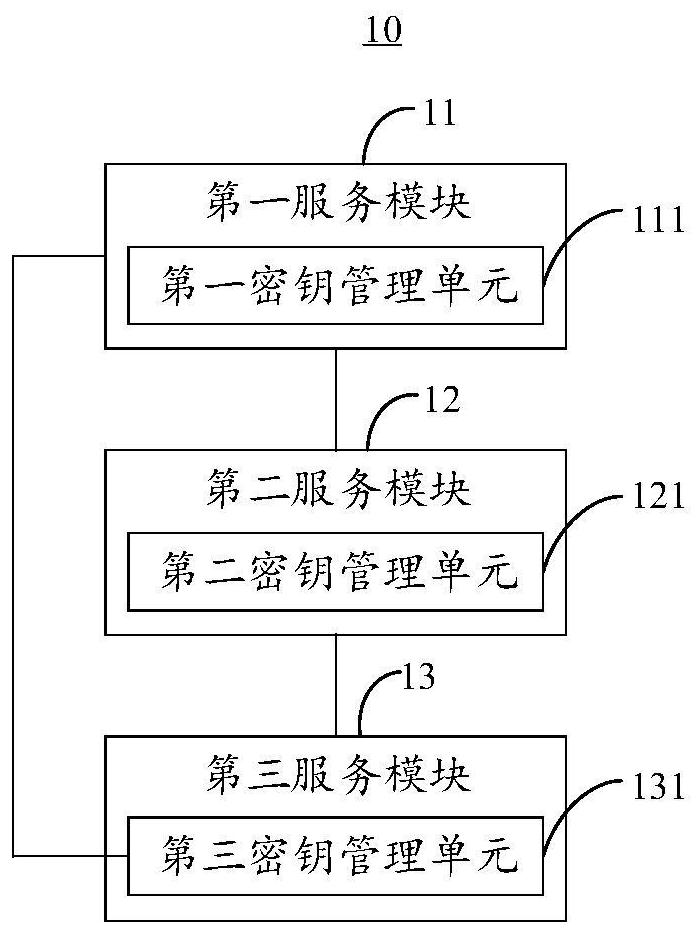
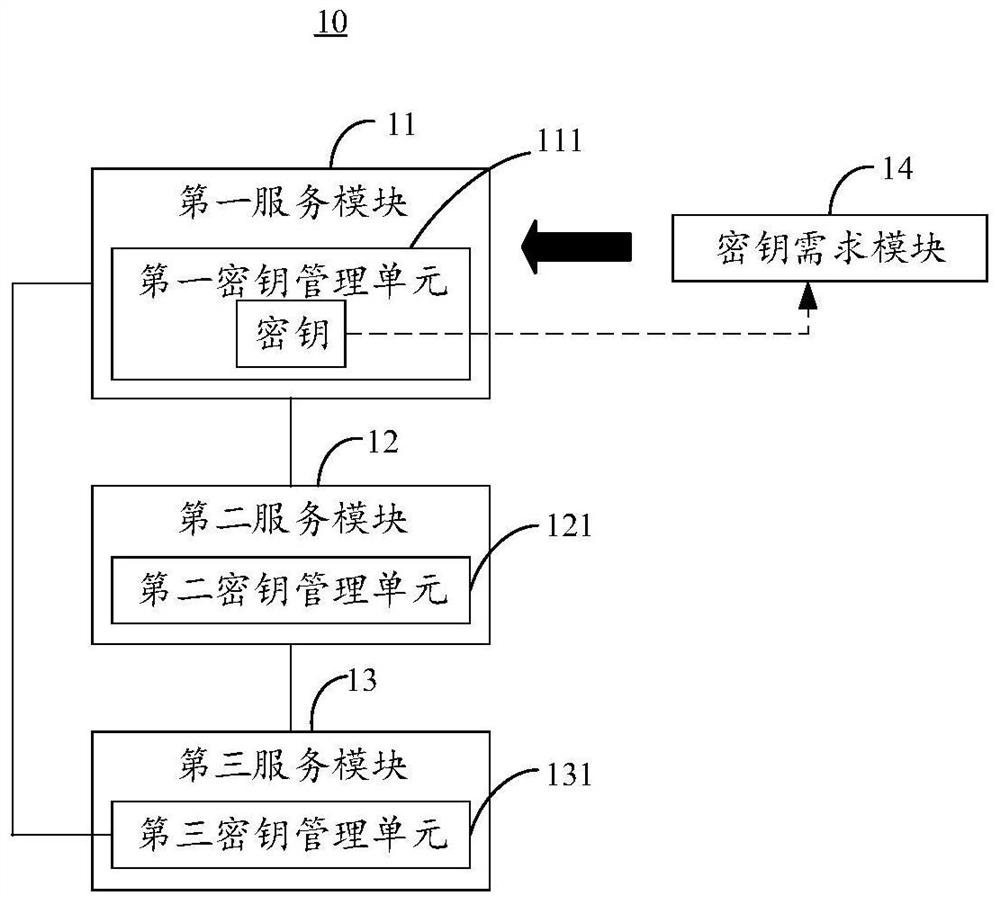
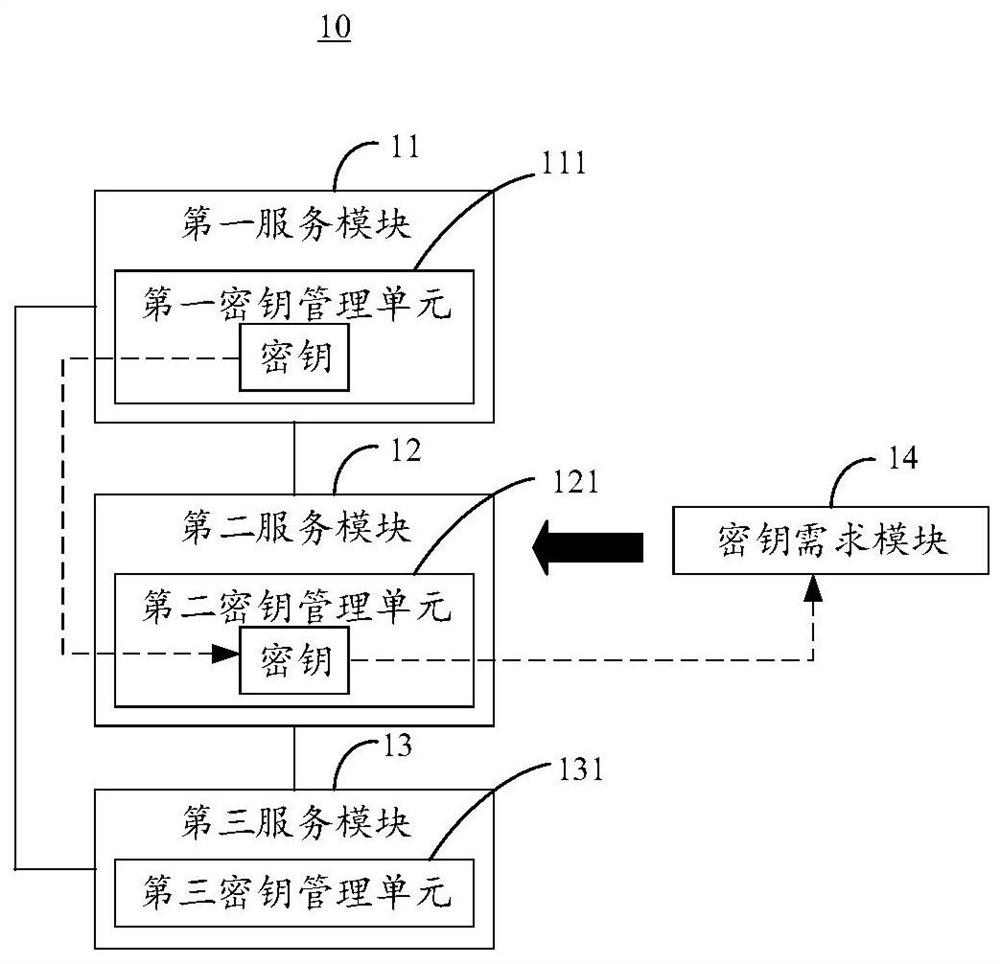
Patents
Literature
129results about How to "Improve security and confidentiality" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
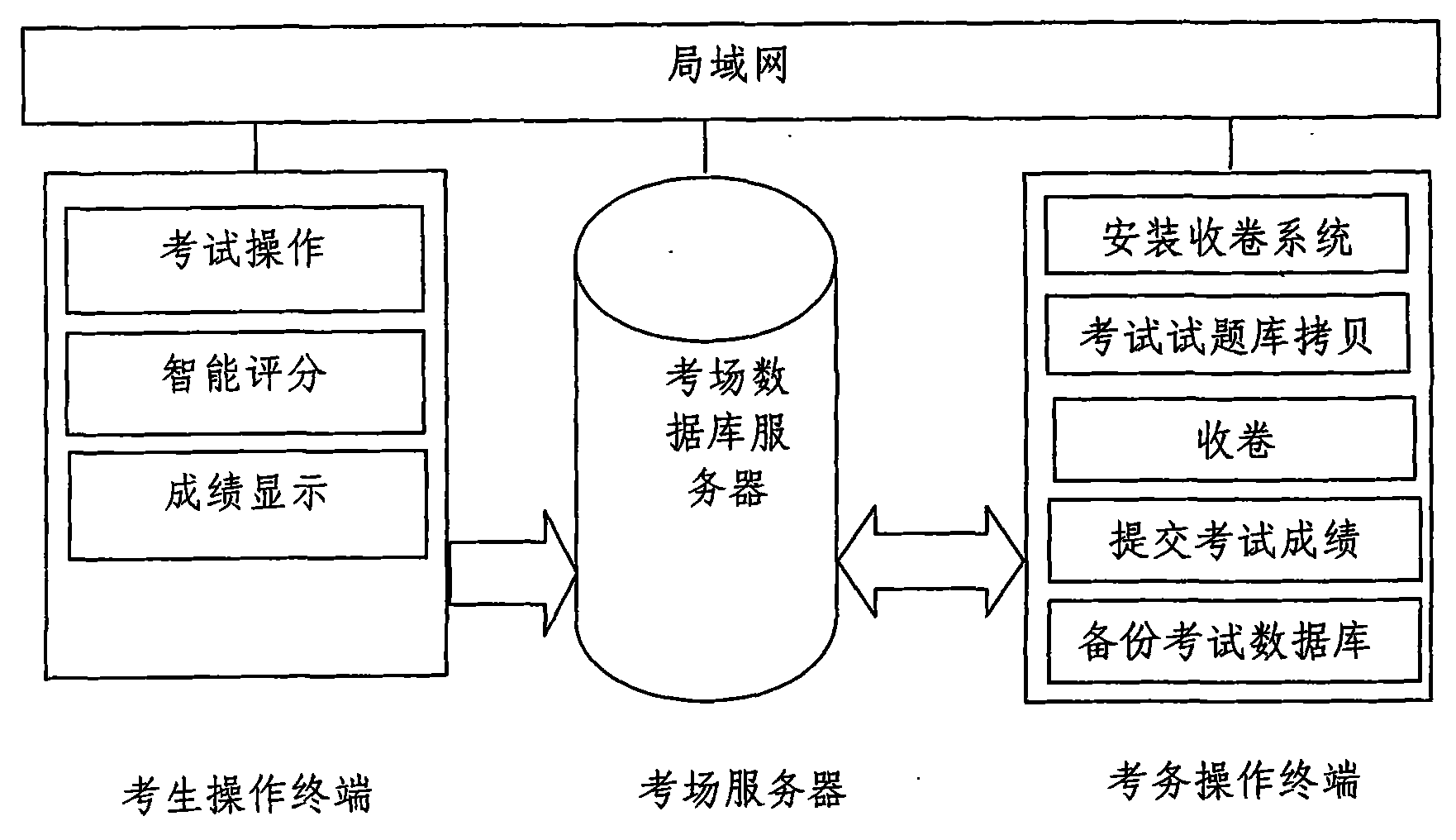
Local area network-based network examination system and implementation method thereof
InactiveCN101964152AReduce investmentGuarantee data securityData switching by path configurationElectrical appliancesArea networkBody area network
The invention discloses a local area network (LAN)-based network examination system and an implementation method thereof. The LAN-based network examination system adopts a client / server (C / S) mode framework; an examination room server, an examination affair operating terminal and examinee operating terminals form a local are network; and examination test questions in the examination room server are decrypted by the examination affair operating terminal and then converted into a data format which can be identified by the examinee operating terminals. The examination affair operating terminal classifies and collects data files of problems worked by examinees and archives examination data. The examinee operating terminals display the identified data and provide an examination environment for examinees. The LAN-based network examination system has lower requirements on network and hardware configurations, stronger adaptability and high compatibility, and only each examinee operating terminal is communicated with a twisted pair cable and is connected with each other by using an exchanger to form the local area network, thereby greatly saving the input of network equipment. The examination data are transferred in the local area network and has no physical contact with the internet, thereby guaranteeing data security and stability of the examination system.
Owner:KUNMING METALLURGY COLLEGE
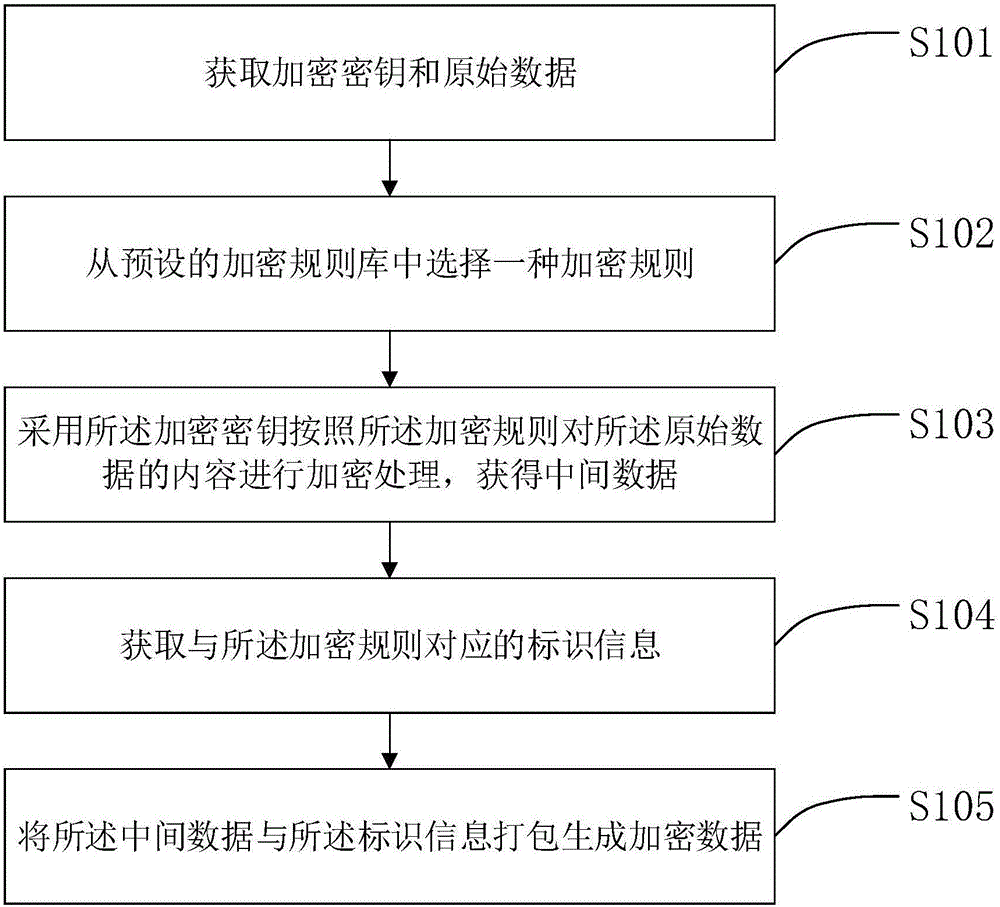
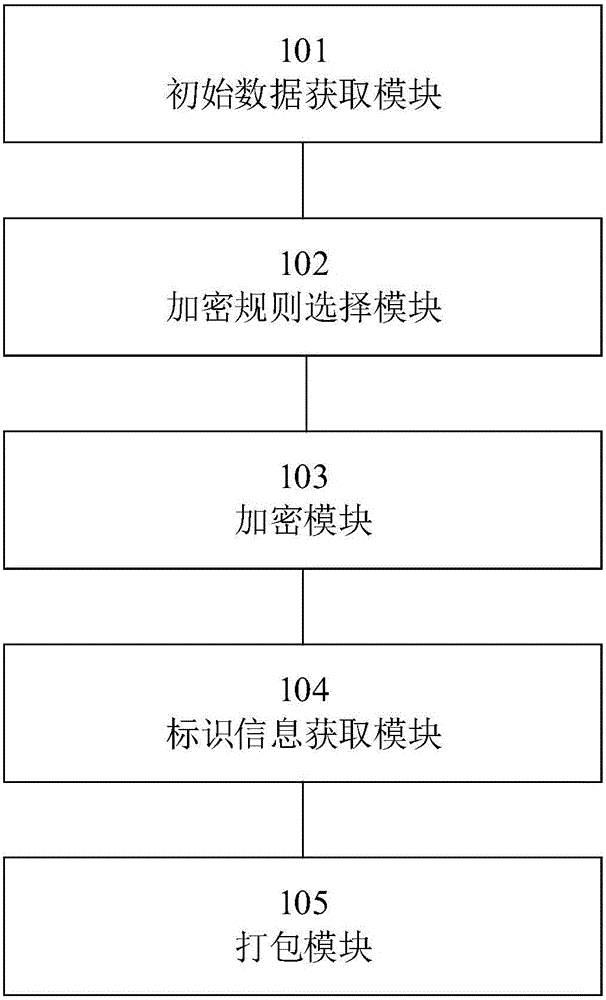
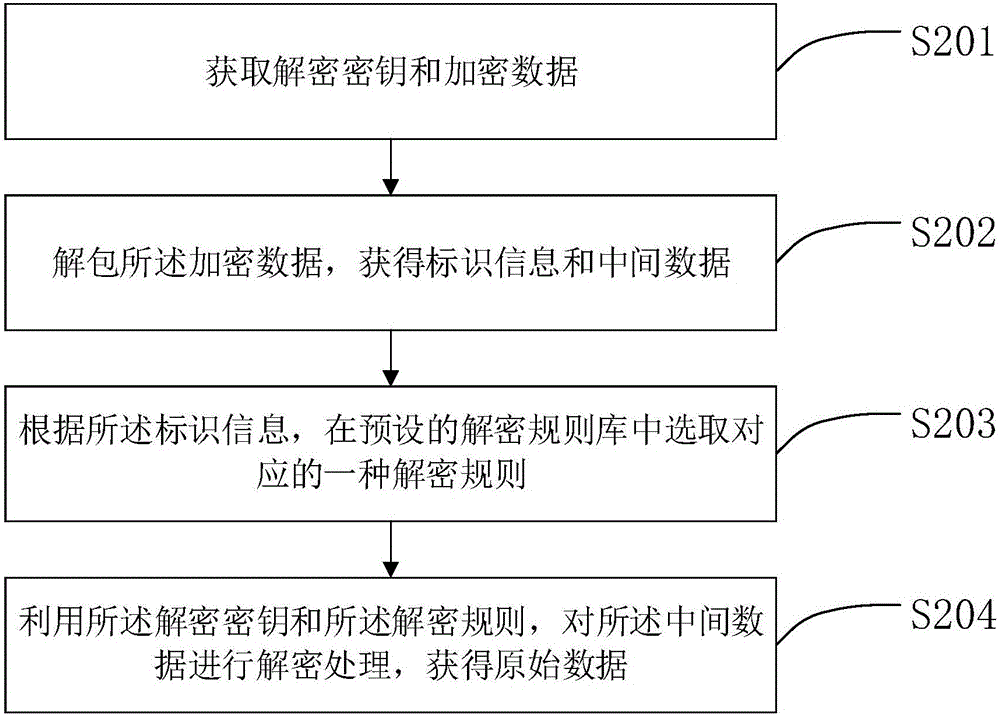
Data encrypting method and device and data decrypting method and device
ActiveCN105760765ARealize multi-dimensional encryptionAvoid crackingEncryption apparatus with shift registers/memoriesDigital data protectionComputer hardwareOriginal data
The invention relates to the field of data encrypting and decrypting, in particular to a data encrypting method and device and a data decrypting method and device.The data encrypting method comprises the steps that at first, an encryption key and original data are obtained; then, an encryption rule is selected from a preset encryption rule base; the encryption key is adopted for encrypting the original data according to the encryption rule to obtain intermediate data; then, identification information corresponding to the encryption rule is obtained; finally, the intermediate data and the identification information are packaged to generate encrypted data.Compared with the prior art, encryption information does not only depend on the carrier key, the encryption rule is selectively used, and the encryption rule is encrypted; meanwhile, in the file transmitting process, only the identification information of the encryption rule exists in the transmission information, and the specific content of the encryption rule does not exist, so that multi-dimensional encryption is achieved, the encryption means is more complex, the key can not be decrypted easily, and encryption safety is higher.
Owner:BEIJING SEEYON INTERNET SOFTWARE CORP
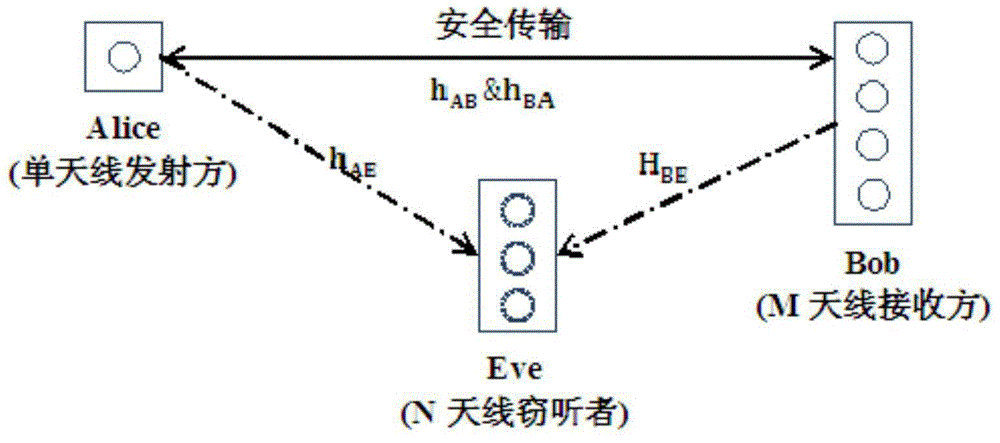
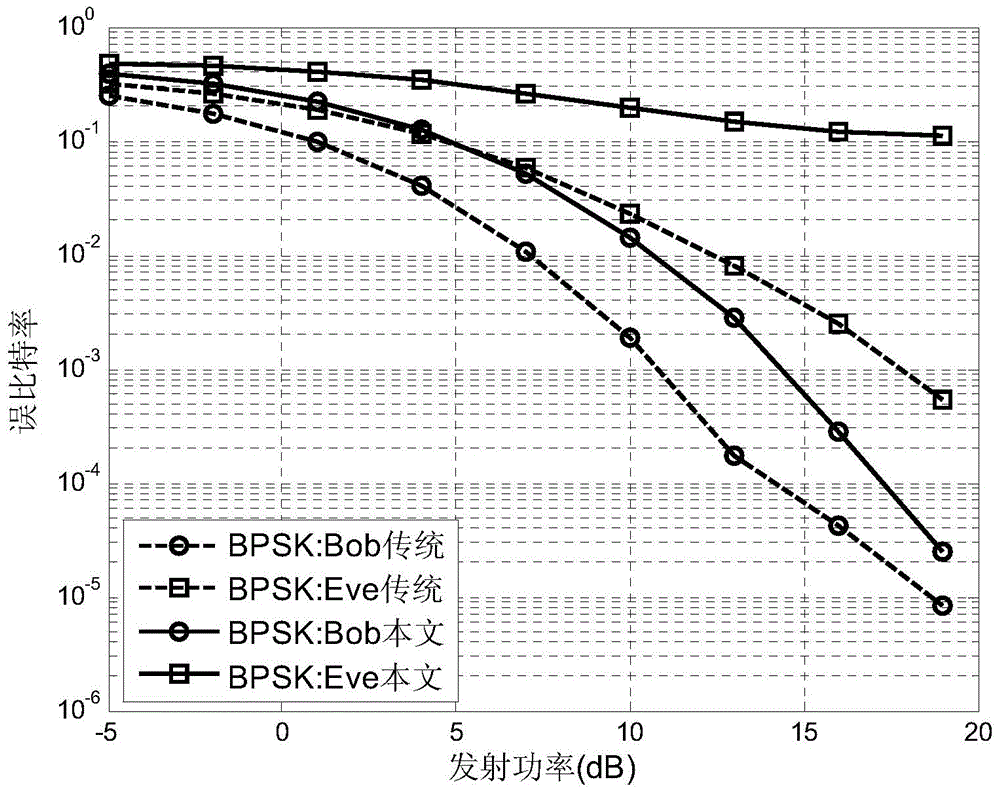
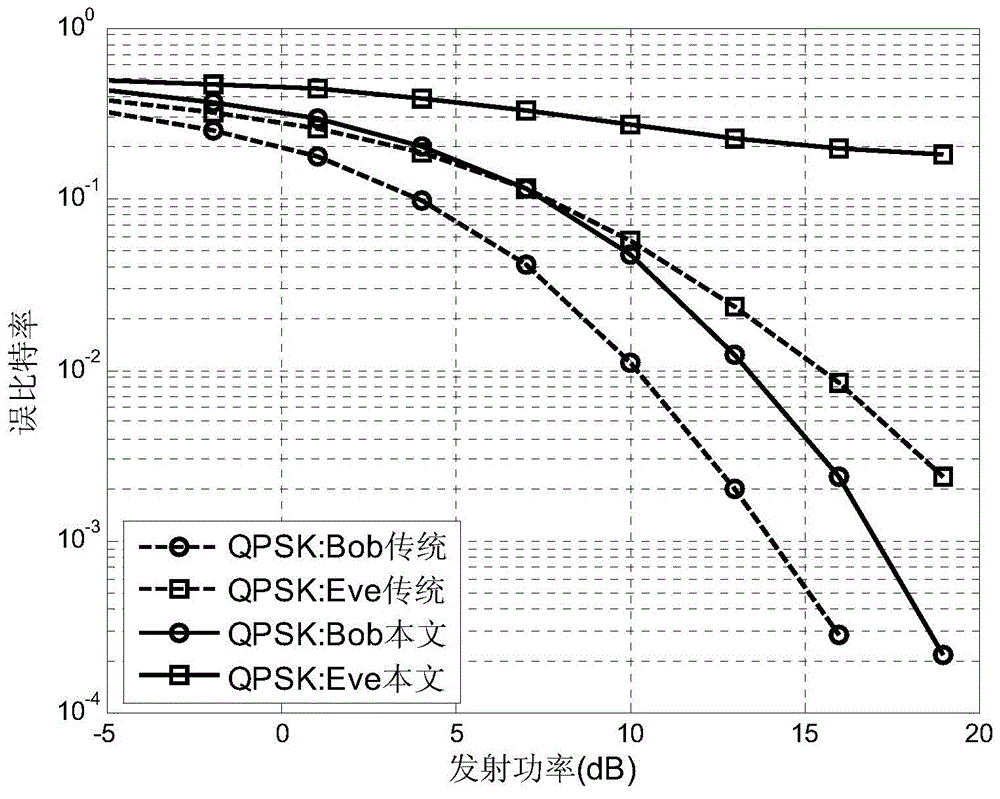
Physical layer safety transmission method used for SIMO wireless communication system
ActiveCN103986545AImprove physical layer security performanceImprove security and confidentialitySpatial transmit diversitySecret communicationCommunications systemSecure transmission
The invention discloses a physical layer safety transmission method used for an SIMO wireless communication system. Firstly, a receiving expecting party emits a random reference signal reversely, an emitting party scrambles and transmits symbols to be transmitted through the received reference signal, and finally the receiving expecting party demodulates the received signal through the known reference signal to obtain information transmitted by the emitting party. In the first step, the multi-antenna receiving party sends not only the reference signal, but also an artificial noise signal, the space where the artificial noise signal is located is in quadrature with a main channel vector, so that the artificial noise has no influence on receiving the reference signal of the emitting expecting party. For an eavesdropper, due to different channels, eavesdropping is interfered with by artificial noise signals, the random reference signal is difficult to evaluate accurately, the probability of successfully eavesdropping encrypted signals is greatly reduced, and safety transmission of the SIMO wireless communication system is guaranteed finally.
