Sub-zone protecting method and device of Android system
A technology for Android systems and protection devices, applied in computer security devices, platform integrity maintenance, instruments, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] In order to explain in detail the technical content, structural features, achieved goals and effects of the technical solution, the following will be described in detail in conjunction with specific embodiments and accompanying drawings.
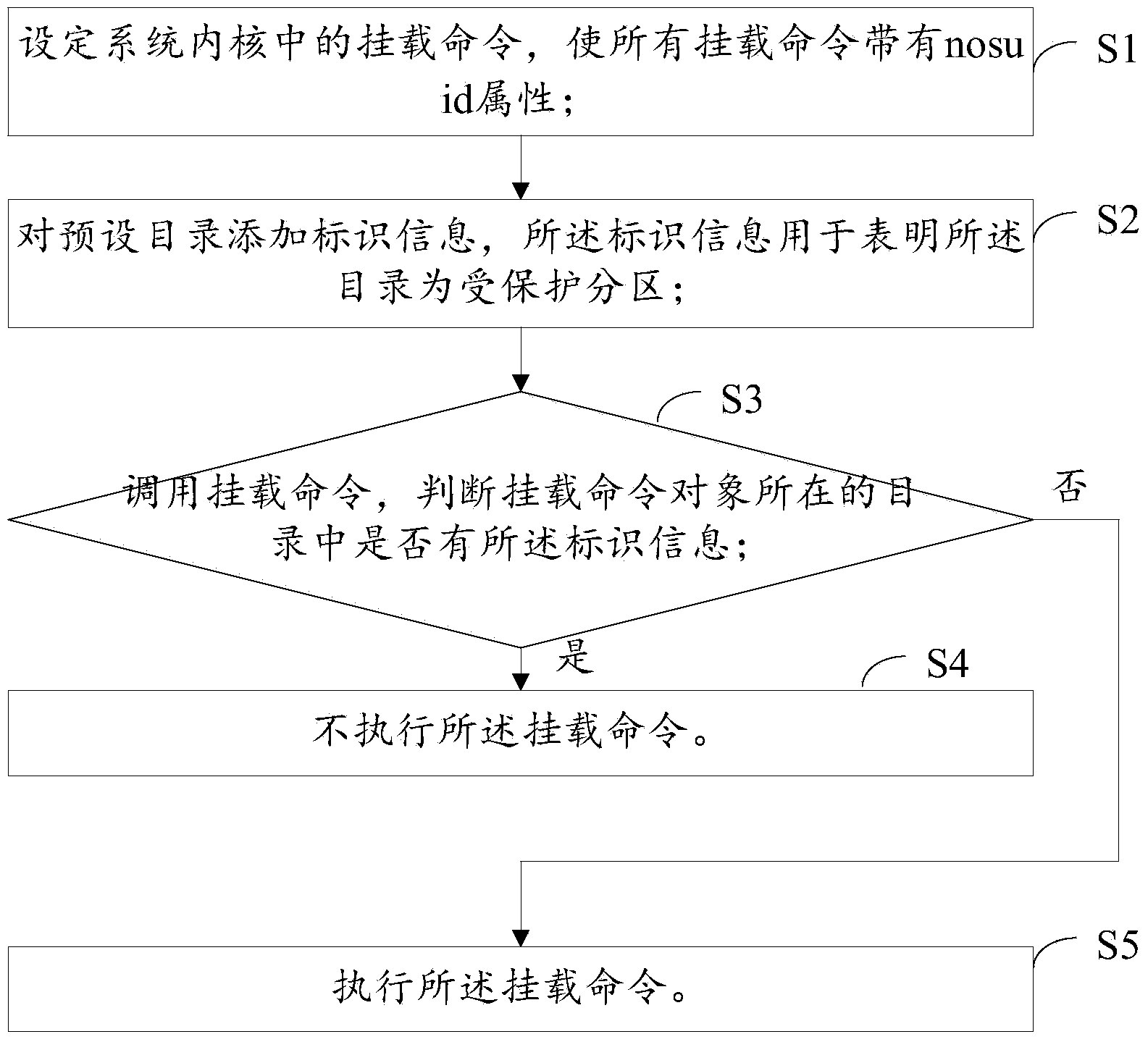
[0039] see figure 1 , is a flow chart of the partition protection method of the Android system described in an embodiment of the present invention; the method includes the following steps:
[0040] S1. Set the mount commands in the system kernel, so that all mount commands have the nosuid attribute;
[0041] S2. Add identification information to the preset directory, where the identification information is used to indicate that the directory is a protected partition;
[0042] S3. Call the mount command, and judge whether there is the identification information in the directory where the mount command object is located; if so, enter step S4, otherwise enter step S5;
[0043] S4. The mount command is not executed.
[0044] S5. Execut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com