Patents
Literature
579 results about "Linux kernel" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
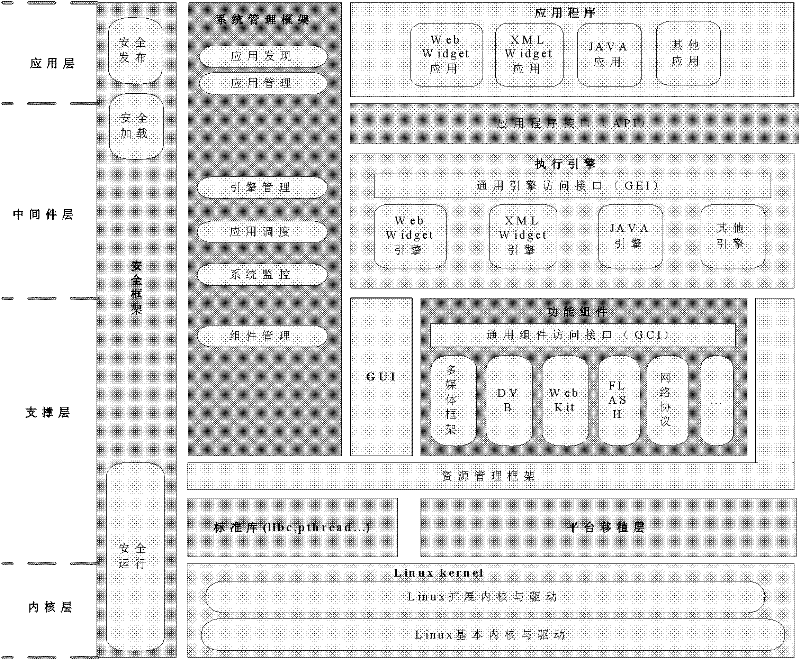
The Linux kernel is a free and open-source, monolithic, Unix-like operating system kernel. The Linux family of operating systems is based on this kernel and deployed on both traditional computer systems such as personal computers and servers, usually in the form of Linux distributions, and on various embedded devices such as routers, wireless access points, PBXes, set-top boxes, FTA receivers, smart TVs, PVRs, and NAS appliances. While the adoption of the Linux kernel in desktop computer operating system is low, Linux-based operating systems dominate nearly every other segment of computing, from mobile devices to mainframes. Since November 2017, all of the world's 500 most powerful supercomputers run Linux. The Android operating system for tablet computers, smartphones, and smartwatches also uses the Linux kernel.
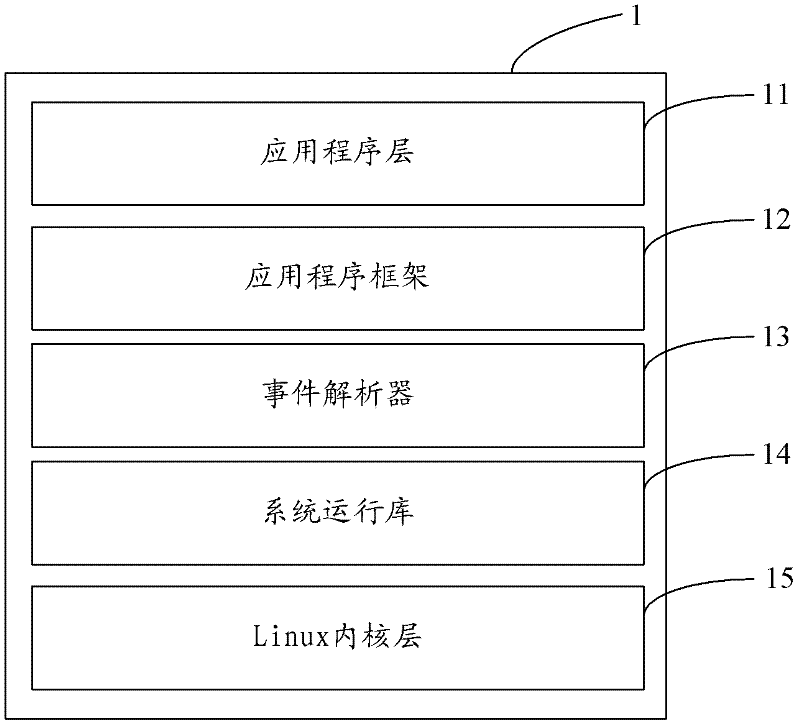
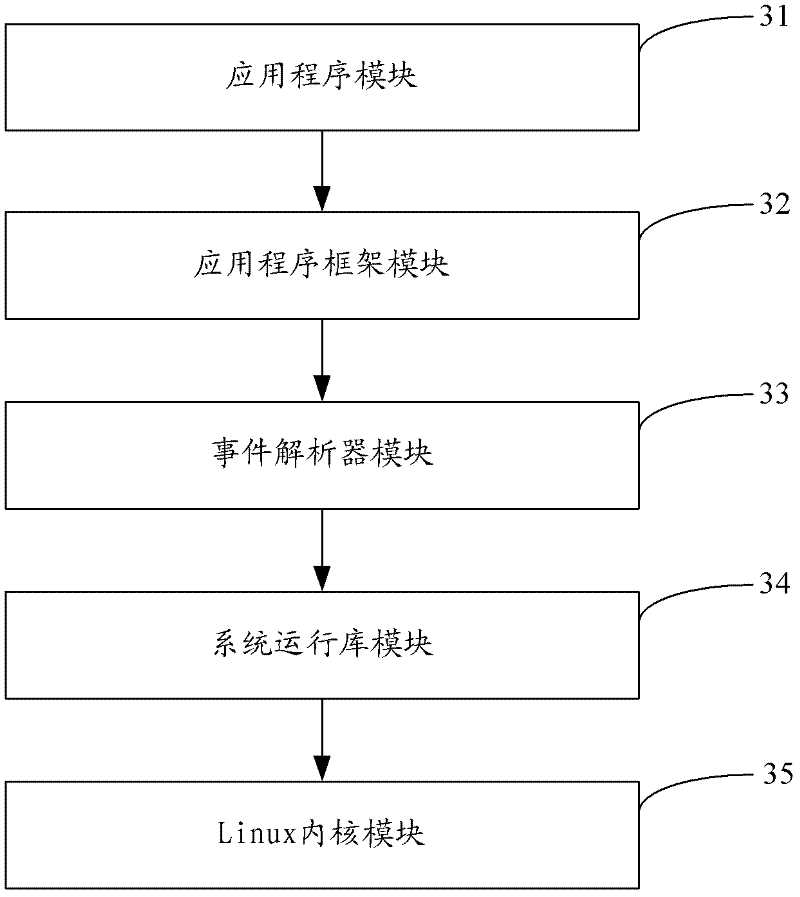
Android system development framework and development device
ActiveCN102314348AReduce couplingSolve the problems of low development efficiency and poor portabilitySpecific program execution arrangementsCouplingInteraction interface
The invention is applicable to the technical field of computers, and provides an Android system development framework and a development device; the Android system development framework comprises an application program level, an application program framework, a system runtime library and a Linux inner core level, and is characterized in that: the Android system development framework also comprises an event analyzer; and the event analyzer is used for standardizing interaction information which is received from an interaction interface. By adding the event analyzer for standardizing the interaction information which is received from the interaction interface in the existing Android system development framework, the embodiment of the invention solves the problems that the existing Android system cannot provide an effective development framework so that the application program development efficiency is low and the transplantation performance is poor, improves the development efficiency and the transplantation performance of application programs, and simultaneously reduces the coupling degree of the Android system.
Owner:TCL CORPORATION
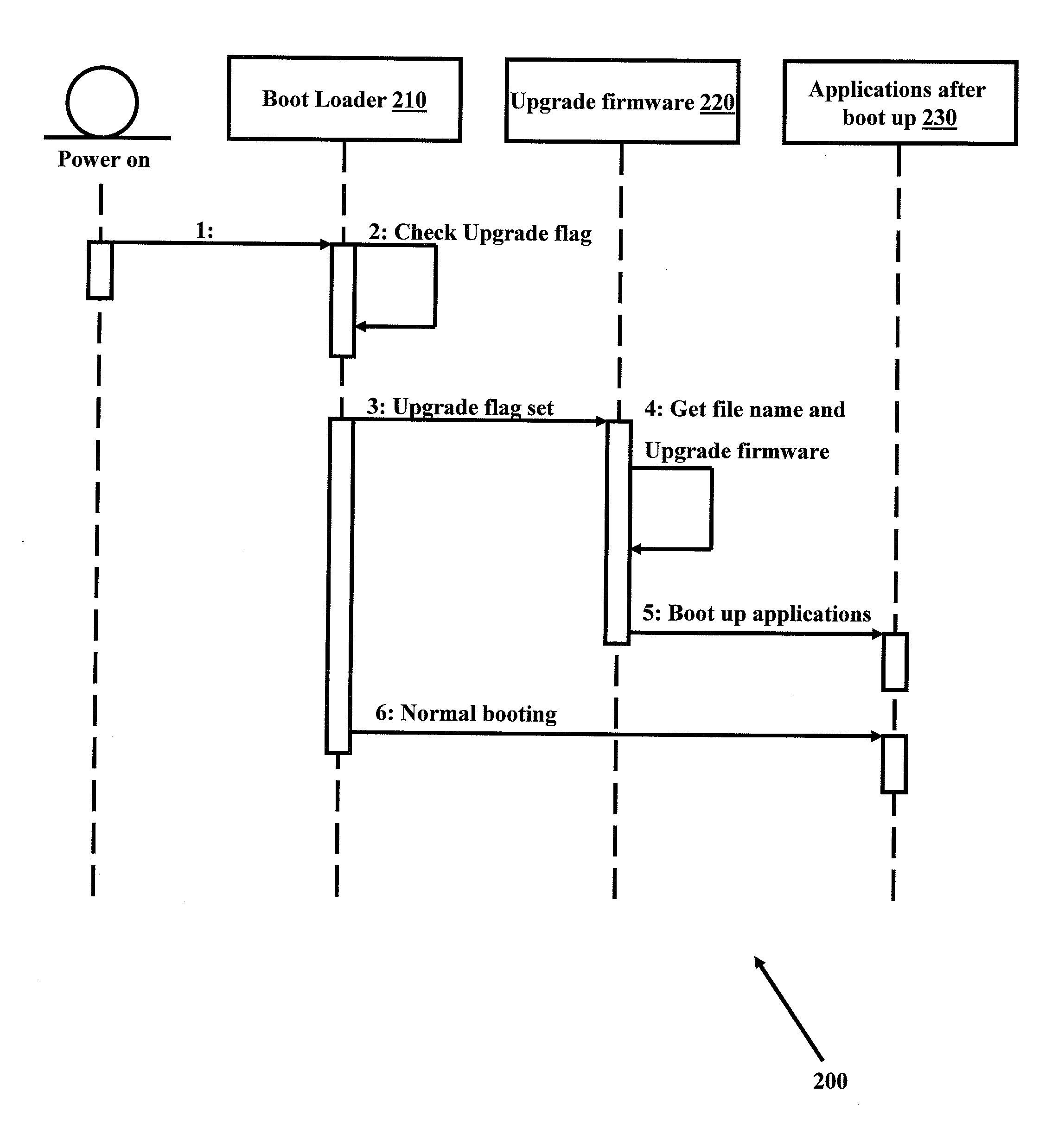
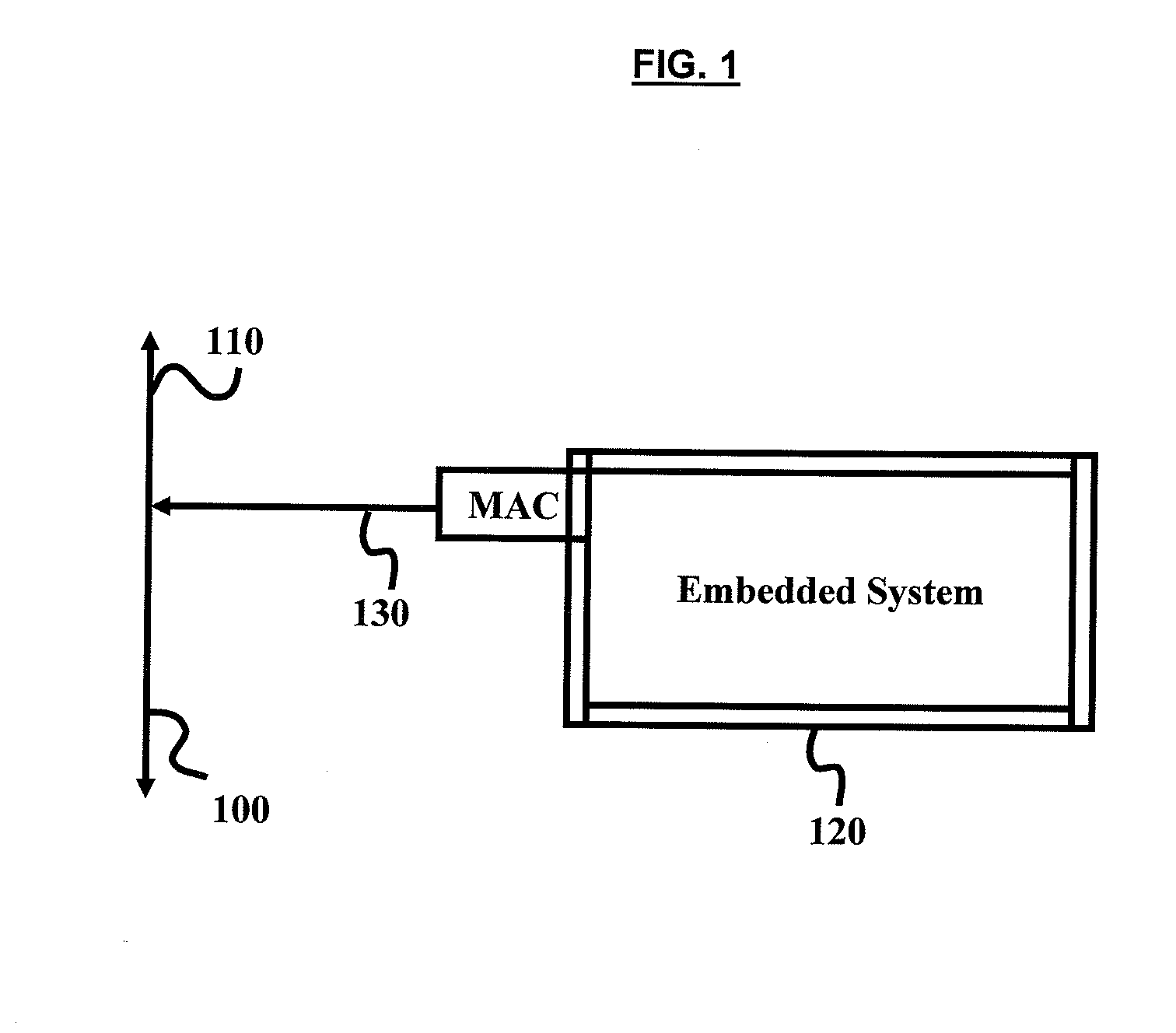
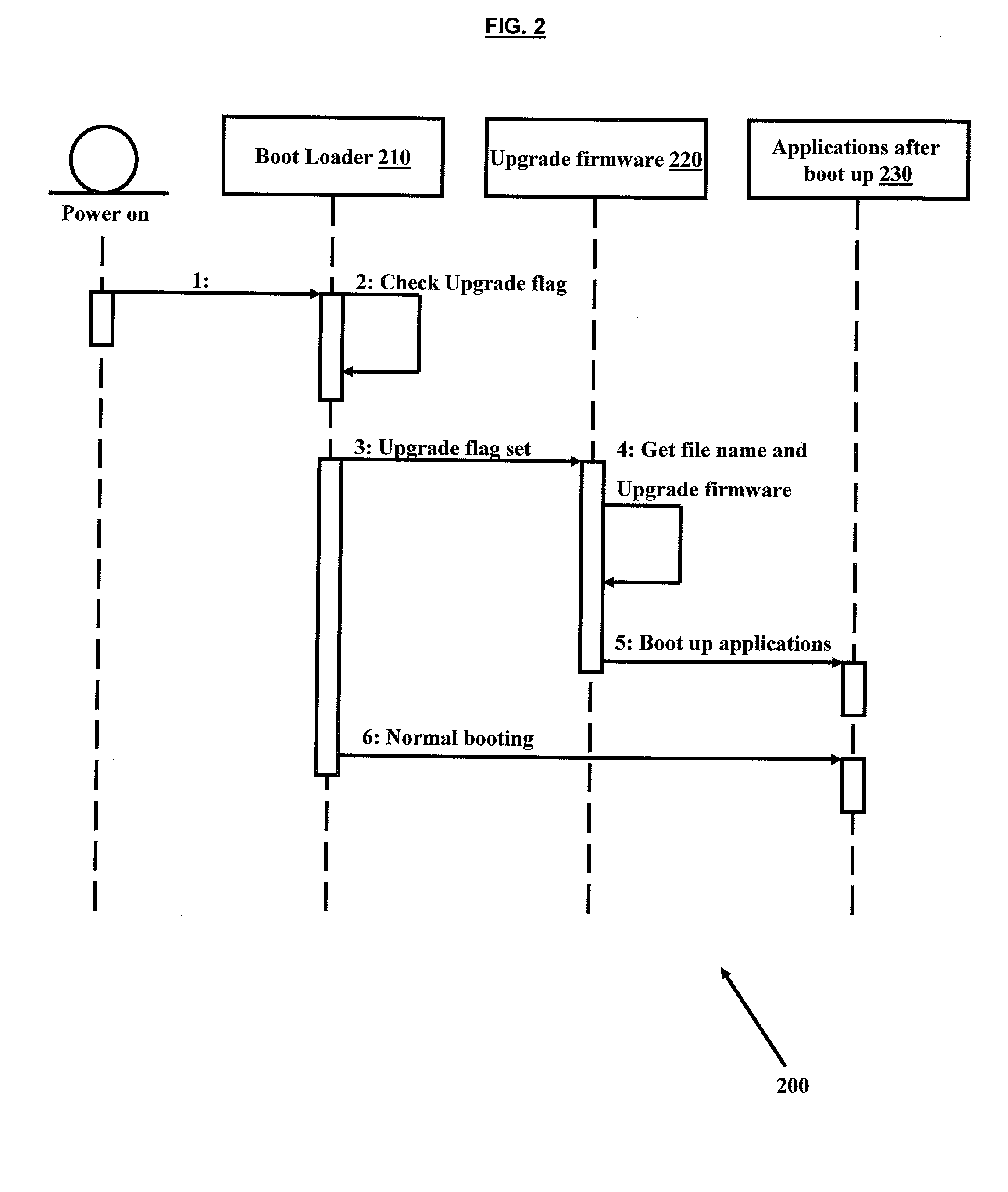
Automatic complete firmware upgrade
InactiveUS20090271780A1Memory adressing/allocation/relocationSpecific program execution arrangementsFile systemSingle image
A method for automatic firmware upgrade on a target embedded system connected to a TFTP server and a web console is disclosed. The method includes generating a single image from Linux kernel image and file system image and providing single image name as input to web console for firmware upgrade. The web console write upgrade flag and single image name in the kernel configuration and issue a restart command to the embedded system. At boot up time, the start up module checks for firmware upgrade flag set and issue commands for loading the image on target board and boots up with the upgraded image. The firmware upgrade is performed over the network. Further, the embedded system is upgraded with very less user interaction reducing firmware upgrade time and by reducing dependence of experienced / skilled person.
Owner:MOSCHIP SEMINCONDUCTOR TECH
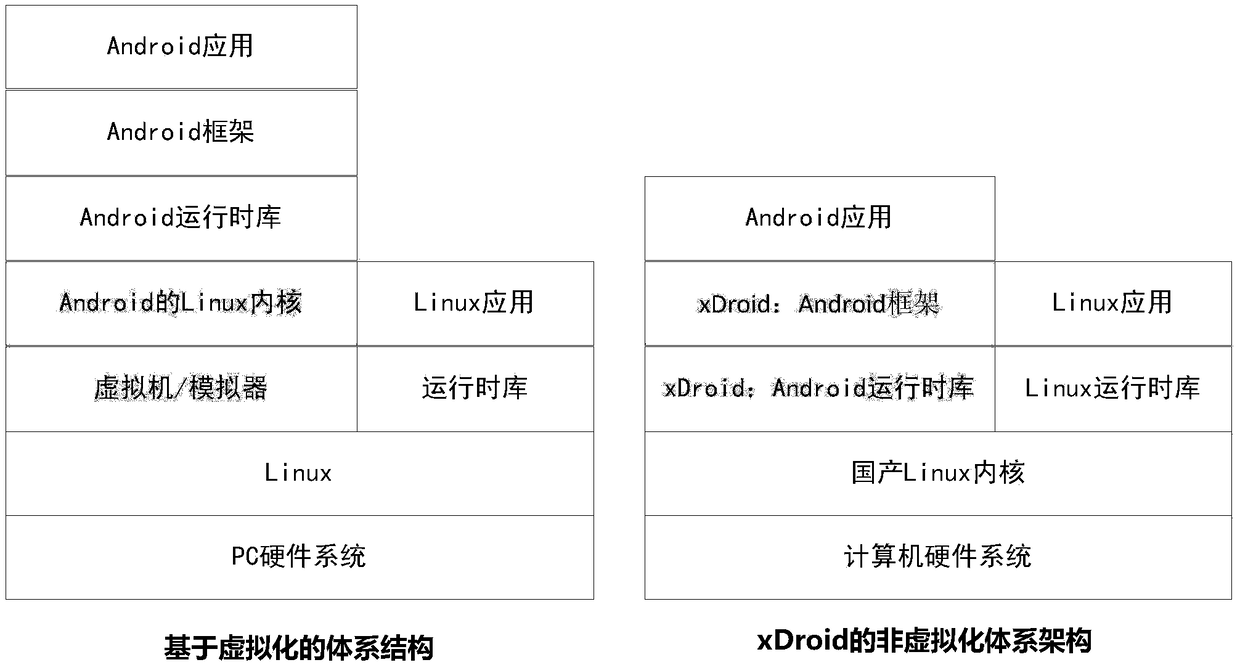
Android running environment realization method based on non-virtualized system architecture
The invention belongs to the field of computer basic software and relates to an Android running environment realization method based on a non-virtualized system architecture. According to the method,an Android running environment is constructed on an existing Linux kernel and recorded as xDroid, and an Android application framework and an Android running time library are migrated to a standard Linux kernel. The xDroid does not need the virtualization technology but stands from a basic library and a basic running mechanism provided by a desktop operating system kernel, an Android bottom running supporting library needed for Android application running is realized layer by layer from bottom to top, then efficient migration of the Android running time library is realized, and the Android running environment is realized on a desktop operating system platform. Compared with a virtualization-based technology, ecological complete fusion of desktop applications and Android applications is realized in a true sense through the xDroid, and the applications are high in starting speed and high in performance; and meanwhile realization is based on different platforms, so that cross-platform running is easy to realize.
