Patents
Literature
32results about How to "Realize real-name authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
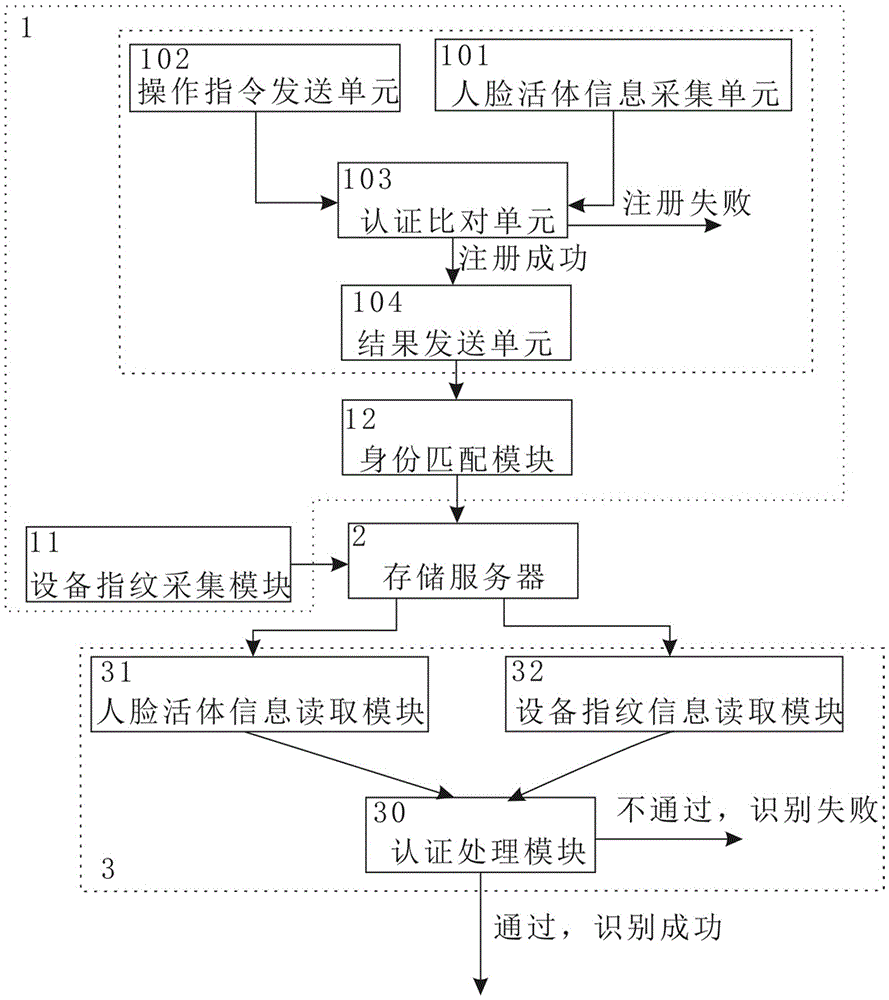
Identity recognition method and system based