Patents
Literature
54 results about "Stub file" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
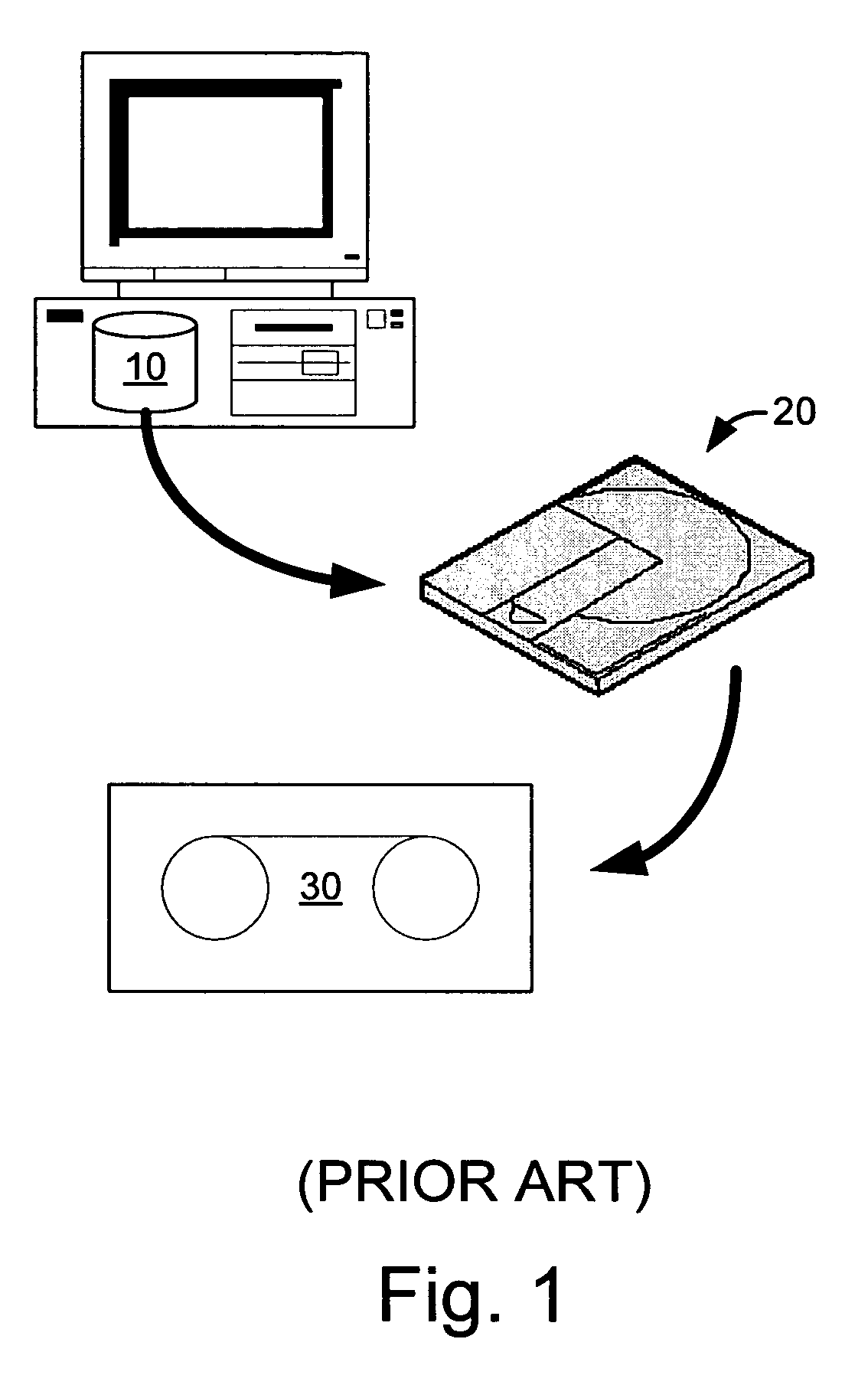
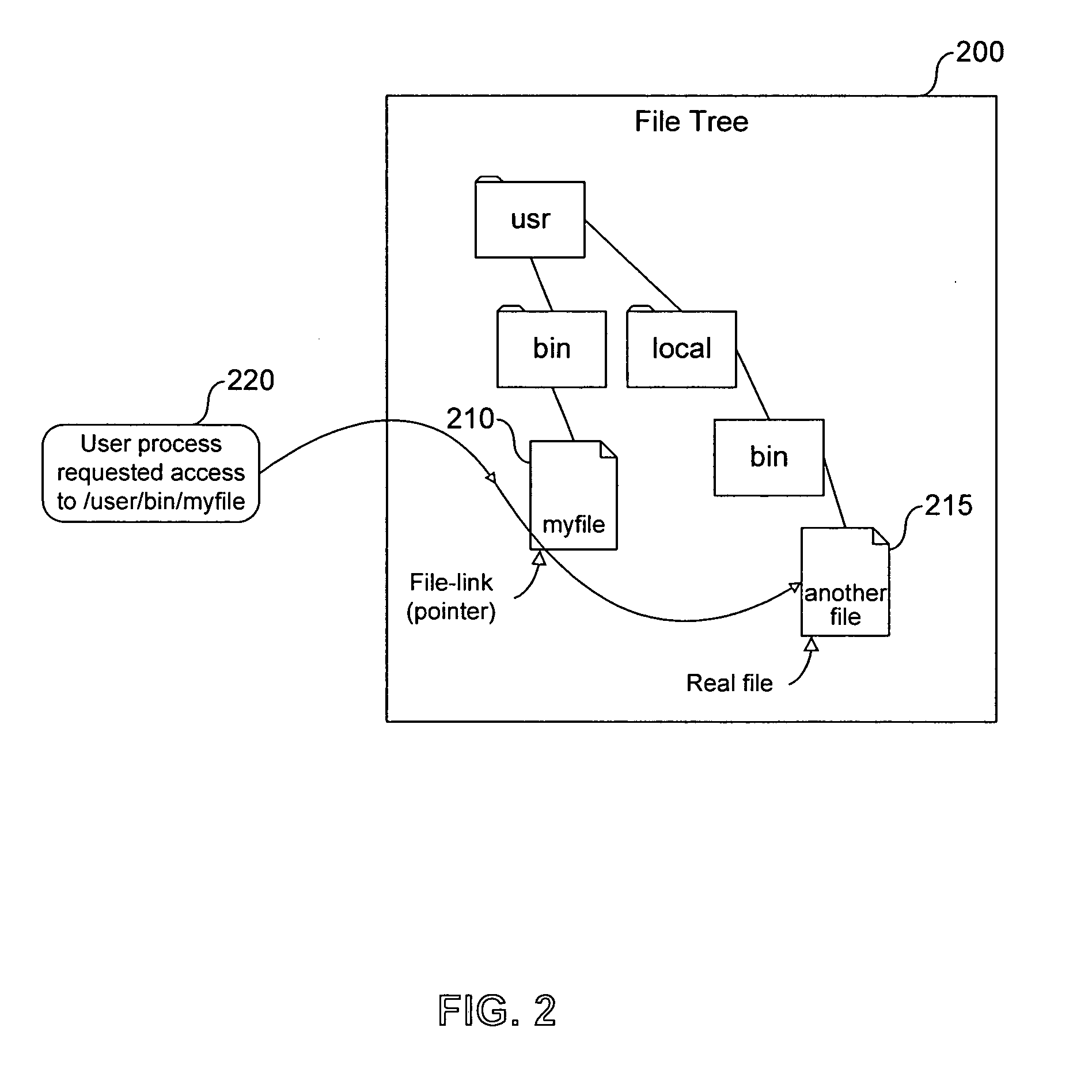
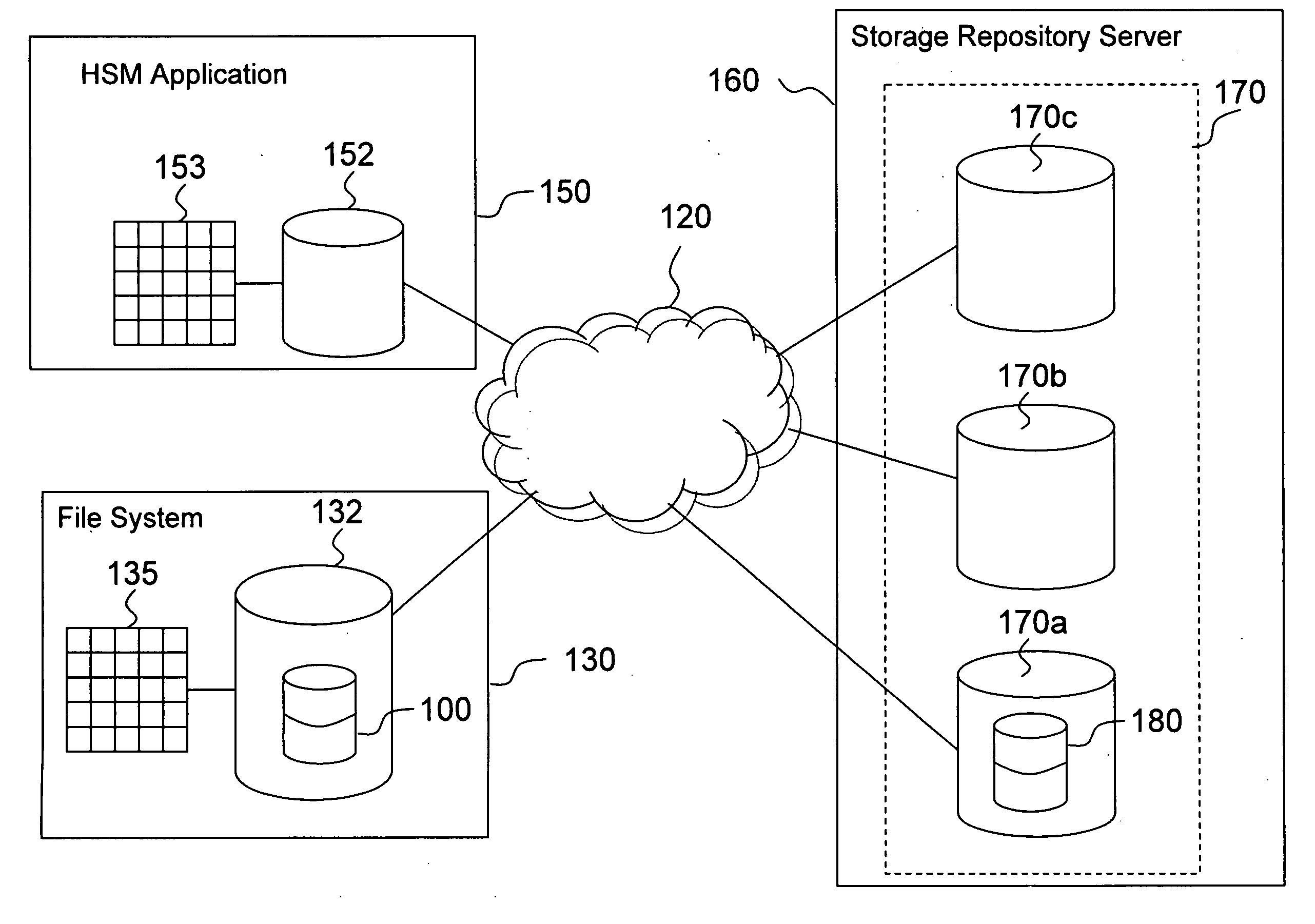
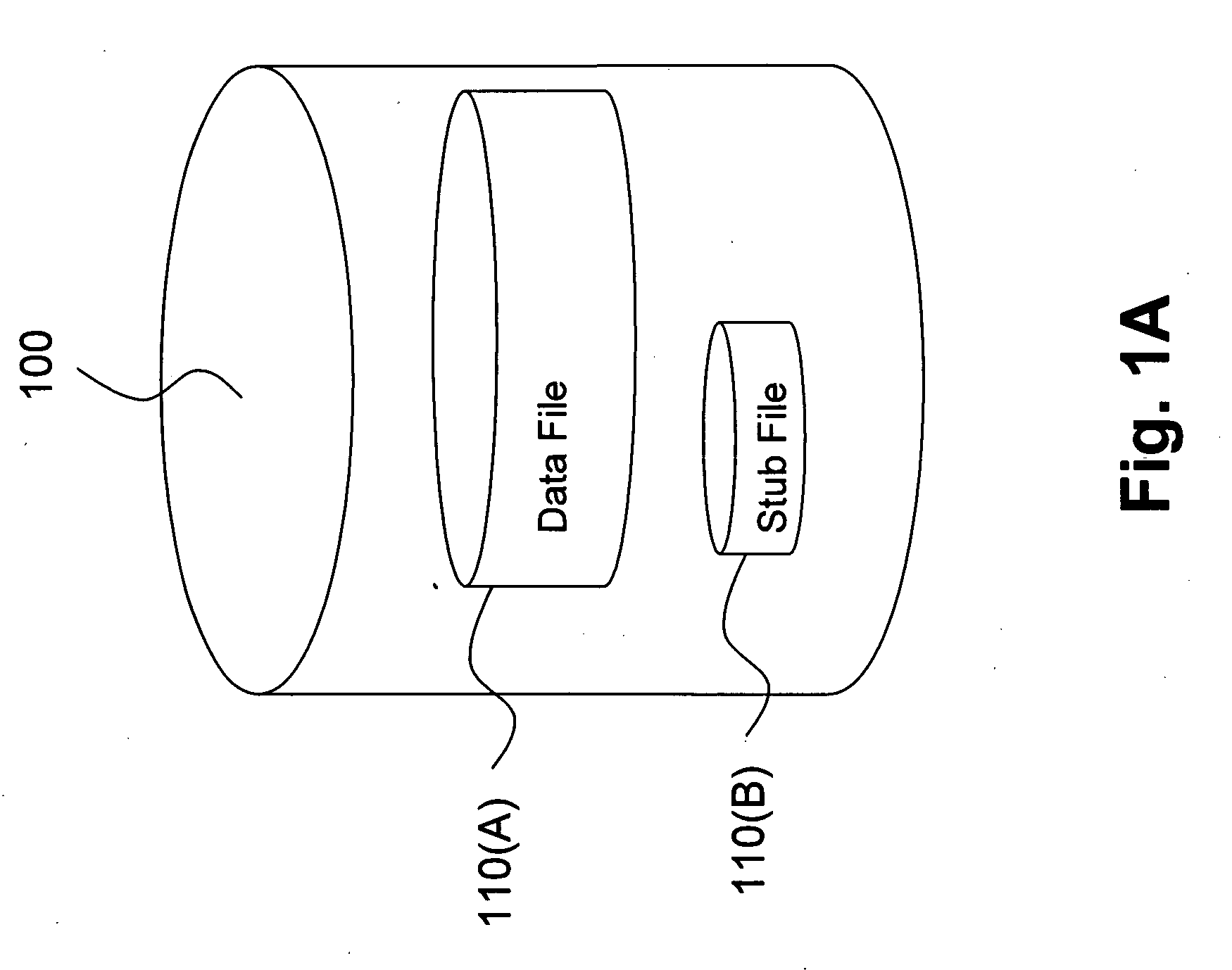
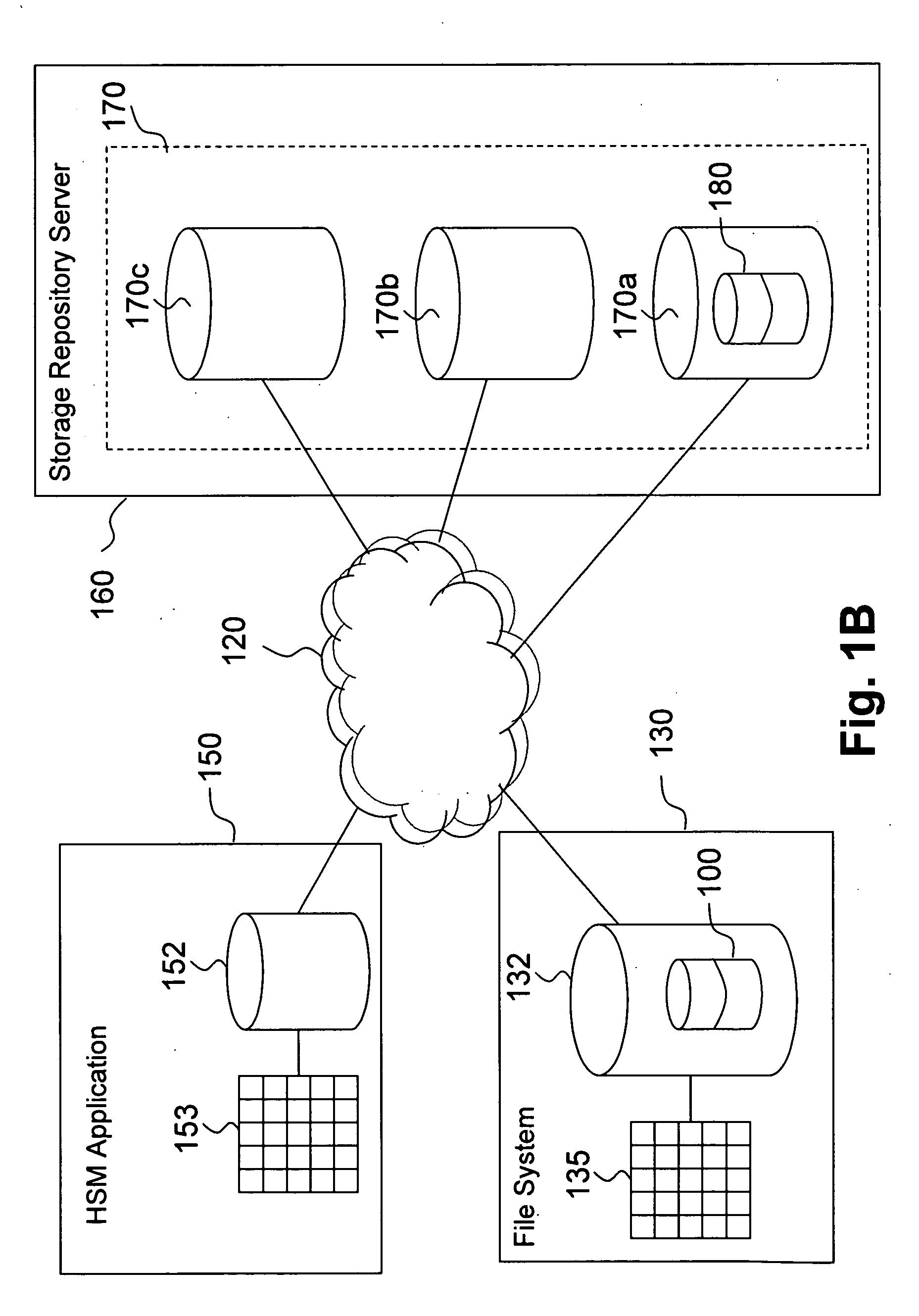
A stub file is a computer file that appears to the user to be on disk and immediately available for use, but is actually held either in part or entirely on a different storage medium. When a stub file is accessed, device driver software intercepts the access, retrieves the data from its actual location and writes it to the file, then allows the user's access to proceed. Typically, users are unaware that the file's data is stored on a different medium, though they may experience a slight delay when accessing such a file.
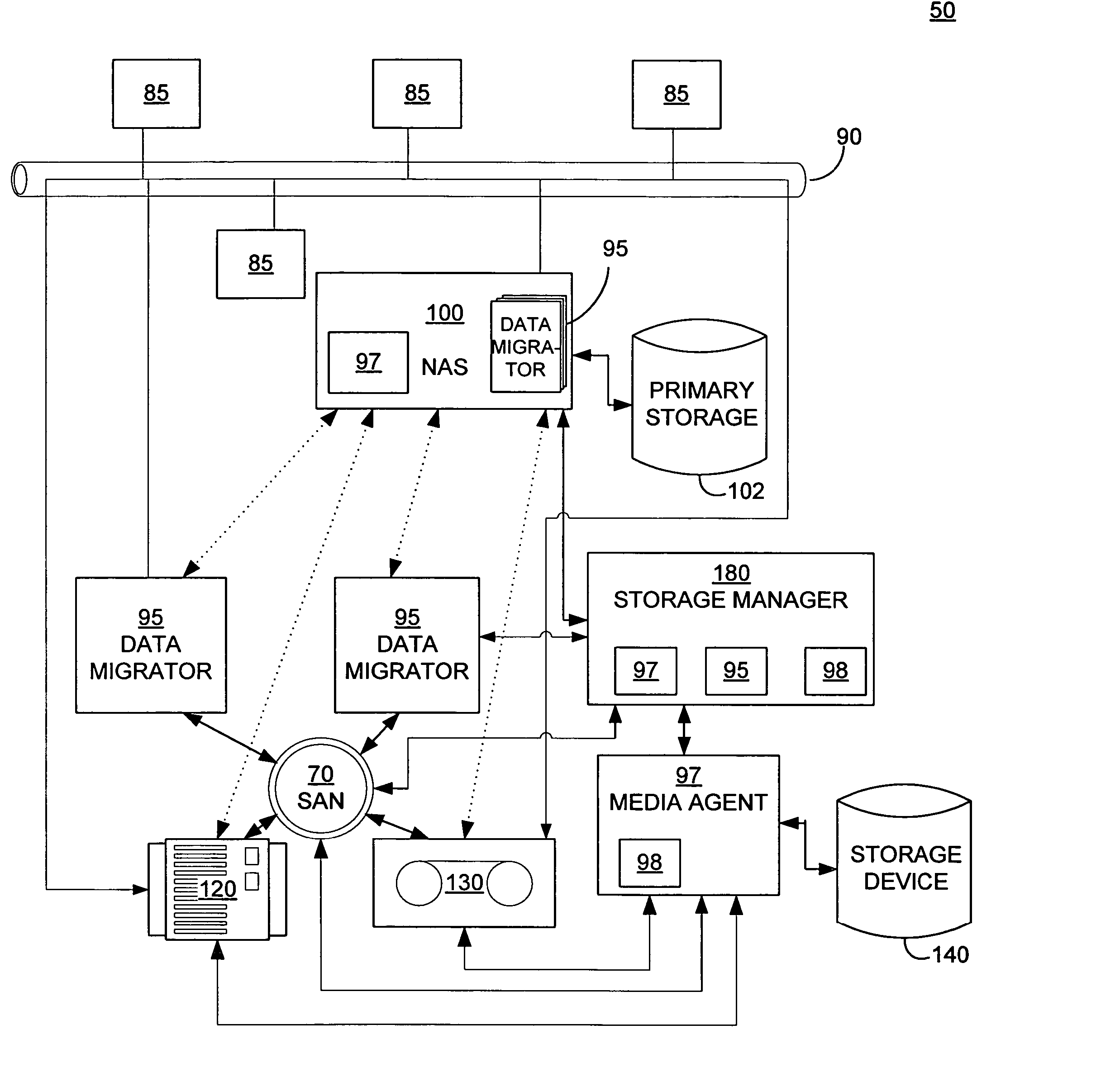
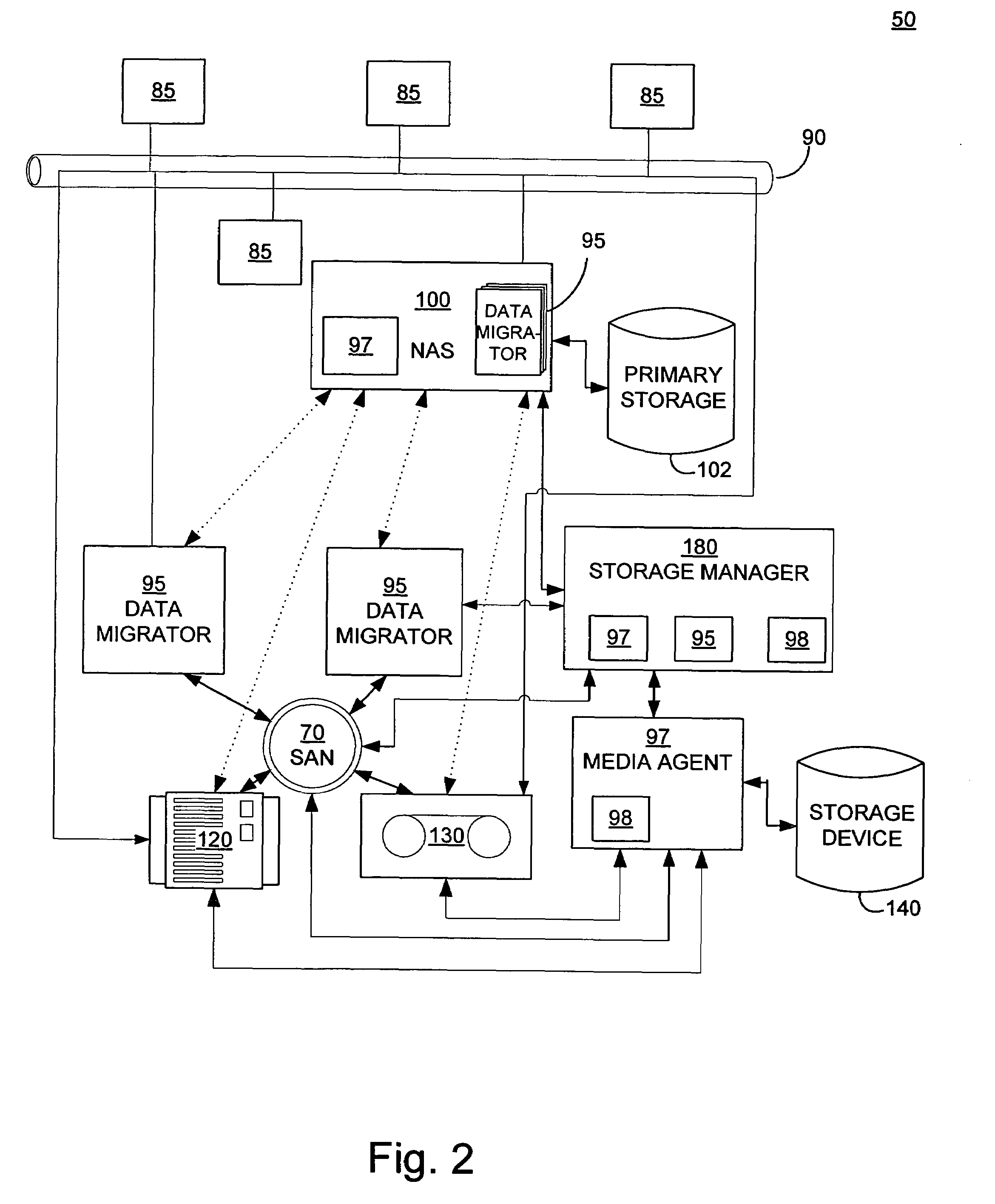
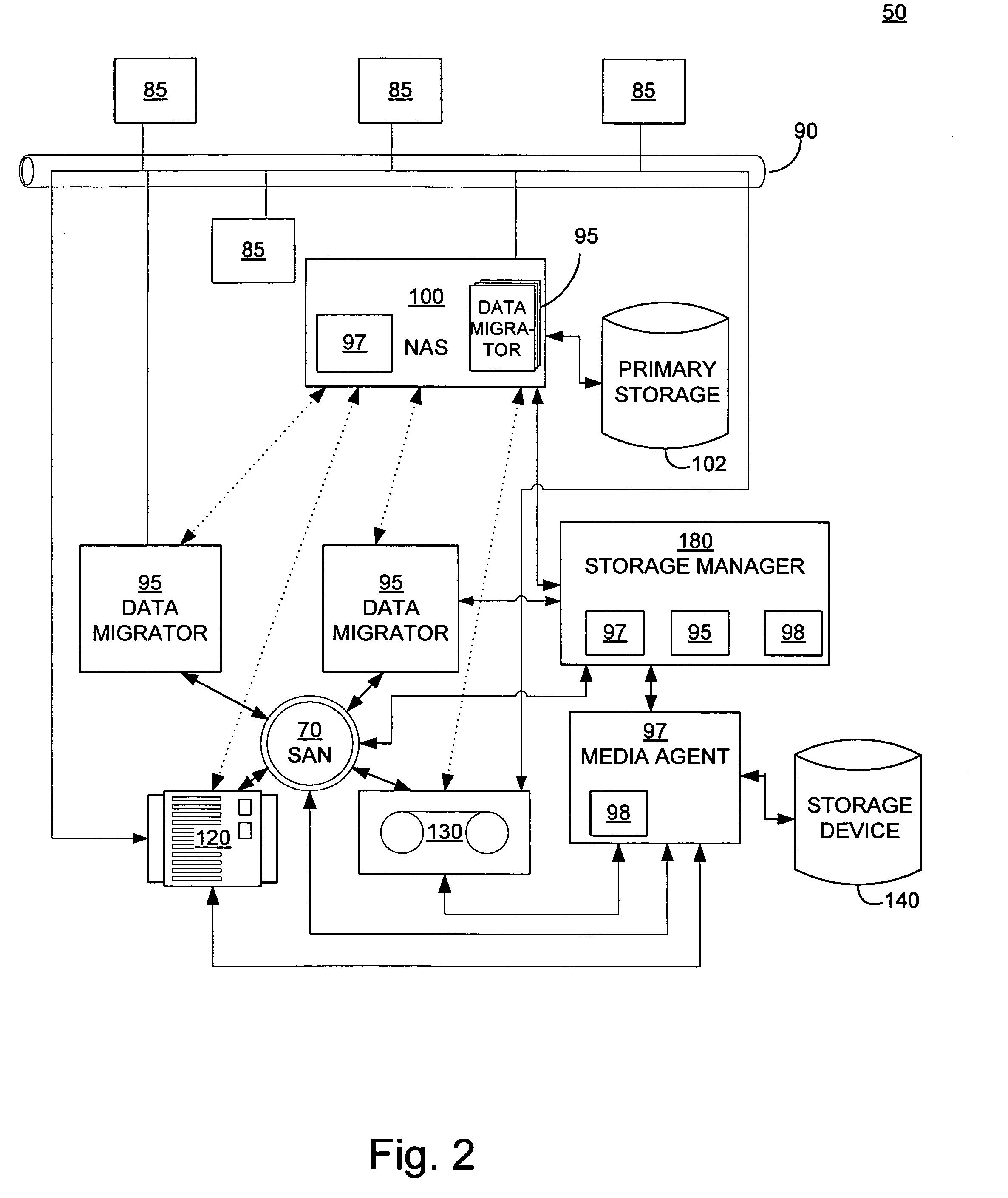
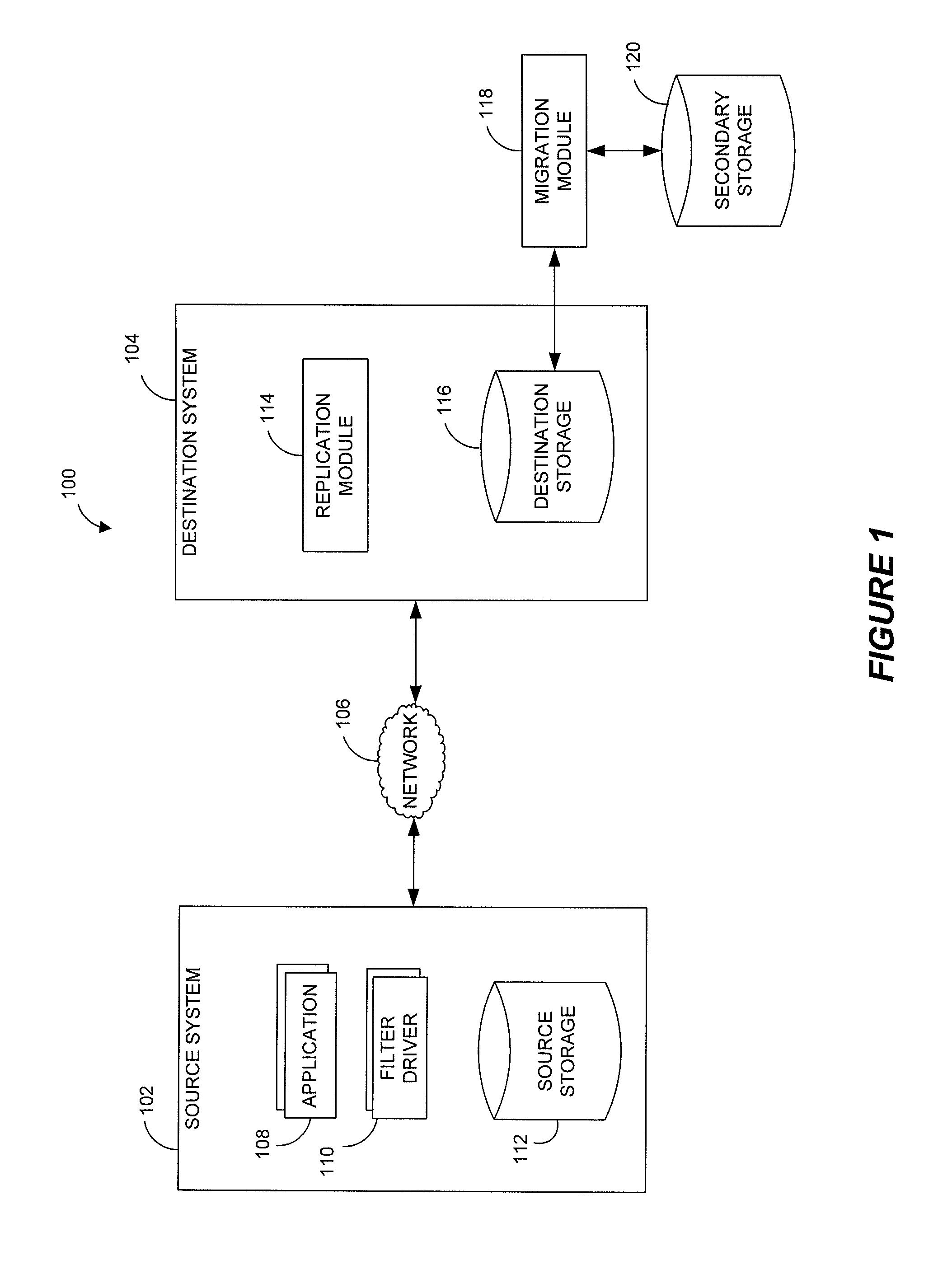
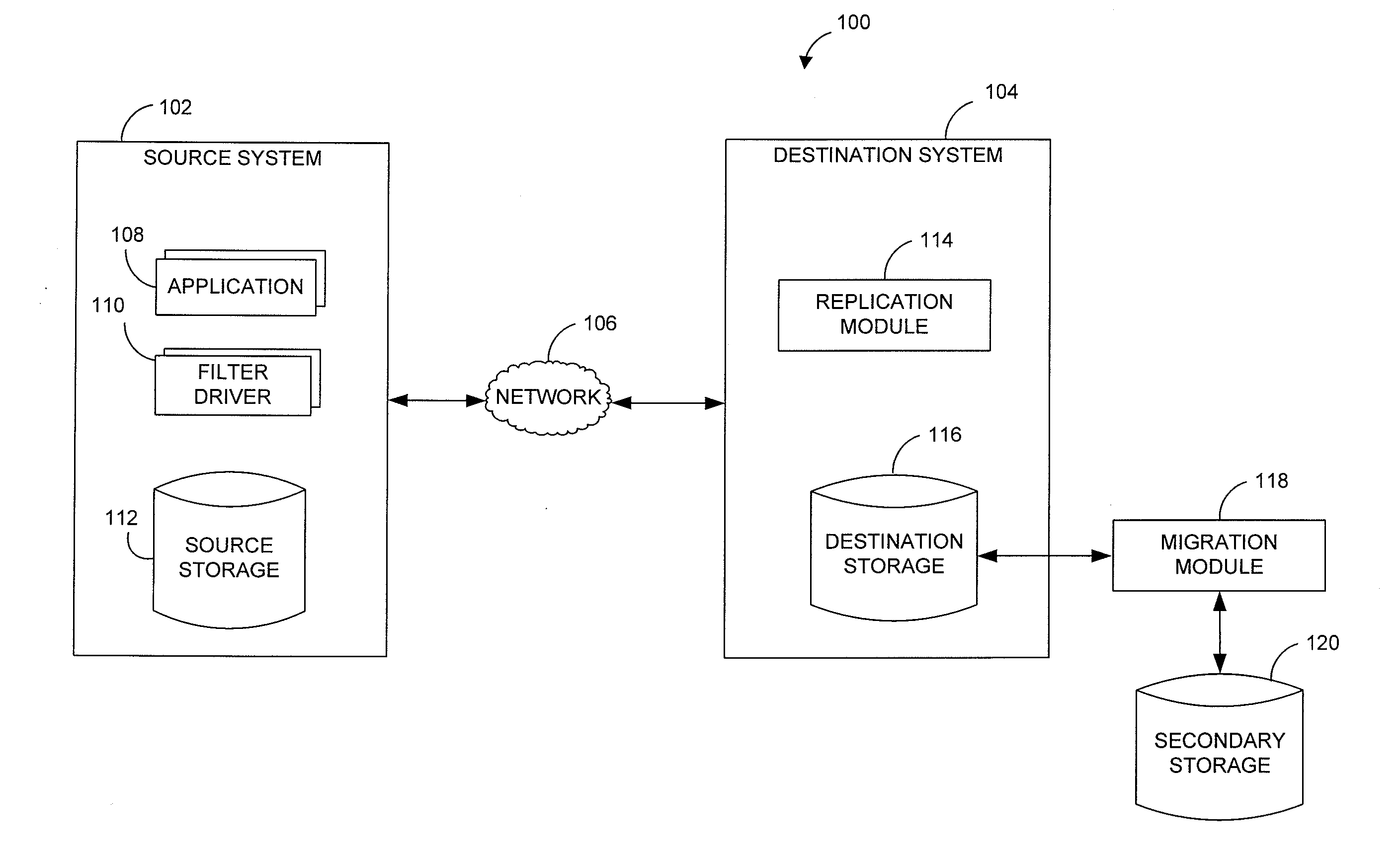
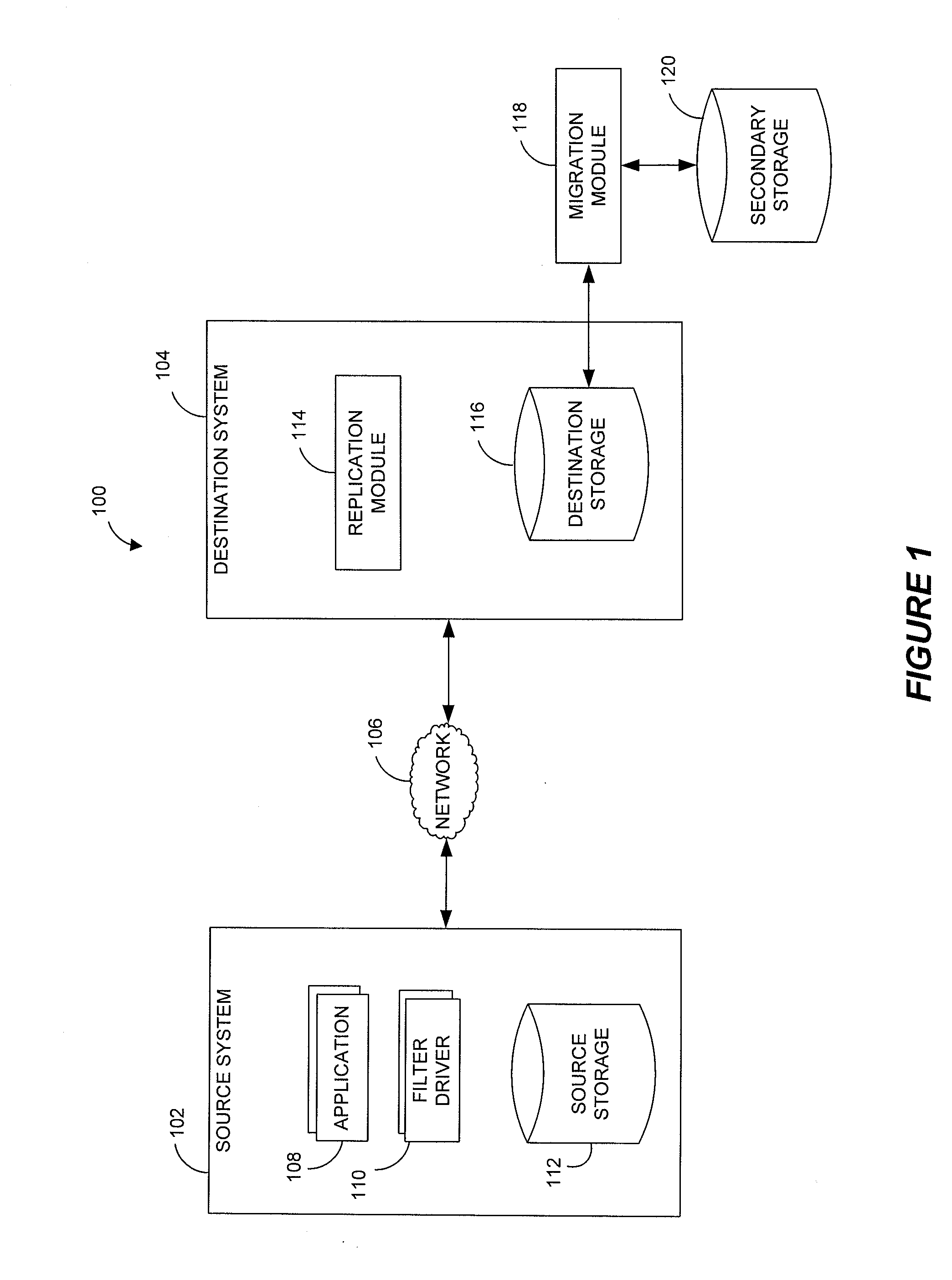
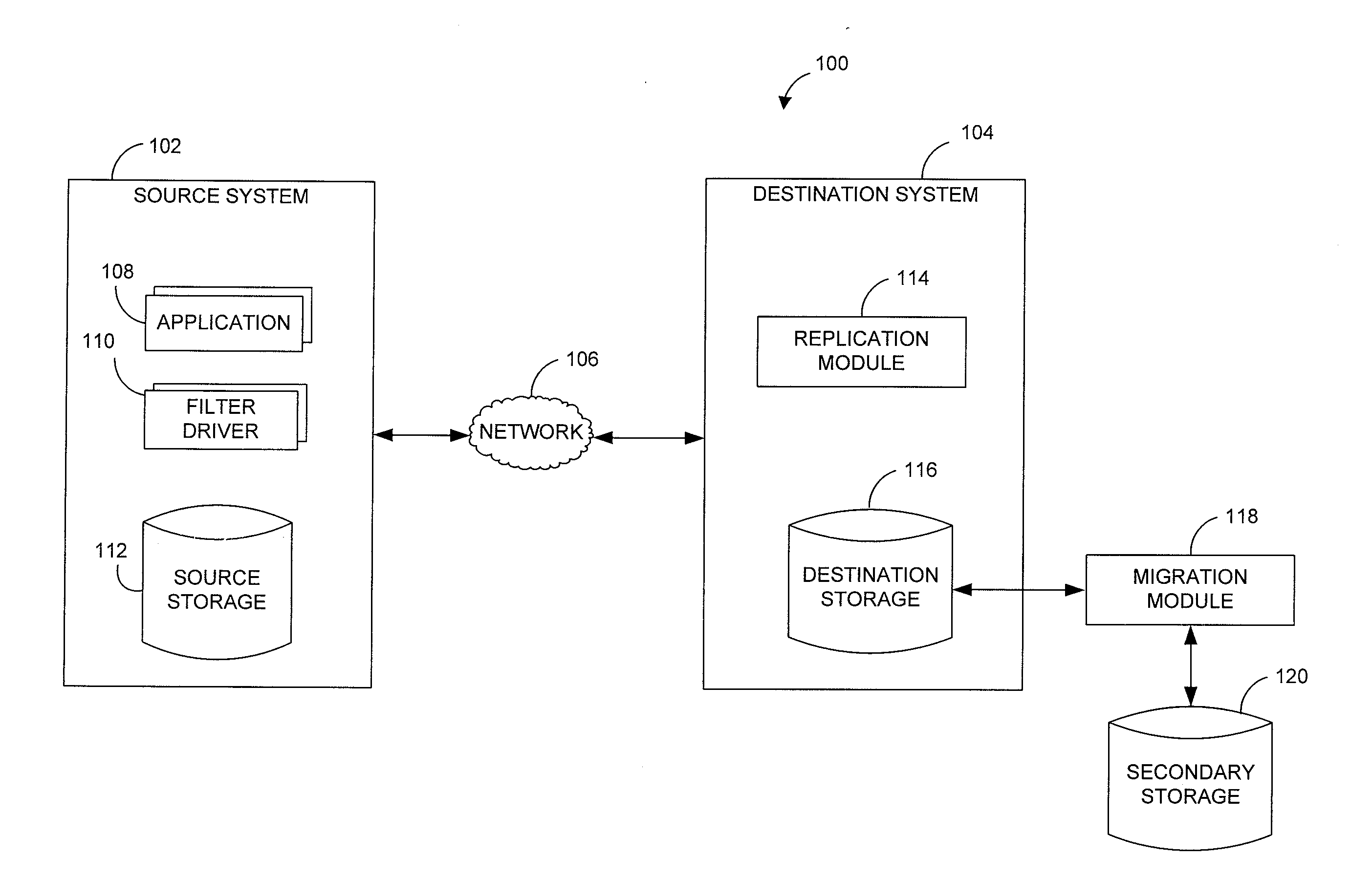
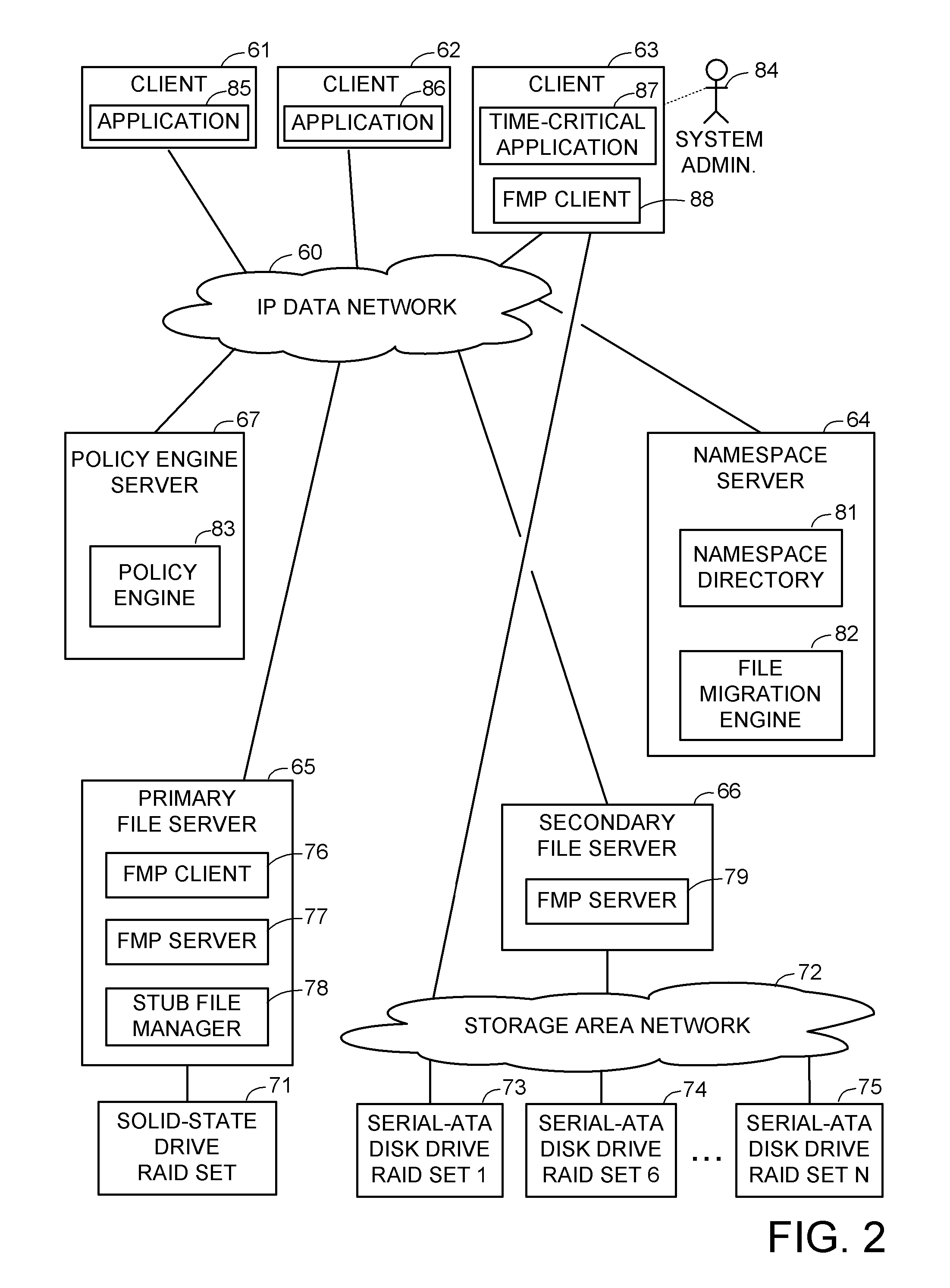
Systems and methods for performing storage operations using network attached storage
ActiveUS7546324B2More processedData processing applicationsDigital data information retrievalAuxiliary memoryData storing
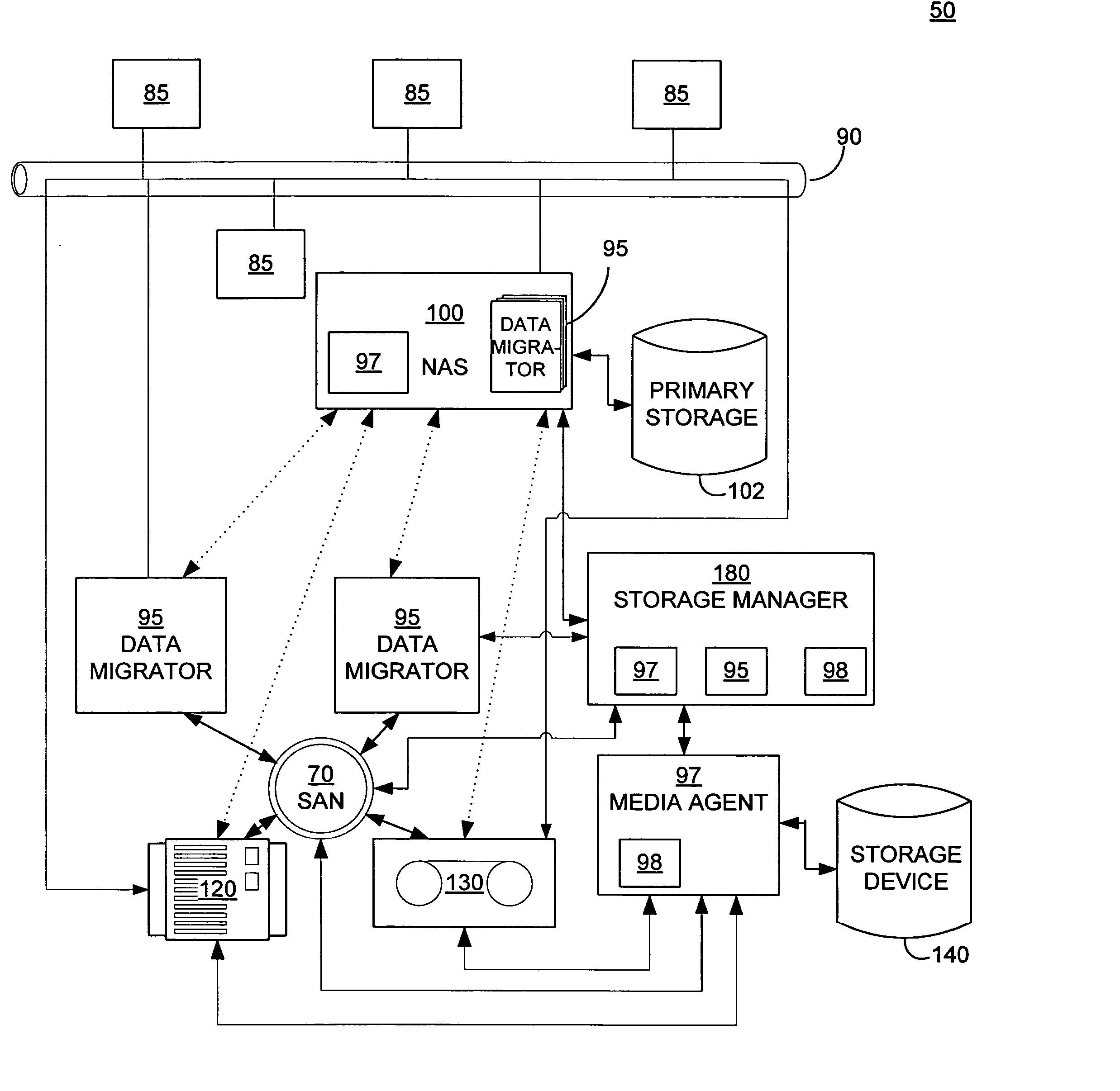
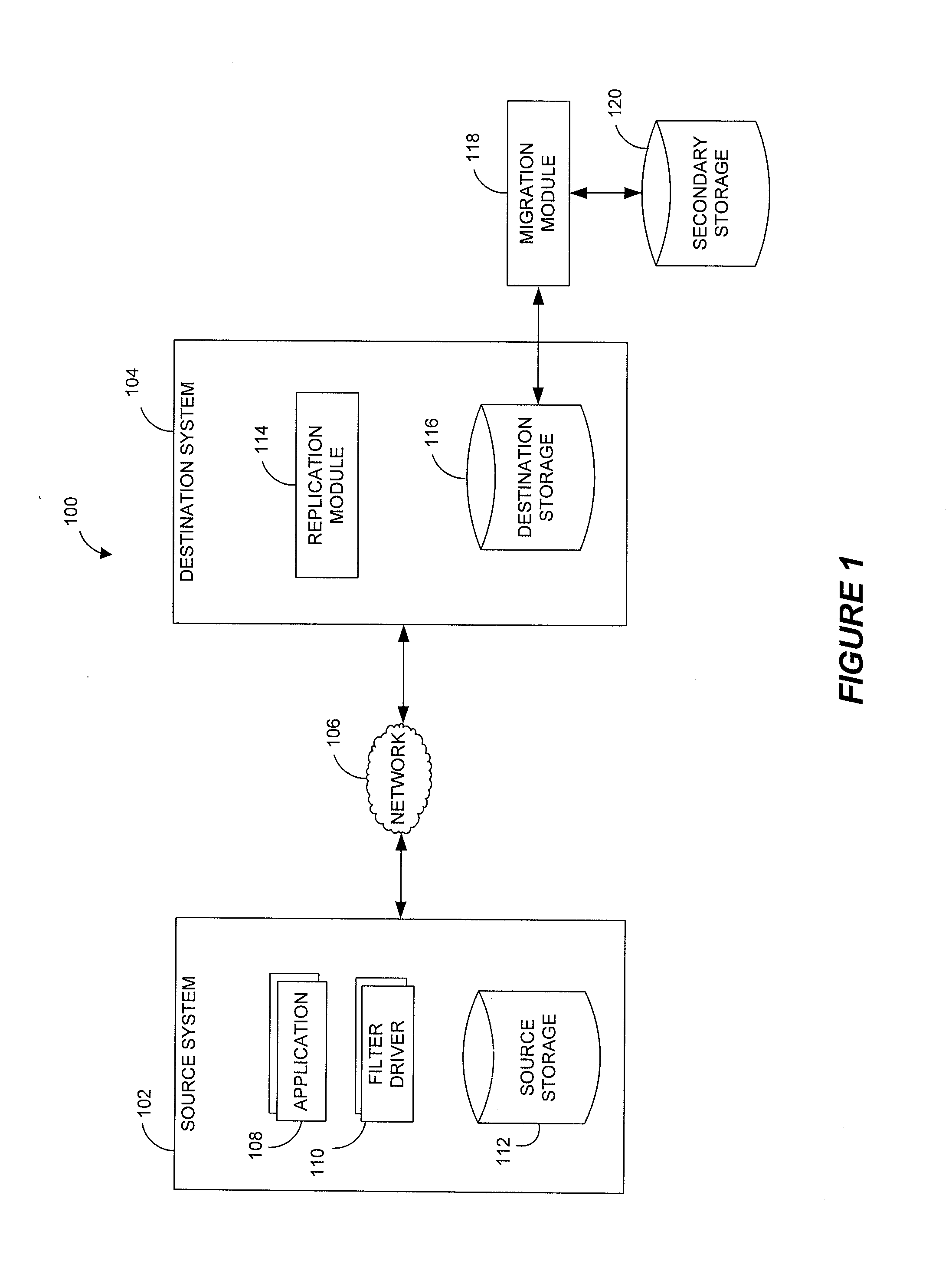
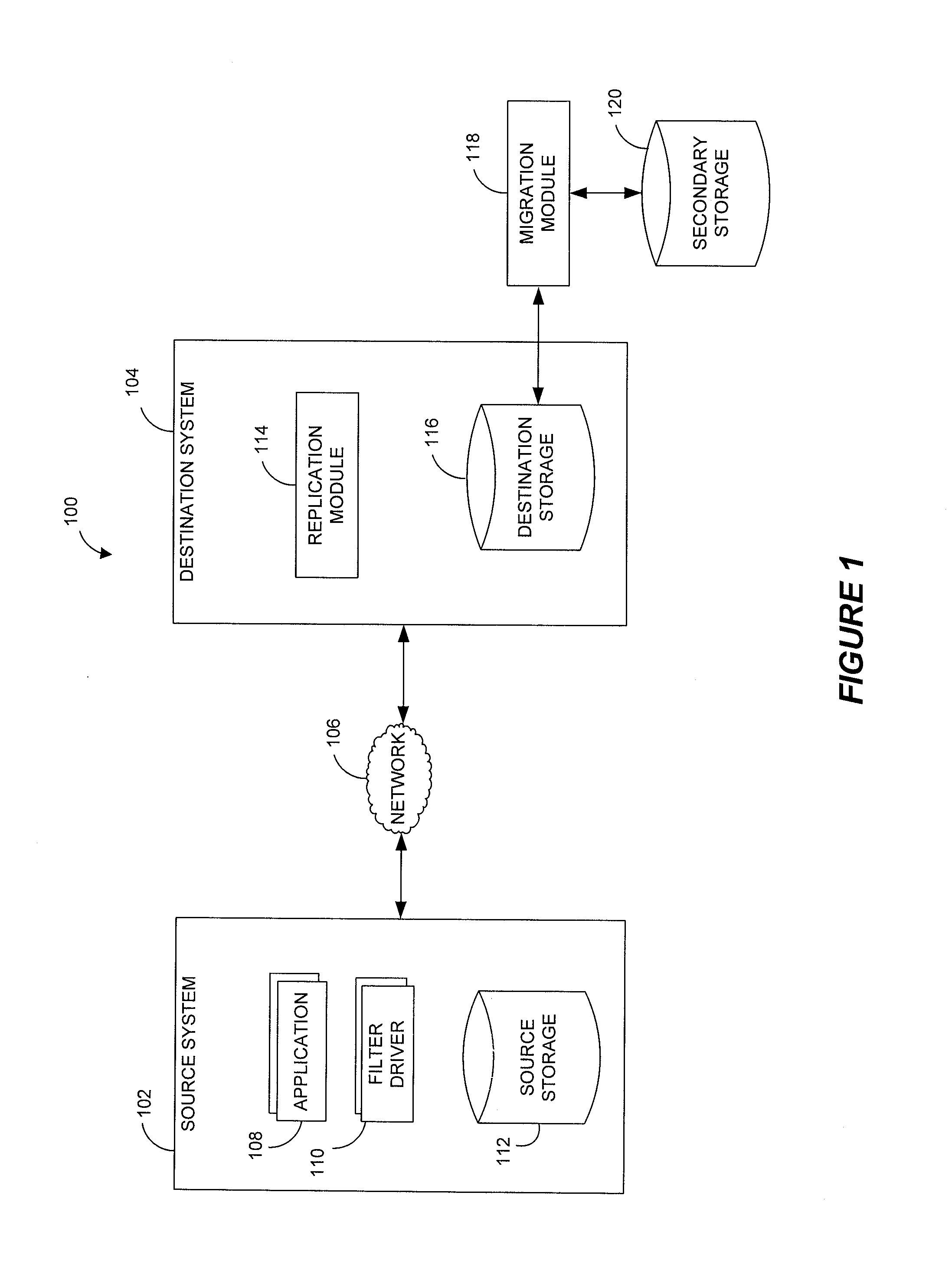
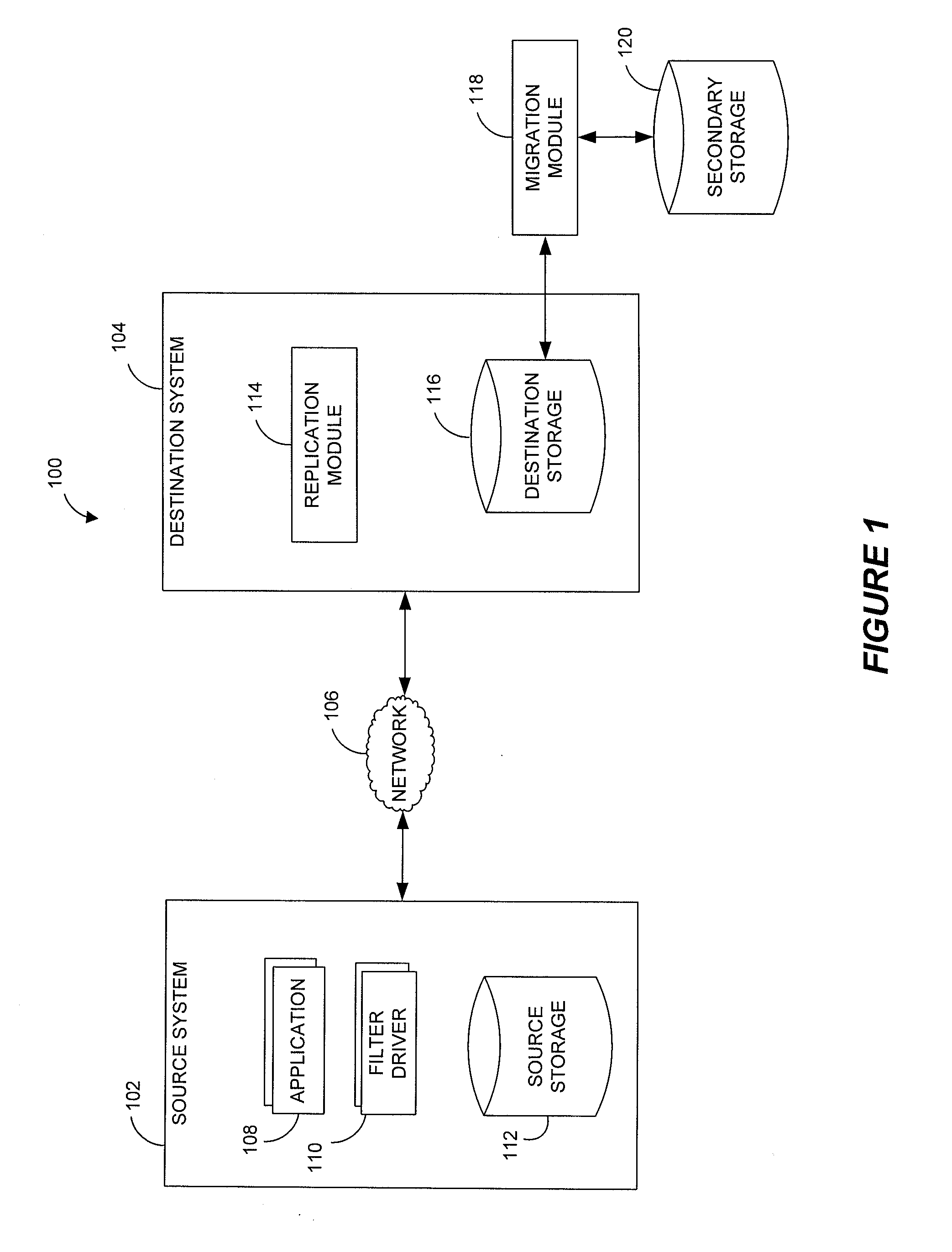