Owner:北京麟卓信息科技有限公司
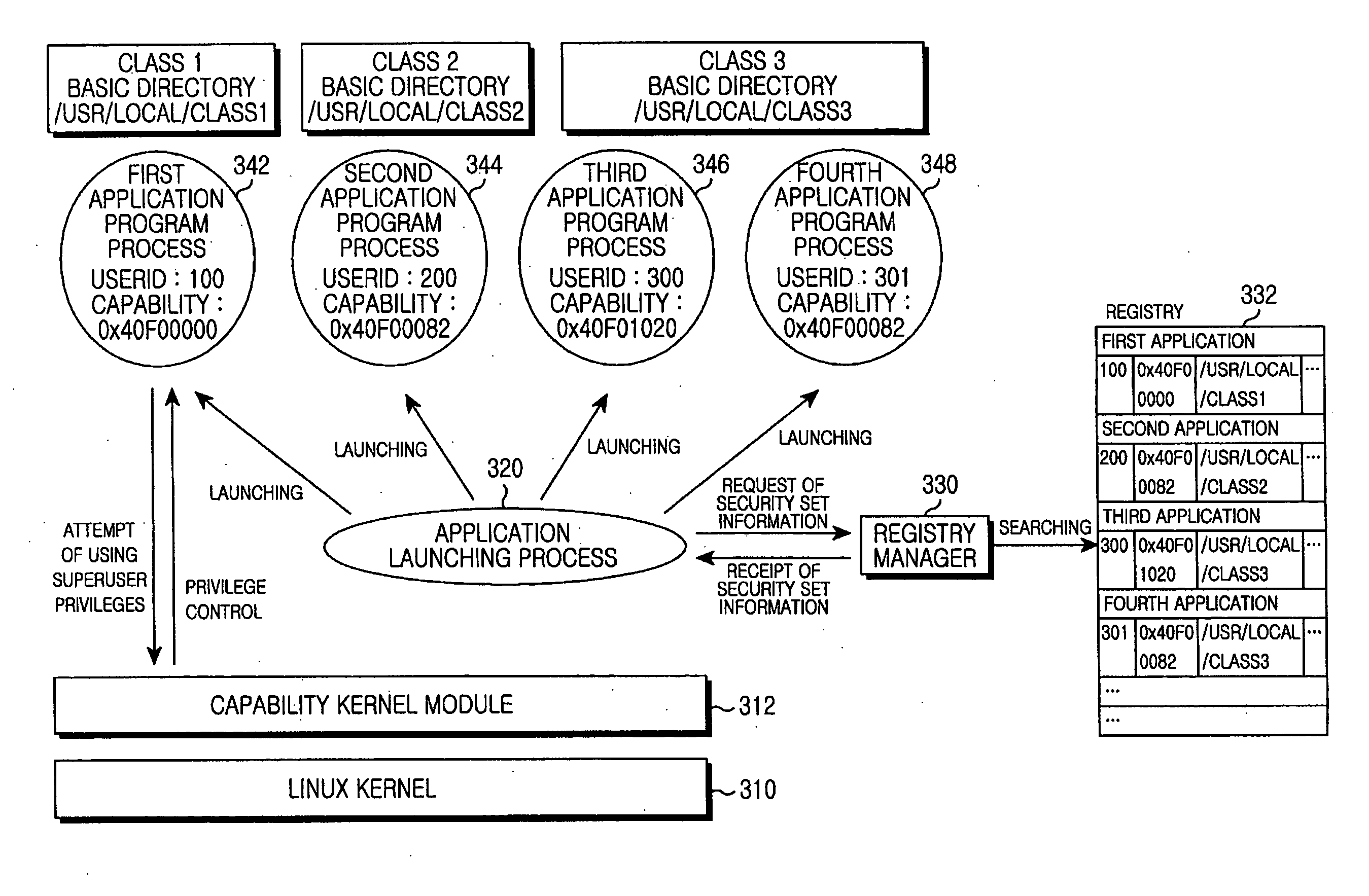
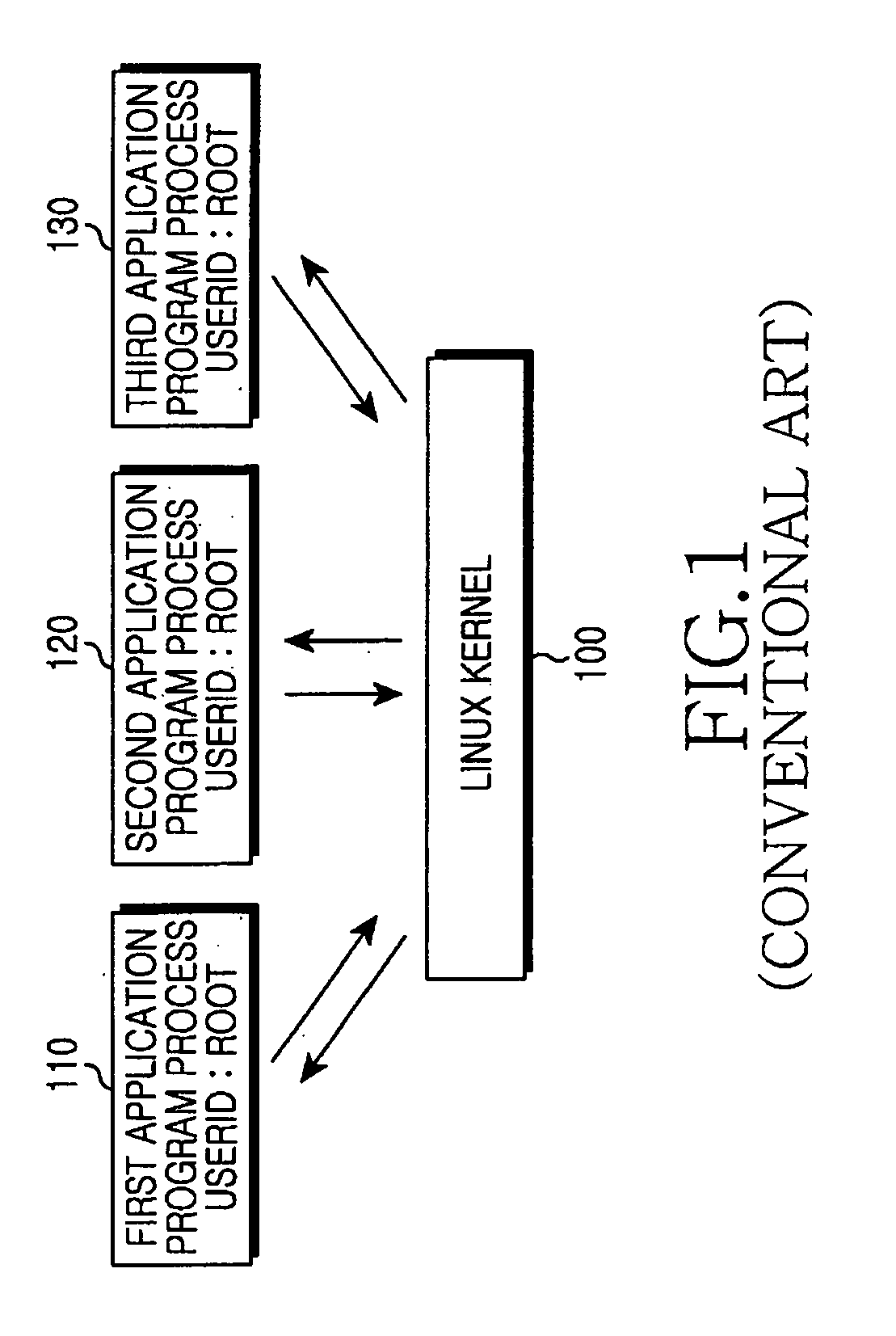
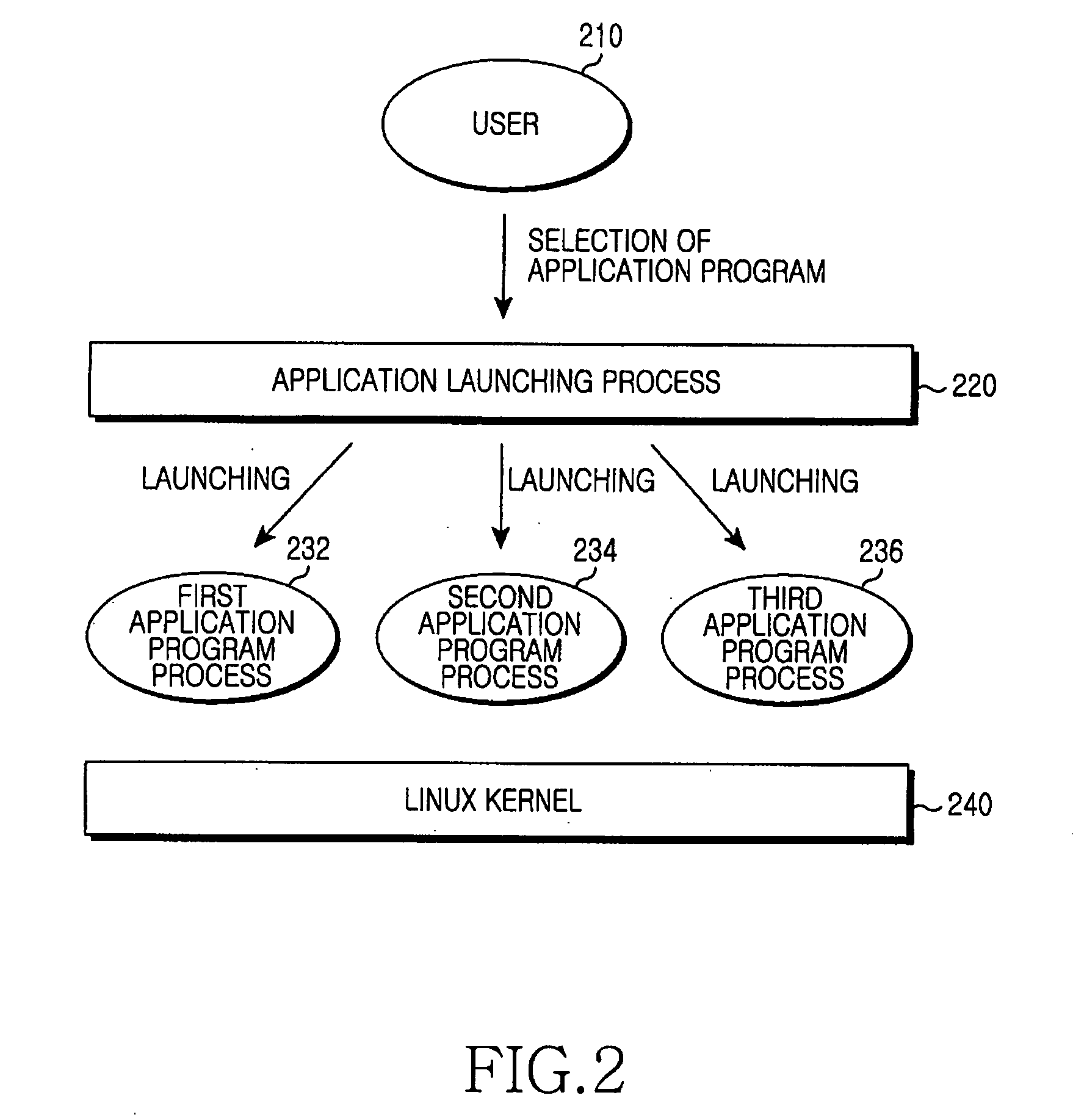
Application program launching method and system for improving security of embedded linux kernel
InactiveUS20080134325A1Digital data processing detailsDigital computer detailsComputer networkLinux kernel
Provided is an application program launching method and system for improving security of an embedded Linux kernel by distributing superuser privileges. The method includes: searching security set information on an application program selected by a user; changing a user account for a processor of the application program to a user ID associated with the application program in the security set information; setting a capability for the processor according to setting information for the capability in the security set information; changing a basic directory for the processor according to a basic directory in the security set information; and launching the application program.
Owner:SAMSUNG ELECTRONICS CO LTD +1
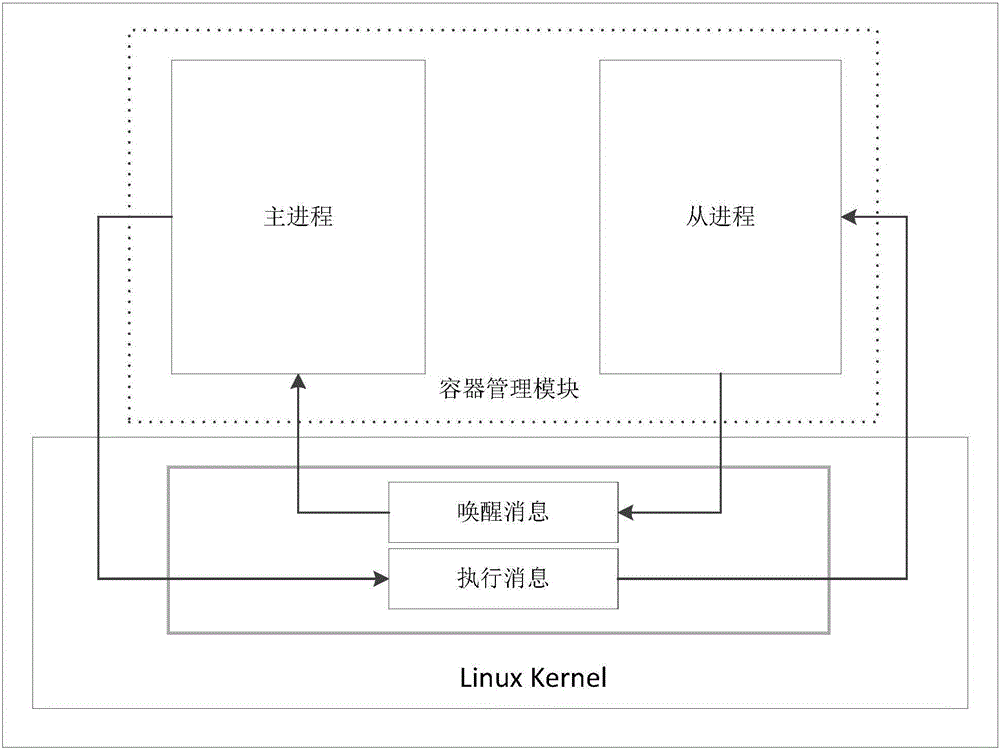
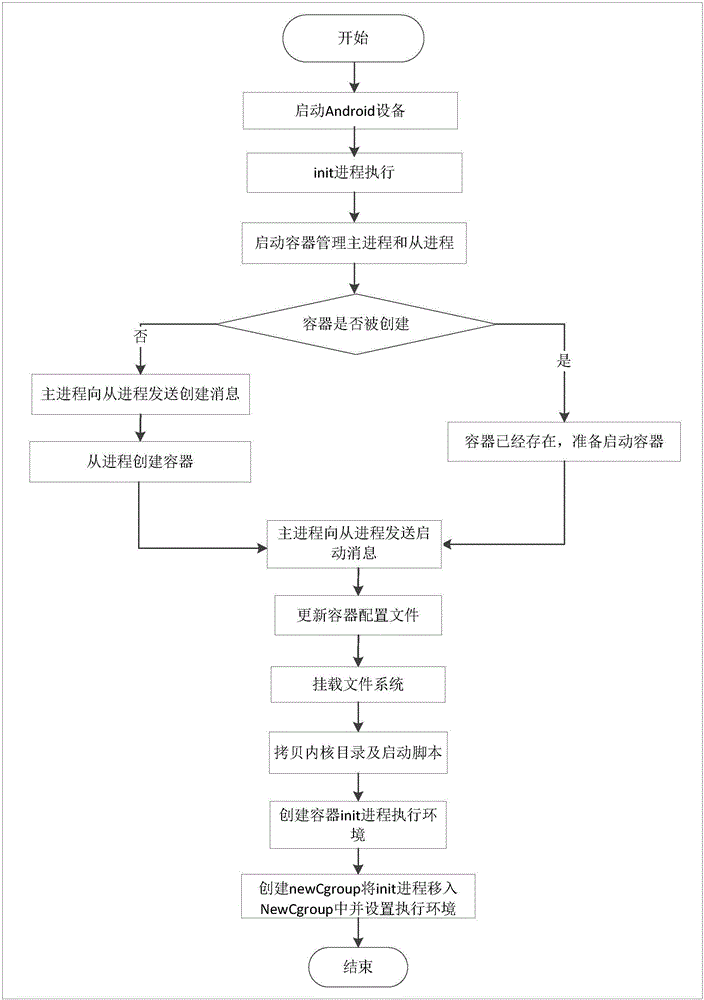
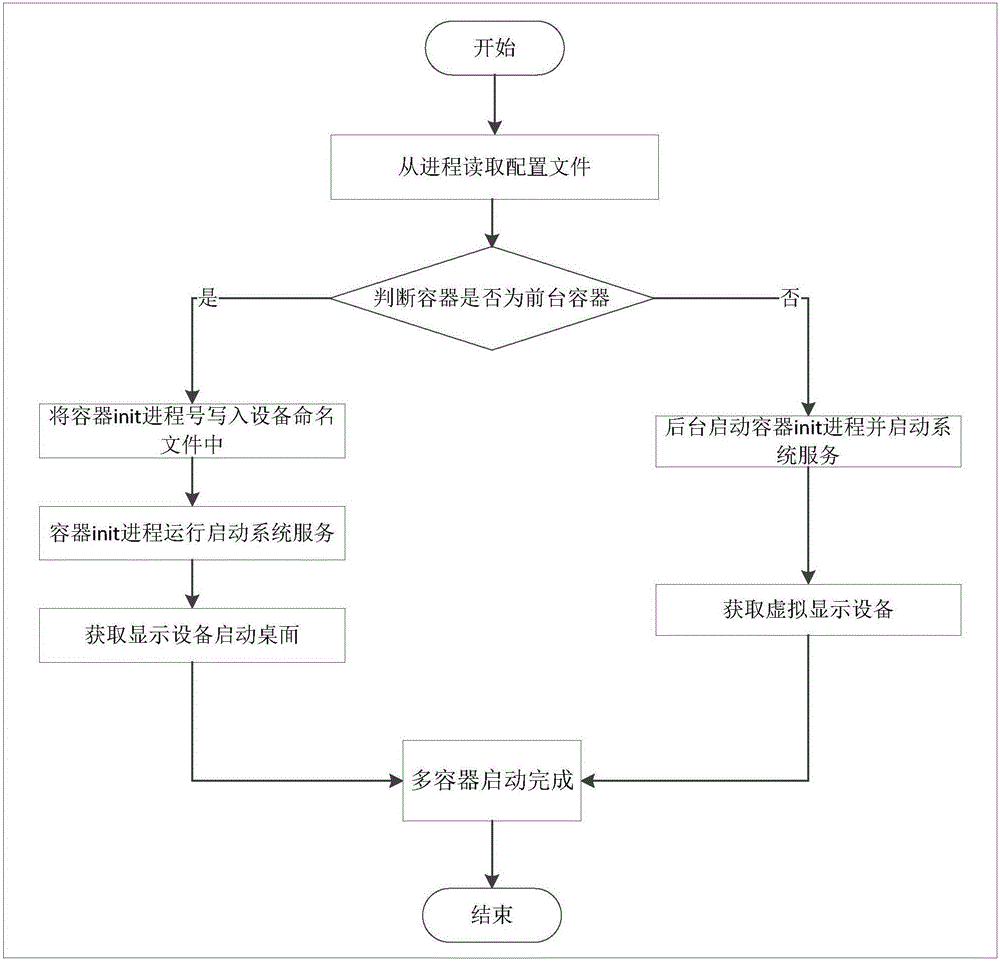
Multi-Android-system container automatic creating and starting method
The invention relates to a Linux kernel container technology and a display equipment multiplexing technology, in particular to a multi-Android-system container automatic creating and starting method of a system level container technology. Containers are automatically created in a Linux kernel, systems in the containers are started, and it is ensured that each container independently runs one Android system; communication between a container management host process and a container management auxiliary process is s achieved, on the basis, the container management host process sends creating and starting information to the container management auxiliary process, and the container management auxiliary process receives and processes the information. According to the multi-Android-system container automatic creating and starting method, the containers are automatically created and started in the Linux kernel; equipment is started again, and a container management module starts the containers according to the containers created in the system.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
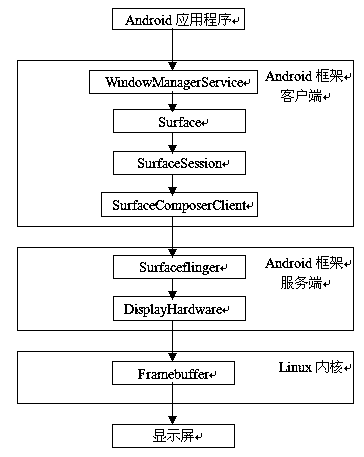
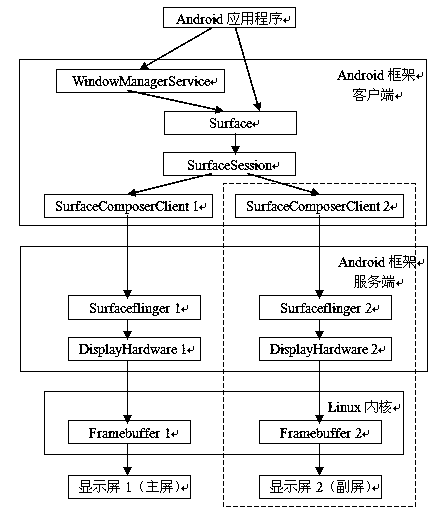
Android double-screen extraordinary image display method
InactiveCN104123110AMake full use of Android's powerful display output functionPowerful display output functionDigital output to display deviceComputer hardwareImage resolution
The invention provides a method for achieving a double-screen extraordinary image displaying function on an Android platform. The method comprises the steps of adopting two display screens on the Android platform, wherein one display screen is a main screen, the other display screen is an auxiliary screen, and the main screen and the auxiliary screen are independent physically and can have different resolution ratios and sizes and be provided with different data transmission interfaces; establishing two frame buffer drives in a Linux kernel; establishing two DisplayHardware objects on the server-side of an Android frame display system and starting two display screens; establishing service of two Surfaceflinger on the server-side of the Android frame display system, wherein each Surfaceflinger represents one screen and is used for invoking of an Android client-side; establishing two SurfaceComposerClient objects on the client-side of the Android frame display system, wherein each SurfaceComposerClient object is connected with one corresponding Surfaceflinger; making Android application program to be capable of displaying different contents on two display screens; configuring standard Android application program interferences for the Android application program so as to output display elements on two display screens, wherein the standard Android application program interferences are seamlessly compatible with native Android application program development interfaces.