Owner:XI AN JIAOTONG UNIV
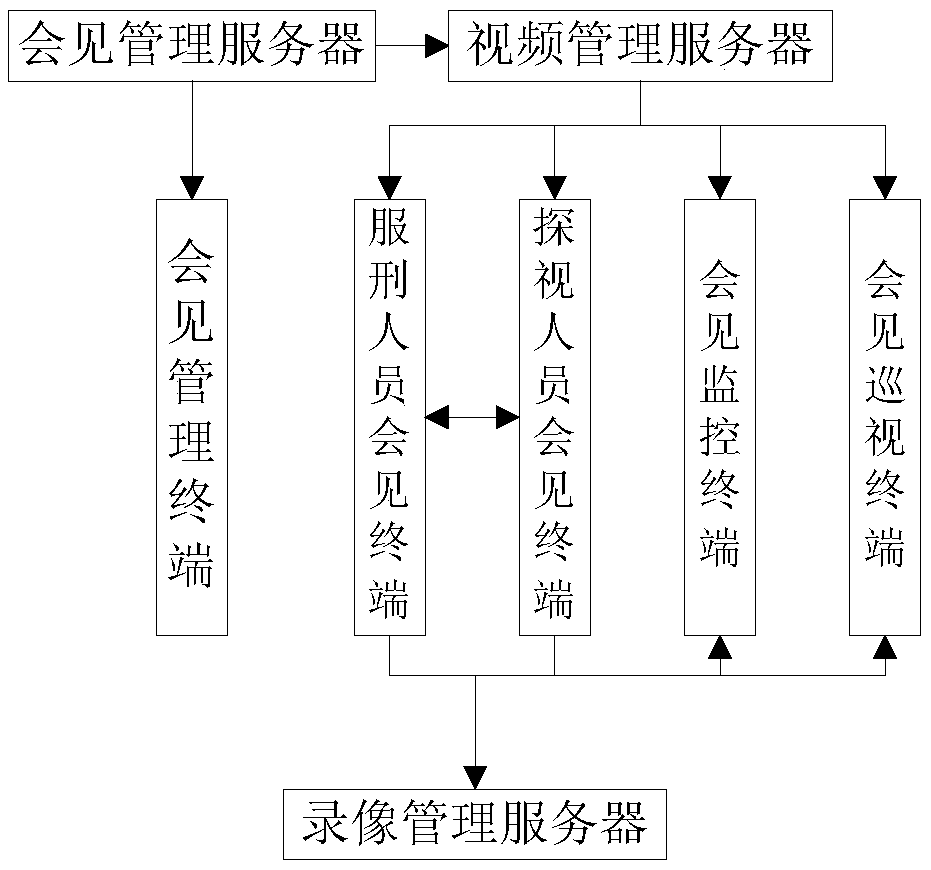
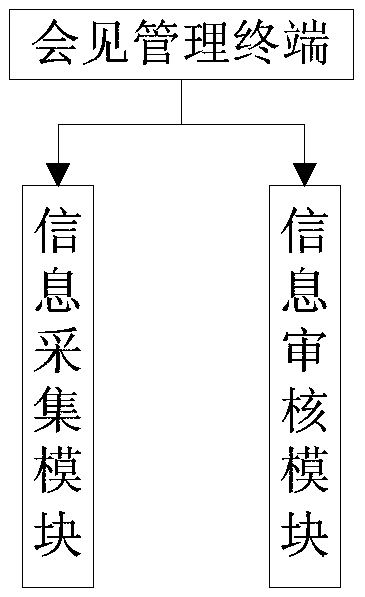
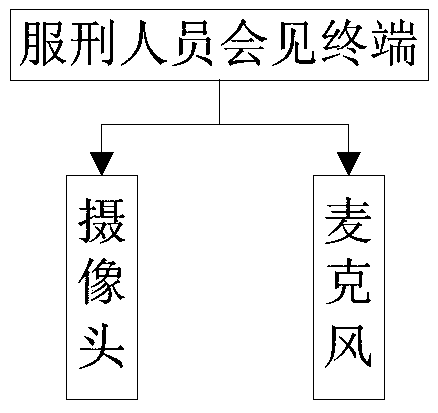
Remote video meeting system
InactiveCN105516330AImprove security and confidentialityRealize unified security managementClosed circuit television systemsTwo-way working systemsService conditionReal-time computing
The invention provides a remote video meeting system. The remote video meeting system comprises a meeting management server and a video management server, wherein the meeting management server is configured with a meeting management terminal for obtaining information of a visitor and a prisoner and matching to confirm the visitor and the prisoner; the video management server is configured with a meeting monitoring terminal, a prisoner meeting terminal and a visitor meeting terminal, the prisoner meeting terminal is used for obtaining and sending information of images and sounds of the prisoner in a meeting process, the visitor meeting terminal is used for obtaining and sending information of images and sounds of the visitor in the meeting process, and the meeting monitoring terminal is used for monitoring the obtained information of the images and the sounds of the prisoner and the obtained information of the images and the sounds of the visitor. The invention provides a special remote video meeting terminal to meet objective service conditions of a prison, thereby providing a stable and reliable meeting apparatus for the prisoners and the visitors.
Owner:SHANDONG ZHONGCI ROMOTE VIDEO TECH
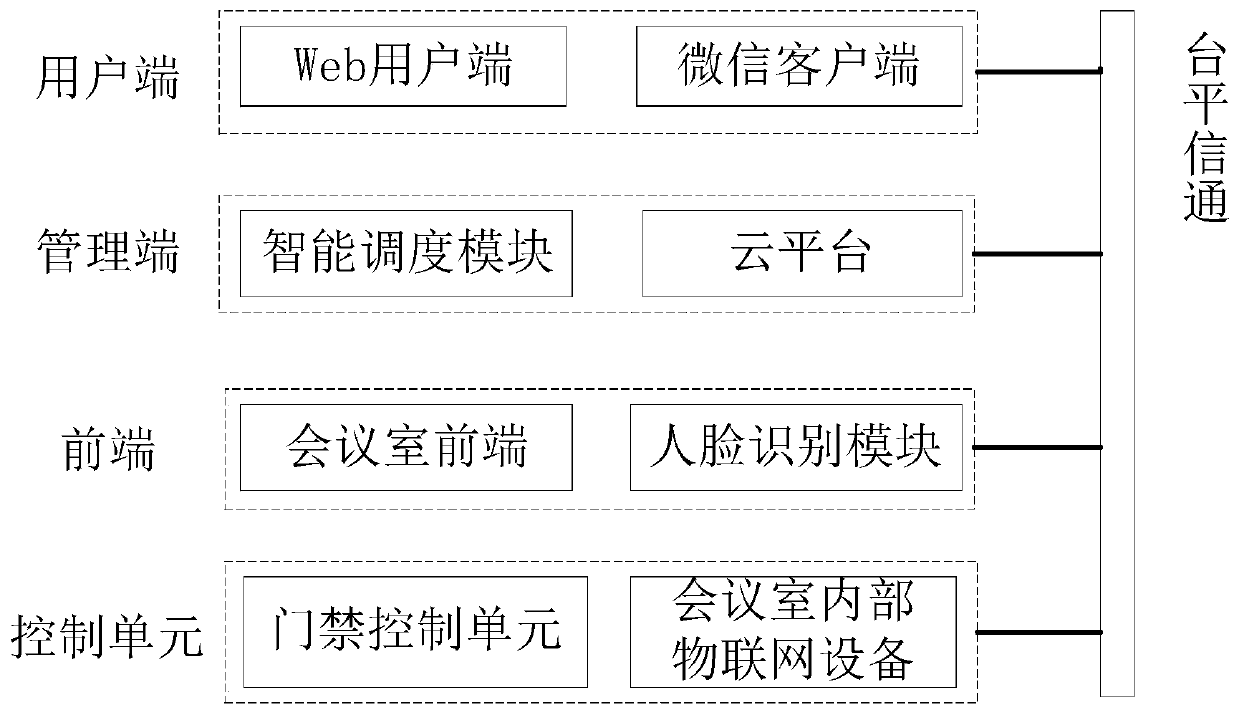
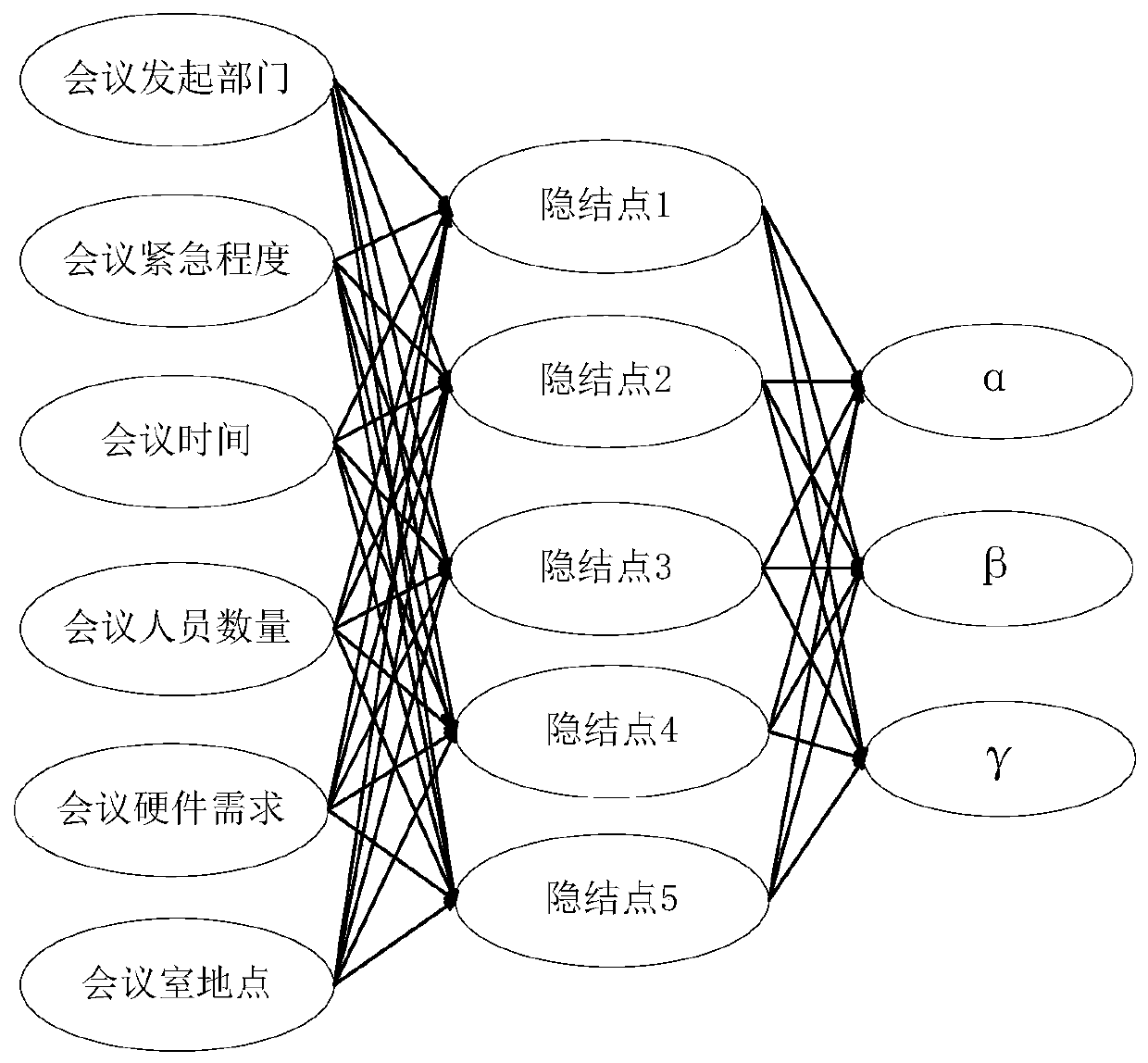
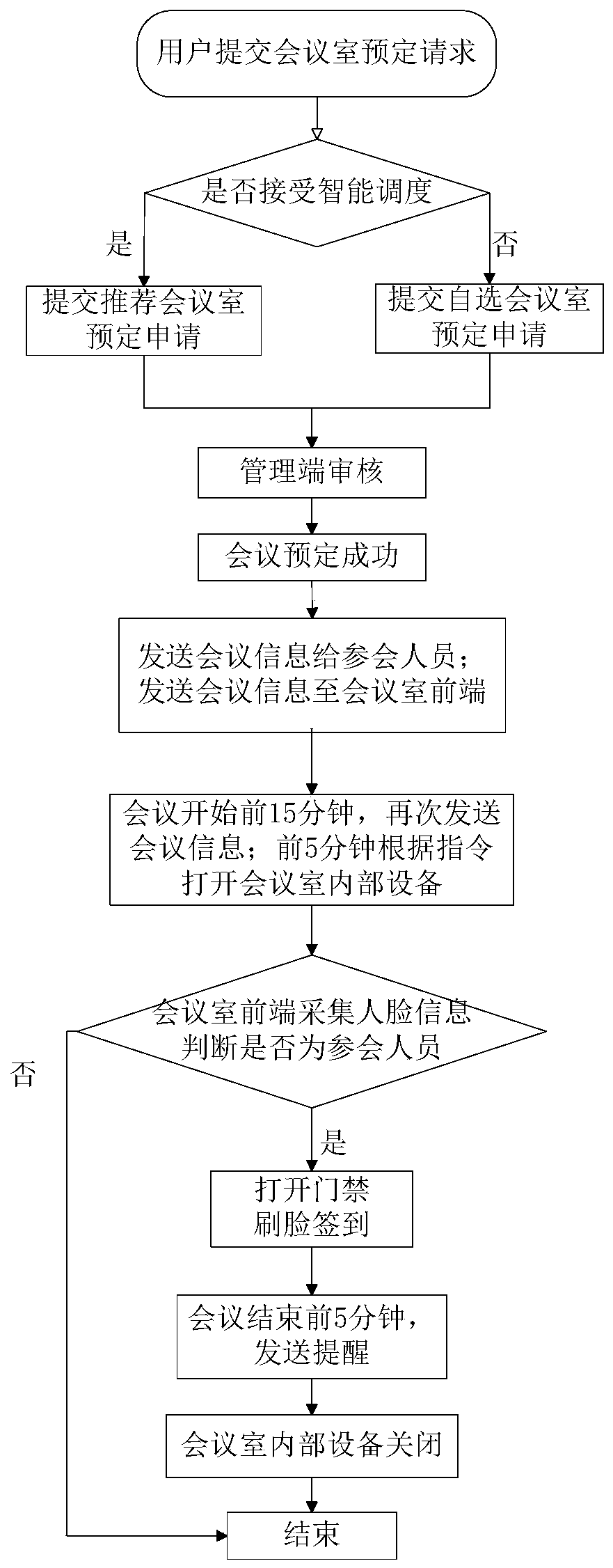
Conference room management system and method based on intelligent scheduling algorithm
ActiveCN110310089ARealize intelligent managementReduce wasteReservationsOffice automationThe InternetHuman–computer interaction
The invention discloses an intelligent conference room management system and method. The system comprises a user end, a management end, a front end and a control unit. The user end provides the conference room real-time reservation and query functions; an intelligent scheduling module in the management end intelligently matches an optimal conference room with the conference room requirements submitted by the user based on a BP neural network and a GA algorithm, and returns the predetermined information to the user through a cloud platform; the conference room front end provides the conferencequery and reservation functions, meanwhile, collects the human face information and calls a human face recognition module of a PCA algorithm based on feature weighting for human face recognition, so that the functions of conference face swiping sign-in and access control are achieved. Meanwhile the Internet of Things equipment in a conference room are turned on according to a control instruction.According to the present invention, the conference room resources are efficiently utilized, and the function of avoiding the conference room conflicts is achieved.
Owner:HOHAI UNIV CHANGZHOU
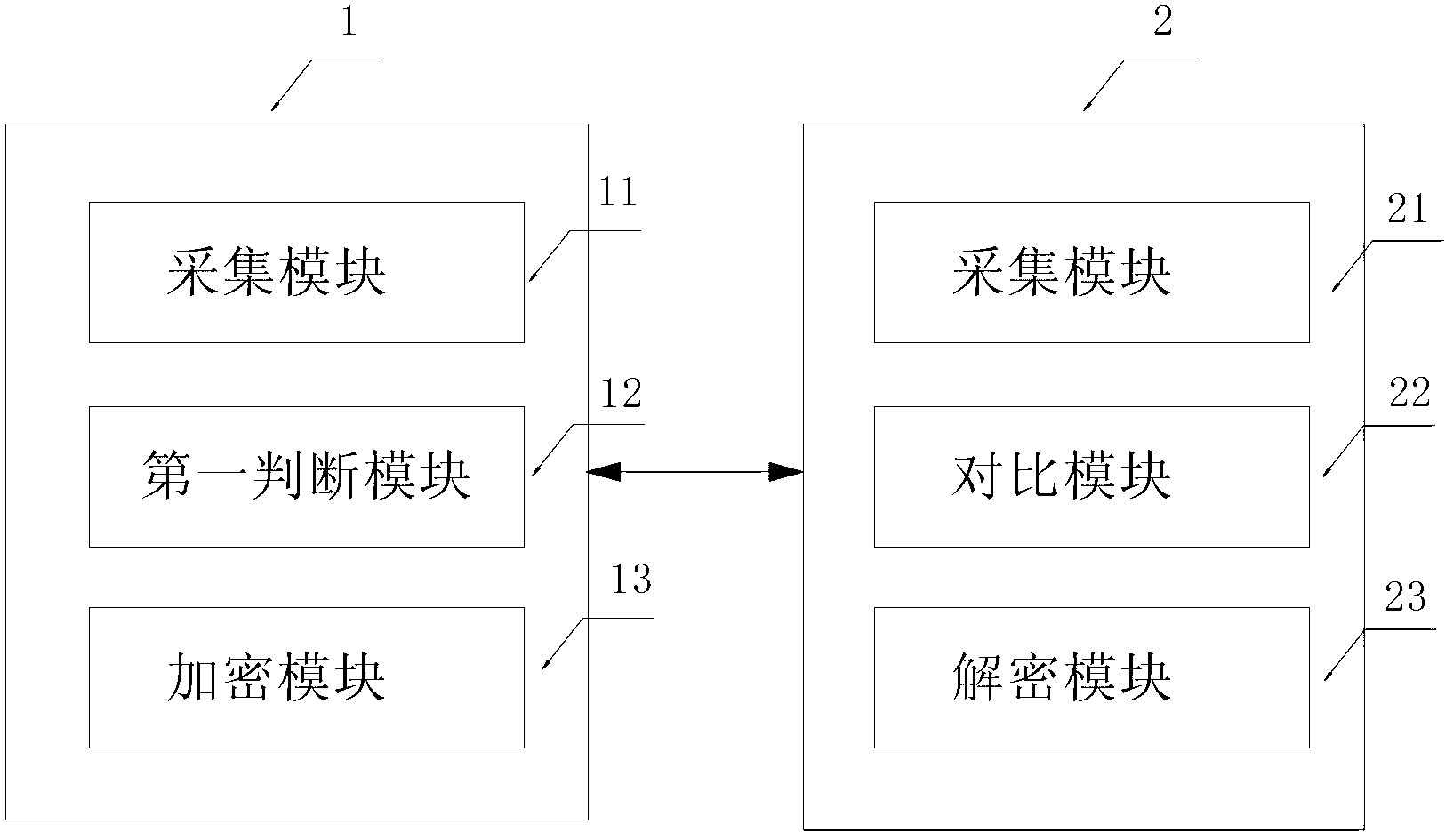
System and method for fingerprint encryption and decryption
InactiveCN103200009AEnsure communication securityCircumstances to prevent decryptionUser identity/authority verificationTime rangePassword
A system for fingerprint encryption and decryption comprises a sending terminal and a receiving terminal, wherein the sending terminal and the receiving terminal are provided with fingerprint identifying devices. The sending terminal comprises a collection module used for collecting user fingerprints and recording time when the user fingerprints are collected, the sending terminal is used for judging whether continuous time of collection of the user fingerprints exceeds a preset first time range, if yes, a first judging module of a preset encryption option, and an encryption module are called out, and the encryption module is used for encrypting information or files or folders needing to be sent to the receiving terminal by means of collected user fingerprints through the encryption option. The receiving terminal comprises a collection module, a comparing module and a decryption module, wherein the collection module is used for collecting the user fingerprints, the comparing module is used for comparing prestored user fingerprints and the user fingerprints collected by the collection module in real time, and the decryption module is used for decryption. The system effectively utilizes fingerprints to encrypt communication data, and can avoid the facts that memorization of passwords causes using inconvenience, or the passwords are stolen to cause problems of information safety and the like.
