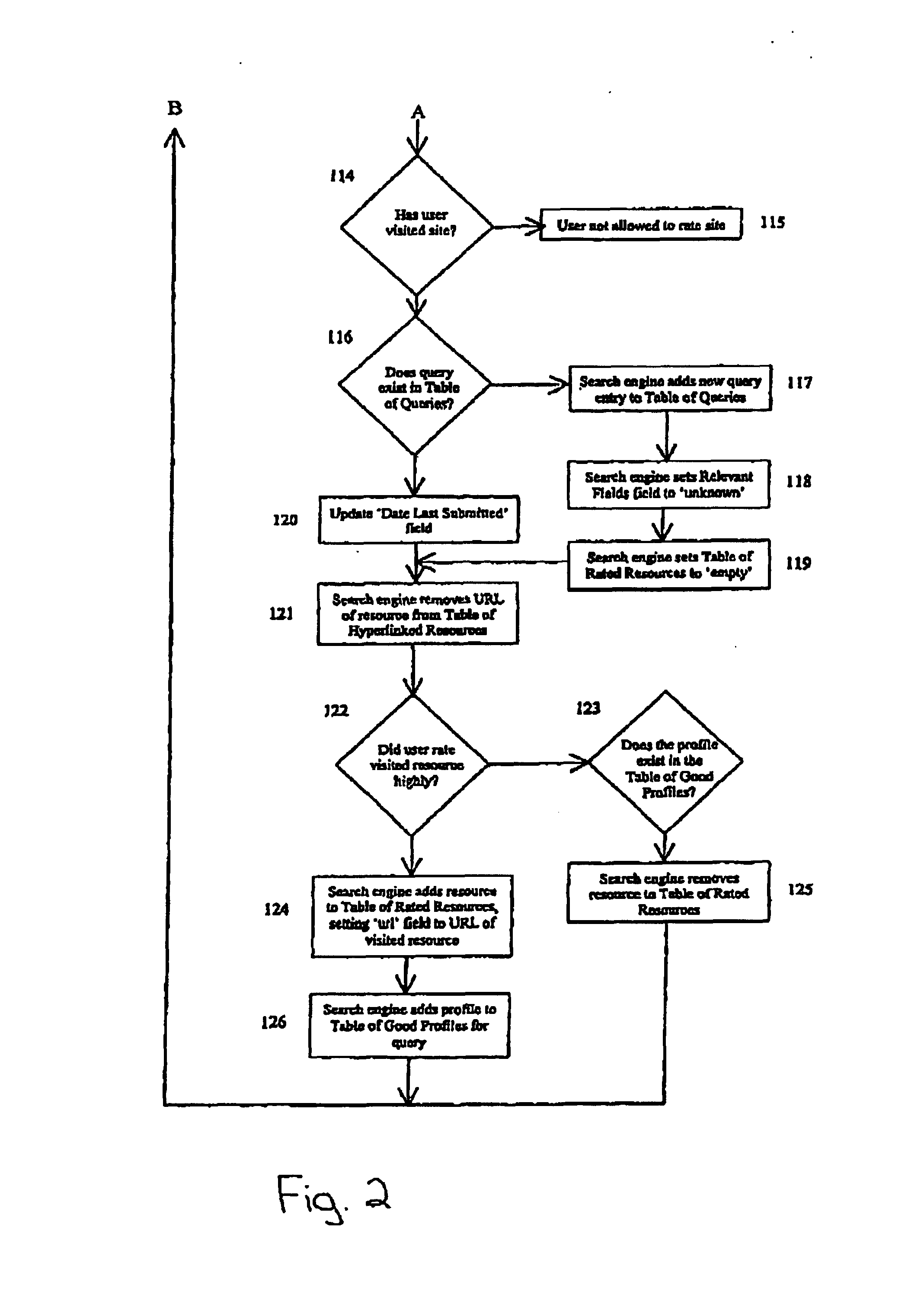
Process for improving search engine efficiency using feedback
InactiveUS7072888B1Increased its relevancyIncreasing potential relevancyData processing applicationsDigital data information retrievalUniform resource locatorInternet search engines
A process for refining the results of a query to an internet search engine database by the use of user feedback is disclosed. It is a method to allow a user to rate the relevancy of URLs returned for a specific query. The relevancy ratings for a specific query are combined by the internet search engine with data from a user profile of personal information defined by the user. The internet search engine can determine which items of data in the profile are common between users who have rated a query result highly. The search engine can then modify the search algorithm to return those URLs rated highly by users with common profile attributes. The benefit to the internet is more efficient searching and retrieval of information for users.
Owner:TRIOGO
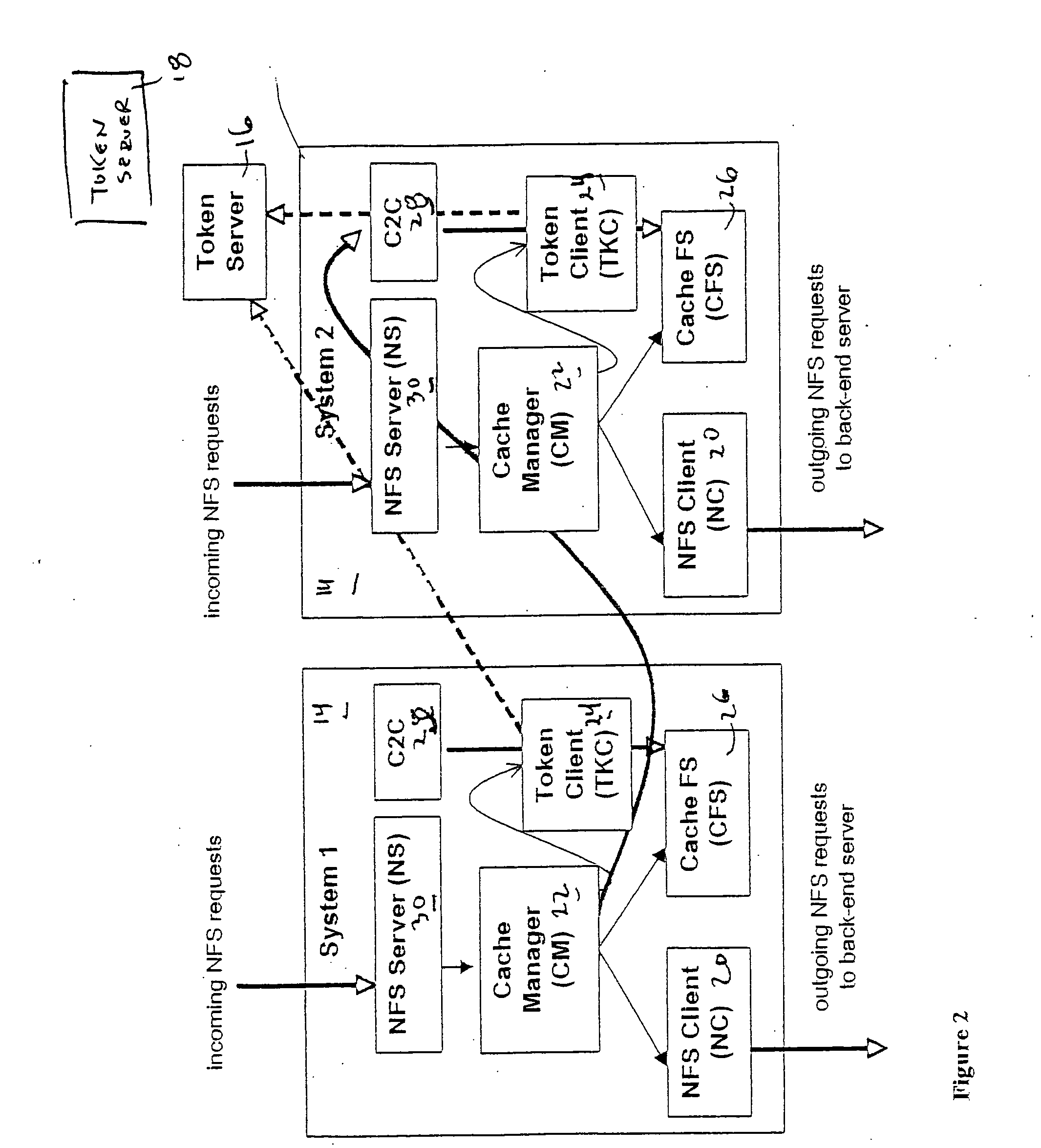
File storage system, cache appliance, and method
ActiveUS9323681B2Avoid the needMemory architecture accessing/allocationDigital data processing detailsFile systemBack end server
A file storage system for storing data of a file received from a client includes a back-end file server in which the data is stored. The system includes a cache appliance in communication with the file server, such that the appliance stores portions of the data or attributes of the file, and uses the stored data or attributes to process file system requests received from the client, and which reads and writes data and attributes to the back-end file server independently. A system for responding to a file system protocol request in regard to a back-end server includes a token server. The system includes a plurality of cache appliances in communication with the token server, each of which receives tokens from the token server to synchronize access to data and attributes caches of the cache appliances, and reading and writing data and attributes to the back-end servers when tokens are revoked, the cache appliance having persistent storage in which data are stored, and the token server having persistent storage in which tokens are stored. A storage system includes a plurality of backend servers. The system includes a token server which grants permission to read and write file attributes and data system, and includes a plurality of cache appliances in communication with at least one of the backend servers and the token server for processing an incoming NFS request to the one backend server. Each cache appliance comprises an NFS server which converts incoming NFS requests into cache manager operations; a token client module in communication with the token server having a cache of tokens obtained from the token server; a cache manager that caches data and attributes and uses tokens from the token client module to ensure that the cached data or attributes are the most recent data or attributes, and an NFS client which sends outgoing NFS requests to the back-end file server. Methods for storing data of a file received from a client.
Owner:MICROSOFT TECH LICENSING LLC
Rule driven automation of file placement, replication, and migration
InactiveUS20070022129A1Digital data information retrievalData processing applicationsDriving automationFile copying
Owner:PARASCALE
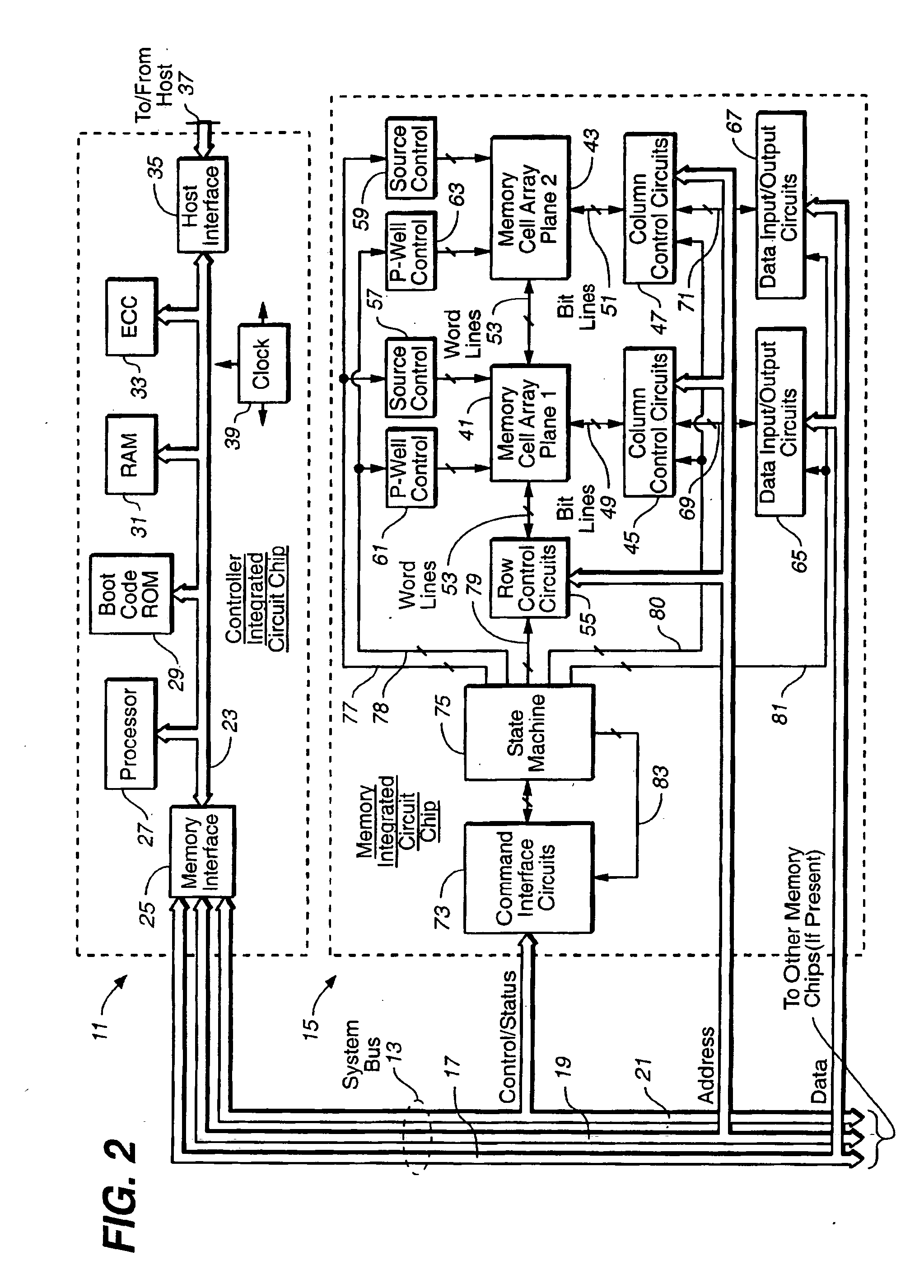
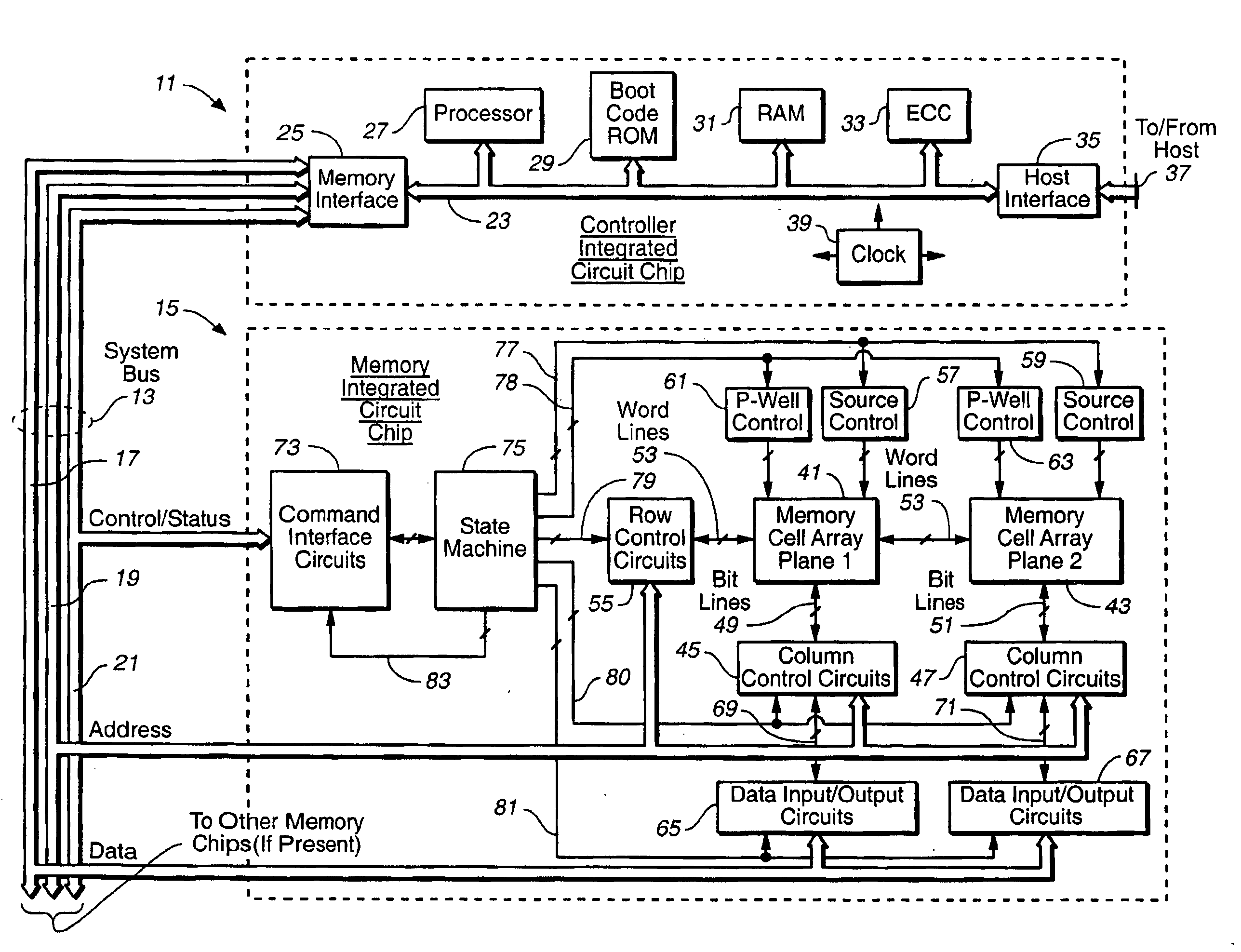
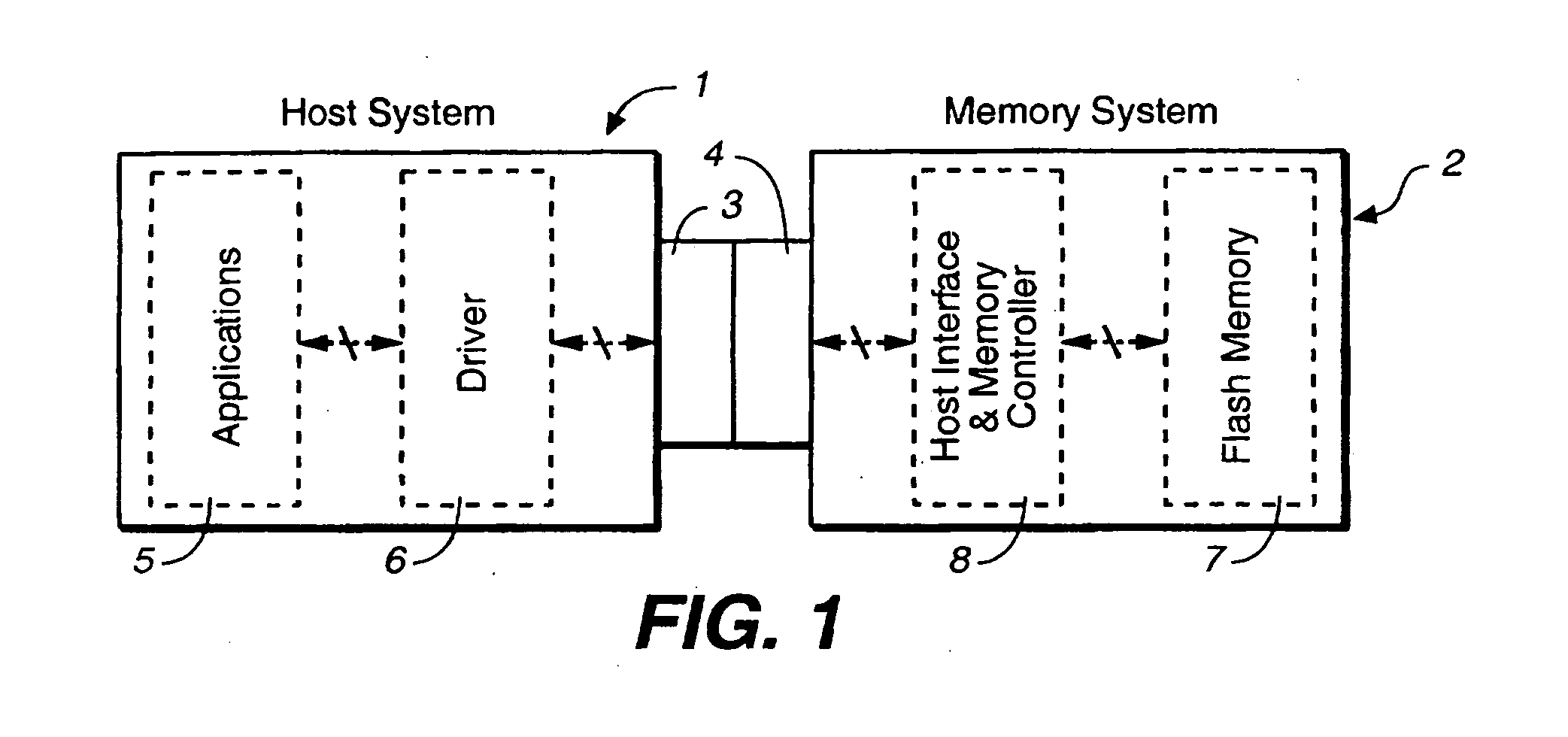
Methods for adaptive file data handling in non-volatile memories with a directly mapped file storage system
InactiveUS20070143561A1Promote high performanceImprove performanceMemory systemsData compressionWaste collection
In a memory system with a file storage system, an optimal file handling scheme is adaptively selected from a group thereof based on the attributes of the file being handled. The file attributes may be obtained from a host or derived from a history of the file had with the memory system. In one embodiment, a scheme for allocating memory locations for a write operation is dependent on an estimated size of the file to be written. In another embodiment, a scheme for allocating memory locations for a relocation operation, such as for garbage collection or data compaction, is dependent on an estimated access frequency of the file in question. In this way, the optimal handling scheme can be used for the particular file at any time.
