Patents
Literature
42 results about "Email encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Email encryption is encryption of email messages to protect the content from being read by entities other than the intended recipients. Email encryption may also include authentication. Email is prone to the disclosure of information. Most emails are currently transmitted in the clear (not encrypted) form. All emails sent using Gmail or Outlook are encrypted by default. It is possible to send an unencrypted email using Gmail but a warning icon will appear in the address bar. By means of some available tools, persons other than the designated recipients can read the email contents.
Encryption messaging system
ActiveUS8837739B1Easy to useRaise the level of confidentialityKey distribution for secure communicationPublic key for secure communicationKey exchangeS/KEY
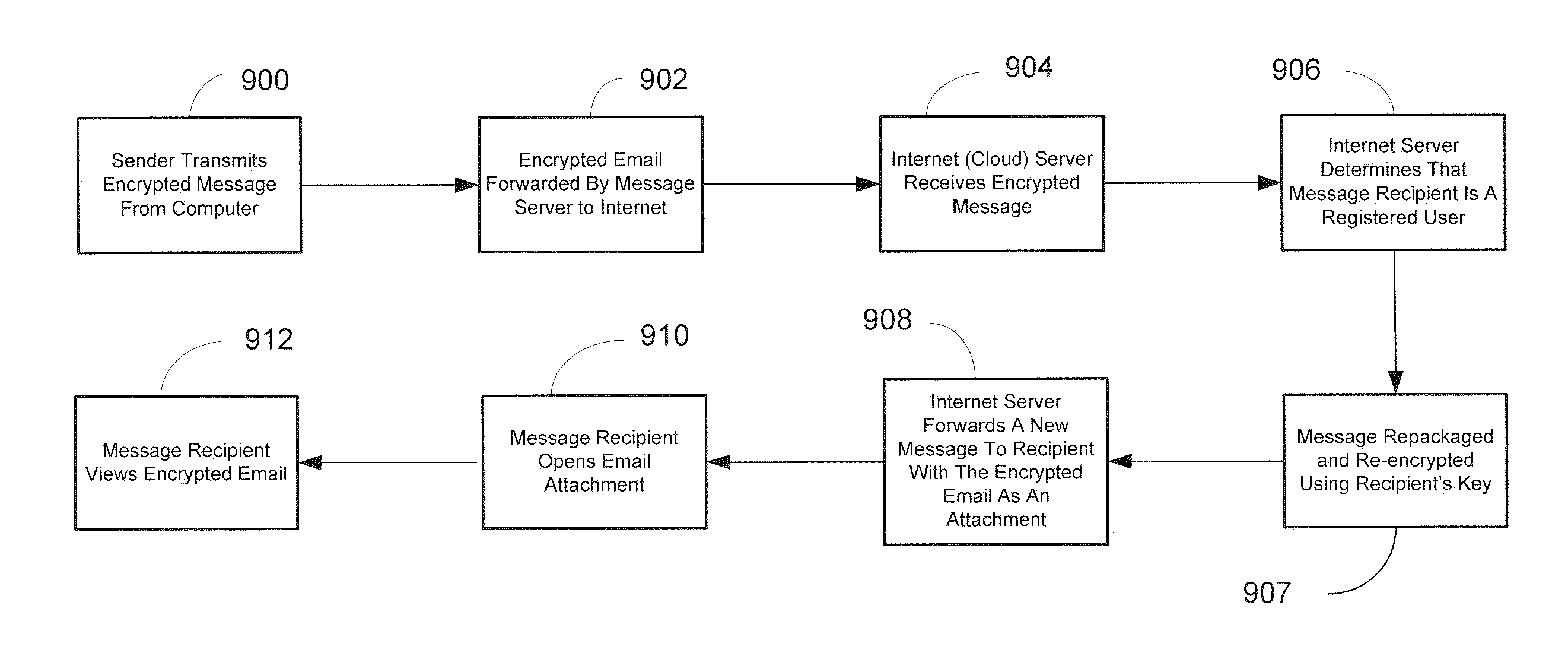
This invention provides a user friendly, email encryption system allowing users to send and receive encrypted messages for registered and unregistered users. Encrypted messages can be sent to registered or non-registered users by transmitting the encrypted message to cloud system servers. The cloud system servers acquire certificates from certificate authorities or any end-to-end exchange of keys between the sender and the recipient of the encrypted message. For registered users, messages sent by senders are encrypted by the sender and sent to the cloud system servers which decrypt the message and re-encrypt the message with the recipient's key. For non-registered users, once the encrypted message is decrypted at the cloud system servers, another message is sent to the non-registered informing them that an encrypted message awaits them if they select a link in the message which allows them to log into the cloud system servers and view the original message.
Owner:IDENTILLECT TECH
System and Method for End-to-End Electronic Mail-Encryption
InactiveUS20090327714A1Reduce riskCreate and manageMultiple keys/algorithms usageUser identity/authority verificationInternet privacyAuthorization
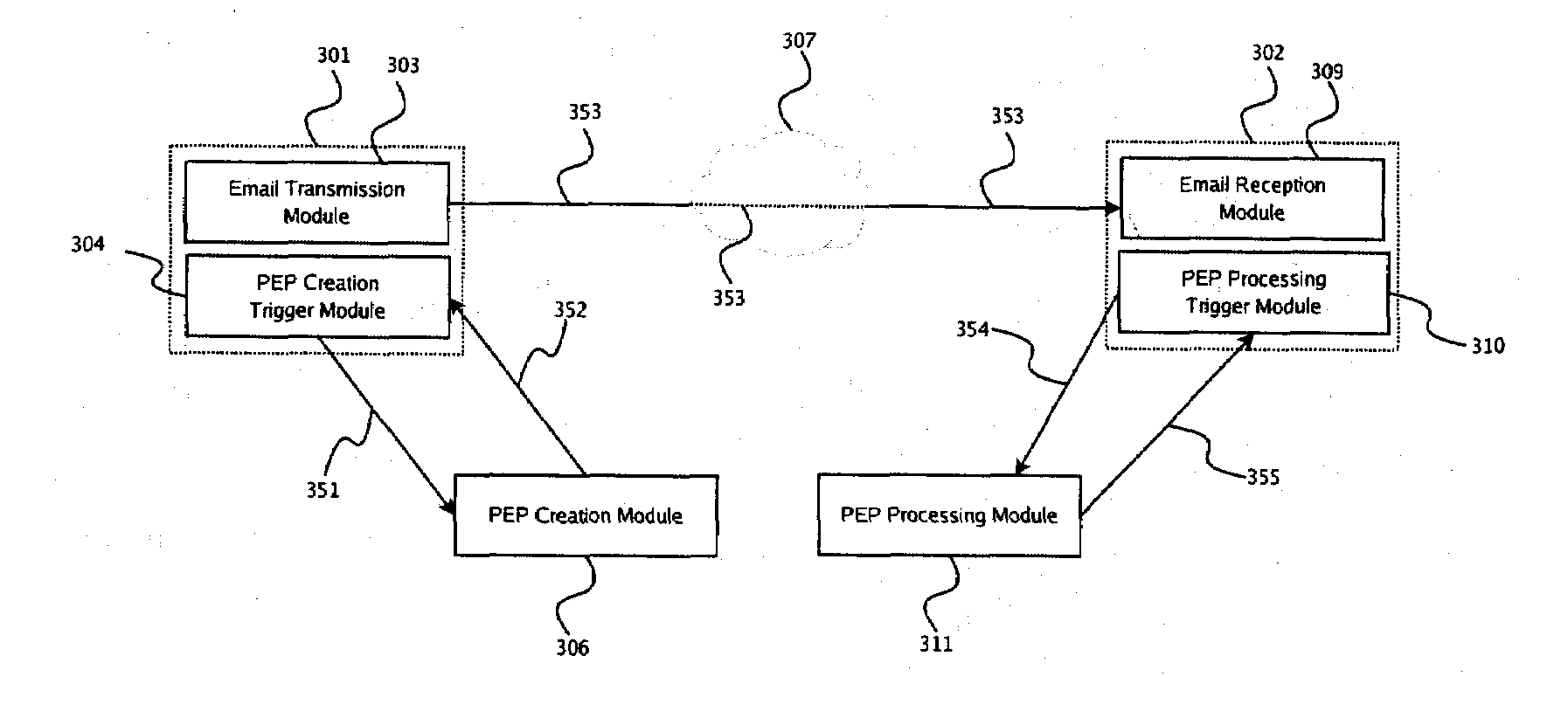
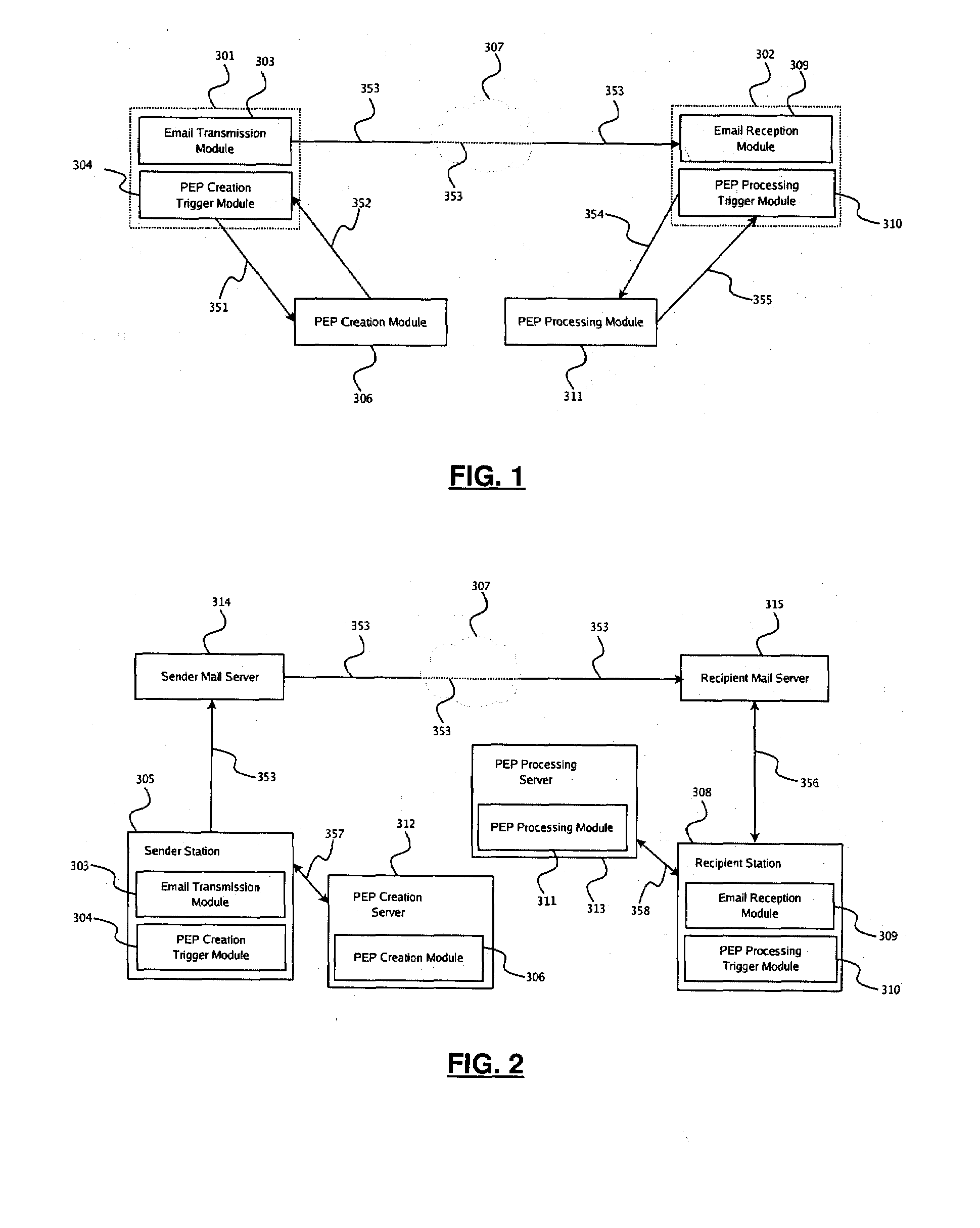
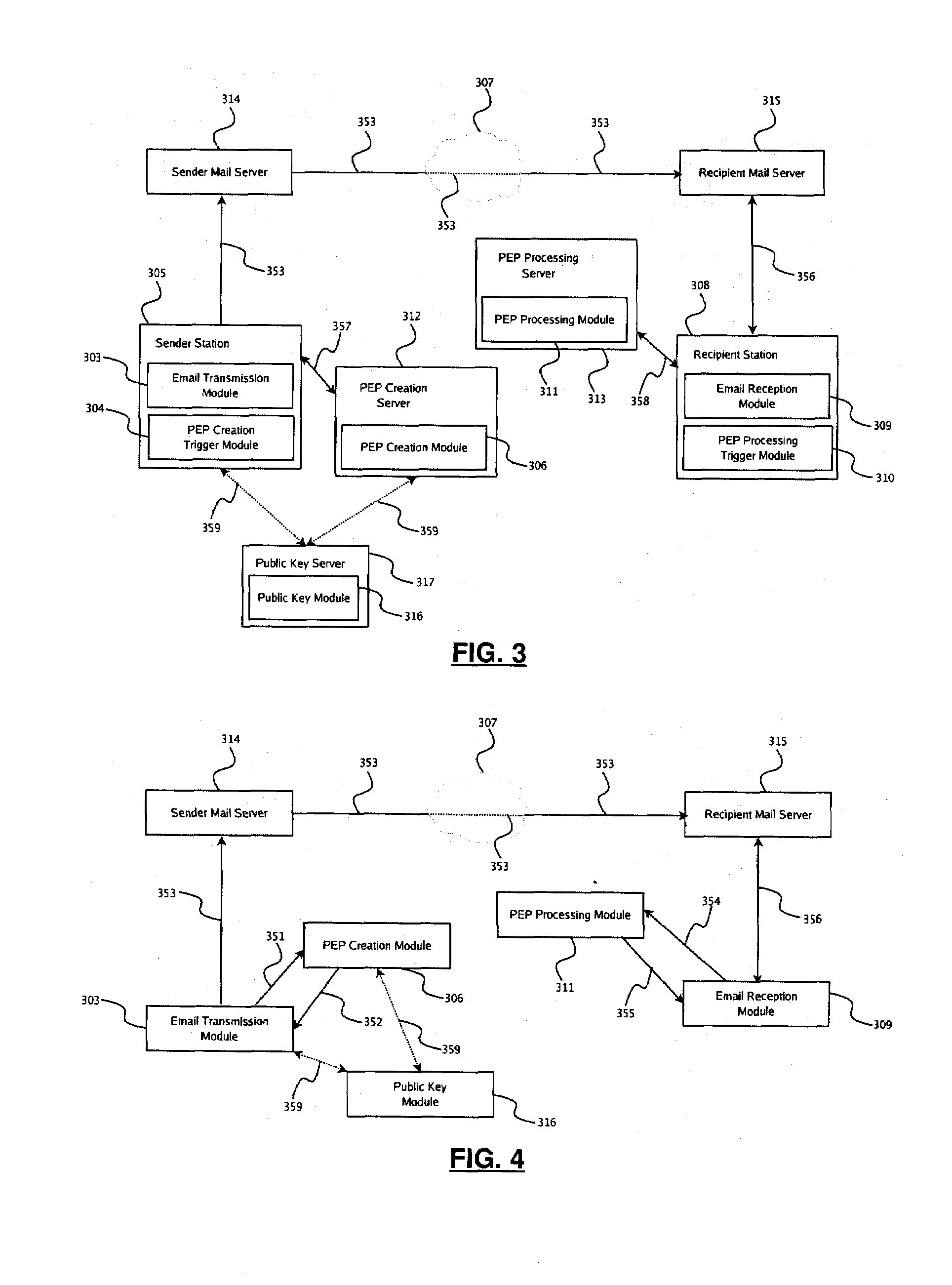
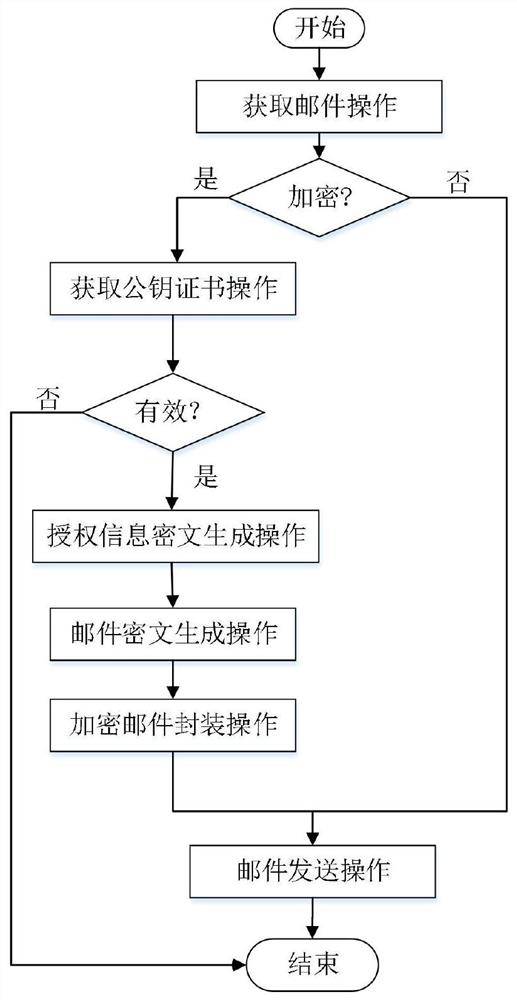
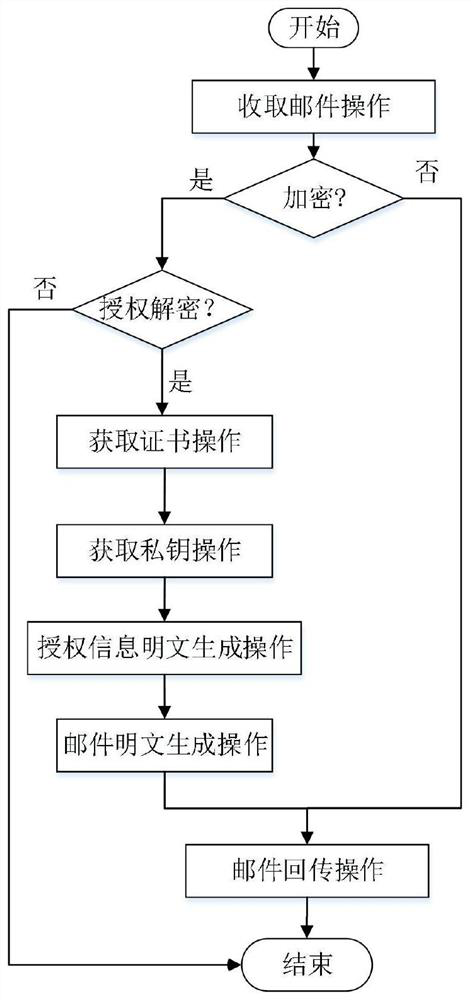
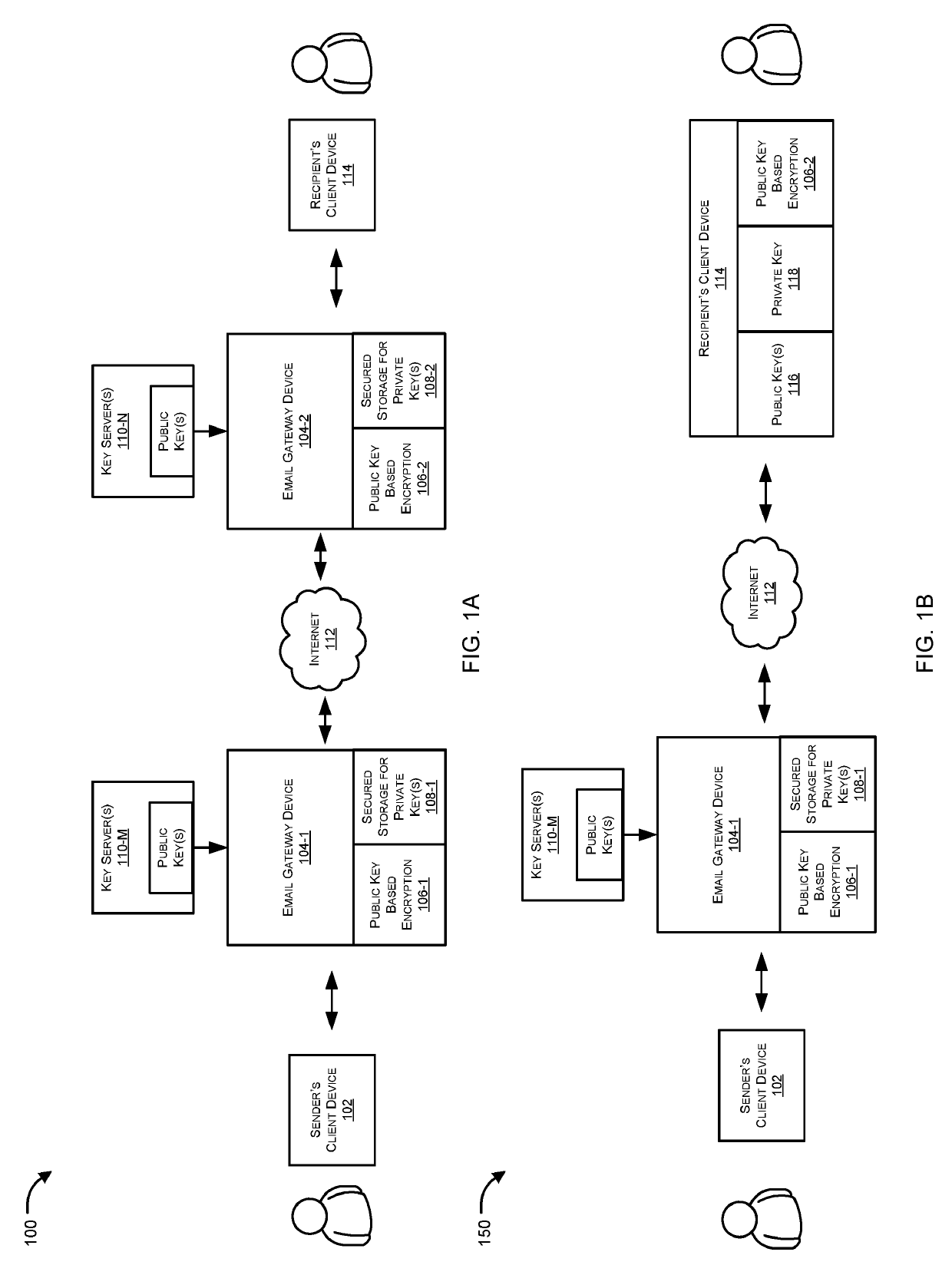
The present disclosure provides a system and method for end-to-end electronic mail encryption. In one embodiment, the sender contacts a payload-encryption-packet creation server which receives the message the sender would like to encrypt, generates an encrypted message and a payload-encryption-packet, and returns both to the sender. The sender then uses his regular email infrastructure to transmit to the recipient the encrypted message and the payload-encryption-packet as a single email. Upon receiving the sender's email, the recipient contacts a payload-encryption-packet processing server and sends it the payload-encryption-packet and authorization information. Depending on the validity of the authorization information, said server processes the payload-encryption-packet and provides the recipient with information usable for extracting the original message from the encrypted message.