Owner:DISKON INFORMATION SCI & TECH SHANGHAI
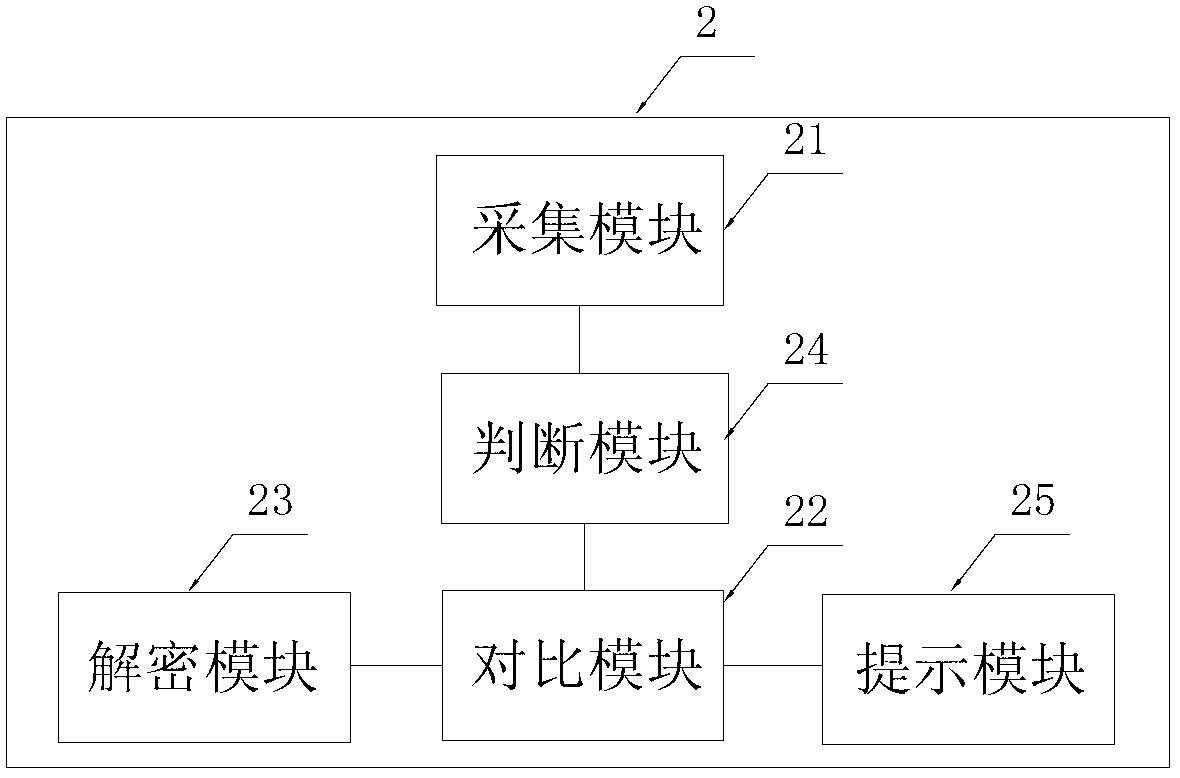
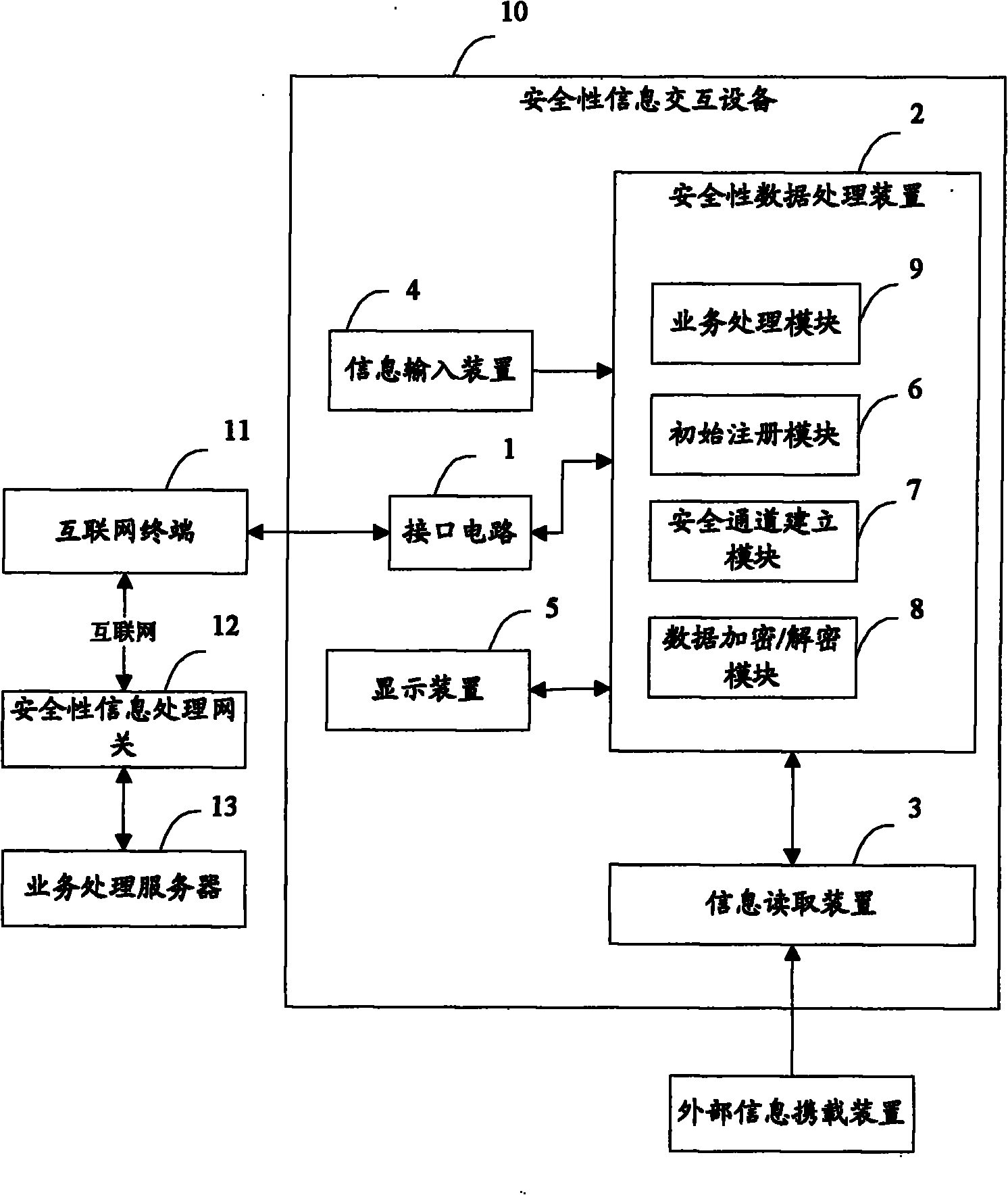
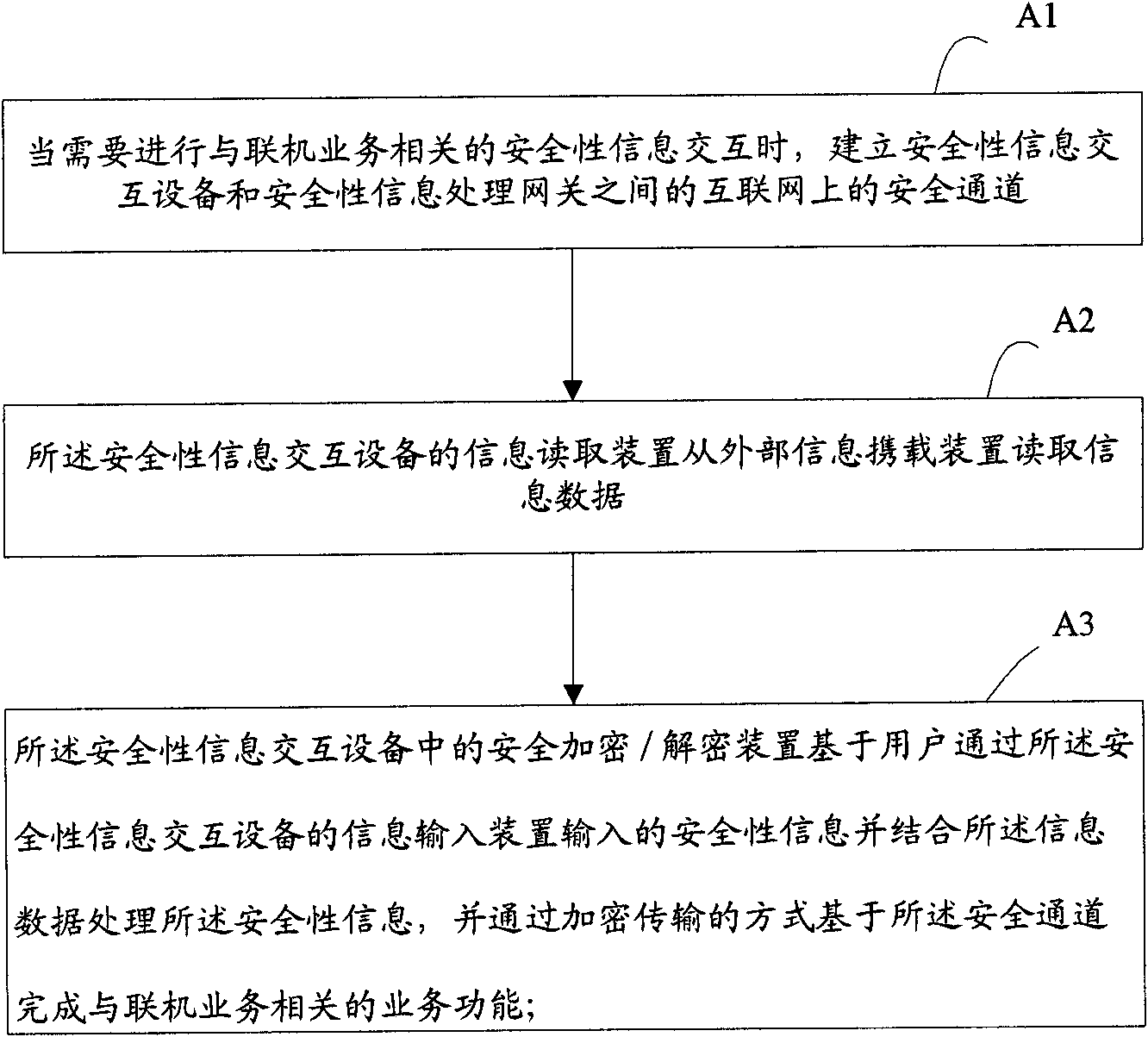
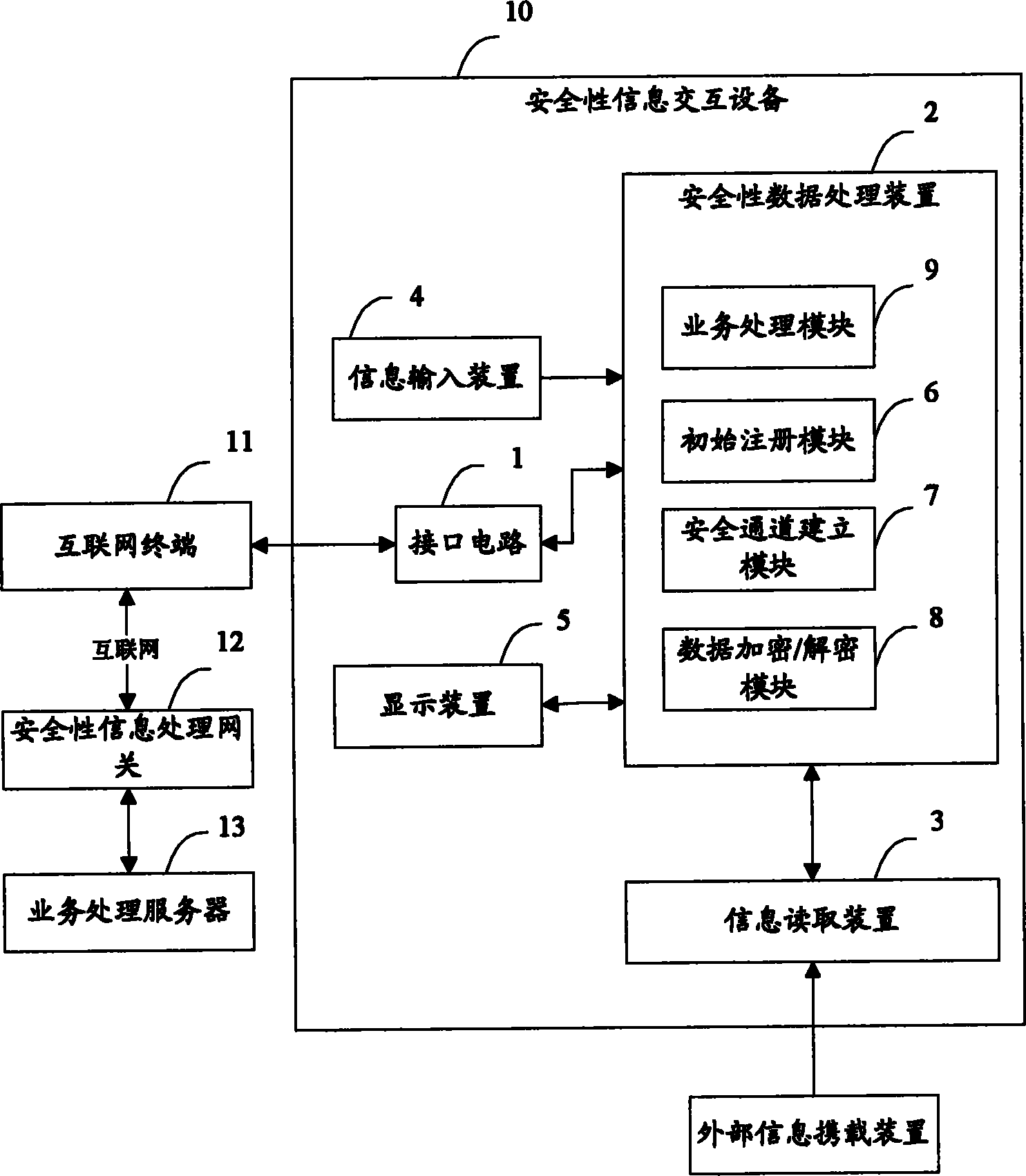
Internet-based system and method for security information interaction
ActiveCN102694781AIncrease flexibilityImprove security and confidentialityPayment architectureDigital data authenticationInteraction deviceSecurity information
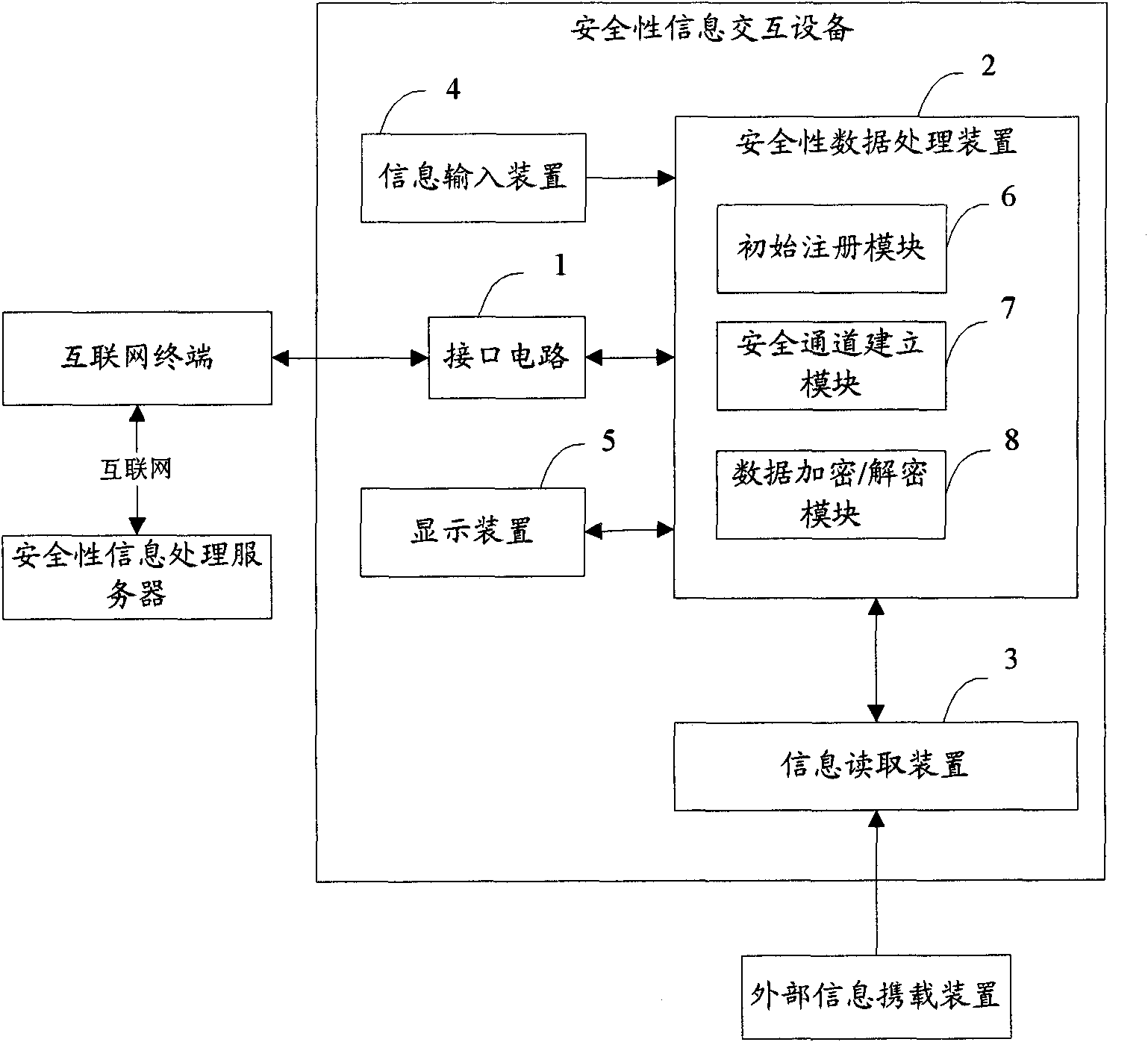
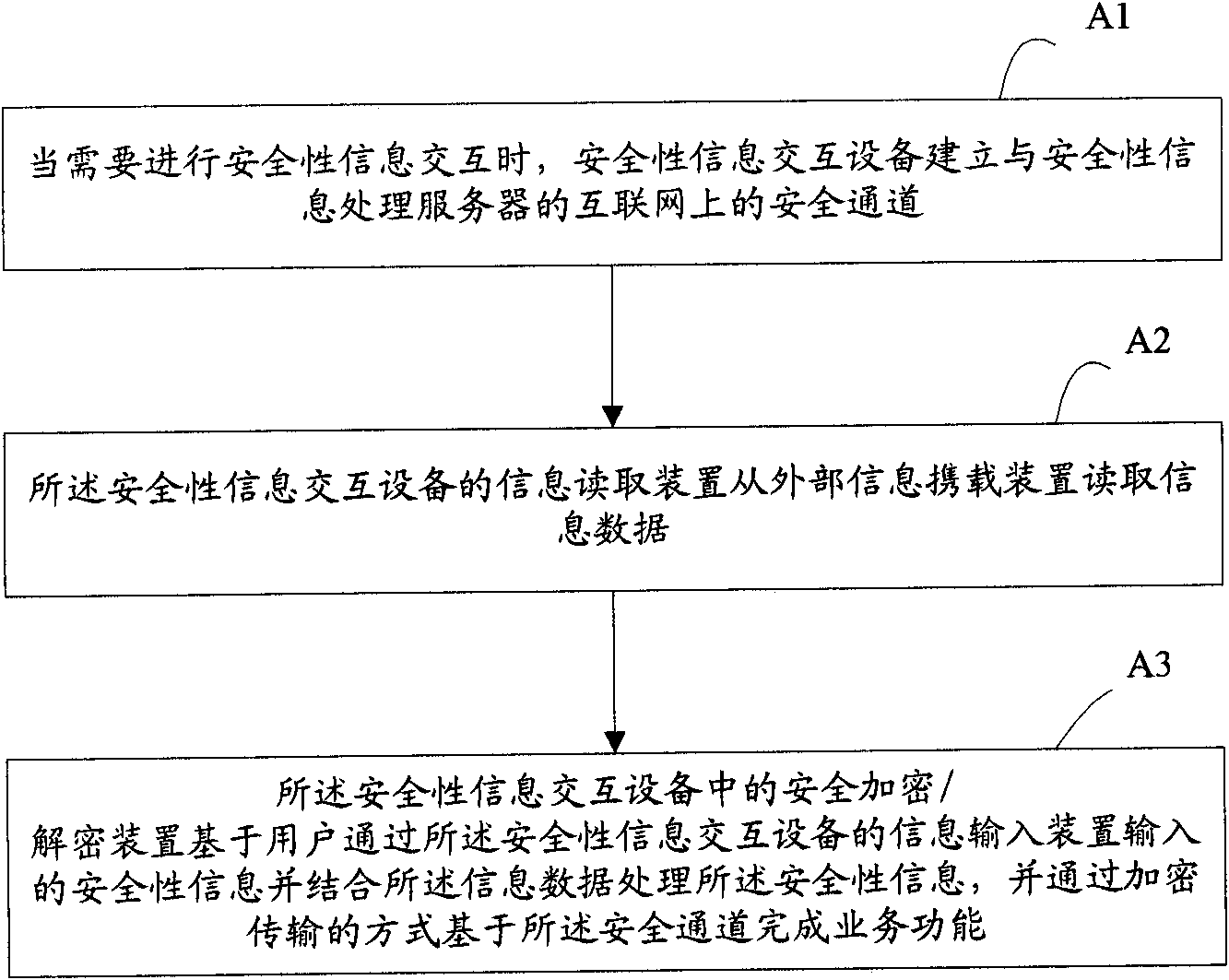
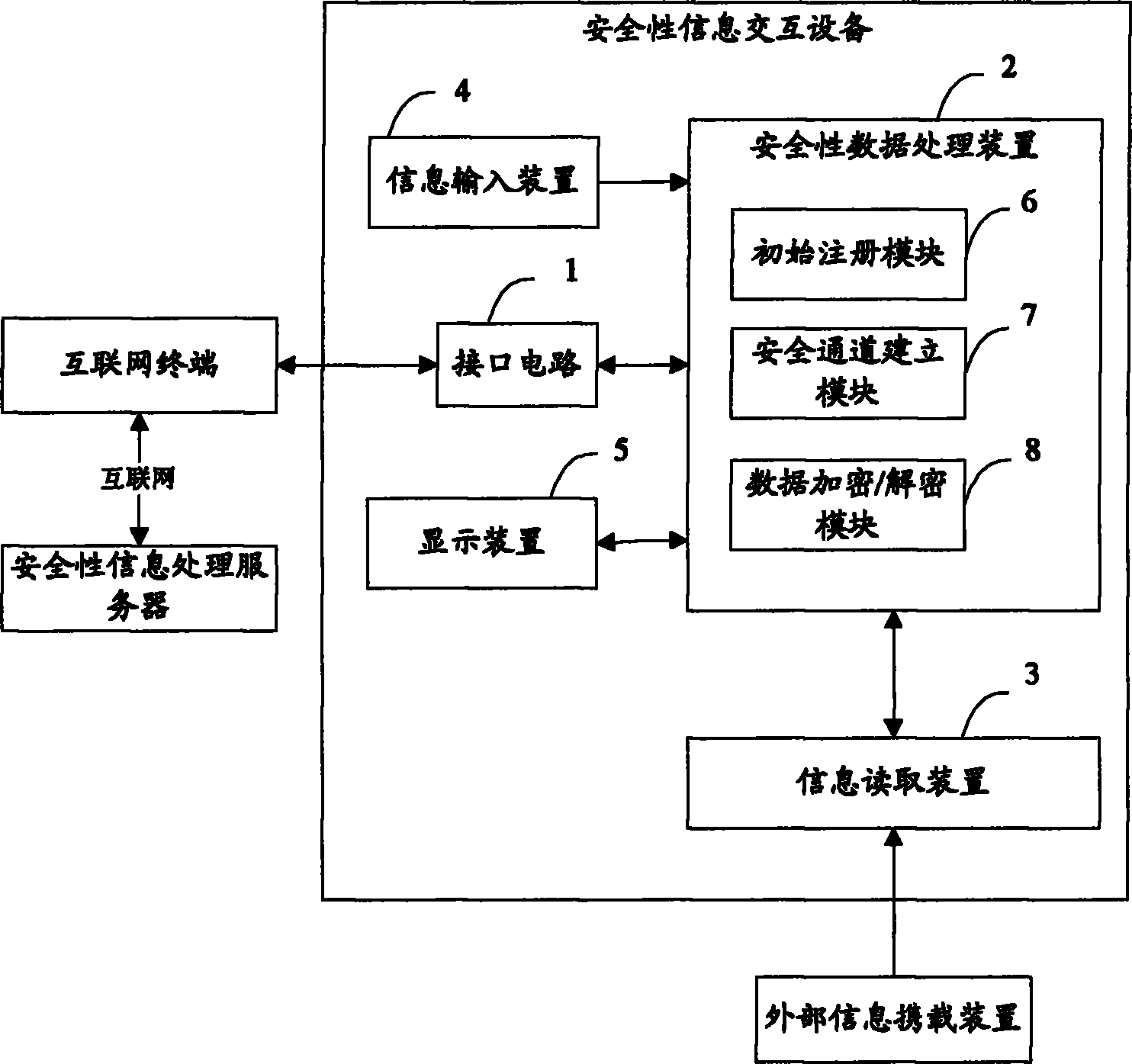
The invention brings forward an internet-based system and method for security information interaction. The security information interaction system comprises a security information interaction device, which is used for obtaining security information input by a user, reading information data from an external information carrying device and establishing a secure channel to a security information processing gateway by an internet terminal, thereby completing a server function. And the security information interaction device can complete the service function without need of on-line processing. According to the internet-based system and method for security information interaction, flexibility and efficiency of an information processing system as well as operation load balancing can be improved; and security of the information processing system can be enhanced.
