Patents
Literature
37results about How to "Implement authorization" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
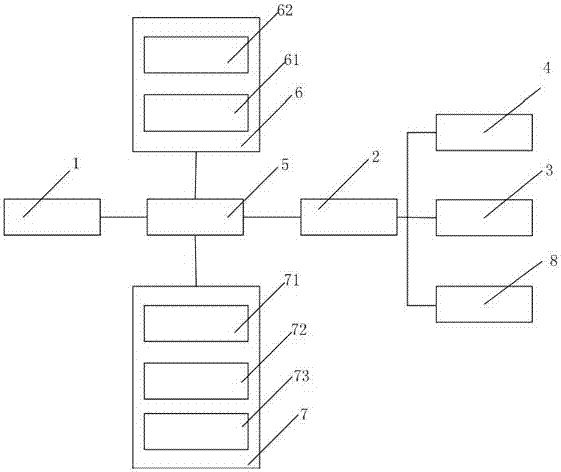
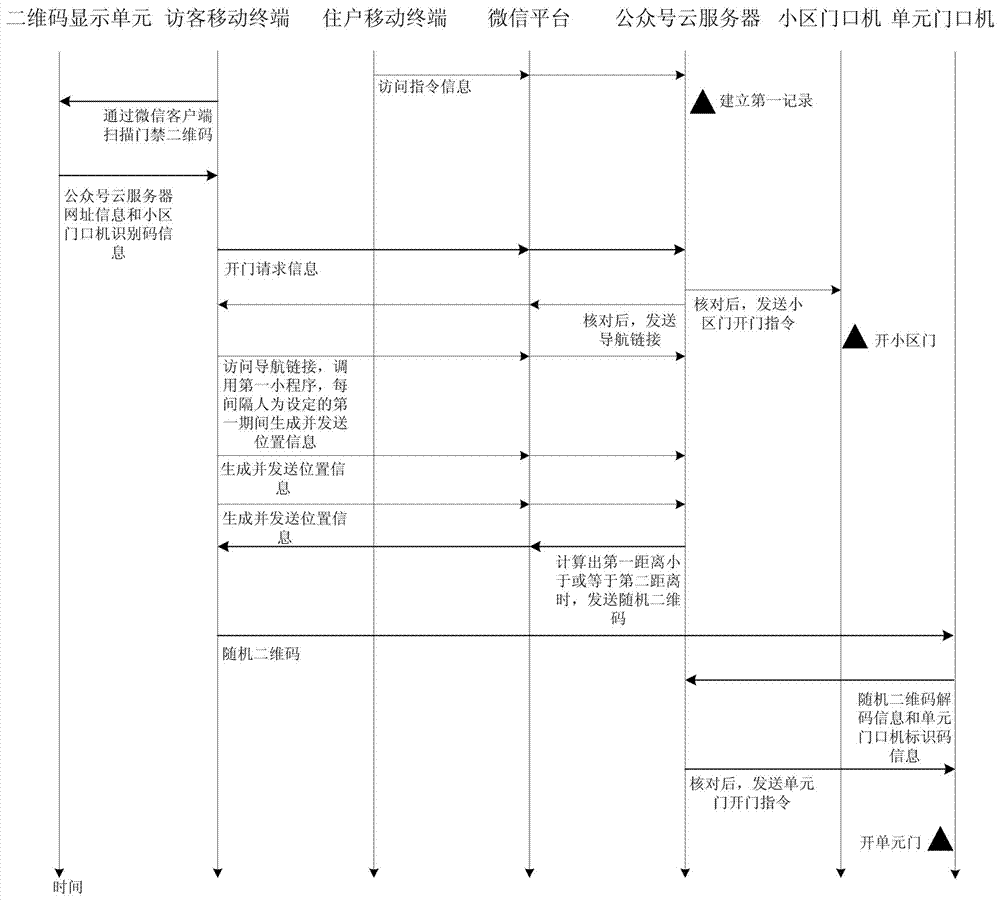
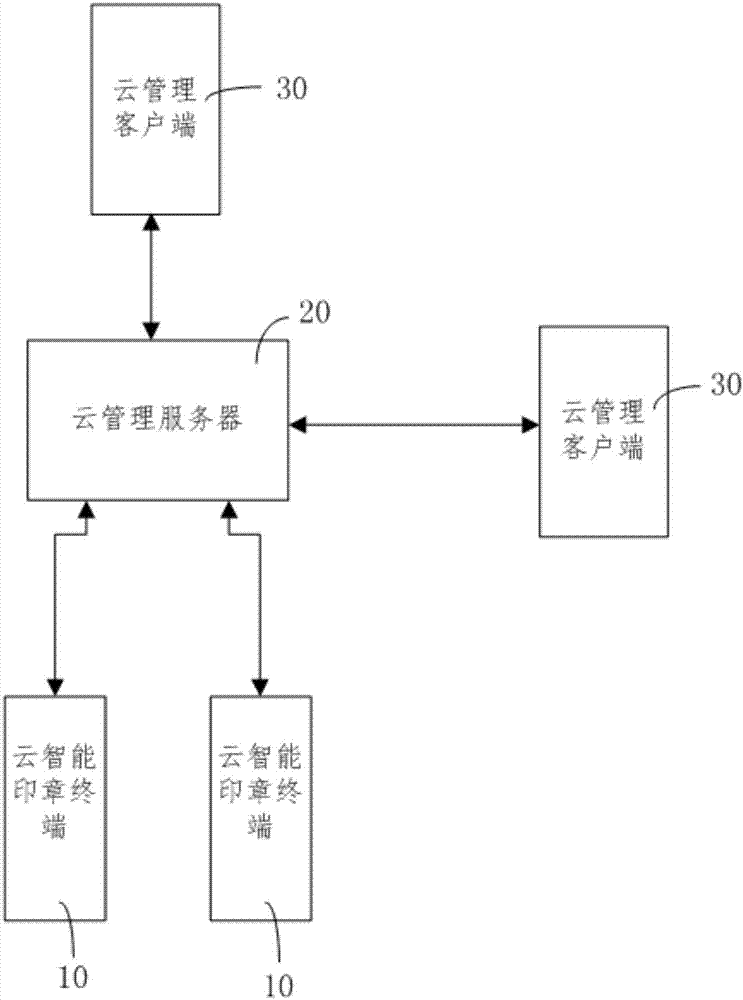
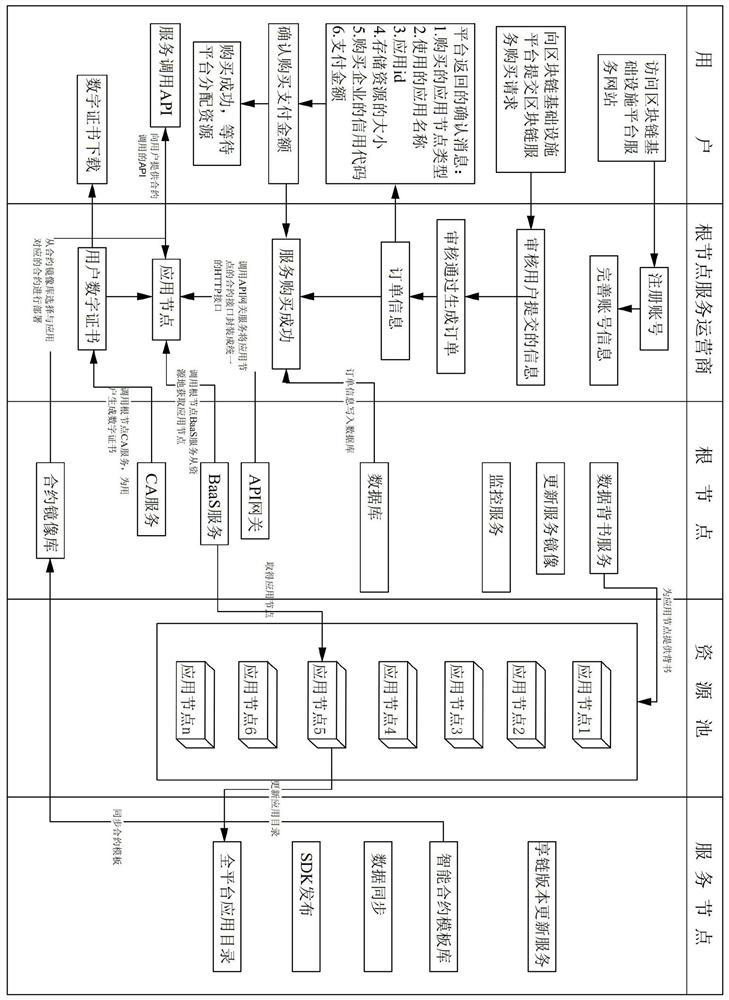
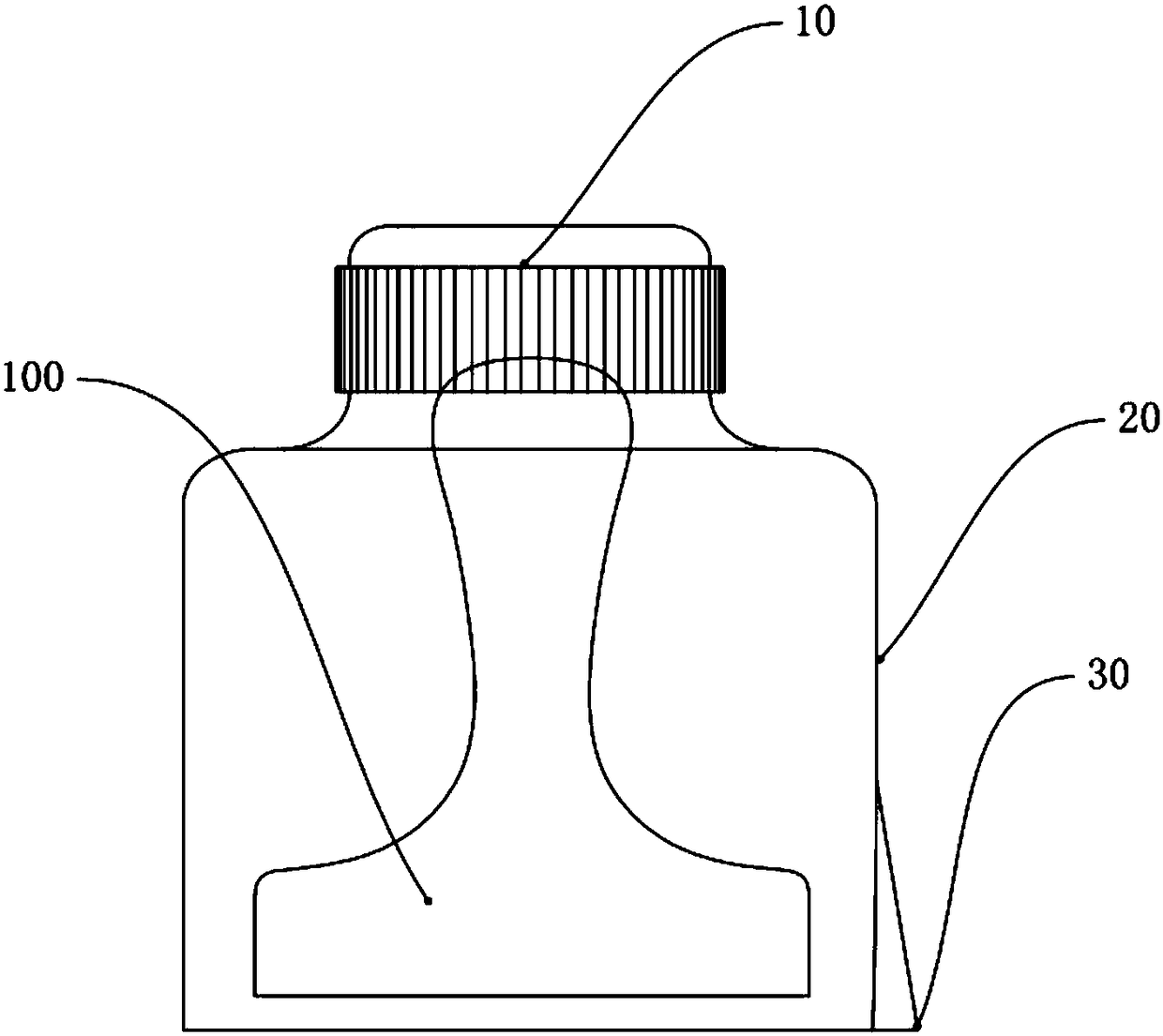
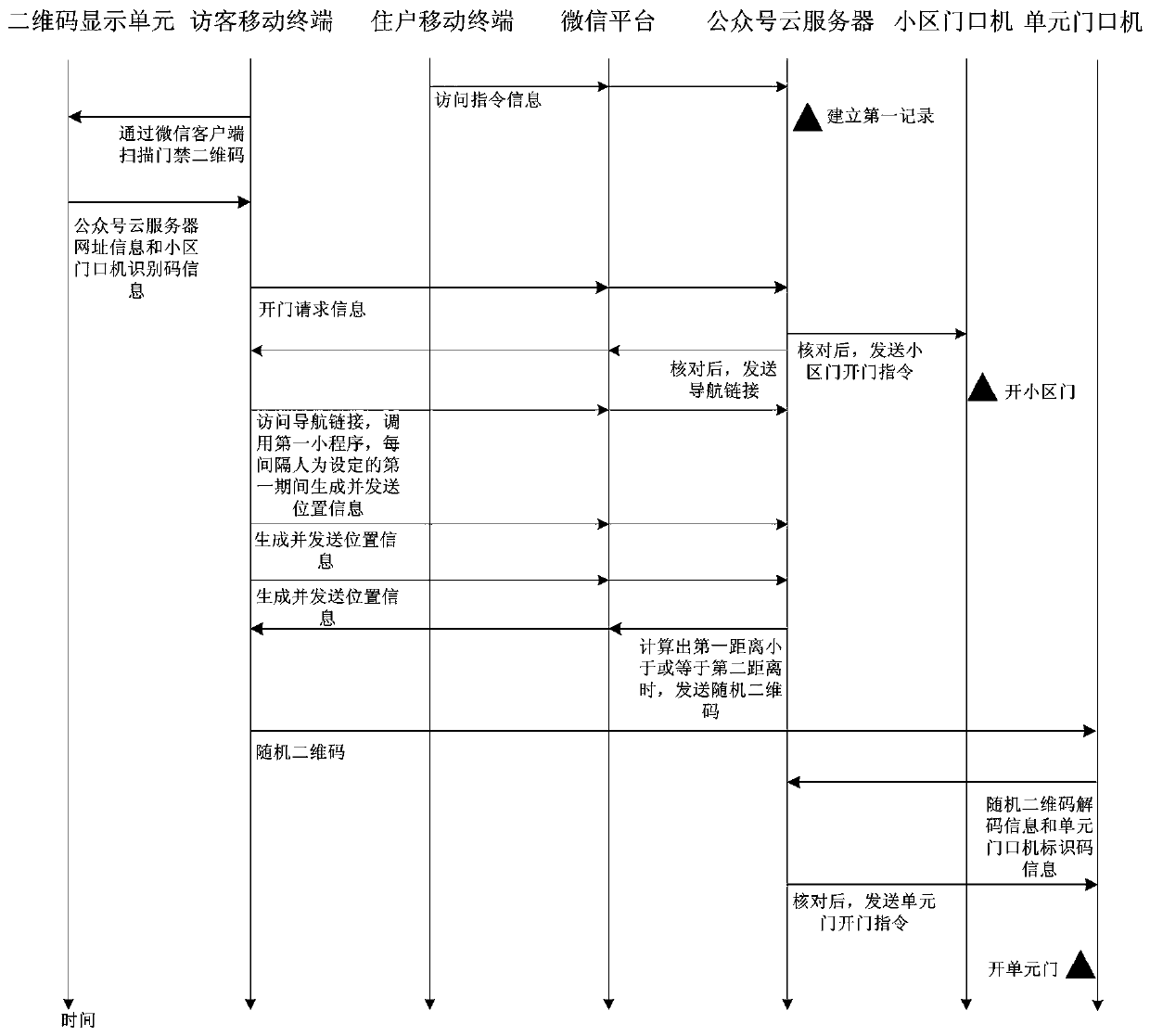
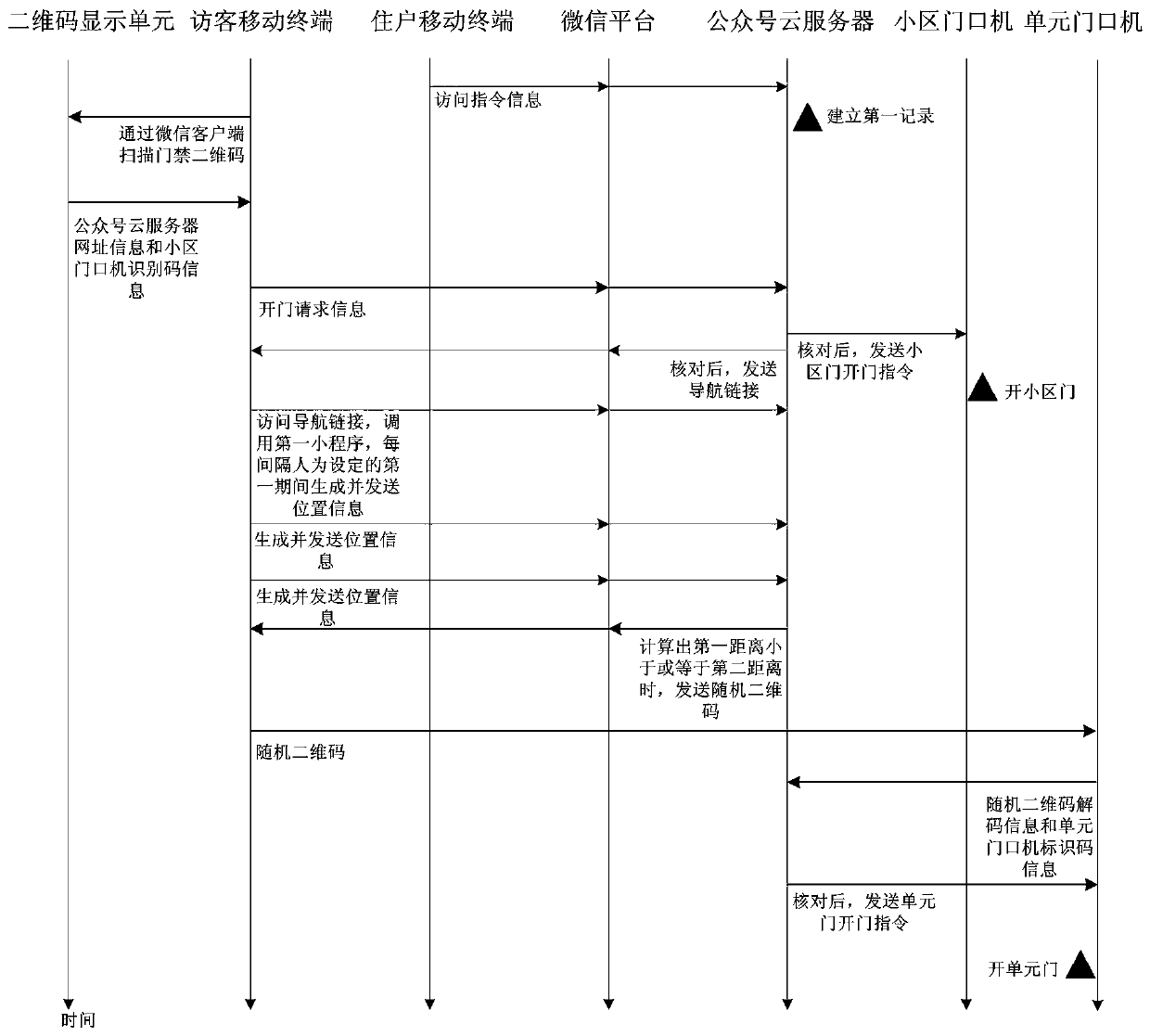
Community access control system based on WeChat and door opening method
ActiveCN107507305AWide range of servicesLow costIndividual entry/exit registersData switching networksAccess timeComputer terminal
The invention discloses a community access control system based on WeChat and a door opening method. The community access control system based on WeChat comprises a two-dimensional code display unit, a WeChat platform, a household mobile terminal, a visitor mobile terminal, an official account cloud server, a community entrance machine and a unit entrance machine. By subscribing an access control cloud service WeChat official account through the household mobile terminal and the visitor mobile terminal, communication of the official account cloud server and the household mobile terminal with the visitor mobile terminal can be realized. In the relevant door opening method, the household can carry out pre-authorization and limit the access time of a visitor, also the method can achieve identity verification of the visitor, also can provide navigation for the visitor from the community entrance machine to the unit entrance machine, and enhances the door opening experience of the household and visitor.
Owner:XIAMEN DNAKE INTELLIGENT TECH CO LTD
Dynamic access control method of pervasive computing
InactiveCN101039322AImplement authorizationImplement dynamic access controlData switching networksBiological activationMedia access control
The present invention discloses an access control method for common computing environment. The method realizes dynamic access control by combining a hierarchy credit mode with a role-based access control mode. The hierarchy credit mode is a structure with two hierarchies, wherein the bottom credit value determines the role assignment; the upper credit value determines the role activation and the permitted activation. The upper credit value is related to applied context, different upper credit values correspond to different activated roles and permission, thus the obtained service is different. The method is mainly applied in solving the problem of authorization in common computing environment as well as in realizing access control to the applied resources in other dynamic environments.