Owner:SHANGHAI DONGQIAN TECH DEV
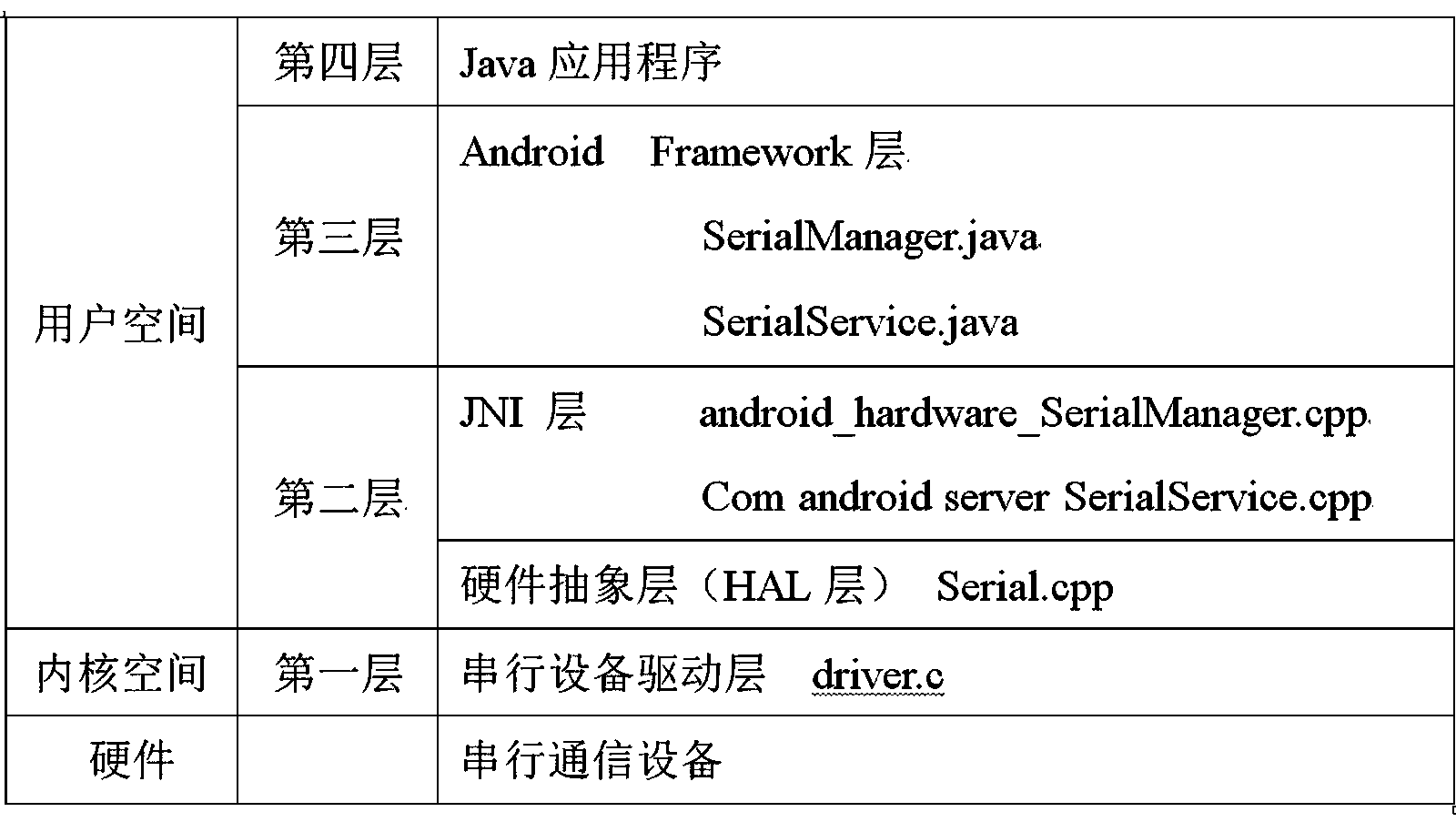
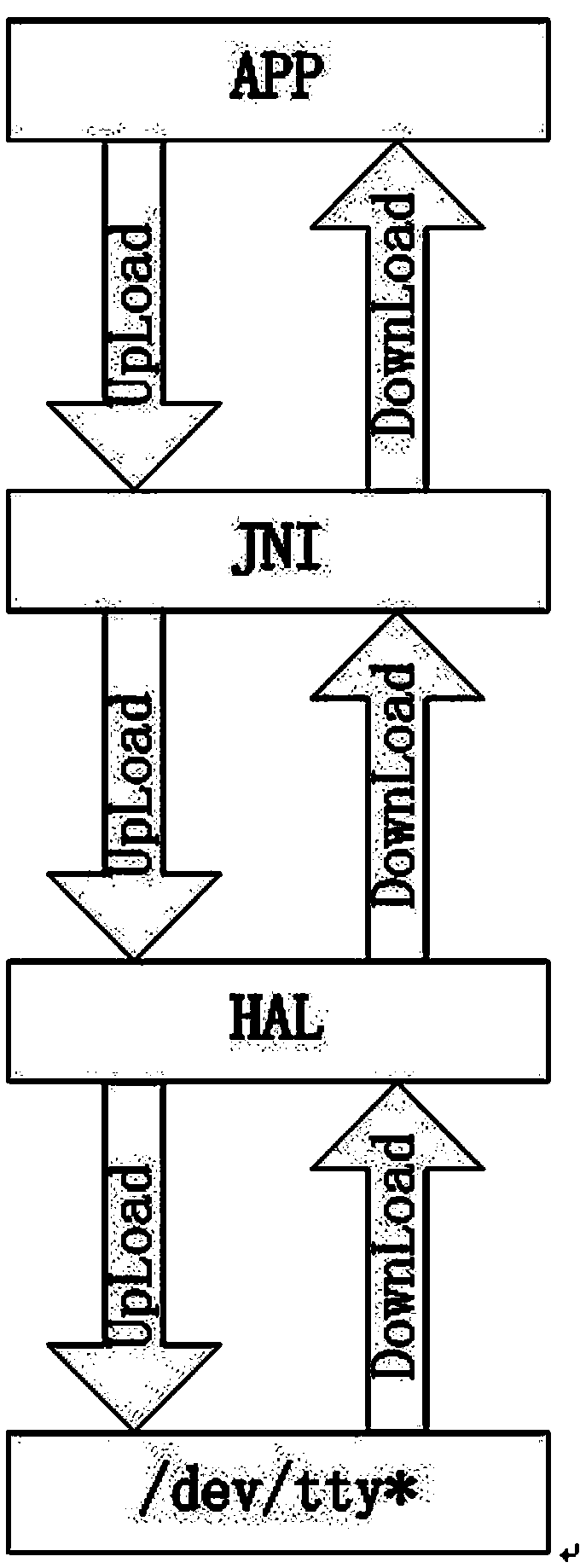
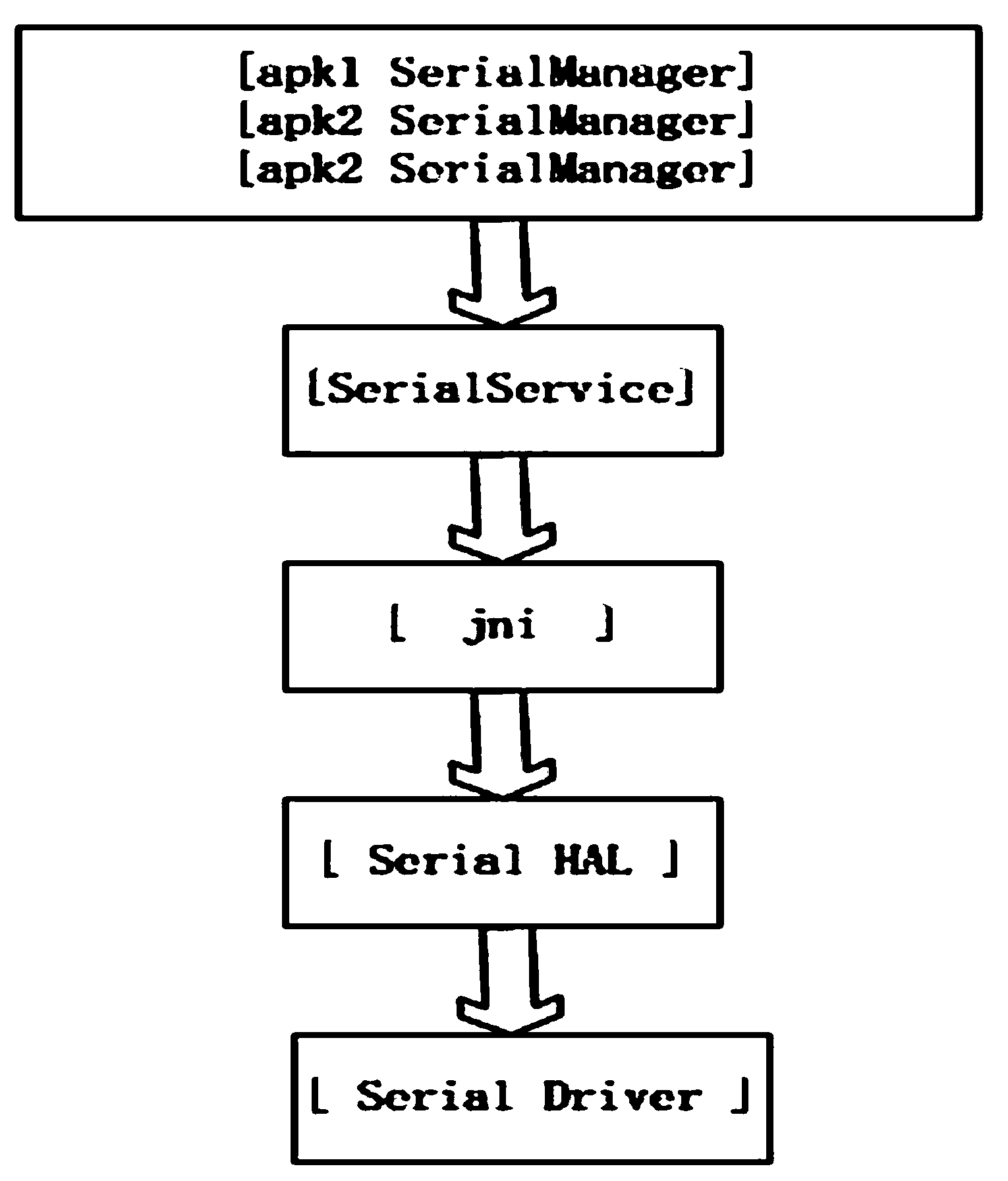
Universal serial device communication module based on Android system
InactiveCN103353839AApplied to the convenience of calling devices with serial portsEasy to callSpecific program execution arrangementsLinux kernelApplication software
The invention provides a universal serial device communication module based on an Android system, which can realize calling to various serial devices under the Android system, and provides a solution for mutual exclusion produced when various (APK) application processes access to the same serial device at the same time. The universal serial device communication module is in operation on a Linux kernel and under an Android frame, and comprises a serial device drive layer, a hardware abstraction layer, a Framework layer and a JNI (Java Native Interface) layer. The universal serial device communication module provides convenience for the Android system to be applied in industries needing to call the serial devices.
Owner:杭州竞航科技股份有限公司
Safe embedded operating system capable of supporting multi-stage loading
ActiveCN102479097AAchieve isolationRealize dynamic loading and runningProgram loading/initiatingProgram/content distribution protectionEnd to end securityGraphical user interface
The invention provides a safe embedded operating system capable of supporting multi-stage loading. The safe embedded operating system supports the dynamic loading operation of an application program of an embedded terminal, realizes the isolation of the application program and an embedded terminal platform and comprises a system management module, a safety management module, a resource management module, a functional unit module, a GUI (Graphical User Interface) module, an application execution engine module, an application program interface (API) module and the like. Meanwhile, the safe embedded operating system is at least divided into a basic stage and an expansion stage by adopting stage treatment on the basis of the traditional Linux inner core, a basic stage module is fixedly loaded, each module and each functional module in the expansion stage are selectively and dynamically loaded according to application requirements under the scheduling of a system management framework, and thus, loading the system by stage is realized. By using the safe embedded operating system, a function of safety management and control for the application program through a safe framework module is achieved, mechanisms such as end-to-end safe issuing and loading of an application, safe operation protection based on an application process isolation and trust mechanism, application operation monitoring and the like are applied, and safe management and control on the whole life cycle of the application from issuing, downloading, loading to operating is realized.
Owner:ZHENGZHOU SEANET TECH CO LTD
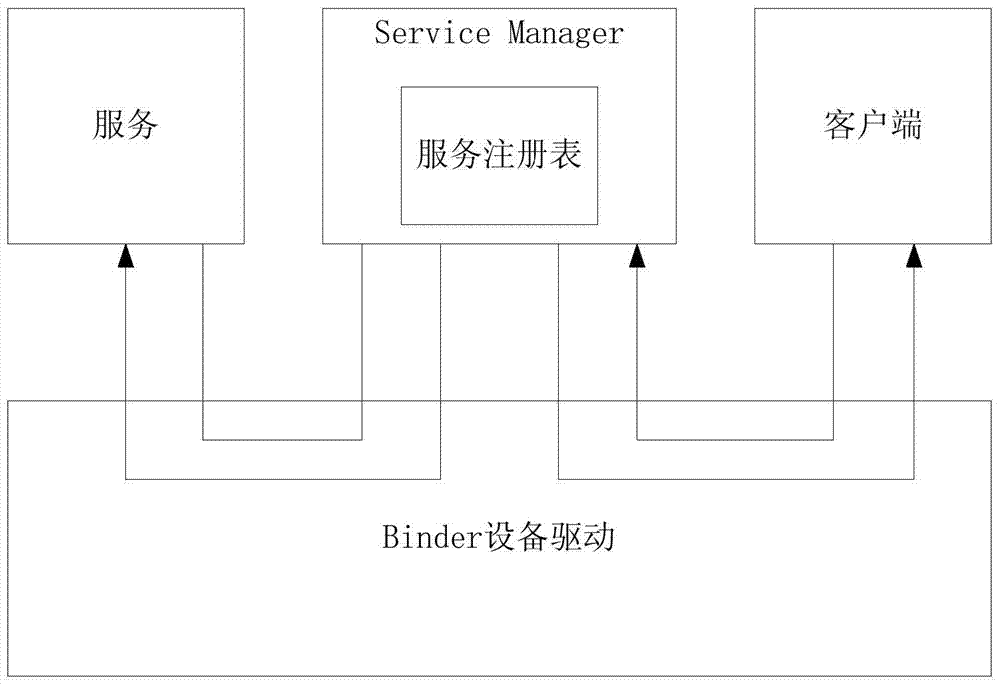
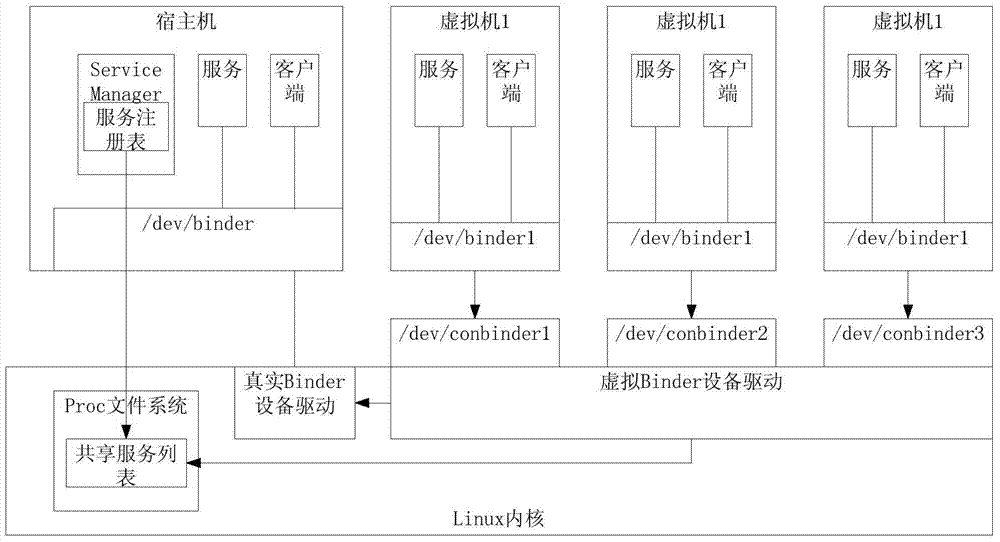
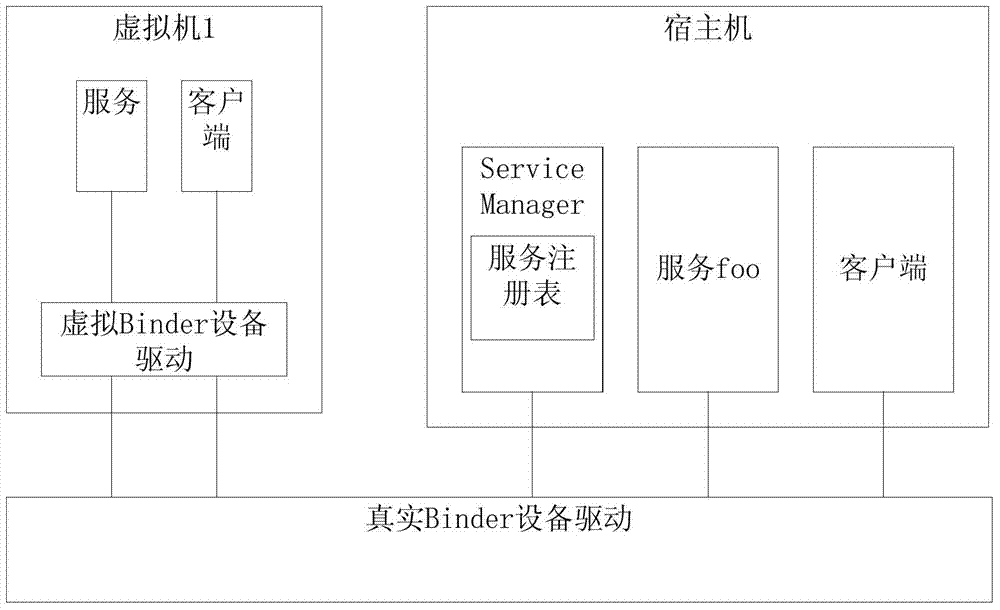
Method for multiplexing Binder IPC mechanism by multiple Android systems in mobile virtualization scene
ActiveCN103593225ASolve the problem of service name conflictIncrease flexibilitySoftware simulation/interpretation/emulationVirtualizationFile allocation
The invention discloses a method for multiplexing a Binder IPC mechanism by multiple Android systems in a mobile virtualization scene. The method comprises the steps that a virtual Binder device drive is set up in the Android systems of a host machine, the virtual Binder device drive is used for logging in multiple virtual Binder devices to a Linux inner core, and device files corresponding to the virtual Binder devices are distributed into virtual machines; when the virtual machines send out access requests of the Binder devices, firstly the virtual Binder device drive is called, and then use requests are forwarded to a real Binder device drive through the virtual Binder device drive; in the process of forwarding the operation to the real Binder device drive, the virtual Binder device drive conducts corresponding interception, filter and modification on conflicting service names. On the premise that operation of the multiple Android systems is achieved, the high efficiency of the system performance is ensured.
Owner:ZHEJIANG UNIV
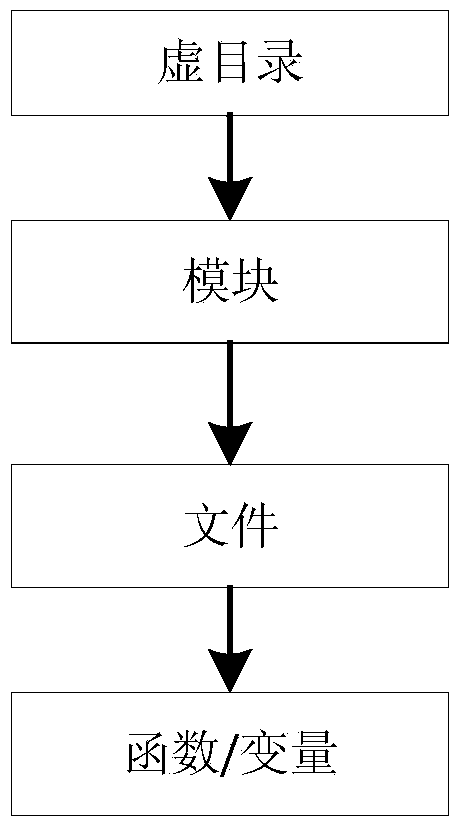
Linux kernel module relation extracting method based on compiling options
InactiveCN103699389AEasy to useClear accessSpecific program execution arrangementsSource code fileComputer module
The invention discloses a Linux kernel module relation extracting method based on compiling options. The method includes the steps of 1), dividing kernel source codes according to the functions and logic relations of the same to form virtual directories; 2), performing syntactic analysis on each Kconfig file under Linux real directories to identify all the compiling options; analyzing the source code file required by each compiling option from the compiling file under the same directory; 3), according to the virtual directories, using the source code files as intermediary agents, dividing the compiling options into corresponding virtual directories; 4), performing regular analysis on each source code file to obtain the function and variable defined in the source code file; 5), analyzing the specific realizing source code of each function and variable to extract the calling relations among functions and variables; 6), constructing a kernel framework according to the relations. The method has the advantages the method does not rely on one kernel version, and the relations among kernel modules can be obtained clearly.
Owner:PEKING UNIV
Dynamic stubbing technology based time-delay analysis method for data packet processing
InactiveCN102346710AControl overheadReduce overheadDigital computer detailsSoftware testing/debuggingTime delaysLinux kernel
The invention discloses a dynamic stubbing technology based time-delay analysis method for data packet processing. The method comprises the following five main steps of: 1, collecting a kernel symbol table and acquiring a function list capable of being stubbed; 2, determining a function list to be stubbed; 3, configuring a stubbing module, inserting a section of codes into each function to be stubbed, and adding function addresses and time stamps for function calling to a current data packet under processing; 4, starting a packet sending and receiving module; and 5, counting and analyzing the data packets stored in the step 4 to obtain the time consumed by each function of a kernel. The method disclosed by the invention has the advantages of less expense and very strong instantaneity and adaptability, can be used for elaborately analyzing the expense brought by each function and time delay for the data packets to wait in a queue in a process of treating the data packets by the Linux kernel, can provide a powerful basis for network analysis and optimization, and has a better practical value and a wide application prospect in the technical field of computers.
Owner:BEIHANG UNIV
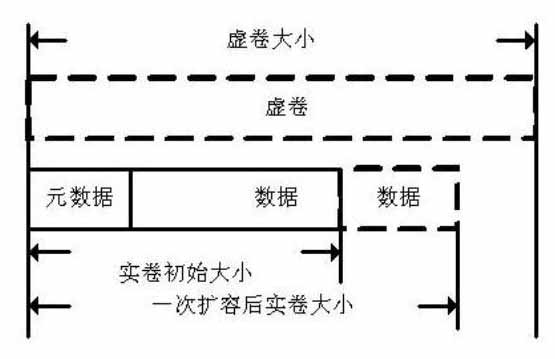
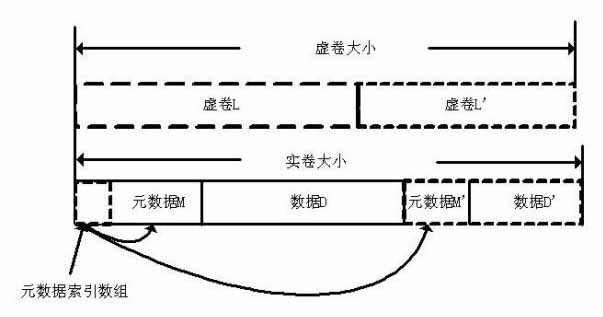
Method for creating allocation-on-demand incremental volume
InactiveCN102073464AImprove space utilizationEasy to acceptInput/output to record carriersShardPhysical space
The invention belongs to the technical field of network storage, and discloses a method for creating an allocation-on-demand incremental volume. The volume has a two-layer volume structure, and realizes separation of a physical space and a logical space. The creating method comprises that: a user state interface participates in a new parameter (N) in a user state command lvcreate of a logical volume manger (LVM). The real volume of the bottom layer is a common logical volume, and the virtual volume of the upper layer is a data structure in a Linux kernel. The physical space of the real volume is allocated according to the actual requirement, so the utilization rate of a disk space is improved. Real-time monitoring of the physical space of the real volume and automatic capacity expansion of the actual space effectively avoid overflow of the spaces. A user can randomly designate capacity expansion increment magnitude as required to perform capacity expansion of the virtual volume. The volume processes the write request by adopting a mode of additional write. Moreover, the volume processes garbage fragments by adopting a quick and effective garbage reclamation algorithm.
