Patents
Literature
93 results about "Superuser" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, the superuser is a special user account used for system administration. Depending on the operating system (OS), the actual name of this account might be root, administrator, admin or supervisor. In some cases, the actual name of the account is not the determining factor; on Unix-like systems, for example, the user with a user identifier (UID) of zero is the superuser, regardless of the name of that account; and in systems which implement a role based security model, any user with the role of superuser (or its synonyms) can carry out all actions of the superuser account. The principle of least privilege recommends that most users and applications run under an ordinary account to perform their work, as a superuser account is capable of making unrestricted, potentially adverse, system-wide changes.
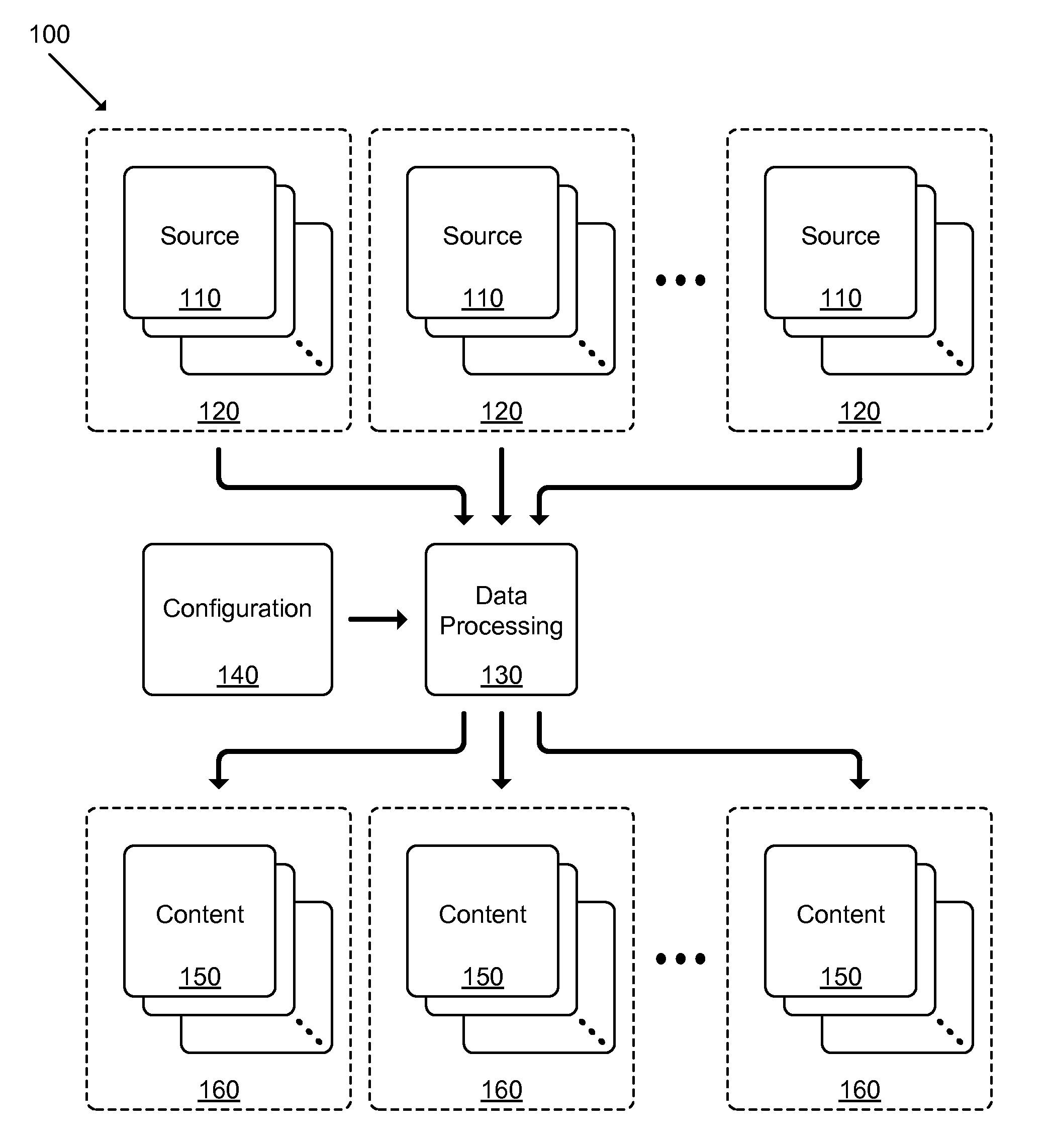
Multi-constituent attribution of a vendor's product catalog
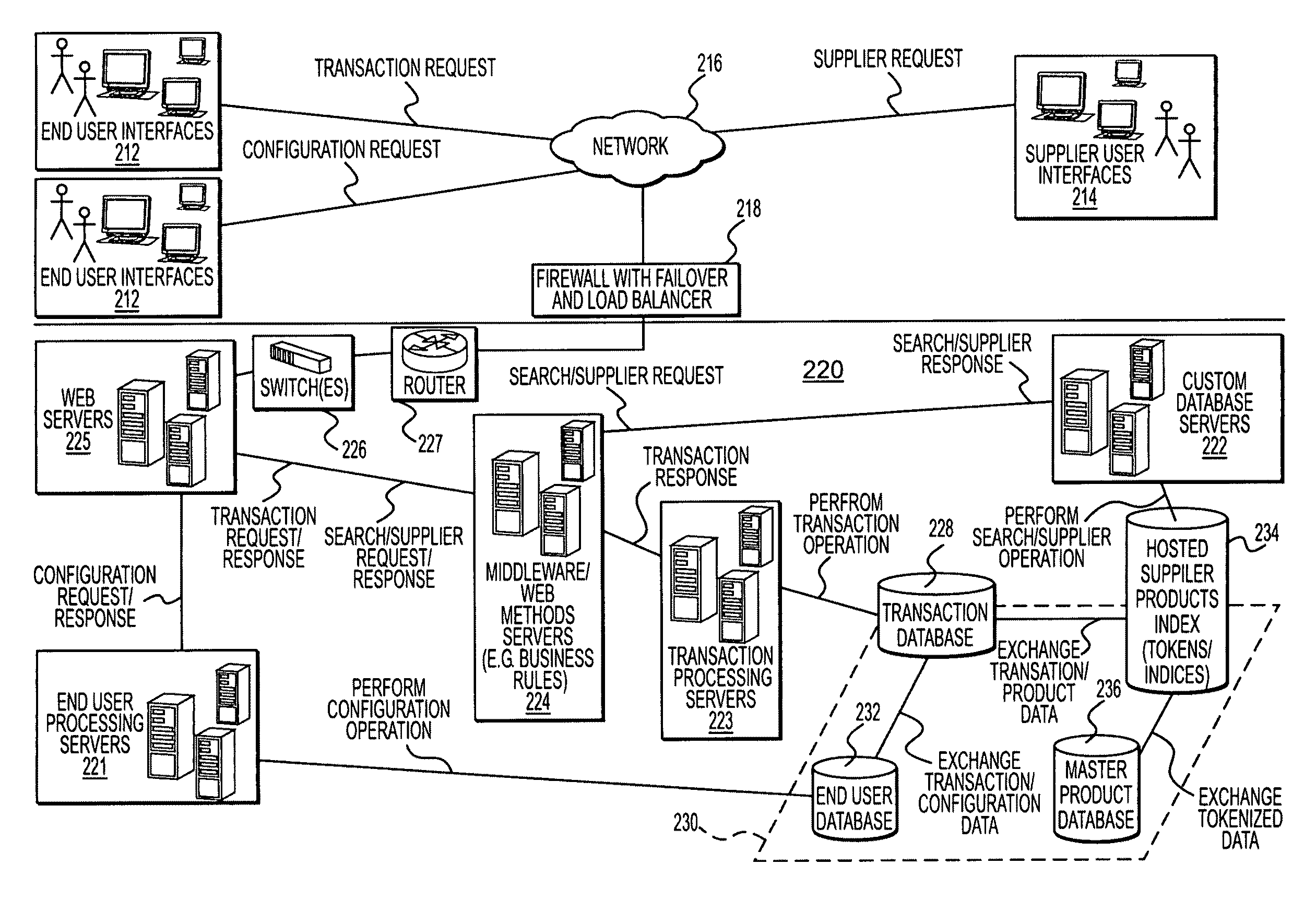
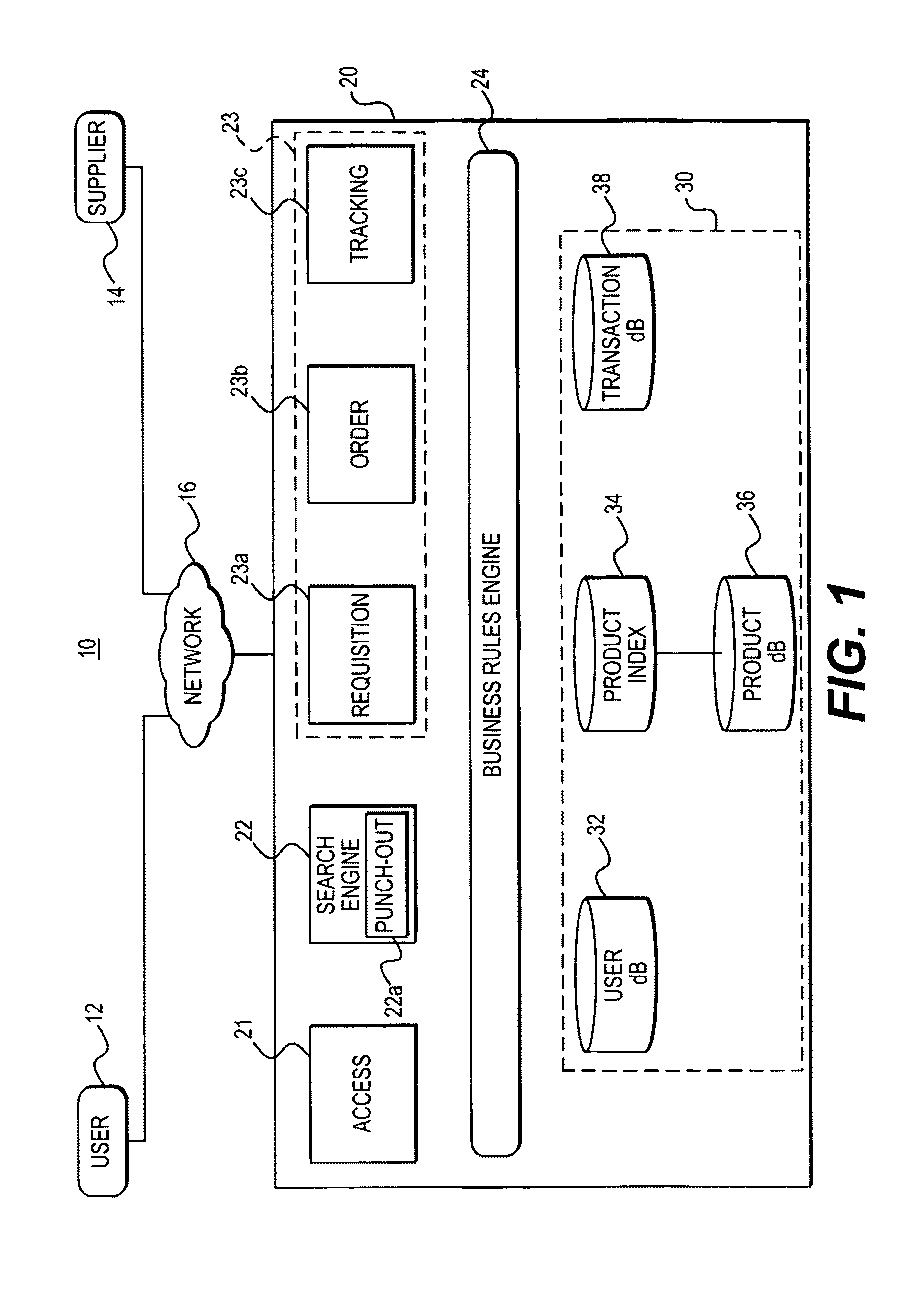
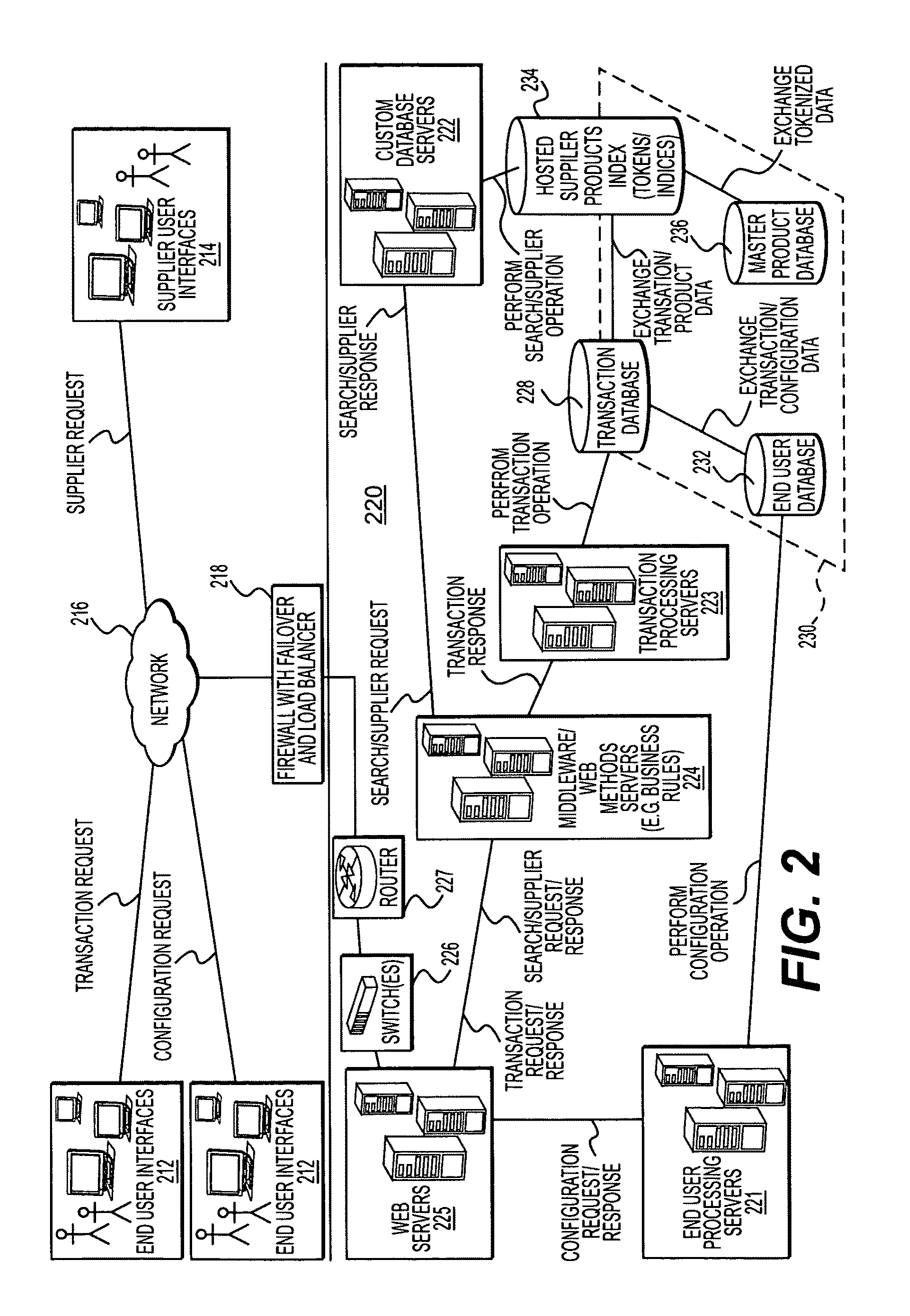
A single instance, multi-tenant procurement system, includes an access module to provide access to a plurality of end users associated with an organization to their respective accounts, each account being customized by a super user of the organization, a search engine to execute searches for products offered by one or more suppliers, a transaction module to process and track one or more requisitions generated by the plurality of end users, a business rules module to apply business rules established between the organization and the one or more suppliers to process the requisitions, and a data repository to store data generated on the system.
Owner:SCIQUEST
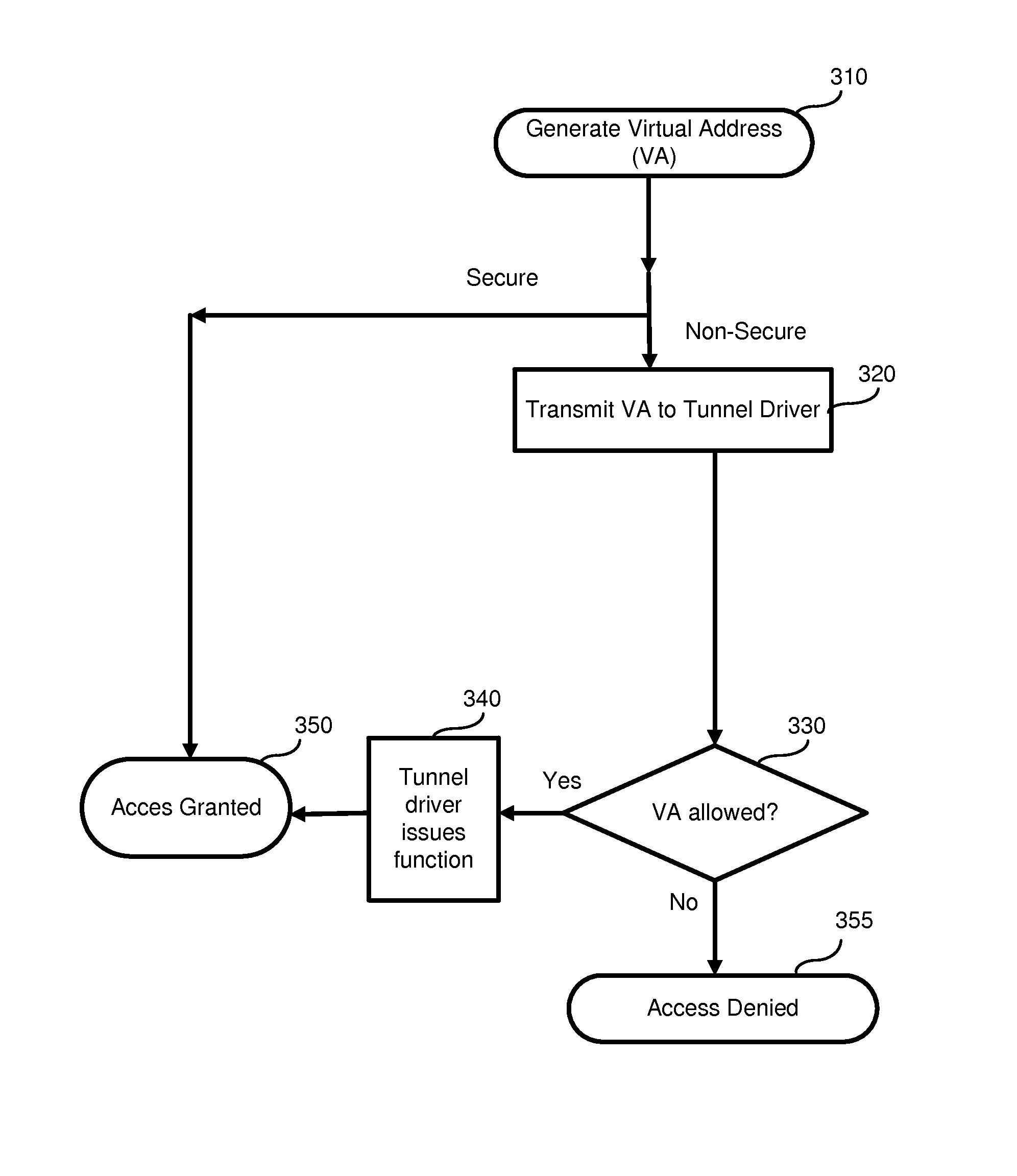
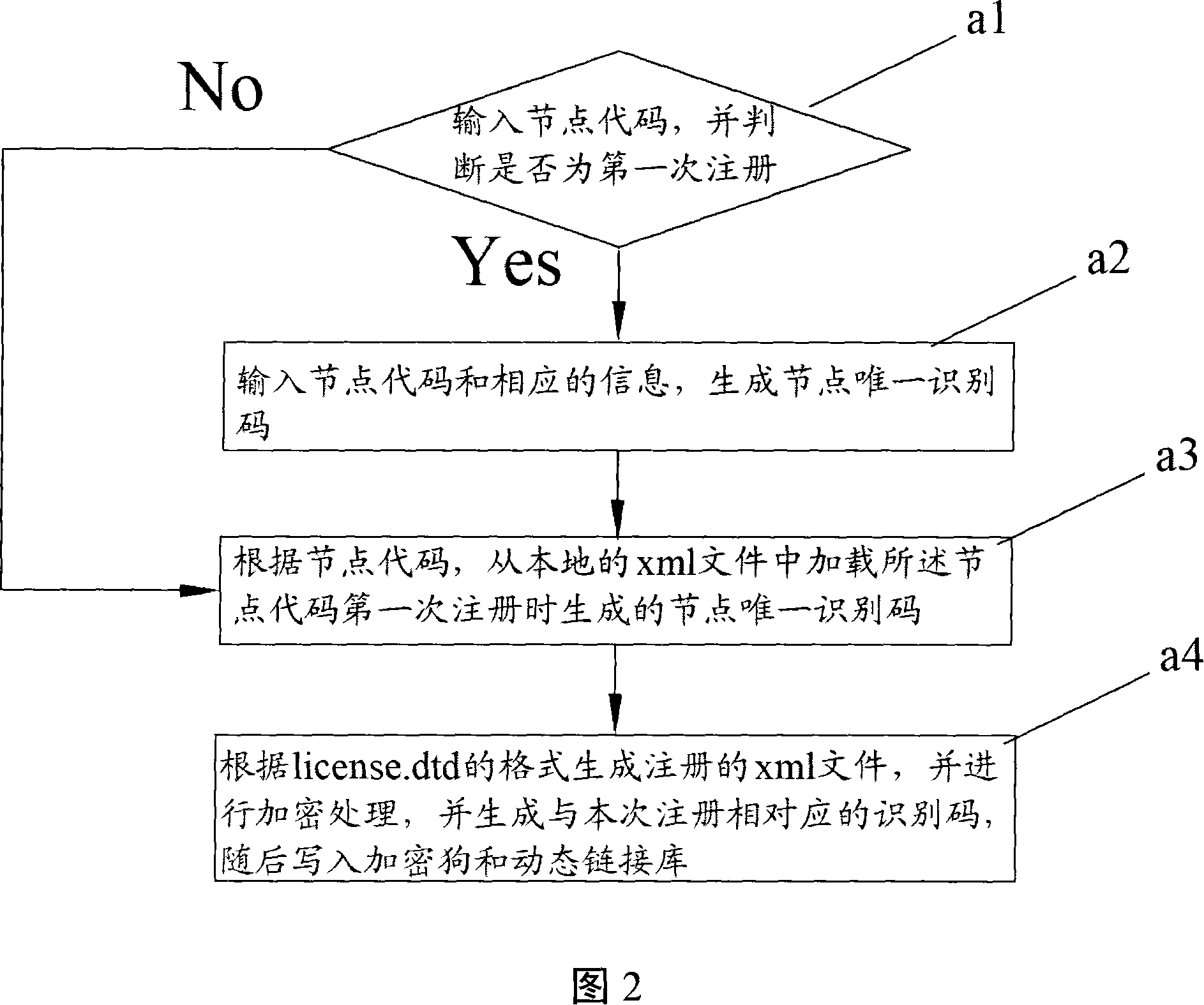
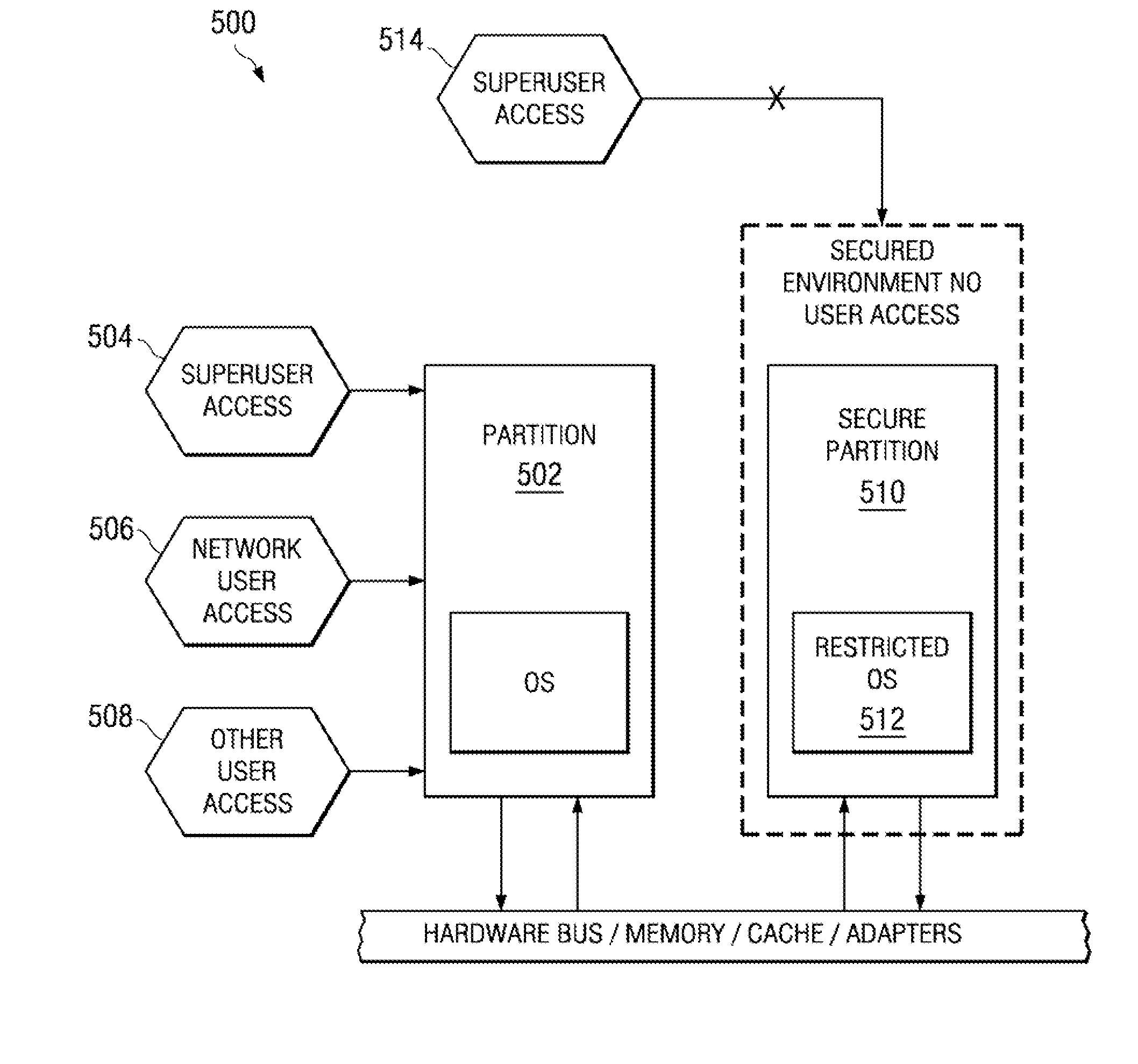
Methodology for secure application partitioning enablement
InactiveUS20090118839A1Memory loss protectionError detection/correctionData processing systemSoftware engineering
A computer implemented methods data processing system, and computer program product for configuring a partition with needed system resources to enable an application to run and process in a secure environment. Upon receiving a command to create a short lived secure partition for a secure application, a short lived secure partition is created in the data processing system. This short lived secure partition is inaccessible by superusers or other applications. System resources comprising physical resources and virtual allocations of the physical resources are allocated to the short lived secure partition. Hardware and software components needed to run the secure application are loaded into the short lived secure partition.