Owner:HUAZHONG NORMAL UNIV
Data query method and device
ActiveCN110096899AImplement authorizationImprove securityDigital data protectionData miningData query
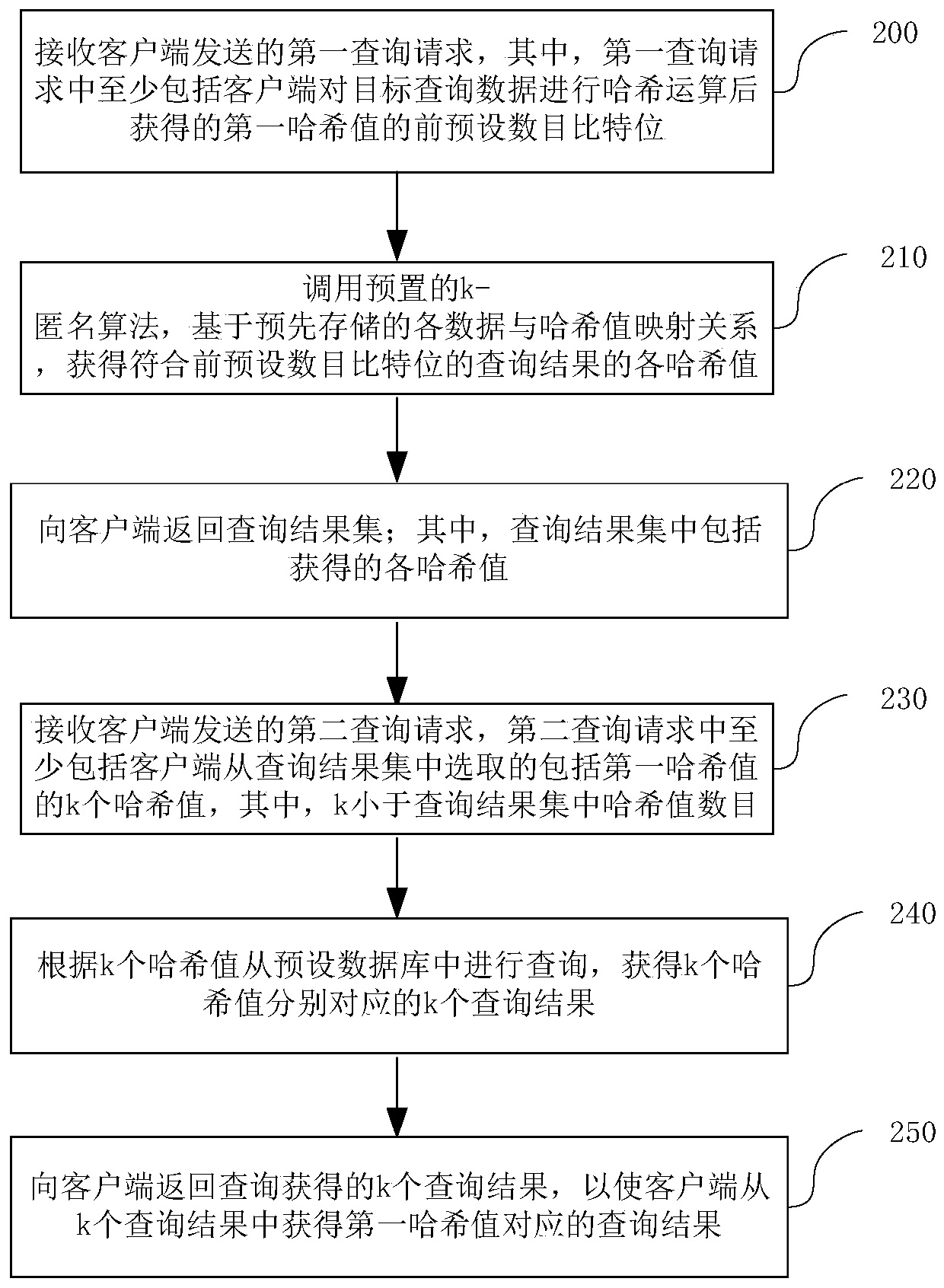
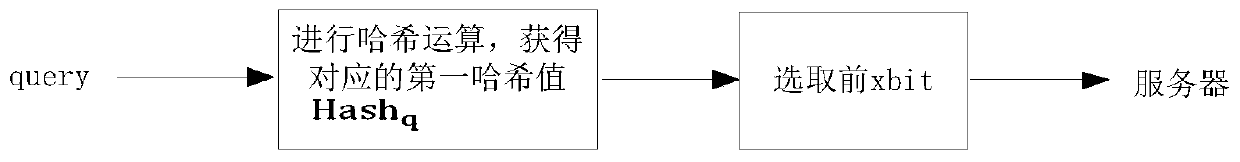
The invention relates to the technical field of computers, in particular to a data query method and device, and the method comprises the steps: receiving a first query request sent by a client, the first query request at least comprising a previous preset number of bits of a first Hash value obtained after the client performs Hash operation on target query data, and calling a preset k-anonymous algorithm for obtaining hash values of the query results conforming to the previous preset number of bits on the basis of pre-stored mapping relationships between the data and the hash values; and according to the obtained Hash values, performing query from a preset database, and returning k query results to the client, so that the client obtains a query result corresponding to the first Hash valuefrom the k query results. In this way, data query desensitization protection is realized based on the k-anonymous algorithm, and a server cannot determine a target query result in k query results, sothat the target query data cannot be leaked even if the target query data does not exist in a database, and the security is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Intelligent stamp cloud management system and stamp use content abnormality identification and control method
InactiveCN107451793ASolve control problemsPlug management loopholesOffice automationTransmissionBlind zoneManagement process
The present invention provides an intelligent stamp cloud management system and a stamp use content abnormality identification and control method. The system comprises a cloud management server, cloud smart stamp terminals and cloud management clients; the cloud smart stamp terminals send stamping information and stamped document pictures to the cloud management server for storing the stamping information and the stamped document pictures, and generate search codes; the cloud management clients are used for document stamping application, inquiry, approval and warning and upload original documents which people apply for stamping the cloud management server through a cloud network; and the cloud management server is used for verifying the authenticity of stamped documents and sending verification results to the cloud management clients. According to the intelligent stamp cloud management system and the stamp use content abnormality identification and control method of the invention, the cloud management server of stamps is connected with the cloud smart stamp terminals with intelligent functions and network functions, and the cloud management clients, and therefore, stamp control cloud-based intellectualization and control flow integrity can be realized, and the problems of incomplete management flow monitoring and high control risk caused by the blind zones of a traditional stamp management flow can be solved.
Owner:童迎伟
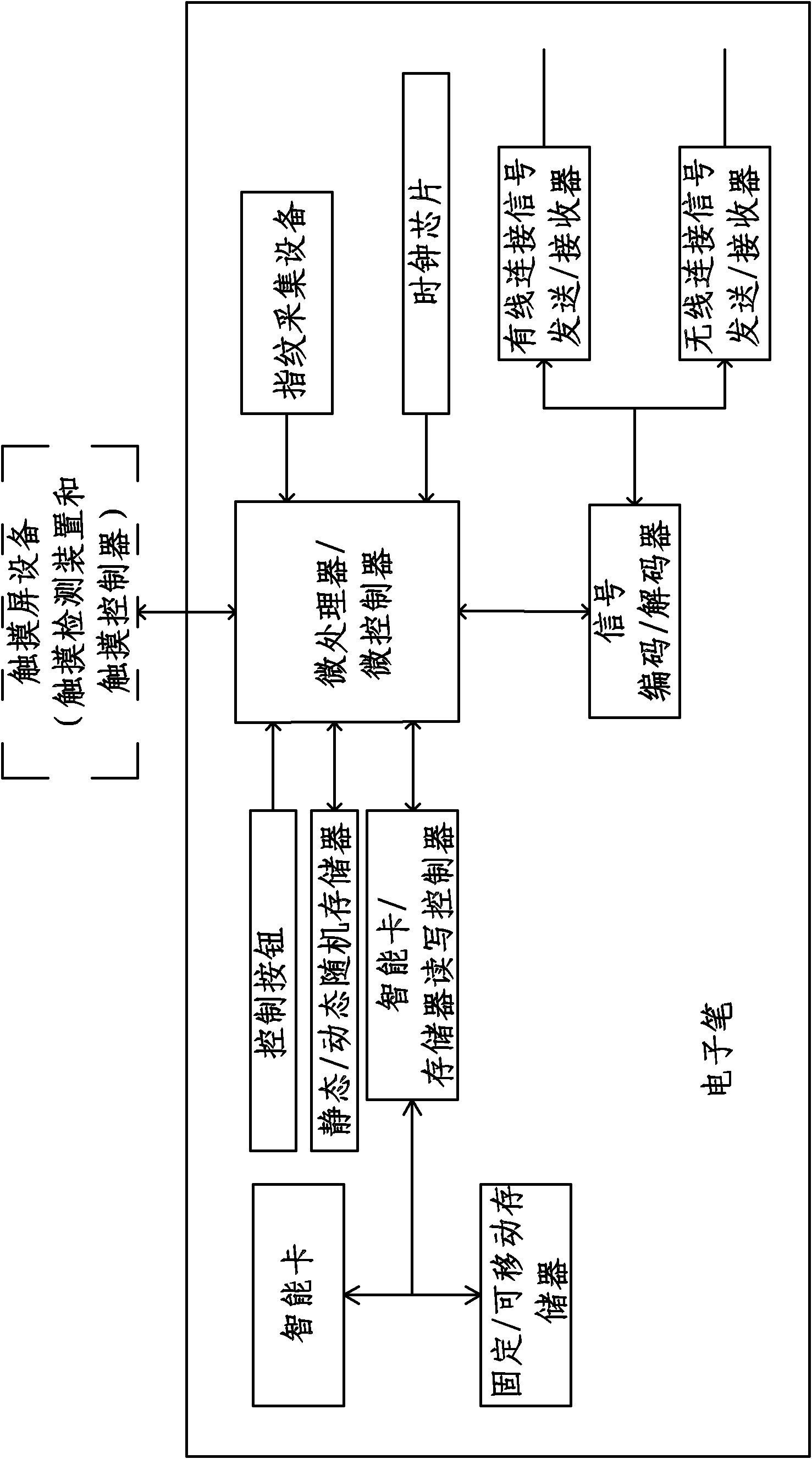
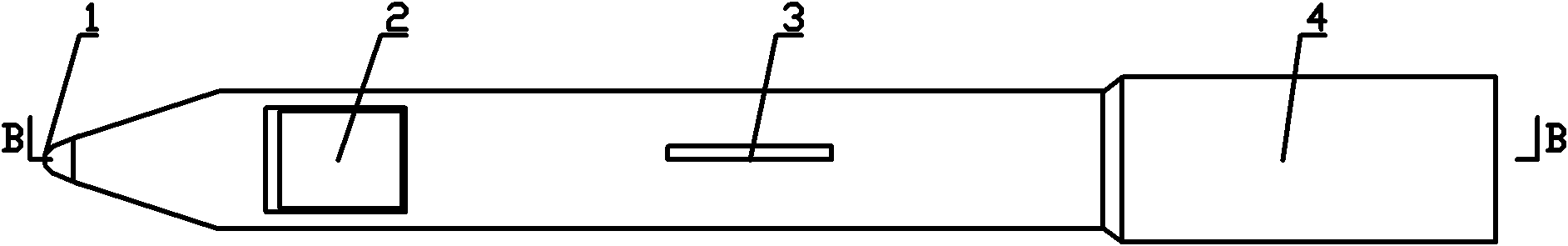
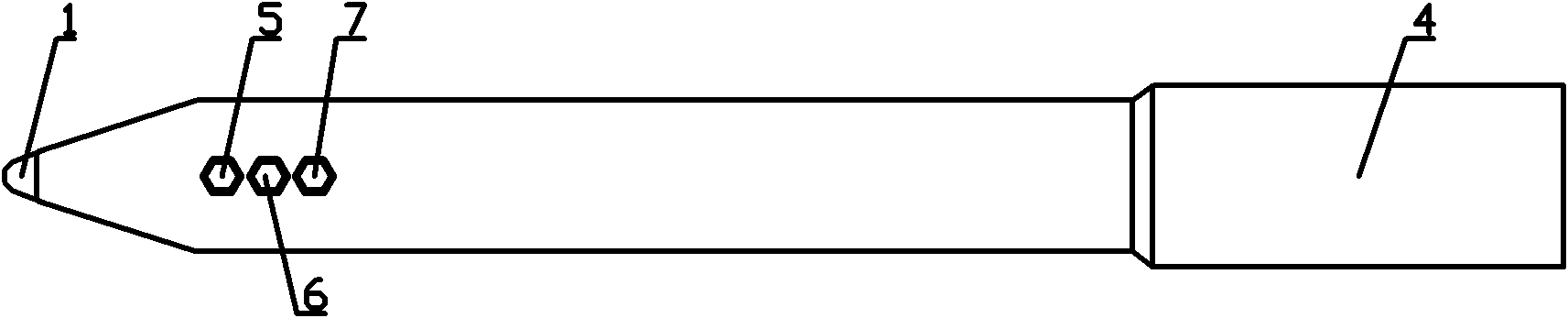
Multifunctional electronic pen and software authorization method thereof
InactiveCN102163091ATraceableAchieving non-combinabilityWriting implementsProgram/content distribution protectionControl systemComputer module
The invention discloses a multifunctional electronic pen and a software authorization method thereof. The electronic pen comprises a pen body and a pen refill part which is arranged in the pen body, wherein the pen refill part comprises a writing pen refill and an electronic pen refill; a writing end of the writing pen refill is arranged in a pen nib at the lower end of the pen body; the electronic pen refill comprises a power system, a data processing module, a function control system, a clock chip, a card read-write system and a fingerprint acquisition processing system and a wired or wireless connection device; the power system and the data processing module are arranged in the pen body; the function control system, the clock chip and the card read-write system are connected with the data processing module; the fingerprint acquisition processing system is arranged on the central section of the pen body; and the wired or wireless connection device is arranged at the rear end of the pen body. The electronic pen can be used for writing electronically, can realize ink writing, can carry out recording and storage in the process of electronic writing, can add identity identifiers and time identifiers into writing tracks in storage process, and can effectively guarantee personal intellectual products by combining the software authorization method of the multifunctional electronic pen.
Owner:王东
Method and system for intensively operating and controlling several network security devices
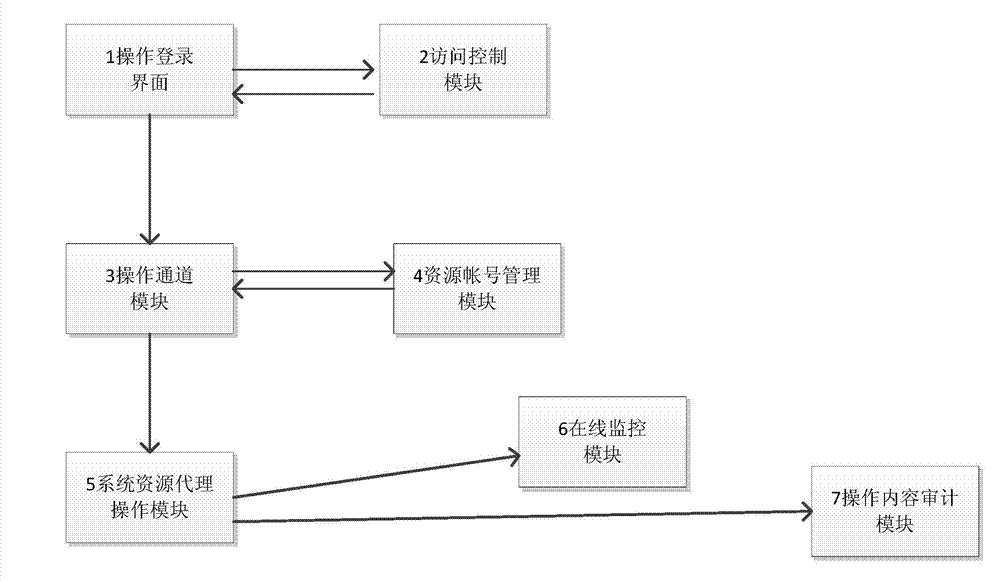
ActiveCN104753959APrevent leakageRealize identity authenticationUser identity/authority verificationData switching networksOriginal dataHeterogeneous network
The invention relates to a method and a system for intensively operating and controlling several network security devices. An access control module is connected with an operation login interface, a resource account management module is connected with an operation channel module, and an online monitoring module and an operation content audit module are connected with a system resource agency operation module. The method includes starting remote operation security device requests, and acquiring remote management passwords of the security devices from a password bank; converting the operation requests into original device operation commands, and letting system agencies log in; analyzing original data packets of operation into original commands, recording the original commands of the operation to realize audit. The method and the system for intensively operating and controlling the network security devices have the advantages that the system adopts the security operation control and audit technology to set up a centralized operation portal, for operation of the heterogeneous network system, intensive multi-identity verification, authorized access control, remote control, monitoring and recording of operation behaviors are realized, and rule-breaking operations are stopped.