Owner:KRYPTIVA
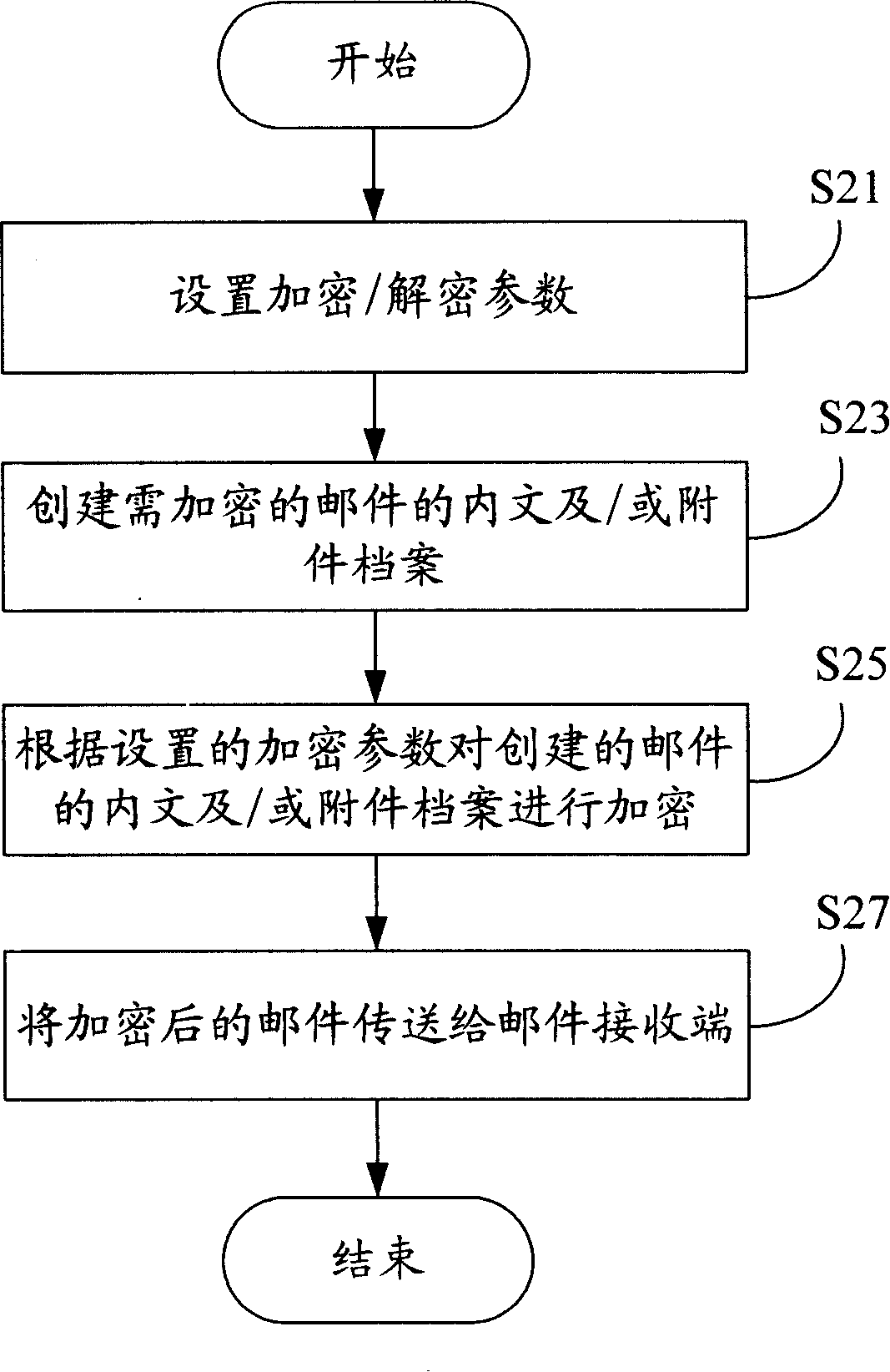
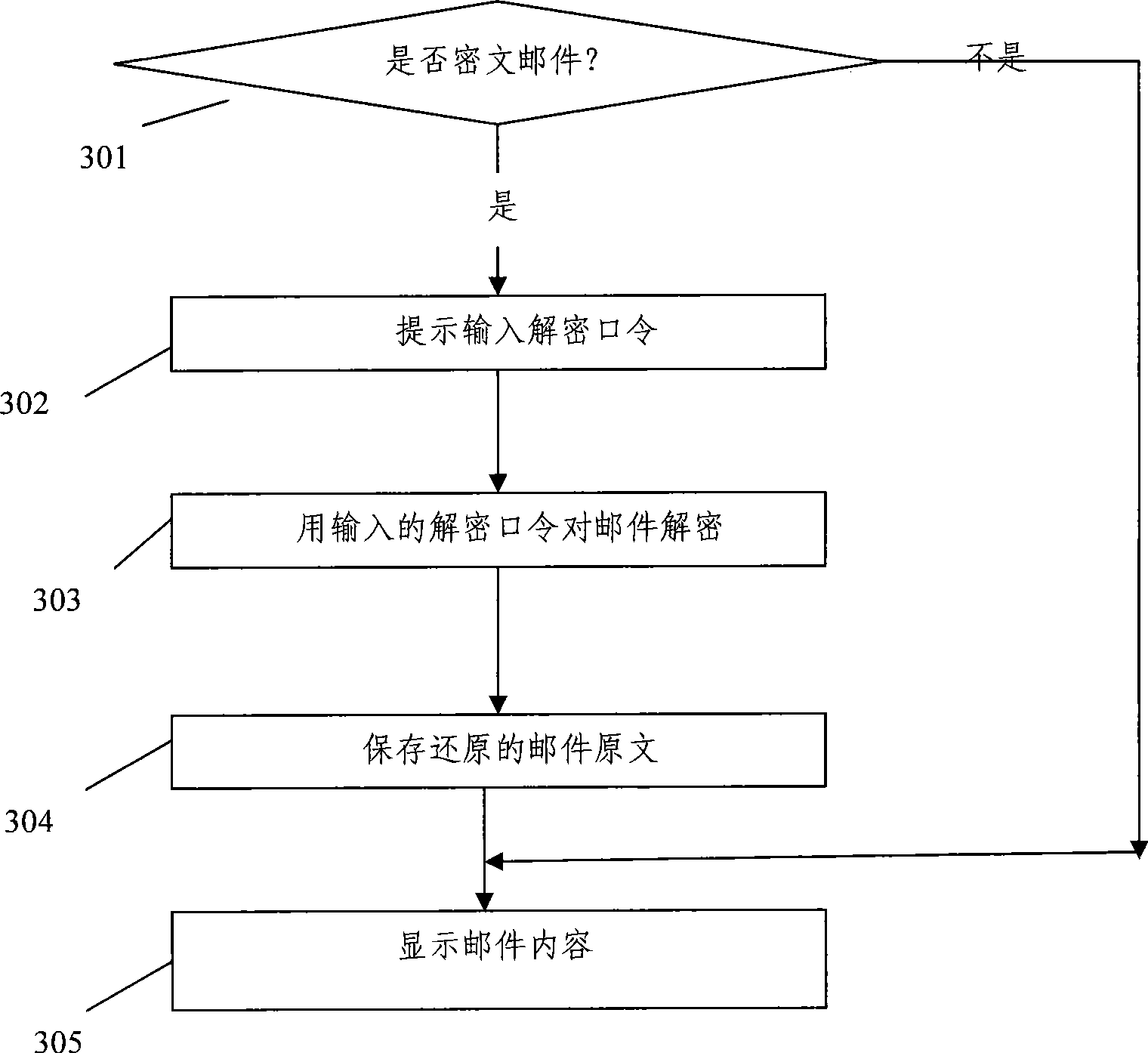
Email encryption/decryption system and its method
InactiveCN101170401AConsider securityPrevent leakageData switching networksSecuring communicationInternet privacyCommunications software
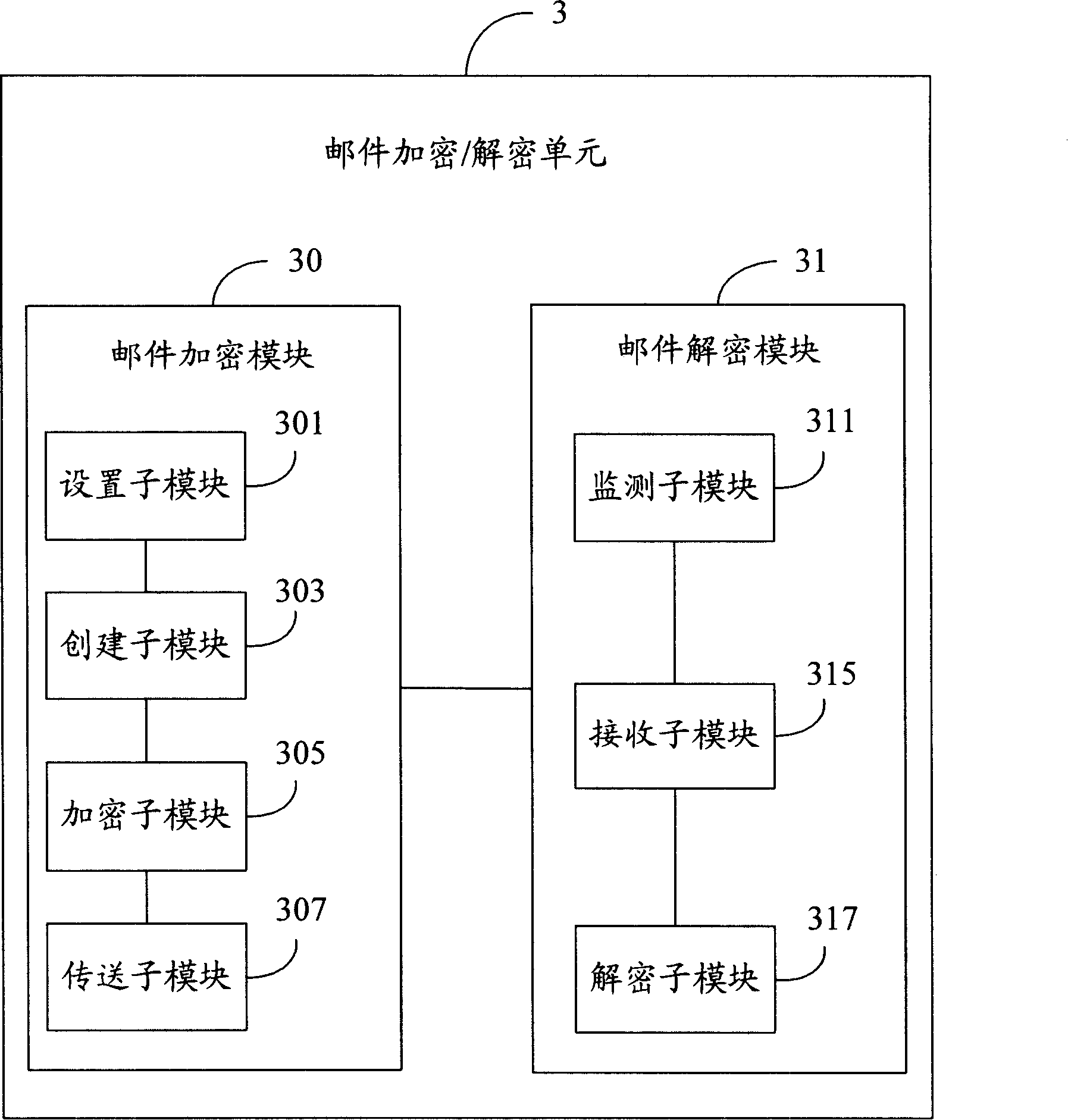
The invention provides a mail encryption / decryption system comprising a plurality of computers with communication connection mutually. The computer is arranged with mail communication software and a mail encryption / decryption unit which comprises a mail encryption module which is used to set parameters for mail encryption / decryption. The mail communication software is applied to establish a mail text and / or an attachment file to be encrypted. The mail text and / or the attachment file is / are encrypted in accordance with the set mail encryption parameters and the encrypted mail is sent to the computer which receives the mail. The mail encryption / decryption unit also comprises a mail decryption module, which is used to monitor and receive the sent encryption mail. The received encryption mail is decrypted in accordance with the mail decryption parameters and the decrypted mail content is displayed through the mail communication software. The mail encryption / decryption system and the method of the invention avoid the leak of the confidential materials.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
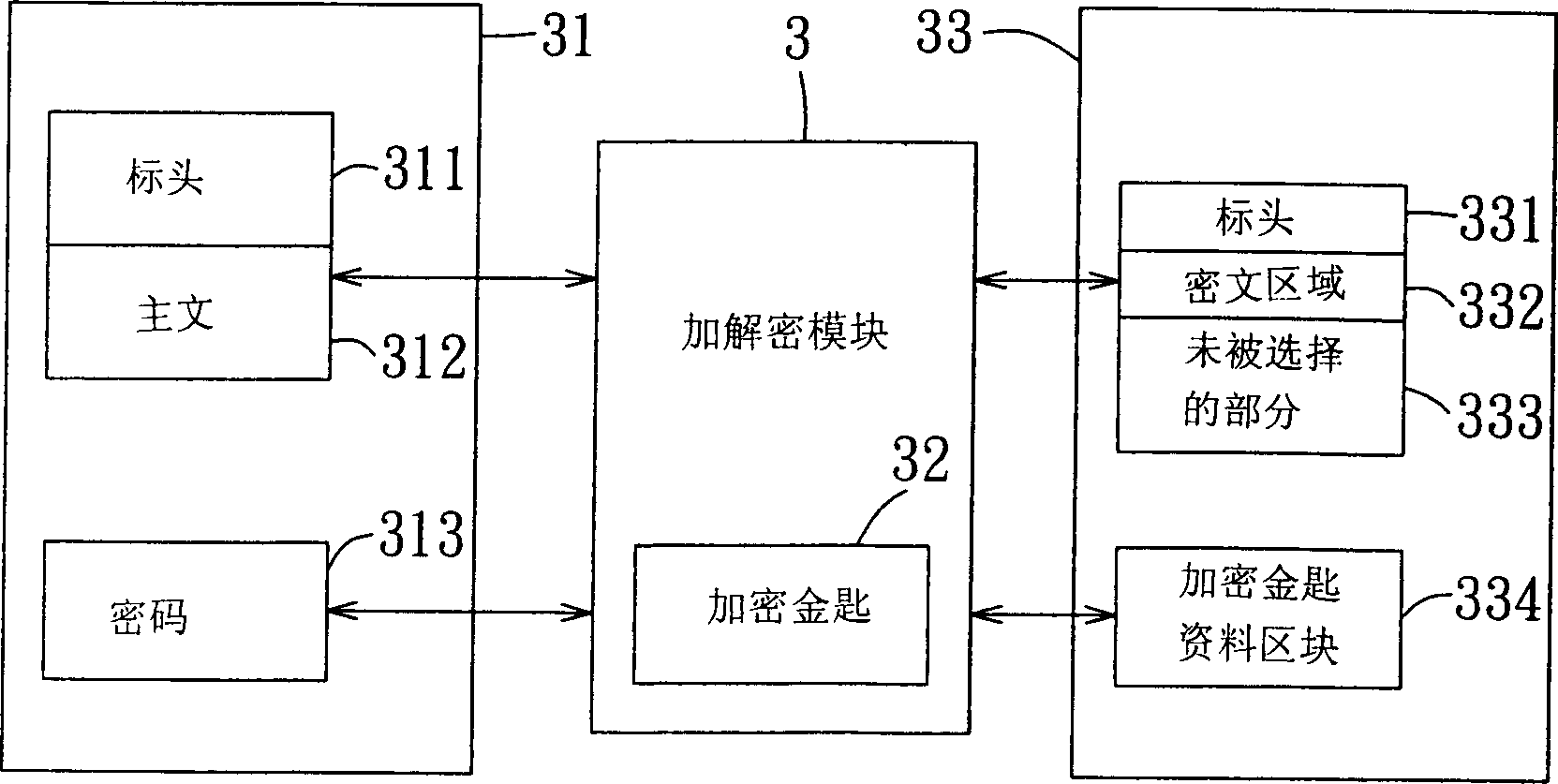
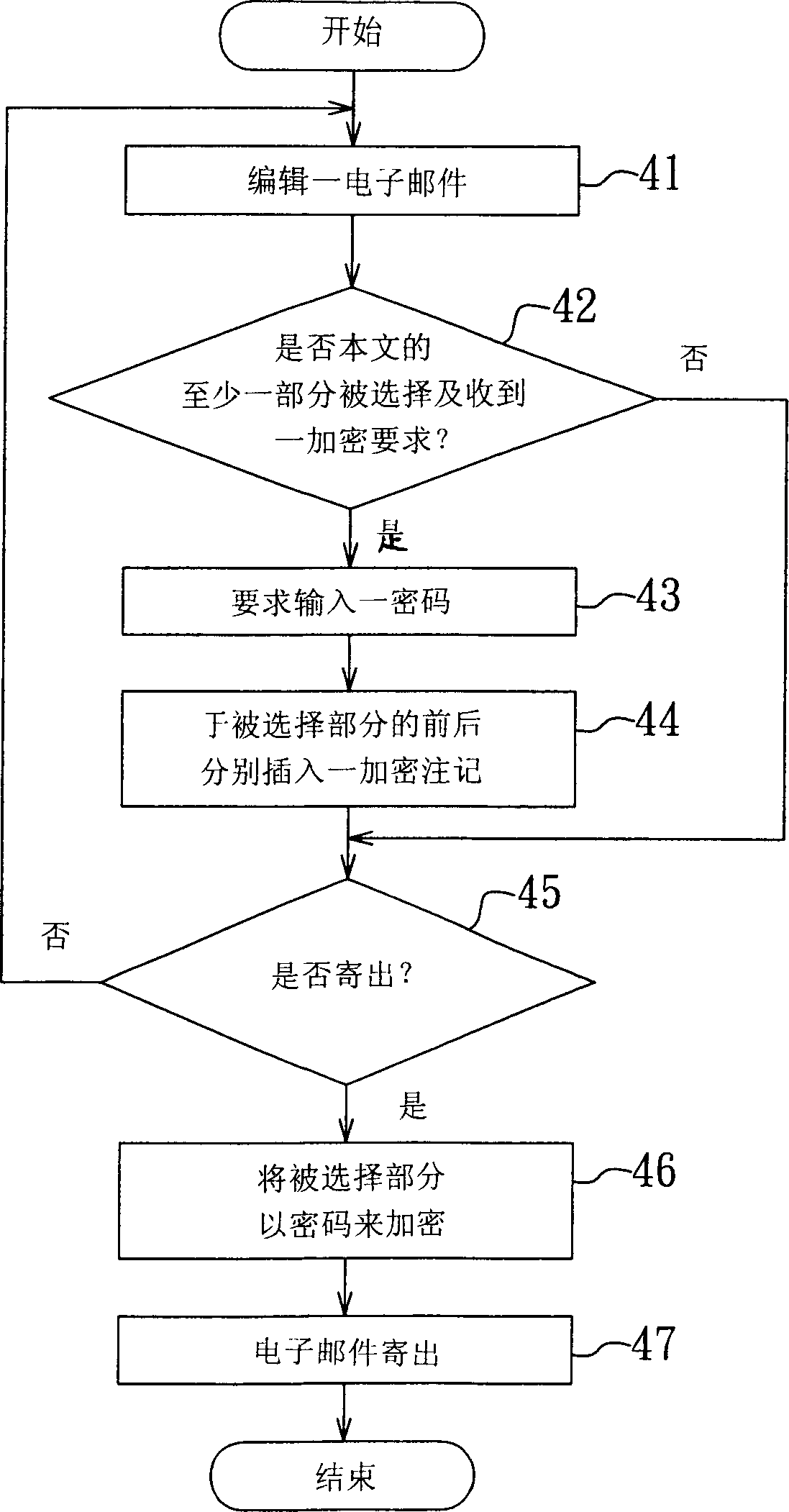
Method for encrypting/decrypting e-mail, and storage medium and module
InactiveUS20060294377A1Easy to useImprove securityUser identity/authority verificationData switching networksPasswordEncryption decryption
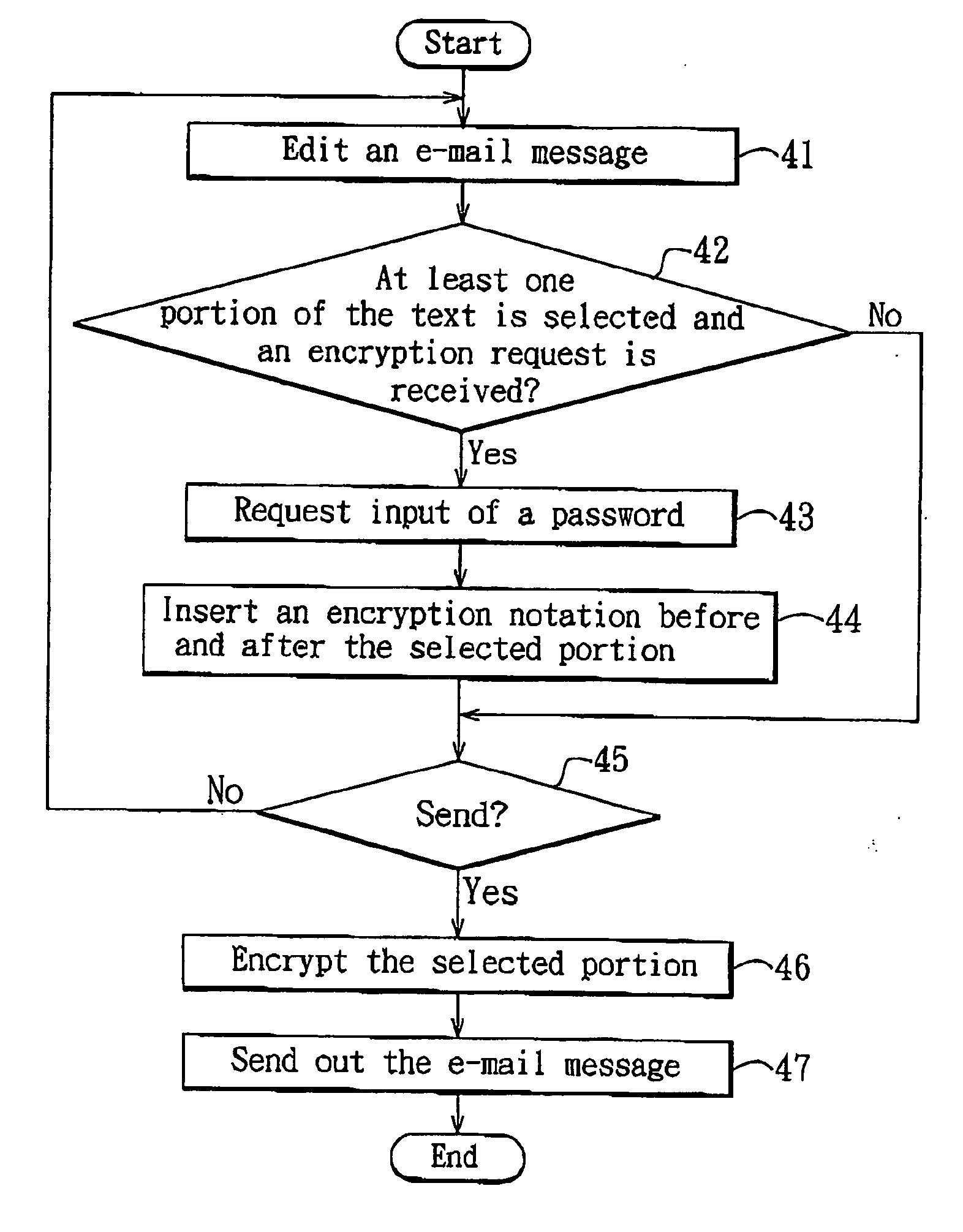
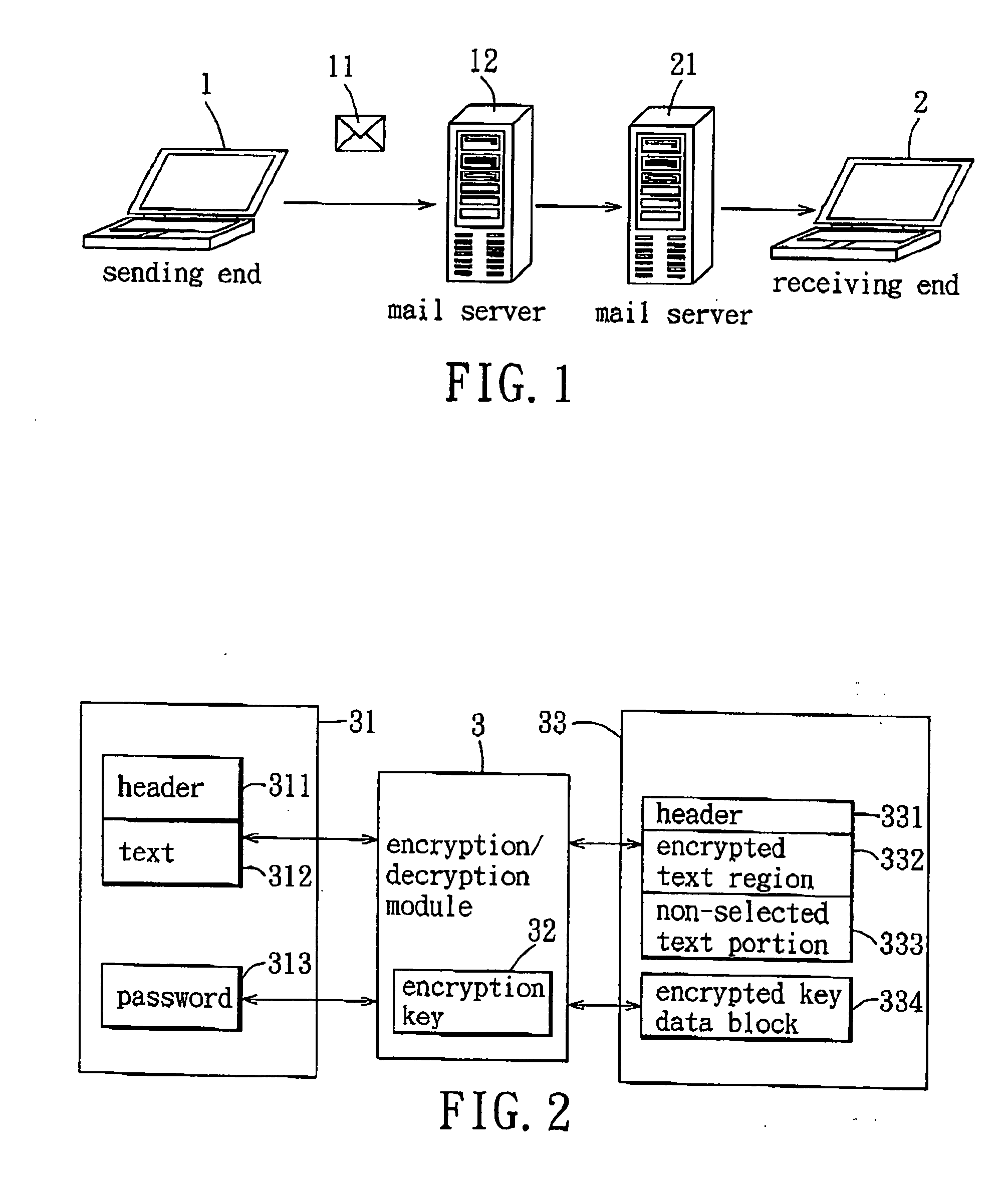
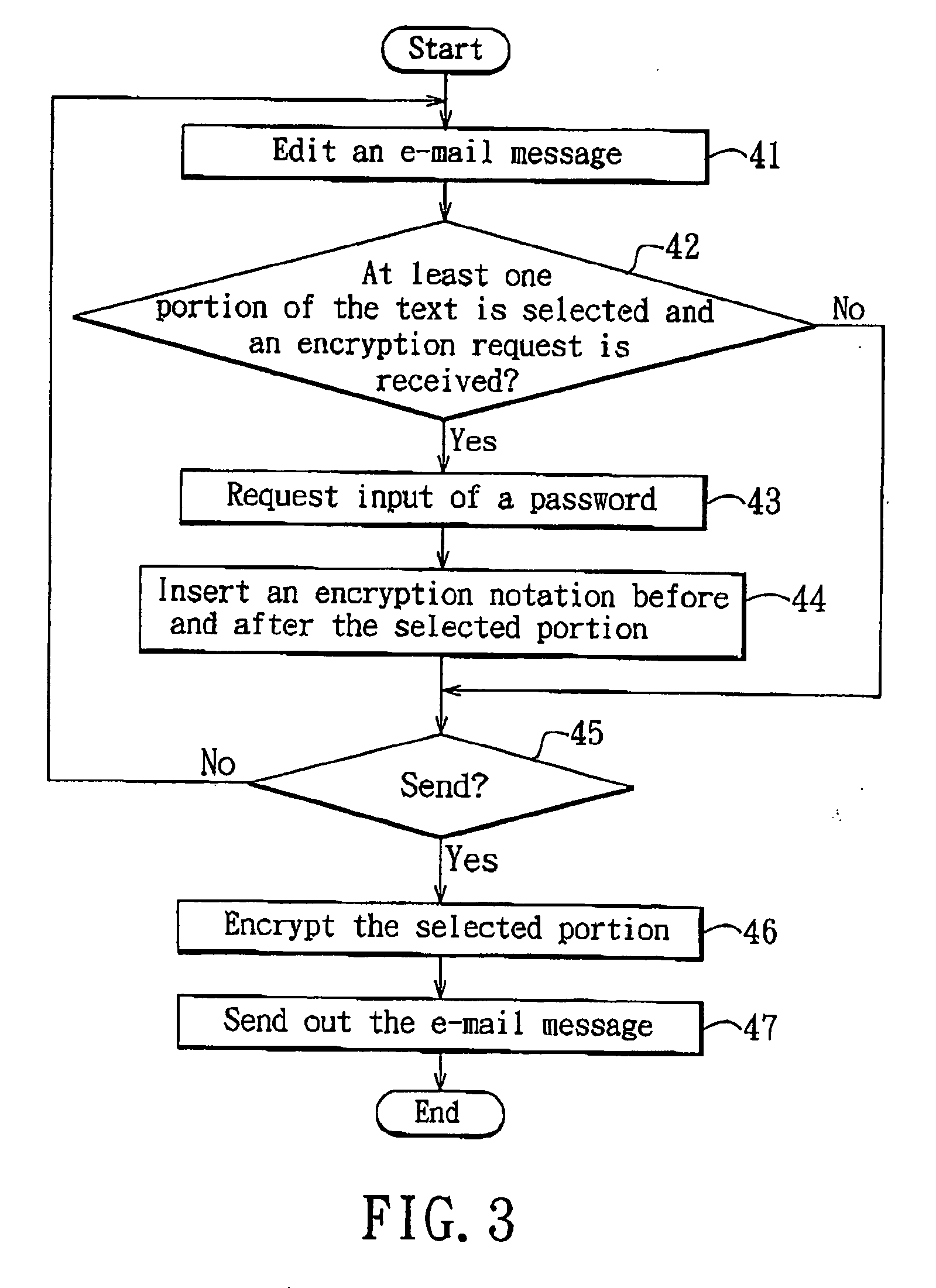
In an e-mail encryption / decryption method, an e-mail encryption process is executed at a sending end before sending an e-mailmessagetoareceivingend. The e-mail encryption process is includes providing an e-mail message having a header and text, requesting selection of at least one portion of the text and decision of a password set corresponding to the selected portion, and encrypting the selected portion into an encrypted text region to be decrypted using the password set before sending the e-mail message to the receiving end upon receipt of a sending request. The header, encrypted text region and non-selected text portion of the e-mail message are timely displayed when the receiving end receives the e-mail message. Thus, the sending end can select to encrypt an e-mail message in part to facilitate use.