Systems and methods for performing hierarchical storage operations on electronic data in a computer network are provided. In one embodiment, the present invention may store electronic data from a network device to a network attached storage (NAS) device pursuant to certain storage criteria. The data stored on the NAS may be migrated to a secondary storage and a stub file having a pointer pointing to the secondary storage may be put at the location the data was previously stored on the NAS. The stub file may redirect the network device to the secondary storage if a read request for the data is received from the network device.
Owner:COMMVAULT SYST INC
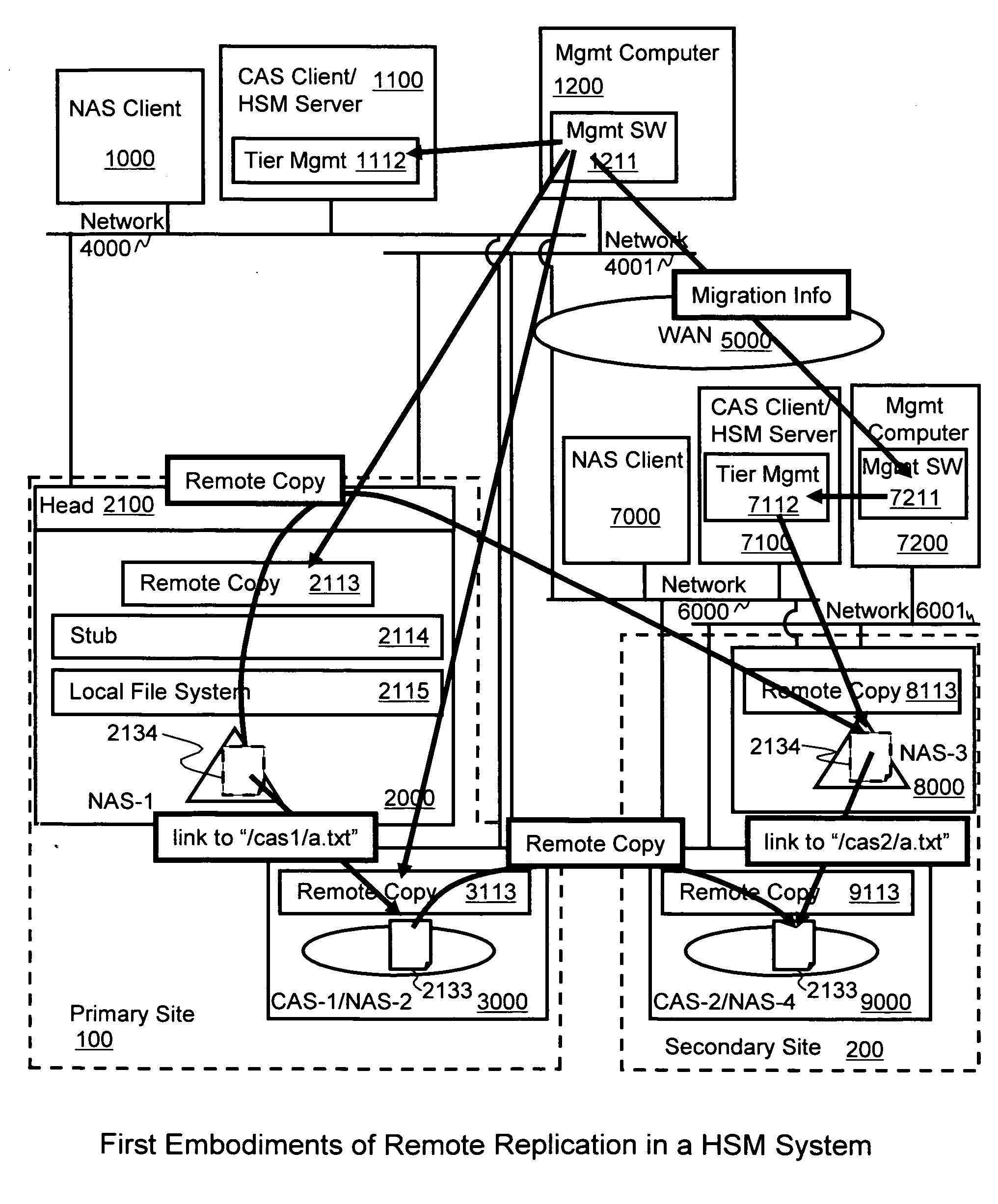
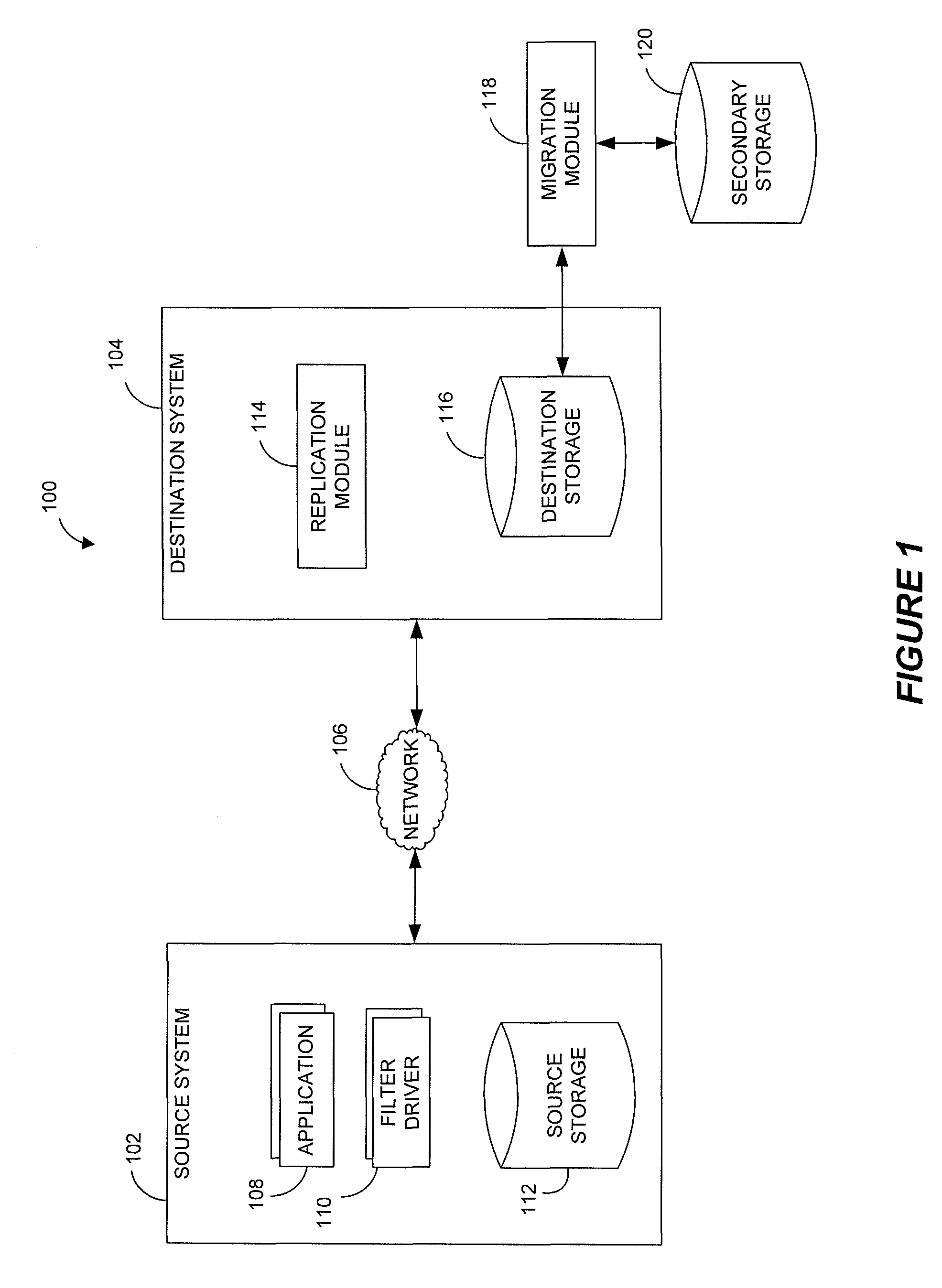
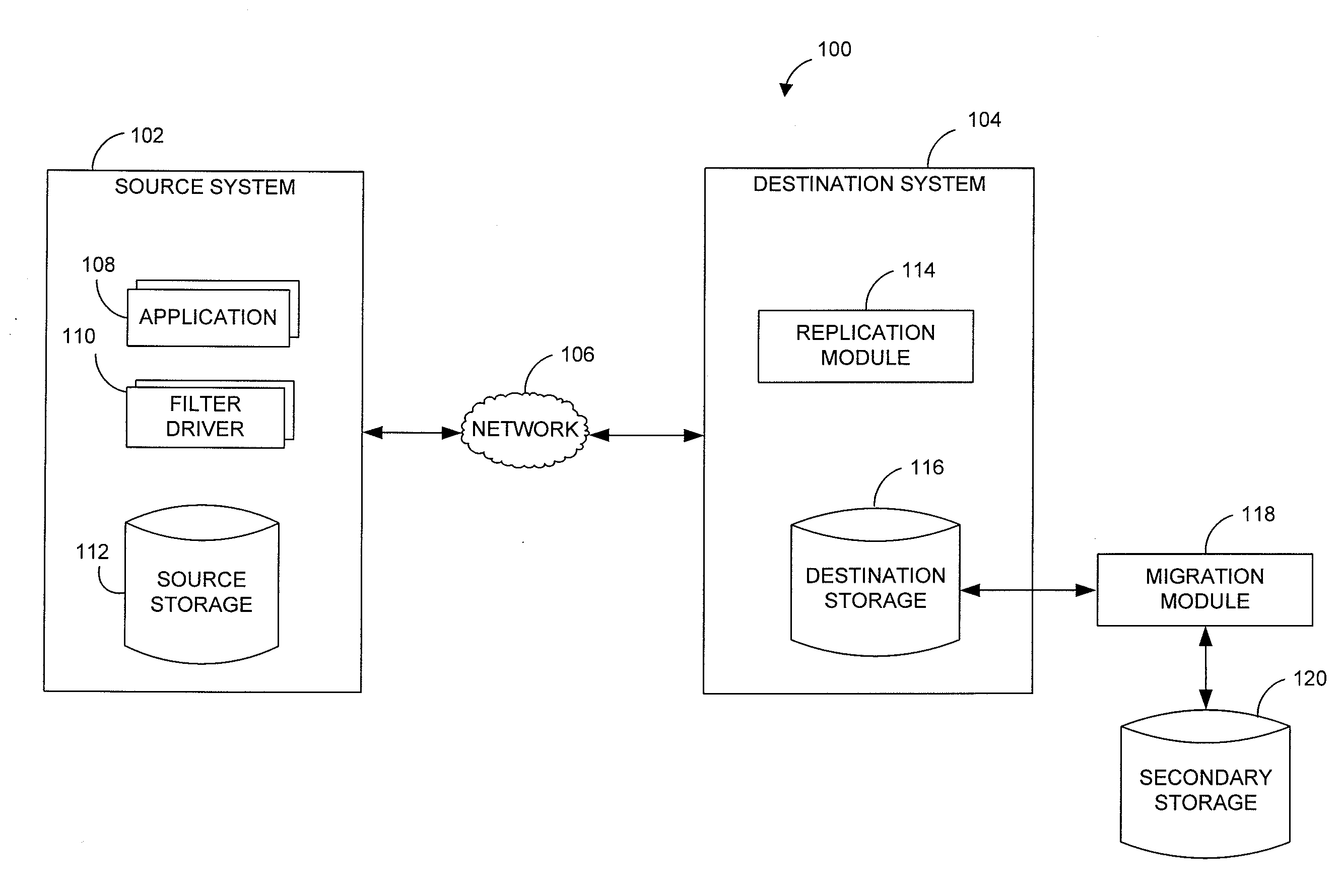
Integrated remote replication in hierarchical storage systems
InactiveUS20090300079A1Digital data processing detailsMemory adressing/allocation/relocationHybrid storage systemOperating system
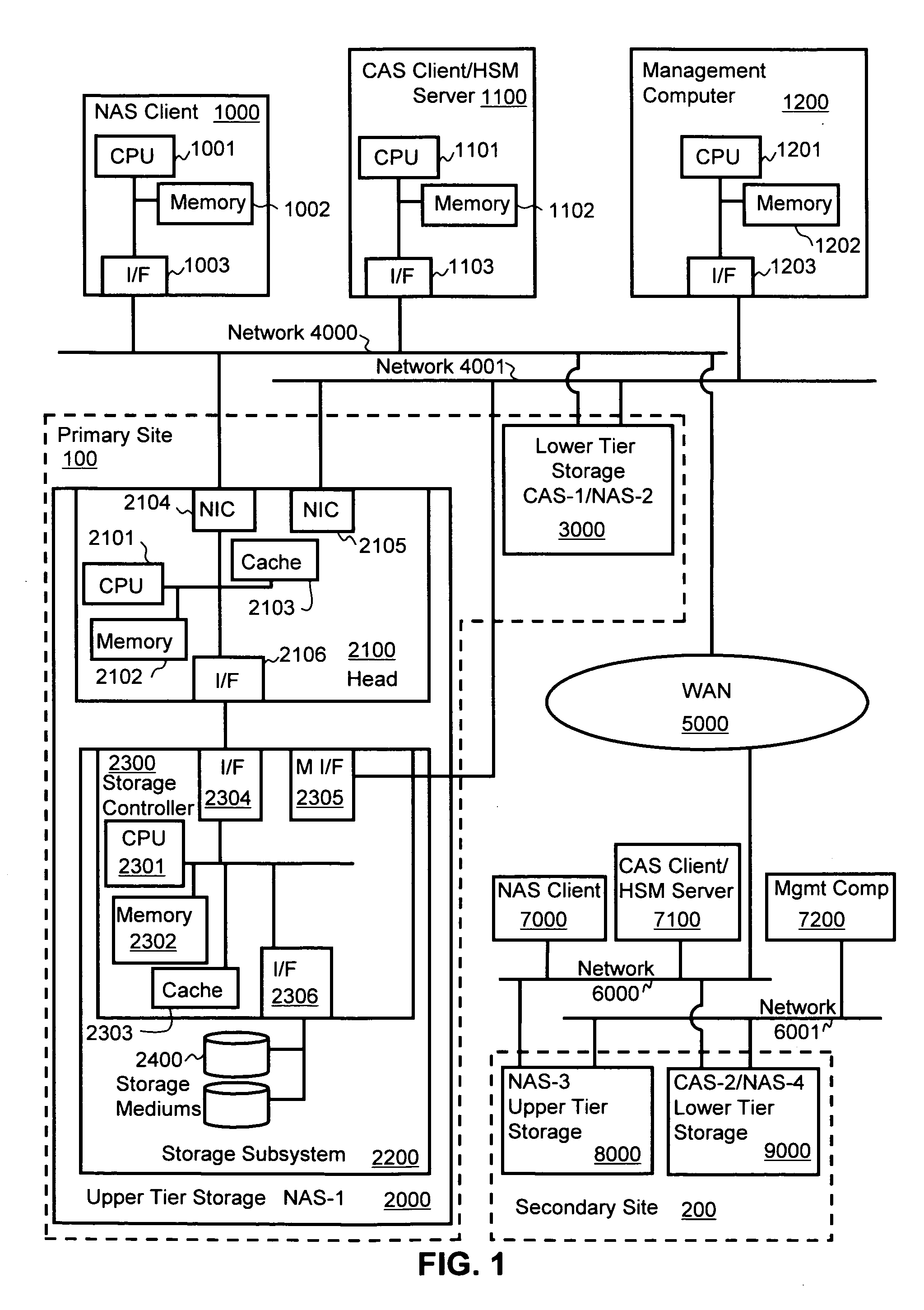
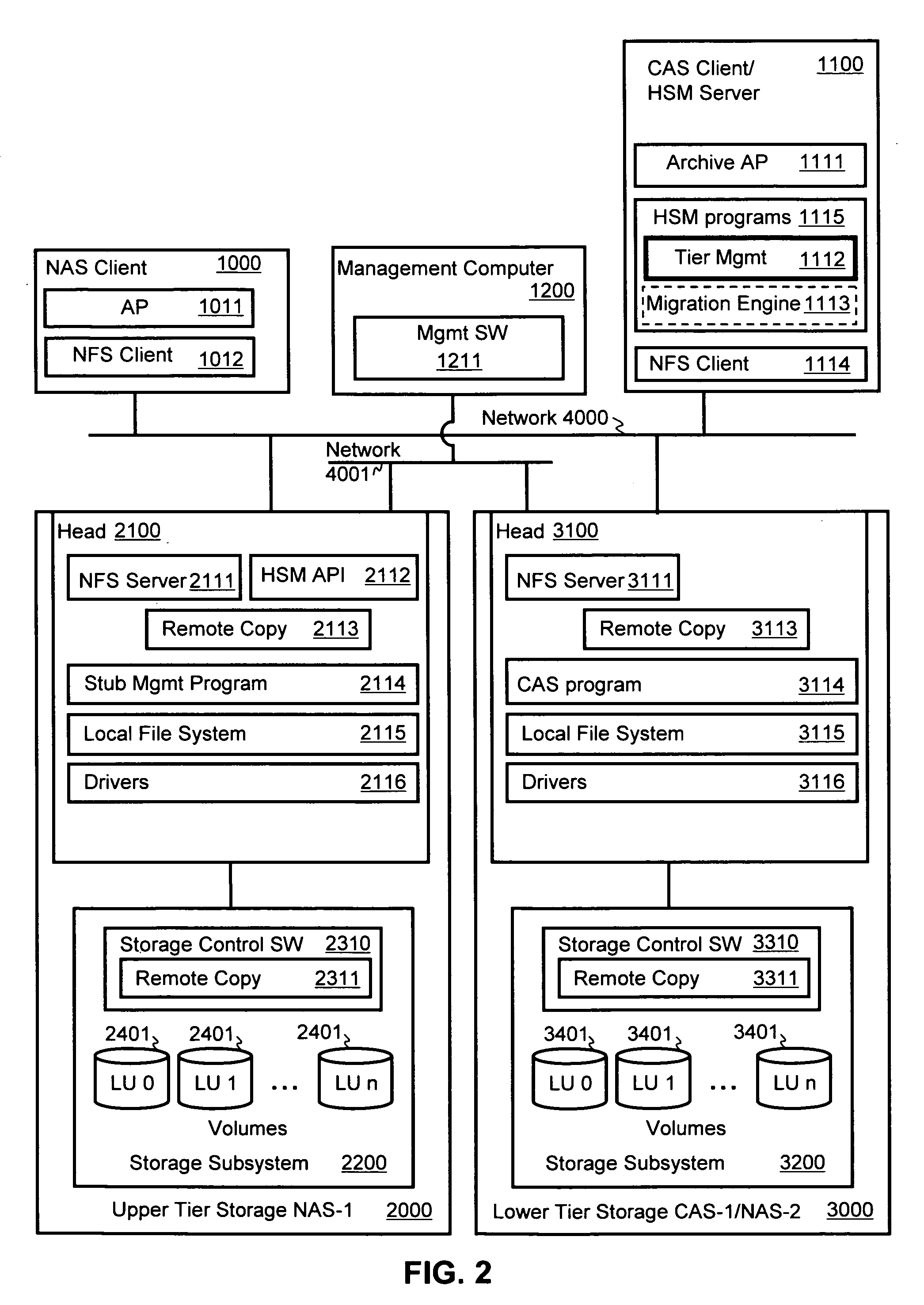
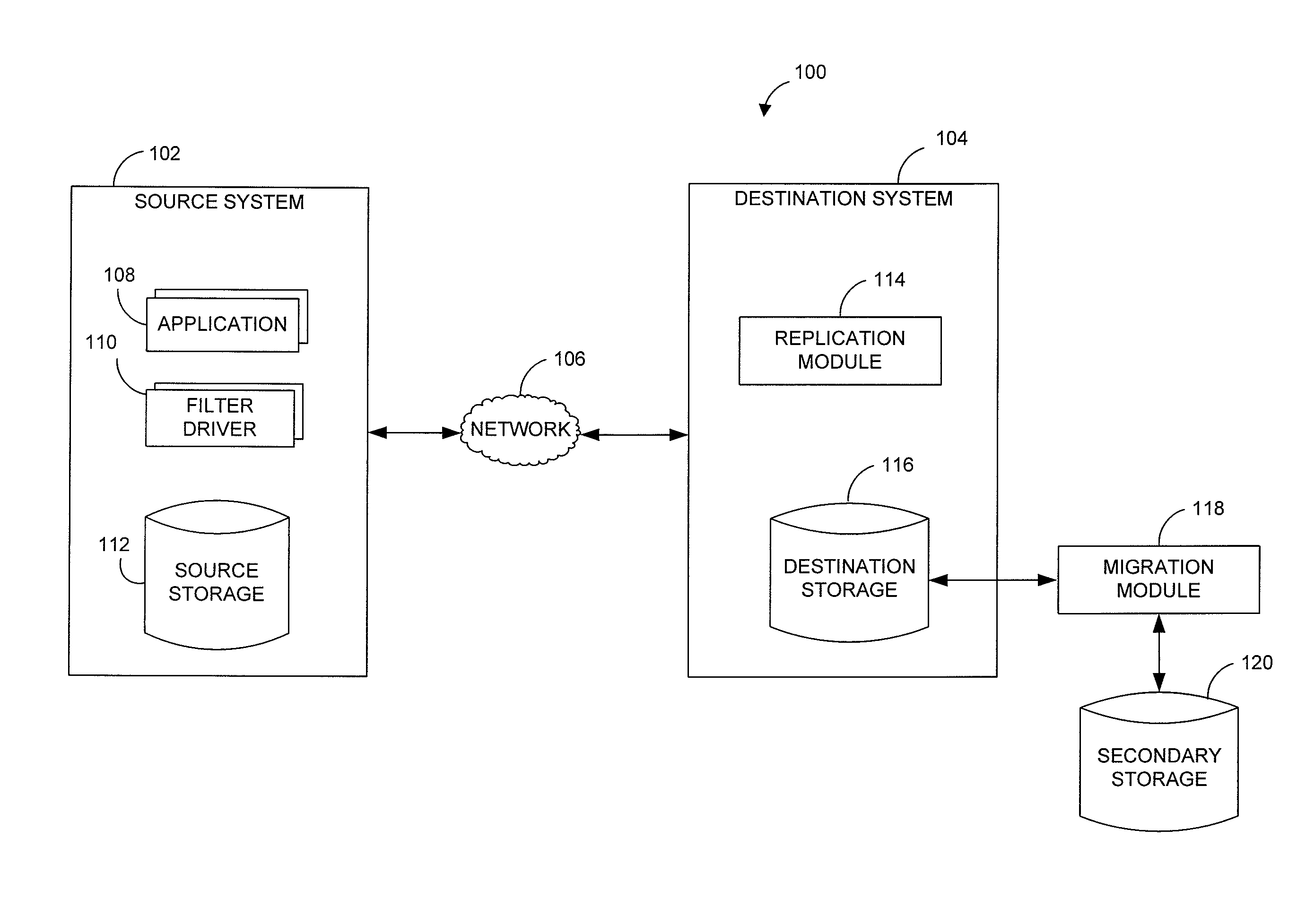
Remote replication is implemented with hierarchical storage. In exemplary embodiments, a first storage site has a first storage system providing an upper tier of storage and a second storage system providing a lower tier of storage. A remote second storage site has third and fourth storage systems configured to receive remote replication from the first and second storage systems, respectively. When a file is migrated from the upper tier to the lower tier, a stub file is stored in place of the migrated file indicating a storage location of the migrated file on the second storage system. When copies of the migrated file and the stub file are replicated to the fourth and third storage systems, respectively, information is transmitted to the second storage site for linking the copy of the stub file at the third storage system to the copy of the migrated file at the fourth storage system.
