Method and system for authorizing to acquire terminal attack alarming information log
一种报警信息、日志的技术,应用在通信领域,能够解决终端设备攻击报警信息恶意窃取、无法知晓攻击报警的原因等问题,达到加强安全保密性、确保合法性、确保安全性的效果
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] In order to explain in detail the technical content, structural features, achieved goals and effects of the technical solution, the following will be described in detail in conjunction with specific embodiments and accompanying drawings.
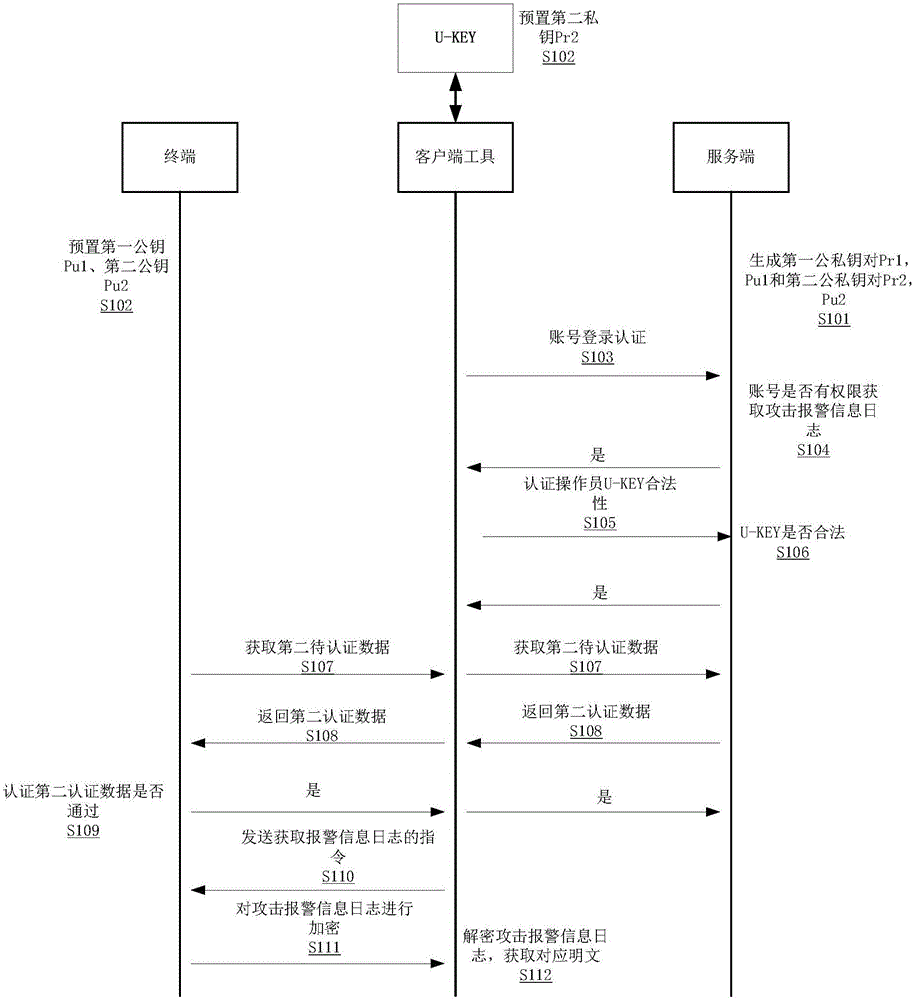
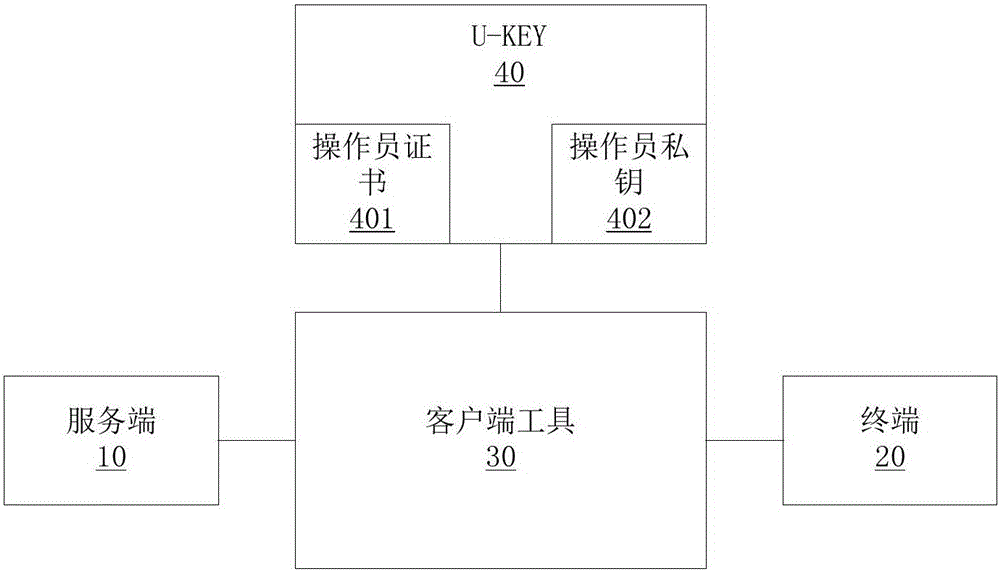
[0028] see figure 1 , in this embodiment, the U-KEY is inserted on the client tool. In this embodiment, the client tool is a PC, wherein the U-KEY stores an operator certificate and an operator private key. When the U-KEY is inserted After being installed on the client tool, interactive software is installed on the client tool, so that the client tool can obtain the operator certificate from the U-KEY and directly use the operator's private key. Secondly, in this embodiment, a specific APP is installed on the PC. On the APP login interface, maintenance personnel need to enter the account and password to log in to the system; through the account and password to log in to the system, the server will judge the authority of the account an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com