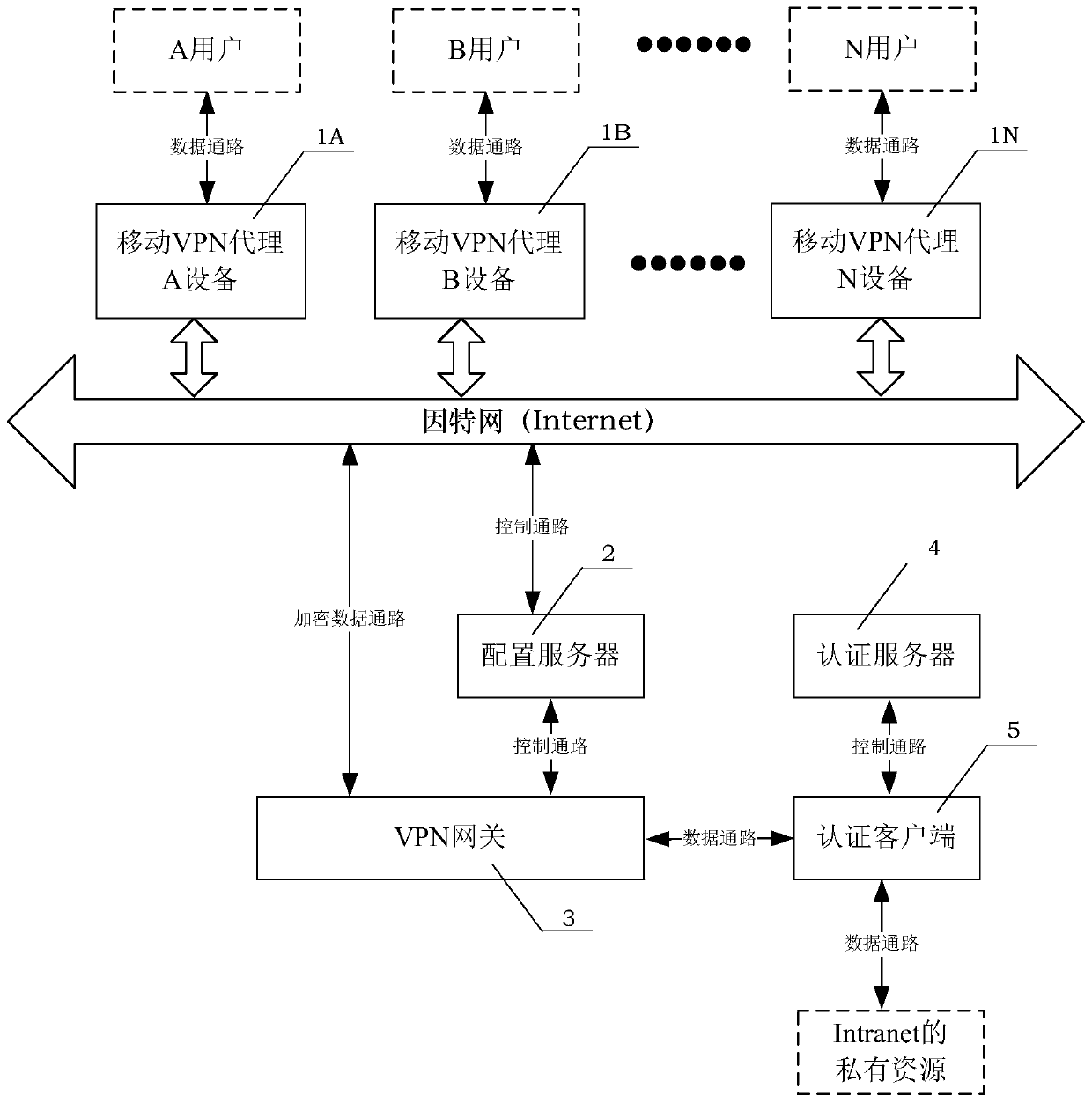
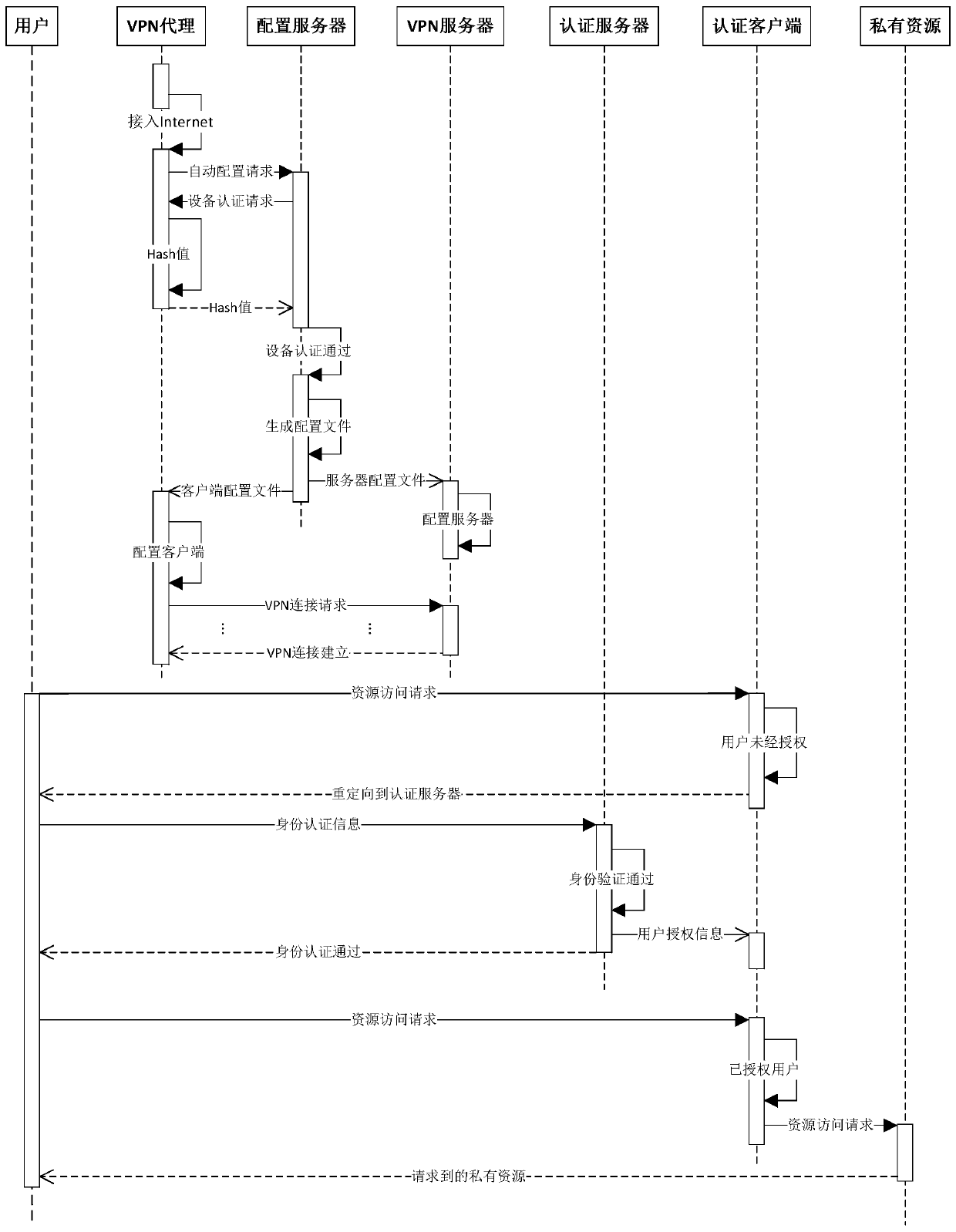
Intranet access system based on IPsec VPN proxy
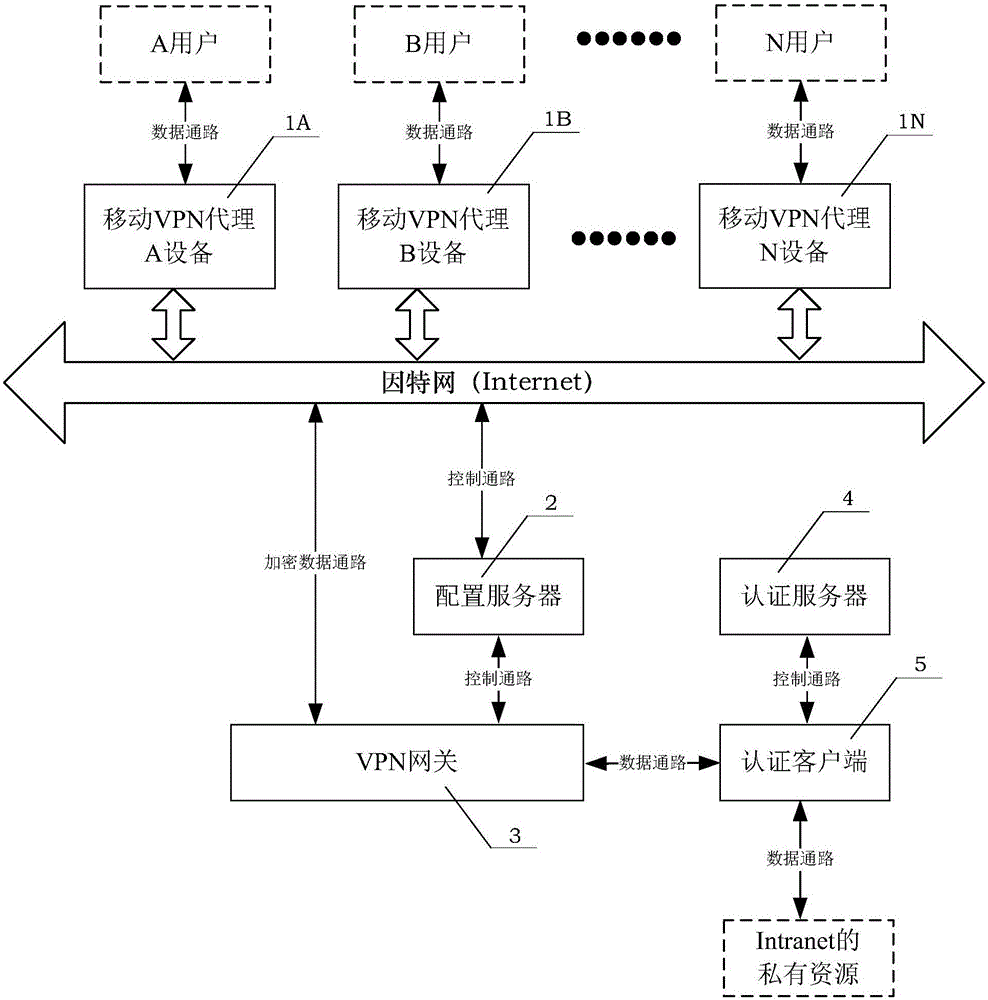
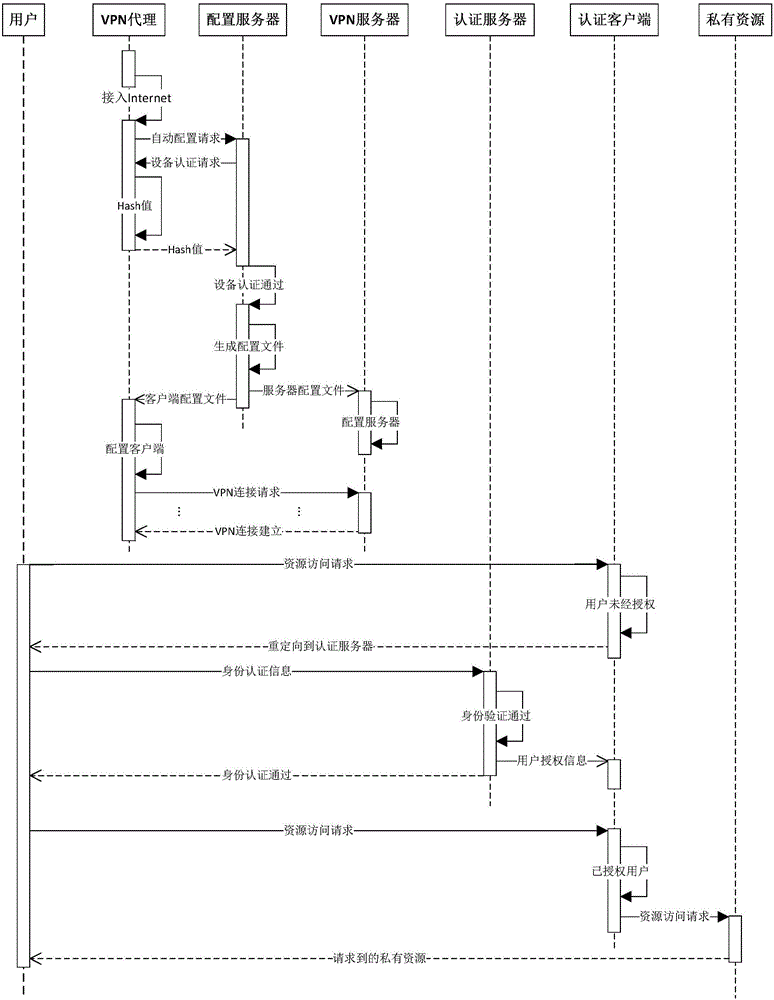
ActiveCN106685785ASimplify configuration managementEasy background maintenanceNetworks interconnectionIPsecAuthentication server
The invention discloses an Intranet access system based on an IPsec VPN proxy. The system comprises a mobile VPN proxy device, a configuration server, a VPN gateway, an authentication server and an authentication client. The mobile VPN proxy device is communicated with the configuration server and the VPN gateway through the internet; a user request is transmitted through the mobile VPN proxy device and the VPN gateway, so that the user request reaches the authentication client; then the user request authorization is achieved by the authentication client and the authentication server through an intranet. By means of the access system, a user accesses the Intranet through the mobile VPN proxy device, and then the user access request authorization is achieved through the authentication server and the authentication client. An IPsec tunnel is established by the VPN gateway and the mobile VPN proxy device without user participation, the threshold for using the IPsec VPN is lowered, and the disadvantage that the IPsec VPN is difficult to use and maintain is overcome.
Owner:BEIHANG UNIV
File safety management system based on mobile terminal
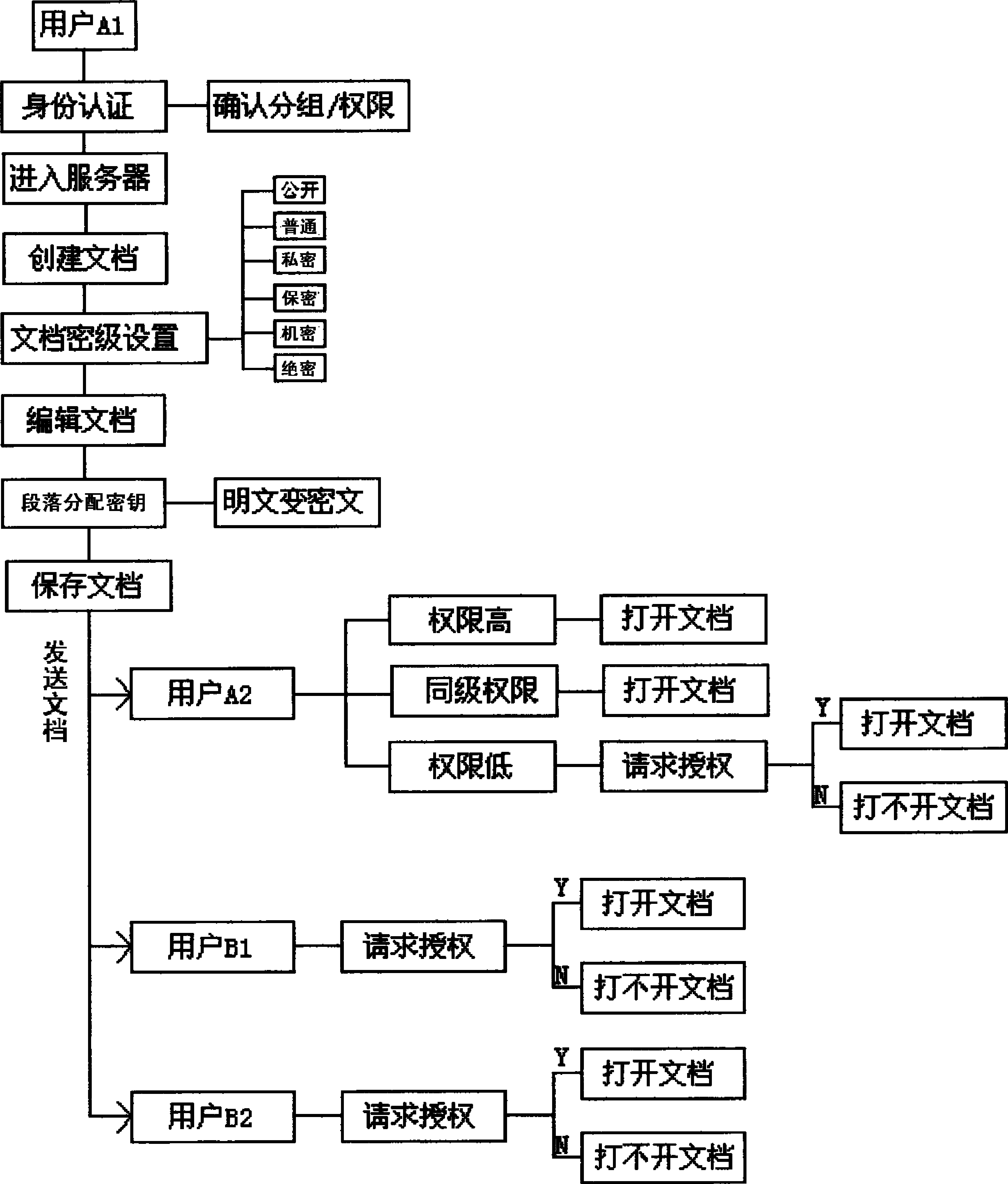
InactiveCN102938762AImplement authorizationRealize confidentiality managementKey distribution for secure communicationUser identity/authority verificationWireless mesh networkPacket loss
The invention discloses a file safety management system based on a mobile terminal. The system is realized by an authority grouping module, an access identity authentication module, a key distribution module and a security classification management module, a terminal user and a user group are connected to a server by a wireless network and are connected with each other by the wireless network to transmit and receive a file; and due to the adoption of the methods such as access identity authentication, authority grouping and key distribution, not only can file authorization and security classification management in the mobile terminal be realized, but also the inquiry of a ciphertext can not be affected by the error of the ciphertext under the condition of the error code or packet loss of a wireless network, and the error code robustness is good.
Owner:深圳出入境检验检疫局信息中心 +1
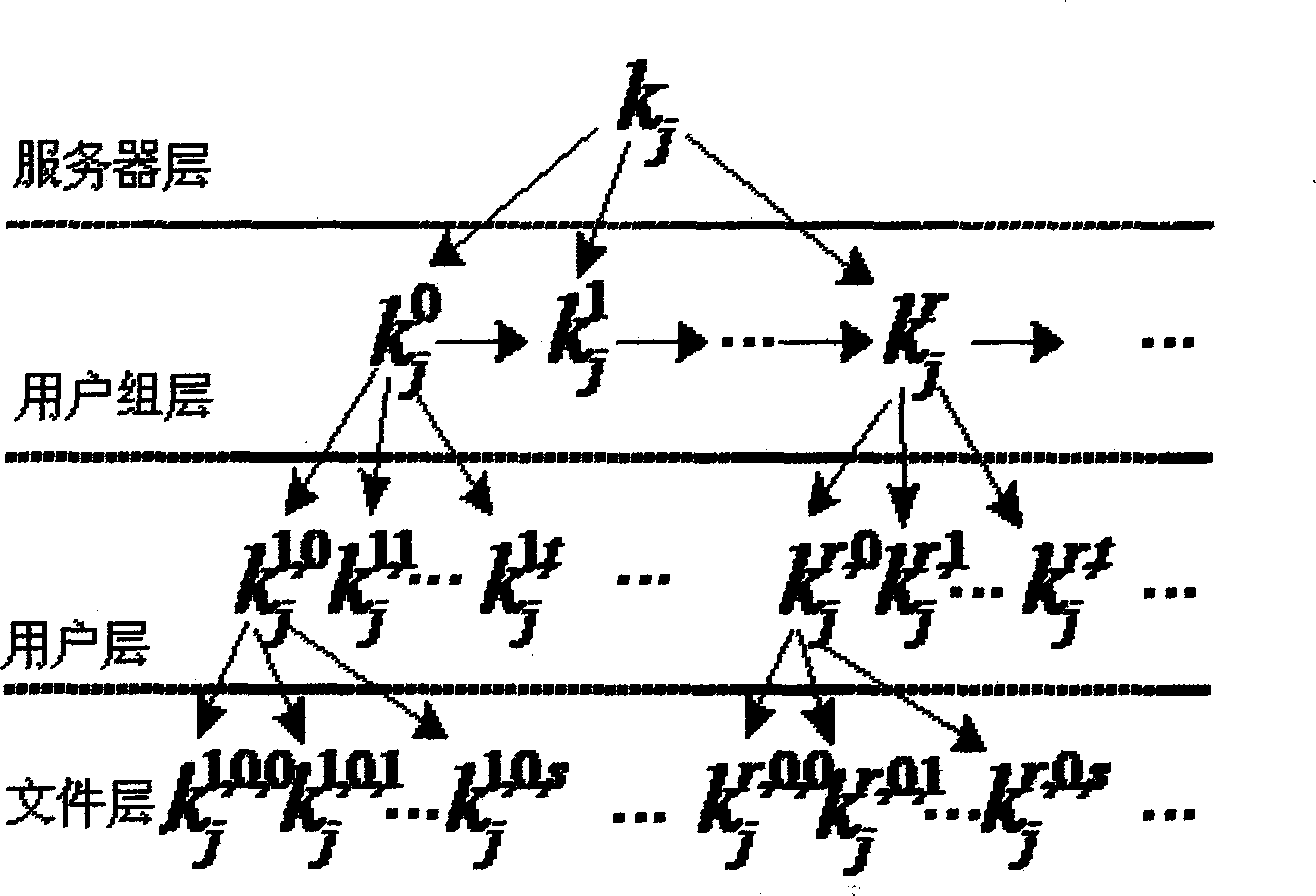
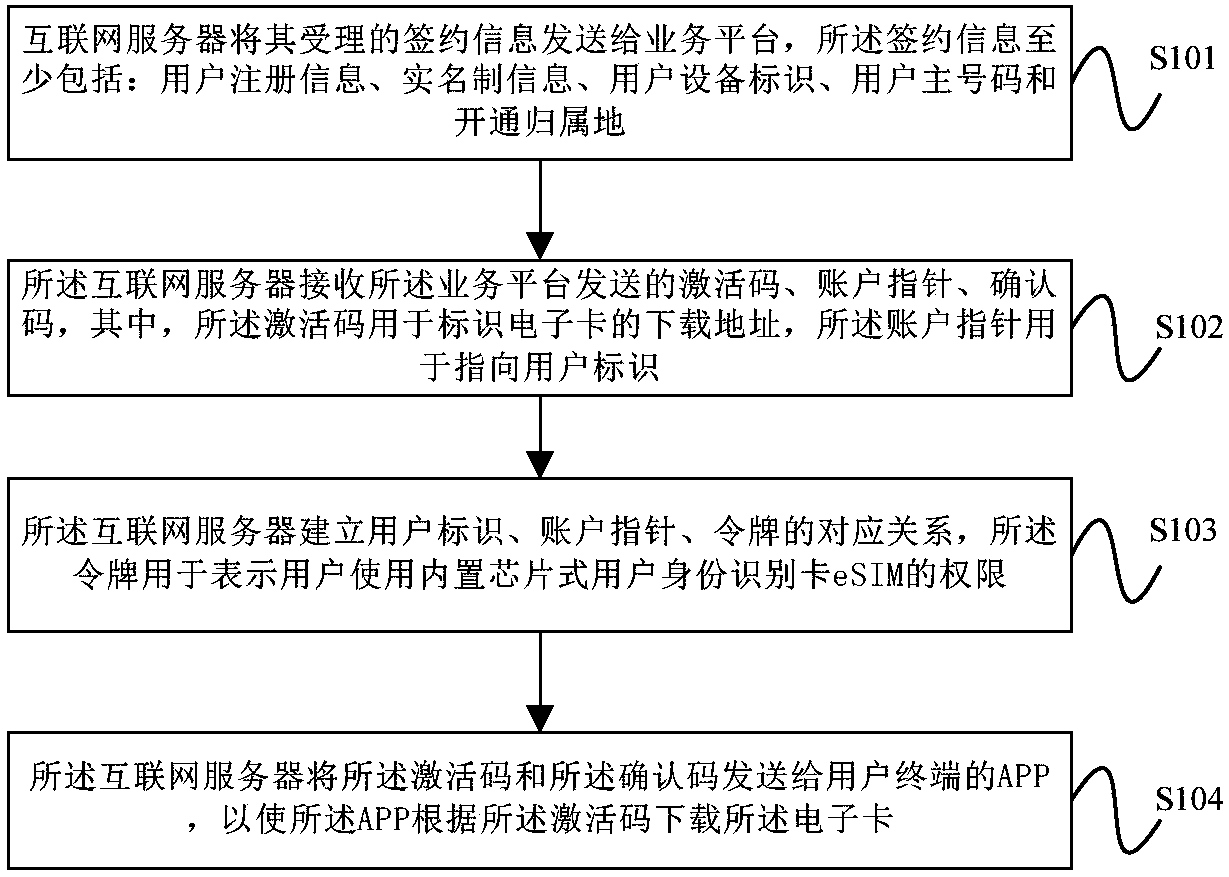
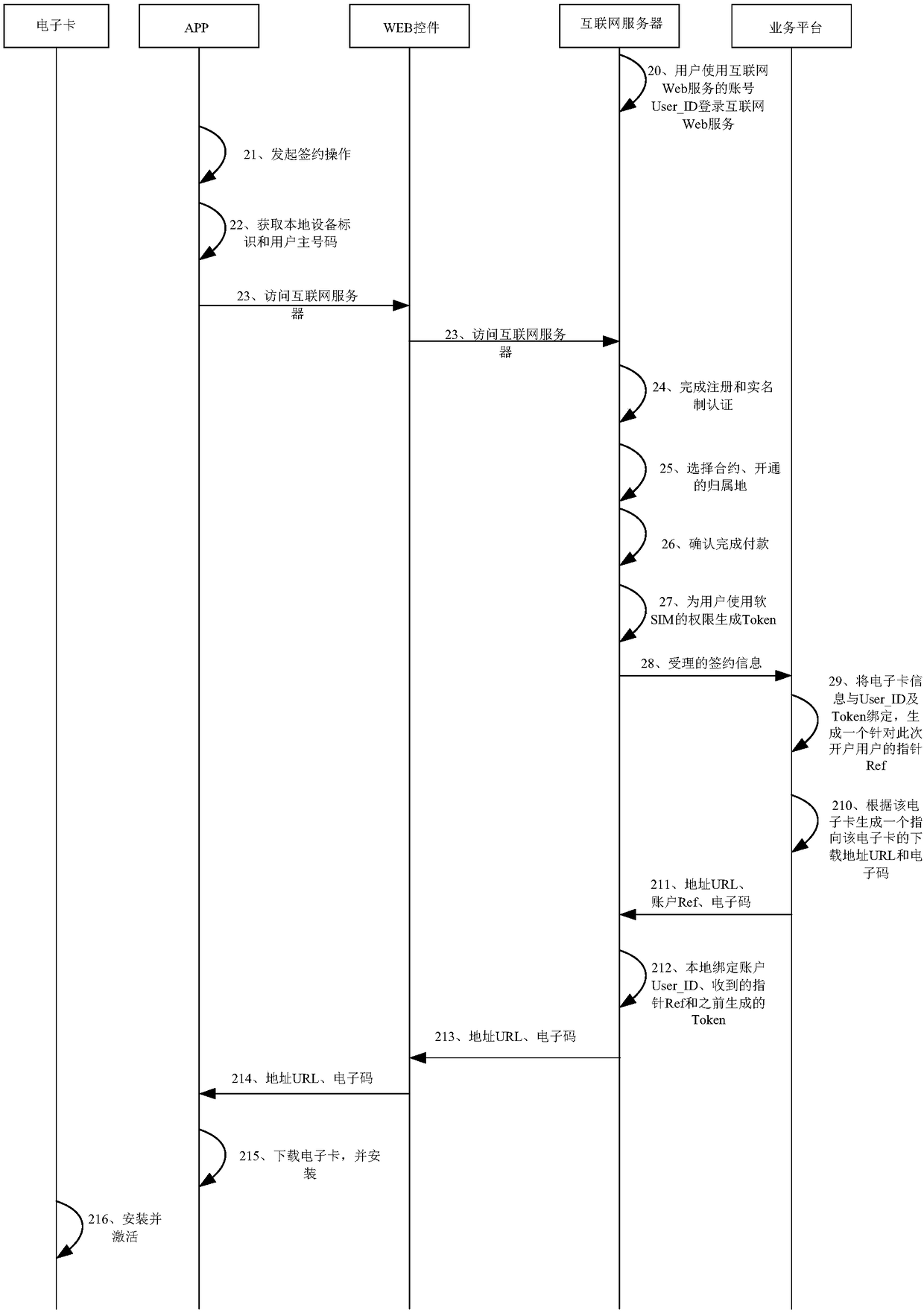
Data processing method and apparatus of mobile communication electronic SIM card
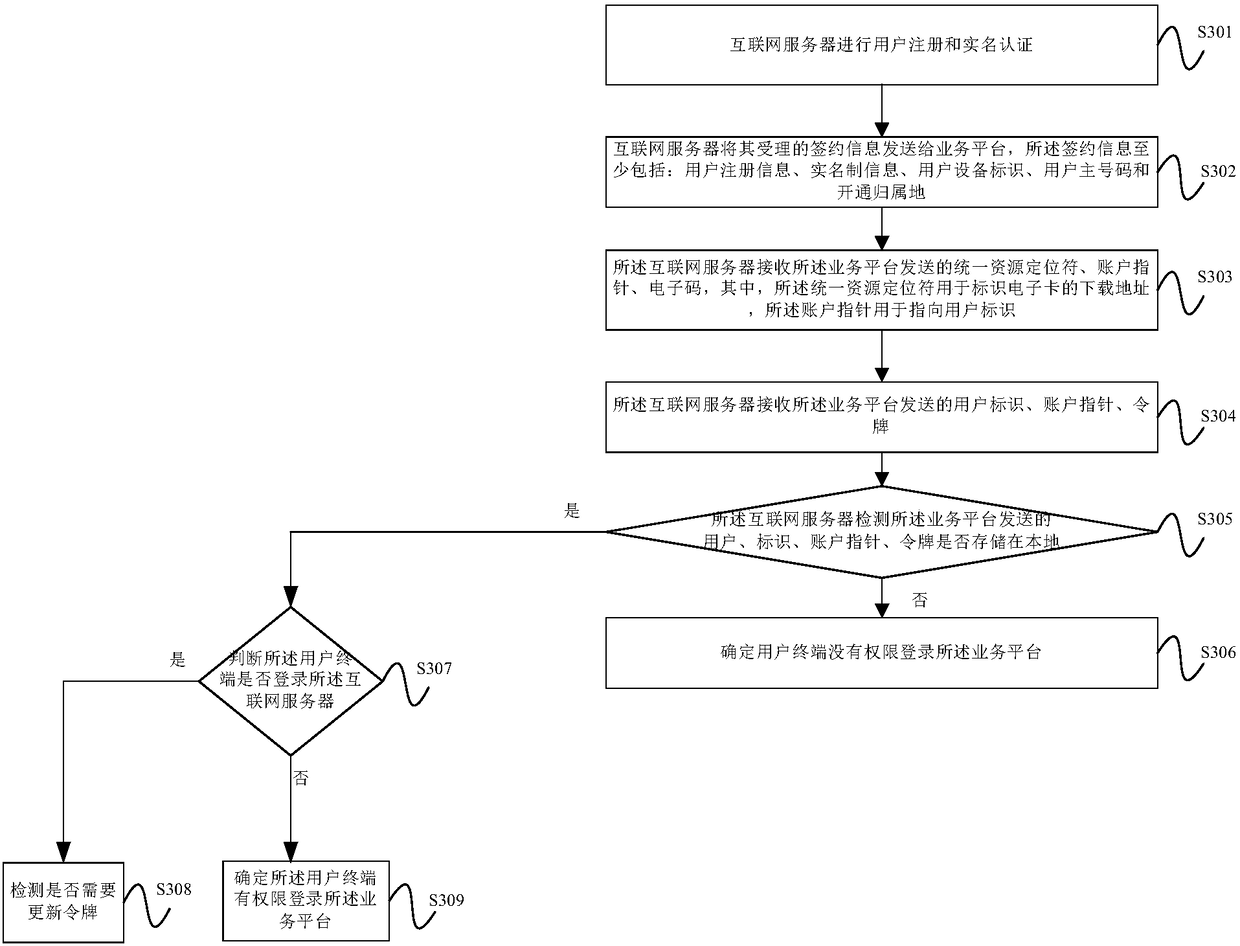
ActiveCN108200568ARealize real-name authenticationImplement identity authenticationNetwork data managementComputer terminalUser identifier
The embodiment of the invention provides a data processing method and apparatus of a mobile communication electronic SIM card. The method comprises the following steps: sending, by an Internet server,accepted subscription information to a service platform; receiving an activation code, an account pointer and a confirmation code sent by the service platform; establishing a corresponding relationship between a user identifier, the account pointer and a token; and sending the activation code and the confirmation code to an APP of a user terminal. In the embodiment of the invention, the acceptedsubscription information is sent to the service platform by the Internet server, the activation code, the account pointer and the confirmation code sent by the service platform are received, the corresponding relationship between the user identifier, the account pointer and the token is established, and the activation code and the confirmation code are sent to the APP of the user terminal, so thatthe APP downloads the electronic card according to the activation code, and real name authentication and user identity authentication in mobile communication are achieved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Automatic logion method based on IC card for server with multiple main domains