Owner:EGIS
Method and system for encrypting and deciphering E-mail
InactiveCN101083524AEnsure safetyAdequate securityData switching networksSecuring communicationCommunications securityEncryption decryption
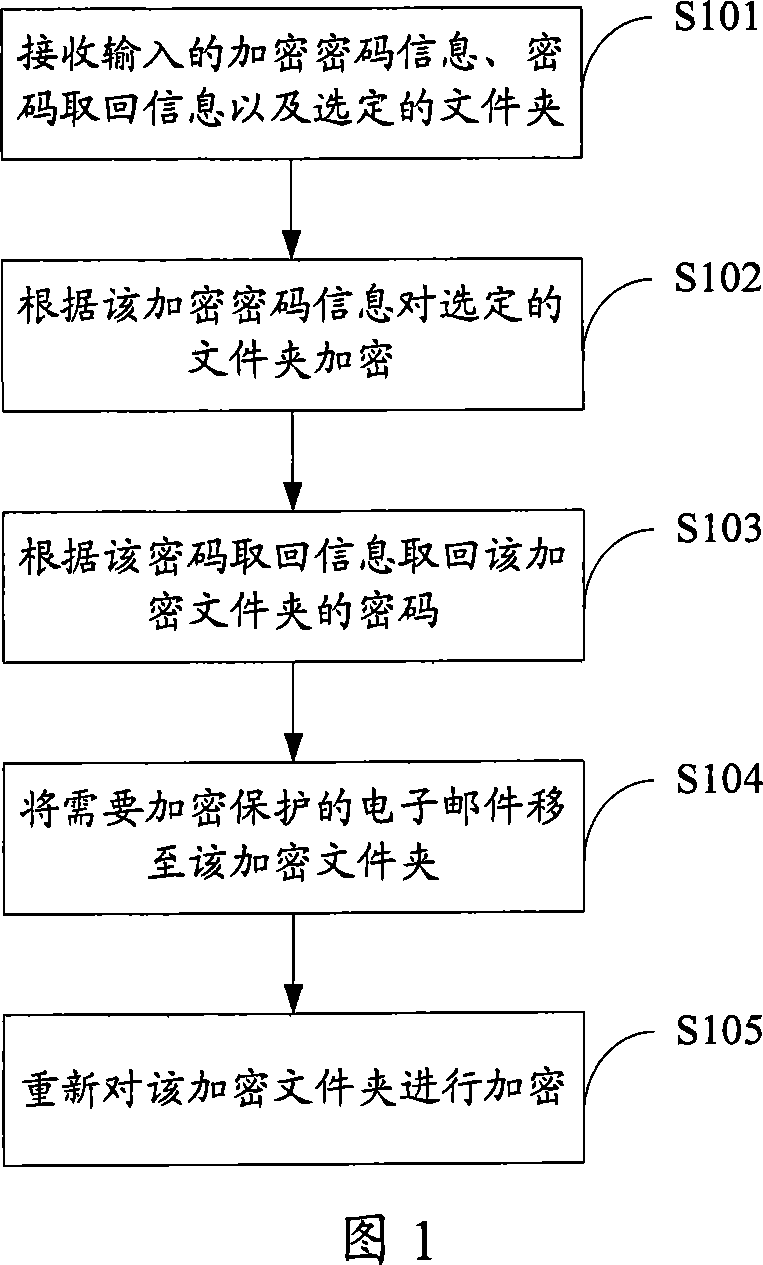
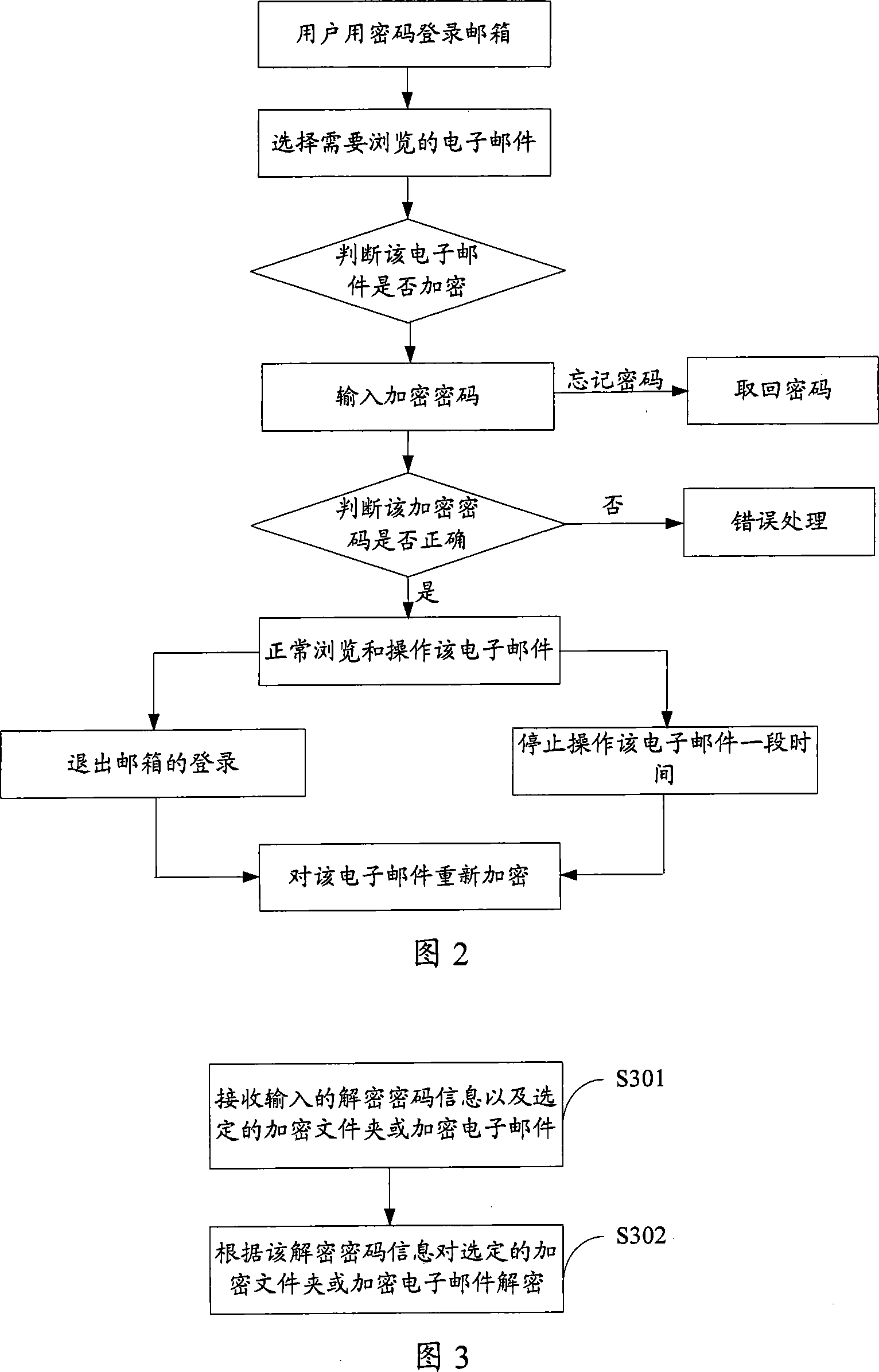
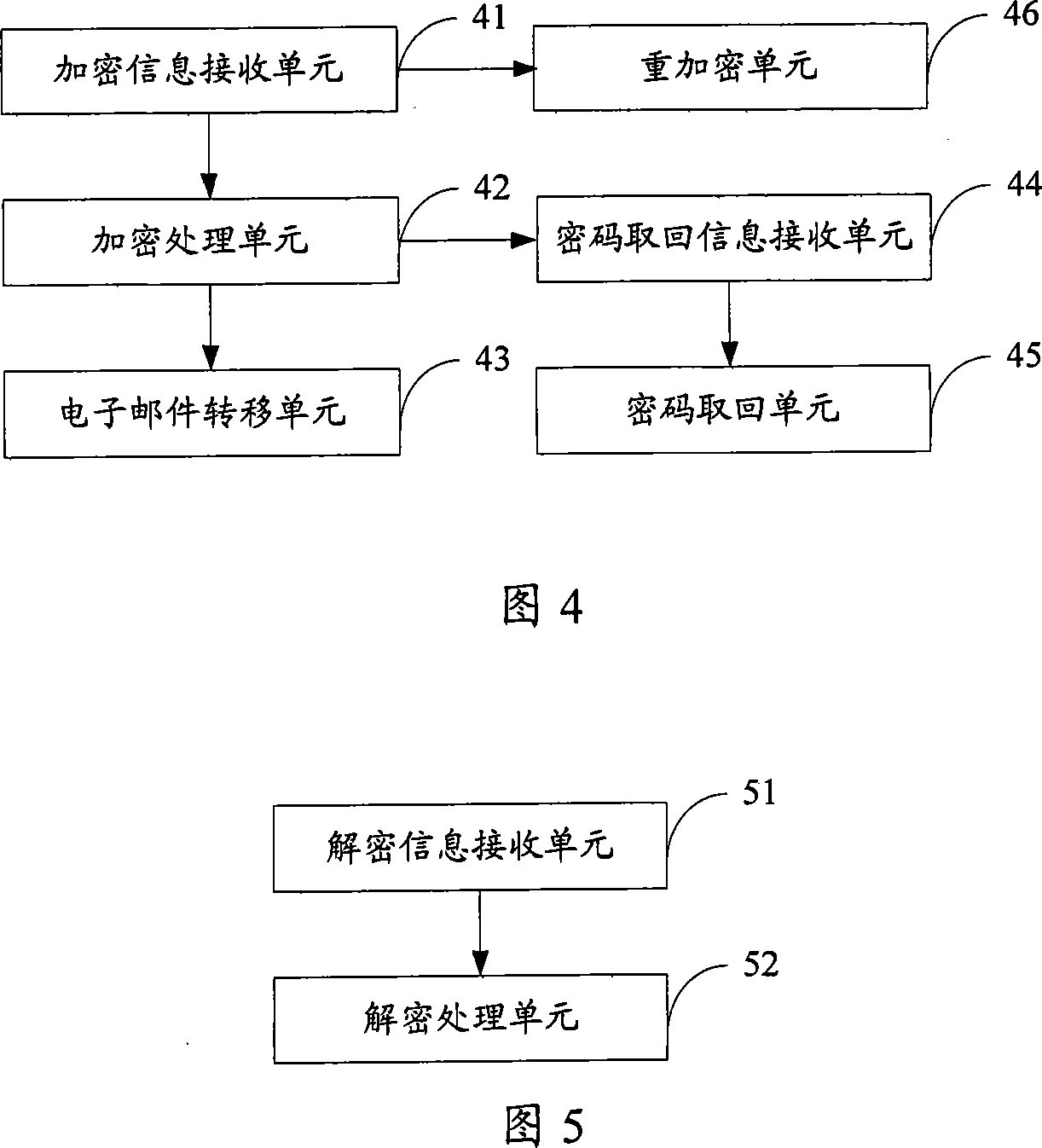
The invention is applied to the communication safety field, providing an E-mail encrypting and decrypting method and system, and the method comprises the steps of: receiving input encryption cipher information and selected folder information in mainbox; adopting encryption algorithm to generate encryption cipher according to the encryption cipher information and encrypting the selected folder in mailbox. Thus, the method provides secondary cipher protection for E-mail in encrypted folder, and assures E-mail security, and especially provides full safety assurance for users' important and private data.
Owner:TENCENT TECH (SHENZHEN) CO LTD
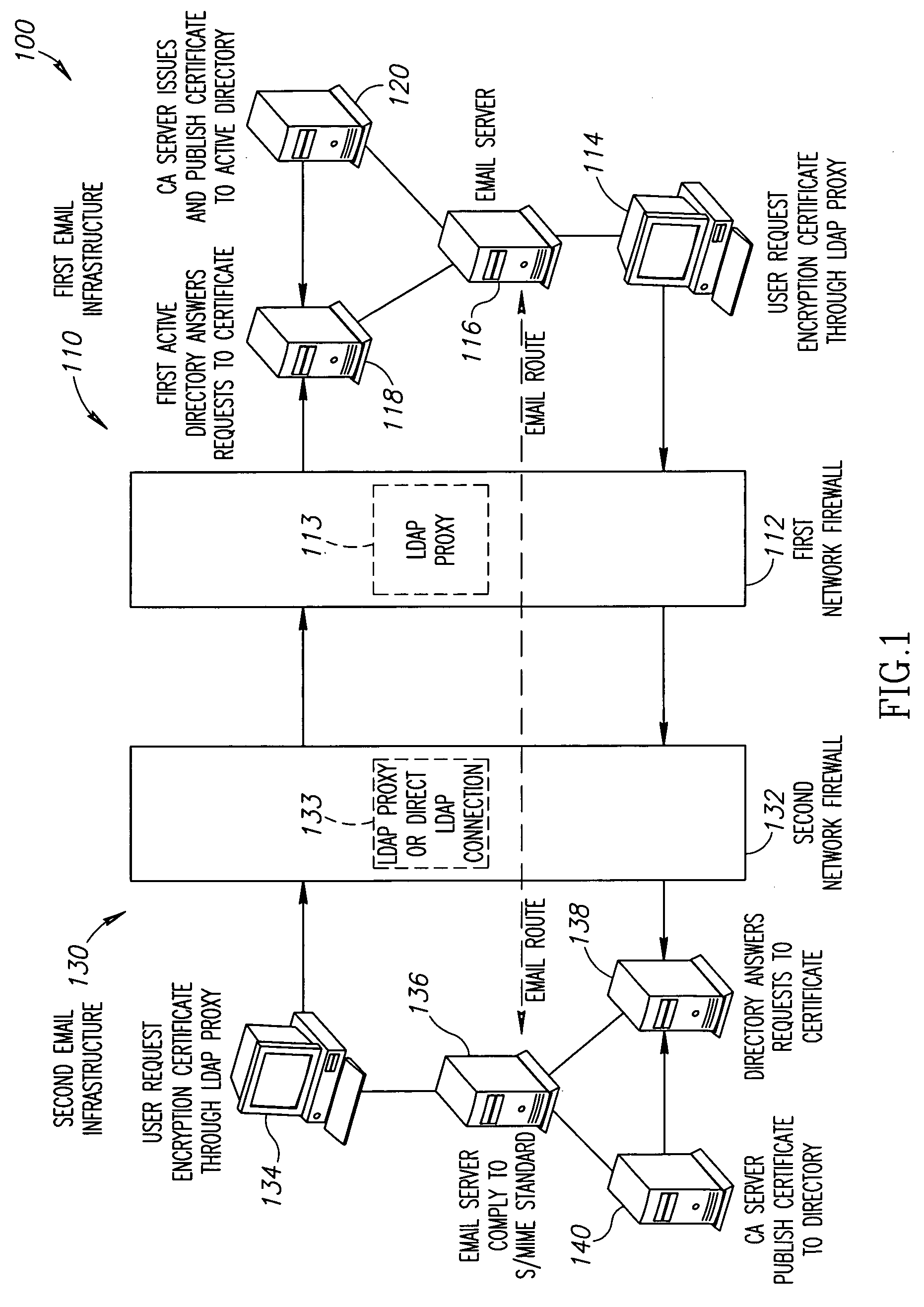
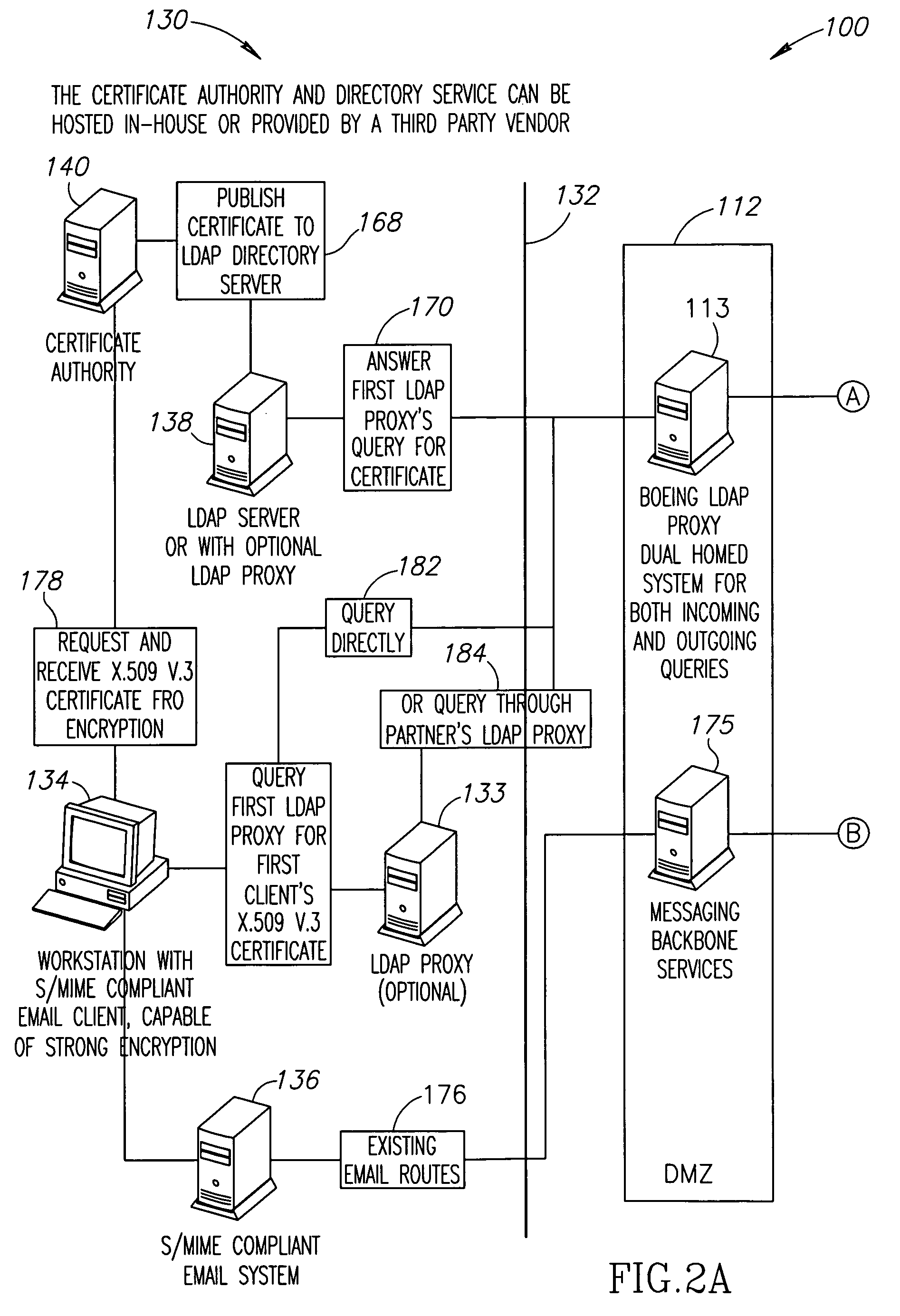
Systems and methods for automated exchange of electronic mail encryption certificates
ActiveUS7664947B2Efficient executionGuaranteed normal transmissionDigital data processing detailsUser identity/authority verificationInternet privacyEmail encryption
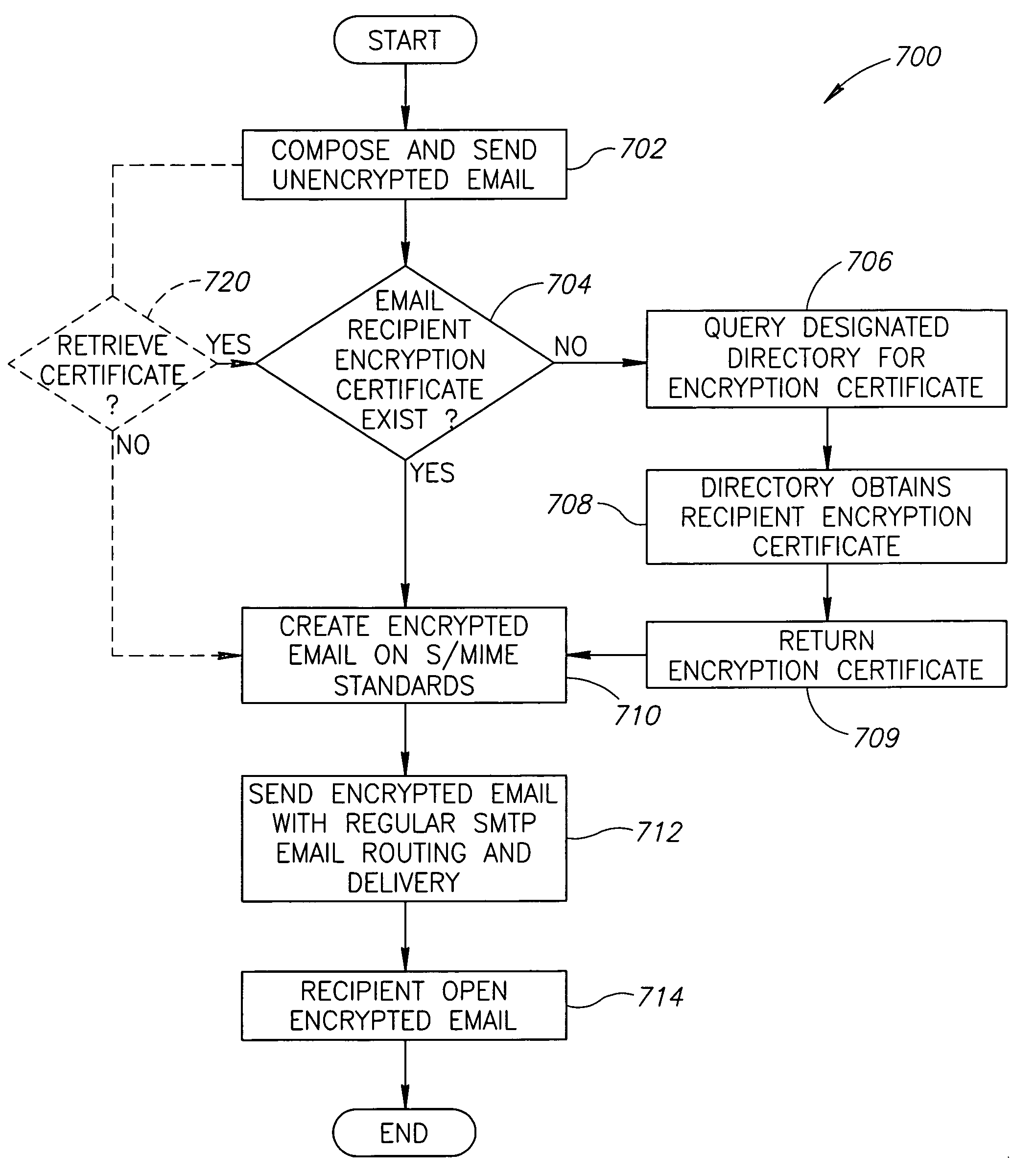
Systems and methods for automated exchange of encryption certificates for transmitting and receiving encrypted email messages are disclosed. In one embodiment, a method of communicating an encrypted email message includes providing a recipient identifier, creating an unencrypted email message, automatically querying a recipient email domain for a recipient encryption key corresponding to the recipient identifier, automatically receiving the recipient encryption key from the recipient email domain, automatically encrypting the unencrypted email message using the recipient encryption key, and transmitting the encrypted email message to the recipient identifier.
Owner:THE BOEING CO
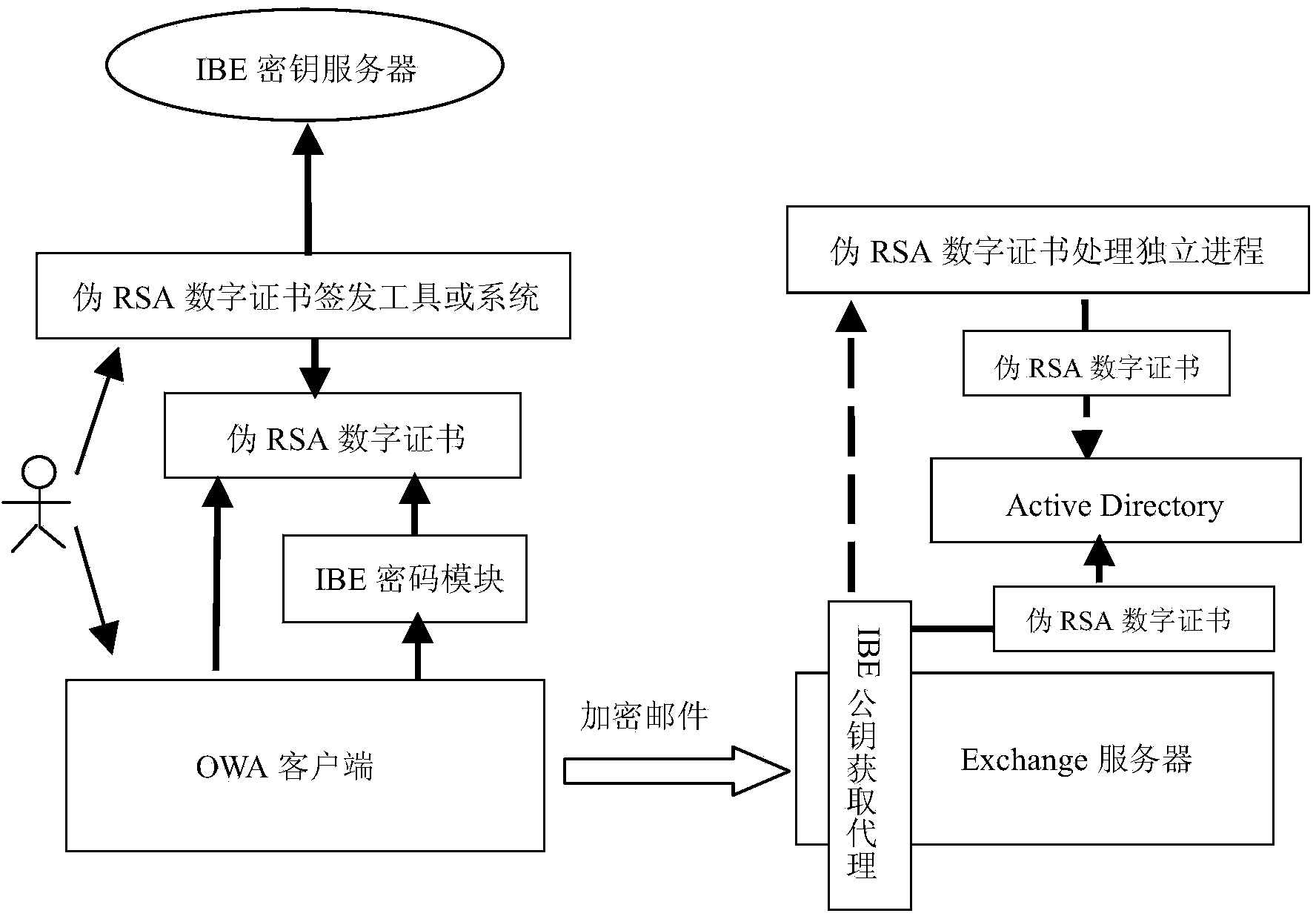
E-mail IBE (identity based encryption) system aiming at OWA (outlook web access)
ActiveCN103532704AKey distribution for secure communicationTransmission channelHyper text transport protocol
The invention relates to an OWA (outlook web access) e-mail IBE (identity based encryption) system applying a pseudo-RSA (Rivest, Shamir and Adleman) digital certificate. The system comprises an OWA client, the pseudo-RSA digital certificate, an IBE cryptogrammic module, a pseudo-RSA digital certificate issuing tool or system, an Exchange server, an AD (advertisement) server, an IBE public key acquisition agent and an IBE secret key server, wherein the IBE public key acquisition agent is an HTTP (hyper text transport protocol) agent or plugin arranged or inserted in an HTTP transmission channel between the OWA client and the Exchange server; the HTTP agent or plugin stops a request of the OWA client for acquiring public keys of encrypted digital certificates of an encrypted e-mail sender and an encrypted e-mail receiver from the AD server by Exchange and generates or returns pseudo-RSA digital certificates or pseudo-RSA public keys of the e-mail sender and the e-mail receiver, so that e-mail IBE encryption based on the OWA is realized, and the manual operation involved in the application of the pseudo-RSA digital certificates in the OWA is reduced and simplified.