Owner:IBM CORP
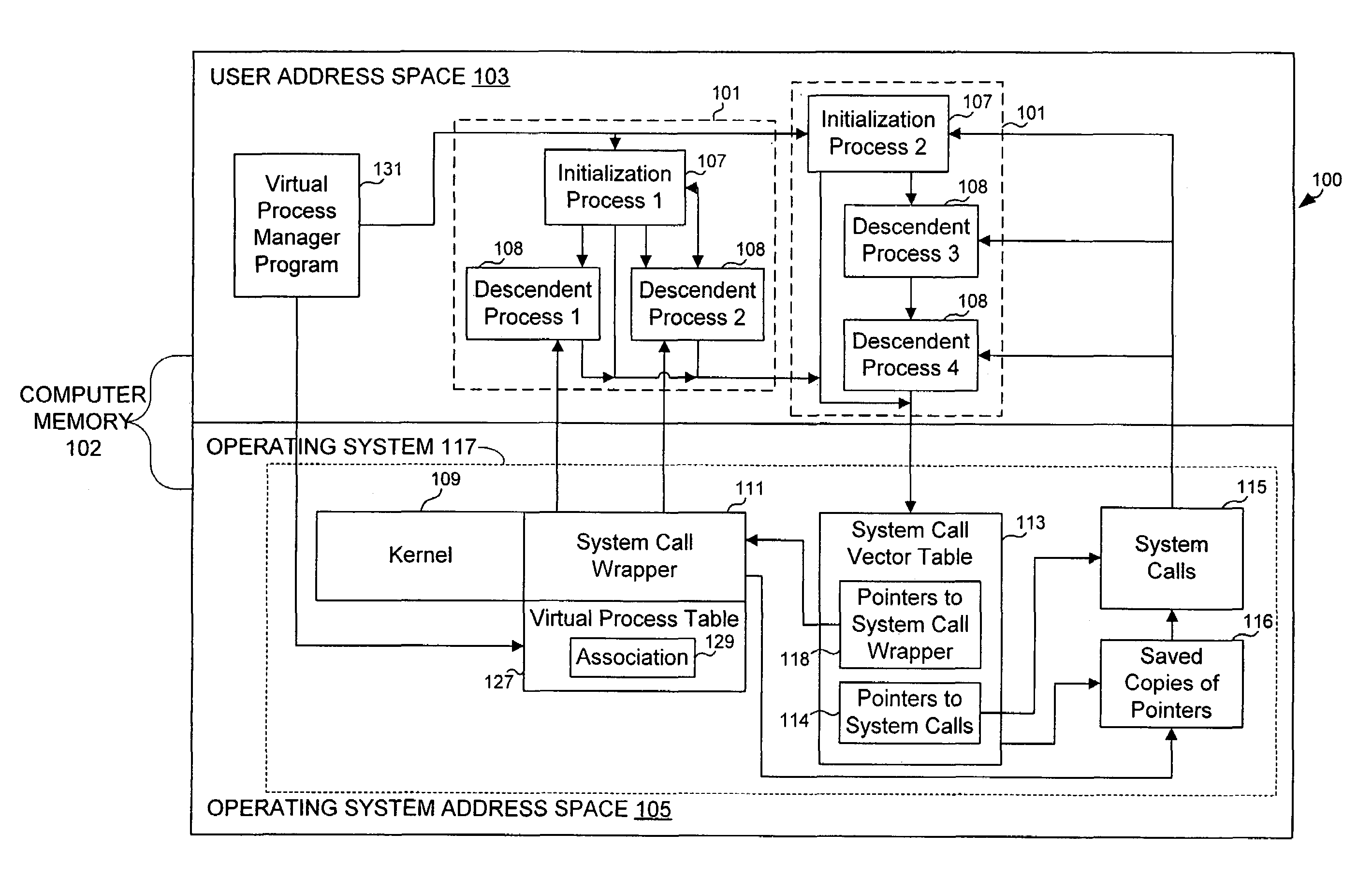
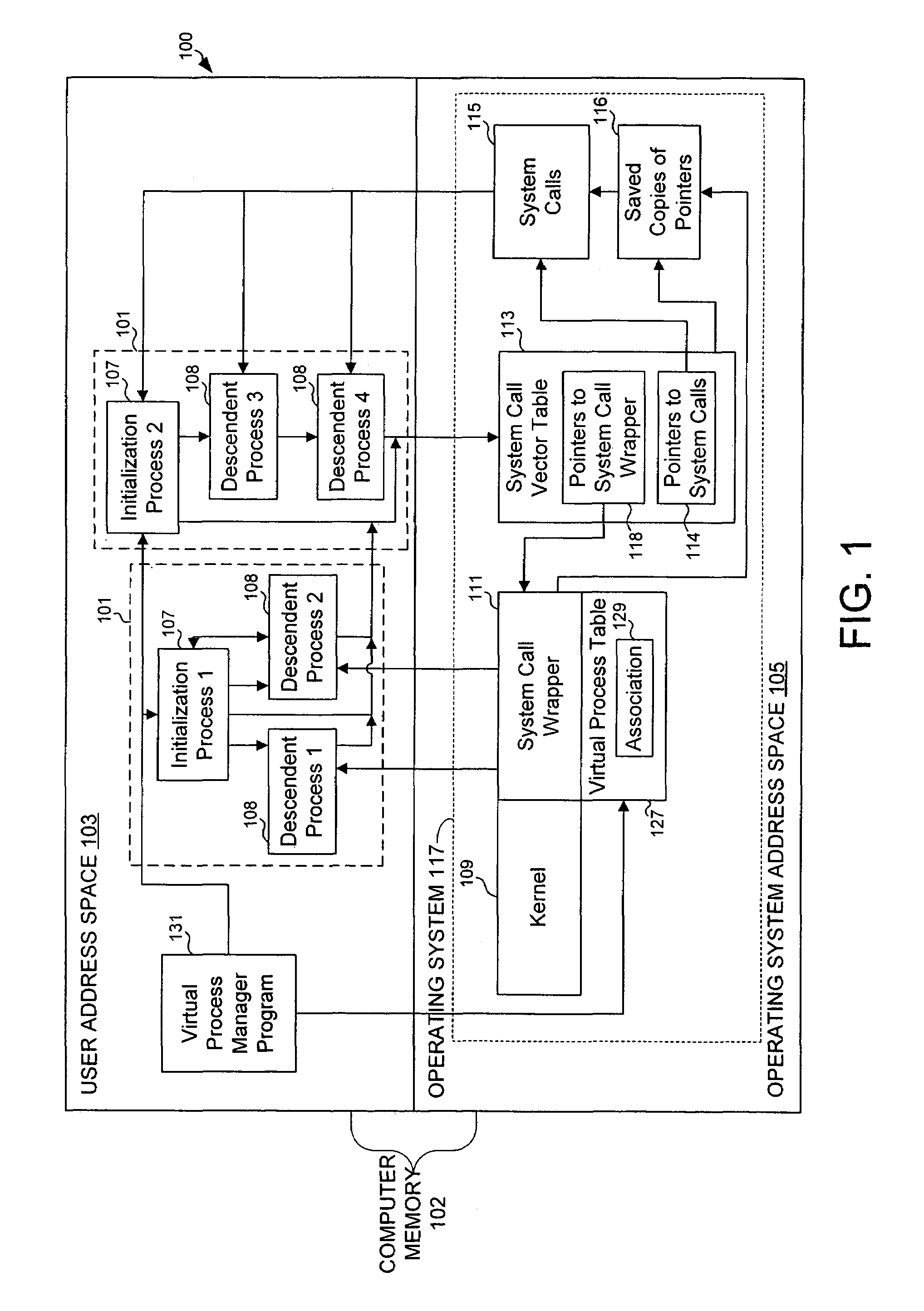
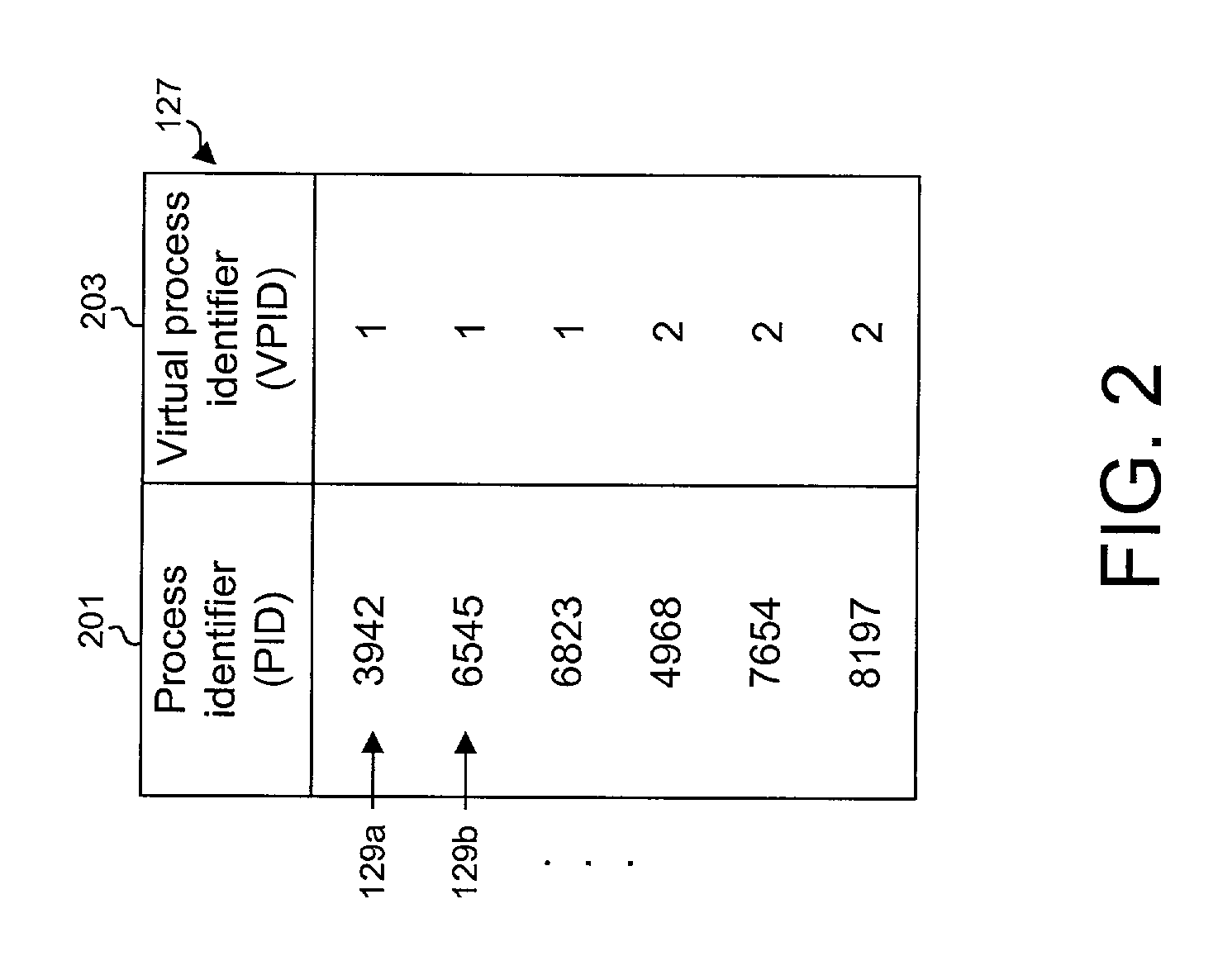
Virtualizing super-user privileges for multiple virtual processes
Super-user privileges are virtualized by designating a virtual super-user for each of a plurality of virtual processes and intercepting system calls for which actual super-user privileges are required, which are nevertheless desirable for a virtual super-user to perform in the context of his or her own virtual process. In one embodiment, a computer operating system includes multiple virtual processes, such as virtual private servers. Each virtual process can be associated with one or more virtual super-users. When an actual process makes a system call that requires actual super-user privileges, the call is intercepted by a system call wrapper.
Owner:CUFER ASSET LTD LLC +1
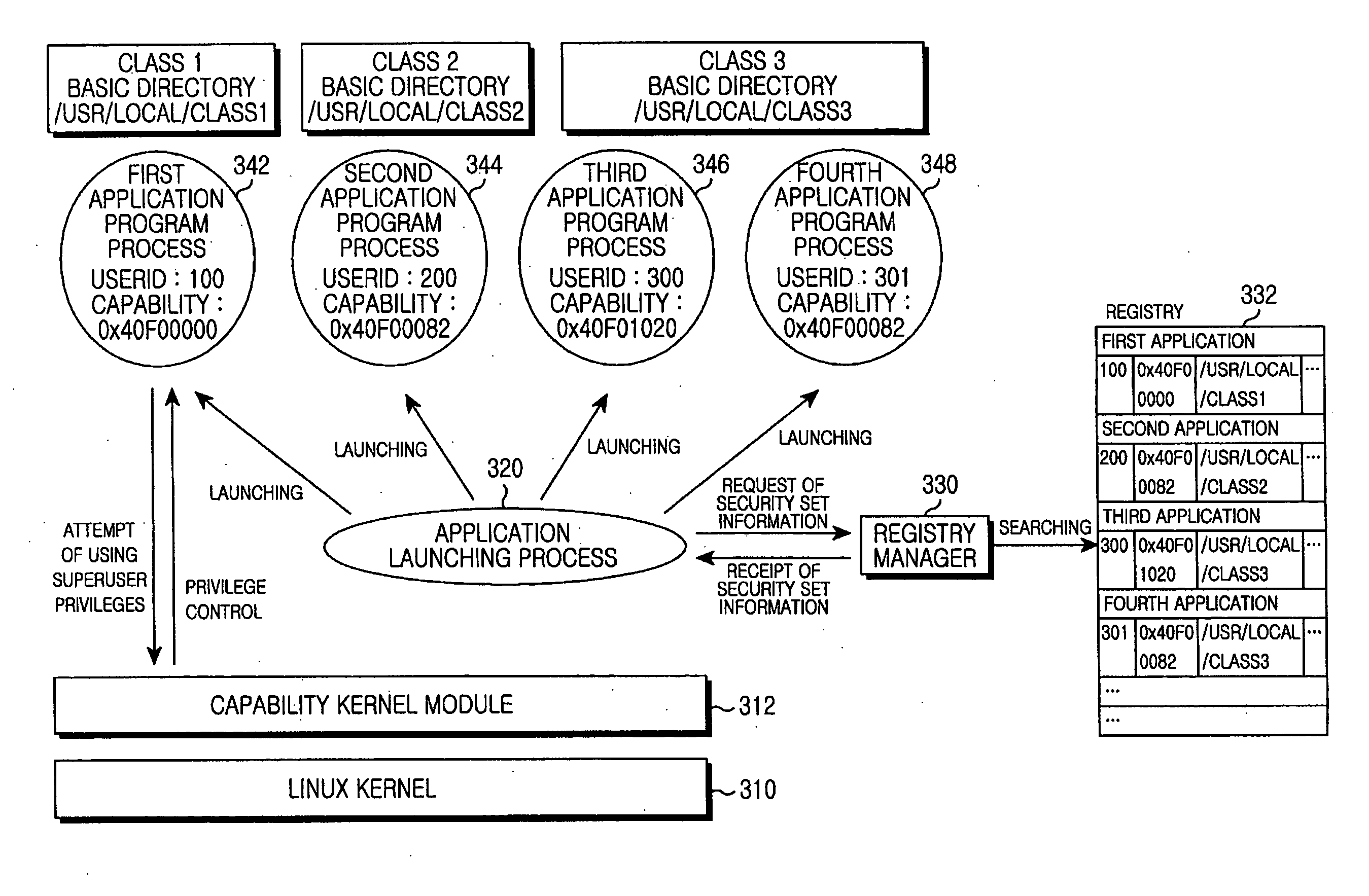
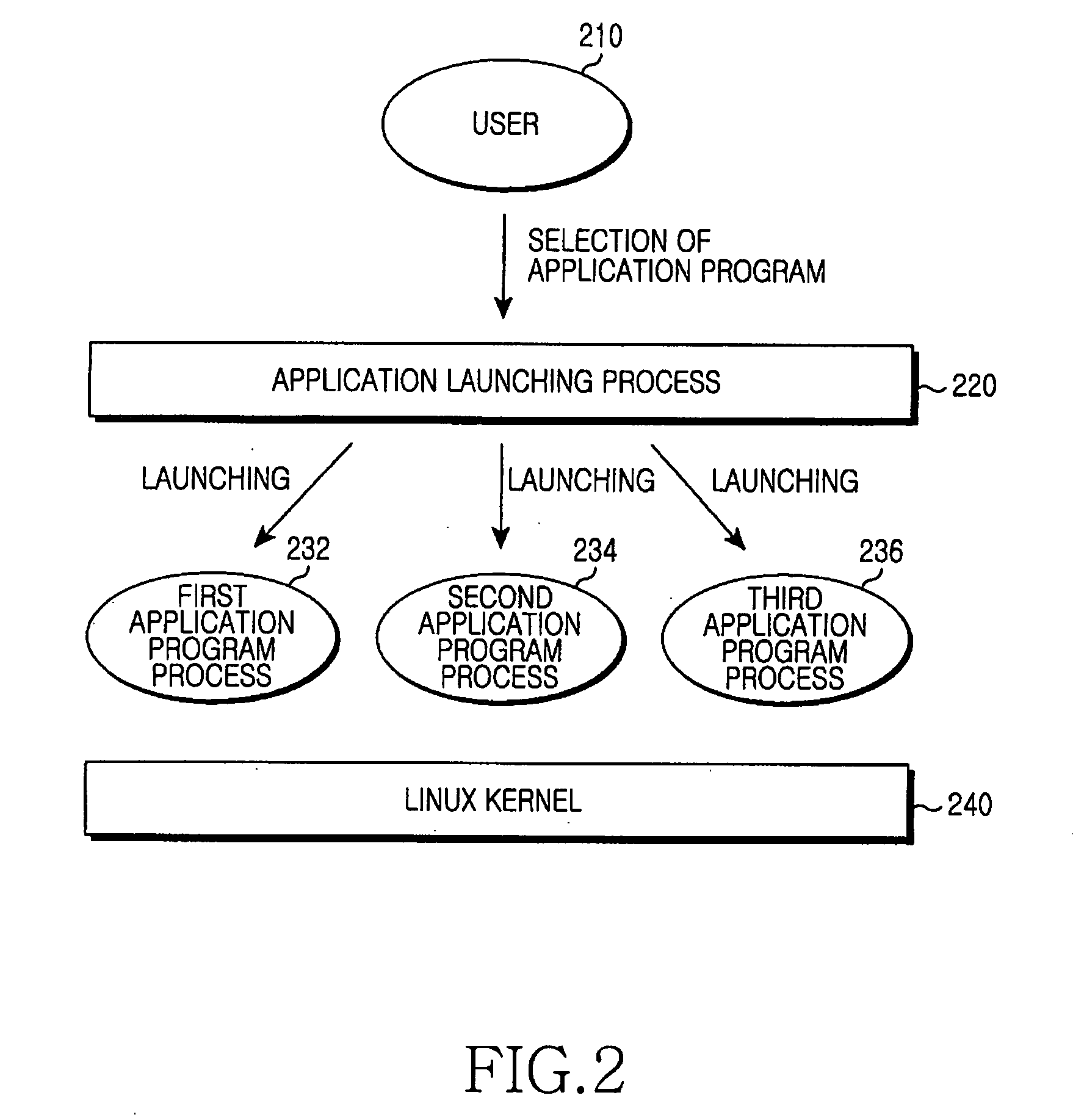
Application program launching method and system for improving security of embedded linux kernel
InactiveUS20080134325A1Digital data processing detailsDigital computer detailsComputer networkLinux kernel
Provided is an application program launching method and system for improving security of an embedded Linux kernel by distributing superuser privileges. The method includes: searching security set information on an application program selected by a user; changing a user account for a processor of the application program to a user ID associated with the application program in the security set information; setting a capability for the processor according to setting information for the capability in the security set information; changing a basic directory for the processor according to a basic directory in the security set information; and launching the application program.
Owner:SAMSUNG ELECTRONICS CO LTD +1
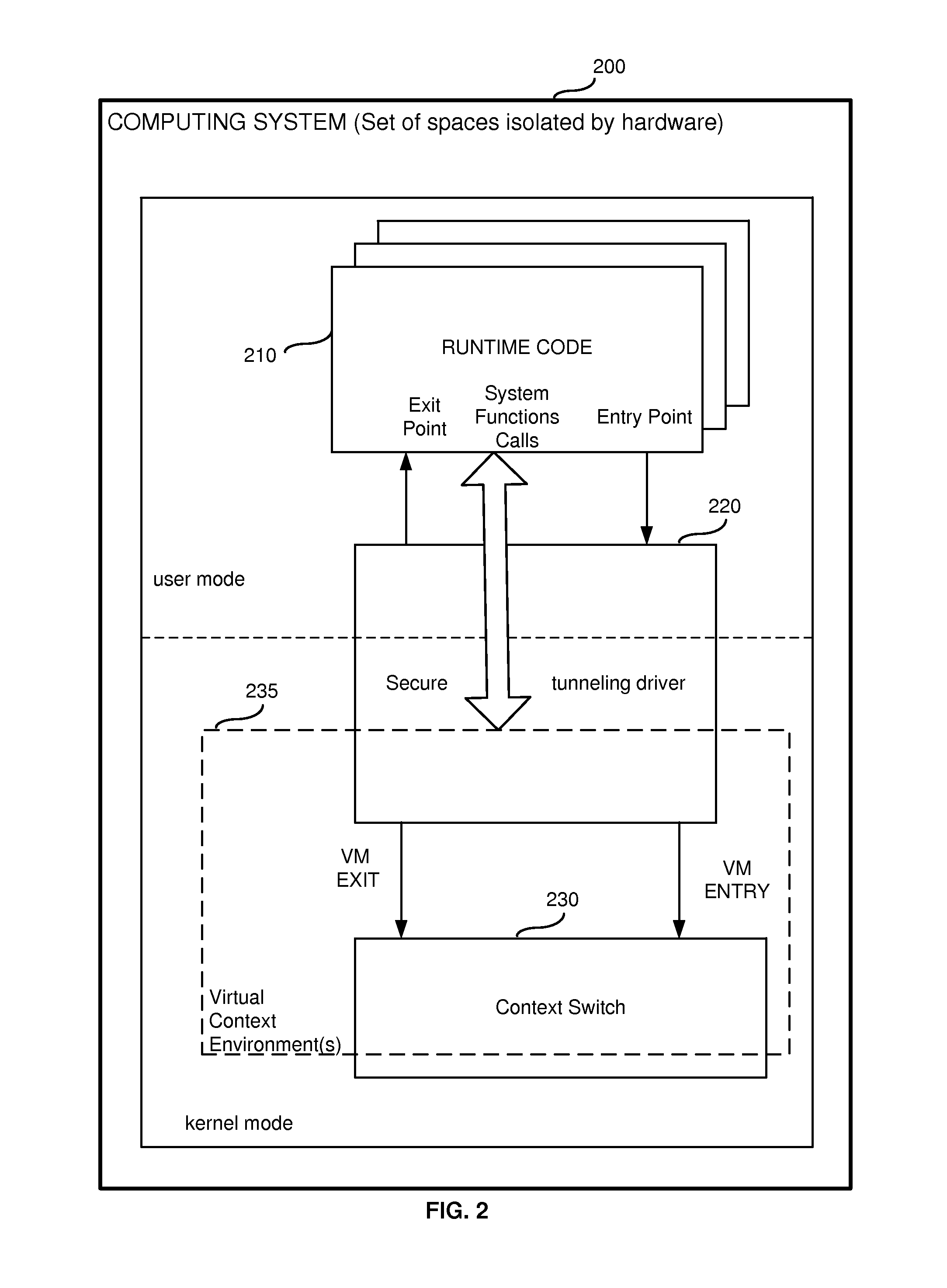
Thin hypervisor for native execution of unsafe code
ActiveUS9274823B1Platform integrity maintainanceSoftware simulation/interpretation/emulationApplication softwareUser modeling
A system, method and computer program product for implementing a thin hypervisor. The thin hypervisor does not have any association with a VM. The thin hypervisor serves as a wrapper over hardware capabilities of a processor. The processor has privileged low-level capabilities EPT VTX, AMD V and the ARM has virtualization technology. In order to use processor hardware capabilities and receiving root privileges, the system operates in a “super user” mode. The VM operates in a VM environment with kernel privileges in a user mode. A super user space is created in a safe mode. A user space application (or a process) is created. A user space virtualization framework library is used. These entities are separated by a user space and a kernel space. A thin hypervisor is implemented in the user space.