Owner:NANKAI UNIV
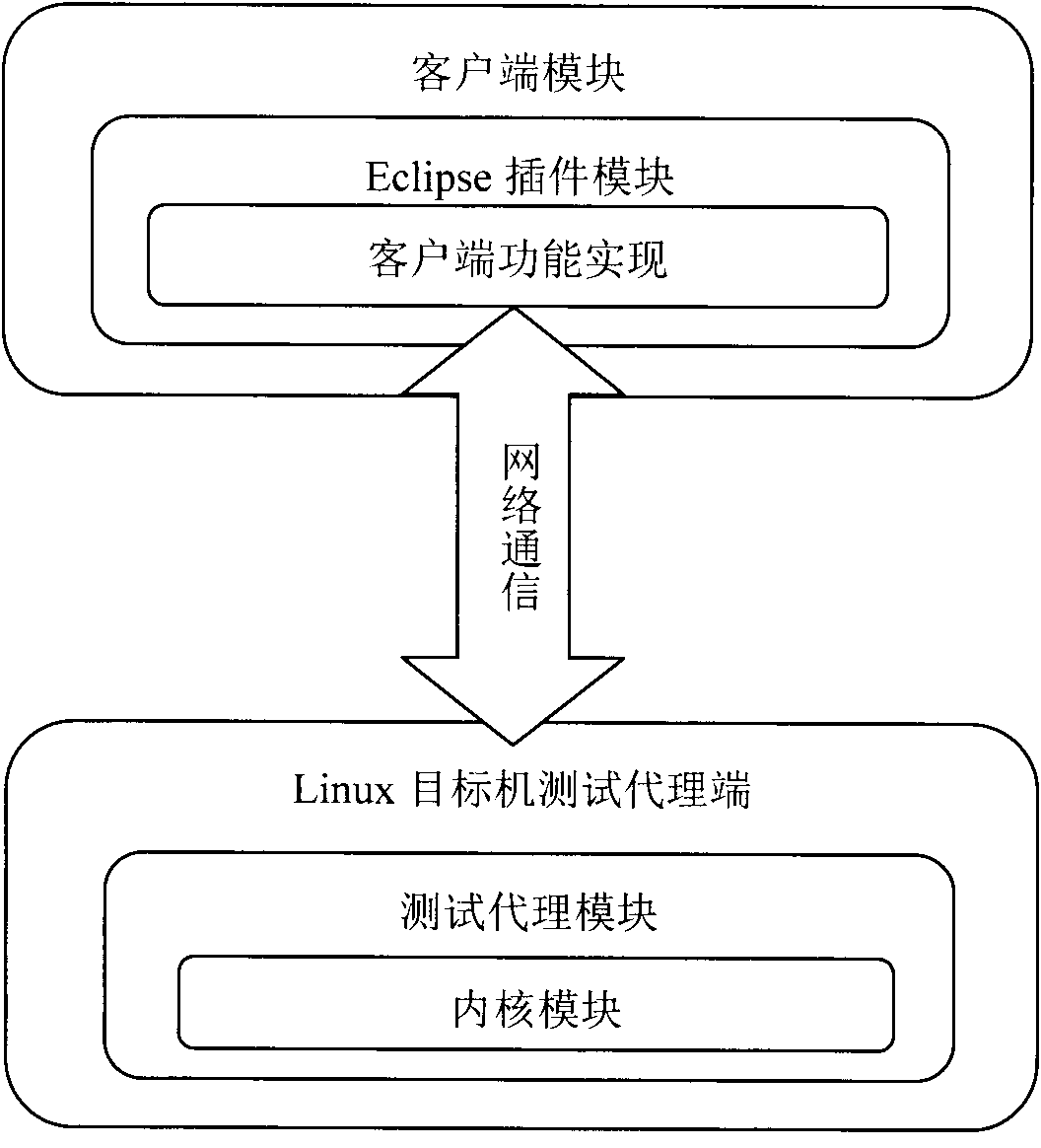
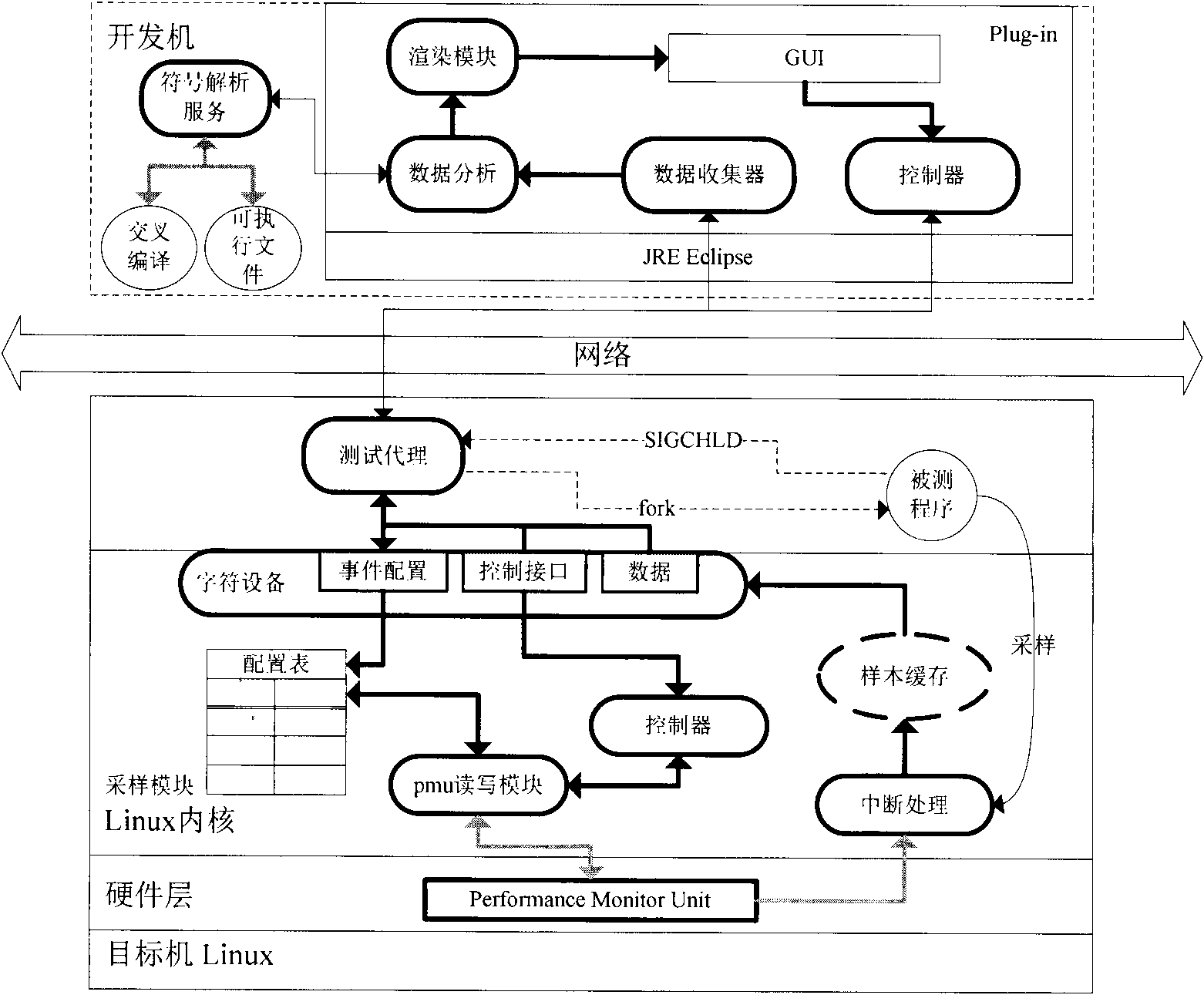
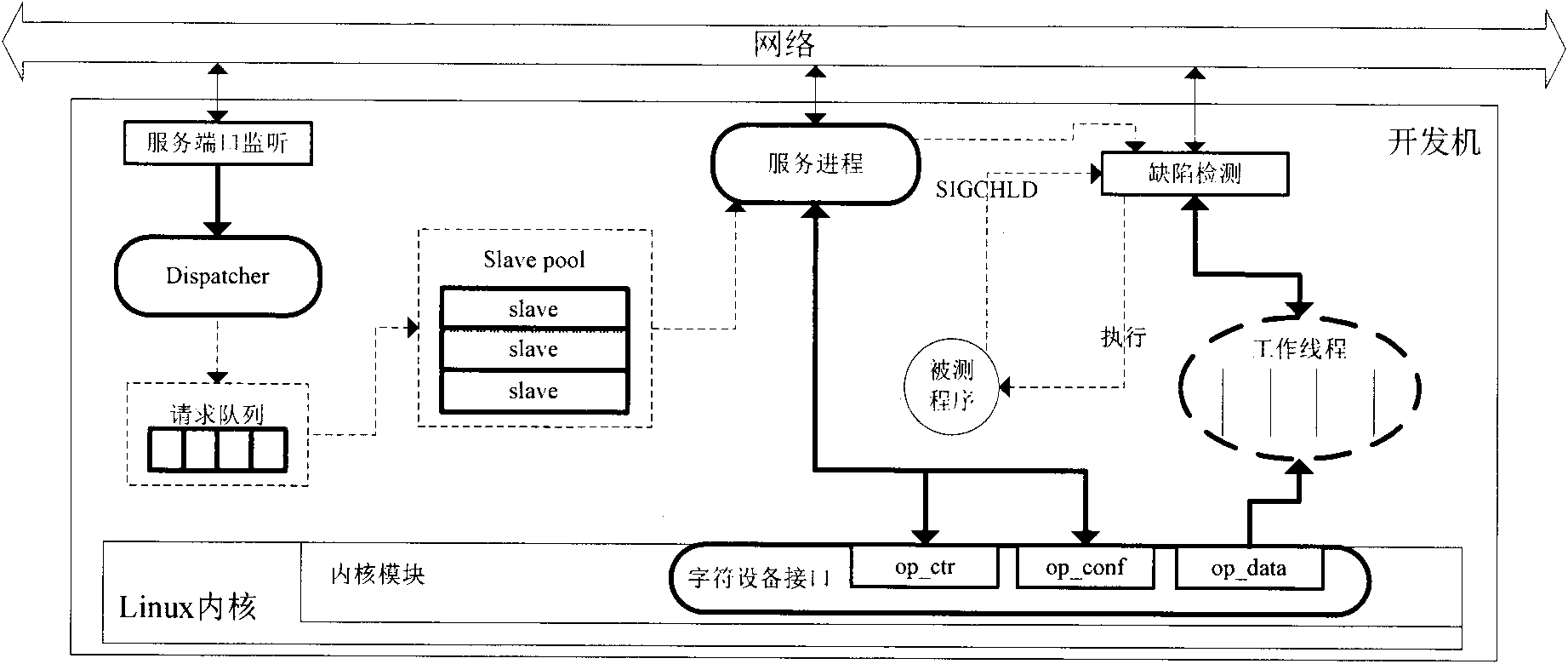
Dynamic defect detection method for embedded software
InactiveCN101937392AMultiple digital computer combinationsSoftware testing/debuggingPower Management UnitEmbedded software
The invention provides a dynamic defect detection method for precise embedded software. The embedded software comprises a test proxy module and a client module which are communicated with each other through a network, wherein a test proxy runs on a target machine to detect a detected program, sample and extract needed data and information and send the data and information to a client; the test proxy comprises a sampling module and the test proxy module; the sampling module is loaded to a kernel space in a mode of a Linux kernel module to operate a power management unit (PMU) register and sample an instruction address; the test proxy module is used for the proxy of interaction between the kernel module and the client, receiving the request, configuration and the like of the client, correspondingly setting the kernel module, reading sample data from the kernel module and sending the sample data to the client; and the client is developed and integrated to a GDIX embedded software test platform in a form of Eclipse plug-in. In the method, through the test proxy module and the client module, an embedded software dynamic defect detection service is provided and the processing and display of test result data are performed on line in real time.
Owner:SOUTH CHINA UNIV OF TECH
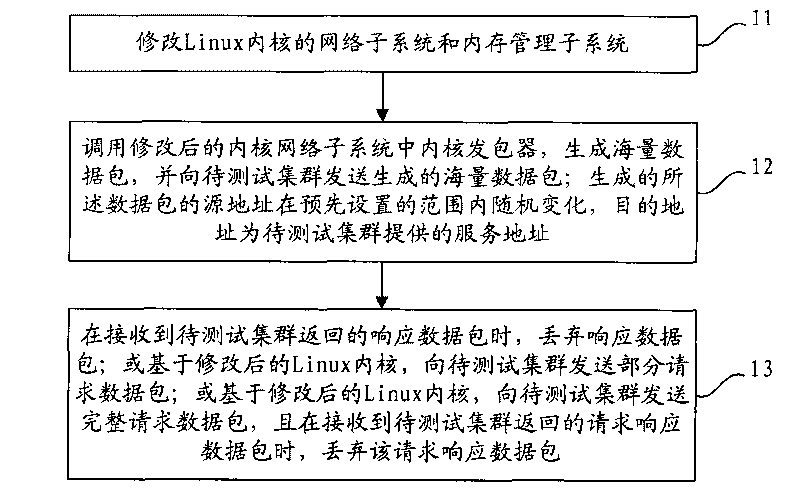
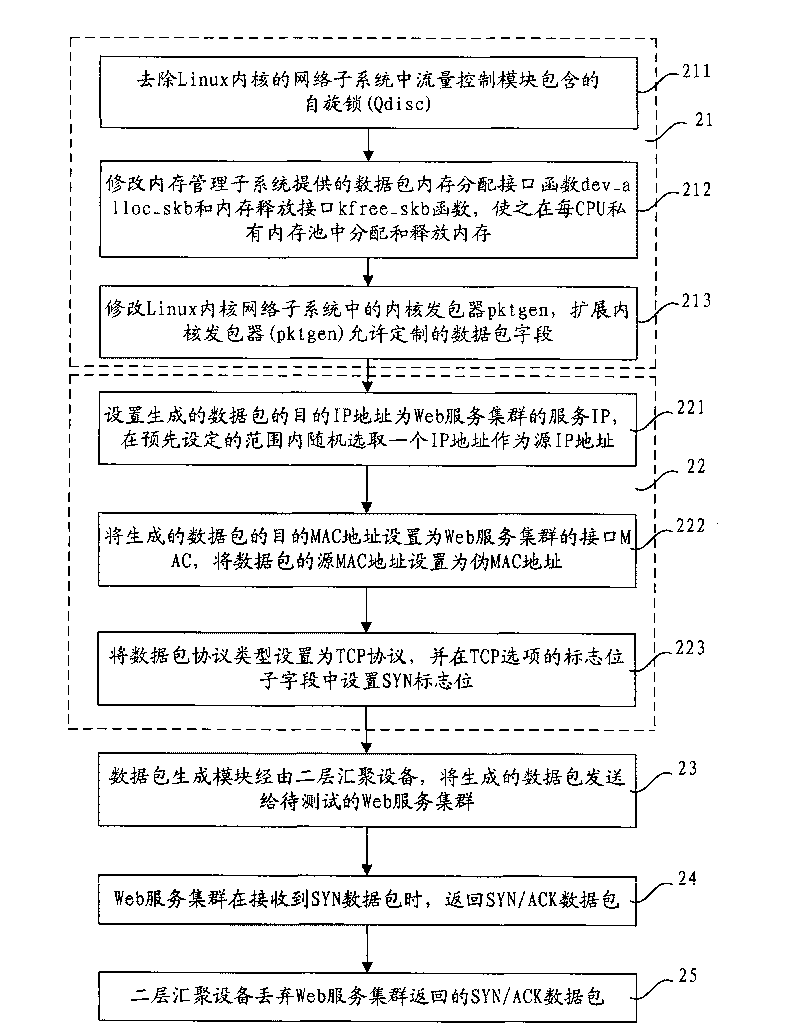
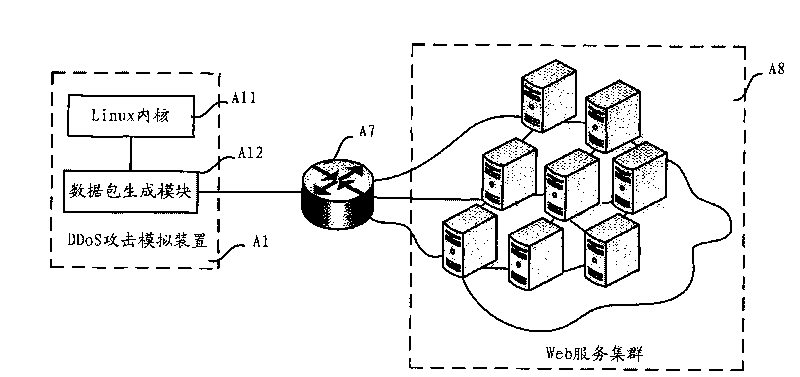
Method, device and system for testing DDOS (distributed denial of service) attacks
ActiveCN101753315AIncrease flexibilityImplementation LatencyData switching networksSecuring communicationLinux kernelStochastic variation
The invention relates to a method, a device and a system for testing DDOS (distributed denial of service) attacks. The method comprises the following steps of: modifying the network subsystem and the memory management subsystem of a Linux kernel; invoking a kernel package sending engine in the modified kernel network subsystem to generate massive data packets and sending a generated data packet to a cluster to be tested; wherein the source address of the generated data packet randomly changes in a preset range, and a target address is a service address provided by a cluster to be tested; when receiving a response data packet returned by the cluster to be tested, discarding the response data packet sent by the cluster to be tested; or sending a partial request data packet to the cluster to be tested; or sending a complete request data packet to the cluster to be tested, and when receiving the request / response data packet returned by the cluster to be tested, discarding the request / response data packet. The invention realizes the DDoS attack tests based on the modified Linux kernel without special hardware for design, thereby reducing the cost of DDoS attack test products.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD +1
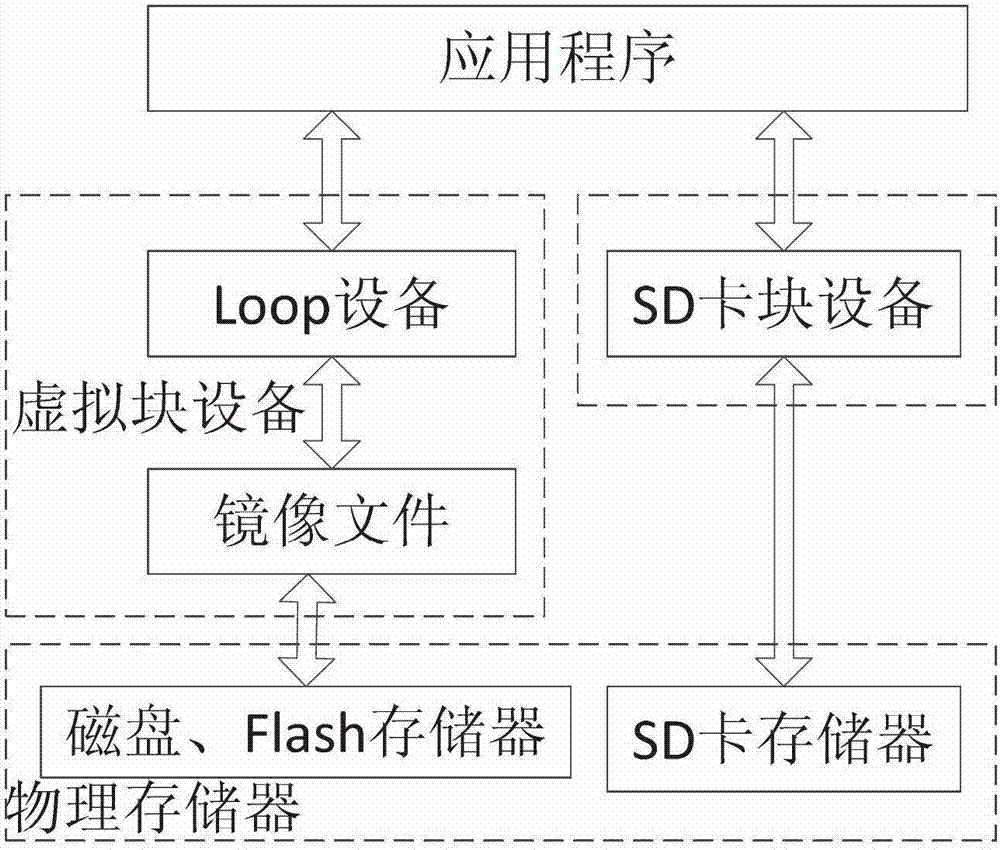
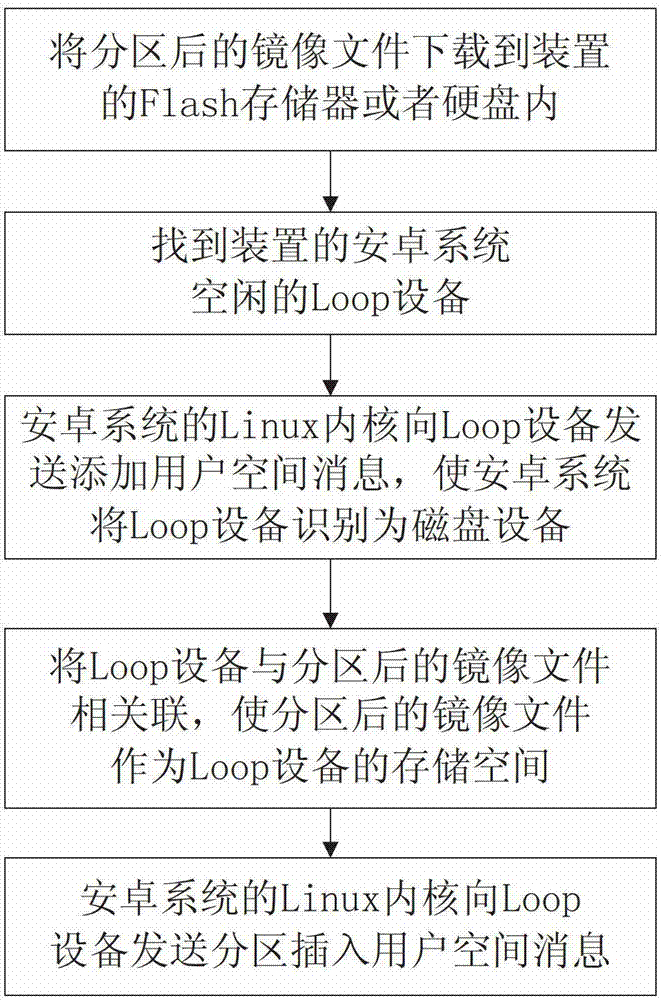
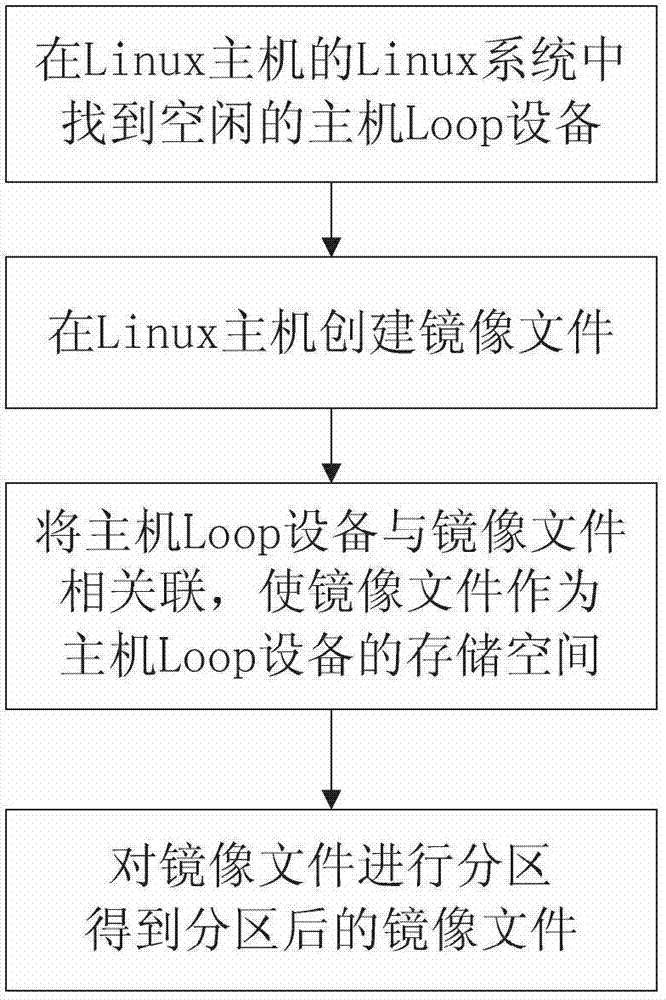
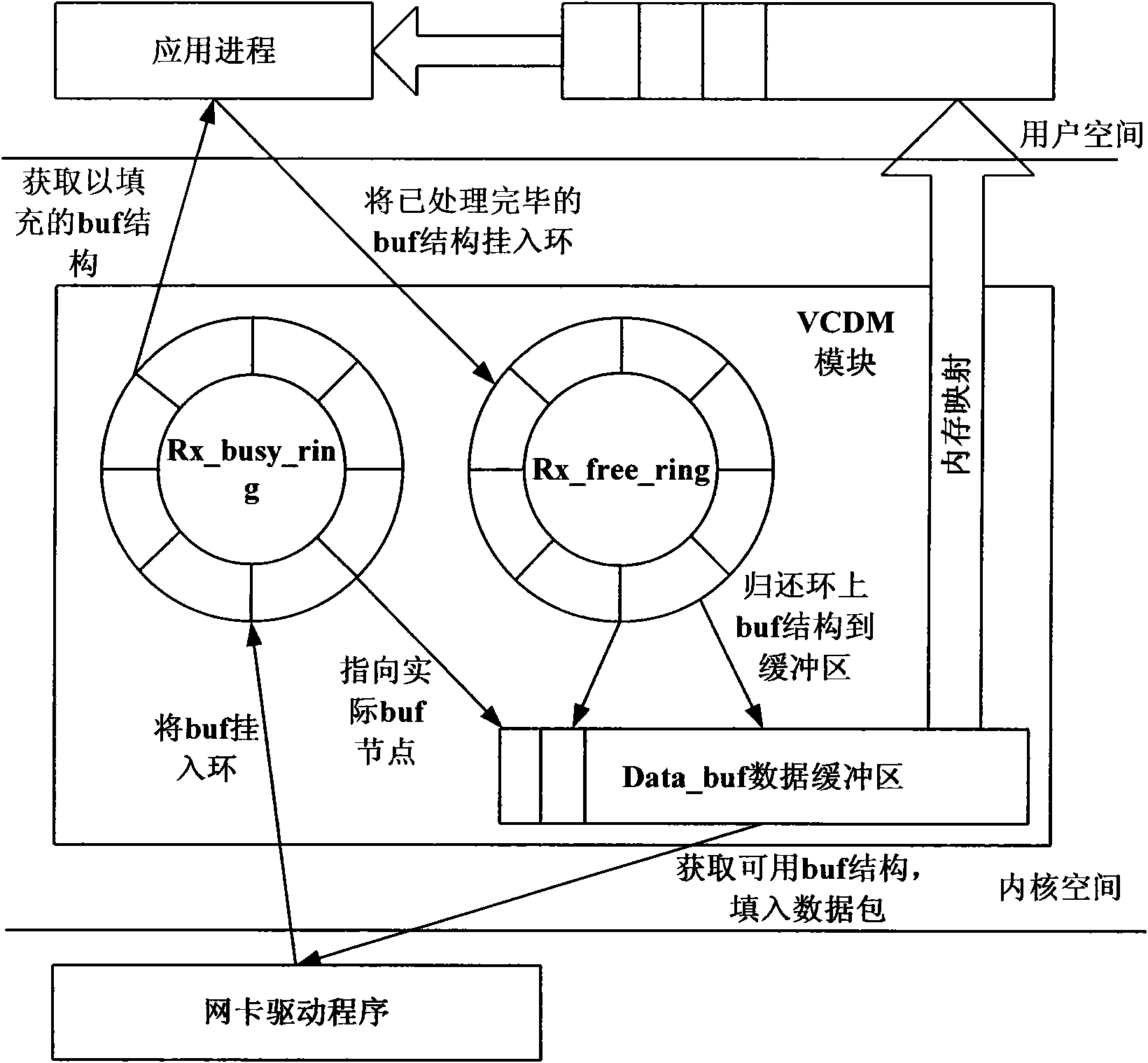
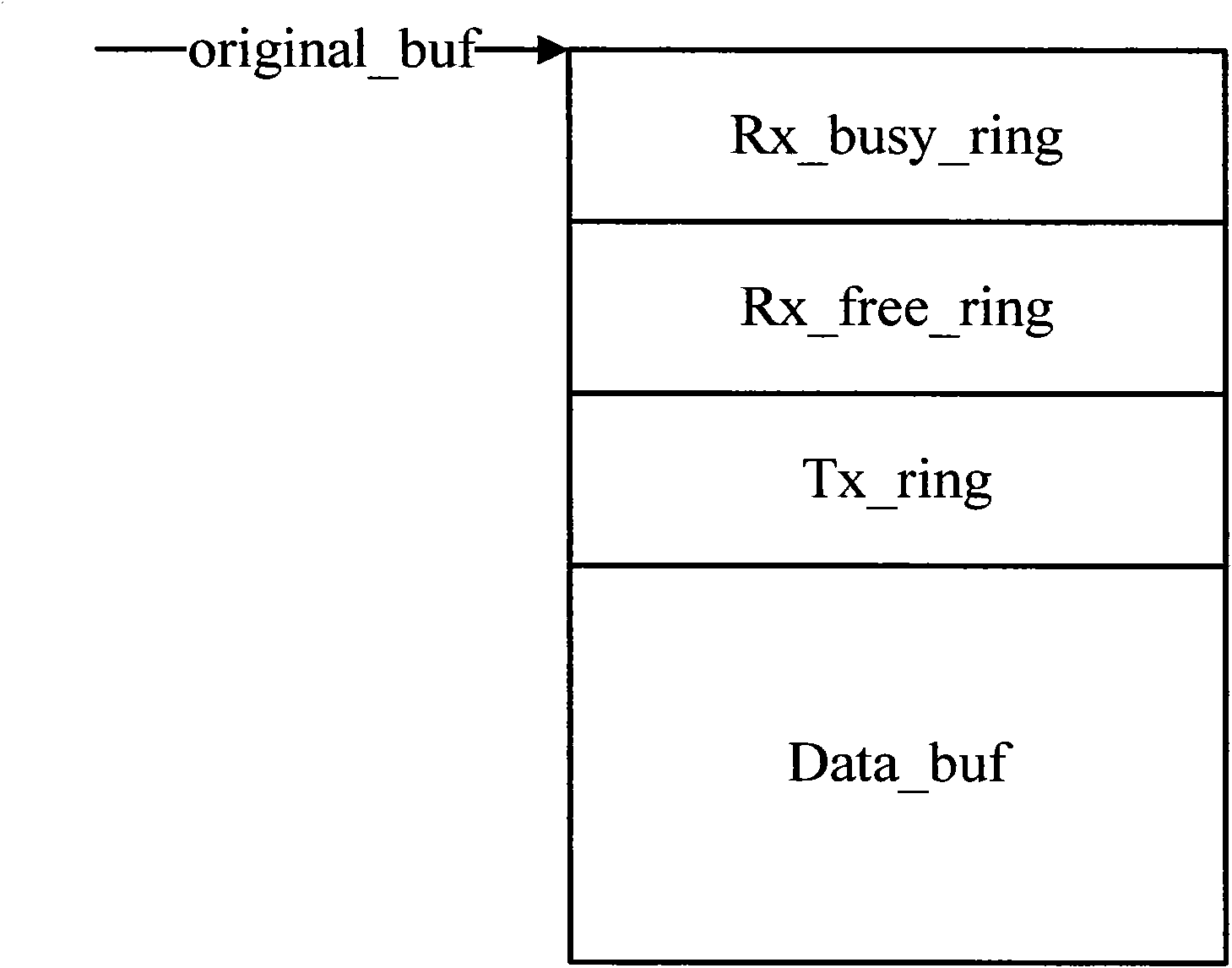
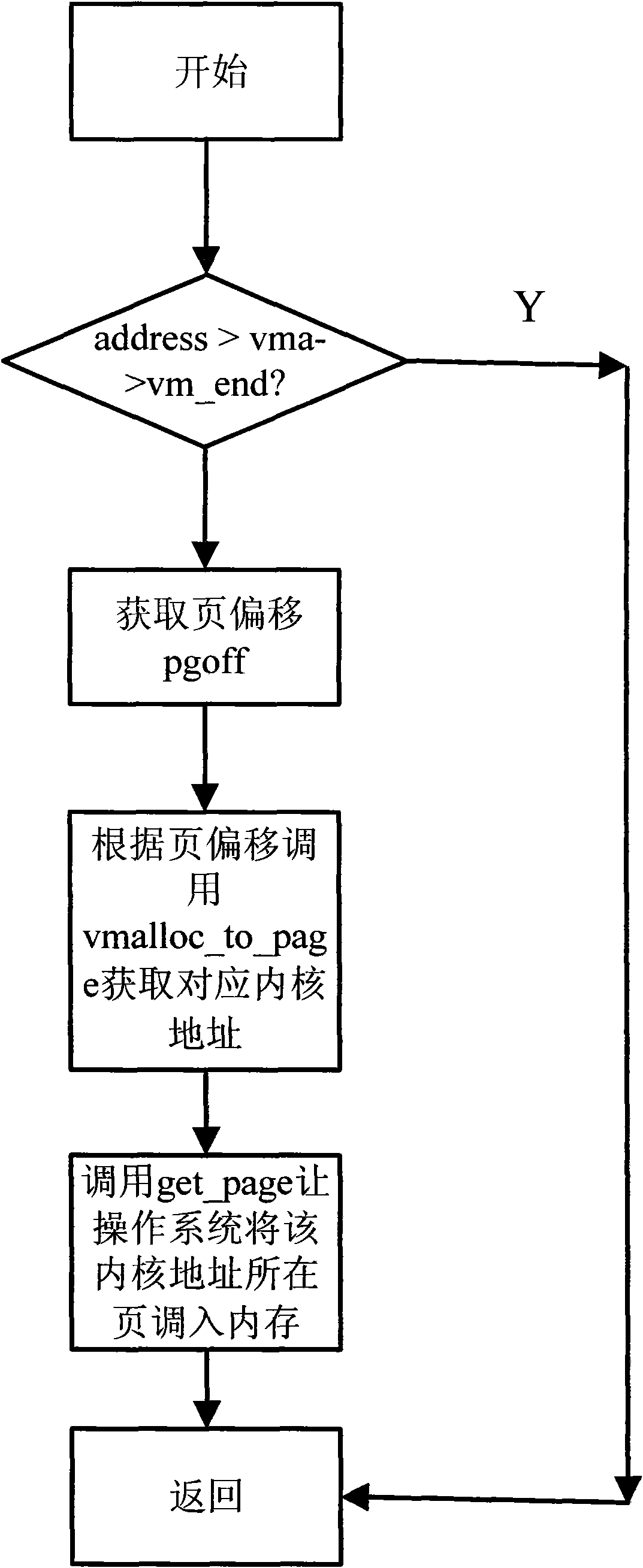
Method of virtual SD (Security Digital) card on device with android system
ActiveCN102880498ALow access speedFast accessProgram loading/initiatingSoftware simulation/interpretation/emulationVirtual slideLinux kernel
Owner:深圳市佳创软件有限公司
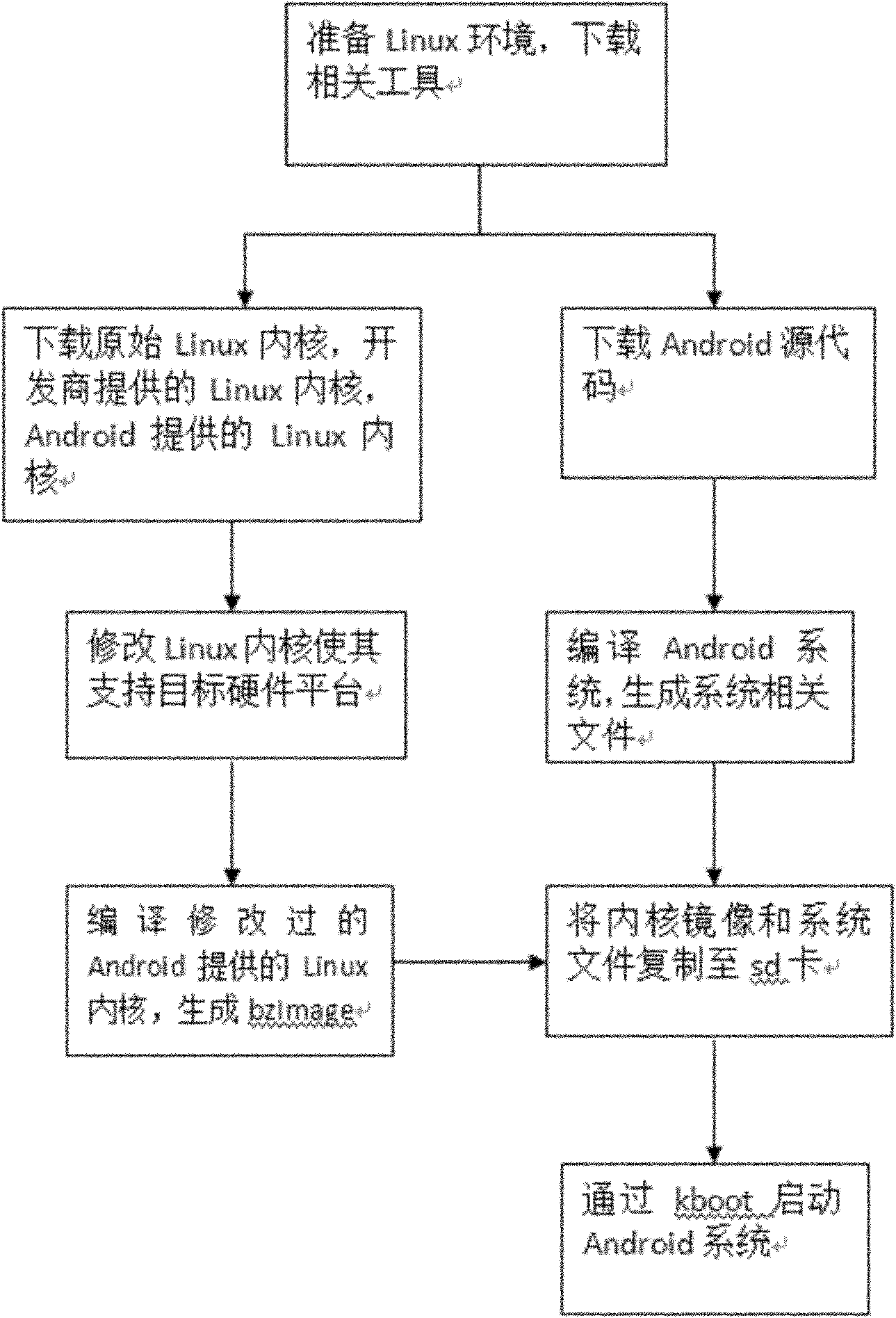
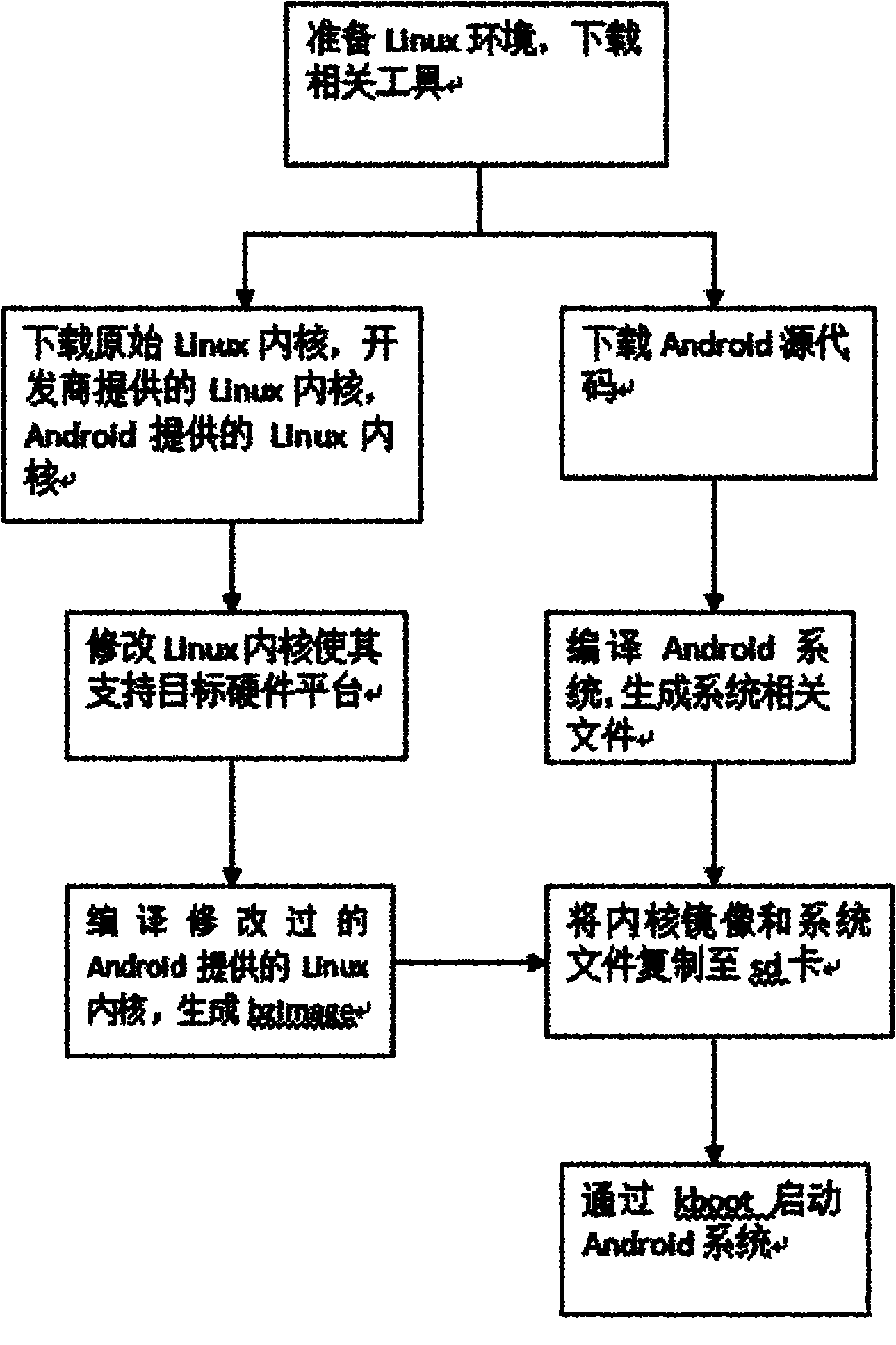
Method for transplanting Android mobile phone operating system to Atom development board