InactiveCN1373429AAdvantages of the automatic login methodChange the physical structureMultiple digital computer combinationsRecord carriers used with machinesApplication softwareOperating system
An automatic login method for multi-maindomain server based on IC card is characterized by that the user can use IC card and PIN cipher to log in. Its advantages are no change of physical structure of network, no addition to network load, independency of application, and low cost of program transplantation.
Owner:上海光华如新信息科技股份有限公司
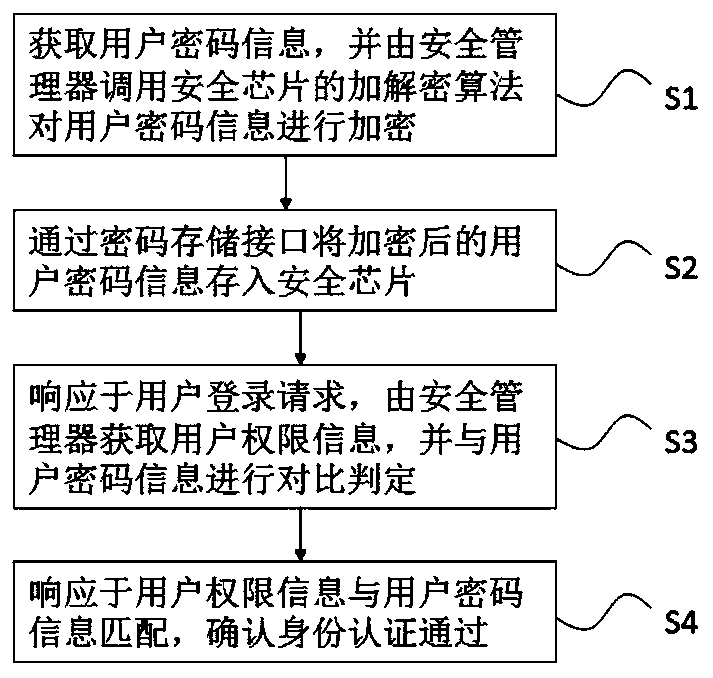
Identity authentication method and device based on security chip, and medium
PendingCN110765449AImplement identity authenticationImplement authorizationDigital data protectionDigital data authenticationSession managementUser Privilege
The invention discloses an identity authentication method based on a security chip, which comprises the following steps: acquiring user password information, and calling an encryption and decryption algorithm of the security chip by a security manager to encrypt the user password information; storing the encrypted user password information into a security chip through a password storage interface;in response to the user login request, acquiring user permission information by the security manager, and comparing the user permission information with the user password information for judgment; and in response to matching of the user permission information and the user password information, confirming that identity authentication is passed. The invention further discloses a computer device anda readable storage medium. According to the identity authentication method and device based on the security chip and the medium, basic security services are provided for a system platform and software by using the security chip, a safer and more reliable system platform environment is established, and the functions of identity authentication, authorization, encryption, session management and thelike of an application program are further achieved.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
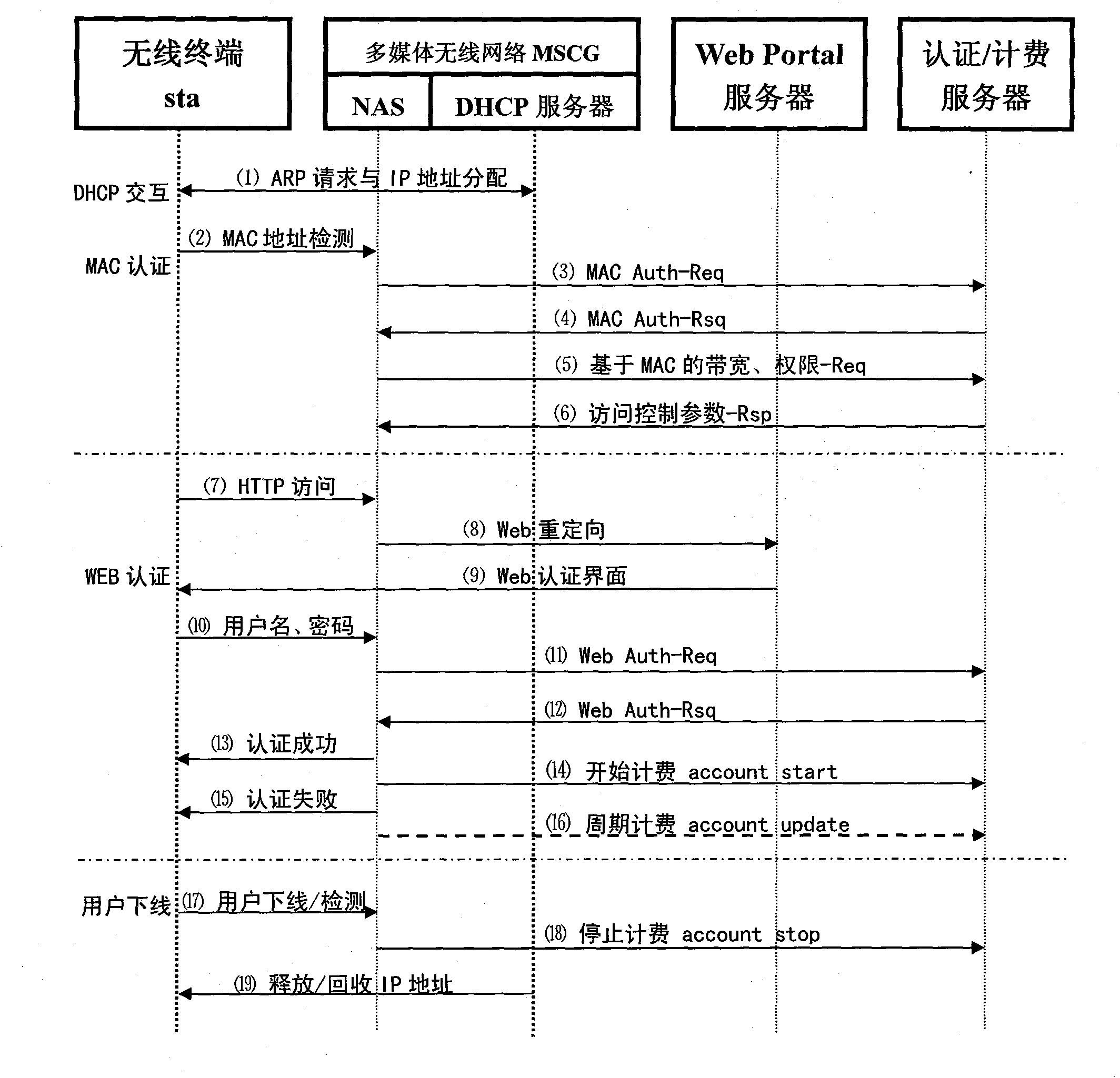
Authentication system capable of supporting multimedia wireless gateway
InactiveCN101778386AImplement access controlImplement priority controlUser identity/authority verificationSecurity arrangementQuality of serviceOperational system
The invention discloses an authentication system capable of supporting a multimedia wireless gateway, and is a software system for authentication, authorization and management between users on local or ex-situ remote wireless hot point networks and terminal equipment. The software system can control the priority of service access, bandwidth and quality of service, and also can support services such as wi-fi / voip mobile phone authentication and position service. The software system is developed on an Linux operating system, and adopts a My SQC or Oracle database; and the main function modules of the software system comprise Radius authentication and authorization software, service authority management and control software, an MAC address authentication and Wi-Fi mobile phone / PDA terminal and Voip service support software, and position information collecting and processing software.
Owner:北京天昭信息通信系统开发有限责任公司
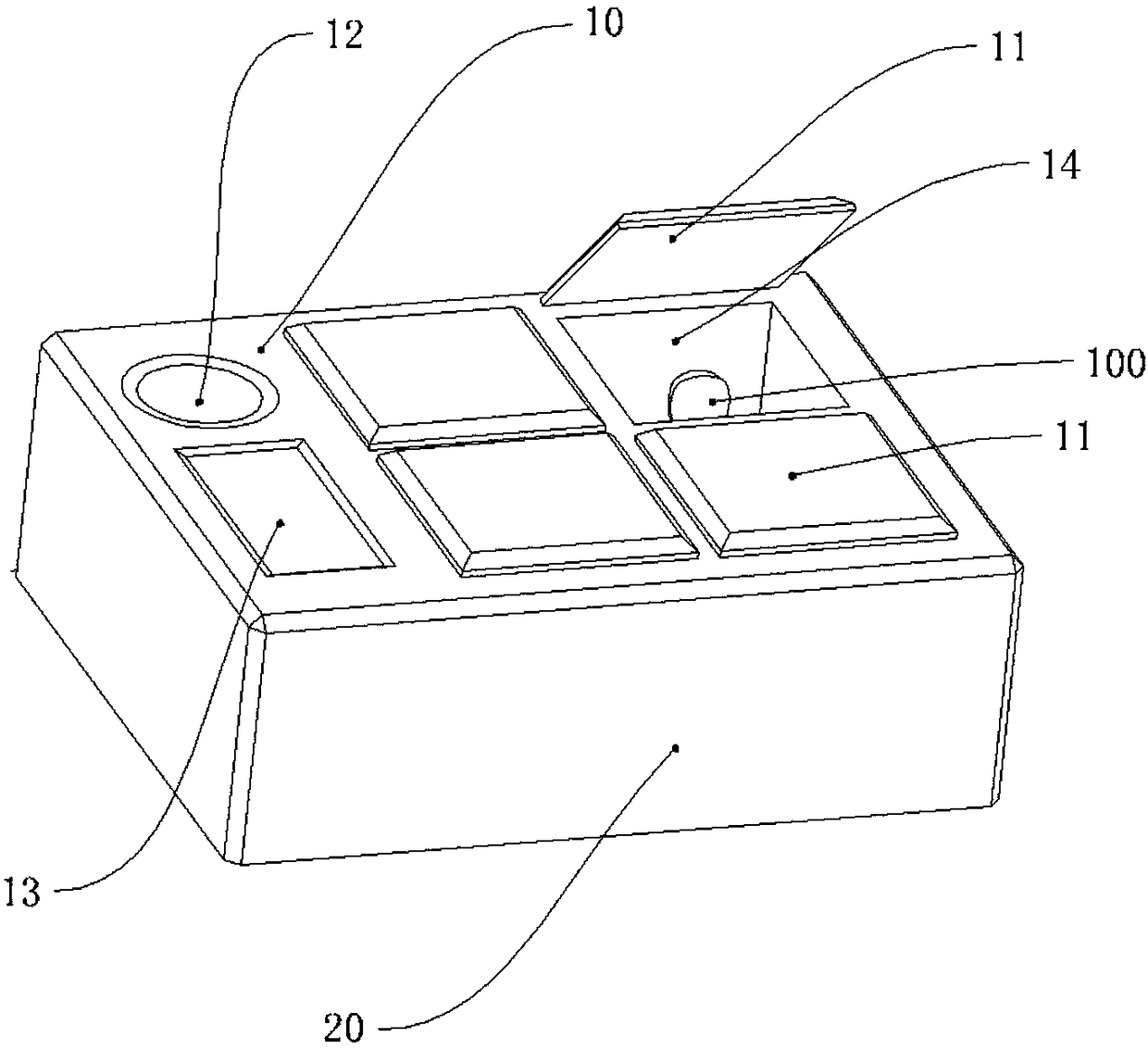
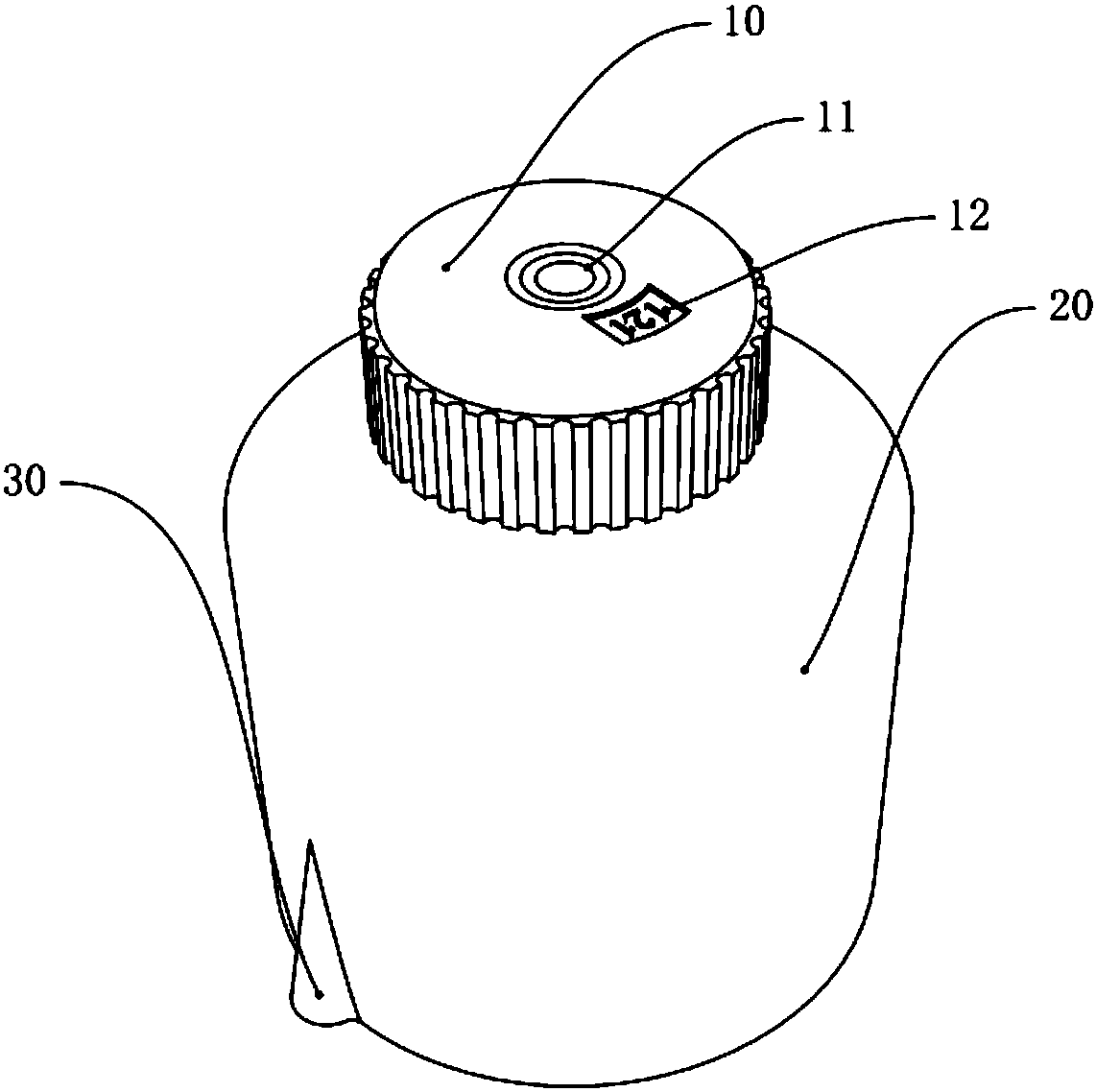
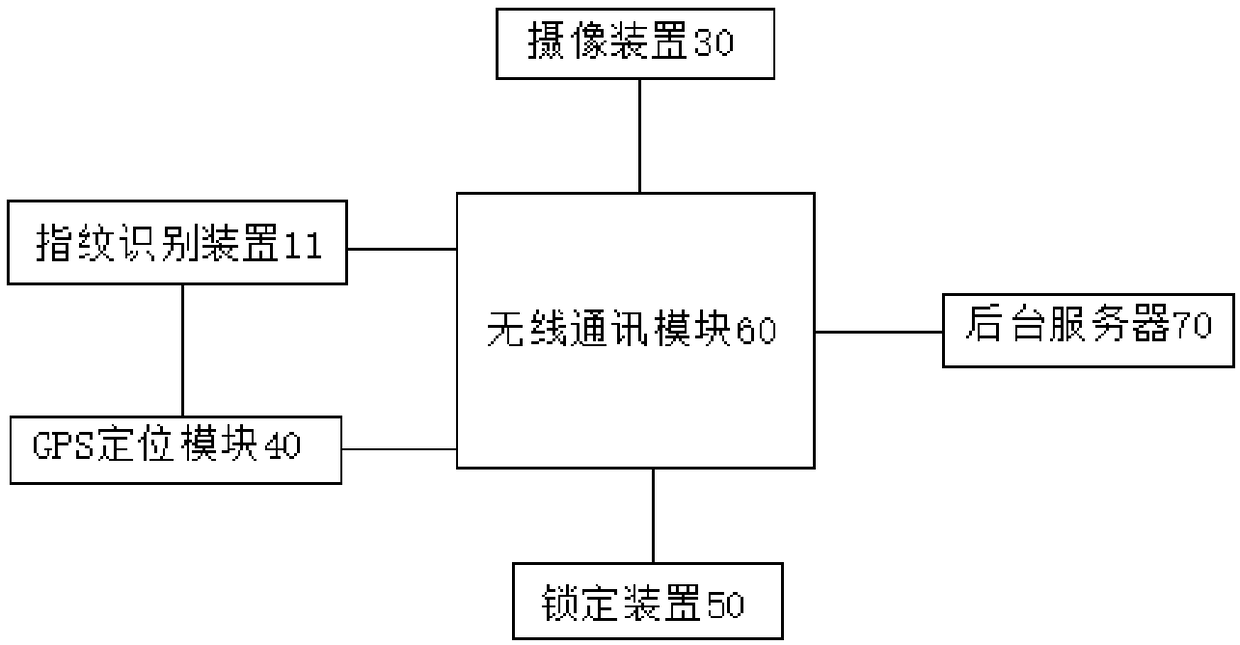
Seal protection box and application method of seal protection box
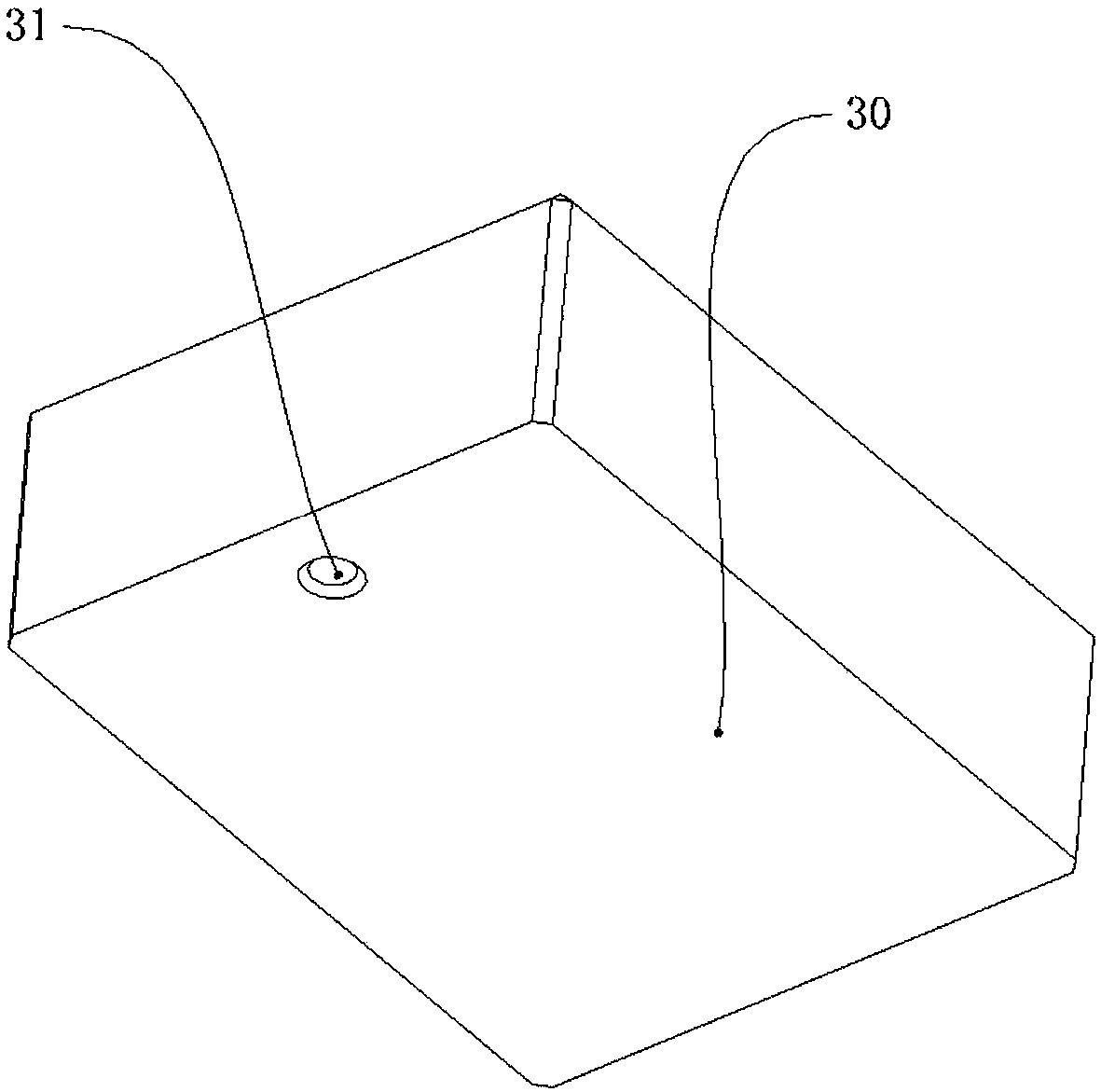
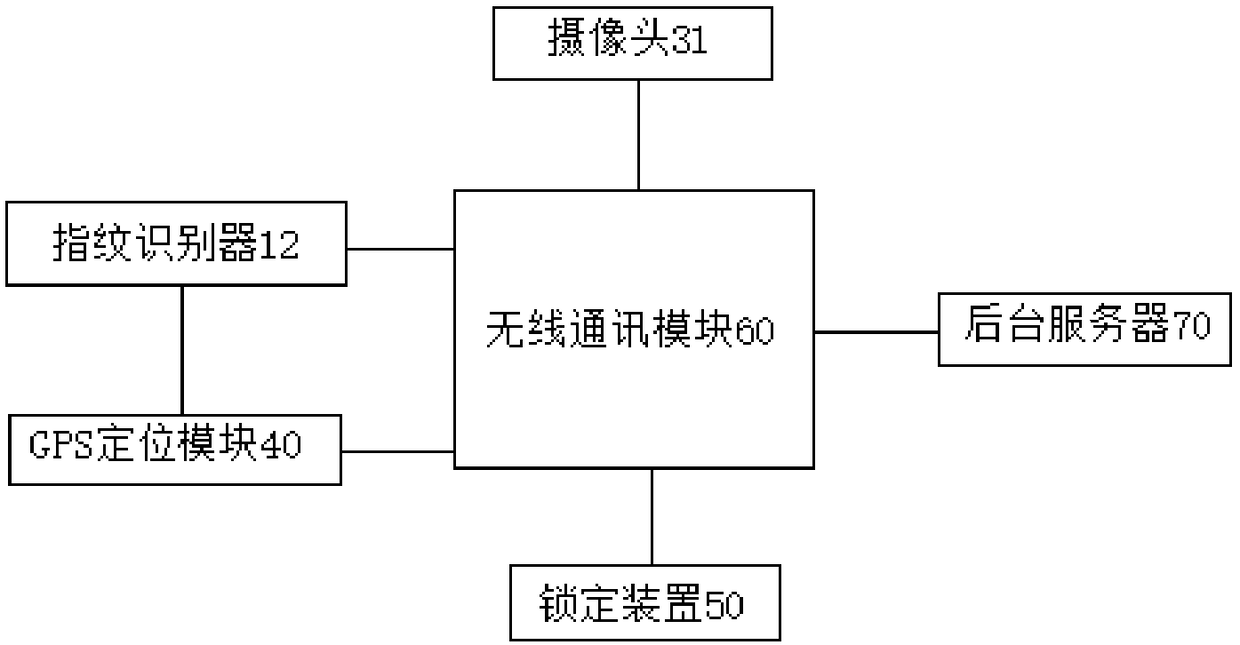