Owner:CHINA UNIONPAY
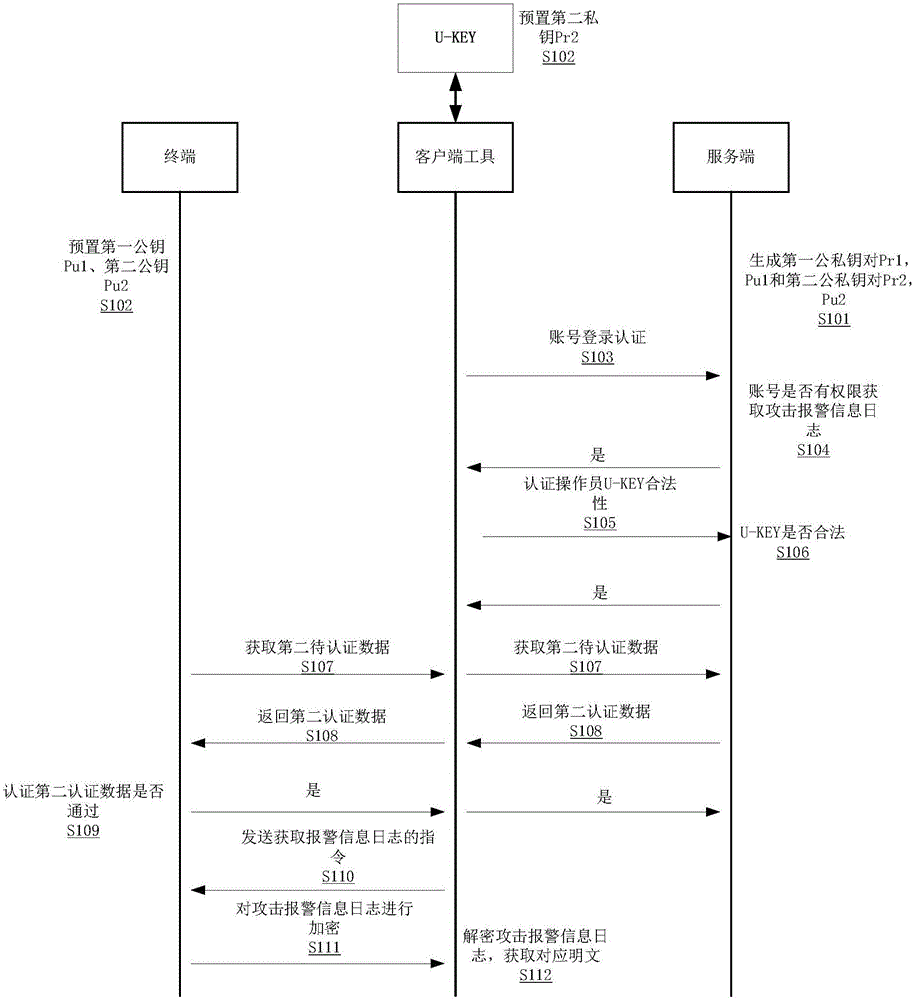
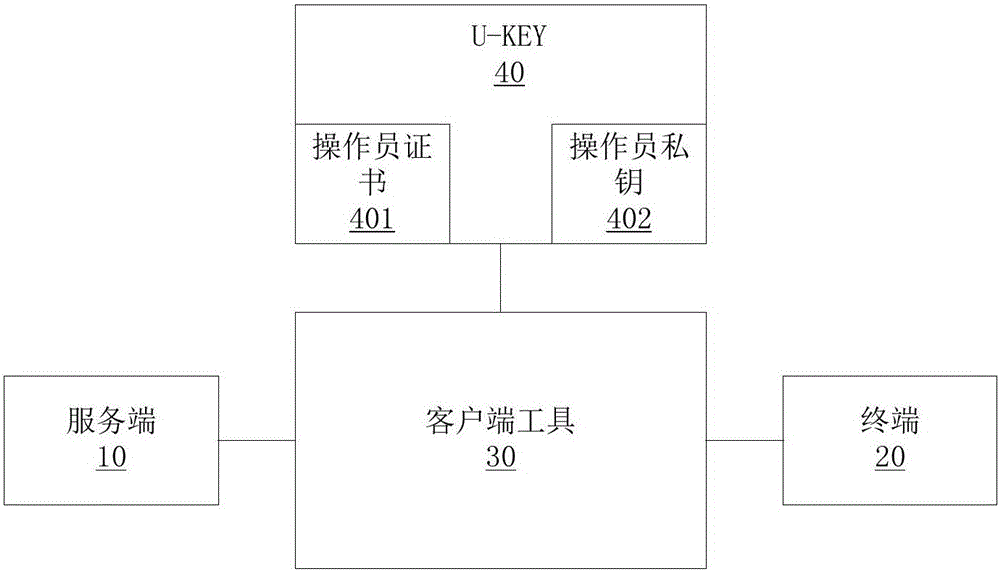
Method and system for authorizing to acquire terminal attack alarming information log
ActiveCN106372531AImprove security and confidentialityGuaranteed legalityDigital data protectionDigital data authenticationComputer terminalClient-side
The invention provides a method and a system for authorizing to acquire a terminal attack alarming information log and belongs to the technical field of communication. The method for authorizing to acquire the terminal attack alarming information log comprises the following steps: after acquiring an authentication account of an attack alarming information log authority by a server, authenticating the legitimacy of a client tool by the server; after the legitimacy passes, sending second data to be authenticated to the client tool by a terminal and sending the data to the server by the client tool; if the authentication of the server on the second data to be authenticated passes, encrypting the second data to be authenticated to generate second authentication data and sending the second authentication data to the terminal; if the authentication of the terminal on the second authentication data passes, acquiring the attack alarming information log by the terminal and encrypting the attack alarming information log; and after encrypting, sending the attack alarming information log to the client tool. A whole process adopts double-factor authentication and ensures the safety; and an instruction of acquiring the terminal attack alarming information log by the terminal is a legal behavior approved by the client and the legitimacy of acquiring an operation instruction is ensured.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
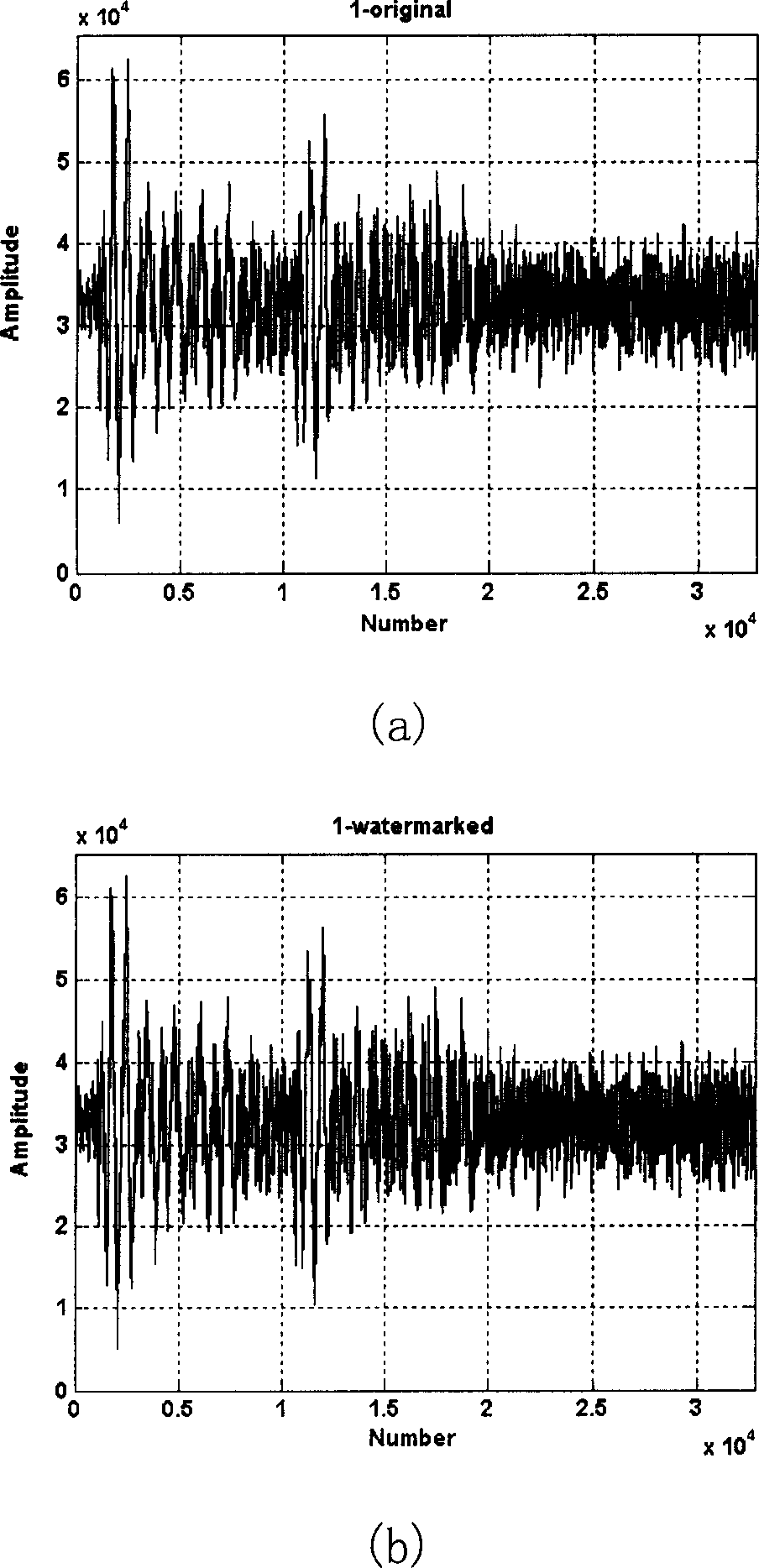
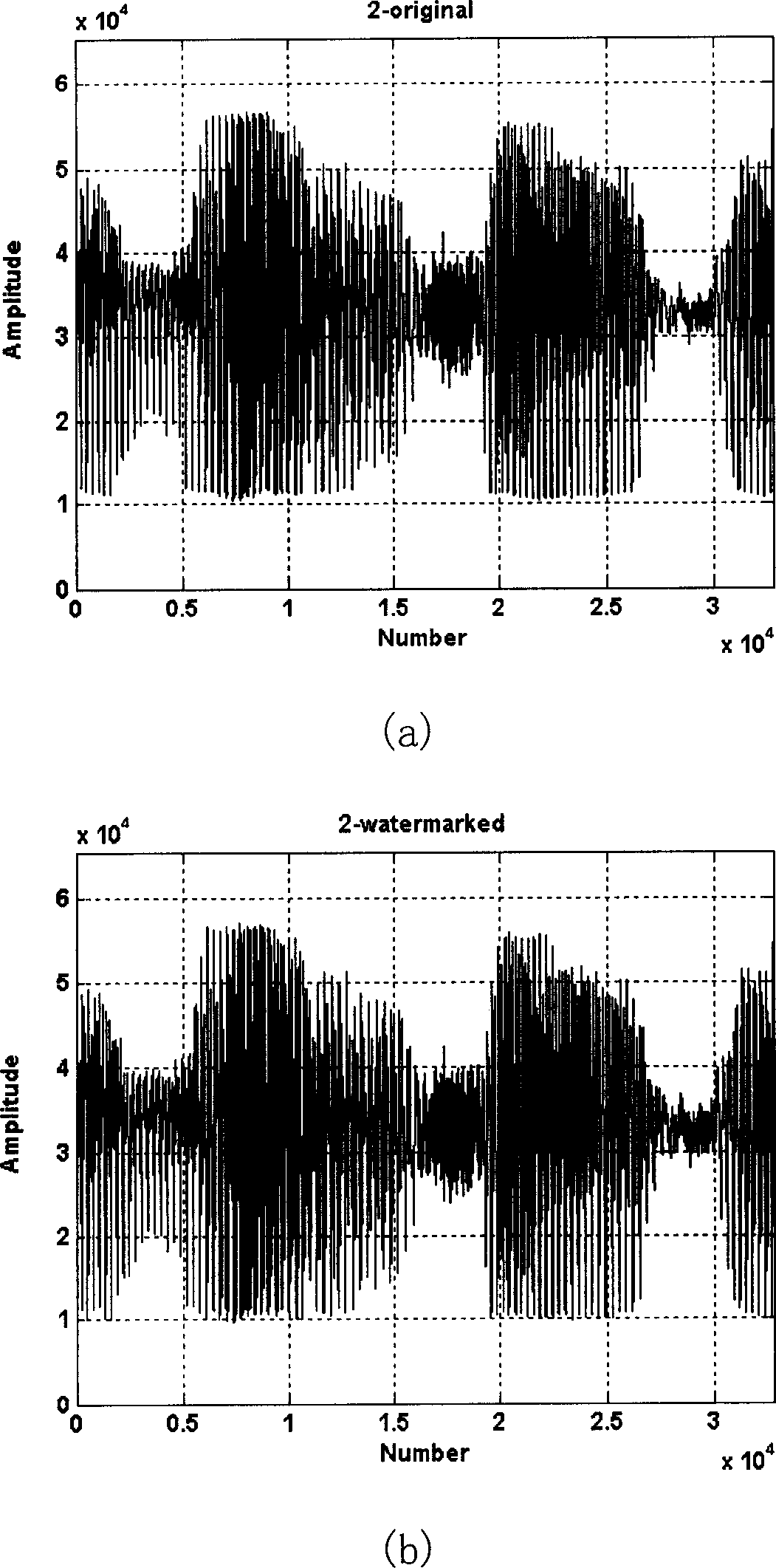
Non-uniform discrete Fourier transform based robust digital watermark method for audio
InactiveCN1808970AImprove performance against malicious attacksEffective copyright protectionProgram/content distribution protectionSecuring communicationWatermark methodIntermediate frequency
This invention discloses one robust audio digital water print method based on non-even dispersed Fourier conversion, which Combines robust audio water print needed conditions and no uniform discrete Fourier transform characteristics to get the middle frequency range at NDFT zone with imbedded water print and uses one rule on each section of audio signal to select one water print imbedded frequency points and coverts the frequency points and imbeds water print.
Owner:SOUTHWEST JIAOTONG UNIV
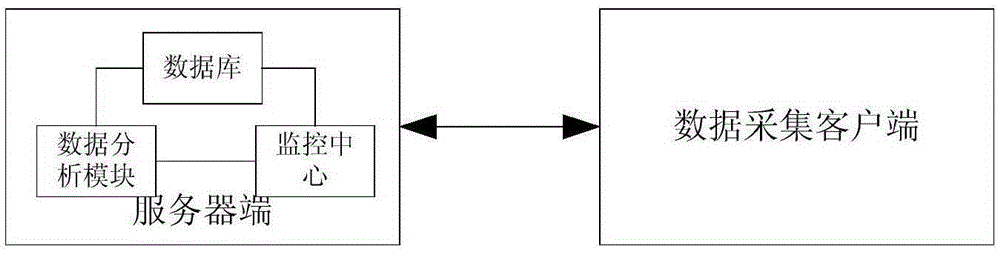
Mail detection and monitoring system
InactiveCN106656728AReduce duplication of investmentEnsure safetyData switching networksIp addressData acquisition
The invention discloses a mail detection and monitoring system. A data collection client is used for deciding whether to audit the computer of a user according to a mail address configured by the audit management; and if so, an IP address of the computer terminal of the user is obtained, the IP address information of the computer terminal of the user is transmitted to a monitoring center of a server side after association with a mail message through a Webmail system, the monitoring center establishes a log file with the mail message associated with the IP address information and stores the log information, audit log information is transmitted to a database through log real-time acquisition, the keyword and feature threshold are set in a data analysis module, the data in the database are retrieved through the data analysis module for keyword and feature threshold analysis, and a mail message result is displayed through a web browser. The invention avoids the problem of the frequent occurrence of safety accidents to existing safety products, and also reduces repeated investment of the user.
Owner:STATE GRID CORP OF CHINA +1
Communication system and method for improving security performance of physical layer by energy station
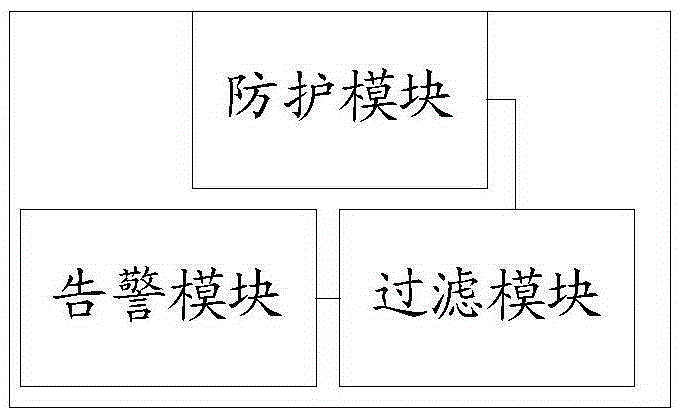
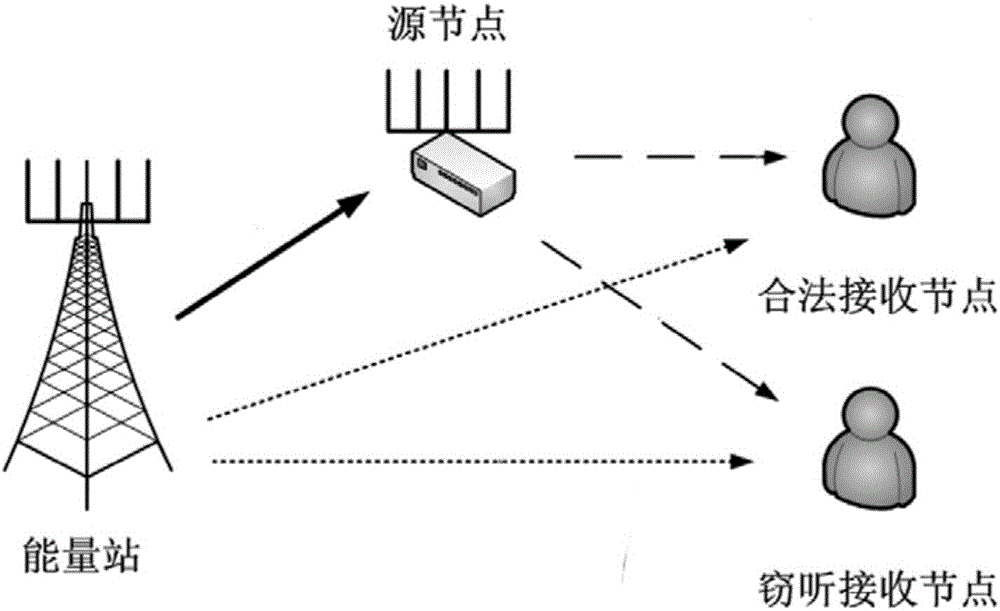
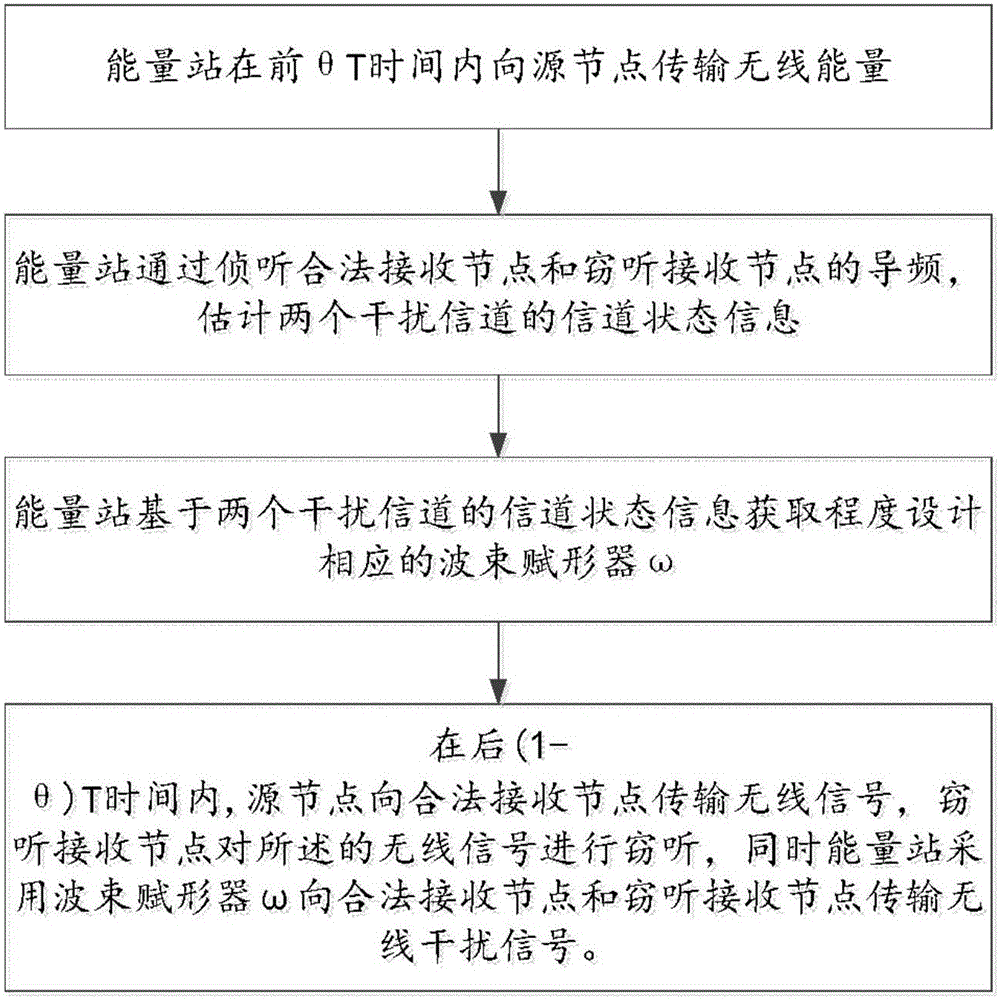
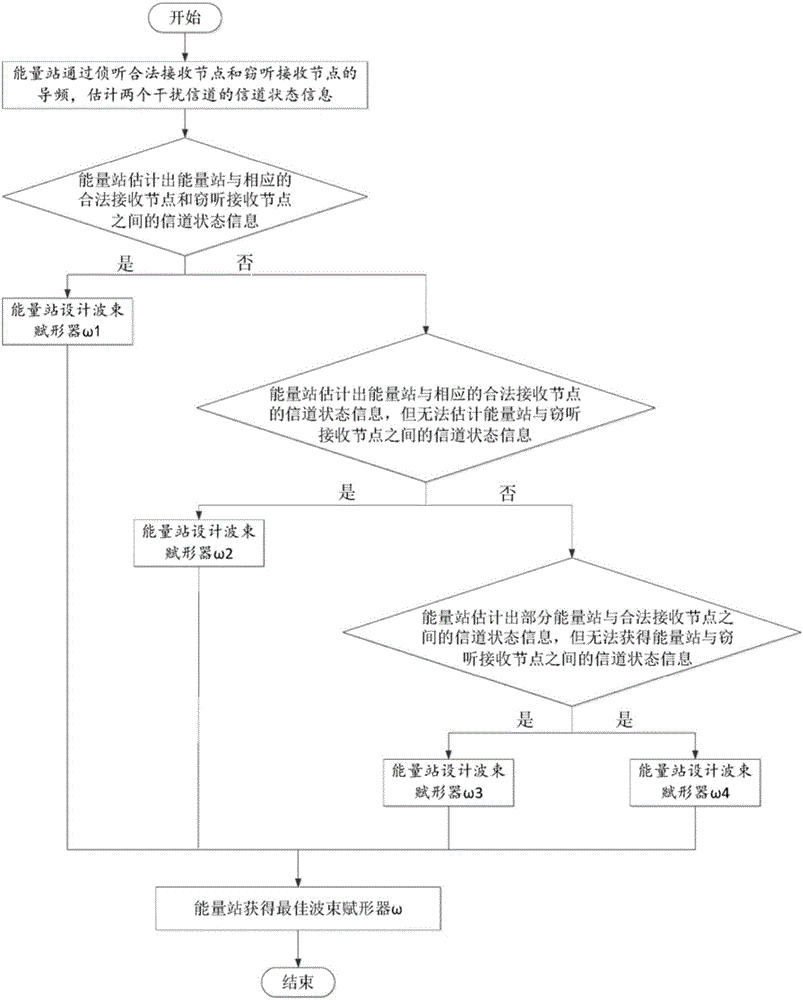
ActiveCN105744516AImprove battery lifeImprove security and confidentialitySpatial transmit diversitySecurity arrangementCommunications systemPhysical layer
The invention relates to a communication system and method for improving the security performance of a physical layer by an energy station. The communication system comprises a source node, a legitimate receiving node, an eavesdropping receiving node and the energy station; the energy station is equipped with N antennas, the source node is equipped with M antennas, and the legitimate receiving node and the eavesdropping receiving node are equipped with a single antenna respectively; the energy station and the source node constitute a wireless energy transmission subsystem; the source node and the legitimate receiving node constitute a wireless signal transmission subsystem; the energy station, the legitimate receiving node and the eavesdropping receiving node constitute a wireless interference signal transmission subsystem; and the energy station is provided with a beamformer w. The invention further relates to a method for improving the security performance of the physical layer by the energy station. The energy station can not only serve as a terminal to provide energy for the source node, but also can serve as an interference source and transmit a wireless interference signal, and the wireless interference signal generates relatively large interference to the eavesdropping receiving node, so the security performance of the physical layer is greatly improved.
Owner:ZHEJIANG UNIV
Spin lock and key thereof
InactiveCN1963122AImprove security and confidentialityAnti-dialingKeysCylinder locksEngineeringSpin lock
The spiral lock comprises a body and a core within the body, featuring on the spiral key hole in the core and the spirally arranged hoodle holes on the said core, with the bottom of the spiral key hole connected with the hoodle holes which correspond to the holes on the body. A key, with its handle equipped with spiral teeth matched with the spiral key hole, is meant to match with the said spiral lock. The invention adds security with the effects of anti-poking and anti-vibration.
Owner:中山市明丰五金制品有限公司
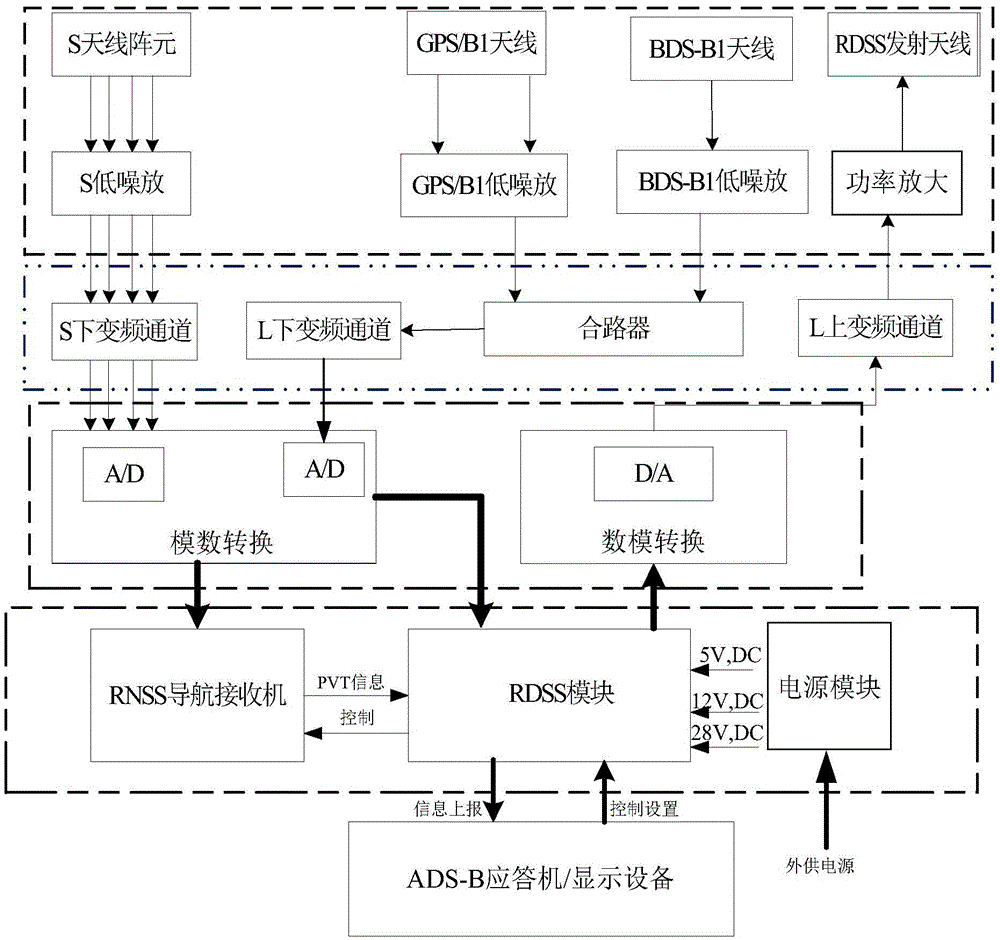
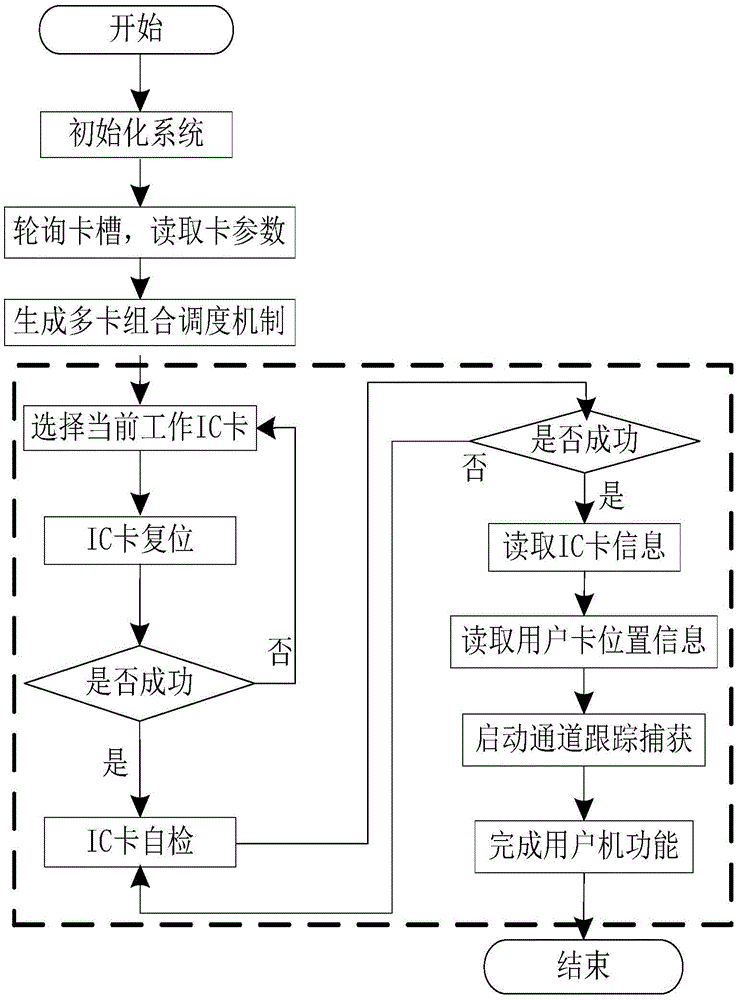
Beidou dual-mode terminal equipment based on navigation ADS-B application and control method thereof
ActiveCN105629271ASolve the current situation of adopting GPSSimple structureSatellite radio beaconingShort Message ServiceConfidentiality
The invention provides Beidou dual-mode terminal equipment based on a navigation ADS-B application. The Beidou dual-mode terminal equipment comprises a baseband processing unit, a digital-to-analog processing unit and an antenna unit. The key resides in that the baseband processing unit comprises an RNSS module and an RDSS module. The mode of combination of the RDSS module and the RNSS module is adopted, position information of an aircraft is measured by utilizing the RNSS module and then position reporting is performed to the air traffic control department by utilizing the inbound short message service of the RDSS module. The RDSS module adopts the basic principle of an integrated scheduling mechanism of multiple IC user cards and is divided into two modes of a static mode and a dynamic mode so that the use requirements of users under different scenes can be flexibly supported, the situation that the positioning data source of an ADS-B system uses the GPS for a long time can be solved, the Beidou resources of our country can be fully utilized and security and confidentiality can be enhanced.
