Key management method and related device
A key management and key technology, which is applied to secure communication devices and key distribution, can solve problems such as easy damage or loss of external modules, reduced security of key confidentiality, and increased complexity of key management to achieve enhanced Confidentiality Security, Complexity Reduction, Effect of Complexity Reduction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
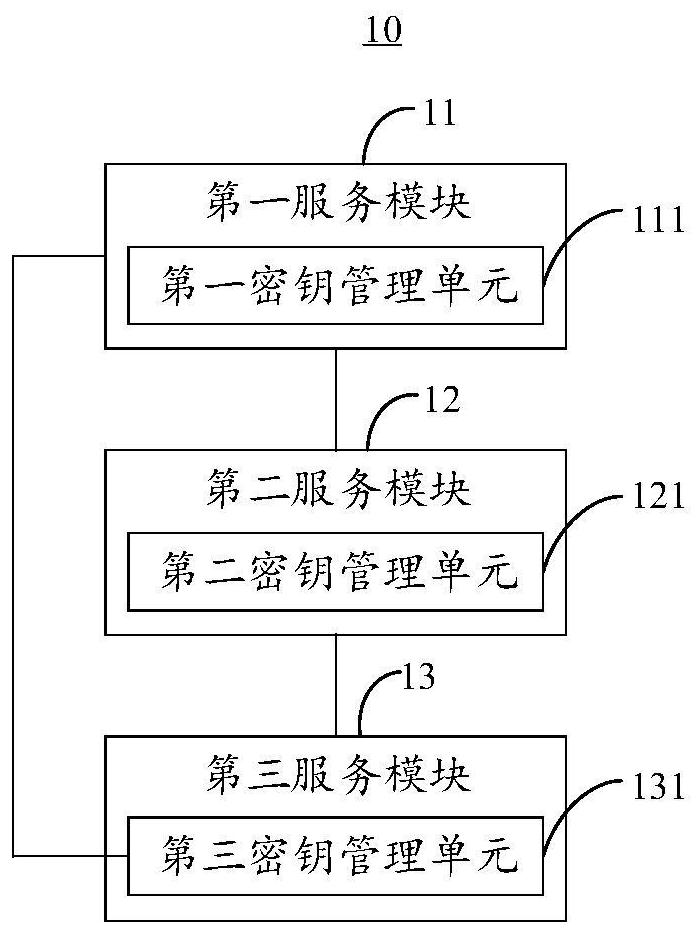
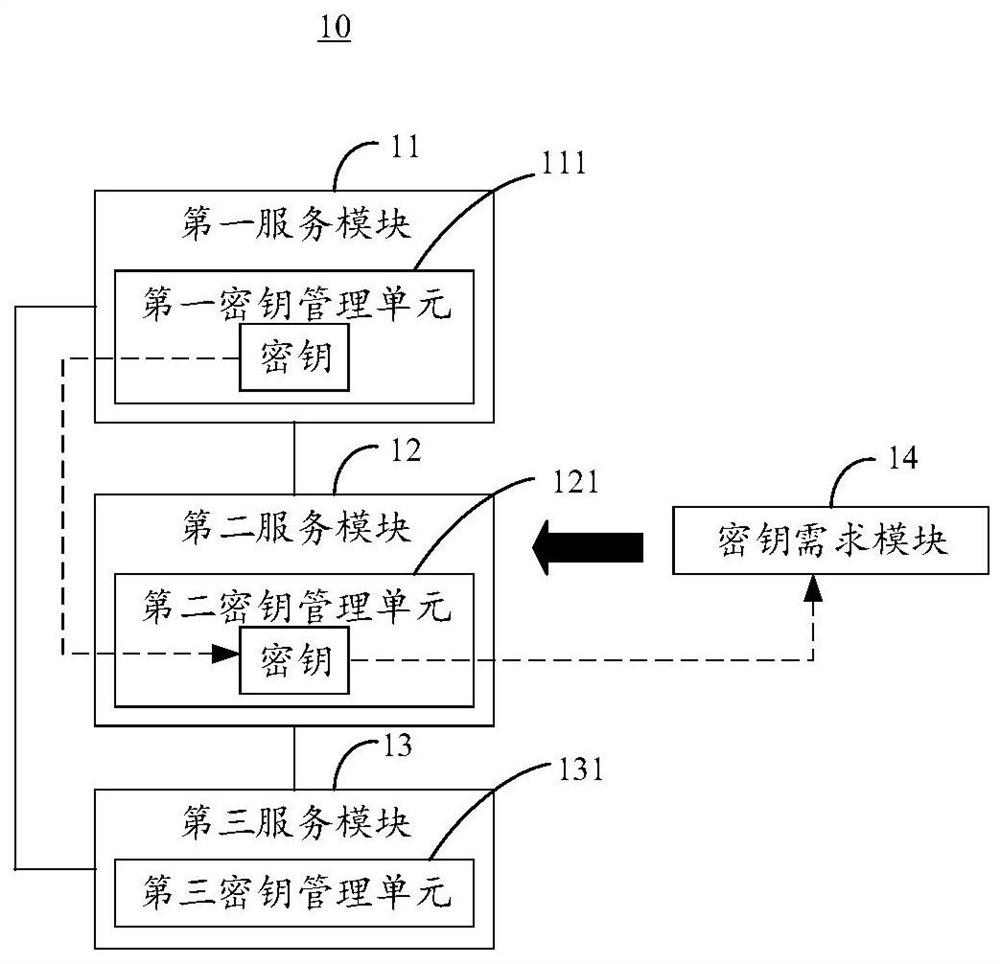
[0053] In order to solve the above technical problems, see figure 1 , figure 1 A key management system provided by the present invention, the system can be applied to distributed clusters, the key management system 10 includes: a first service module 11, a second service module 12 and a third service module 13, wherein the first A service module 11 includes a key management unit 111, a second service module 12 includes a key management unit 121, and a third service module 13 includes a key management unit 131; the first service module 11 is used for the second service module 12 and the second service module 12 The third service module 13 provides key management services; the second service module 12 is used to provide key management services for the third service module 13 when the first service module 11 fails.