Owner:HITACHI LTD
Systems and methods for performing storage operations using network attached storage
ActiveUS20060010154A1More processedData processing applicationsDigital data information retrievalAuxiliary memoryData storing
Systems and methods for performing hierarchical storage operations on electronic data in a computer network are provided. In one embodiment, the present invention may store electronic data from a network device to a network attached storage (NAS) device pursuant to certain storage criteria. The data stored on the NAS may be migrated to a secondary storage and a stub file having a pointer pointing to the secondary storage may be put at the location the data was previously stored on the NAS. The stub file may redirect the network device to the secondary storage if a read request for the data is received from the network device.
Owner:COMMVAULT SYST INC
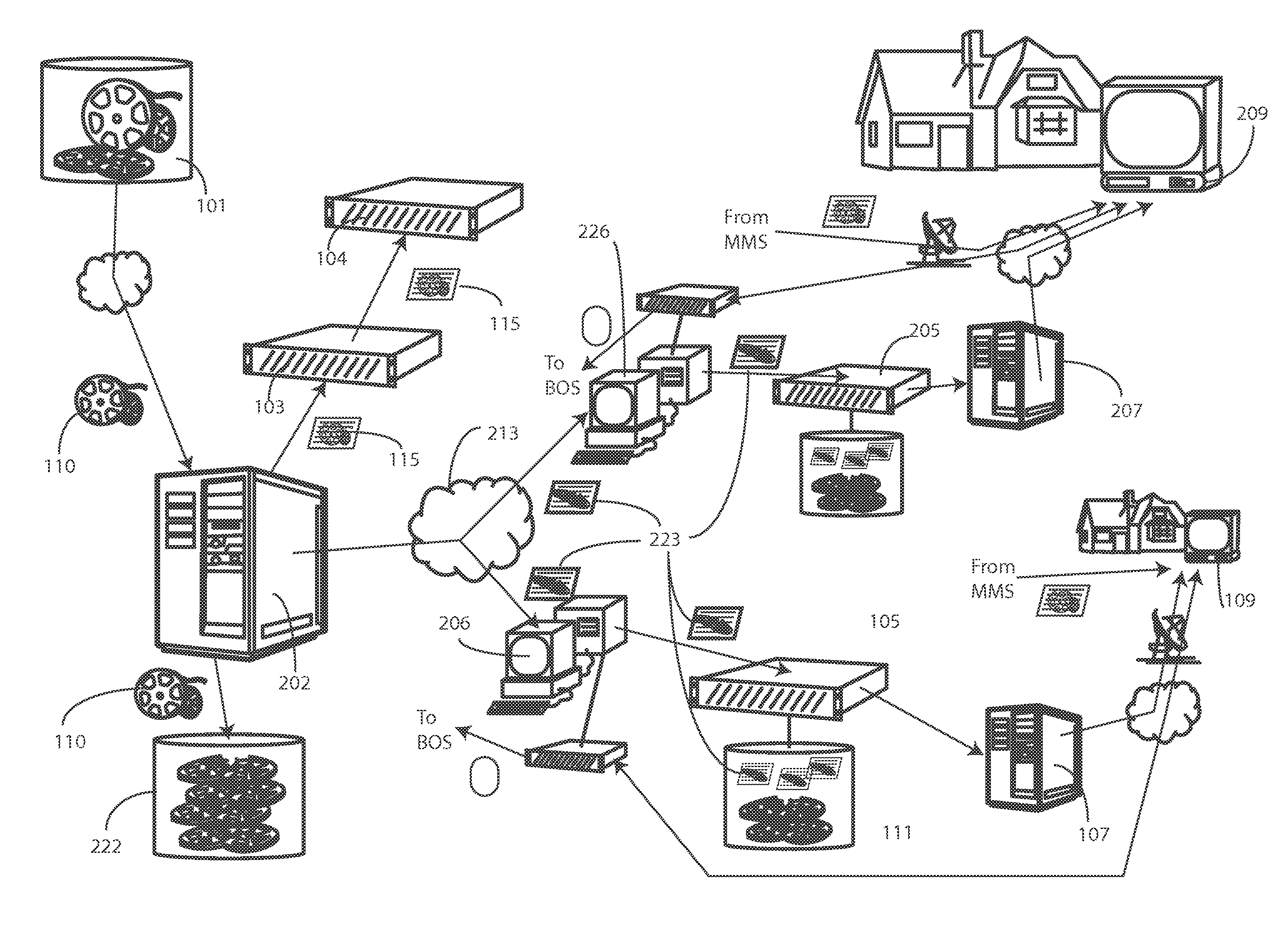
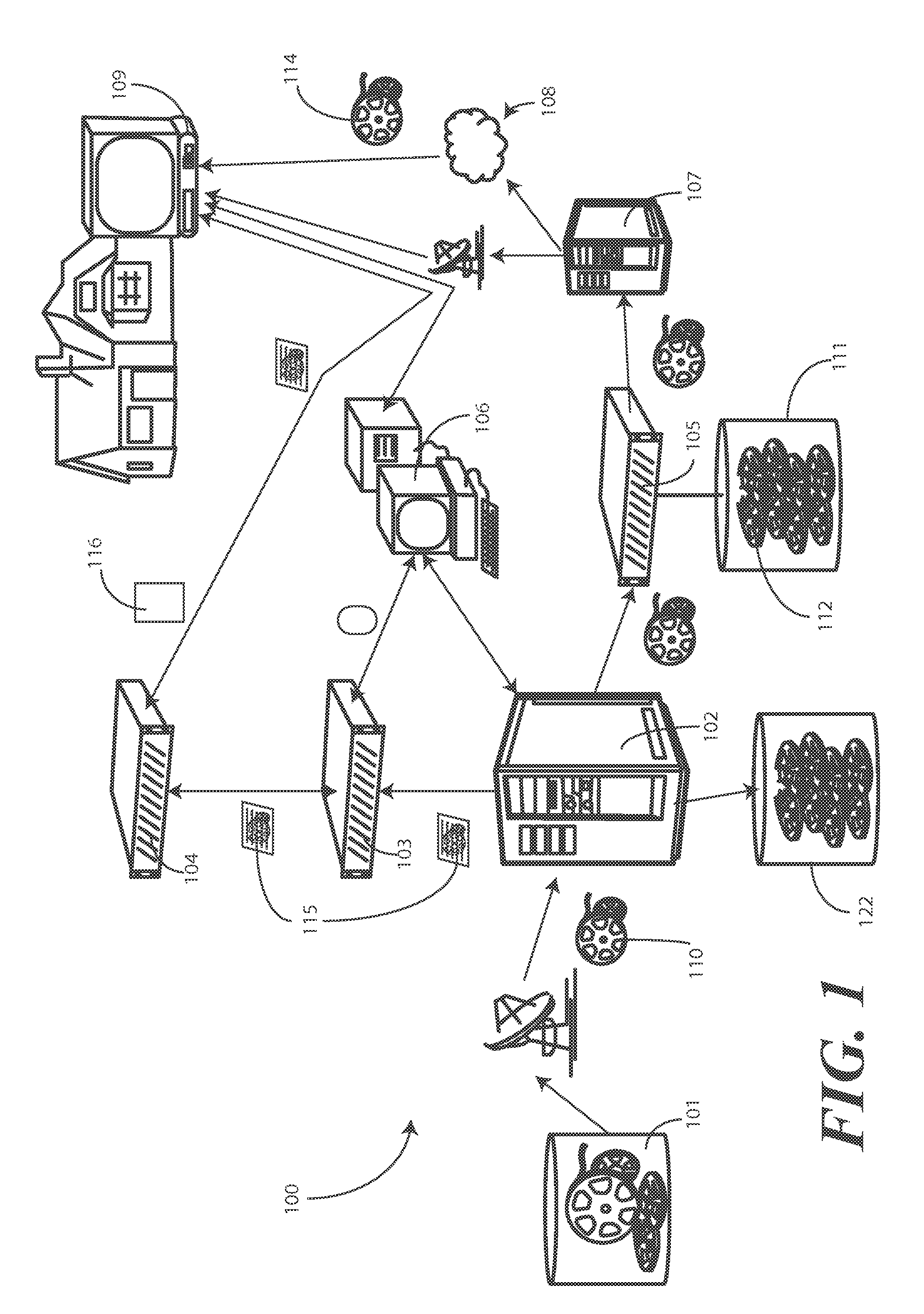
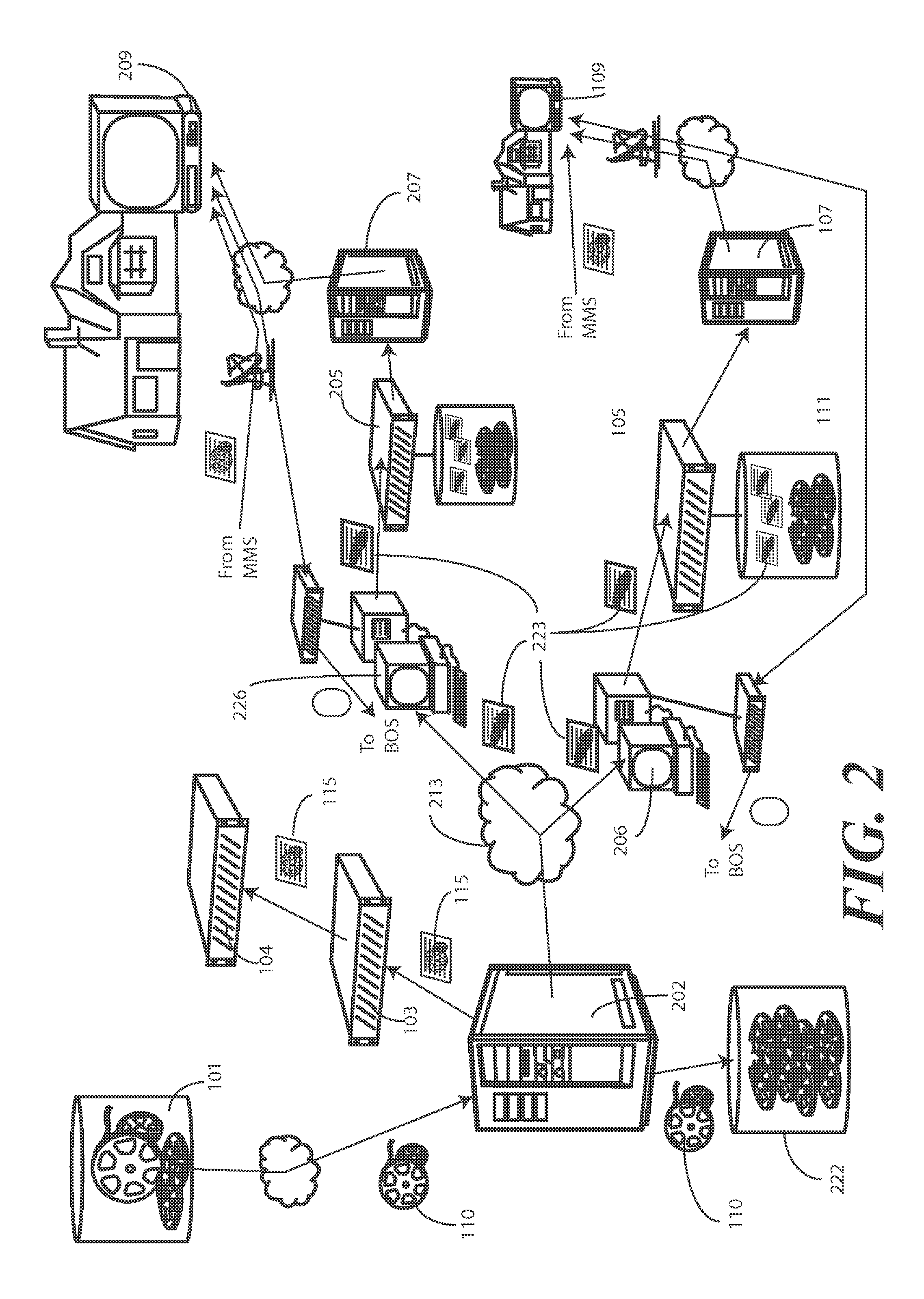
Demand-based edge caching video content system and method
ActiveUS8505057B2Multiple digital computer combinationsTwo-way working systemsResource Management SystemOperating system
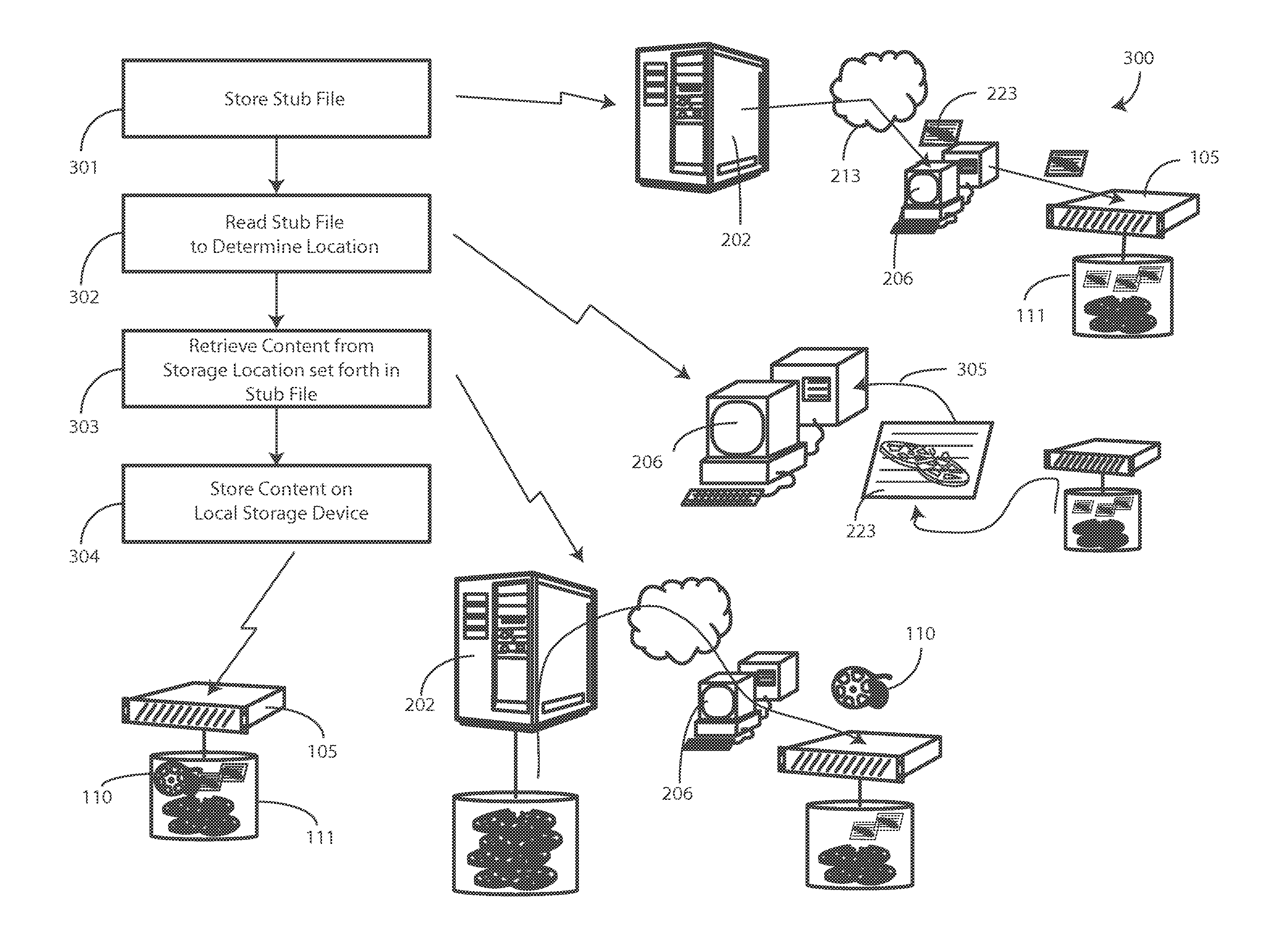
A method (300) and system (200) for of conserving resources in a video-on-demand environment are provided. The method (300) includes storing a stub file (223) on an edge storage device while storing content (110) at a central storage device (222). When a video-on-demand request (440) is received, a resource management system (206) reads (305) the stub file (223) to determine a storage location at the central storage device (222). The resource management system (206) then retrieves the content (110) from the storage location determined from the stub file (223) and either stores it at an edge storage device (111) or delivers it the a subscriber device (109) to fulfill the video-on-demand request (440).
Owner:VECIMA NETWORKS
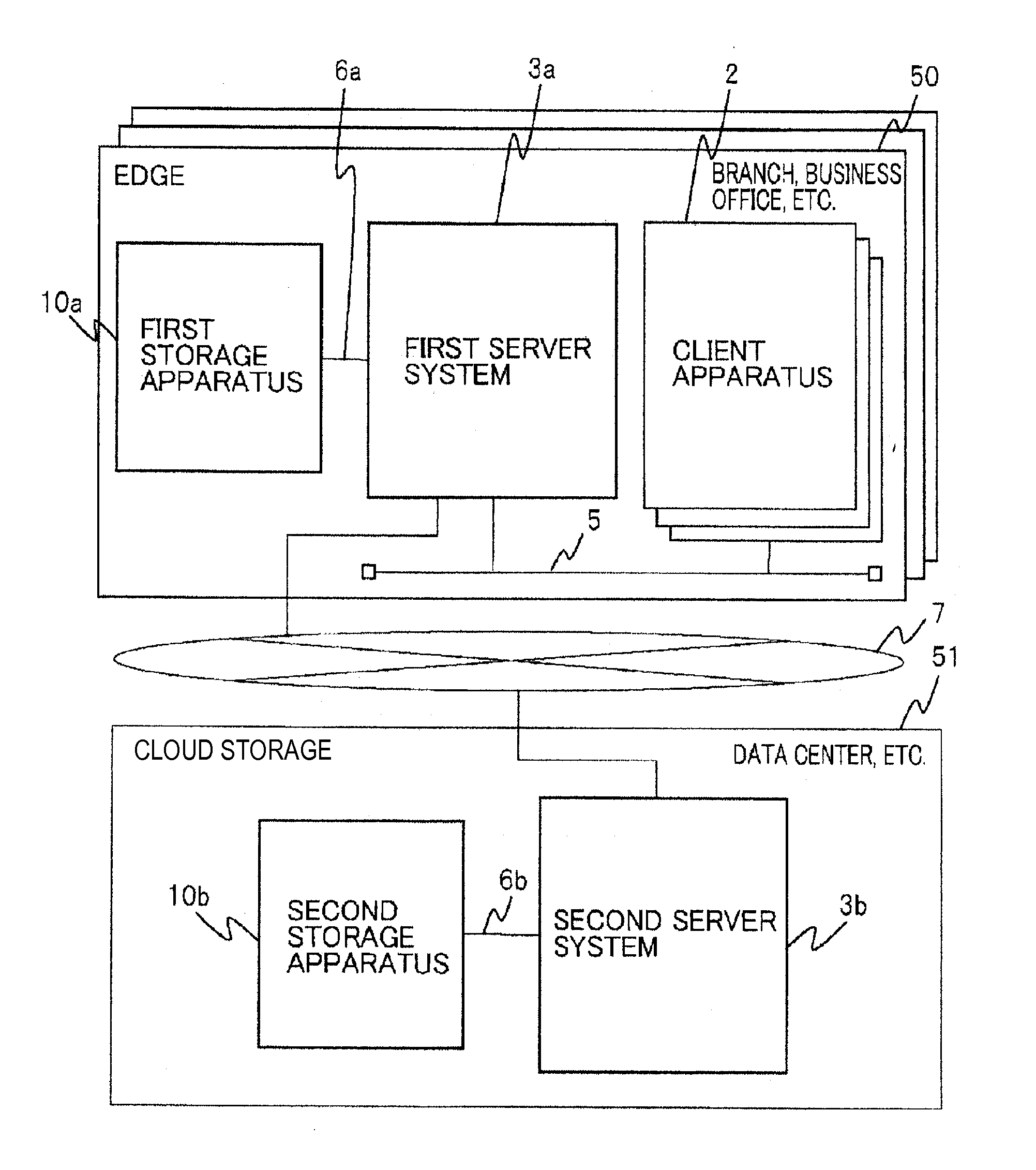
Storage management system and method and program
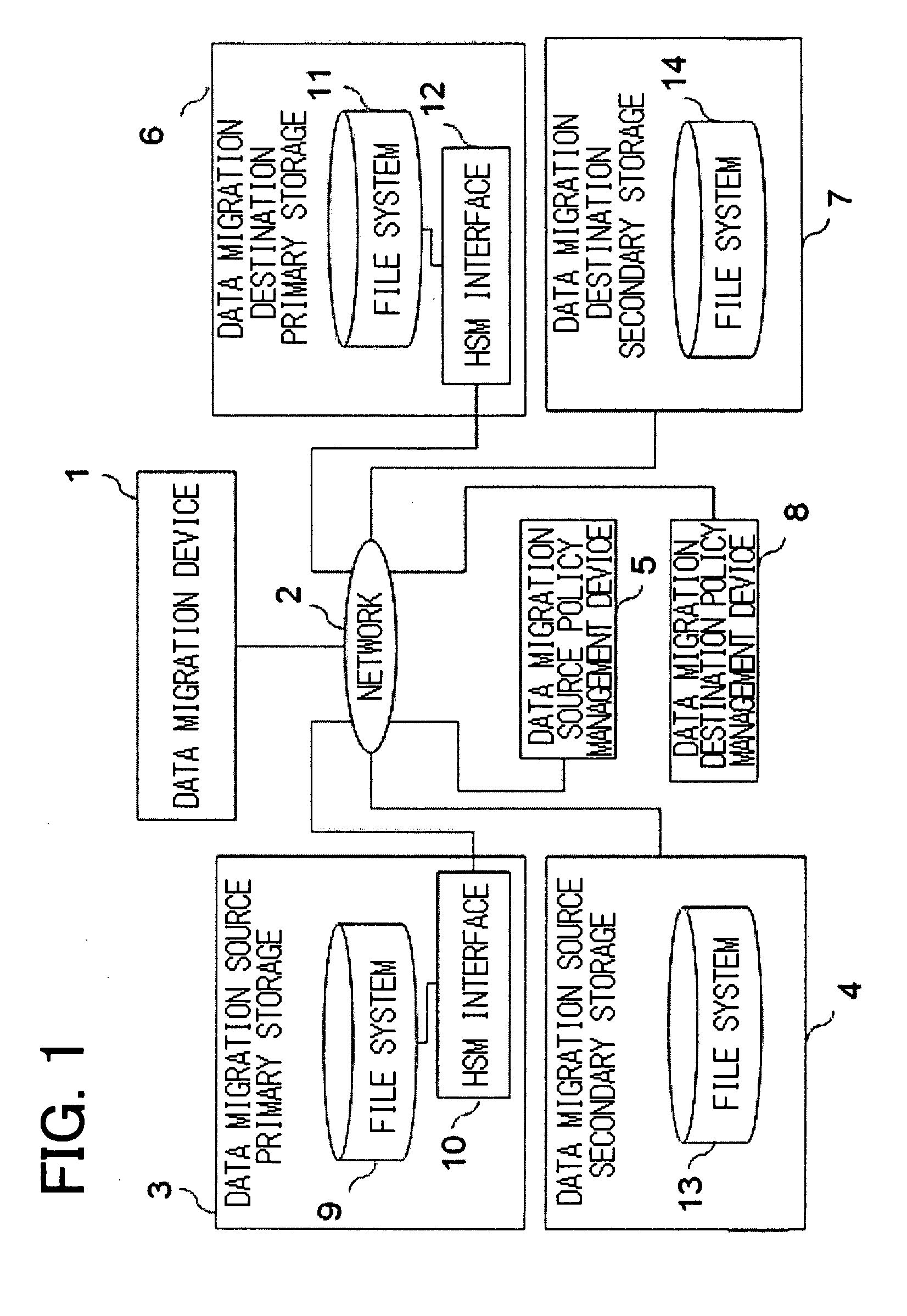
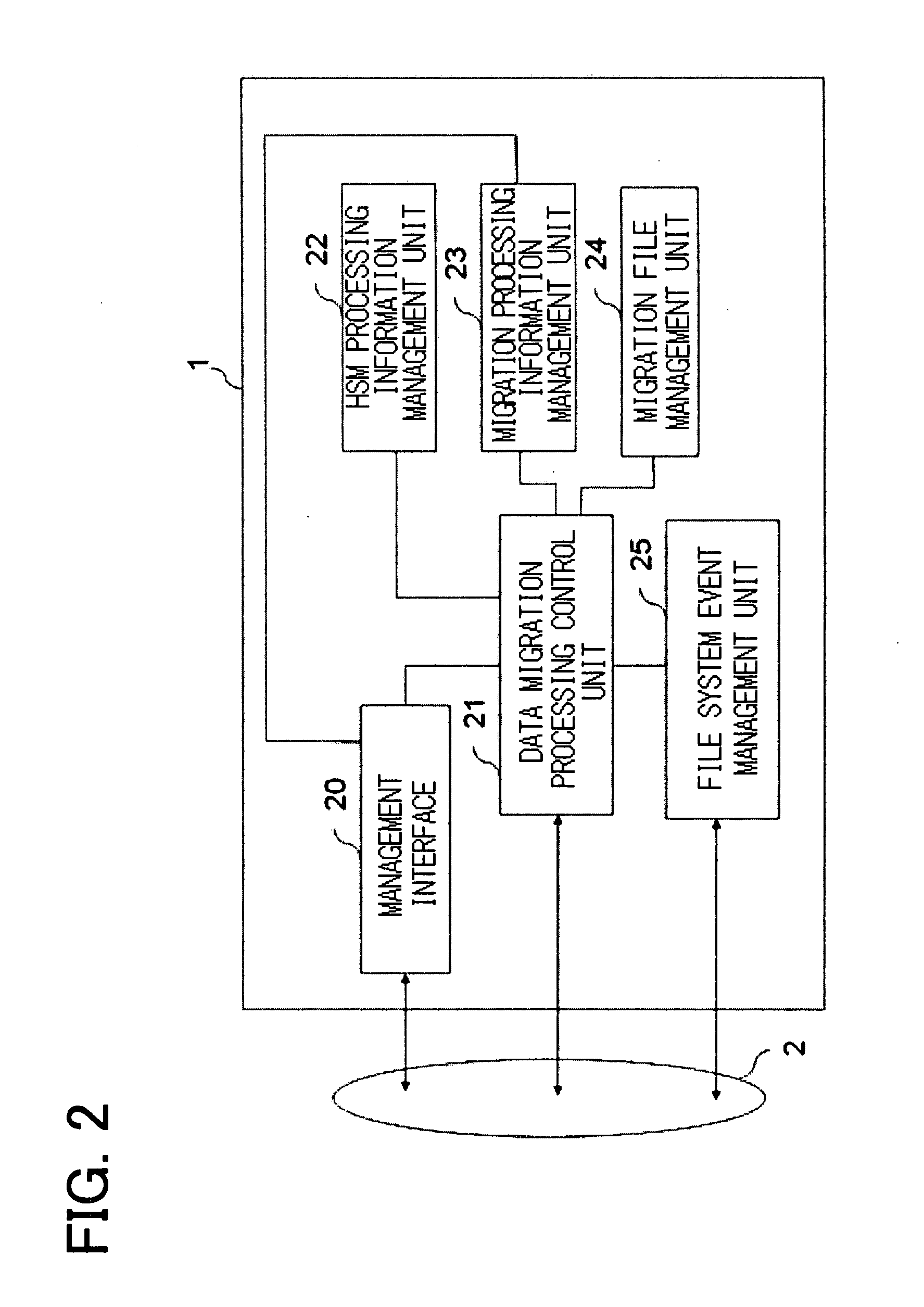
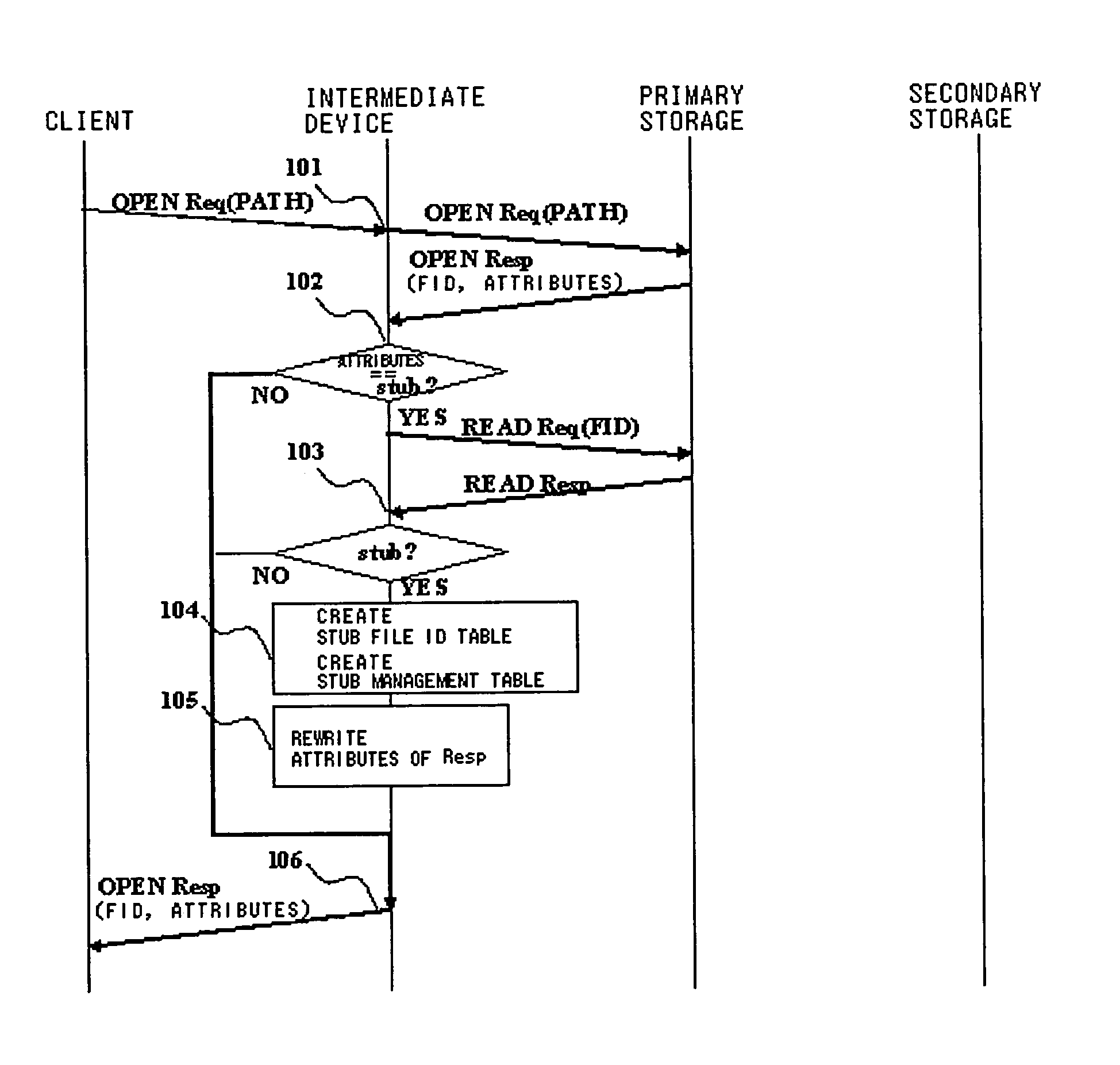
InactiveUS20060129537A1Digital data information retrievalDigital data processing detailsStorage managementClient-side
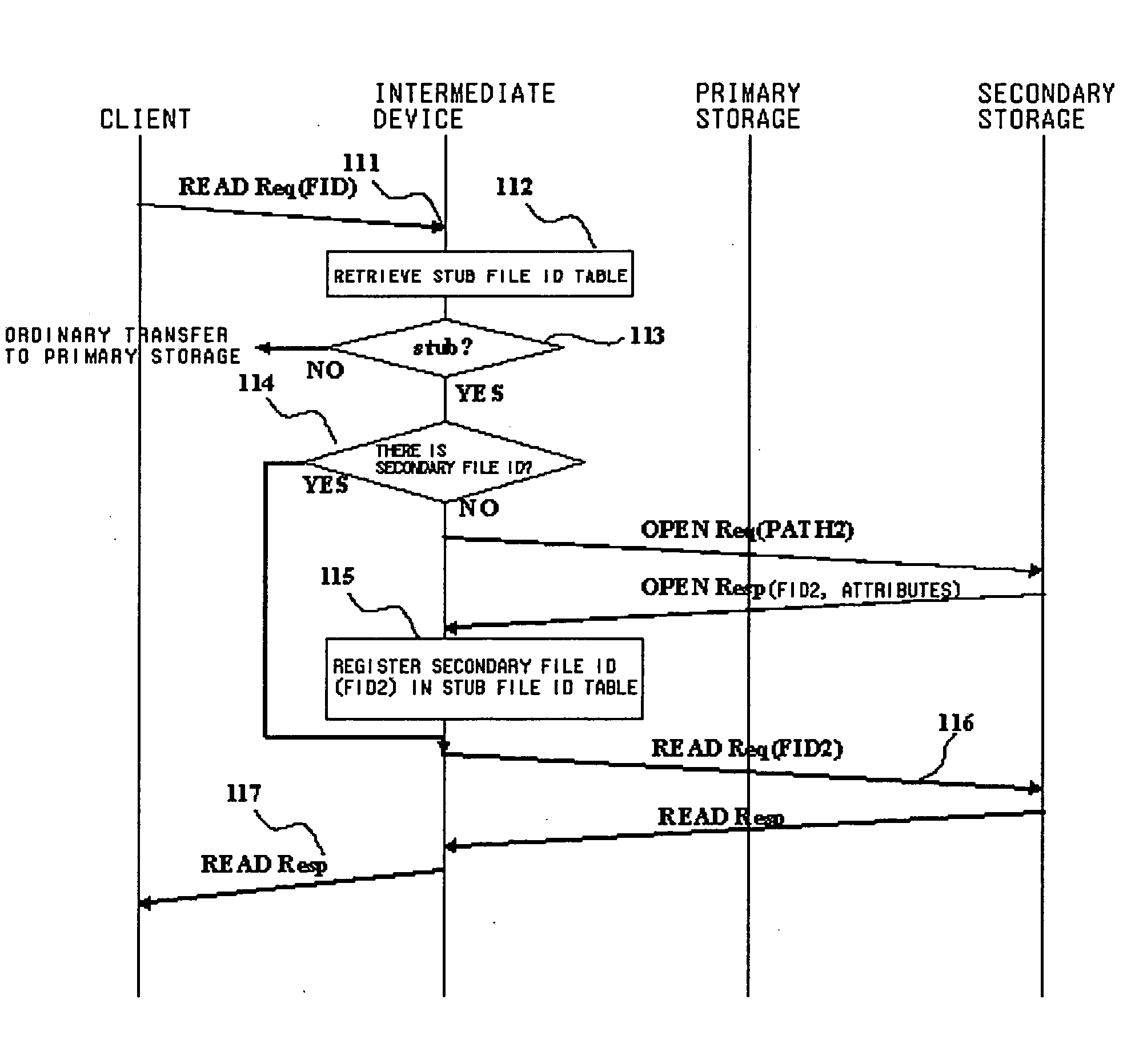
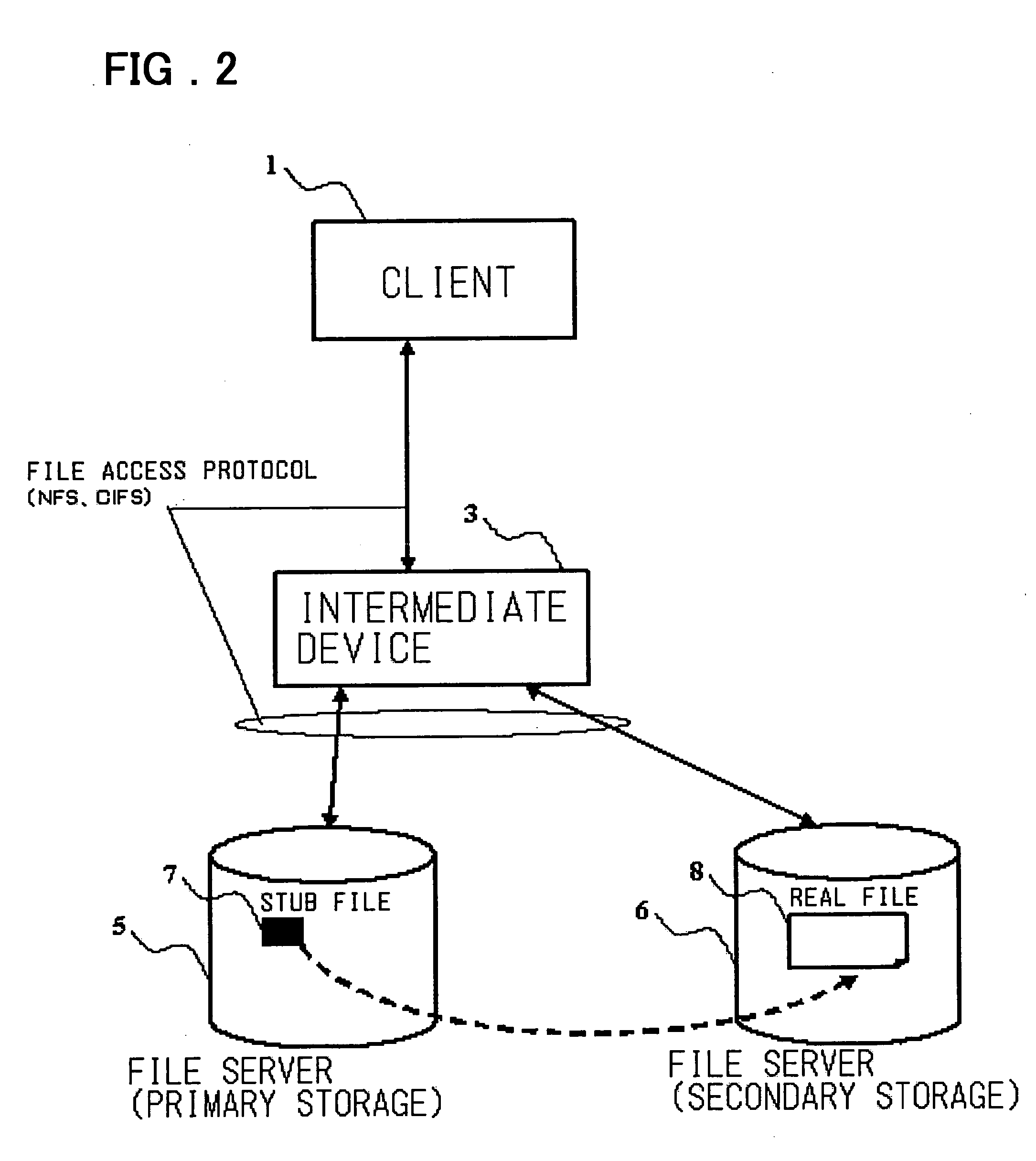