Owner:SANDISK TECH LLC
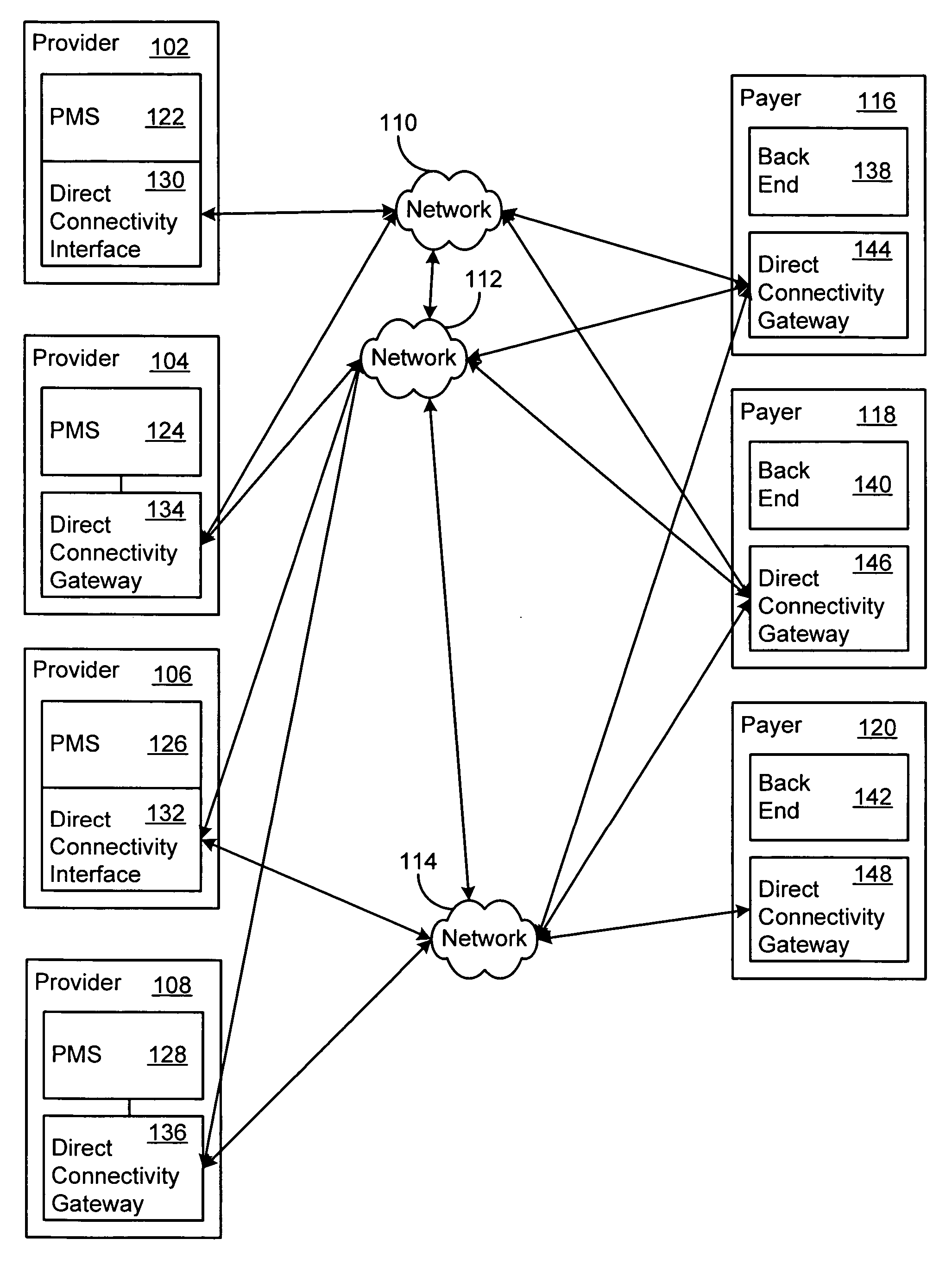
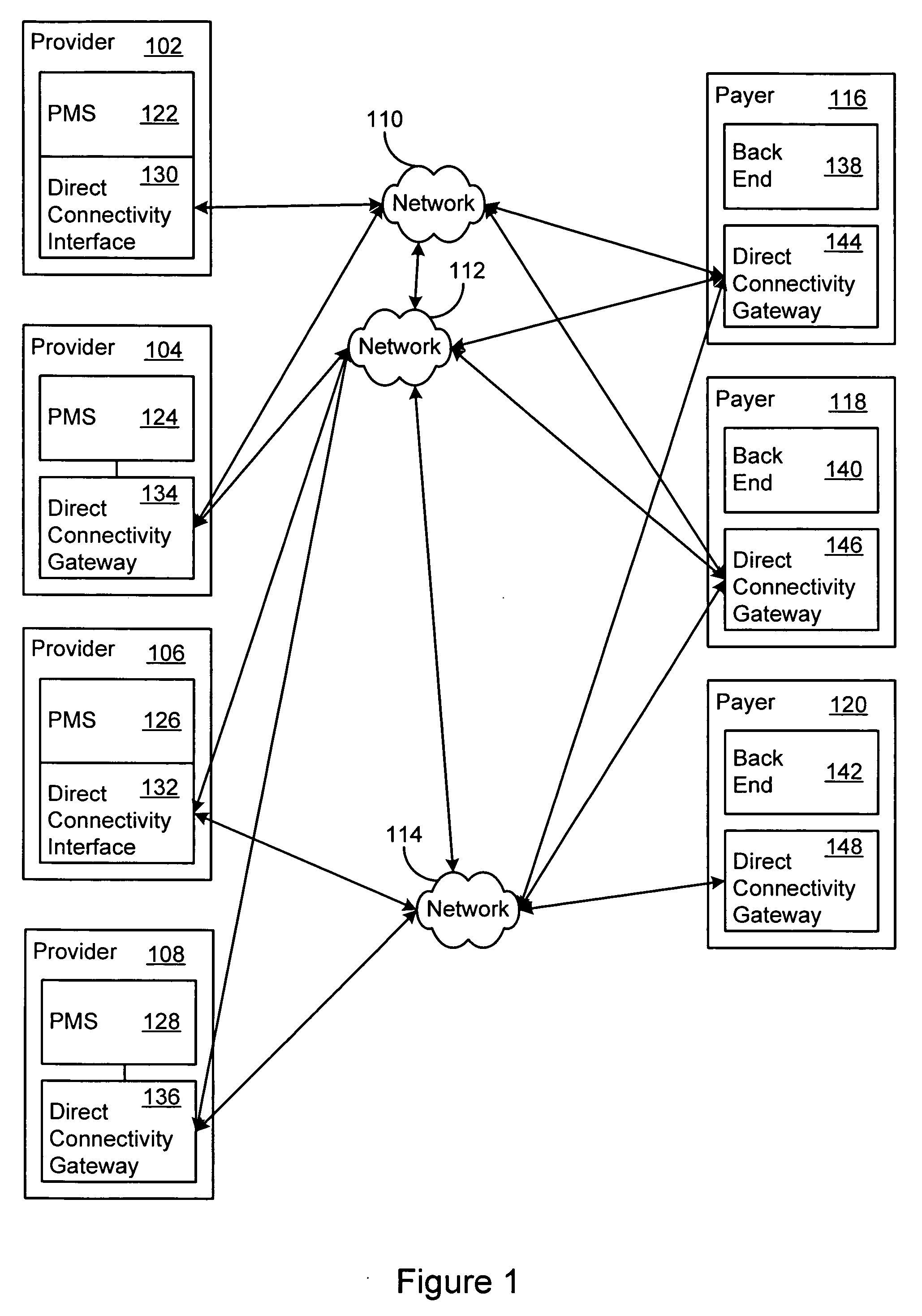
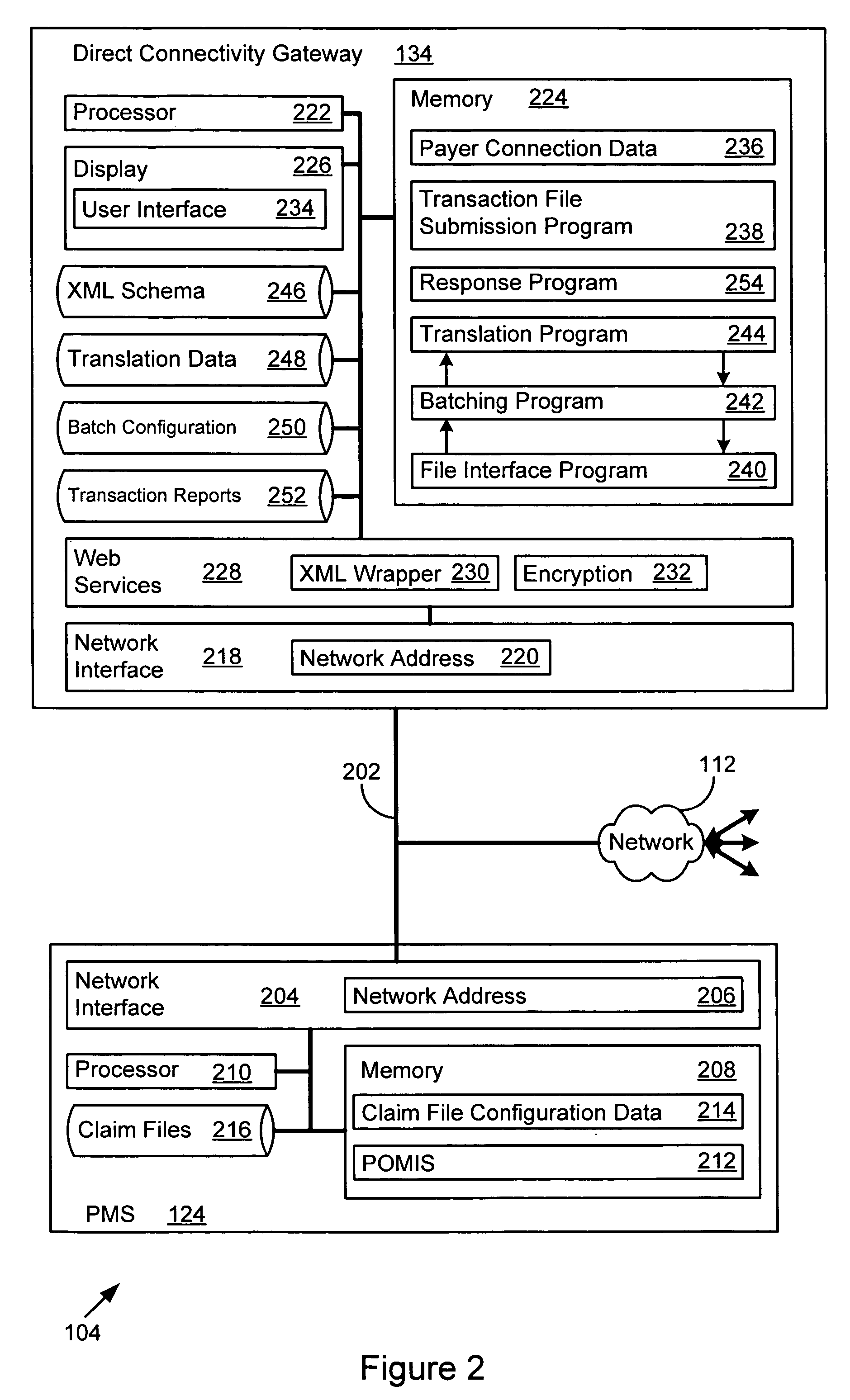
Direct connectivity system for healthcare administrative transactions
A direct connectivity system provides automated healthcare administrative transaction submission, including claim submission, eligibility verification and claim status, from healthcare service providers directly to payers. The direct connectivity system bypasses transaction processing intermediaries such as clearinghouses by directly connecting providers to payers in a many to many manner. Existing single payer web portals are supplanted by a many to many network that has a common interface across multiple payers. The direct connectivity system may receive responses directly from payers and may prepare or process the responses for a practice management program so that the service provider receives rapid feedback on the administrative transaction submission. The direct connectivity system may automatically analyze transaction file attributes to determine one or more of many payers to which to send a transaction file, from one of many providers. Batch and singleton file transfer is supported for multiple file formats, optionally with secure file transfer.
Owner:ACCENTURE GLOBAL SERVICES LTD
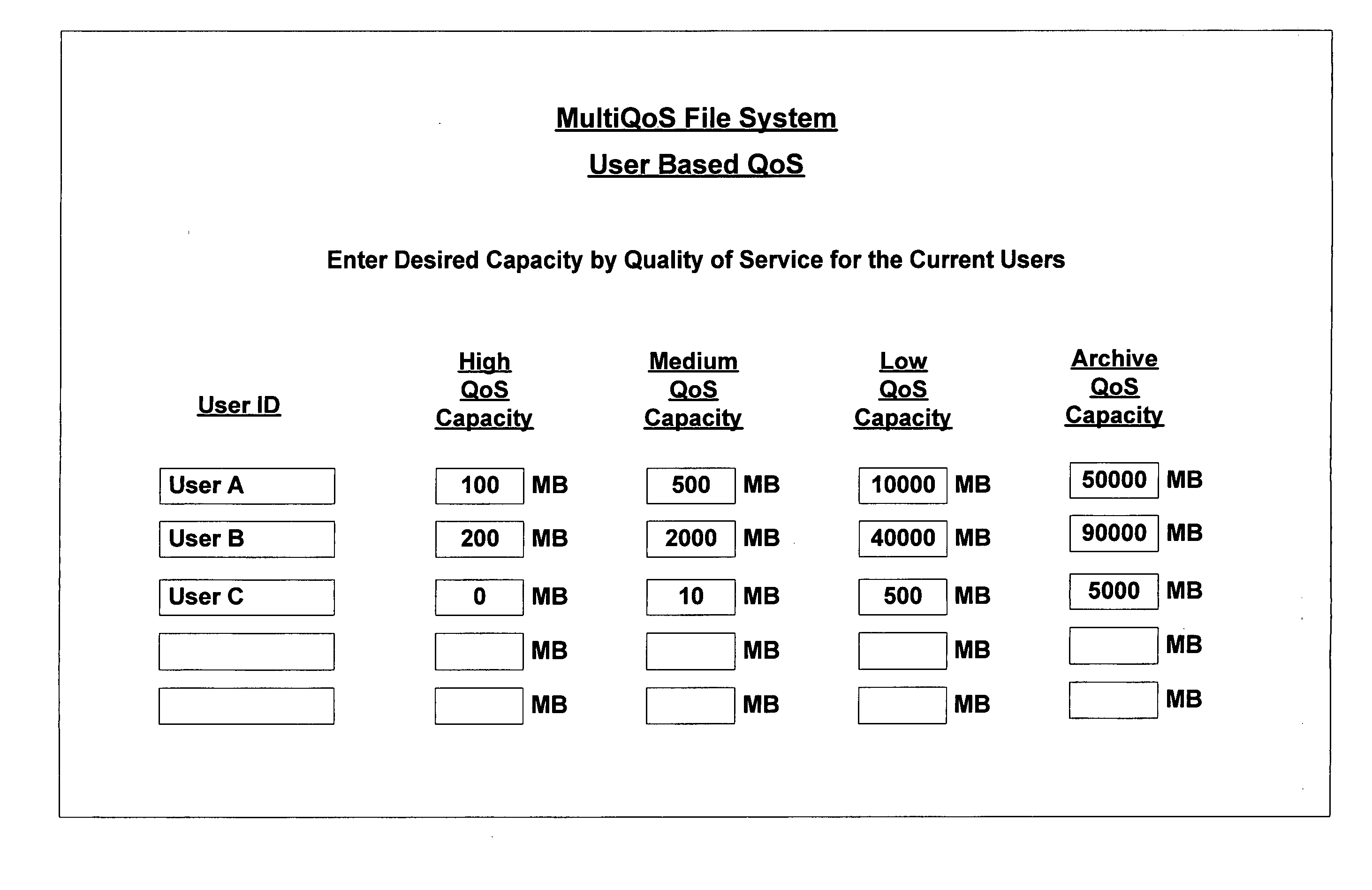
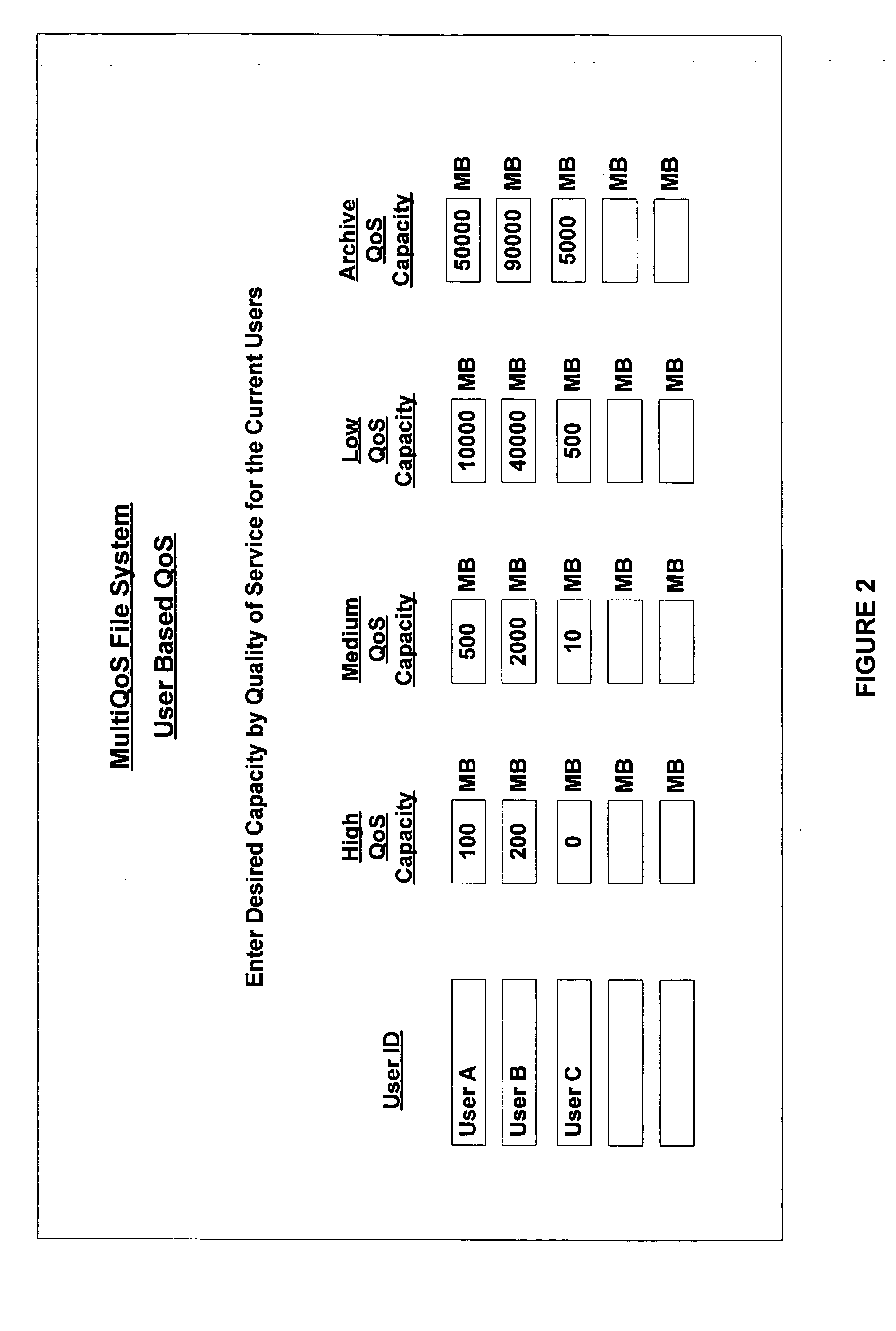
Multiple quality of service file system
InactiveUS20070083482A1Enhances descriptive informationIncreasing the IT administrator workloadDigital data information retrievalSpecial data processing applicationsQuality of serviceFile system
The invention relates to a multiple QoS file system and methods of processing files at different QoS according to rules. The invention allocates multiple VLUNs at different qualities of service to the multiQoS file system. Using the rules, the file system chooses an initial QoS for a file when created. Thereafter, the file system moves files to different QoS using rules. Users of the file system see a single unified space of files, while administrators place files on storage with the new cost and performance according to attributes of the files. A multiQoS file system enhances the descriptive information for each file to contain the chosen QoS for the file.
Owner:PILLAR DATA SYSTEMS
Heuristic malware detection
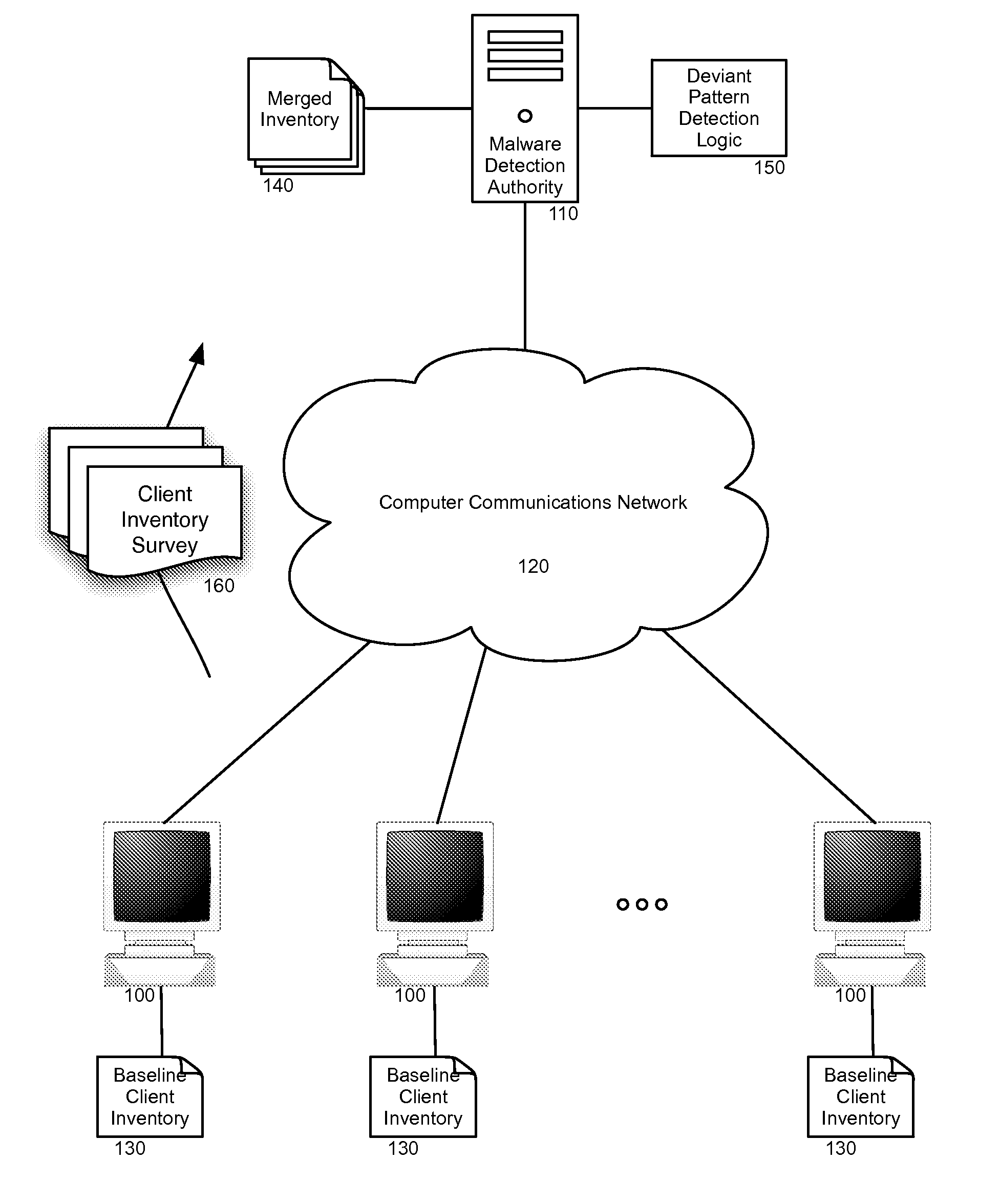
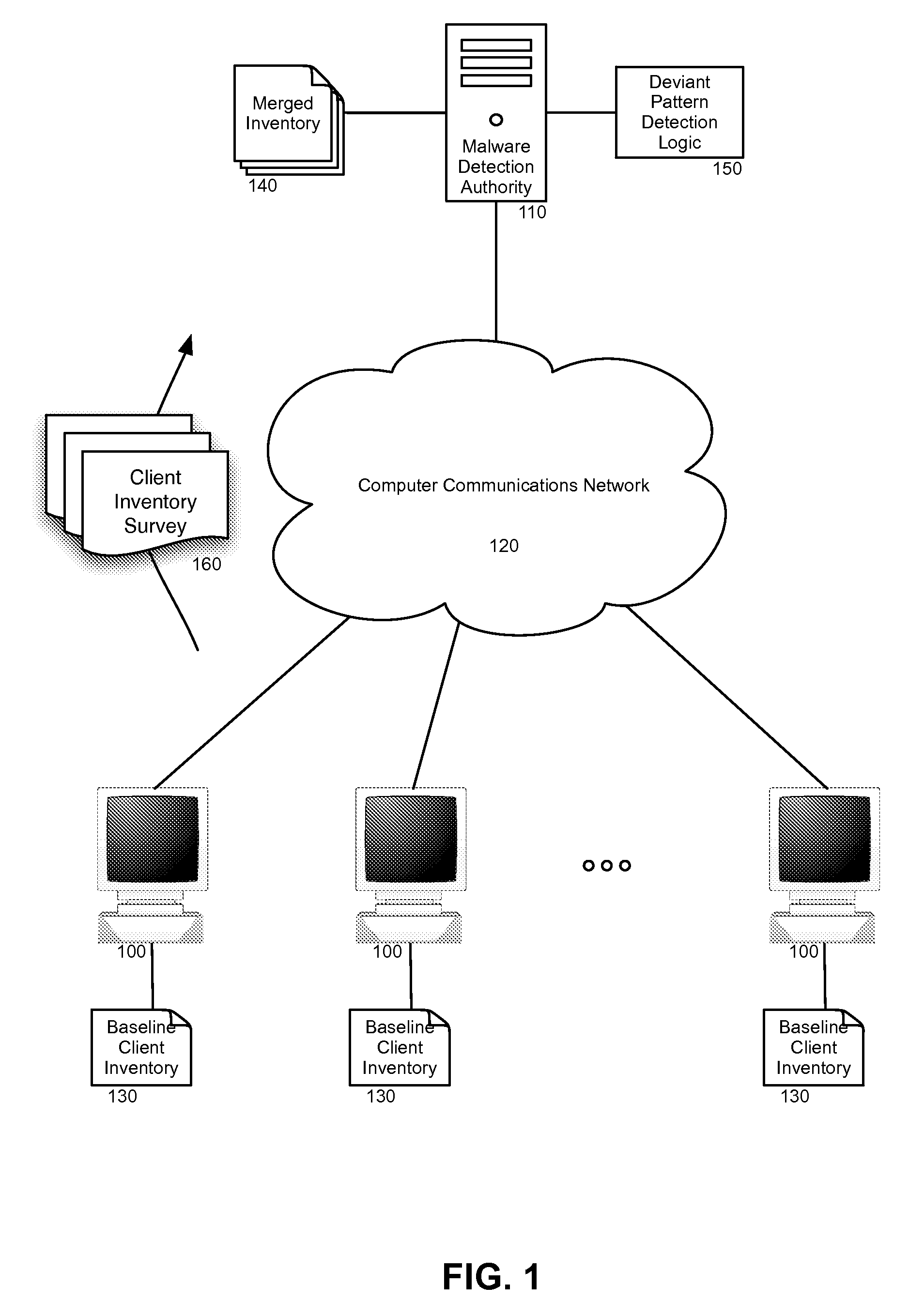
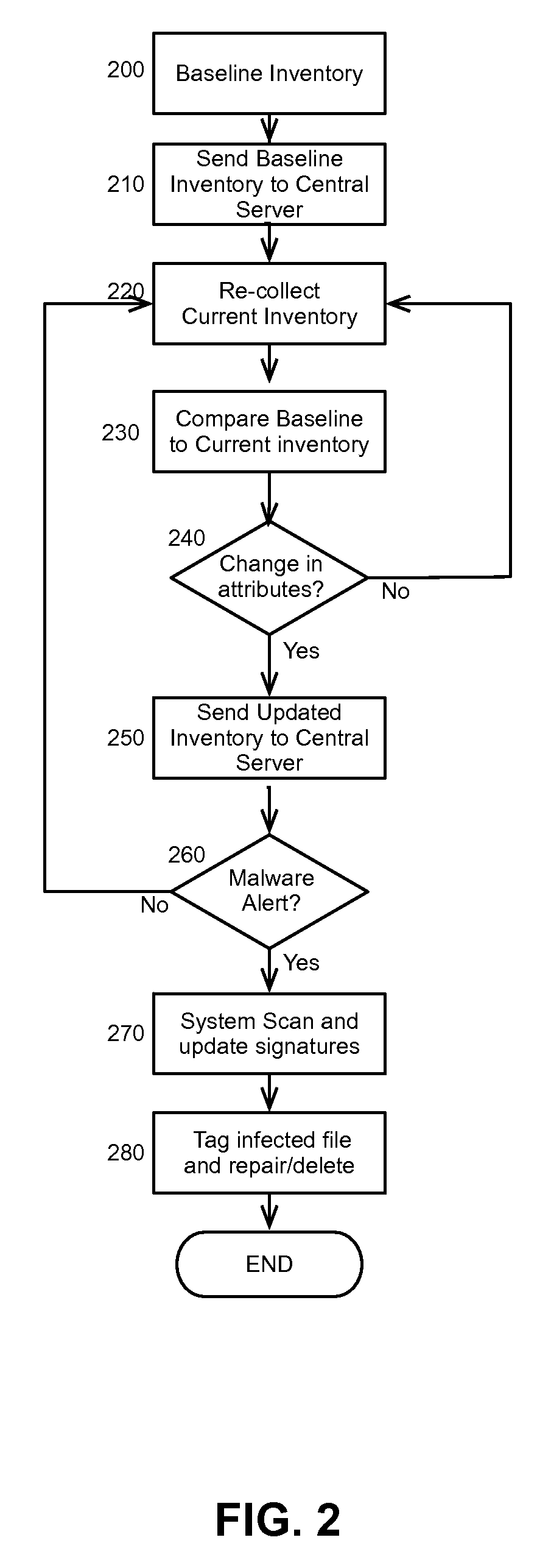
Embodiments of the present invention provide a method, system and computer program product for the heuristic malware detection. In one embodiment of the invention, a heuristic malware detection method can include merging a baseline inventory of file attributes for respective files from each client computing system in a community of client computing systems into a merged inventory. The method further can include receiving an updated inventory of file attributes in a current inventory survey from different ones of the client computing systems. Each received survey can be compared to the merged inventory, and in response to the comparison, a deviant pattern of file attribute changes can be detected in at least one survey for a corresponding client computing system. Thereafter, the deviant pattern can be classified as one of a benign event or a malware attack. Finally, malware removal can be requested in the corresponding client computing system if the deviant pattern is classified as a malware attack.