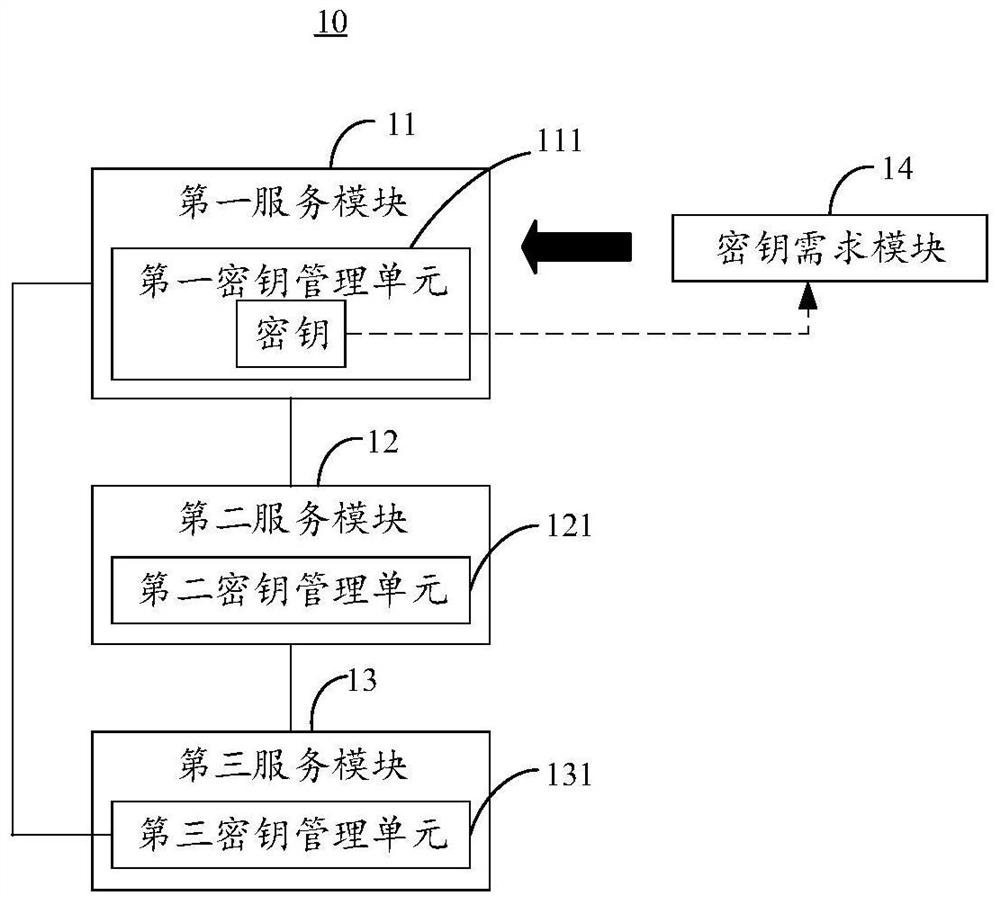
[0054] The first service module 11 is used to generate and store the key through the first key management unit 111 after the key demand module joins the distributed...
Embodiment 2
[0095] The following will combine the above image 3 and Figure 4 The example shown in the key management system and server architecture provides a key management method, and the execution subject of the method can be image 3 master server 110A in , where, image 3 The master server 110A in contains internally the Figure 4 For the first system disk 110A-1 of the shown structure, refer to Figure 7 , Figure 7 It is a flowchart of a key management method provided by an embodiment of the present invention, and the method specifically includes:
[0096] Step 701: In response to a new data disk joining the distributed cluster, generate a key in the first controller chip, and save the key in the first memory.
[0097] Specifically, the first controller chip is used to generate a key, encrypt and decrypt the key, and the first memory is used to store the key generated by the first controller chip.
[0098] Step 702, Synchronize the key to the new data disk.
[0099] Specif...
Embodiment 3
[0131] The following will combine the above Figure 5 and Figure 6 An example of the key management system and server architecture shown, and another key management method is given, and the execution subject of this method is Figure 5 The main server 110B in, wherein, image 3 The master server 110B in the internally contains the Figure 4 For the first encryption card 110B-1 of the shown structure, see Figure 8 , Figure 8 Another key management method flowchart provided by the embodiment of the present invention, the method may specifically include:
[0132] Step 801, in response to a new encryption card joining the distributed cluster, generate a key in the first controller chip, and save the key in the first memory.
[0133] Specifically, the first controller chip is used to generate a key, encrypt and decrypt the key, and the first memory is used to store the key generated by the first controller chip.
[0134] Step 802, Synchronize the key to the new encryption ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com