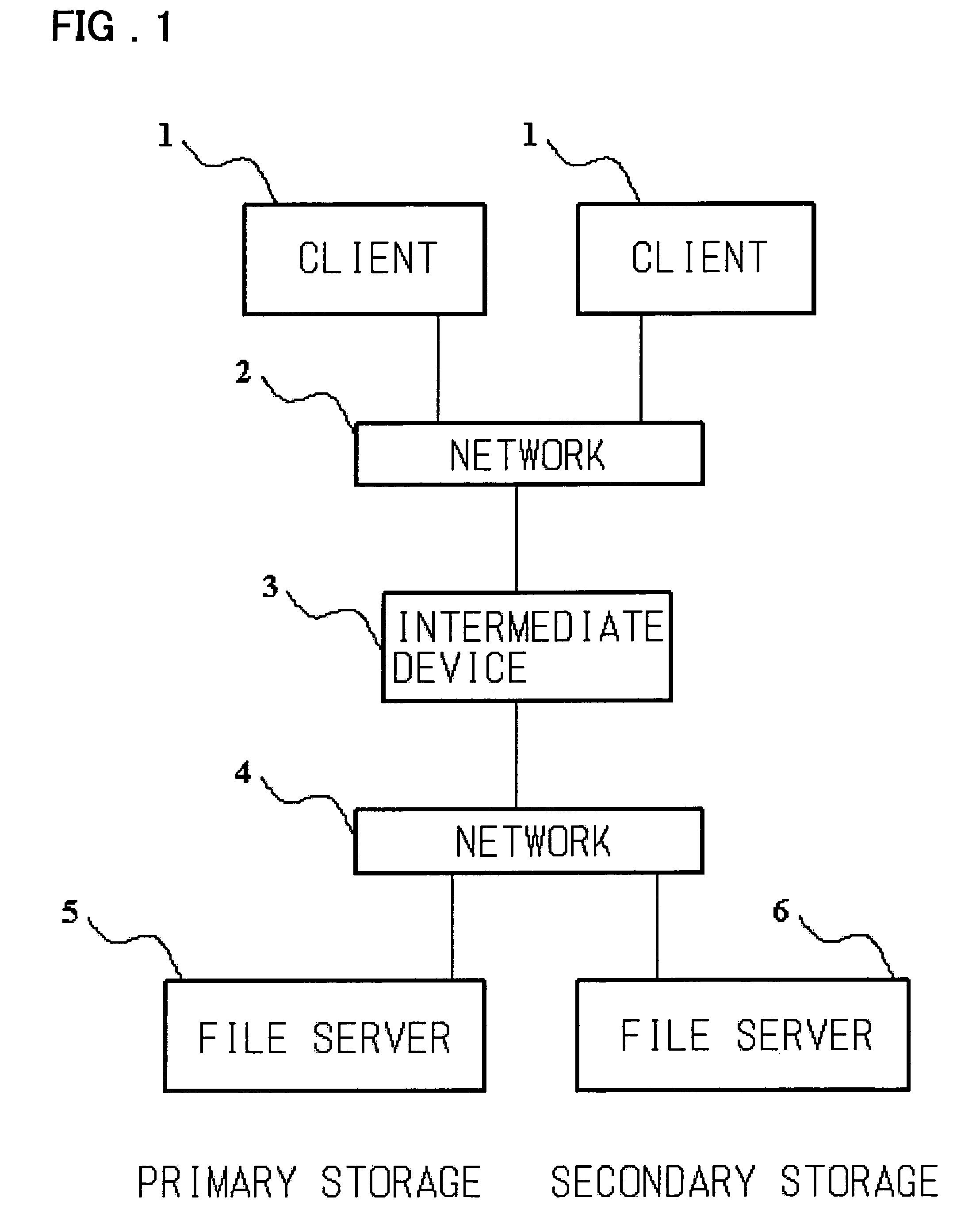
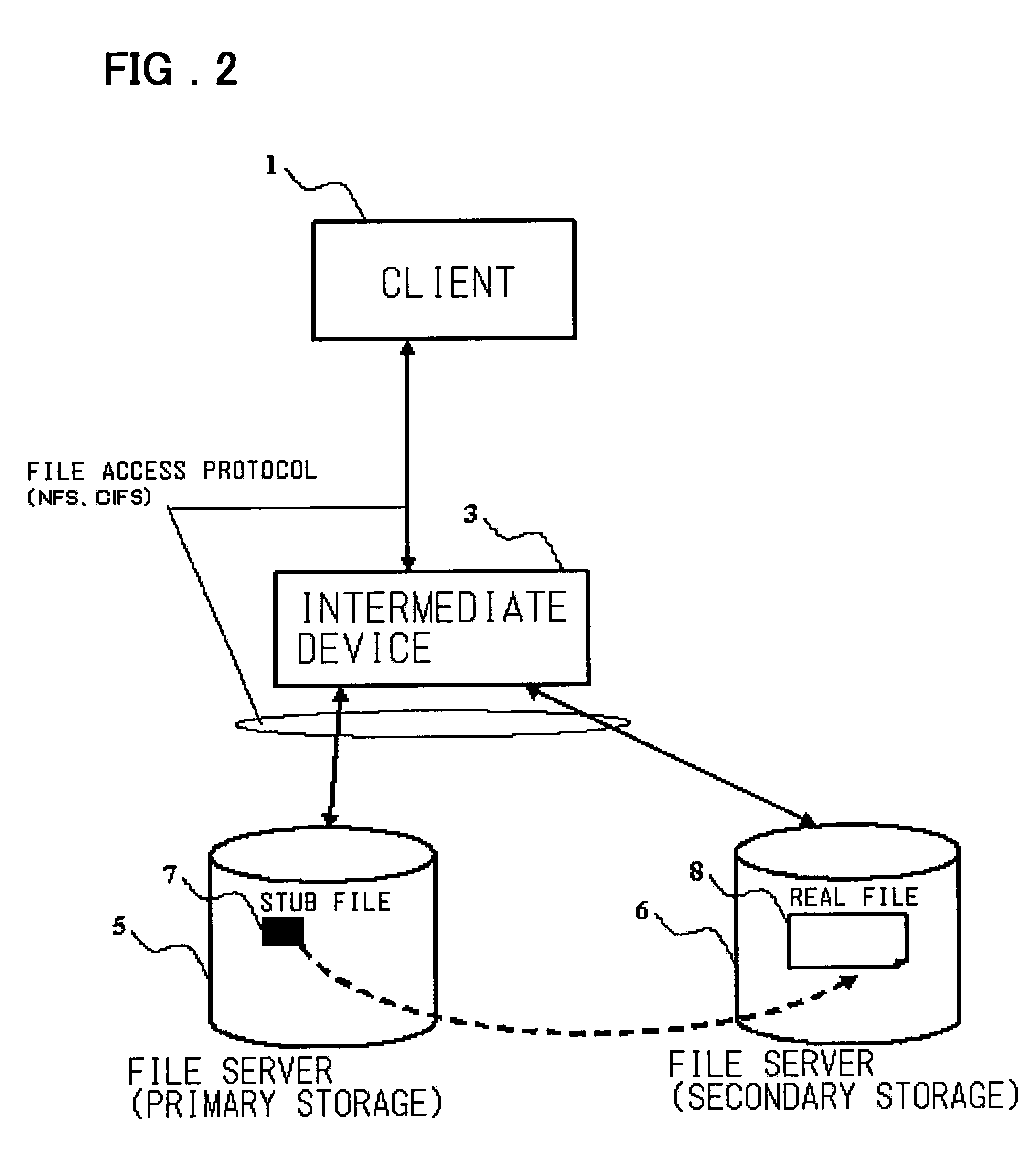
Disclosed is a storage management system including at least one client, a first server having a primary storage, a second server having a secondary storage, and an intermediate device logically arranged between the client and the first and second servers. The primary storage includes a stub file in which there is recorded the position information of the real file migrated from the primary storage to the secondary storage. The intermediate device exercises control so that, when a file access request of the primary storage of a first server, issued by the client, is received by the intermediate device, the intermediate device receives the file access request and, if the file to be accessed is a stub file, and the access request necessitates accessing to the real file, the intermediate device accesses the real file of the secondary storage using the information of the stub file to return a response.
Owner:NEC CORP
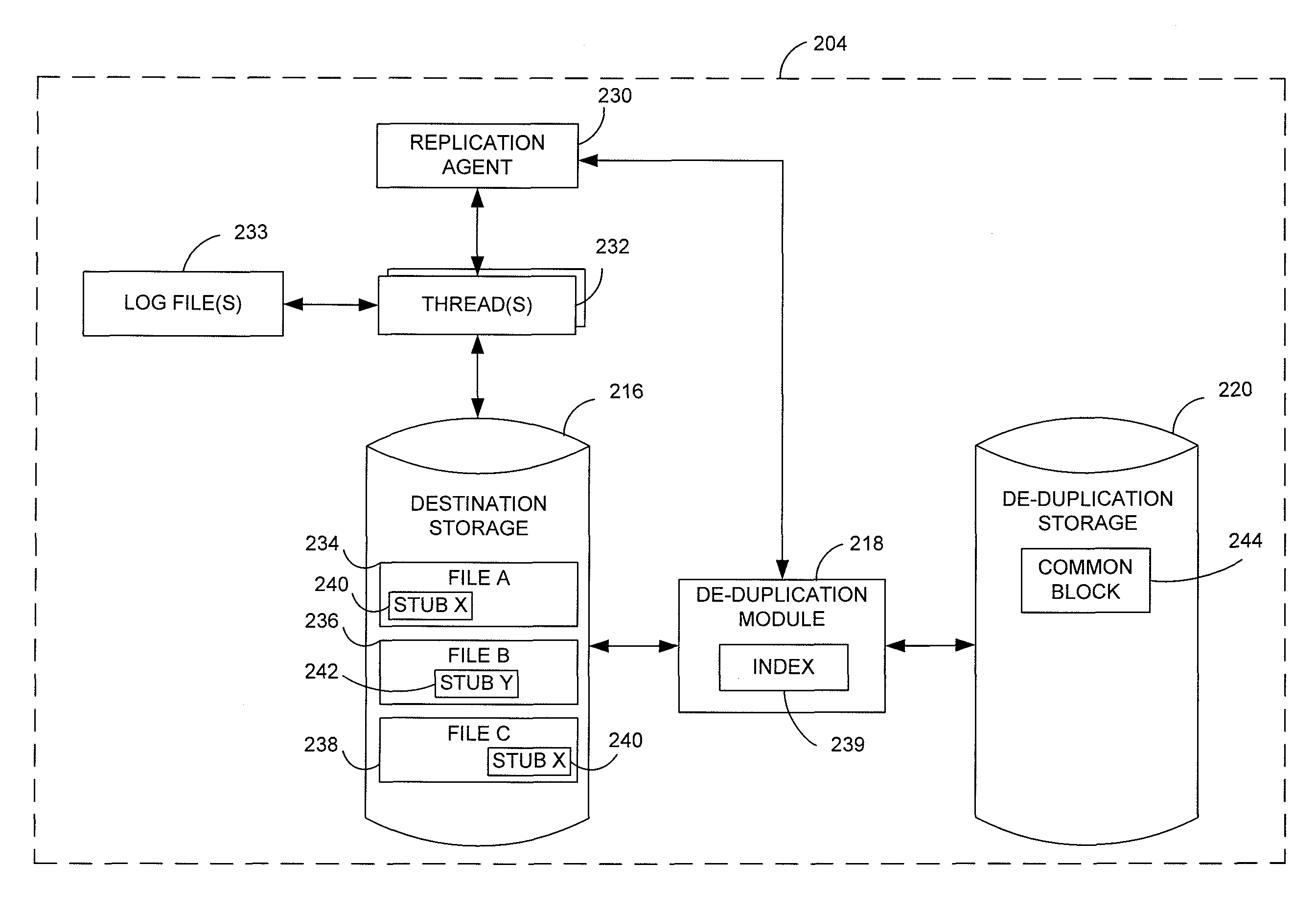
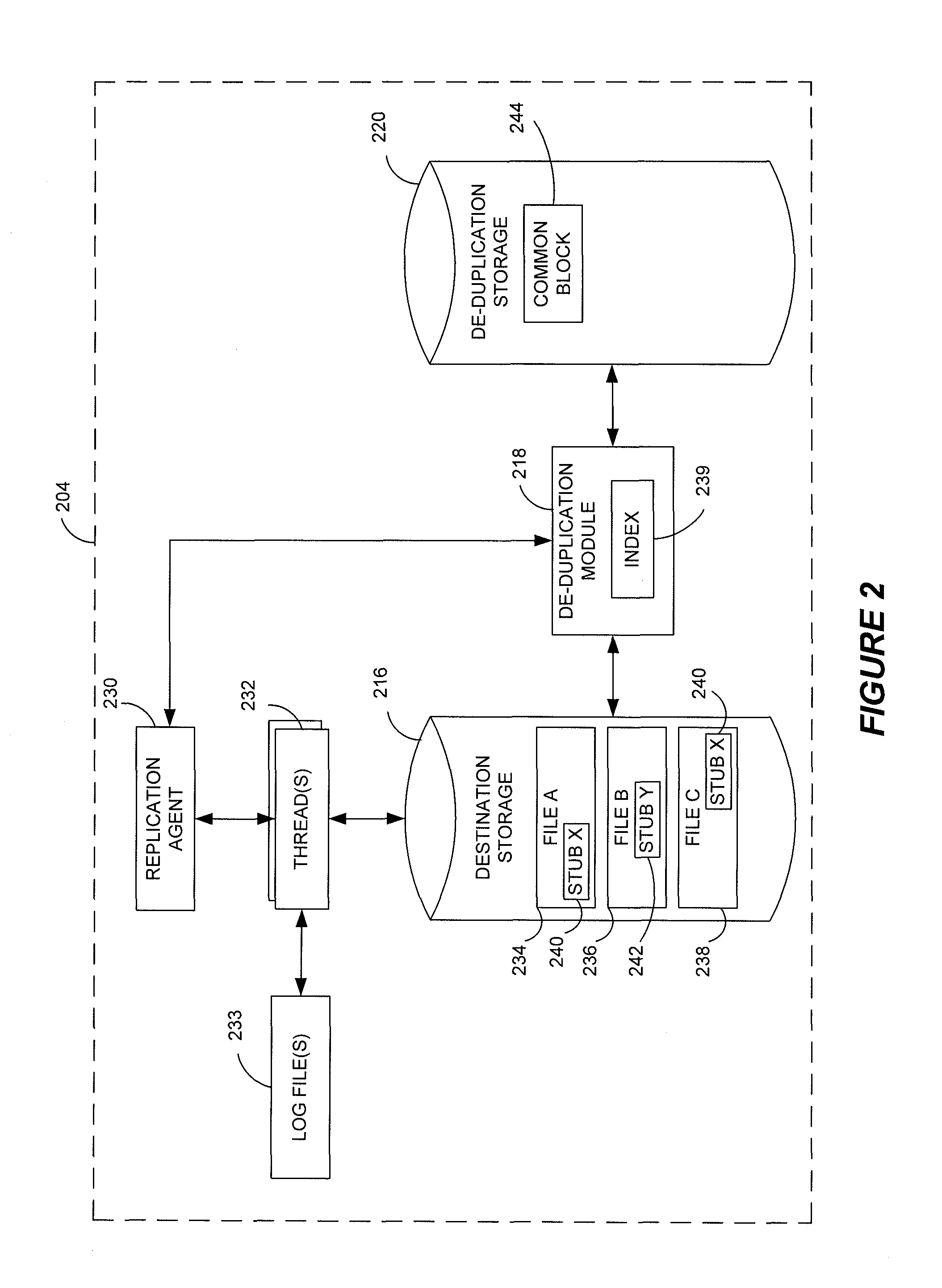
Data restore systems and methods in a replication environment
ActiveUS8352422B2Digital data information retrievalDigital data processing detailsData managementGoal system
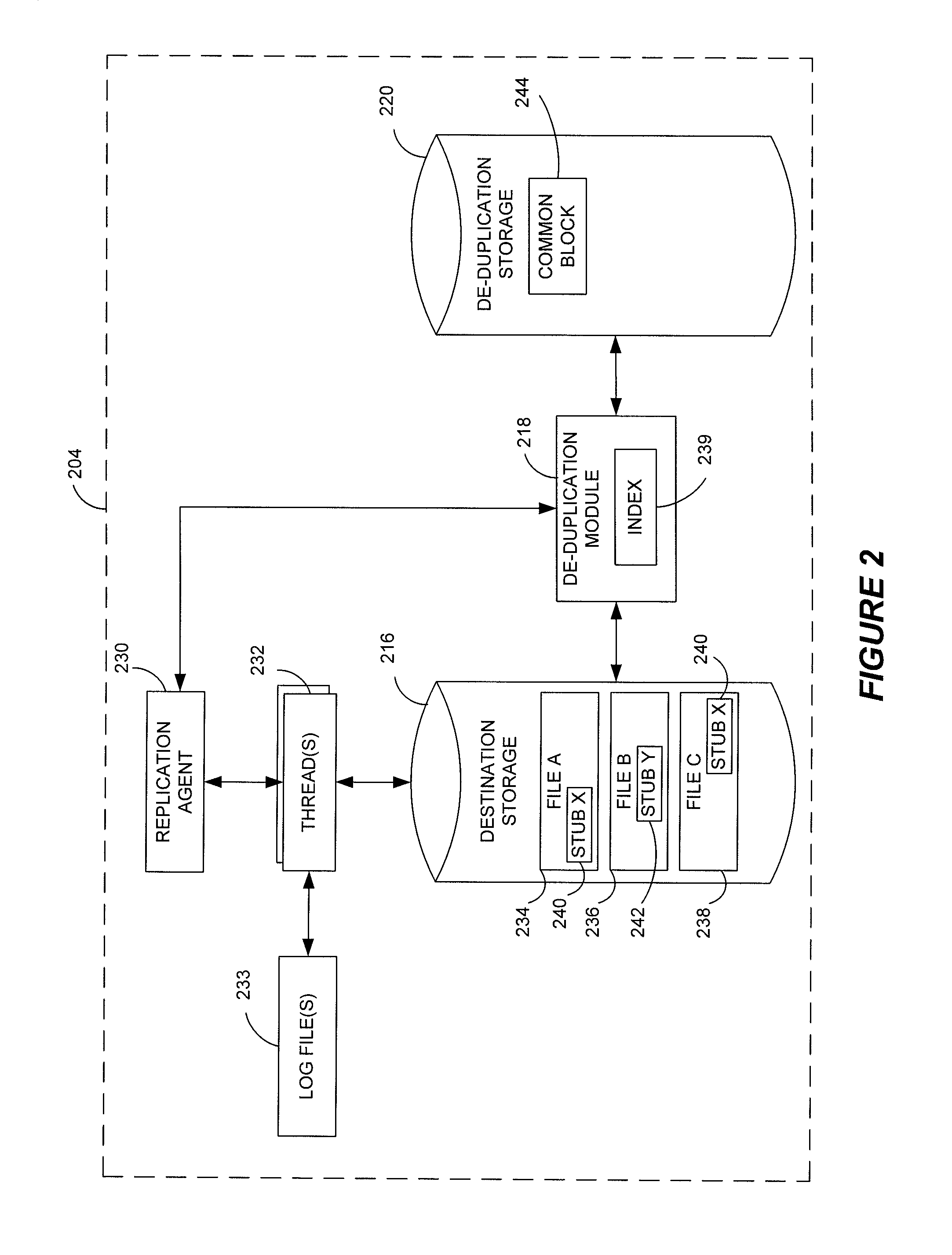
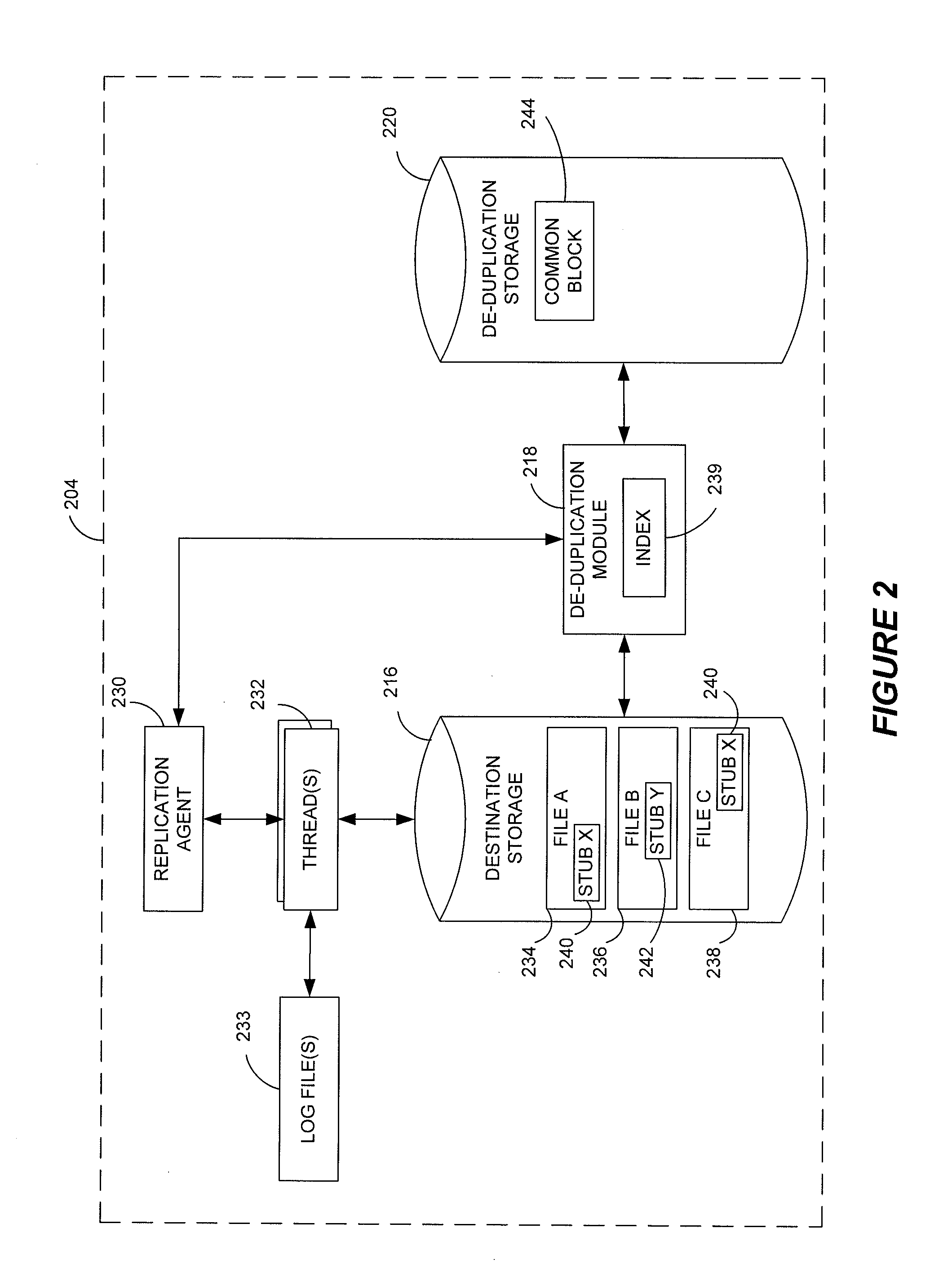
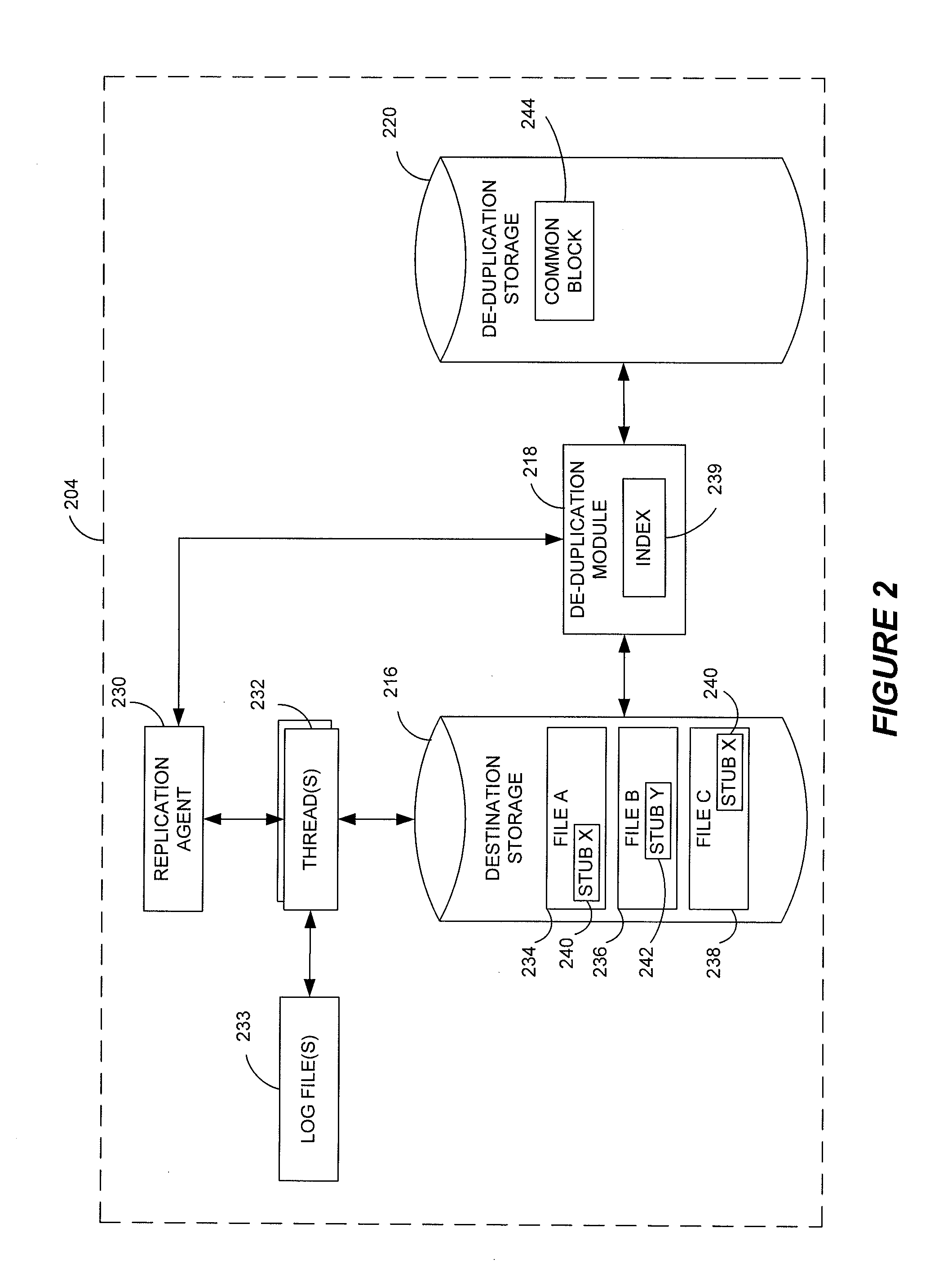
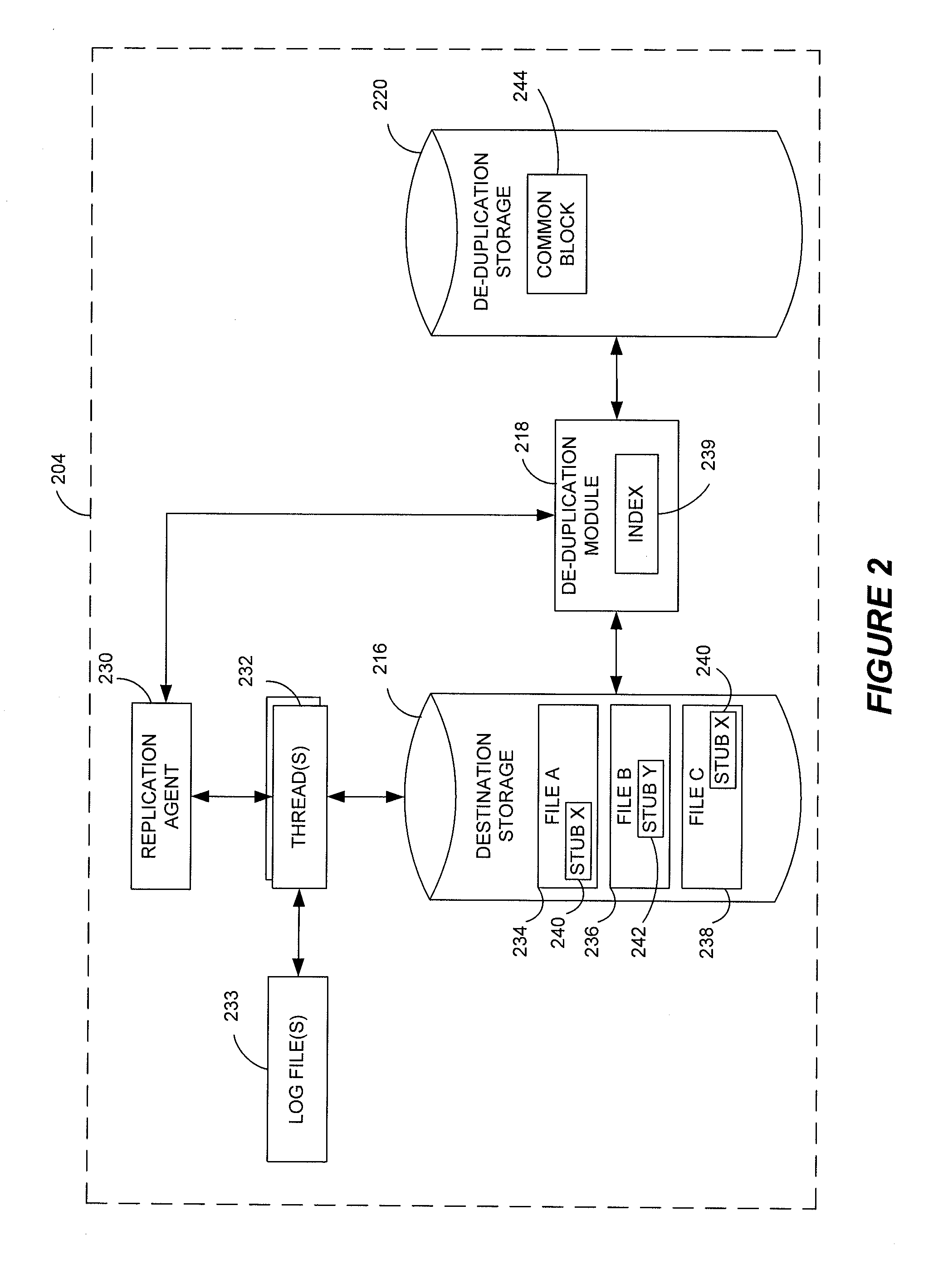
Stubbing systems and methods are provided for intelligent data management in a replication environment, such as by reducing the space occupied by replication data on a destination system. In certain examples, stub files or like objects replace migrated, de-duplicated or otherwise copied data that has been moved from the destination system to secondary storage. Access is further provided to the replication data in a manner that is transparent to the user and / or without substantially impacting the base replication process. In order to distinguish stub files representing migrated replication data from replicated stub files, priority tags or like identifiers can be used. Thus, when accessing a stub file on the destination system, such as to modify replication data or perform a restore process, the tagged stub files can be used to recall archived data prior to performing the requested operation so that an accurate copy of the source data is generated.