Owner:WUHAN UNIV OF TECH
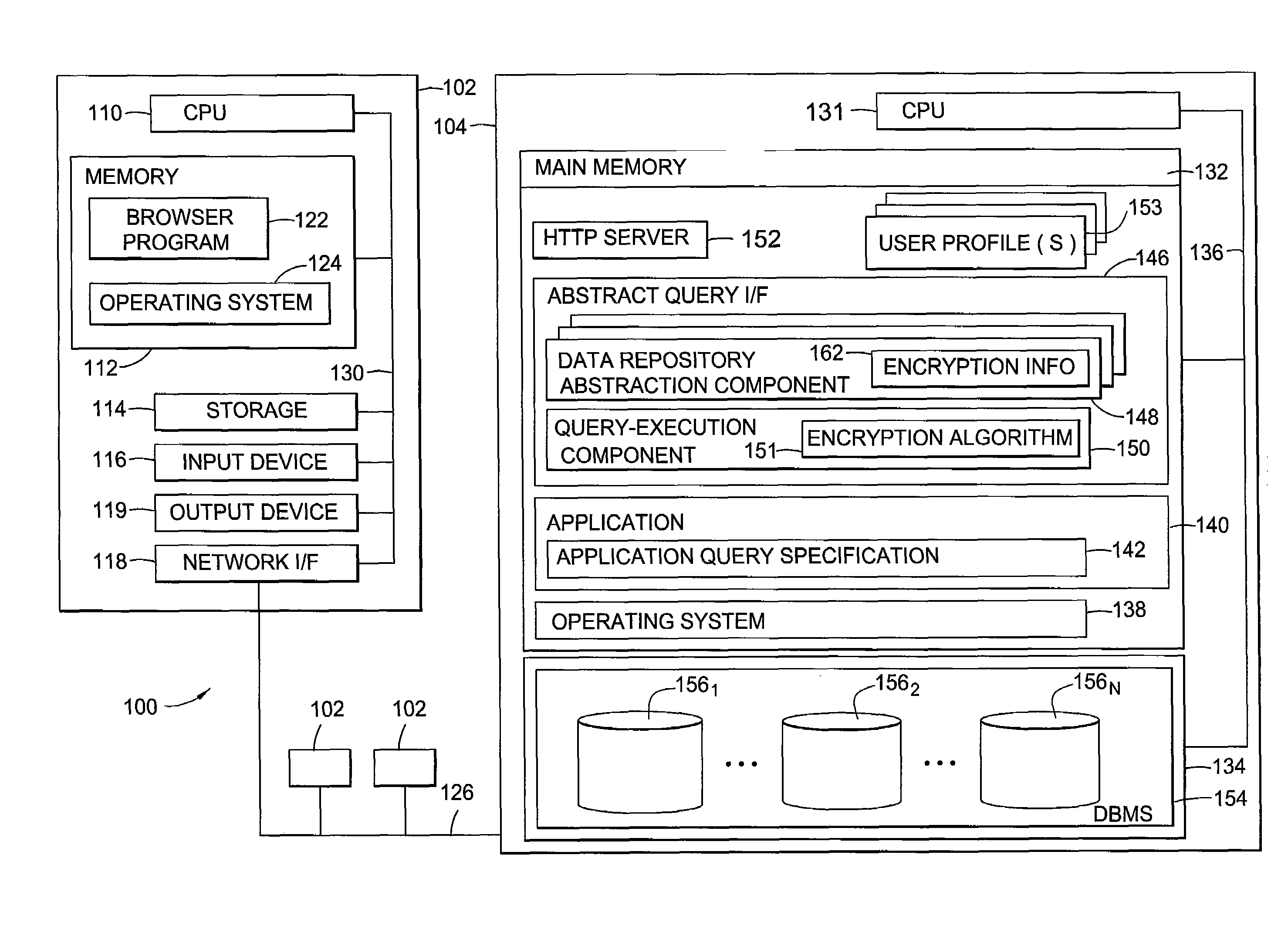
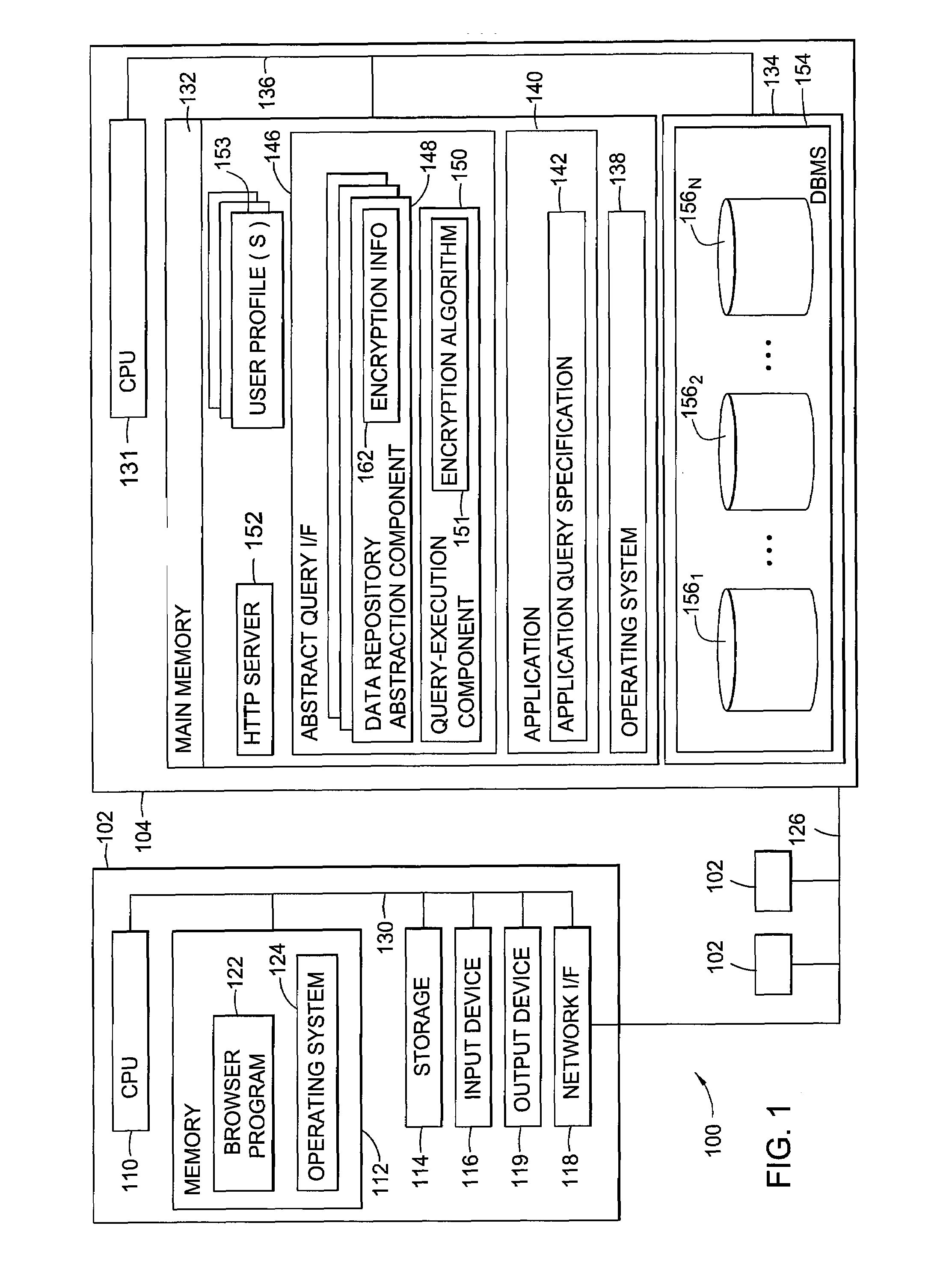
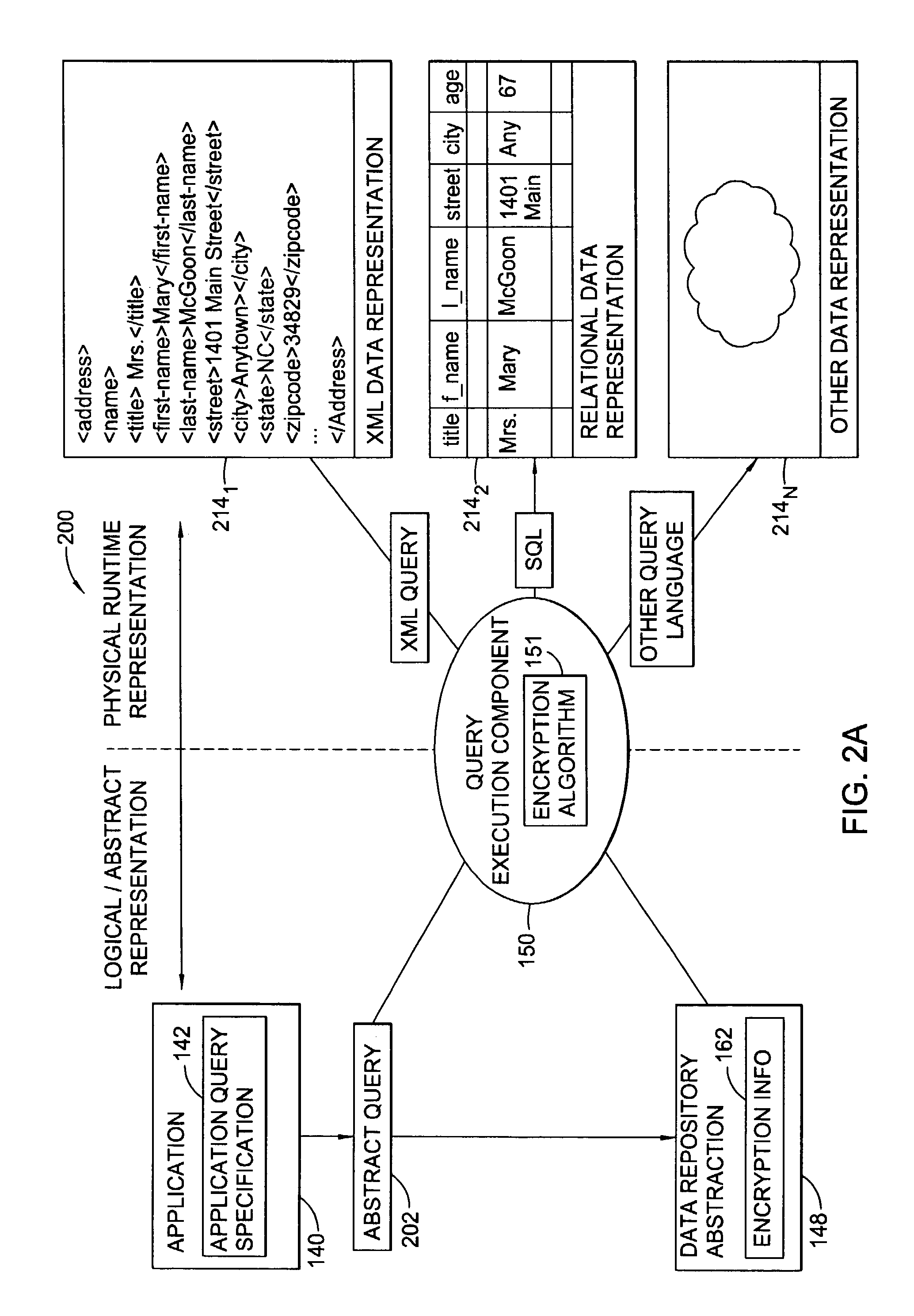
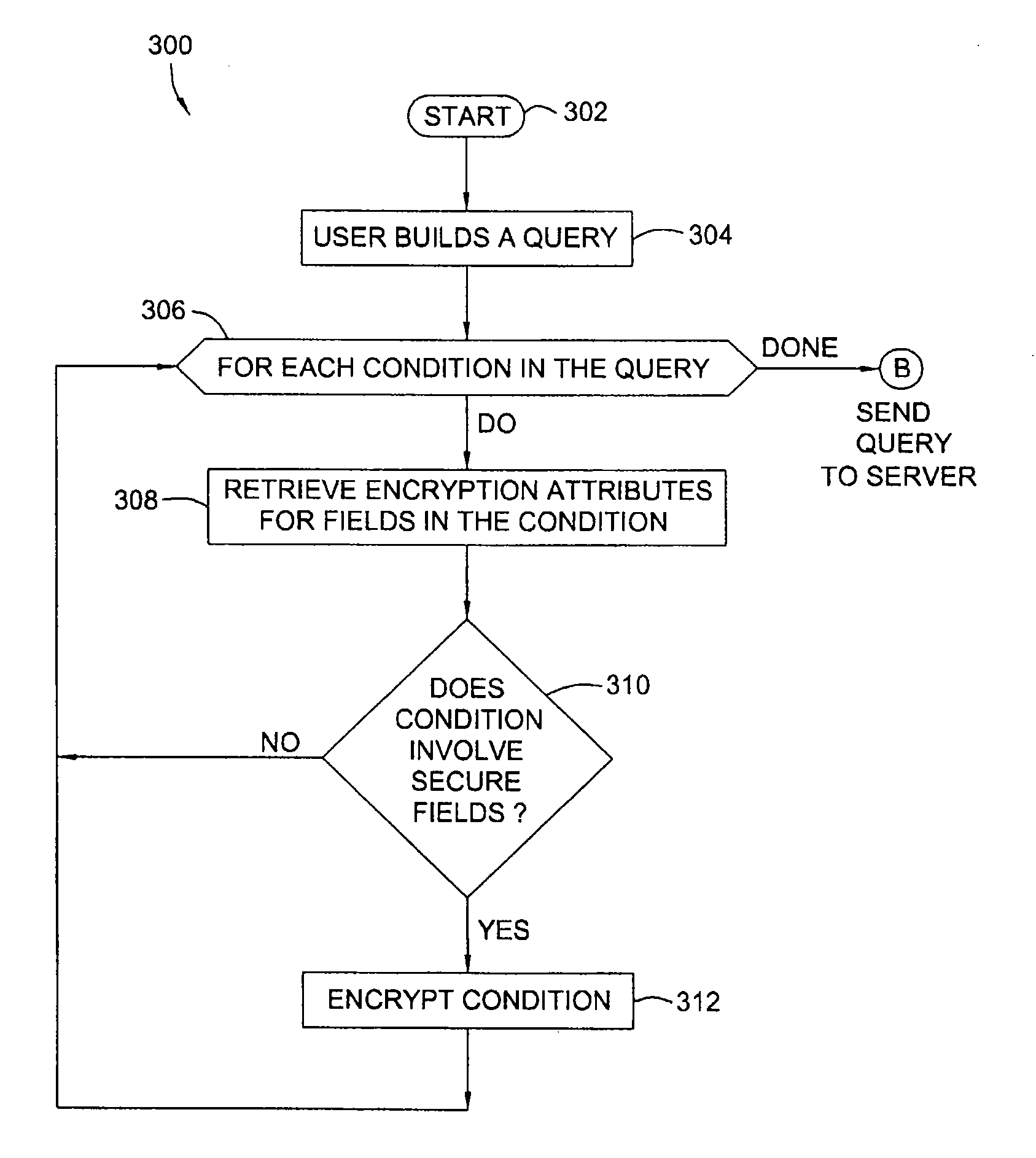
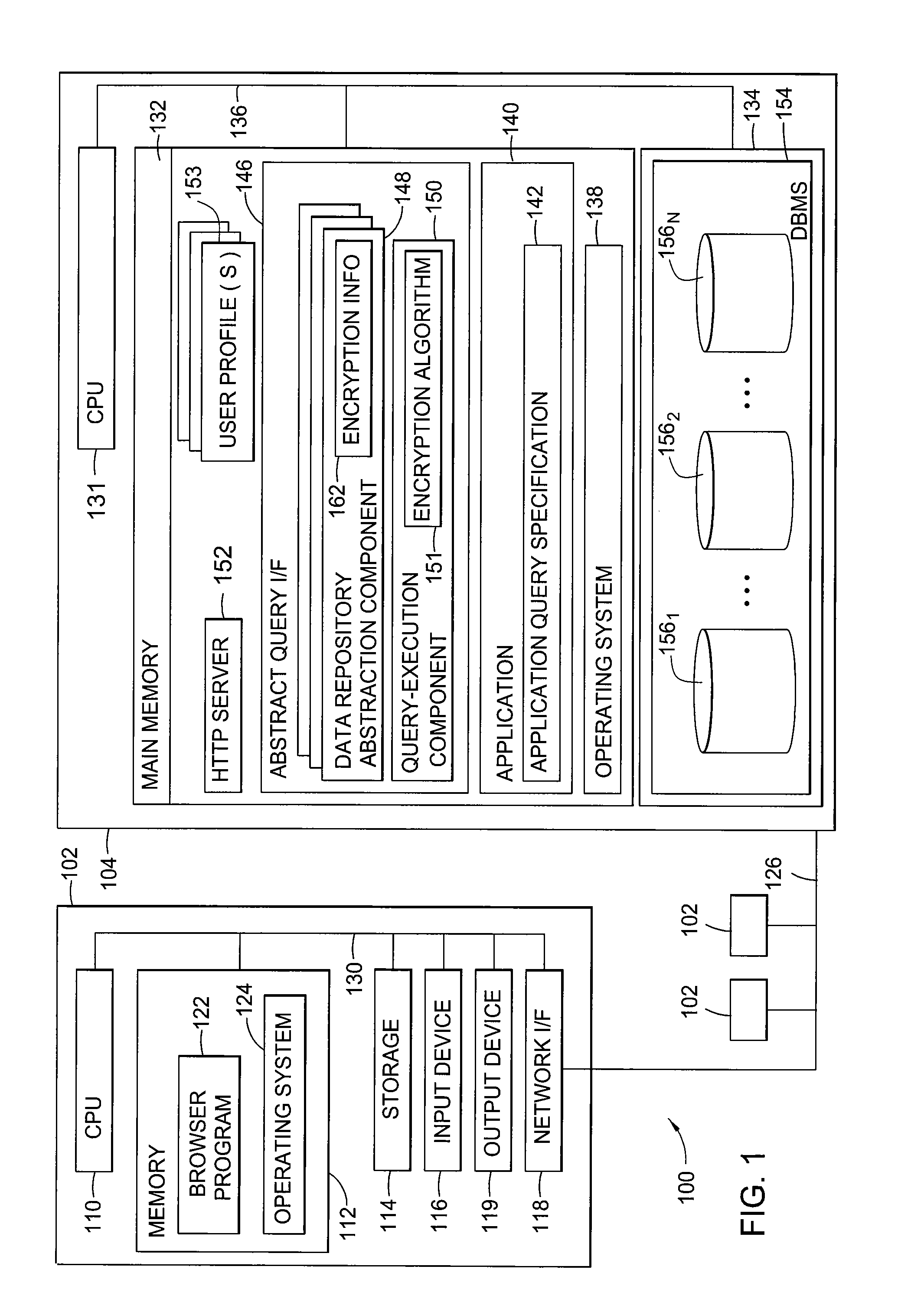
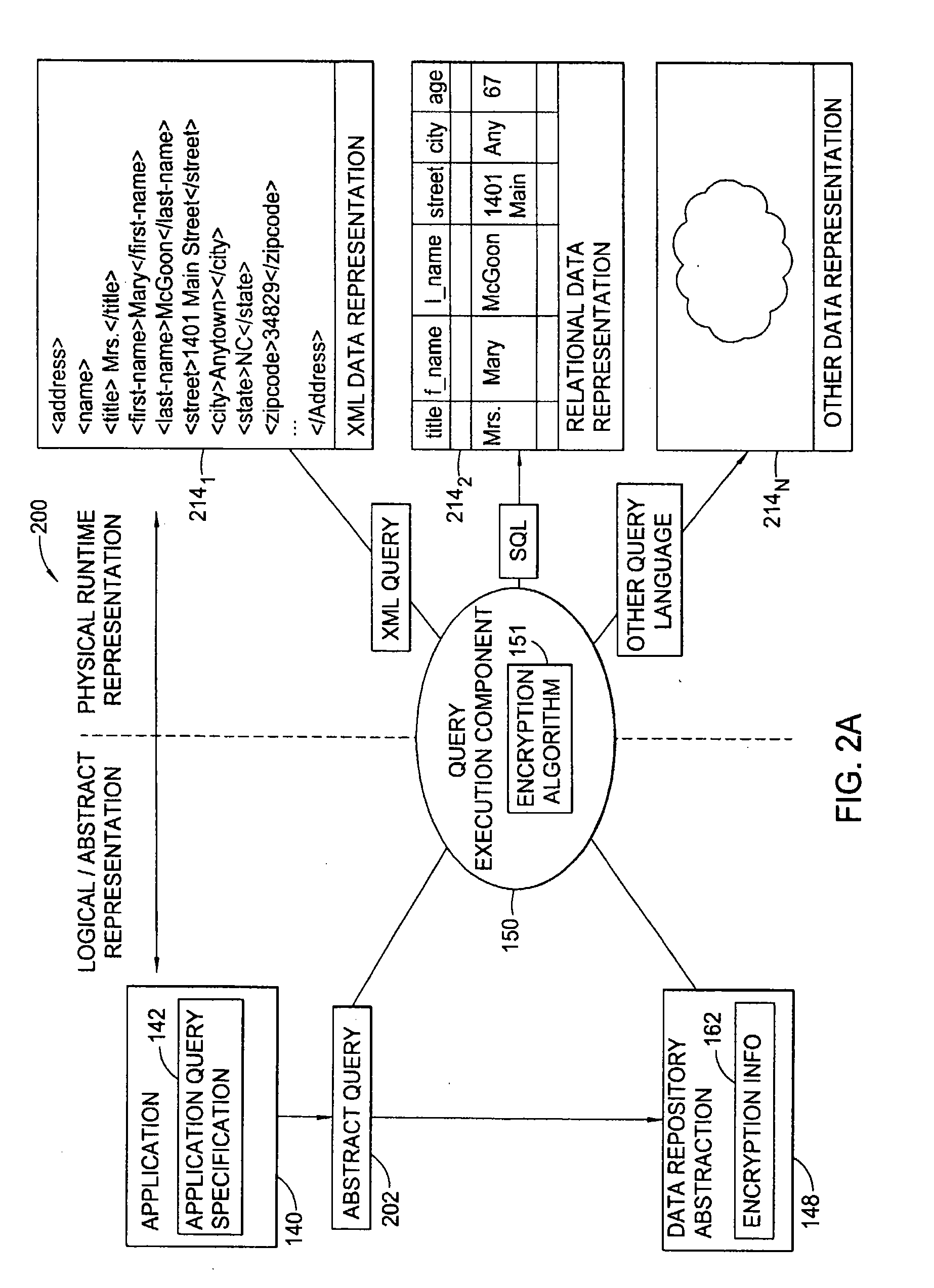
Secure database access through partial encryption
ActiveUS7418600B2User identity/authority verificationUnauthorized memory use protectionDatabase serverDocument recognition
The present invention generally is directed to systems, methods, and articles of manufacture for securing sensitive information involved in database transactions. Embodiments of the present invention selectively encrypt only portions of transactions involving sensitive data, thereby reducing or eliminating the processing overhead resulting from wastefully encrypting non-sensitive data. The sensitive data may be identified by a document. The document may be accessed by a requesting entity to determine which portions of a query should be encrypted prior to sending the query to a database server over a network. The document may also be accessed by a database server to determine which portions of query results should be encrypted prior to sending the query results to the requesting entity over the network.
Owner:WORKDAY INC
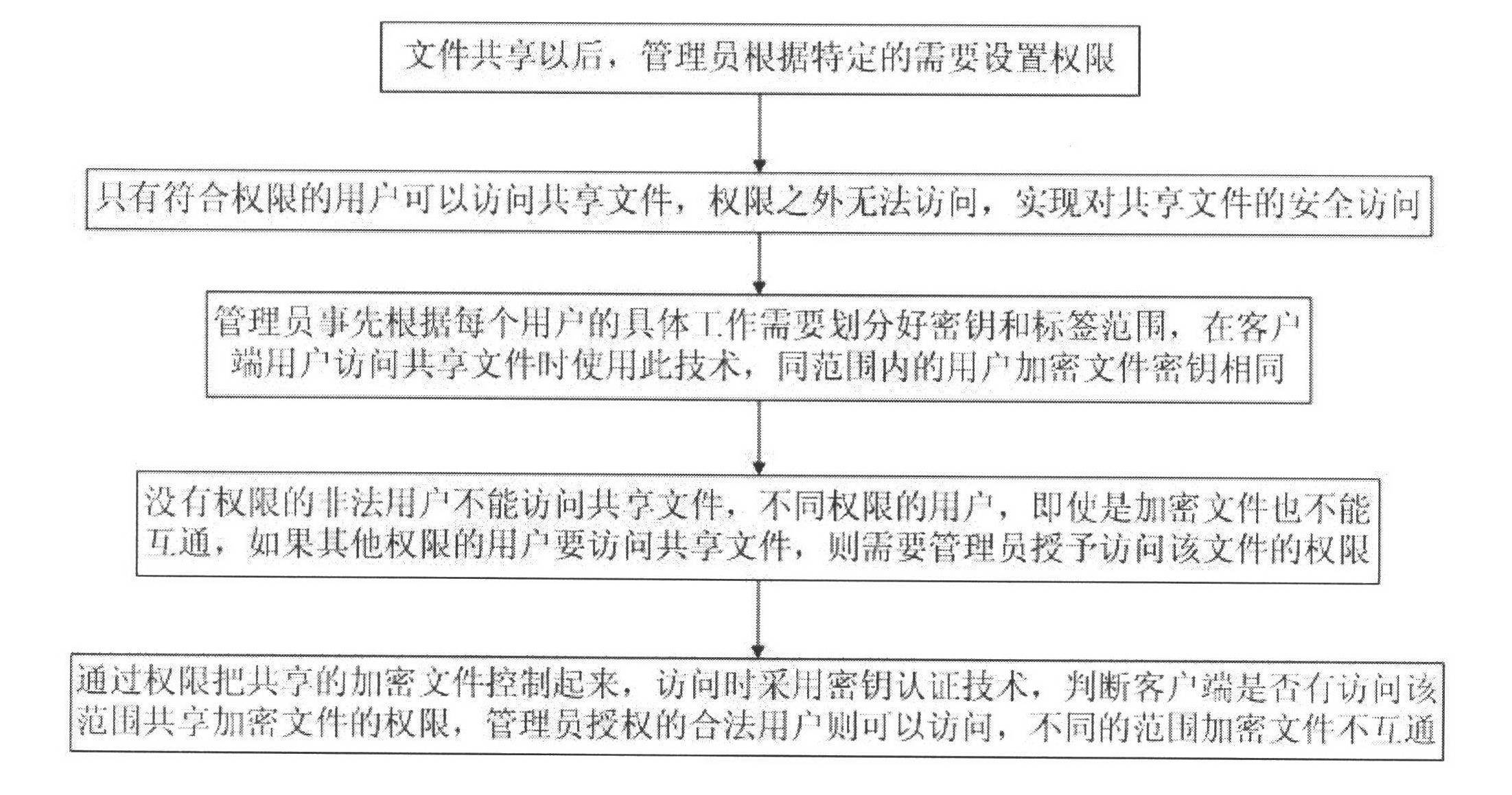
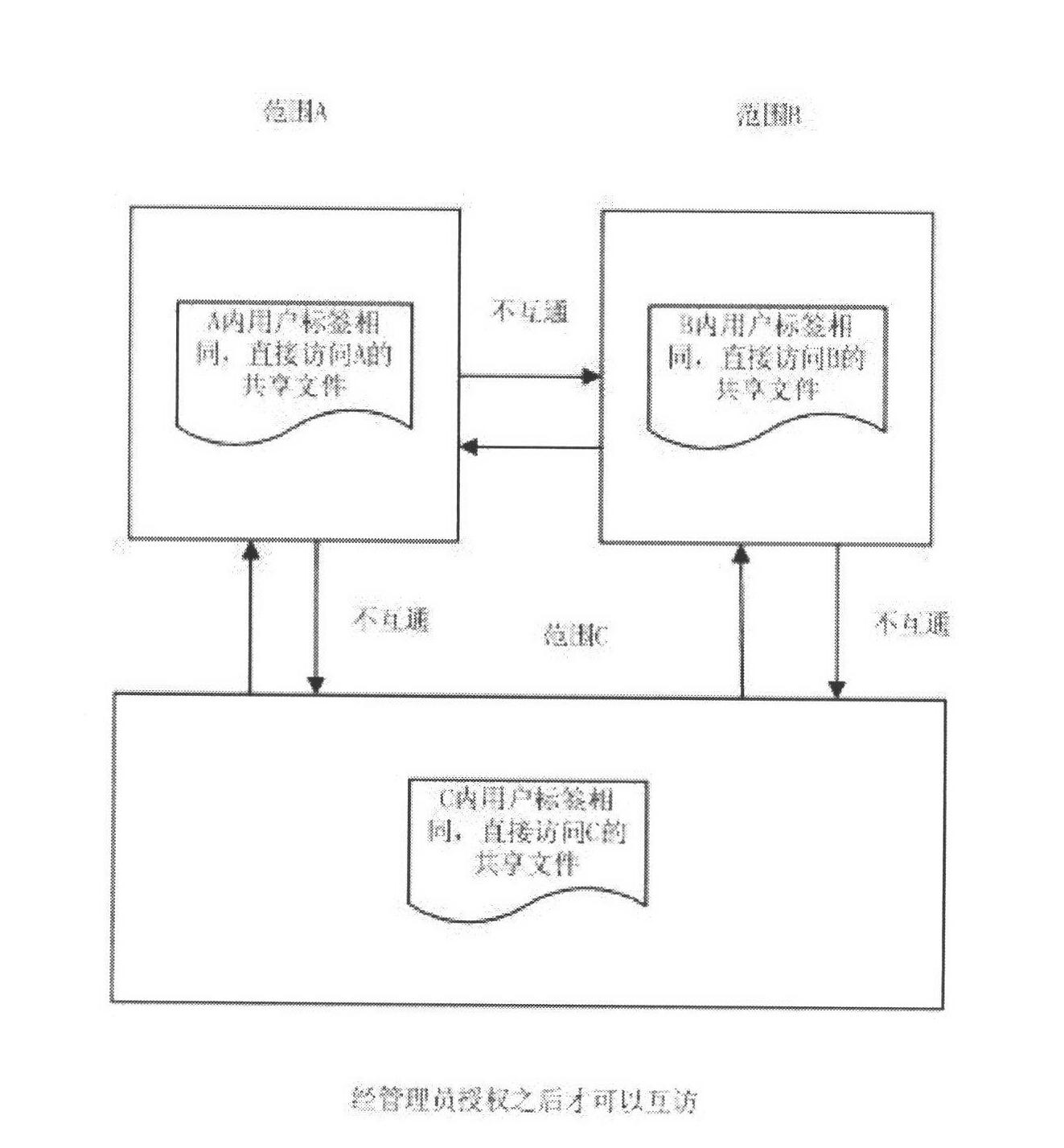
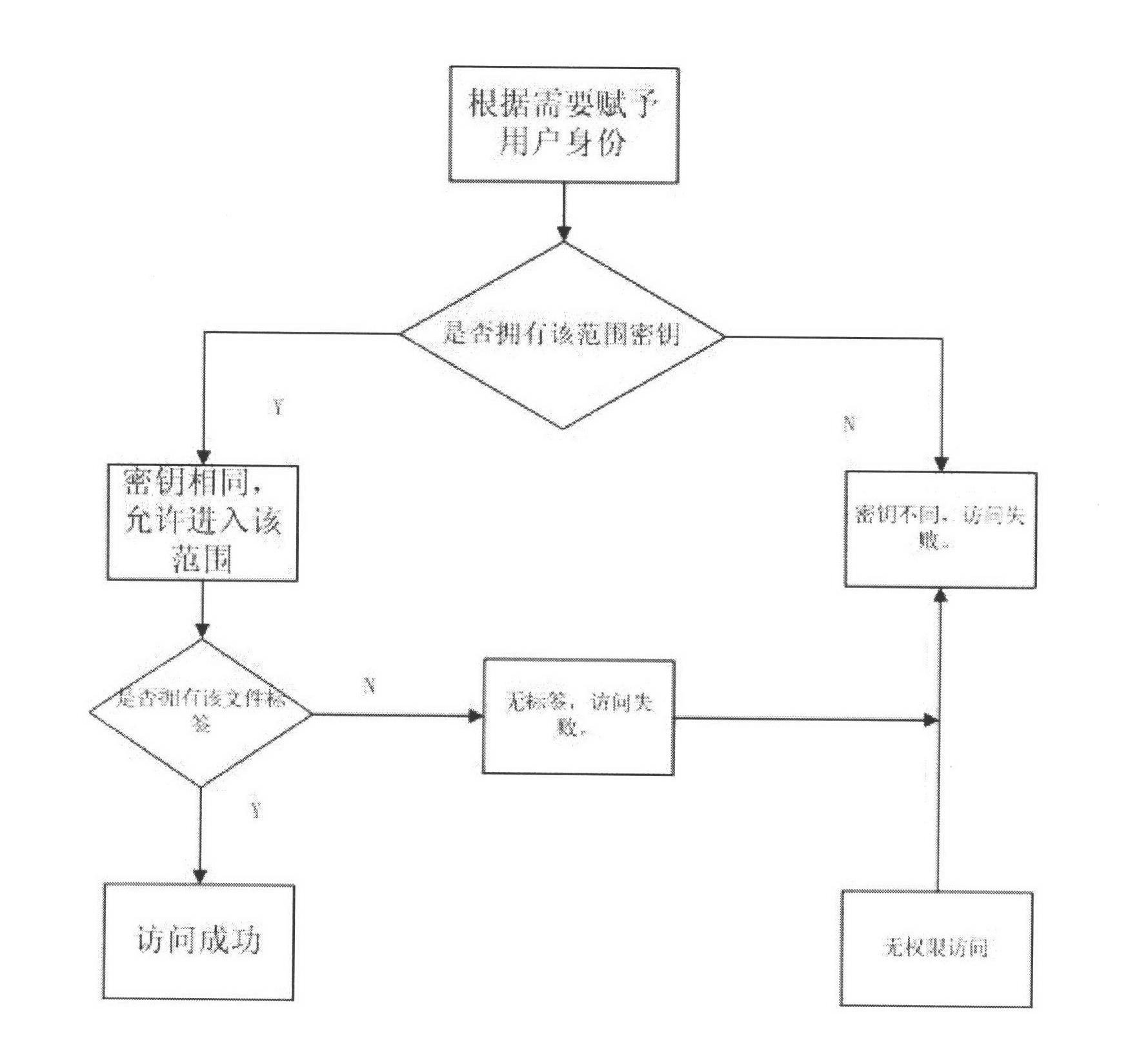
Shared file authority control method
InactiveCN102611686AEnsure safetyDigital data protectionTransmissionXML EncryptionKey authentication
The invention discloses a shared file authority control method which is characterized by comprising the following steps: after a file is shared, an administrator sets authority according to the specific need; only the user conforming to the authority can access the shared file so as to realize the secure access to the shared file; the administrator firstly divides the key and label range according to the concrete working need of each user, and the user encrypted files in the same range share the same key; an illegal user without the authority can not access the shared file; if a user with other authority is to access the shared file, the administrator needs to grant the authority for accessing the file; and when in access, a key authentication technology is adopted to judge whether a client has the authority for accessing the shared encrypted file in the range, wherein the encrypted files in different ranges are not interoperable. Through the invention, based on file encryption, effective control on the authority of the shared file is realized, and the users in the authority range can access the shared encrypted file while the users outside the range can not access the shared encrypted file, thereby ensuring the security of the enterprise information.
