Patents
Literature
55results about How to "Encrypted security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data encrypting method and device and data decrypting method and device
ActiveCN105760765ARealize multi-dimensional encryptionAvoid crackingEncryption apparatus with shift registers/memoriesDigital data protectionComputer hardwareOriginal data
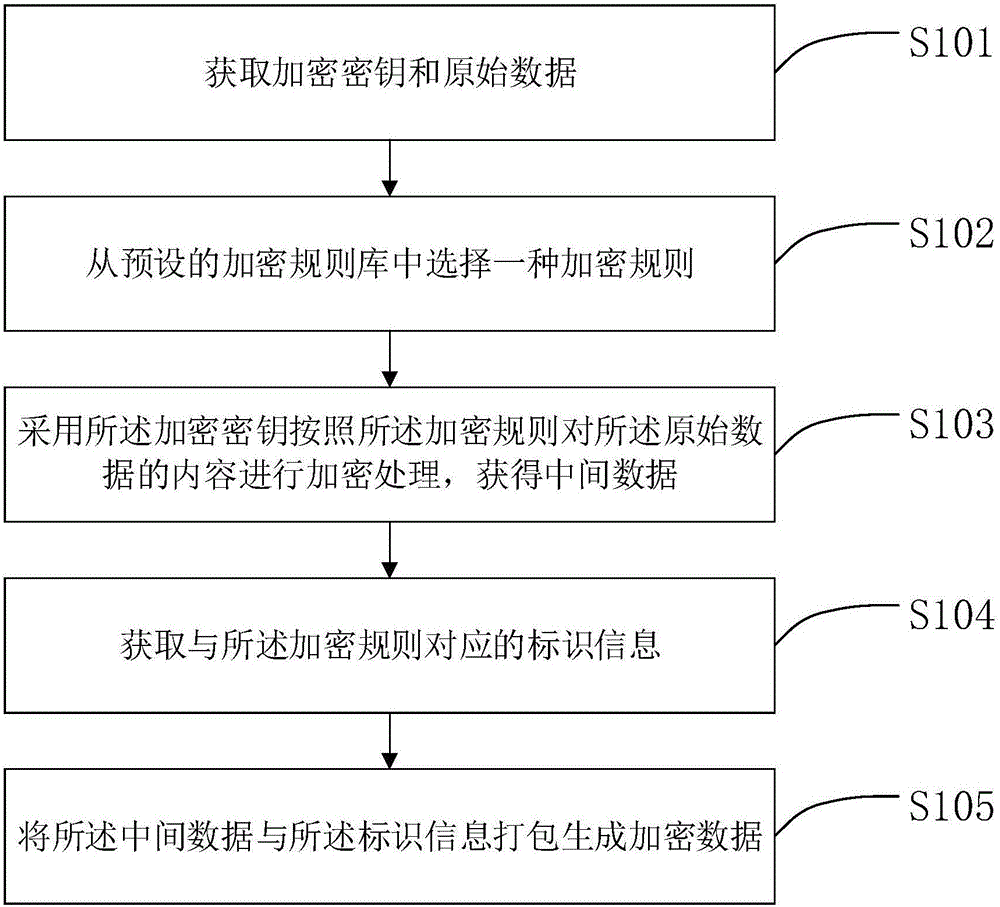
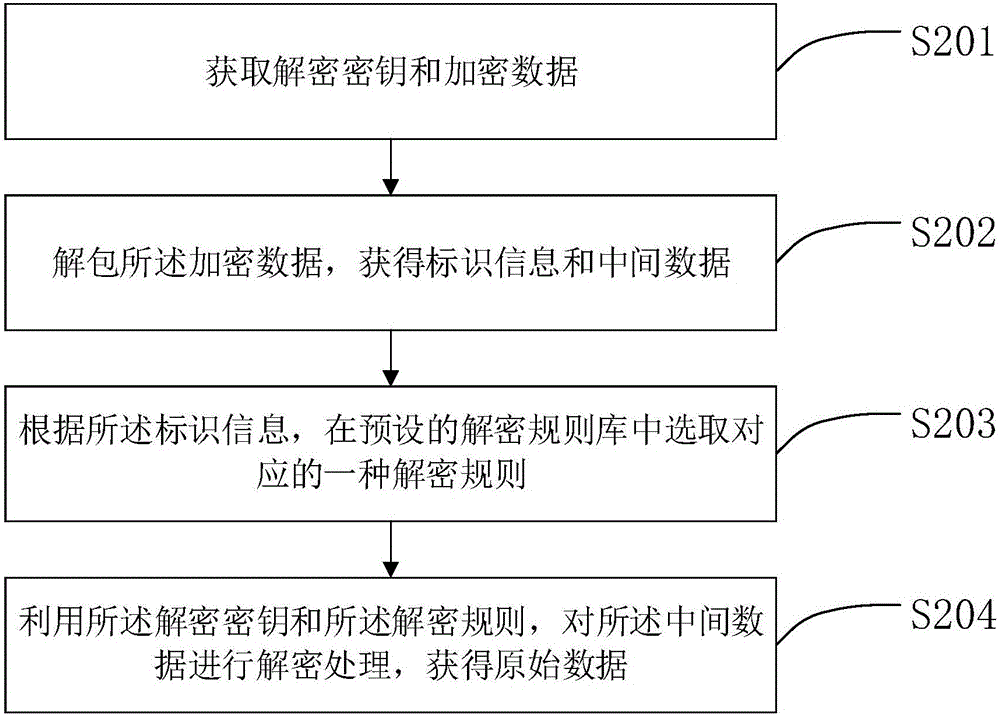
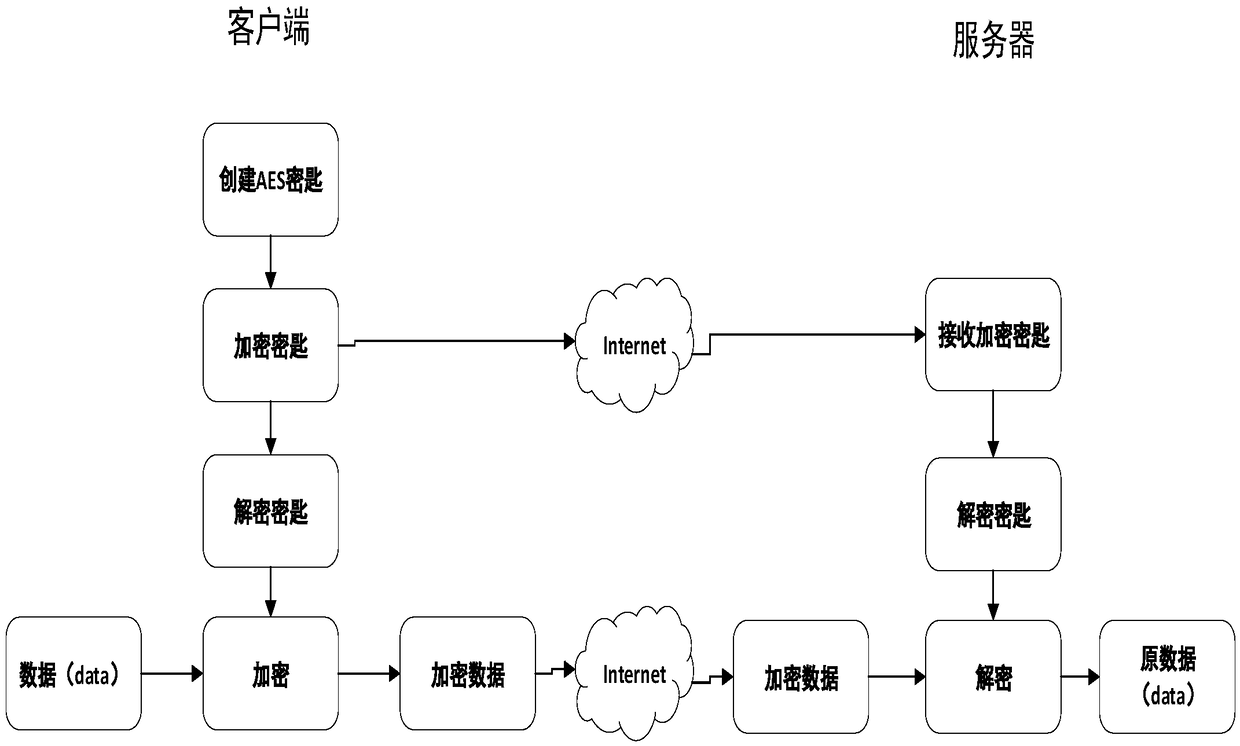
The invention relates to the field of data encrypting and decrypting, in particular to a data encrypting method and device and a data decrypting method and device.The data encrypting method comprises the steps that at first, an encryption key and original data are obtained; then, an encryption rule is selected from a preset encryption rule base; the encryption key is adopted for encrypting the original data according to the encryption rule to obtain intermediate data; then, identification information corresponding to the encryption rule is obtained; finally, the intermediate data and the identification information are packaged to generate encrypted data.Compared with the prior art, encryption information does not only depend on the carrier key, the encryption rule is selectively used, and the encryption rule is encrypted; meanwhile, in the file transmitting process, only the identification information of the encryption rule exists in the transmission information, and the specific content of the encryption rule does not exist, so that multi-dimensional encryption is achieved, the encryption means is more complex, the key can not be decrypted easily, and encryption safety is higher.
Owner:BEIJING SEEYON INTERNET SOFTWARE CORP
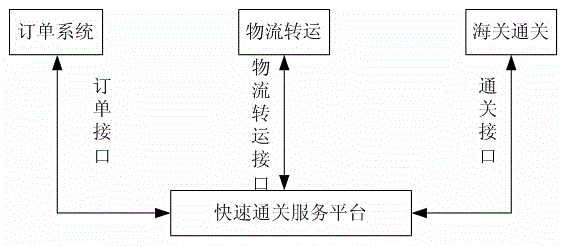
Fast customs clearance method
InactiveCN105046464AReduce investmentImprove customs clearance processing speedLogisticsLogistics managementE-commerce
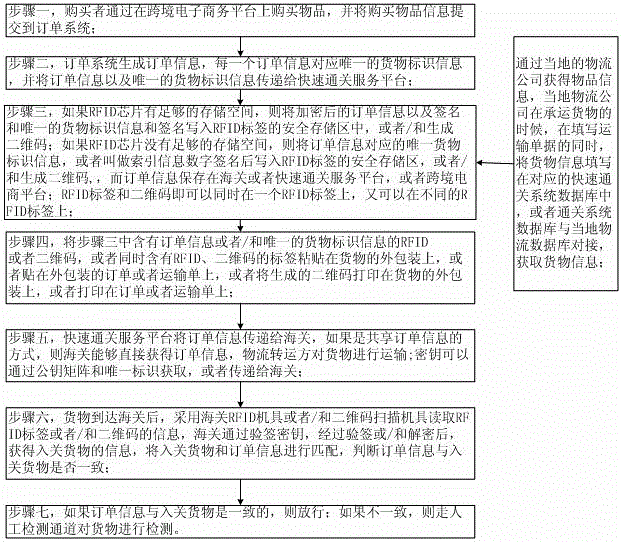
The invention belongs to the technical field of customs clearance and provides a fast customs clearance method. The method comprises that a buyer purchases a product at an international e-commerce platform and submits product information to an order system; the order system generates order information; the order system transmits the order information and / or product identification information to a fast customs clearance service platform in order to write order information and / or product identification information in a RFID tag or generates a two-dimension code; the RFID tag is pasted on the package and the transport sheet of the product or the generated two-dimension code is printed on the package of the product; the order information and a signature verifying secret key are transmitted to a customs in order to notify a logistic transferring company to transport the product; the customs reads the RFID tag or the two-dimension code, matches the product with the order information in order to determine whether the order information is consistent with the product after performing decryption and signature verification by using the signature verifying secret key; the customs passes the product if yes; and the product is processed in a manual detection channel if not. The fast customs clearance method has advantages of low cost, various identification forms, fast processing speed, traceable product source, safe information and convenient supervision.
Owner:上海象形通讯科技股份有限公司
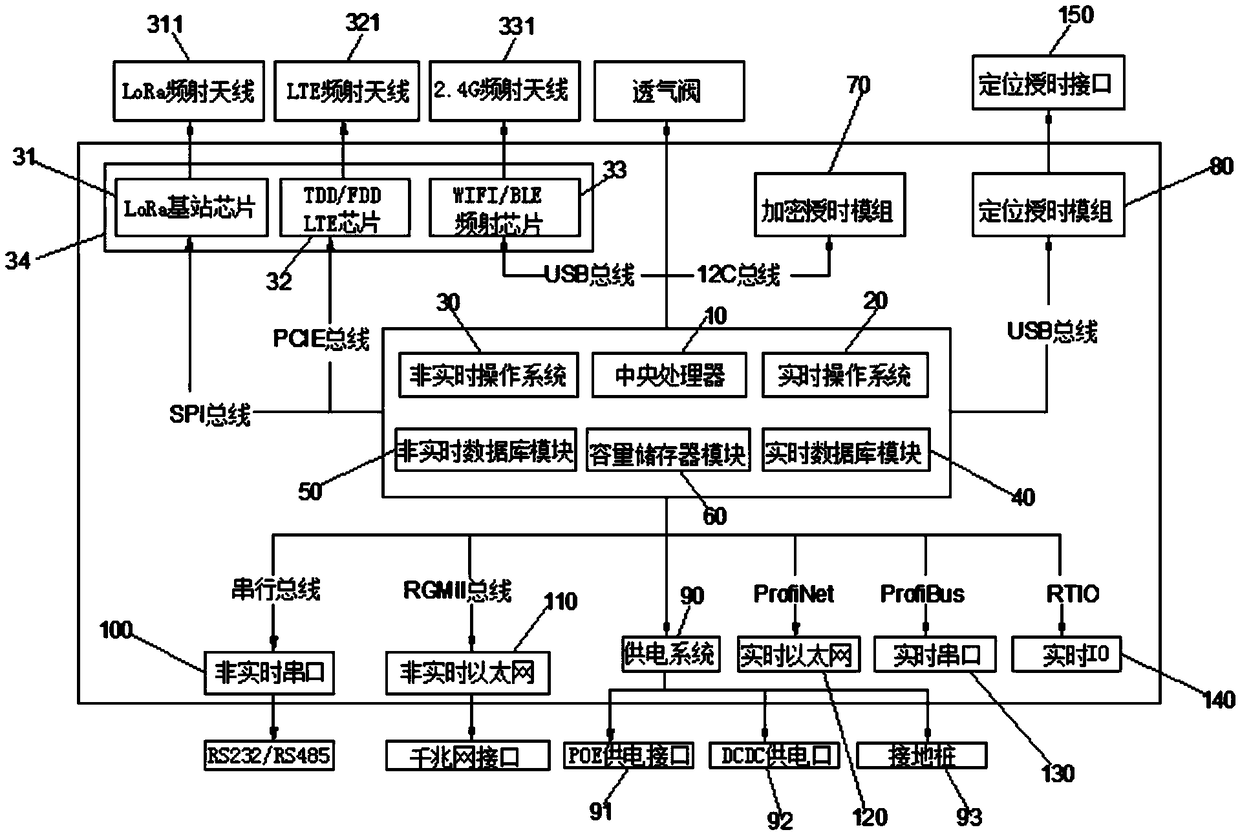
Multi-network fusion edge computing gateway
InactiveCN108768843AReal-time acquisitionRealize shared exchangeNetwork connectionsWireless communicationOperational systemThe Internet
The invention discloses a multi-network fusion edge computing gateway, which comprises a central processing unit, a real-time operating system, a non-real-time operating system, a real-time database module, a non-real-time database module and a capacity storage module. The multi-network fusion edge computing gateway in the invention has the following beneficial effects: an edge computing operatingsystem NECOS is operated in a gateway, which can realize real-time data collection and real-time control; the interior of the operating system is a service environment where a set of non-real-time operating systems and a set of real-time cores coexist; real-time and non-real-time tasks can be configured according to actual business needs; the non-real-time task and the real-time task can be dynamically adjusted according to the resource service condition of the gateway; a special data channel can be established between two environments to achieve the purpose of data share exchange; besides, various Internet-of-Things sensing requirements are collected and controlled in a multi-network fusion manner; rapid response, data optimization filtering, and sensitive data security encryption are realized with strong edge computing capability; and burden is reduced for the cloud, and intelligent upgrade of the Internet of Things is realized.