The invention relates to a method for transplanting an Android mobile phone operating system to an Atom development board, belonging to the technical field of an intelligent mobile phone operating system. The method comprises the following steps: downloading and installing development tools in the Linux environment; downloading a Linux kernel, modifying kernel codes to enable the Linux kernel to simultaneously support the Android system and the Atom CDK development board, and compiling the Linux kernel to generate a kernel mirror image; downloading Android source codes, and compiling the Android system to generate a system file; copying the generated kernel mirror image and the generated system file to an sd card; and installing a PUTTY client on a computer, inserting the sd card on the Atom CDK development board to be connected to the computer, starting the PUTTY client, entering the Kboot program loaded by the Atom CDK development board, and enabling the Kboot to automatically load the kernel mirror image and start the Android system. The invention enables the Android system to support the Intel Atom CDK development board by modifying the Linux kernel codes. As the Android system is more and more popular on the market, the Android system based on the X86 architecture certainly appears, thus the invention has strong foresight and realistic significance.
Owner:ZHEJIANG UNIV
Zero-copy data capture technology based on rt8169 gigabit net card and Linux operating system
InactiveCN101873337AImprove transmission efficiencyRealize data sharingData switching networksSecuring communicationOperational systemZero-copy
The invention relates to a zero-copy data capture technology based on an rt8169 gigabit net card and a Linux operating system, which is characterized in positioning data capture in the Internet backbone network and support gigabit-class network data capture. In the technical scheme, a computer can be linked in a target network in parallel through the gigabit net card to capture data flowing through the target network, and the data capture in the gigabit network can be realized through modifying the net card drive and using the zero-copy technique. Since the technology realizes the zero copy of the network data packet from the kernel to the space of the user through construction of the Linux kernel module and modification of the rt8169 gigabit net card driving program, thereby lowering the complexity of the ordinary data collection, improving the data packet capture capability, reducing the cost of the system, and achieving the purpose of low cost. The technology is realized through three modules, the modified net card driving program, the constructed kernel module and the user process interface module. The modules cooperate with each other in operation to realize the high-speed transmission of the data packet from the net card to the user program.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
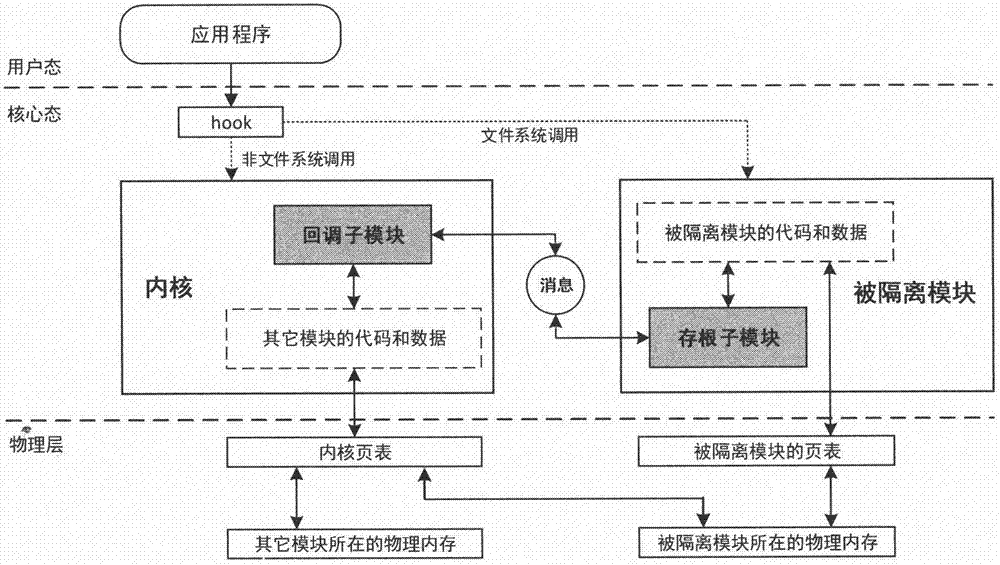
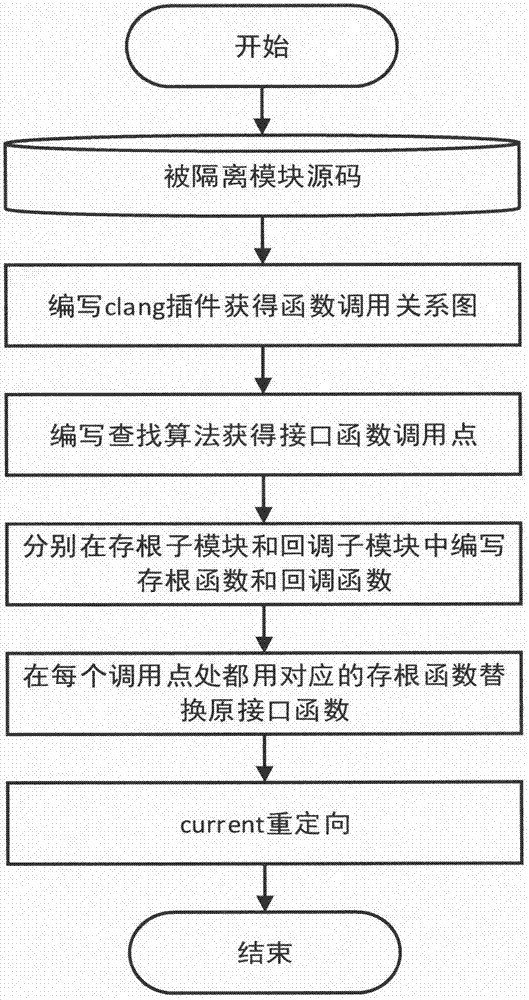
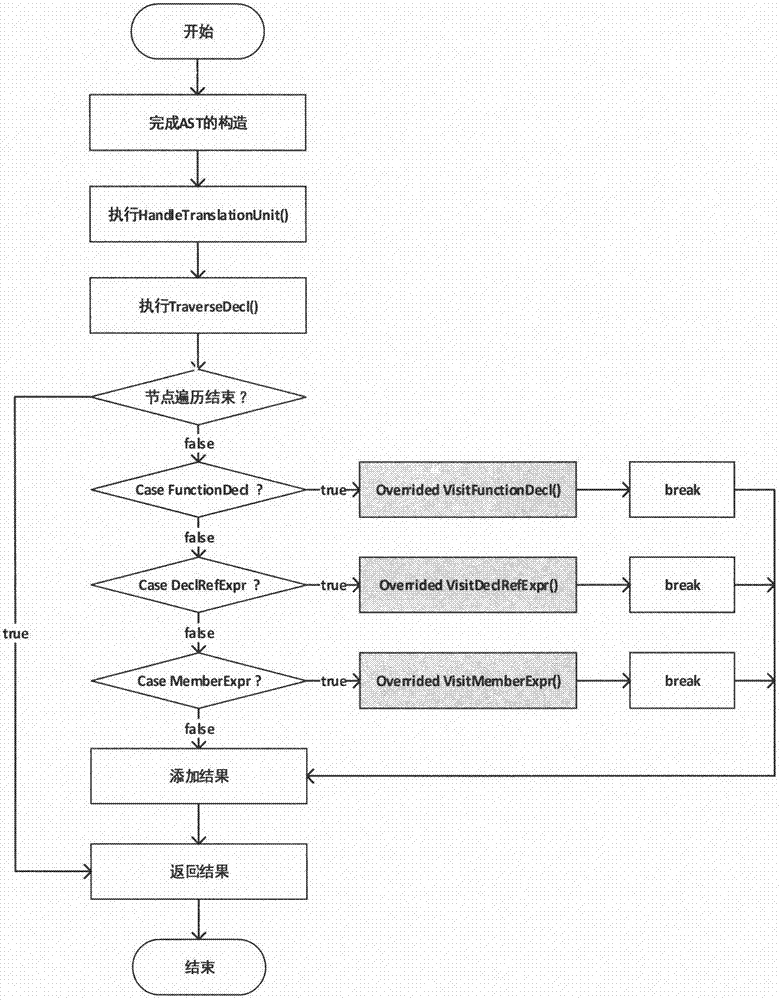
Linux kernel page table isolation-oriented function calling reconstruction method
The invention discloses a Linux kernel page table isolation-oriented function calling reconstruction method. Through kernel page table isolation, codes and data of isolated modules are singly mapped into physical address spaces controlled by a specific page table, and an access interval of the page table is controlled to realize isolation among the modules. The method is mainly used for reconstructing function calling manners among modules of Linux systems, so as to ensure that the isolated modules can normally access the codes and data of other modules in kernels. The method comprises the following steps of: (1) compiling a clang compiler plugin to obtain a function calling relational graph of the isolated modules; (2) compiling a search algorithm to search interface function calling points; (3) respectively realizing stub sub-modules and callback sub-modules in the isolated modules and kernels; (4) replacing an original interface function by a stub function at each calling point; and (5) redirecting a process control block to ensure the data consistency.