Owner:重庆九洲星熠导航设备有限公司
Biological feature information management method and system
InactiveCN106657056AImprove accuracyImprove security and confidentialityTransmissionAcquiring/reconising fingerprints/palmprintsManagement systemLiving body
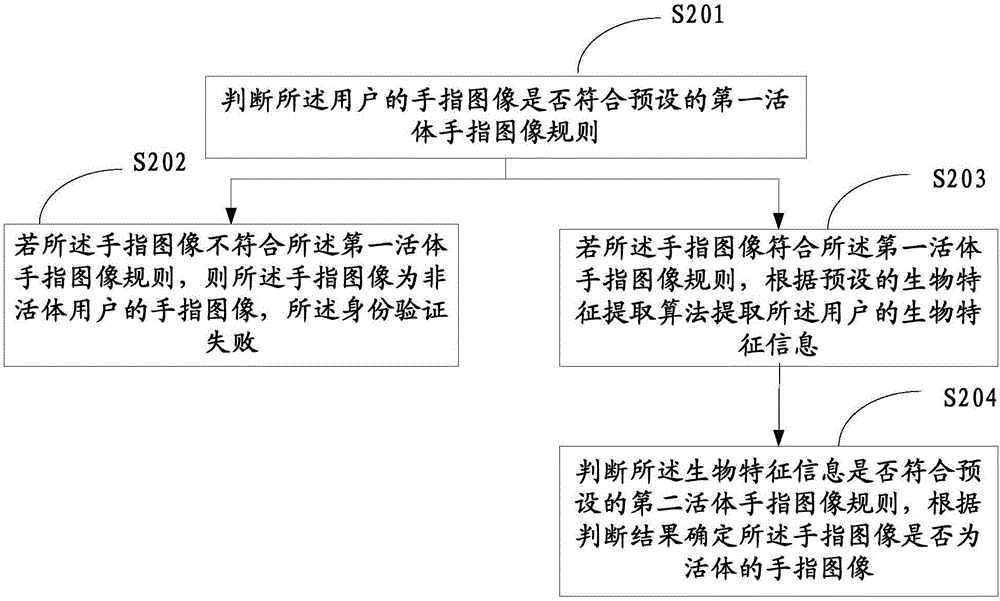
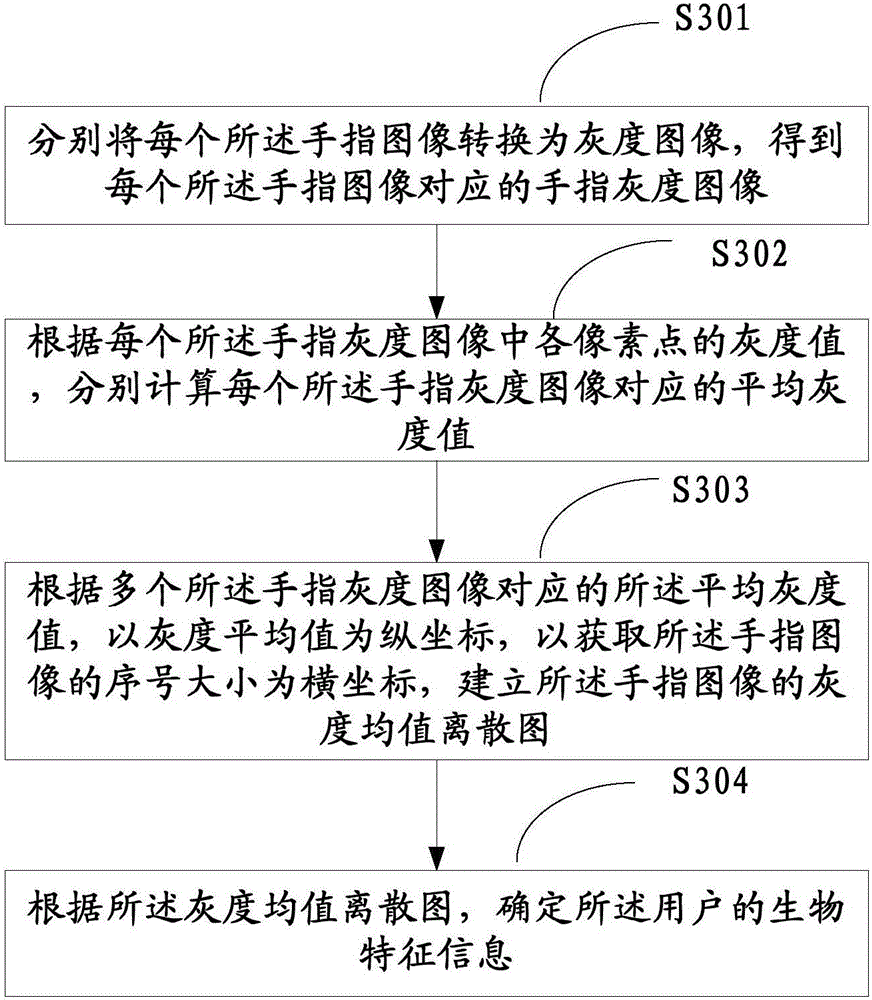
The invention relates to a biological feature information management method and system. The method comprises the steps of obtaining a fingerprint image which is input by a user and is used for carrying out identity authentication; identifying whether the user is a legal user or not according to the fingerprint image and a preset fingerprint template; if the user is the legal user, collecting a finger image of the user according to a preset sampling frequency; judging whether the finger image is the finger image of a living body or not according to a preset living body detection rule; and determining whether the identity authentication is successful or not according to a living body identification result. According to the embodiment of the method and the system, through collection of the fingerprint image, whether the user is the legal user or not is identified, through collection of the finger image of the user, whether a finger of the user carrying out press operation is a living body finger or not is determined, so the problem that an illegal user disguises as the legal user through utilization of disguise technologies such as fingerprint membrane and steals the biological feature information of the user is solved, and the security and confidentiality of the biological feature information management system are improved.
Owner:SHENZHEN CHIPSAILING TECH CO LTD
Three-channel carrier index differential chaos shift keying modem and method
ActiveCN109587090AImprove bit error rate performanceImprove security and confidentialityModulated-carrier systemsSecuring communication by chaotic signalsIndex mappingModem device
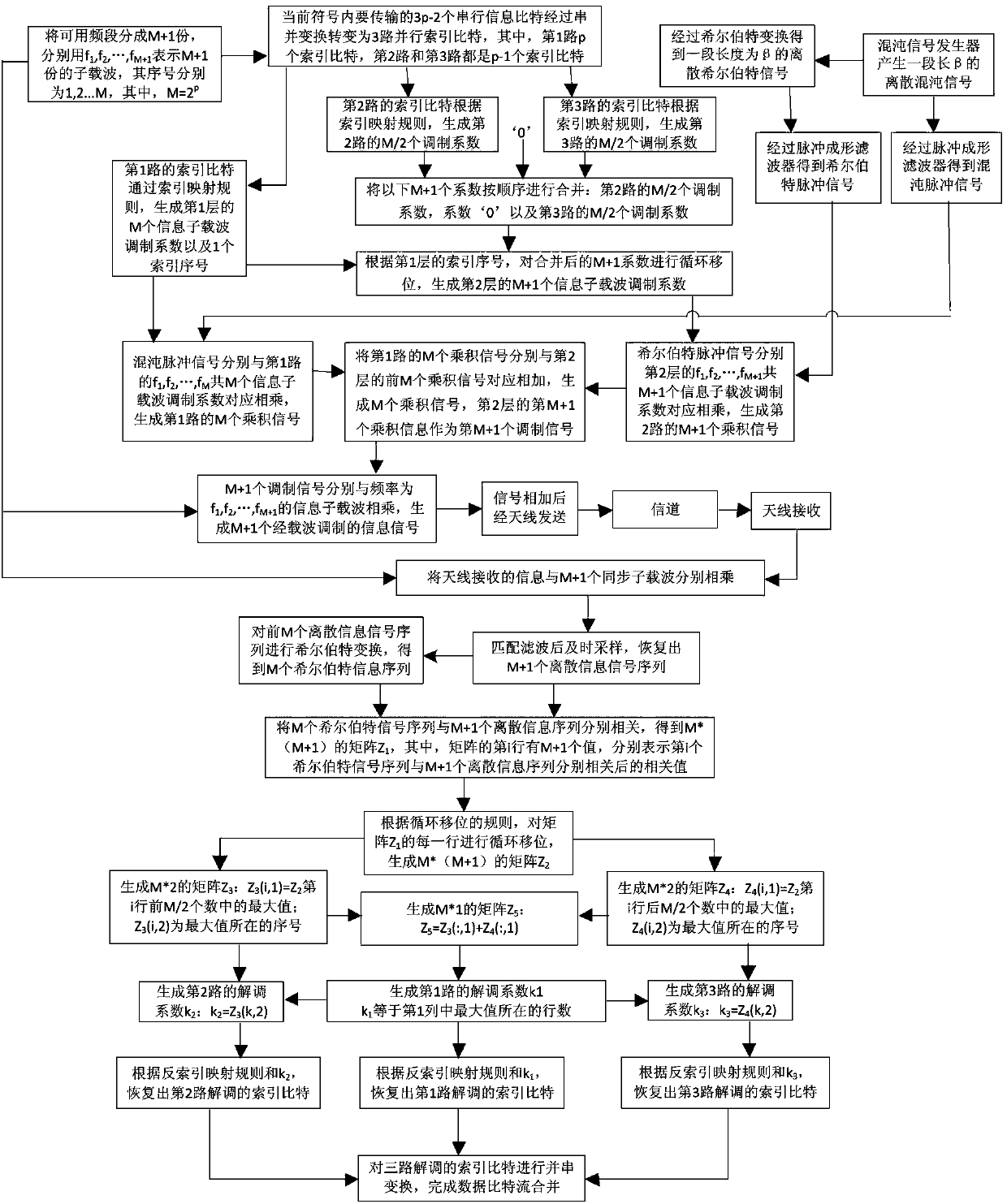
The invention discloses a three-channel carrier index differential chaos shift keying modem and method, which belong to the technical field of chaos communication. Three-channel index modulation is realized by two layers in an inter-channel mutual reference mode, the two layers of modulation are distinguished by chaotic signals and Hilbert signals which are mutually orthogonal, and the signals aremodulated and demodulated by using an index mapping rule and an anti-index mapping rule. On the premise of occupying the same frequency band, in comparison with the existing carrier index differential chaos shift keying system whose reference signals only serve as reference of information signals but do not carry any information, the information signals of each layer in the invention can also serve as reference signals for other layers in the case of information bit transmission, independent reference signals do not need to be transmitted additionally, and thus, a higher bit transmission rate, a higher spectrum utilization rate and better data security can be acquired, and the bit error rate can also be reduced.
Owner:NANJING UNIV OF POSTS & TELECOMM
Artificial intelligence Internet of Things charging valve and method
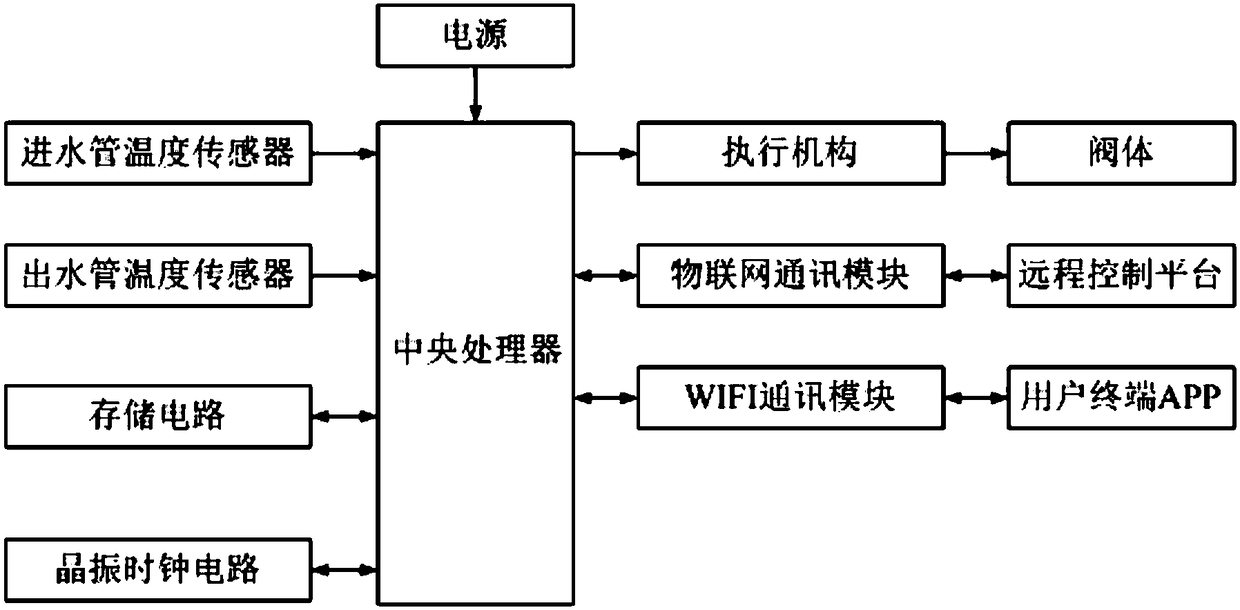
ActiveCN108280637ASolve charging difficultiesReduce labor intensityPayment architectureTransmissionPaymentEngineering
Artificial intelligence Internet of Things charging valve and method are disclosed and relate to an Internet of Things device adopting two-dimensional codes, Alipay and WeChat for charging. The artificial intelligence Internet of Things charging valve and method help solve the problem that a conventional heat metering method and a conventional payment method are not flexible and cannot meet the needs of people. The artificial intelligence Internet of Things charging valve includes a central processor, a water inlet pipe temperature sensor, a water return pipe temperature sensor, a storage circuit, an actuator, a valve body and a WIFI communication module. The device adopts all-electronic devices and is long in service life, simple in structure and high in flexibility and energy conservation performance. The guiding significance of the the artificial intelligence Internet of Things charging valve of the present invention is not only about facilitating charging operation, but also aboutencouraging users to save energy and reduce emissions. The artificial intelligence Internet of Things charging valve and method disclosed in the invention are wide in range of practical applications,simple in structure, and high in flexibility and compileability.
Owner:玉环浩胜电子科技有限公司
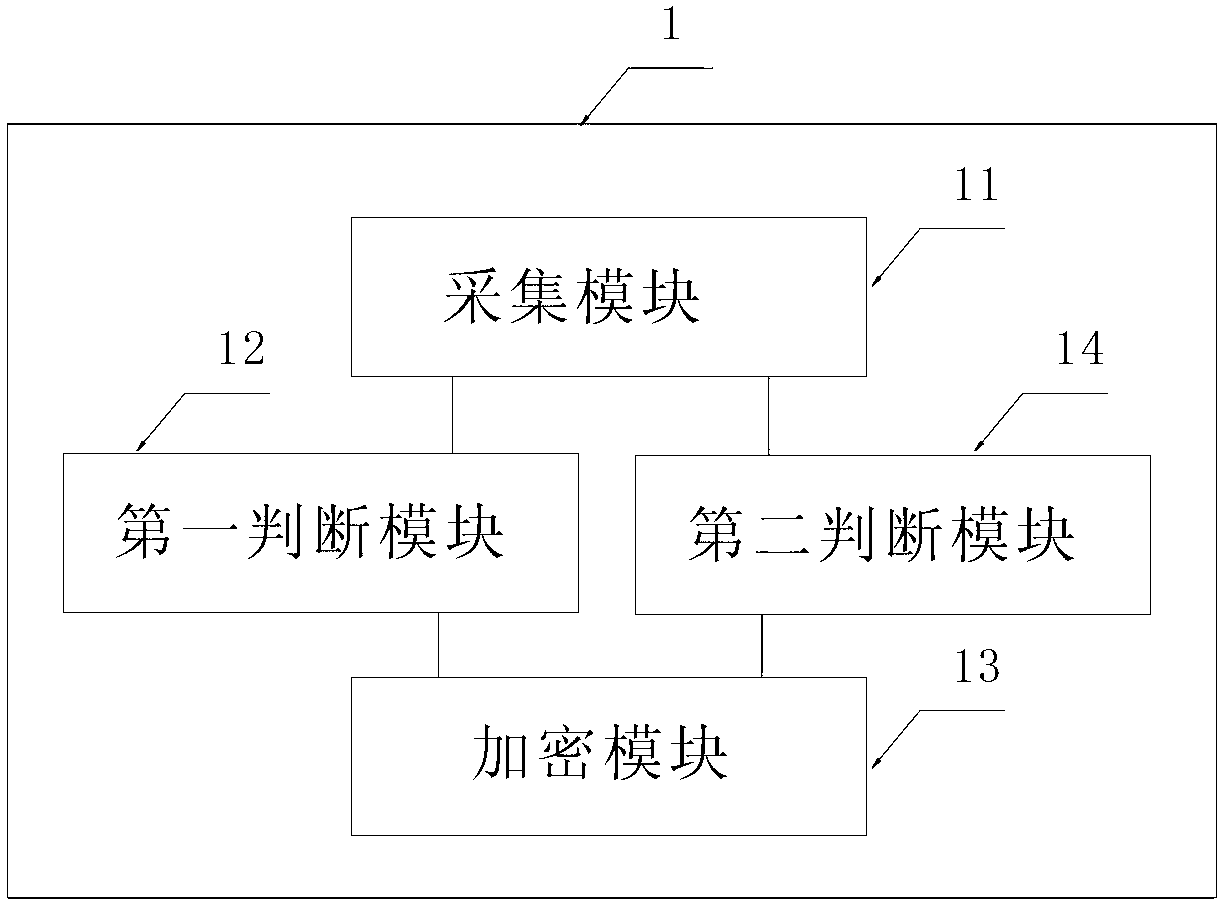
Internet-based device and method for security information interaction
ActiveCN102694782AIncrease flexibilityImprove security and confidentialityWeb data retrievalUser identity/authority verificationInteraction deviceInterface circuits
The invention brings forwards an internet-based device and method for security information interaction. The security information interaction device comprises: an interface circuit, which is used for connecting the security information interaction device to an internet terminal; an information input device, which is used for inputting security information by a user; a secure encryption / decryption device, which is used for storing and processing the security information; and an information reading device, which is used for reading information data from an external information carrying device. The secure encryption / decryption device carries out processing on the security information by combining the information data and carries out interaction with a security information processing server, so that a service function is completed at a secure channel. According to the internet-based device and method for security information interaction provided by the invention, flexibility and efficiency of an information processing system are improved; and security of the information processing system is enhanced and new application of an external information carrying device in an open network environment is extended.
Owner:CHINA UNIONPAY
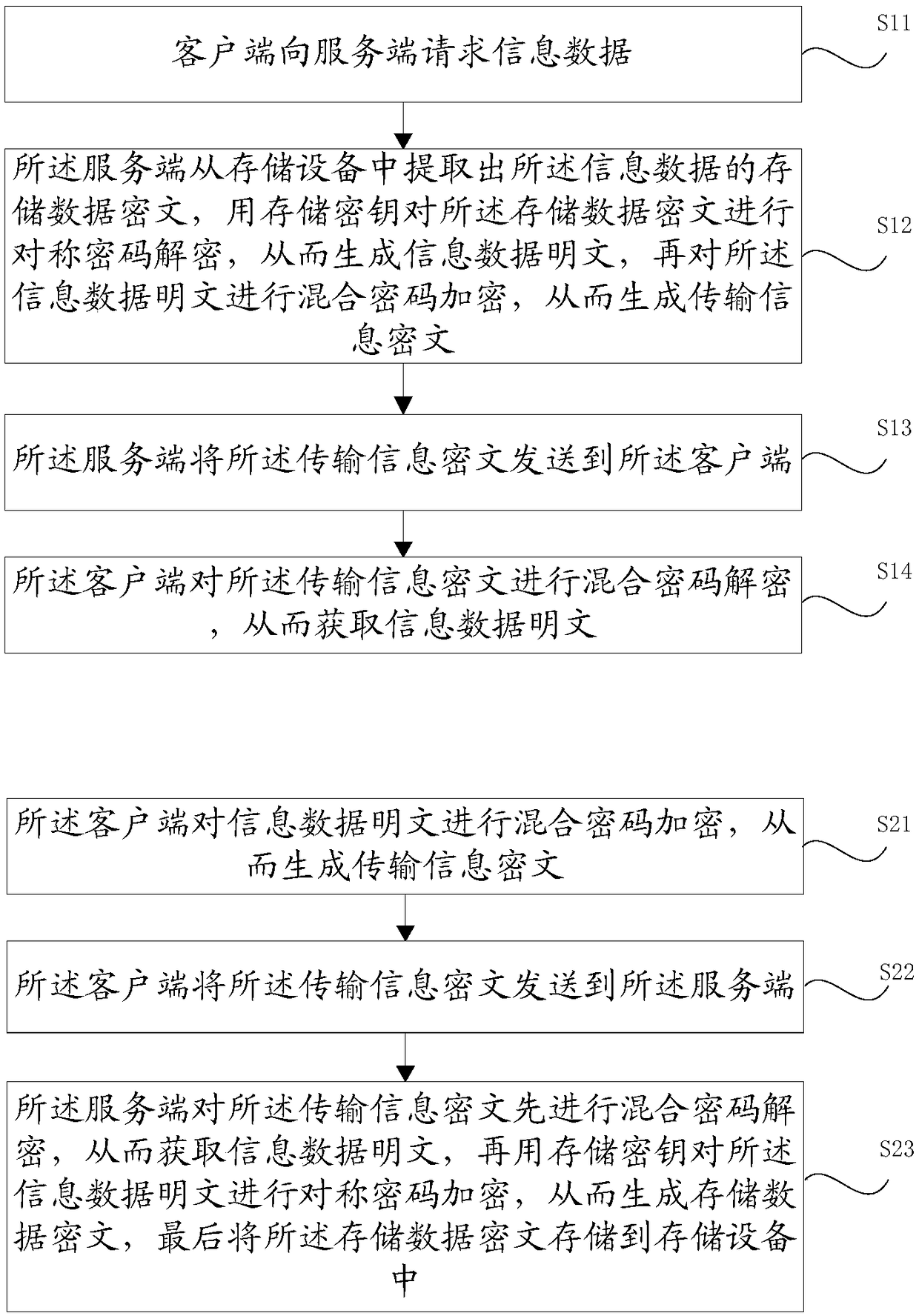
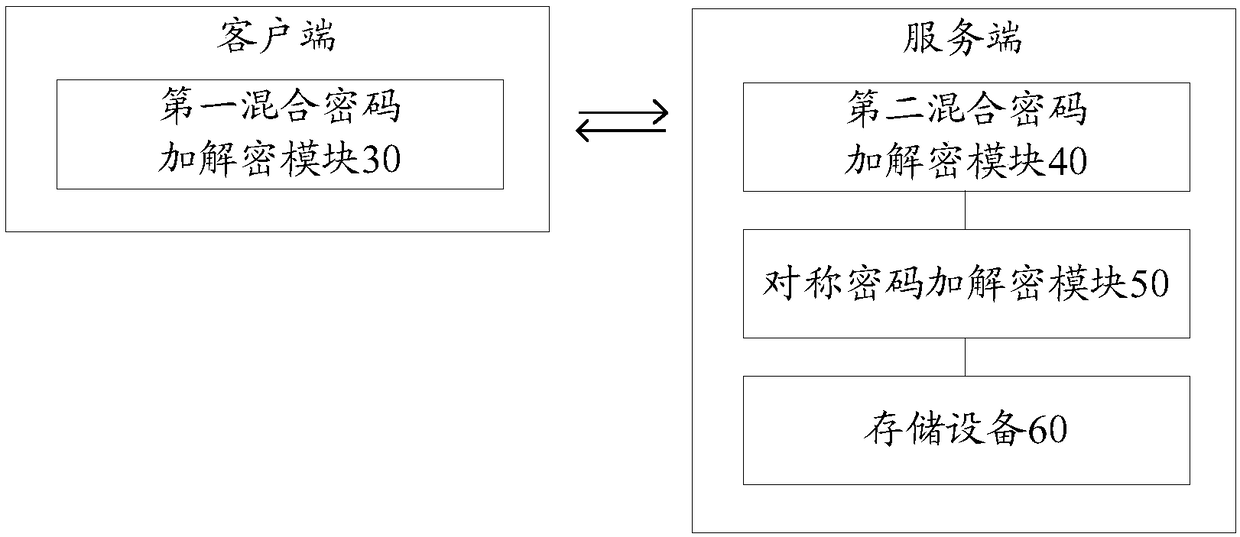
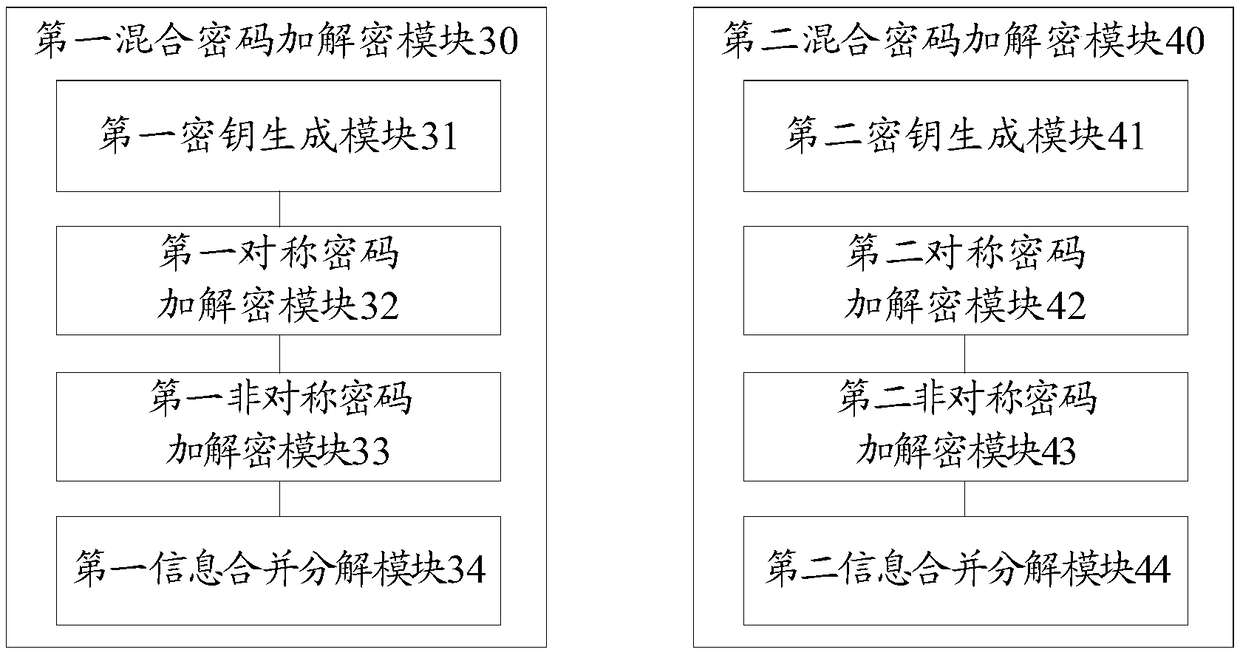
Network data information protection method and device
The embodiment of the invention provides a network information data protection method and a network information data protection device based on a password technology. When information data is transmitting, a mixed password technology is used; when the information data is storing, a symmetric password technology is used, a storage area can be divided into blocks, and when in storage, a storage keycorresponding to the block is used for encrypting; an address converting table is set, and an actual information storage address is provided to the outside after conversion; and in addition, the information with different information sensitive grades (such as security levels) is stored by areas, and the information sensitive grades are corresponding to information reading permissions of users. According to the information data protection method and device provided by the invention, the active demands on information security protection in data sets in internal informatization applications of party and government offices and enterprise and public institutions can be met, and data and information security and secrecy under application modes such as virtualization, big data, cloud storage andapplication system informatization can be effectively ensured.