Owner:COMMVAULT SYST INC
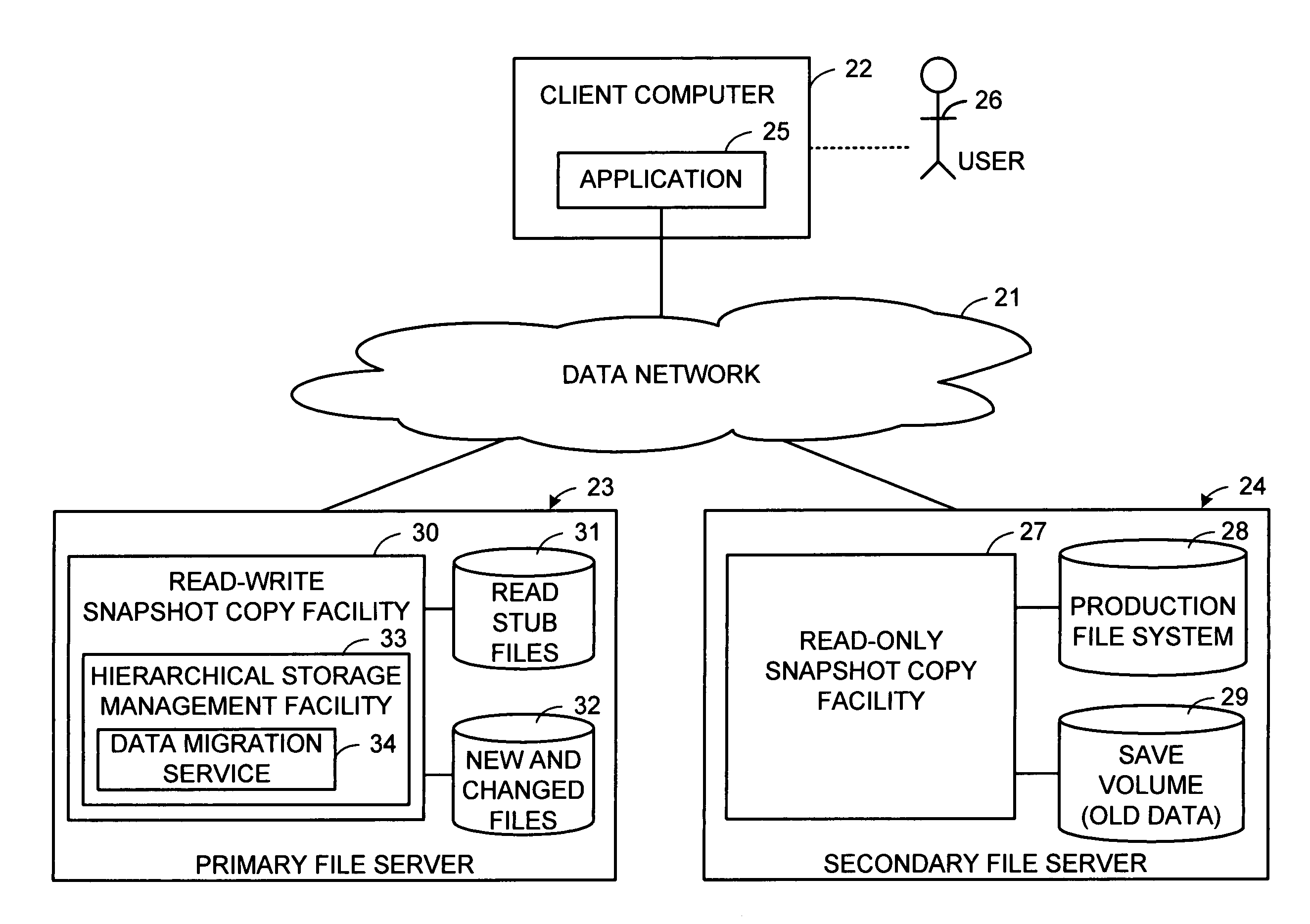
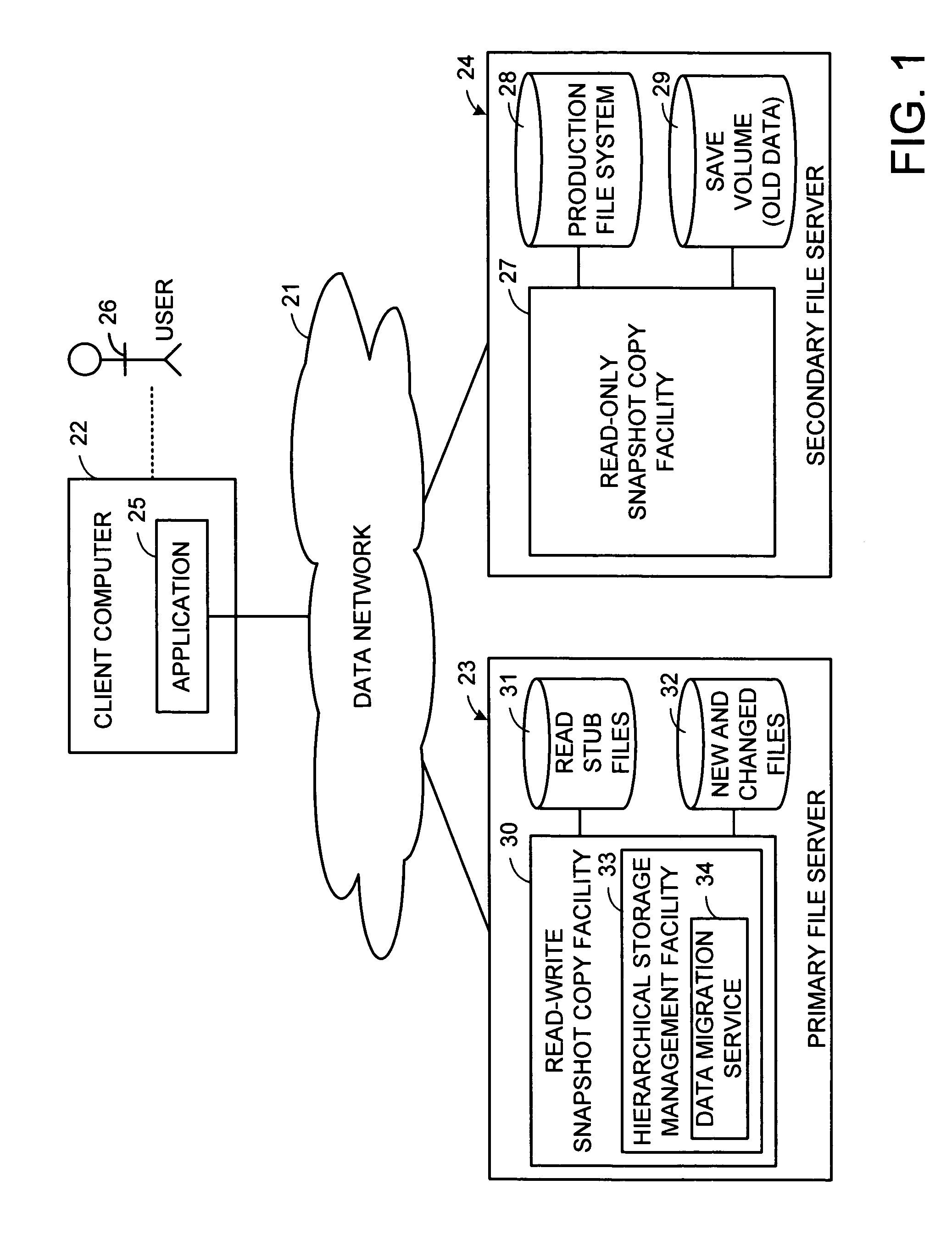
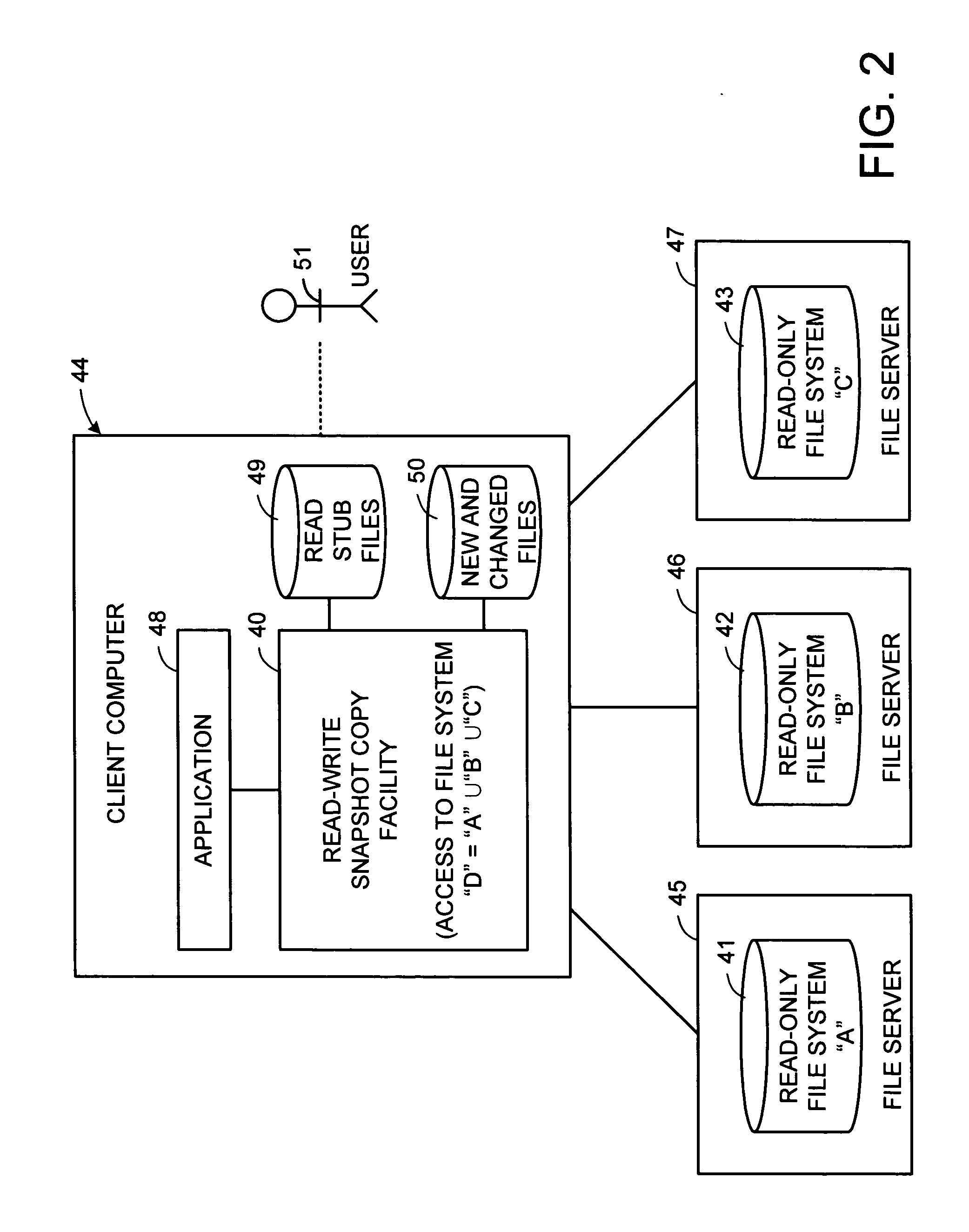
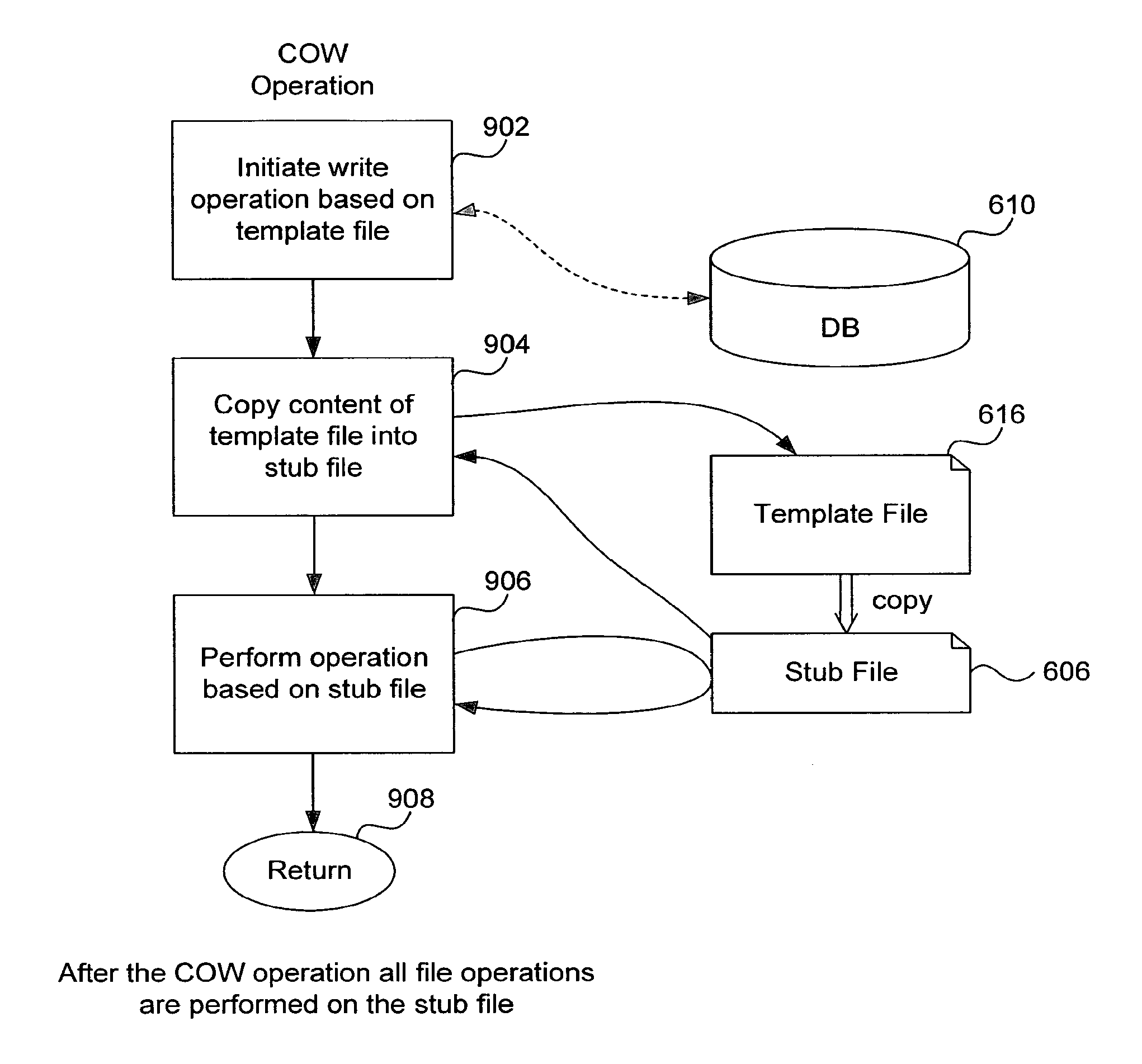
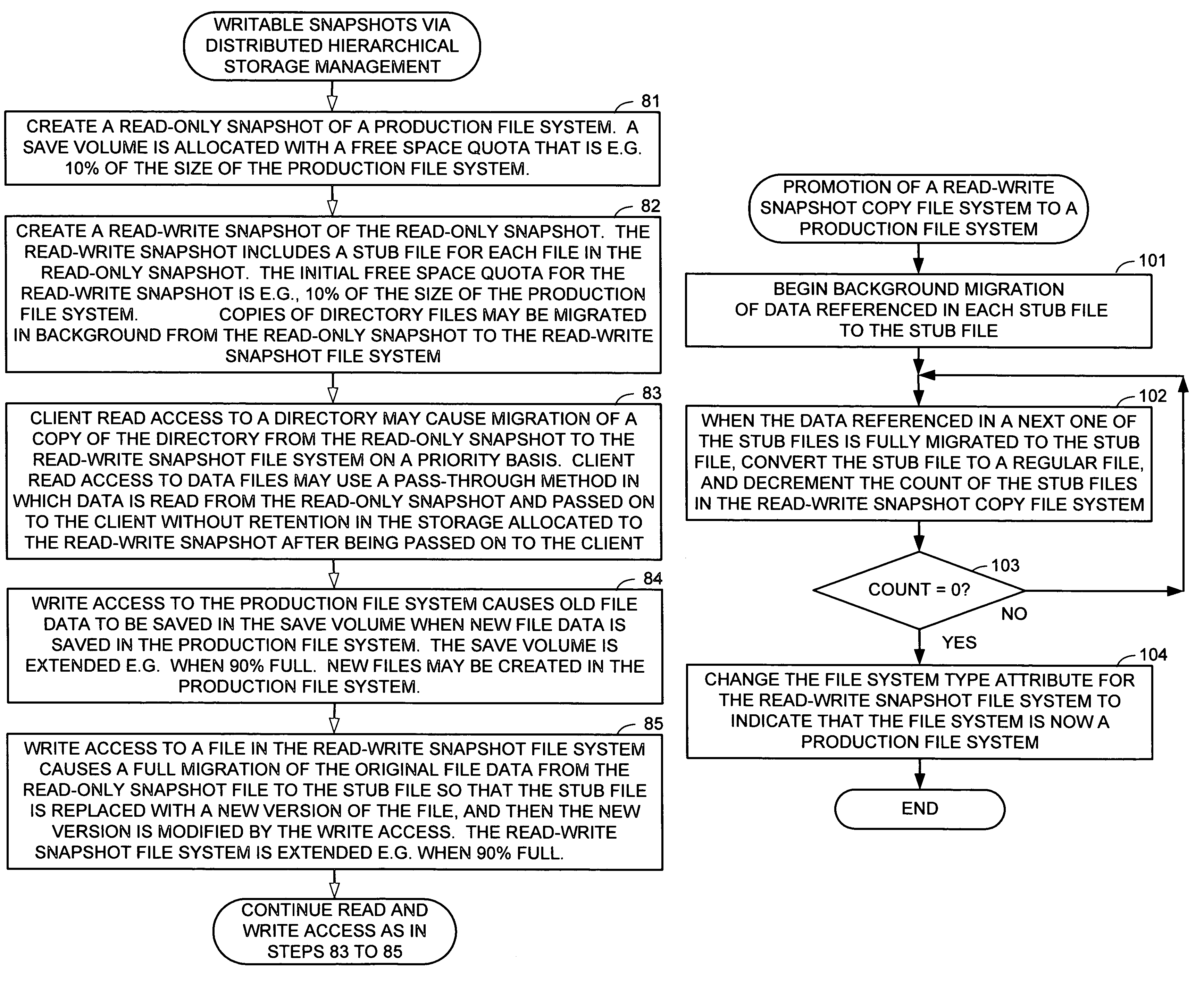
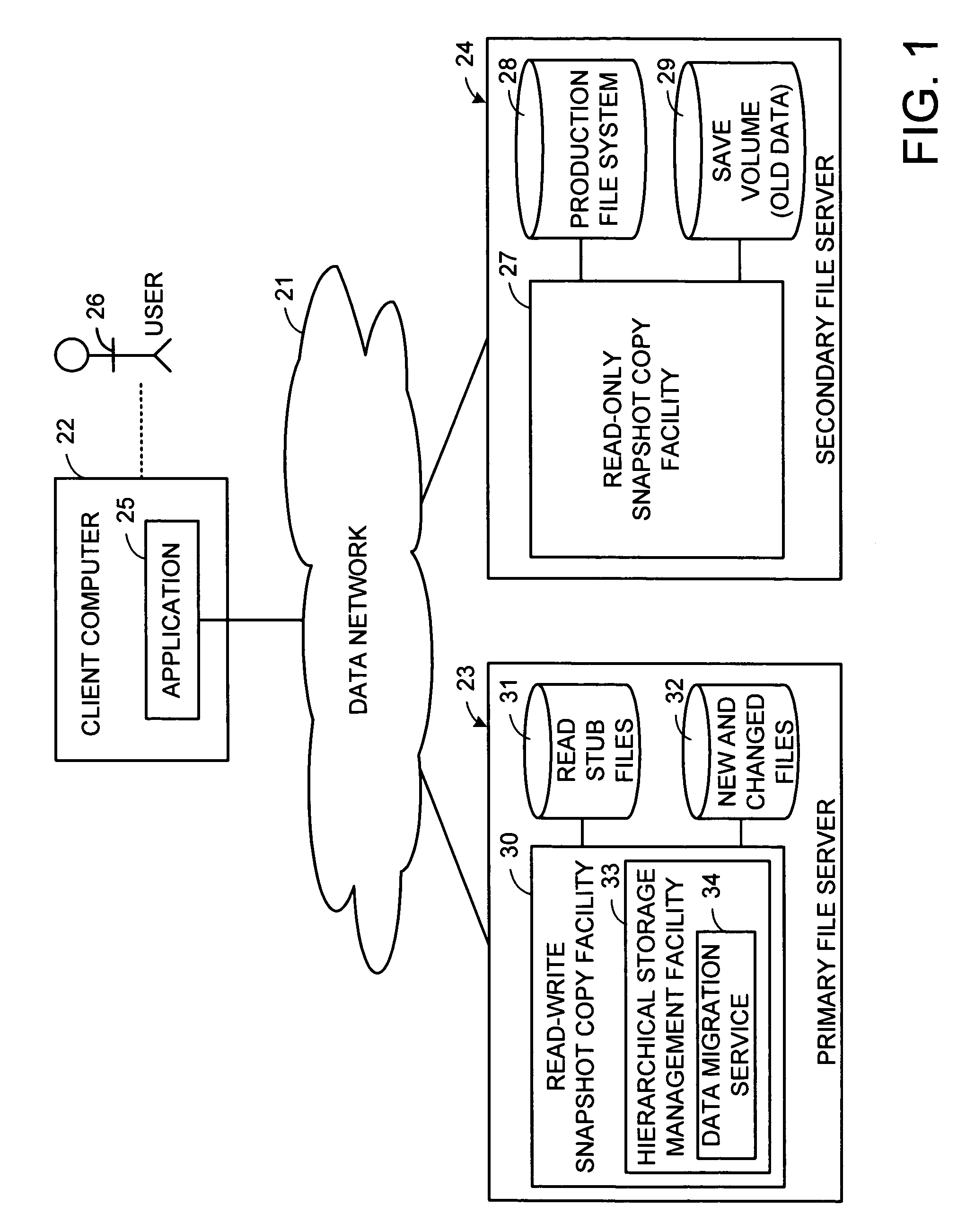
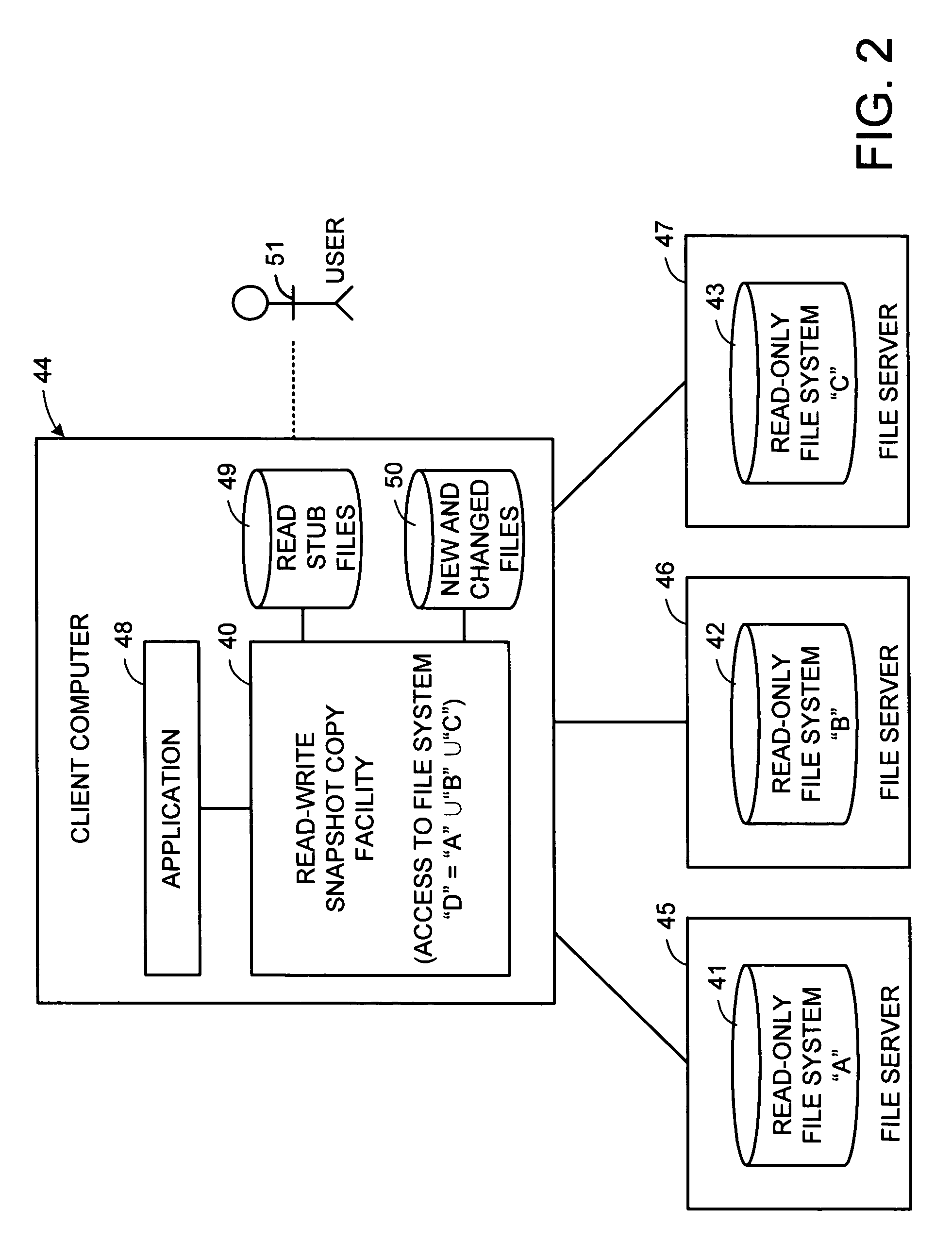
Distributed open writable snapshot copy facility using file migration policies
ActiveUS20060212481A1Data processing applicationsDigital data processing detailsFile systemHeterogeneous network
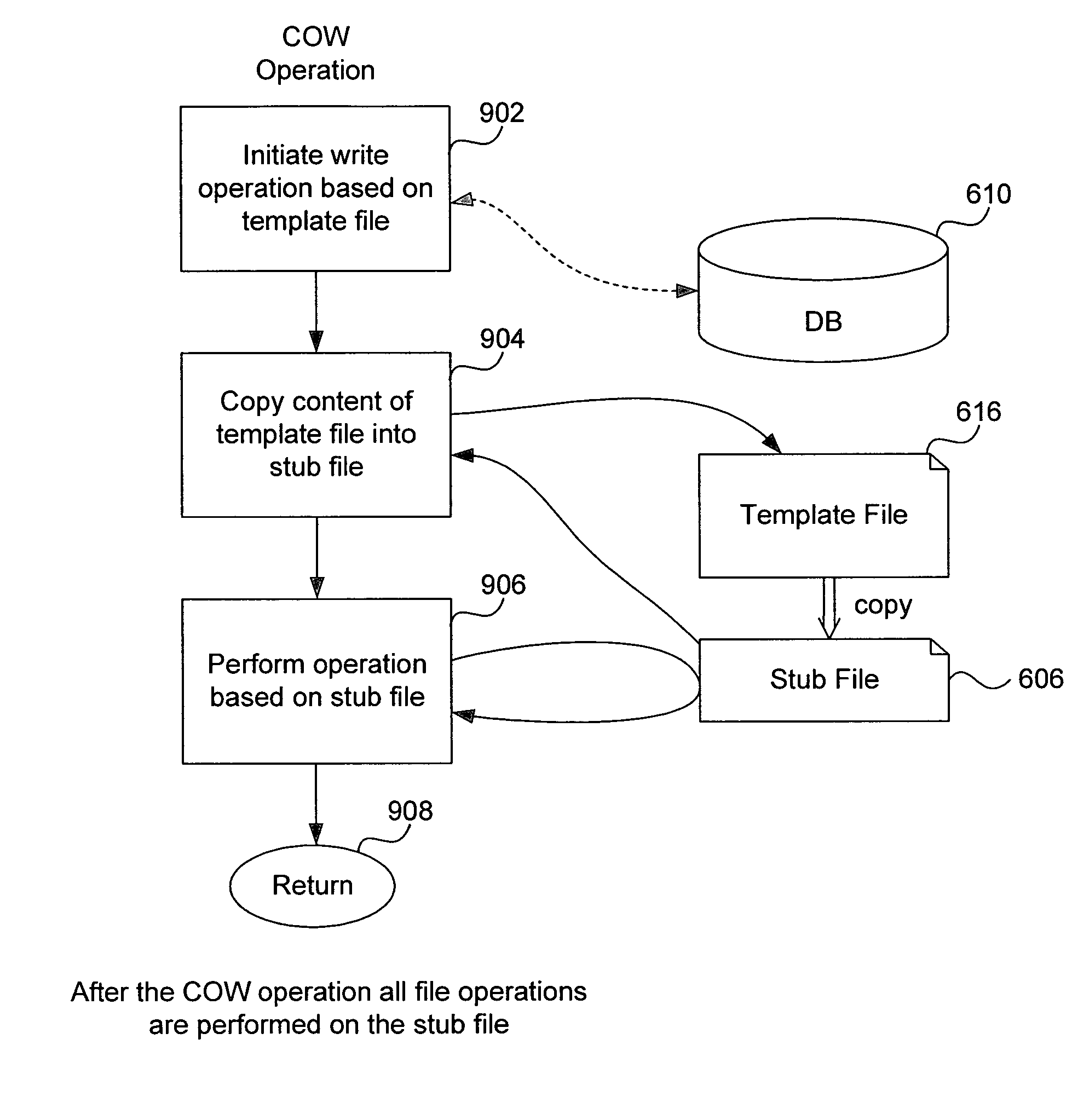
A read-write snapshot copy facility is constructed from a hierarchical storage management facility. The read-write snapshot copy file system initially comprises stub files pointing to the files in a read-only snapshot copy file system. When an application writes to a file in the read-write snapshot copy, the read-write snapshot copy facility migrates a copy of the file to replace the stub file, and then writes to the migrated file. Because the read-write snapshot copy facility references the files in the read-only snapshot file system in a network namespace using standard protocols such as NFS or CIFS, the read-write snapshot copy facility permits referencing of distributed read-only snapshot file systems in an open (heterogeneous) network environment, and the read-write snapshot copy is scalable by linking the read-write snapshot copy facility to multiple file servers containing read-only snapshot file systems.
Owner:EMC IP HLDG CO LLC
Read Ahead Tiered Local and Cloud Storage System and Method Thereof
ActiveUS20140244937A1Efficient storageEfficient recallMemory adressing/allocation/relocationDigital computer detailsCloud storage systemClient-side
A high tier storage area stores a stub file and a lower tier cloud storage area stores the file corresponding to the stub file. When a client apparatus requests segments of the file from the high tier storage area, reference is made to the stub file to determine a predicted non-sequential pattern of requests to the segments by the client apparatus. The high tier storage area follows the predicted non-sequential pattern of requests to retrieve the segments of the file from the cloud prior to the client apparatus actually requesting the segments. As such, the file may be efficiently provided to the client apparatus while also efficiently storing the file on the lower tier cloud storage area.
Owner:HITACHI VANTARA LLC
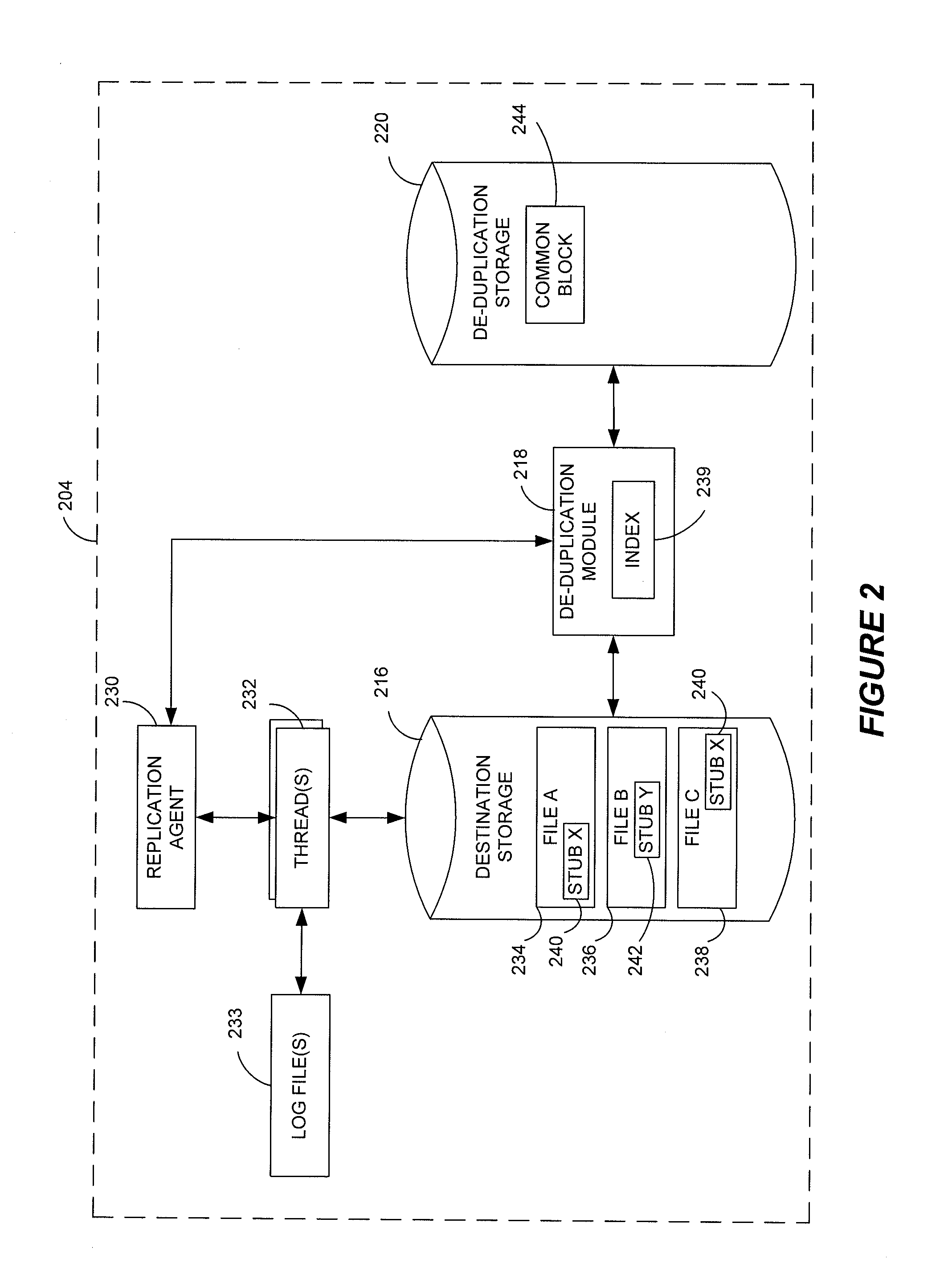
Stubbing systems and methods in a data replication environment
Stubbing systems and methods are provided for intelligent data management in a replication environment, such as by reducing the space occupied by replication data on a destination system. In certain examples, stub files or like objects replace migrated, de-duplicated or otherwise copied data that has been moved from the destination system to secondary storage. Access is further provided to the replication data in a manner that is transparent to the user and / or without substantially impacting the base replication process. In order to distinguish stub files representing migrated replication data from replicated stub files, priority tags or like identifiers can be used. Thus, when accessing a stub file on the destination system, such as to modify replication dath or perform a restore process, the tagged stub files can be used to recall archived data prior to performing the requested operation so that an accurate copy of the source data is generated.
Owner:COMMVAULT SYST INC
Stub file prioritization in a data replication system
ActiveUS20110246429A1Digital data information retrievalDigital data processing detailsGoal systemData management
Stubbing systems and methods are provided for intelligent data management in a replication environment, such as by reducing the space occupied by replication data on a destination system. In certain examples, stub files or like objects replace migrated, de-duplicated or otherwise copied data that has been moved from the destination system to secondary storage. Access is further provided to the replication data in a manner that is transparent to the user and / or without substantially impacting the base replication process. In order to distinguish stub files representing migrated replication data from replicated stub files, priority tags or like identifiers can be used. Thus, when accessing a stub file on the destination system, such as to modify replication data or perform a restore process, the tagged stub files can be used to recall archived data prior to performing the requested operation so that an accurate copy of the source data is generated.