Owner:NANJING UNIV
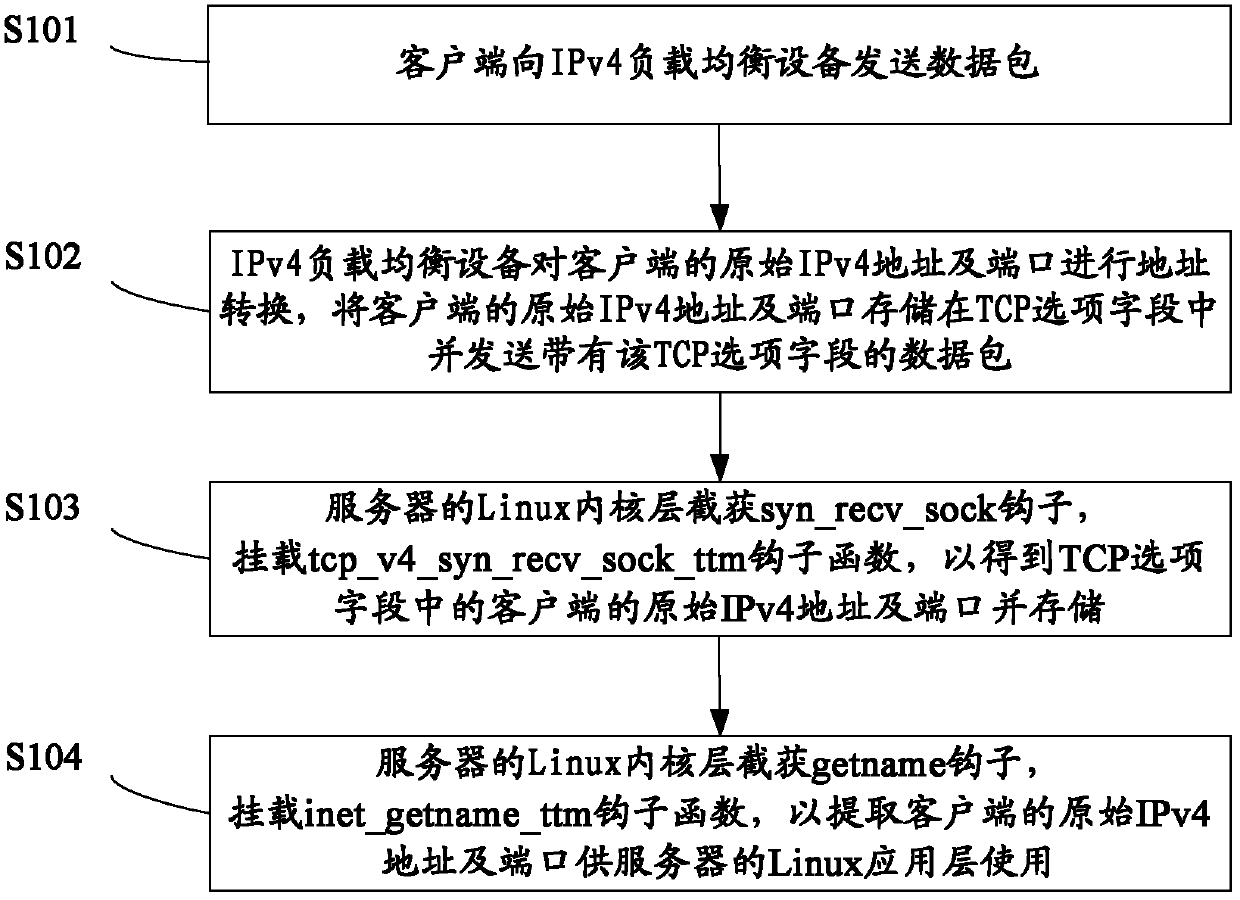
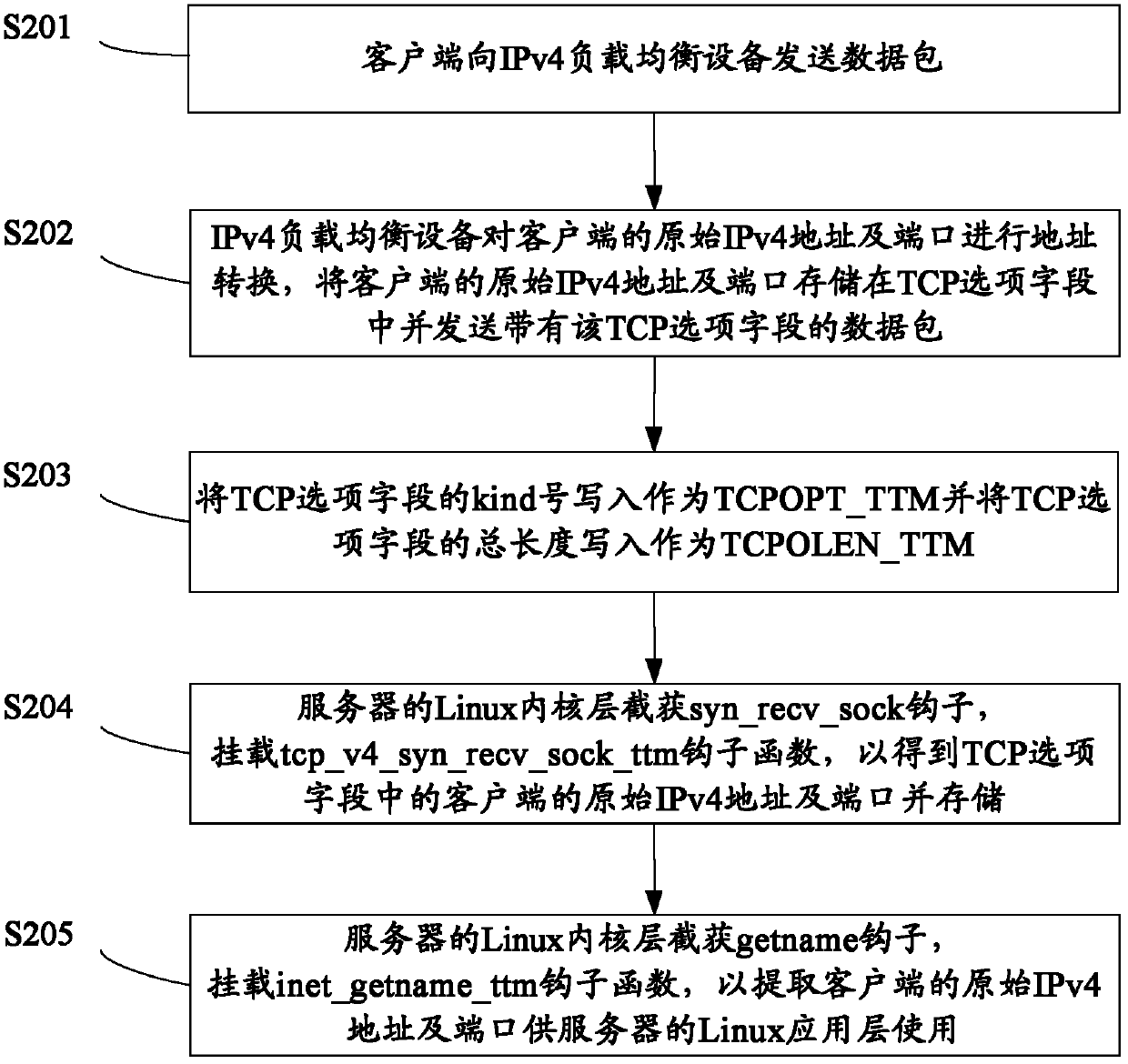
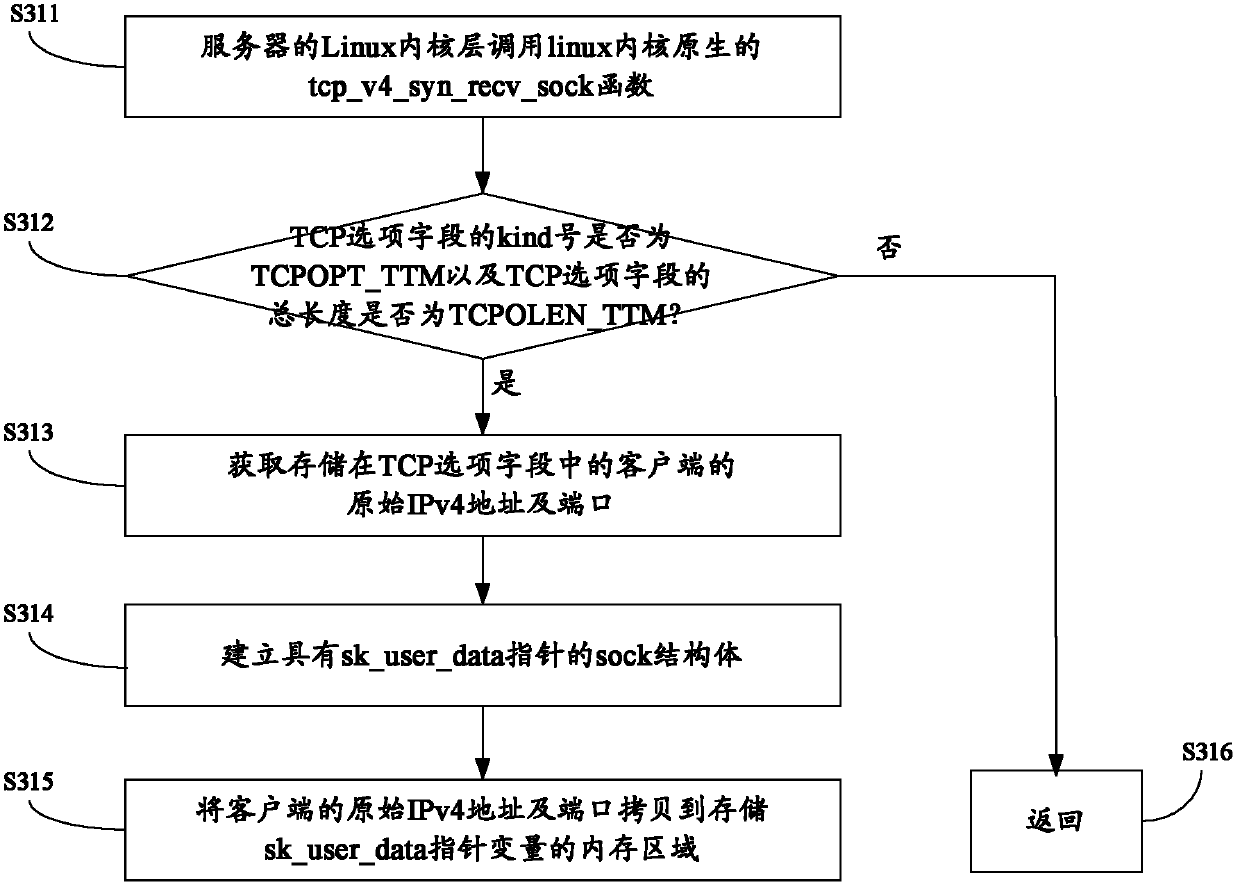
Method and device for transmitting IPv4 address and port of client-side to back-end server
The invention provides a method and device for transmitting an original IPv4 address and a port of a client-side to a back-end server from an IPv4 load balancing device. The method comprises the following steps: the client-side sends data packages to the IPv4 load balancing device; the IPv4 load balancing device carries out address conversion on the original IPv4 address and the port of the client-side, the original IPv4 address and the port of the client-side are stored in a TCP option field, and data packages with the TCP option field are sent; a Linux kernel layer of the server intercepts a syn_recv_sock hook, and a tcp_v4_syn_recv_sock_ttm hook function is mounted so as to obtain and store the original IPv4 address and the port of the client-side in the TCP option field; the Linux kernel layer of the server intercepts a getname hook, and a inet_getname_ttm hook function is mounted so as to extract the original IPv4 address and the port of the client-side to be used by a Linux application layer of the server. Due to the fact that the original IPv4 address and the port information of the client-side are added in the TCP option field, the back-end real server can obtain an original IP and the port information of the client-side, and address positioning can be carried out on a client.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
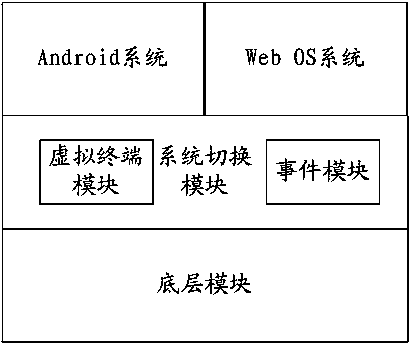
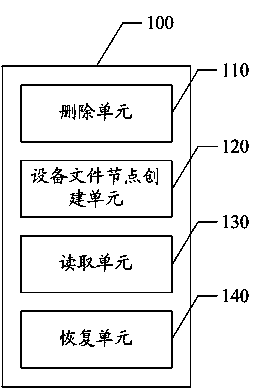
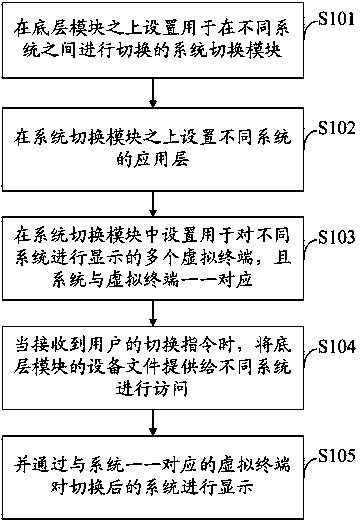
Device and method for obtaining multiple systems through linux kernel
The invention discloses a device and method for obtaining multiple systems through a linux kernel. The device comprises a bottom layer module shared by the different systems, a system switching module arranged on the bottom layer module and used for switching the different systems and the different systems arranged on the system switching module. The system switching module comprises a virtual terminal module and an event module. The virtual terminal module comprises multiple virtual terminals used for displaying the different systems and the systems correspond to the virtual terminals one to one. The event module is used for enabling the different systems to have access to a device file of the bottom layer module according to a switching order of a user.
Owner:TCL CORPORATION
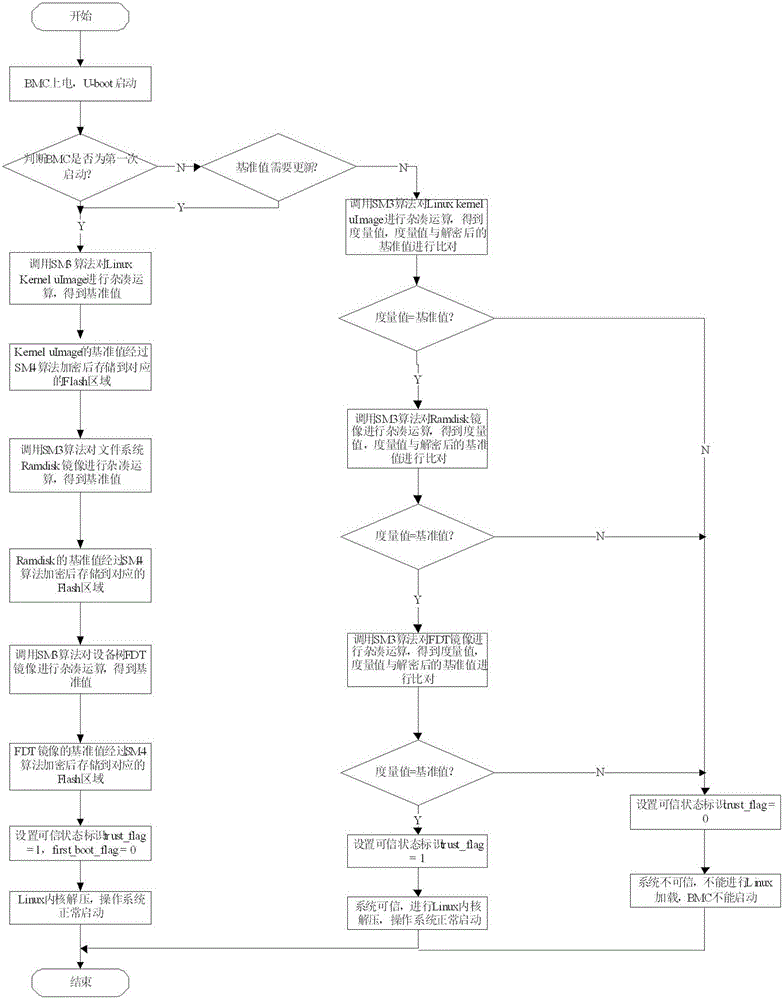
BMC U-boot trusted starting control method
InactiveCN106384052AEnsure credibleIntegrity guaranteedPlatform integrity maintainanceFile systemLinux kernel
The invention discloses a BMC U-boot trusted starting control method; the method comprises the following steps: using SM3 and SM4 cipher algorithms (SM3 refers to a cipher hash algorithm, SM4 refers to a symmetry cipher algorithm) to determine measure and trusted states of a Linux core mirror image, a file system mirror image and an equipment tree mirror image in a U-boot starting guide system process, i.e., comparing a measure value with a reference value; starting an operating system if the measure value-reference value contrast passes, thus allowing the BMC to enter a trusted environment; stop guiding the operating system if the measure value-reference value is not consistent, allowing a BMC administrator to process, thus finally building up a BMC system platform trusted execution environment. Compared with the prior art, the BMC U-boot trusted starting control method can ensure the system integrity and no malicious code is implanted, thus ensuring the trusted BMC system platform execution environment, and helping domestic BMC chip core competitiveness; the BMC U-boot trusted starting control method is strong in practical value, wide in application scope, and easy to promote.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
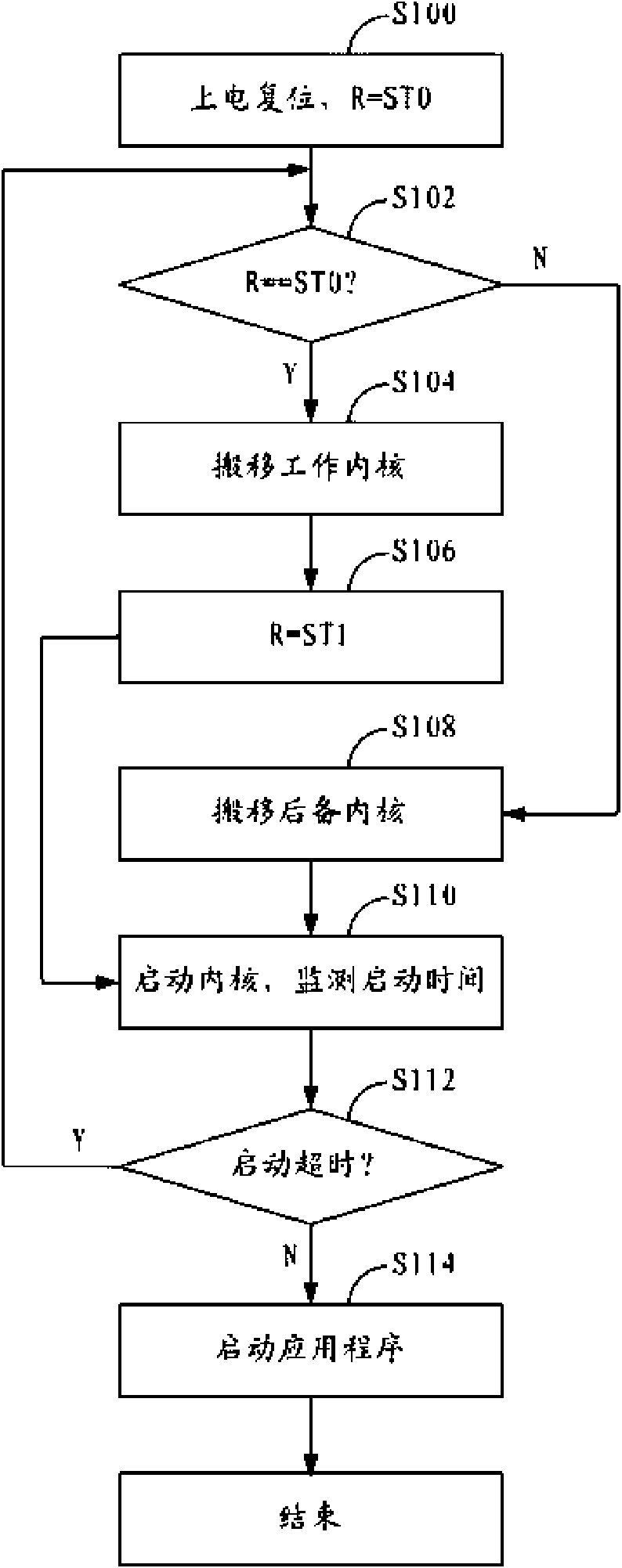
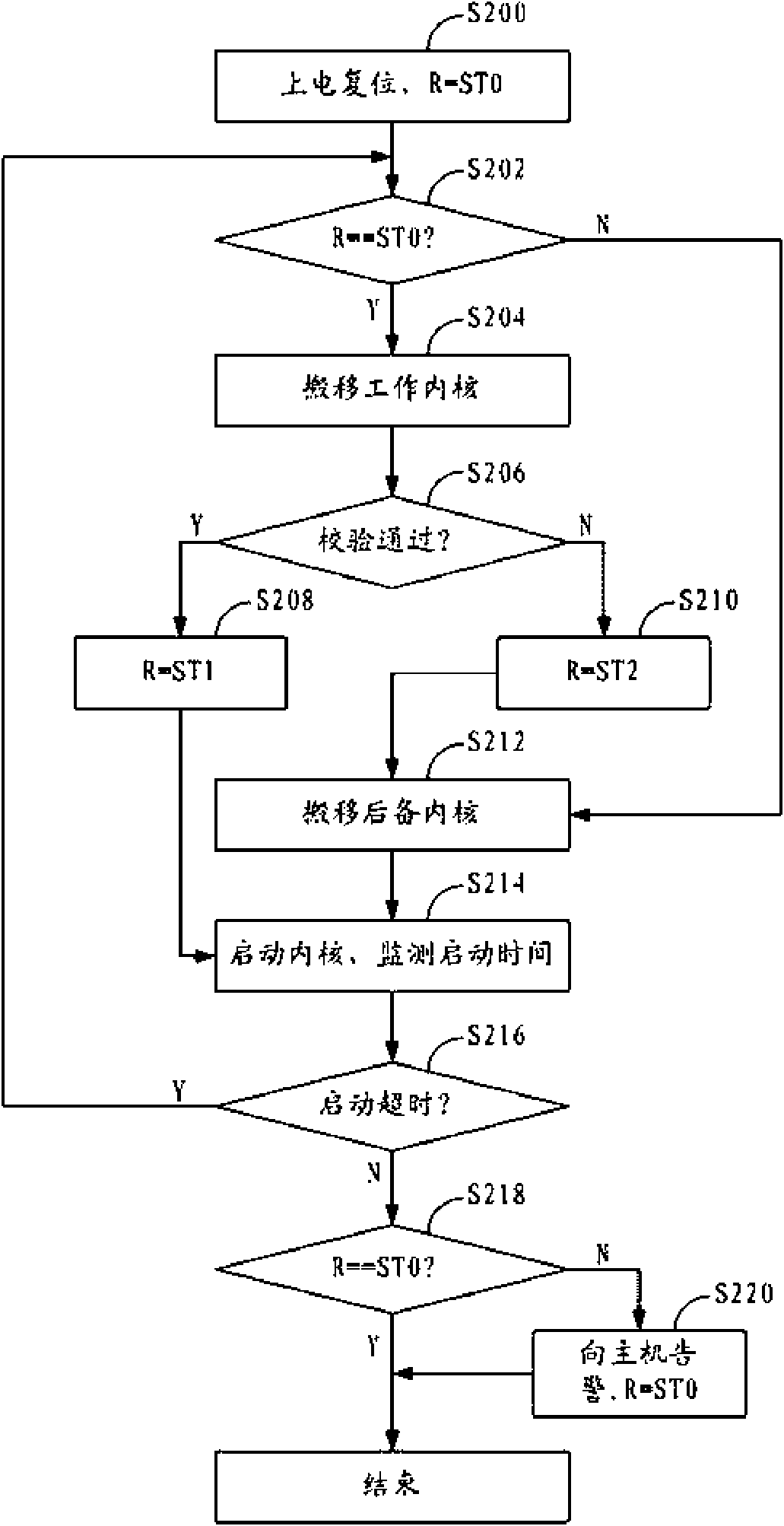
Safe method and system used for remotely upgrading embedded Linux kernel
ActiveCN101556547AFlexible upgradeReliable securityProgram loading/initiatingRedundant operation error correctionNetwork communicationLinux kernel
The invention provides a safe method and a system used for remotely upgrading an embedded Linux kernel, which are applicable for the network communication field. The method includes the following steps: A. two or even more Linux kernel files are stored in a system, wherein the kernel which is booted up by the Linux system by default is a working kernel, and the other Linux kernels are back-up kernels which can ensure successful boot-up of the system; B. the working kernel is taken as an upgrading object for upgrading when the Linux kernels need upgrading; and C. the back-up kernels are started when the working kernel fails to boot up due to upgrading failure.
