E-mail encryption transmitting-receiving system
A technology for sending and receiving systems and e-mails, applied in electrical components, transmission systems, digital transmission systems, etc., can solve the problems of inappropriate AES algorithm, insecure AES algorithm, and no detailed description of encryption algorithm.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
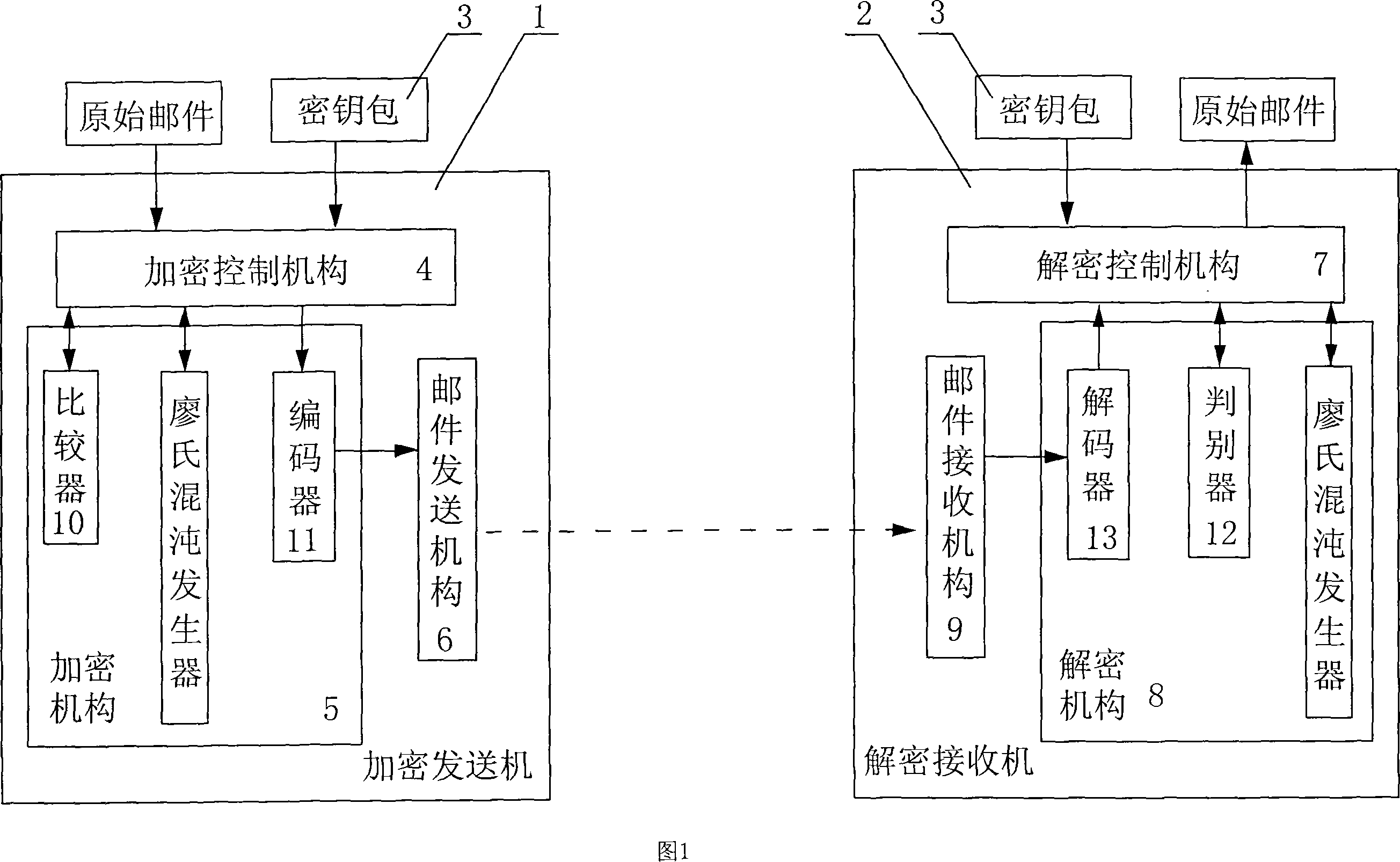
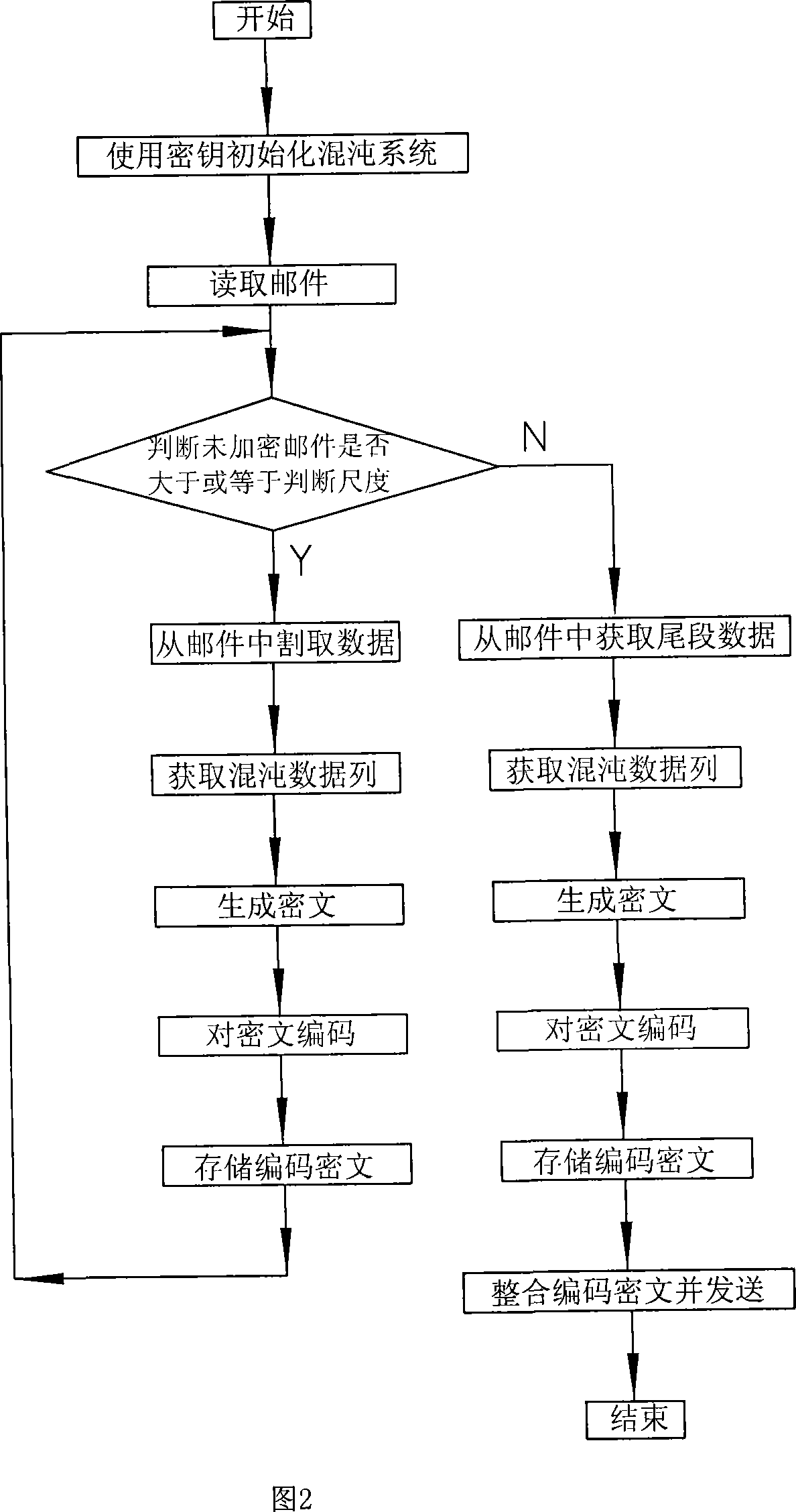
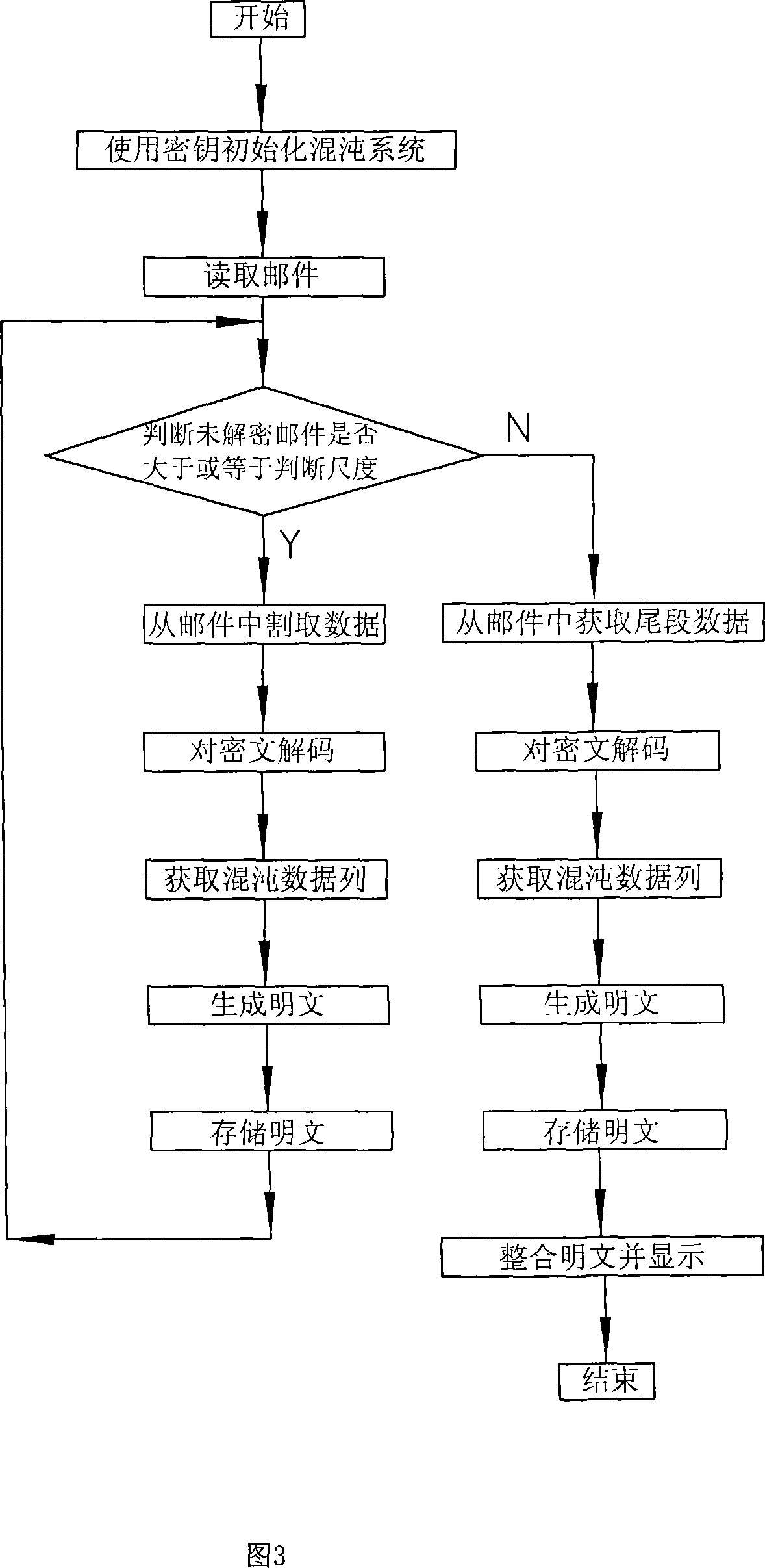
[0074] As shown in Figure 1, the present invention is a kind of electronic mail encryption sending and receiving system, is made up of encrypting transmitter 1, deciphering receiver 2 and key bag 3, and described encrypting transmitter 1 is provided with encryption control mechanism 4, encryption mechanism 5 and a mail sending mechanism 6, wherein the encryption control mechanism 4 obtains the original mail, and reads the key in the key bag 3, and the output end of the encryption control mechanism 4 sends the key and the original mail to the encryption mechanism 5, The encryption mechanism 5 is equipped with a Liao's chaos generator, and the Liao's chaos generator generates the required chaos sequence data. The encryption control mechanism 4 uses the chaos sequence data to encrypt the mail information to obtain encrypted data, and then encodes the encrypted data and Integrated into an encrypted package, the encrypted control mechanism 4 sends the encrypted package to the mail s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com