Owner:WUXI CINSEC INFORMATION TECH
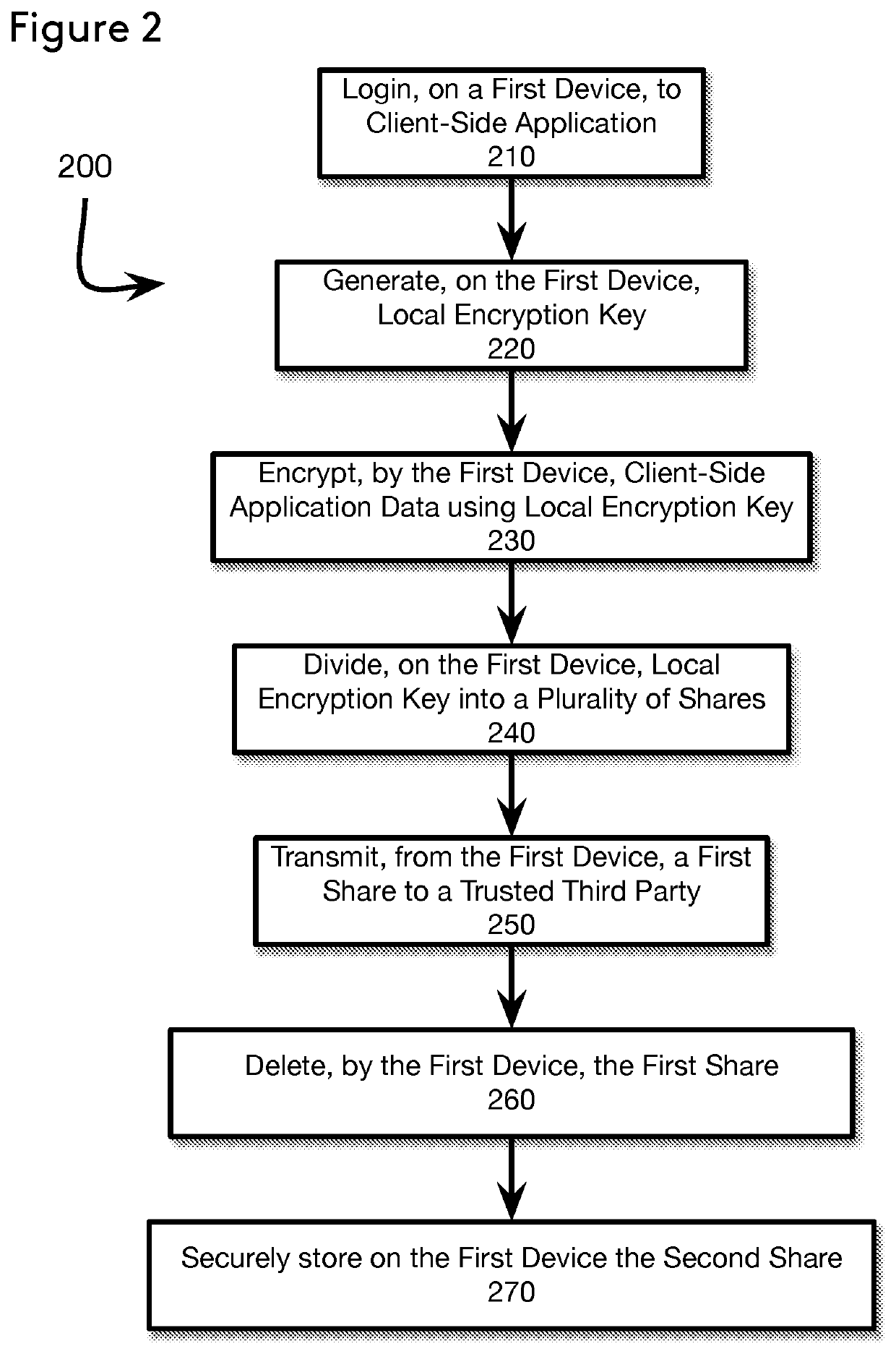
Local Encryption for Single Sign-On
ActiveUS20190356650A1Key distribution for secure communicationUser identity/authority verificationThird partySecret share
The present disclosure describes techniques that allow for a client-side application, located on a first client device, to generate a random encryption key and encrypt locally-stored application data with the random encryption key. In order to ensure that the client-device application is unable to decrypt the locally-stored encrypted application data prior to authenticating with an external authentication source (i.e., SSO, IdP), the client-side application divides the random encryption key into at least a first share and a second share according to a secret sharing algorithm. The first share is transmitted to a trusted third party, while the second share is encrypted locally and stored in a secure location on the client device. Upon successful authentication, the trusted third party returns the second share to the first client device. The client-side application derives the random encryption key and decrypts the locally-stored encrypted application data to be used by the client-side application. By dividing the key used to encrypt the client-side application data and storing one of the secret shares necessary to deriving the key at a trusted third party, the present disclosure solves the problem of how to encrypt local application data when the login credentials for the application are managed by a trusted third party, such as an SSO system.
Owner:AMAZON TECH INC +1
Systems and methods for public-key encryption for transmission of medical information
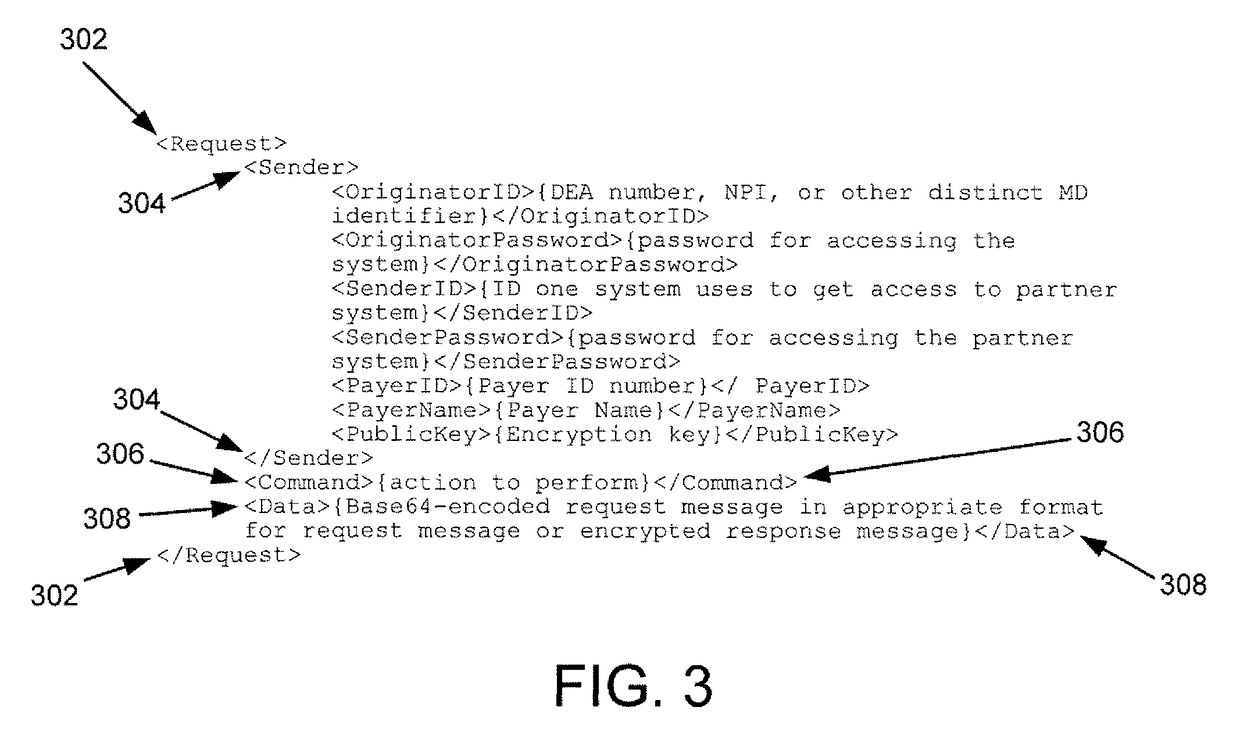
ActiveUS7908487B2Public key for secure communicationDigital data processing detailsEmail encryptionXML
The invention is directed to systems and methods for communicating sensitive and / or confidential medical information with the use of encryption. Specifically, the invention is directed to transmitting a request for sensitive medical data, where the request includes a public key for encryption as an XML node. The public key may be used by the responding party to encrypt at least a portion of the response and respond to the request. The only party in the network path that is able to decrypt the message is the originator of the request because the requestor will have a private keys which is required to decrypt the response data.
Owner:NDCHEALTH CORP
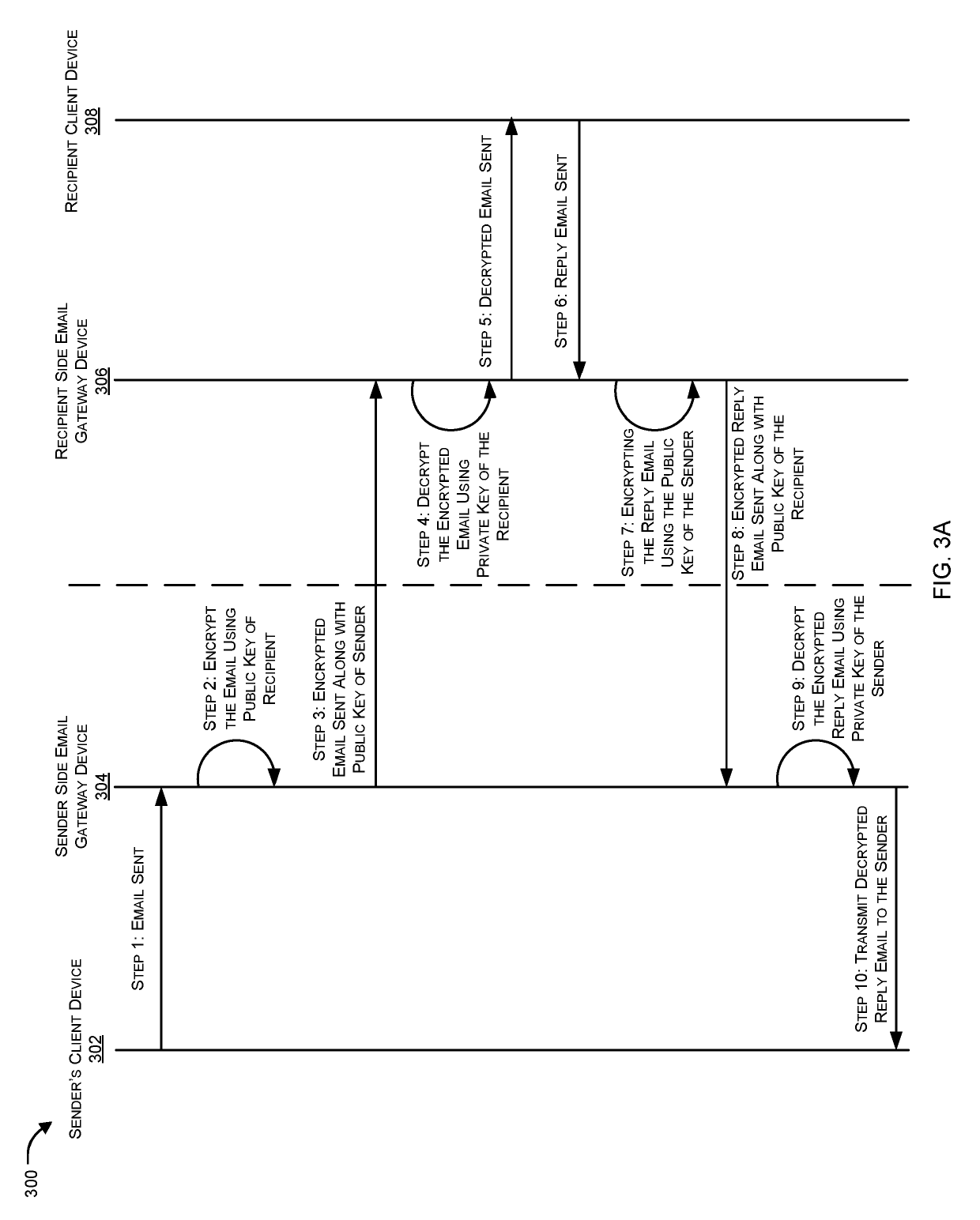
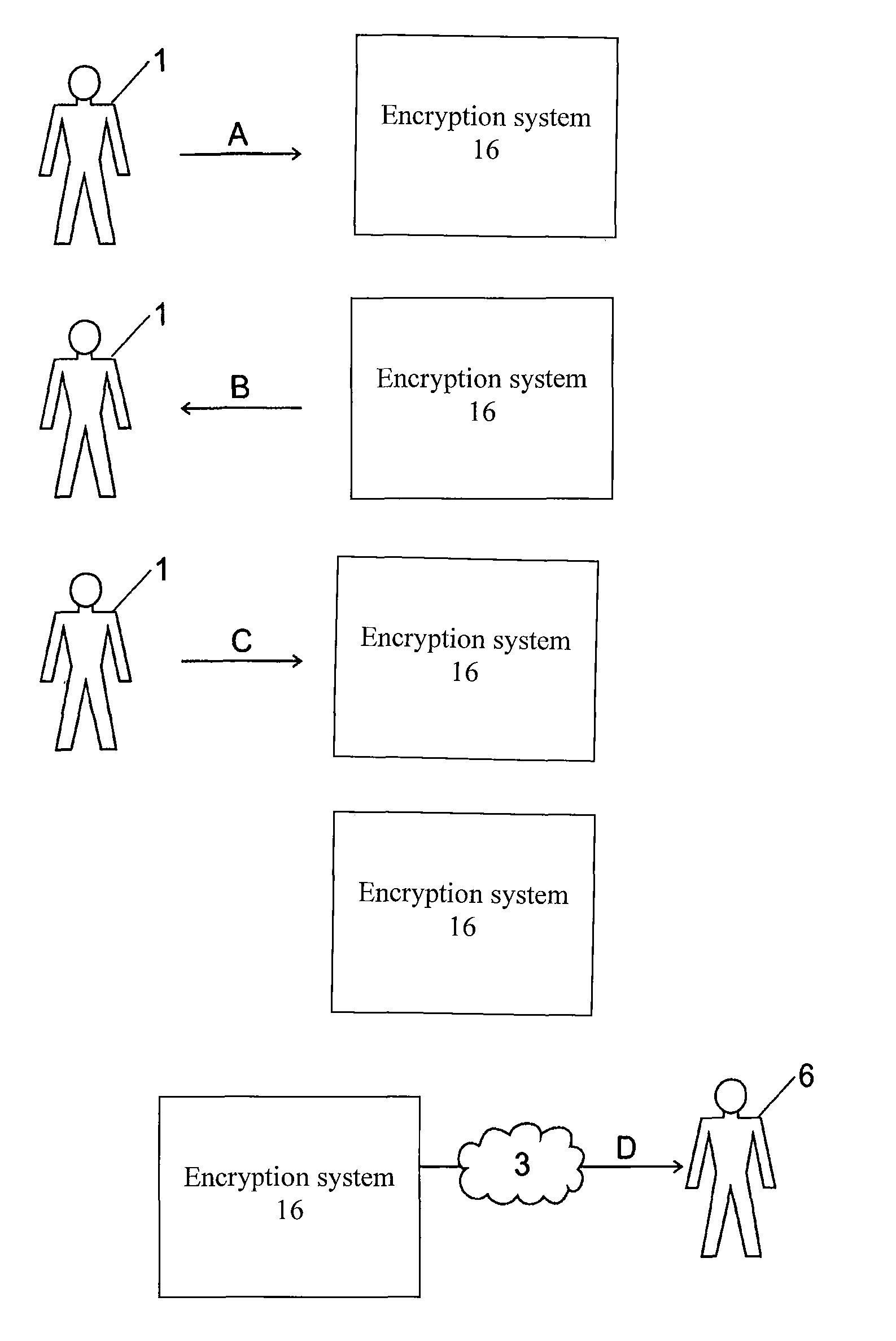
Method for establishing a secure e-mail communication channel between a sender and a recipient
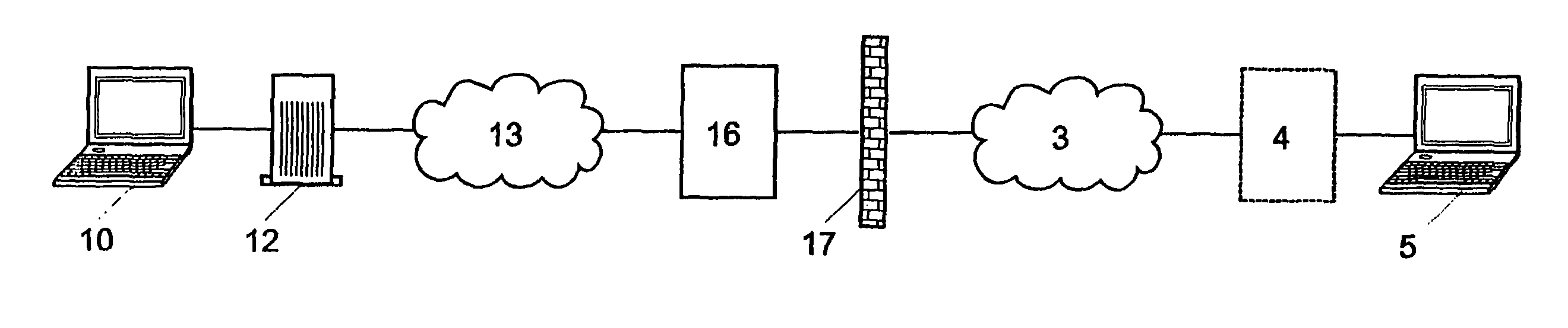
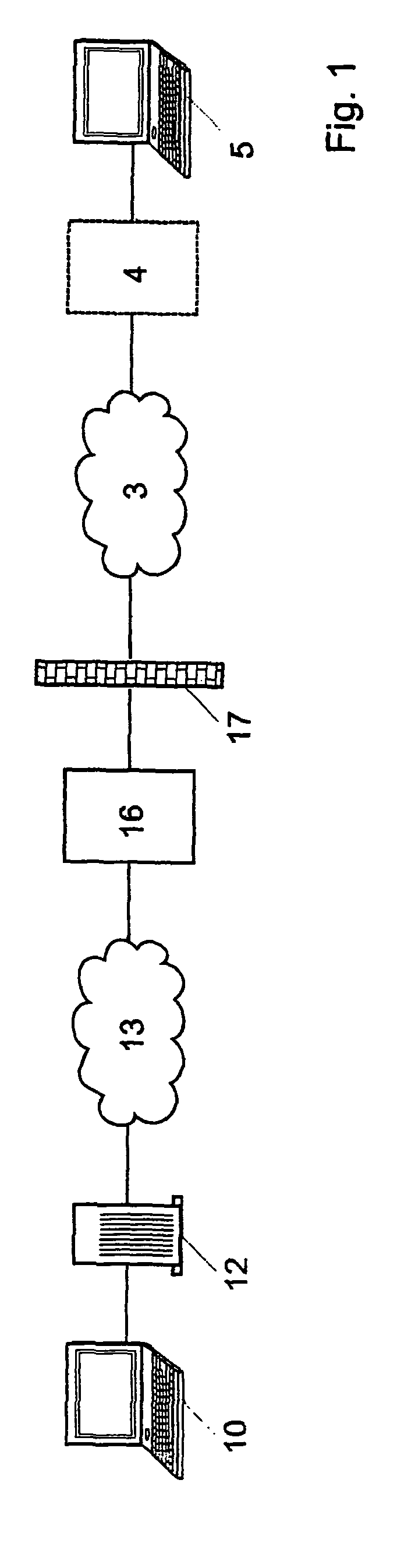
ActiveUS8032750B2User identity/authority verificationComputer security arrangementsRecipient sideElectronic mail
A method for establishing a secure e-mail communication channel between a sender (10) and a recipient (5), wherein:1) said sender sends an e-mail addressed to said recipient over an e-mail encryption system (16),2) said encryption system (16) verifies in a database (160) of recipients if a public key of said recipient is available,3) if said public key of said recipient is available, said encryption system encrypts said e-mail with said public key, and forwards the encrypted e-mail to the recipient (5),4) if, on the other hand, said public key of said recipient is not available in said database (160), said encryption system sends instead enrolment message (1220) to said recipient, said enrolment message containing an invitation for said recipient to choose among one of the following options:i) access to said email over a secured web mail interface, orii) sends a reply to said encryption system from which said public key can be extracted, orii) initiate generation of a public key on the recipient's side.
Owner:TOTEMO
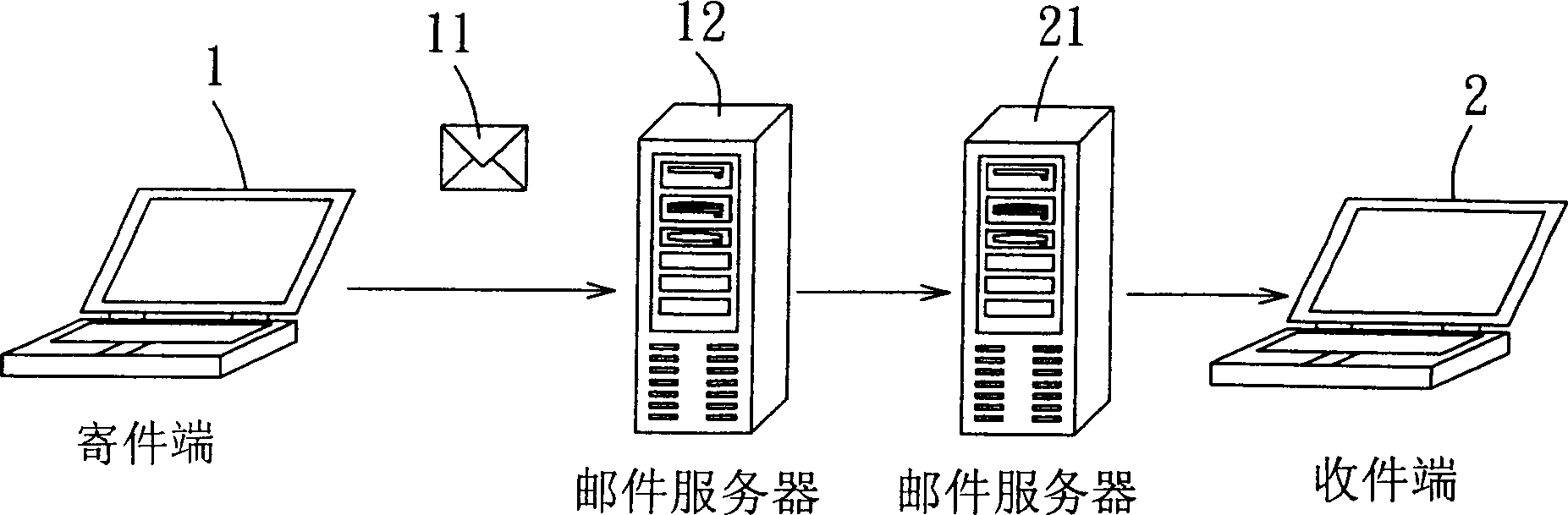
Electronic mail sending and receiving system
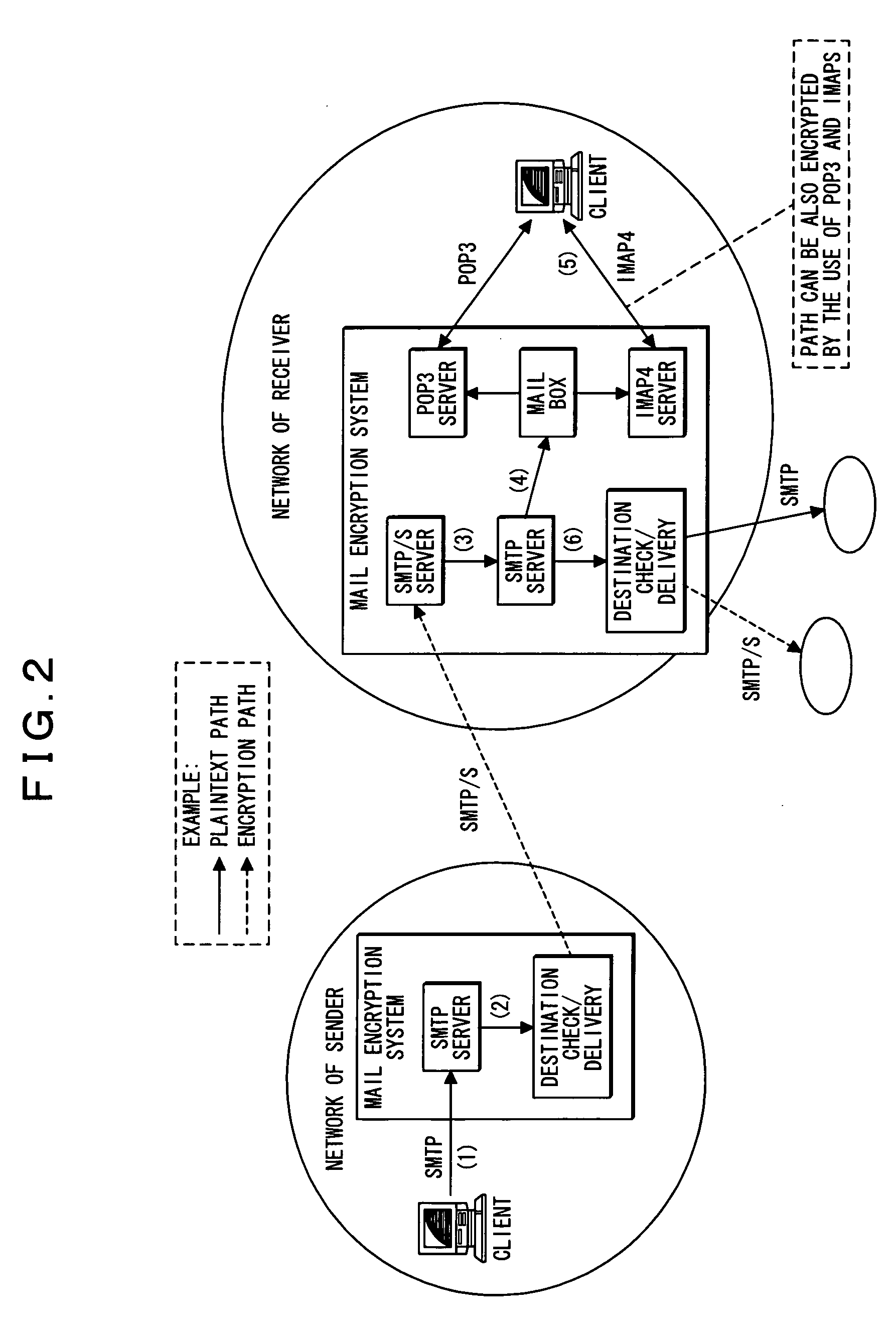
InactiveUS20060168071A1Multiple digital computer combinationsData switching networksClient-sideElectronic mail
There is provided an electronic mail sending and receiving system capable of encrypting an electronic mail including its header when sending it without installing an encryption system in a sender client and decrypting the electronic including its header mail when received without installing an encryption system in a receiver client. A sender's mail server includes an SMTP server for receiving a plaintext electronic mail sent from a sender client, destination check means for checking an electronic mail destination, and electronic mail encrypting and sending means for encrypting the electronic mail by using an SMTP / S protocol if the destination check result shows that the electronic mail delivery destination supports the SMTP / S protocol when sending the mail. A receiver's mail server includes an SMTP server for receiving an electronic mail and mail decryption / reception means for decoding the electronic mail received.
Owner:NETAGENT
Secure database access through partial encryption
InactiveUS20090083548A1User identity/authority verificationUnauthorized memory use protectionDatabase serverDocument recognition
The present invention generally is directed to systems, methods, and articles of manufacture for securing sensitive information involved in database transactions. Embodiments of the present invention selectively encrypt only portions of transactions involving sensitive data, thereby reducing or eliminating the processing overhead resulting from wastefully encrypting non-sensitive data. The sensitive data may be identified by a document. The document may be accessed by a requesting entity to determine which portions of a query should be encrypted prior to sending the query to a database server over a network. The document may also be accessed by a database server to determine which portions of query results should be encrypted prior to sending the query results to the requesting entity over the network.
Owner:INT BUSINESS MASCH CORP
E-mail encryption method and system based on group cryptosystem
ActiveCN108011885AEasy to superviseEasy accessMultiple keys/algorithms usageData switching networksCryptosystemPublic key certificate
The invention relates to the field of information technology, in particular to an E-mail encryption method and system based on a group cryptosystem for secure data exchange. The E-mail encryption system manages a group public key based on the group cryptosystem, generates a different private key for each user, and implements an encryption mechanism for one or more designated authorized users through the group public key, and the user key is issued and managed by a server, so the system can supervise the encrypted mail content; the mail encryption only needs to acquire a group public key certificate of a recipient's mail system, this certificate is managed by the mail system, and compared with a personal public key certificate, the storage and maintenance are relatively simple; for multiplerecipients in the same mail system, the group public key certificate only needs to be acquired once; and the method and the system have the advantages of simple certificate verification and high encryption efficiency.