Owner:成都芯通软件有限公司
Method for processing embedded multi-module Internet of Things mobile terminal device data system
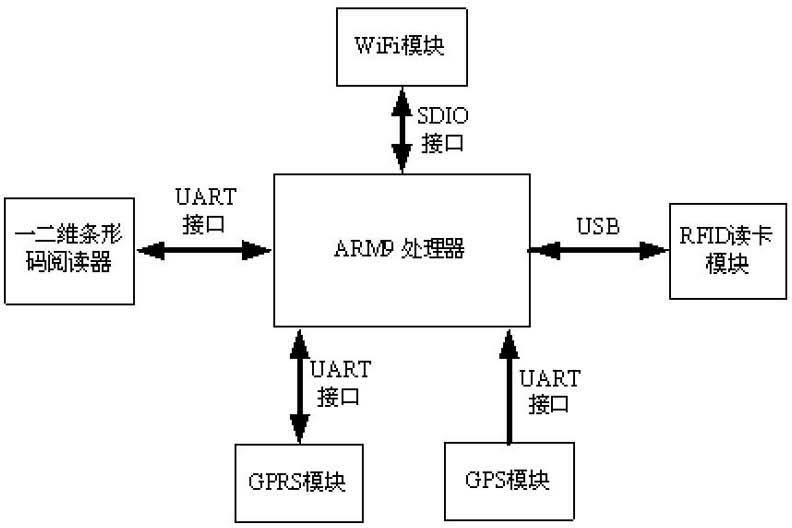
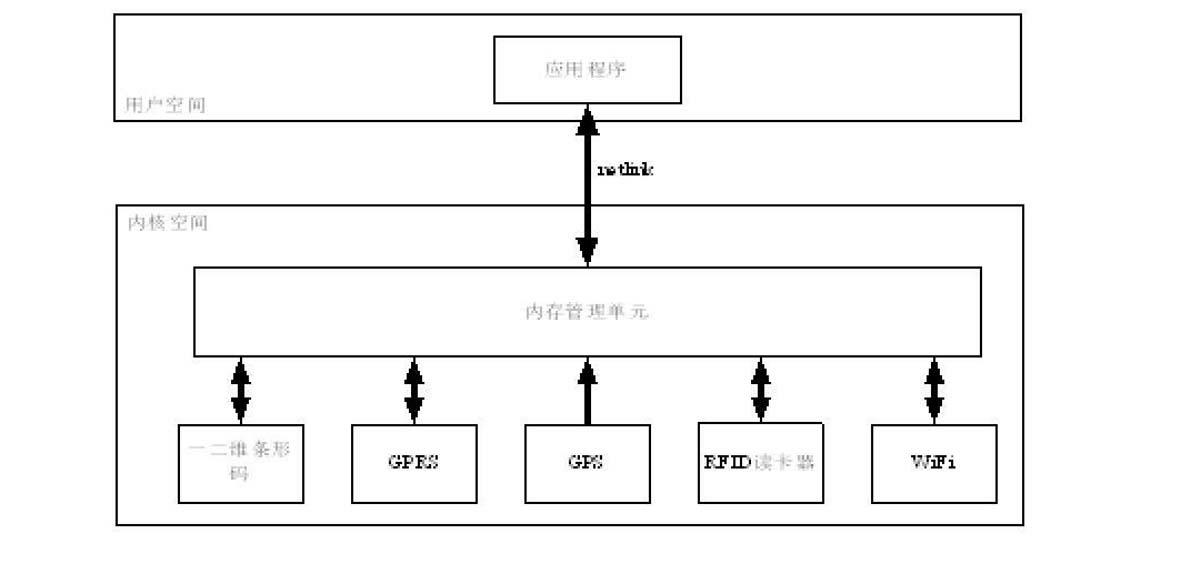
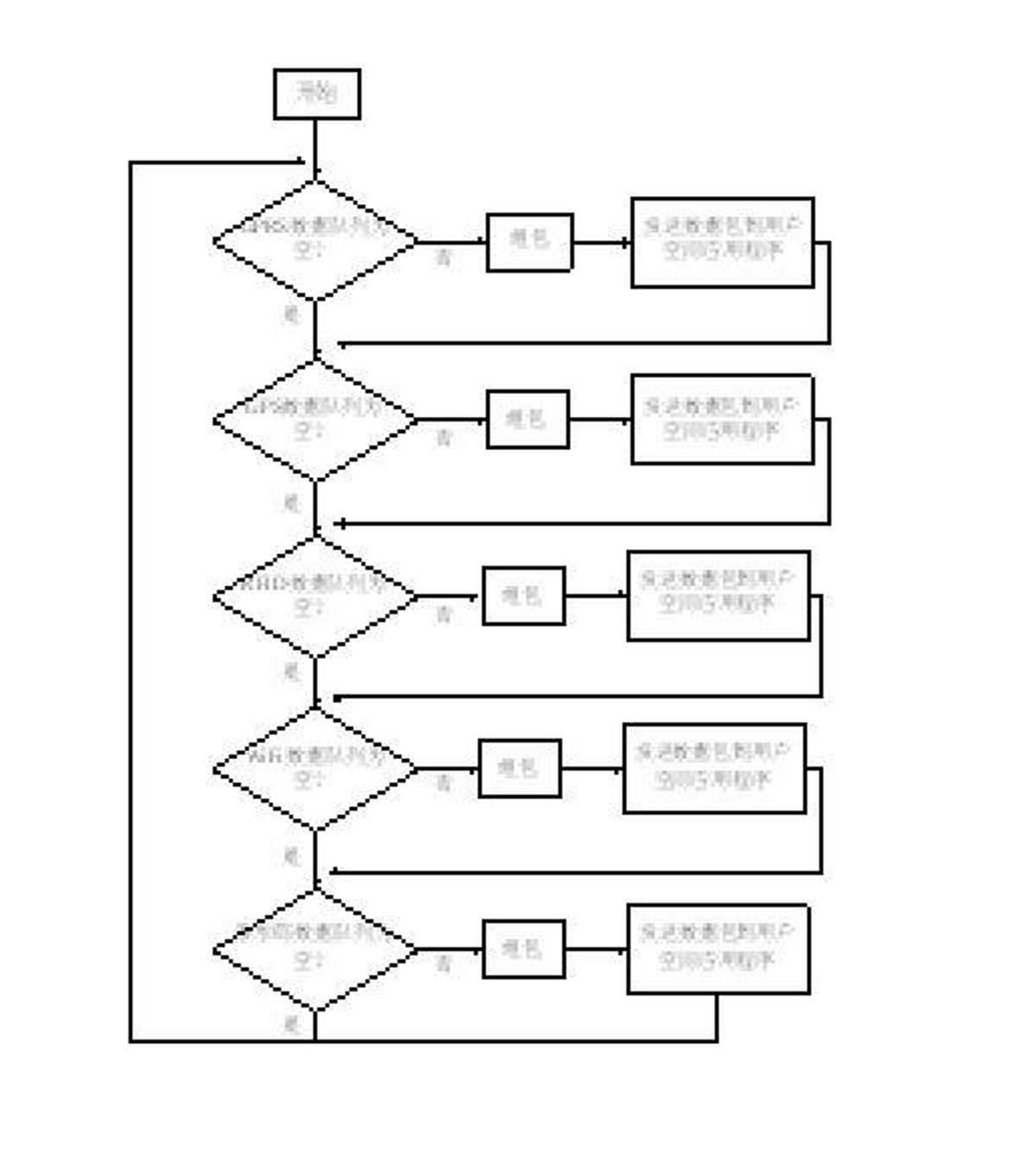
InactiveCN102629202ACo-operative working arrangementsSpecific program execution arrangementsProgram EfficiencyControl data
The invention relates to a method for processing an embedded multi-module Internet of Things mobile terminal device data system. The system comprises an application unit, a memory management unit and hardware modules, wherein the memory management unit comprises a Linux kernel module, the hardware modules comprise hardware kernel modules, a communication mode is established by the memory management unit between the application unit and the hardware modules, and each of the hardware modules communicates with the outside through an antenna. According to the method for processing the embedded multi-module Internet of Things mobile terminal device data system, a memory management unit driving module is designed to communicate with the rest of the hardware modules in a driving mode, and simultaneously a netlink mode is utilized to provide only one communication channel between an underlying driver and an upper-layer application program to control the distribution and collection of data. By means of the method for processing the embedded multi-module Internet of Things mobile terminal device data system, the programming is extremely flexible, and the program efficiency is extremely high.
Owner:VOTO COMM
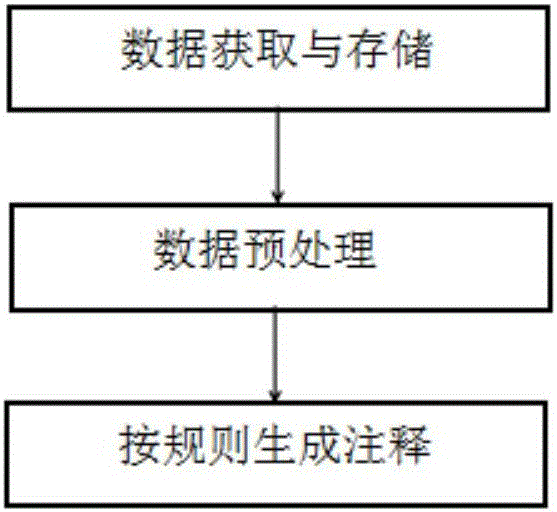
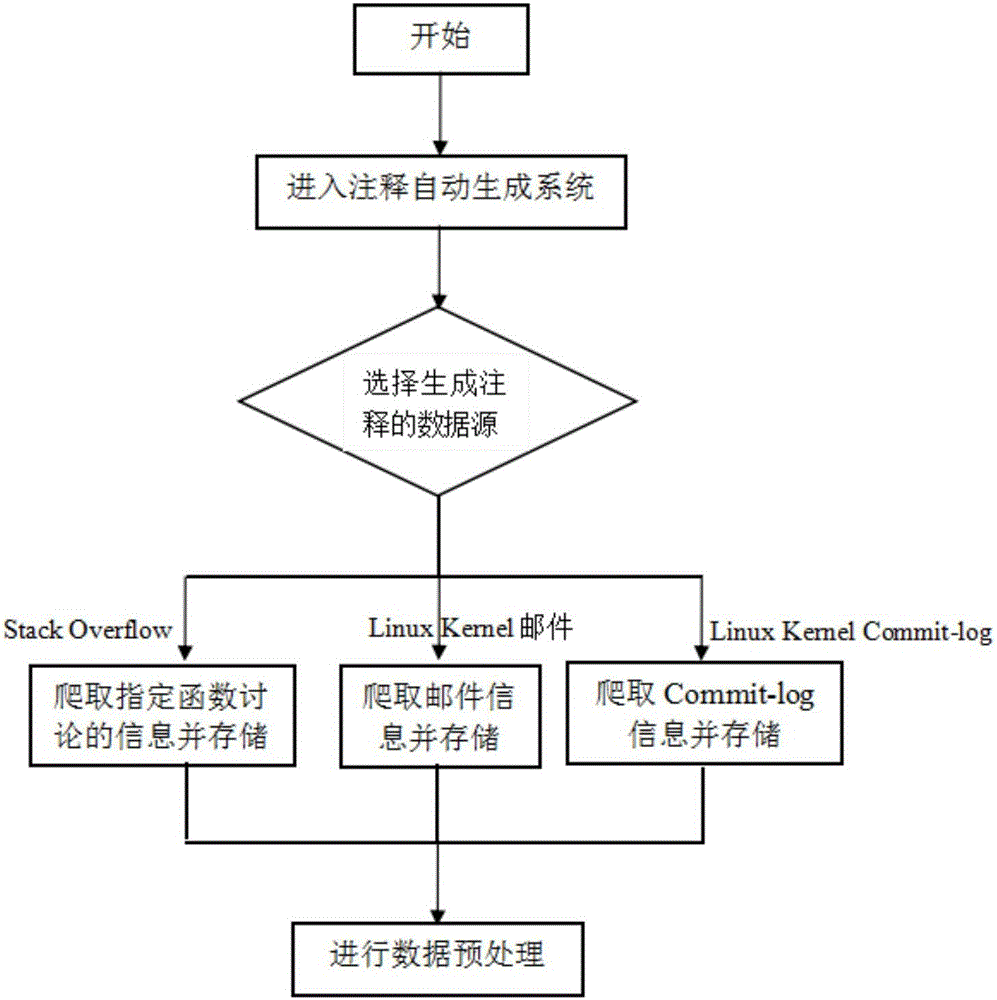
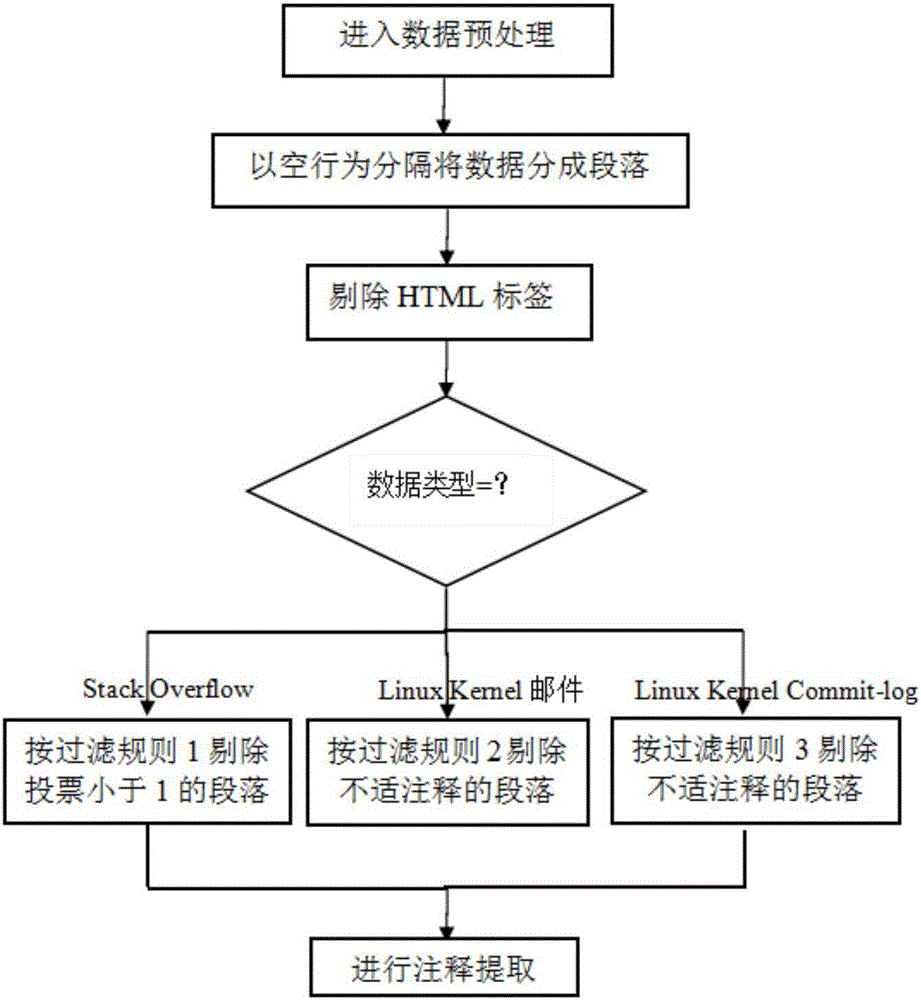
Automatic source code annotation generation method based on data mining
InactiveCN106681708ARealize automatic generationImprove readabilityWeb data indexingProgram documentationData sourceFiltering rules
The invention relates to an automatic source code annotation generation method based on data mining. The method includes the steps that texts containing needed annotations are extracted from three kinds of data sources; three filtering rules are formed by combining respective characteristics of the data sources to reject irrelevant noise information, and a text processing technology is used for character format preprocessing; two extraction rules of describing function annotation key characteristics are formed through summarization, and function general annotation is automatically generated according to the two extraction rules combined with the characteristics of the three data sources. The extracted annotation can enrich traditional function annotation, provide multi-dimensional information and support version alternation. Customization is carried out on linux kernel annotation and is easy to implement, and function annotation information which is high in readability and reliable can be provided with small cost; the blank of automatic linux kernel function annotation is effectively filled up, richer reference information is provided for learning and development, and development workload and difficulty are effectively reduced.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
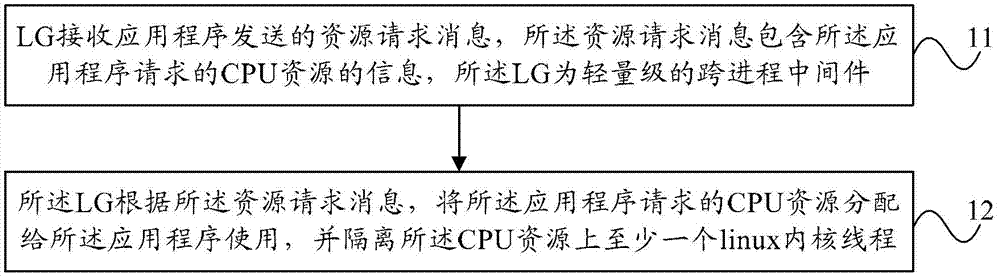
Method and equipment for scheduling multi-core processor
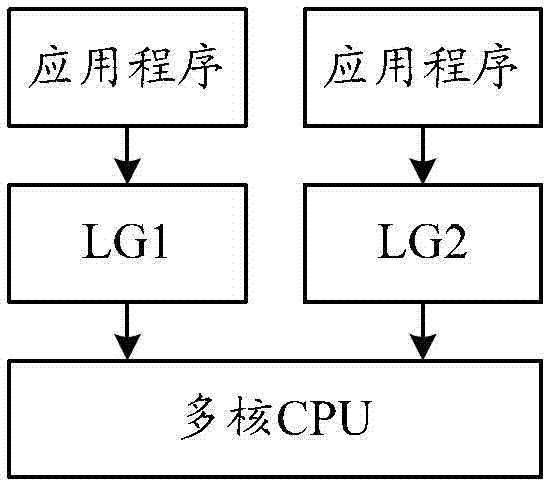
InactiveCN102831015AReduce overheadImprove resource utilizationResource allocationLinux kernelApplication software
The invention provides a method and equipment for scheduling a multi-core processor. The method comprises the following steps of: receiving source request information sent by an application program by an LG (Linear Generator), wherein the resource request information comprises information of CPU (Central Processing Unit) resources requested by the application program, and the LG is a lightweight-class cross-course intermediate piece; and distributing the CPU resources requested by the application program to the application program for use according to the resource request information, and isolating at least one Linux kernel thread on the CPU resources. With the adoption of the method and equipment for scheduling the multi-core processor provided by the embodiment of the invention, the cost can be reduced in a multi-core scheduling process; the multi-core displacement is simplified; and the multi-core CPU resource use ratio can be improved.
Owner:HUAWEI TECH CO LTD
Fast detection method of data packets in user space based on DPDK
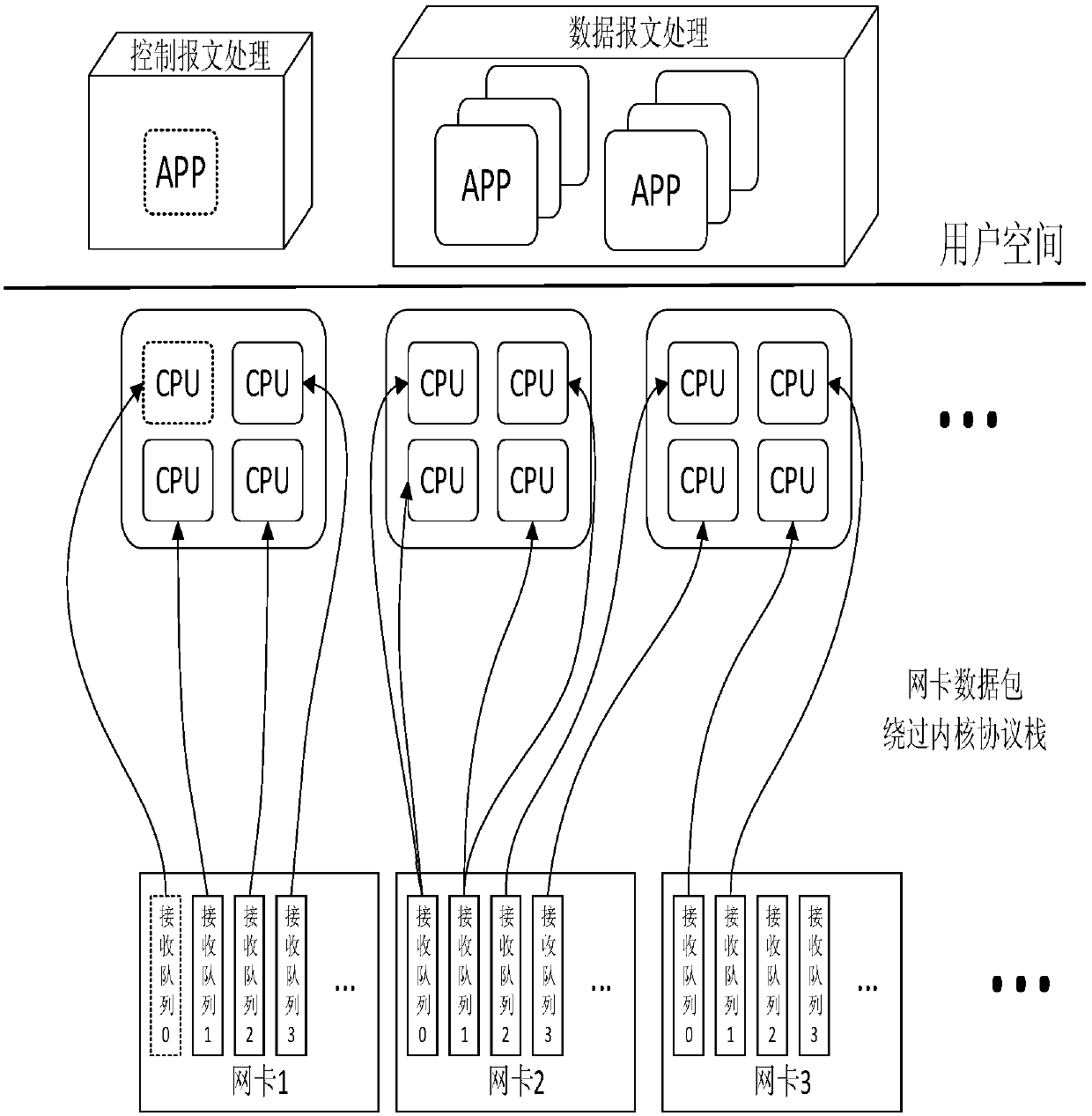
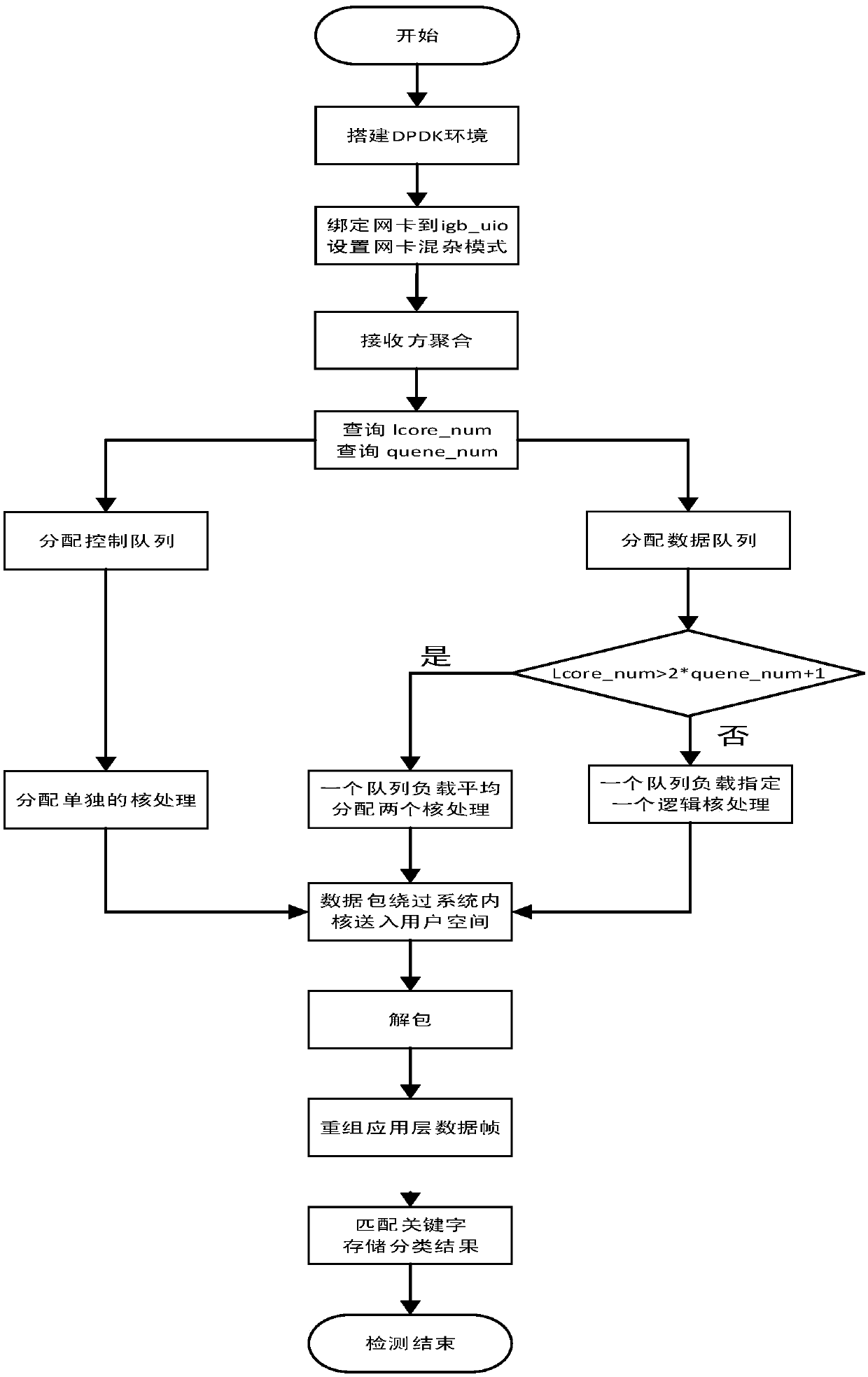
ActiveCN107911237AFast recognitionImprove processing efficiencyInterprogram communicationData switching networksData streamNetwork packet
The invention discloses a fast detection method of data packets in a user space based on DPDK. The method comprises the following steps: A, receiving data streams from a network card, configuring multiple queues of the network card, binding the queues with a specified CPU logic kernel, and transferring the data packets into the user space provided by the DPDK by passing the linux kernel; B, processing the data packets in the user space provided by the DPDK, specifically; B1, stripping off data frames until to application layers; B2, analyzing HTTP message features, and comparing the features of various applications of the application layers for classification and identification; and C, finally recording to classification result, and completing the test.