Owner:国讯芯微(苏州)科技有限公司
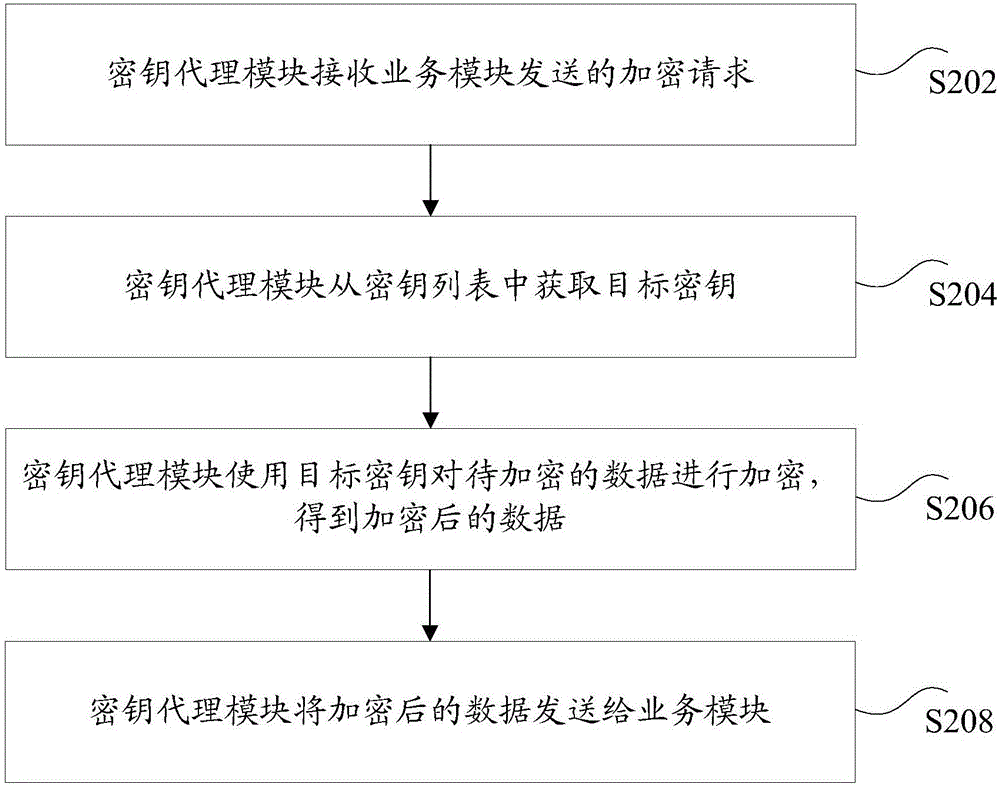
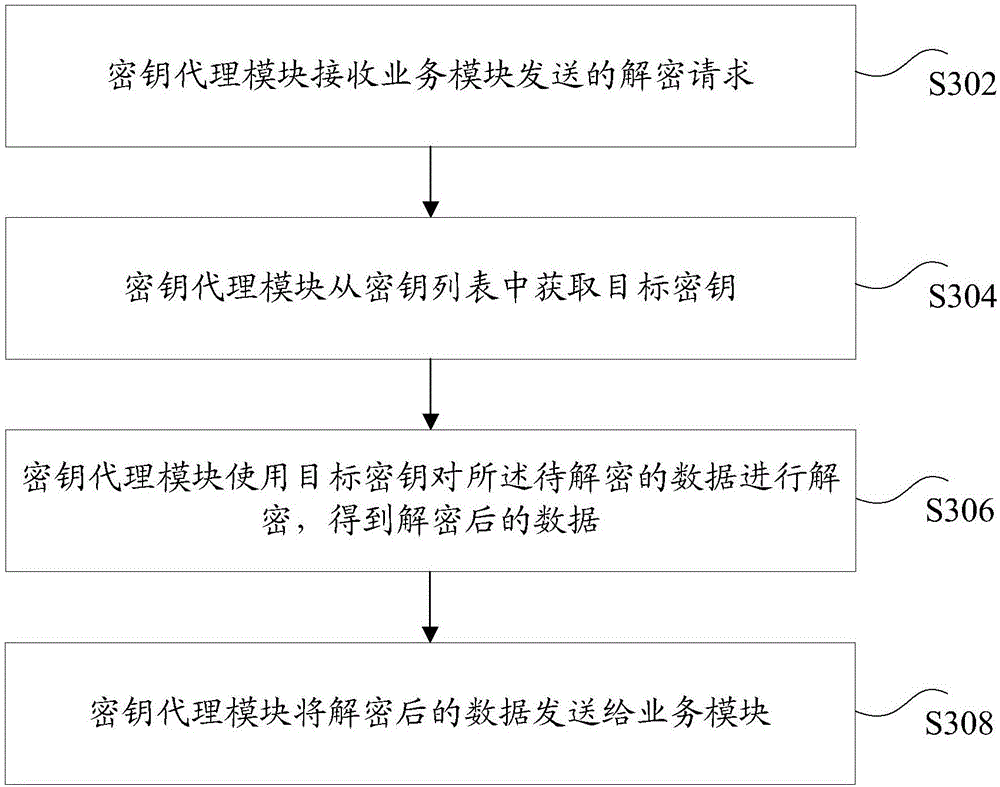
Business encryption/decryption method and device
The invention discloses a business encryption / decryption method and a device. The method comprises steps that an encryption request sent by a business module is received by a secret key agent module, and the encryption request contains the to-be-encrypted data; a target secret key is acquired from a secret key list by the secret key agent module, and the secret key list is acquired from a secret key server in advance; the to-be-encrypted data is encrypted by the secret key agent module through utilizing the target secret key to acquire the encrypted data; the encrypted data is sent by the secret key agent module to the business module. Through the method, a technical problem of relatively low security of secret keys during business encryption in the prior art is solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
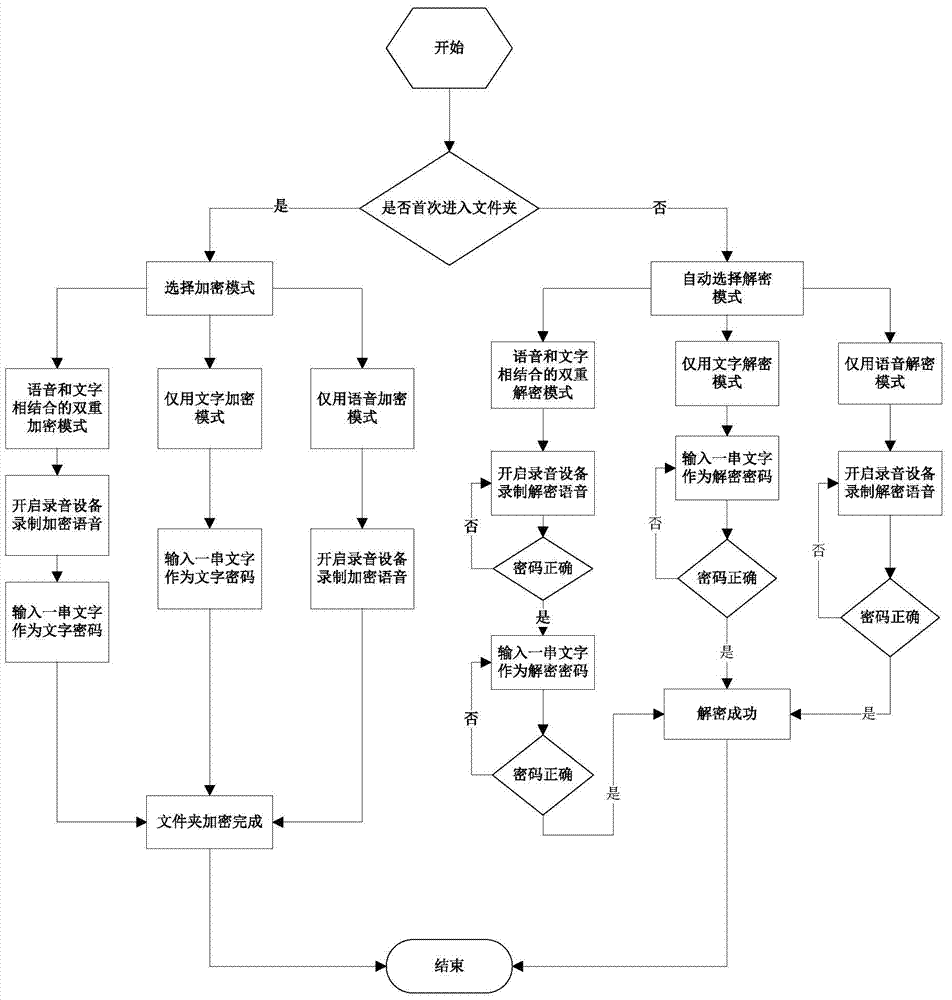
Folder encrypting method
InactiveCN104517066AImprove securityEasy to collectDigital data protectionDigital data authenticationComputer hardwarePassword
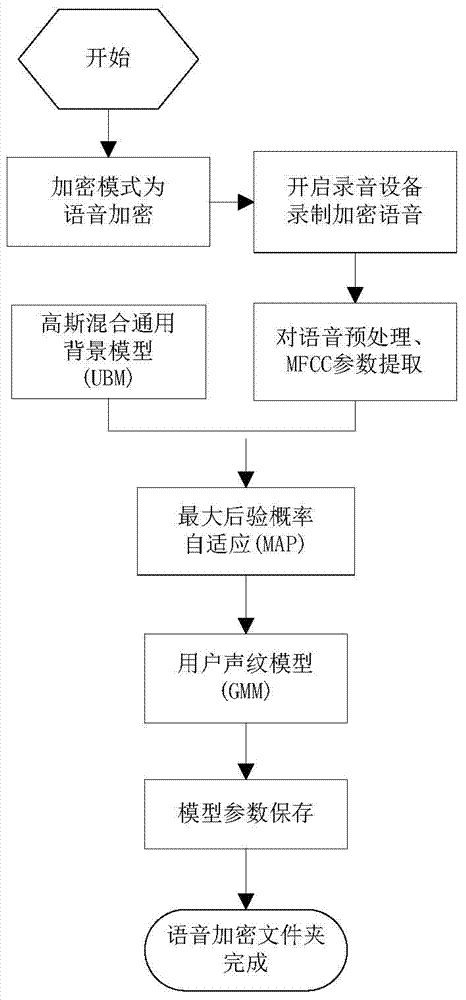
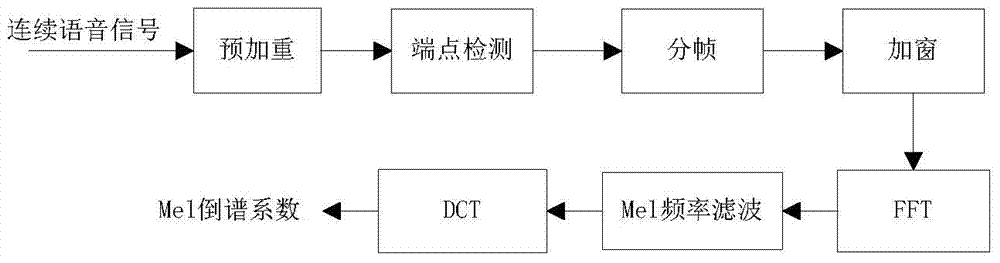
The invention provides a folder encrypting method, and specifically relates to a mode which combines the voiceprint encrypting technology and text passwords for authenticating the indentify of a folder user and confirming and distinguishing an accessor through the combination so as to ensure the security of information of the user folder, and relates to the technical field of information encrypting. The method involves a folder voice encrypting and decrypting module (1), a folder text encrypting and decrypting module (2), and a folder voice and text combined double-encrypting and decrypting module (3). The method is on the basis of the characteristics that voice signals are the natural properties of people, the voiceprint is unique and cannot be lost, and the voice is easily acquired, so that the safety and reliability are superior to the traditional digital or text encrypting mode; the user can flexibly and conveniently encrypt and decrypt; the mode method in combination of voiceprint encrypting and text encrypting, the text encrypting mode method and the voiceprint encrypting mode method are provided for selecting, so that the dual safety is provided to the folder encrypting, and meanwhile, the demand of the user on flexible encrypting modes is met.
Owner:SHANGHAI NORMAL UNIVERSITY
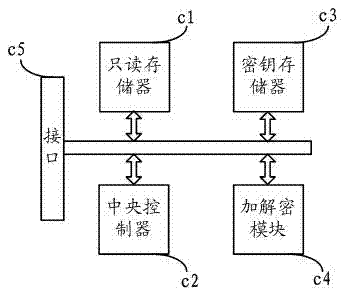
Hand-held equipment data encryption and decryption method and hand-held equipment peripheral equipment thereof
InactiveCN102332077APracticalAvoid the risk of being easily decryptedDigital data protectionSecurity arrangementComputer hardwareEngineering
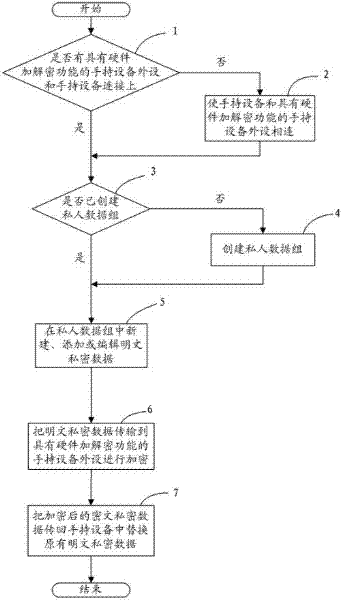
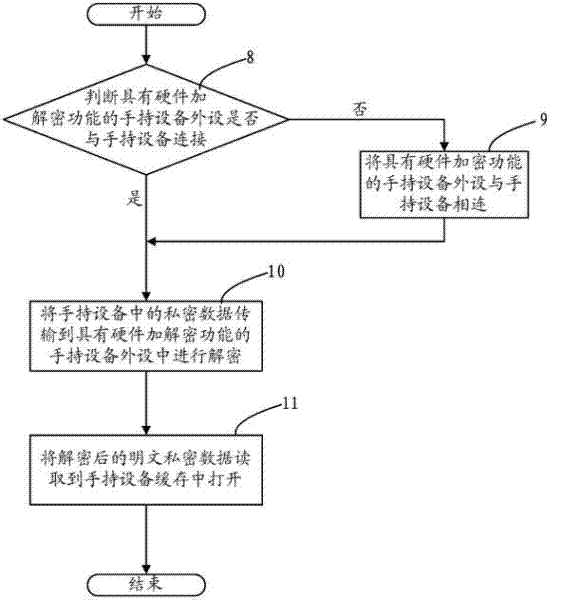
The invention relates to a hand-held equipment data encryption and decryption method and hand-held equipment peripheral equipment with encryption and decryption functions. In the hand-held equipment data encryption and decryption method, the hand-held equipment peripheral equipment with the encryption and decryption functions is used for encrypting and decrypting private data in the hand-held equipment, when the encryption and the decryption are completed, the hand-held equipment peripheral equipment with the encryption and decryption functions can be physically separated from the hand-held equipment, when the hand-held equipment is not connected with the hand-held equipment peripheral equipment with the encryption and decryption functions, the private data in the hand-held equipment can not be encrypted, and the encrypted data can not be decrypted, so the security of the encrypted data is ensured. A key used during the encryption and the decryption is stored in the hand-held equipment peripheral equipment with the encryption and decryption functions and is bound with the hand-held equipment peripheral equipment, and the security and the uniqueness of the encryption key are ensured.
Owner:NATIONZ TECH INC
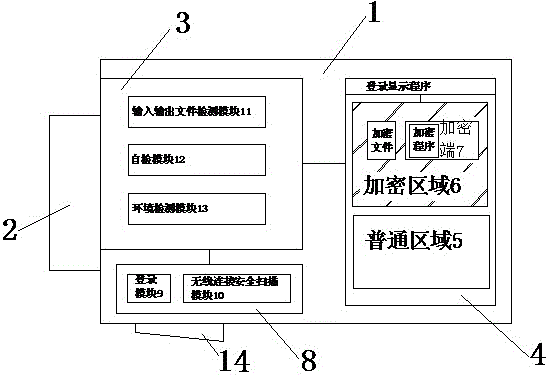
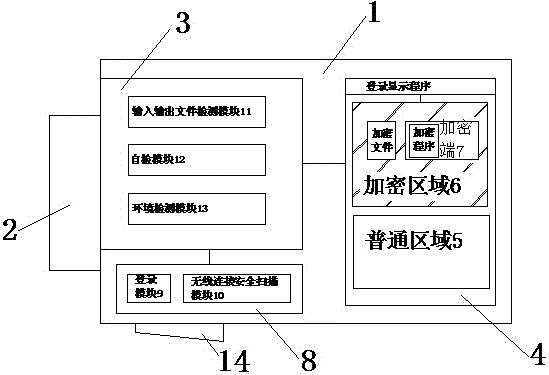
Safety encryption type USB flash disk
InactiveCN106250973AEasy to useEncrypted securityRecord carriers used with machinesUSBComputer science