Owner:LENOVO GLOBAL TECH INT LTD
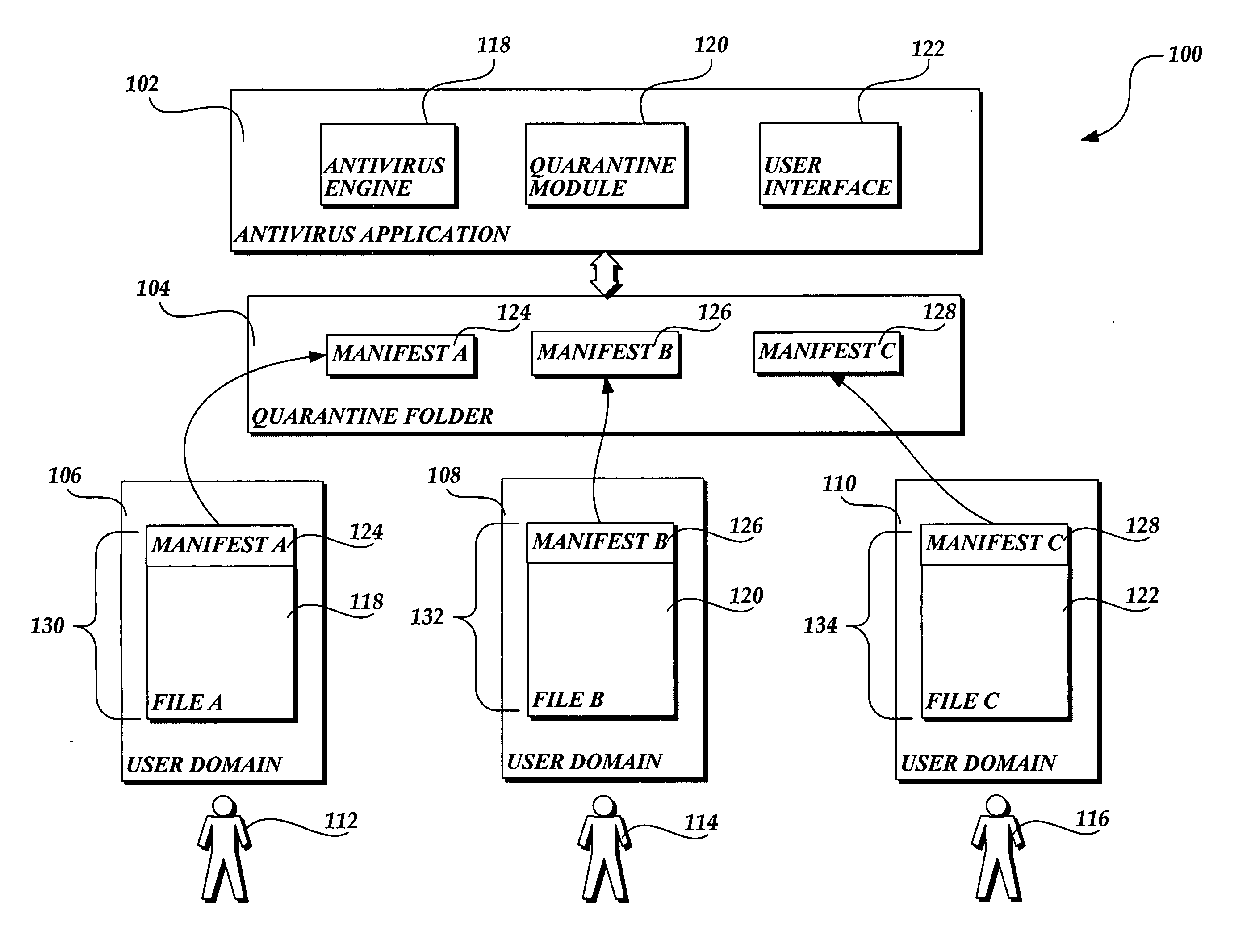
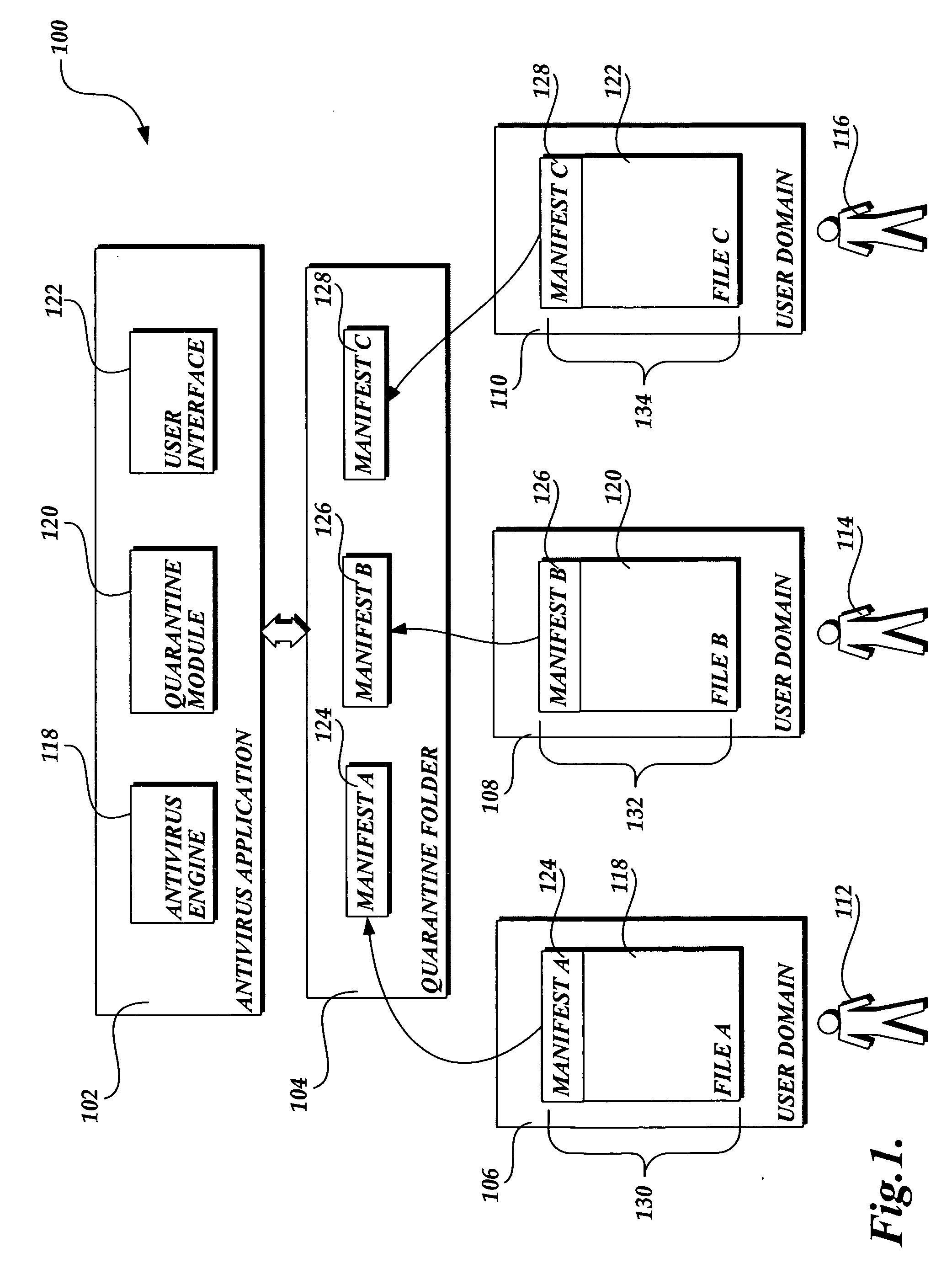
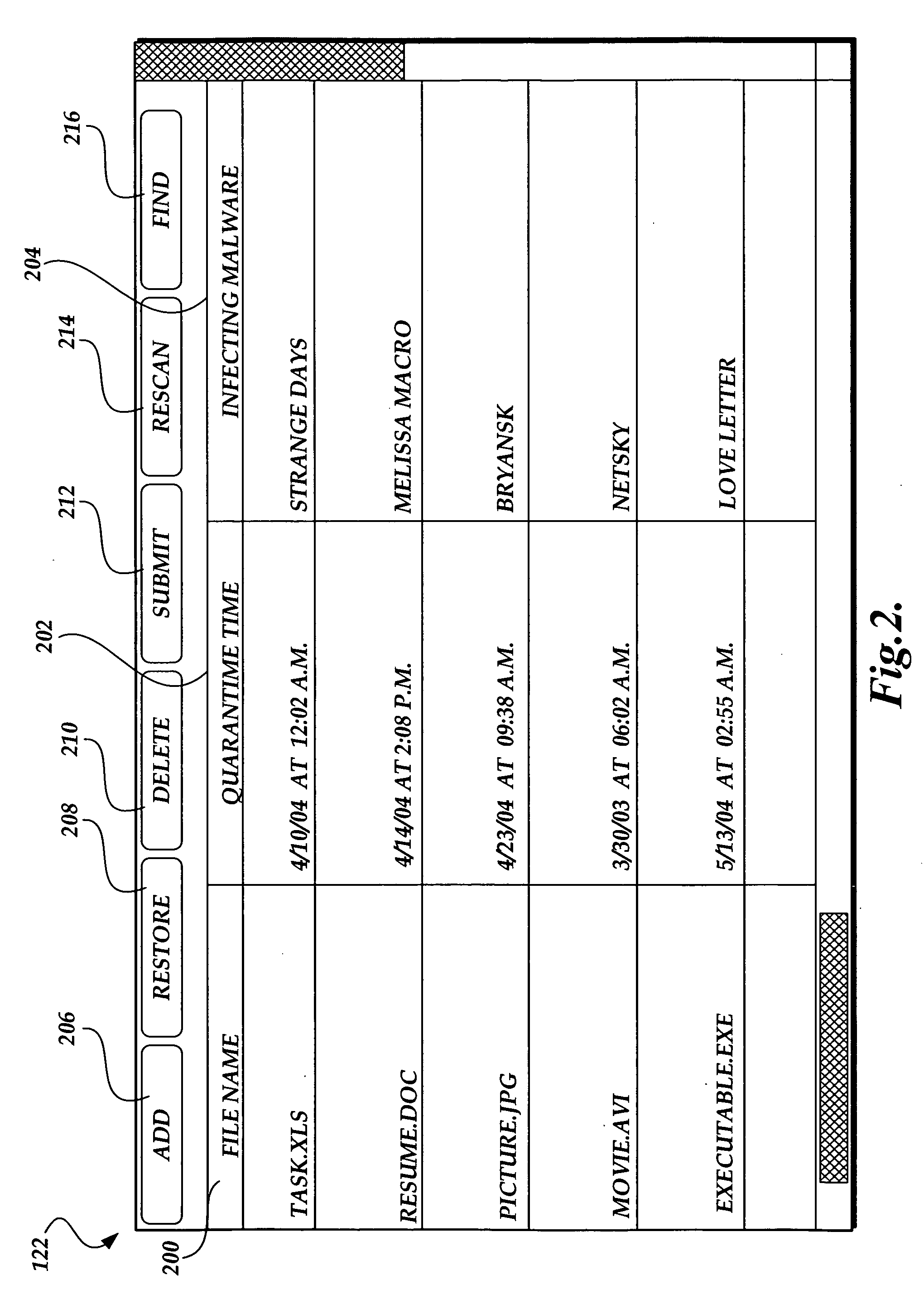
Privacy friendly malware quarantines
The present invention provides a system, method, and computer-readable medium for quarantining a file. Embodiments of the present invention are included in antivirus software that maintains a user interface. From the user interface, a user may issue a command to quarantine a file or the quarantine process may be initiated automatically by the antivirus software after malware is identified. When a file is marked for quarantine, aspects of the present invention encode file data with a function that is reversible. Then a set of metadata is identified that describes attributes of the file including any heightened security features that are used to limit access to the file. The metadata is moved to a quarantine folder, while the encoded file remains at the same location in the file system. As a result, the encoded file maintains the same file attributes as the original, non-quarantined file, including any heightened security features.
Owner:MICROSOFT TECH LICENSING LLC
Non-volatile memories with adaptive file handling in a directly mapped file storage system
InactiveUS20070143378A1Promote high performanceImprove performanceMemory architecture accessing/allocationSpecial data processing applicationsData compressionAccess frequency
In a memory system with a file storage system, an optimal file handling scheme is adaptively selected from a group thereof based on the attributes of the file being handled. The file attributes may be obtained from a host or derived from a history of the file had with the memory system. In one embodiment, a scheme for allocating memory locations for a write operation is dependent on an estimated size of the file to be written. In another embodiment, a scheme for allocating memory locations for a relocation operation, such as for garbage collection or data compaction, is dependent on an estimated access frequency of the file in question. In this way, the optimal handling scheme can be used for the particular file at any time.
Owner:SANDISK TECH LLC
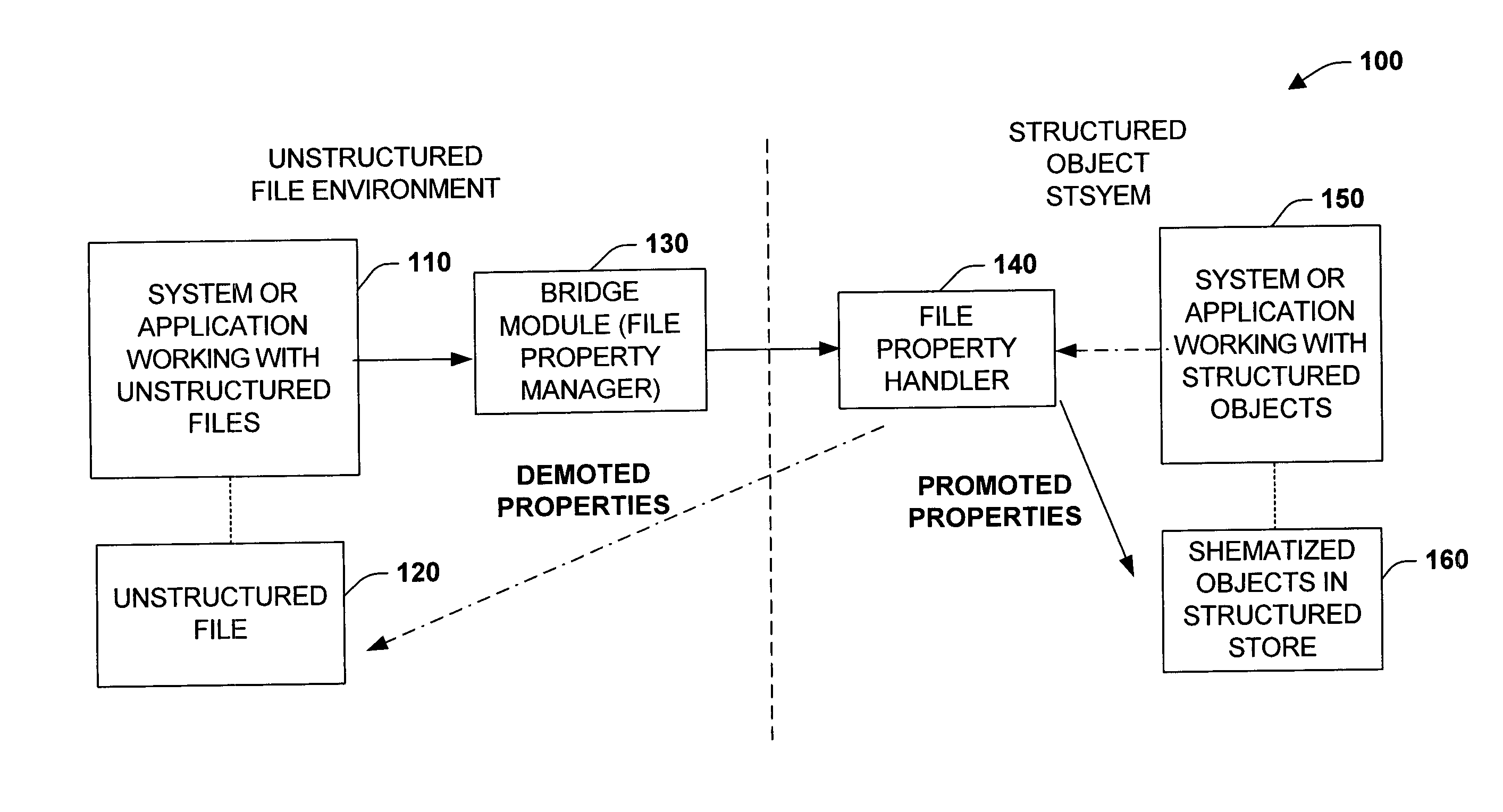
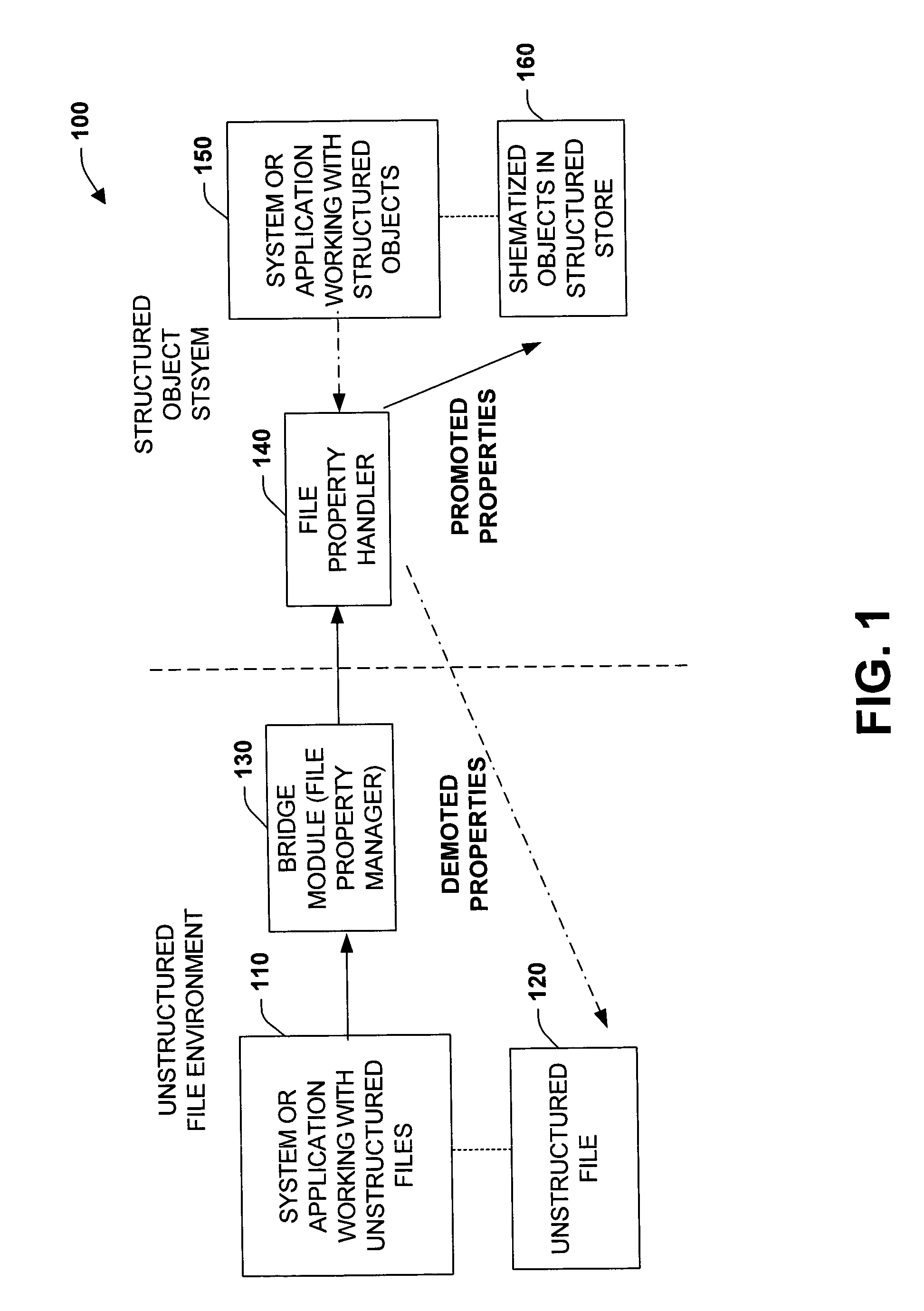
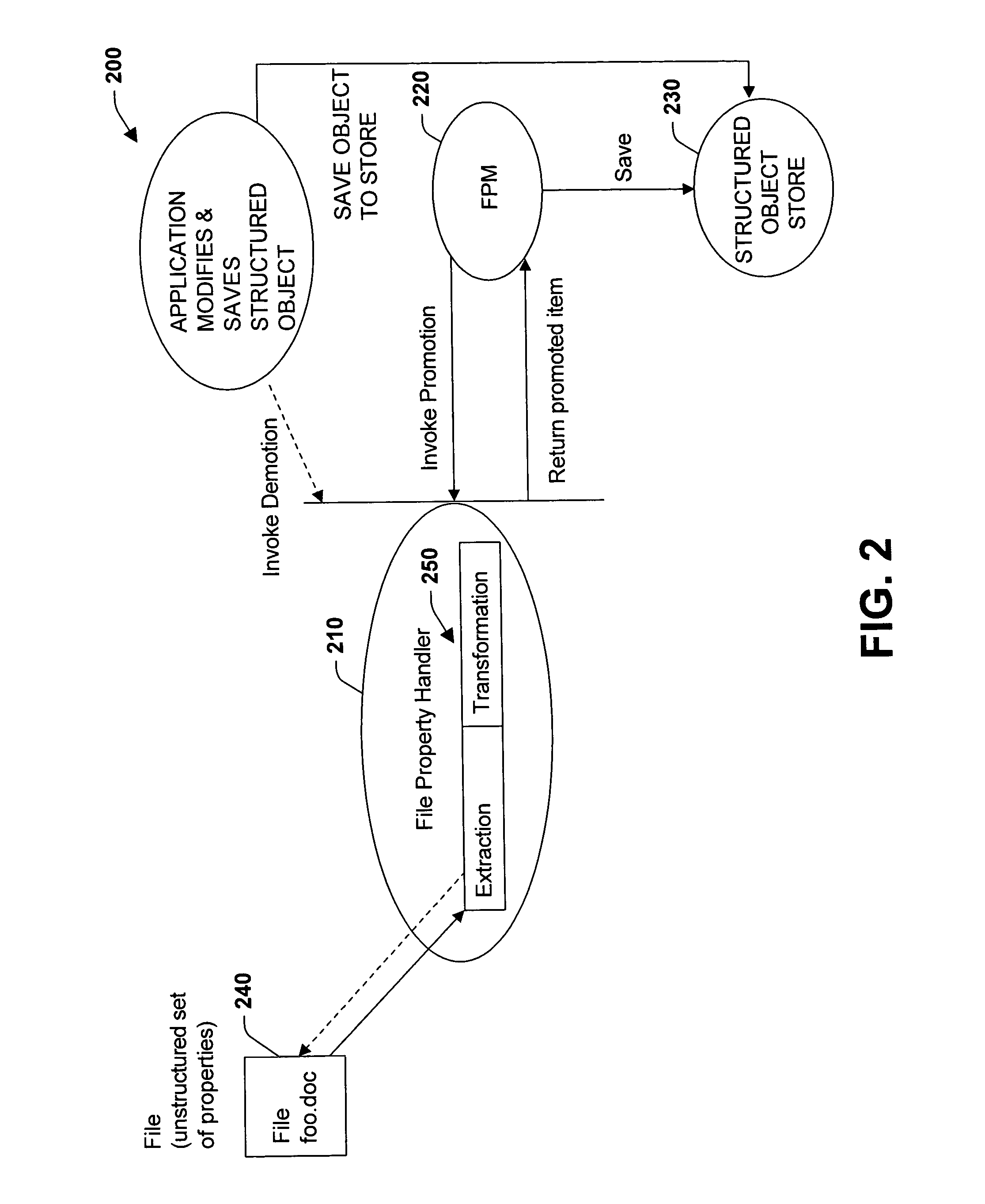
Promotion and demotion techniques to facilitate file property management between object systems
ActiveUS20050091285A1Facilitate file manipulationAchieve consistencyAcutation objectsData processing applicationsComputer compatibilityObject store
The present invention relates to a system and methodology to facilitate interoperability and compatibility between disparate data systems. In one aspect, a file transformation system is provided having at least one file associated with one or more unstructured properties. A file property handler manipulates the unstructured properties in accordance with one or more structured properties associated with a structured object store environment. If an unstructured file is to be operated in the context of a structured object store environment, a promotion operation is performed to update unstructured properties in the file with structured properties suitable for operation in the structured object store environment. If a promoted item were to be manipulated in the structured object store environment, a demotion operation or reverse transformation is performed to update properties in the file.