Owner:NANJING UNIV OF POSTS & TELECOMM
Mobile terminal and controlling method thereof
ActiveUS20130179403A1Improve the environmentMemory loss protectionDigital data processing detailsFile systemComputer terminal
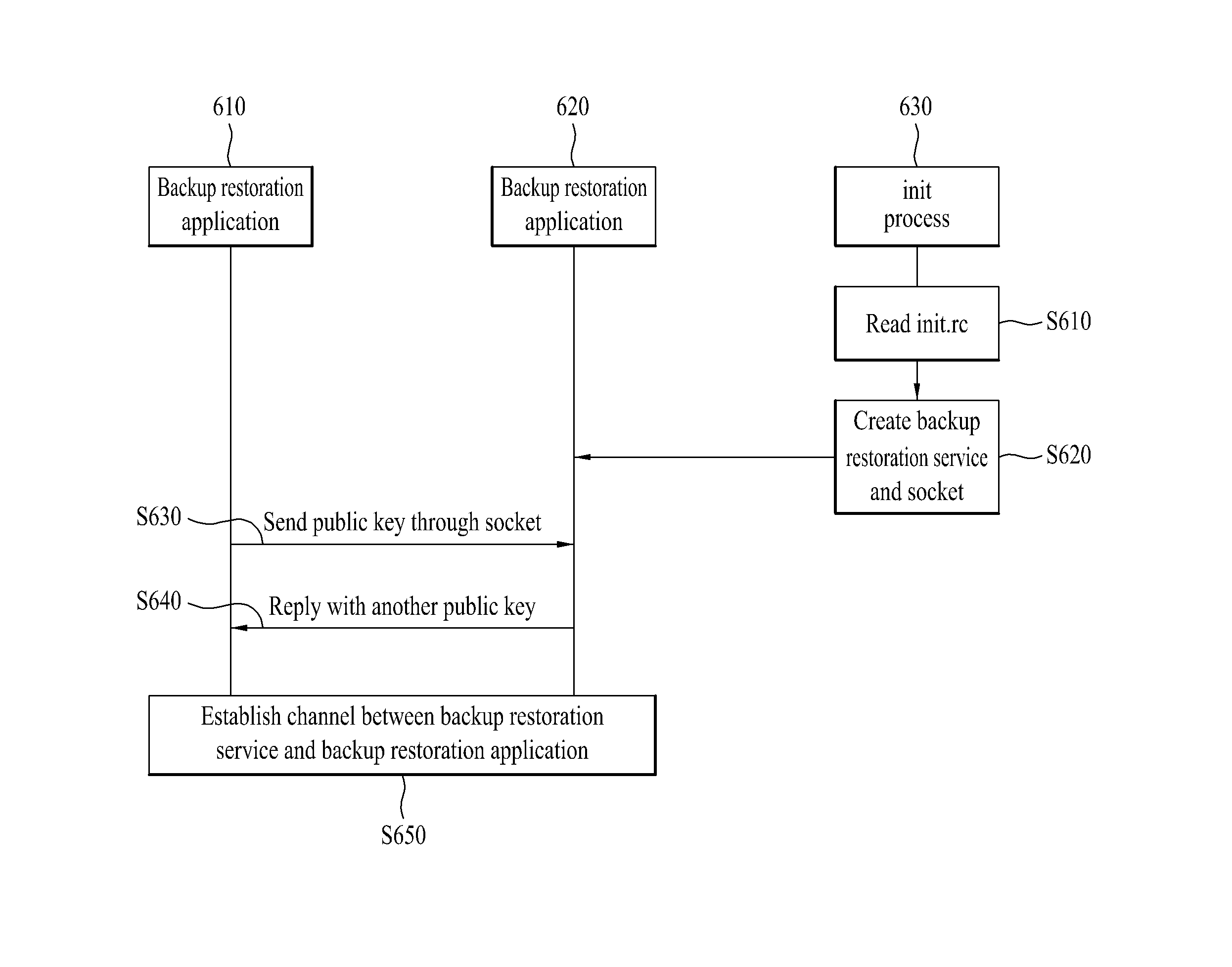
A mobile terminal and controlling method thereof are disclosed, by which restoration and backup operations are performed for the mobile terminal. For example, the mobile terminal includes a controller performing a backup operation and a restoration operation on the mobile terminal, the controller including an application module for activating a backup restoration application and at least one or more applications; and a Linux kernel module for managing a basic hardware function of the mobile terminal, the Linux kernel module including a backup restoration service unit having an access authority for accessing a file system of each of the at least one or more applications, wherein the backup restoration application accesses the file system of each of the at least one or more applications and then performs the backup and restoration operations on data of each of the at least one or more applications.
Owner:LG ELECTRONICS INC
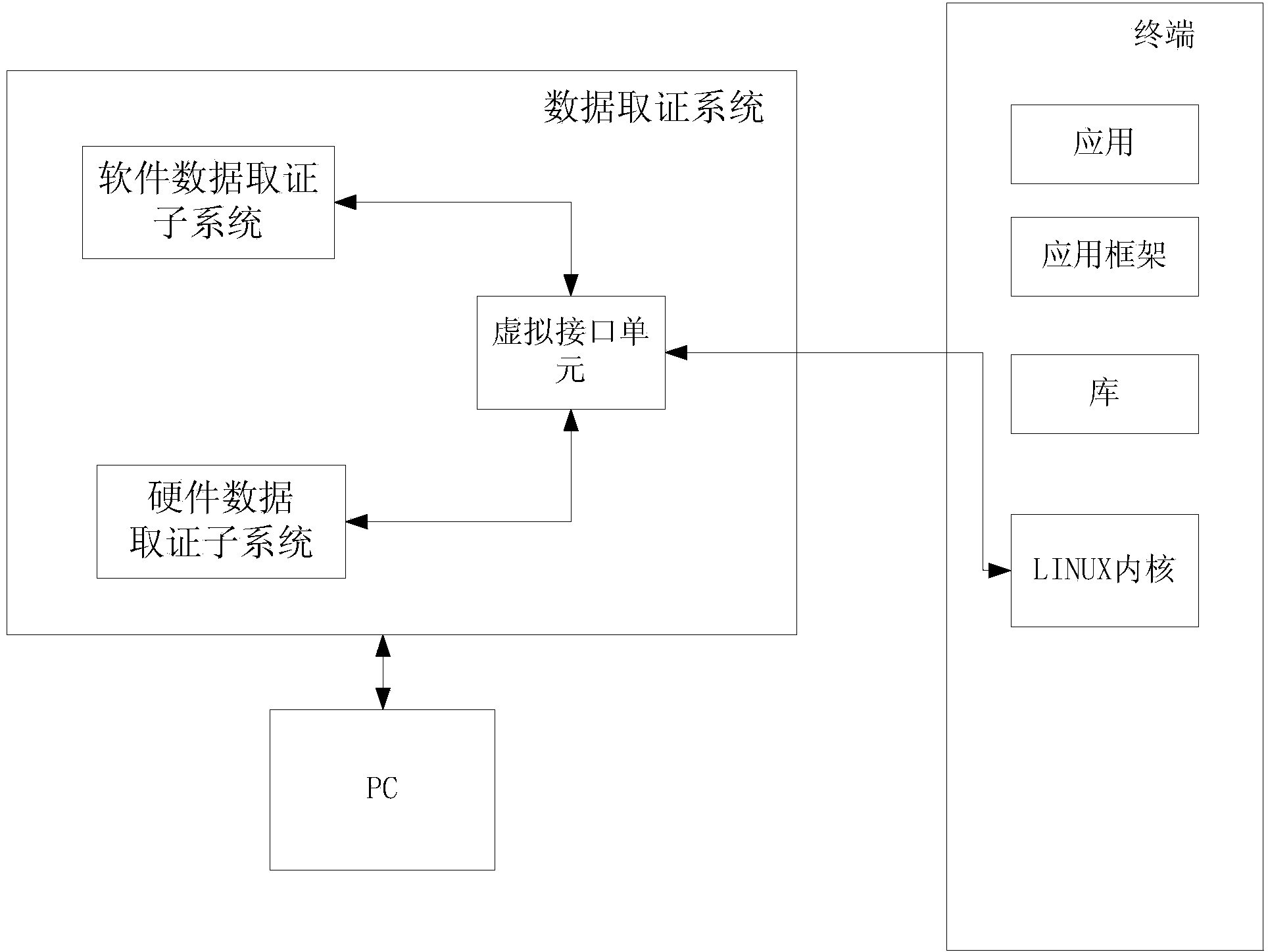
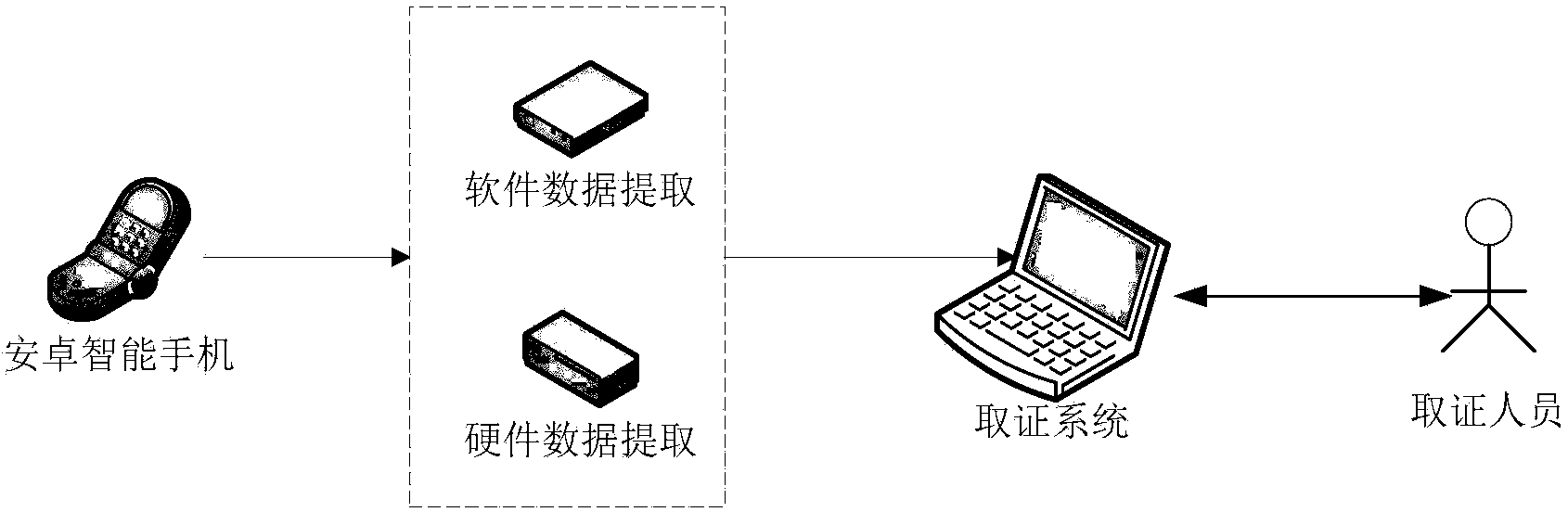
Data evidence obtaining system based on Android
InactiveCN103942054ACompliance with forensicsMeet the requirementsSpecific program execution arrangementsComputer terminalLinux kernel
The invention provides a data evidence obtaining system based on the Android. The data evidence obtaining system based on the Android comprises a virtual interface unit, a software data evidence obtaining subsystem and a hardware data evidence obtaining subsystem. The virtual interface unit is connected with a Linux kernel of the Android of a terminal, a virtual layer is formed between an application framework layer and the Linux kernel of the Android, and the Android using the terminal takes the virtual layer as an application of the Android of the terminal. The software data evidence obtaining subsystem is used for acquiring software data of the terminal. The hardware data evidence obtaining subsystem is used for acquiring chip hardware data of the terminal.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Setting method capable of shortening starting time of Android operating system
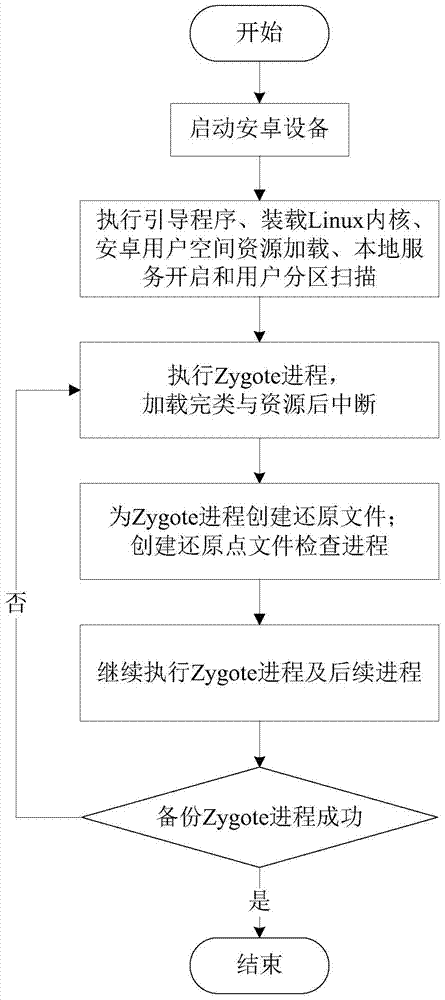
InactiveCN104503788AImprove experienceAvoid duplicationProgram loading/initiatingOperational systemStart time
The invention discloses a setting method capable of shortening starting time of an Android operating system and belongs to the technical field of quick starting of operating systems. The method includes: starting an Android device, executing a bootstrap program, and loading a Linux kernel via the bootstrap program; after Android user space resource loading, local service starting and user partition scanning are executed, executing a Zygote process, after classes and resources needed by an Android virtual machine are loaded, interrupting the process and setting a restore point file for the process, creating a restore point file checking process, setting the restore point file checking process to be started after the bootstrap program loads the Linux kernel, judging whether the restore point file is available or not by the restore point file checking process, and if yes, restoring an Android virtual machine initialization process according to the restore point file; if not, executing the Android virtual machine initialization process. The setting method is applied to the Android devices, and system starting time can be shortened significantly under the premise that user experience is guaranteed.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Android system based on software TCM and trusted software stack and trusted authentication system and method thereof
ActiveCN105718807AImprove securityIncrease inspectionUser identity/authority verificationPlatform integrity maintainanceThird partyTrusted Computing
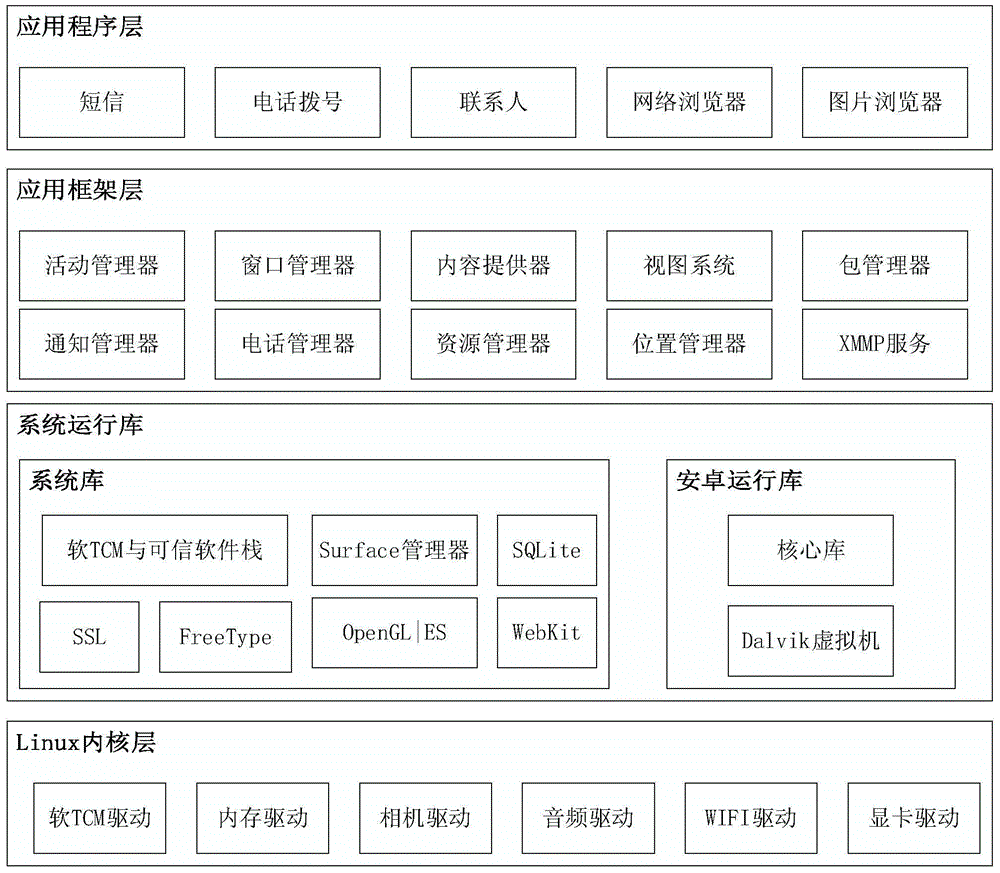
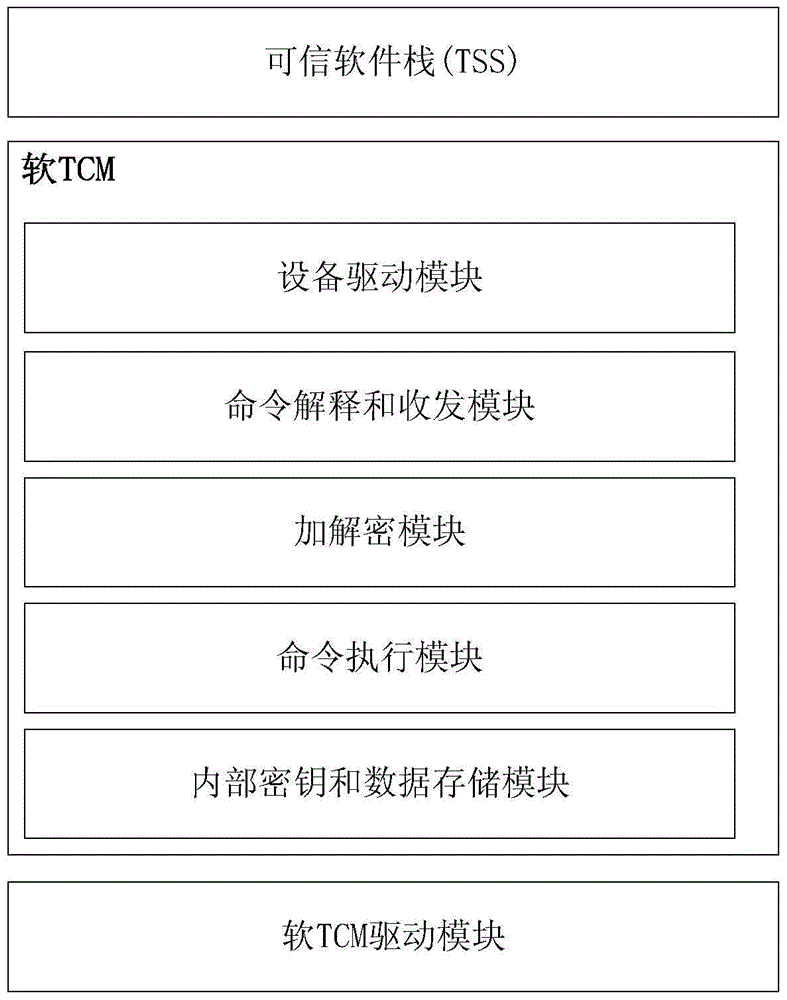
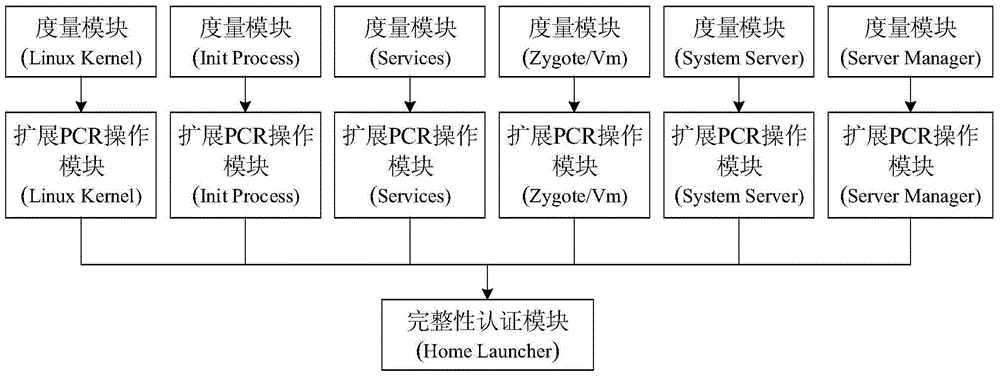
The invention discloses an android system based on software TCM and a trusted software stack and a trusted authentication system and method thereof, and belongs to the technical field of android system and android software safety.The android system comprises the software TCM built on an android core of an existing android system, the trusted software stack and a software TCM driving module; the software TCM and the trusted software stack are embedded into a system library of the existing android system; the trusted software stack is arranged on the software TCM; the software TCM driving module is located on a Linux core layer of the existing android system.The trusted authentication system comprises a trusted authentication system started by the android system and a trusted authentication system installed by the android software.The trusted authentication method includes the steps of the starting trusted authentication process of the android system and the installing trusted authentication process of the android software.According to the android system based on the software TCM and the trusted software stack and the trusted authentication system and method thereof, the integration solution of the safety of the android operating system is achieved based on the trusted computing thought, checkout to the integrity of an android terminal is additionally conducted, protection of a system bottom layer is reinforced, third-party software in the android terminal is also safe and credible, and therefore the android terminal is absolutely safe.
Owner:NORTHEASTERN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com