Database access supervision method
A database and application system technology, applied in the database field, can solve problems such as buffer overflow security attacks, failure of database management system security functions, security protection, etc., to achieve the effect of ensuring transparency and wide applicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be further described below in conjunction with the accompanying drawings.
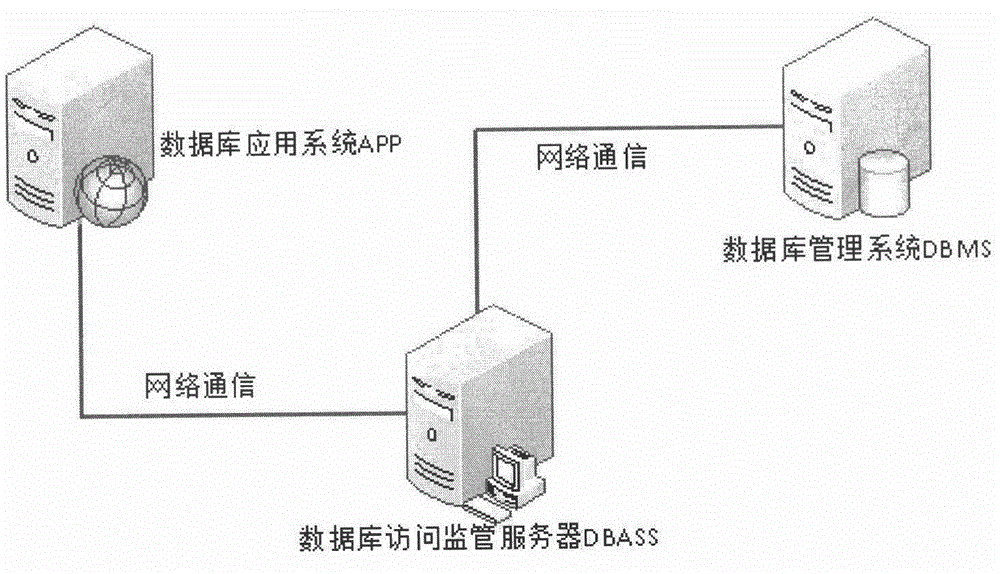
[0021] The database access supervision method is mainly implemented by the database access supervision server DBASS (Database Access Supervising Server), and the DBASS is deployed between the database application system APP (Application) and the database management system DBMS (Database Management System), such as figure 1 shown.
[0022] DBASS cuts off the network communication between the machine where the APP is located and the DBMS, so that direct interaction between the APP and the DBMS is impossible. The access of the APP to the database must be processed by the DBASS, so that the DBASS controls the connection process of the application system to the database and after the connection is established. all access processes.
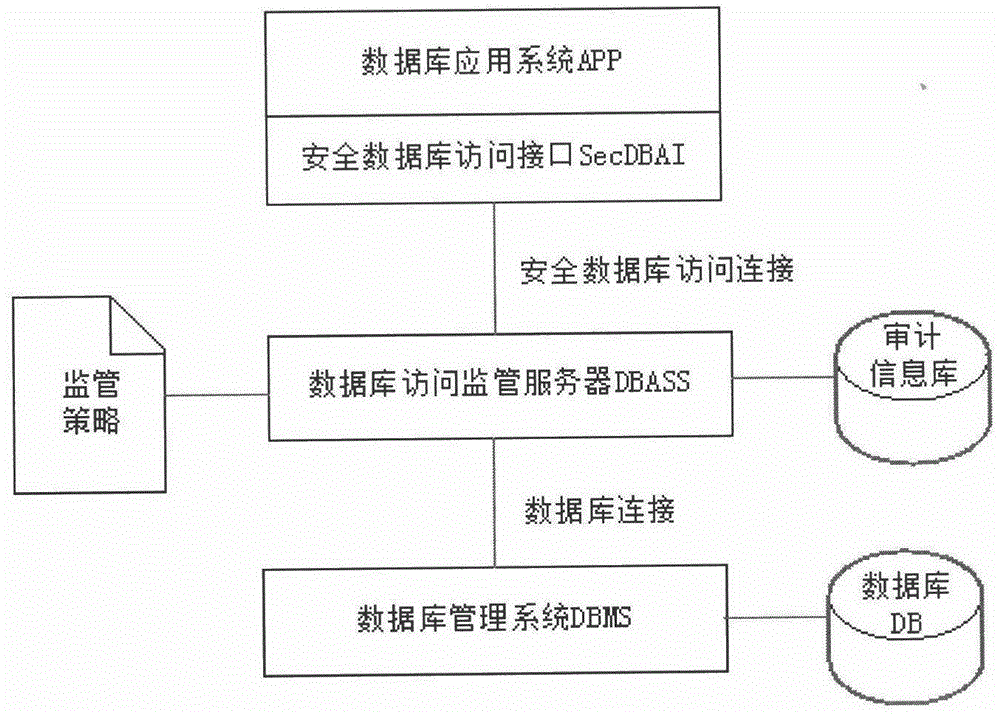
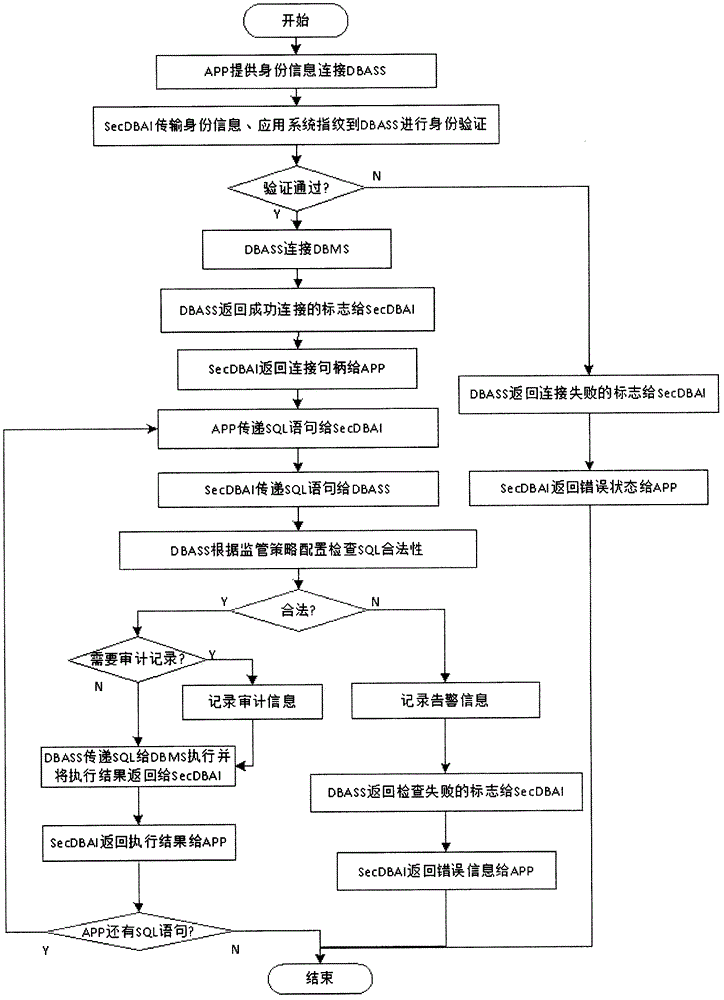
[0023] In order to obtain the characteristics of the application system and provide transparent secure database access support for the applic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com