Owner:刘喆
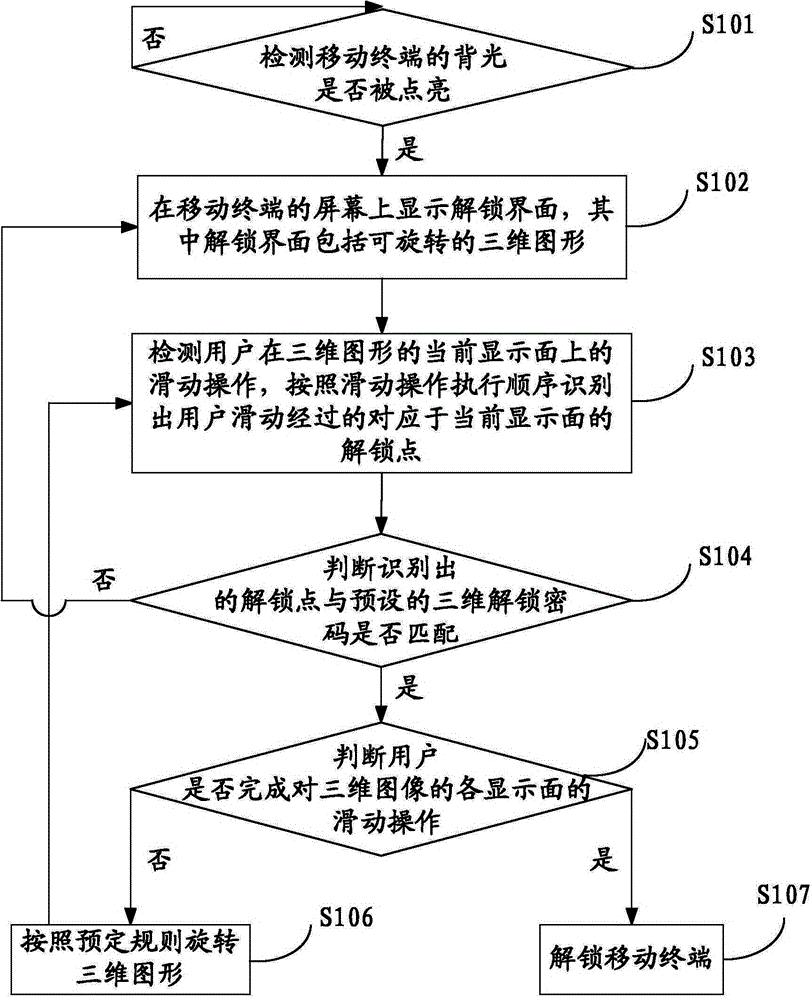
Unlocking method based on mobile terminal and mobile terminal
InactiveCN104991712AEasy to unlockImprove security and confidentialityDigital data authenticationInput/output processes for data processingConfidentialityGraphics
The invention discloses an unlocking method based on a mobile terminal and the mobile terminal. The method comprises that an unlocking interface is displayed on a screen of the mobile terminal, wherein the unlocking interface comprises a rotatable three-dimensional figure; a user's slide operation on the current display interface of the three-dimensional figure is detected, and unlocking points which are passed by the user's slide and corresponding to the current display interface are recognized according to an execution sequence of the slide operation; whether the recognized unlocking points are matched with a preset three-dimensional unlocking password is judged; and if the recognized unlocking points are matched with the preset three-dimensional unlocking password, the three-dimensional figure will be rotated and above operations are repeated until the user completes the slide operations of all the display interfaces of the three-dimensional figure, and the mobile terminal is finally unlocked. By the manner, the mobile terminal is unlocked easily and quickly, and safety and confidentiality of unlocking are increased because the unlocking method provided by the invention is based on the three-dimensional figure.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
Voice outbound system
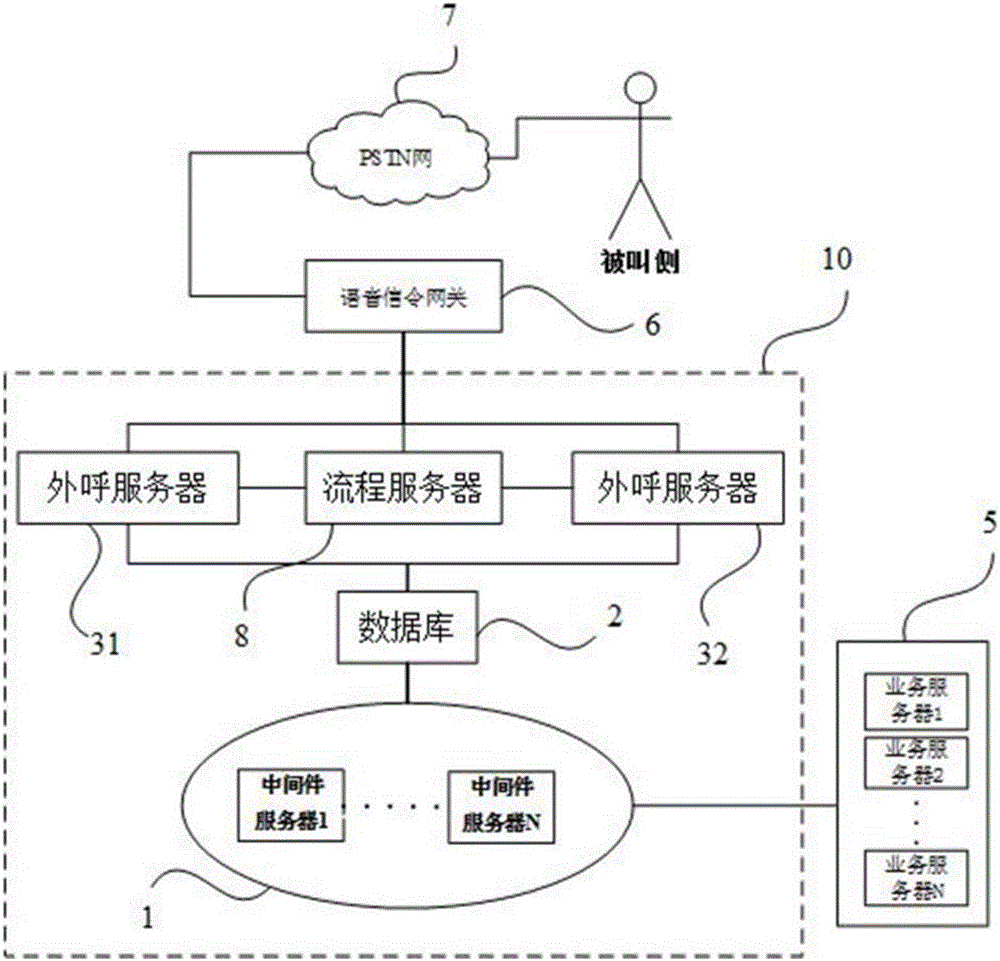
ActiveCN106572087AAchieve diversityImprove security and confidentialityKey distribution for secure communicationAutomatic exchangesReal-time computingSpeech sound
A voice outbound system disclosed by the present invention comprises a middleware server cluster, a set of databases and at least one outbound server, wherein the middleware server cluster obtains an outbound task and records the outbound task in the databases, and the outbound server calls the outbound task from the databases and initiates the outbound operation. An outbound task automatic outbound system constructed by the present invention realizes the outbound automation, and the task diversity is realized. According to the present invention, the seamless access of a heterogeneous system of the servers for pushing different businesses and the intermediate server cluster is realized by a universal interface, and further a multi-business expansion effect is realized.
Owner:SHANGHAI CTRIP COMMERCE CO LTD
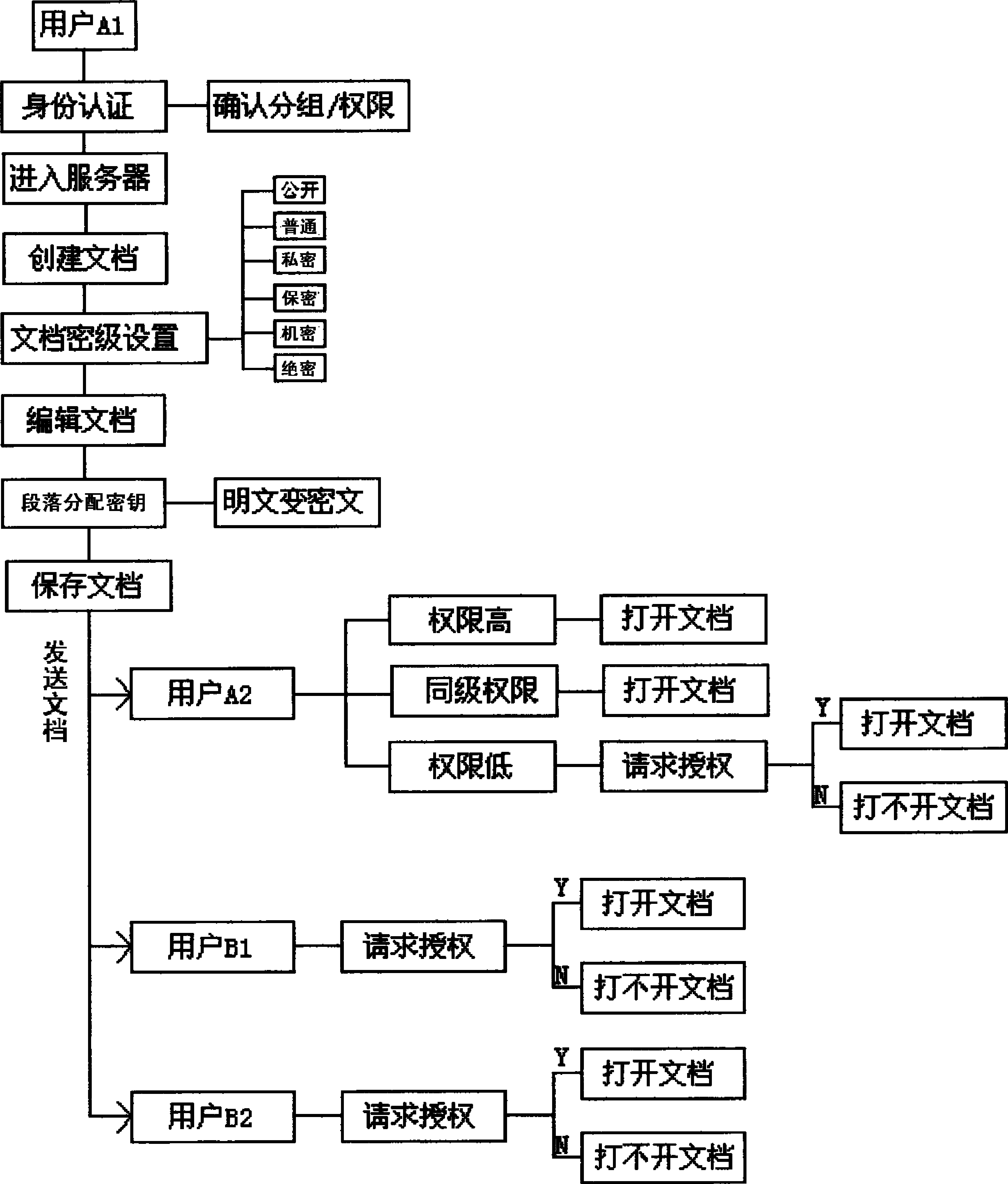
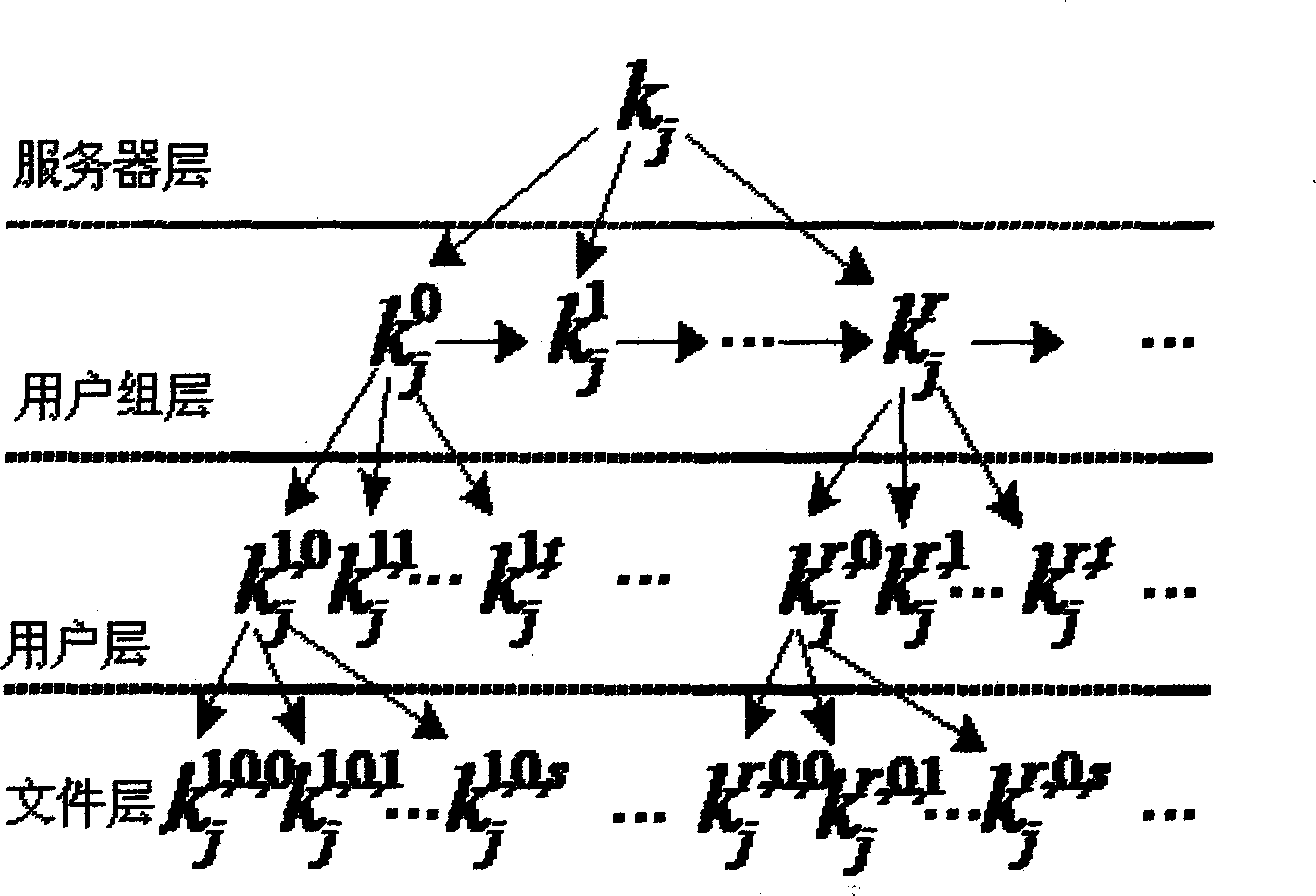
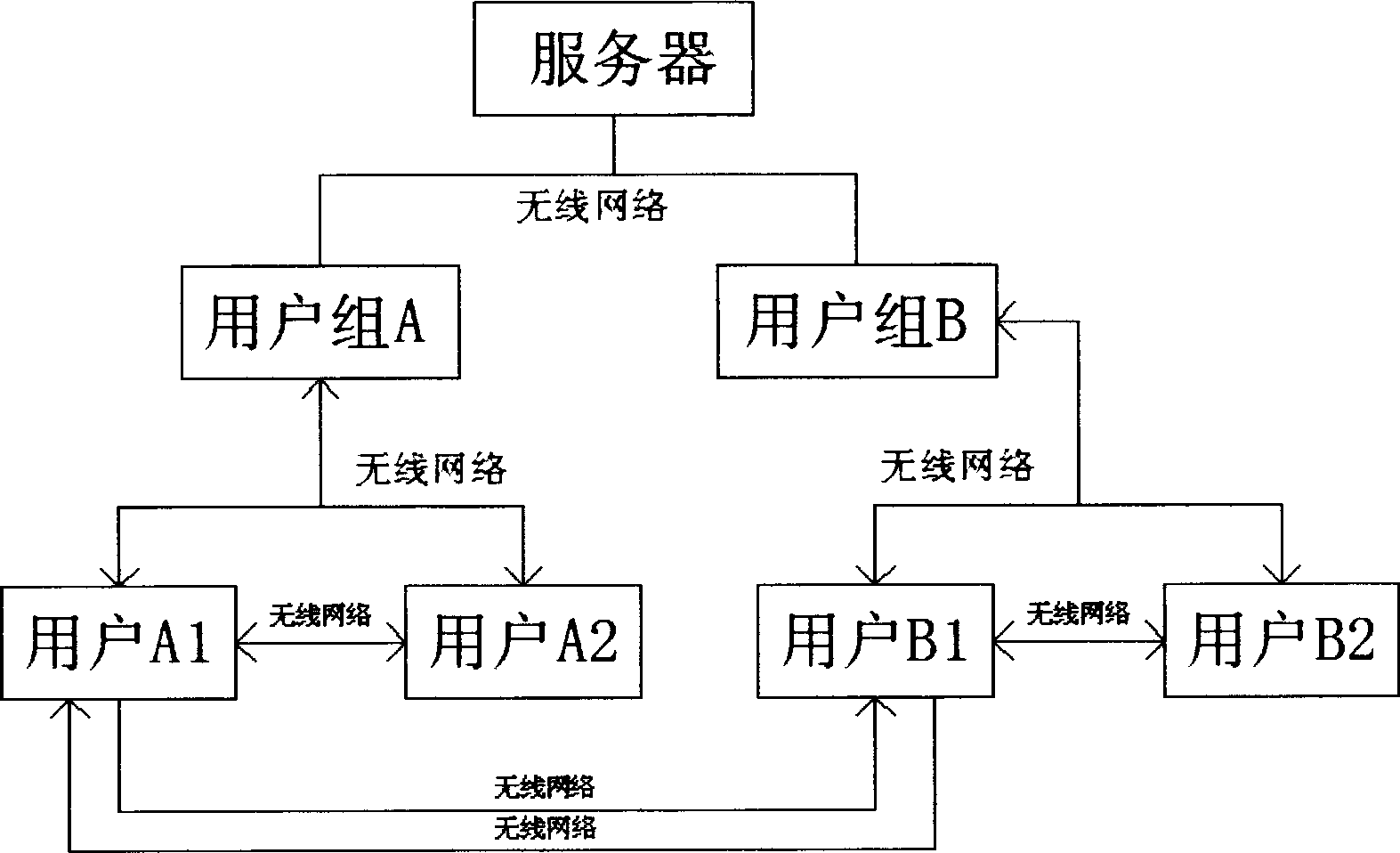
File safety management system based on mobile terminal
InactiveCN102938762AImplement authorizationRealize confidentiality managementKey distribution for secure communicationUser identity/authority verificationWireless mesh networkPacket loss
The invention discloses a file safety management system based on a mobile terminal. The system is realized by an authority grouping module, an access identity authentication module, a key distribution module and a security classification management module, a terminal user and a user group are connected to a server by a wireless network and are connected with each other by the wireless network to transmit and receive a file; and due to the adoption of the methods such as access identity authentication, authority grouping and key distribution, not only can file authorization and security classification management in the mobile terminal be realized, but also the inquiry of a ciphertext can not be affected by the error of the ciphertext under the condition of the error code or packet loss of a wireless network, and the error code robustness is good.