The invention discloses a safety encryption type USB flash disk, which comprise a USB flash disk main body. A main interface is formed on one side of the USB flash disk main body. A control chip and a storage module are arranged inside the USB flash disk main body. The storage module is controlled by the control chip. A common area and an encryption area are arranged in the storage module. The encryption area is set in a hidden mode. A login display program is arranged in the encryption area. An encryption end is arranged on each encrypted file in the encryption area and an independent encryption program is arranged at the encryption end. According to the technical scheme of the safety encryption type USB flash disk, the common area and the encryption area are arranged in the storage module, and the encryption area is set in the hidden mode. After the USB flash disk is connected with a host, the USB flash disk can be displayed only after the login of a special administrator identity. Therefore, encrypted files in the encryption area are very safe. Moreover, each encrypted file in the encryption area is specially provided with one encryption end and one independent encryption program, thus being safer and not easy to be cracked.
Owner:WUHU ZHENHUA RONGKE INTELLIGENT TECH
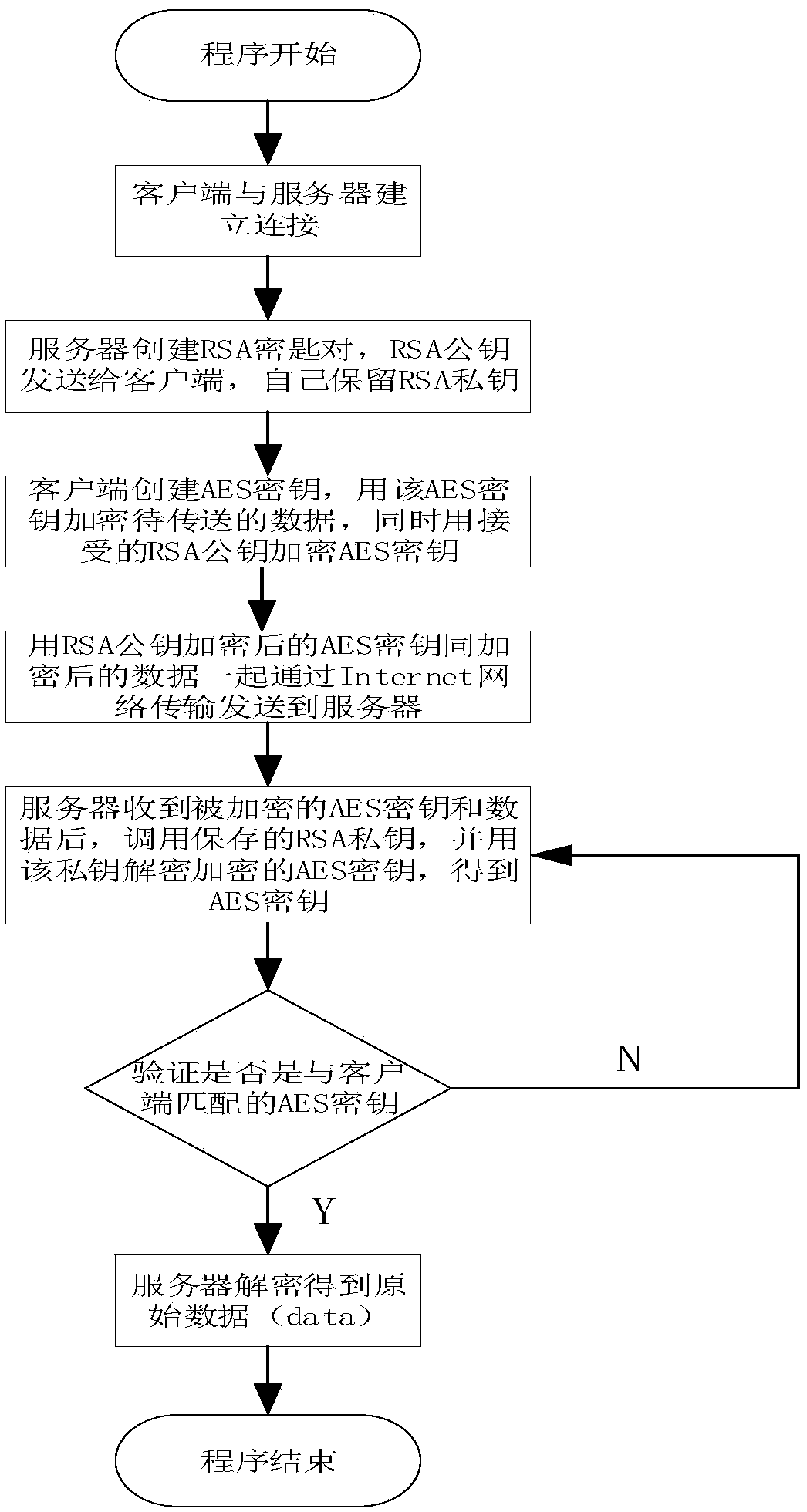
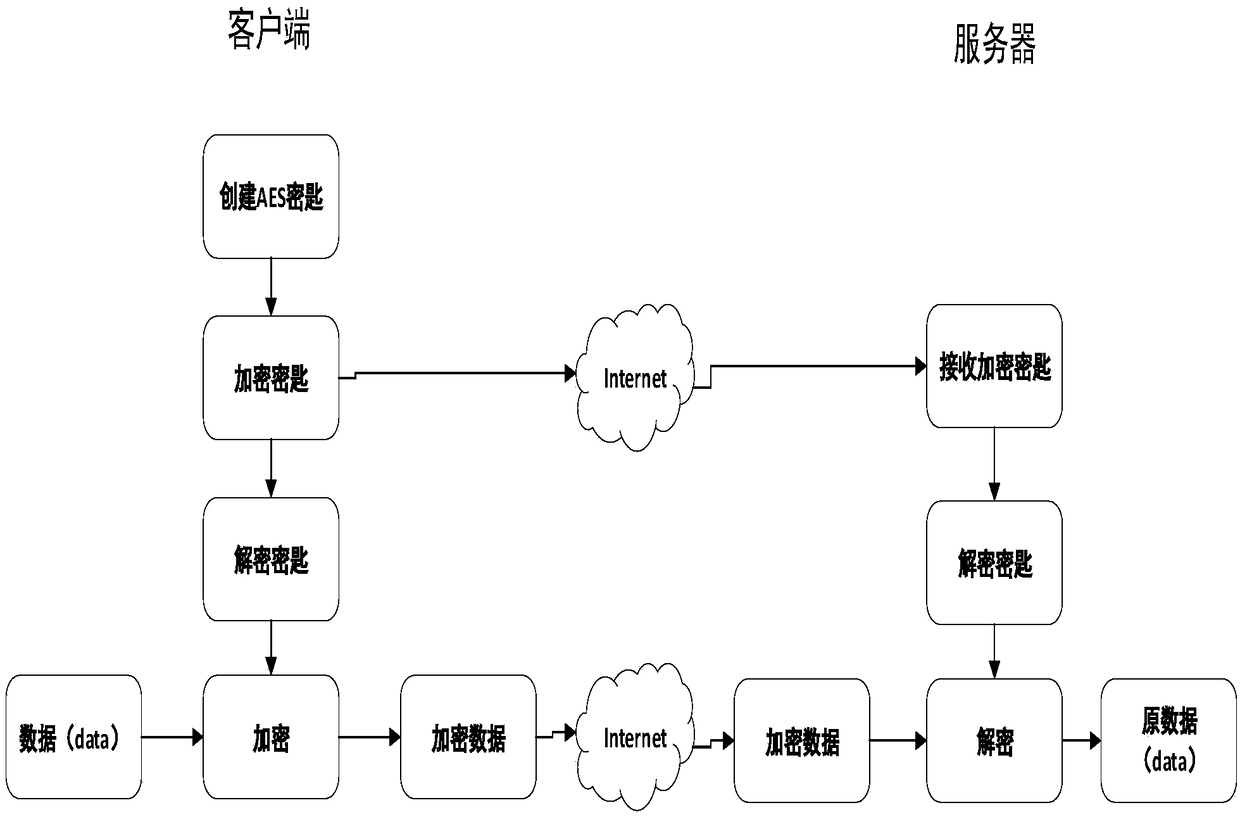
Efficient OPC UA client and server data transmission encryption method
InactiveCN109450615AEncrypted SecurityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesNetworked Transport of RTCM via Internet ProtocolClient-side
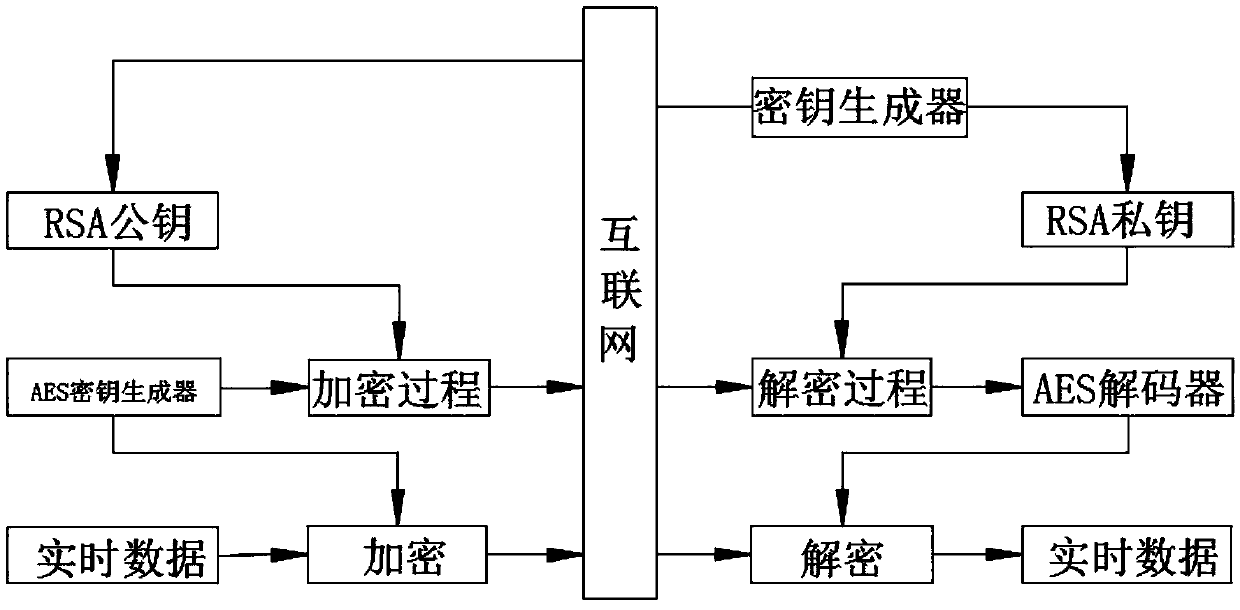
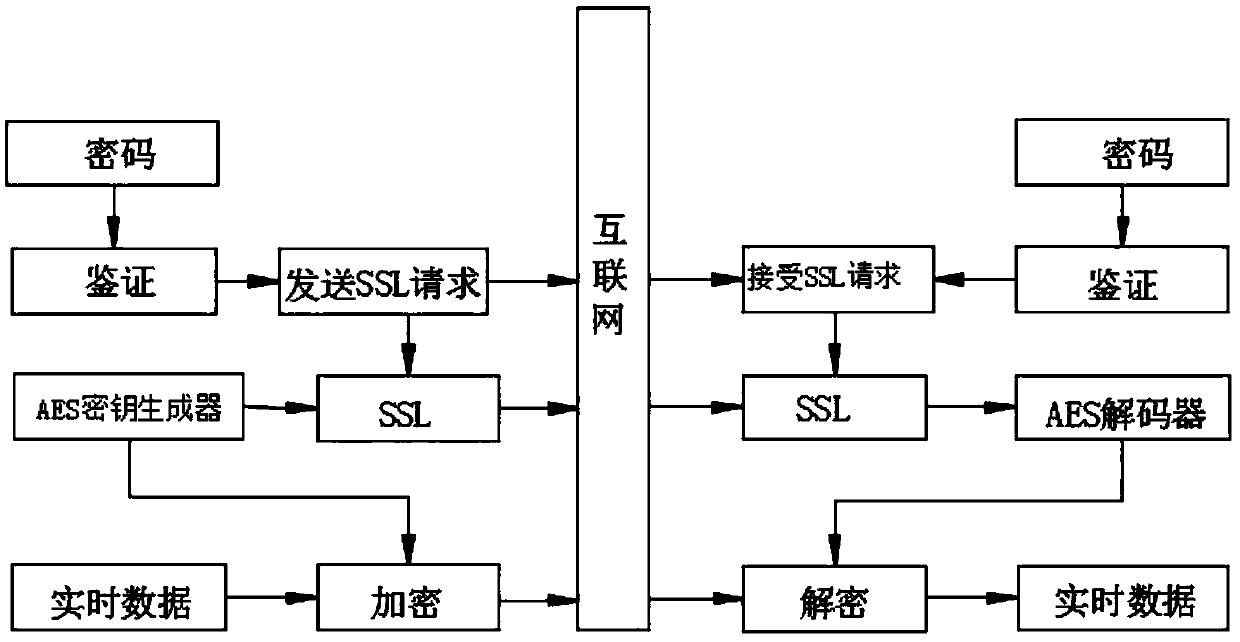
The invention discloses an efficient OPC UA client and server data transmission encryption method and relates to industrial data communication and information security. The method is mainly applied tosecure key information exchanging and data transmission between an OPC UA client and an OPC UA server. The characteristic that AES encryption speed is fast is utilized and secure management is carried out on an AES key through utilization of RSA in a network transmission process, so the whole key exchanging and data transmission timeliness and security between the OPC UA client and the OPC UA server are balanced. For industrial data communication, information security is very important.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Internet of Things system and quantum key distribution method and device thereof
InactiveCN111049645AImprove communication securityEncrypted securityKey distribution for secure communicationInstrumentsInternet of ThingsEngineering
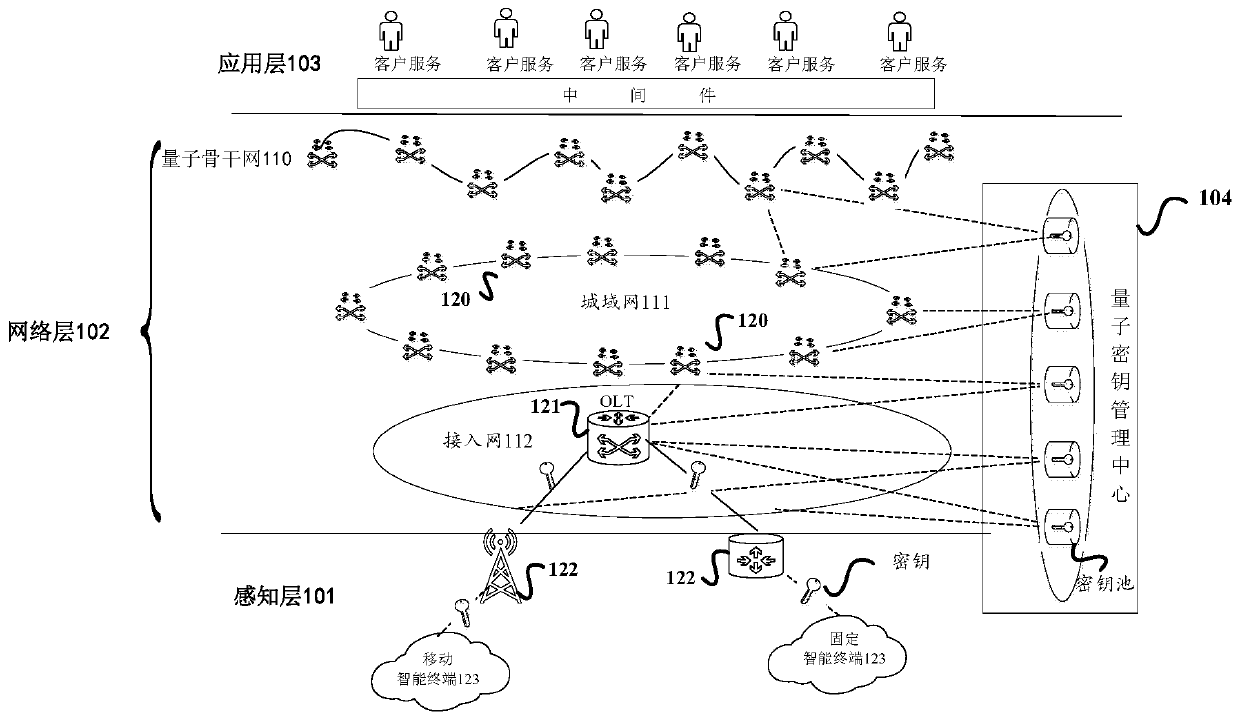
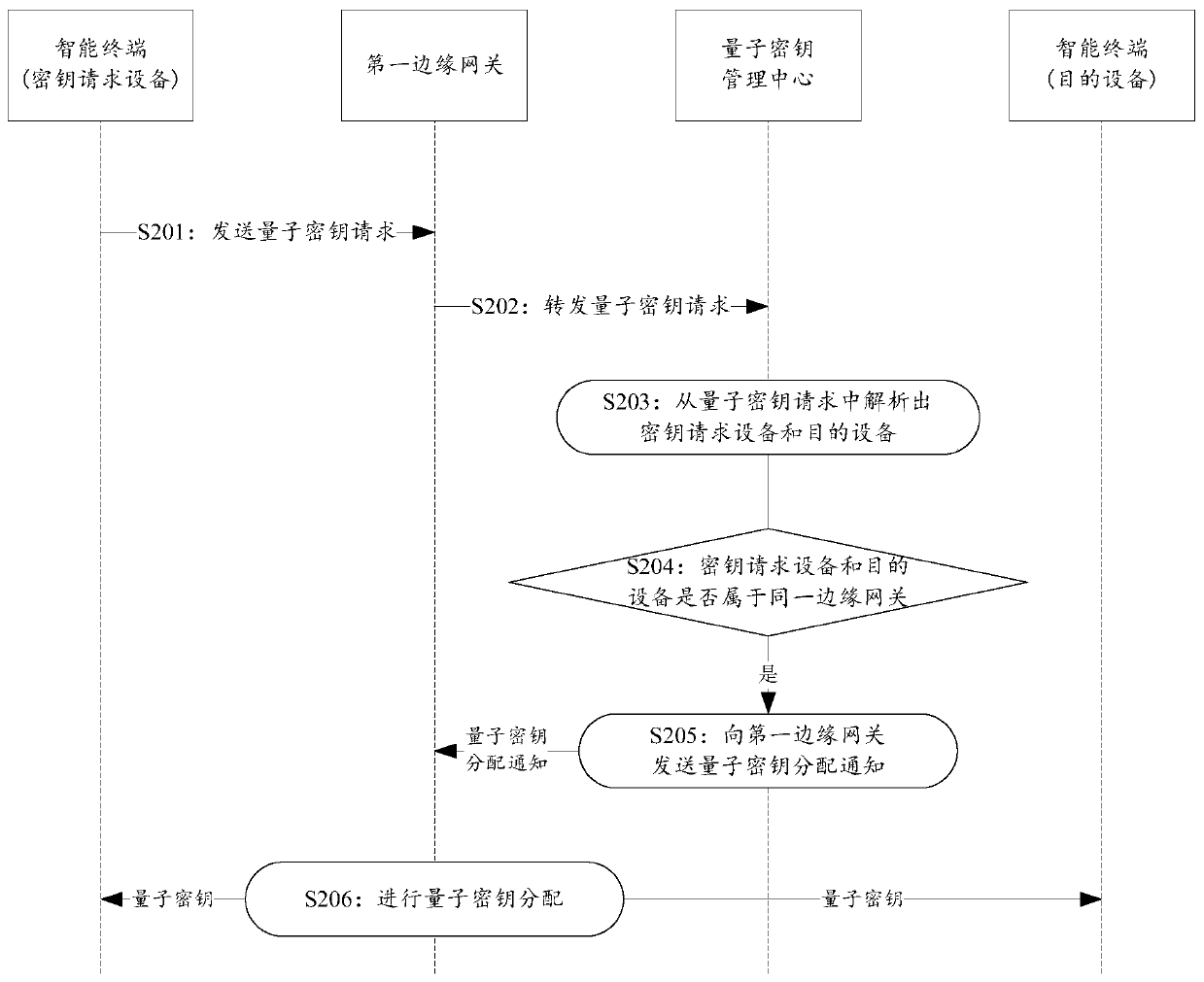
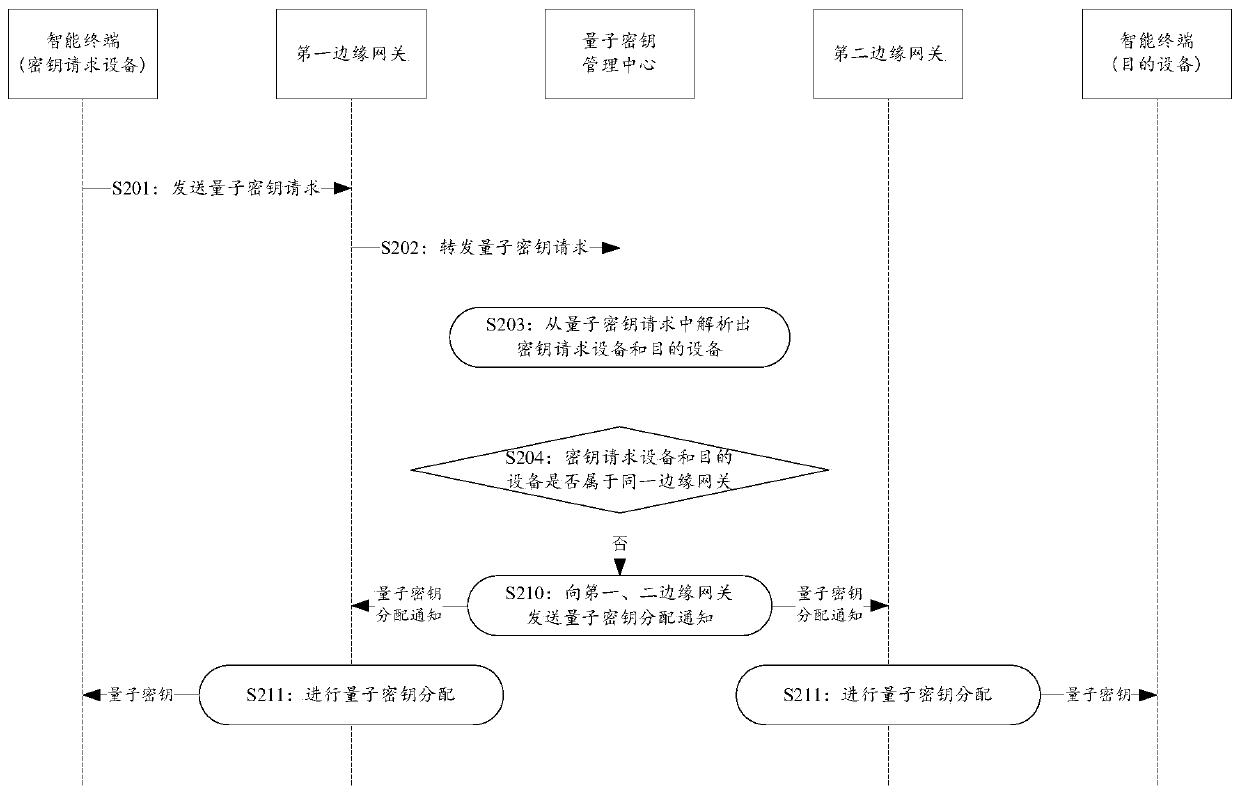
The invention provides an Internet of Things system and a quantum key distribution method and device thereof. The Internet of Things system comprises an application layer, a sensing layer, a network layer and a quantum key management center, wherein the quantum key management center is used for analyzing a key request device and a target device from a quantum key request forwarded by an edge gateway of a sensing layer, and then judging whether the key request device and the target device belong to the same edge gateway or not; if so, indicating the edge gateway to allocate quantum keys in a key pool to the key request device and the destination device; otherwise, indicating the two edge gateways to which the key request device and the destination device belong respectively to distribute the quantum keys in the key pool to the key request device and the destination device respectively. According to the invention, the quantum key can be allocated to the equipment in the Internet of Things system, and the communication safety in the Internet of Things system is improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
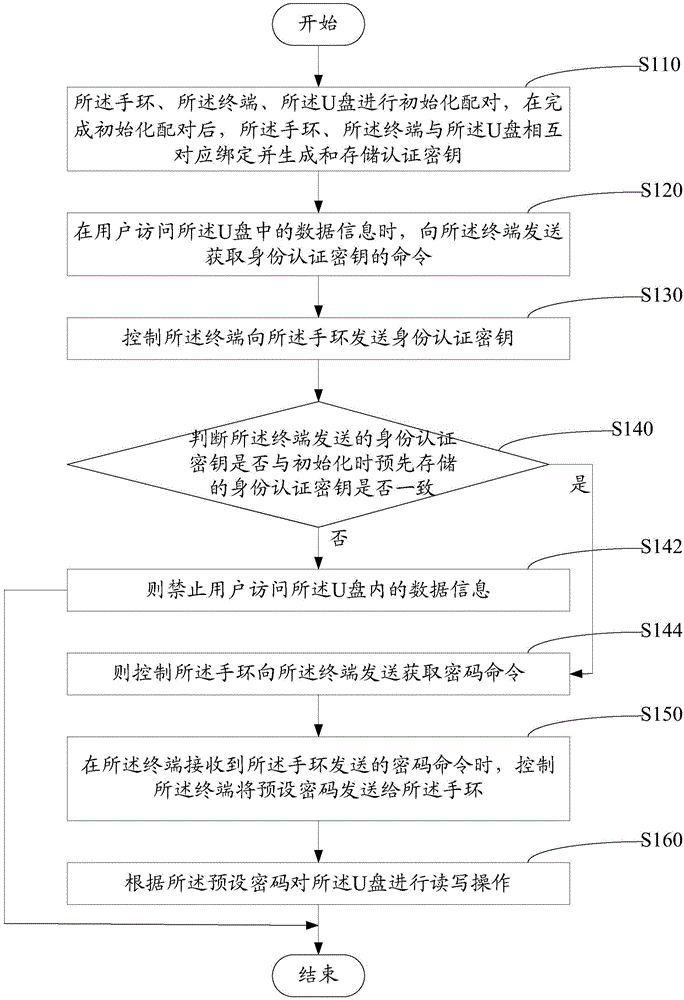
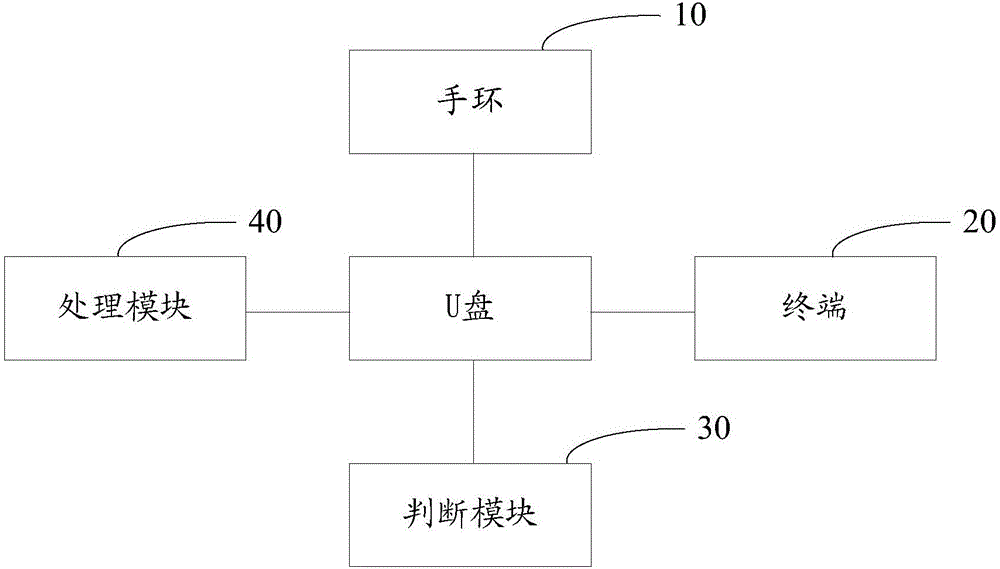
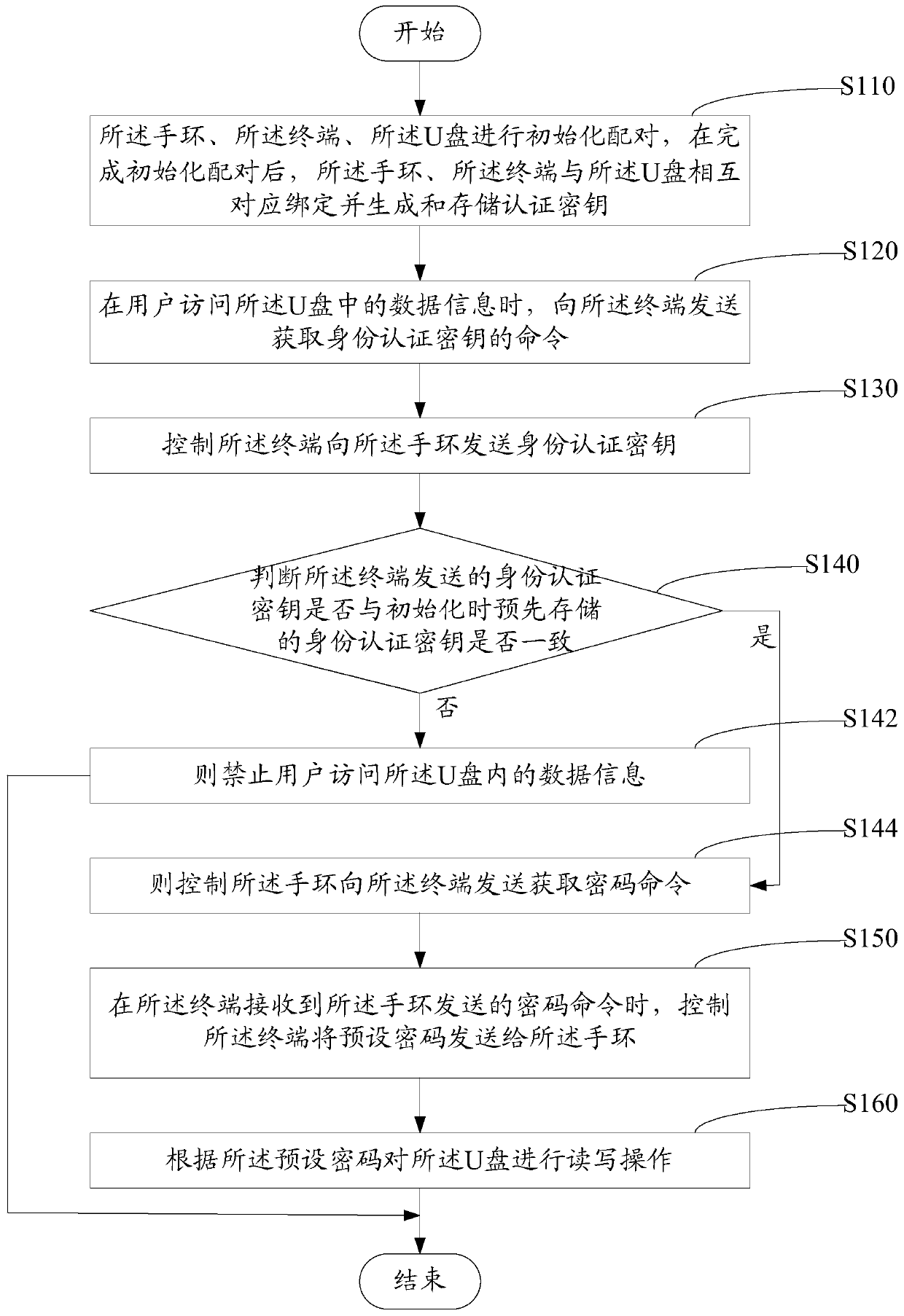
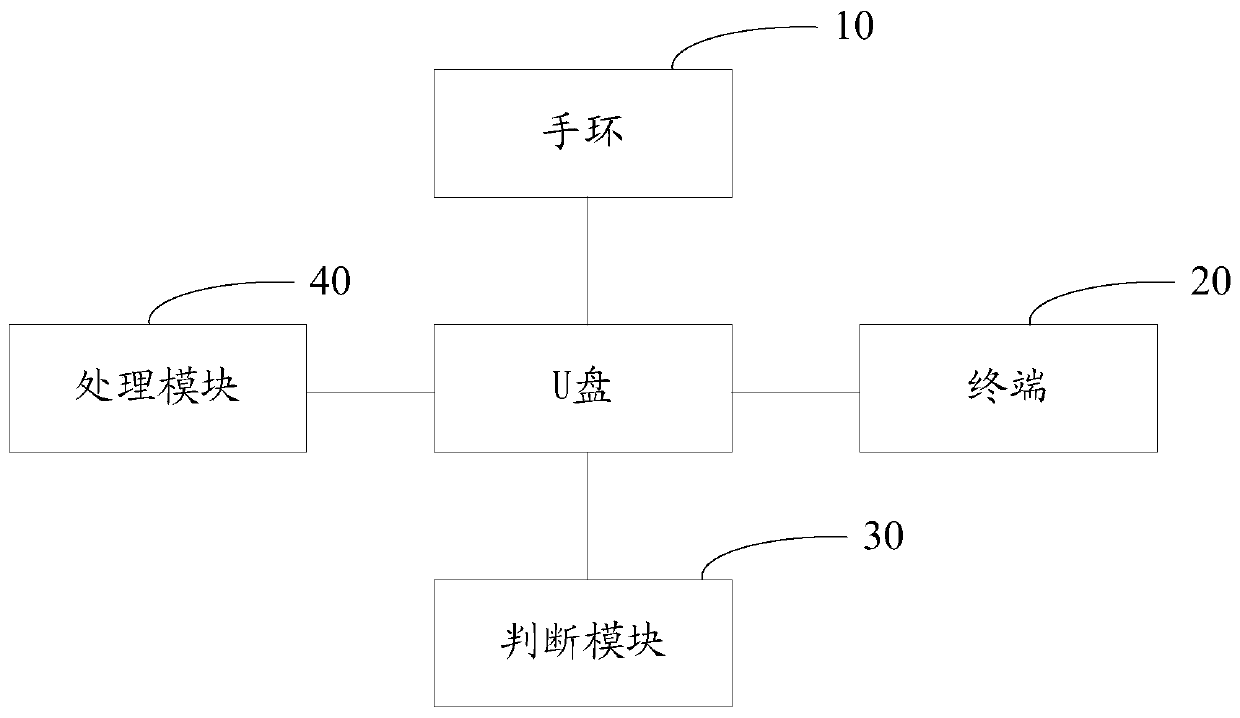
Bracelet and terminal-based U disk encryption method and system
ActiveCN106407825AEncrypted securityUser identity/authority verificationConnection managementDisk encryptionData information