Owner:UNIV OF SCI & TECH BEIJING
E-mail encryption method, mail server and system
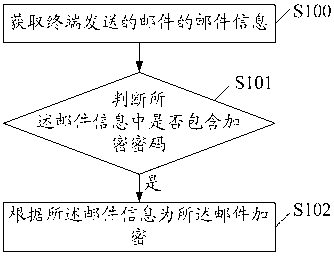
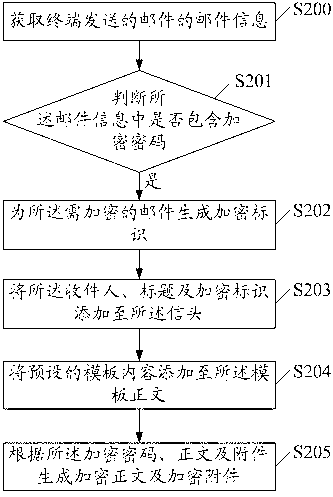
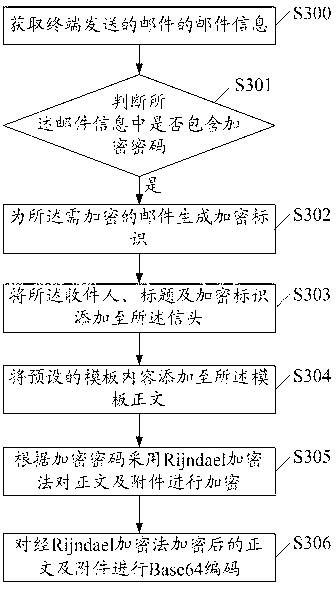
ActiveCN103188129AExtended Standard FormatImprove securityUser identity/authority verificationData switching networksEncryption systemEmail encryption
The invention discloses an E-mail encryption method which comprises the steps that mail information sent by a terminal is acquired, and the mail information comprises a receiver, an object, a text and an attachment; whether an encryption password is comprised in the mail information is judged, when the judgment is confirmed, an E-mail is encrypted according to the mail information, the encrypted E-mail comprises a mail head, a template text, an encrypted text and an encrypted attachment, and the mail head further comprises encryption identification corresponding to the E-mail. The invention further discloses a mail server and an E-mail encryption system. By adoption of the E-mail encryption method, the mail server and the E-mail encryption system, a standard format of an E-mail is expanded, each E-mail can have an independent encryption password, and safety of E-mail data is greatly improved. Simultaneously, because the whole encryption data are placed in an original text of an E-mail, the E-mail can be independently downloaded and decrypted. In addition, the E-mail is encrypted by utilizing an Rijndael encryption method, and entity data of each E-mail are effectively ensured.
Owner:广东盈世计算机科技有限公司
E-mail enciphered transmission method
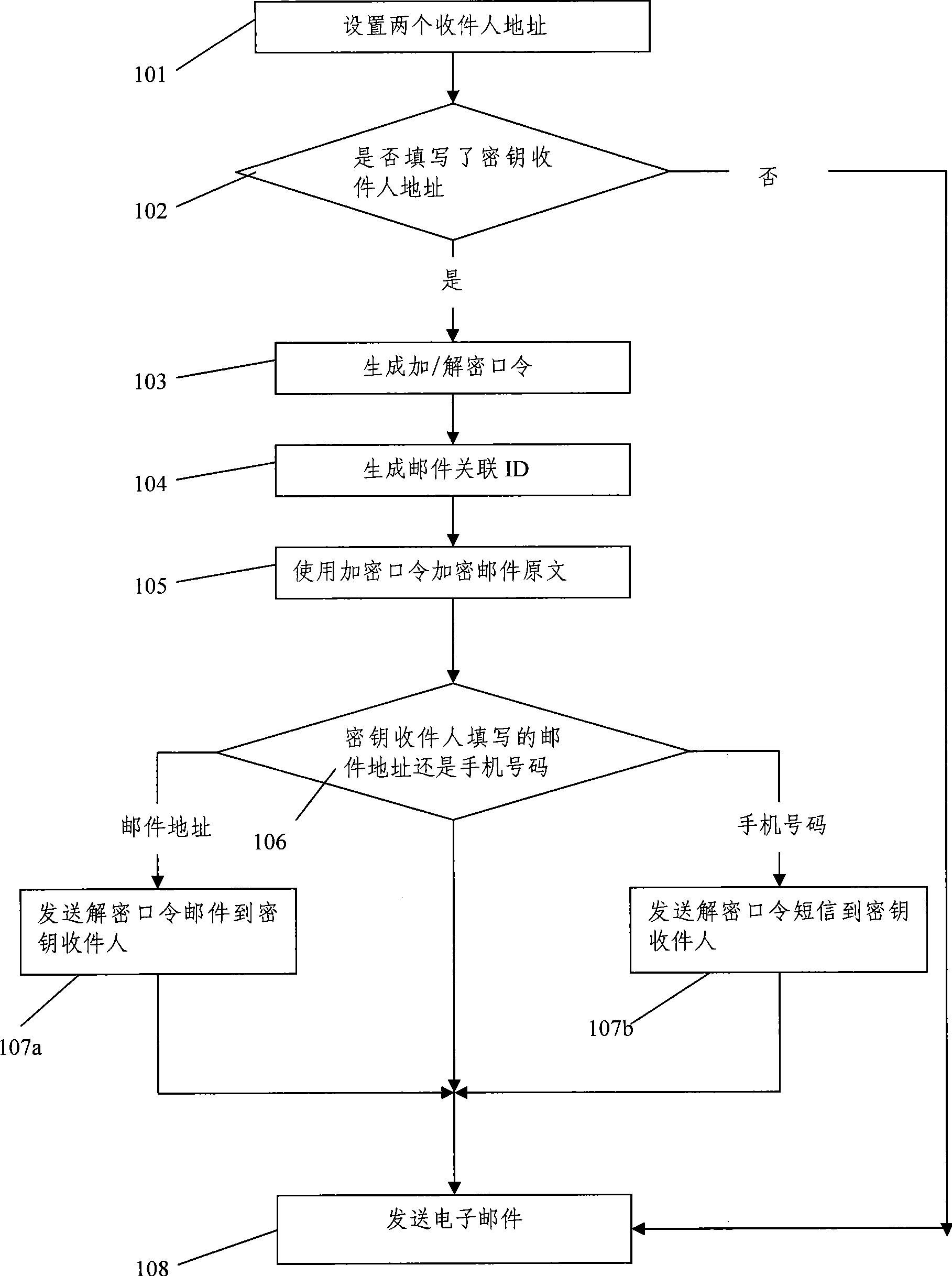
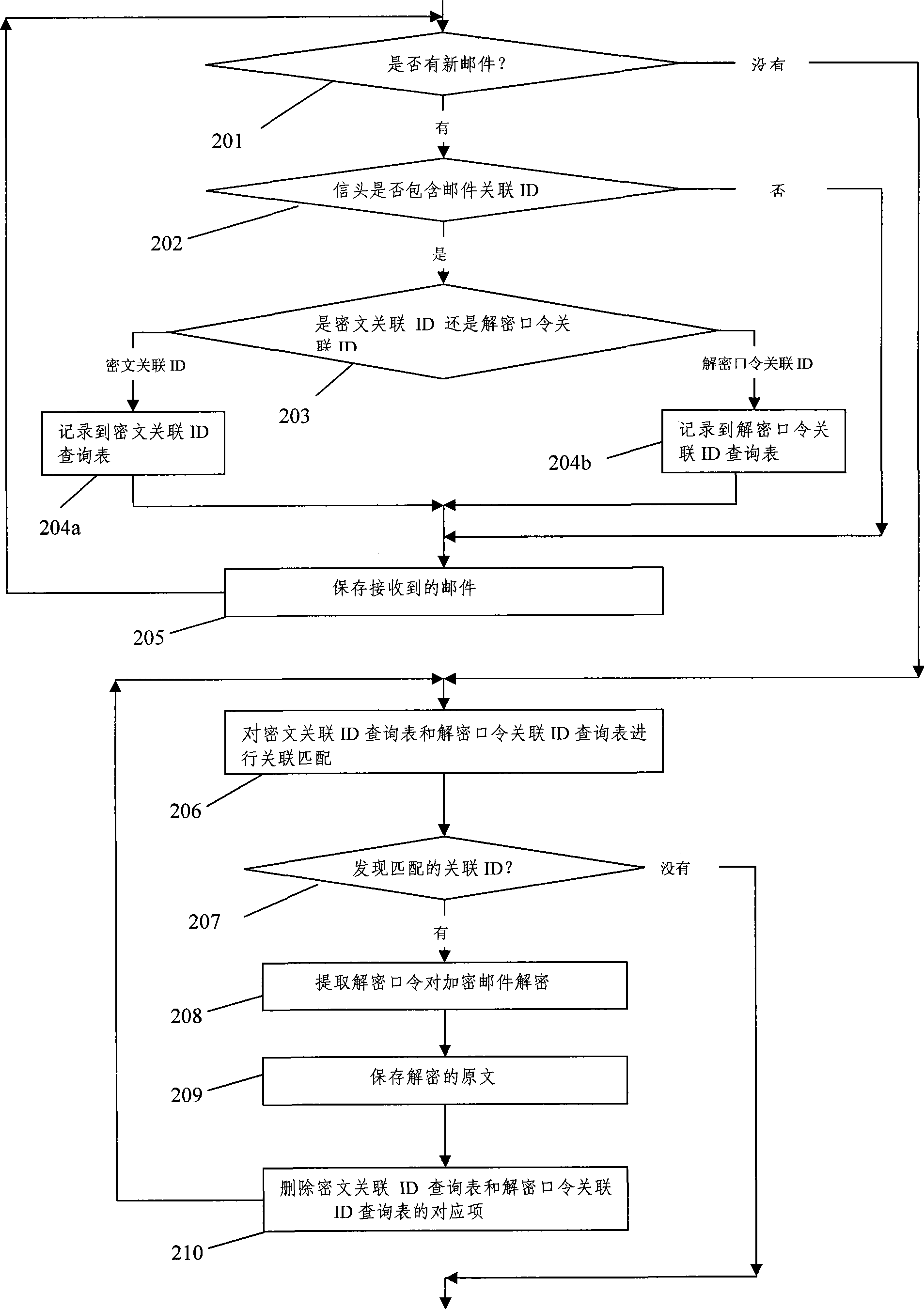
InactiveCN101369887AEasy to sendImprove securitySynchronising transmission/receiving encryption devicesData switching networksPasswordCiphertext
The invention discloses an e-mail encryption transmission method. An e-mail sender generates encryption / decryption passwords before the e-mail is sent, the e-mail sender uses an encryption password to encrypt the e-mail content and send the e-mail cipher text to a first mailbox of the receiver. At the same time the e-mail sender sends the decryption password to a second maibox of the receiver or sends the decryption password to other mobile phones through a short message. A pair of correlative unique identifications exists in the mail heads of the two e-mails, the cipher text mail is automatically decrypted through matching the correlative IDs of the cipher text mail and the decryption password, and the transmission of the encryption e-mail is finished.
Owner:阿里巴巴云计算(北京)有限公司
Secure database access through partial encryption
ActiveUS20080148070A1Unauthorized memory use protectionHardware monitoringDatabase serverDocument recognition
The present invention generally is directed to systems, methods, and articles of manufacture for securing sensitive information involved in database transactions. Embodiments of the present invention selectively encrypt only portions of transactions involving sensitive data, thereby reducing or eliminating the processing overhead resulting from wastefully encrypting non-sensitive data. The sensitive data may be identified by a document. The document may be accessed by a requesting entity to determine which portions of a query should be encrypted prior to sending the query to a database server over a network. The document may also be accessed by a database server to determine which portions of query results should be encrypted prior to sending the query results to the requesting entity over the network.
Owner:IBM CORP
E-mail encryption/decryption method and its storage media and module
InactiveCN1885762AEasy to useImprove securityData switching networksSecuring communicationCiphertextComputer science
The disclosed e-mail enciphering and deciphering method comprises: providing a mail with a head and text, selecting at least part of text and the opposite cipher; after receiving sending request, enciphering the mail to send out; once receiving the mail, displaying its head, enciphered area and other part. This invention is convenient.
Owner:EGIS TECH
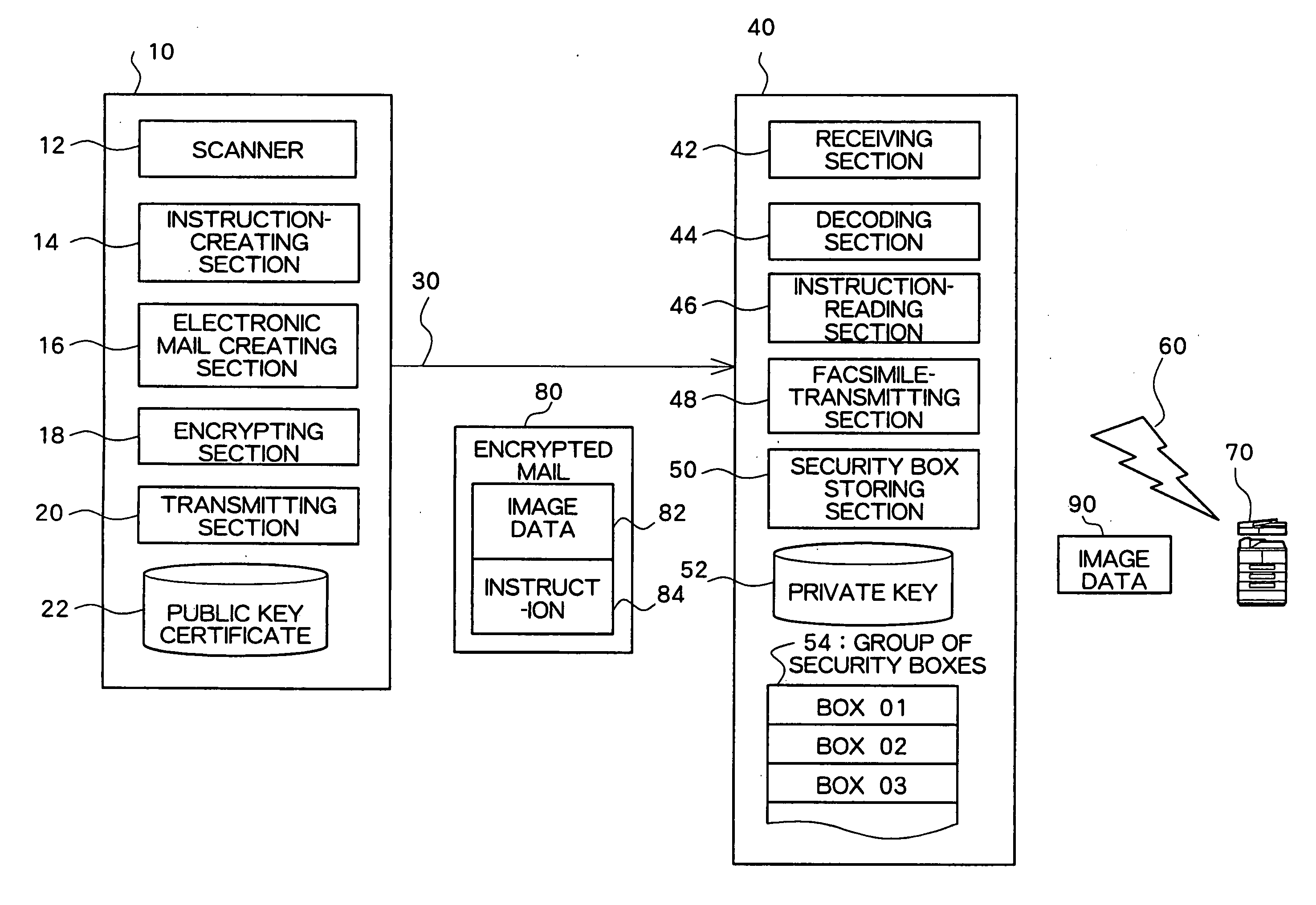
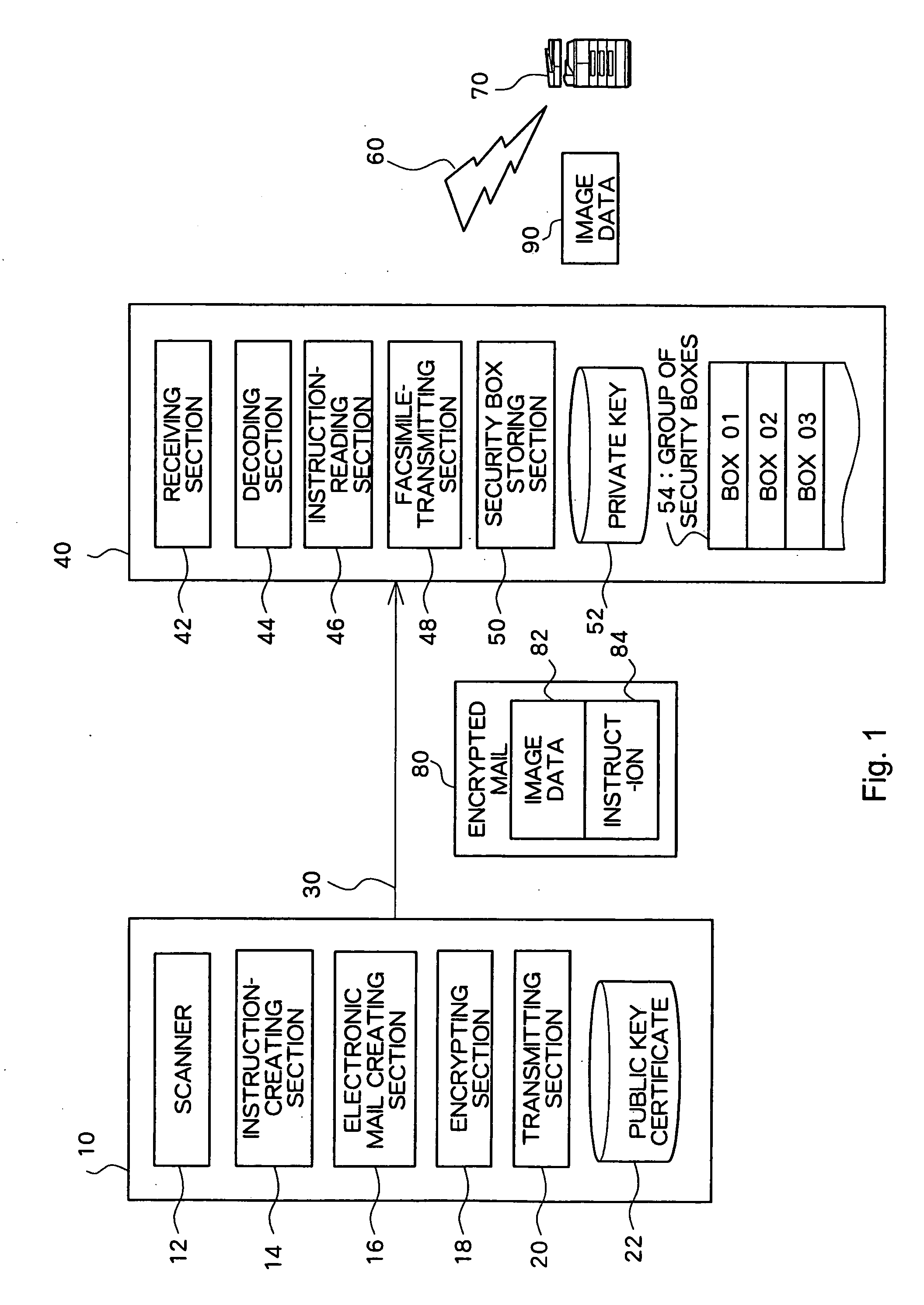
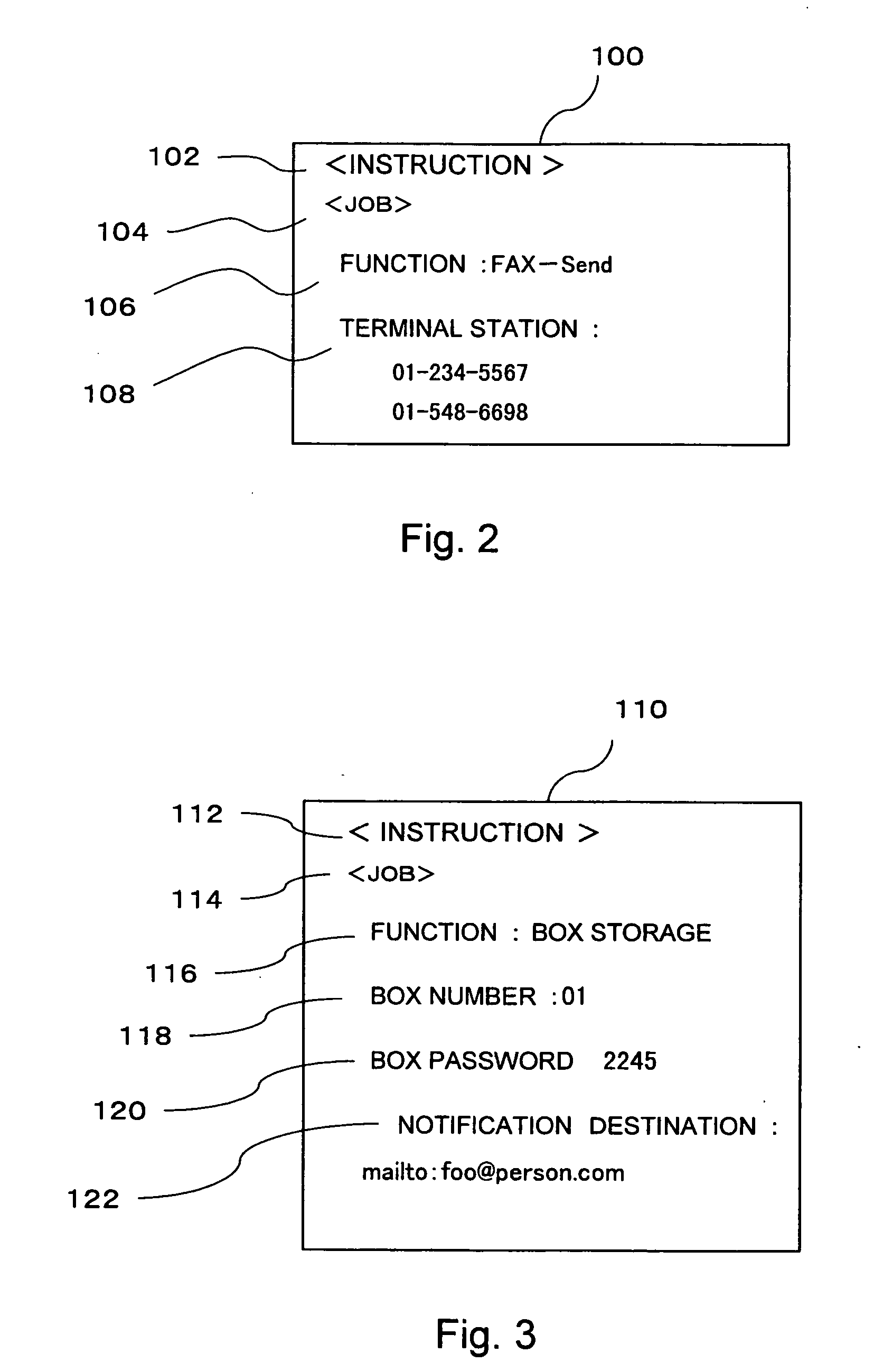
Device, program, and method for transmitting or receiving an image through electronic mail
InactiveUS20070050616A1Coding/ciphering apparatusData switching networksProcessing InstructionEmail encryption
A scanned image transmitting device has an instruction-creating section that creates an instruction describing a process instruction in relation to a scanned image; an electronic mail creating section that creates an electronic mail including the scanned image and the instruction; an encrypting section that encrypts at least a portion of the electronic mail using a public key of a transmission destination; and a transmitting section that transmits the encrypted electronic mail to the transmission destination.
Owner:FUJIFILM BUSINESS INNOVATION CORP
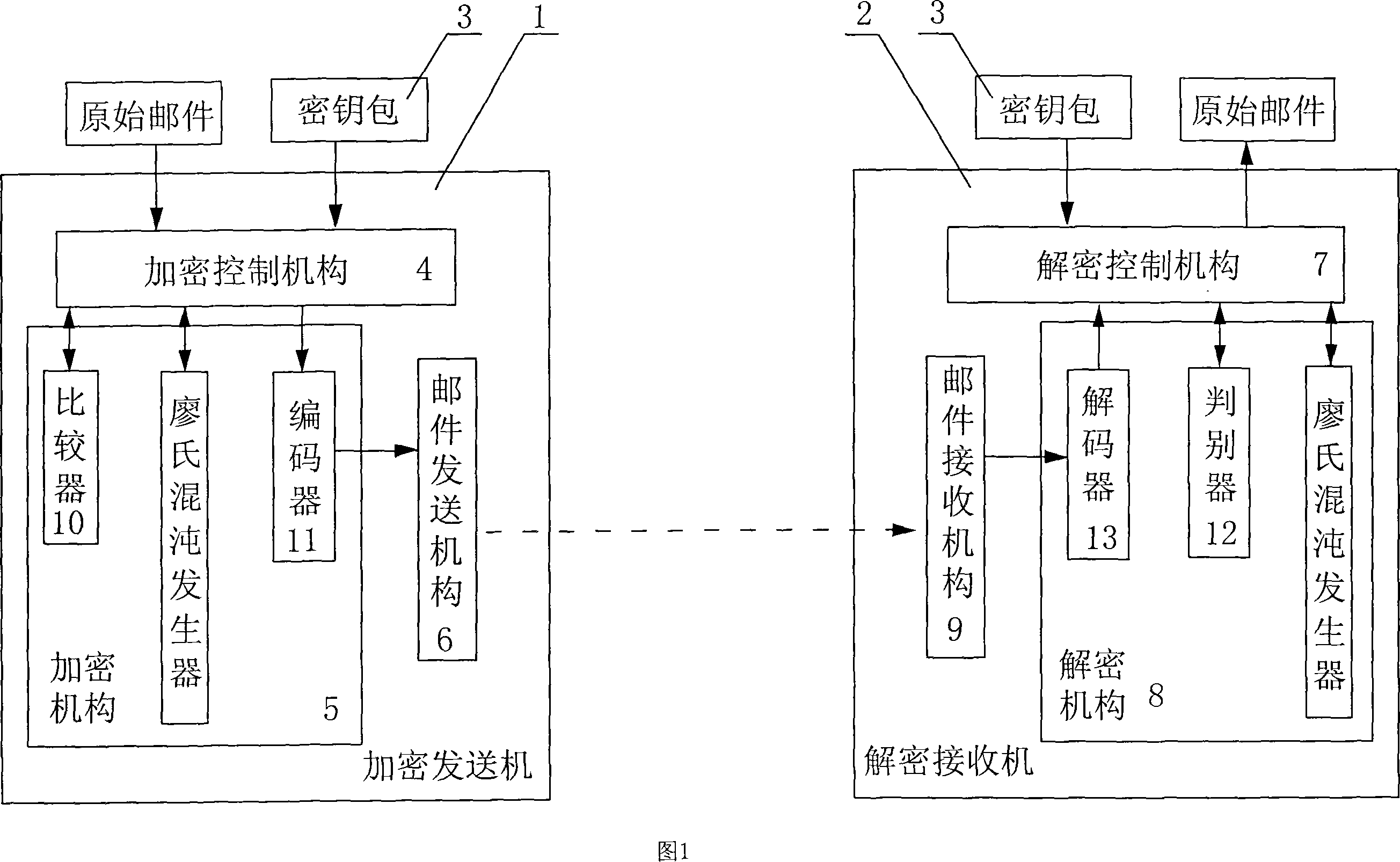
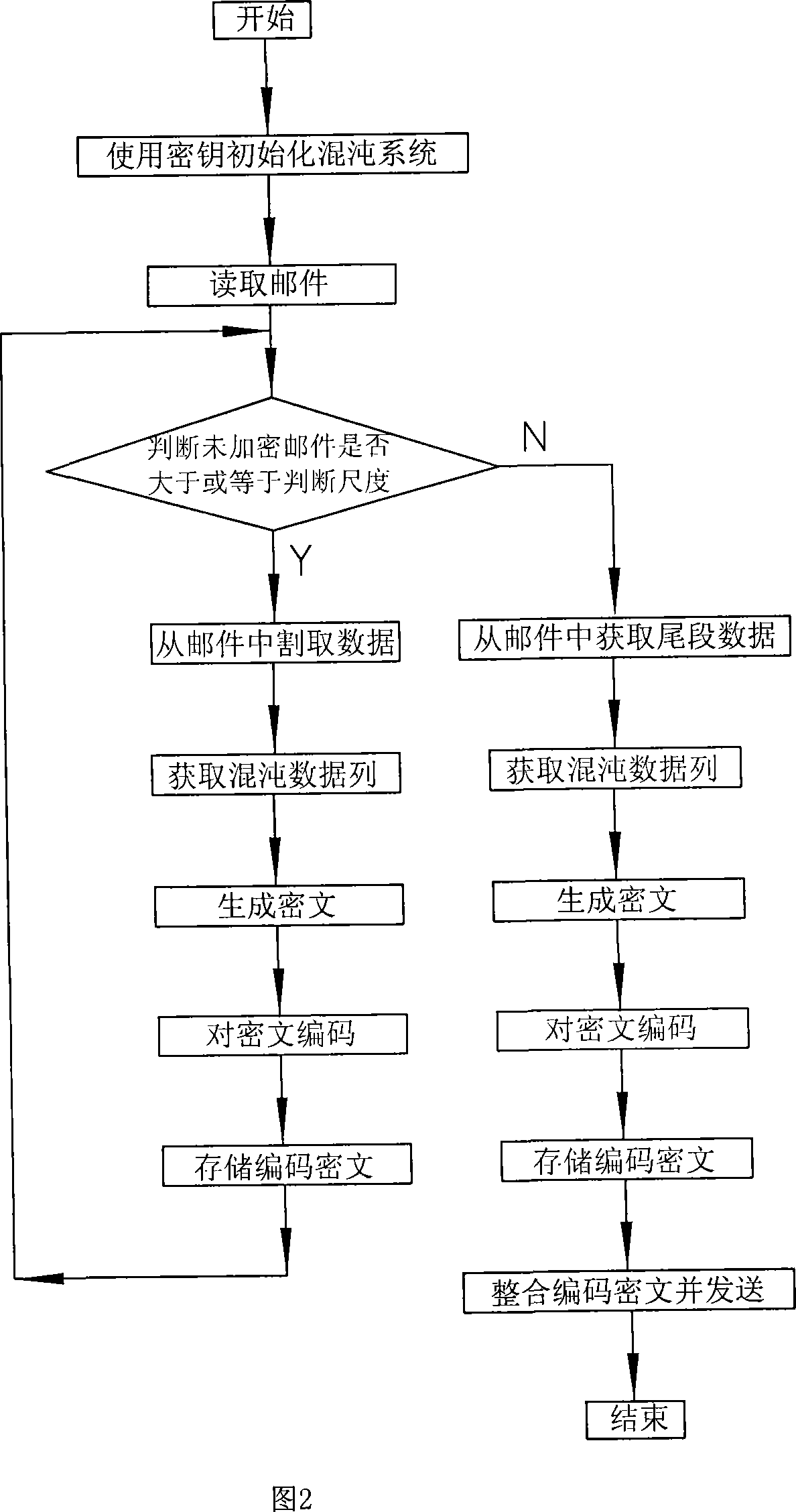
E-mail encryption transmitting-receiving system
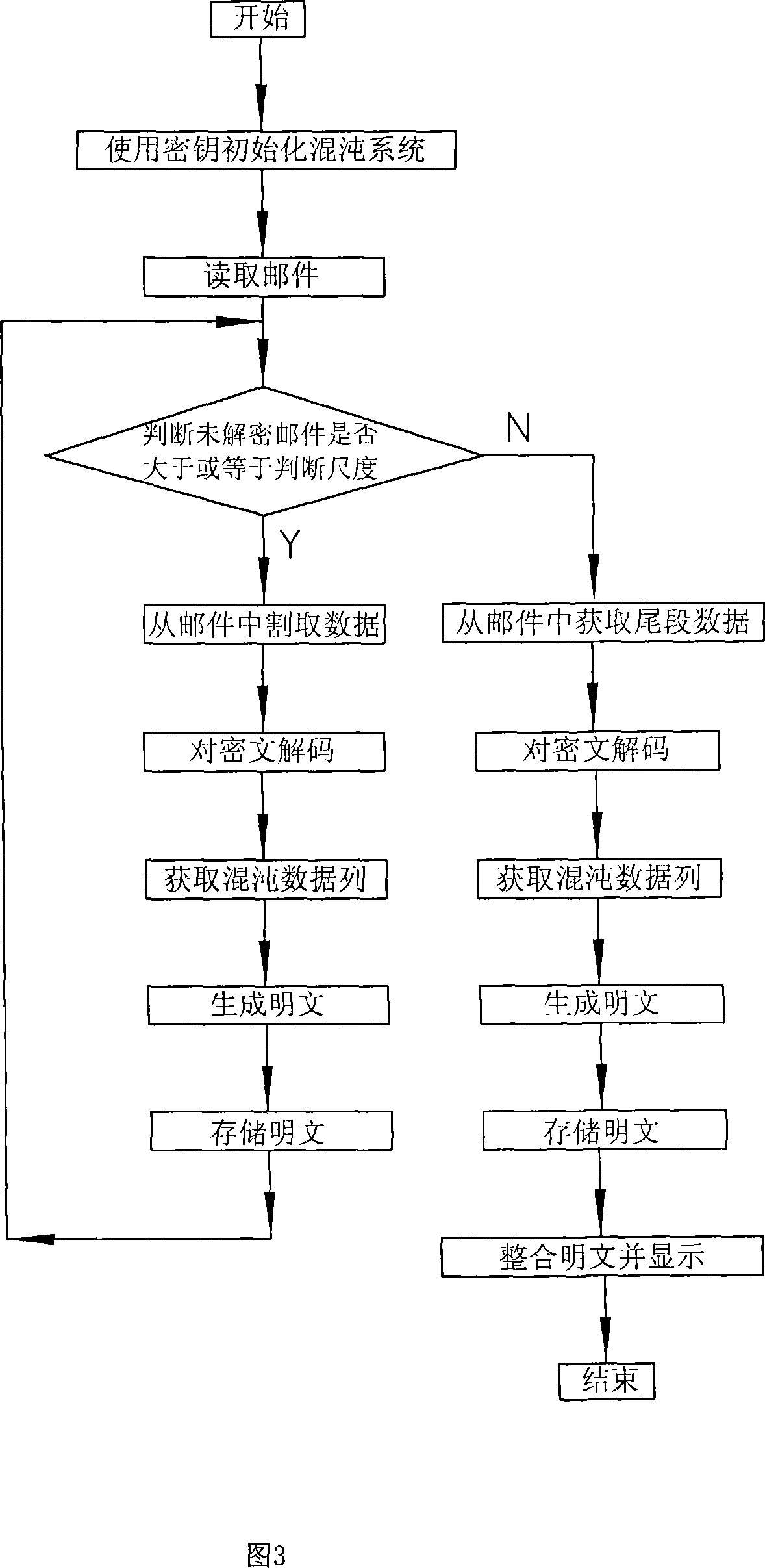
InactiveCN101159546ASimple structureFast encryptionData switching networksSecuring communicationEmail encryptionElectronic mail
An E-mail encryption / reception / transmission system is provided, which comprises an encryption transmitter, a decryption receiver and a key packet. The system is characterized in that the encryption transmitter and the decryption receiver are equipped with Liao's chaos generators which produce required chaotic sequence data. An encryption controller calculates and encrypts E-mail information by using the chaotic sequence data to produce encrypted data, and sends an encrypted E-mail. The decryption receiver calculates and decrypts the E-mail information by using the chaotic sequence data to produce a primary file. The invention has the advantages that the Liao's chaos generators are excellent in the data encryption; the system is simple, rapid and safe to operate, and the E-mail can be encrypted, decrypted and transmitted safely and quickly.