Owner:PARALLELS INT GMBH
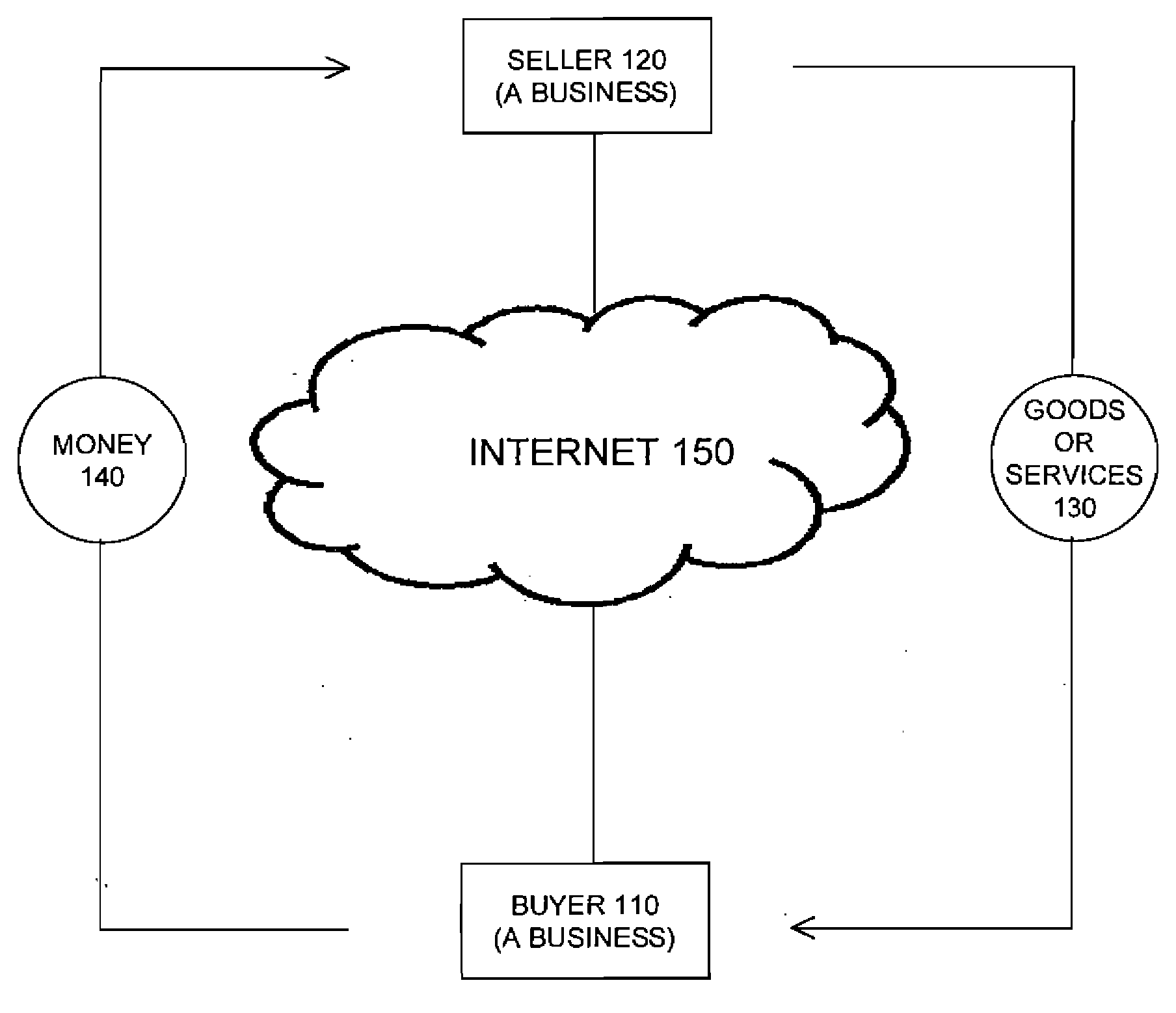
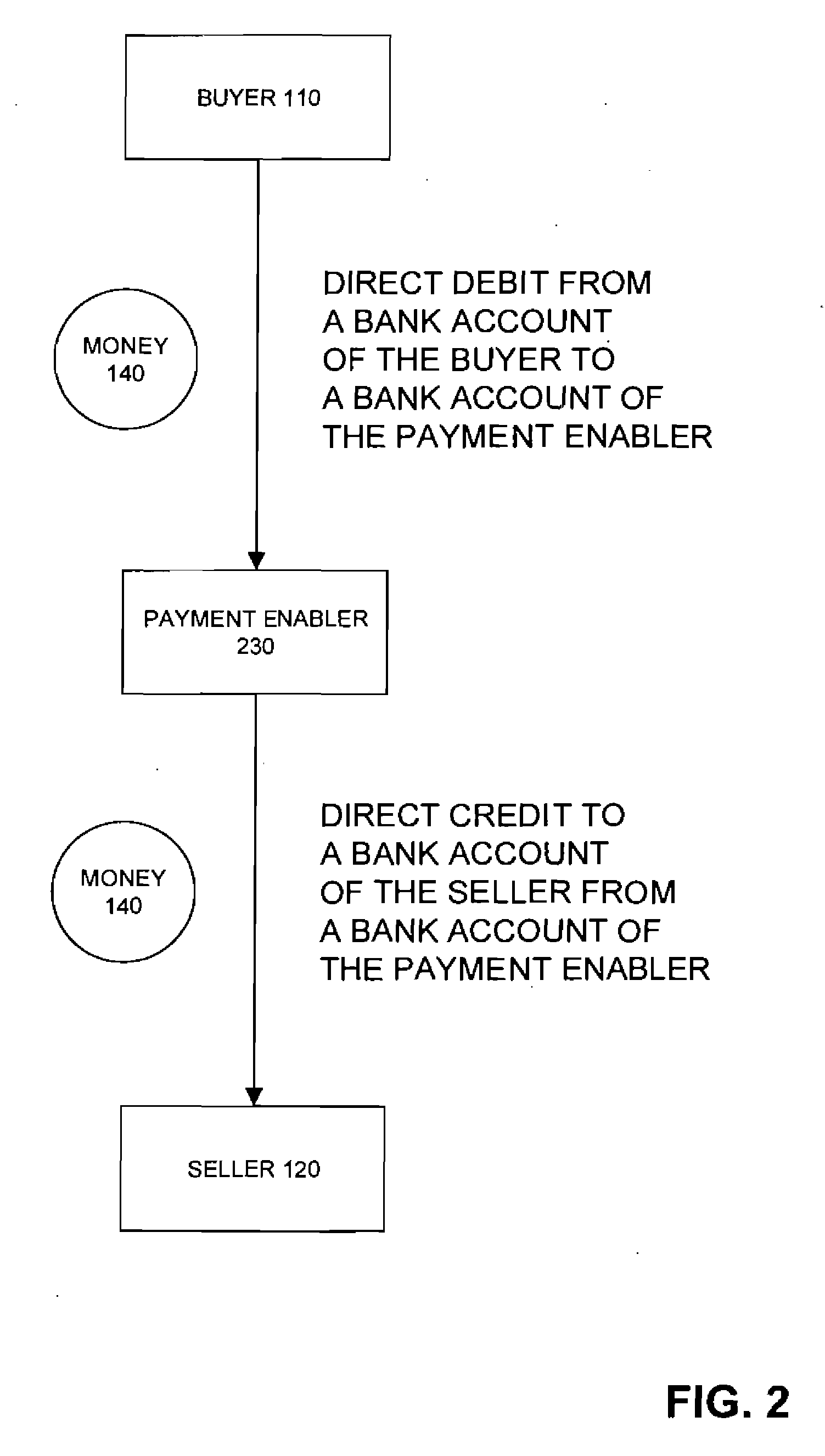
Method and system for transferring money in business-to-business internet transactions
A method for enabling two businesses to complete a transaction that includes payment from one business (the buyer) to another business (the seller). A payment enabler operates the money transfer service over a computer network of nodes, such as the Internet. Typically, the buyer and the seller use the money transfer service of the payment enabler to consummate a transaction that they have arranged over the computer network through a business-to-business transaction facilitator that enables businesses to arrange deals over the computer network. During registration with the payment enabler, a buyer typically provides information about a bank account from which the seller will be paid, and the seller typically provides information about a bank account for receiving the funds from the buyer. The payment enabler facilitates payments for transactions between businesses by enabling the employees of a business registered with the payment enabler to direct the various phases of the payment process on behalf of the business for which those employees work. A super user employee, identified by the business during registration with the payment enabler, has the power to register other employees of the business with the payment enabler and to specify the privileges that the payment enabler should grant each employee to act on behalf of the business.
Owner:THE WESTERN UNION CO
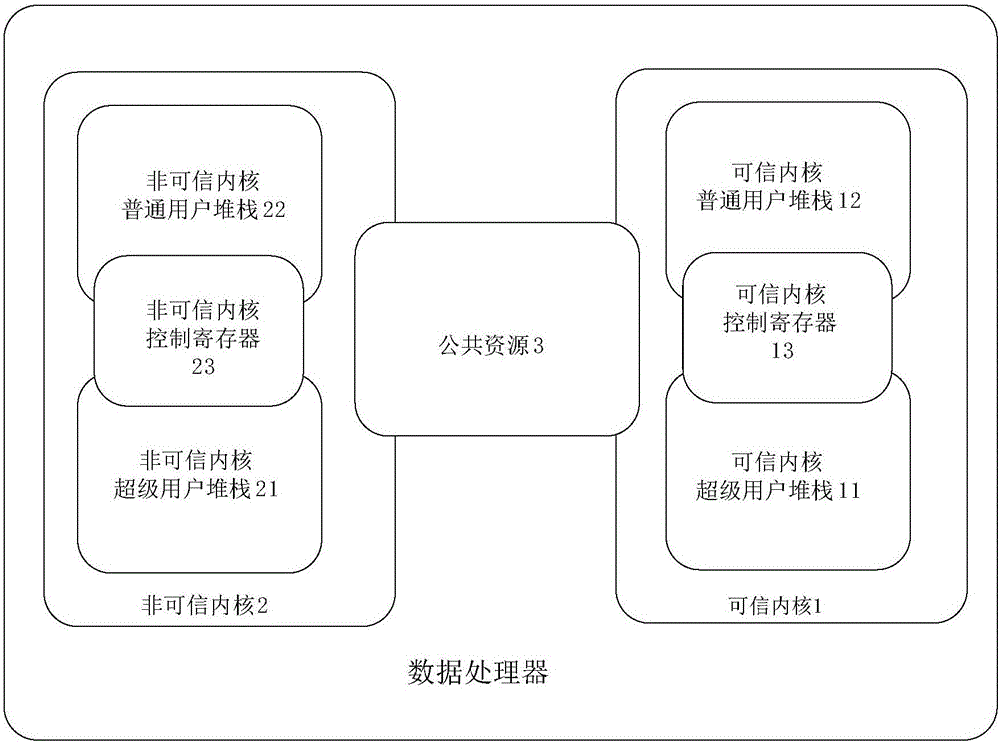
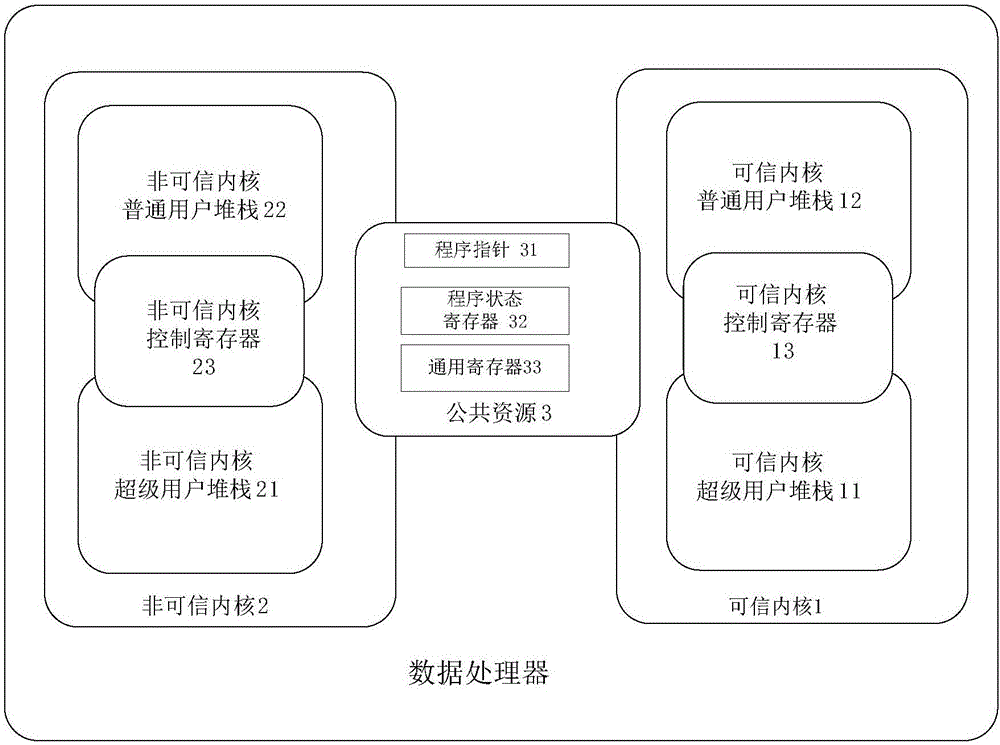
Data processor
ActiveCN106599717ASimple and efficient operationDigital data protectionInternal/peripheral component protectionProtection mechanismControl register
The invention provides a data processor. The data processor comprises a trusted kernel and a non-trusted kernel. The trusted kernel comprises a trusted kernel normal user stack, a trusted kernel superuser stack and a trusted kernel control register. The non-trusted kernel comprises a non-trusted kernel normal user stack, a non-trusted kernel superuser stack and a non-trusted kernel control register. The trusted kernel and the non-trusted kernel share public resources, and the public resources can be accessed by the trusted kernel and the non-trusted kernel. According to the data processor, an underlying hardware protection mechanism is provided for data security through design of a virtual kernel, and a user mode of a current kernel does not need to be considered in a process of returning to the current kernel through a mechanism for storing current scenes in the current kernel superuser stack in a unified way during kernel switching, so that the stack operation is simplified and efficient.
Owner:C SKY MICROSYST CO LTD
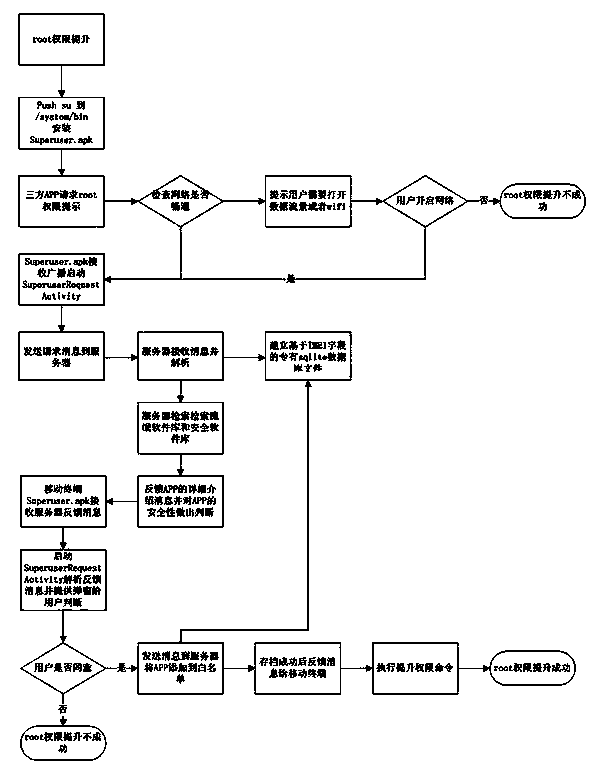
Method and mobile terminal for realizing root request management through manufacturer server
ActiveCN103747433AInteractiveElevate root privilegesSecurity arrangementNetwork data managementDatabase fileBlack list
Owner:天津汇智网络科技有限公司
Application program blocking method and device
InactiveCN105512549AReduce occupancyAvoid consumptionComputer security arrangementsComputer terminalSuperuser
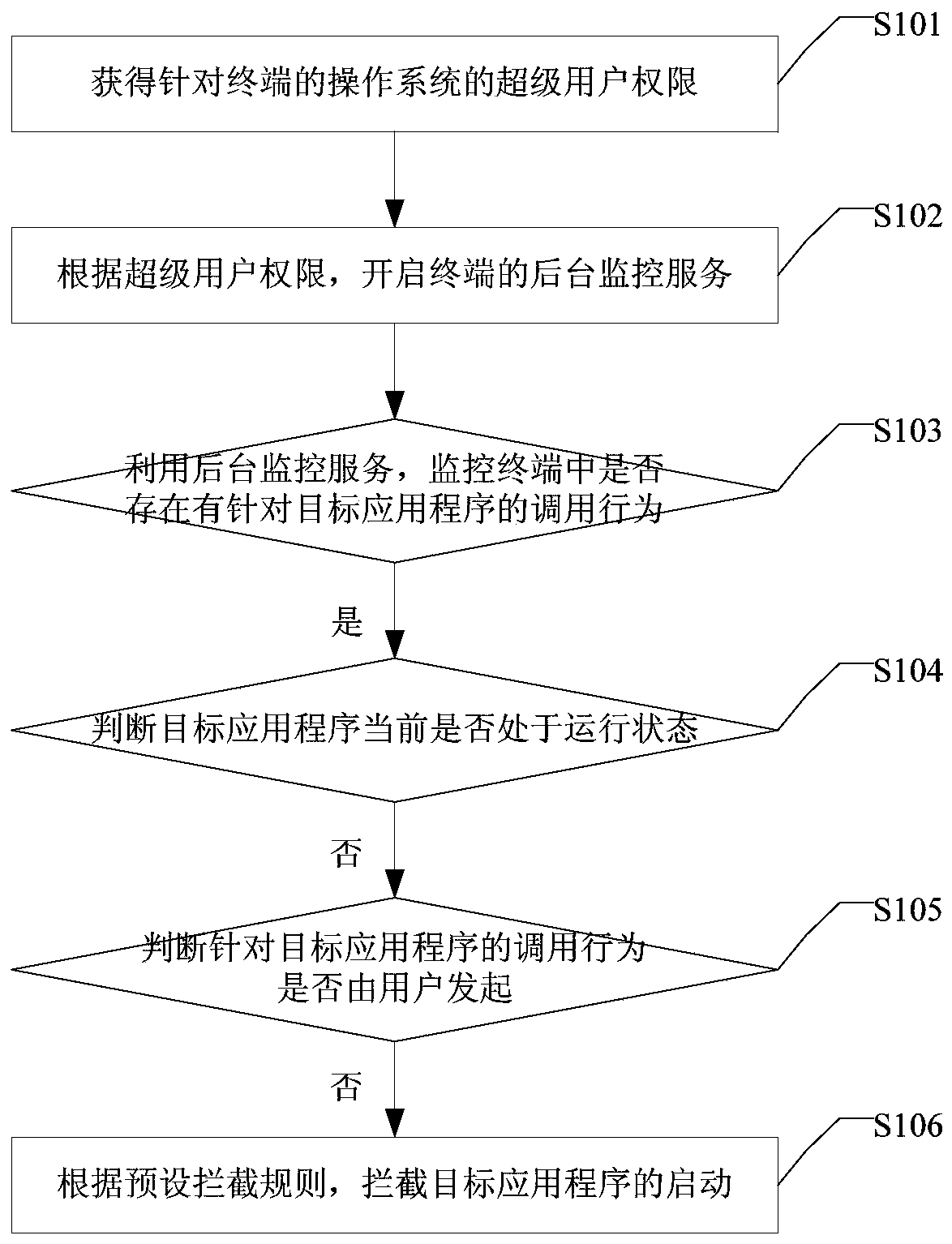
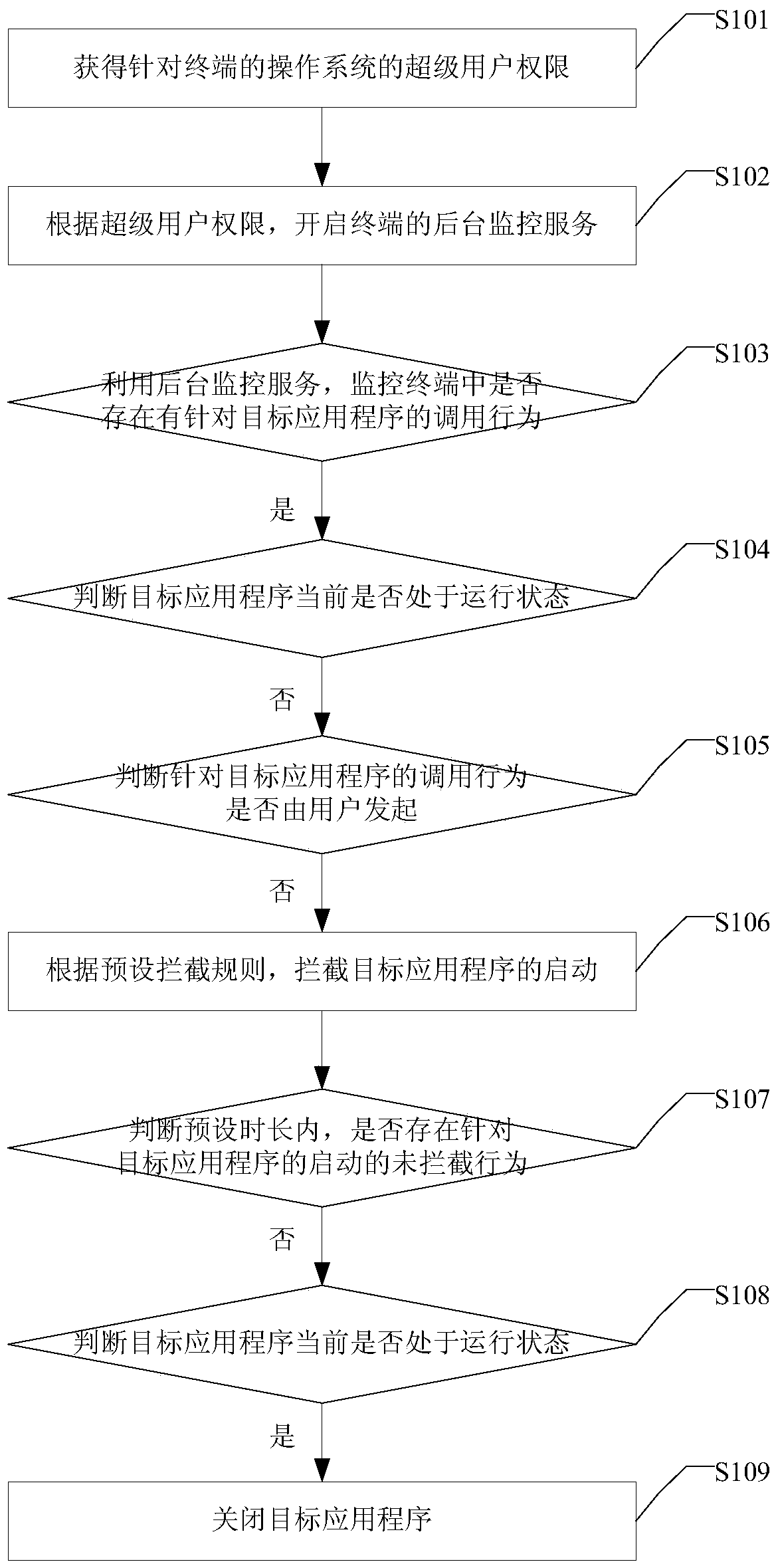
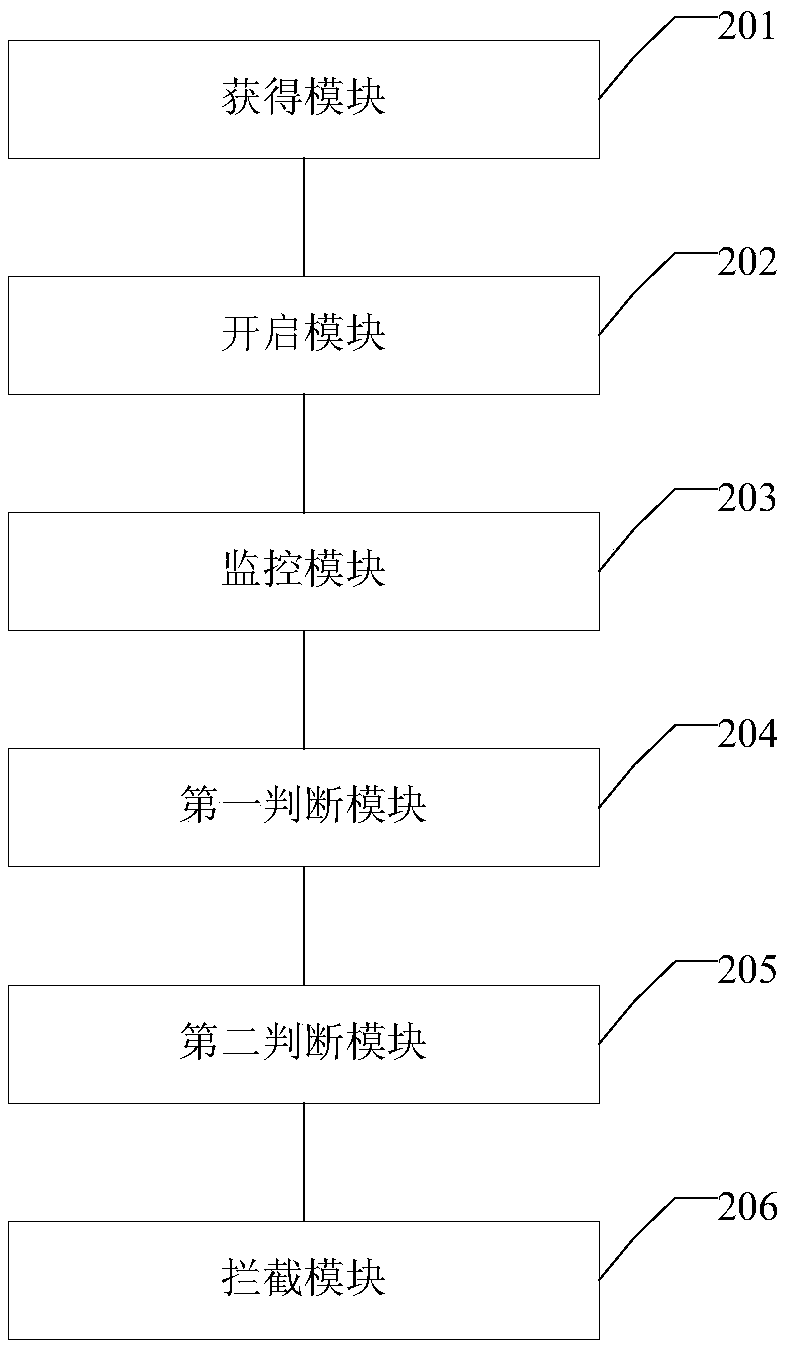
The embodiment of the invention discloses an application program blocking method and device. The method comprises the steps that a superuser permission aiming at an operating system of a terminal is obtained; a background monitoring service of the terminal is started according to the superuser permission; whether a calling behavior aiming at a targeted application program exists in the terminal or not is monitored by means of the background monitoring service; if yes, whether the targeted application program is in a running status or not at present is judged; if the targeted application program is not running at present, whether the calling behavior aiming at the targeted application program is started by a user or not is judged; if not, starting of the targeted application program is blocked according to preset blocking rules. According to the application program blocking method and device, whether the calling behavior according to the targeted application program needs to be blocked or not is judged, if yes, starting of the targeted application program is blocked, occupancy of storage space in a system is saved, and consumption of user traffic is avoided.
Owner:ZHUHAI BAOQU TECH CO LTD
Android one-key root permission software
InactiveCN103324482AImprove the odds of successReasonable structureSpecific program execution arrangementsInformation searchingModel Number
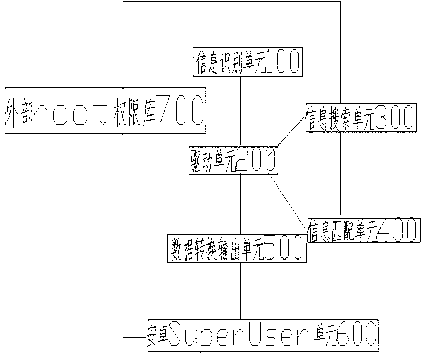
The invention discloses android one-key root permission software and relates to the field of software invention. The android one-key root permission software comprises an information identification unit, a driving unit, an information searching unit, an information matching unit, a data converting and outputting unit and an Android Superuser unit, wherein the driving unit is connected with the information identification unit, the information searching unit, the information matching unit and the data converting and outputting unit, the information searching unit is connected with the information matching unit, the data converting and outputting unit is connected with the Android Superuser unit, and the information searching unit is connected with an external root permission library. By the design, a driver and root software are combined, success rate for operation is increased; the root software is in matched connection with the root permission library, so that corresponding files can be selected according to models of mobile phones, and android one-key root permission software is precise, stable and durable.
Owner:迅尔捷供应链管理(苏州)有限公司
Dynamic, customizable, controlled-access child outcome planning and administration resource
A cloud-based access to child care planning and outcome resource is described. The resource allows multiple end-users to access content related to child care. Such content includes reports, table, graphs, multimedia, lists, forms, reminders, and / or other appropriate elements. The content may be presented via one or more graphical user interfaces (GUIs). Each such GUI may include various input elements such as tabs, buttons, icons, etc. and various content elements such as portlets, or frames, etc. Each GUI may be customized for a particular end-user and / or a particular group of end-users. In this way, an administrator or super-user may generate multiple GUIs, where each is associated with a user group (e.g., parents, teachers, administrators, etc.). In addition, each end-user may be able to customize the GUIs available to the end user. Such customization may include selection of input and / or content elements, layout of elements, graphical features, and / or other appropriate customizations.
Owner:NULINX INTL
Authorization control method aimed at server
InactiveCN101119207AHigh encryption strengthImprove reliabilityUser identity/authority verificationDependabilityAuthorization
The present invention relates to an authorization controlling method aiming at the servers. The present invention controls the quantity of the users who are using the servers, solves the problem that the control of the server admitting authorization is easy to be cracked, realizes the controls of the users with different categories, namely the quantity of the super users, the quantity of the data maintaining users, the quantity of the VIP users and the quantity of the normal users who are on line; the double restoring of the softdog and the disk document is adopted for the admitting authorizing document restoring medium; a the double validating of the softdog and the local document is also adopted for the validation of the admitting authorizing document and the encrypting methods are used by mixing variety of encryptions so as to elevate the reliability of the authorization.