The invention relates to a bracelet and terminal-based U disk encryption method and system. A bracelet, a terminal and a U disk are initially matched and are mutually bound correspondingly and an authentication key is generated and stored. When data information in the U disk needs to be accessed, a command of obtaining an identity authentication key needs to be transmitted to the terminal; the identity authentication key is compared with the identity authentication key during initialization after being transmitted by the terminal; if the identity authentication keys are consistent, the bracelet is controlled to transmit a password obtaining command to the terminal; and the terminal transmits a preset password to the bracelet, so that read-write operation can be carried out on the U disk. That is to say, the identity authentication key of the terminal needs to be compared with that of the U disk, the preset password can be can be transmitted to the bracelet after correct comparison, and then a user completes the read-write operation according to the preset password. By adopting bidirectional authentication, encryption of the U disk is safer and more reliable through authentication for multiple times.
Owner:深圳市魔样科技有限公司
Encryption/decryption method
InactiveCN109104278ASmall delay time differenceEncrypted securityMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesPlaintextCiphertext
The invention discloses an encryption and decryption method, comprising the following steps: selecting plaintext to be encrypted, reading plaintext data through a processor, and reading binary digitaldata in the plaintext by the processor; the AES algorithm is used to encrypt the plaintext data, the plaintext to be encrypted is encrypted by the AES key generator, the AES cipher is an iterative, symmetric key block cipher that can use a 256-bit key and encrypts and decrypts data using a 128-bit block to obtain encrypted plaintext and AES ciphers, adding at least one set of interfering data infront of and behind the plaintext data, and then decrypting the encrypted data. The invention relates to an encryption and decryption method, compared with RSA and AES, the hybrid algorithm of AES andRSA has significant advantages in encryption security, low latency and ciphertext synchronization. The hybrid algorithm of AES and SSL has the smallest delay time difference, and its advantages in encryption security, low latency and effective access authentication are obvious, which brings a better application prospect.
Owner:深圳市琦志航智能科技有限公司
Multipath Bluetooth signal adaptation device
InactiveCN105790803AGuaranteed accuracyReduce resource consumptionNear-field systems using receiversWireless commuication servicesResource consumptionData signal
The invention discloses a multipath Bluetooth signal adaptation device, which comprises a Bluetooth transceiving combined module and an external Bluetooth sensing module, wherein the Bluetooth transceiving combined module is matched with the external Bluetooth sensing module; the Bluetooth transceiving combined module is internally provided with a state indicating lamp system, a Bluetooth signal integration encoding system, a USB signal output interface and a power supply connection interface; and the Bluetooth signal integration encoding system is connected with the USB signal output interface. The multipath Bluetooth signal adaptation device can be used for connecting 15 sets of Bluetooth equipment, solves the problems that the traditional Bluetooth equipment can only in one-to-one connection, the transmission distance is short, the equipment are not compatible and the like; and the 15 sets of Bluetooth equipment are subjected to unified coding, the transmission efficiency of data signals is increased, the structure is compact, the resource consumption of the device is low, the power consumption is low, the cost is low, and the operation is stable and reliable.
Owner:ZHEJIANG SCI-TECH UNIV
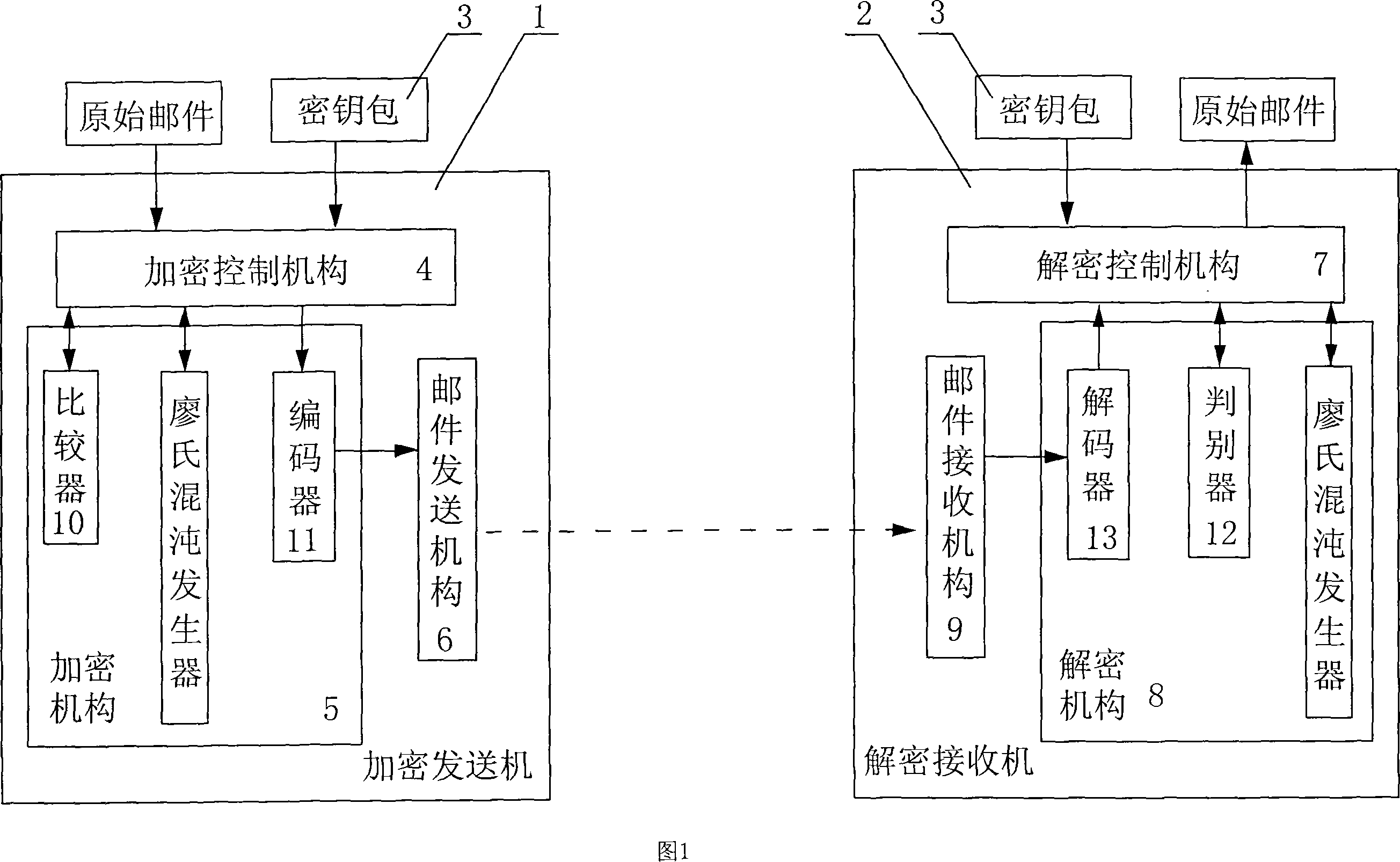
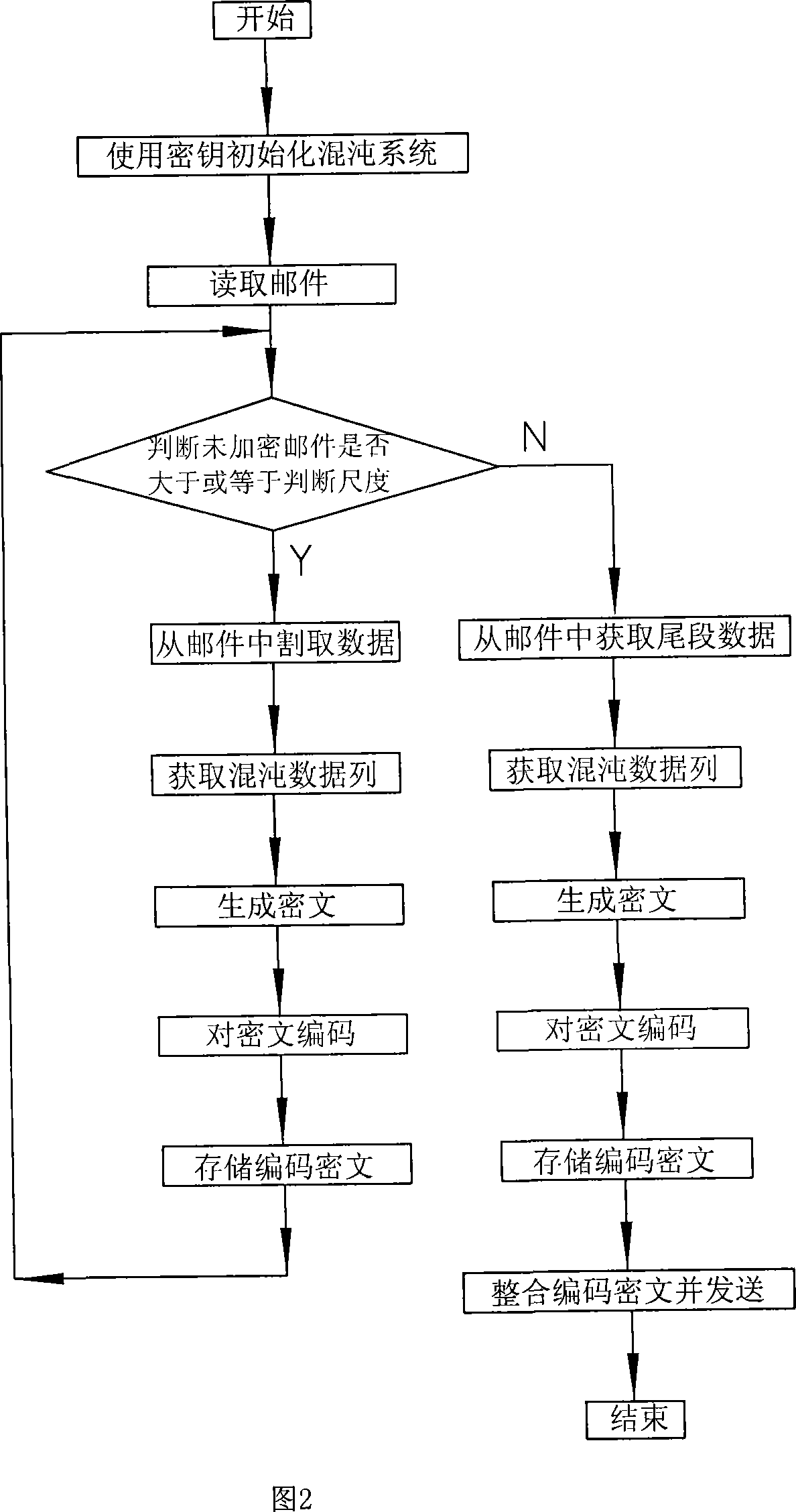
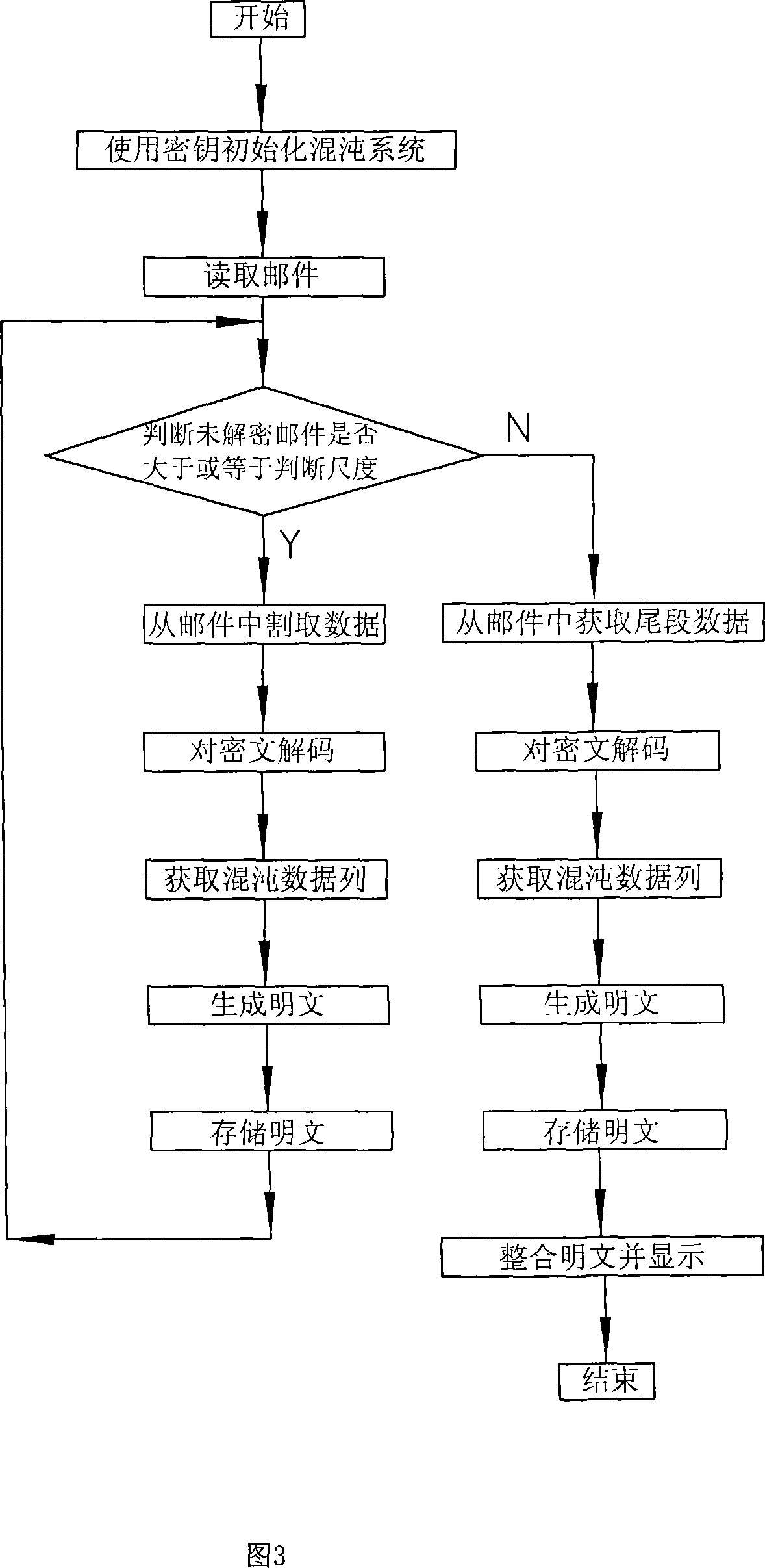
E-mail encryption transmitting-receiving system
InactiveCN101159546ASimple structureFast encryptionData switching networksSecuring communicationEmail encryptionElectronic mail
An E-mail encryption / reception / transmission system is provided, which comprises an encryption transmitter, a decryption receiver and a key packet. The system is characterized in that the encryption transmitter and the decryption receiver are equipped with Liao's chaos generators which produce required chaotic sequence data. An encryption controller calculates and encrypts E-mail information by using the chaotic sequence data to produce encrypted data, and sends an encrypted E-mail. The decryption receiver calculates and decrypts the E-mail information by using the chaotic sequence data to produce a primary file. The invention has the advantages that the Liao's chaos generators are excellent in the data encryption; the system is simple, rapid and safe to operate, and the E-mail can be encrypted, decrypted and transmitted safely and quickly.