Owner:MICROSOFT TECH LICENSING LLC
Accumulating access frequency and file attributes for supporting policy based storage management
ActiveUS20070136308A1Digital data information retrievalDigital data processing detailsAccess frequencyStorage management
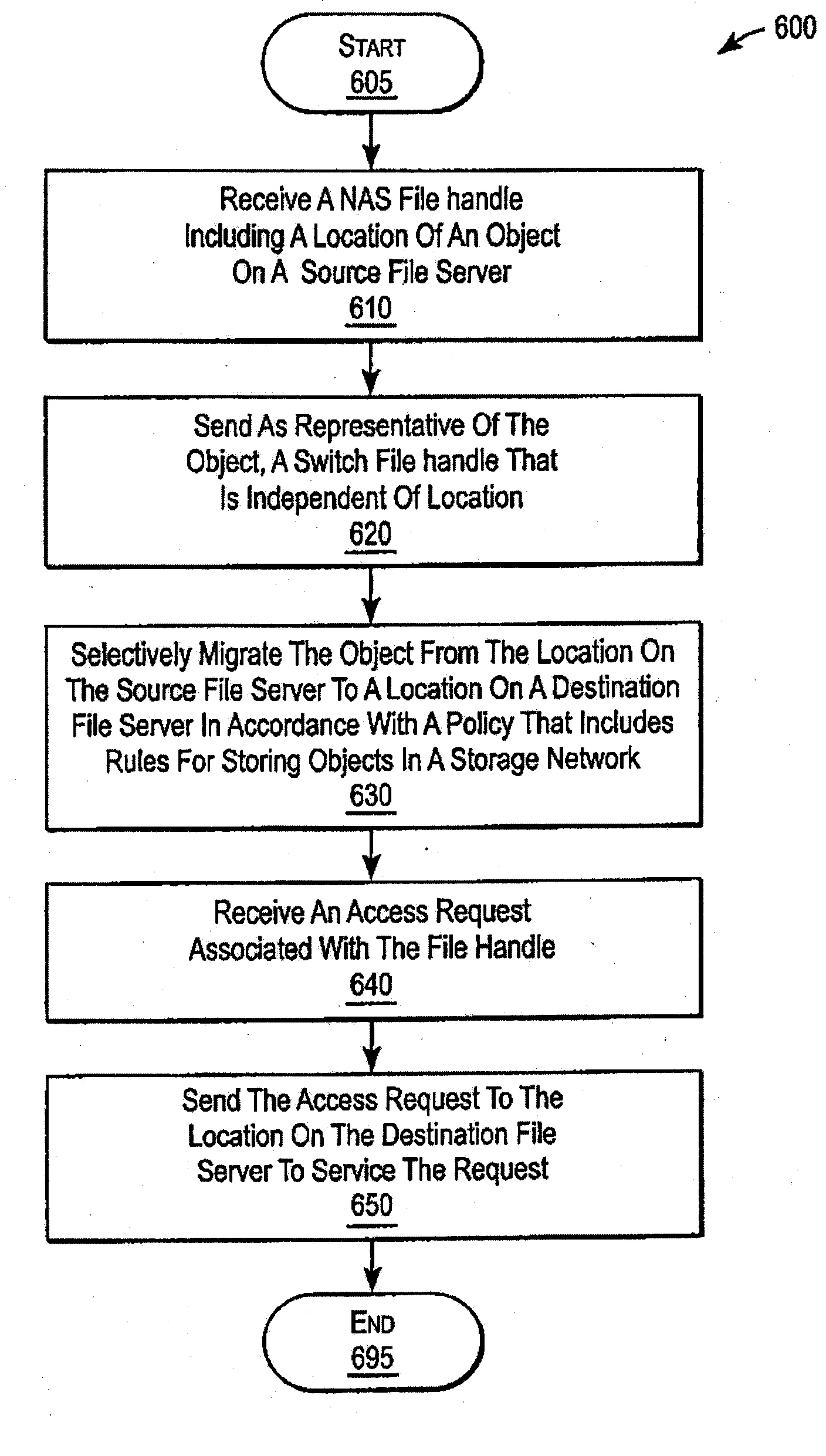
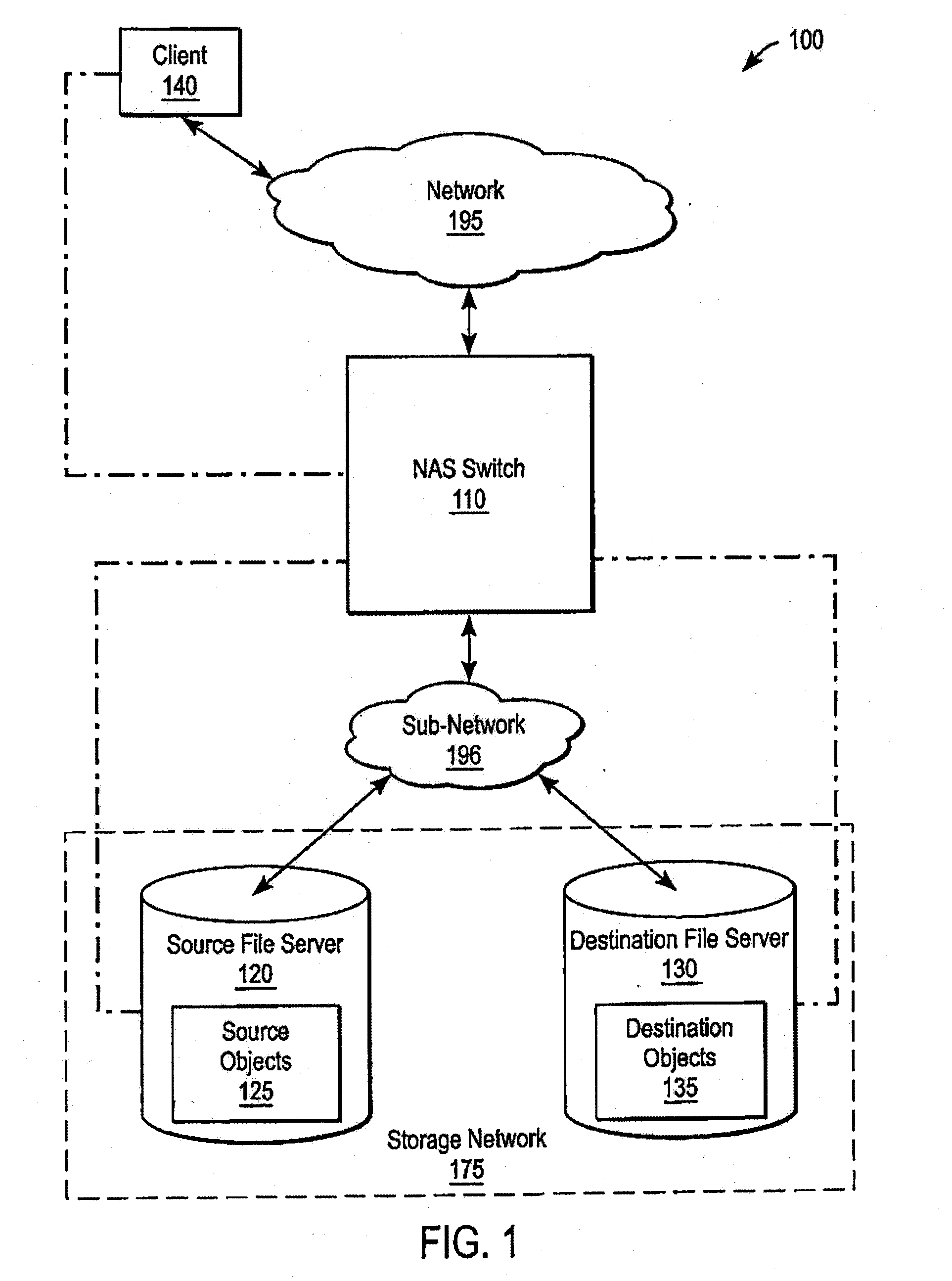
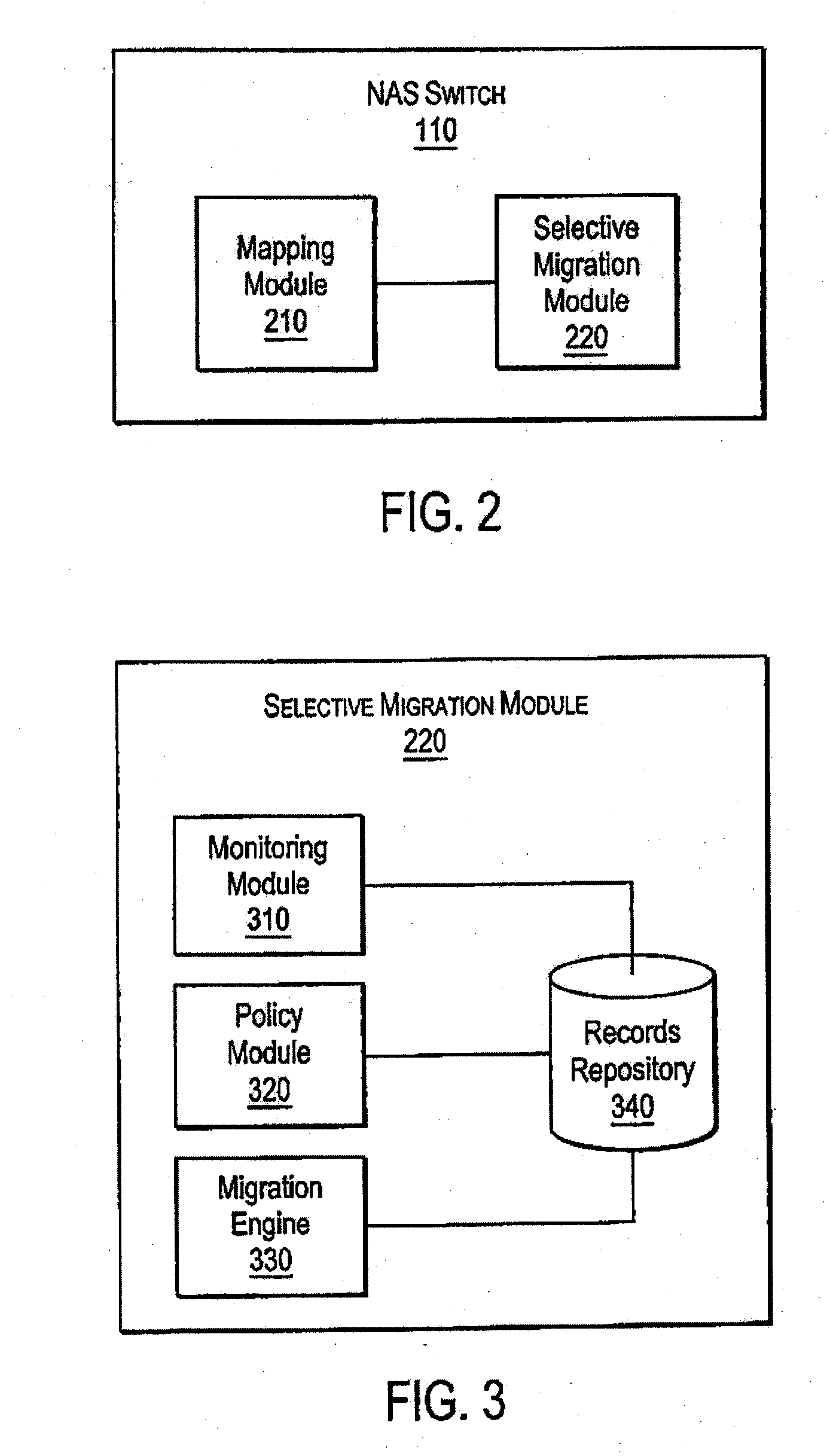
A system and method for performing policy-based storage management using data related to access frequency and file attribute accumulation. A switch device provides transparency for transactions between a client and a storage network. The transparency allows objects (e.g., files or directories) to be moved (e.g., migrated) on the storage network without affecting a reference to the object used by the client (e.g., a file handle). A monitoring module generates accumulation data associated with the transactions for use in policy-based management. The accumulation data can describe uses of the file such as how often certain files are accessed, modifications to files such as creations of new directories or files, and other uses.
Owner:CISCO TECH INC
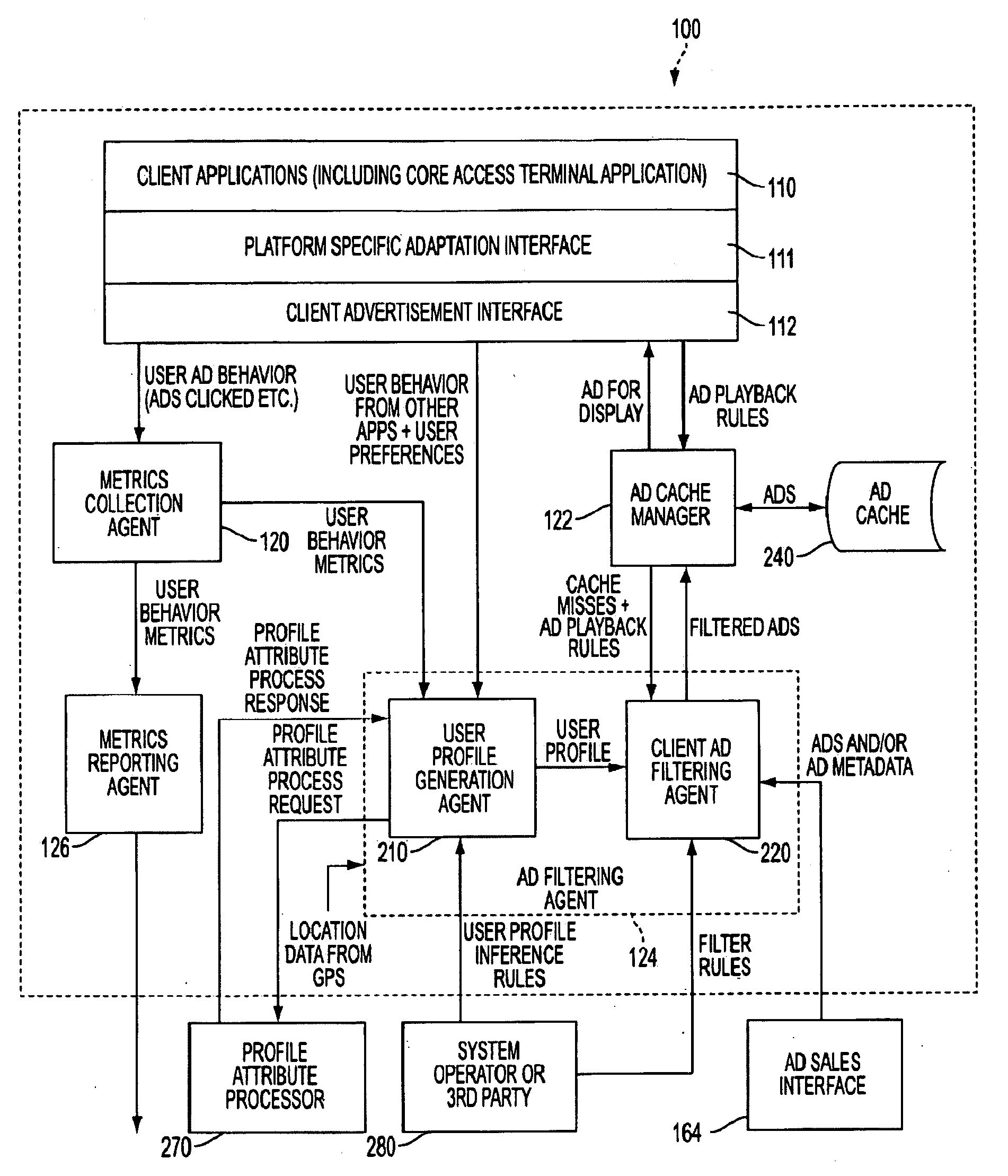
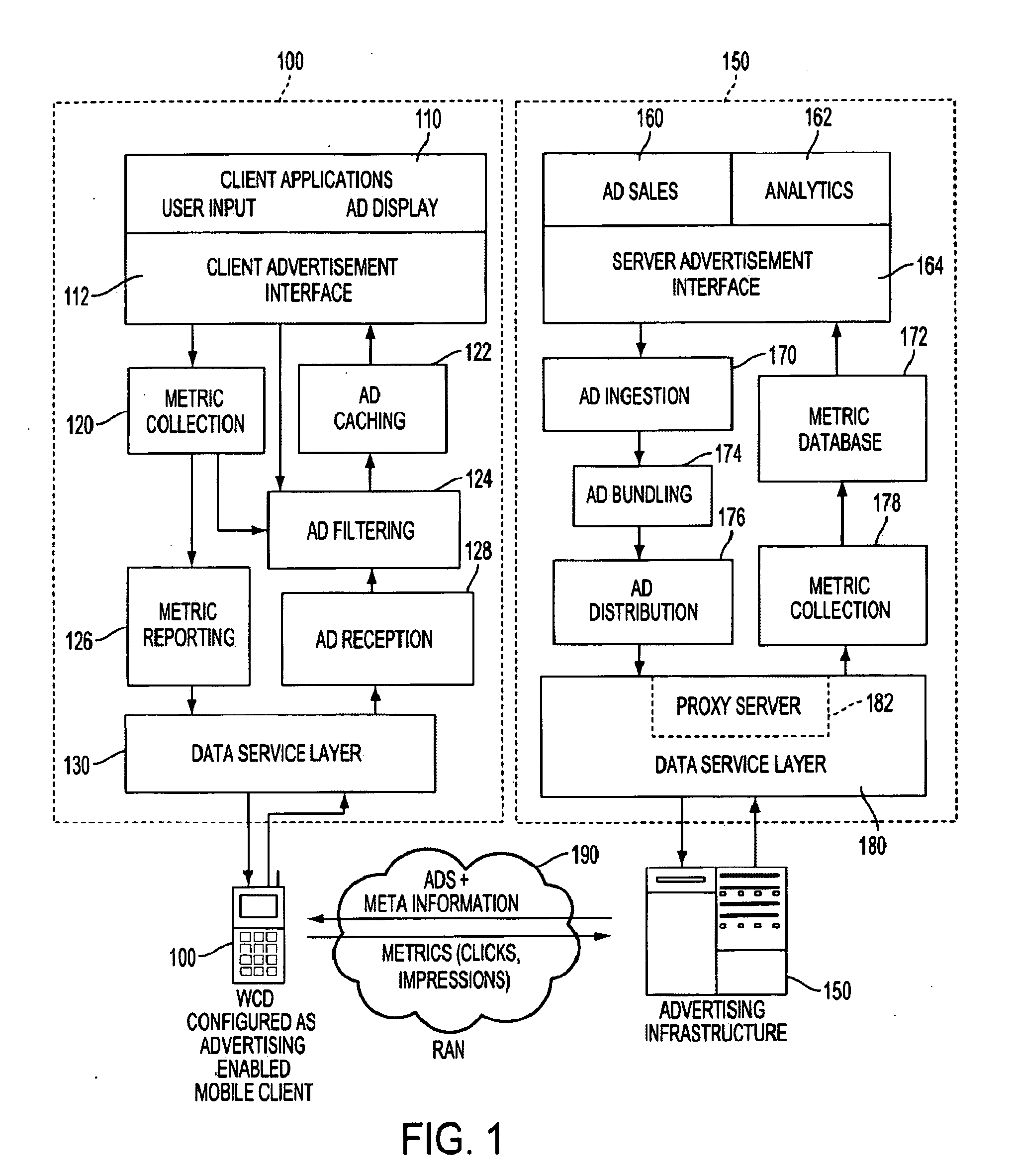
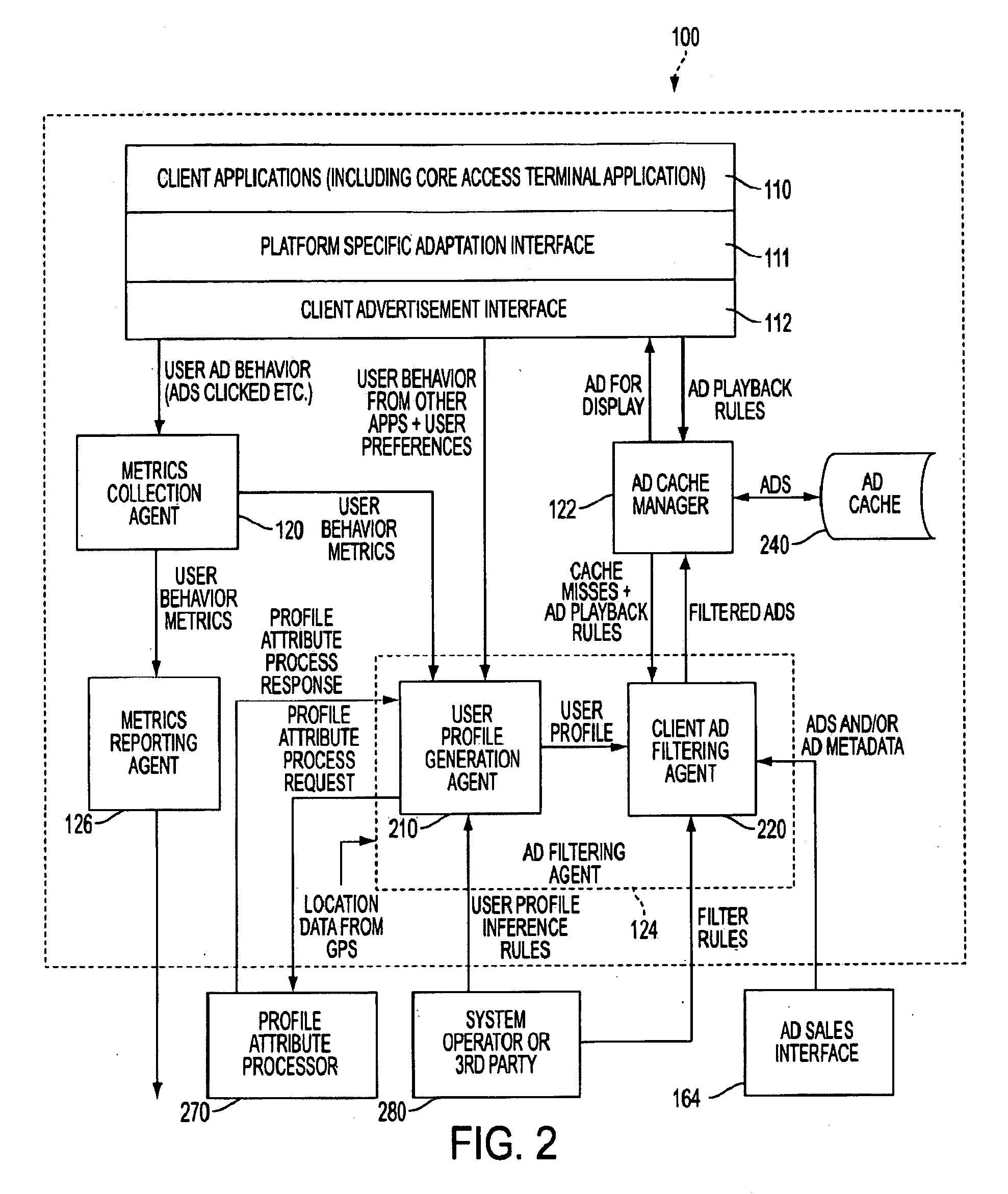
User profile generation architecture for targeted content distribution using external processes
InactiveUS20090048977A1Computer security arrangementsNavigation instrumentsContent distributionUser profile
A targeting-message profile may be obtained by a wireless access terminal (W-AT) by receiving a rule for establishing a user profile, synthesizing at least one profile attribute based on user behavior, and determining a need for further information based on the at least one profile attribute. Then, the W-AT may request the further information from an apparatus external to the W-AT, such as a server containing census information, receive the further information from the apparatus, and generate the profile based on the profile attributes and the further information.
Owner:QUALCOMM INC
Method and system for graphical file management
Owner:BONADIO ALLAN R
System, method and computer program product for multi-level file-sharing by concurrent users
ActiveUS7328225B1Efficient multi-user accessEfficient file sharingData processing applicationsSpecial data processing applicationsOperational systemFile size
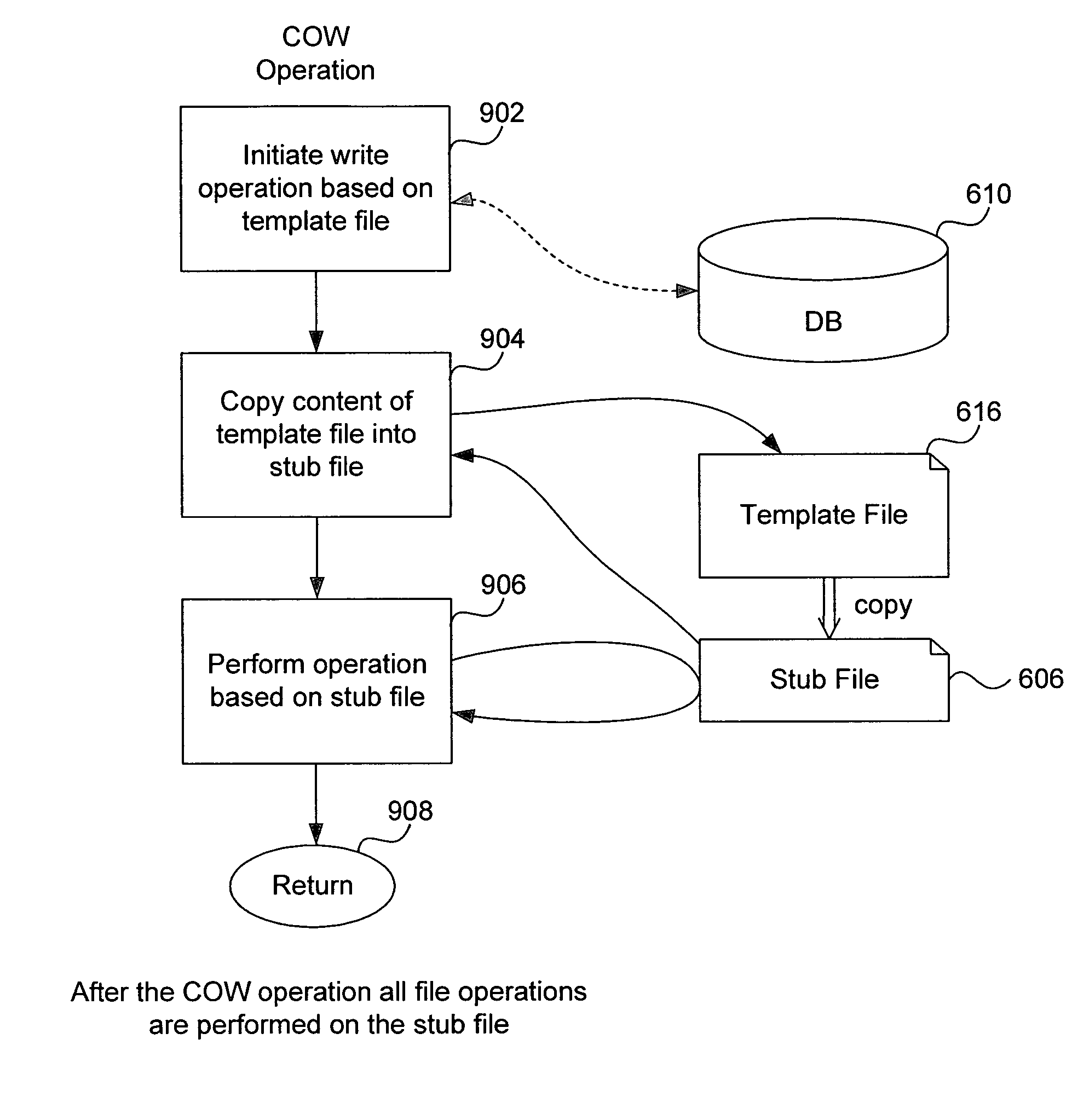
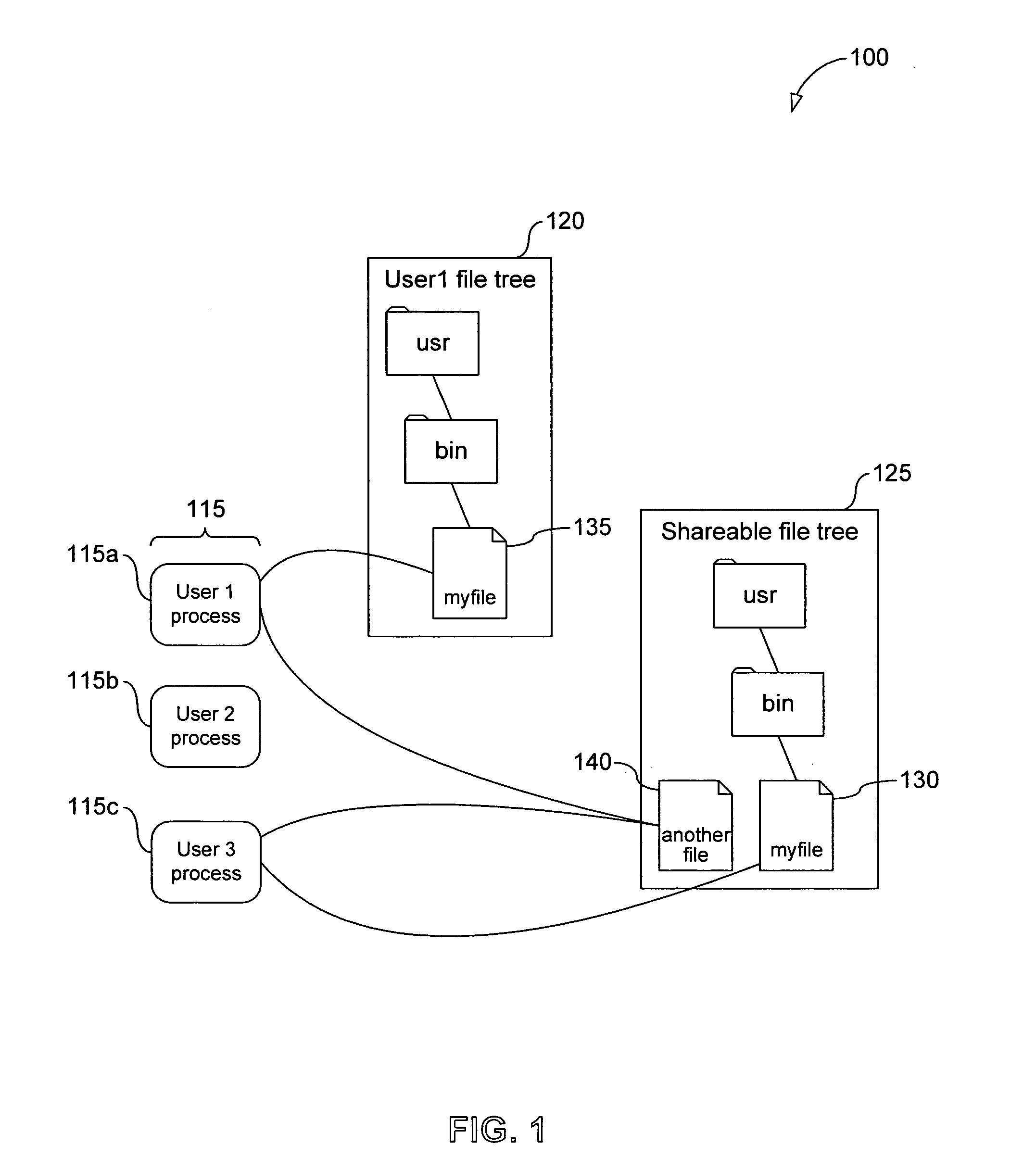
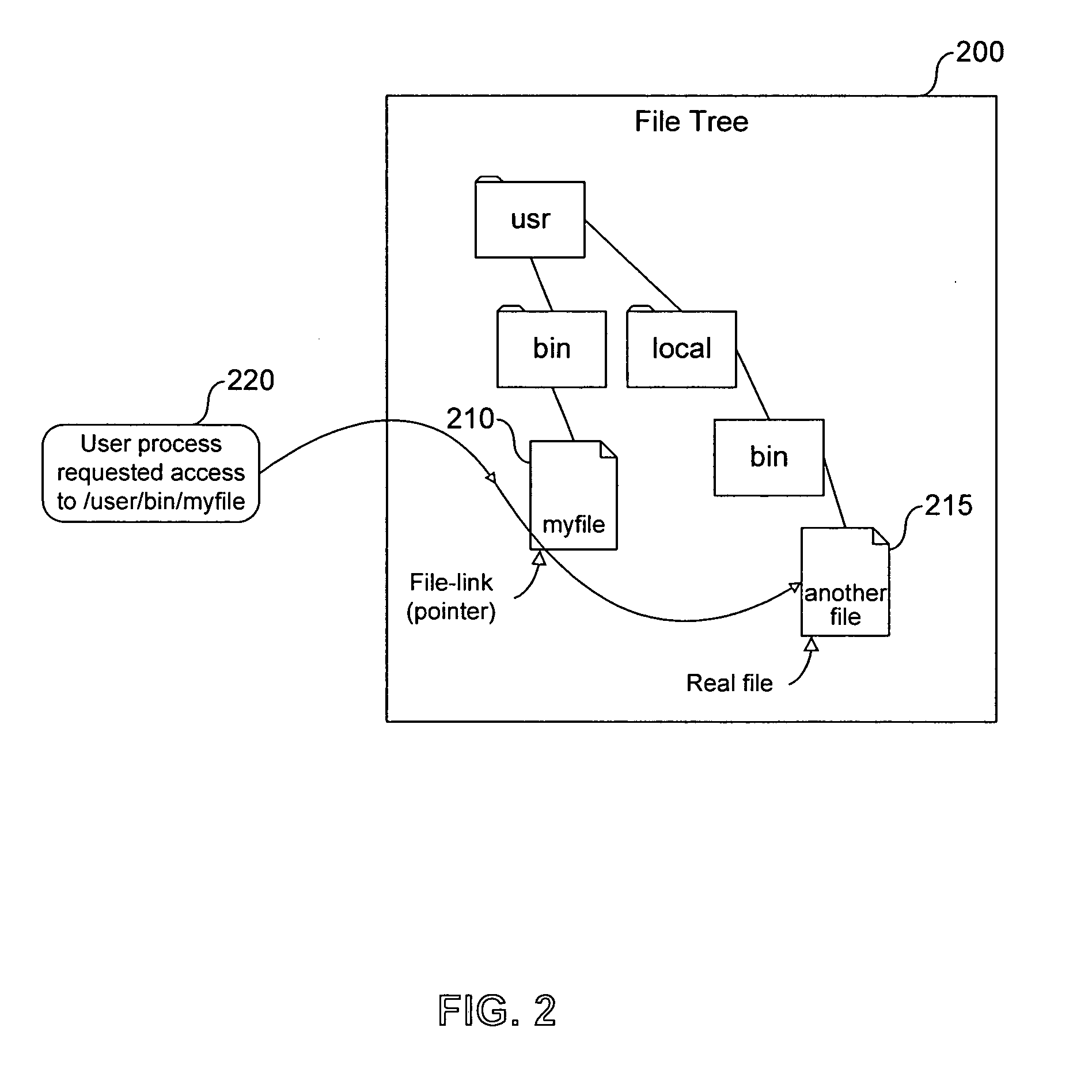
A method of accessing a shareable computer file includes receiving a request to access the shareable computer file, retrieving a file ID from a stub file corresponding to the shareable computer file, retrieving a file name from a database corresponding to the file ID, accessing the shareable computer file if a user has not modified the shareable computer file, and accessing a modified copy of the shareable file stored in the stub file if the user has modified the shareable computer file. A database is generated in operating system space or accessed using the operating system, and includes file IDs and their corresponding file names for shareable computer files. The stub file is generated locally to correspond to the shareable computer file, and includes a modified copy of the shareable computer file if the shareable computer file has been modified, and a link to the shareable computer file if the shareable computer file has not been modified. If the shareable computer file has not been modified, a read-only operation retrieves any of file contents, file position and file size from the shareable computer file. File attributes relating to the shareable computer file can be retrieved from the stub file. The database is provided by the operating system for use by a Virtual Private Server.