PendingCN108573557AImplement security managementTimely transmissionIndividual entry/exit registersStampingFingerprintAuthorization
The invention discloses a seal protection box and an application method of the seal protection box. The seal protection box comprises a shell body, a top wall, a bottom wall and at least two upper covers, wherein a fingerprint identifier is arranged at the first side of the top wall; the shell body is internally provided with a cavity; the cavity is internally provided with a wireless communication module, a GPS (Global Positioning System) positioning module and a locking device; the GPS positioning module, the fingerprint identifier and the locking device are communicated with a background server through the wireless communication module; a containing cavity is formed between one upper cover and the shell body; an opening is formed above the containing cavity and the upper cover covers the opening of the containing cavity. According to the application method disclosed by the invention, the seal protection box is authorized to use. The seal protection box disclosed by the invention canbe used for conveniently and effectively realizing utilization authorization of a seal, and accurate tracking of a seal position, supervision, authorized utilization and safekeeping can be realized;the risks that the seal is stolen and abused are reduced; the safety management of the plurality of seals can be realized at the same time.
Owner:珠海实跃科技有限公司
Digital TV set top box
InactiveCN1731849AImplement authorizationSolve interactive data transferTwo-way working systemsSelective content distributionData informationConditional access
A digital TV set top box is composed of a channel decoding module, a signal source decoding module, a flash memory, a dynamic random access memory, a condition receiving module, a infrared receiver and a mobile communication receiving module, a mobile communication transmitting module, a built-in client identification card adopted by the mobile phone, an additive phone universal interface. The invention adopts the mobile data communication means to accomplish all the functions necessary for the digital TV set top box so that it realizes to watch TV program and all kind of data information on the simulated TV on the one-way wired TV network and transmits all kinds of data information. The invention realizes the digital TV transmitting function of the two-way wired TV network on the one-way wired TV network and identifies the client by the client information, and realizes the phone communication function by the phone universal interface.
Owner:孙文欢
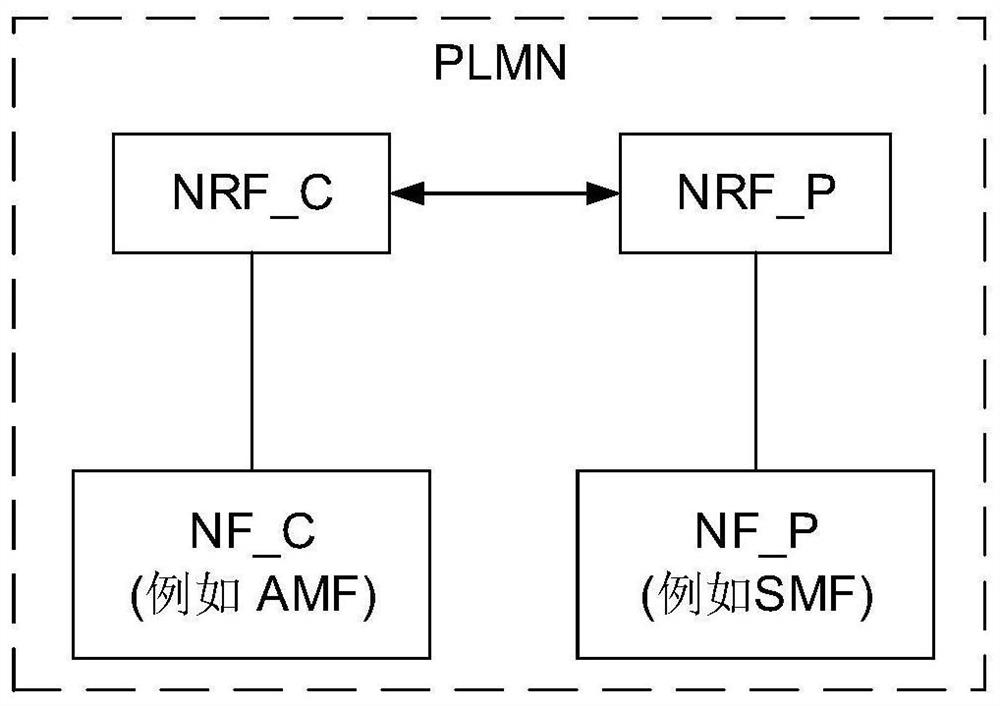
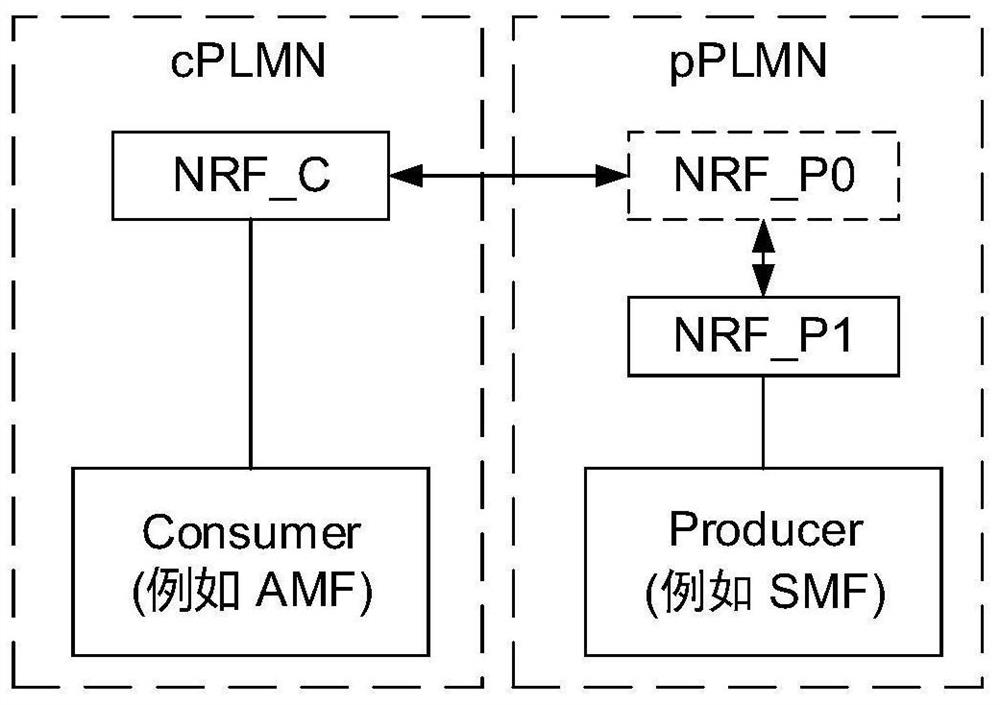
Authorization method under multiple NRF scenes
InactiveCN112492592AMake up for the vacancyImplement authorizationUser identity/authority verificationSecurity arrangementEngineeringAuthorization
The embodiment of the invention provides a network function service authorization method and device, and the method comprises the steps that a first network storage function network element NRF receives a first token request, and the first token request comprises the identification of a service provider network function NF_P; the first NRF determines a target network storage function network element NRF registered by each service provider NF_P according to the identifier; if a second network storage function NRF exists in the target NRF, a second token request is sent to the second NRF; the second NRF generates a token according to the second token request and returns the token to the first NRF; and after the first NRF receives the token sent by the second NRF, the generated and / or received token are sent to a token requester. According to the technical scheme, the authorization problem under the condition that multiple NRF scenes exist in the same public land network PLMN can be solved.