Owner:CHONGQING UNIV
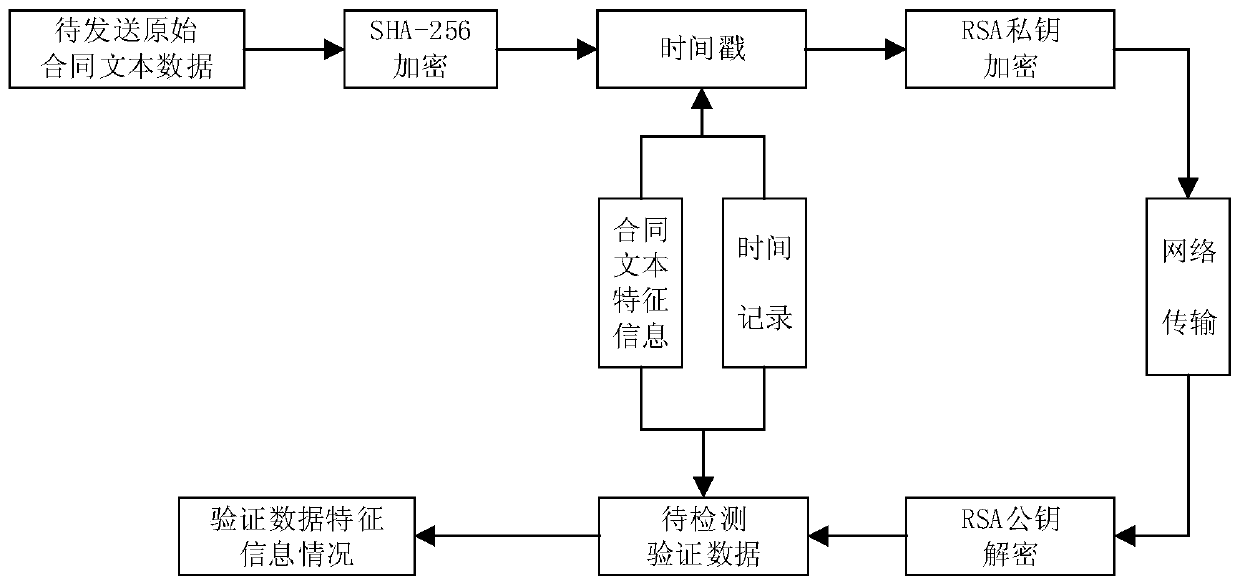
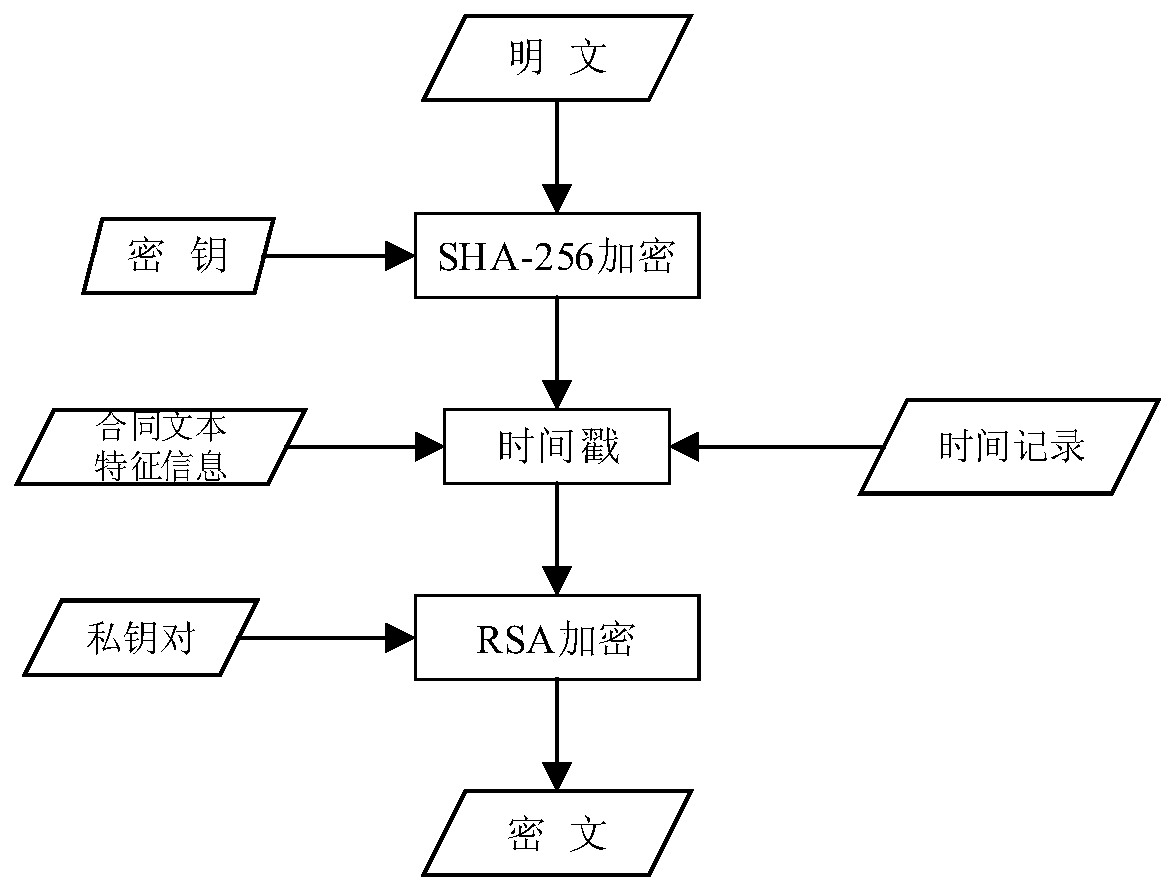
Contract text protection method based on RSA encryption sha-256 digital signature
InactiveCN110955918AEncrypted securityImplement tamper detectionDigital data protectionSignature fileTimestamp
The invention discloses a contract text protection method based on RSA encrypted sha-256 digital signature. The method comprises the following steps: 1) obtaining to-be-sent contract text original data; 2) encrypting the original contract text data by using a sha-256 algorithm to generate a signature file; 3) adding a timestamp to the signature file which is encrypted for the first time, and performing encrypting again in combination with the RSA private key of the sender to generate a digital signature; 4) storing the generated digital signature in a data head for network transmission; 5) performing decrypting by using the RSA public key of the sender, acquiring data by the receiver, performing user identity authentication in combination with a timestamp, and obtaining a sha-256 digital signature abstract; 6) carrying out sha-256 signature on the original contract text to calculate an abstract; (7) comparing and verifying whether the calculated abstract is consistent with a decryptedsignature abstract or not, and (8) reading original contract text data. The method improves the system security and prevents harm caused by malicious data tampering.
Owner:ZHEJIANG UNIV OF TECH
U disk security encryption management method
InactiveCN106372541AEasy to useAvoid wastingDigital data protectionInternal/peripheral component protectionComputer hardwareEncryption
The invention discloses a U disk security encryption management method. The method comprises the following steps of 1) establishing a connection; 2) performing login; 3) performing general region operation; 4) performing encrypted region operation; 5) performing transmission file security management; 6) performing storage file security management; and 7) performing hardware environment security management. According to the U disk security encryption management method, a general region is arranged in a U disk, so that the U disk is used as a general U disk; an encrypted region is arranged in the U disk, so that the U disk is used as an encrypted U disk; the encrypted region is hidden when not in use; when the encrypted region needs to be used, the login is performed as an administrator through a login display program set in the encrypted region, so that files of the encrypted region can be displayed; each encrypted file is provided with an encryption end and an independent encryption program, so that the encrypted files are very secure and difficult to decrypt; and the usage efficiency of the U disk is fully improved.
Owner:WUHU ZHENHUA RONGKE INTELLIGENT TECH
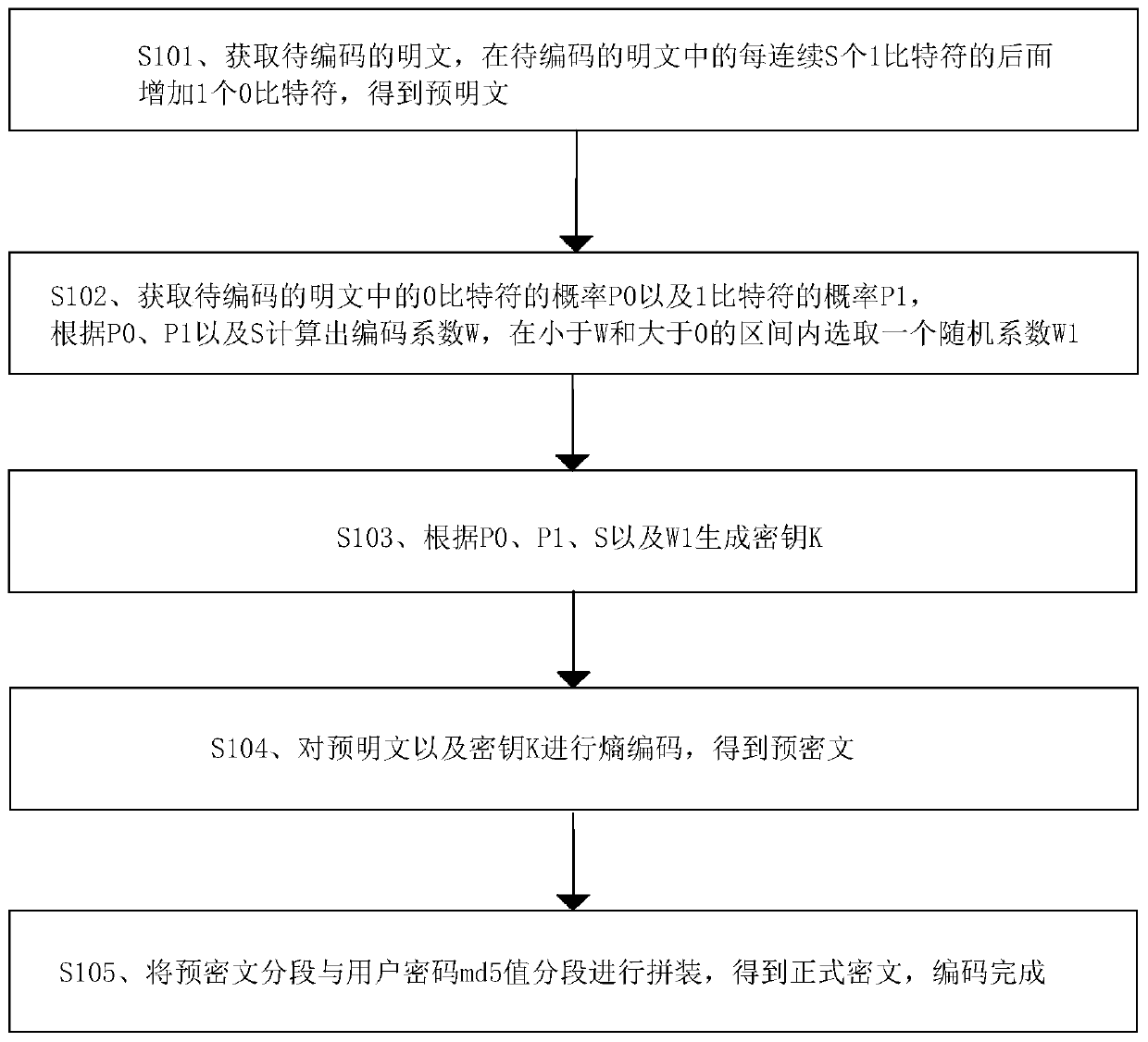
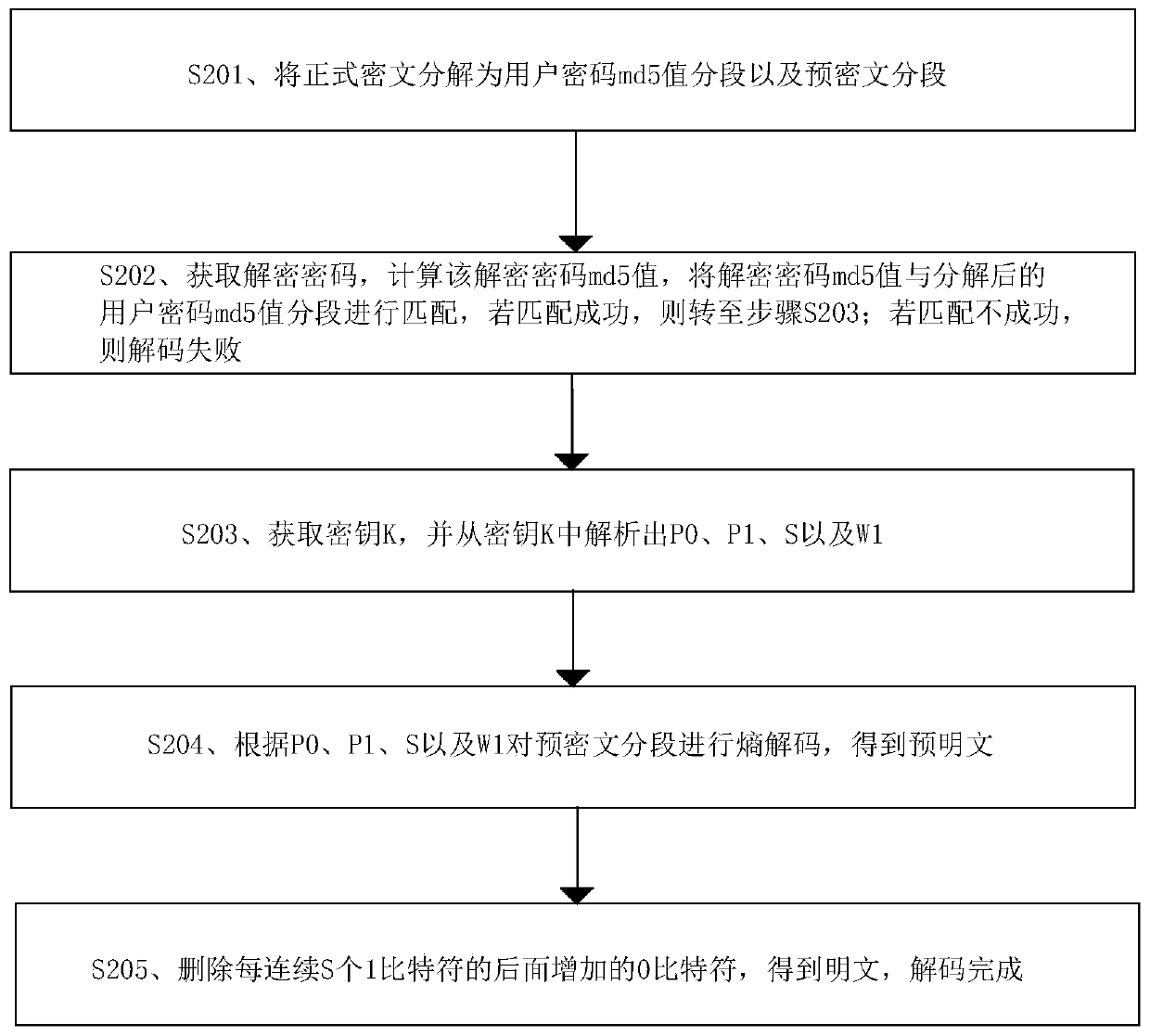
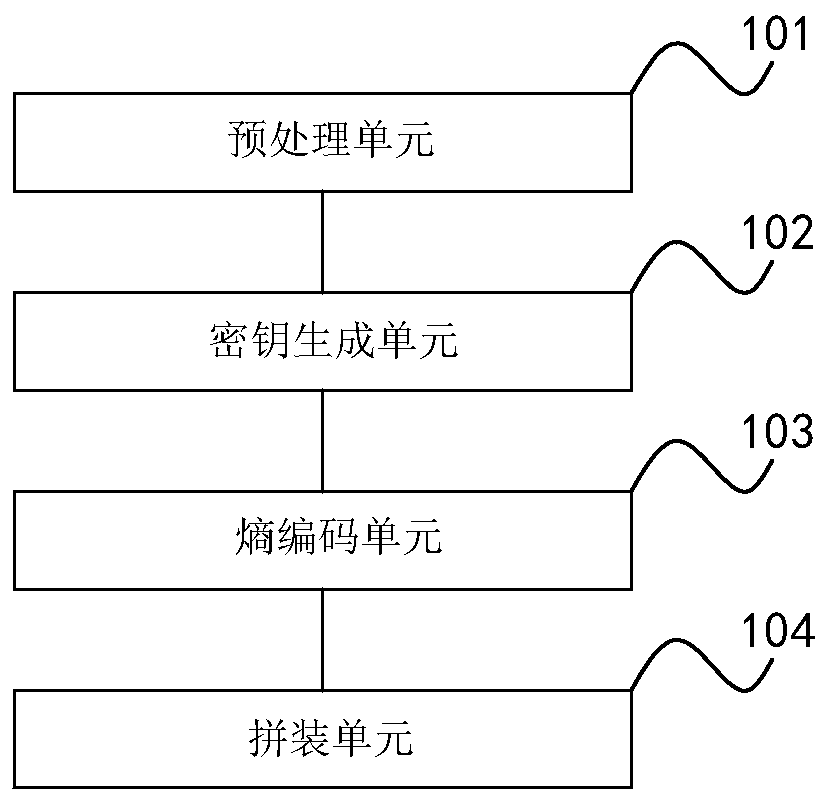
Data encoding and decoding method, device, equipment and storage medium
ActiveCN110474876AImprove securityCapable of compressingKey distribution for secure communicationPlaintextPassword
The invention discloses a data encoding and decoding method, a device, equipment and a storage medium. The data encoding method comprises the following steps: firstly, preprocessing a plaintext to beencoded, secondly, generating a key according to pseudo-random parameters in the plaintext to be encoded, then, carrying out entropy encoding encryption, and finally, splicing user passwords to generate a formal ciphertext. The data decoding method comprises the following steps: decomposing a formal ciphertext into a user password segment and a pre-ciphertext segment, and firstly decoding the userpassword segment; secondly, obtaining a secret key, analyzing pseudo-random parameters, performing entropy decoding on the pre-ciphertext segments through the pseudo-random parameters to obtain a pre-plaintext, and finally restoring the pre-plaintext into a plaintext. According to the data encoding and decoding method provided by the invention, the security and the application range of the formalciphertext are improved, and the formal ciphertext has the compression capability while the security of the formal ciphertext is improved.
