Method for integrating safety E-mail and Lotus Notes
An e-mail and security technology, applied in the direction of electrical components, electrical digital data processing, special data processing applications, etc., can solve problems such as being cracked, strength limited, fixed, etc., to reduce operating steps, improve encryption strength, and reduce learning time Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055] The present invention will be further described below by the following examples.
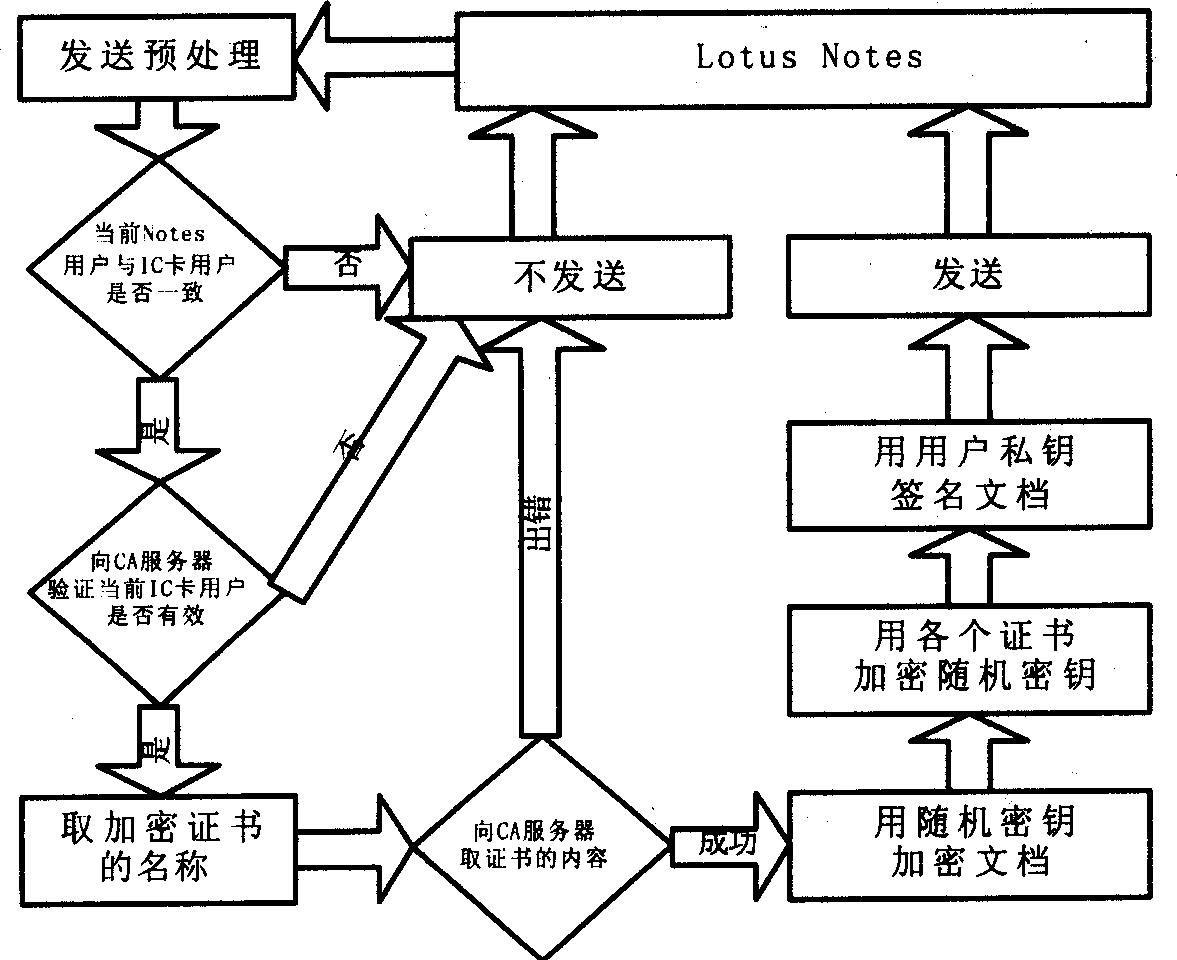
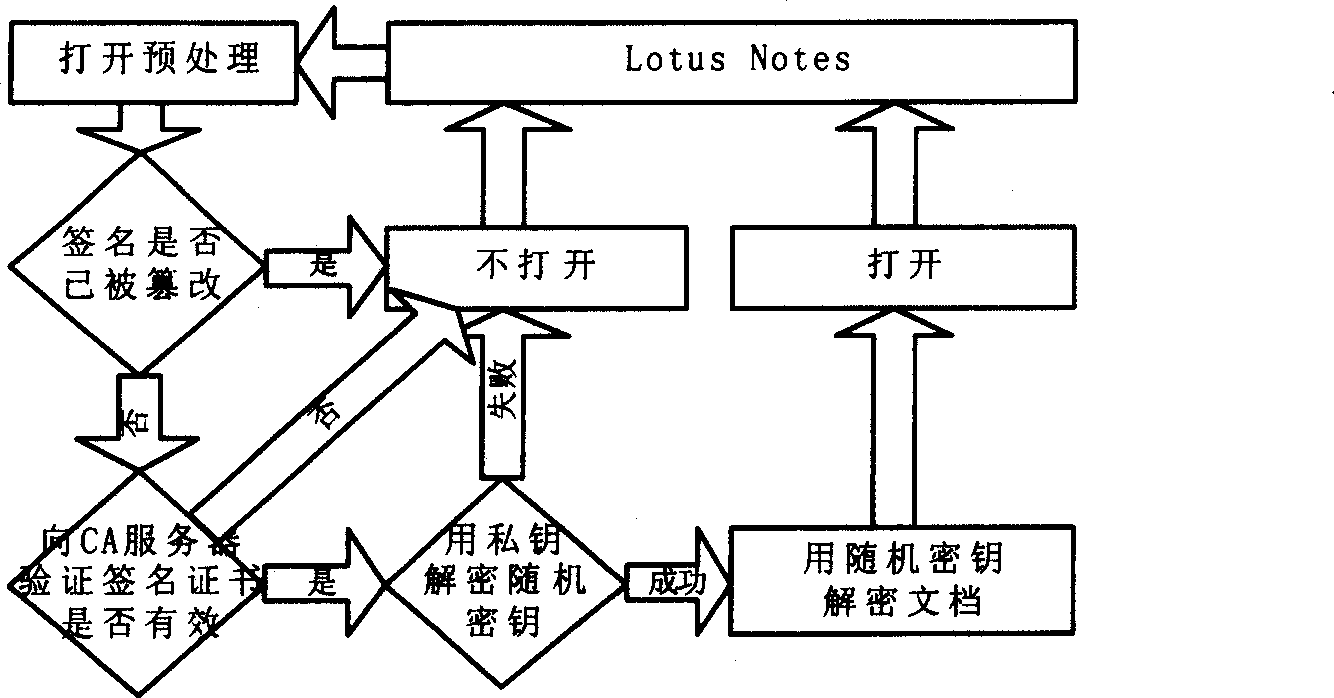
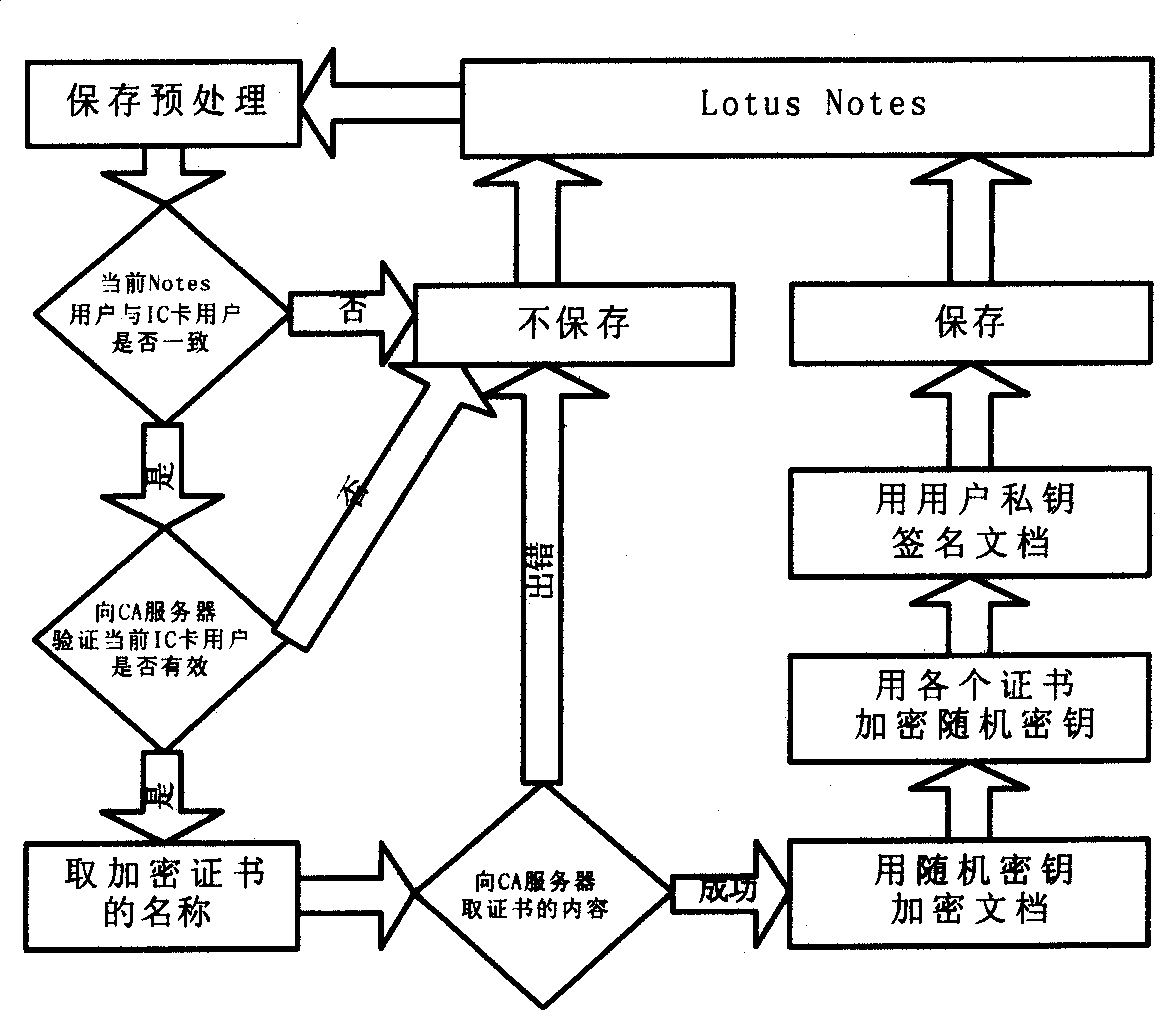
[0056] The Lotus Notes security extension component uses Notes script language and sub-forms to customize the Notes interface. The Lotus Notes security extension component consists of an application layer and a base layer, and the base layer includes a digital management center. In the implementation of Lotus Notes security extension, each Notes user needs to apply for a certificate from the digital management center to identify his identity. The issuance, revocation, downloading, verification of validity, and update of the certificate revocation list will be managed and maintained by the digital certificate management center. The digital certificate corresponding to each Notes user is called the user identifier, and the information contained in the user identifier, including the certificate and its corresponding private key, is called user information. The part of Lotus Notes security e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com