Owner:VIRTUOZZO INT GMBH
Rapid virus scan using file signature created during file write
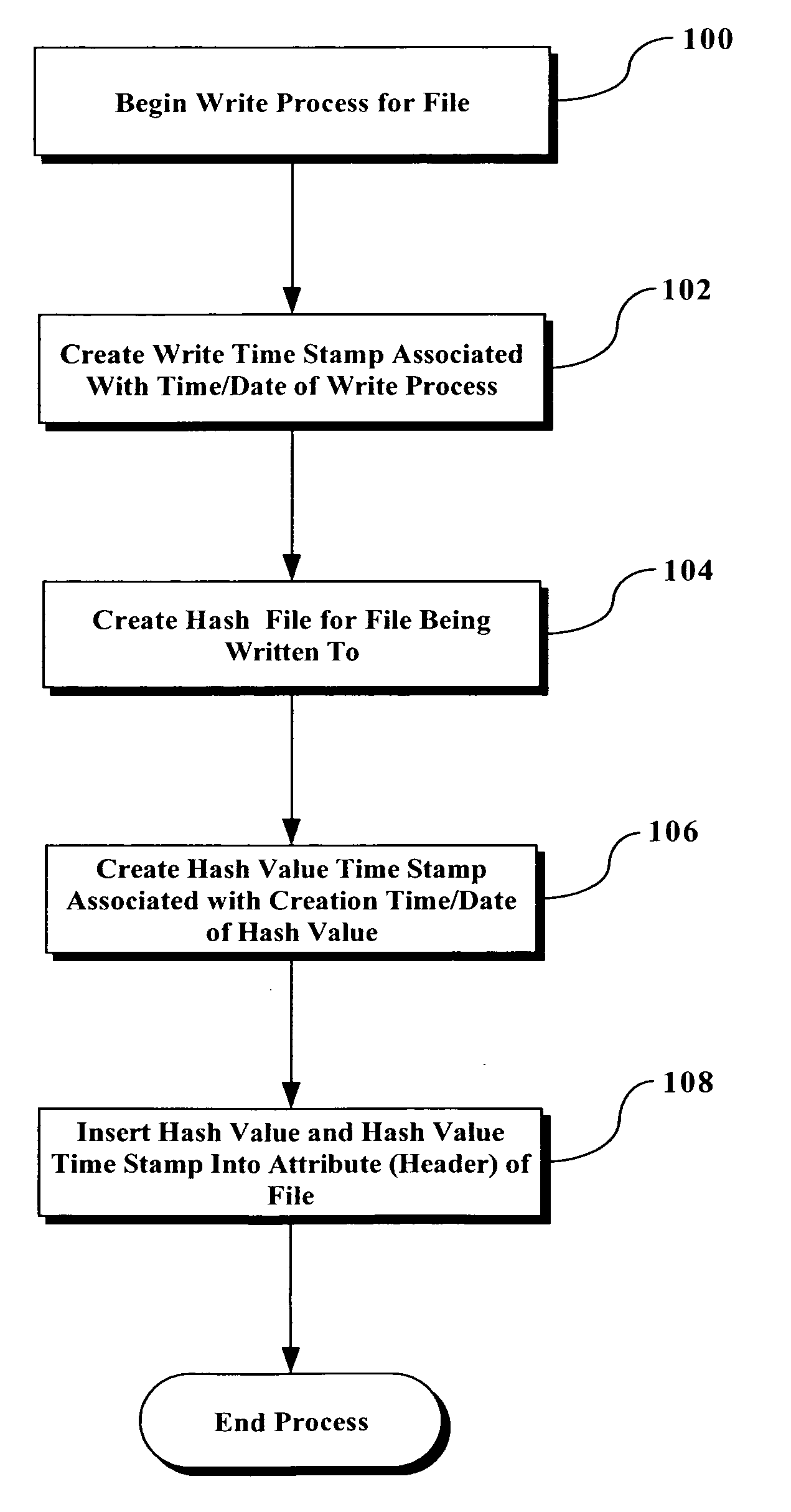
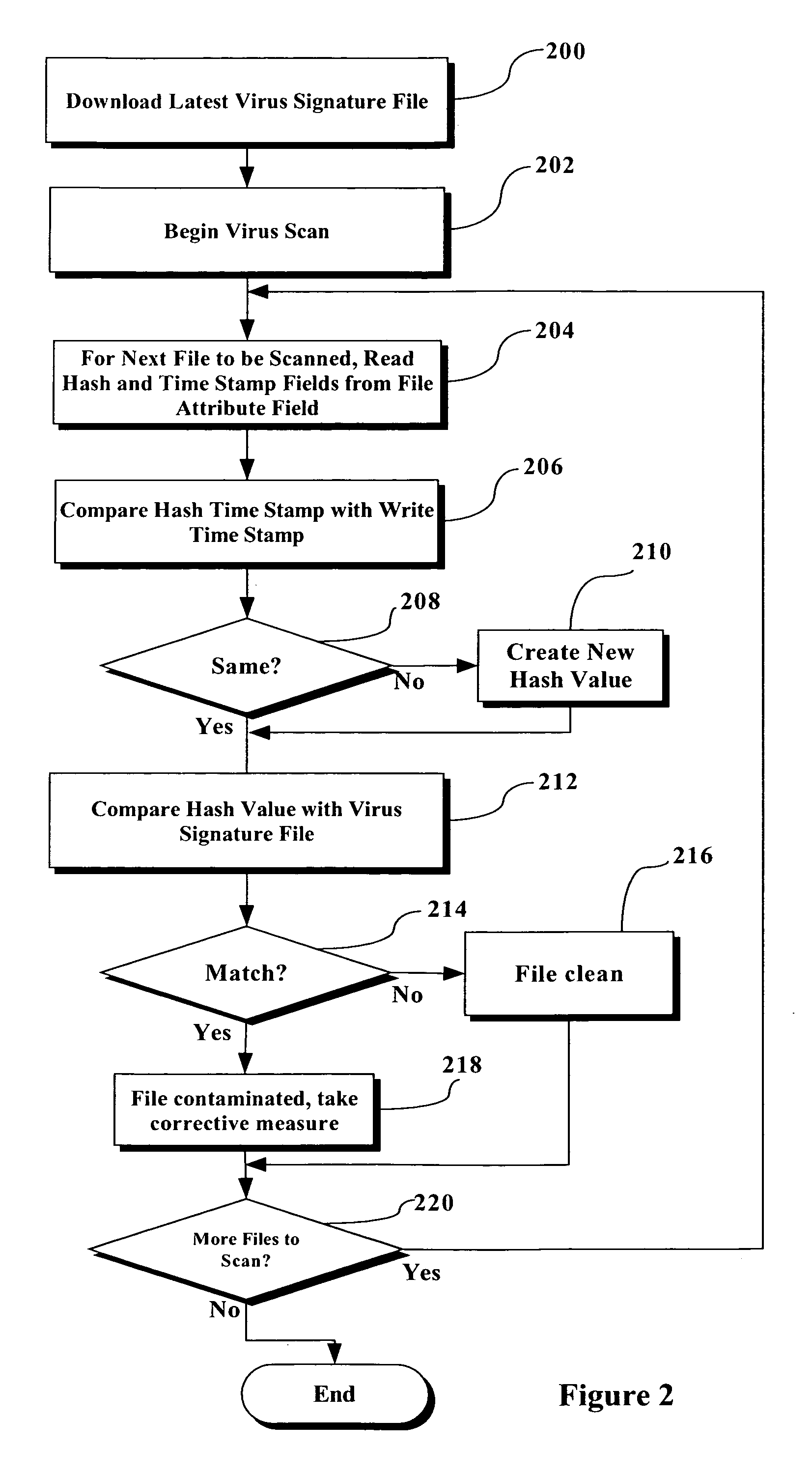
ActiveUS20060143713A1Amount of timeMemory loss protectionDetecting faulty computer hardwareSignature fileVirus
A procedure and implementations thereof are disclosed that significantly reduce the amount of time necessary to perform a virus scan. A file signature is created each time a file is modified (i.e., with each “file write” to that file). The file signature is inserted, with a date stamp, into the file attributes. The virus scan program checks the previously-created file signature against the virus signature file instead of creating the file signature for every file during the virus scan. Checks to ensure that the file signature is secure, and is valid and up to date, are also implemented. Only if the file signature is not valid and up-to-date does the virus scan program create a new file signature at the time of the running of the virus scan.
Owner:LENOVO PC INT
Project-based configuration management method and apparatus
InactiveUS20050091291A1Data processing applicationsDigital data processing detailsUser PrivilegeConfigfs
A configuration management system creates (602) each configuration by assigning a configuration identifier to each configuration. In addition, relational information is computed (706) that indicates the relationships between the configuration and any configurations upon which it is based. The system then tracks (604) changes to files of the configuration by storing information associating each new file version with the configuration identifier. The system also tracks (1210) changes to file properties. A configuration is then reconstructed (608) as of a desired date, by identifying (2104, 2106) the file versions and properties associated with that configuration as of the desired date. A determination is made (2110) whether a user that has requested the file versions has access privileges by first checking a security cache (2600) for the user privileges information. If the information is not on the cache, it is computed from a security table (2800) and stored on the cache. The system automatically compresses (3118) and reconstitutes (3006) file versions that are stored in the version store.
Owner:SZ DJI TECH CO LTD
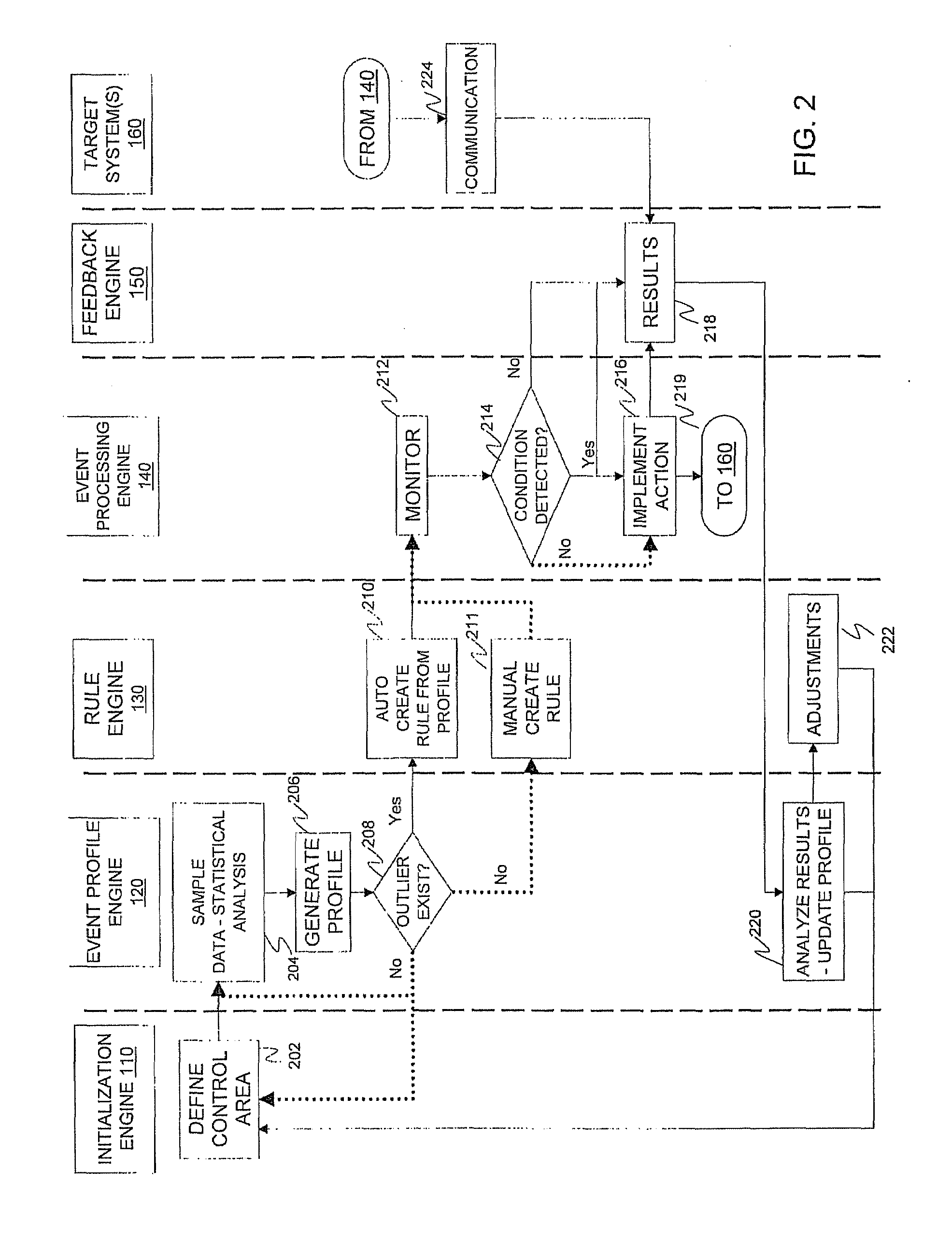
Statistical condition detection and resolution management
InactiveUS20110010209A1Digital computer detailsKnowledge representationImage resolutionStatistical analysis
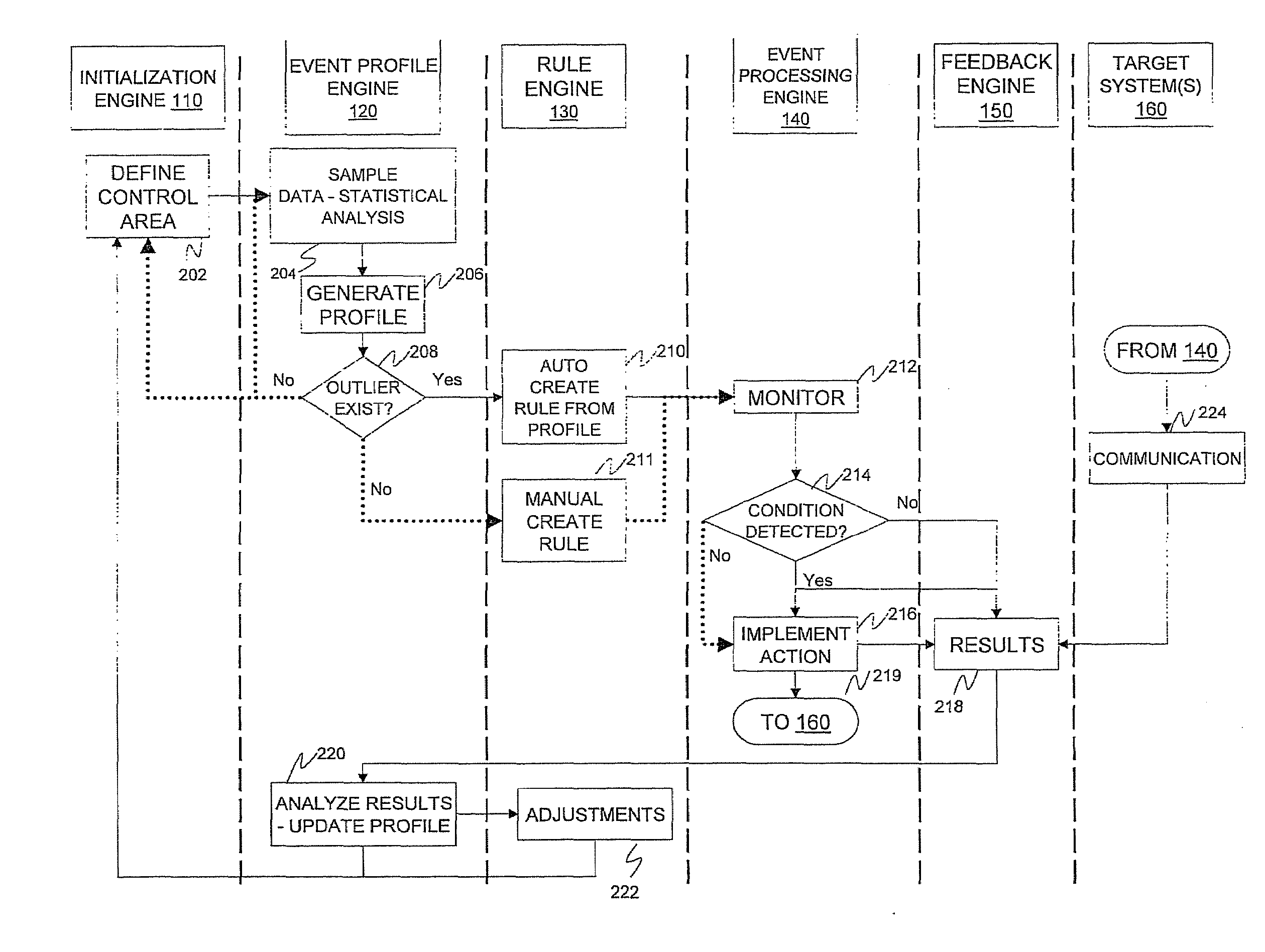
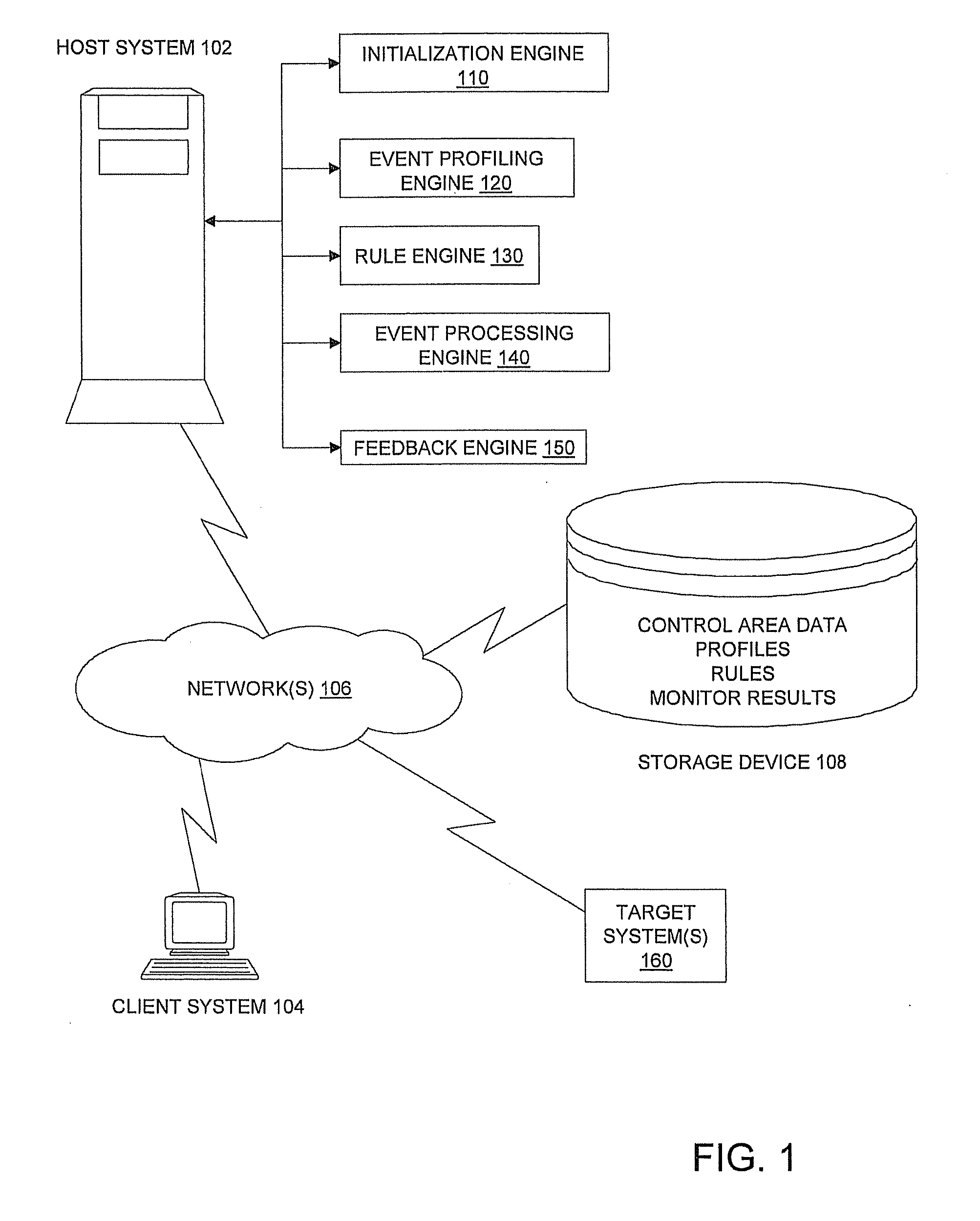
A statistical condition detection and resolution management method includes sampling data and performing statistical analysis on the sampled data, the sampled data representing events detected by an event profiling engine. The method also includes generating, a profile from results of the statistical analysis, the profile indicating a normative value of an attribute identified in the sampled data, and any outliers identified in the sampled data. Upon discovering an outlier, the method includes creating, via a rule engine in communication with the event profiling engine, a rule that defines an action to be taken for a condition identified as a result of the statistical analysis, and monitoring, via an event processing engine in communication with the rule engine, real-time operational data corresponding to attributes of the profile. When in response to the monitoring the condition is met, the method includes implementing the action identified in the rule.