Owner:CHONGQING UNIV
Method for realizing encryption of E-mail
InactiveCN1509098AUser identity/authority verificationRadio/inductive link selection arrangementsProcess moduleThe Internet
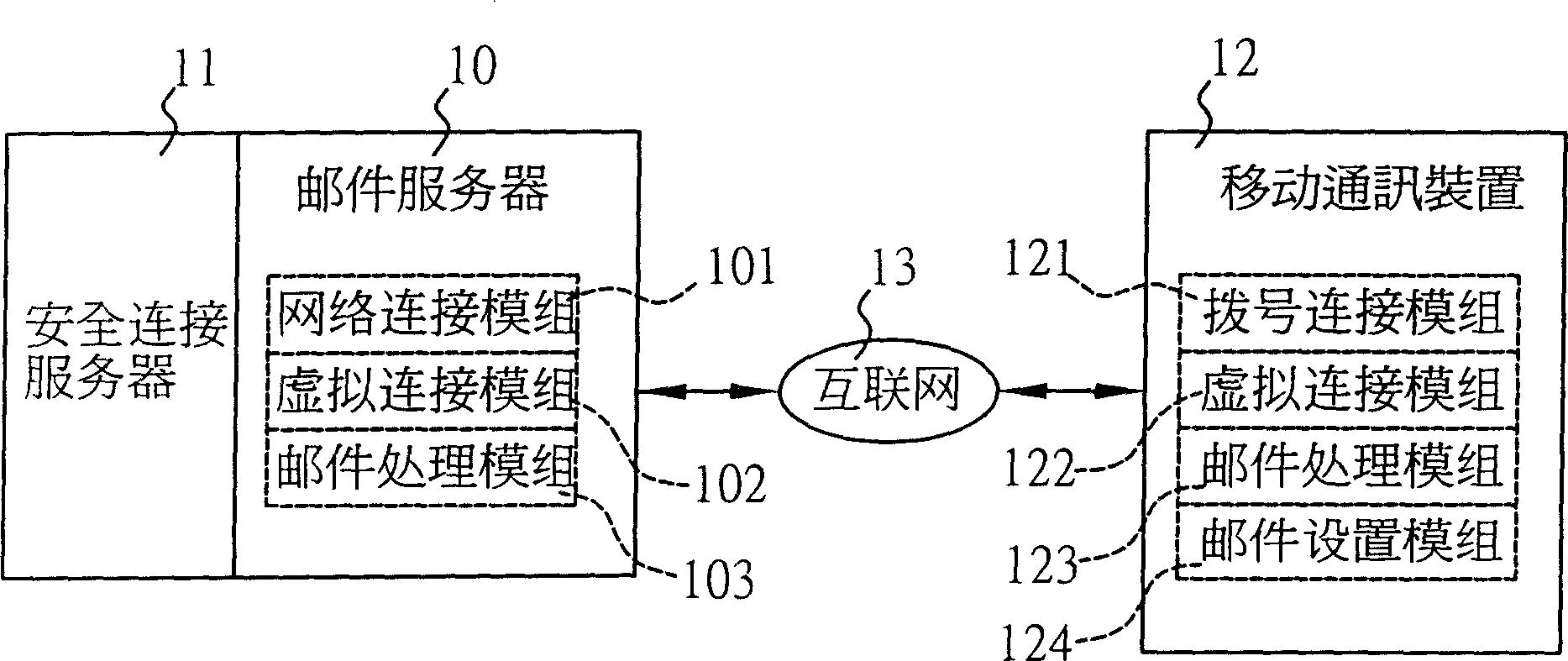
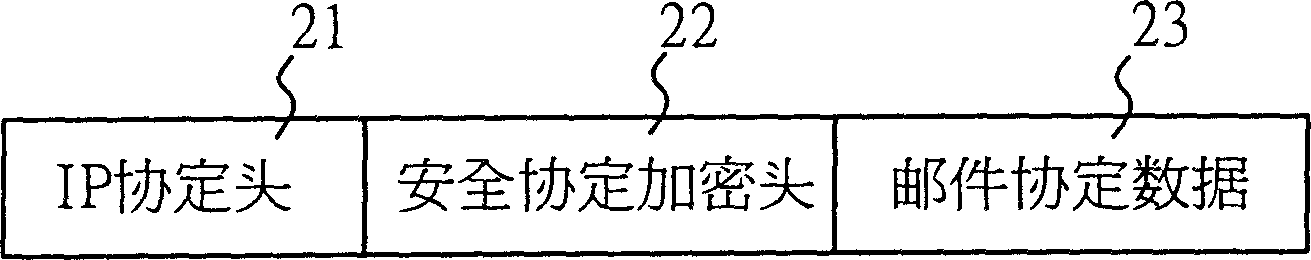
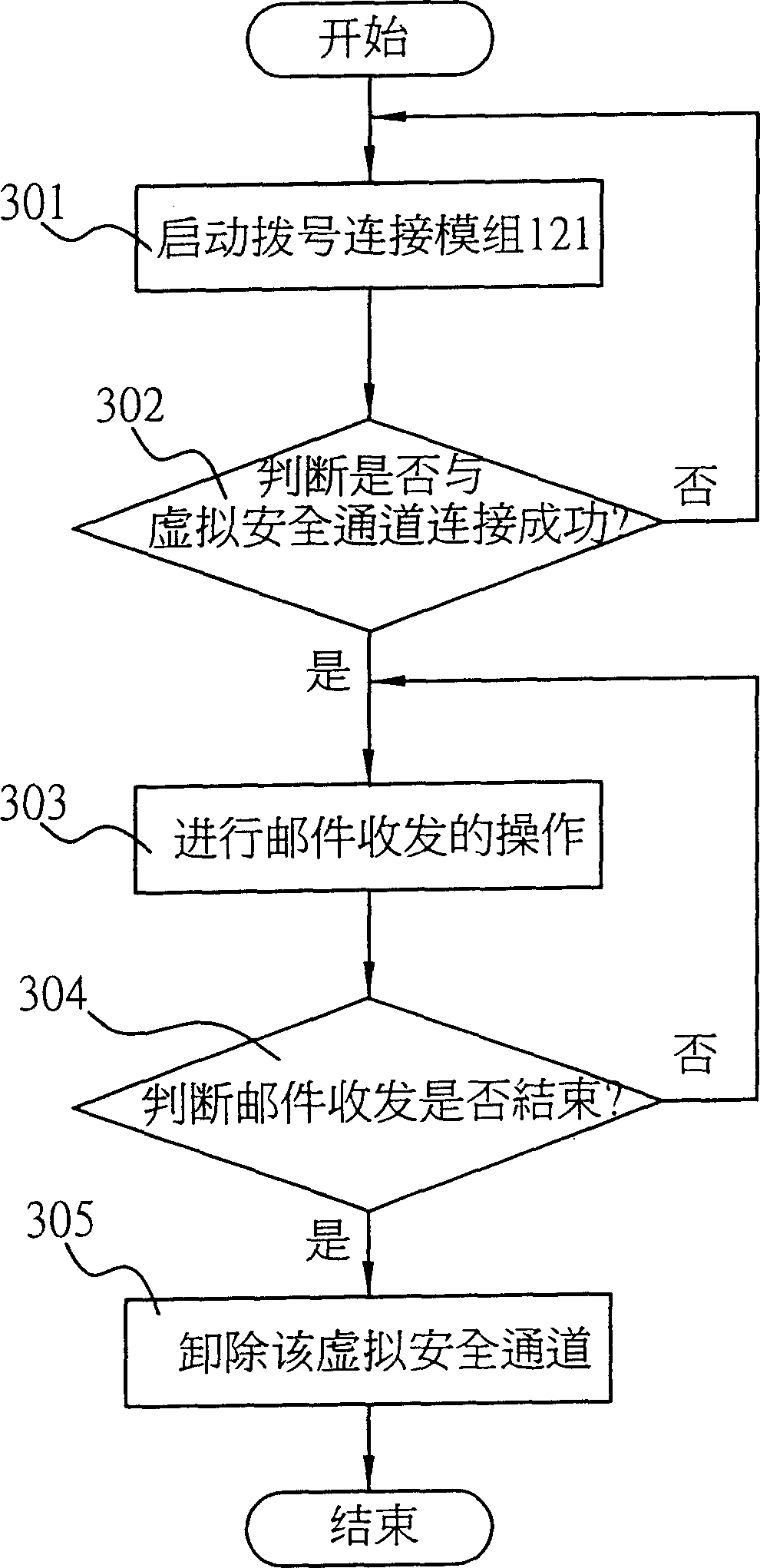
The invention sets up a safety connection server in a mail server, and sets up an address useable in the mail server into a mobile communication device. User selects sending and receiving E-mail through mobile communication device, and logs on Internet. Based on the said address, the mobile device connects to the mail server. After successful connecting, the safety connection server is started up. Procedures of authenticating id and exchanging cipher key is carried out for the said address and address of the mail server by the safety connection server so as to build a virtual channel between the mobile device and the safety connection server. Data encrypted with a cipher key in E-mail can be transmitted through the virtual safety channel. Normal sending and receiving E-mail is carried out through a mail processing module inside the mobile device. Thus, important information in E-mail will not be intercepted or stolen by other persons.
Owner:INVENTEC(NANJING) TECH CO LTD
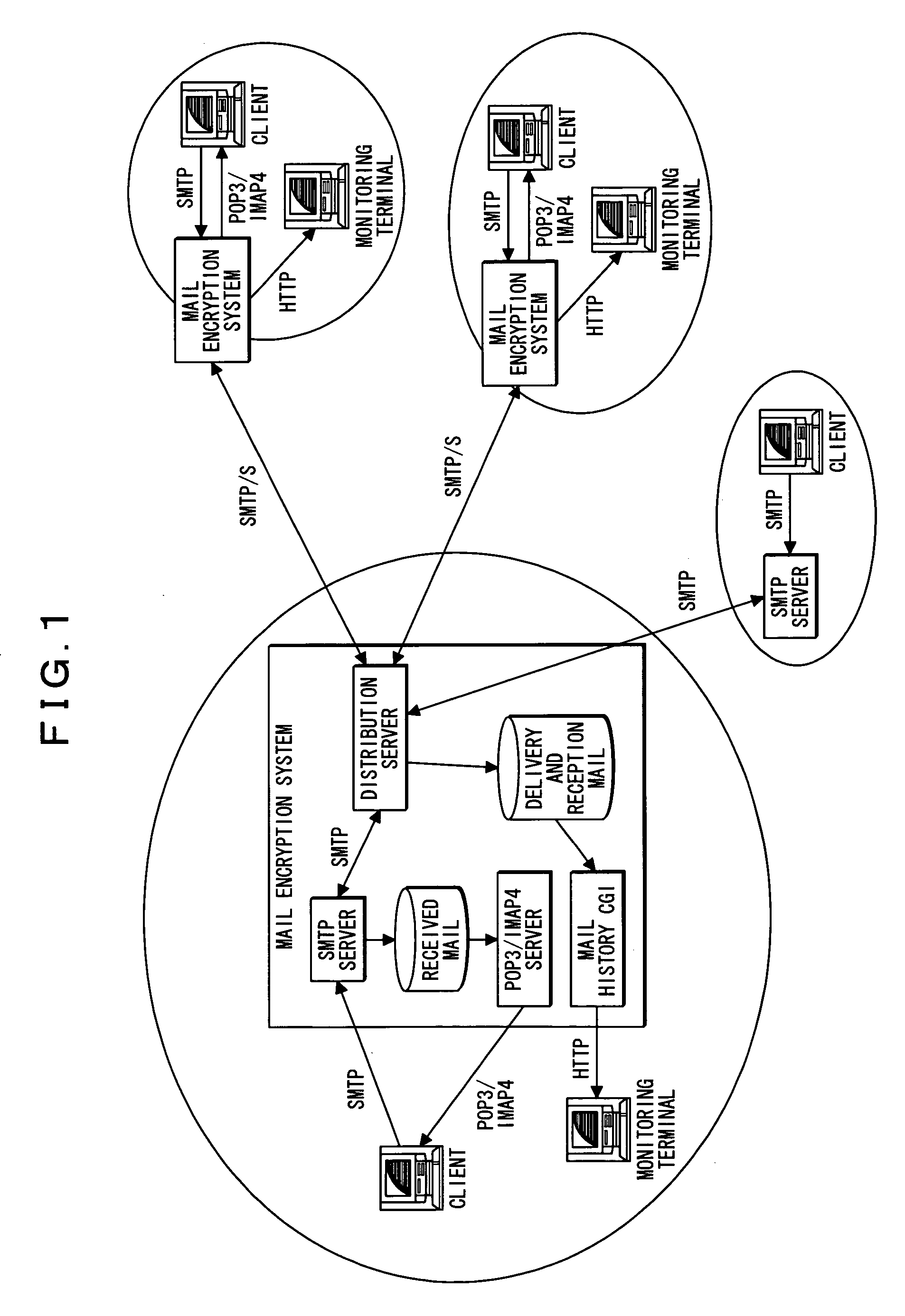
Network security system
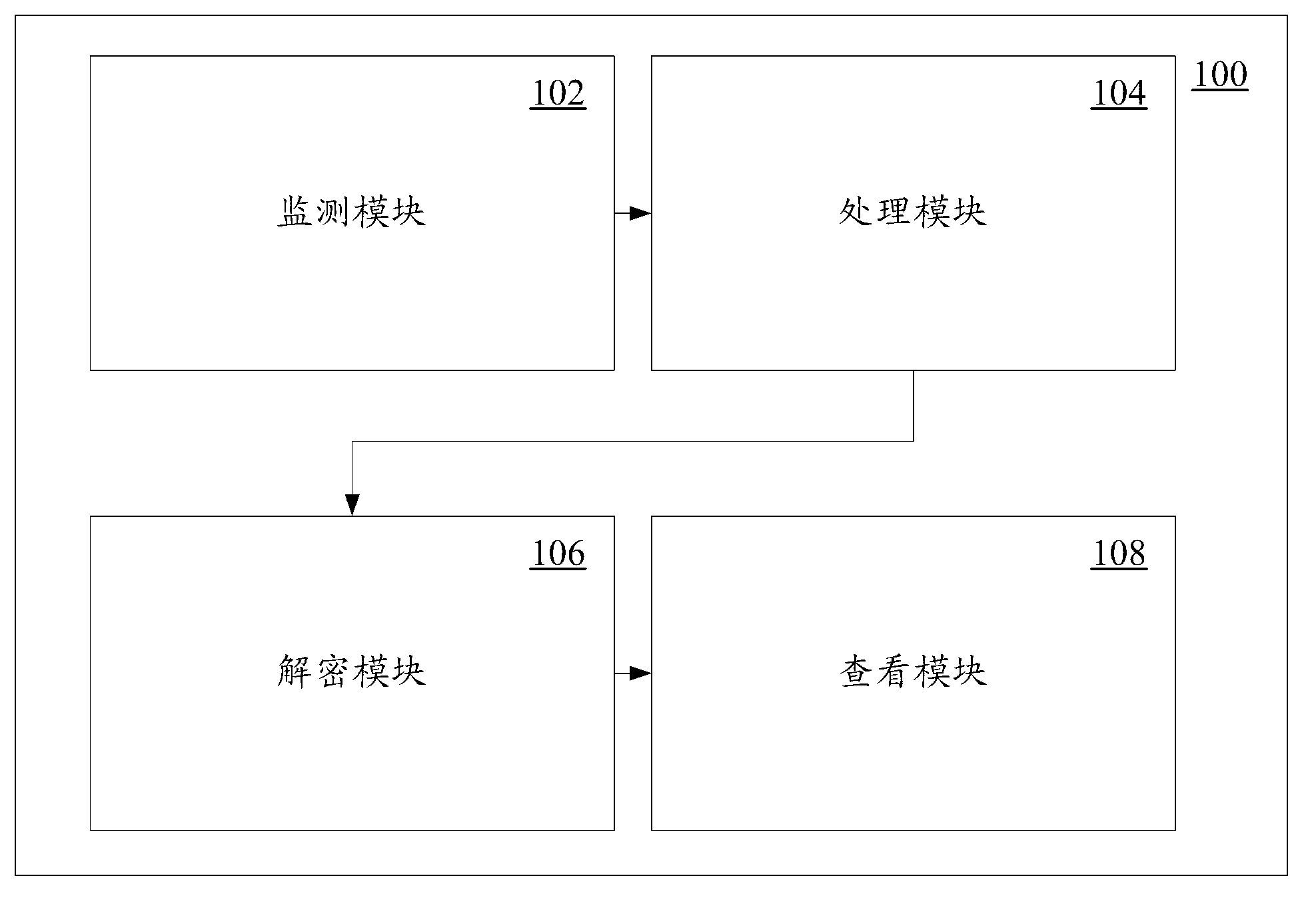
ActiveCN103023655AImprove securityUser identity/authority verificationData switching networksSecurity monitoringElectronic mail
The invention provides a network security system. The network security system comprises a monitoring module, a processing module, a deciphering module and a viewing module, wherein the monitoring module is used for conducting security monitoring on received electronic mails, the processing module is used for encrypting electronic mails, the deciphering module is used for deciphering encrypted electronic mails, and the viewing module is used for viewing deciphered electronic mails. The network layer security performance can be improved through the network security system.
Owner:DAWNING CLOUD COMPUTING TECH CO LTD
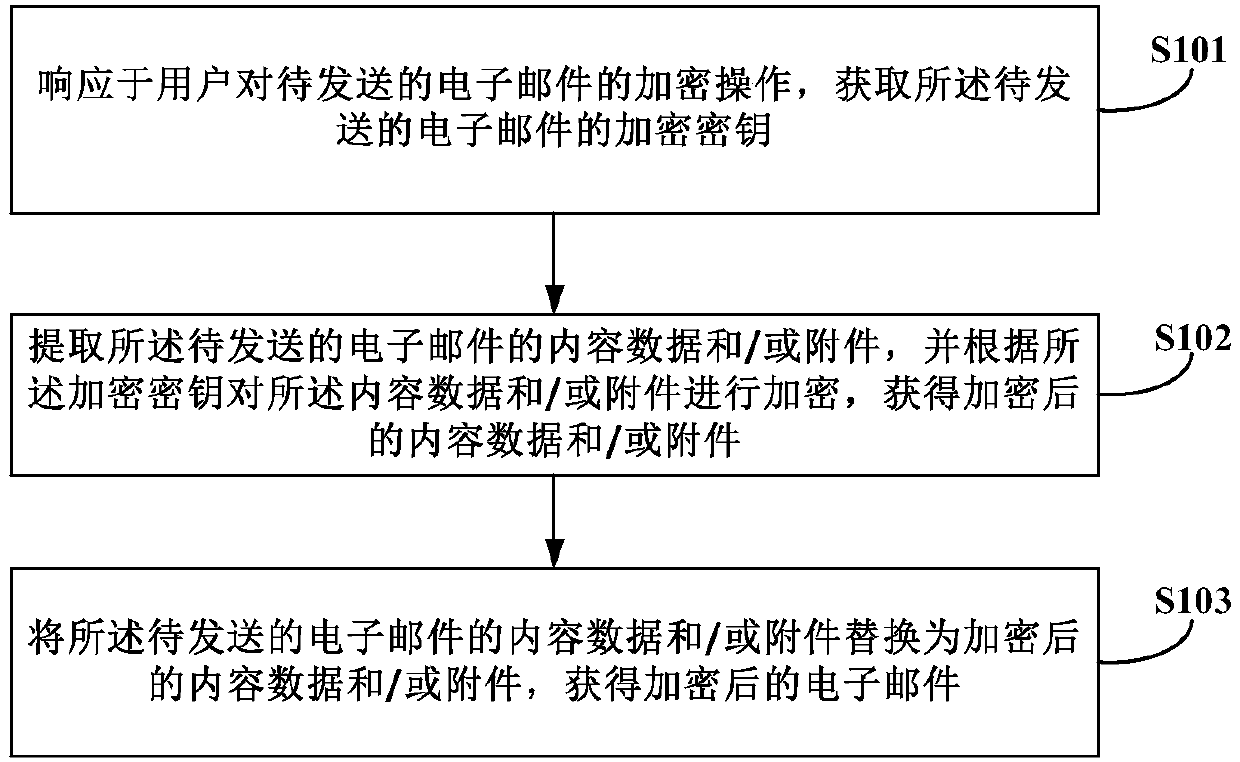
Email encryption and decryption method, storage medium and electronic device
ActiveCN108055271ADifferentiated confidentiality requirementsAvoid LeakageData switching networksComputer scienceEmail encryption
The embodiment of the invention provides an email encryption and decryption method, a storage medium and an electronic device, and relates to the field of email communication. The email encryption anddecryption method comprises the following steps: in response to an encryption operation of a user to a to-be-sent email, obtaining an encryption key of the to-be-sent email; extracting content data and / or an attachment of the to-be-sent email, and encrypting the content data and / or the attachment according to the encryption key to obtain encrypted content data and / or attachment; and replacing thecontent data and / or the attachment of the to-be-sent email with the encrypted content data and / or attachment to obtain an encrypted email. By adoption of the email encryption and decryption method provided by the embodiment of the invention, the to-be-sent email can be encrypted according to the demand of the user, and different encryption demands can be provided for different emails sent to thesame receiver.
Owner:北京亿赛通科技发展有限责任公司
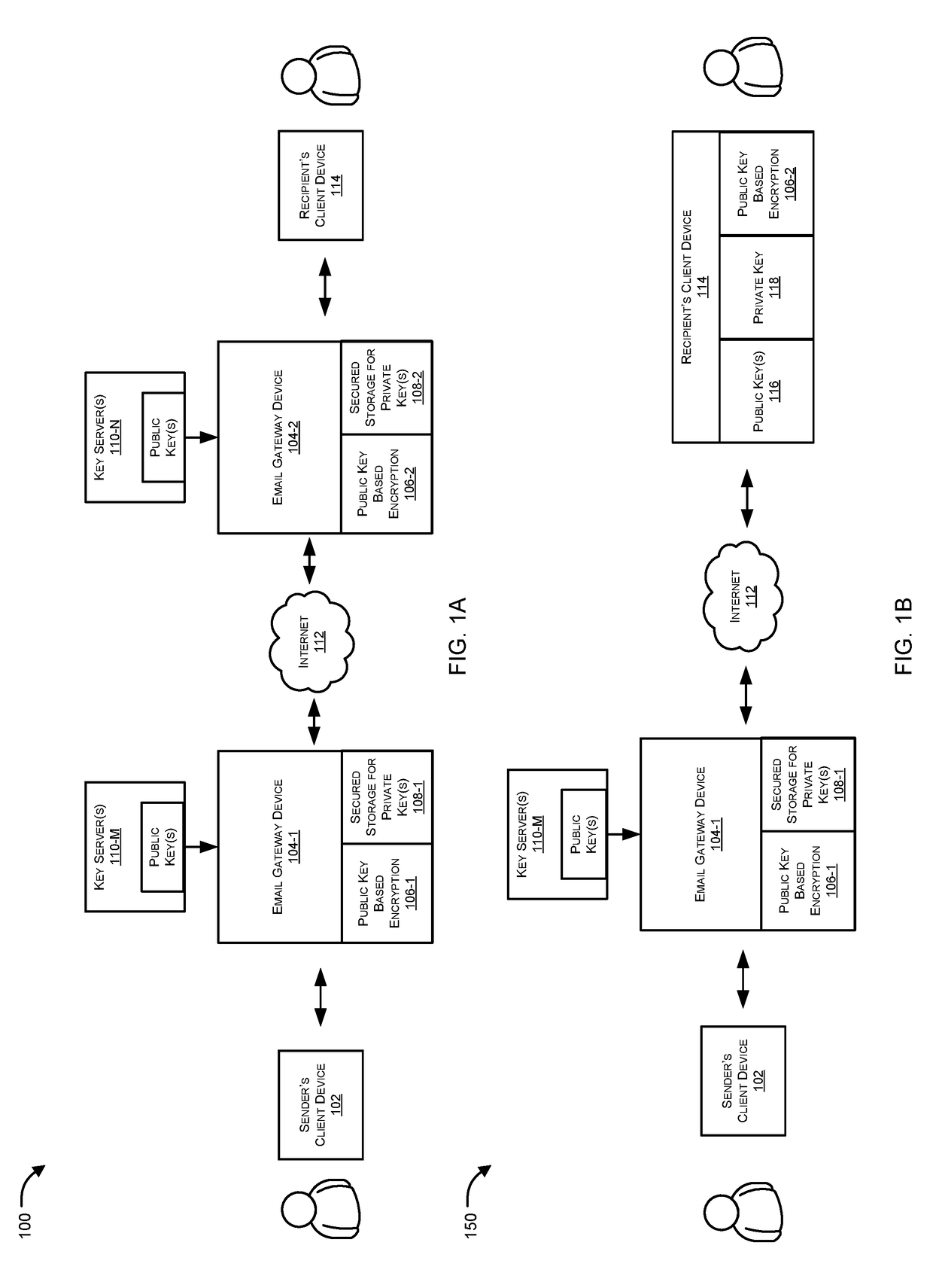
Automatic electronic mail (EMAIL) encryption by email servers
Systems and methods for automated email encryption between email servers are provided. According to one embodiment, an email, originated by a sender using a client device coupled with a private network and directed to a recipient, is received by an email server associated with the private network. A key server is queried for public keys of the recipient and the sender. When the recipient's public key is returned by the key server, it is used to encrypt the email message; otherwise, no encryption is performed. When the sender's public key does not exist on the key server, the email server automatically generates a temporary key pair for the sender on the fly and without requiring intervention on the part of the sender. Finally, both the email message and the public key of the sender are transmitted by the email server to the recipient.