Owner:HUNAN YAOSHENG COMM TECH CO LTD
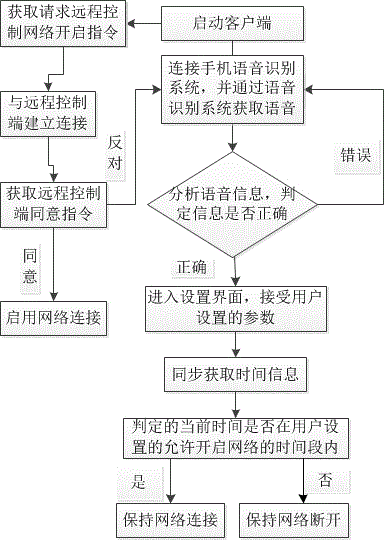
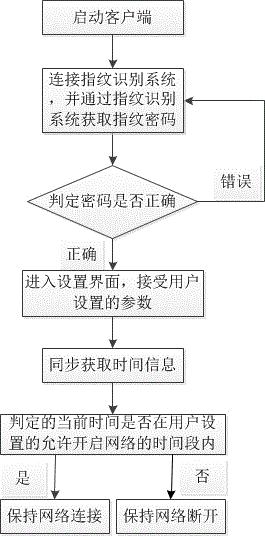
Mobile phone network remote control method based on voice recognition
InactiveCN104994162AWill not affect learningSolve the problem of connecting to the network in special casesTransmissionRemote controlNetwork connection
The invention relates to a mobile phone network remote control method based on voice recognition. The method comprises the following steps: starting a client; judging the situation; connecting a mobile phone voice recognition system under a conventional situation, and acquiring voice through the voice recognition system; analyzing voice information to judge whether or not the information is correct; if the information is judged to be wrong, returning a login interface for acquiring voice once again; if the information is judged to be correct, entering a setting interface, and accepting parameters set by a user; synchronously acquiring current time information and making a judgment; if the judged current time is within a time interval in which a network is allowed to be enabled set by the user, keeping network connection; if the judged current time is outside the time interval in which the network is allowed to be enabled set by the user, keeping network disconnection; and if the situation is a special situation, requesting remote permission. The mobile phone network remote control method has the beneficial effectives that parents can set the time interval in which the network of a mobile phone is allowed to be enabled, and network control is performed, so that the call function of the mobile phone is not influenced, and learning of children is not influenced. The influences of games and undesirable Internet information on juveniles are effectively prevented.
Owner:成都亿邻通科技有限公司
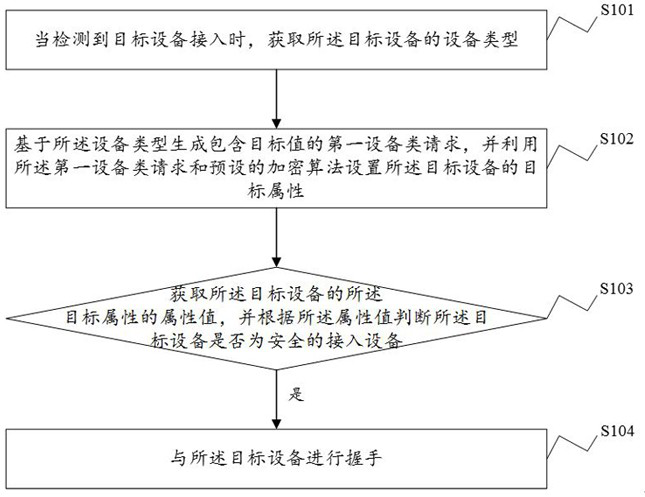
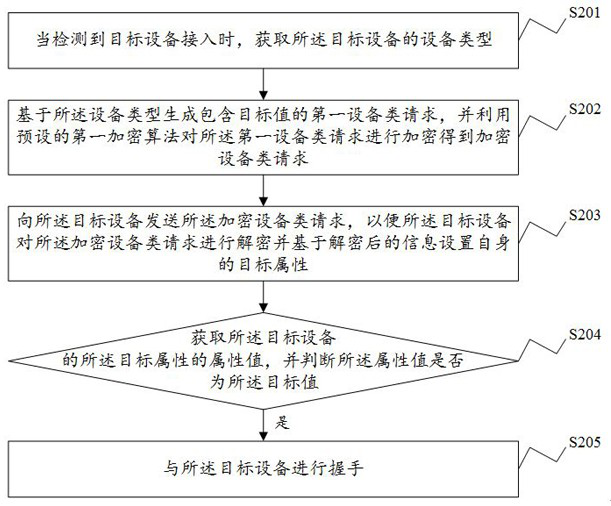
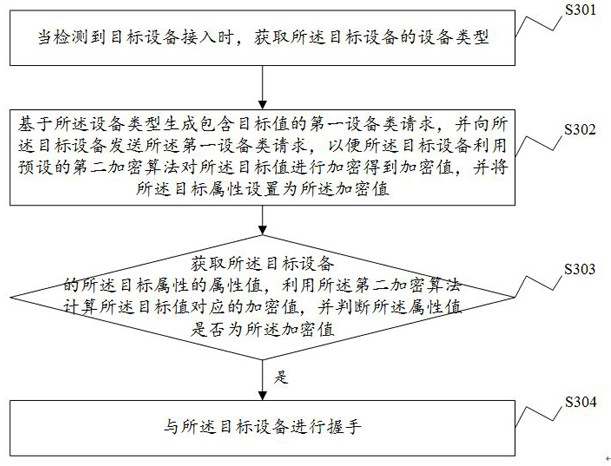
Communication method and device, electronic equipment and storage medium
ActiveCN111859361AEncrypted securityImplement encryptionDigital data protectionDigital data authenticationDevice typeEngineering
The invention discloses a communication method and device, electronic equipment and a computer readable storage medium, and the method comprises the steps: obtaining the equipment type of target equipment when the access of the target equipment is detected; generating a first equipment type request containing a target value based on the equipment type, and setting a target attribute of the targetequipment by utilizing the first equipment type request and a preset encryption algorithm; obtaining an attribute value of the target attribute of the target equipment, and judging whether the targetequipment is safe access equipment or not according to the attribute value; if the target device is a safe access device, carrying out handshaking with the target device. Therefore, according to the communication method provided by the invention, the encryption of the secure access device is realized, the privacy of the access device can be fully ensured, and the security and reliability of the access device are improved.
Owner:GEER TECH CO LTD
U disk encryption method and system based on bracelet and terminal
ActiveCN106407825BEncrypted securityUser identity/authority verificationConnection managementData informationPassword
The invention relates to a bracelet and terminal-based U disk encryption method and system. A bracelet, a terminal and a U disk are initially matched and are mutually bound correspondingly and an authentication key is generated and stored. When data information in the U disk needs to be accessed, a command of obtaining an identity authentication key needs to be transmitted to the terminal; the identity authentication key is compared with the identity authentication key during initialization after being transmitted by the terminal; if the identity authentication keys are consistent, the bracelet is controlled to transmit a password obtaining command to the terminal; and the terminal transmits a preset password to the bracelet, so that read-write operation can be carried out on the U disk. That is to say, the identity authentication key of the terminal needs to be compared with that of the U disk, the preset password can be can be transmitted to the bracelet after correct comparison, and then a user completes the read-write operation according to the preset password. By adopting bidirectional authentication, encryption of the U disk is safer and more reliable through authentication for multiple times.
Owner:深圳市魔样科技有限公司
Code-controlled data encryption method for variability key
The invention discloses a code-controlled data encryption method for a variability key, and relates to an information electronic technology. The invention mainly provides a data encryption method fora non-fixed secret key, and the core of the method is the transformation of'a clear key + a dark key-a variable key '. According to the method, a dynamic'private key 'and a static'dark key' are introduced and are decomposed into a'control code 'and a'controlled code' after being mixed, and then repeated'code control transformation 'is performed to form a'variability key'. And then encryption is carried out through a variability key. The technology of the invention is an unfixed secret key system with an unfixed secret key, which is created outside the existing fixed secret key system. A thirdsystem, namely a double-key symmetric system, is invented and created outside two existing systems, namely a single-key symmetric system and a double-key asymmetric system. Because the repeated transformation is discrete and agreed, the method is more suitable for the implementation of software and the use of an embedded chip. The technology is simple, convenient, feasible, safe and reliable, andcan be widely applied to the fields of national defense, finance, Internet, daily life and the like.
Owner:陈麟华
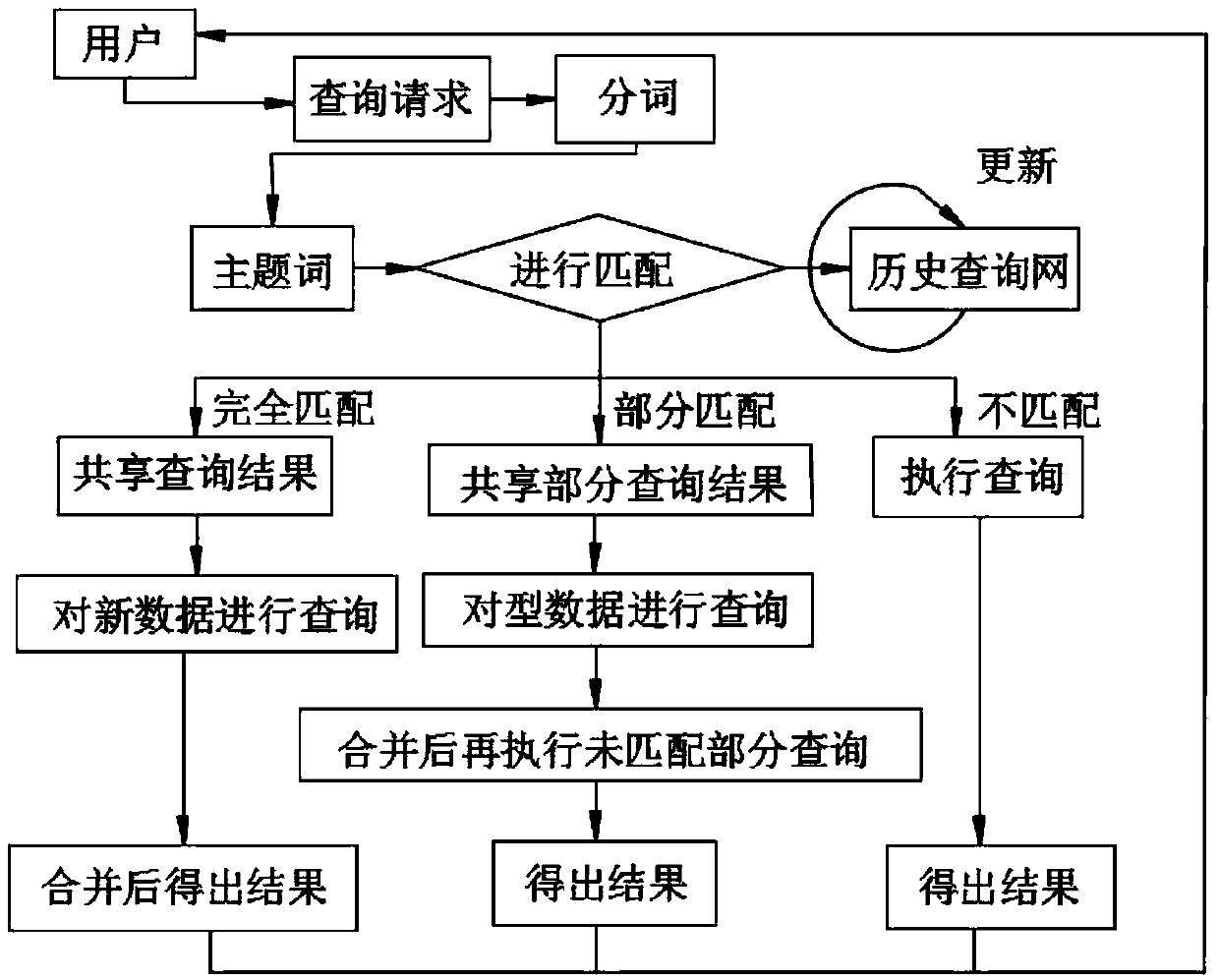
Learning big data search management method
InactiveCN109558485AEncrypted securitySmall delay time differenceEncryption apparatus with shift registers/memoriesUser identity/authority verificationCiphertextKeyword analysis
The invention discloses a learning big data search management method, which comprises the following steps of checking the user information, and opening a corresponding search interface according to the user information; making a query request by a user, analyzing the intention of the query request according to the keyword, segmenting the keyword, and extracting a subject term and an auxiliary term; matching the query subject term with a historical query network, analyzing according to a matching result, extracting a corresponding encrypted file, and completely matching the matching result, ifthe matching result is complete, indicating that the new query request of the user only has the subject term. The invention discloses a learning big data search management method. Compared with an RSAalgorithm and an AES algorithm, the AES and RSA hybrid algorithm has remarkable advantages in the aspects of encryption safety, low delay, password ciphertext synchronization and the like, the delaytime difference of the AES and SSL hybrid algorithm is minimum and the encryption is safer, the advantages of low delay, effective access authentication and the like are remarkable, and a better use prospect is brought.
Owner:安徽创见未来教育科技有限公司
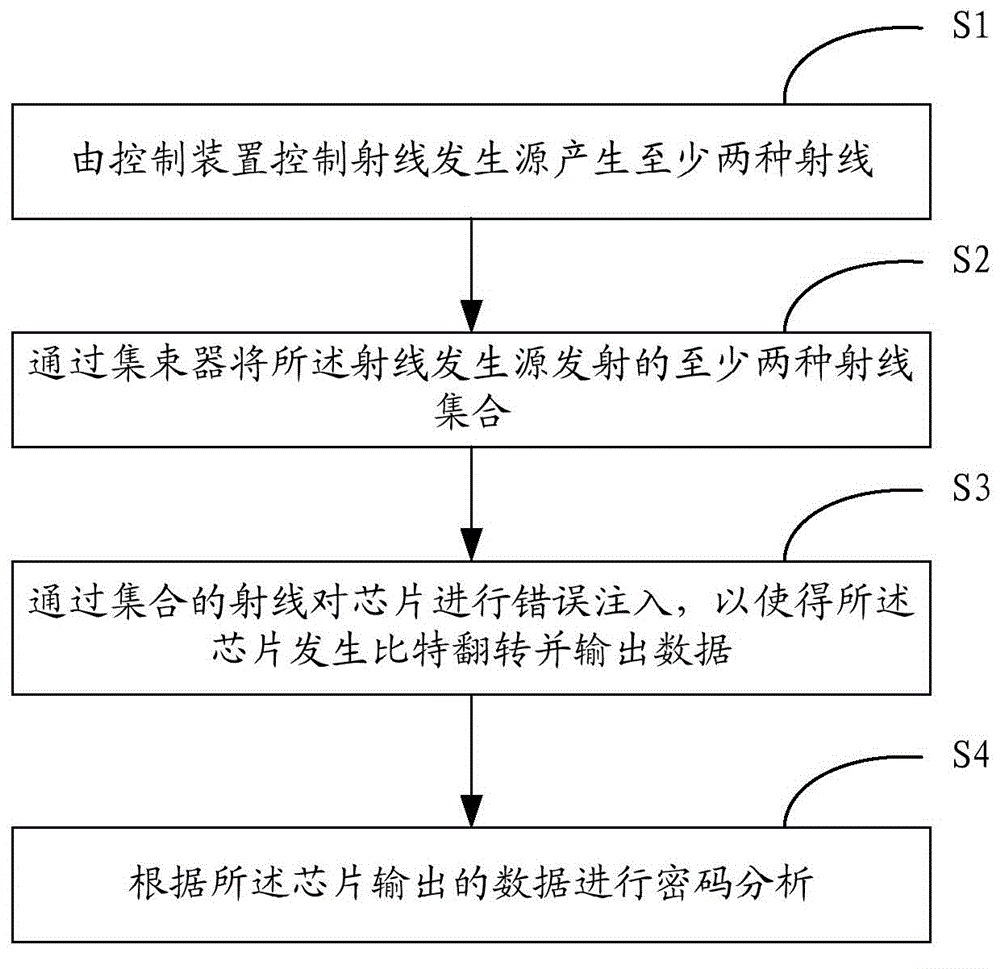
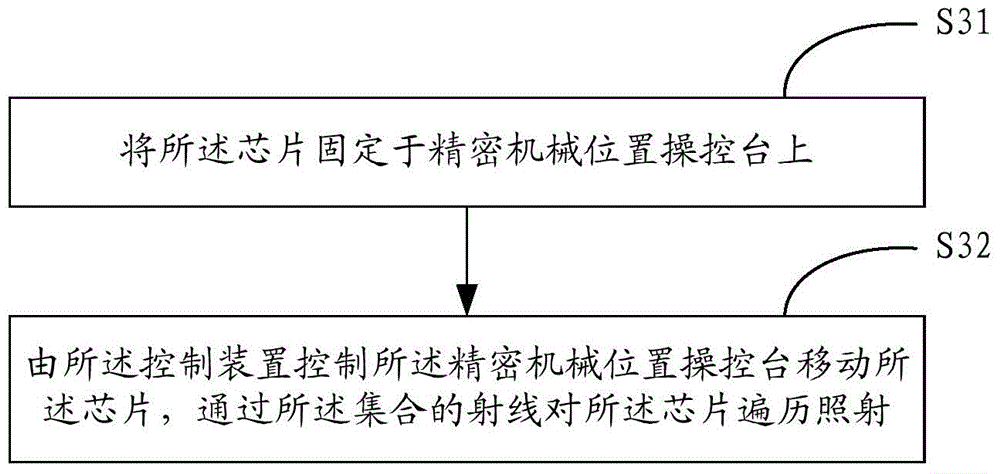
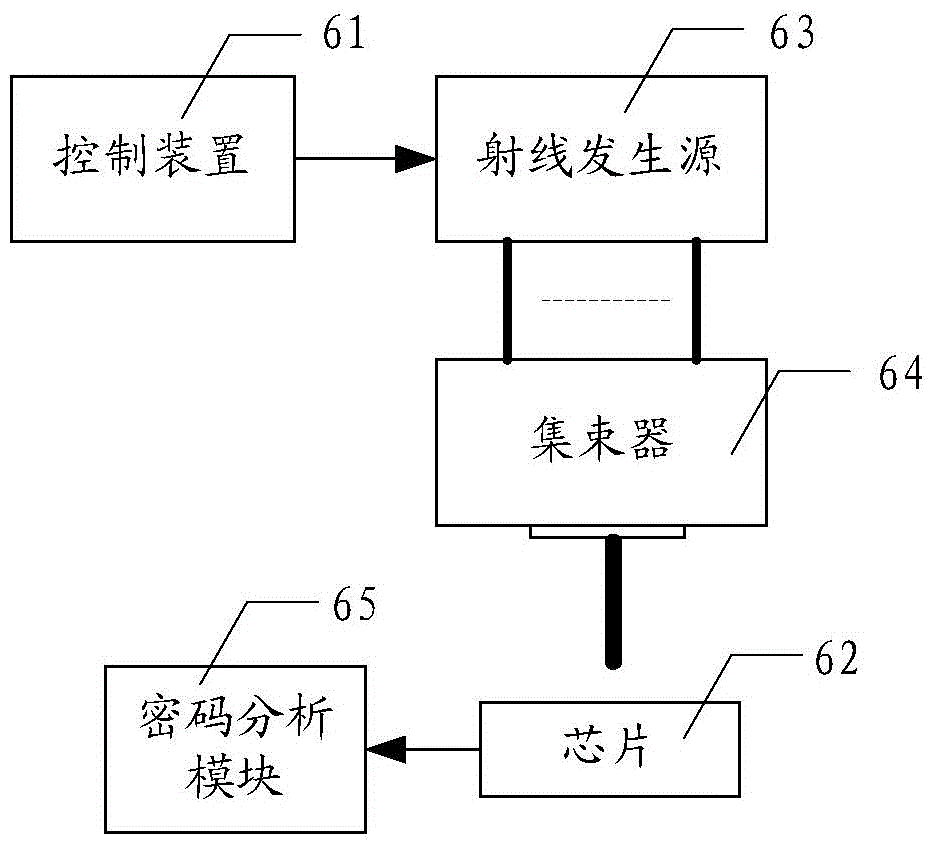
Security test method and system based on chip
InactiveCN105095002AEncrypted securityEasy to useFault responsePlatform integrity maintainancePasswordCryptanalysis
The present invention is applicable to the field of chip testing, and provides a security test method and system based on a chip. The method comprises: controlling a radiation generating source by using a control device to generate at least two types of rays; collecting the at least two types of rays emitted by the radiation generating source by using a buncher; performing fault injection processing on a chip through the collected rays to enable the chip to undergo a bit-flipping and output data; performing cryptanalysis according to data outputted by the chip. If a password analyzed is the correct password, an algorithm used for chip encryption is required to be modified; and if the password analyzed is not the correct password, an encryption algorithm currently used for chip encryption is secure; Accordingly, the problem of chip security is solved from the perspective of fault injection attack defense and the chip can be used securely.
