Folder encrypting method
An encryption method and file folder technology, applied in the direction of instruments, digital data authentication, electrical digital data processing, etc., can solve the problems of text encryption failure, easy to be forgotten, and text passwords are easy to be stolen, so as to achieve good security and speech content Flexible and convenient, easy-to-collect effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
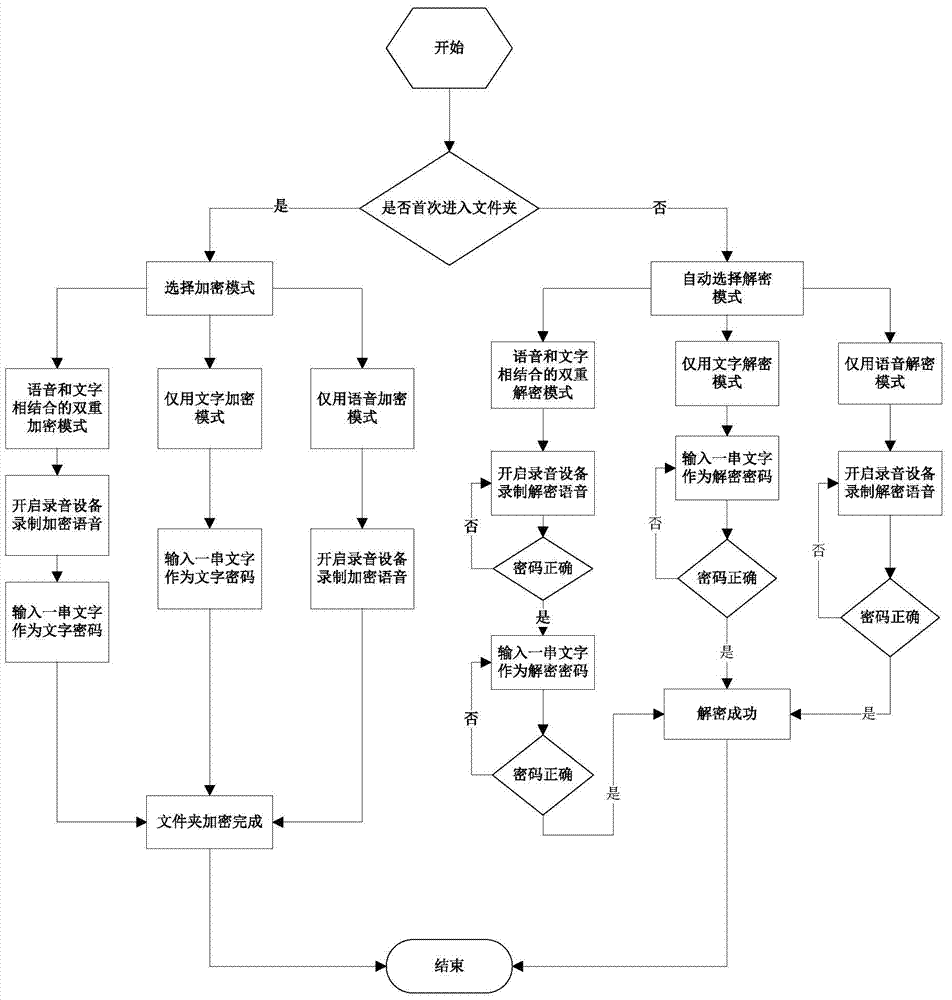
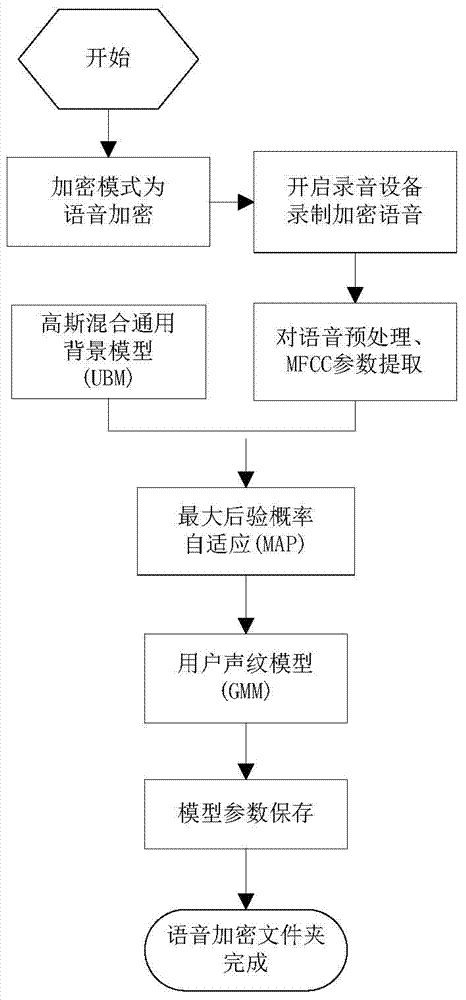
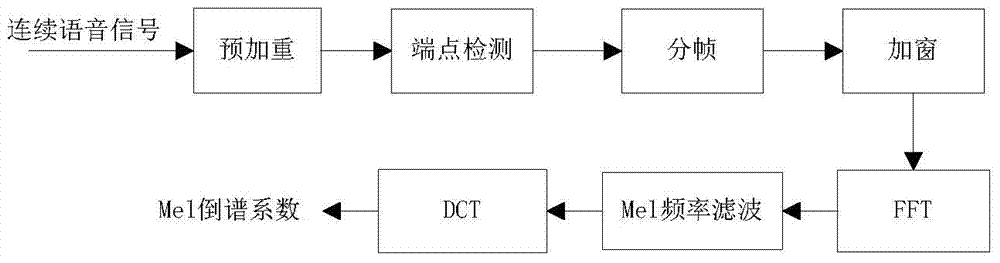
[0038] The invention proposes a folder encryption method, which mainly includes a folder speech encryption and decryption module 1, a folder text encryption and decryption module 2, and a folder speech and text double encryption and decryption module 3.
[0039] Based on the method provided by the present invention, a set of folder encryption system has been constructed, wherein the technology used in the voice encryption and decryption part involved is voiceprint recognition technology, and the overall system design process (as attached figure 1 shown) include:
[0040] A. When entering the folder to be encrypted for the first time, the user can choose to use voice encryption or text encryption or double encryption mode of voice and text.
[0041] B. According to the selected encryption mode, the system guides the user to enter the password in the cor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com