Owner:北京意科能源技术有限公司
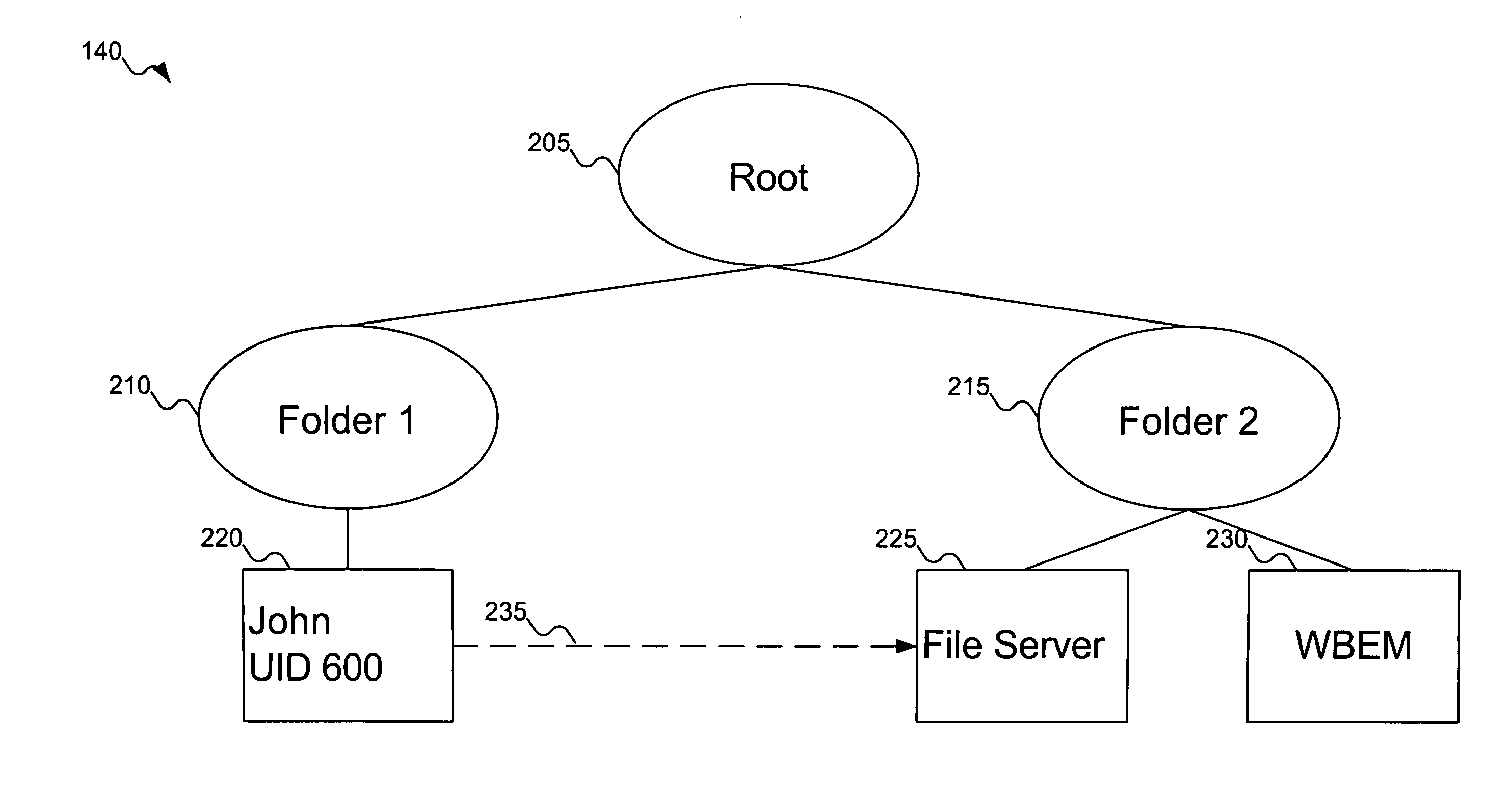
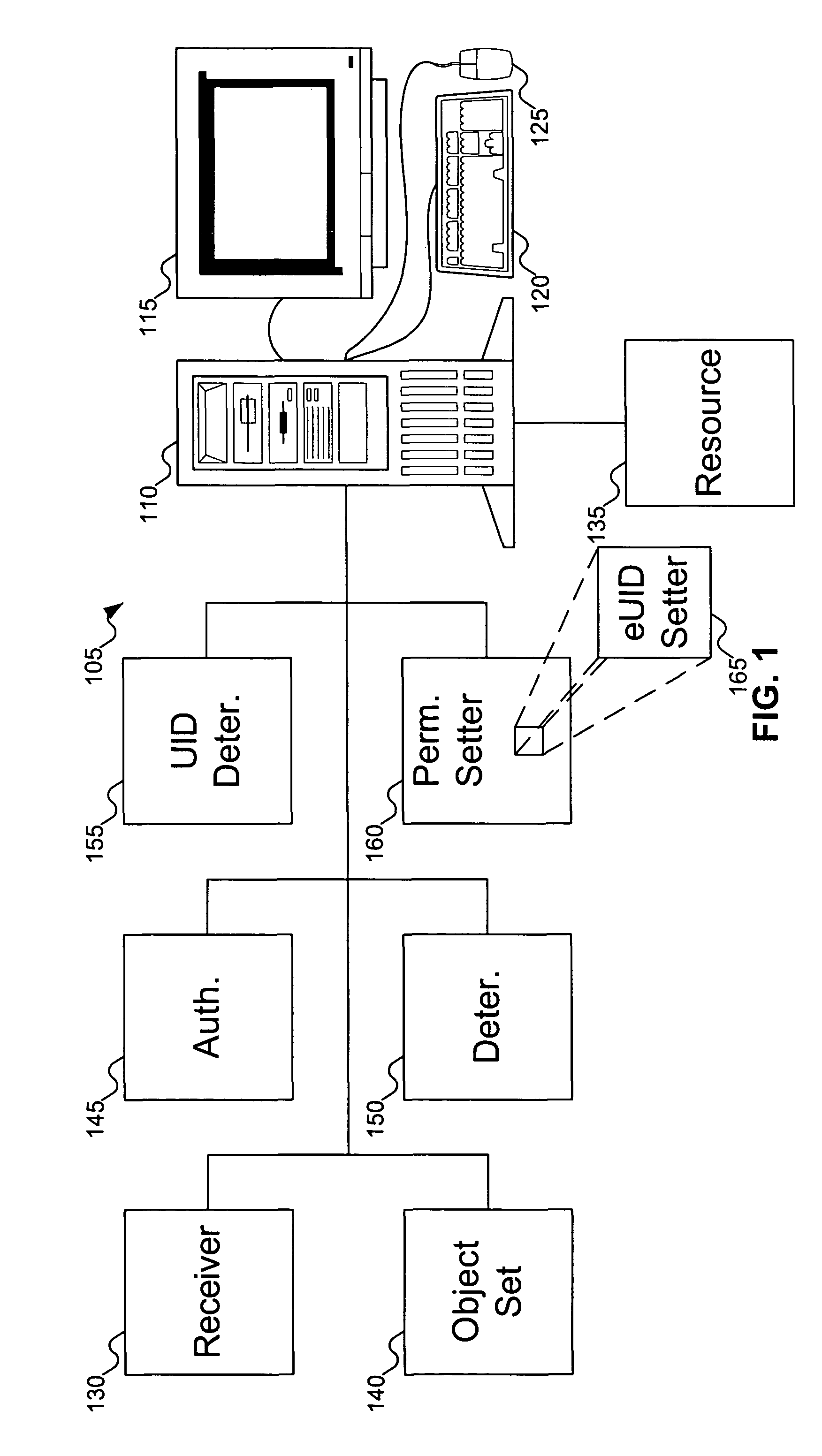
Synthesized root privileges
InactiveUS8271785B1Digital data processing detailsAnalogue secracy/subscription systemsPasswordTechnical standard
Users provide their standard username and password and are authenticated to the system. The system then determines from an object set, such as a container hierarchy, whether the user should have special administrative privileges for any of the resources on the machine to which they are logging in. These administrative privileges can be determined from configurable sets of pre-existing relationships between the user and resources on the system, stored within the object set. If the user is an administrator, then the system sets the UID number for that user to the UID number for administrator users. The system can even be configured to set the administrative UID to be the UID for the super-user “root” (typically, zero). If the user has no administrative privileges, the system sets the UID number for that user to the user's standard UID number.
Owner:NOVELL INC
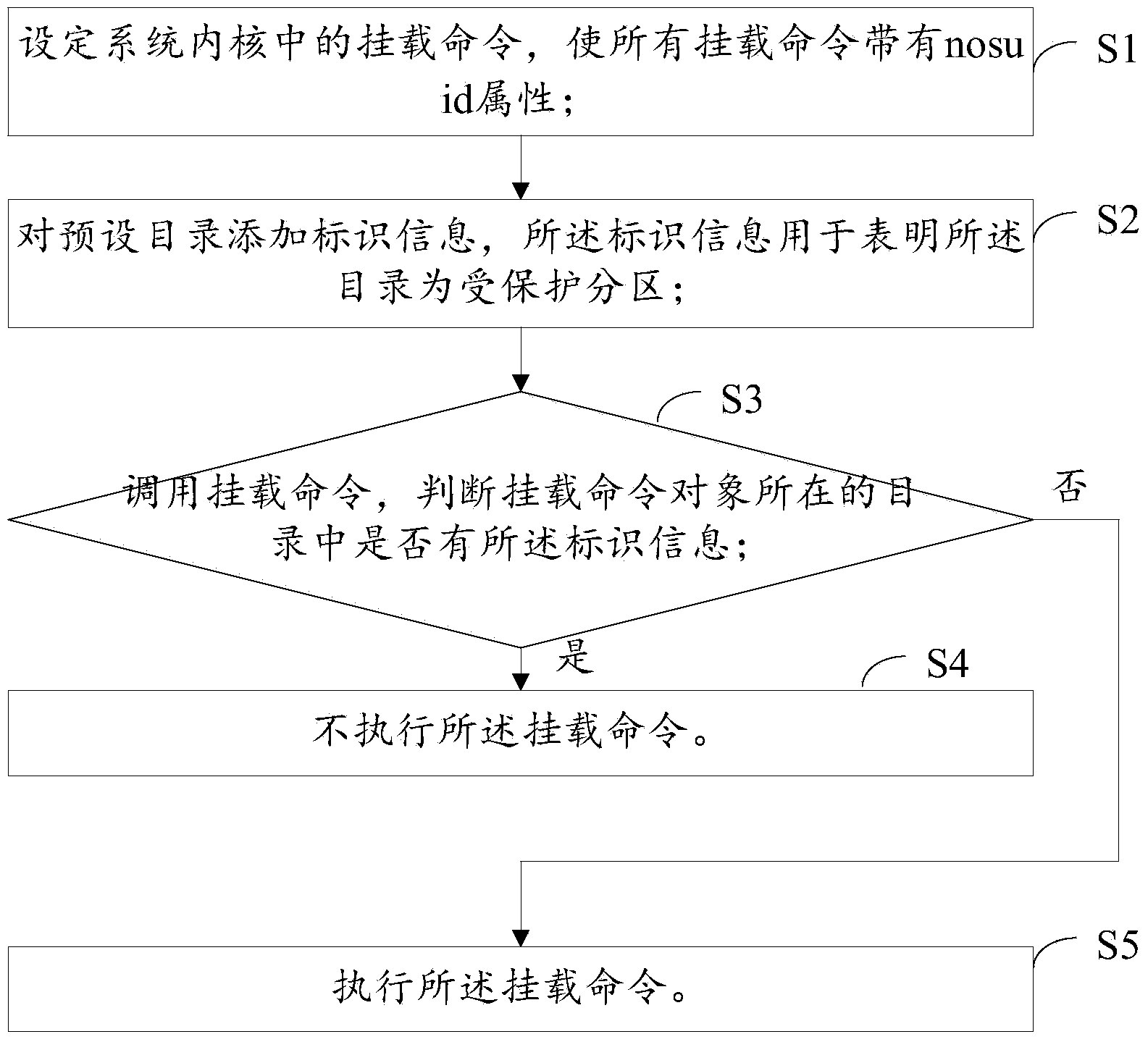
Sub-zone protecting method and device of Android system
ActiveCN104268462AEffective control authority switchingFree from malicious tamperingDigital data authenticationPlatform integrity maintainanceUser PrivilegeComputer science
The invention provides a sub-zone protecting method and device of the Android system. The method comprises the following steps: setting mounting commands in system kernel and enabling all mounting commands carry with nosuid properties; adding identification information to a default directory, wherein the identification information is used for showing that the directory is a protected sub-zone; transferring the mounting commands; determining whether the directory of the mounting command objects contains the identification information; if so, stopping performing the mounting commands; otherwise, performing the mounting commands. According to the technical scheme, the method and device have the advantages that the authority management mechanism is perfected; in addition, the security defense scheme is further set under the condition that vulnerability occurs in the authority management defense; therefore, the user authority switching can be effectively controlled, and meanwhile, the protected sub-area and the file in the protected sub-area can be prevented from malicious tempering; moreover, the sub-zone can be prevented from malicious tempering after the superuser authority is obtained by a special mode.
Owner:银捷尼科(福建)科技有限公司
Methodology for secure application partitioning enablement
InactiveUS8424078B2Memory loss protectionDigital data processing detailsData processing systemApplication software
A computer implemented methods data processing system, and computer program product for configuring a partition with needed system resources to enable an application to run and process in a secure environment. Upon receiving a command to create a short lived secure partition for a secure application, a short lived secure partition is created in the data processing system. This short lived secure partition is inaccessible by superusers or other applications. System resources comprising physical resources and virtual allocations of the physical resources are allocated to the short lived secure partition. Hardware and software components needed to run the secure application are loaded into the short lived secure partition.
Owner:INT BUSINESS MASCH CORP
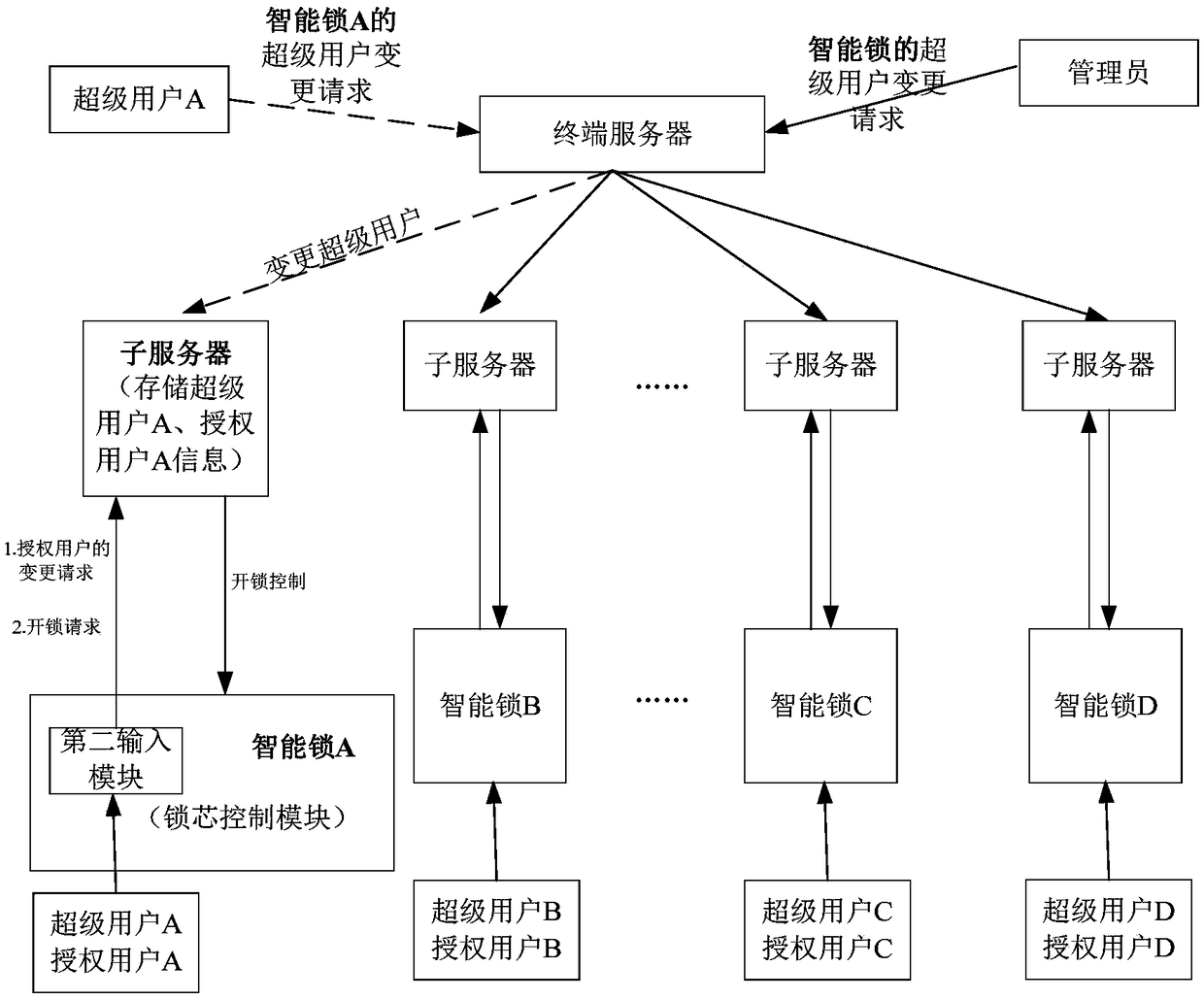
Intelligent lock system
ActiveCN108712389AImprove convenienceEnsure safetyUser identity/authority verificationTerminal serverComputer terminal
The invention discloses an intelligent lock system comprising an intelligent lock terminal and a terminal processing system, wherein the terminal processing system comprises an input module, a terminal server and a plurality of sub-servers; the terminal server is used for storing identity information of super-users corresponding to each intelligent lock and managing the superusers of all intelligent terminals; one sub-server is corresponding to one intelligent lock terminal, and used for performing information management (storing the super-user information and the authorized user information of the intelligent lock, and updating) on the users of the intelligent lock terminal, unlocking verification and recording of unlocking events. The invention is the lock system combined with the intelligent terminal and provided with secondary encryption management, and achieves a transparent security management mechanism; according to the system, the security of the lock under autonomous management can be ensured; convenience of security management of the lock can be achieved; authorization transferring, casual users, paid users and multiple cooperative mechanisms are supported, and thus multiple commercial modes are achieved.
Owner:浙江责联科技有限公司
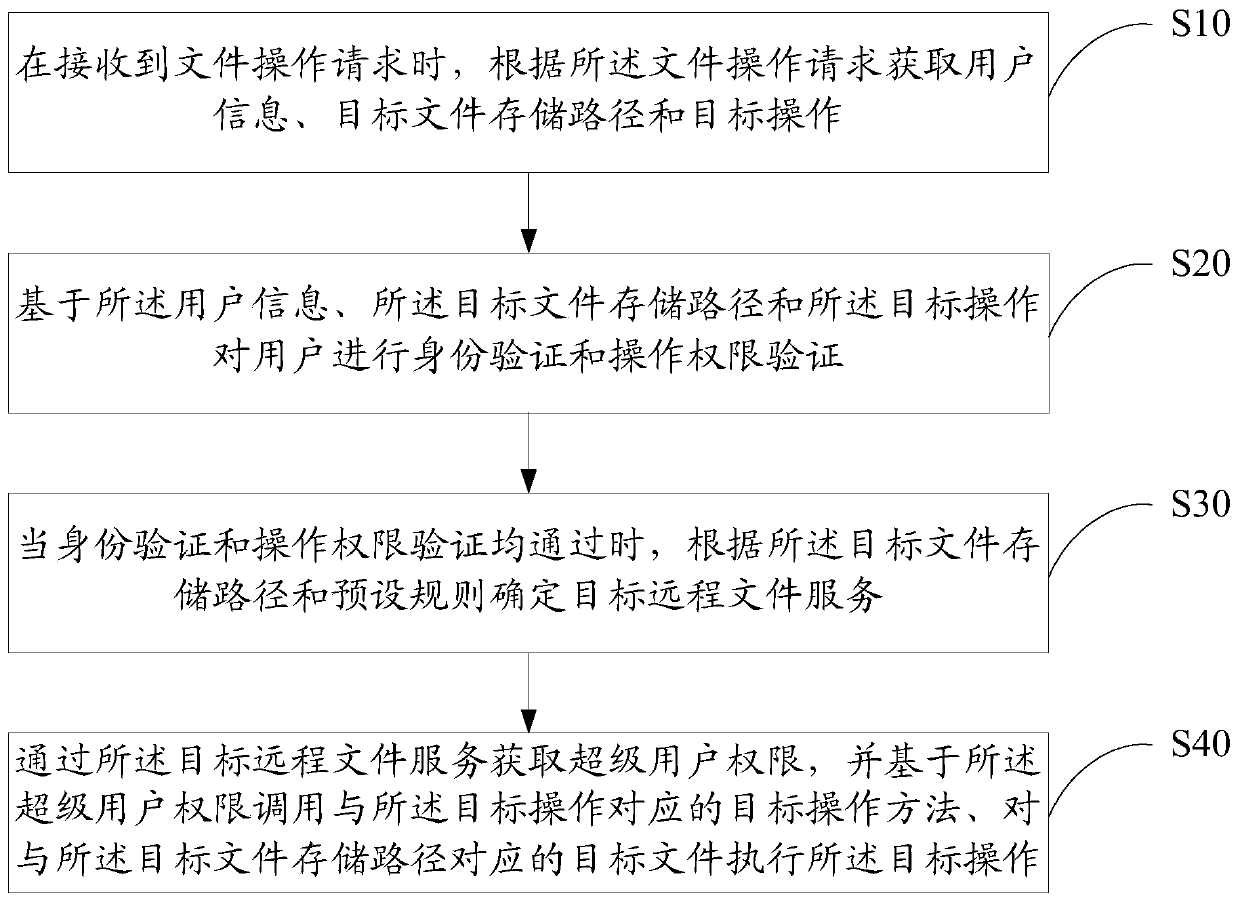
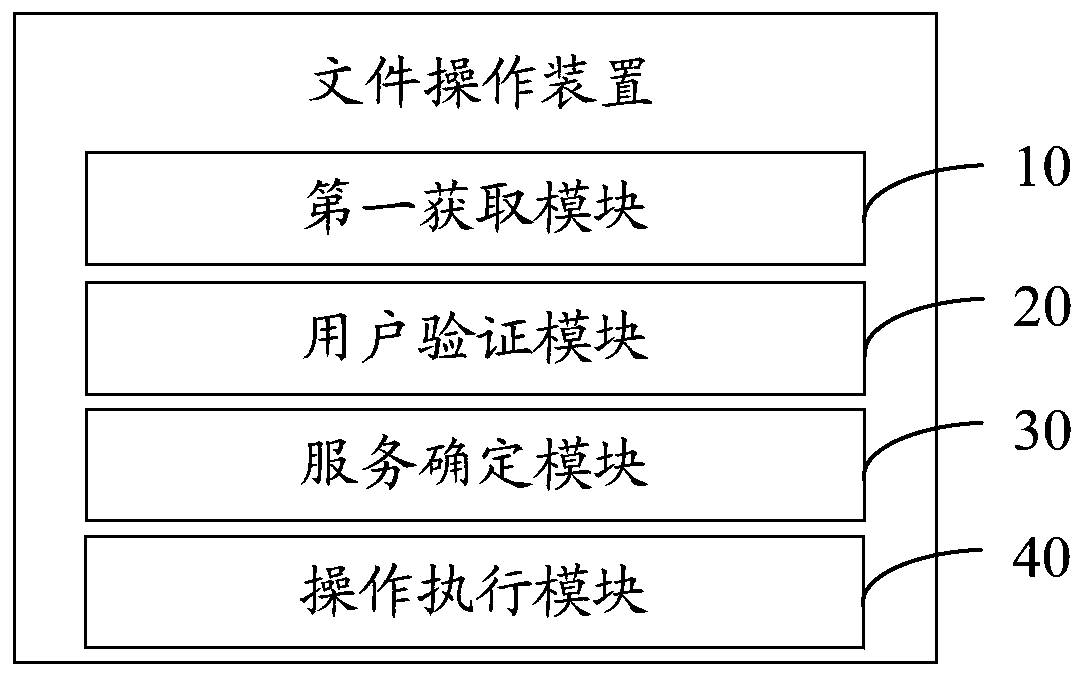
File operation method, device, equipment, system and computer readable storage medium
ActiveCN110363026ARealize controllableImprove securityDigital data protectionDigital data authenticationFile systemControllability
The invention relates to the technical field of financial science and technology, and discloses a file operation method, a device, equipment, a system and a computer readable storage medium. The fileoperation method comprises the steps that when a file operation request is received, user information, a target file storage path and target operation are acquired according to the file operation request; the identity verification and operation authority verification is performed on the user based on the user information, the target file storage path and the target operation; when the identity verification and the operation authority verification are both passed, a target remote file service is determined according to the target file storage path and a preset rule; and a super user permissionis obtained through the target remote file service, a target operation method corresponding to the target operation is called based on the super user permission, and the target operation is executed on a target file corresponding to the target file storage path. According to the invention, the controllability of user permission management and the security of file system operation access can be improved.
Owner:WEBANK (CHINA)
Multi-subscriber bank settlement account with different operation authority
InactiveCN1835032AEnsure safetyRealize added valueComplete banking machinesPasswordHuman–computer interaction
The invention is a multiuser balance account with different operation authorities, having plural users, a super user and several operating users, and different users possess different trade authorities, and the account holder acts as the only super user and holds a super password (changeable or modifiable); the super user establishes and terminates the operating users and sets and cancels trade authorities of the operating users (trade kinds and limit); the operating users hold operating passwords (changeable or modifiable) and make operations only in the authorized range of the super user. It builds a credit platform between super user and operating users.