Owner:NATIONZ TECH INC
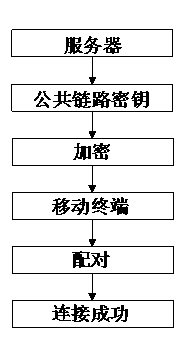
Network connecting encryption method of mobile terminal
InactiveCN103297228AReduce the chance of being attackedRelieve pressureMultiple keys/algorithms usagePublic key for secure communicationComputer terminalNetwork data
The invention discloses a network connecting encryption method of a mobile terminal. The network connecting encryption method includes that a first initial link secret key is generated by a network connecting module of the mobile terminal, a second initial link secret key is generated by a server, a public link secret key is generated by mutual verification performed by the mobile terminal and the server, and the public link secret key is the secret key with identification code length of 4; the server encrypts received network data through the public link secret key and sends the encrypted network data to the mobile terminal, the mobile terminal receives and matches the data, and connection is built when the data match successfully. By the means, the network connecting encryption method of the mobile terminal is simple in encryption, the secret key with the identification code length of 4 can meet requirements of mobile devices, pressure on data processing of the server is effectively reduced, encryption is safe, attacked rate of the mobile terminal is effectively lowered, and user's information can be protected.
Owner:JIANGSU QIYIDIAN NETWORK
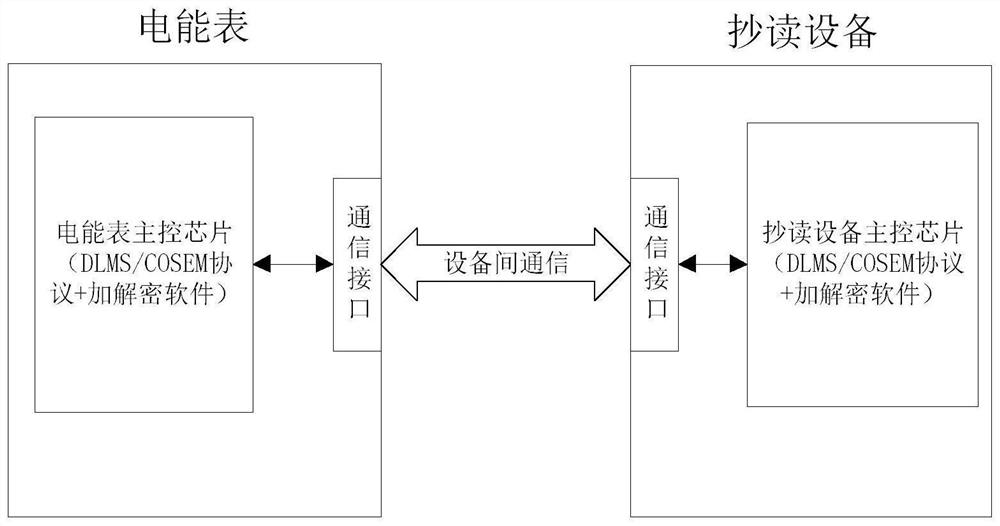
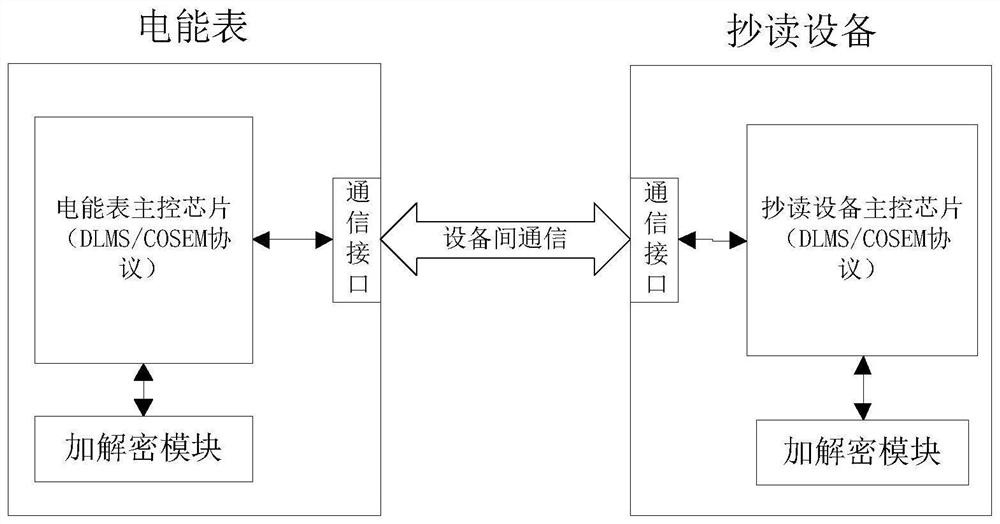
Encryption and decryption module and meter reading system suitable for DLMS/COSEM communication protocol
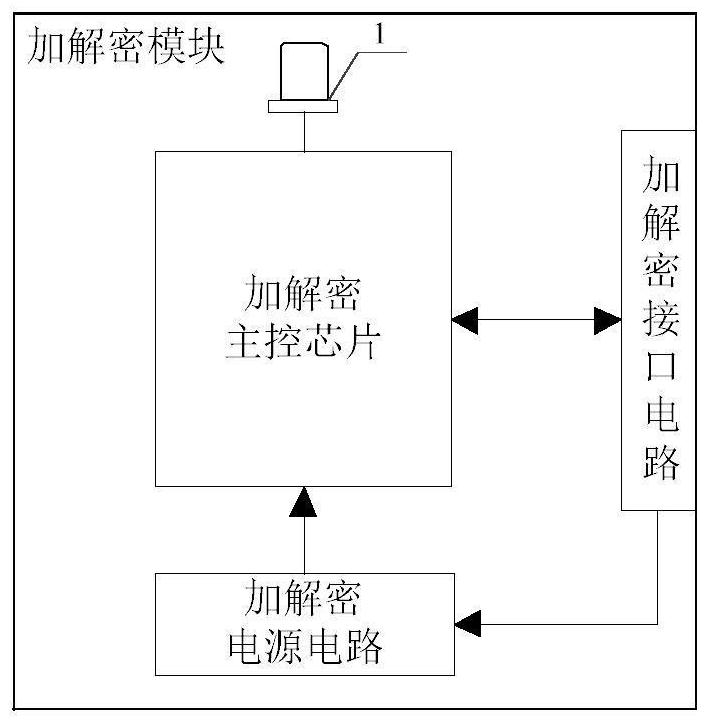
ActiveCN114244511AEncrypted securityPrevent theftKey distribution for secure communicationUtility meters data arrangementsInterface circuitsEmbedded system
The invention provides an encryption and decryption module and a meter reading system suitable for a DLMS / COSEM communication protocol, the encryption and decryption module is applied to an electric energy meter and a reading device in the meter reading system, the encryption and decryption module comprises an encryption and decryption main control chip, an encryption and decryption interface circuit, an encryption and decryption power supply circuit and an operation indicating lamp, and the encryption and decryption main control chip is used for completing encryption and decryption operation of data; the encryption and decryption interface circuit is used for data and signal interaction between the encryption and decryption module and an external module; the encryption and decryption power supply circuit is used for converting a power supply level input by the encryption and decryption interface circuit into a level required by the encryption and decryption module; and the operation indicating lamp is used for displaying the operation state of the encryption and decryption module. According to the encryption and decryption module and the meter reading system, an encryption algorithm is separated from a service program, so that encryption is safer and more reliable; the key is stored in the encryption and decryption module, so that the key is effectively prevented from being stolen; the encryption and decryption module integrates various encryption algorithms in DLMS / COSEM communication, system developers do not need to develop any more, the burden of the developers is relieved, and the product development period is shortened.
Owner:HANGZHOU VANGO TECH
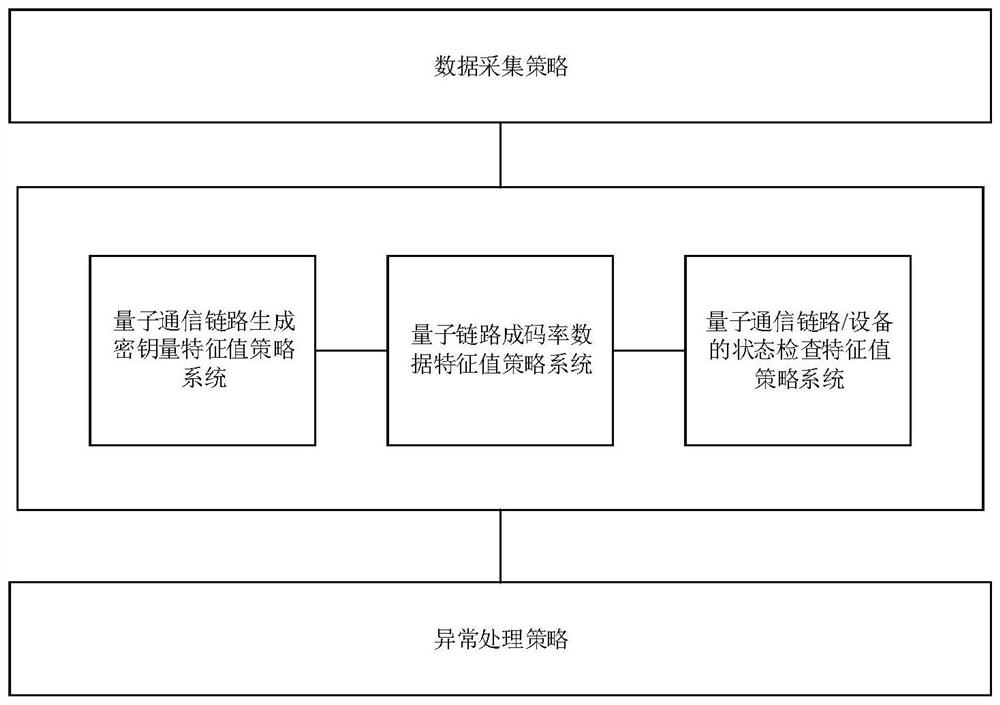
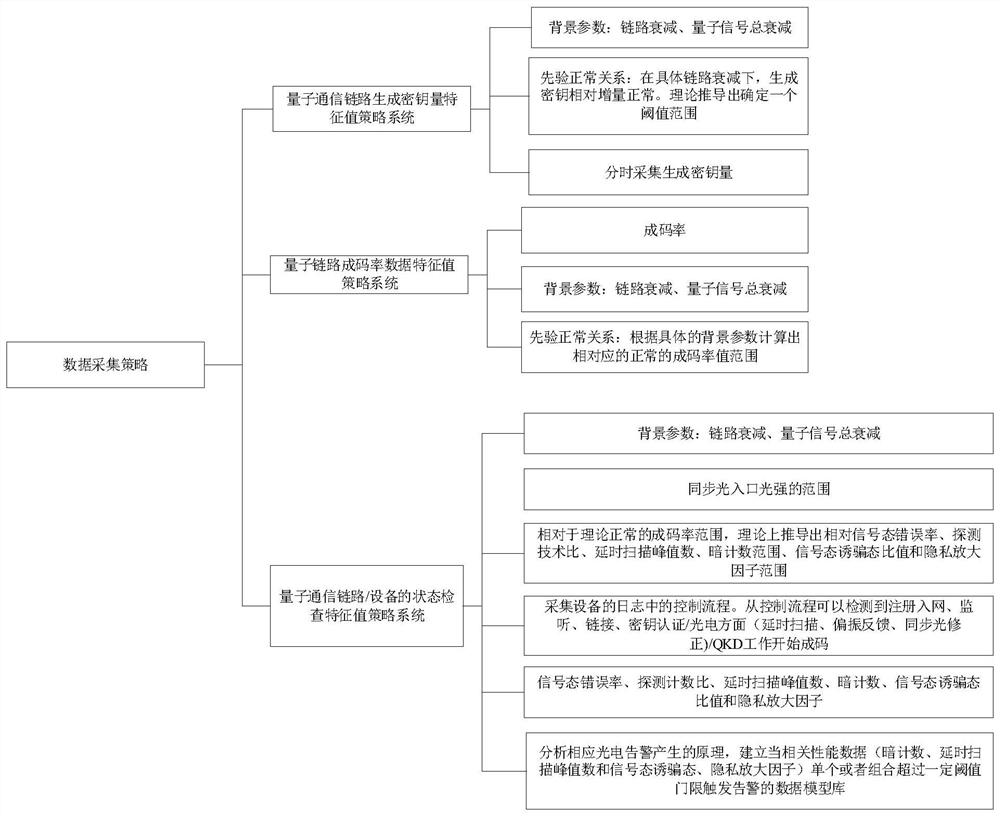
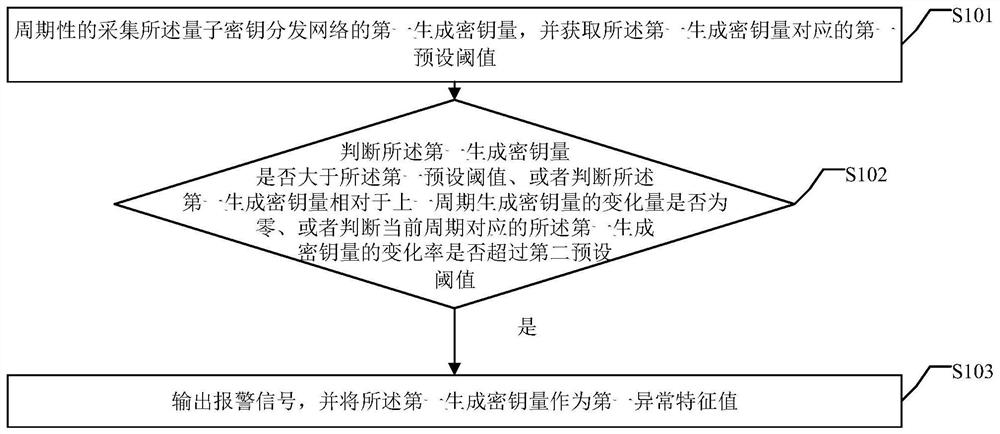
Intelligent data operation and maintenance system of quantum key distribution network
PendingCN114765535AEfficient encryptionEncrypted securityKey distribution for secure communicationMaintenance systemSystems engineering
The invention provides an intelligent data operation and maintenance system for a quantum key distribution network, and the system comprises a data collection strategy which carries out the intelligent data collection according to a business feature value strategy; according to the business characteristic value strategy, corresponding characteristic values are set according to the normal state and the abnormal state of the corresponding business data, and a processing strategy corresponding to the corresponding characteristic values is determined according to the corresponding characteristic values; and according to the exception handling strategy, in combination with the characteristics of the quantum key distribution network, the real-time state of the equipment / link is collected and compared with the characteristic value, and then the correct corresponding handling strategy is adopted. By applying the embodiment of the invention, a series of intelligent strategies are established, and the intelligent data operation and maintenance system is formed through organic combination according to the characteristics of the quantum key distribution network; according to the invention, the device / link service performance data can be automatically and efficiently collected according to the real-time network architecture and the state of the device / link, the fault is judged, the fault is intelligently processed, and the network performance is optimized.
