Encryption method in data transfer of electric power system
A technology for power systems and encryption methods, applied in information technology support systems, electrical components, circuit devices, etc., can solve problems such as security defects and irreparable losses, achieve high security, improve encryption strength and crack difficulty, security high effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The present invention will be further described in detail below in conjunction with the accompanying drawings, so that those skilled in the art can implement it with reference to the description.
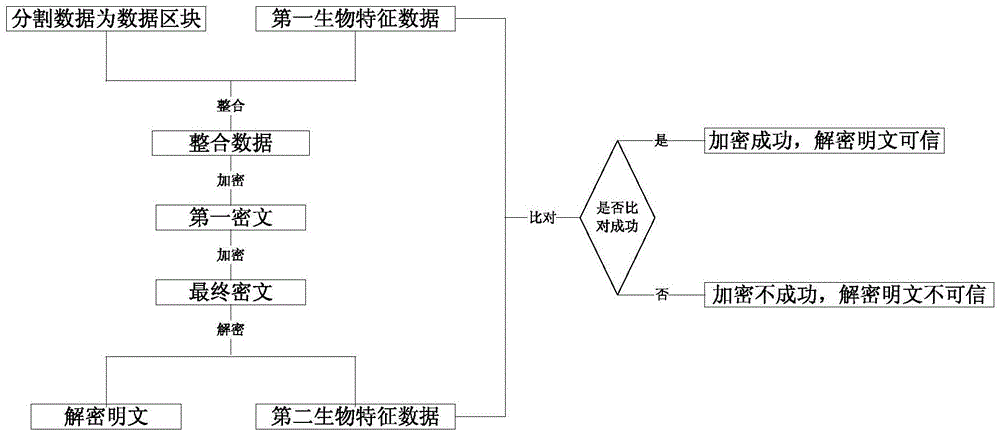
[0032] Such as figure 1 As shown, an encryption method in power system data mobilization includes the following steps:
[0033] When the electromechanical transient simulation system or the electromagnetic transient simulation system serves as the sending end to send data to the other party, the data is divided to generate multiple data blocks.
[0034] Both the electromechanical transient simulation system and the electromagnetic transient simulation system are connected with biometric identification equipment, which is used to collect the voiceprint characteristics and other biological characteristics of the sender. feature, the other biometric features are any one or two of fingerprint features, palmprint features, face features, iris features, keystroke features, and sig...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com