Owner:COMMVAULT SYST INC
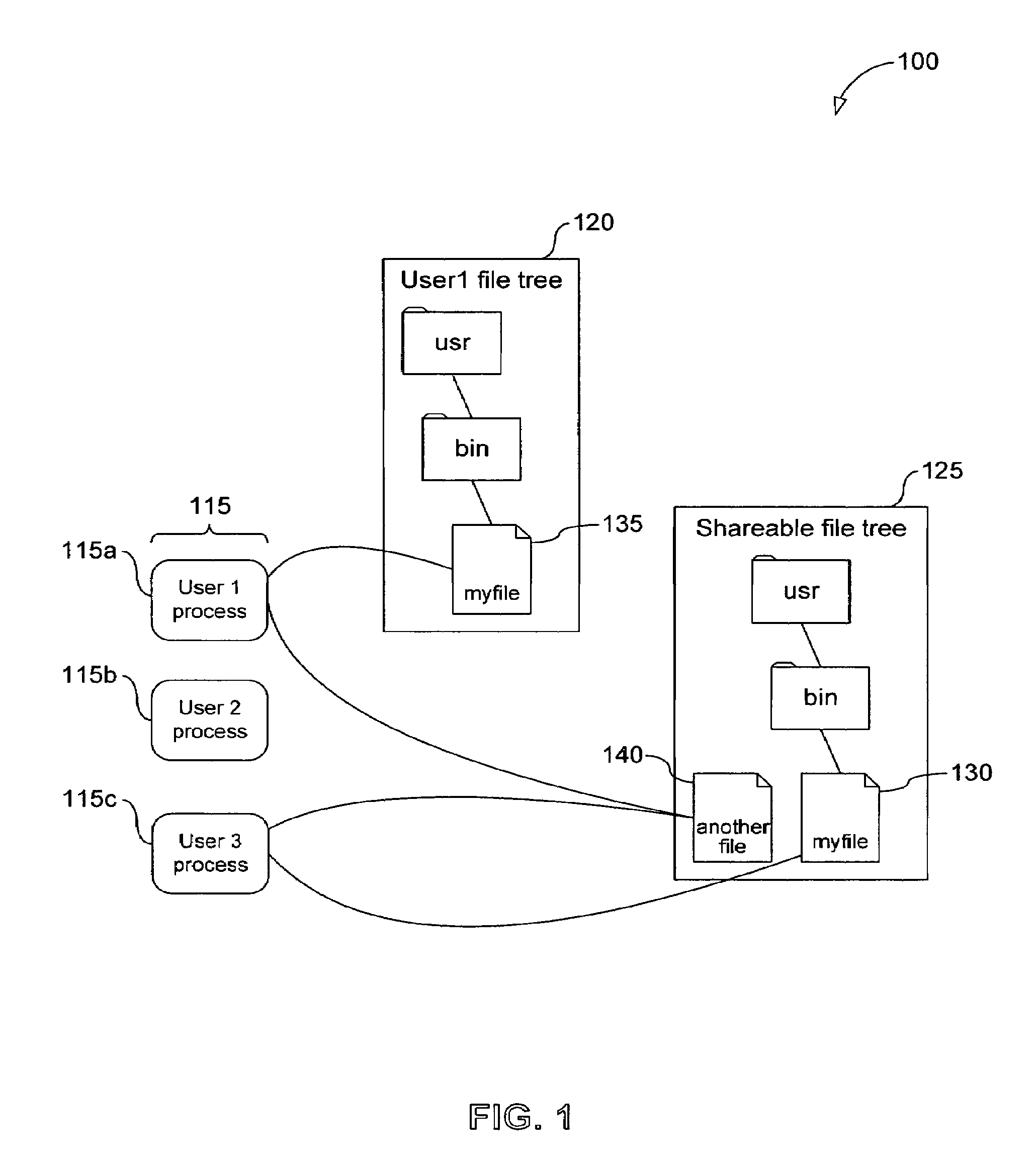
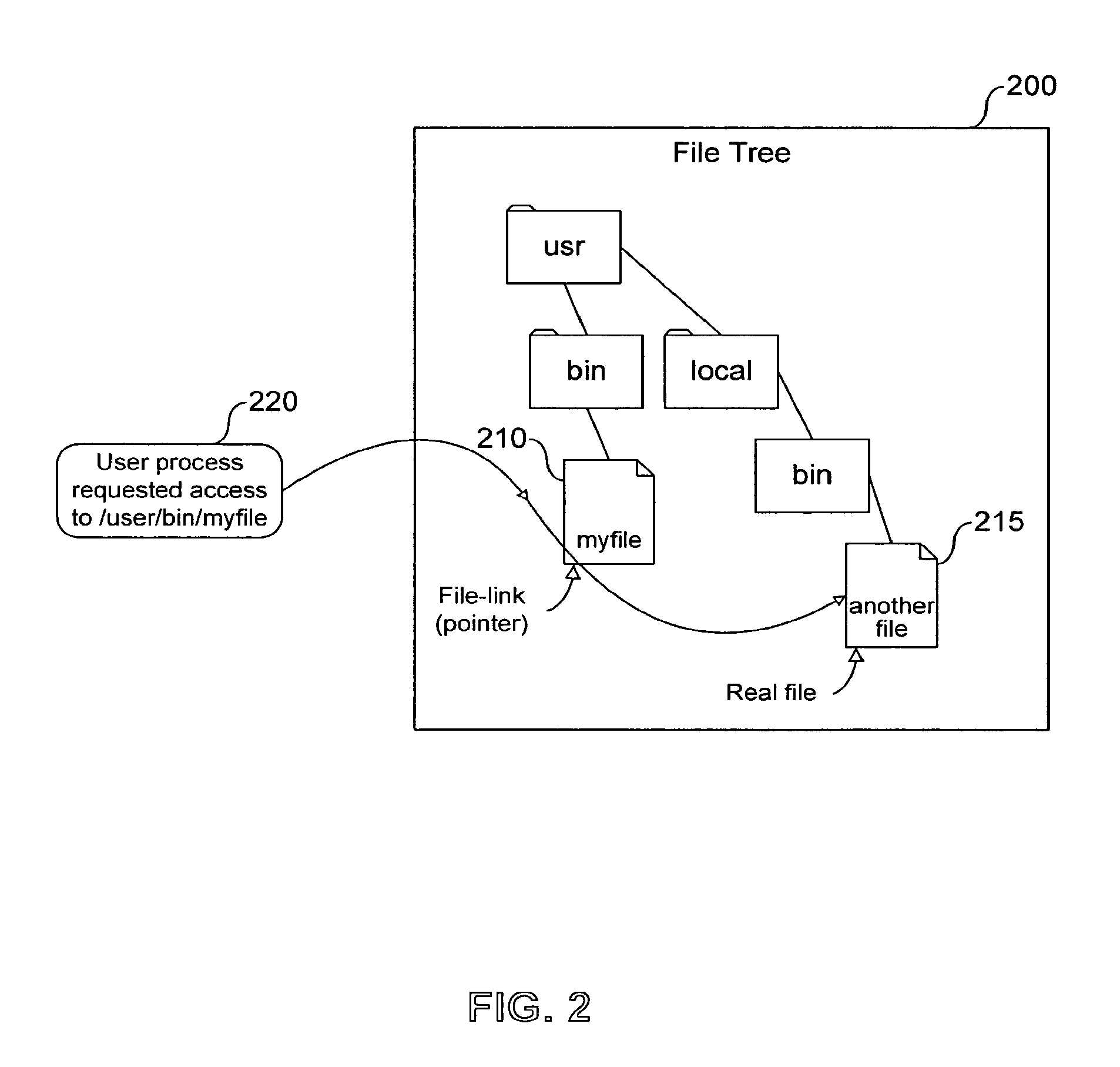
System, method and computer program product for multi-level file-sharing by concurrent users
ActiveUS7328225B1Efficient multi-user accessEfficient file sharingData processing applicationsSpecial data processing applicationsOperational systemFile size
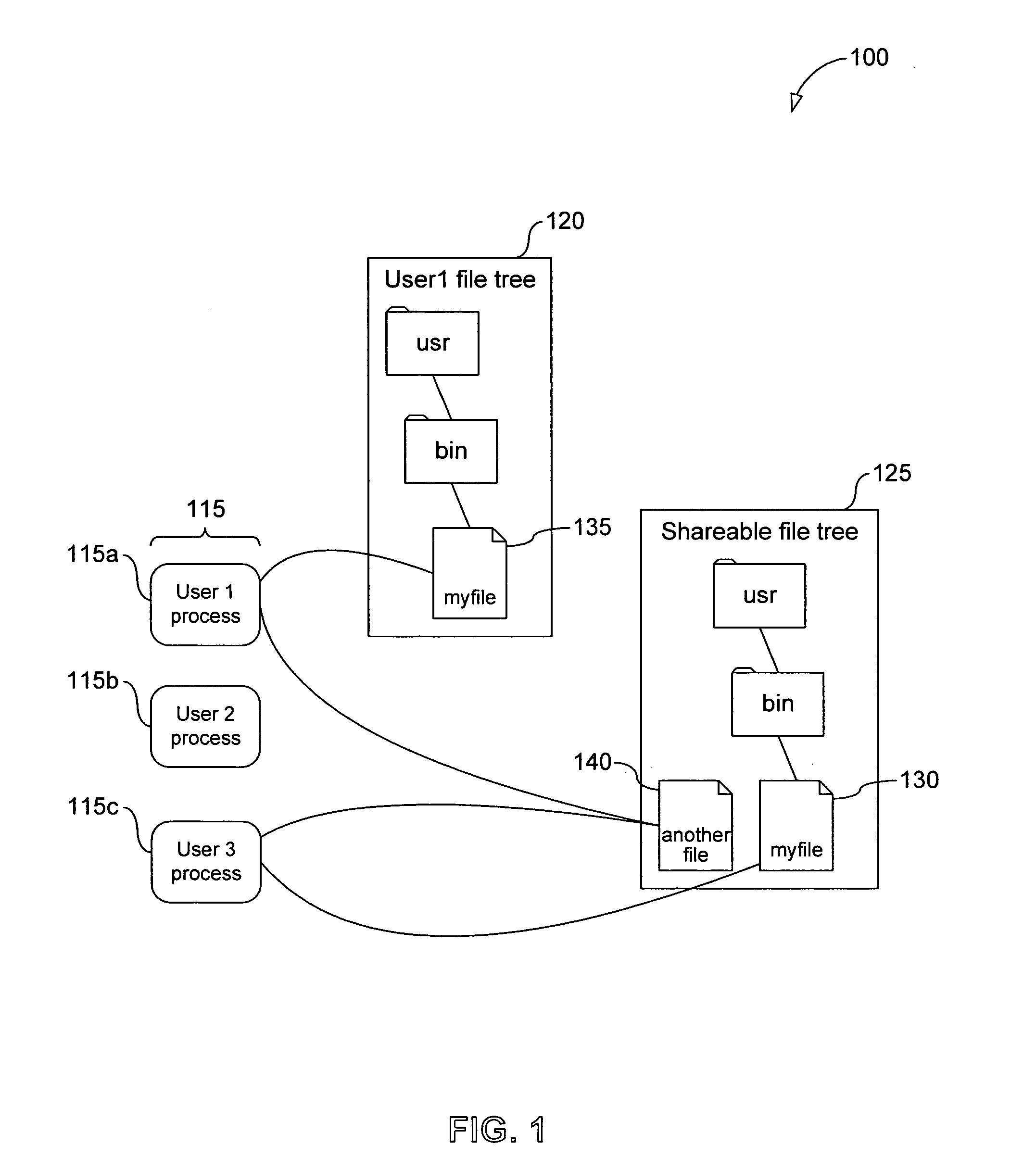
A method of accessing a shareable computer file includes receiving a request to access the shareable computer file, retrieving a file ID from a stub file corresponding to the shareable computer file, retrieving a file name from a database corresponding to the file ID, accessing the shareable computer file if a user has not modified the shareable computer file, and accessing a modified copy of the shareable file stored in the stub file if the user has modified the shareable computer file. A database is generated in operating system space or accessed using the operating system, and includes file IDs and their corresponding file names for shareable computer files. The stub file is generated locally to correspond to the shareable computer file, and includes a modified copy of the shareable computer file if the shareable computer file has been modified, and a link to the shareable computer file if the shareable computer file has not been modified. If the shareable computer file has not been modified, a read-only operation retrieves any of file contents, file position and file size from the shareable computer file. File attributes relating to the shareable computer file can be retrieved from the stub file. The database is provided by the operating system for use by a Virtual Private Server.
Owner:VIRTUOZZO INT GMBH
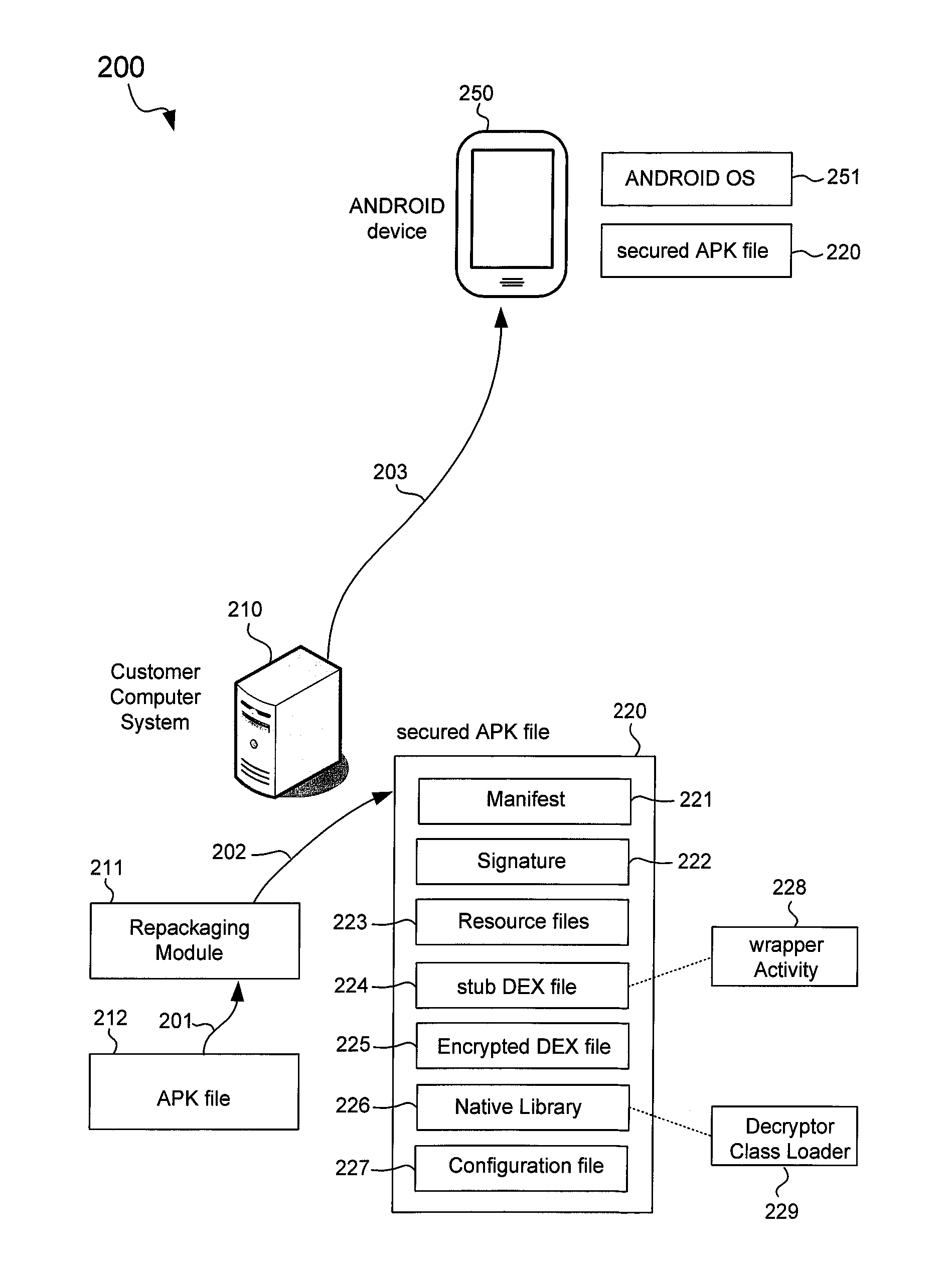
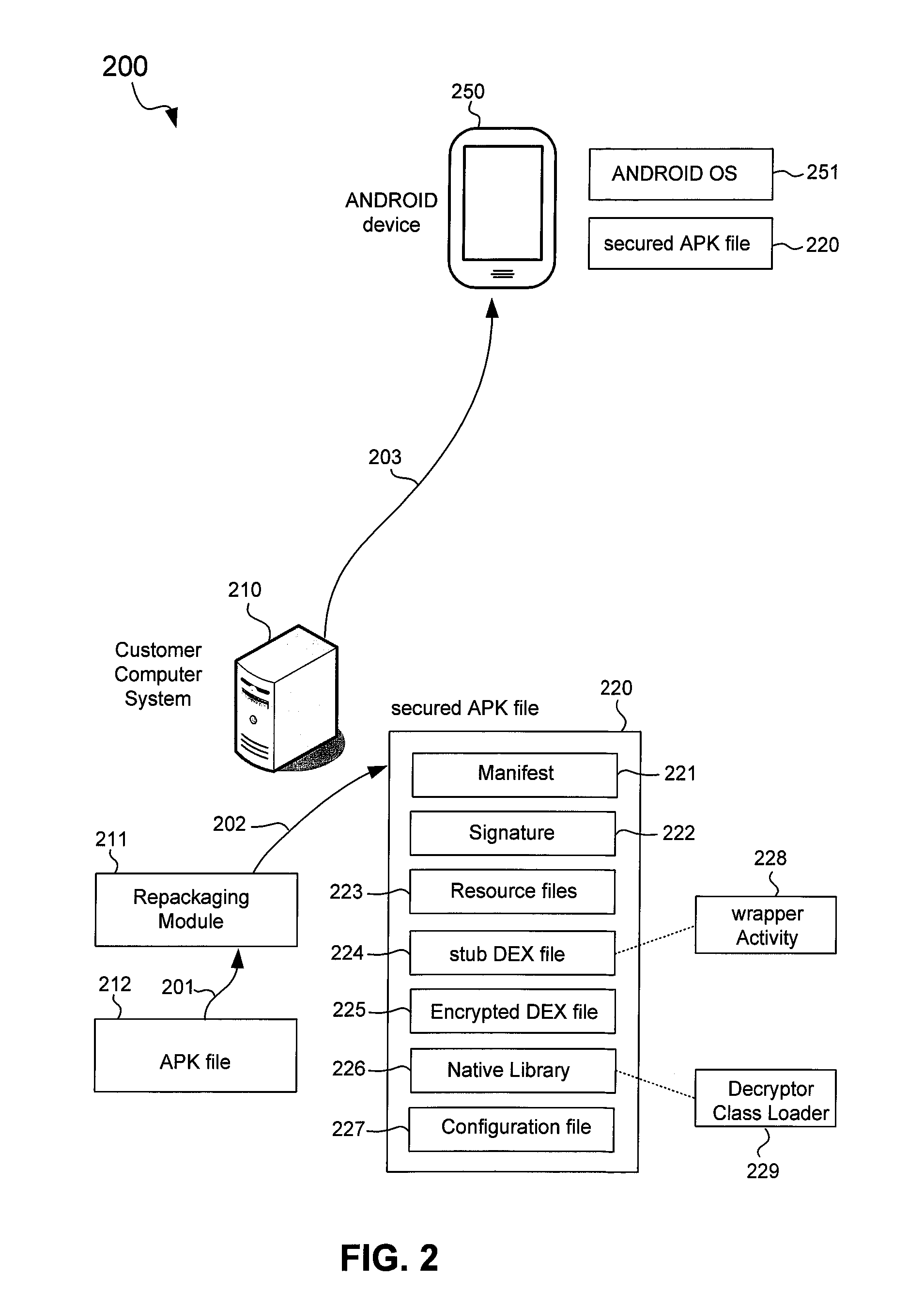
Secured application package files for mobile computing devices
An ANDROID application package (APK) file for an application is repackaged into a secured APK file to protect a Dalvik executable (DEX) file of the application. The DEX file is encrypted to generate an encrypted DEX file that is included in the secured APK file along with a stub DEX file. The secured APK file is received in a mobile computing device where the stub DEX file is started to start a wrapper Activity. The wrapper Activity replaces an APK class loader of a mobile operating system of the mobile computing device with a decryptor class loader. The decryptor class loader decrypts the encrypted DEX file to recover the DEX file, and loads classes of the DEX file into a Dalvik virtual machine. The original Activity of the application is then started to provide the functionality of the application in the mobile computing device.
Owner:TREND MICRO INC
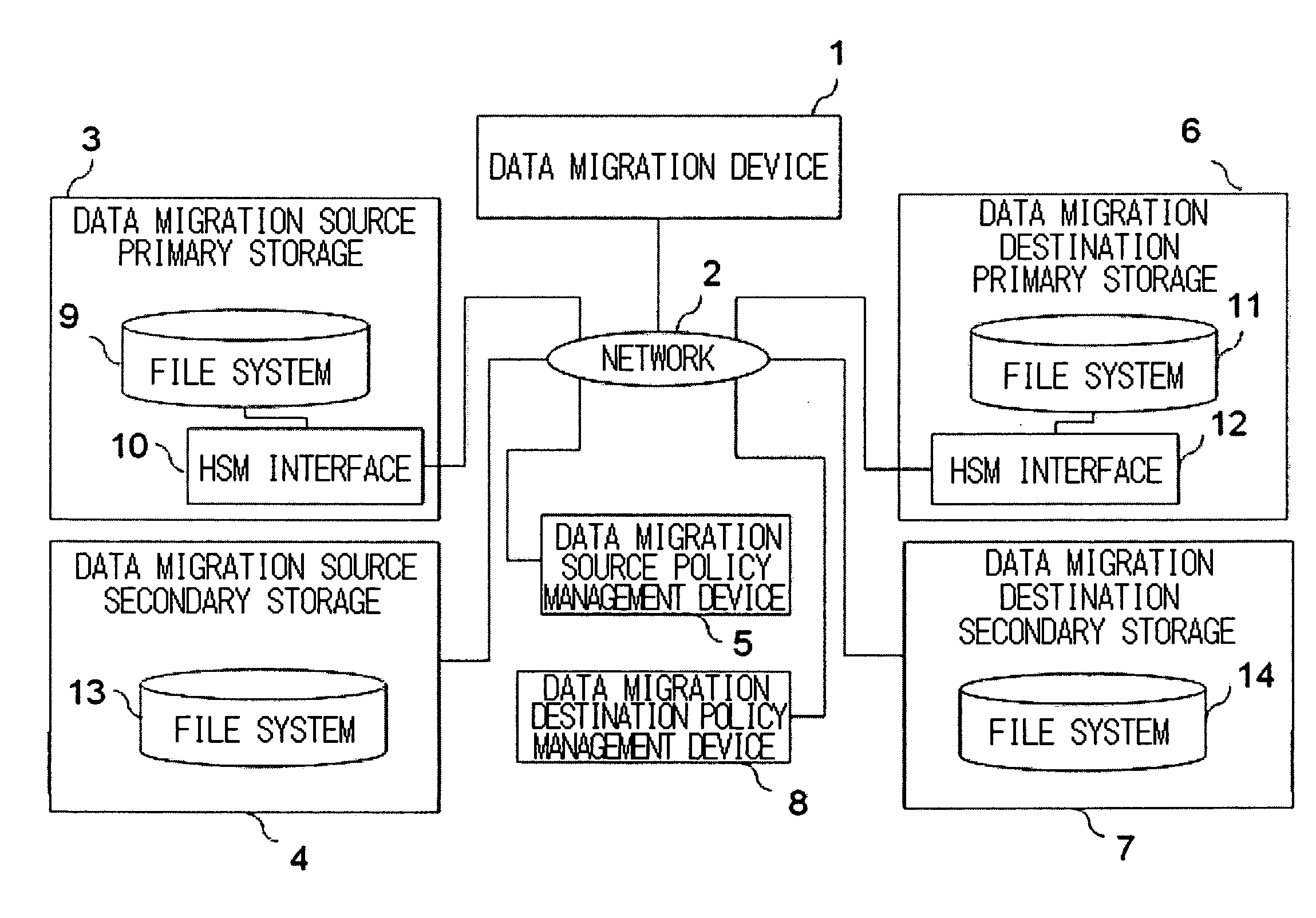
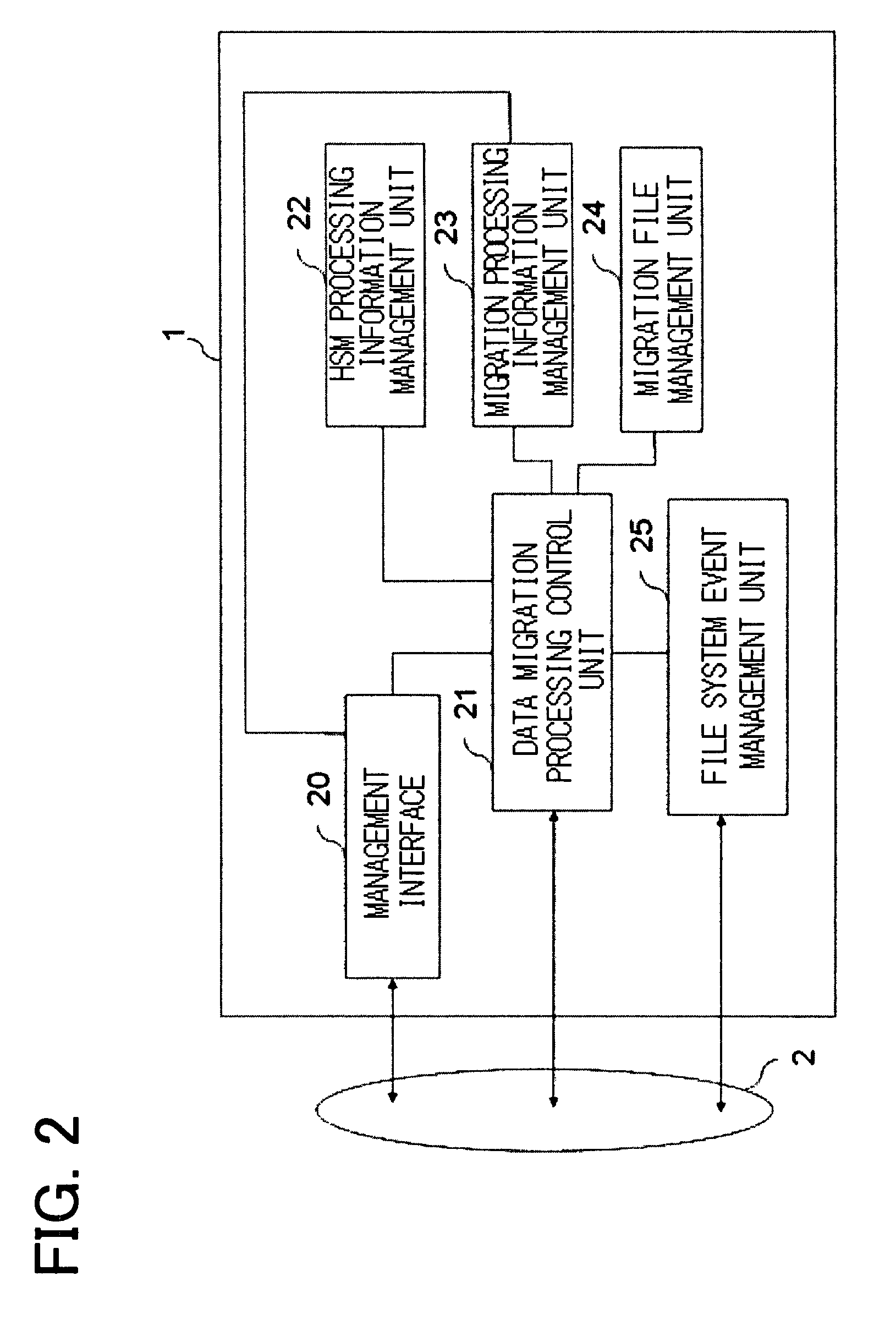
Data migration apparatus, method, and program
ActiveUS20080010325A1Low costEliminate needDigital data information retrievalDigital data processing detailsAuxiliary memoryData storing
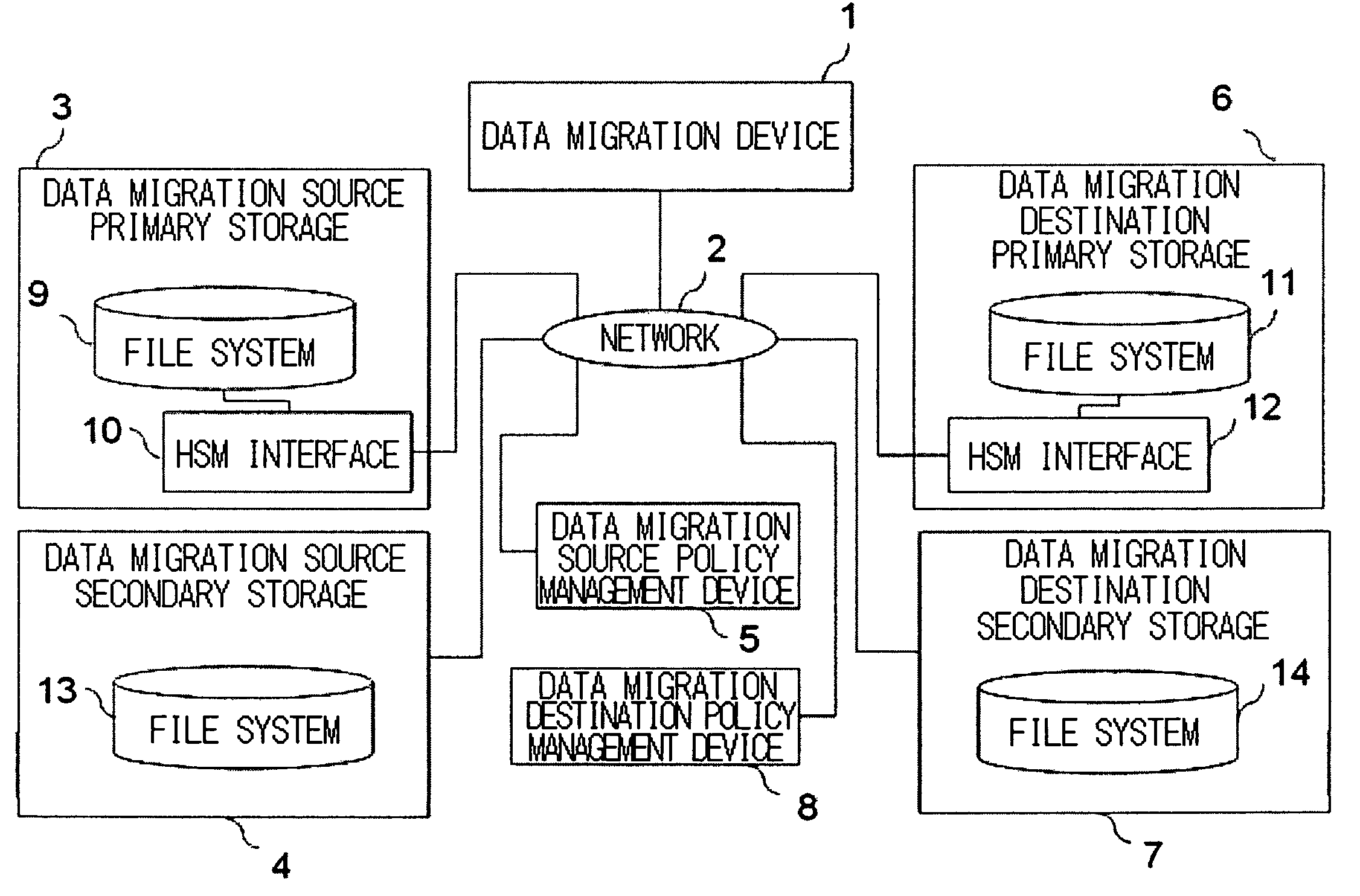
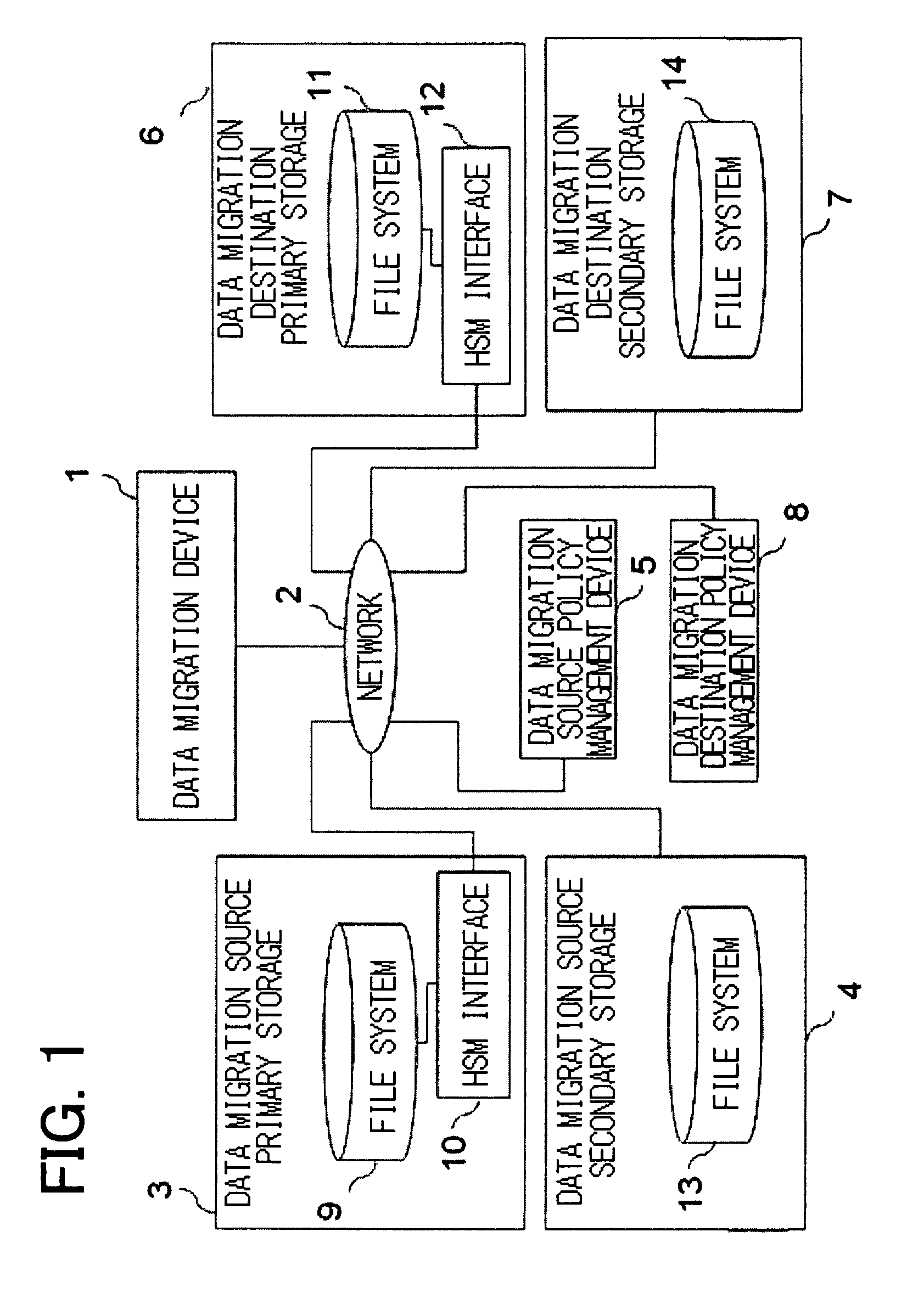
When a migration object is a stub file, a data migration apparatus, which migrates data from a migration source HSM execution environment to a migration destination HSM execution environment, reads data from migration source secondary storage based on a data storage address in the data migration source secondary storage. This data storage address is stored in the stub file stored in data migration source primary storage. The data migration apparatus writes the data, read from the migration source secondary storage, into migration destination secondary storage according to a rule for storing data into the migration destination secondary storage and reads attribute information on the stub file stored in the migration source primary storage. The data migration apparatus creates, in migration destination primary storage, a stub file having the same name as that of the stub file in the migration source and, according to the stub file generation format in the migration destination primary storage, supplies the address of the data stored in the migration destination secondary storage and the attribute information acquired from the data migration source primary storage to the created stub file to complete the data migration.
Owner:NEC CORP
Storage management system and method and program
InactiveUS7818287B2Digital data information retrievalDigital data processing detailsInformation accessAuxiliary memory
Disclosed is a storage management system including at least one client, a first server having a primary storage, a second server having a secondary storage, and an intermediate device logically arranged between the client and the first and second servers. The primary storage includes a stub file in which there is recorded the position information of the real file migrated from the primary storage to the secondary storage. The intermediate device exercises control so that, when a file access request of the primary storage of a first server, issued by the client, is received by the intermediate device, the intermediate device receives the file access request and, if the file to be accessed is a stub file, and the access request necessitates accessing to the real file, the intermediate device accesses the real file of the secondary storage using the information of the stub file to return a response.