Owner:QUANTUMCTEK
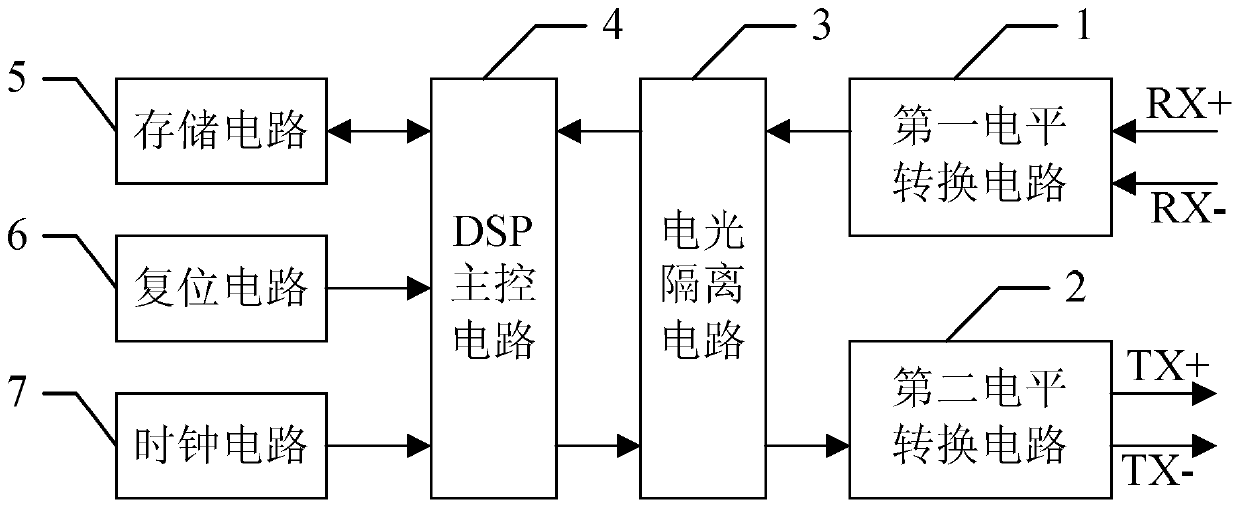
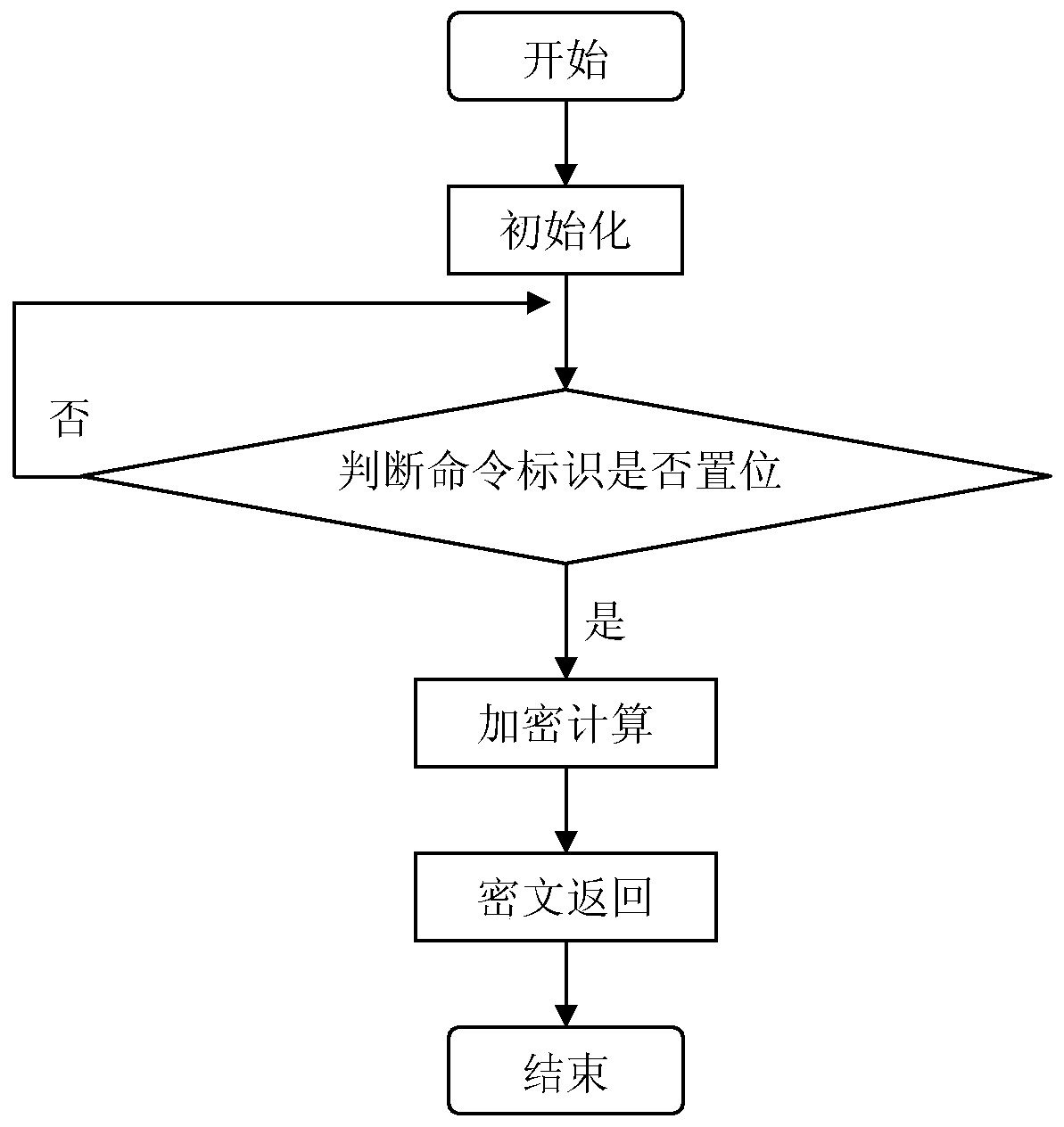
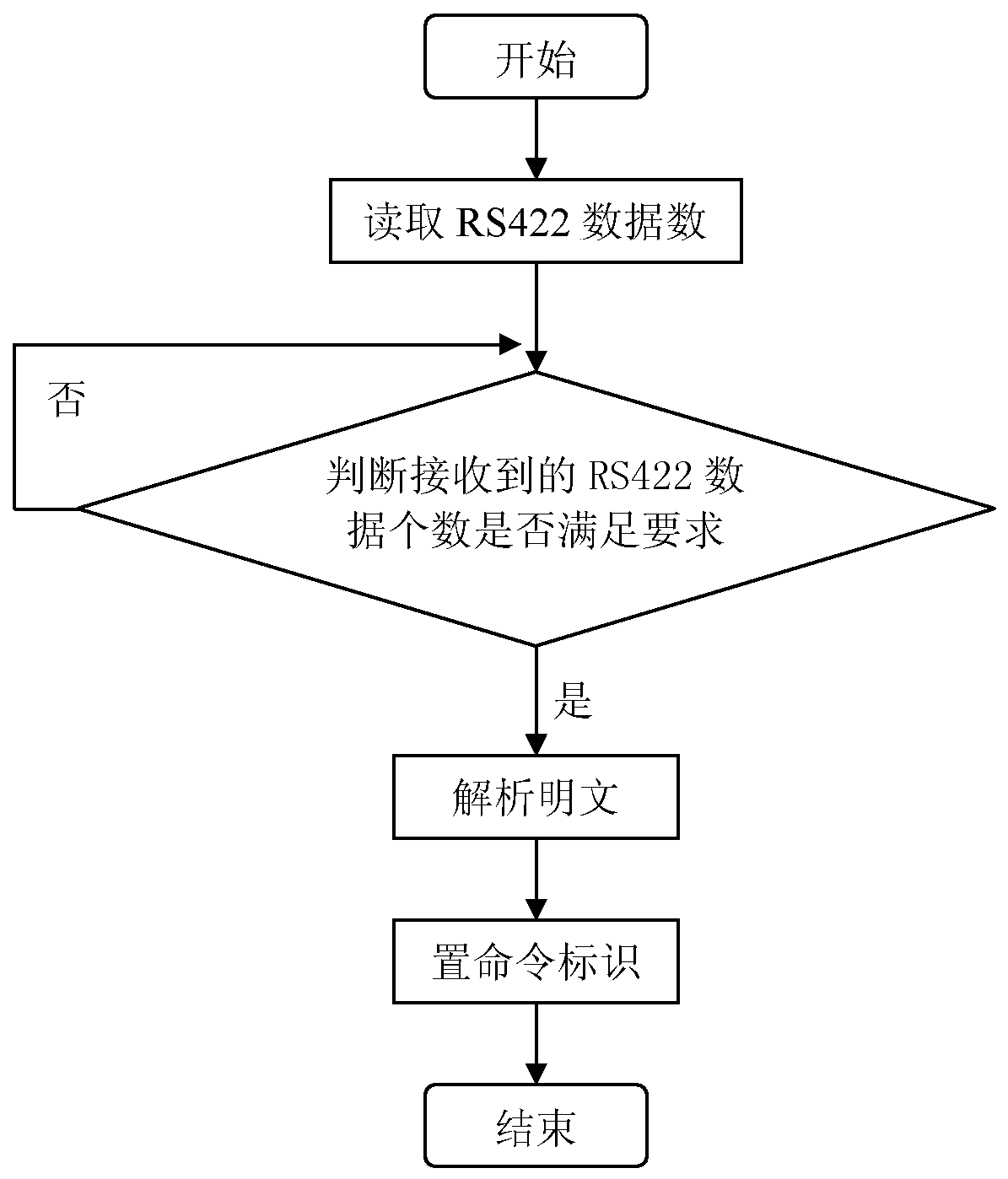
An encryption card and encryption method based on rs422
ActiveCN106778363BReduce usageIllegal use prevention using USBKeyInternal/peripheral component protectionDigital data authenticationComputer hardwareCiphertext
The invention provides a RS422 based encryption card and an encryption method, and relates to the field of electronic measurement. The RS422 plain data are sent to a DSP main control circuit by an external main control computer in sequence through a first electrical level switch circuit and a photoelectric isolation circuit, the RS422 plain data are received by the DSP main control circuit through the interruptions and when the amount of data reach the specified length through detections, the DSP main control circuit indicates that completed plain data has been received, command identifiers are set in place, when the command identifier information is identified by a DSP main program, the plain data are computed through encryption by adopting a symmetric encryption algorithm, so that encrypted texts are obtained, and finally the encrypted texts are sent to the external main control computer in sequence through the photoelectric isolation circuit and a second electrical level switch circuit. The encryption card can be integrated into the inner side of an automatic test system, through use of the encryption card and the encryption method, the secret keys can be set by utilizing the external computer through the RS422 port and are encryption processed, and the legitimate use of the automatic test system is safeguarded.
Owner:HARBIN INST OF TECH
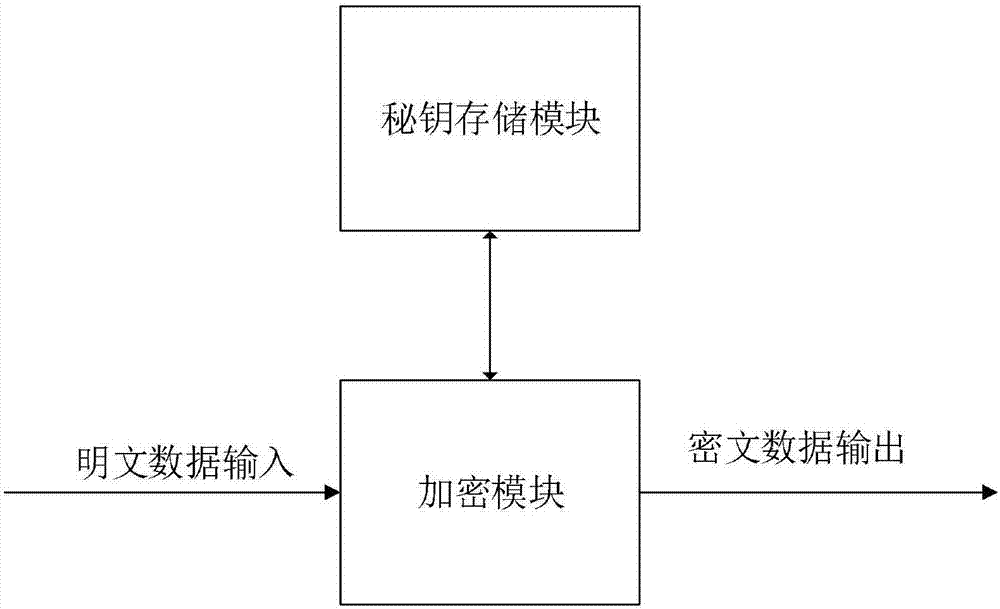
Encryption method of CAD model
InactiveCN107241194AGood encryptionEncrypted securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesData pointKey storage
The invention provides an encryption method of a CAD design model. The encryption method includes a secret key storage module and an encryption module, wherein the secret key storage module is connected with the encryption module and is used for storing a secret key; and the encryption module is used for encryption processing. The encryption method provided by the invention is to encrypt a whole CAD model, thereby enabling an encryption effect to be better, and after others obtain an encryption model, the designed model cannot be restored as well, thereby enabling a more practical effect to be achieved than an existing CAD encryption method; and at the same time, in a CAD model encryption process, random data points are obtained for the whole CAD model, and the encrypted secret key uses a characteristic value of an iris, so that the CAD model is encrypted more safely and the whole CAD model can be encrypted.
Owner:长沙善道新材料科技有限公司
Mobile phone network control method based on fingerprint identification
InactiveCN105046129AWill not affect learningEncrypted securityDigital data authenticationComputer hardwareNetwork connection
The invention relates to a mobile phone network control method based on fingerprint identification. The method comprises the following steps of: starting a client; obtaining fingerprint password information through a fingerprint recognition system; judging whether a password is correct or not; if the judging result is NO, returning to a login interface to obtain a password again; if the judging result is YES, entering a setting interface and accepting parameters set by a user; synchronously obtaining the current time information, and performing judgment; if the judged current time is in the network opening allowing time period set by the user, maintaining the network connection; and if the judged current time is beyond the network opening allowing time period set by the user, maintaining the network disconnection. The mobile phone network control method has the beneficial effects that a parent can set the network opening allowing time period of a mobile phone; the goal is achieved through network control; the communication function of the mobile phone cannot be influenced; the study of a child cannot be influenced; and the influence of games and Internet adverse information on juveniles is effectively avoided.
Owner:成都亿邻通科技有限公司
Mobile application information safety system for power system, and transmission method of mobile application information safety system
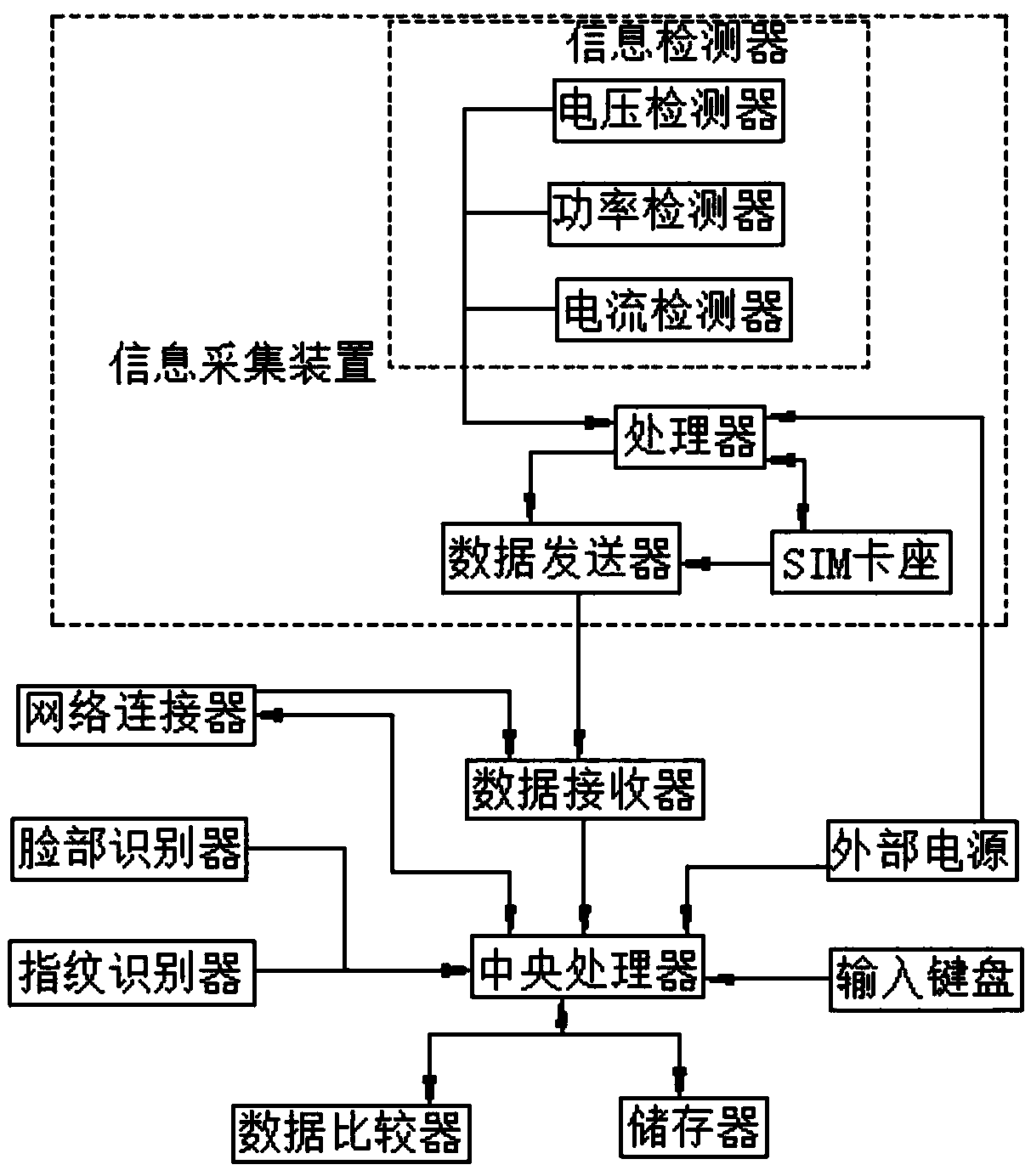
InactiveCN108684009AEasy transferSimple structureParticular environment based servicesElectrical testingElectricityInformation transmission
The invention proposes a mobile application information safety system for a power system, and a transmission method of the mobile application information safety system. The safety system comprises a central processor, and the input end of the central processor is electrically connected with a face recognizer, a fingerprint recognizer, an input keyboard and an output end of a data receiver, whereinthe input end of the data receiver is electrically connected with an output end of an information collection device. The input end of the central processor is electrically connected with the output end of an external power supply. The central processor is in bidirectional connection with a data comparator, a network connector and a storage unit. The output end of the network connector is electrically connected with the input end of the data receiver. The safety system is simple in structure, is convenient to operate, enables the detection to be more convenient, enables the information transmission to be more convenient, brings convenience to the people, and enables the information to be safer through the encryption of fingerprints, face and digits.
Owner:TAIZHOU LIWEI ENVIRONMENTAL TECH CO LTD
Information hiding method and system based on elliptic curve cryptography
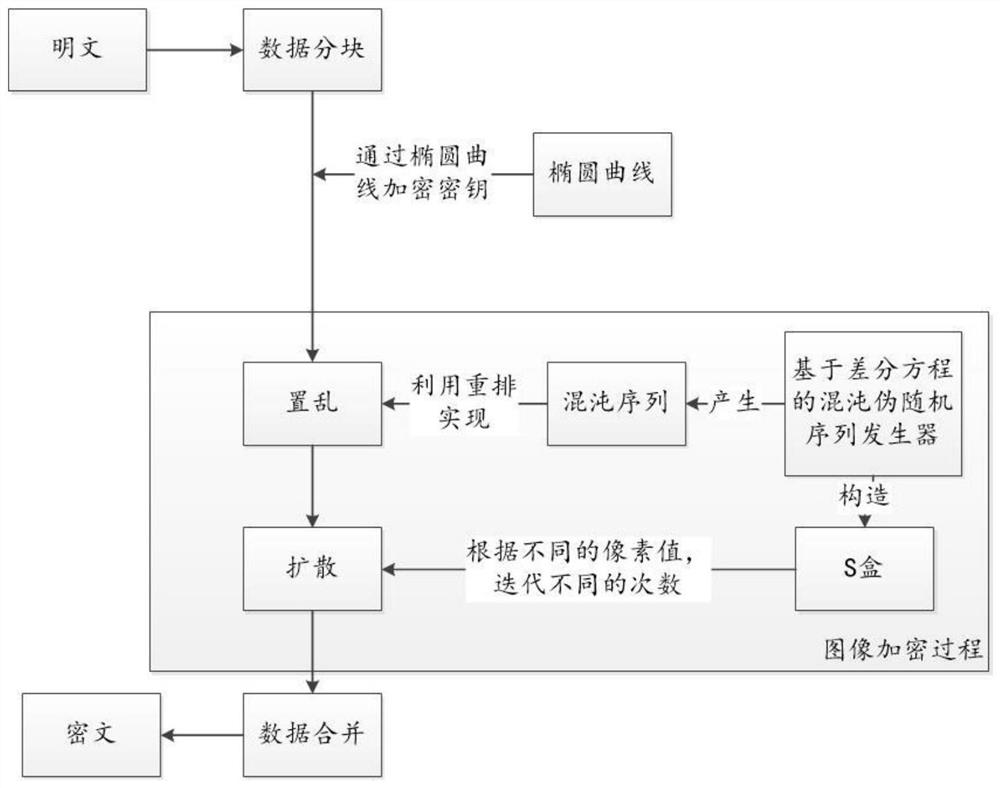
PendingCN113645021AAchieve scramblingImplement encryptionPublic key for secure communicationSecuring communication by chaotic signalsKey spaceKey (cryptography)
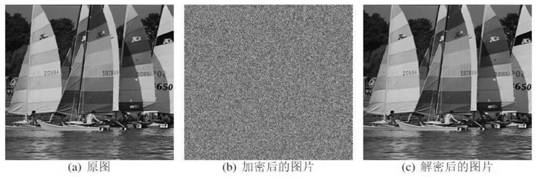
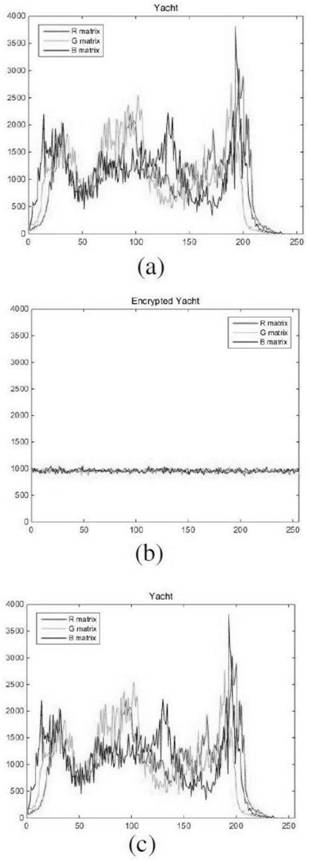
The invention discloses an information hiding method and system based on elliptic curve cryptography, and the method comprises the steps: employing an elliptic curve based on a finite field as a substrate, carrying out the scrambling of a secret key, and generating a chaotic sequence through fractional order chaotic mapping. A plaintext picture is scrambled by using the randomness of a chaos sequence, and then picture pixels are encrypted by using the chaos sequence and pixel values to carry out XOR operation, so that the scrambling and diffusion effects are achieved. According to the method, the elliptic curve public key cryptography and the private key encryption based on the fractional order chaotic mapping are combined, the algorithm complexity is improved, the key space is increased, and the algorithm has good anti-attack ability.
Owner:SHANGHAI UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com