Authorization control method aimed at server
An authorization control and server technology, which is applied in the field of authorization control for servers, can solve problems such as illegal cracking, destruction, and authorization is not guaranteed, and achieves the effect of improving reliability and encryption strength.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The above and other technical features and advantages of the present invention will be described in more detail below in conjunction with the accompanying drawings.
[0032] First of all, the present invention controls the number of users using the server and divides them into four types. Of course, this can be increased or decreased according to actual needs. In this system, users are subdivided according to business needs, divided into four types: The four types are controlled separately, and these four types of users are the number of super users, the number of data maintenance users, the number of VIP users, and the number of online ordinary users.
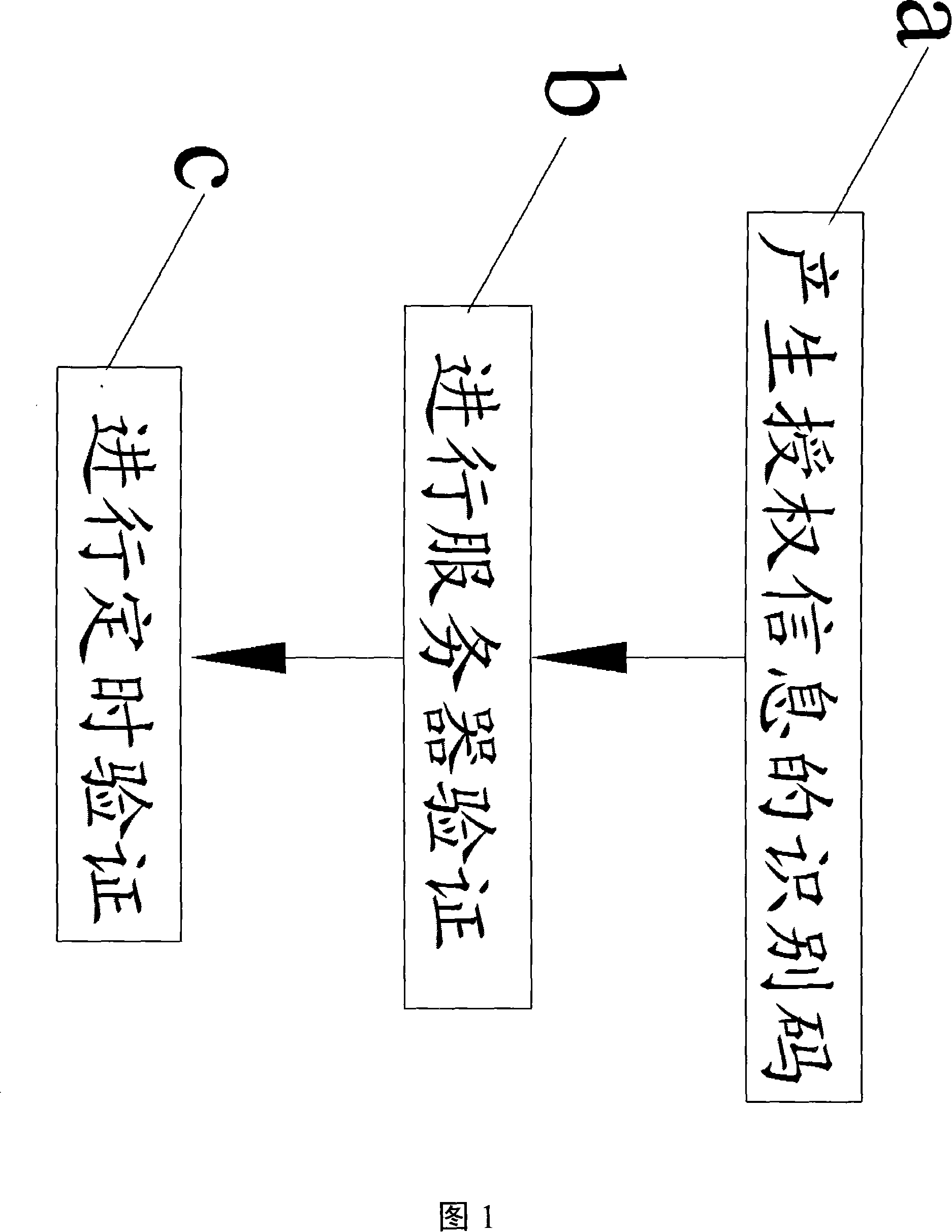
[0033] Please refer to FIG. 1, which is a flow chart of a preferred embodiment of the authorization control method for the server of the present invention; the steps it includes are:
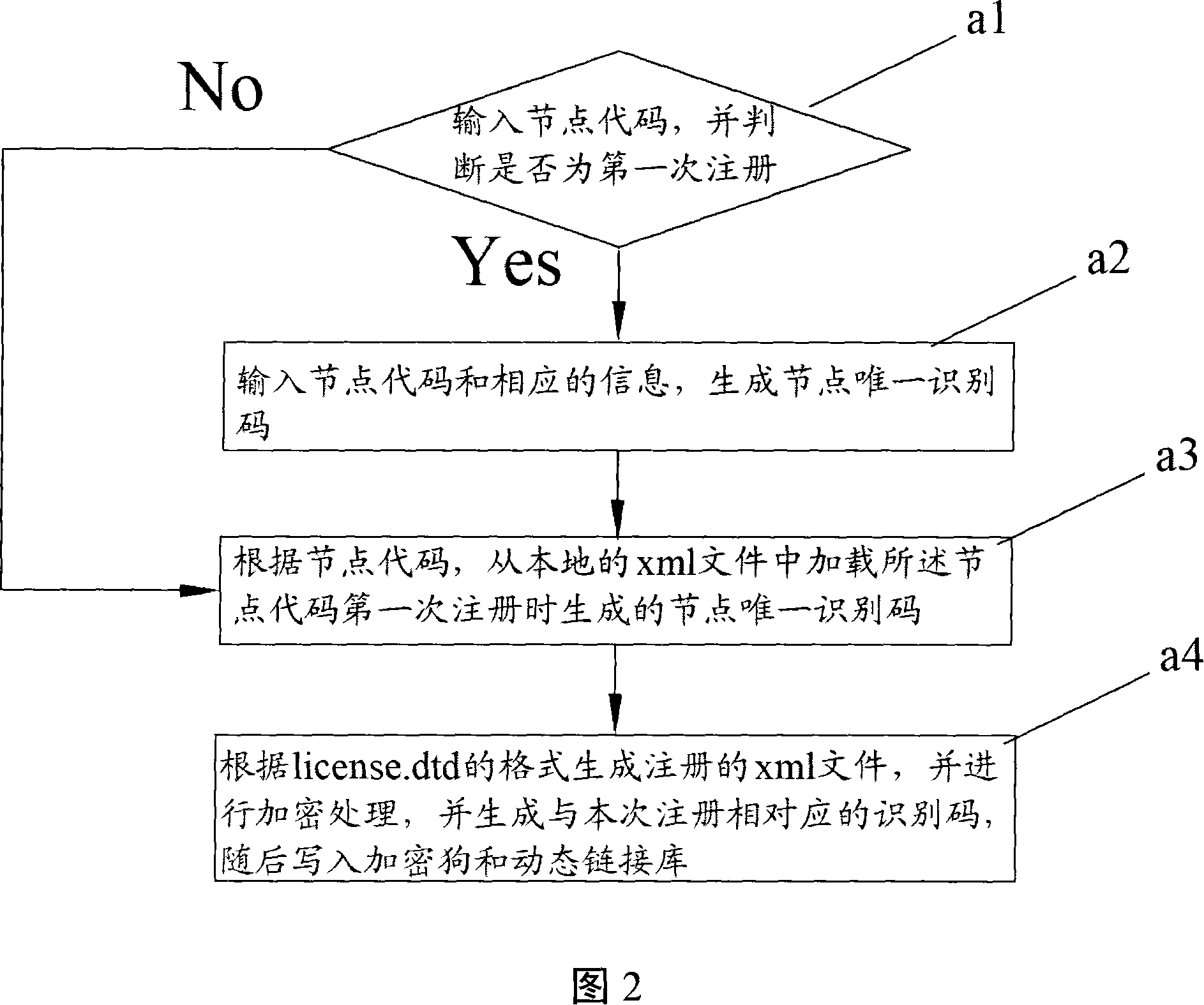
[0034] Step a: generating an identification code for authorization information;
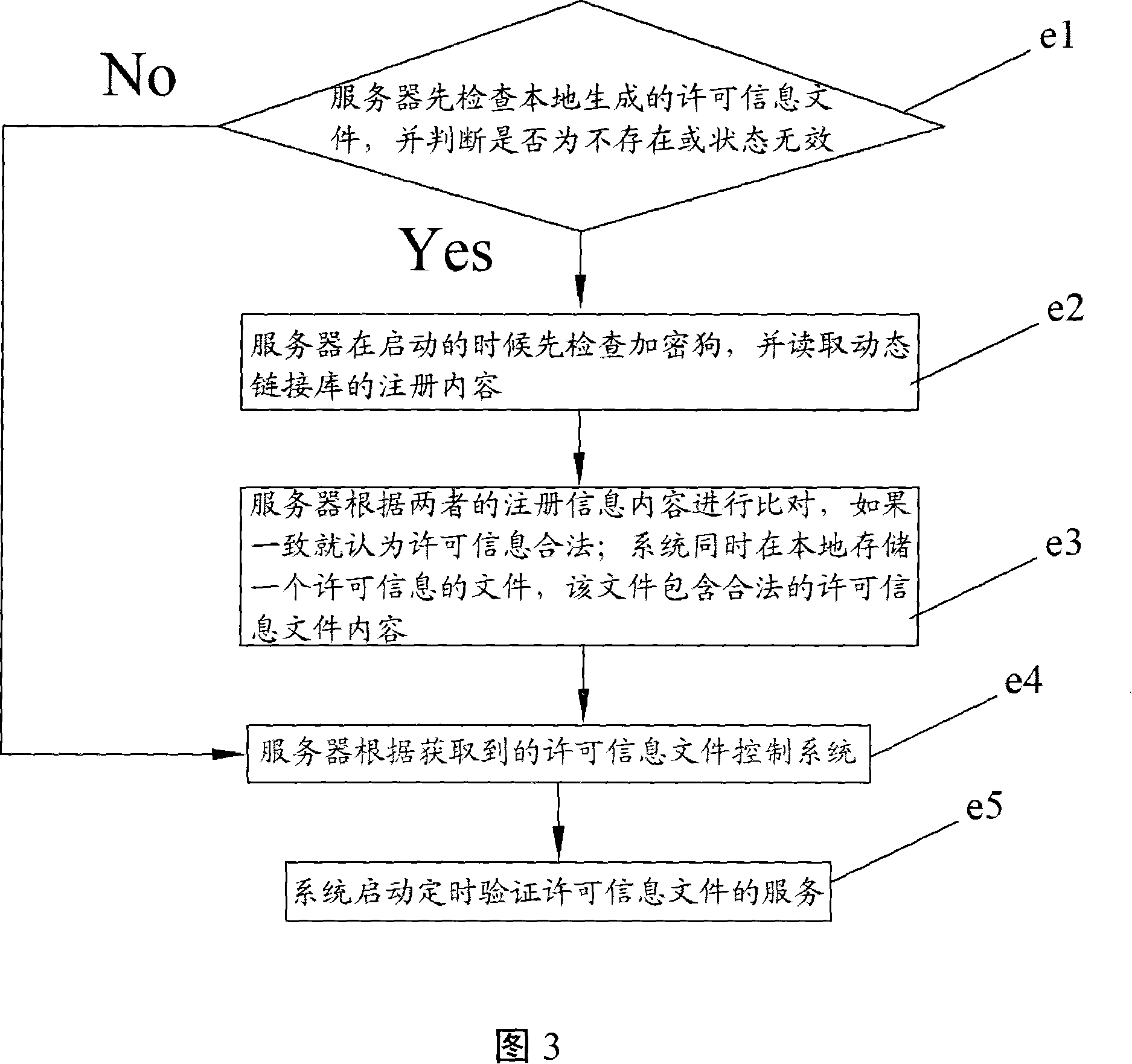
[0035] Step b: Perform server verification;
[0036]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com