Owner:HUAWEI TECH CO LTD
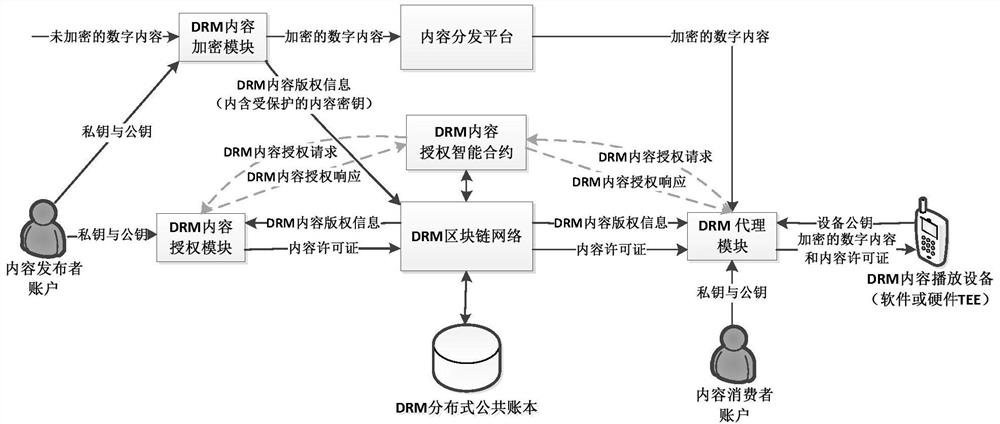
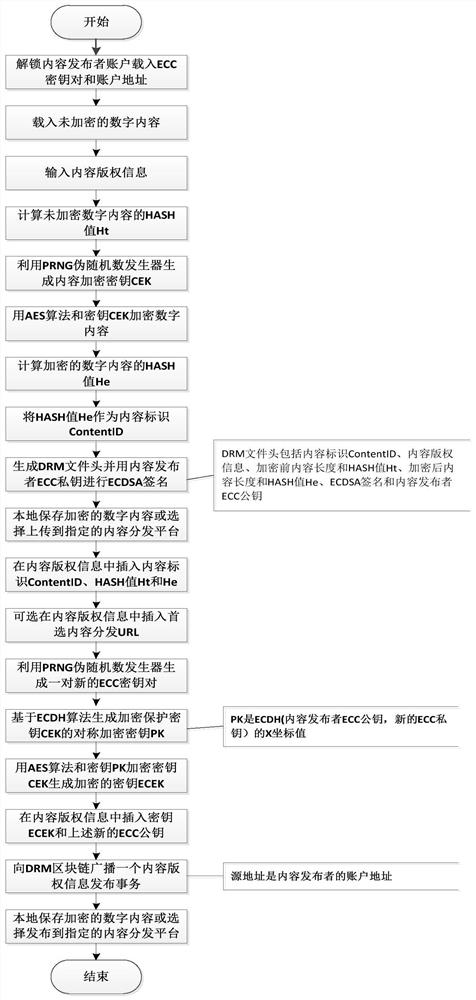
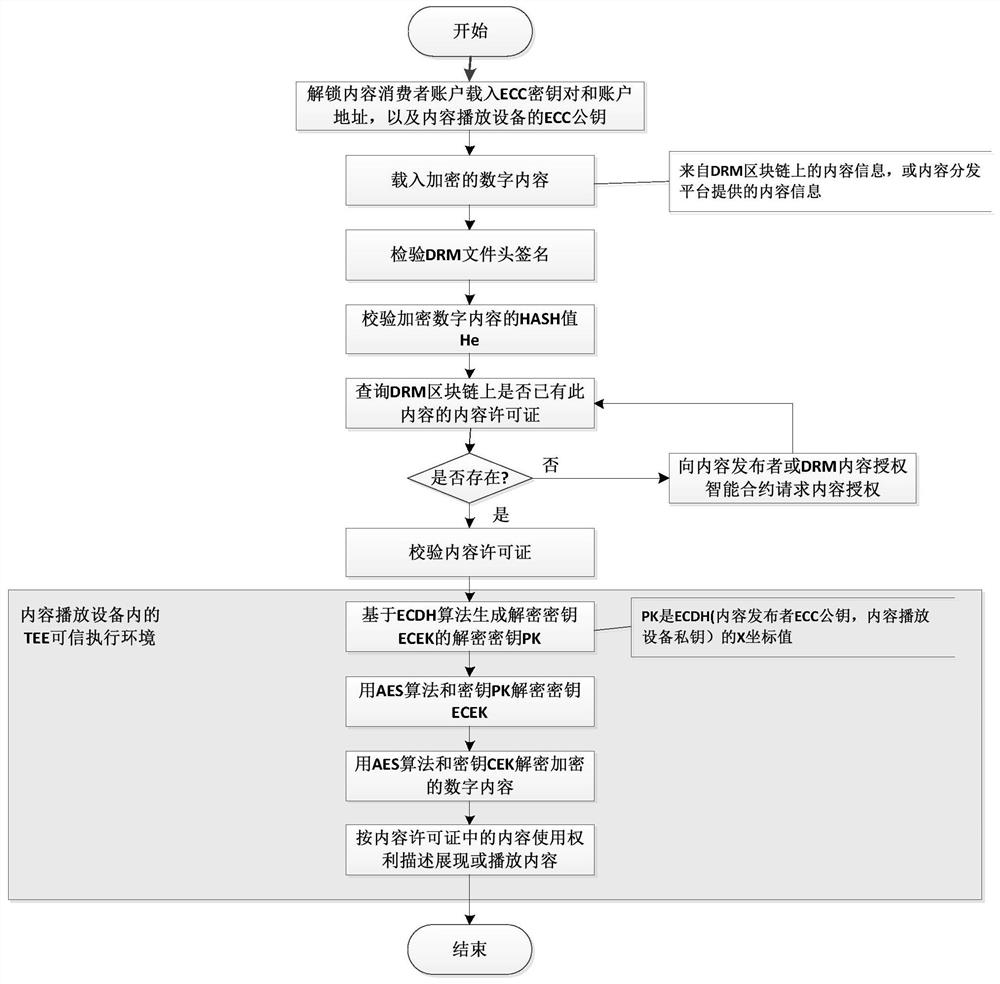
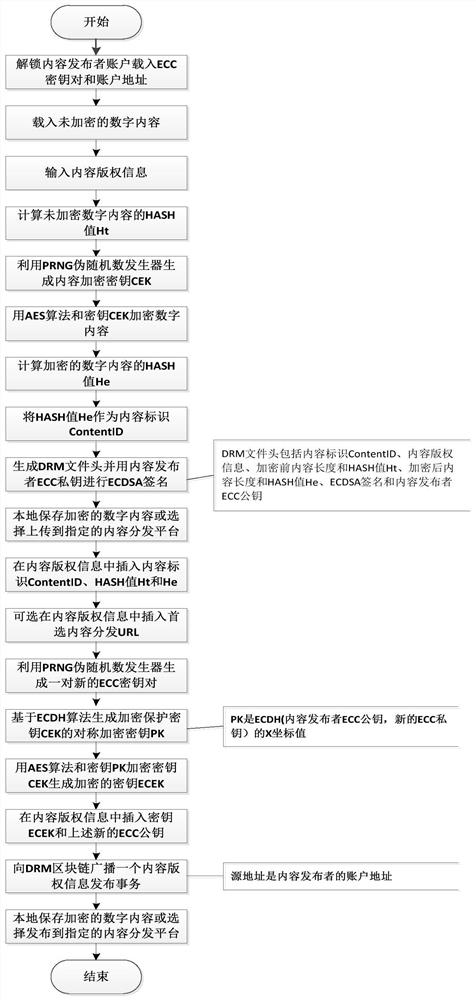
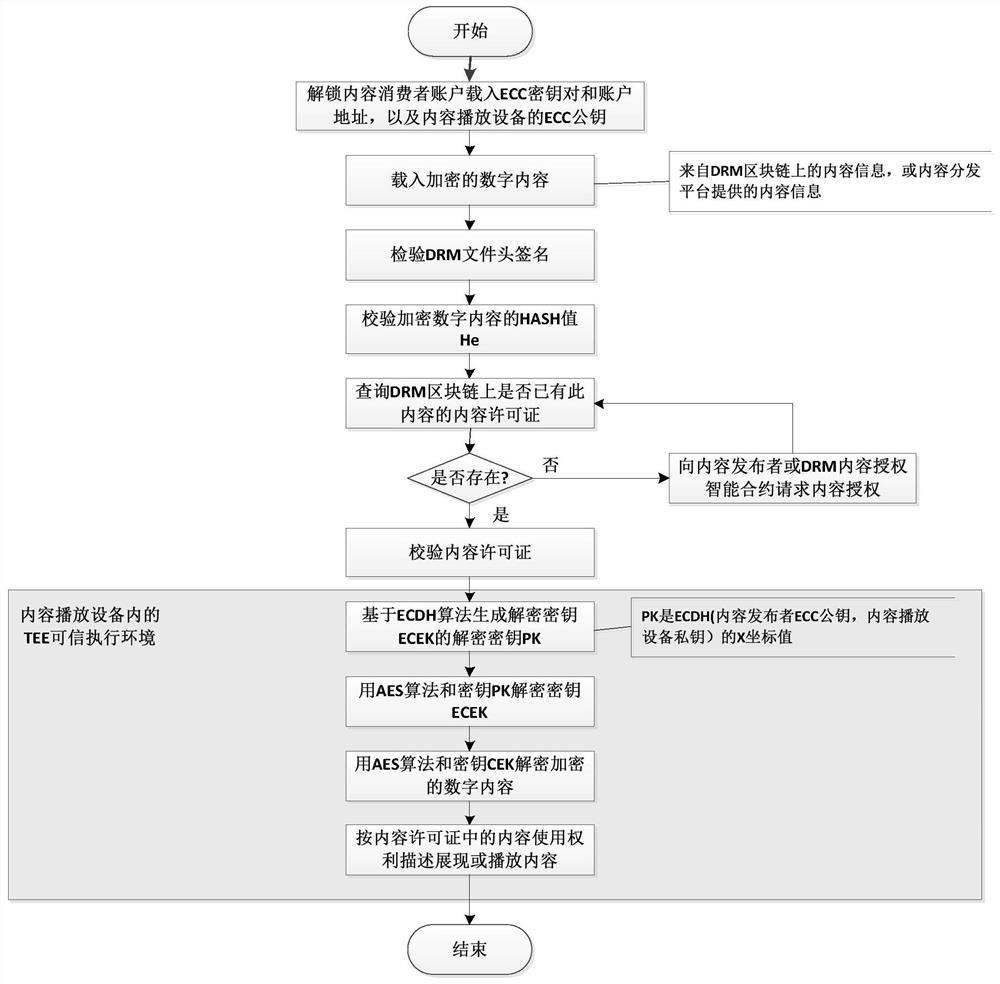
Distributed digital rights management (DRM) system based on blockchain
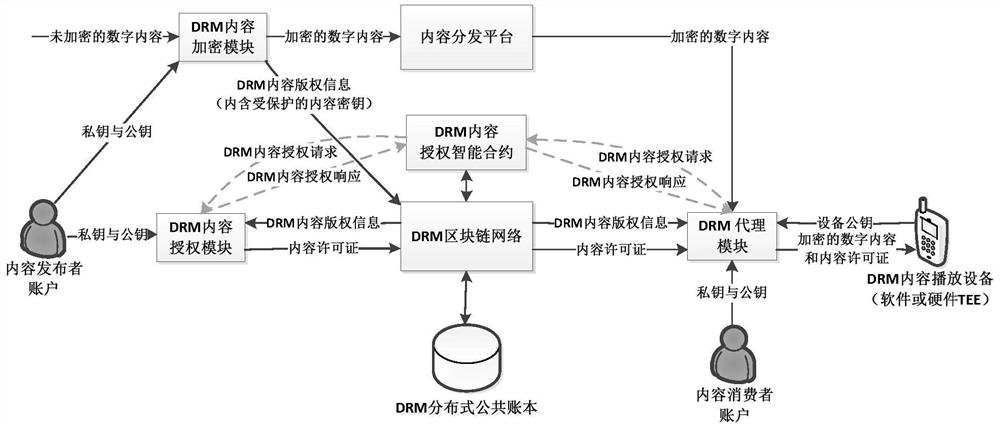
ActiveCN111818000AContent copyright management is open and transparentImplement authorizationKey distribution for secure communicationUser identity/authority verificationContent distributionInternet privacy
The invention relates to a distributed digital rights management (DRM) system based on a blockchain. The method belongs to the technical field of digital copyright protection and the technical field of blockchain. The system comprises a blockchain network supporting an intelligent contract, a distributed public account book, a content publisher, a content consumer account, a DRM content encryptionmodule, a DRM content authorization module, a DRM agent module, a DRM content authorization intelligent contract, a DRM content playing device, a content distribution platform and the like. The blockchain distributed public account book records the content copyright information and the content license of the encrypted digital content besides recording the account state, the transfer transaction,the smart contract code and the like, and the content copyright information and the content license both contain protected content encryption keys. Content encryption keys of digital content and content licenses authorized to consumers by content publishers are safely managed on blockchain, content copyright management is open and transparent, and DRM content authorization can be directly carriedout between any content publisher and the consumers in a point-to-point mode on the Internet through the system.
Owner:北京子辰飞马科技有限公司
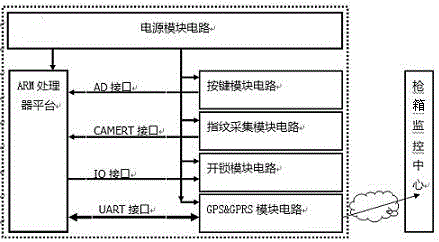
Portable intelligent gun box device
PendingCN106597926AAdd address IDAdd low power designProgramme controlComputer controlIdentity recognitionComputer science
The invention discloses a portable intelligent gun box device, which comprises a power module circuit, an ARM processor platform and a fingerprint acquisition module circuit, wherein the power module circuit is connected onto power ends of the ARM processor platform, the fingerprint acquisition module circuit, a GPS&GPRS module circuit and a peripheral module circuit for providing power; and the CAMER interface of the ARM processor platform is connected with the fingerprint acquisition module circuit for fingerprint extraction and comparison, and only an authorized legal user can open the gun box. The fact that the fingerprint for the identity of a gun-taking person is quickly compared and the gun box is legally opened can be realized, remote increased and decreased authorization on the identity of the gun-taking person can be realized, the fact that each gun box has a global unique ID series number can be realized, and the uniqueness of each gun box is ensured; the fact that the position unlocking information and the unlocking time of the gun-taking person are recorded to the gun box device for facilitating query is realized; the portable intelligent gun box device is applicable to military and public security exercises for realizing quick gun-taking person identity recognition, remote monitoring and real-time authorization; and due to records of the gun-taking person identity information, the time and the space, supervision by a relevant department is facilitated.
Owner:CHANGCHUN HONGDA OPTOELECTRONICS & BIOSTATISTICS IDENTIFICATION TECH
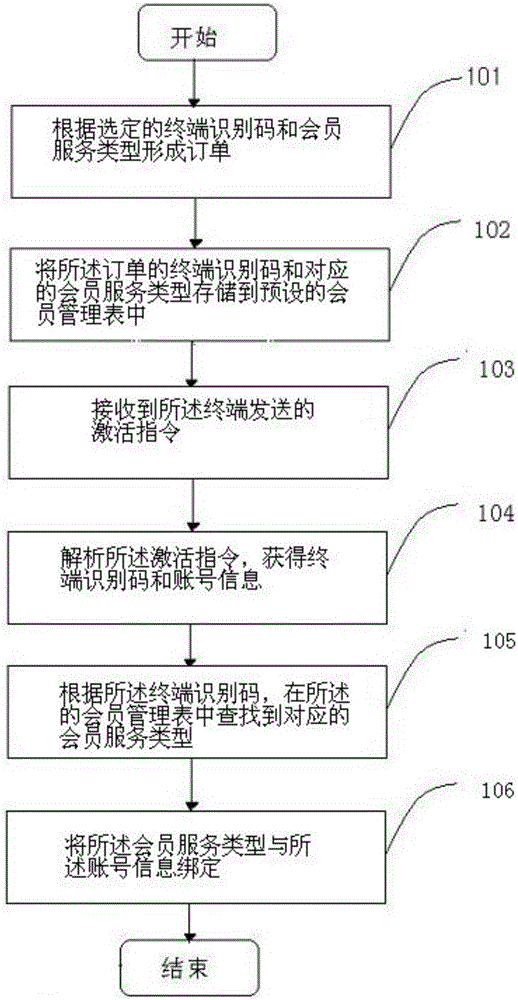
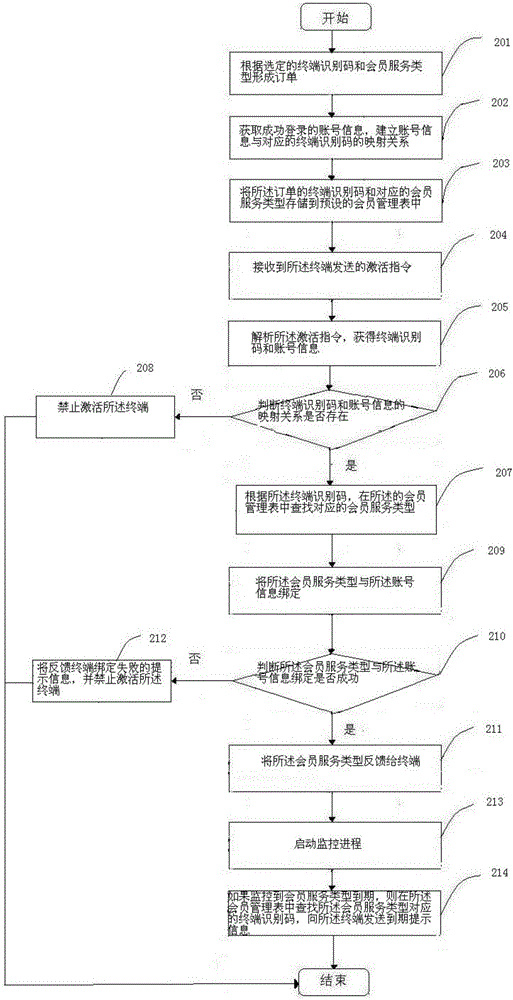
Method and device for selling terminals associated with member service
InactiveCN105894271AAchieve salesImplement authorizationMarketingProtocol authorisationSoftware engineeringComputer terminal
The invention discloses a method and device for selling terminals associated with member service. The method comprises steps of: forming an order according to a selected terminal identification code and a member service type and storing the terminal identification code of the order and the corresponding member service type in a preset member management list; analyzing, when an activation instruction sent from the terminal is received, the activation instruction to obtain the terminal identification code and account information; searching the corresponding member service type in the member management list according to the terminal identification code and binding the member service type to the account information. The method and device for selling terminals associated with member service may achieve card-free member service sale, authorization and activation, simpler operation, and better user experience.
Owner:LETV HLDG BEIJING CO LTD +1
System and method for telephone permit work ticket management and control
ActiveCN105243717BDoes not affect integrityImprove securityIndividual entry/exit registersTransformerControl system
A telephone license operation order management and control system is characterized by comprising an operation and maintenance center server, an intelligent lock control host, a computer key, and transformer station access control locksets. The operation and maintenance center server is in communication connection with intelligent lock control host via wireless network; the computer key matches with the intelligent lock control host; the computer key conducts wireless communication with the intelligent lock control host through the communication module; unlock permission of each access control and corresponding RFID coding of an RFID chip in the lock are stored in the intelligent lock control host; and the computer key reads the RFID coding in the transformer station access control mechanical lockset, and opens the lockset in each transformer station access. The system can effectively solve the problem of incapability of telephone license operation order management and control in the previous work; after using the system, the process of remote licensing and operation order termination by maintenance personnel is standardized, and the action area of maintenance personnel in the work process is strictly controlled, so as to lay a good foundation for safe power production.
Owner:STATE GRID CORP OF CHINA +1
Method for efficiently developing and deploying blockchain applications
PendingCN111736854AImplement authenticationImplement authorizationFinanceDigital data protectionSoftware engineeringAuthorization
The invention discloses a method for efficiently developing and deploying blockchain applications and specifically relates to the technical field of blockchains. The method comprises the steps of a block chain application efficient deployment method and a block chain application efficient development method. Through the steps, a developer only needs to simply apply for use; after authorization isobtained, a set of complete block chain cluster service which is already deployed and can meet requirements can be obtained within one minute, and operations, such as data chaining, inquiring and identity authentication, related to the block chain can be completed only by providing simple parameters for an http interface in interaction with the block chain.
Owner:贵阳信息技术研究院
Stamp protector and application method thereof
PendingCN108564701ATimely transmissionImplement authorizationSatellite radio beaconingIndividual entry/exit registersComputer moduleIdentification device
The invention discloses a stamp protector and an application method thereof. The stamp protector comprises an upper cover and a shell, wherein the surface of the upper cover is provided with a fingerprint identification device; a cavity is formed between the upper cover and the shell and is provided with a wireless communication module, a GPS positioning module and a locking unit; and the GPS positioning module, the fingerprint identification device and the locking unit all exchange information with a background server through the wireless communication module. The application method of the invention authorizes the use of stamps in virtue of the above stamp protector. The stamp protector of the invention can conveniently and effectively authorize the use of stamps, can realize the accuratetracking of stamp positions and supervision, authorized use and safe storage of stamps, reduces the risks of stealing and abusing of stamps, and improves stamping efficiency.
Owner:珠海实跃科技有限公司
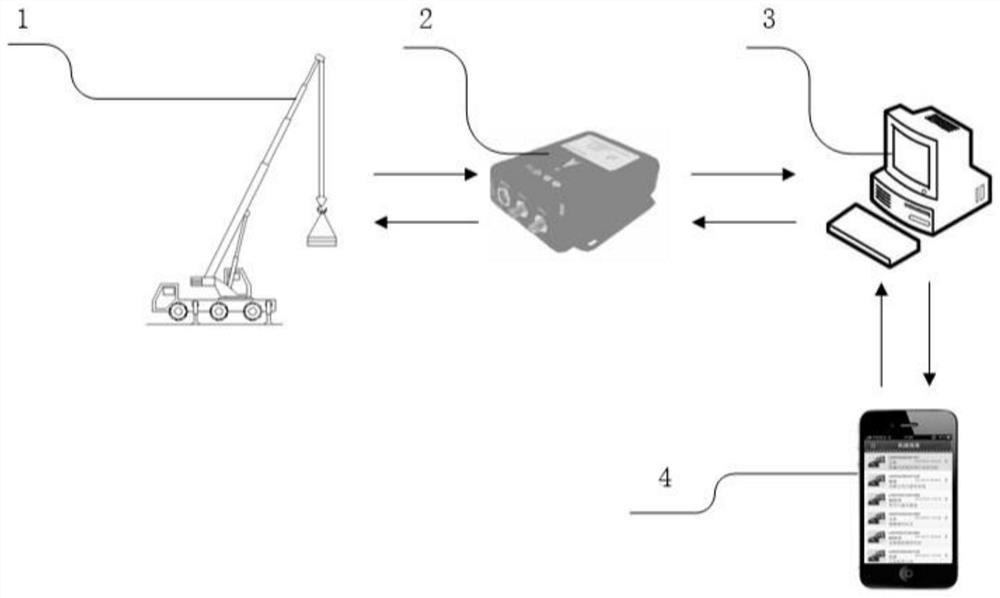
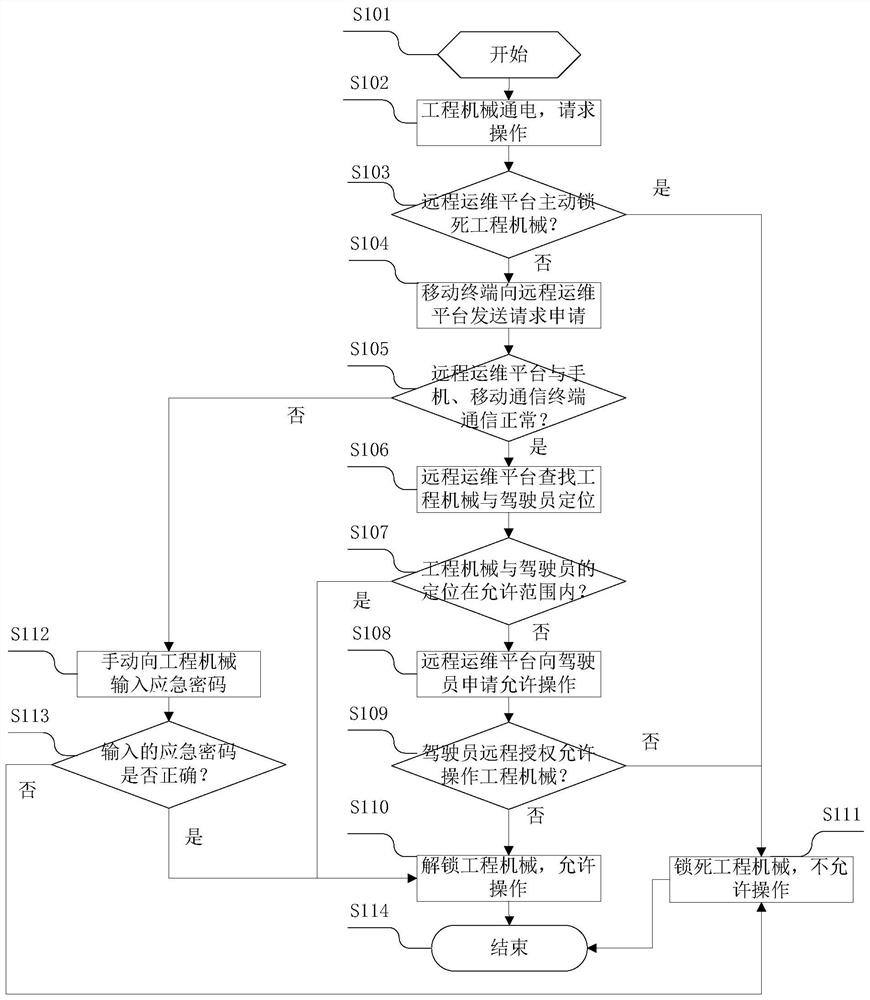
Engineering machinery driver identity recognition system and method
ActiveCN111915776AGuaranteed traceabilityGuaranteed reasonablenessIndividual entry/exit registersDriver/operatorIdentity recognition
The invention discloses an engineering machinery driver identity recognition system and method. The system comprises: a remote operation and maintenance platform; a first mobile communication terminaland a second mobile communication terminal which establish communication with the remote operation and maintenance platform and are used for respectively positioning engineering machinery and a driver. The remote operation and maintenance platform is used for authorizing the first mobile communication terminal according to the distance between the engineering machine and the second mobile communication terminal or permission or permission rejection information sent by the second mobile communication terminal after the engineering machine is powered on and an application for allowing operationof the engineering machine is obtained from a request sent by the first mobile communication terminal. The first mobile communication terminal is used for controlling the engineering machinery to beunlocked or locked. The identity recognition system and method provided by the invention are accurate in recognition, and can guarantee the use safety of the engineering machinery.