Owner:石瑞雪
Method for controlling file security of block distributed file system
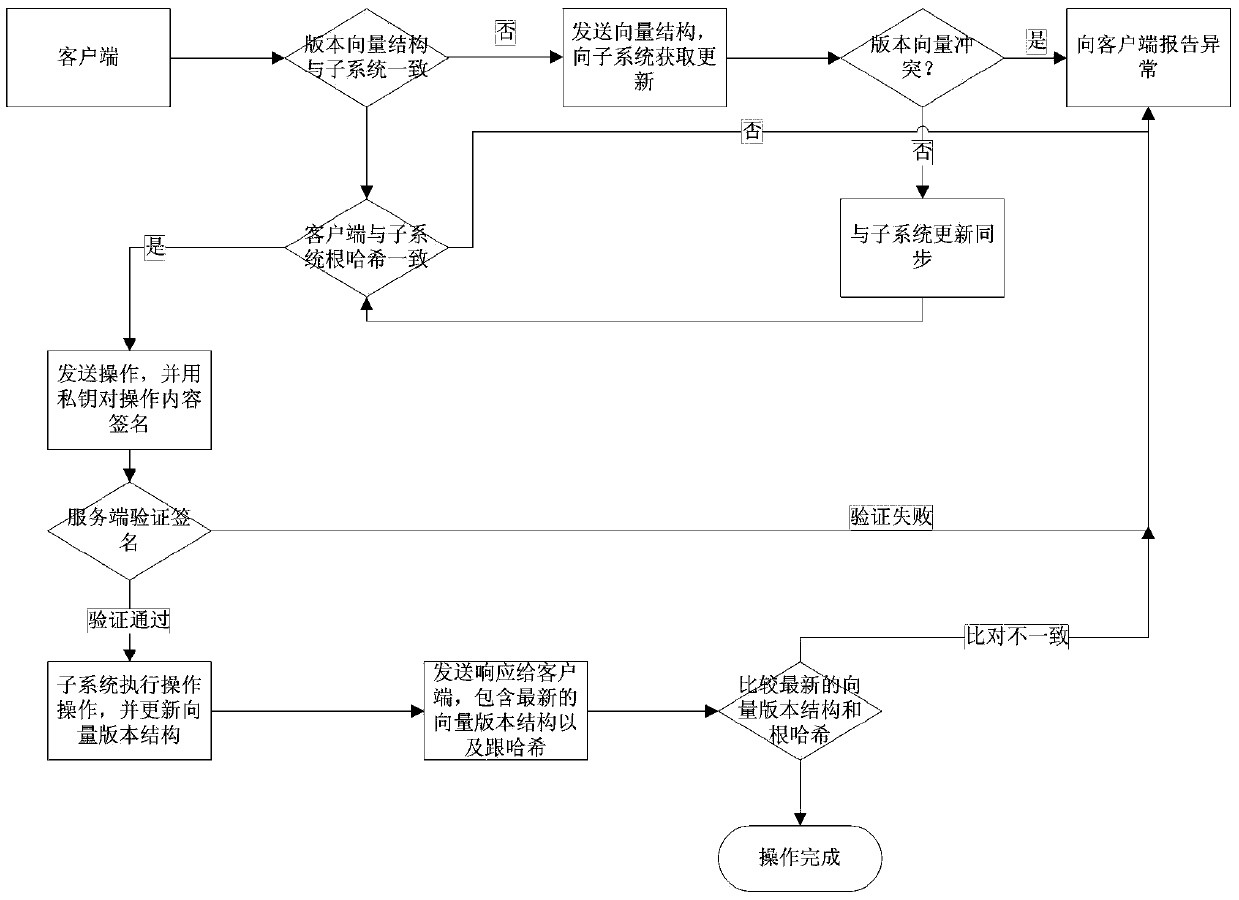
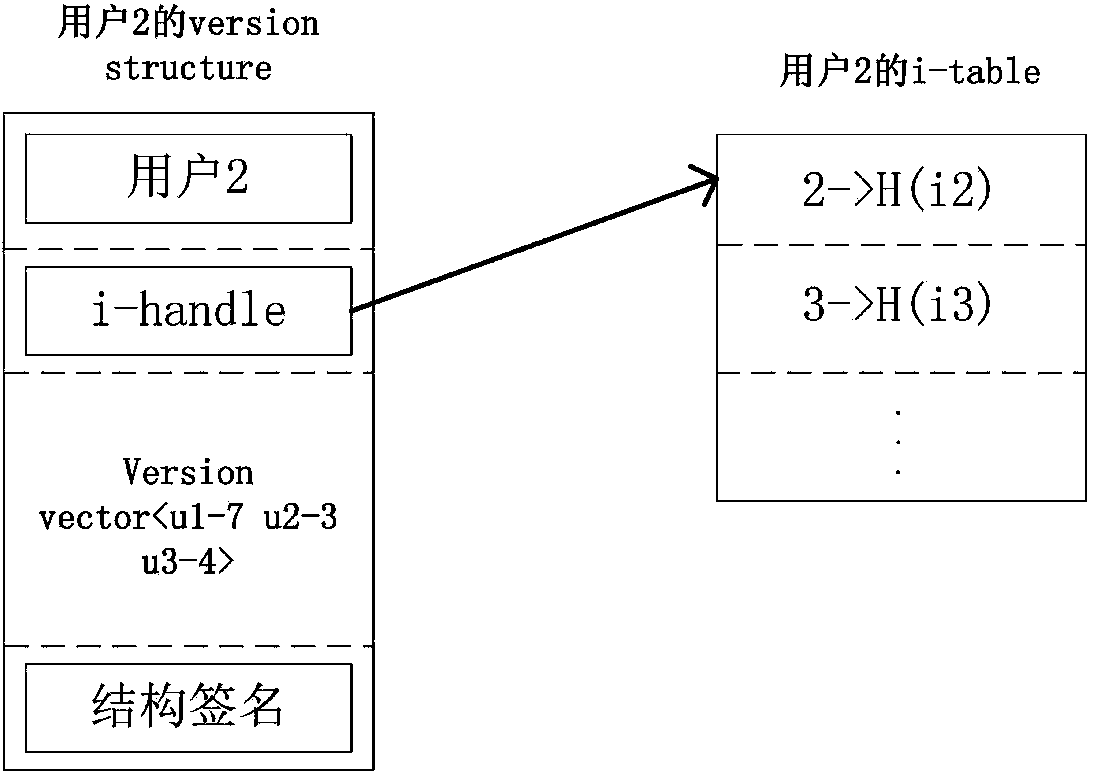
The invention discloses a method for controlling the file security of a block distributed file system. The method includes that a distributed storage system is logically divided into a plurality of subsystems, each subsystem comprises a super user and user list files, the subsystems adopt public secret key encryption algorithms, private keys of the super users are stored in an offline manner, and private keys of users are only stored on clients after being generated; the subsystems record logs for all operation and abstract the logs by the aid of Hash trees, hash values of root nodes of the most recently operated Hash trees are reserved on the clients, whether the file system is illegally modified or not is judged by means of comparing the Hash values on the clients to hash values on servers, and the consistency of the file system which is operated by the multiple users is checked by the aid of a version-vector algorithm. The method has the advantages that the storage security is provided for the distributed file system, trust management is carried out on the distributed file system, and whether files are reliable and correct or not still can be detected even under the condition that the servers are unreliable.
Owner:ZHEJIANG UNIV
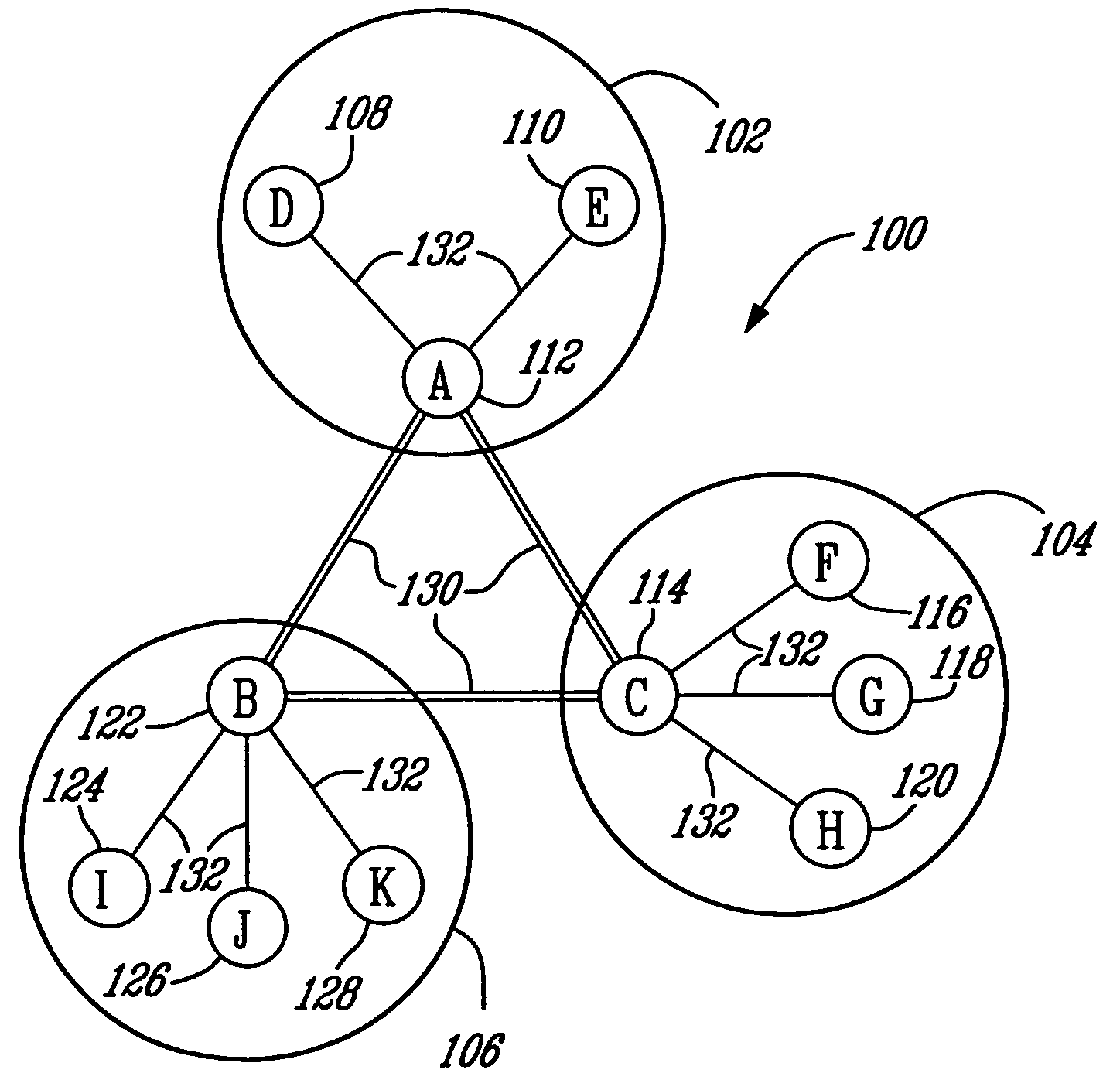
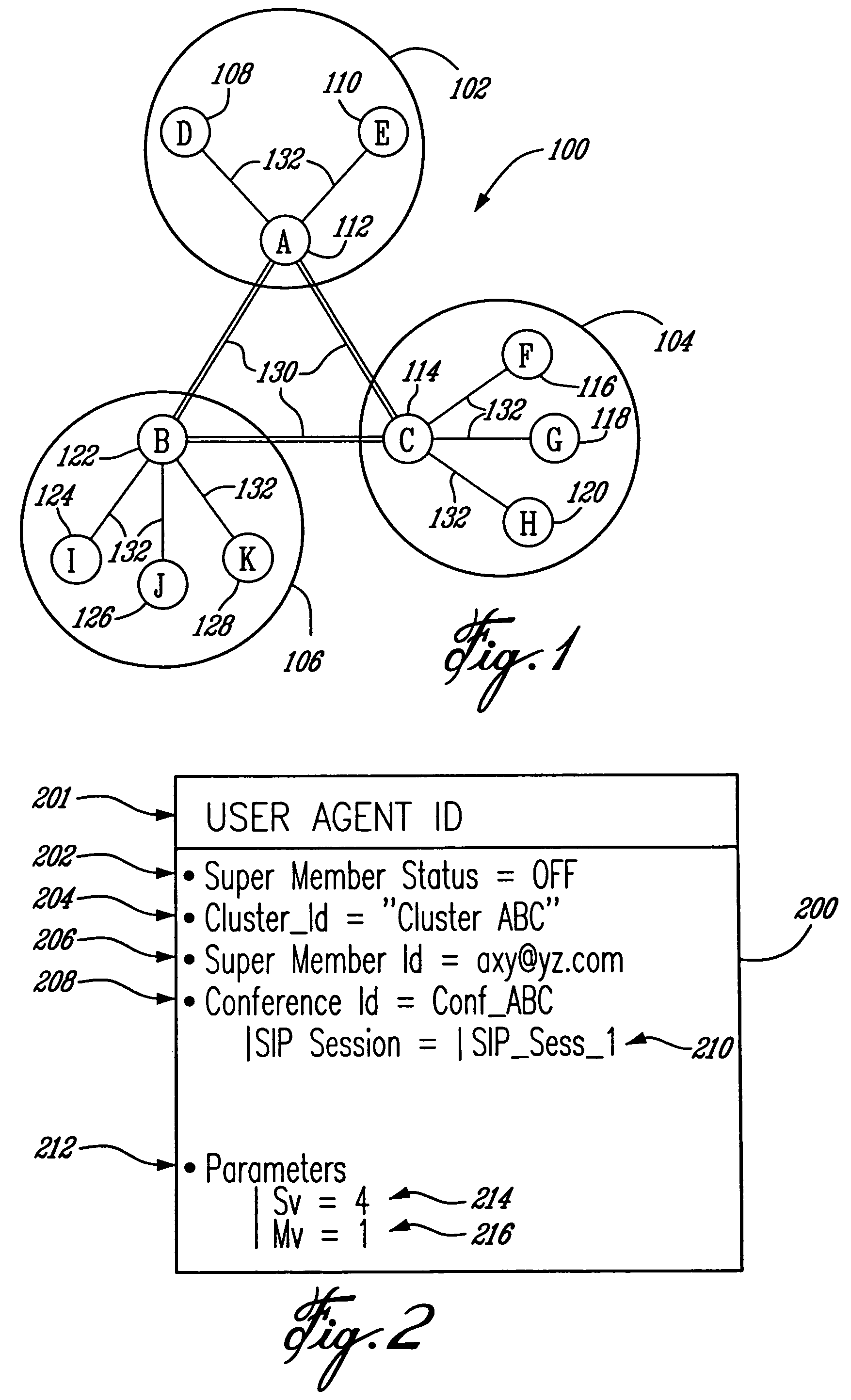
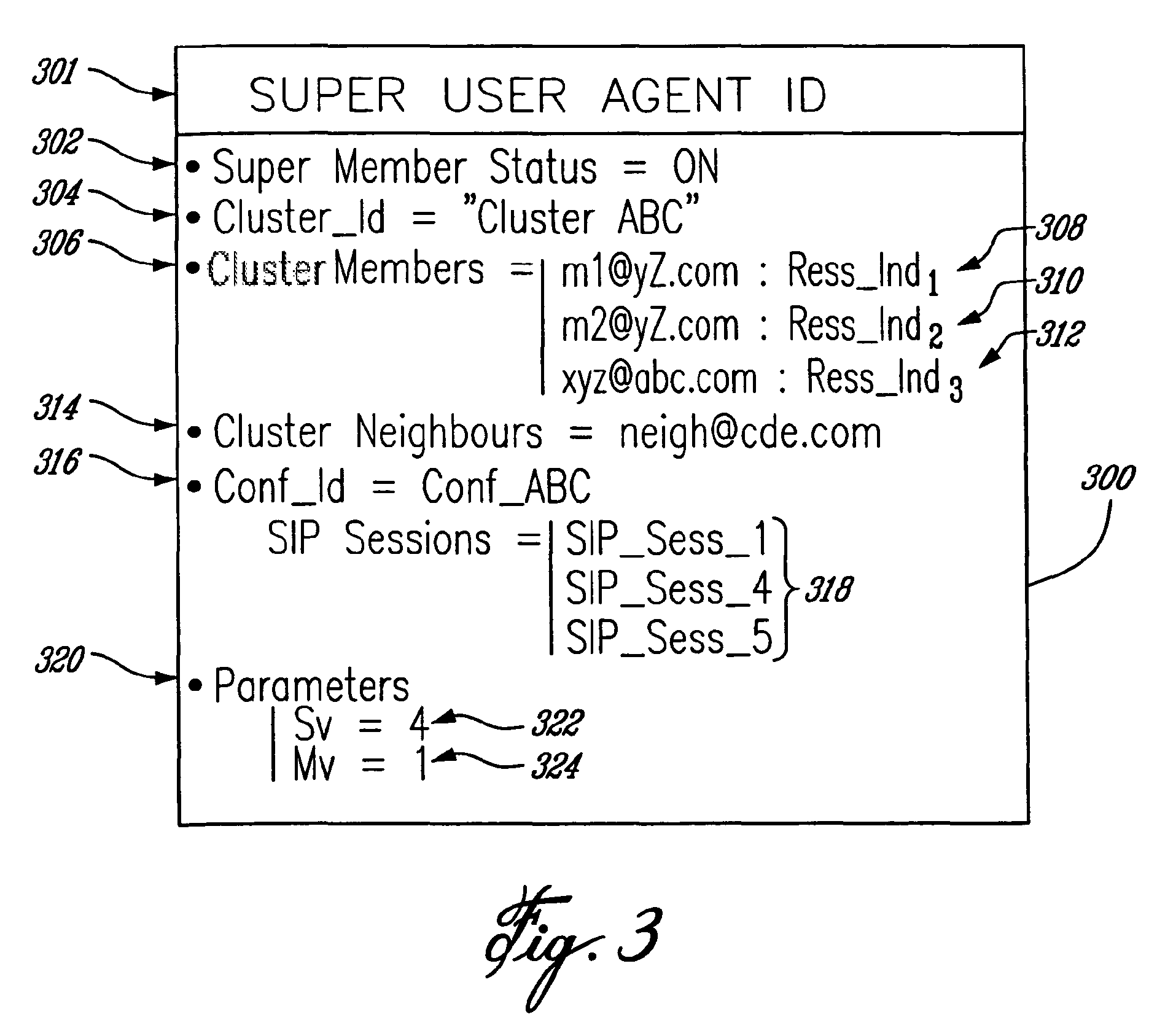
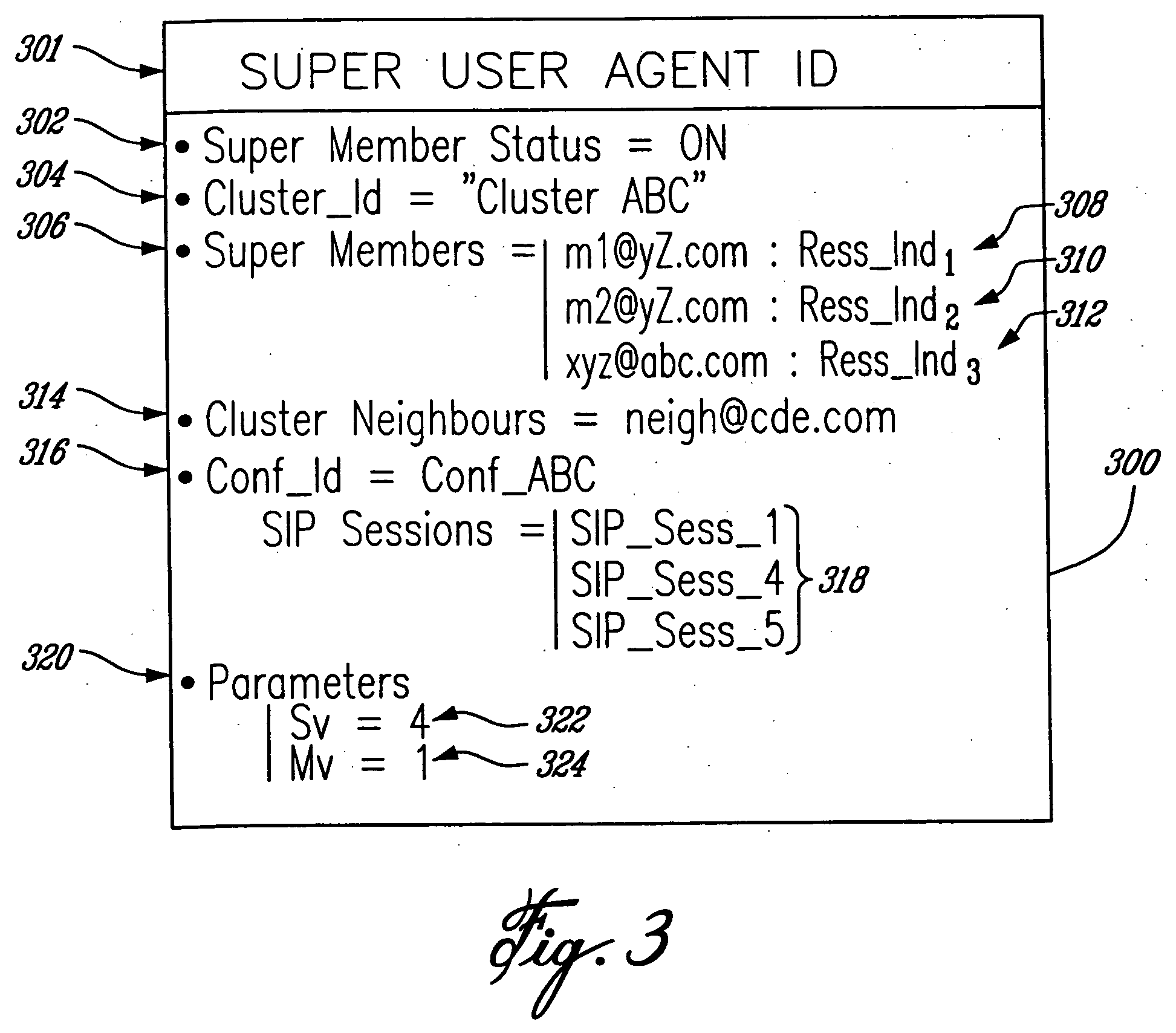
Cluster of terminals and ad-hoc network for cluster-based multi-party conferencing
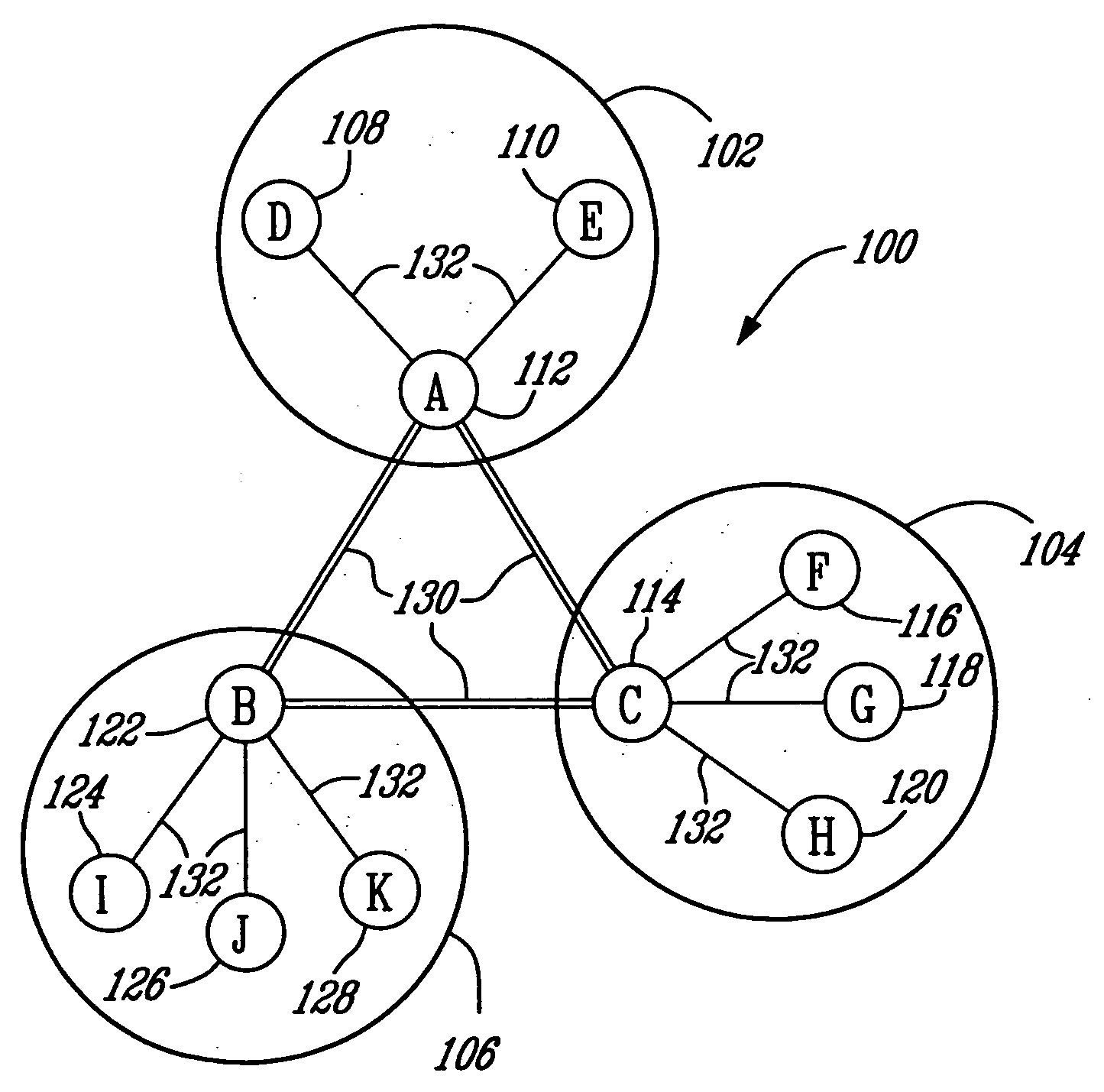
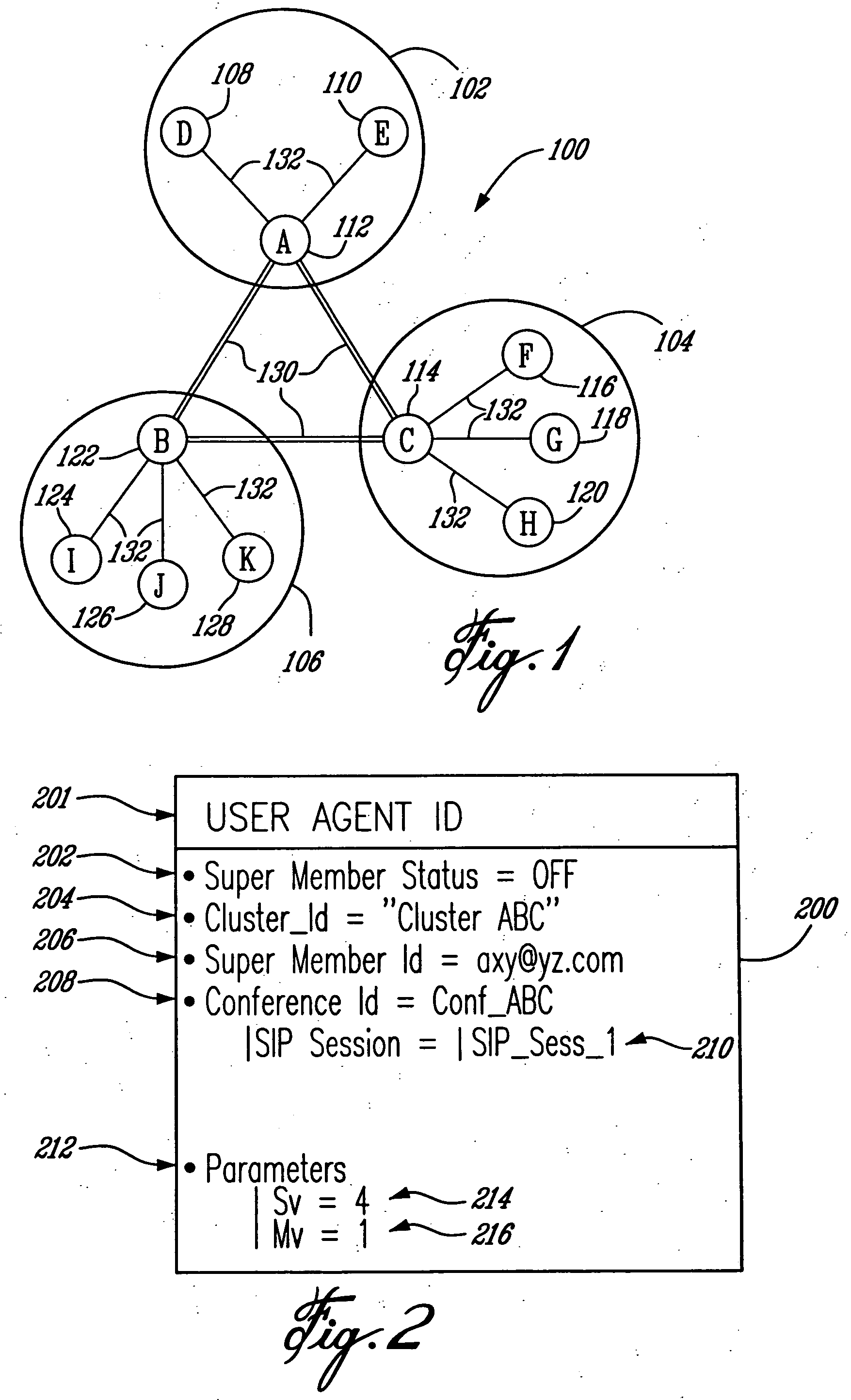
InactiveUS7697490B2Data switching by path configurationWireless commuication servicesCluster basedDistributed computing
A cluster of terminals, and an ad-hoc network of two or more such clusters, for carrying a multi-party, cluster-based, conference, wherein each cluster includes a super member comprising a super user agent, and one or more members including a user agent. Communications sessions are established between the super member of each cluster and each member terminals of the same cluster, and between the super members of each one of the first and second clusters. The user agent comprises identity of the super member, a conference identity, cluster parameters including a split value (Sv) indicative of a maximum number of terminals that may be part of the cluster, wherein when Sv is reached during the conference the cluster is split, and a merge value (Mv) indicative of a minimum number of terminals that may be part of the cluster, wherein when Mv is reached the cluster is merged with another cluster. The super user agent comprises a cluster member list, the conference identity, a cluster neighbour list, the one or more terminals also participating to the same conference, and cluster parameters.