Owner:NEC CORP
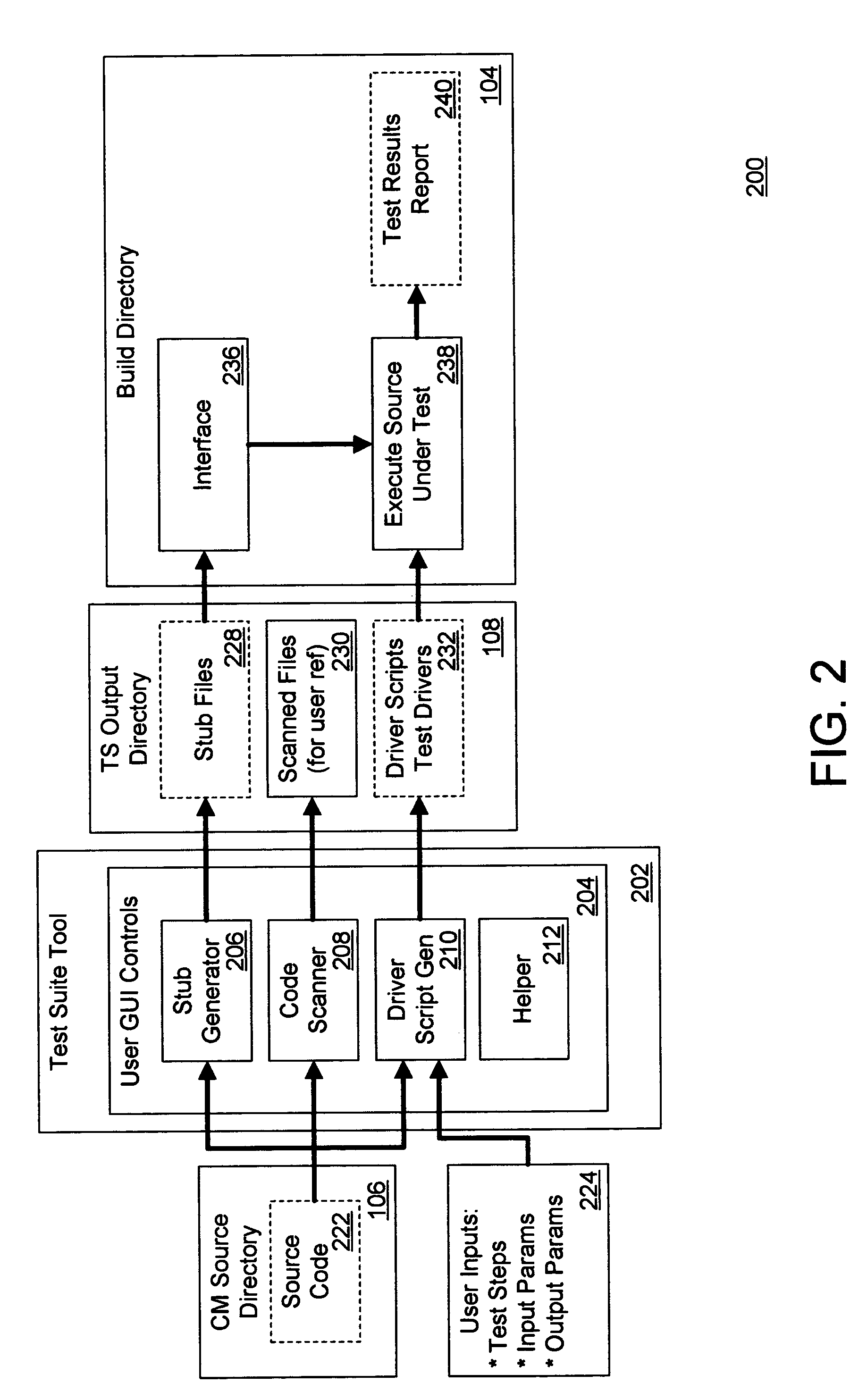
Method and system for object level software testing
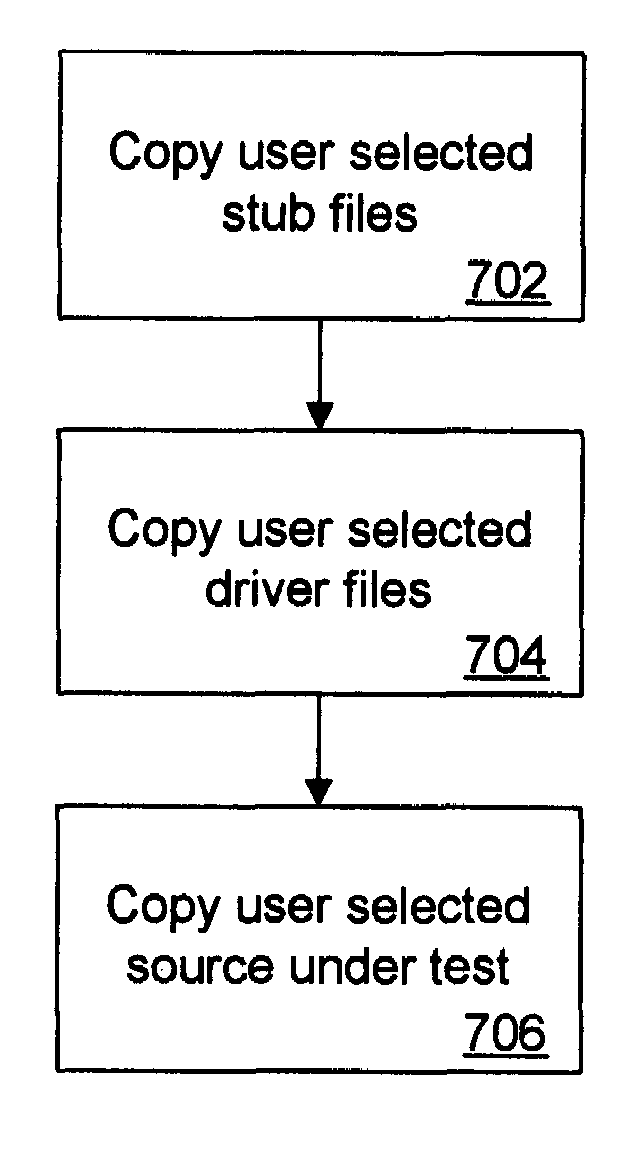
A system, method, and computer program product for software testing, including analyzing the source code under test to generate a scan file, including a map of the source code under test and a tree structure for the source code under test; generating a stub file for the source code under test based on the scan file; generating a driver test script file based on the scan file and the stub file; generating a test driver based on the driver test script file; and running the test driver on the source code under test to generate a results file for summarizing the results of the software testing.
Owner:ENSCO INC
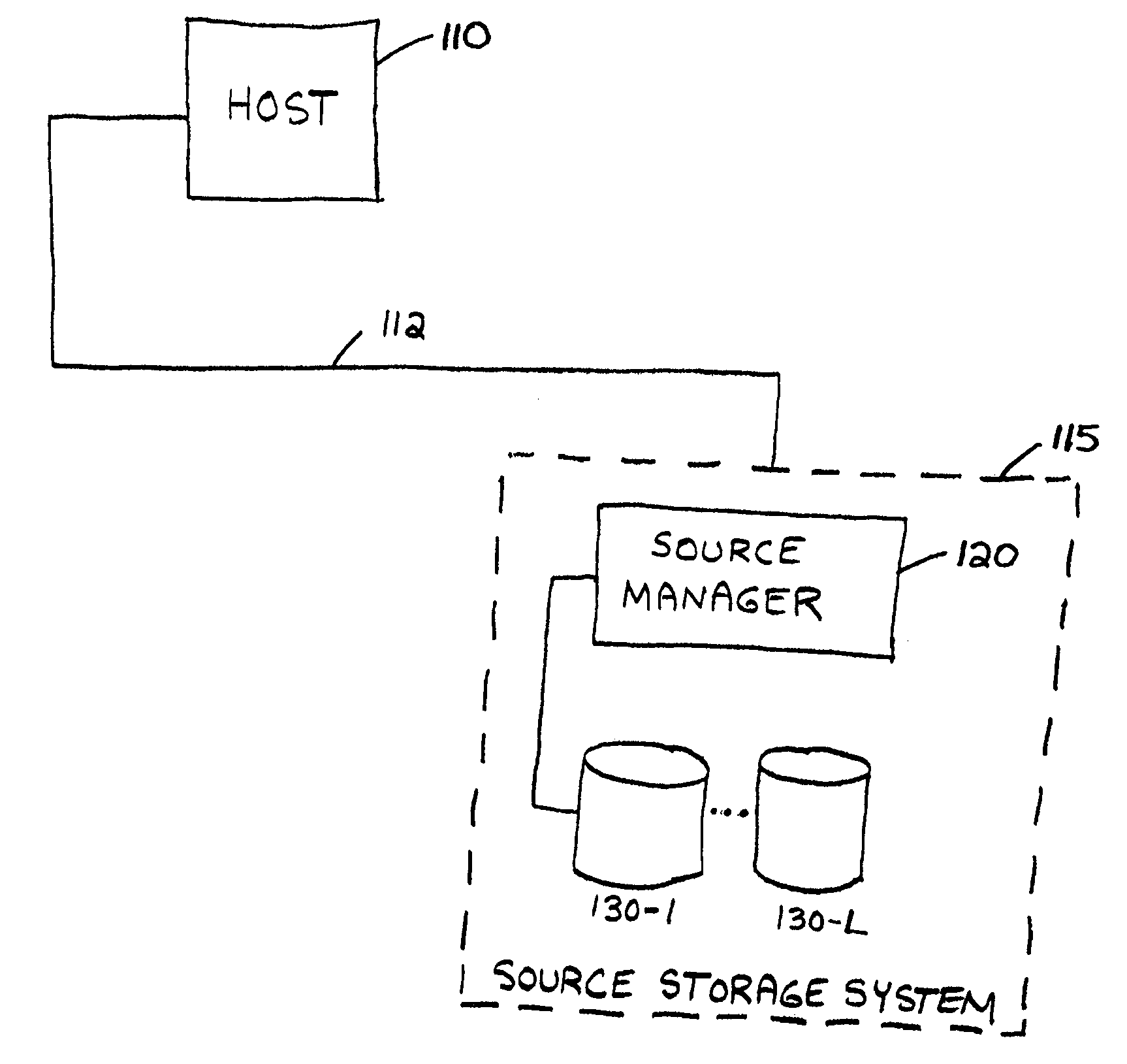
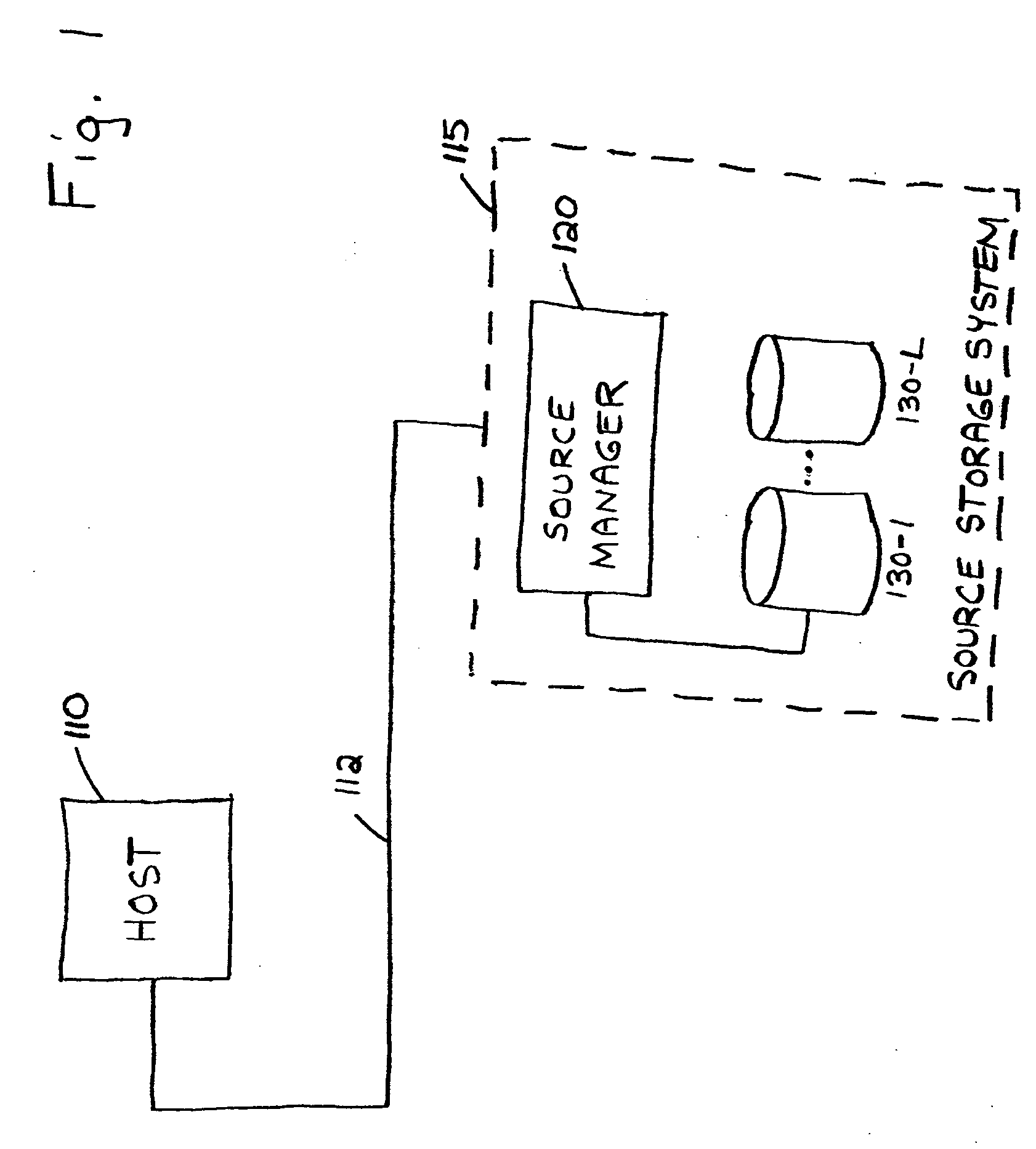
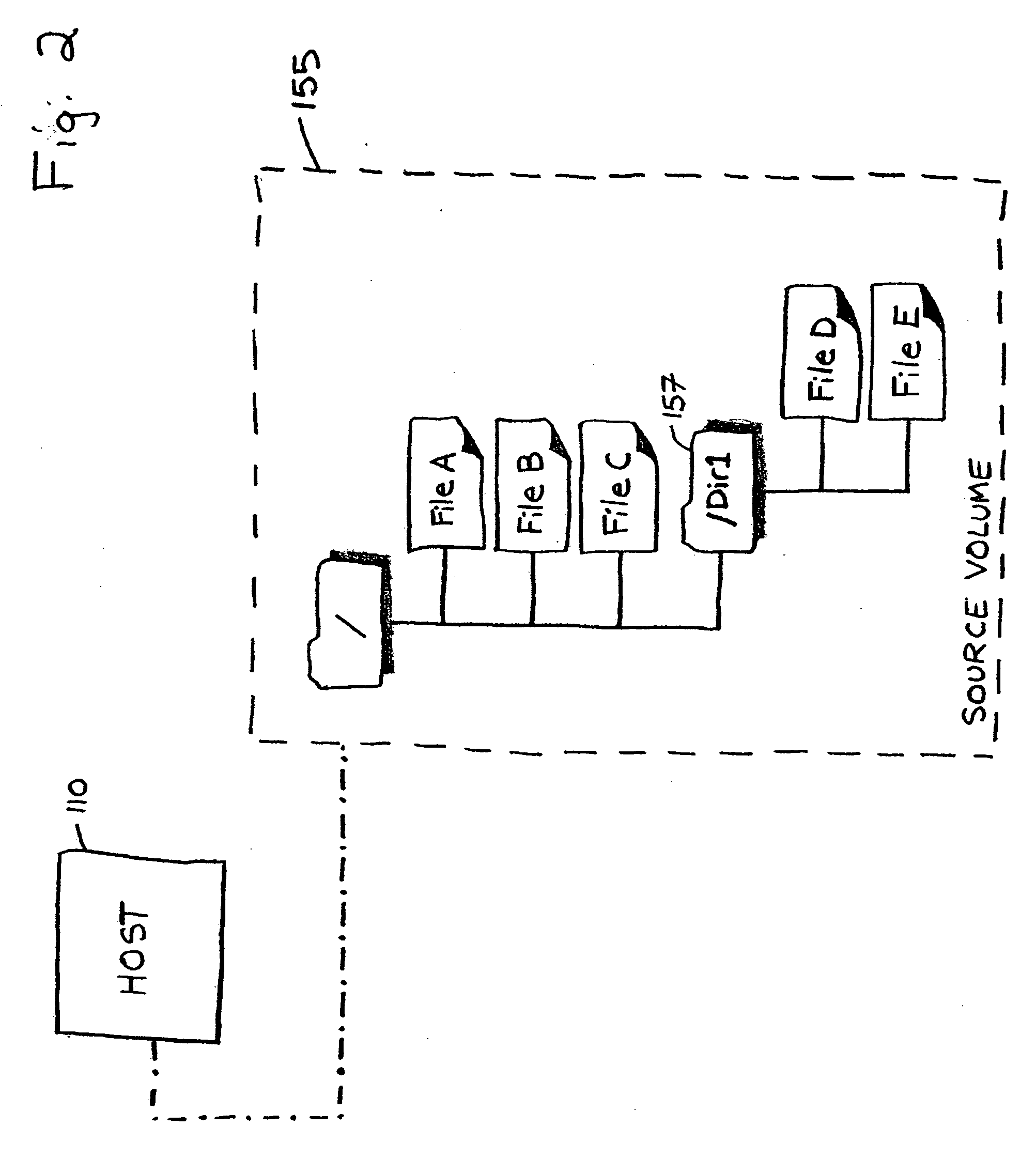
System and method for file migration
A system and method are provided for migrating data files from a source file volume to a target file volume, wherein a target file volume is generated on a target storage device, and a target directory is created based on a directory in the source file volume. In addition, for each file stored in the source file volume, a corresponding stub file is created in the target file volume. The target file volume is mounted to enable a host to access data stored in the target file volume. Files are then copied from the source file volume to the target file volume. In one embodiment, a data processing request is received from the host specifying a stub file stored in the target file volume, a file in the source file volume is identified that corresponds to the specified stub file, and the file is copied from the source file volume to the target file volume. Requested data is retrieved from the copied file and provided to the host.
Owner:FALCONSTOR
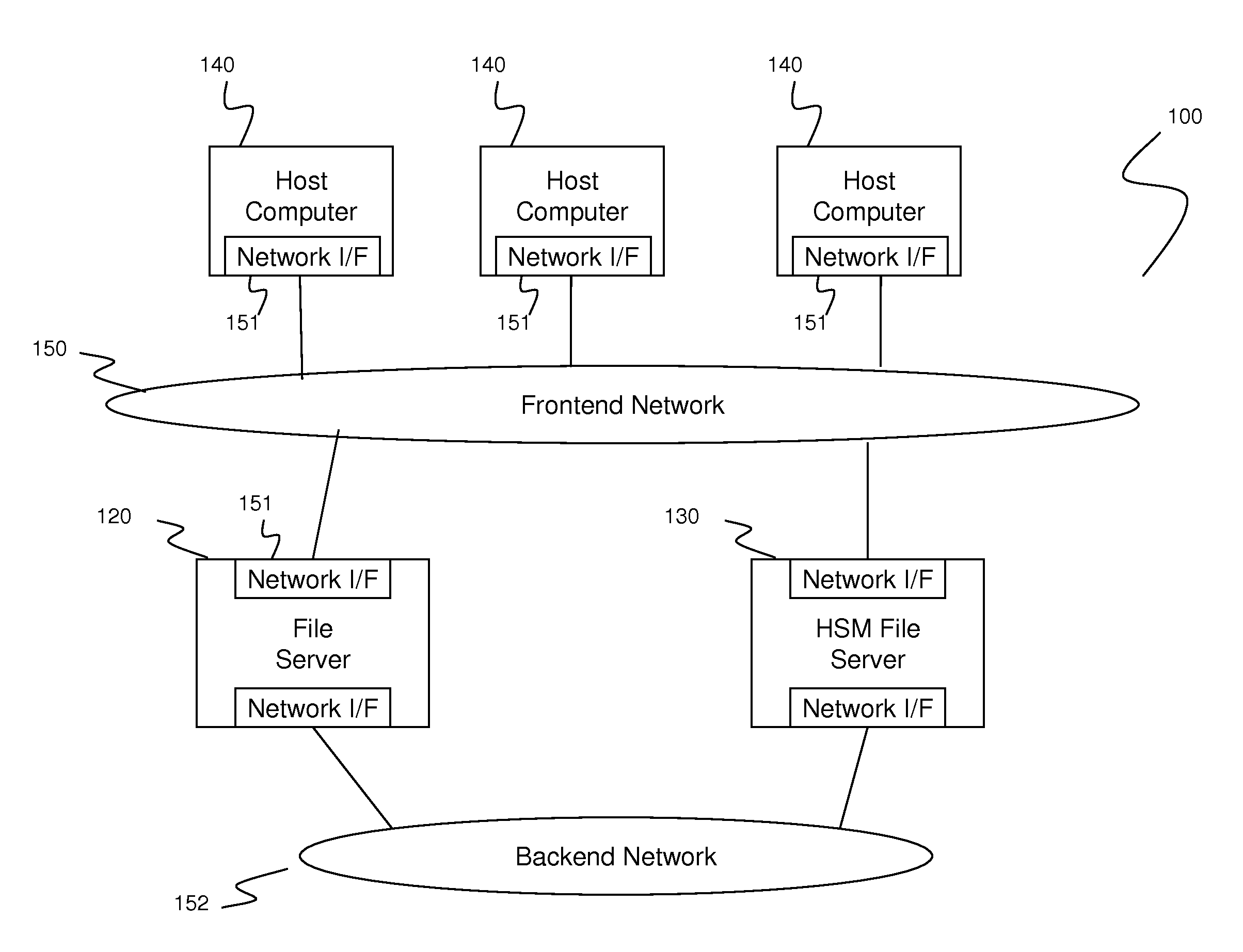
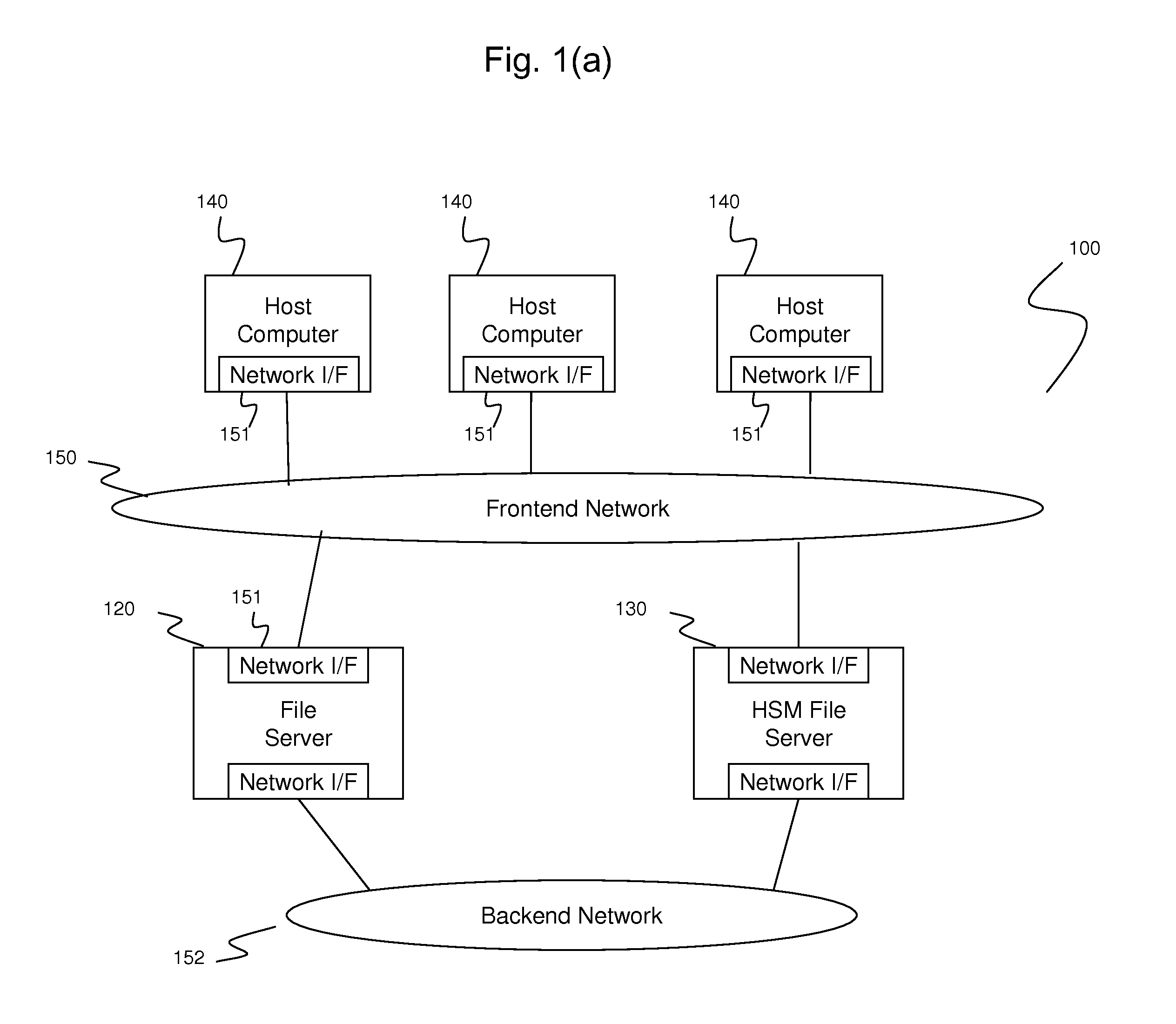
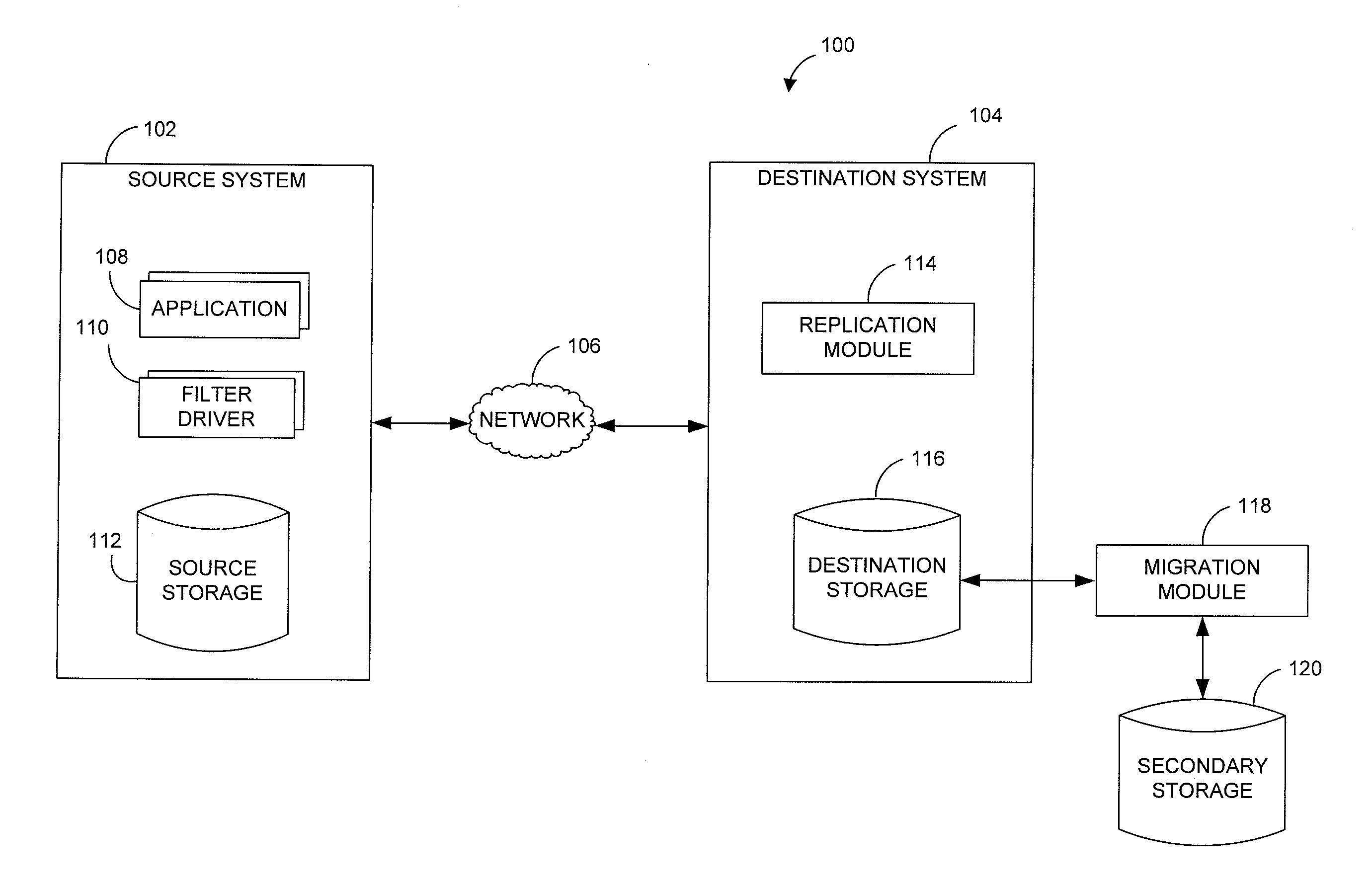
Data synchronization among file storages using stub files
ActiveUS20120150799A1Enable non-disruptive file storage system transitionAvoid useless data synchronizationDigital data information retrievalDigital data processing detailsFile synchronizationData synchronization
A method switches file server from old file server to new file server which are coupled via a backend network and provides data synchronization. The old file server and new file server are coupled with one or more host computers via a frontend network to direct input / output (I / O) requests from the one or more host computers. The method comprises creating stub files in the new file server, the stub files including stub information indicating location of data in the old file server; switching I / O requests directed to old file server to I / O requests directed to the new file server; checking whether the new file server has any stub files; and, if the new file server has one or more stub files, recalling data corresponding to the one or more stub files from the old file server according to the stub information to replace the one or more stub files.
Owner:HITACHI LTD
Stubbing systems and methods in a data replication environment
Stubbing systems and methods are provided for intelligent data management in a replication environment, such as by reducing the space occupied by replication data on a destination system. In certain examples, stub files or like objects replace migrated, de-duplicated or otherwise copied data that has been moved from the destination system to secondary storage. Access is further provided to the replication data in a manner that is transparent to the user and / or without substantially impacting the base replication process. In order to distinguish stub files representing migrated replication data from replicated stub files, priority tags or like identifiers can be used. Thus, when accessing a stub file on the destination system, such as to modify replication data or perform a restore process, the tagged stub files can be used to recall archived data prior to performing the requested operation so that an accurate copy of the source data is generated.
Owner:COMMVAULT SYST INC
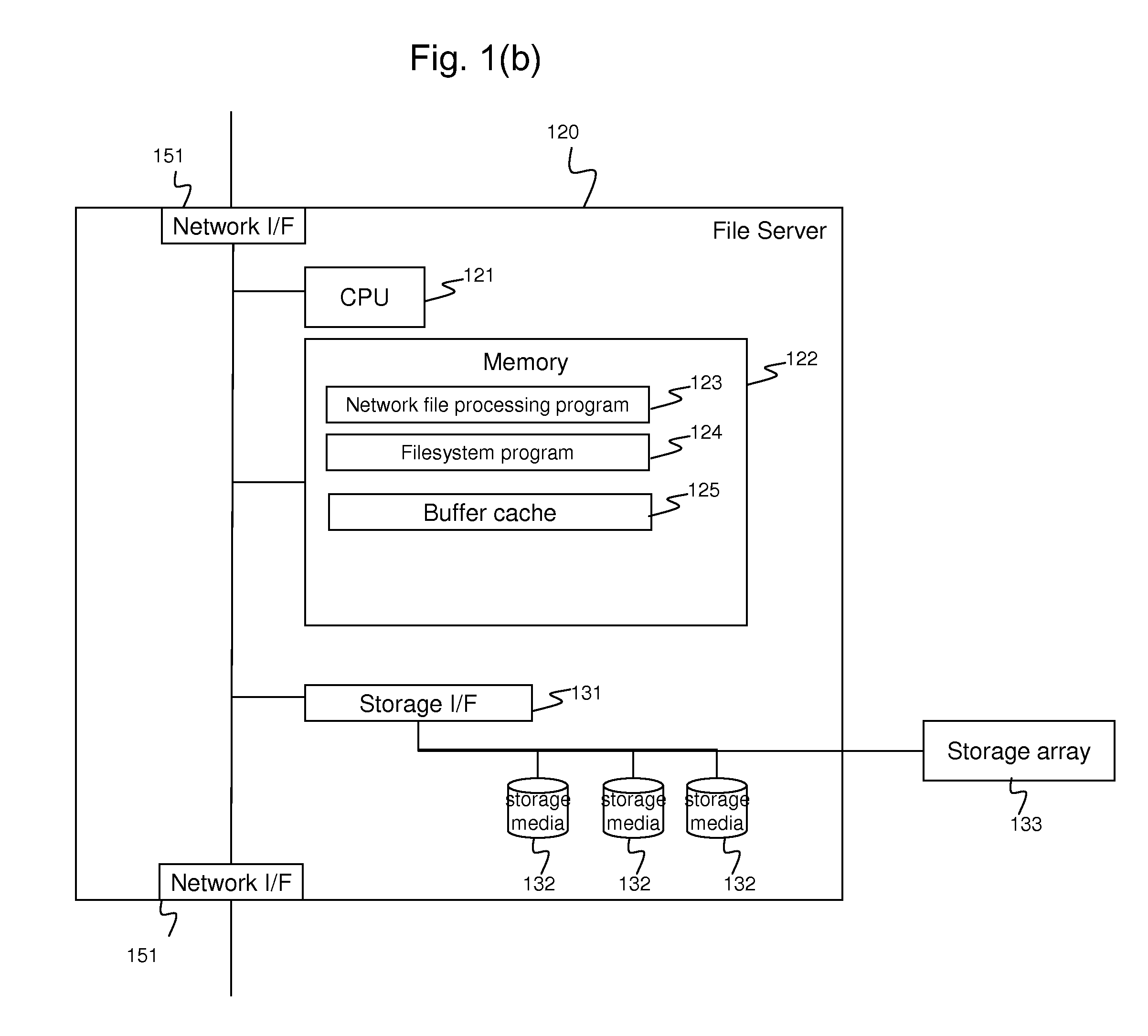
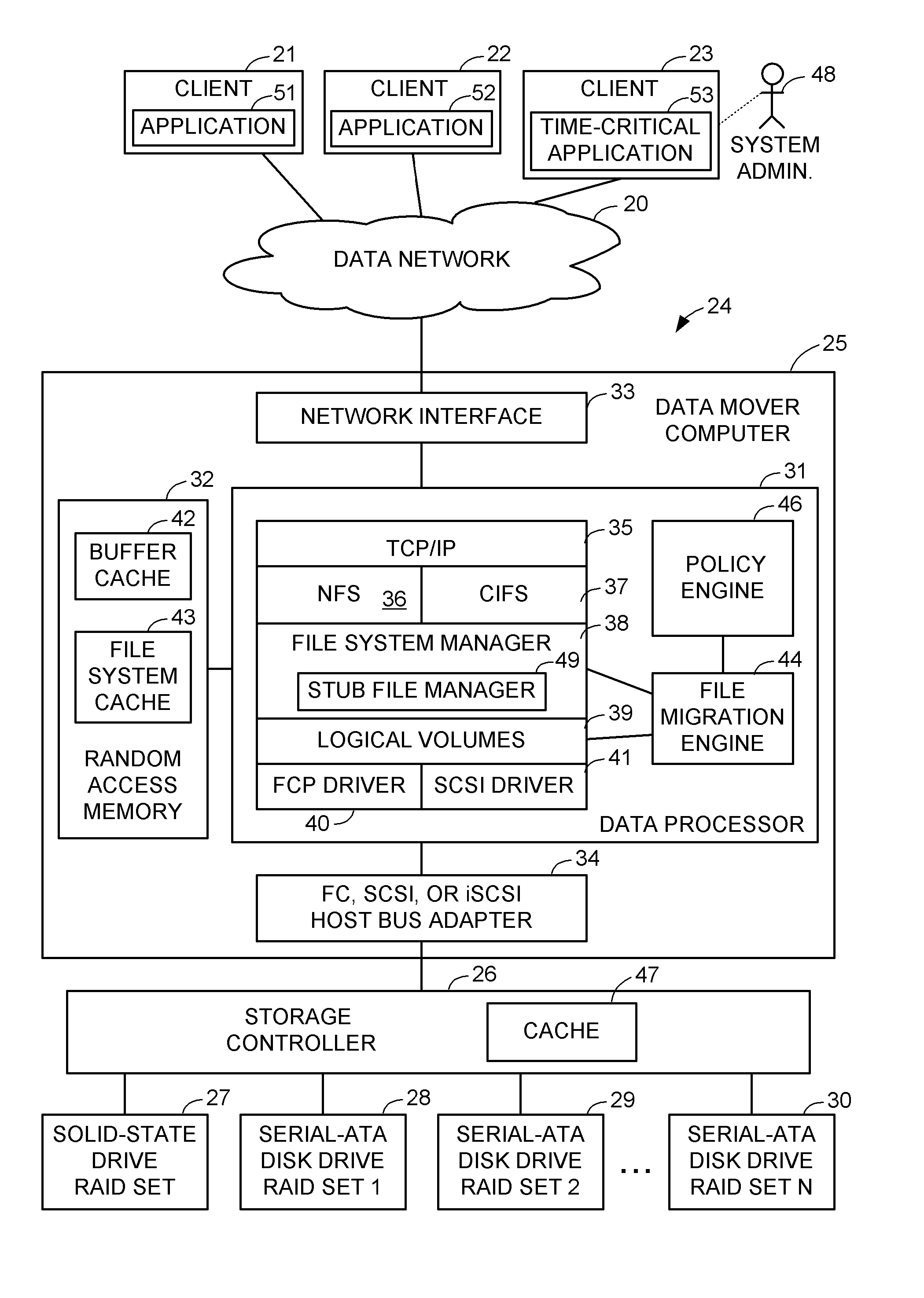
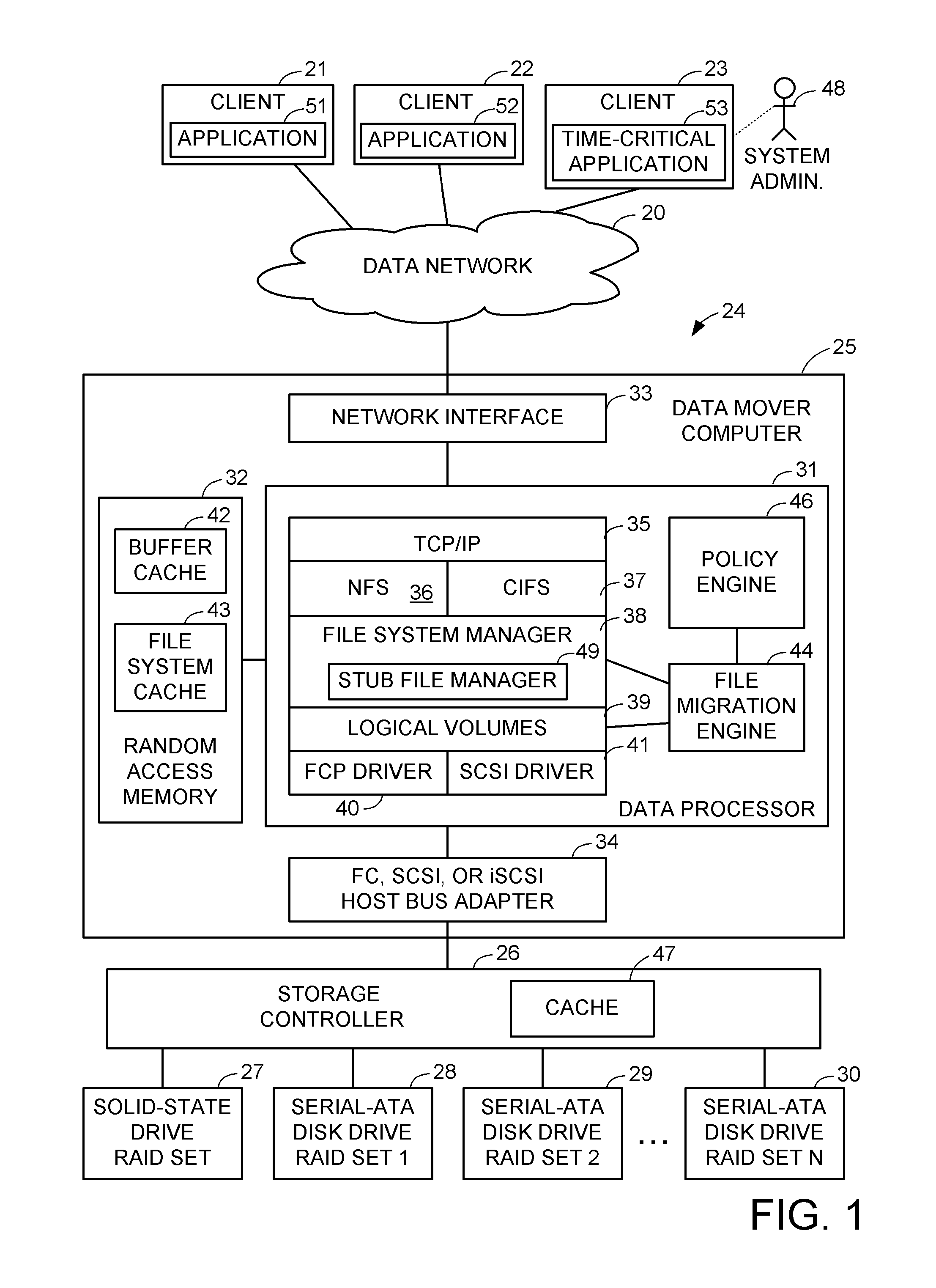
File server system having tiered storage including solid-state drive primary storage and magnetic disk drive secondary storage
ActiveUS9213721B1Digital data information retrievalDigital data processing detailsLoad SheddingFile system
A file server system having solid-state drive primary storage and magnetic disk drive secondary storage aggressively moves newly created files from the primary storage to selected file systems in the secondary storage to match expected access patterns upon the files to different configurations of the file systems and for load balancing upon the file systems in the secondary storage. Upon read access to a file that has been moved to the secondary storage, or upon migration of a newly created file that was read in primary storage after creation, a corresponding stub file containing file mapping metadata is created in the primary storage. The file mapping metadata in the stub file maps the extent of the file to logical storage addresses in the secondary storage.