Owner:IBM CORP
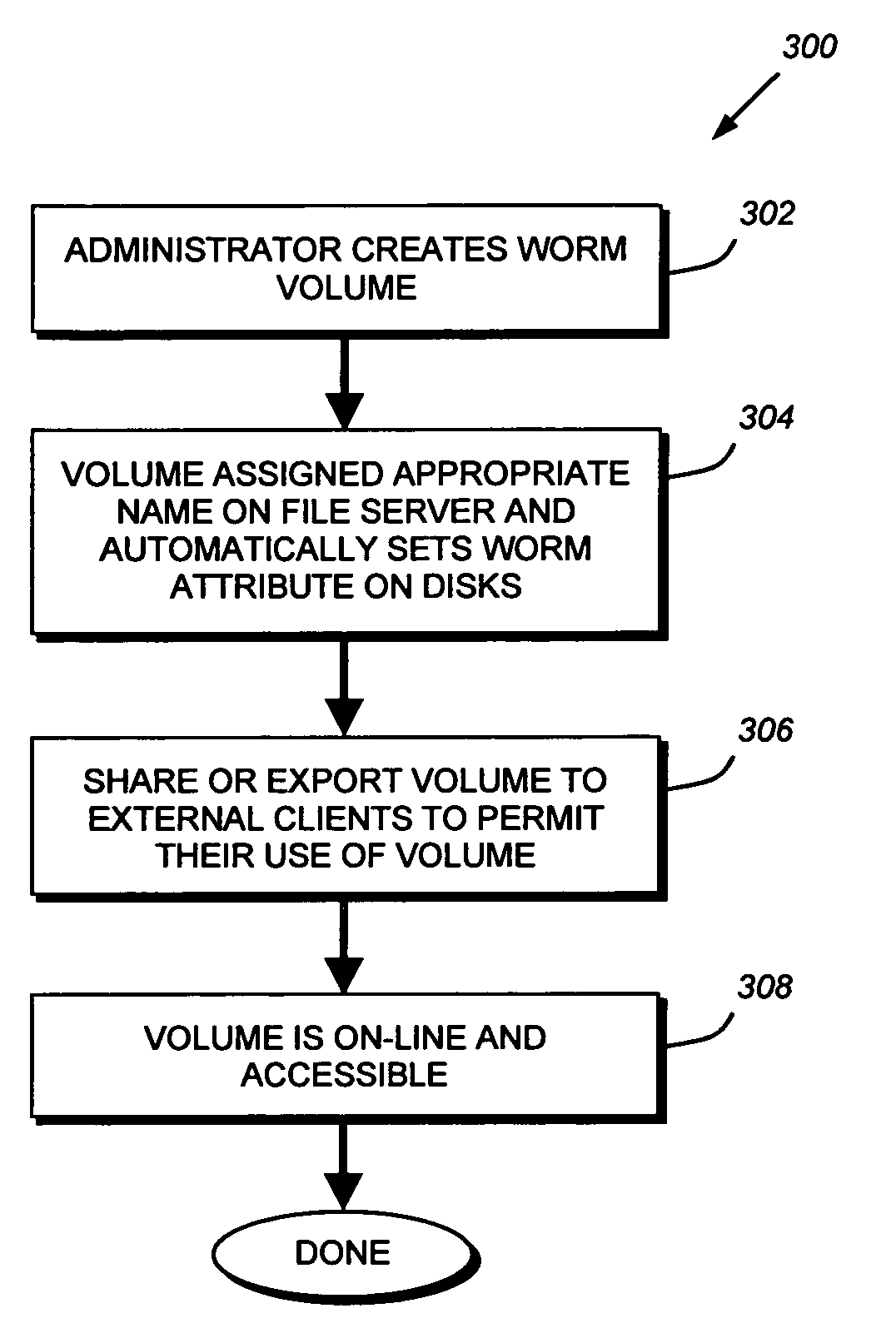
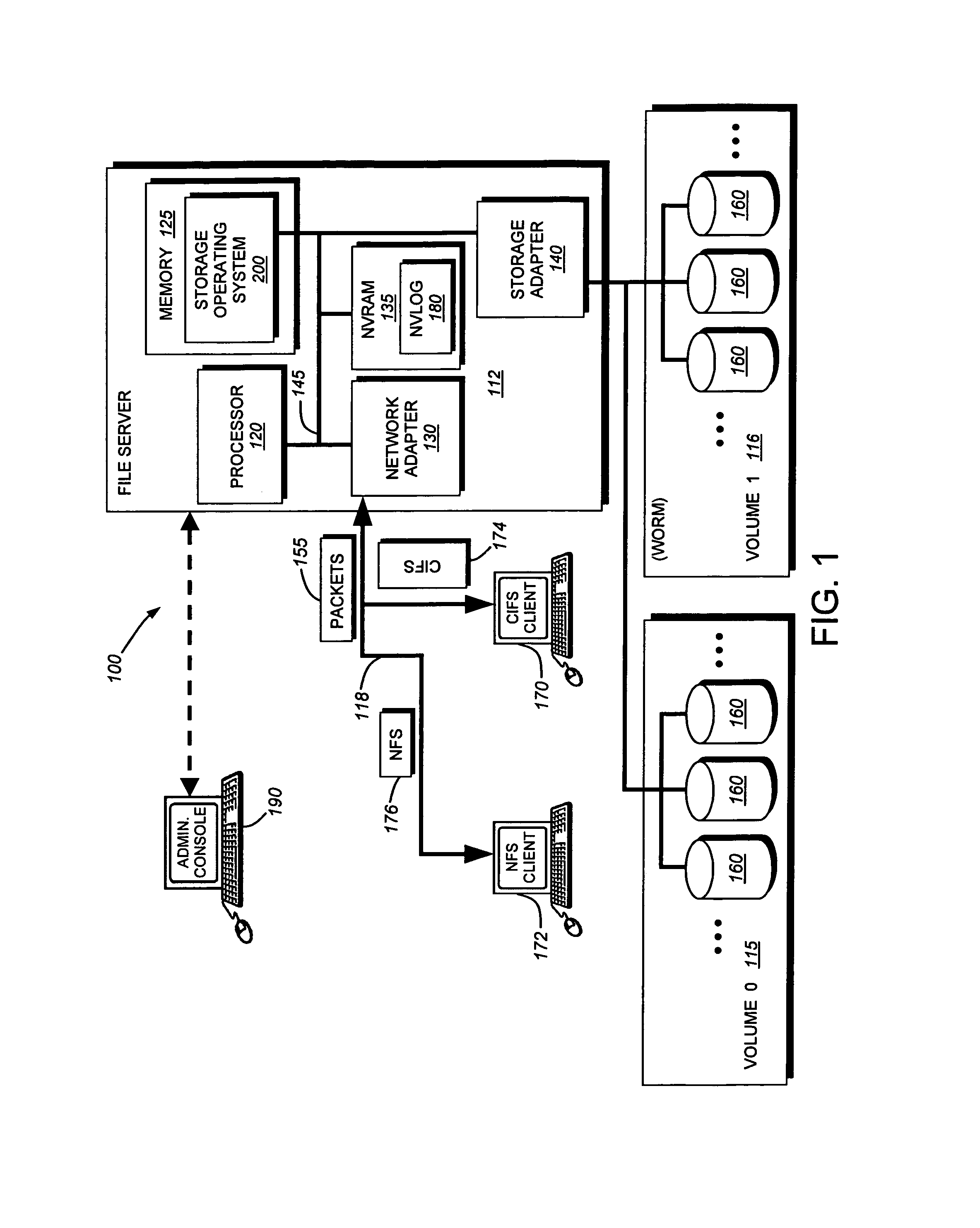
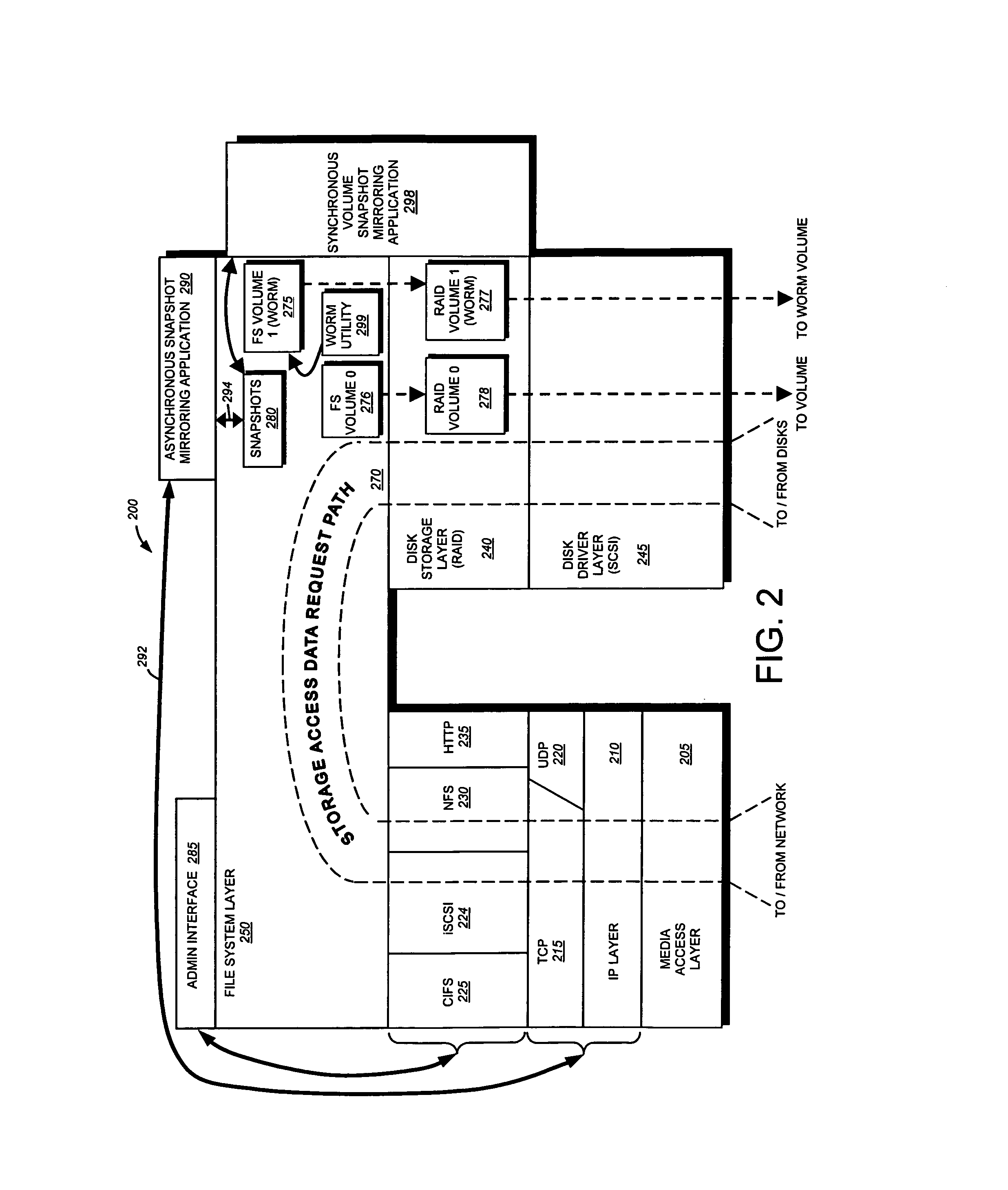
Write-once-read-many storage system and method for implementing the same
ActiveUS7155460B2Improve performanceInput/output to record carriersData processing applicationsOperational systemFile system
A write-once-read-many (WORM) storage system that employs large-capacity and relatively inexpensive disks in connection with a file system on a file server is provided. The file system contains most or all of the required WORM functionality so as to impose a minimal footprint on client applications, client operating systems and open protocols if desired. The system is organized around WORM storage volumes that contain files that, when committed to WORM storage, cannot be deleted or modified. Any file path or directory tree structure used to identify the file within the WORM volume is locked and cannot be deleted. In one embodiment, the administrator creates a WORM volume, capable of storing designated WORM files. The client then creates an appropriate WORM file using the appropriate protocol semantics. The file is written to the volume and committed by transitioning the file attributes from a not-read-only to a read-only state. The file system recognizes the persistently stored WORM attribute of any file in a WORM volume as WORM file. Henceforth, any attempt to modify the file attributes, write to the file, or delete the file, by clients, administrators or other entities is rejected and a request denied message is returned to the attempting party
Owner:NETWORK APPLIANCE INC
Method and System for Managing Digital Goods
ActiveUS20070220051A1Facilitates bulk uploadDigital data processing detailsBuying/selling/leasing transactionsDigital goodsXML
Owner:FLEXERA SOFTWARE
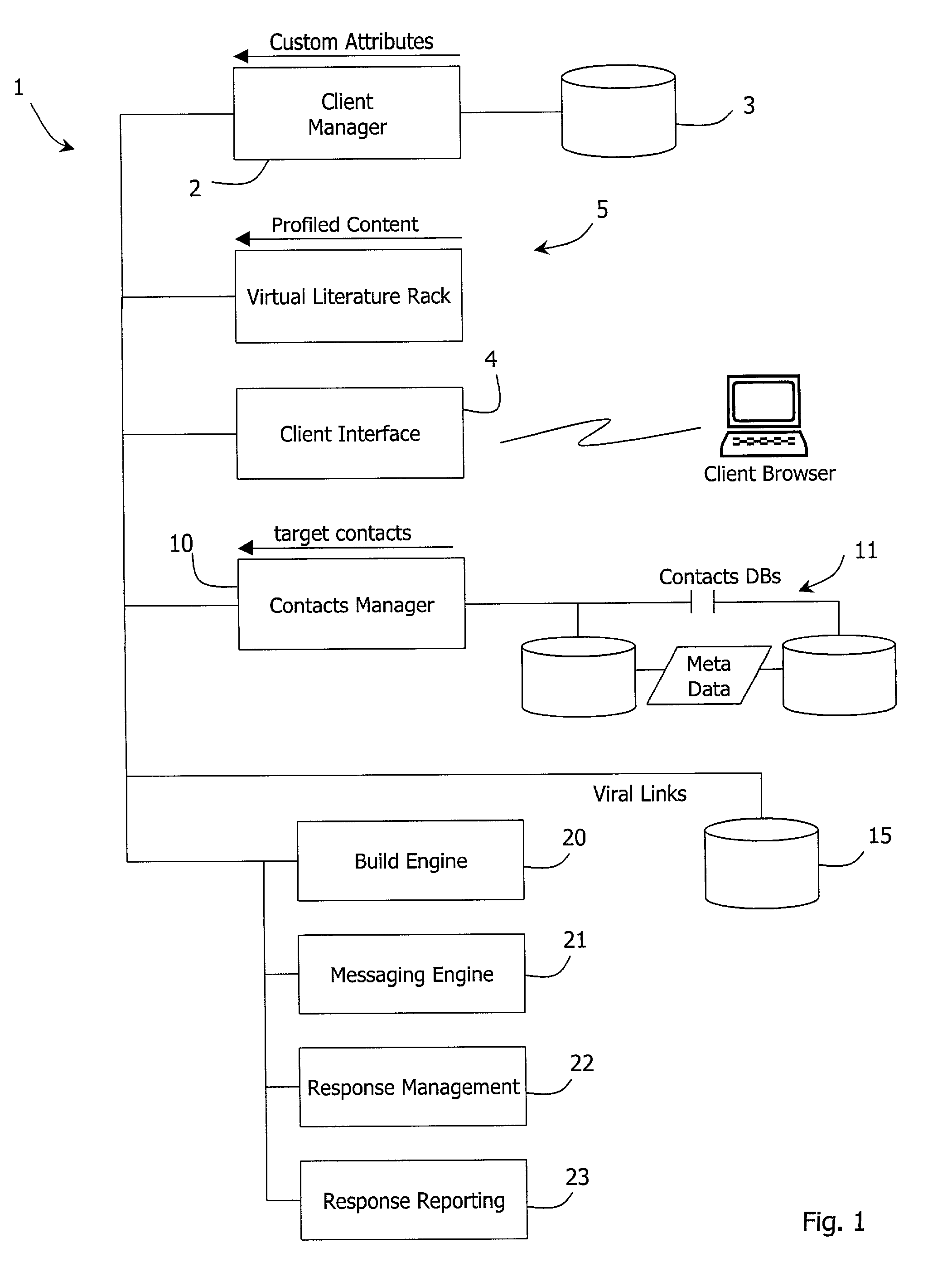
Messaging system
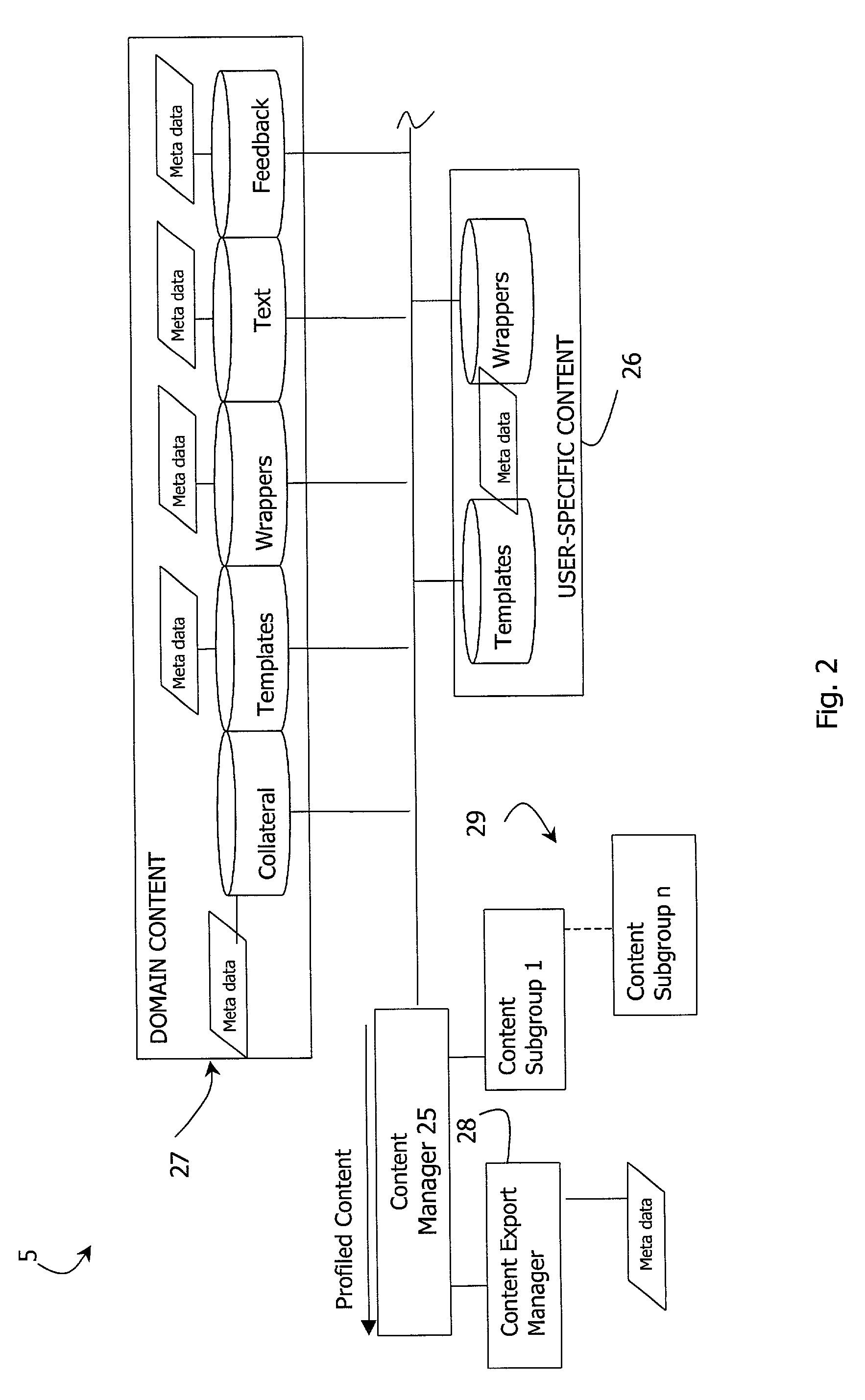
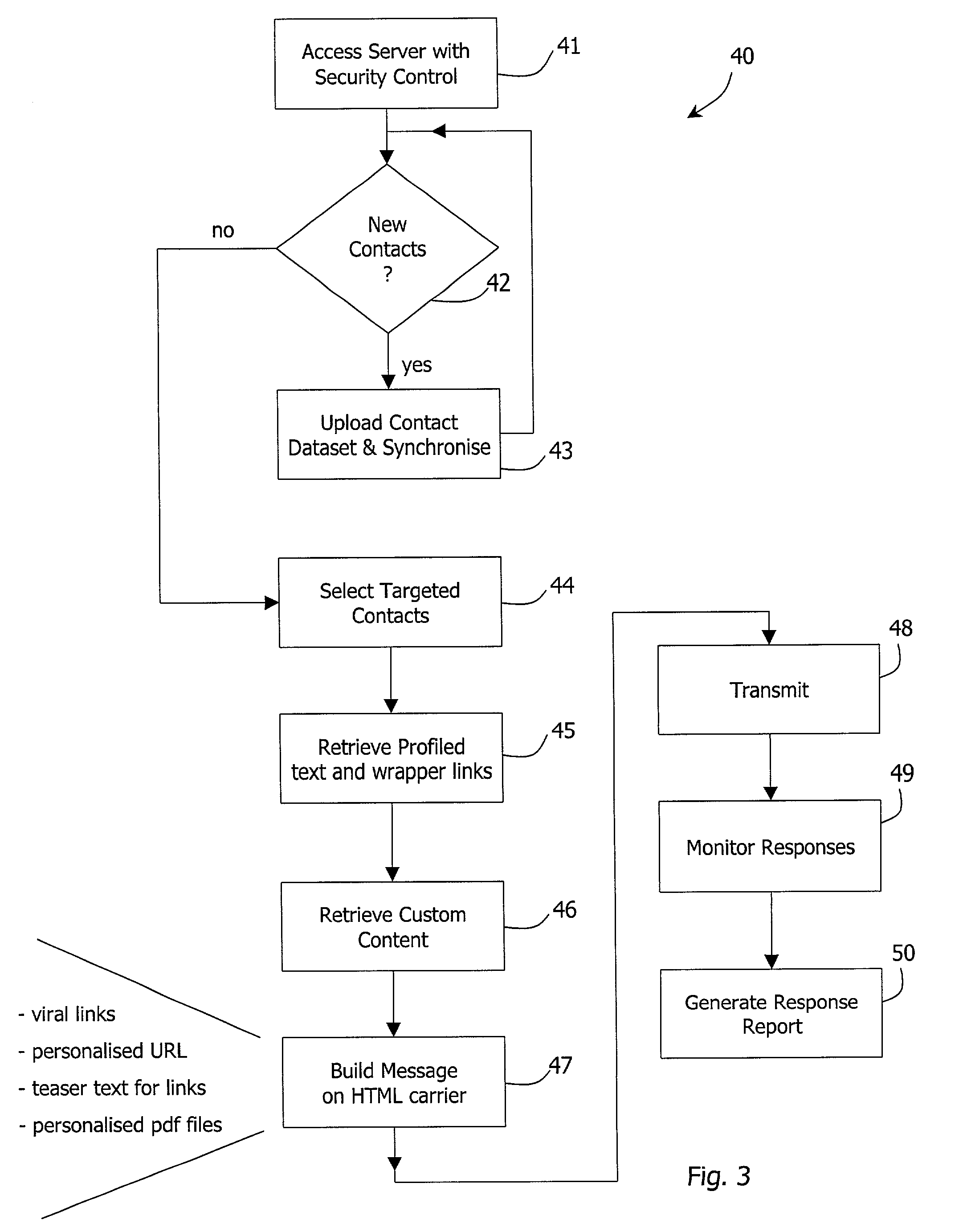
A messaging system (1) comprises a server which registers (2) clients (users) and stores uploaded contact data in contacts databases (11). The contact databases have meta data including profile attributes indicating the subject matter profiles of the contacts. A content manager (25) receives content items such as collateral parts and message text and stores them in content databases, also with meta data having profile attributes. When a client requests a message to be sent to a contact, the content manager (25) automatically identifies relevant content items according to the profile attributes, and a messaging engine (21) sends a message with a wrapper having links to these content items. When the contact responds, a response management function (22) captures response data and instructs a build engine (20) to build content from the identified items. The content is then sent to the contact.