Owner:TELEFON AB LM ERICSSON (PUBL)
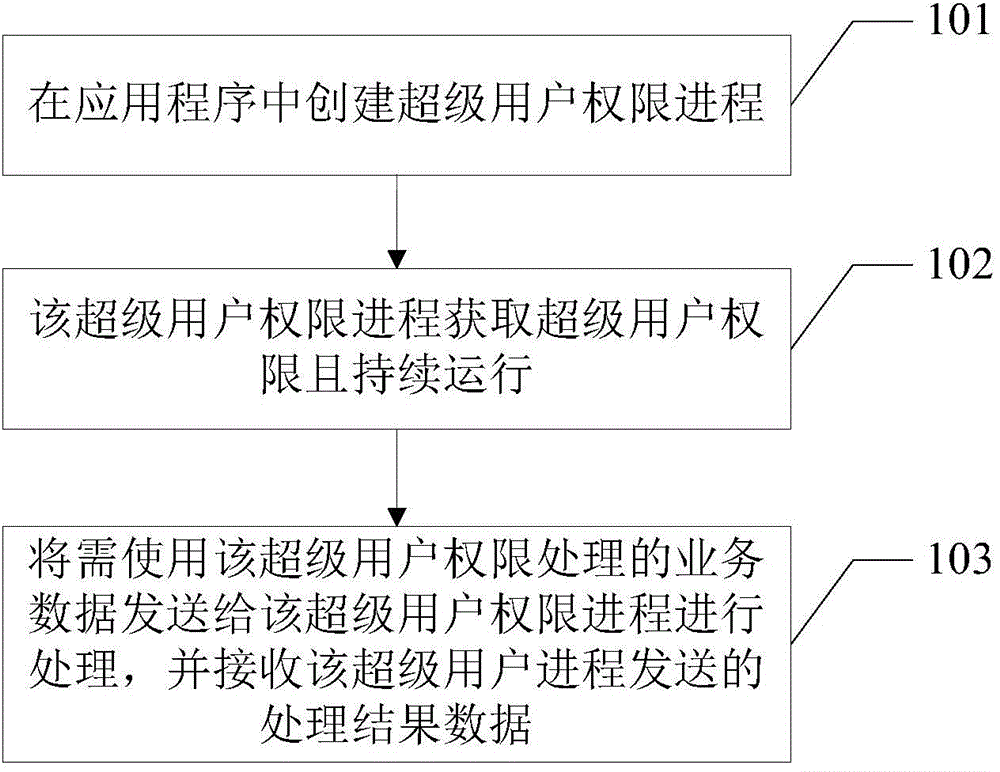
Method and device for running application program by superuser identity
ActiveCN104572158AReduce processing timeProcessing speedProgram loading/initiatingApplication softwareSuperuser
The invention relates to a method for running an application program by a superuser identity. The method comprises the following steps that a superuser right process is created in an application program, the superuser right process obtains the superuser right and continuously runs, service data required to be processed by the superuser right is sent to the superuser right process to be processed, and in addition, processing result data sent by the superuser process is received. The method and a device for running the application program by the superuser application program have the advantage that the data processing speed can be accelerated.
Owner:TENCENT TECH (SHENZHEN) CO LTD
File pulling method, device and system
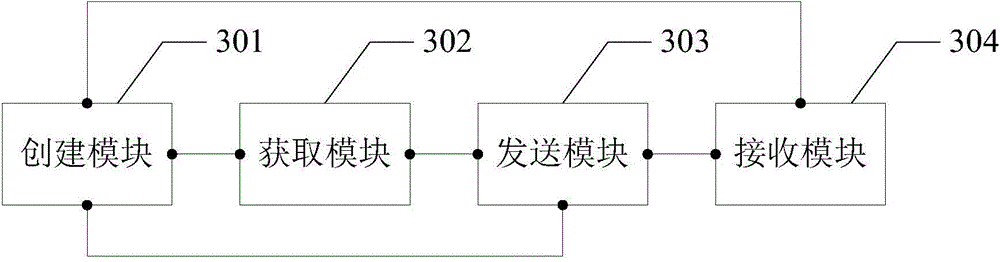
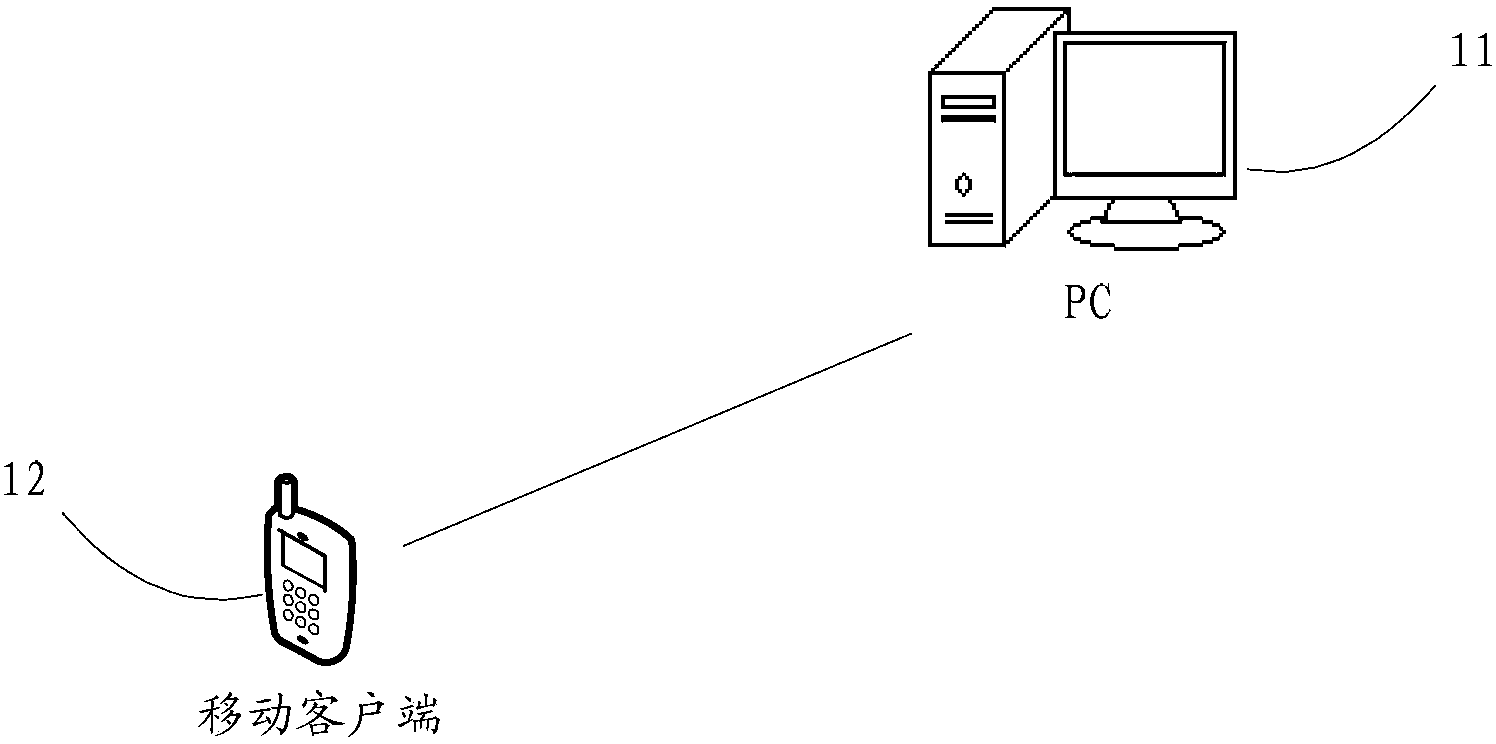
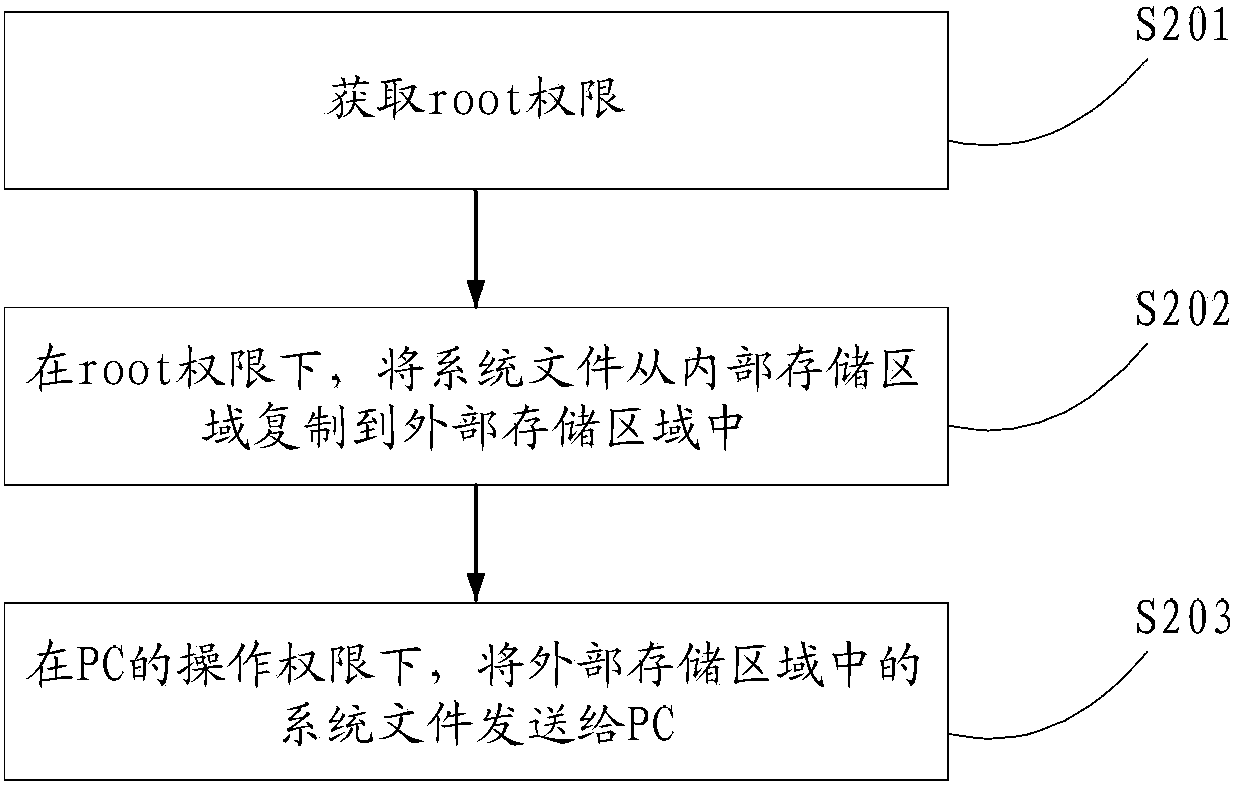
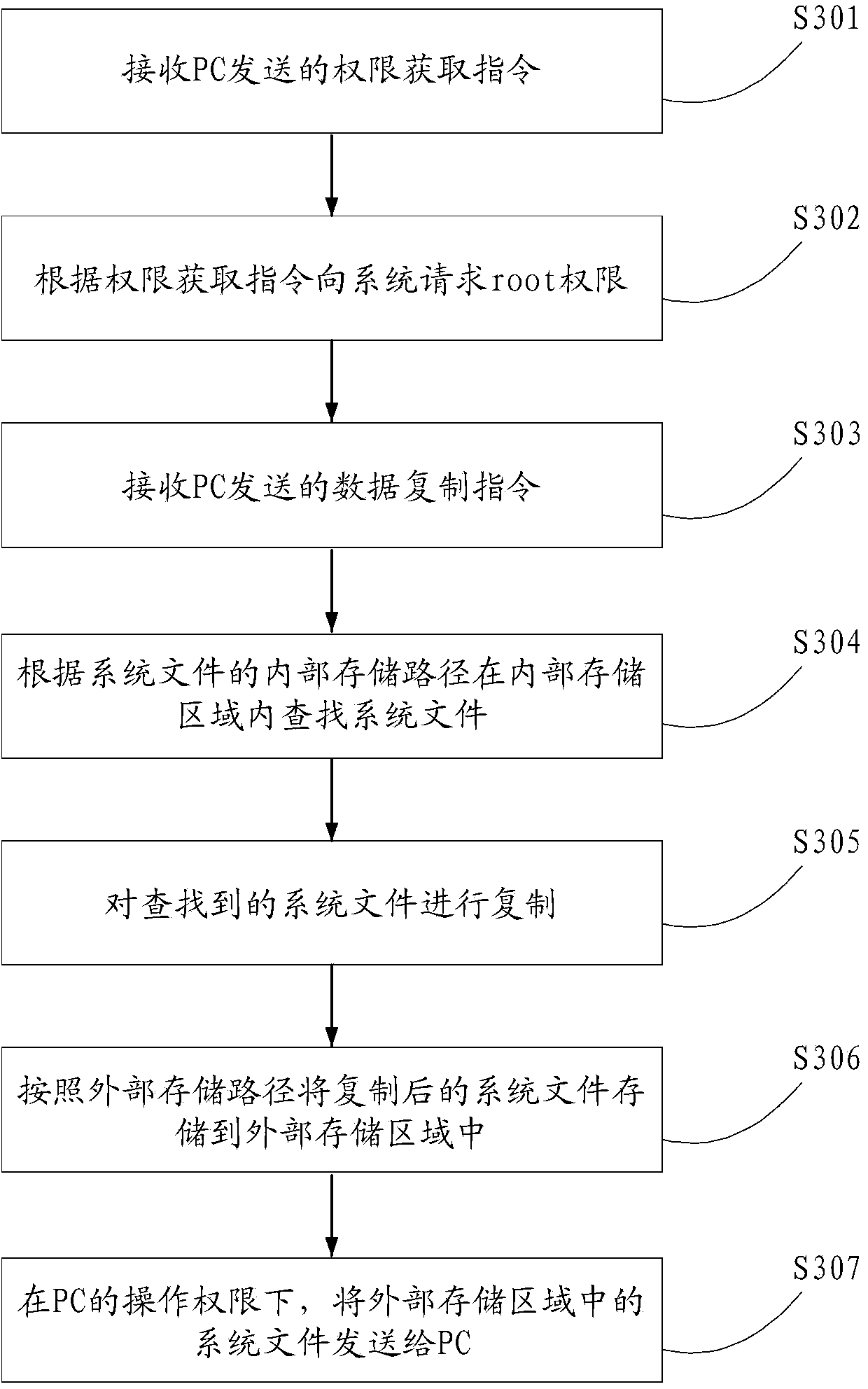
ActiveCN104252587AReduced operating authoritySoftware testing/debuggingDigital data authenticationExternal storagePersonal computer
The invention discloses a file pulling method, device and system, and relates to the technical field of communication. A system file in a mobile client can be successfully pulled to a PC (Personal Computer). The file pulling method comprises the following steps that the mobile client obtains a superuser (root) privilege which is the highest privilege of the mobile client; under the root privilege, the system file is copied to an external storage region from an internal storage region, and the access privilege of the system file in the external storage region is lower than that of the system file in the internal storage region; under the operation privilege of the PC, the system file in the external storage region is sent to the PC. The file pulling method, device and system provided by the invention are mainly applied to the process of detecting a mobile phone system.
Owner:TENCENT TECH (SHENZHEN) CO LTD
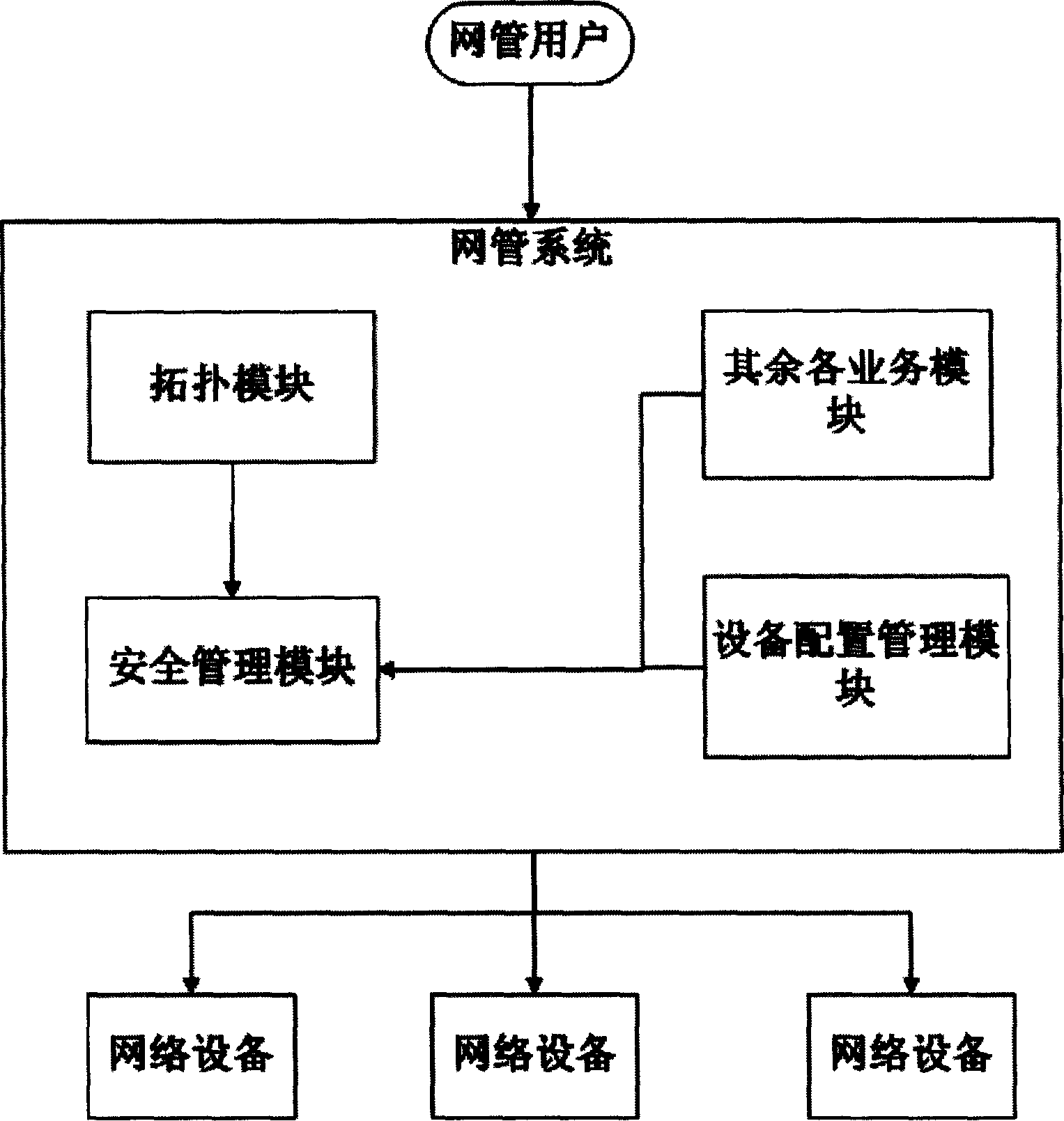
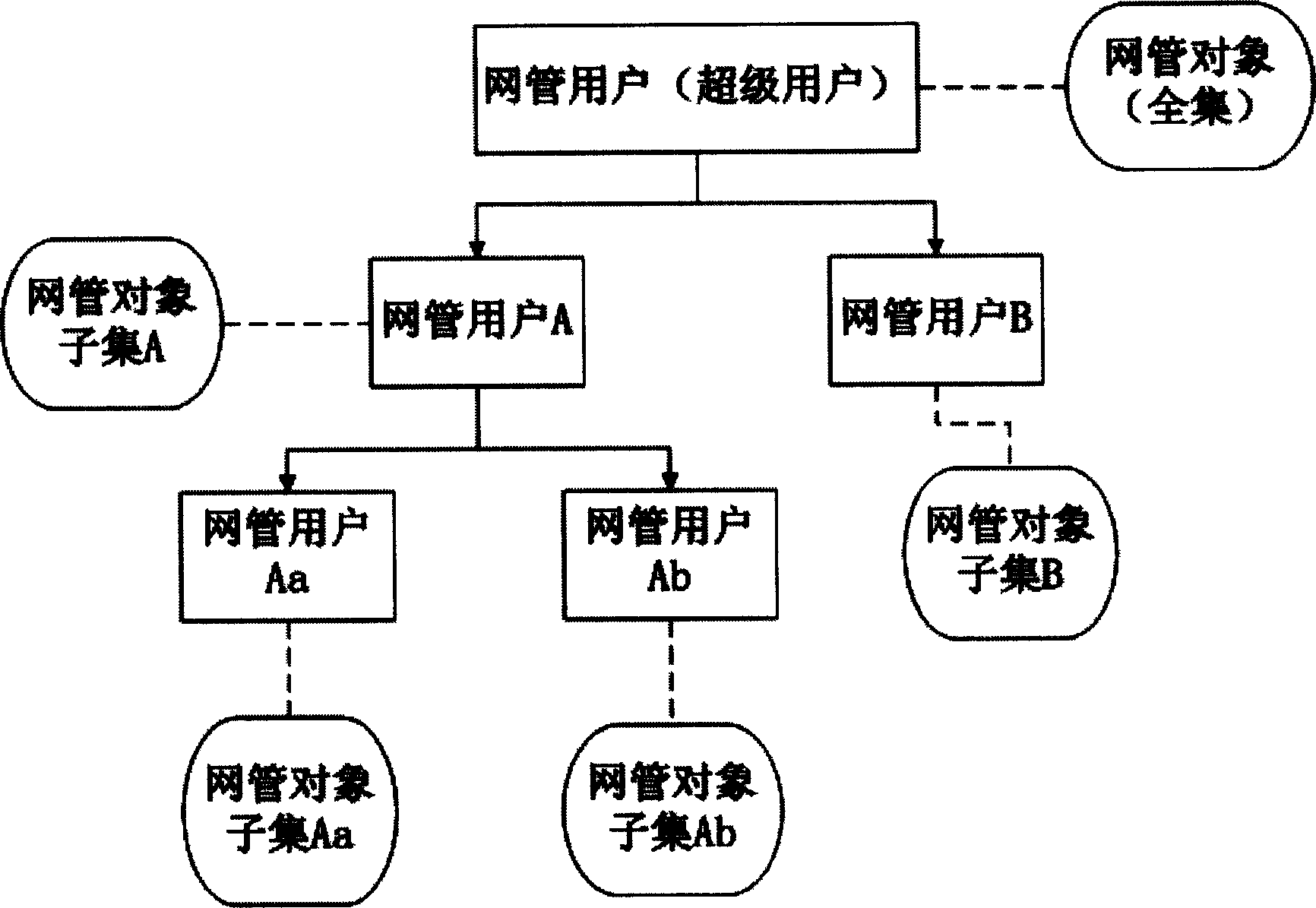
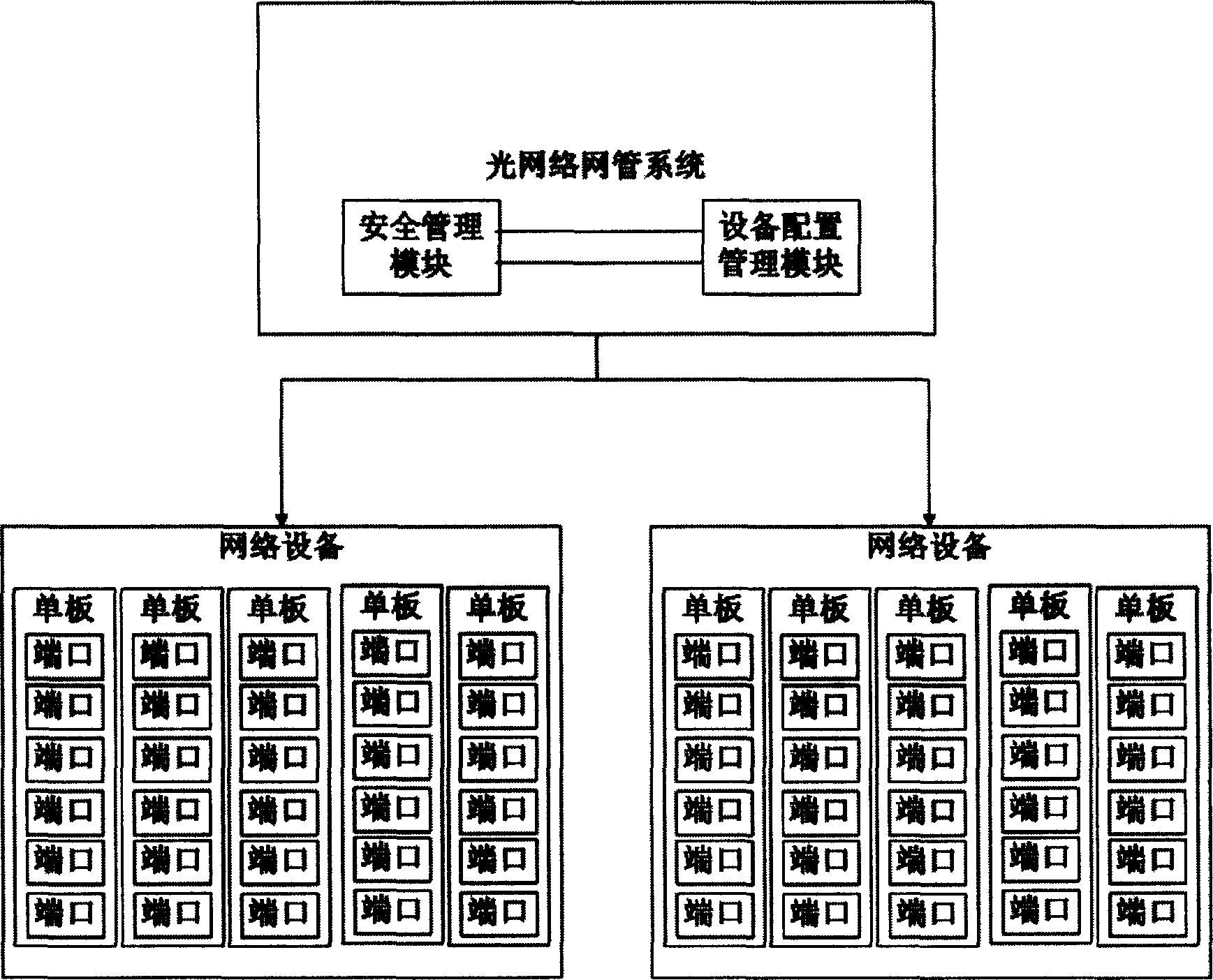
Safety decentralization management system of distribution type network management platform
InactiveCN1556615AFlexible managementAchieve security decentralization managementData switching networksLower gradeNetwork communication
The invention provides a secure decentralized managing system for a distributed network managing platform, which belongs to computer network communication field. The slave objects of the network device and the network device are used as network managed object to be stored in the network managing system, the network managing system has a default super user, the super user creates the network managing user, the network managing user creates the subjacent user, the network managing object is allocated to the network managing user through super user, the upper grade network managing user allocates the network managing object to the lower grade of user, each user has a network managing object assemble, when the network user logs in the network management, the network security model carries on the check to the operation permission of the login user according to the network managing object assemble. The network managing security model judges the relation between the object assemble and the object needed to be operated, it determines the efficiency of the network managing user operation, thus realizes the decentralized managing to distributed network platform.