Owner:JIANGSU INTERNET OF THINGS TECH DEVCO
An Intranet Access System Based on ipsec VPN Proxy
ActiveCN106685785BSimplify configuration managementEasy background maintenanceNetworks interconnectionInternet privacyIPsec
The invention discloses an IPsec VPN agent-based intranet access system, which includes a mobile VPN agent device, a configuration server, a VPN gateway, an authentication server and an authentication client. The mobile VPN proxy device communicates with the configuration server and the VPN gateway through the Internet; the user request is forwarded through the mobile VPN proxy device and the VPN gateway, so that the user request reaches the authentication client; then the authentication client and the authentication server are realized through the enterprise intranet The authorization requested by the user. The access system of the present invention implements the user's access to the Intranet through the mobile VPN proxy device, and then implements the authorization of the user's access request through the authentication server and the authentication client. IPsec tunnels are established by VPN gateways and mobile VPN proxy devices without user participation, which lowers the threshold for using IPsec VPNs and overcomes the shortcomings of difficult use and maintenance of IPsec VPNs.
Owner:BEIHANG UNIV
A WeChat-based community access control system and door opening method
ActiveCN107507305BWide range of servicesLow costIndividual entry/exit registersData switching networksAccess timeComputer terminal
Owner:XIAMEN DNAKE INTELLIGENT TECH CO LTD
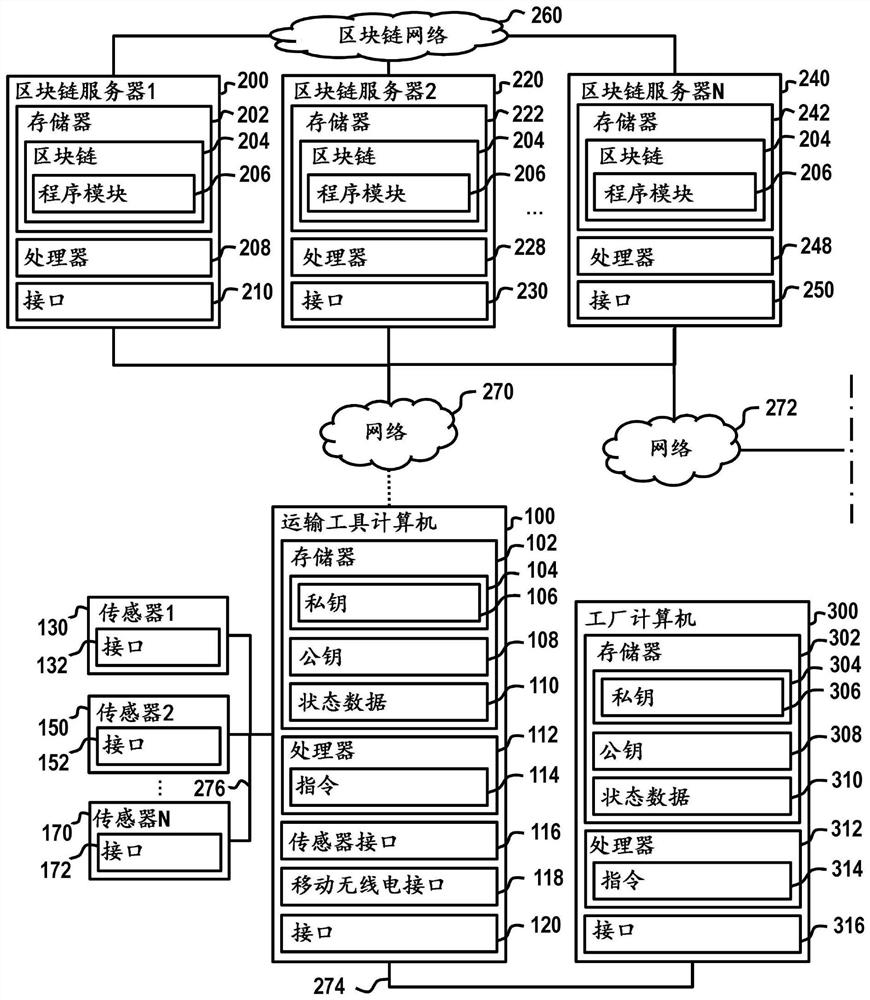
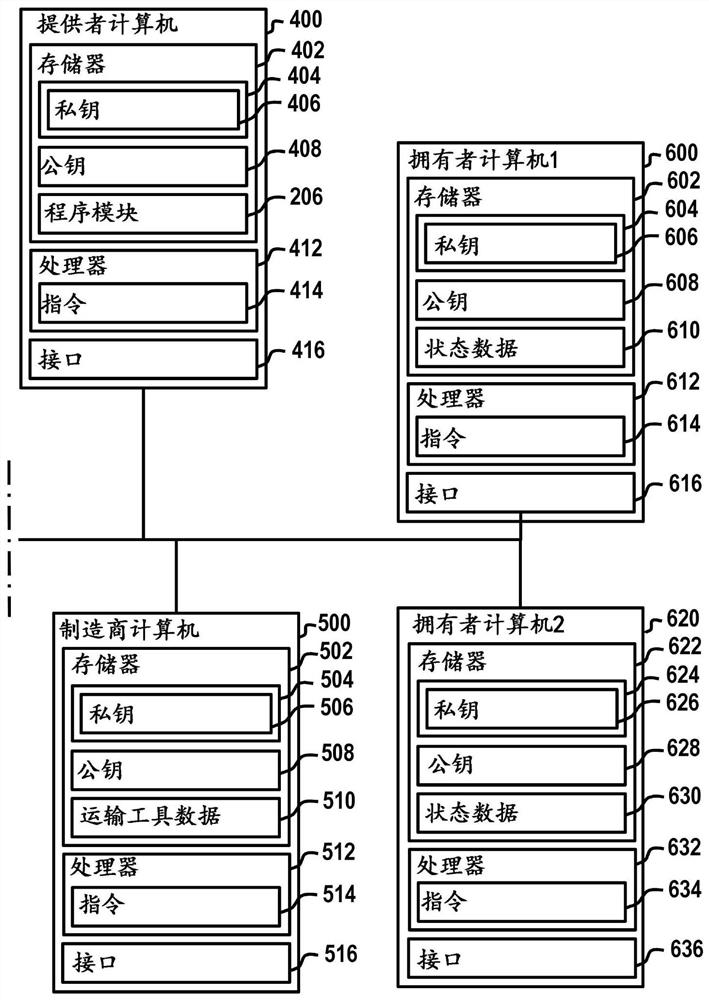
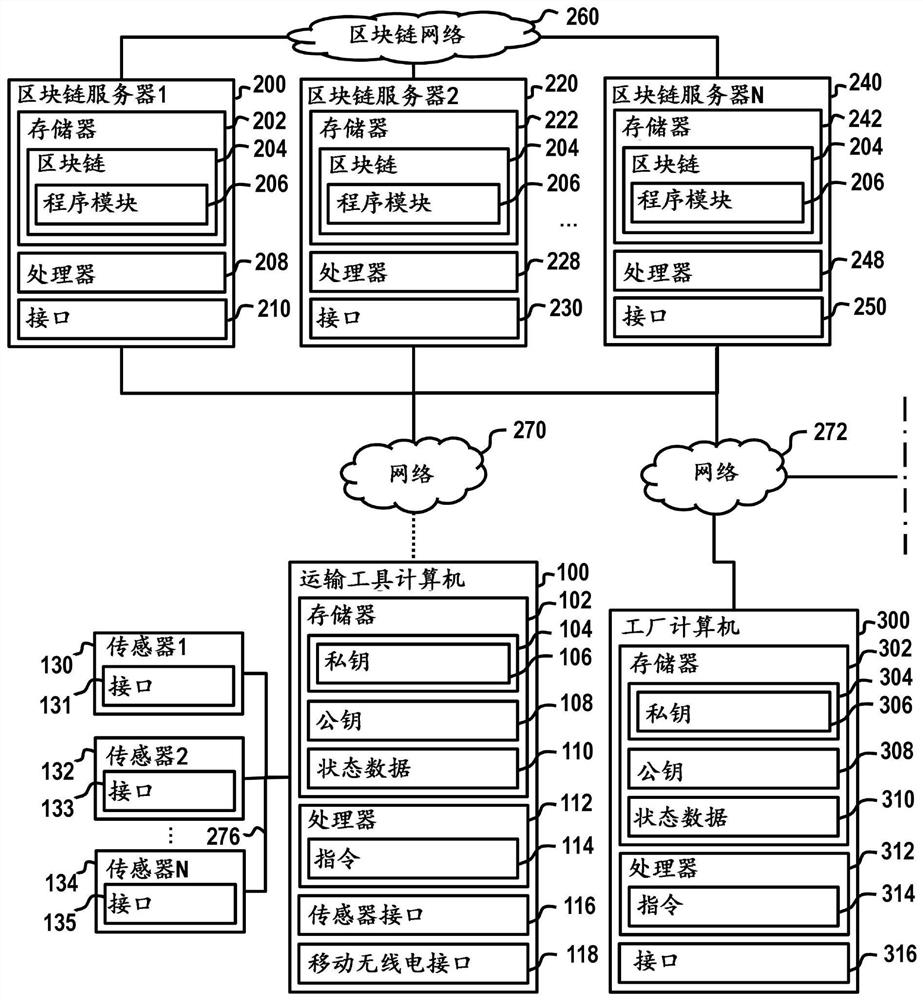
Creating a vehicle certificate using a blockchain
ActiveCN112292841AImplement authorizationCommerceSpecial data processing applicationsTamper resistanceOperating system
The invention relates to a method for tamper-proof saving of vehicle data (110, 310, 510, 610) of a vehicle in a blockchain (204). The method comprises: creating a signed output instruction for outputting a vehicle certificate (282), having a data record characterizing the vehicle, using the blockchain (204), in the case of a valid signature, receiving the vehicle certificate (282), outputting thevehicle certificate (282), wherein the output vehicle certificate comprises a machine-readable code (284), wherein the machine-readable code (284) comprises a private cryptographic key of an asymmetric key pair, wherein a public cryptographic key of the asymmetric key pair is identified in the blockchain (204) as a test value for testing a signature of a read request for reading vehicle data of the vehicle certificate (282) from the blockchain (204).
Owner:BUNDESDRUCKEREI GMBH
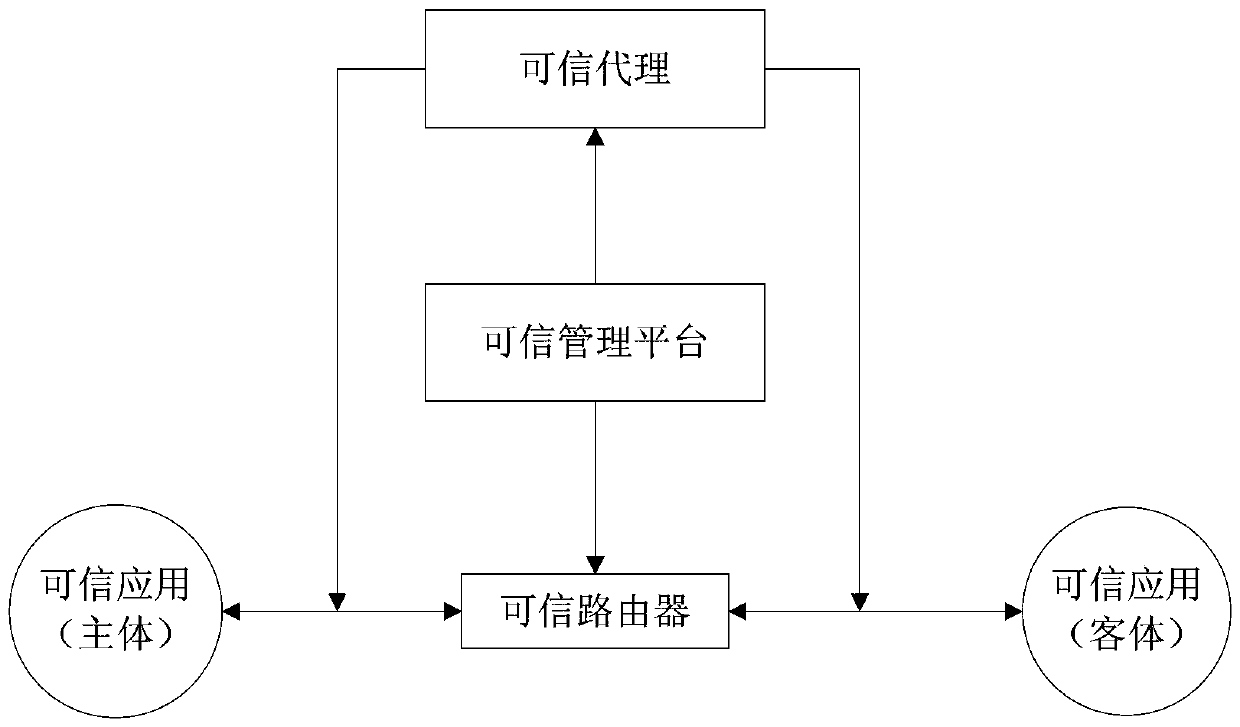
A working method of trusted network and trusted network
InactiveCN103581156BMeet the requirements of grade protectionEnable secure accessTransmissionAccess routeClass of service
The invention discloses a trusted network which comprises a trusted application, a trusted tag, a trusted agent, a trusted management platform and a trusted router. An active offensive method is adopted by the trusted network so that safety certification can be conducted on source terminals (such as identity, application programs and procedures) of the network and safe tagging can be conducted according to a set rule. A trusted network device and a tagging management platform are combined so that safety admittance of a user terminal according to role authority can be achieved, and therefore network layer authority is achieved; according to the class of services and the service authority, a safety access route is proposed, so that an object and a subject only and logically exist in the network, and therefore data are prevented from being stolen and tampered. Through management platform tagging and CIPSO message control, the shortage of a traditional safety protection means is offset, integrated linkage safety protection is conducted on the network according to the aspects of data transmission, a network perimeter and a master terminal, and the requirement for network grade protection is satisfied in the true sense.
Owner:中铁信(北京)网络技术研究院有限公司
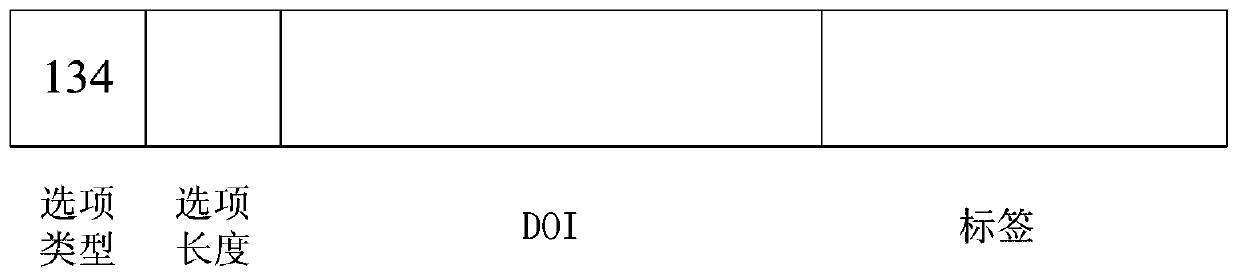
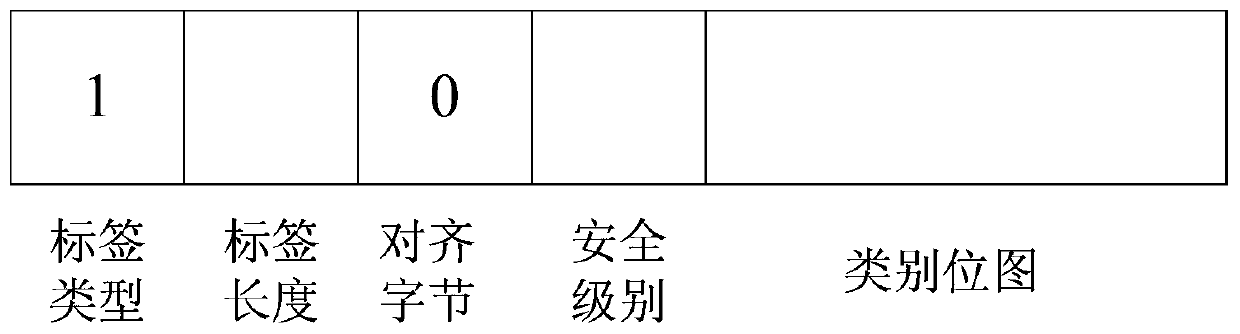
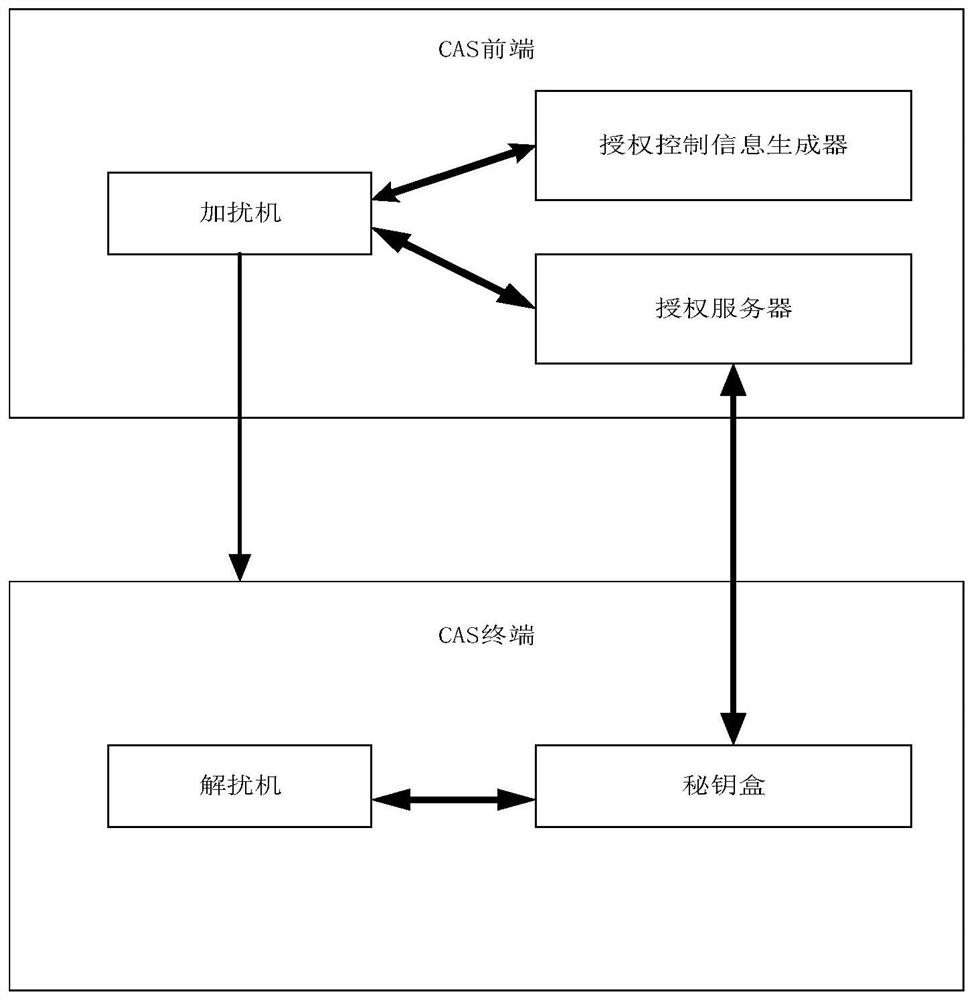
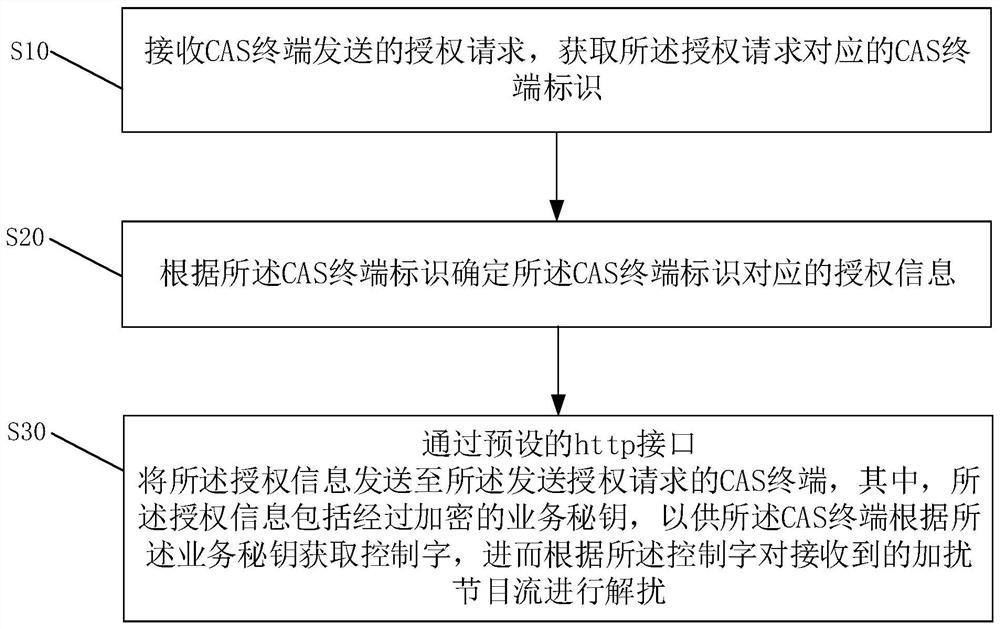
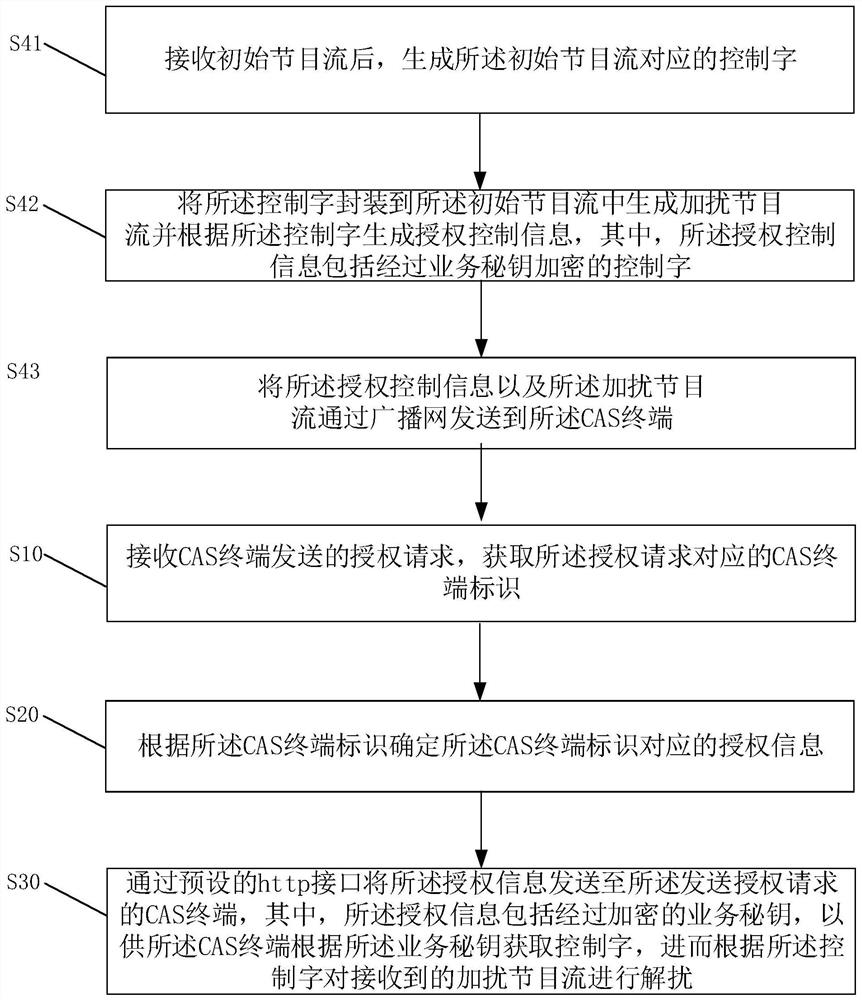
Method and device for realizing on-demand authorization of CAS terminal
The invention discloses a method for realizing on-demand authorization of a CAS terminal, and the method comprises the steps: receiving an authorization request sent by the CAS terminal, and obtaining a CAS terminal identifier corresponding to the authorization request; determining authorization information corresponding to the CAS terminal identifier according to the CAS terminal identifier; sending the authorization information to the CAS terminal sending the authorization request through a preset hypertext transfer protocol (http) interface, wherein the authorization information comprises an encrypted service secret key, so that the CAS terminal obtains a control word according to the service secret key, and the received scrambled program stream is descrambled according to the control word. The invention also discloses a device for realizing on-demand authorization of the CAS terminal and a computer readable storage medium. According to the invention, the authorization request sent by the CAS terminal is received, and then the authorization information is sent to the CAS terminal in a unicast manner, so that the problem that the authorization information occupies a large amount of bandwidth when the authorization information is broadcasted to all the CAS terminals in a one-way manner is solved.