Owner:深圳出入境检验检疫局信息中心 +1
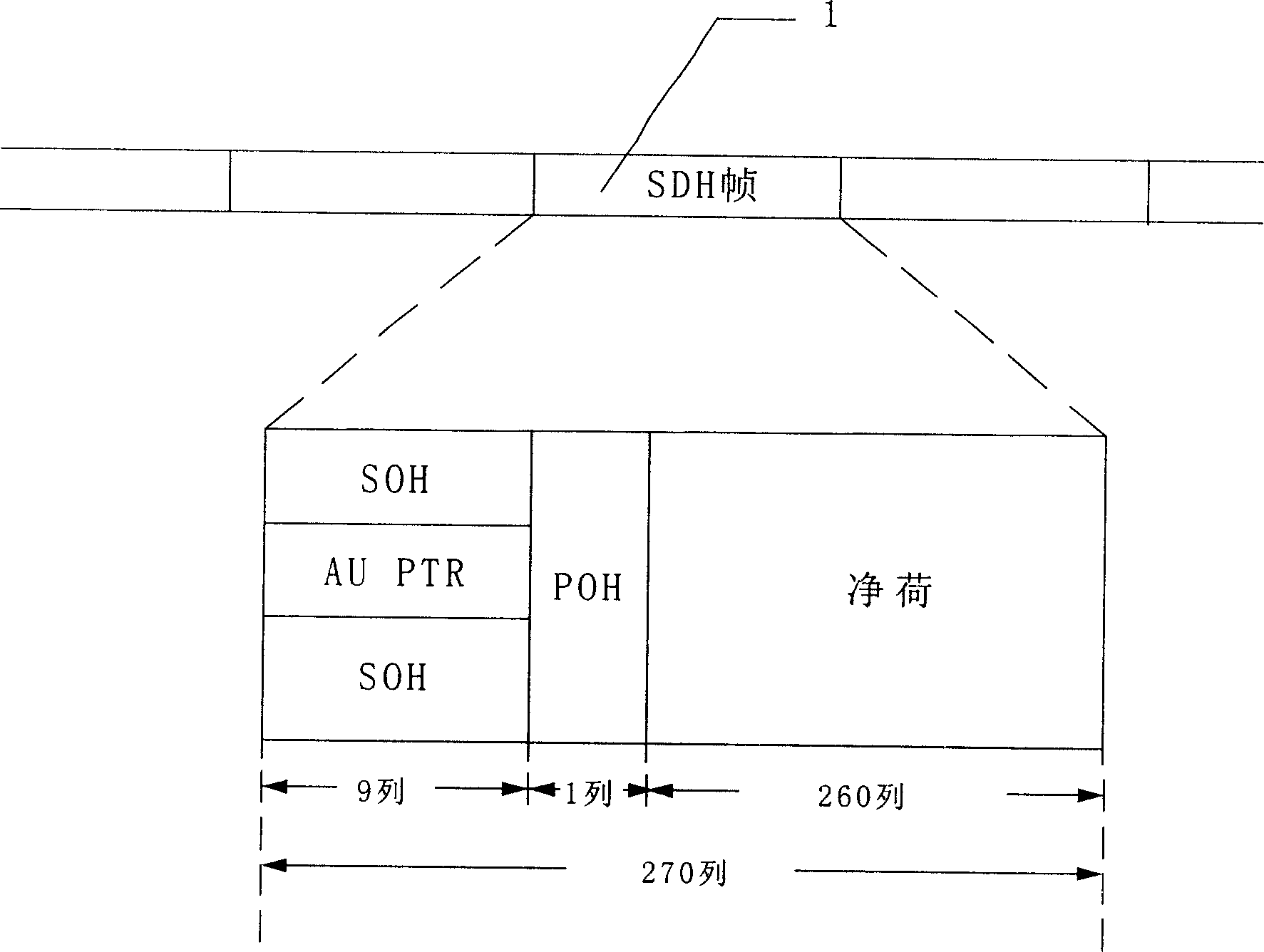
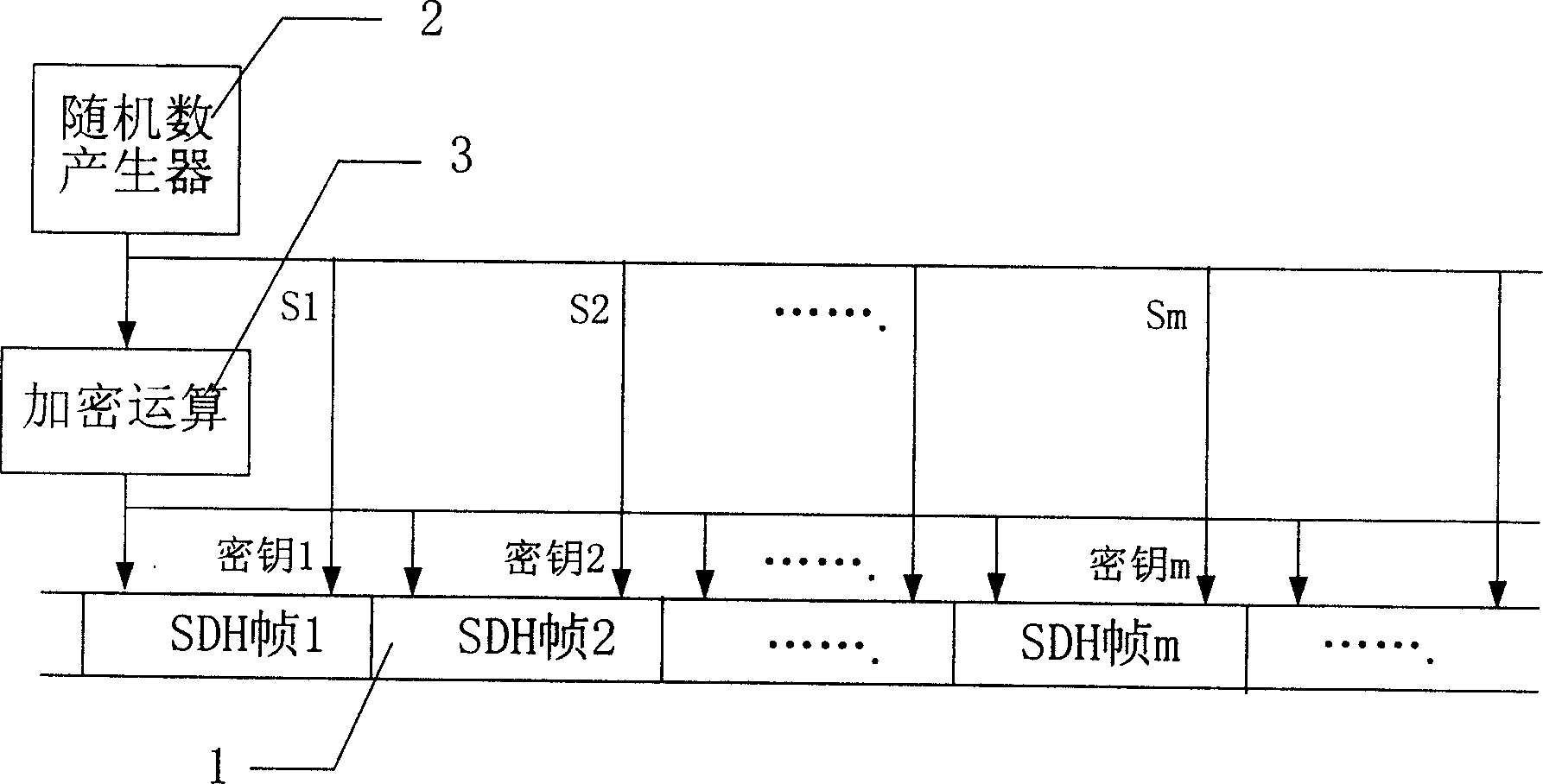
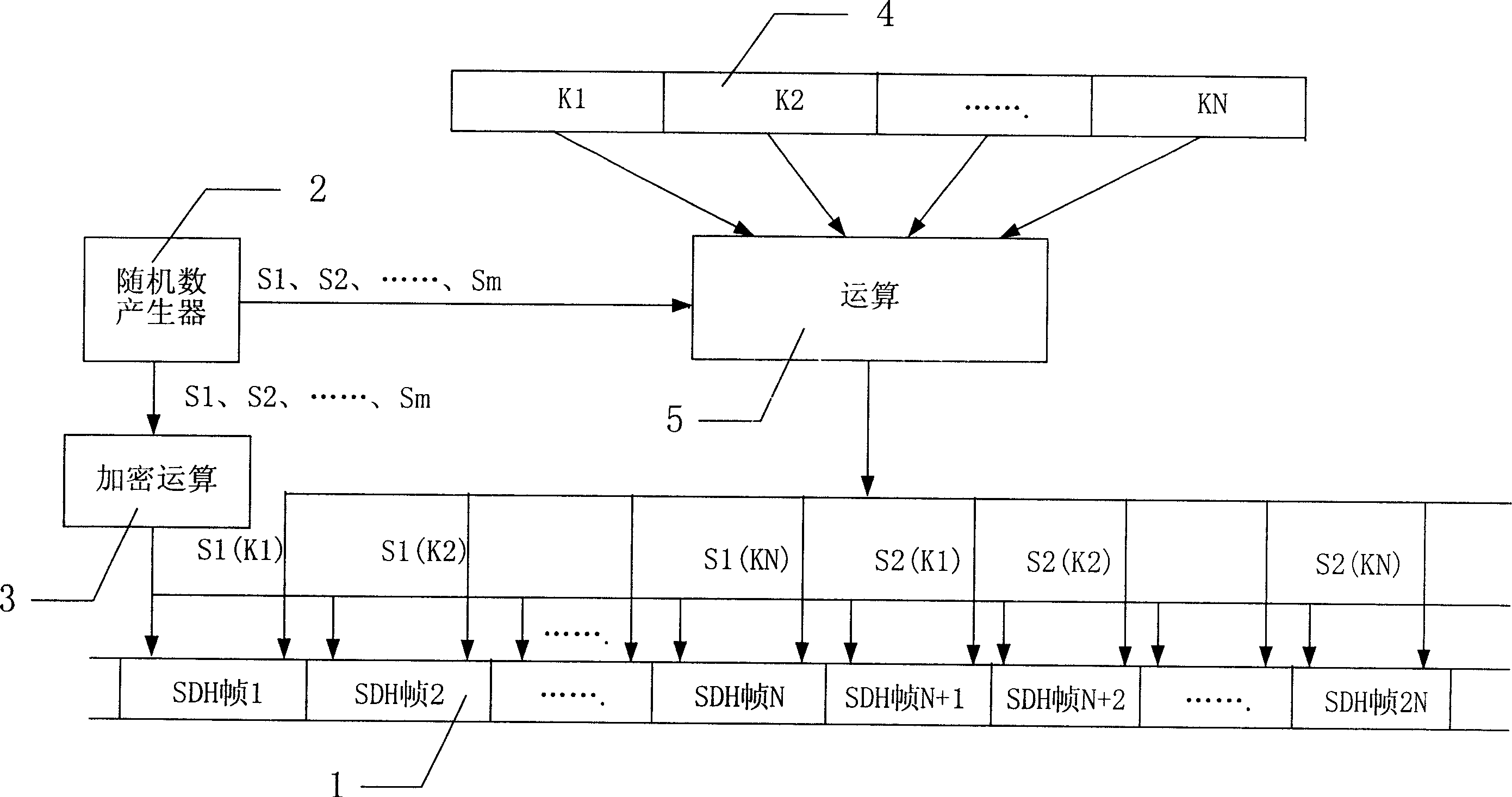
An encryption method applicable to SDH
This invention discloses a ciphering method for synchronous digital series characterizing in applying a random number generator to generate different random numbers, using said different random numbers as the ciphered keys to cipher different frames. The random numbers as the deciphered keys are transferred to the deciphering end utilizing the reserved bytes in the frame structure. This invention is a ciphering method for synchronous digital series. Since the ciphered keys generated by the generator are randomly generated, the ciphered results of same cleartexts are not the same, which increases its safety and security
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
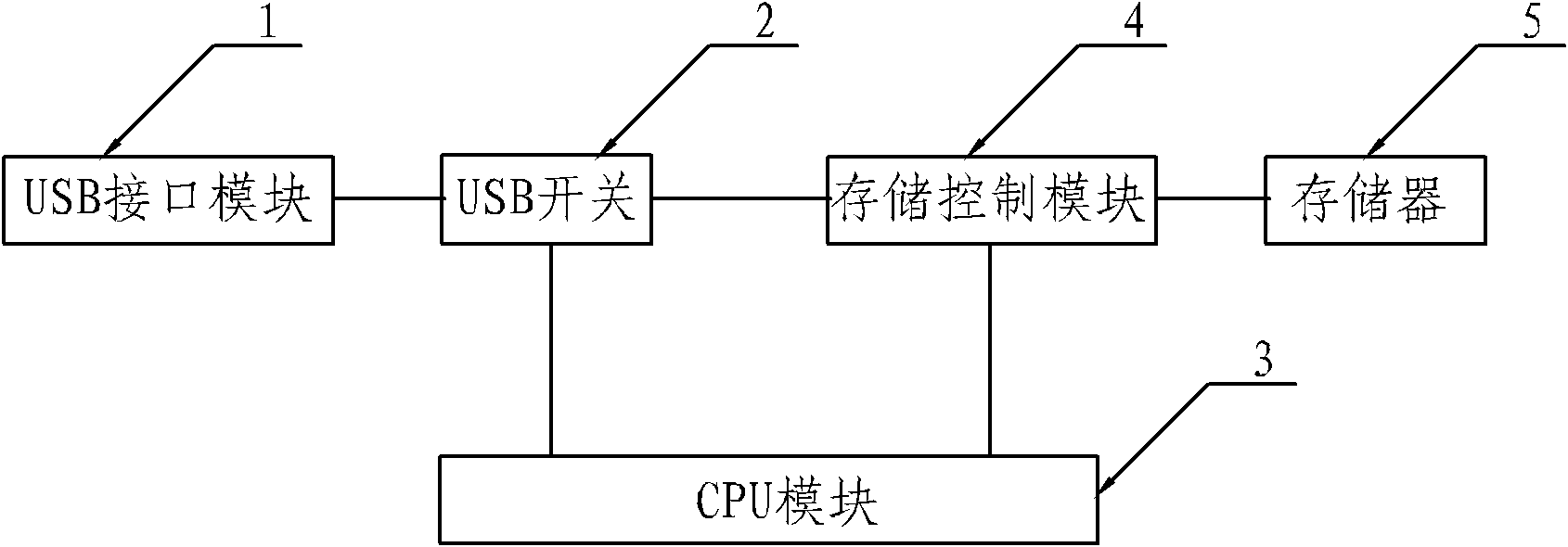
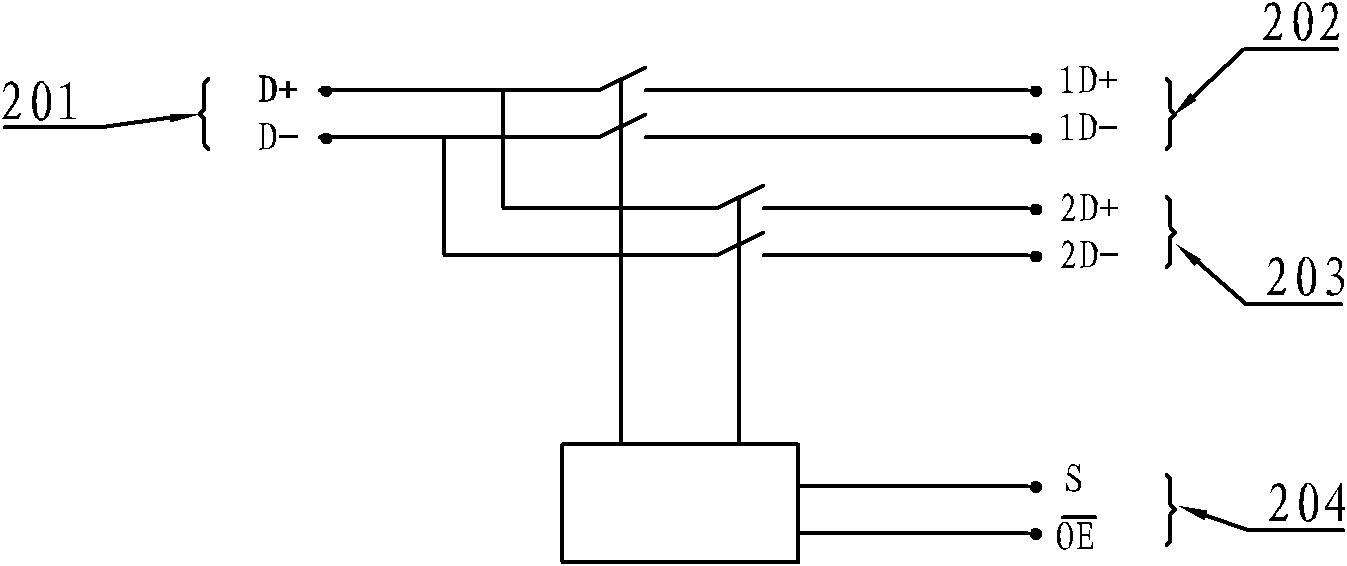
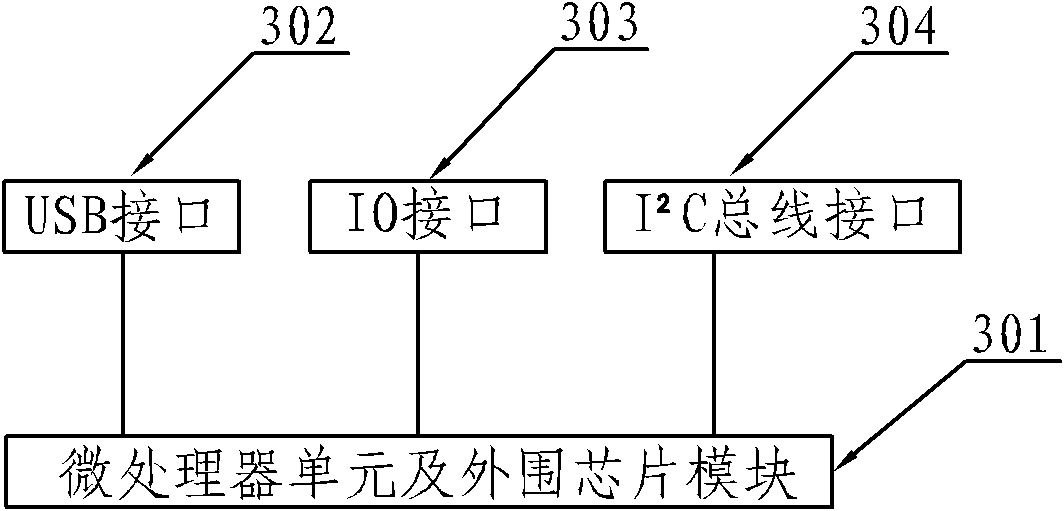
USB storage device based on hardware encryption
ActiveCN102004705APrevent leakageImprove securityUnauthorized memory use protectionUser authenticationData transmission
A USB storage device based on hardware encryption belongs to the computer technical field and mainly solves the problem that the encryption performance of the existing USB storage device is low. The USB storage device comprises a USB interface module, a USB switch, a CPU module, a storage control module and a Flash memory, wherein the CPU module is used to control the USB switch to switch the USB interface module and the CPU module and the data transmission of the storage control module; and the connection control of the USB storage device hardware and the control of read-write limit can be realized through user authentication. In the USB storage device of the invention, the USB switch and the CPU module are added on the basis of the traditional USB storage device and a Z8HM2 memory main-control chip is adopted, thus the user identity can be verified and the login information of the user can be stored; and the hardware can be used to encrypt a file written in the storage device, thus preventing that the right file can be obtained from the memory through the mode of low-level disk access.
Owner:国核信息科技有限公司
Method and system for safely sending out data
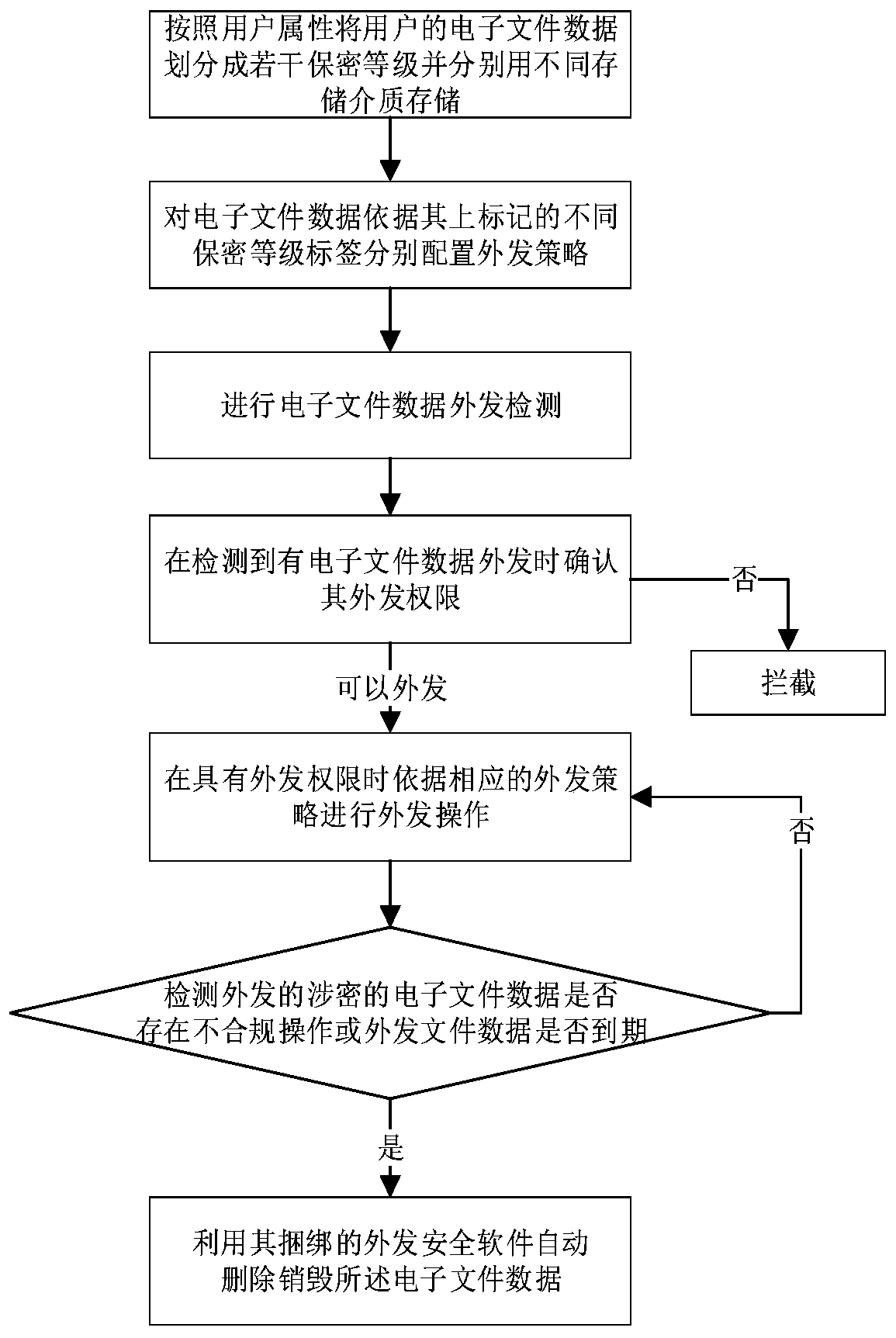
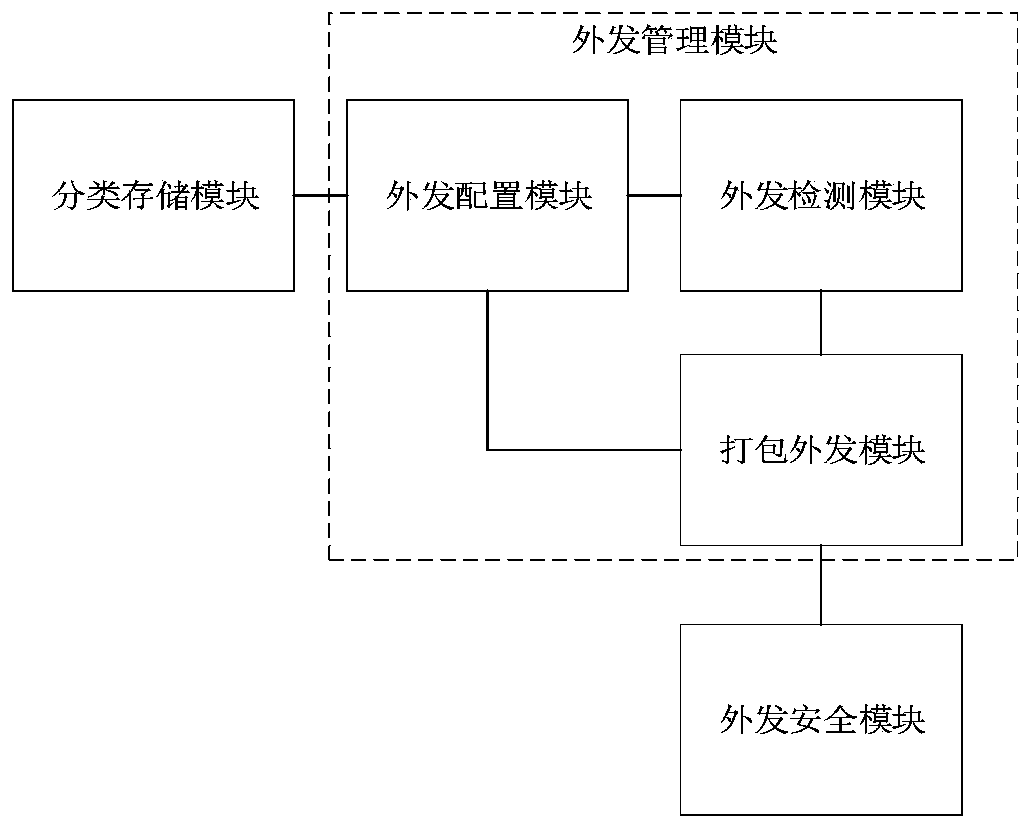
InactiveCN110502906AAvoid risk of leakageImprove security and confidentialityDigital data protectionConfidentialitySecurity software
The invention relates to a method for safely sending out data. The method comprises the following steps: dividing electronic file data of a user into a plurality of confidentiality levels according touser attributes and respectively storing the confidentiality levels by different storage media; configuring outgoing strategies for the electronic file data according to different confidentiality level labels marked on the electronic file data; carrying out electronic file data outgoing detection; when it is detected that the electronic file data is sent out, confirming the sending-out permissionof the electronic file data; when the user has the outgoing permission, carrying out the outgoing operation according to the corresponding outgoing strategy; when the confidential electronic file data has a leakage risk, utilizing the bound outgoing security software to automatically delete and destroy the electronic file data. According to the method, the problems of poor timeliness, poor security and confidentiality, inflexible file data receiving and sending operation and the like of file data sending in the prior art are solved, the whole process is simple, rapid and flexible, complex sending approval is not needed, and the security and confidentiality of the electronic data sending process are enhanced. The invention further relates to a system for safely sending out the data.