Owner:HUAWEI TECH CO LTD
Protecting cognitive code and client data in a public cloud via deployment of data and executables into a secure partition with persistent data
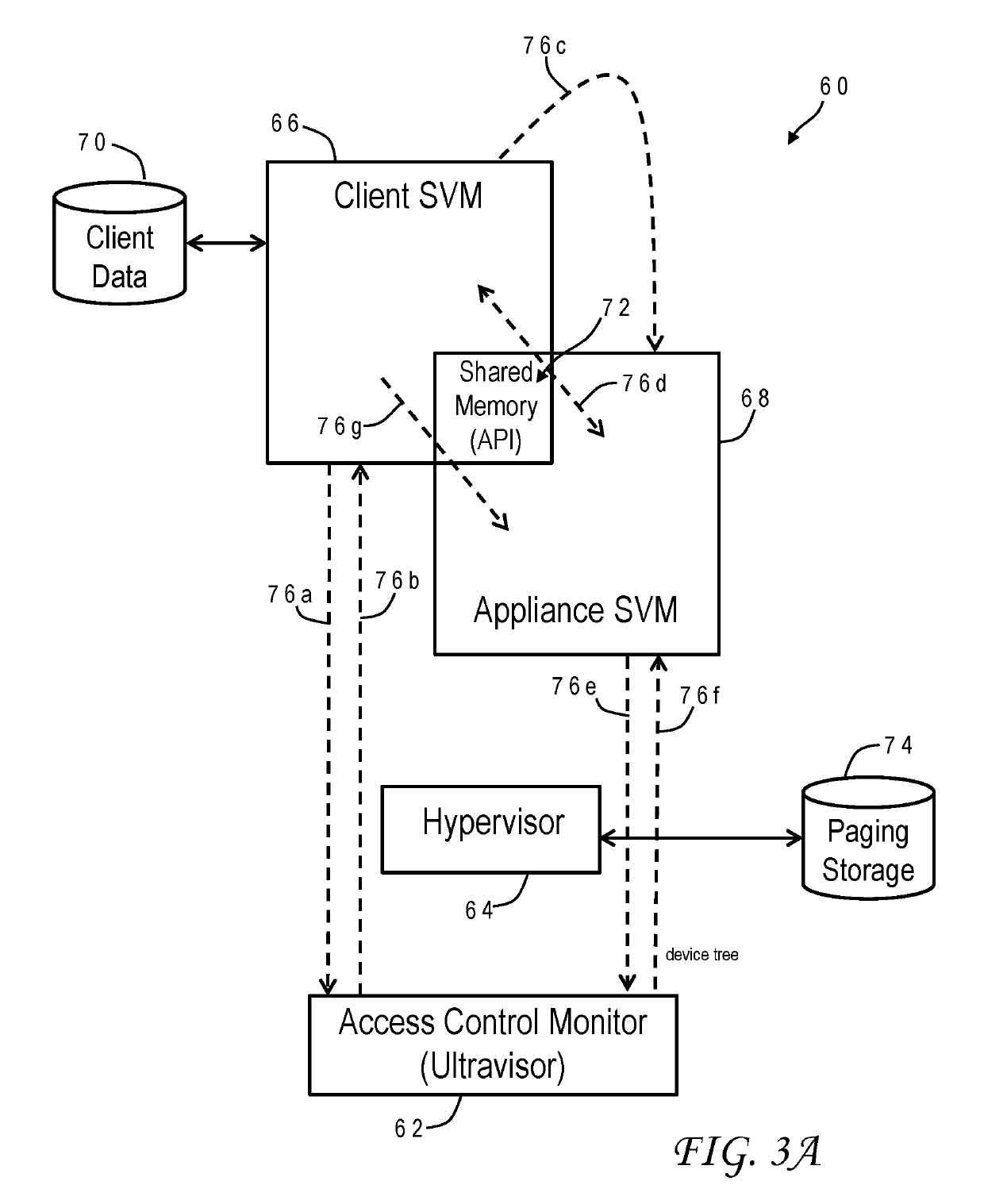
ActiveUS20190278918A1Public key for secure communicationUser identity/authority verificationOperational systemConfidentiality
A secure cloud computing environment protects the confidentiality of application code from a customer while simultaneously protecting the confidentiality of a customer's data from intentional or inadvertent leaks by the application code. This result is accomplished without the need to trust the application code and without requiring human surveillance or intervention. A client secure virtual machine (SVM) is accessible by a client who supplies commands, operand data and application data. An appliance SVM has the application code loaded therein and includes an application program interface that accesses a memory area shared by both SVMs. All access to the appliance SVM is initially revoked by an ultravisor, except for the shared memory and an encrypted persistent storage. The appliance SVM stores the application data in the persistent storage. The ultravisor manages an SVM by maintaining exclusive control over a device tree used by the operating system of the SVM.
Owner:IBM CORP
Cluster of terminals and ad-hoc network for cluster-based multi-party conferencing
InactiveUS20060114843A1Multiplex system selection arrangementsSpecial service provision for substationEngineeringSelf-organizing network
A cluster of terminals, and an ad-hoc network of two or more such clusters, for carrying a multi-party, cluster-based, conference, wherein each cluster includes a super member comprising a super user agent, and one or more members including a user agent. Communications sessions are established between the super member of each cluster and each member terminals of the same cluster, and between the super members of each one of the first and second clusters. The user agent comprises identity of the super member, a conference identity, cluster parameters including a split value (Sv) indicative of a maximum number of terminals that may be part of the cluster, wherein when Sv is reached during the conference the cluster is split, and a merge value (Mv) indicative of a minimum number of terminals that may be part of the cluster, wherein when Mv is reached the cluster is merged with another cluster. The super user agent comprises a cluster member list, the conference identity, a cluster neighbour list, the one or more terminals also participating to the same conference, and cluster parameters.
Owner:TELEFON AB LM ERICSSON (PUBL)
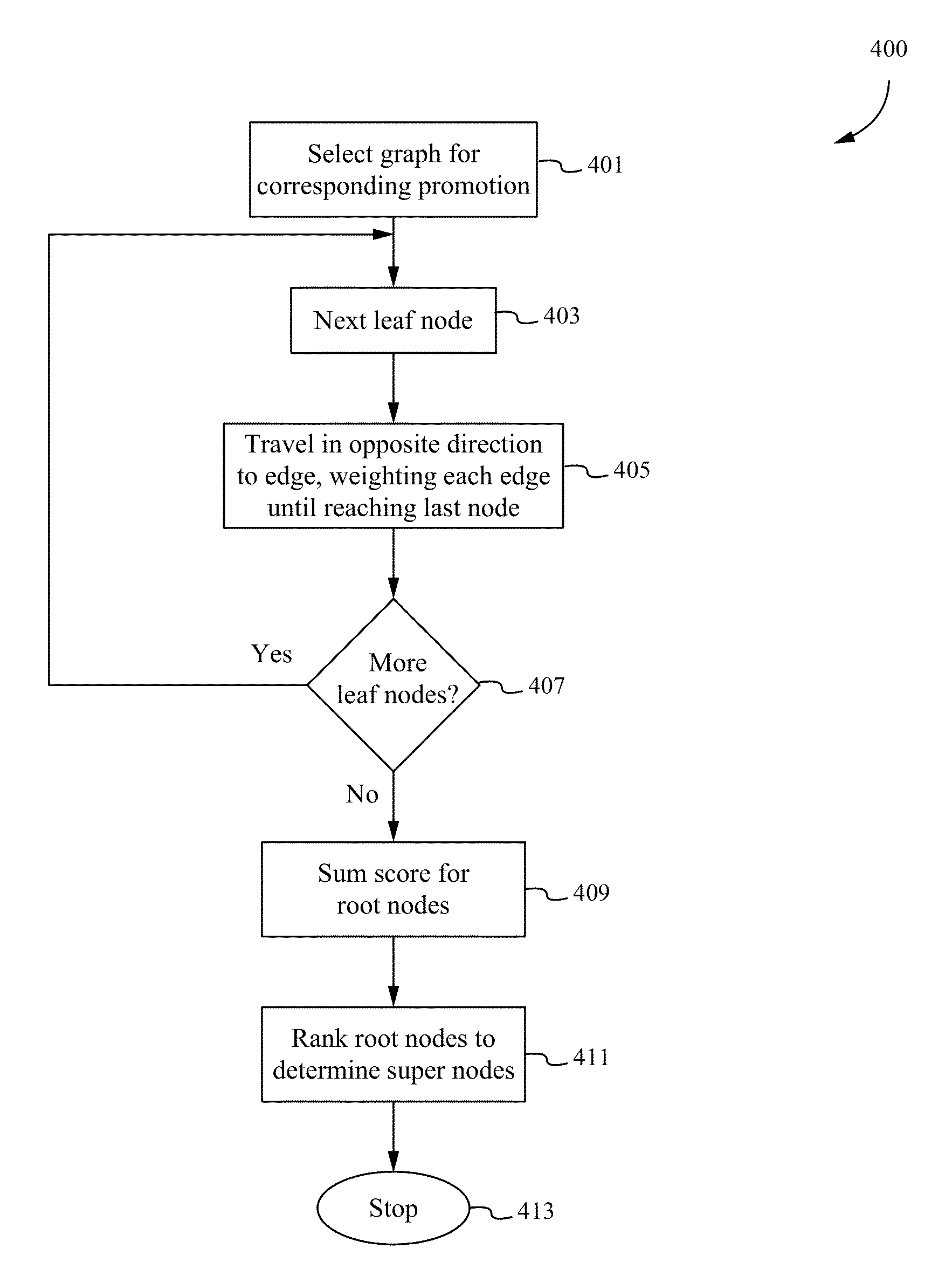
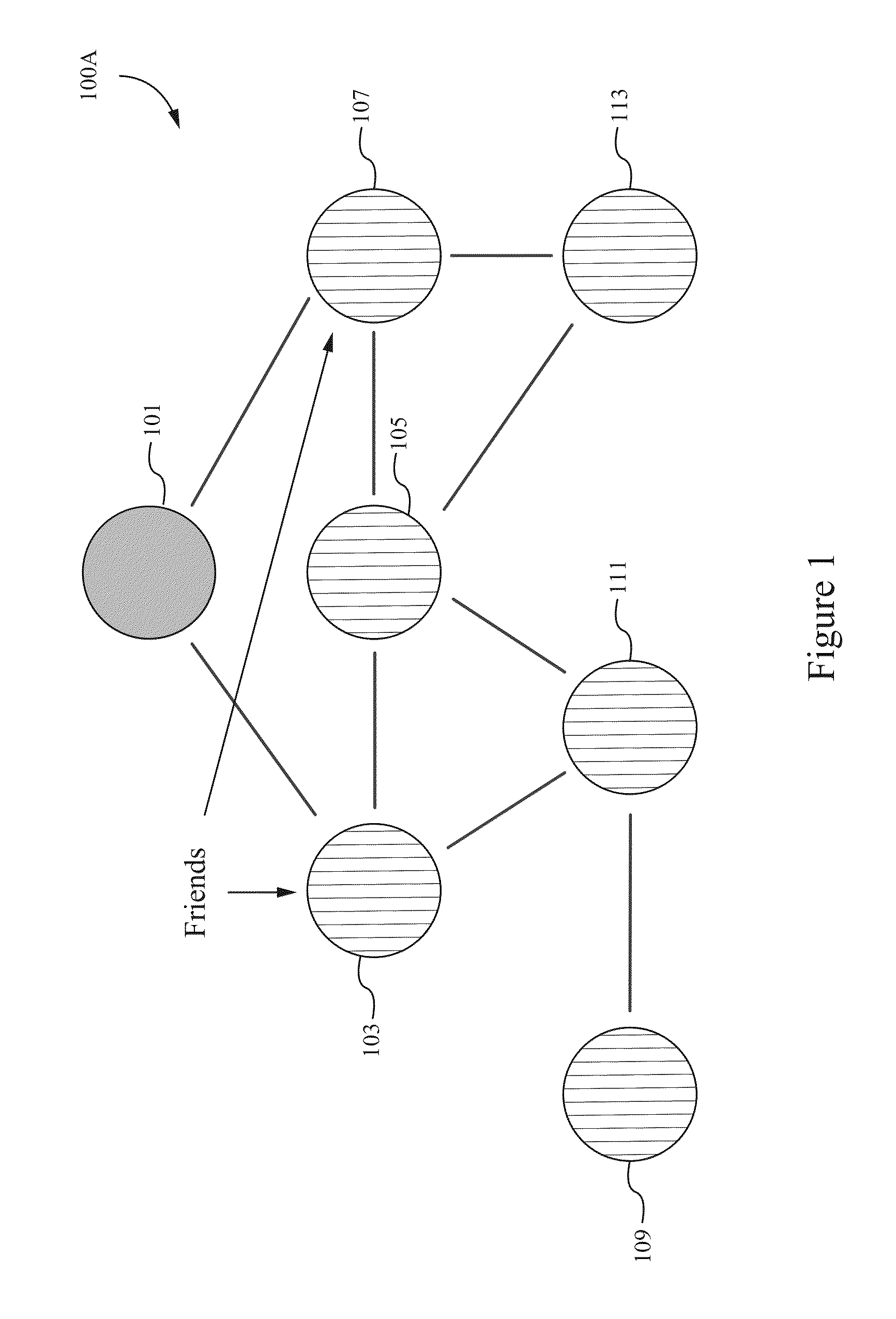
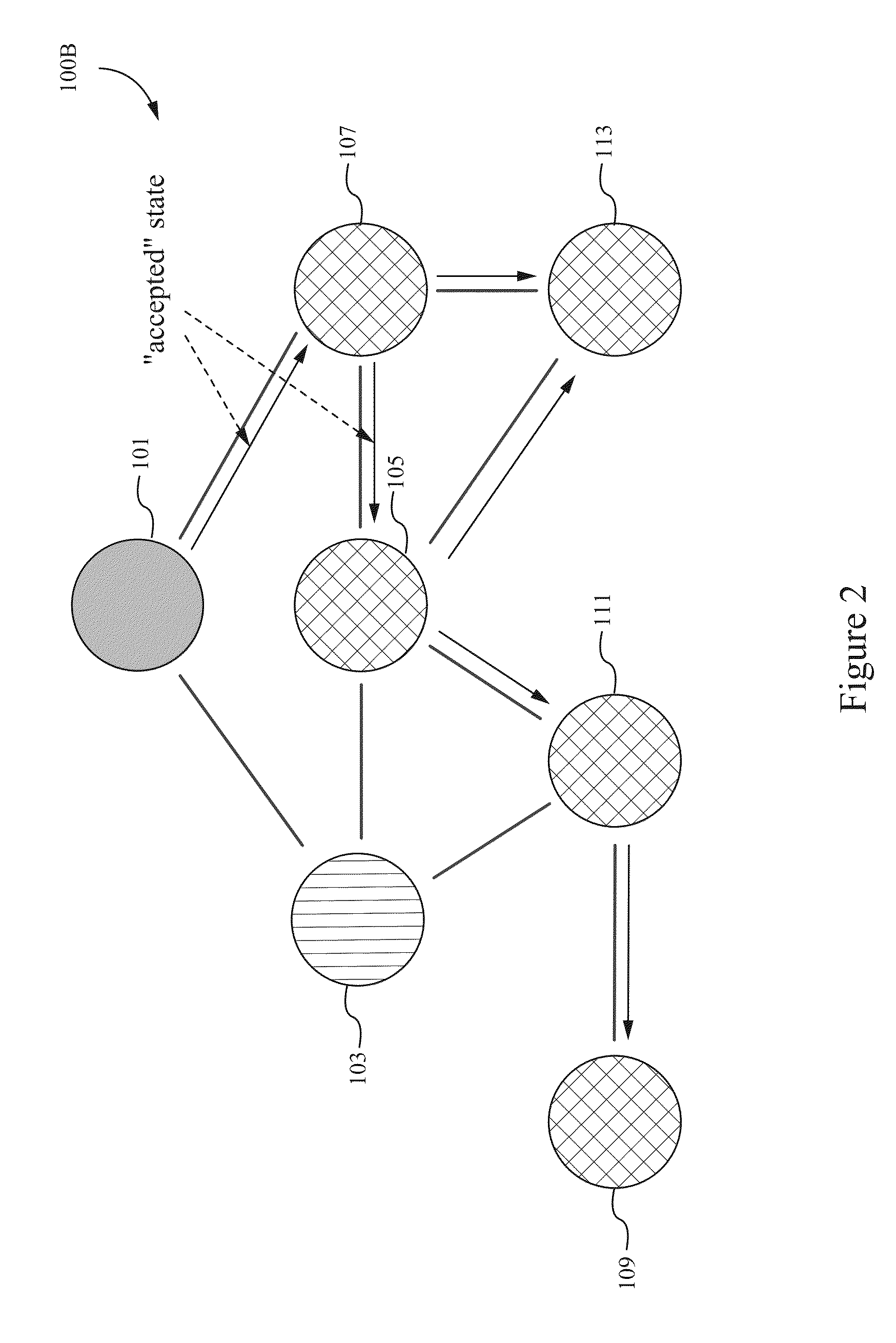
Method of constructing a loyalty graph
InactiveUS20130030865A1Reduces Internet trafficMinimizes email spamMarket data gatheringTheoretical computer scienceWeighted score
Offers for goods or services are targeted more efficiently to potential consumers by using a loyalty graph having nodes that correspond to users and edges that correspond to relationships between the users. The offers are transmitted to only superusers, corresponding to supernodes in the loyalty graph. By targeting only the superusers, the number of invitations transmitted as part of the promotion is reduced. The superusers are determined by calculating a weighted score for each node. Each weighted score corresponds to a number of directed connections between a node and its leaf nodes, with the supernodes determined as the subset of nodes having a weighted sum above a pre-determined threshold. After identifying superusers, subgraphs can be generated corresponding to each superuser. The subgraphs can be selected according to different criteria. In this way, promotions can be targeted to superusers in only selected subgraphs or to all the users in selected subgraphs.
Owner:NOVA VENTUS CONSULTING
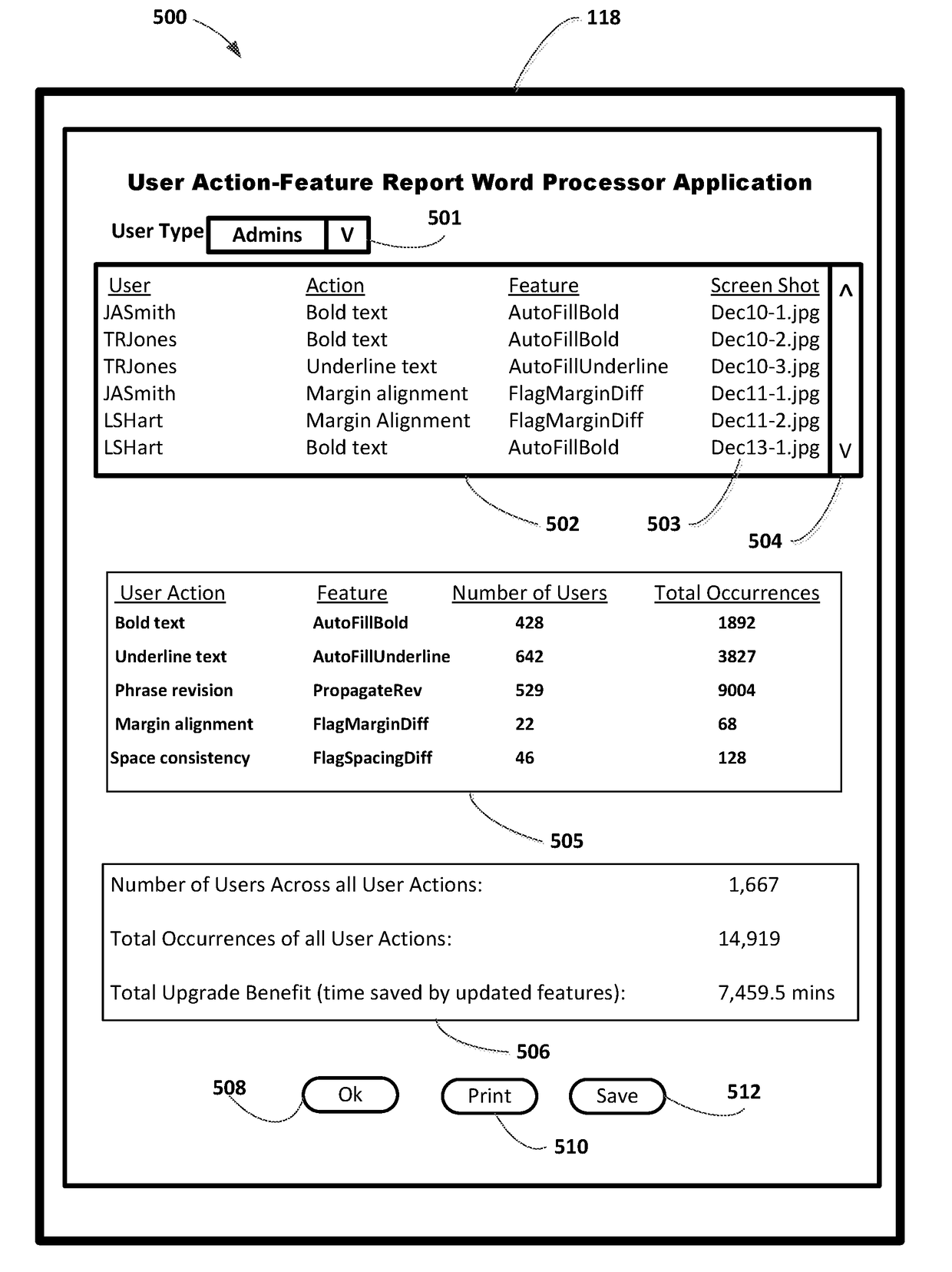
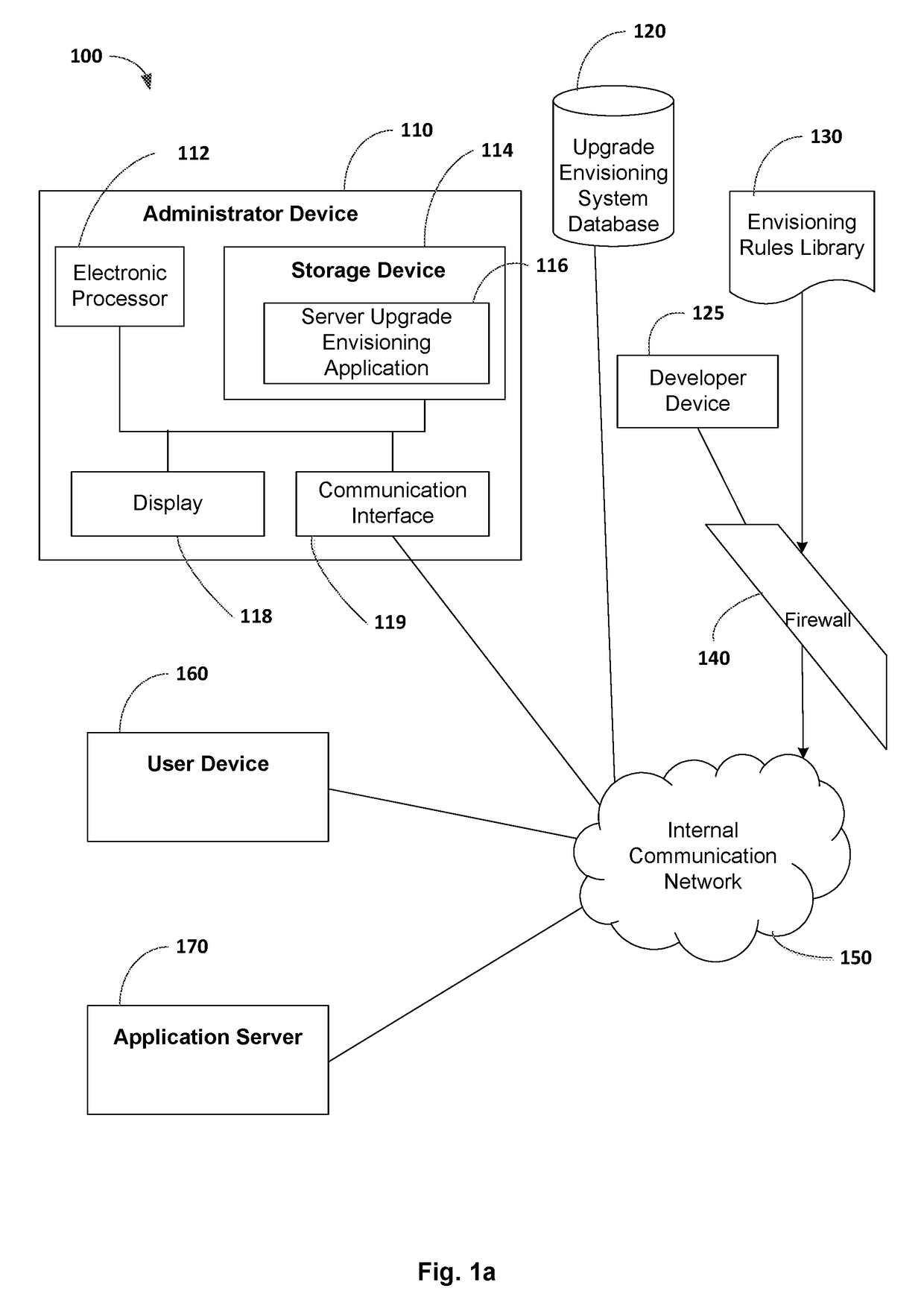
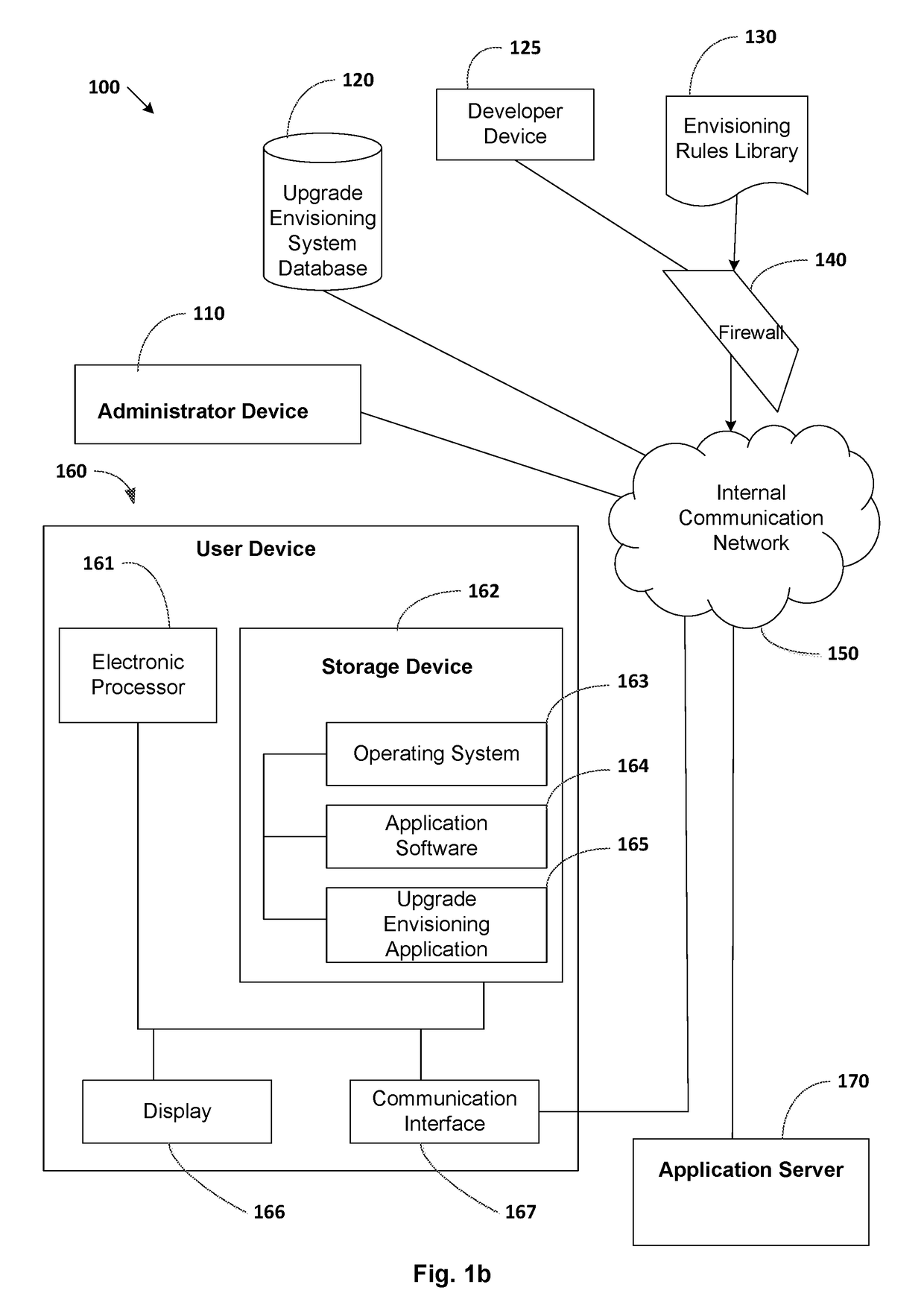
Software upgrade envisioning application
ActiveUS20180217829A1Increase productivityImprove effectivenessVersion controlProgram loading/initiatingApplication softwareSoftware upgrade
Methods and systems for envisioning benefits of a software upgrade. One system includes at least one electronic processor configured to detect when a user performs actions within a software application, capture data about user actions and application features, and determine through a set of rules if an updated or new feature to perform the user actions exists in an upgraded version of the application software. The electronic processor is also configured to, when a rule triggers, store user and application data and present to the user a visualization of the updated feature available in the upgraded application software. User and application data can be aggregated for a plurality of users, a plurality of application software, or both. Display of new features to a plurality of users can be user controlled or controlled by a super user based on analysis and reporting of user data accumulated over time.