Owner:EMC IP HLDG CO LLC
System, method and computer program product for multi-level file-sharing by concurrent users
ActiveUS7676526B1Efficient multi-user access and file sharingSolve excessive overheadData processing applicationsSpecial data processing applicationsOperational systemFile size
A method of accessing a shareable computer file includes receiving a request to access the shareable computer file, retrieving a file ID from a stub file corresponding to the shareable computer file, retrieving a file name from a database corresponding to the file ID, accessing the shareable computer file if a user has not modified the shareable computer file, and accessing a modified copy of the shareable file stored in the stub file if the user has modified the shareable computer file. A database is generated in operating system space or accessed using the operating system, and includes file IDs and their corresponding file names for shareable computer files. The stub file is generated locally to correspond to the shareable computer file, and includes a modified copy of the shareable computer file if the shareable computer file has been modified, and a link to the shareable computer file if the shareable computer file has not been modified. If the shareable computer file has not been modified, a read-only operation retrieves any of file contents, file position and file size from the shareable computer file. File attributes relating to the shareable computer file can be retrieved from the stub file. The database is provided by the operating system for use by a Virtual Private Server.
Owner:VIRTUOZZO INT GMBH
Distributed open writable snapshot copy facility using file migration policies
A read-write snapshot copy facility is constructed from a hierarchical storage management facility. The read-write snapshot copy file system initially comprises stub files pointing to the files in a read-only snapshot copy file system. When an application writes to a file in the read-write snapshot copy, the read-write snapshot copy facility migrates a copy of the file to replace the stub file, and then writes to the migrated file. Because the read-write snapshot copy facility references the files in the read-only snapshot file system in a network namespace using standard protocols such as NFS or CIFS, the read-write snapshot copy facility permits referencing of distributed read-only snapshot file systems in an open (heterogeneous) network environment, and the read-write snapshot copy is scalable by linking the read-write snapshot copy facility to multiple file servers containing read-only snapshot file systems.
Owner:EMC IP HLDG CO LLC
Stub file prioritization in a data replication system
ActiveUS8725698B2Digital data information retrievalError detection/correctionGoal systemData management
Stubbing systems and methods are provided for intelligent data management in a replication environment, such as by reducing the space occupied by replication data on a destination system. In certain examples, stub files or like objects replace migrated, de-duplicated or otherwise copied data that has been moved from the destination system to secondary storage. Access is further provided to the replication data in a manner that is transparent to the user and / or without substantially impacting the base replication process. In order to distinguish stub files representing migrated replication data from replicated stub files, priority tags or like identifiers can be used. Thus, when accessing a stub file on the destination system, such as to modify replication data or perform a restore process, the tagged stub files can be used to recall archived data prior to performing the requested operation so that an accurate copy of the source data is generated.
Owner:COMMVAULT SYST INC
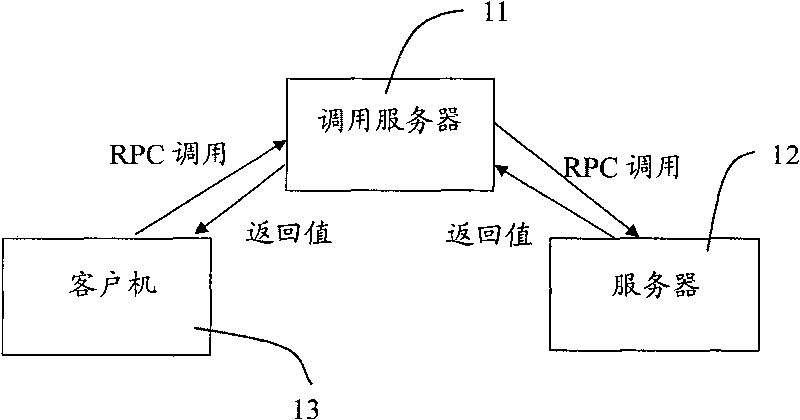
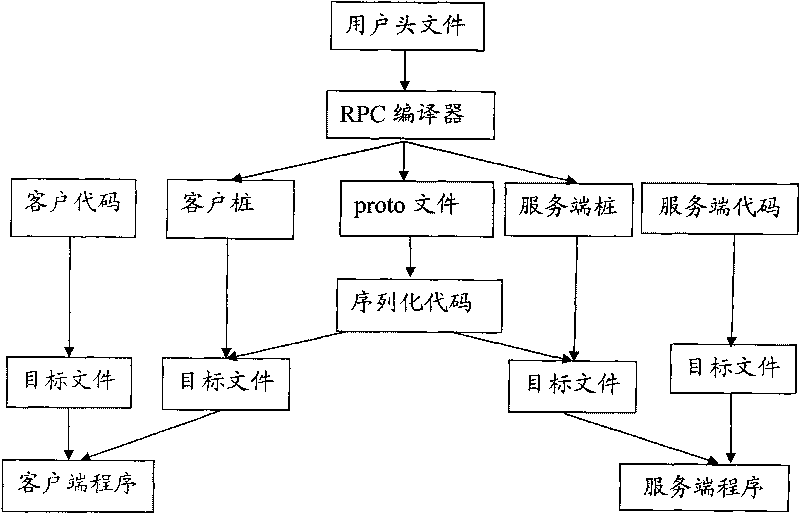
Remote procedure calling (PRC) method and system
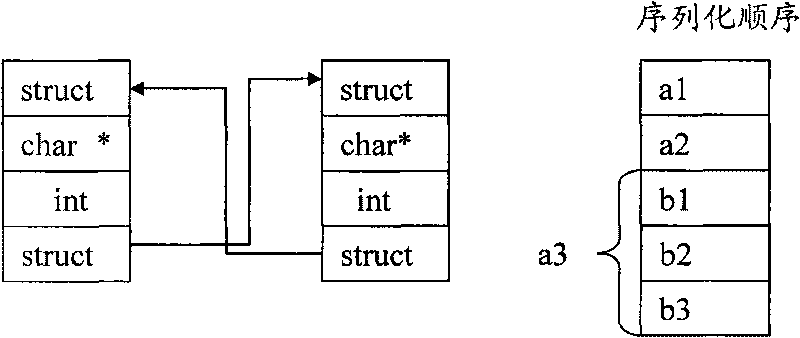
The invention discloses remote procedure calling (PRC) method and system, wherein the system comprises a communication module, a serializing module, a scheduling module and a compiling module, wherein the communication module is used for providing a basal communication mechanism for RPC; the serializing module is used for carrying out serialization and deserialization to a transmitted message; the scheduling module is used for scheduling the whole RPC and comprises an asynchronous calling management mechanism, a time-out mechanism and a transaction mechanism; the compiling module is used for providing a support for the conversion among an interface definition language (IDL) file, a user header file and a stub file. The invention overcomes the defects of Web service in the aspects of efficiency and asynchronous calling, and has the advantages of platform independence, simple and easy user code center, and the like.
Owner:SHENZHEN SKYWORTH DIGITAL TECH CO LTD
Hsm two-way orphan reconciliation for extremely large file systems
InactiveUS20100088271A1Maintain integrityMaintaining file system integrityDigital data information retrievalProgram control using stored programsFlash file systemGlobal file system
One aspect of the present invention provides an operation for recovering lost space and maintaining data consistency in a storage environment by providing a two-way orphan reconciliation method for extremely large file systems, such as a Hierarchical Storage Management (HSM) system which manages billions of files. This highly scalable and parallelizable orphan identification process may be used in a HSM controlled environment to enable the execution of a two-way file orphan check. In one embodiment, this orphan check identifies file system client orphans and server object orphans in a single pass by comparing a queue containing a list of migrated files on a storage repository server with a queue containing a list of stub files on a file system. If the queue elements do not match, a file system orphan or server object orphan can appropriately be identified.
Owner:IBM CORP
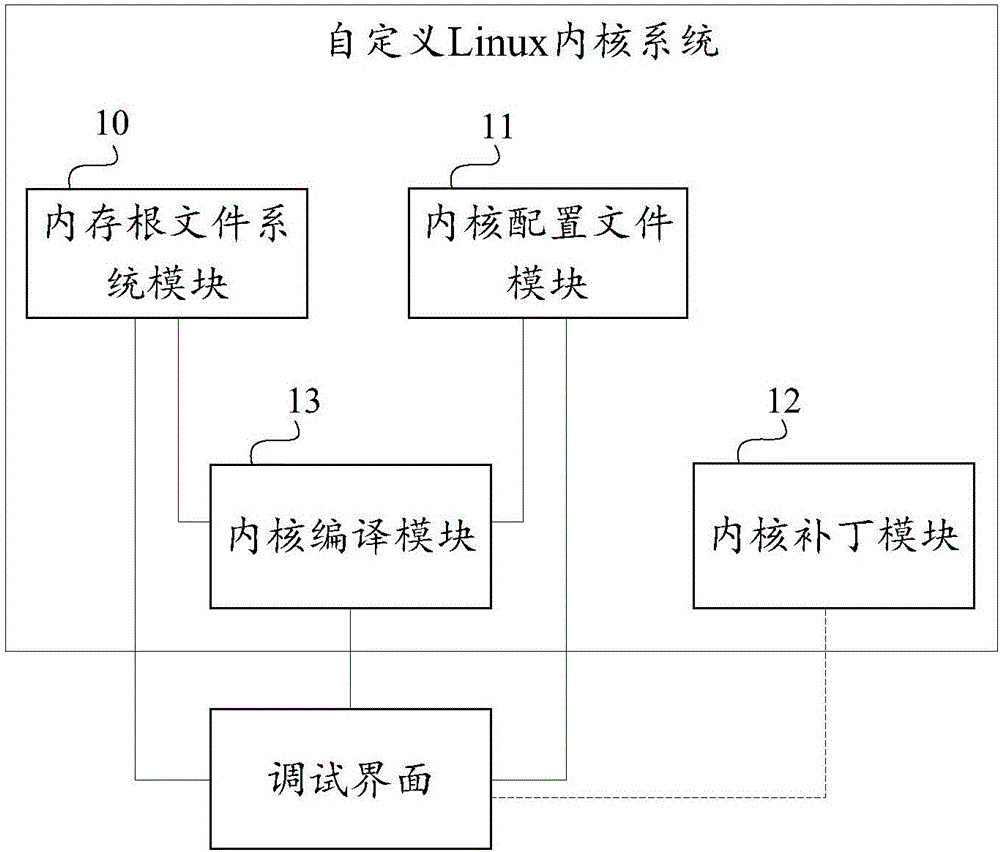
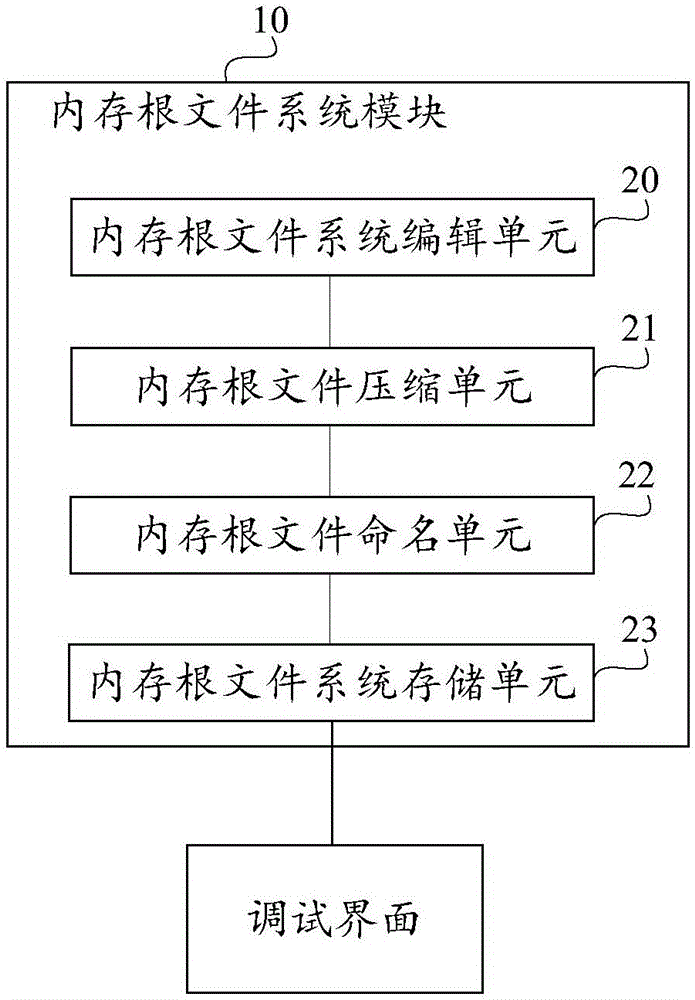
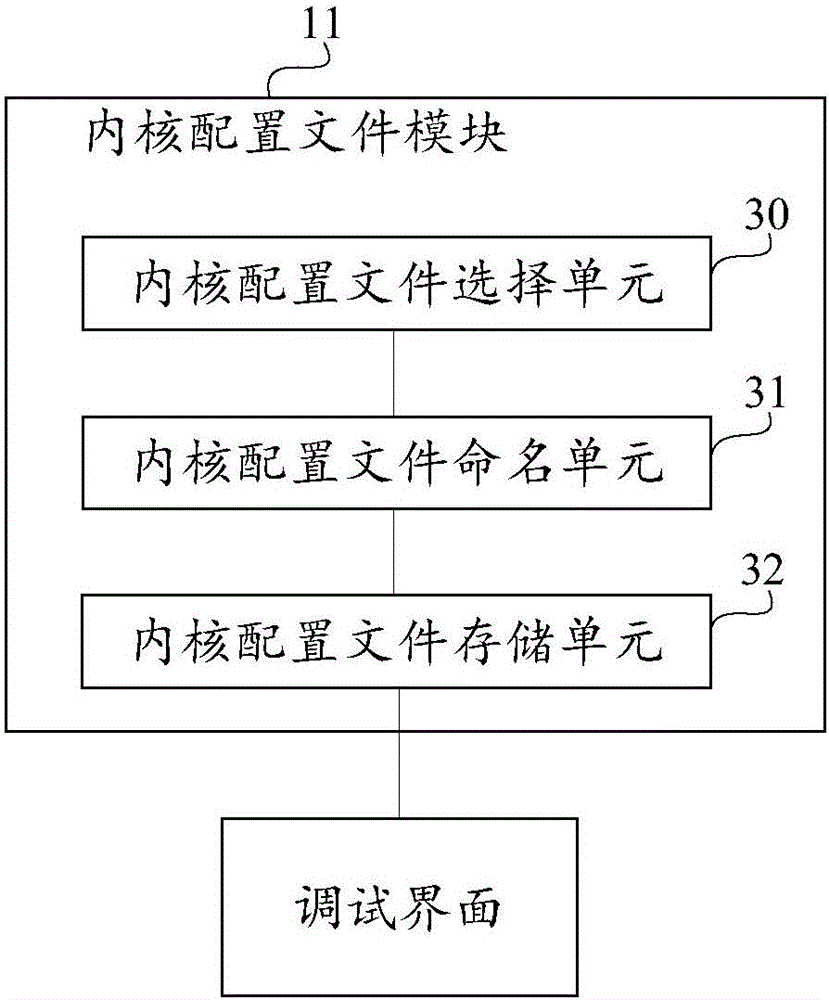
Custom Linux kernel system for quick change
PendingCN106293756AFast transplantQuick changeVersion controlProgram code adaptionFile systemCoupling
The invention provides a custom Linux kernel system for quick change. The custom Linux kernel system is provided with a self-compiling kernel patch module, a memory root file system module, a kernel configuration file module and a kernel compiling module; before executing a compile script by the memory root file system, the memory root file system is complied and stored in a custom way; the kernel configuration file module is used for storing a kernel configuration file in a custom way before executing the compile script; the kernel patch module is used for pre-storing the modification of a Linux kernel in a development process before executing the compile script and a target kernel patch is required; and the kernel compiling module is used for pre-compiling the compile script before executing the compile script in a custom way. The custom Linux kernel system for quick change provided by the invention can effectively reduce the coupling degree of a kernel used by network equipment and an original kernel, accurately and reliably realize rapid transplantation and replacement of different Linux kernel versions, improve the efficiency of kernel version upgrade of the network equipment, and realize the fast support for new hardware drive or new characteristic functions.
Owner:OPZOON TECH
Stubbing systems and methods in a data replication environment
Stubbing systems and methods are provided for intelligent data management in a replication environment, such as by reducing the space occupied by replication data on a destination system. In certain examples, stub files or like objects replace migrated, de-duplicated or otherwise copied data that has been moved from the destination system to secondary storage. Access is further provided to the replication data in a manner that is transparent to the user and / or without substantially impacting the base replication process. In order to distinguish stub files representing migrated replication data from replicated stub files, priority tags or like identifiers can be used. Thus, when accessing a stub file on the destination system, such as to modify replication data or perform a restore process, the tagged stub files can be used to recall archived data prior to performing the requested operation so that an accurate copy of the source data is generated.
Owner:COMMVAULT SYST INC
Data migration apparatus, method, and program for data stored in a distributed manner
ActiveUS7765189B2Low costEliminate needDigital data information retrievalDigital data processing detailsAuxiliary memoryData storing
Owner:NEC CORP
Demand-Based Edge Caching Video Conten System and Method
ActiveUS20120084821A1Multiple digital computer combinationsTwo-way working systemsResource Management SystemComputer science
A method (300) and system (200) for of conserving resources in a video-on-demand environment are provided. The method (300) includes storing a stub file (223) on an edge storage device while storing content (110) at a central storage device (222). When a video-on-demand request (440) is received, a resource management system (206) reads (305) the stub file (223) to determine a storage location at the central storage device (222). The resource management system (206) then retrieves the content (110) from the storage location determined from the stub file (223) and either stores it at an edge storage device (111) or delivers it the a subscriber device (109) to fulfill the video-on-demand request (440).
Owner:VECIMA NETWORKS
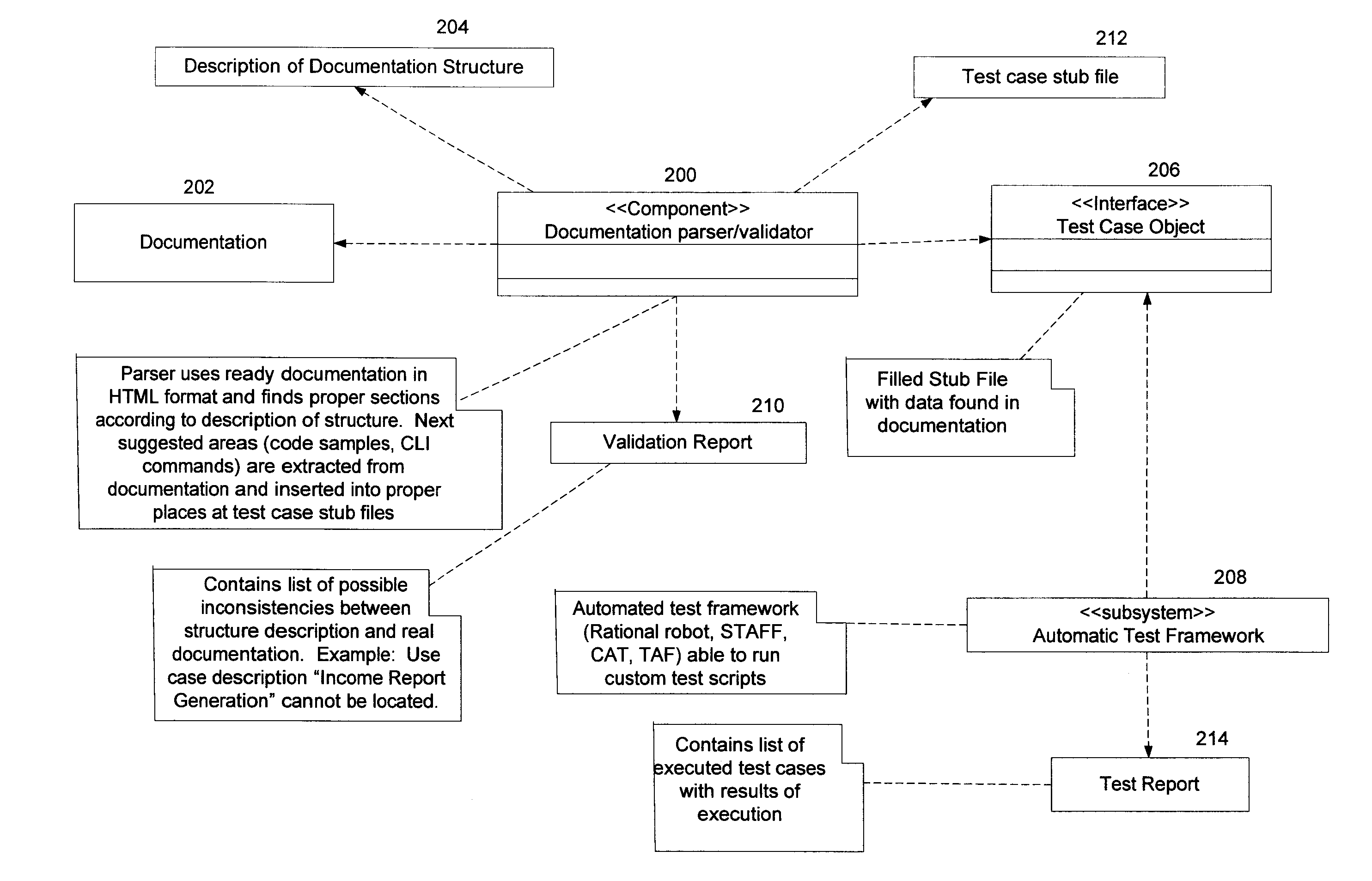
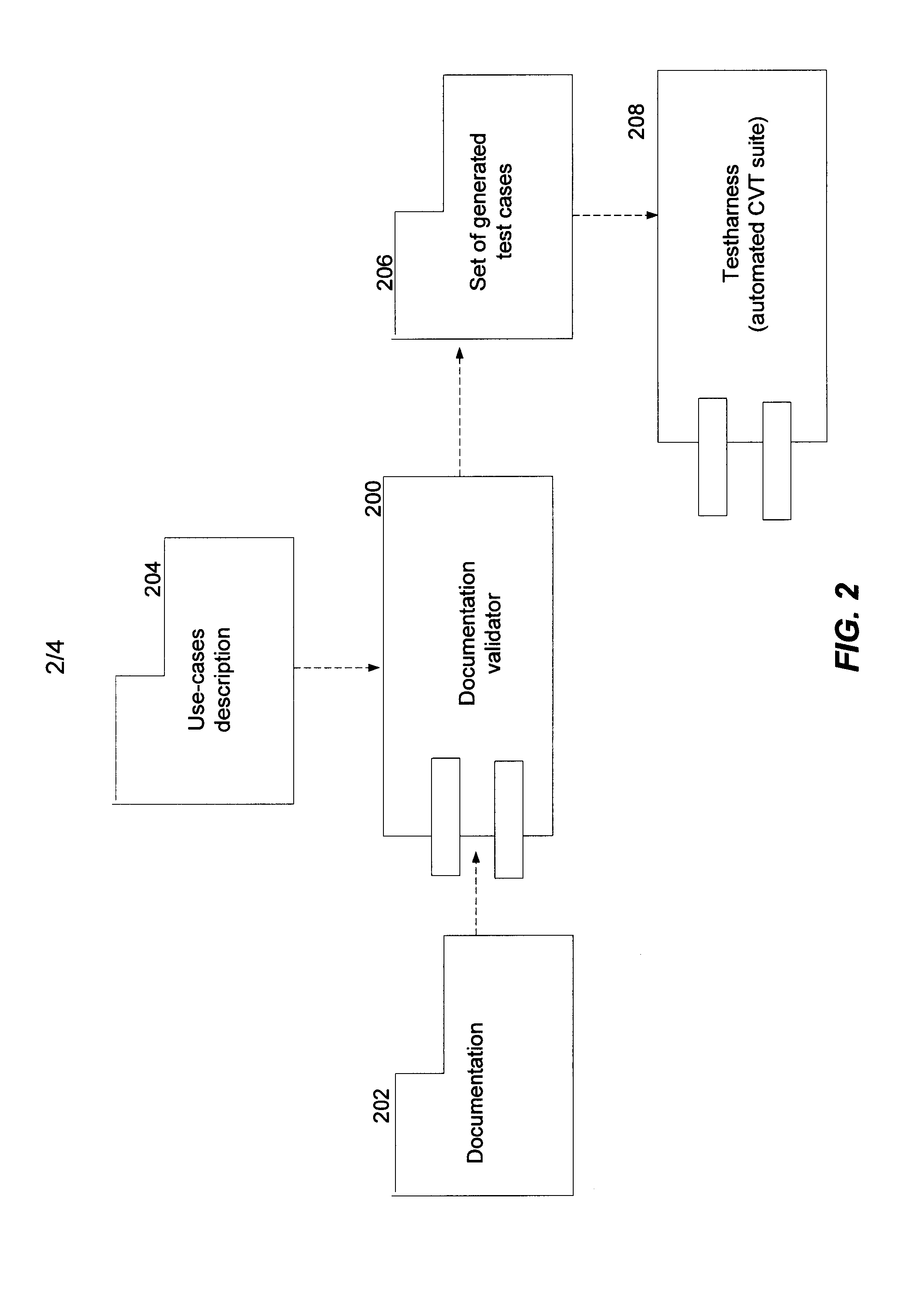
Automatic Tests of Product Documentation
InactiveUS20090288072A1Error detection/correctionSpecific program execution arrangementsComputer architectureDocumentation procedure
A computer implemented method of software product documentation review involves importing a description of a structure of the product documentation for use in determining locations in the product documentation from which to extract code and / or command portions of the product documentation for testing and providing pre-defined test case stub files for the product documentation into which are inserted extracted portions of the product documentation for testing. The test case stub files are run with the code and / or command portions inserted to determine whether or not they are runnable which is indicative of whether or not an error is present in the documentation.
Owner:IBM CORP
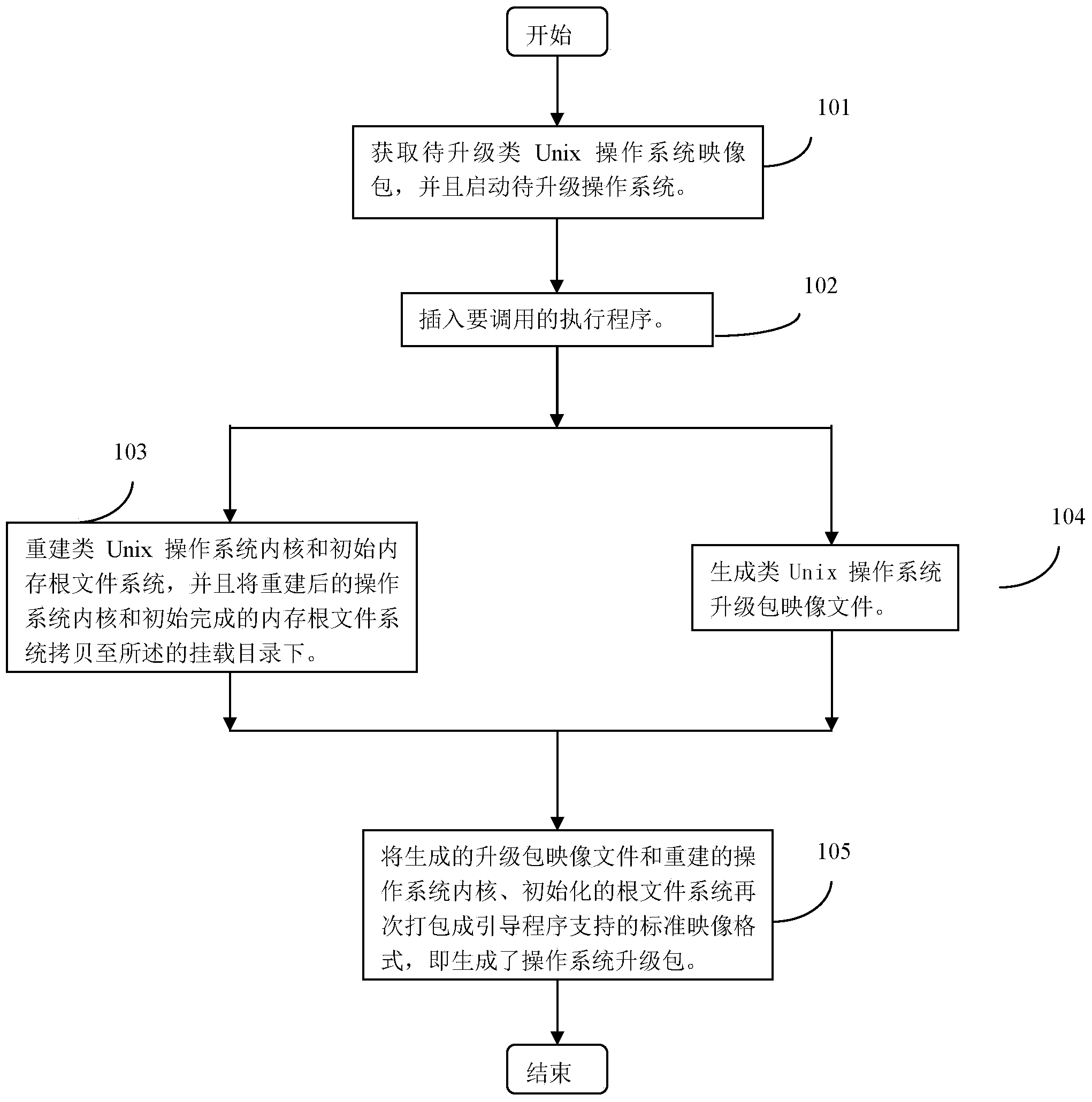
Method and device for manufacturing Unix-like operating system upgrade patch
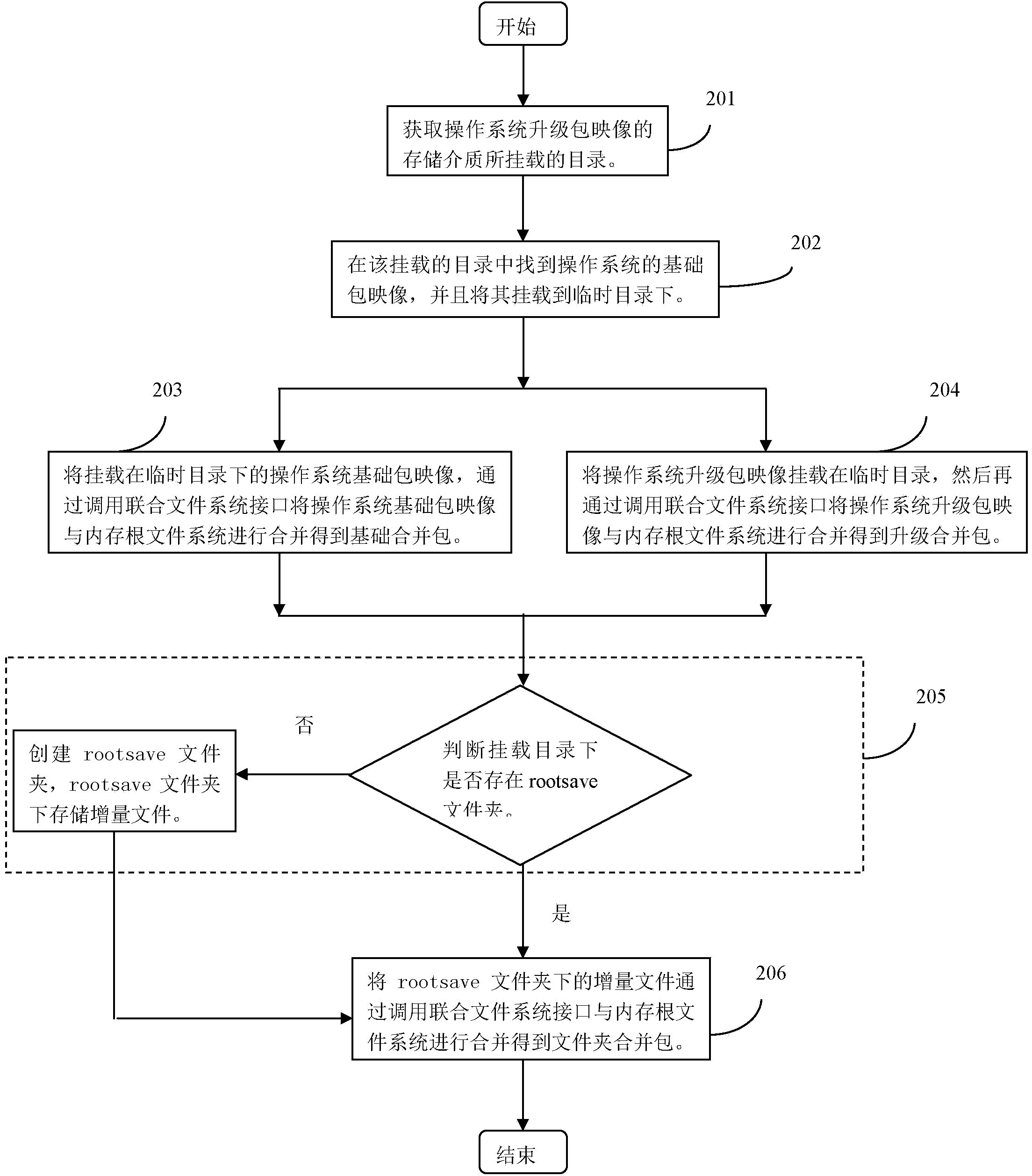
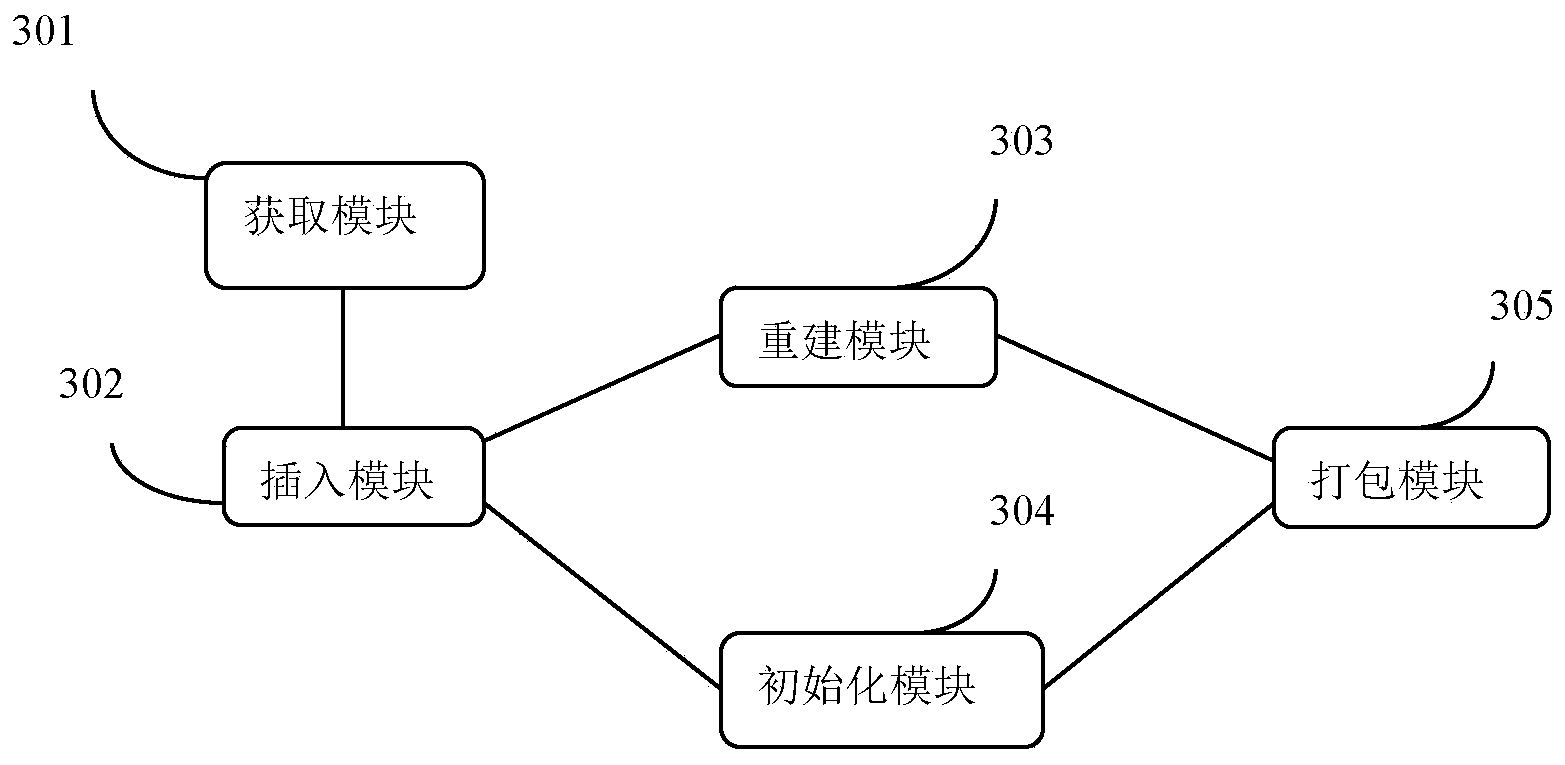
ActiveCN103777953AImprove upgrade experienceSpecific program execution arrangementsOperational systemFile system
The invention discloses a method and a device for manufacturing a Unix-like operating system upgrade patch. The method comprises the following steps of obtaining a Unix-like operating system mapping patch to be updated, and starting an operating system to be updated; rebuilding a Unix-like operating system core, initializing a memory root file system, and copying the rebuilt operating system core and the initialized memory root file system to a mounting catalogue; generating a Unix-like operating system upgrade patch mapping file; packaging the generated upgrade patch mapping file, the rebuilt operating system core and the initialized root file system once more to generate a standard mapping format which guides program support, namely generating the operation system update patch. The manufacturing process of the operating system upgrade patch is greatly simplified, and the adaptability and the flexibility of the operation system are improved.
Owner:BEIJING GUODIANTONG NETWORK TECH CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com