Owner:TWELVE HORSES TECH
Role-based access control enforced by filesystem of an operating system
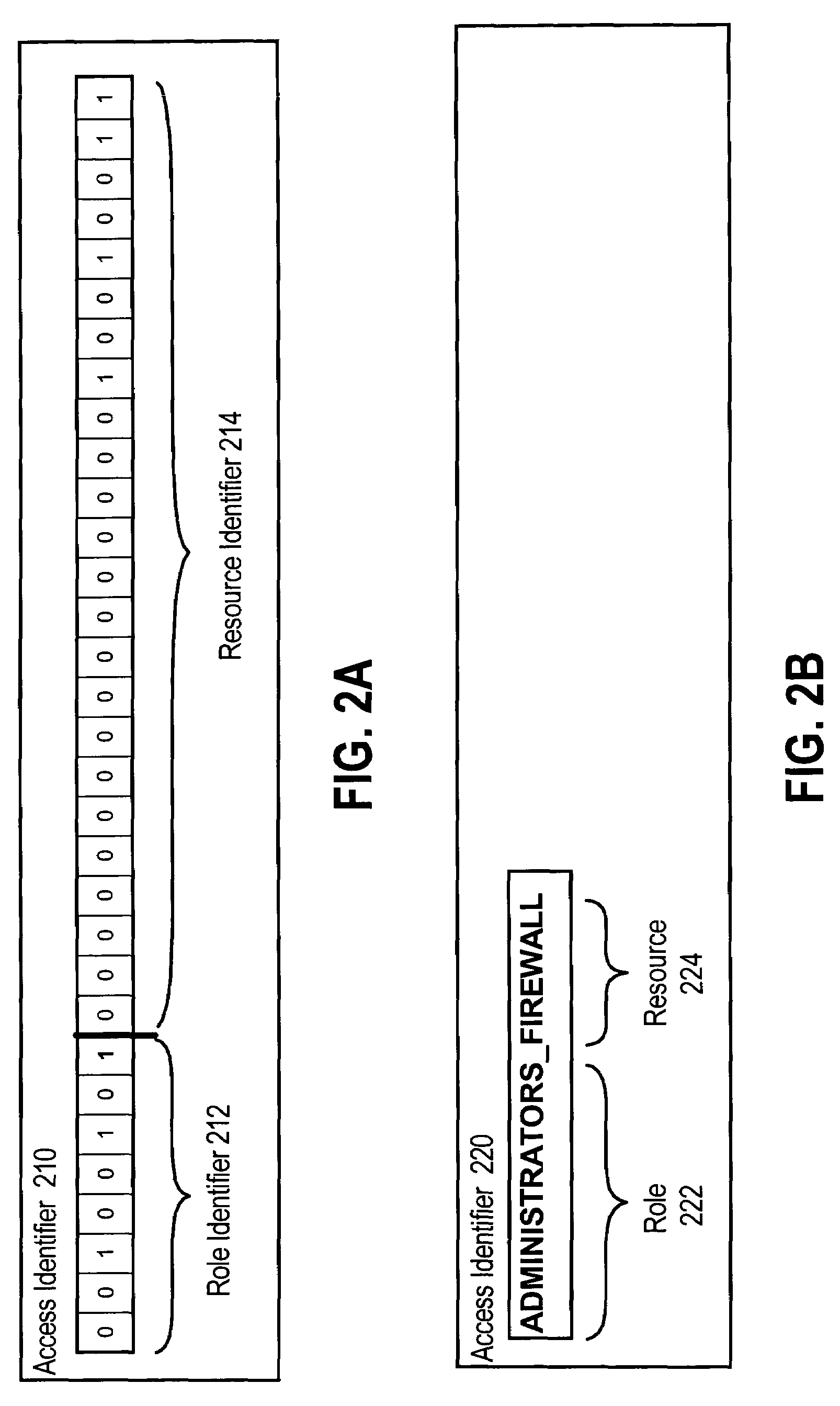
InactiveUS7702693B1Digital data processing detailsComputer security arrangementsOperational systemFile system
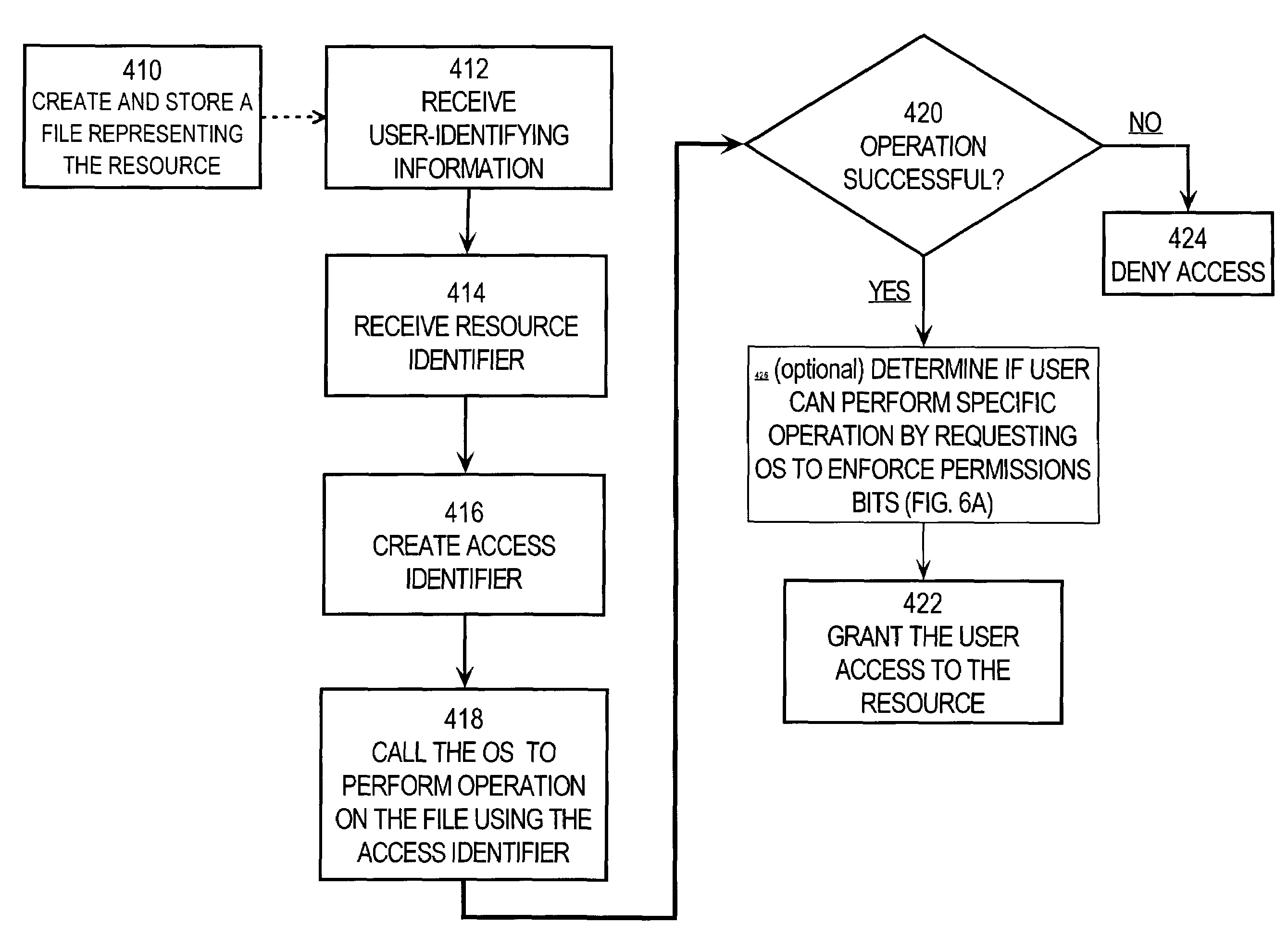
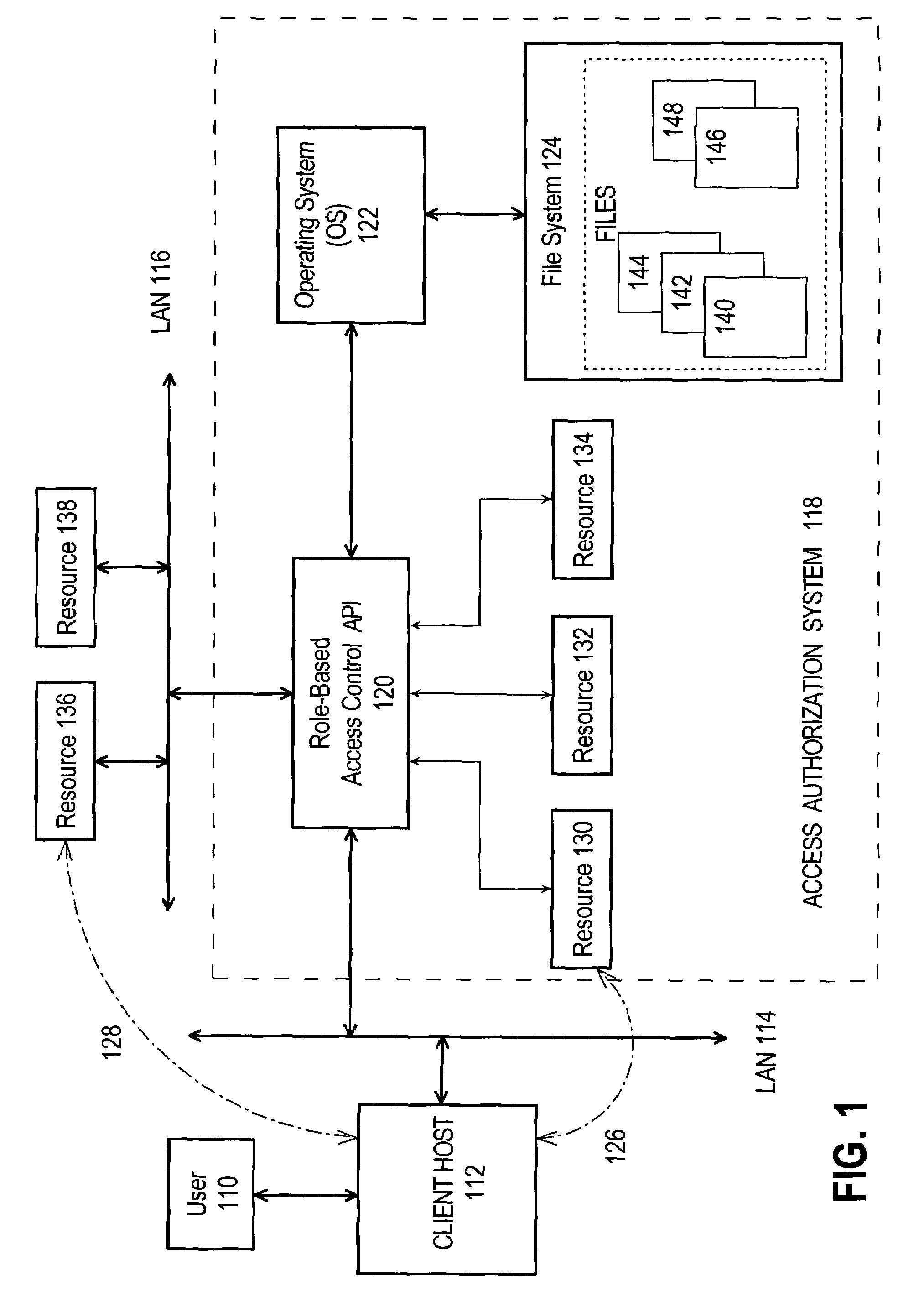
A method and system for role-based access control enforced by an Operating System filesystem are provided. A file representing a resource is created and stored in the Operating System filesystem. A user requests access to the resource and provides user-identifying information and a resource identifier. An access identifier is created based on the user-identifying information and the resource identifier, and is formatted as the file attribute used by the Operating System to manage file access. A system call to the Operating System is made to perform an operation on the file representing the resource, where the system call uses the access identifier to gain access to the file. The user is granted access to the resource only if the operating system successfully performs the operation on the file representing the resource.
Owner:CISCO TECH INC
Key encryption method based on file attribution
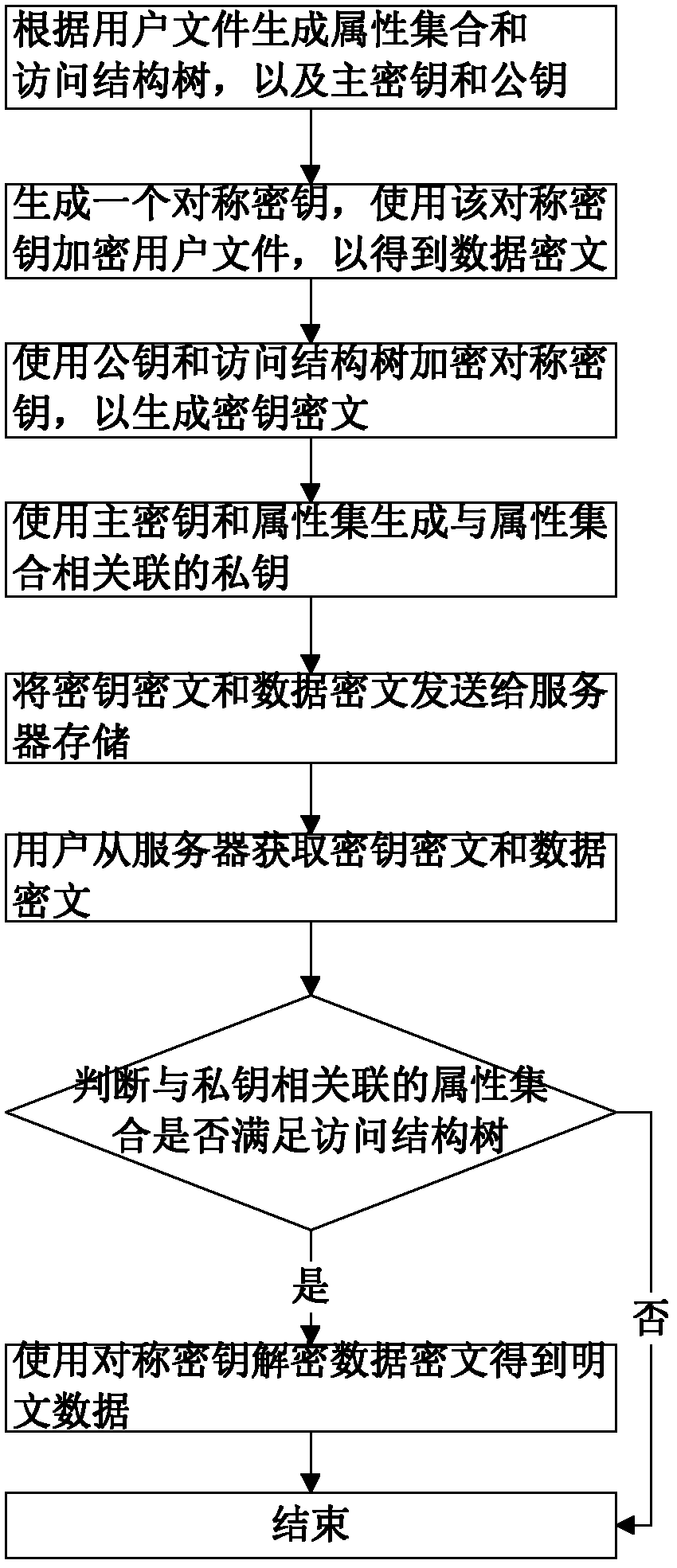
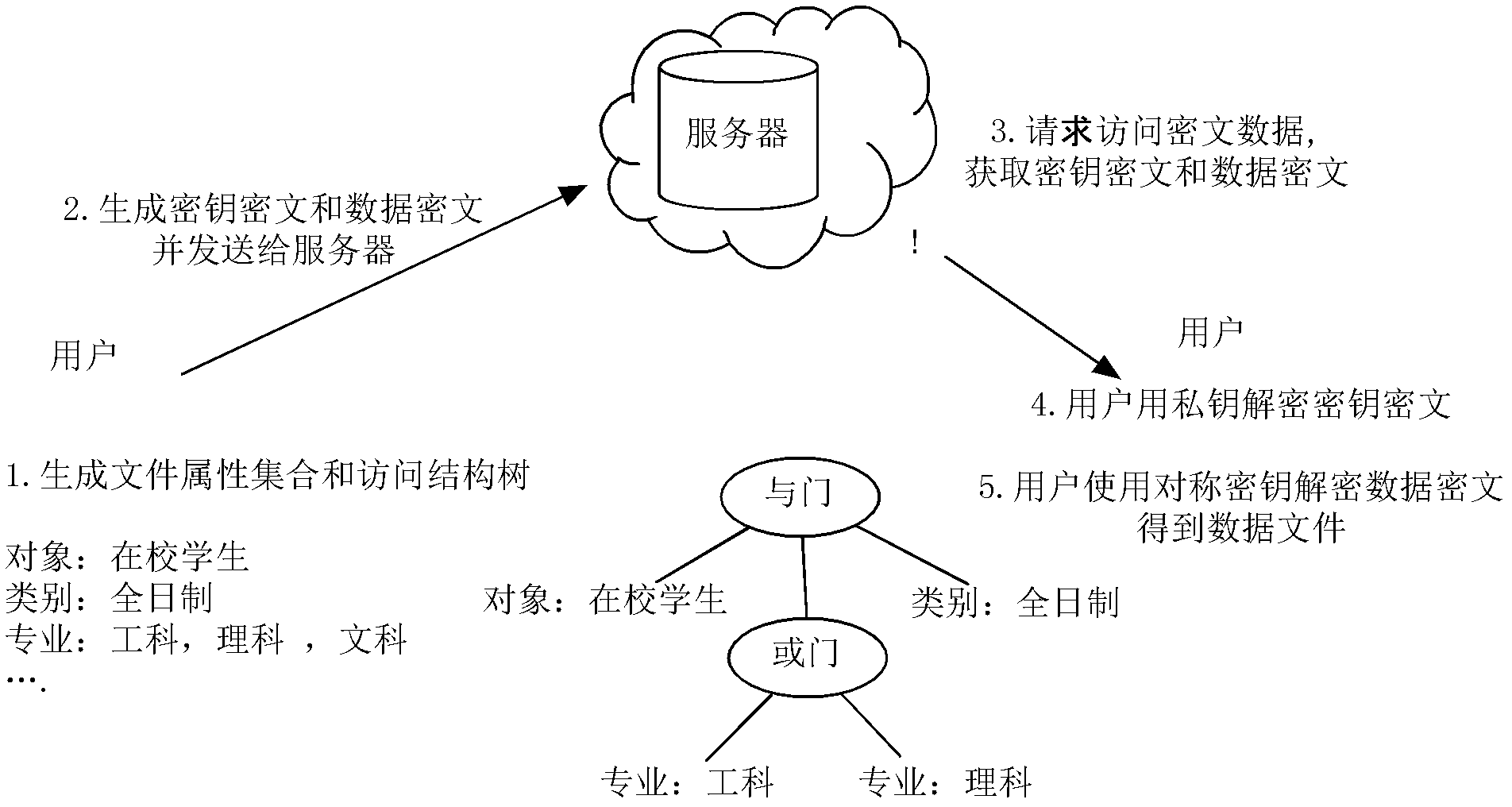
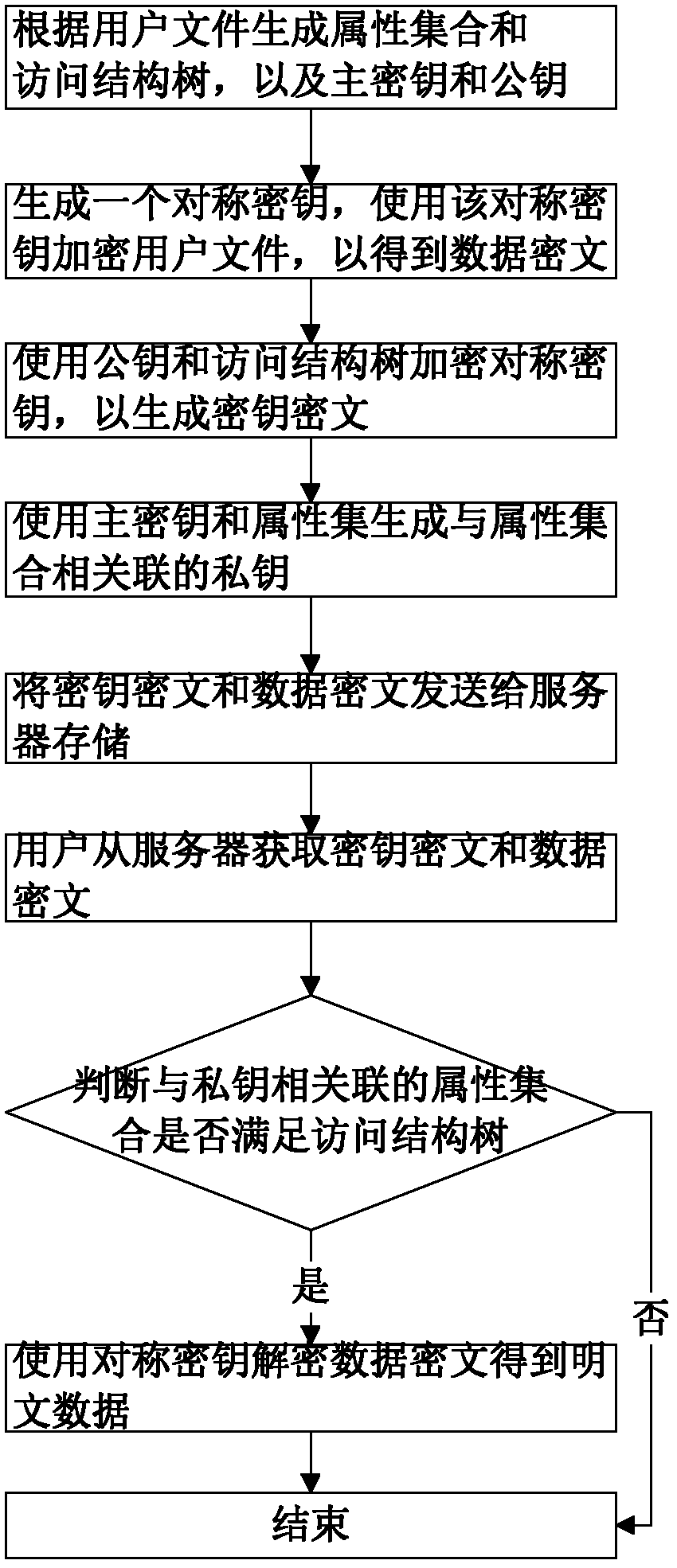
InactiveCN102624522AEfficient encryptionReduce multiplication (exclusiveSecuring communicationPlaintextAccess structure
The invention discloses a key encryption method based on file attribution. The key encryption method comprises the following steps of: receiving a user file, generating an attribution aggregate, an access structure tree, a main key and a public key according to the user file, randomly generating symmetric keys, encrypting the user file by using the symmetric keys and a symmetric encryption algorithm to obtain data cipher text, encrypting the symmetric keys by utilizing the public key and the access structure tree to generate a key cipher text, generating a private key associated with the attribution aggregate by utilizing the main key and the attribution aggregate, transmitting the key cipher text and the data cipher text to a server to store, obtaining the key cipher text and the data cipher text from the server by a user, decrypting the key cipher text by using the private key by the user to judge whether the attribution aggregate associated with the private key meets the access structure tree or not, and if meeting the access structure tree, decrypting the symmetric key and decrypting the data cipher text by utilizing the symmetric key through the user to obtain plaintext data. According to the key encryption method based on the file attribution, disclosed by the invention, data is encrypted by the symmetric encryption algorithm, the safety of the symmetric key is protected based on attribution encryption, and the high-efficiency safe access of encrypted data is realized.
Owner:HUAZHONG UNIV OF SCI & TECH
Harvesting file system metsdata
InactiveUS8612404B2Efficient storageEfficient accessDigital data information retrievalDigital data processing detailsFile systemChecksum
Owner:INT BUSINESS MASCH CORP
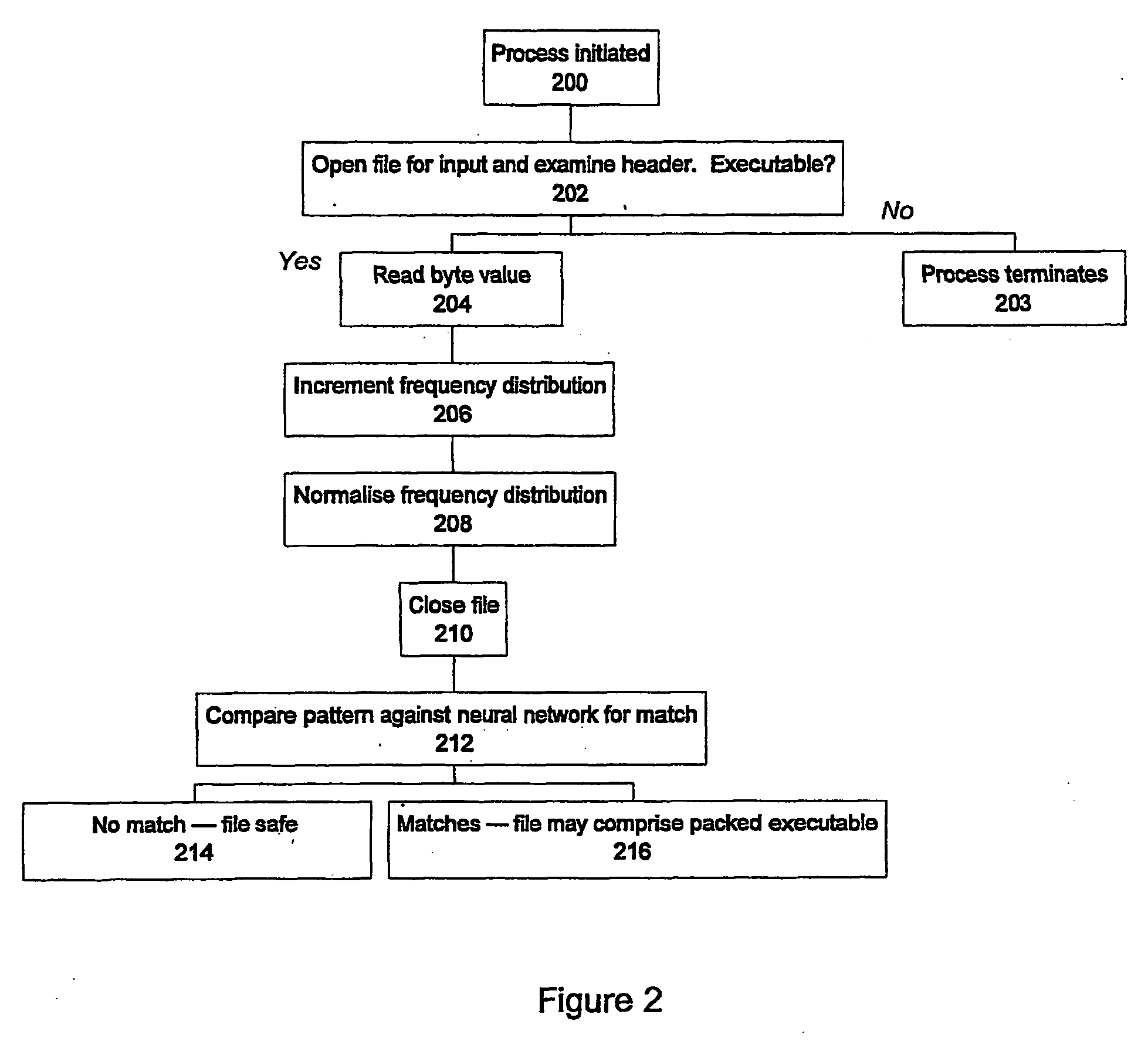
File analysis
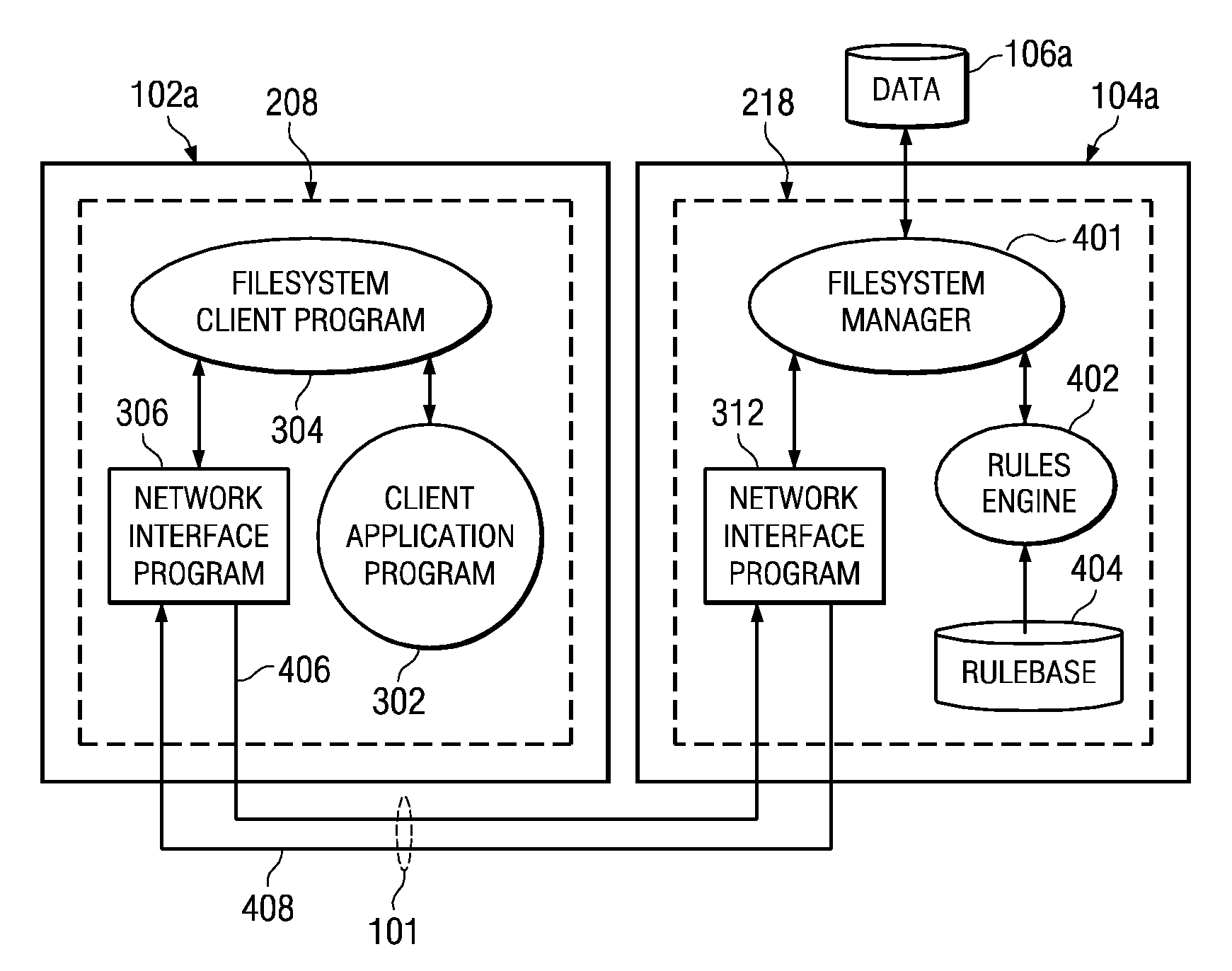
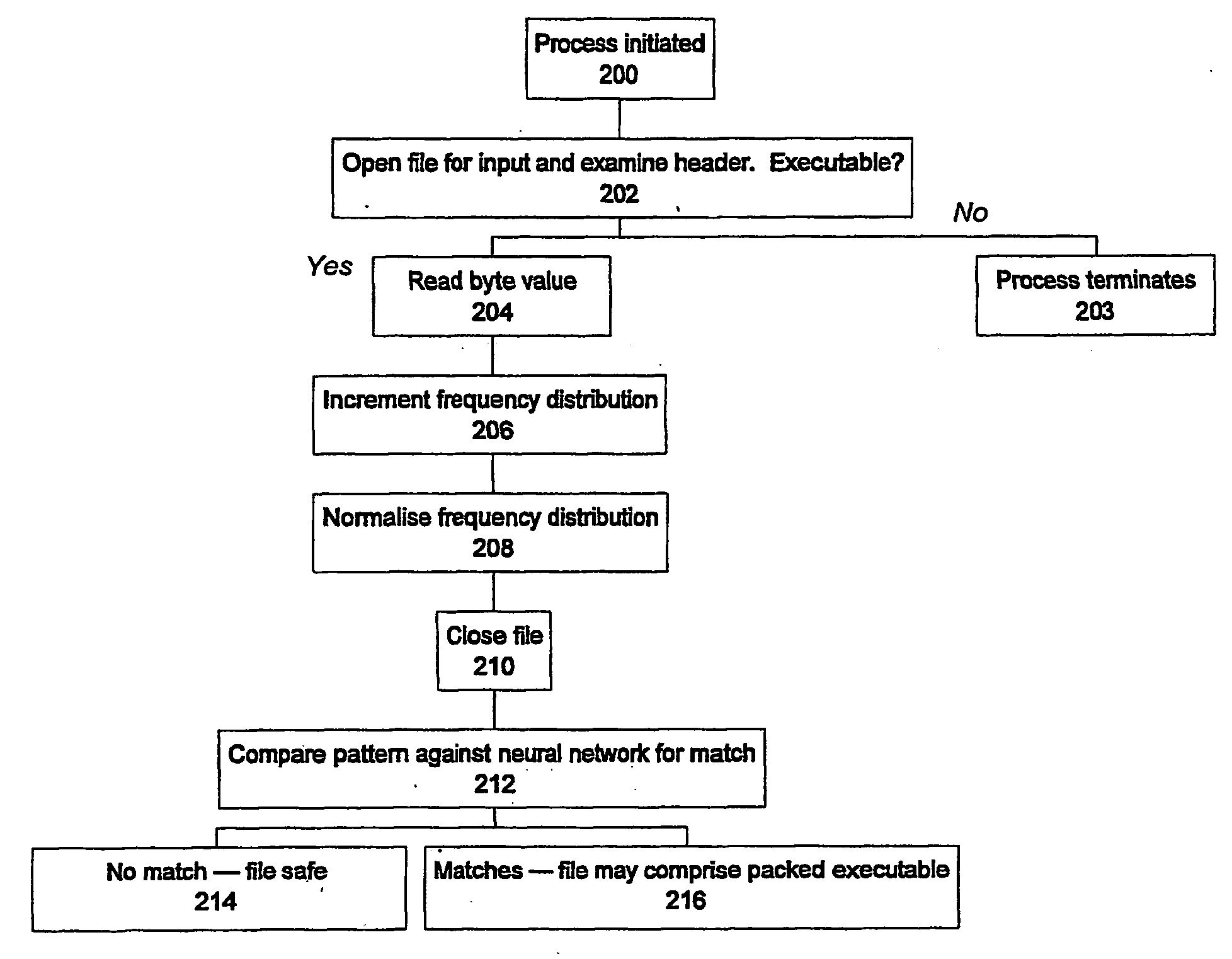
A method of analysing the properties of an electronic file, especially to detect a packed executable file. A neural network is used to determine if a given file is a packed executable from analysis of byte distributions within the file without unpacking the fiel from its compressed form.