Owner:MICROSOFT TECH LICENSING LLC
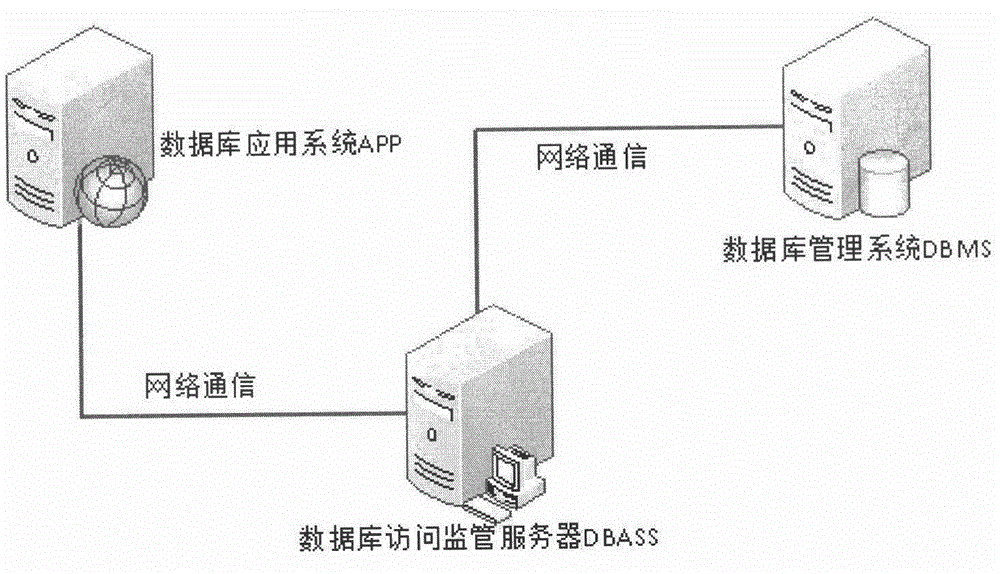
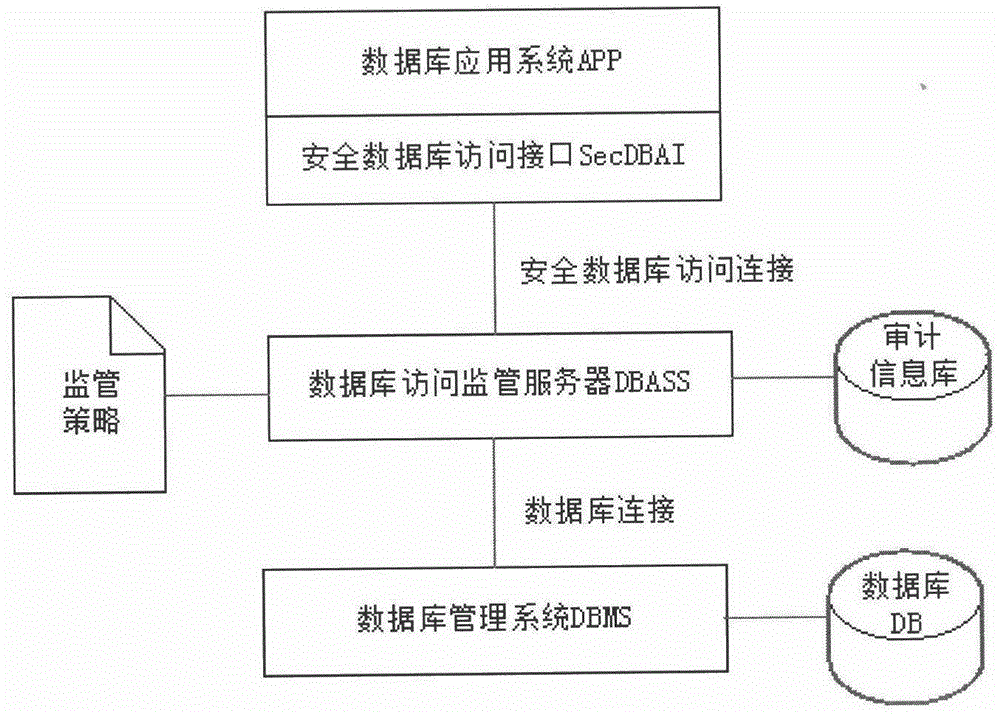
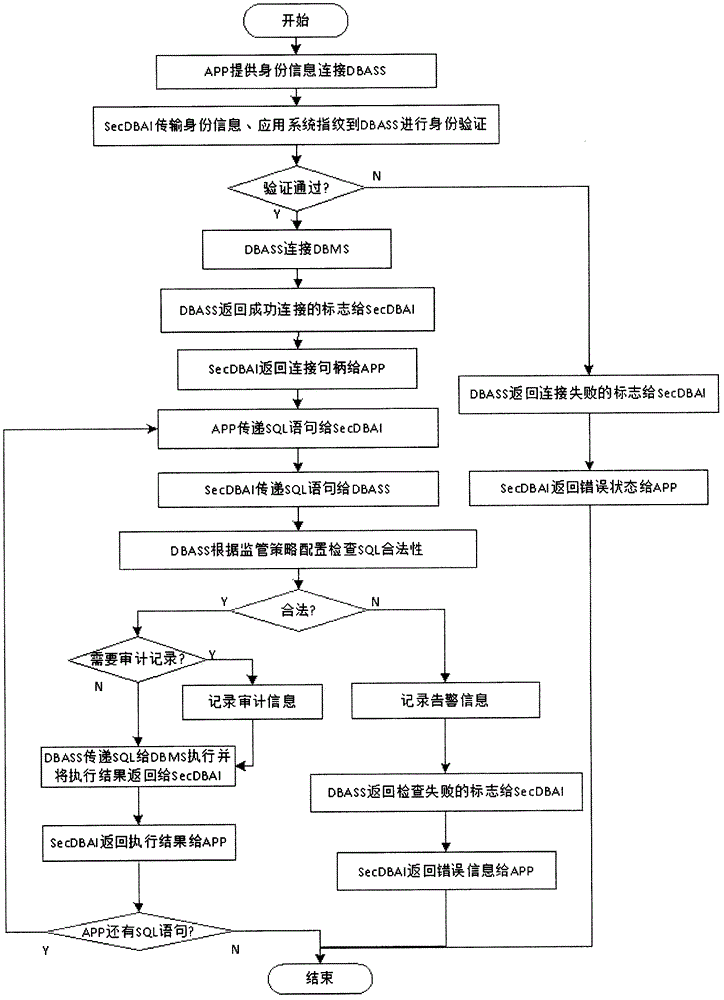
Database access supervision method
InactiveCN105893376AEnsure transparencyWide applicabilitySpecial data processing applicationsControllabilityDatabase connection
The invention discloses a database access supervision method, which comprises the following steps: 1) deploying a database supervision server before a database is deployed, intercepting access to the database through an application layer proxy technology, and putting all pieces of database access under the control of the supervision server; 2) controlling a user name and a password for connecting the database, and adopting a one-time one-authorization way for a database connection request to guarantee the controllability of database connection; 3) identifying the fingerprint of the application system to control the application system which can access the database to guarantee the credibility of the application system; and 4) analyzing, checking, auditing and controlling a SQL (Structured Query Language) statement which accesses the database. The database access supervision method can avoid a phenomenon that a user optionally directly connects with the database to operate, monitors all database access activities, can effectively improve the safety of a database system, and overcomes harm which may be caused to database safety by a superuser, the backdoor and the bug of a database management system, the bug of the application system and the like.
Owner:GUANGXI UNIV
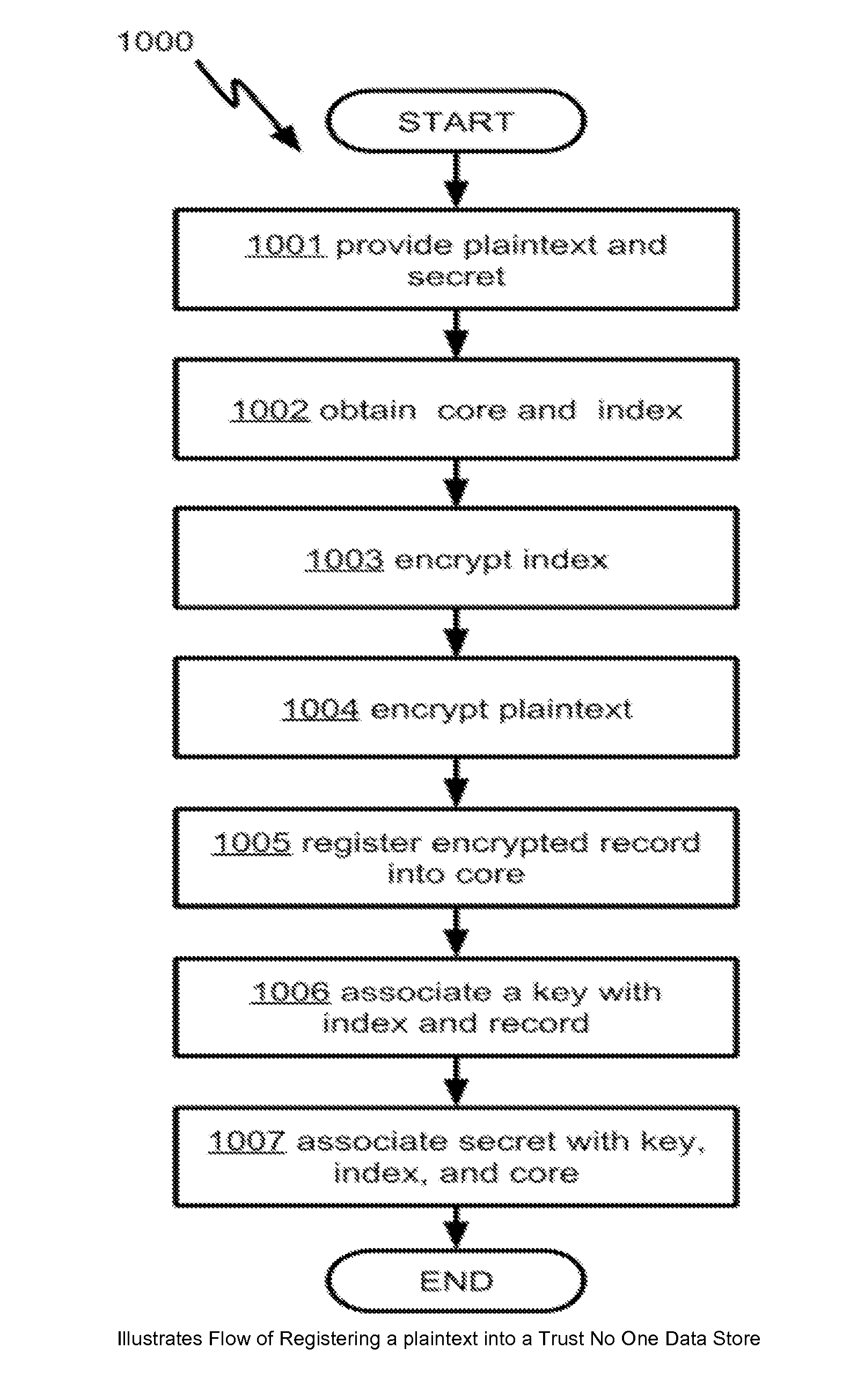
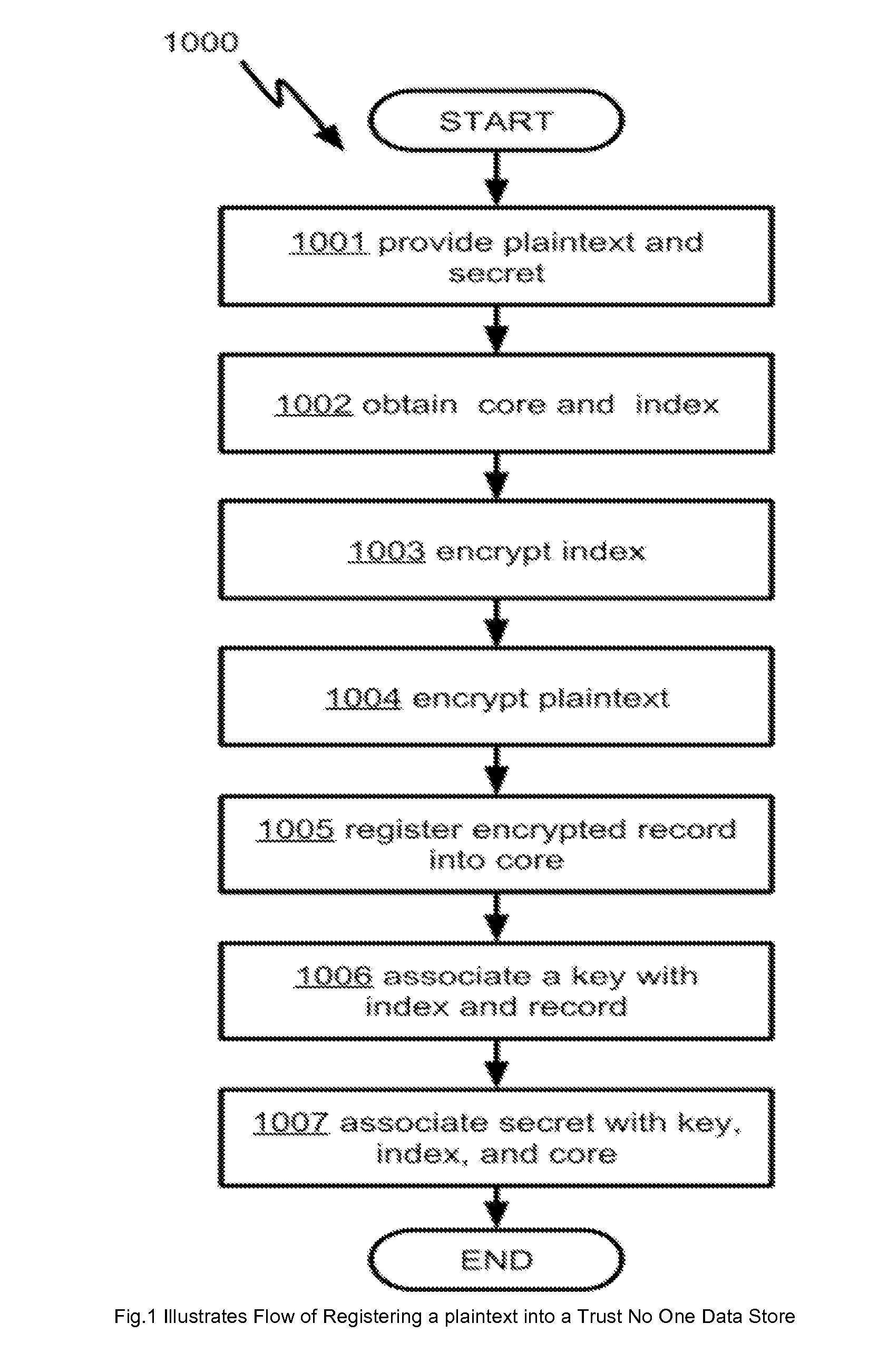
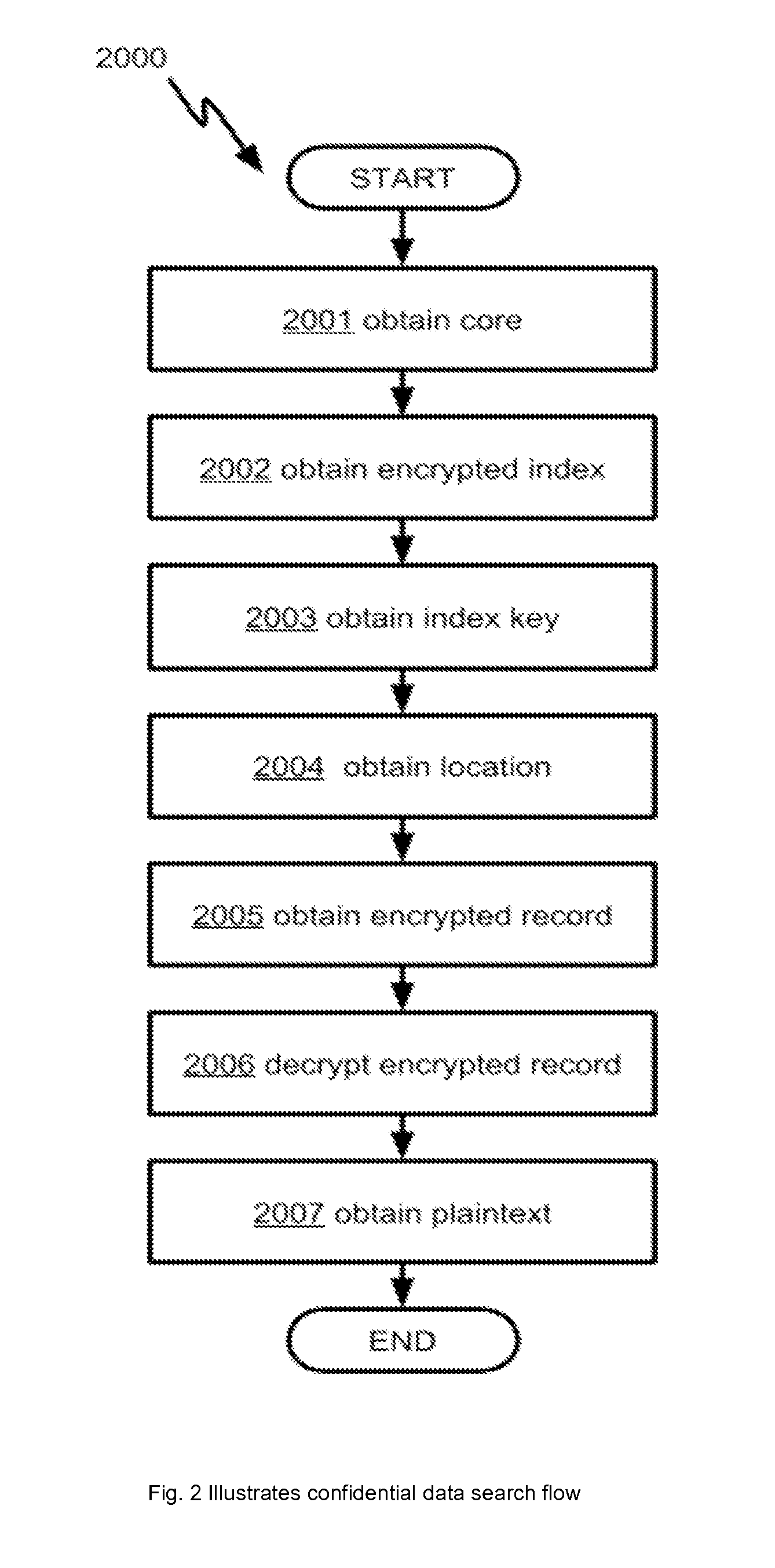
Methods and apparatus for sharing encrypted data
The present invention is directed to methods and systems in which data are stored as encrypted records on a computer usable medium, and search requests are processed based on user identities to retrieve the data without decrypting all the stored records. Individual decryption keys are associated with identities of respective owners, without being revealed to the owners and are kept internal inside a computer. Finally, all keys are overwritten from the computer usable medium upon completion of each search request to take access away from a superuser or any unauthorized access to the system.
Owner:WONG SZE YUEN
System and method for dynamically setting supervisor password
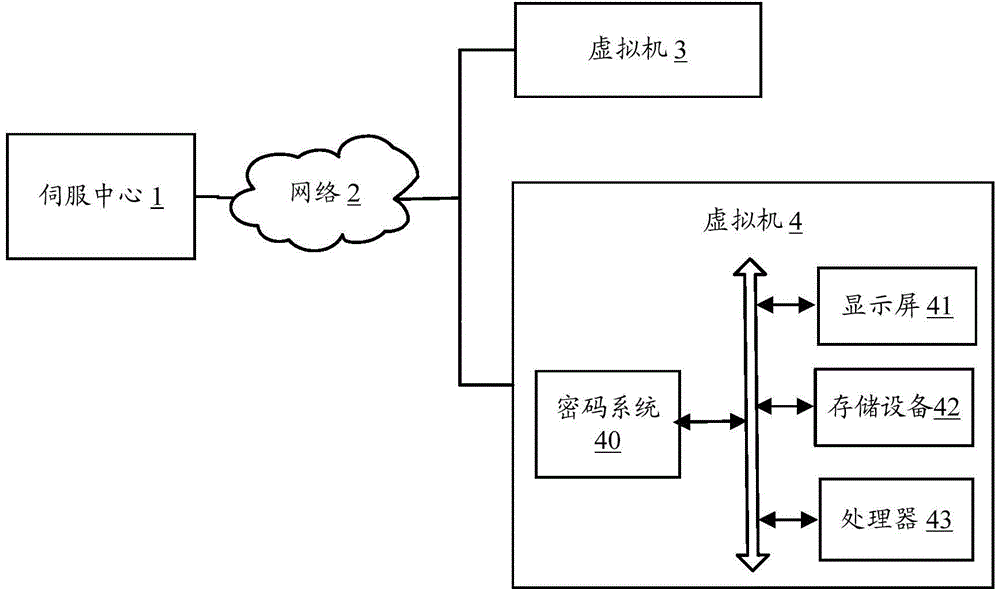
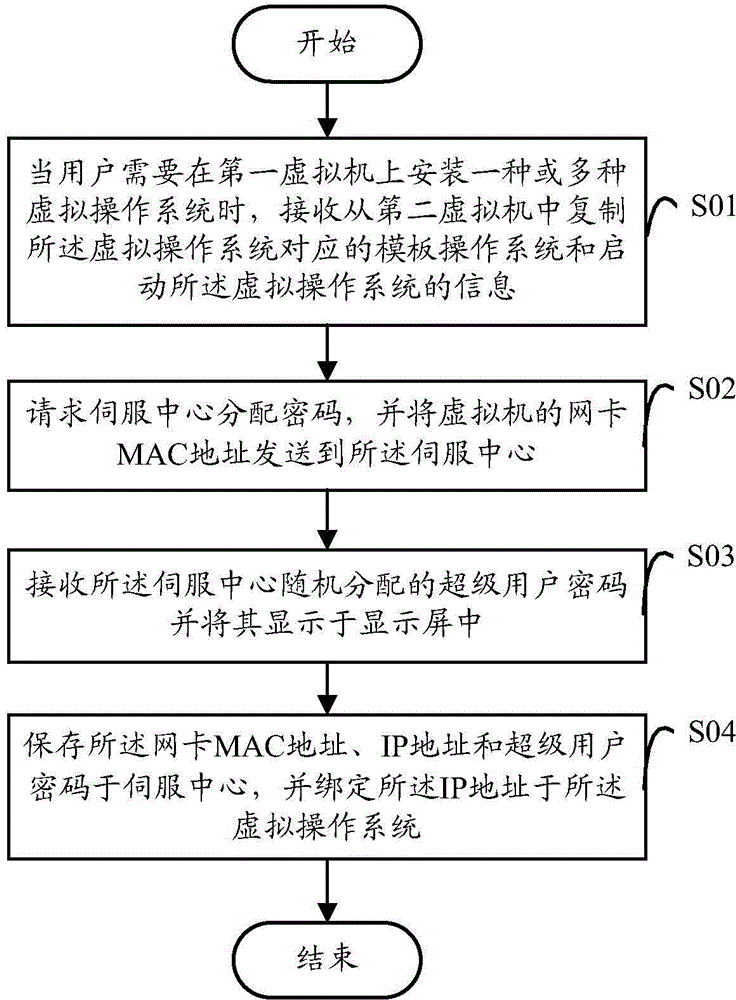
InactiveCN104866759AEffective initial password managementDigital data authenticationUser needsPassword
The invention provides a method for dynamically setting a supervisor password. The method comprises the following steps: when a user needs to install one or a plurality of virtual operating systems on a first virtual machine, copying a template operating system corresponding to the virtual operating system, and receiving information used for starting the virtual operating system; requesting a servo center to distribute a password, and meanwhile, sending a network card MAC (Media Access Control) address of the virtual machine to a servo center; and receiving the supervisor password randomly distributed by the servo center, and displaying the supervisor password in a display screen. The invention also provides a system for dynamically setting the supervisor password. Passwords can be randomly generated from the servo center to dynamically and effectively manage an administrator initial password of each operating system.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com