Owner:SHENZHEN SDMC TECH CO LTD
A method and device for accessing a network instance
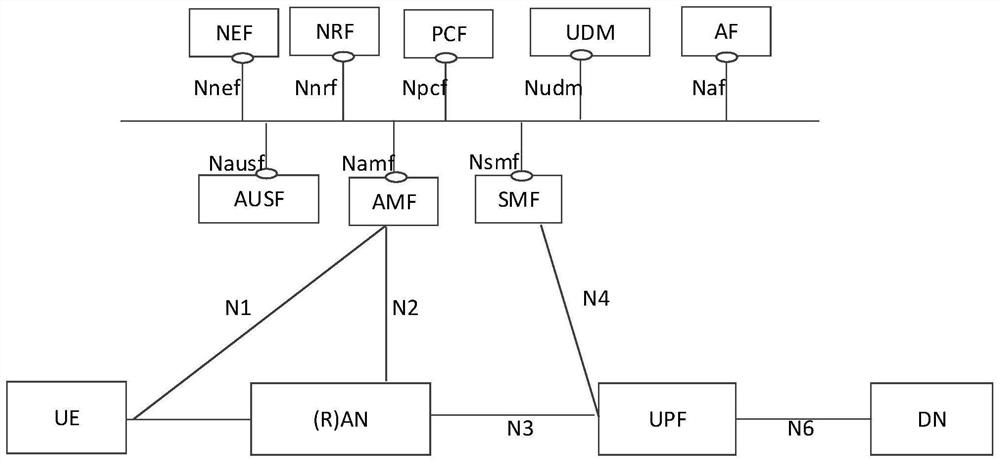
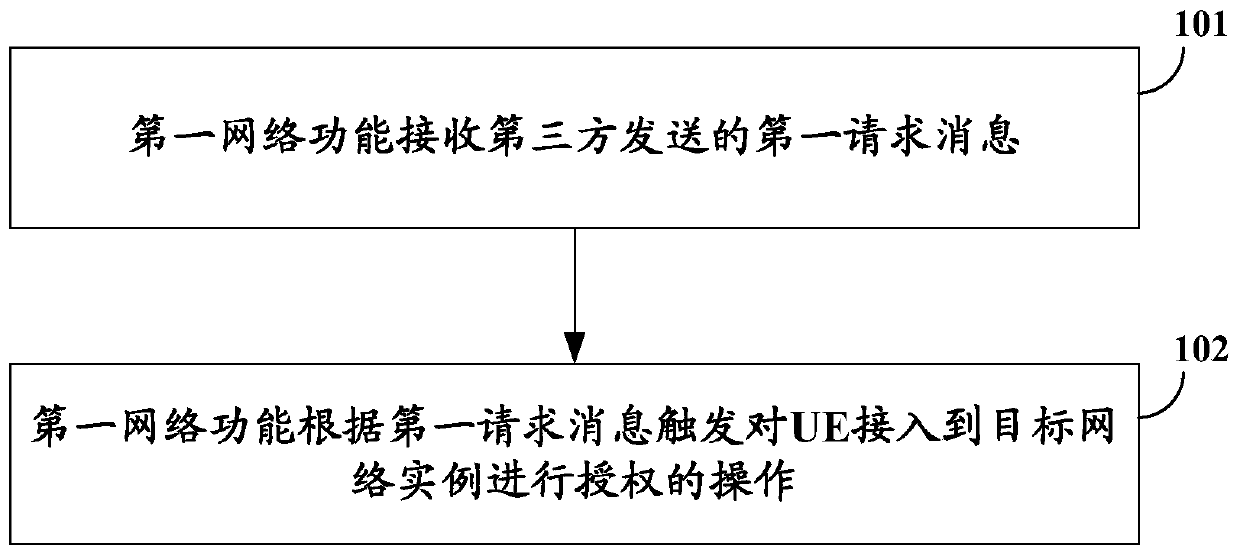
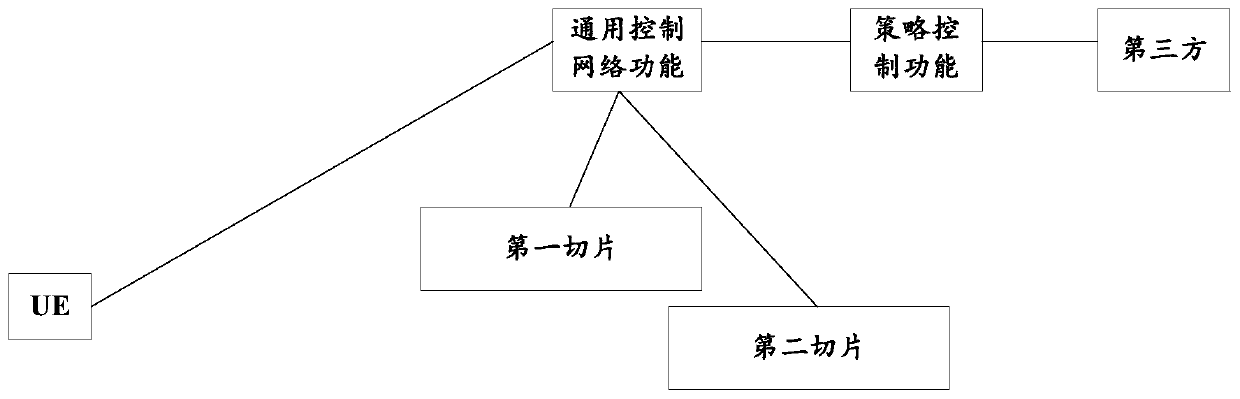
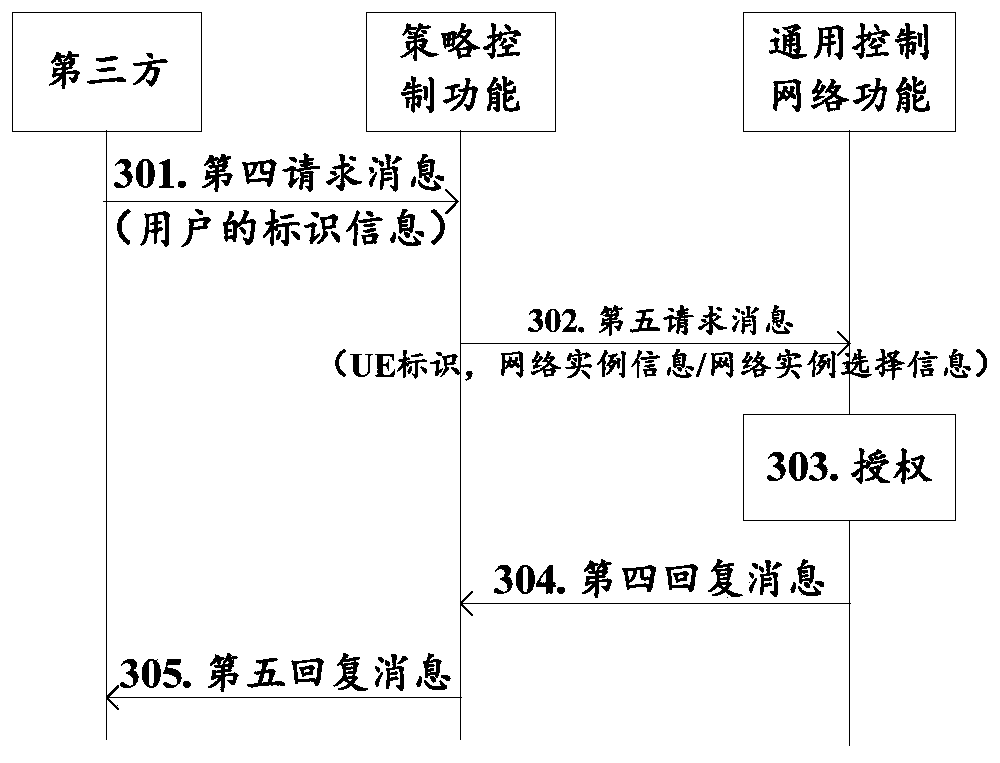
ActiveCN108307350BImplement authorizationService provisioningConnection managementThird partyComputer network
Embodiments of the present invention provide a method and device for accessing a network instance. The method includes: the first network function receives a first request message sent by a third party; the first network function triggers a request according to the first request message The operation of authorizing the UE to access the target network instance enables the third party to trigger the network to authorize the UE to access a specific network instance and establish a connection for the UE in the target network instance.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Authorization method and device, authorization platform and storage medium
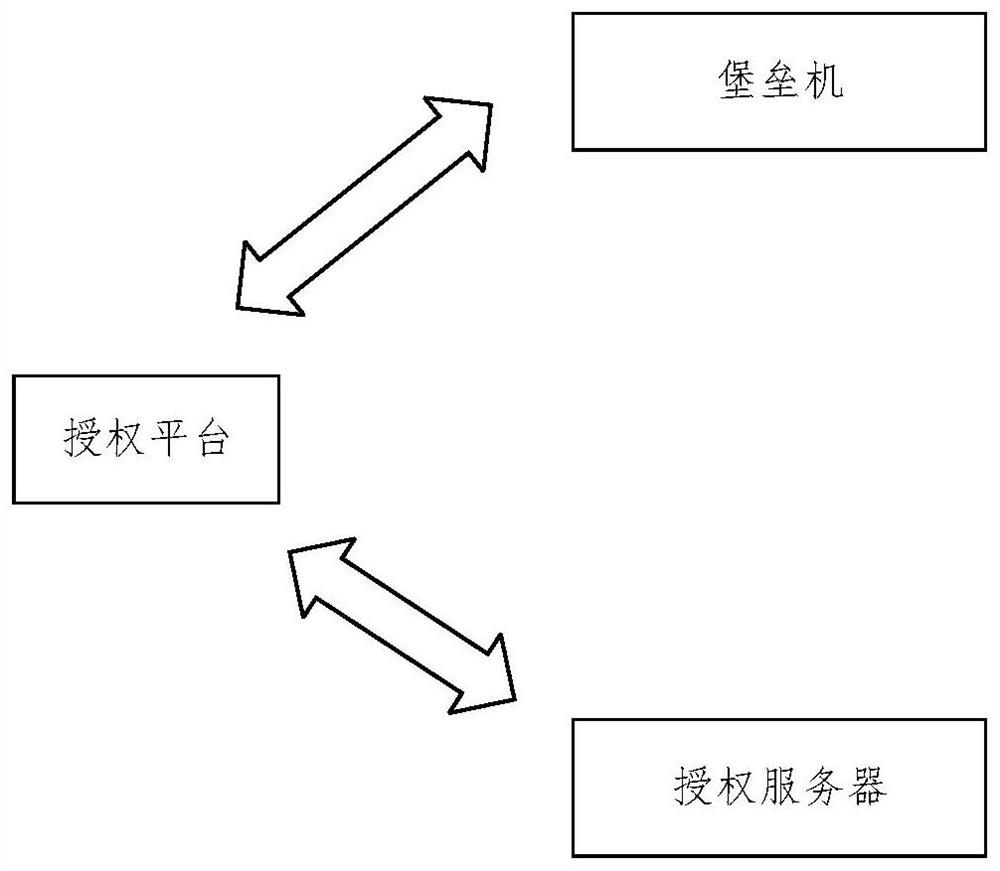
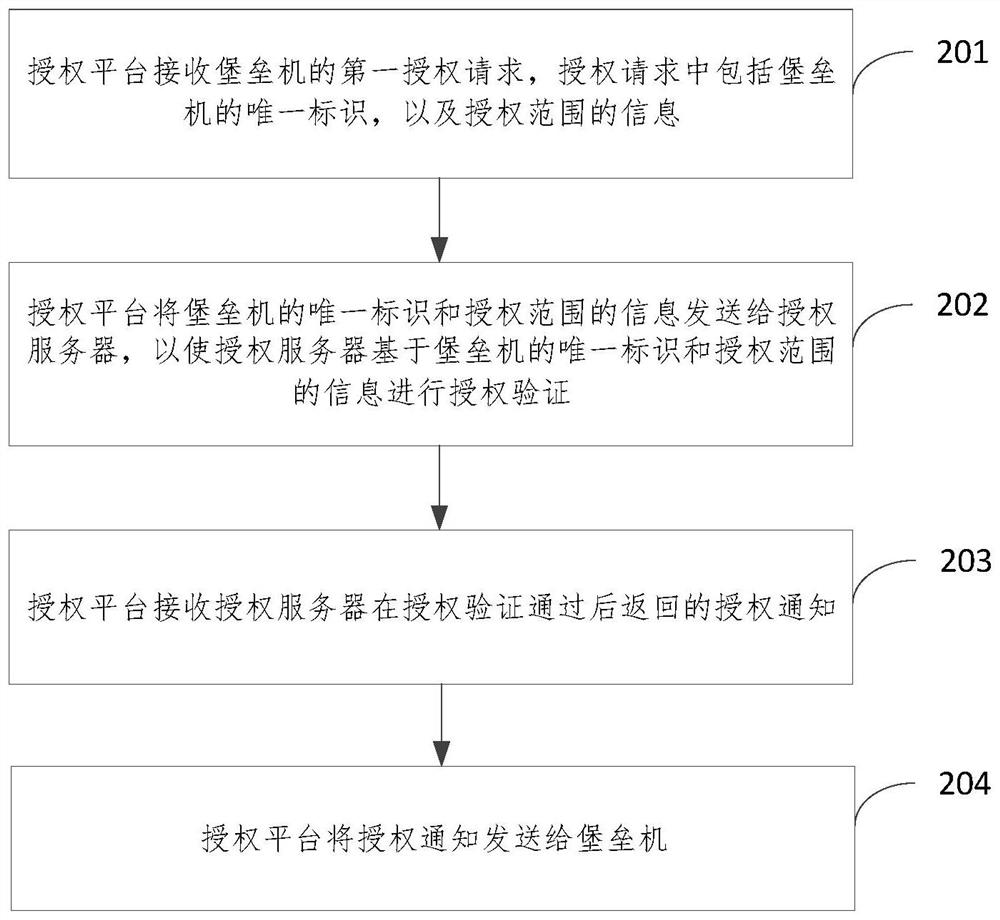
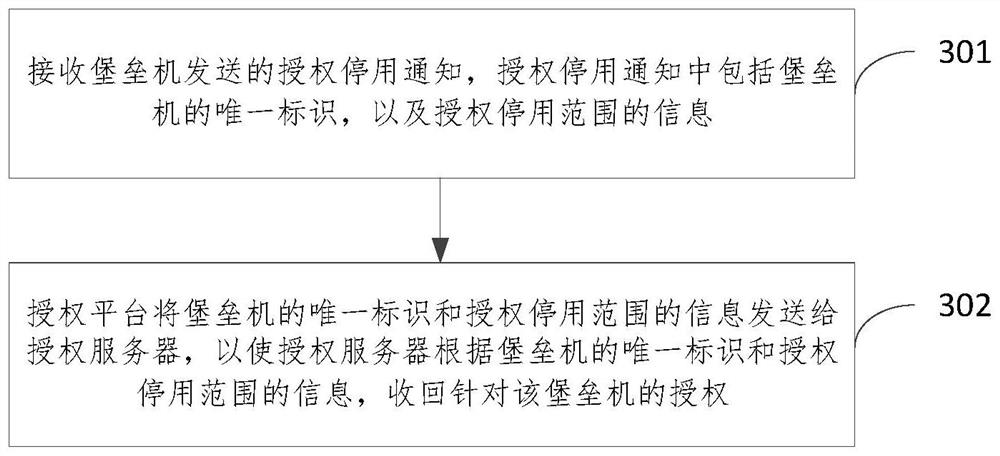
PendingCN113992381AImplement authorizationRealize unified managementSecuring communicationUnique identifierEngineering
The embodiment of the invention relates to an authorization method and device, an authorization platform and a storage medium. The method comprises the steps that a first authorization request of a bastion host is received through an authorization platform, wherein the authorization request comprises a unique identifier of the bastion host and information of an authorization range; the authorization platform sends the first authorization request of the bastion host to an authorization server, so that the authorization server performs authorization verification based on the unique identifier of the bastion host and the information of the authorization range; and then the authorization platform receives an authorization notification returned by the authorization server after the authorization verification is passed and sends the authorization notification to the bastion host. According to the scheme provided by the invention, the bastion host and the authorization server under different networks are linked by setting the authorization platform capable of communicating with the bastion host and the authorization server under different networks, so that authorization and unified management of the bastion host under different network environments are realized, and the flexibility and security of authorization management are improved.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
A blockchain-based distributed digital rights management (drm) system
ActiveCN111818000BContent copyright management is open and transparentImplement authorizationKey distribution for secure communicationUser identity/authority verificationContent distributionInternet privacy
The present invention relates to a blockchain-based distributed digital rights management (DRM) system. It belongs to the field of digital copyright protection technology and the field of block chain technology. The system of the present invention includes a blockchain network supporting smart contracts, a distributed public ledger, content publishers and content consumer accounts, a DRM content encryption module, a DRM content authorization module, a DRM agent module, a DRM content authorization smart contract, and a DRM content playback equipment, and content distribution platforms, etc. In addition to recording account status, transfer transactions and smart contract codes, the blockchain distributed public ledger also records content copyright information and content licenses of encrypted digital content. Both content copyright information and content licenses contain protected Content encryption key. The secure management of the content encryption key of the digital content and the content license authorized by the content publisher to the consumer on the block chain is realized, and the content copyright management is open and transparent. DRM content authorization can be carried out point-to-point directly.
Owner:北京子辰飞马科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com