Owner:北京泰立鑫科技有限公司
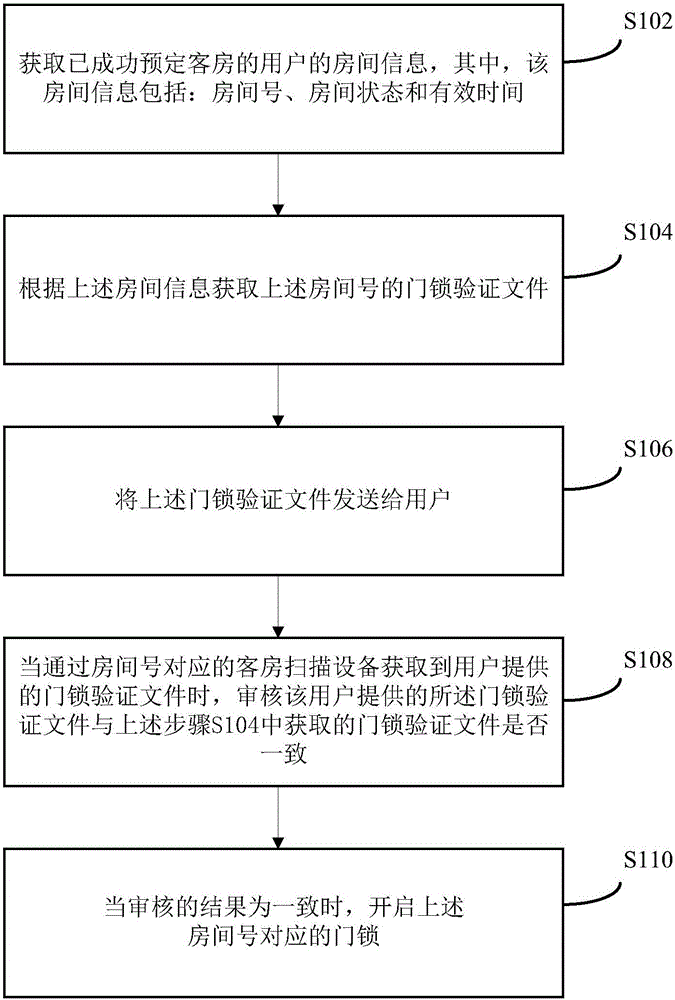
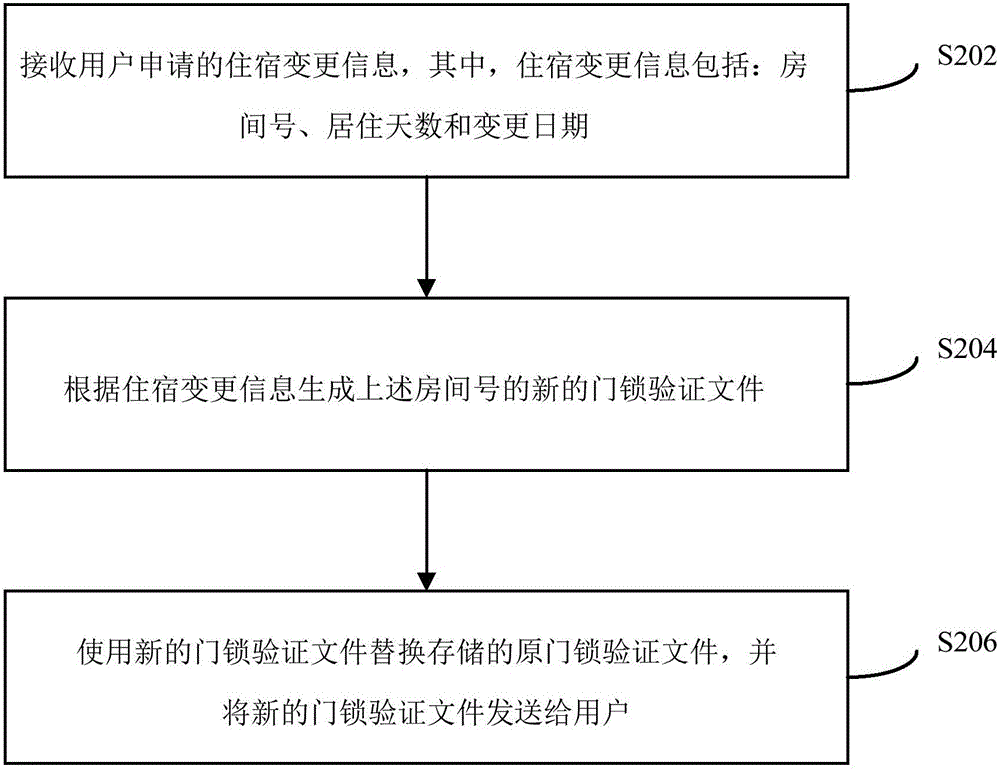
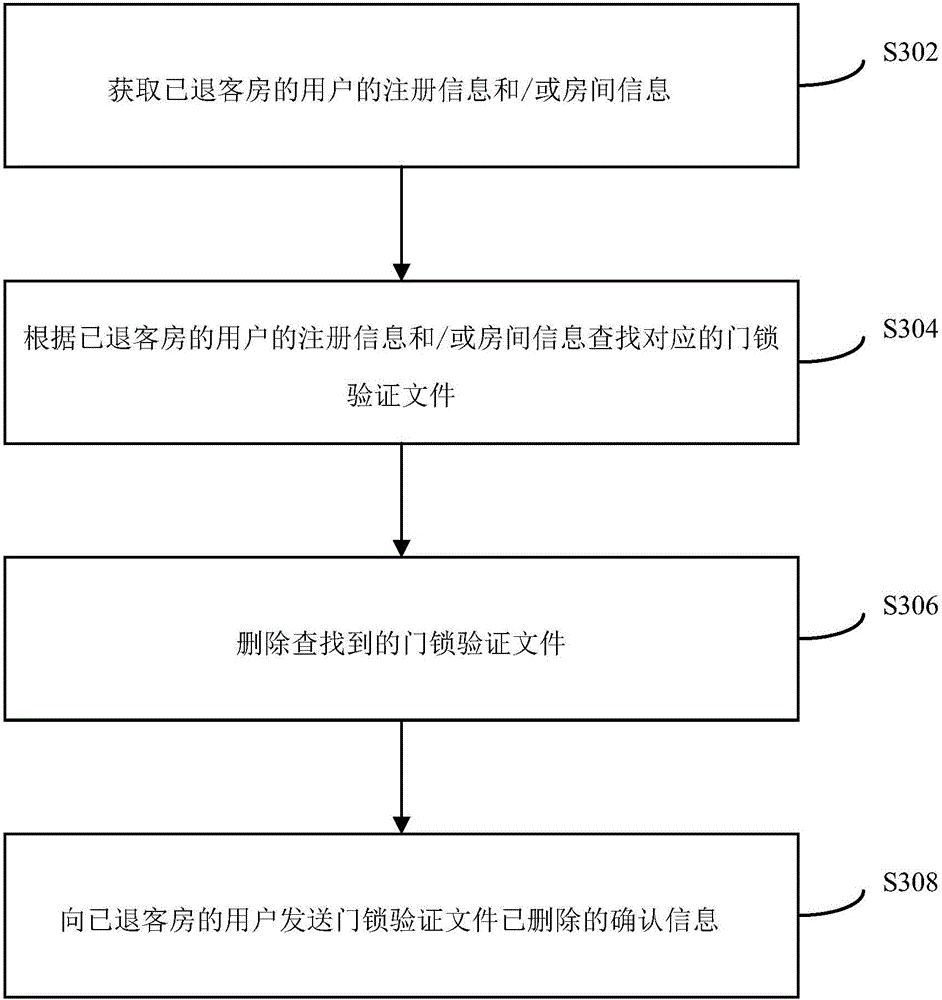
Guest room door lock management method and device
InactiveCN105894640AImprove security and confidentialityReduce hardware and labor costsData processing applicationsIndividual entry/exit registersHardnessEffective time
The invention provides a guest room door lock management method and device. The guest room door lock management method comprises the steps that room information of users successively reserving guest rooms is obtained, wherein the room information includes room numbers, room states and effective time; door lock verification files of the room numbers are obtained according to the room information and are sent the users; when the door lock verification files provided by the users are obtained through guest room scanning devices corresponding to the room numbers, whether the door lock verification files provided by the users are consistent to the obtained door lock verification files are verified or not; when the verification results are consistent, door locks corresponding to the room numbers are opened. The guest room door lock management method replaces a traditional guest room door lock management mode, so that much manual intervention in the guest room door lock management process is omitted, the confidentiality and safety of the door locks are improved, the labor costs and hardness costs are reduced, and improvement of guest room operating efficiency is also promoted.
Owner:BEIJING JIAYANG TECH CO LTD
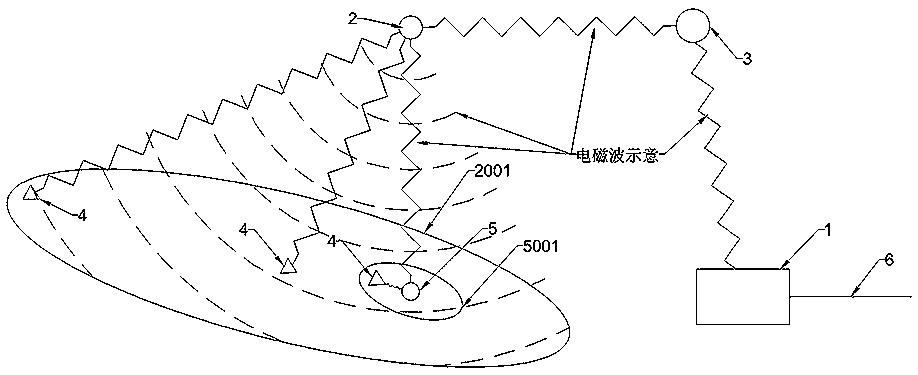
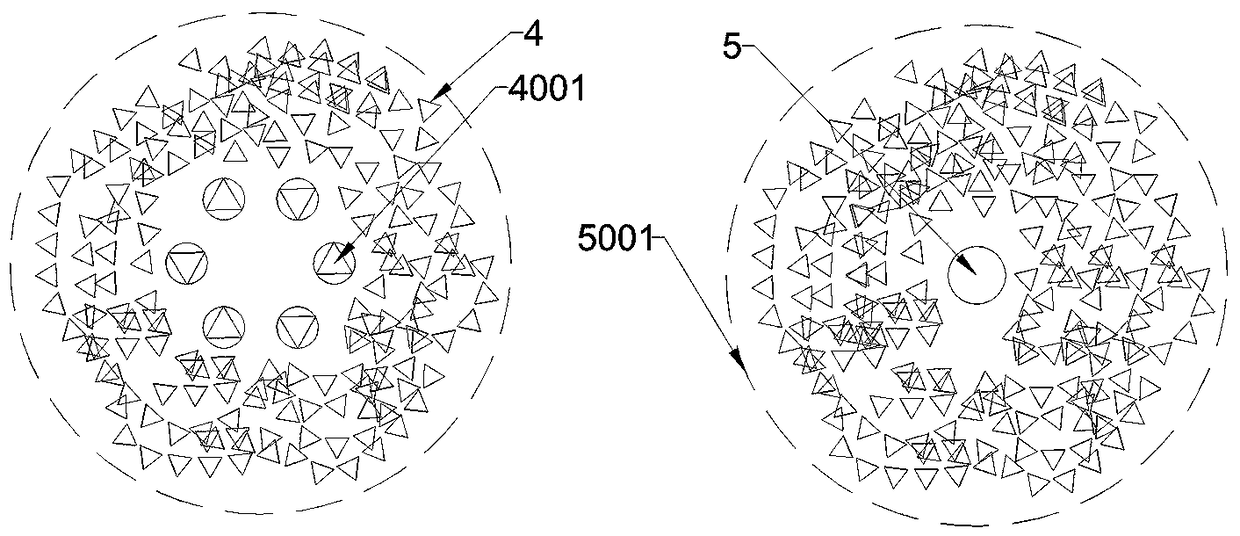
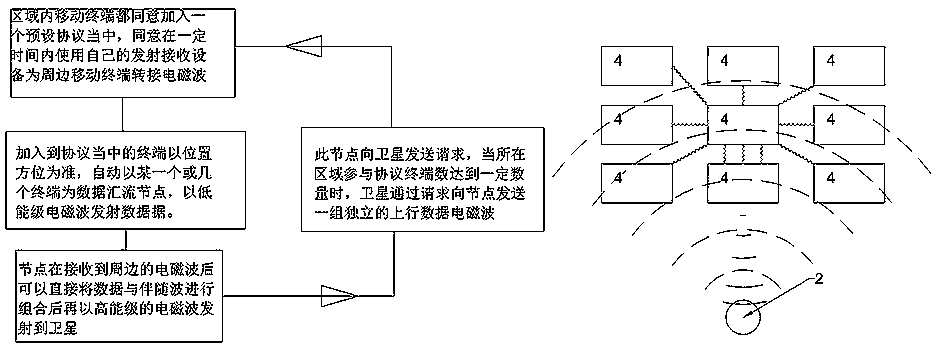
Electromagnetic wave data transmission rule and system
ActiveCN109217914AIncrease the range of referentialityIncrease the number of launchesRadio transmissionSatellite antennasInterference (communication)
The invention discloses an electromagnetic wave data transmission system, which includes terrestrial master information node, communication satellite, relay satellite, uplink control carrier, relay satellite antenna unit, the ground main information node is connected with the outside through the wired broadband, A main information node on that ground is connected with a communication satellite through a relay satellite, A telecommunication satellite includes a telecommunication satellite service area, The communication satellite is respectively connected with a mobile terminal and a ground data aggregation node, wherein the mobile terminal and the ground data aggregation node are arranged in the service scope of the communication satellite, the mobile terminal comprises a data aggregationnode, and the ground data aggregation node is arranged in the service scope of the ground data aggregation node; The invention not only reduces the upgrading requirement of the terrestrial wireless digital base station, but also reduces the application requirement of the wireless spectrum bandwidth. And avoid the problem of interference cancellation of electromagnetic wave peak and valley, and further increase the number of electromagnetic wave serial emission per unit time.
Owner:XUZHOU SPACE TIME THOUGHT INTELLIGENT TECH CO LTD
Full-secret retrieval research of big data security
InactiveCN112702379AImprove security and confidentialitySimplify work reporting processDigital data protectionTransmissionCiphertextBig data security
The invention discloses full-secret retrieval research of big data security, which is high-security file storage software aiming at solving the problems that secret files in enterprises are illegally stolen, the transmission process is captured, sensitive files are safely stored and the like. Functions of file security storage, file transmission channel encryption, document full ciphertext retrieval, picture retrieval, file sharing, authority hierarchical access and the like can be realized. The system is mainly divided into a client and a server, and file encryption and retrieval services (including document retrieval and picture retrieval) are performed through channel encryption interaction; the server side stores the ciphertext index of the file, retrieval is carried out in the server, and the data storage server only stores the encrypted file. In this way, privacy scanning and detection of the data server on the user are eradicated. And the data storage server supports a private cloud OpenStack and an FTP server.
Owner:纬领(青岛)网络安全研究院有限公司 +1
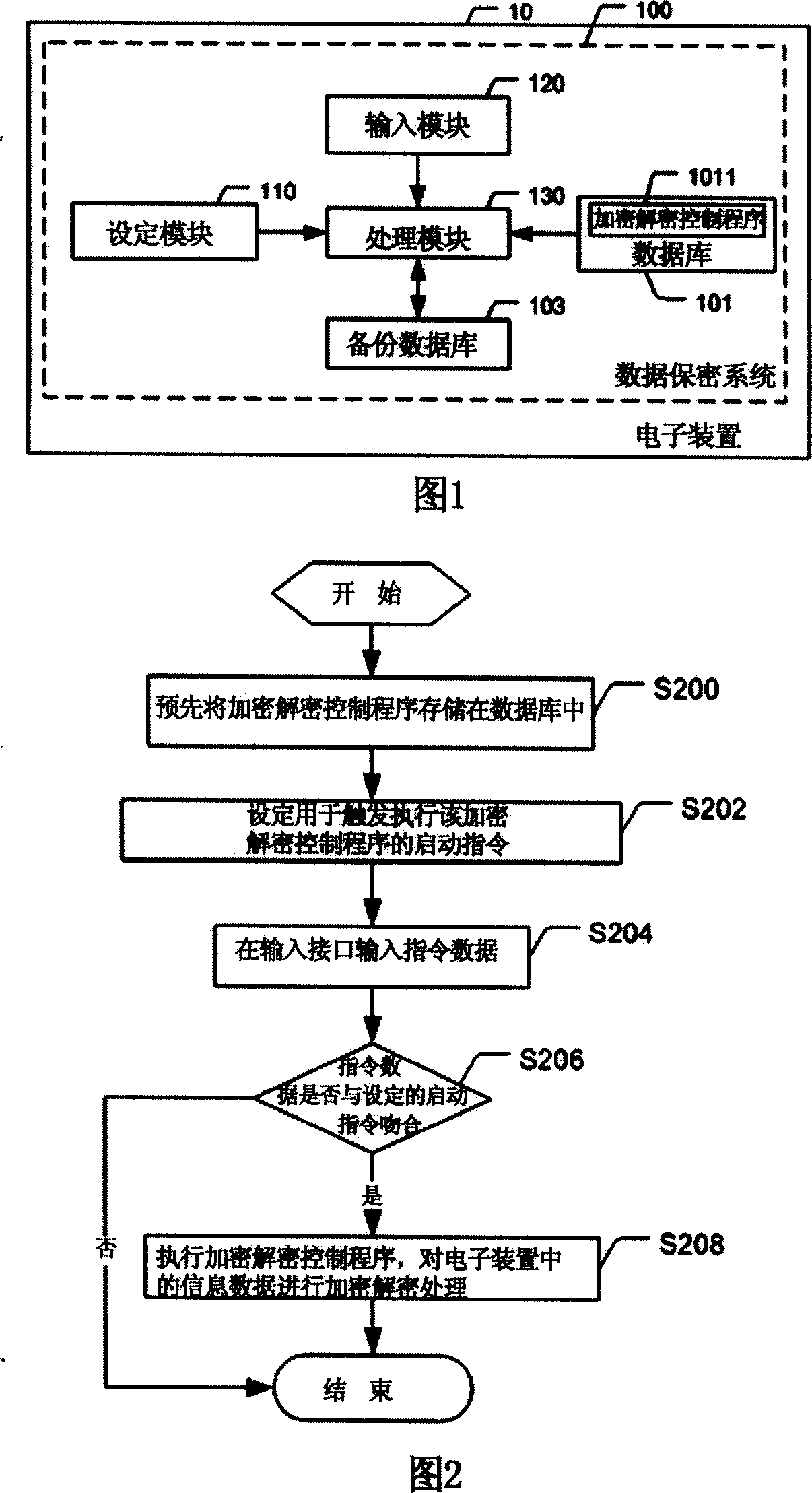
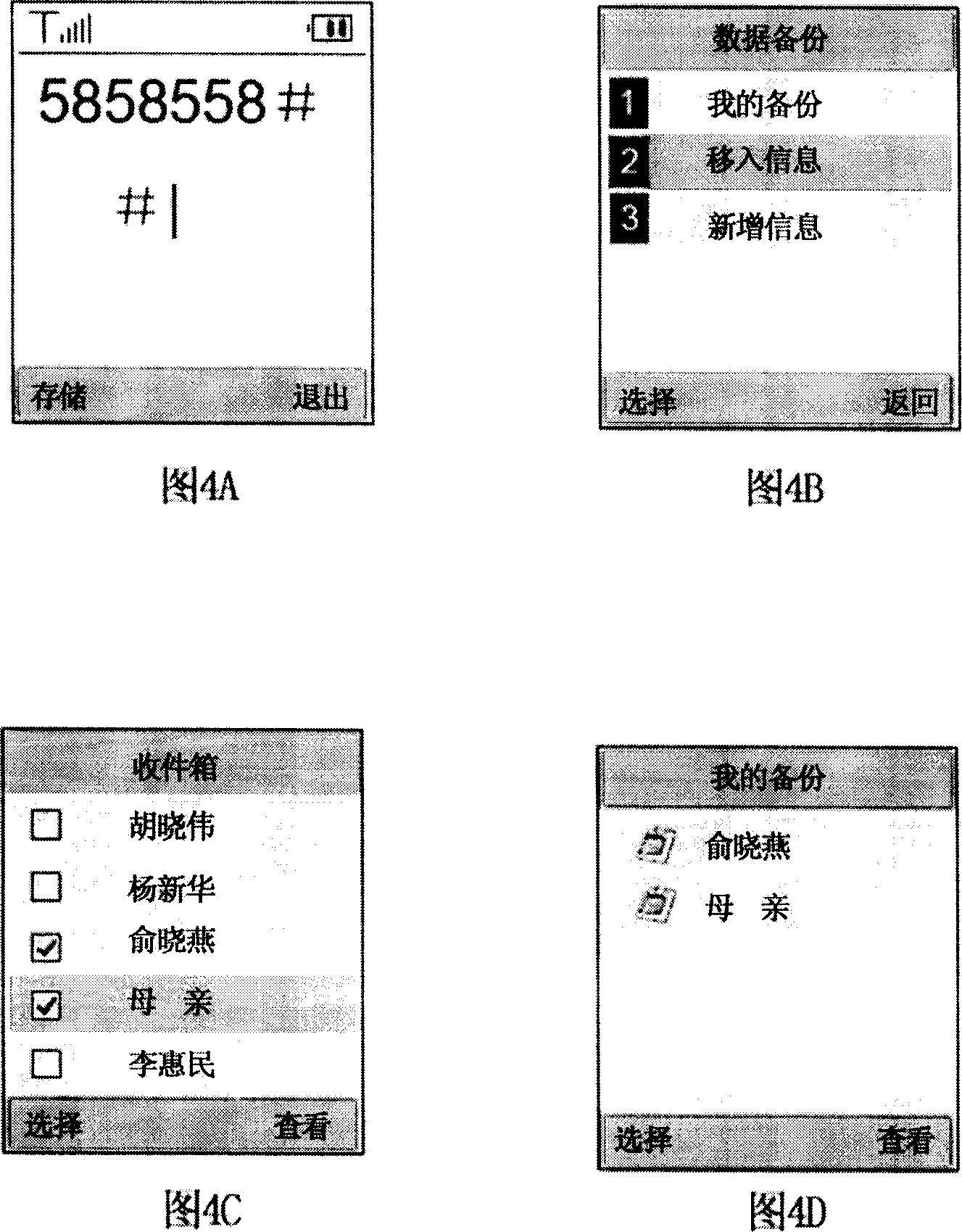
Data secrecy system and method
InactiveCN101009878AUser-friendly encryption and decryption processingImprove security and confidentialityComputer security arrangementsRadio/inductive link selection arrangementsRelevant informationComputer module
The disclosed data privacy system, which is used in the electric device of mobile phone to encipher and decipher data for protection, comprises an encipher / decipher control program, a setting module, an input module, and a processing module. This invention applies special command data to start the stored encipher / decipher control program and execute encipher / decipher operation according to user request, increases humanization in operation process, and improves data security.
Owner:INVENTEC CORP
Key management method and related device
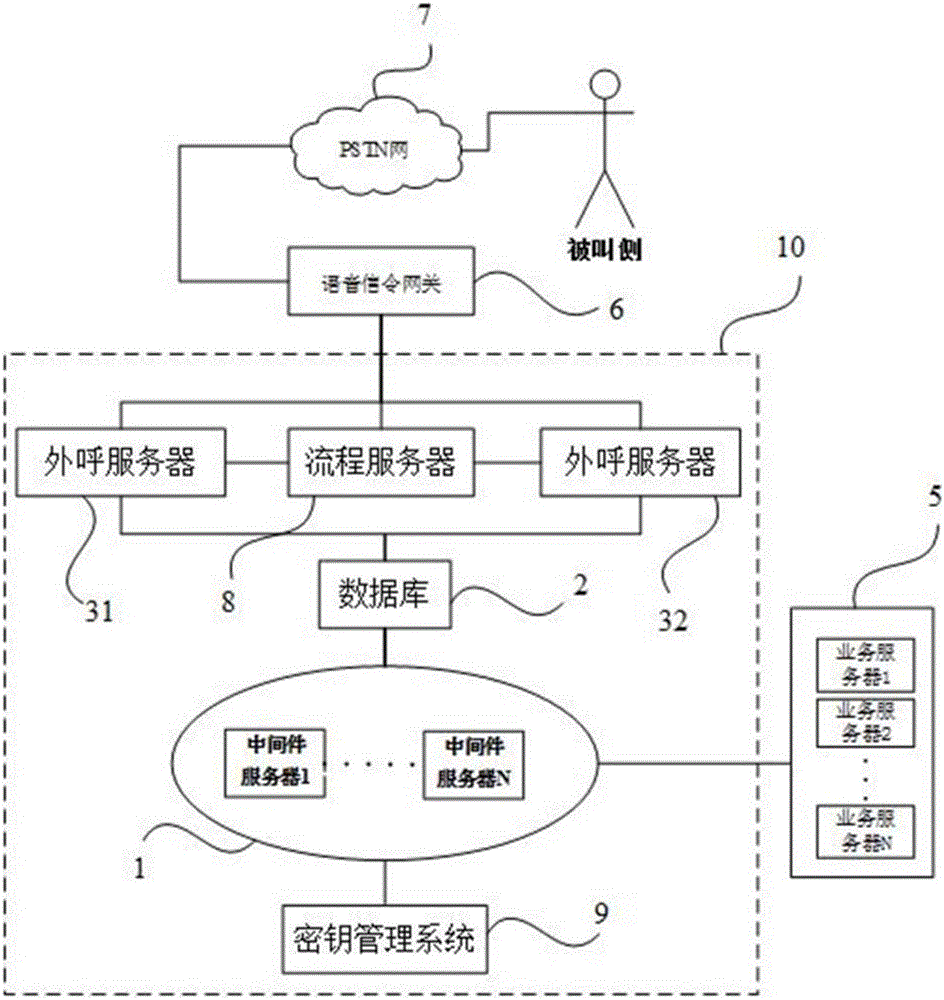
ActiveCN111654372AReduce complexityImprove security and confidentialityKey distribution for secure communicationOperational systemDistributed computing
The key management method and the related device provided by the embodiment of the invention are applied to a main server in a distributed cluster, the main server comprises a first system disk, and the first system disk comprises a first controller chip and a first memory and is used for storing an operating system of the main server; the main server responds to the new data disk to join the distributed cluster, generates a secret key through the first controller chip, and stores the secret key in the first memory; and the secret key is synchronized to the new data disk. Compared with the prior art, the secret key can be generated, stored and synchronized in the main server, and the beneficial effect of reducing the complexity of secret key management is achieved on the premise of havingconfidentiality.
Owner:JIANGSU XINSHENG INTELLIGENT TECH CO LTD
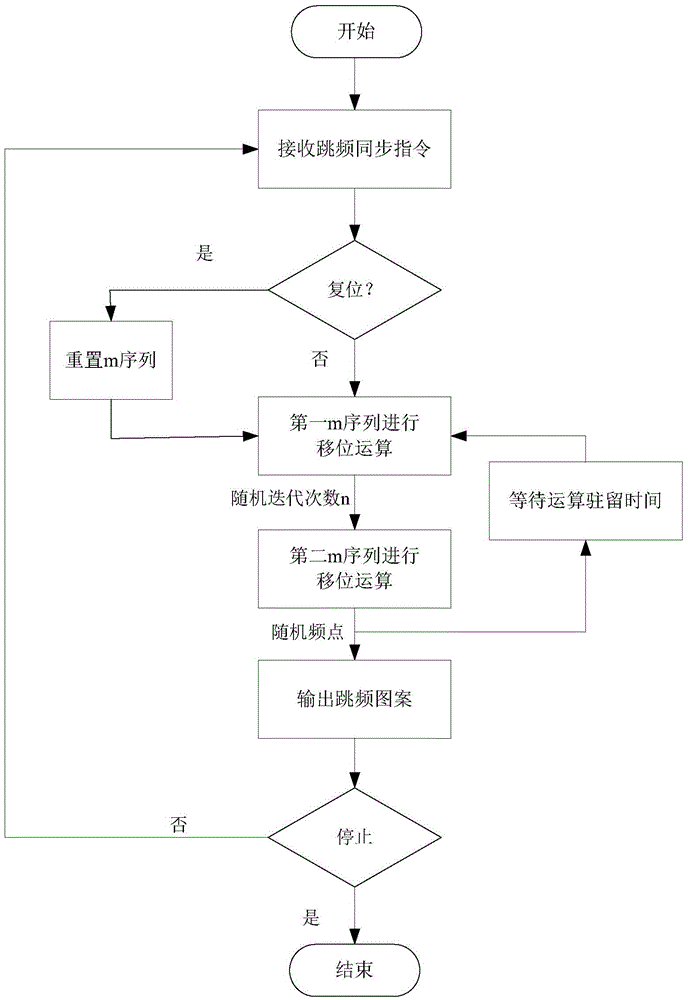
Method for generating cyclical iteration m sequence frequency hopping patterns
The invention discloses a method for generating cyclical iteration m sequence frequency hopping patterns in a frequency hopping system. On the basis of present generation methods of m sequence frequency hopping patterns, cyclical iteration is added so that the provided method has more flexible and changeable cycle period and the security of the frequency hopping system is effectively increased compared with previous frequency hopping pattern generation method.
Owner:NO 54 INST OF CHINA ELECTRONICS SCI & TECH GRP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com