Owner:CLEARSWIFT
Method and apparatus for file system virtualization
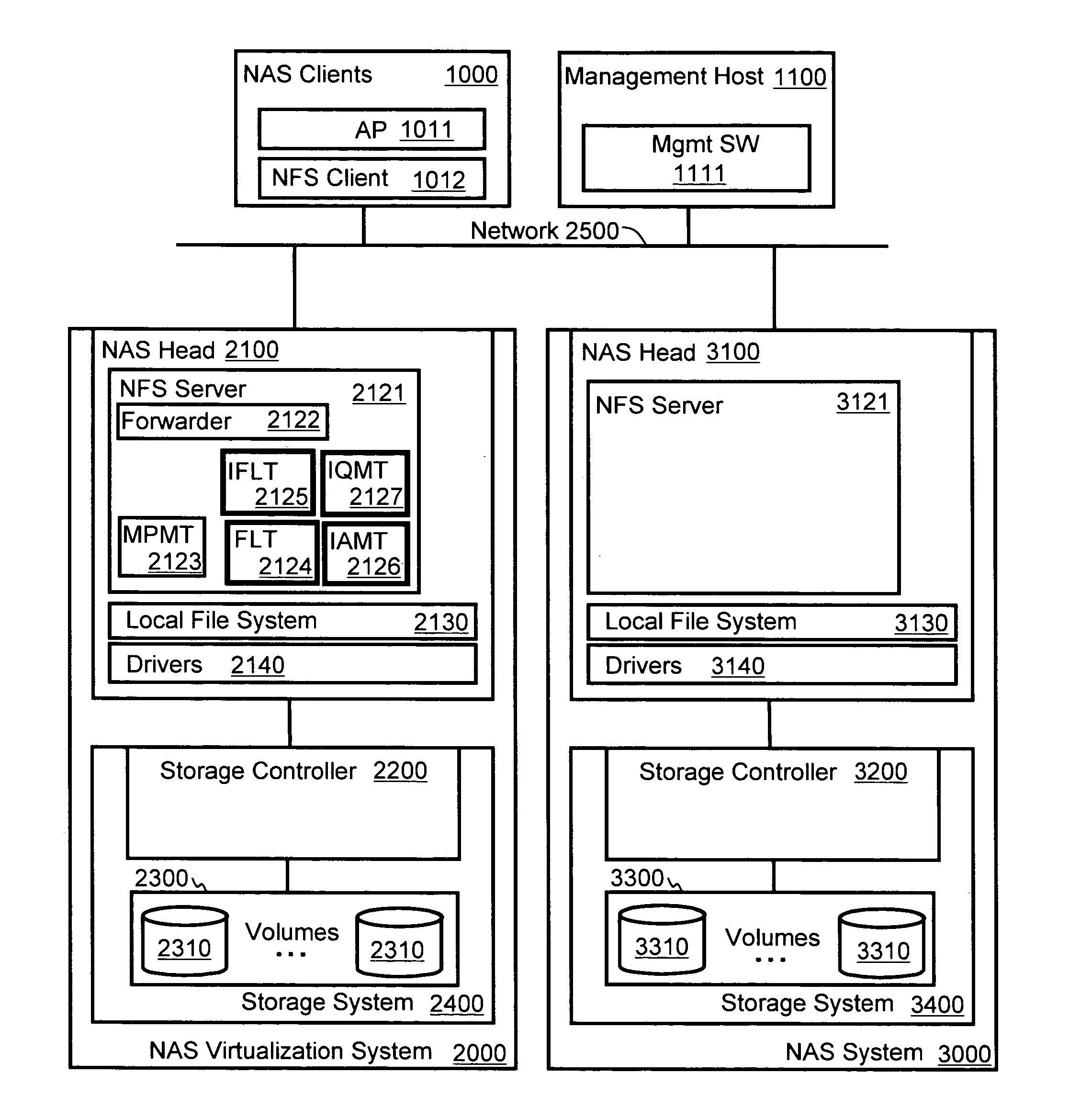
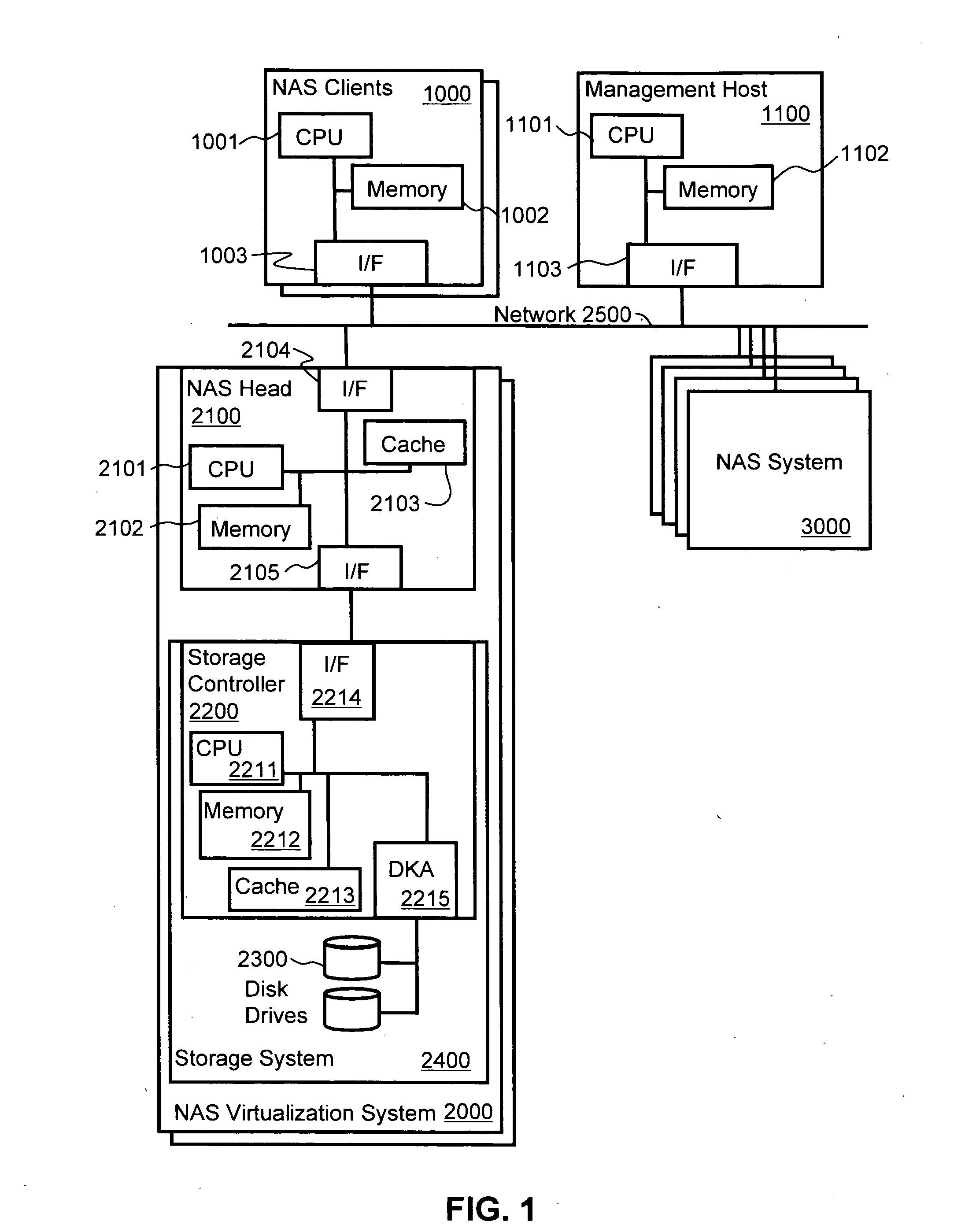
InactiveUS20080155214A1Digital data information retrievalMemory loss protectionVirtualizationFile system
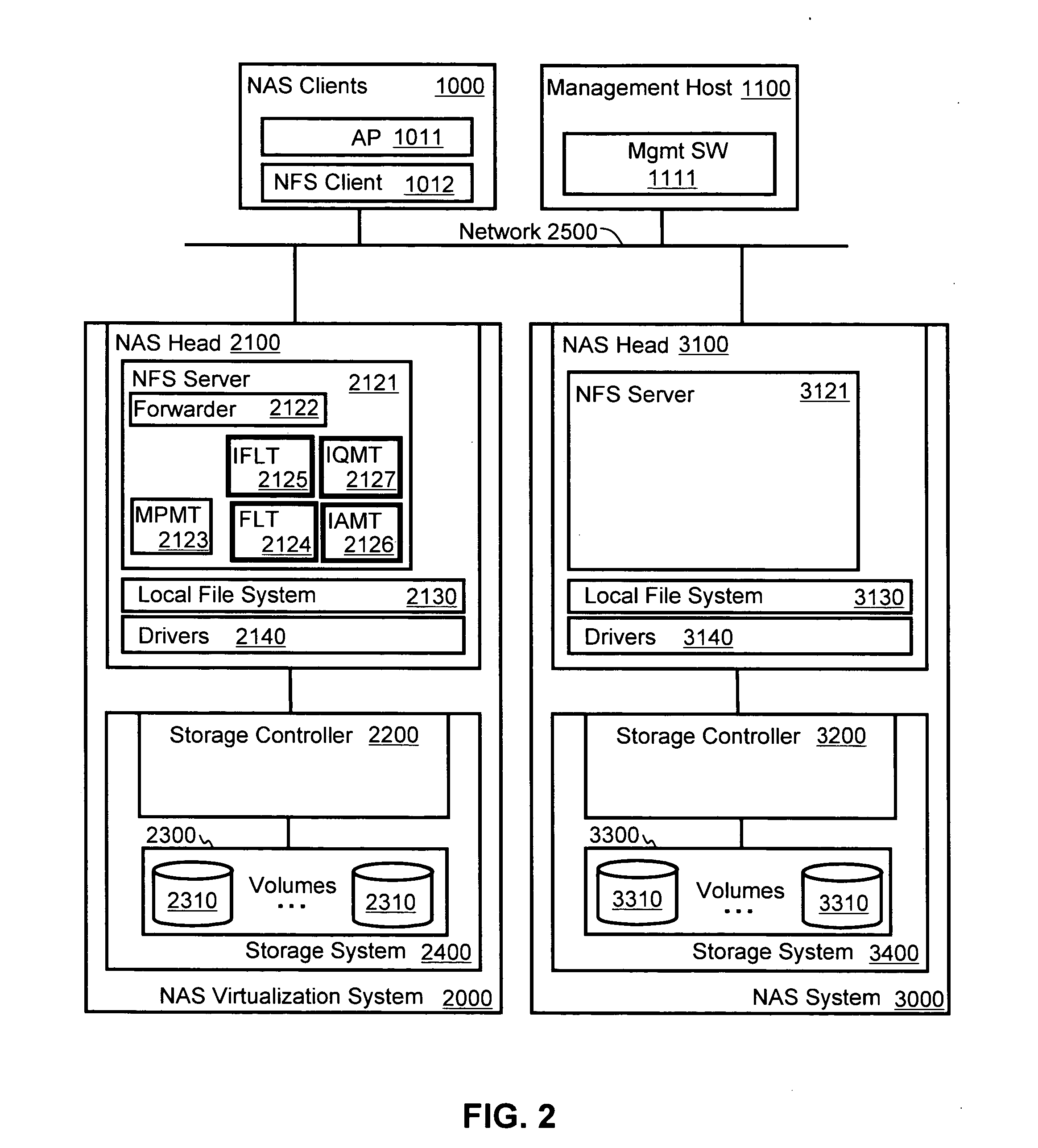
File system virtualization and migration in a Global Name Space on network attached storage (NAS) system, includes file system virtualization by managing file attributes on a NAS virtualization system. The NAS virtualization system receives a file access operation sent from a client computer directed to one of the underlying NAS systems. The NAS virtualization system locates a file identifier included in the file access operation. The file identifier includes node information identifying a second NAS as a destination of the file access operation. The NAS virtualization system removes the node information from the file identifier and forwards the file access operation to the second NAS identified by the node information. The NAS virtualization system receives a reply from the second NAS, adds the node information back to the file identifier included with the response, and forwards the response to the computer with file identifier and appended node information.
Owner:HITACHI LTD
Safe access method of cloud storage system
ActiveCN102546764AReduce access control overheadSolve the dynamic expansion problemKey distribution for secure communicationAccess methodPassword
The invention relates to a safe access method of a cloud storage system, which belongs to the technical field of storage technology and information safety of computer, and solves the problem that secret key is complex to manage and dispense in safe access methods in prior arts. The method of the invention comprises a client progress, an authentication terminal progress and a storage terminal process. The client generates a main secret key and public parameters for each user based on an attribute password mechanism; the authentication terminal loads a user attribute database, a file attribute database and an attribute secret key database. In the invention, attributes of definite user, file and file operation type form an access control string to decide the access right of the user to the file, and thus problems of fine-grained access control and large scale user dynamic expansion in the complex cloud storage system can be solved, thereby greatly reducing the access control expenditure of the cloud storage system and providing an access control mechanism which is flexible, effective and safe for the safe access to the storage system.
Owner:HUAZHONG UNIV OF SCI & TECH
File attributes for flexible linking
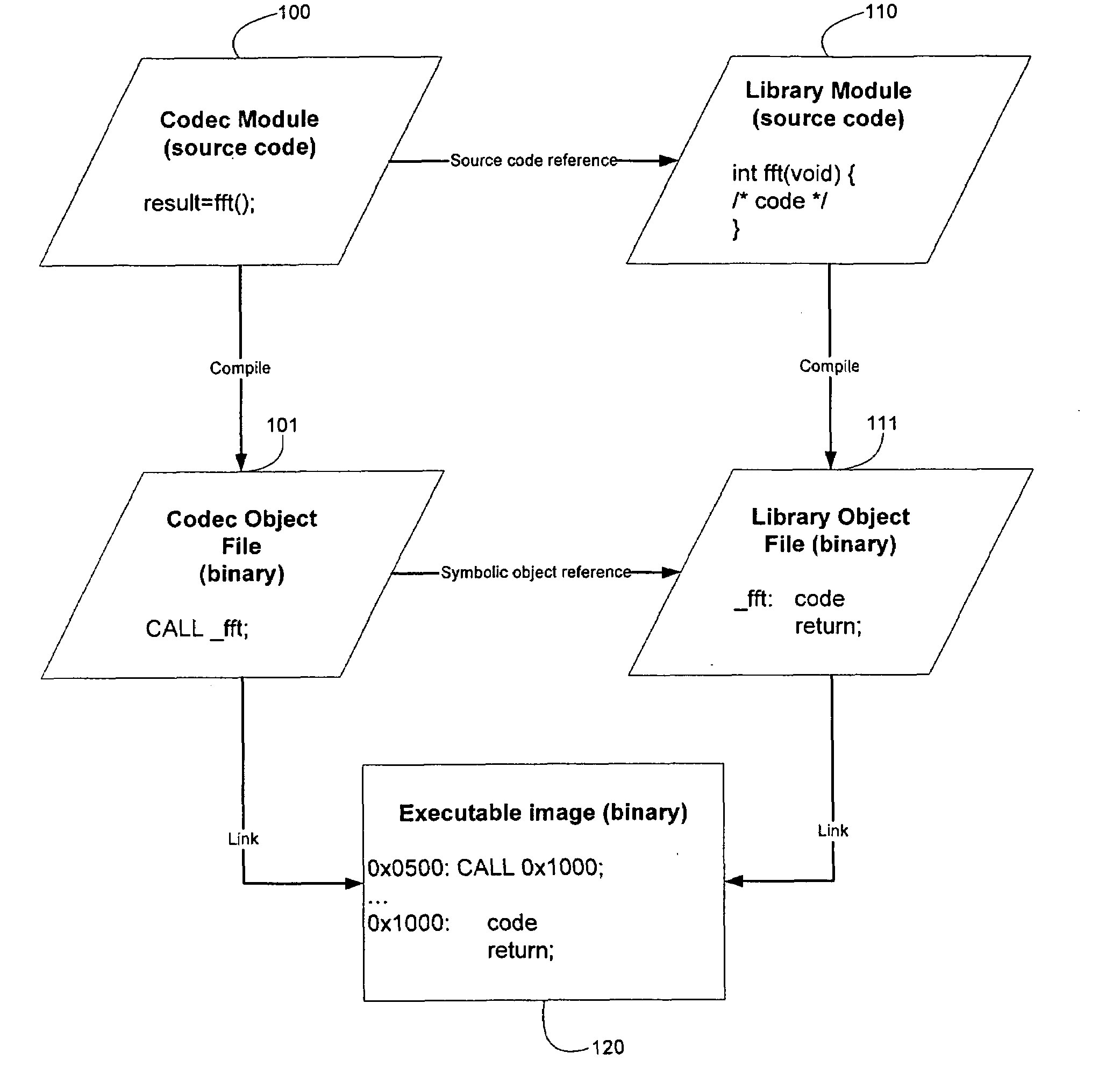
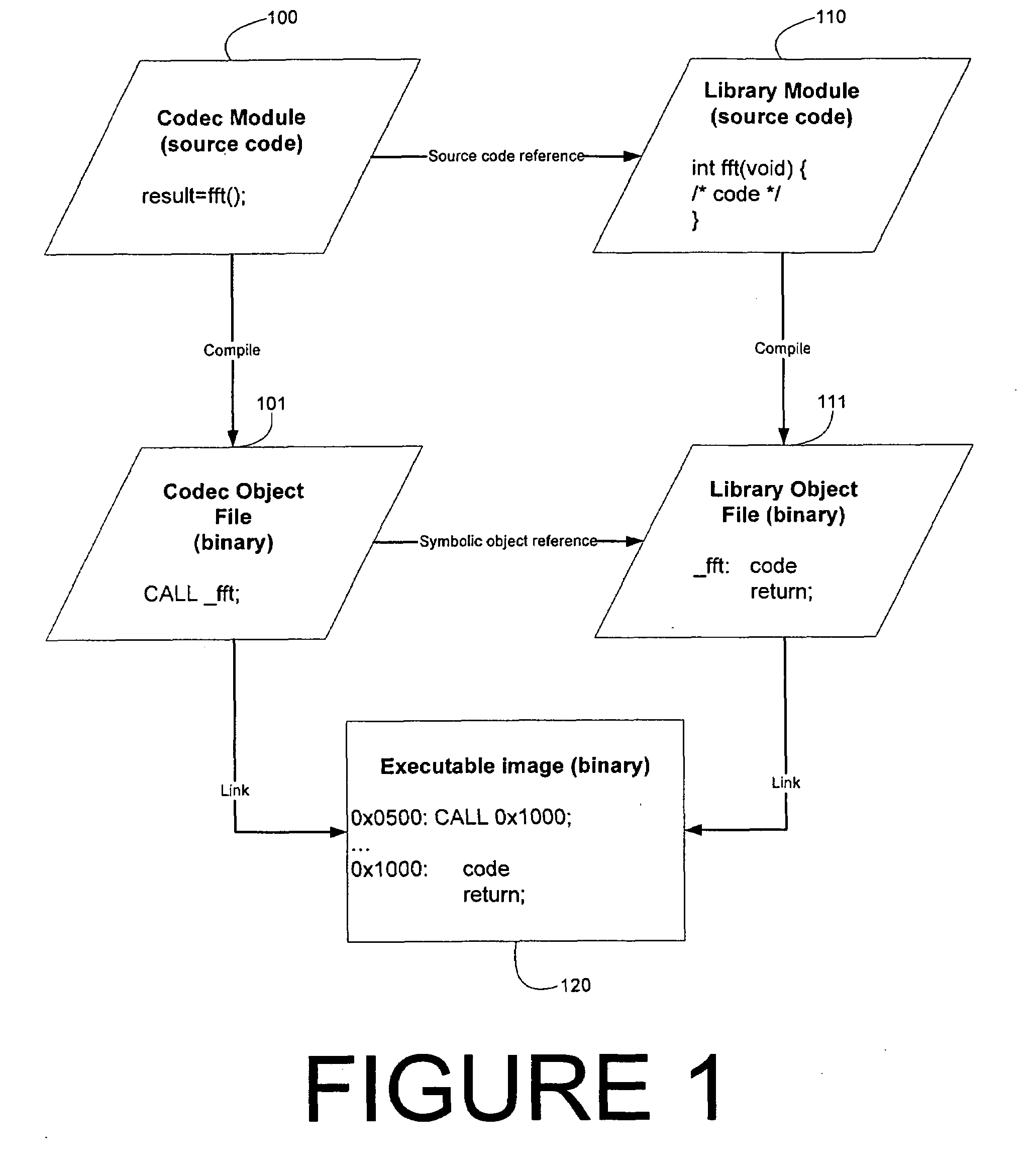
ActiveUS20080098378A1Permit useEffective resourcesLink editingVersion controlObject fileFile attribute
The object file format and linker are enhanced to provide file attributes to allow flexible selection and placement of objects.
Owner:ANALOG DEVICES INC
Data structure generated in accordance with a method for identifying electronic files using derivative attributes created from native file attributes
InactiveUS20060277154A1Patent retrievalSpecial data processing applicationsFile attributeData structure
A data structure for use with a computer-implemented method and program for identifying electronic files from a set of electronic files contains one or more derivative attribute(s) representative of: the relevance to a selected electronic file to a predetermined topic; the amount of electronically readable text for each electronic file; and / or the file class for each electronic file.
Owner:EI DU PONT DE NEMOURS & CO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com