Owner:FORTINET
File encryption system based on third party key management
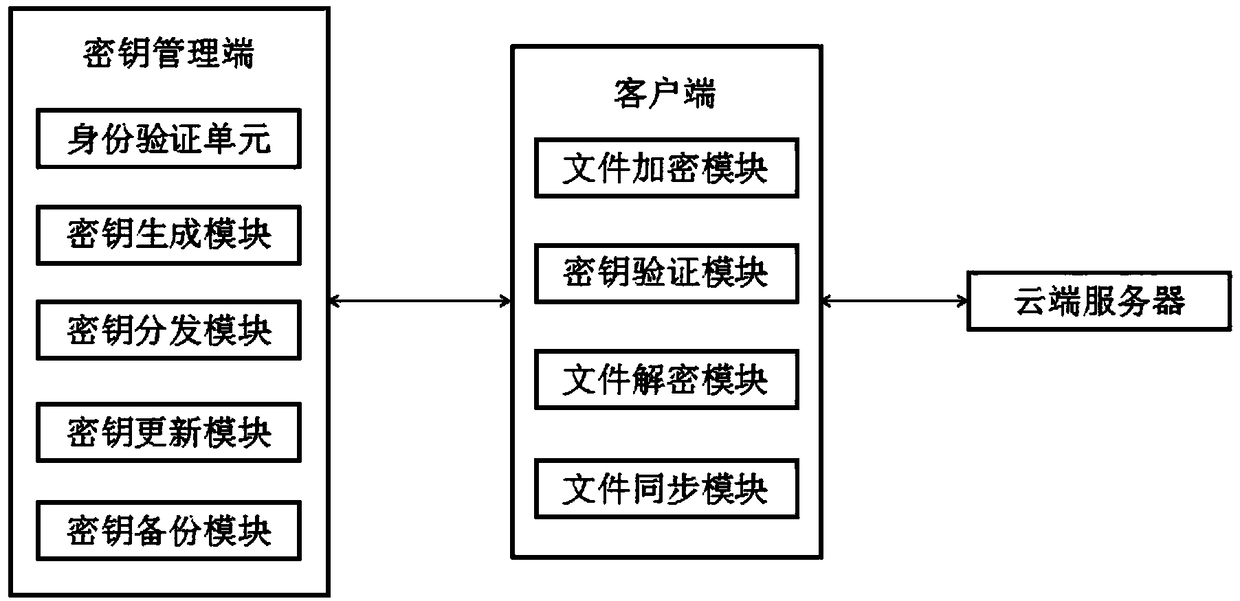
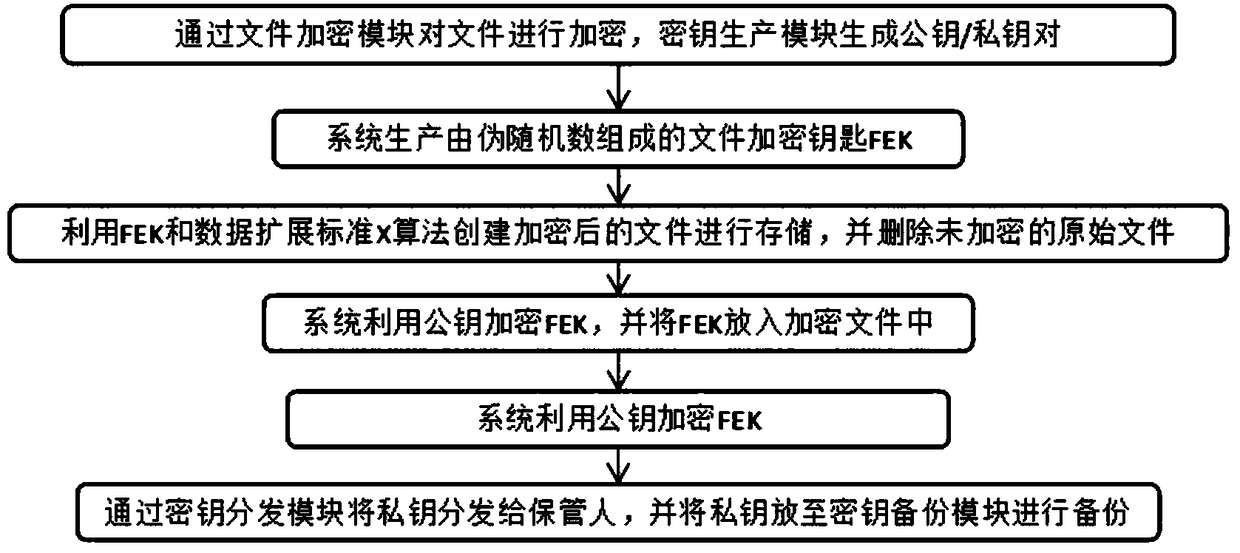
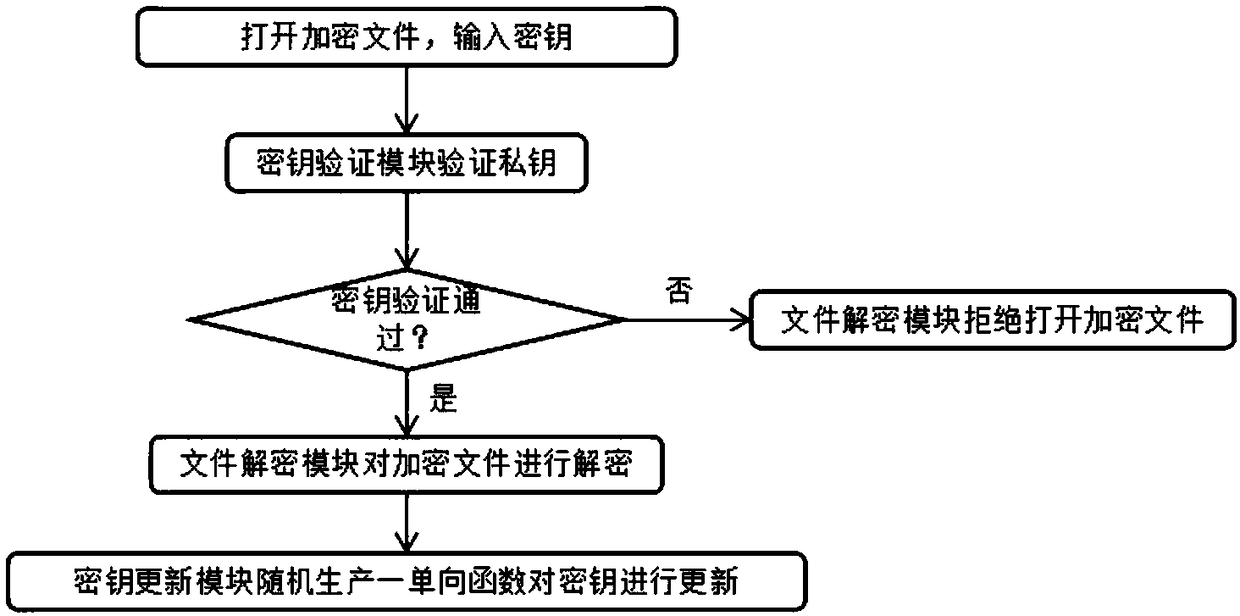
ActiveCN108173880AReduced risk of crackingSolve security encryption problemsTransmissionThird partyXML Encryption
The invention discloses a file encryption system based on third party key management, which relates to the technical field of information security. The file encryption system comprises a key manager used for managing keys, a client used for file encryption / decryption and synchronization, and a cloud server used for storing and backing up encrypted files. The client and the cloud server carry out information interaction through the Ethernet. The client encrypts / decrypts files, and transmits the files to the cloud server for storage and backup. According to the invention, keys are managed by theindependent third party key manager, an encrypted file can be opened only when the key is obtained, and it is ensured that only the user himself or herself can see the file being decrypted and opened. Moreover, the file is encrypted / decrypted and synchronized to the cloud server by the client. The problem on how to encrypt a file securely is well solved. A key is updated by a key update module after the key is verified by a key verification module, and therefore, the risk of key cracking is reduced.
Owner:合肥图久智能科技有限公司
An email encryption method and system based on group cryptography
ActiveCN108011885BEasy to superviseMultiple keys/algorithms usageData switching networksCryptosystemEngineering
The invention relates to the field of information technology, in particular to an email encryption method and system based on a group password system, which are used for secure data exchange. The email encryption system manages a group public key based on the group password system, and generates a different private key for each user, and implements an encryption mechanism for one or more designated authorized users through the group public key, and the user password The key is issued and managed by the server, so the system can supervise the content of encrypted emails; email encryption only needs to obtain the group public key certificate of the email system where the recipient is located, and the certificate is uniformly managed by the email system. Compared with the personal public key certificate Storage and maintenance are relatively simple; and for multiple recipients in the same mail system, the group public key certificate only needs to be obtained once, and it has the advantages of simple certificate verification and high encryption efficiency.
Owner:UNIV OF SCI & TECH BEIJING
Method and system for securely storing and using private cryptographic keys
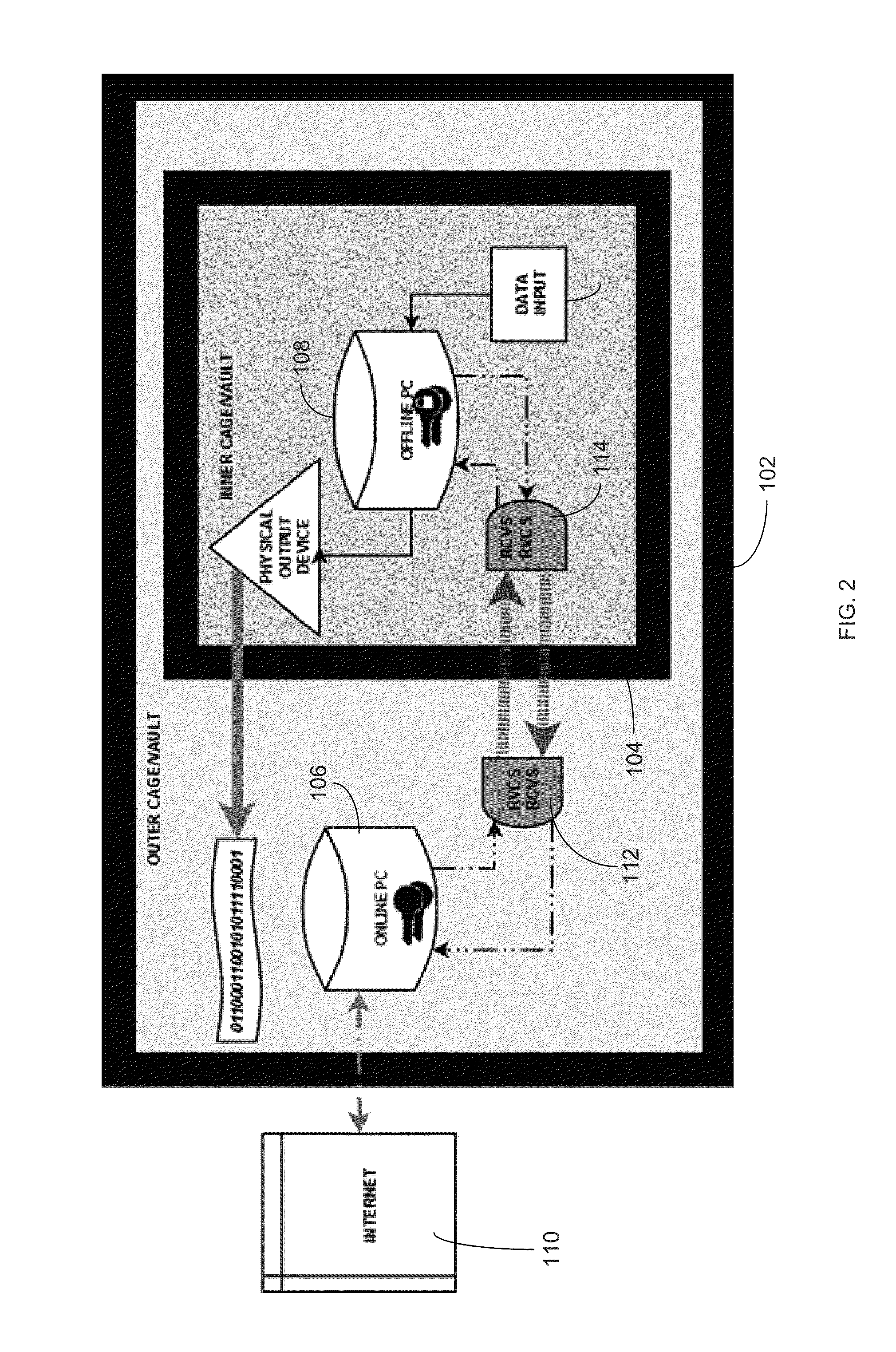
InactiveUS20160218873A1Minimize and reduce riskFacilitate creation and secure use and maintenanceKey distribution for secure communicationDigital data protectionMedical recordFinancial transaction
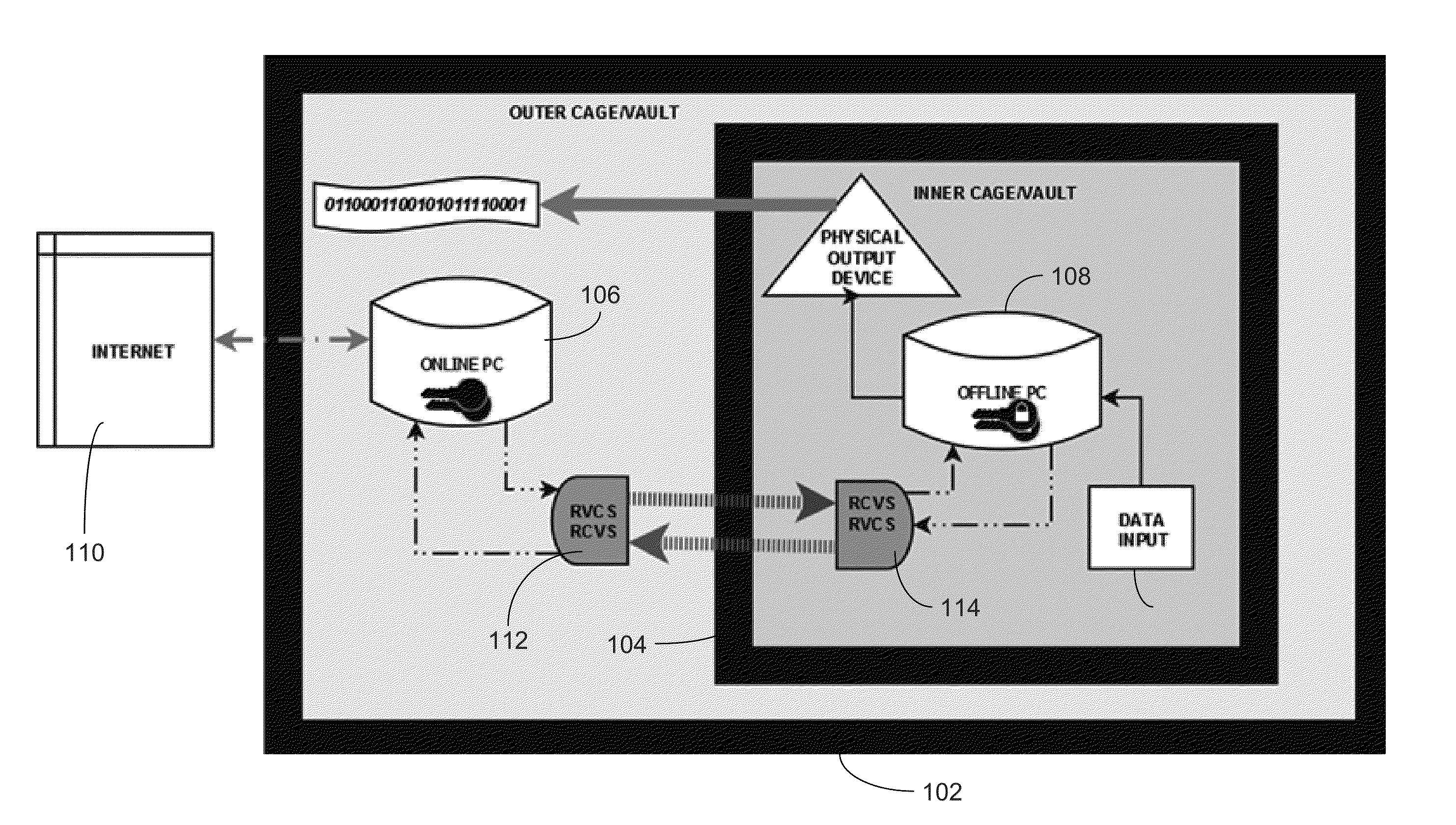
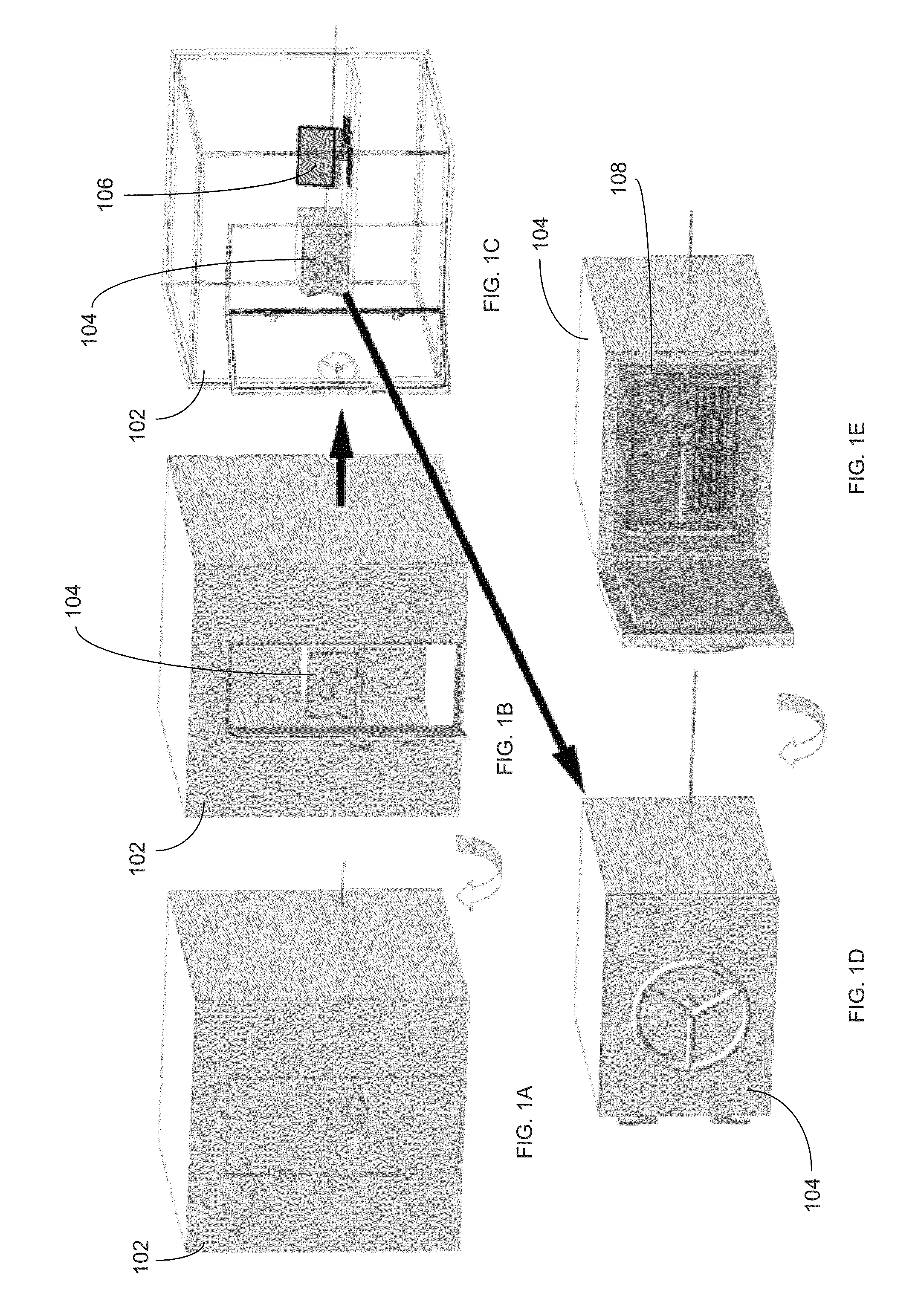
A cryptographic system includes an online computer, an offline computer and custom hardware and software by which the two computers can securely communicate to facilitate the creation, secure use, and maintenance of private cryptographic keys. The system securely stores private cryptographic keys while still enabling the keys to be quickly and easily accessed as needed in a variety of applications including, but not limited to, electronic financial transactions, cryptographic transaction processing, medical record access, email encryption, or any other cryptographic authentication process.
Owner:VERMONT SECURE COMPUTING INC
Automatic electronic mail (email) encryption by email servers
ActiveUS10484397B2User identity/authority verificationData switching networksPrivate networkClient-side
Owner:FORTINET
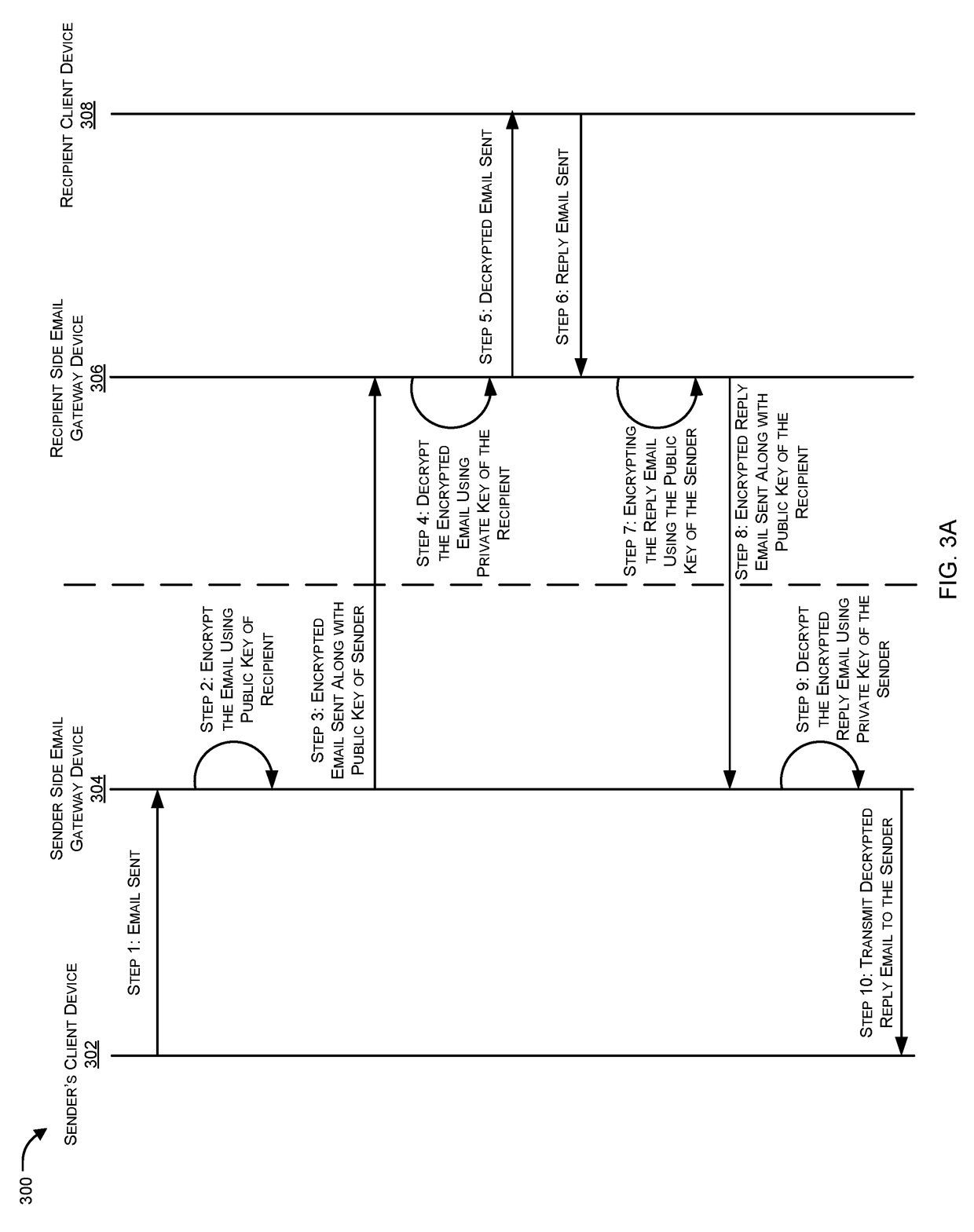
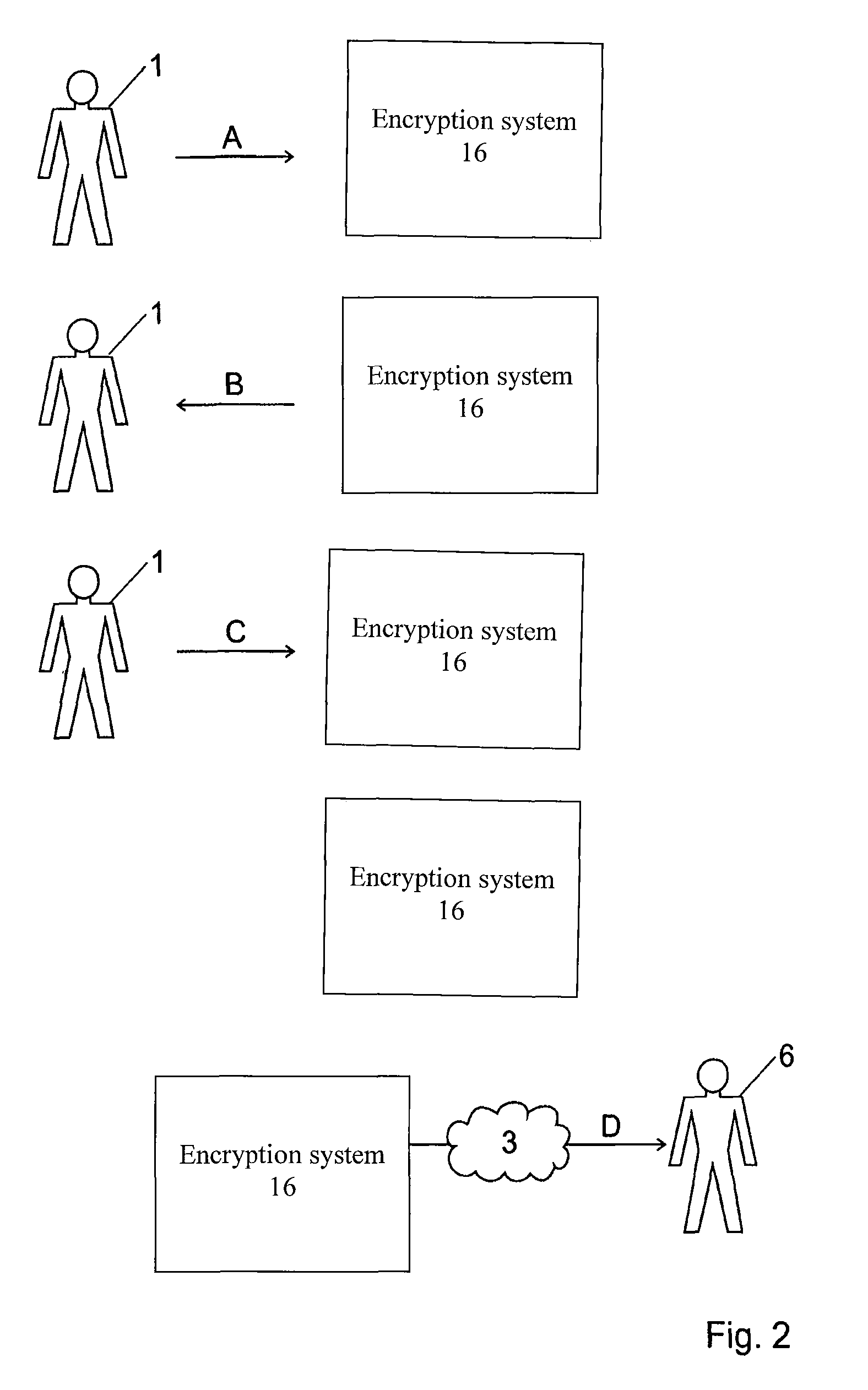
End-to-end encryption method and system for emails
ActiveUS8726026B2Easy accessEasy to makeUser identity/authority verificationData switching networksEnd-to-end encryptionInternet privacy
An end-to-end encryption method for emails sent from a sender (1) to a recipient (6) is disclosed. According to the method, the sender requests from an encryption system (16) a certificate corresponding to the recipient (6), and the encryption system (16) returns to the sender (11) a first, proforma certificate corresponding to the recipient (6). The sender (1) sends with his email client (11) an outgoing email to the recipient encrypted with the proforma certificate, and the email is forwarded through the encryption system (16). The encryption system (16) decrypts the email using a private key corresponding to the certificate and also makes the content of the email available to the recipient (6).
Owner:TOTEMO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com