on multi-biometric feature in combination with device fingerprint
ActiveCN105279416AGuaranteed accuracyRealize real-name authenticationDigital data authenticationIdentity recognitionAuthentication server
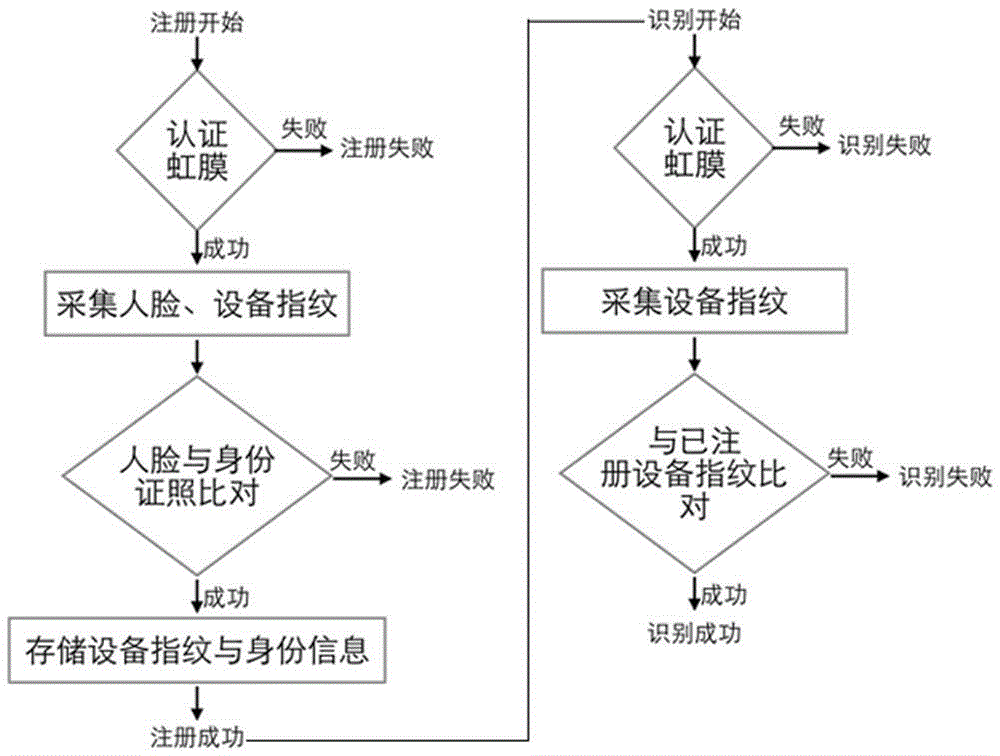
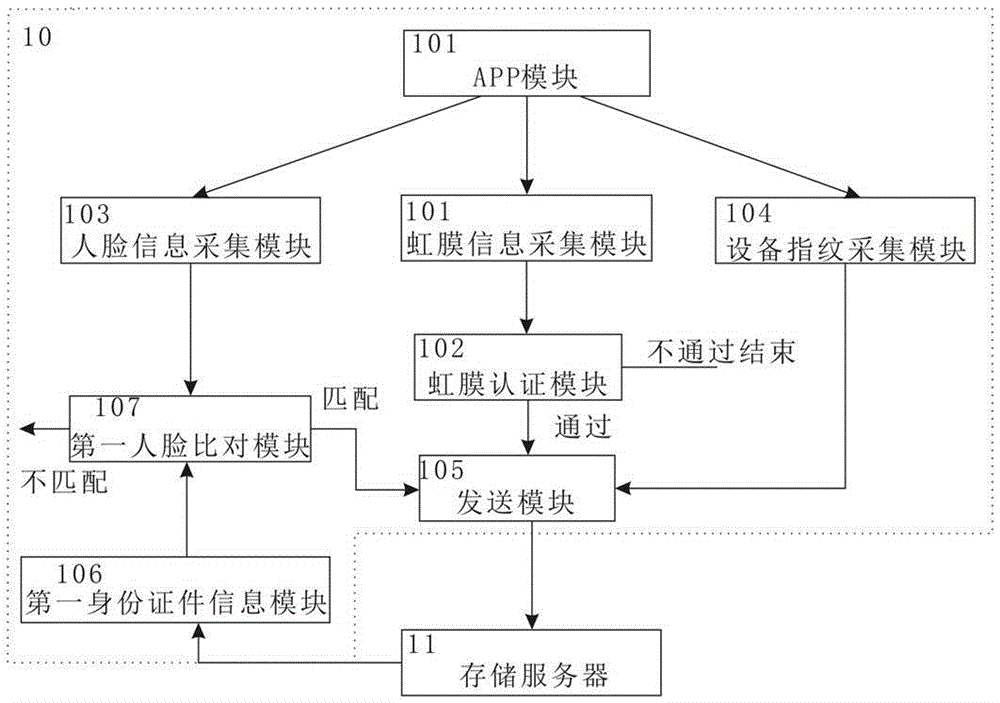
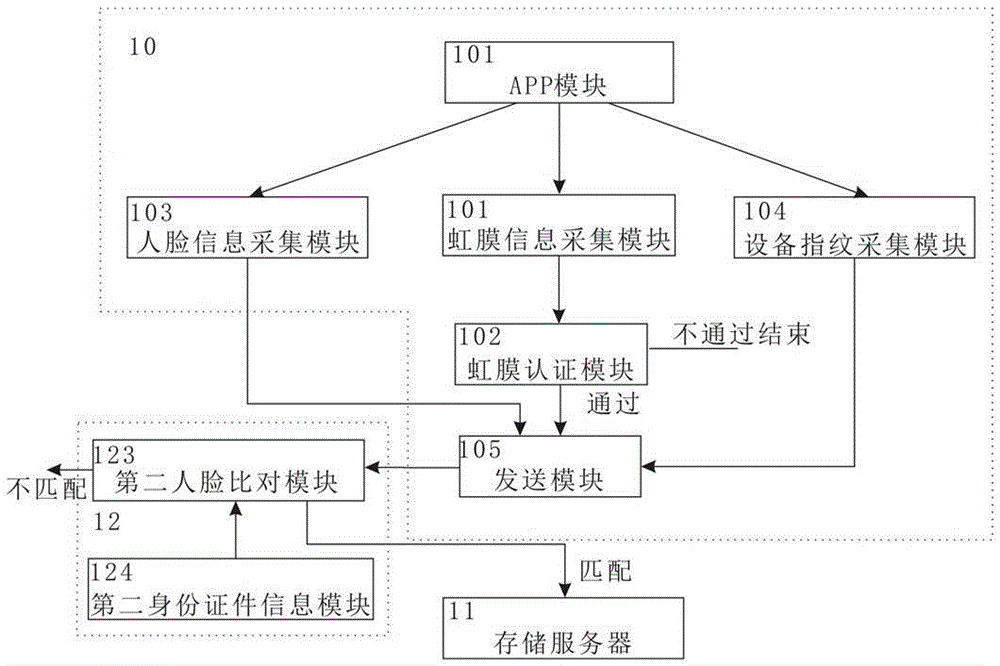
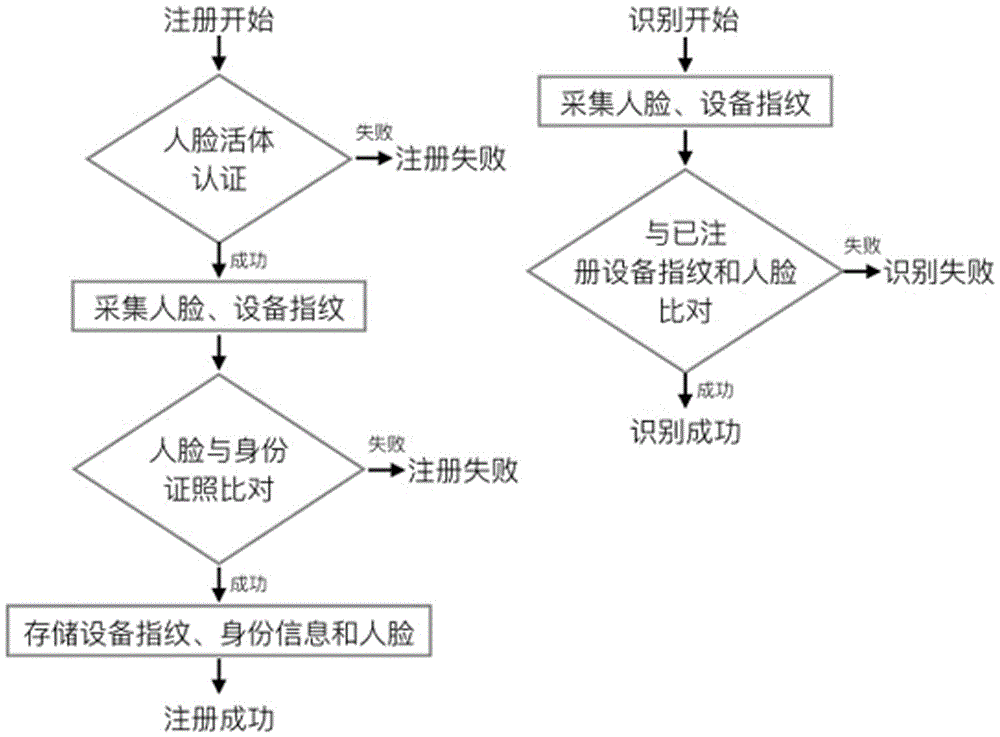
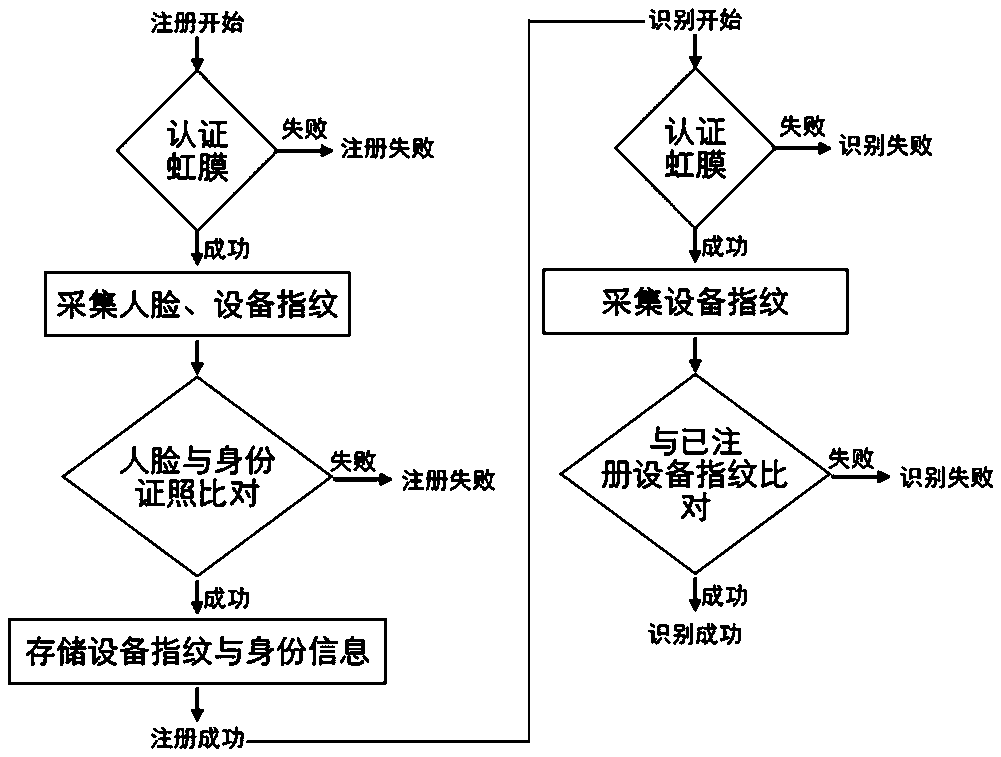
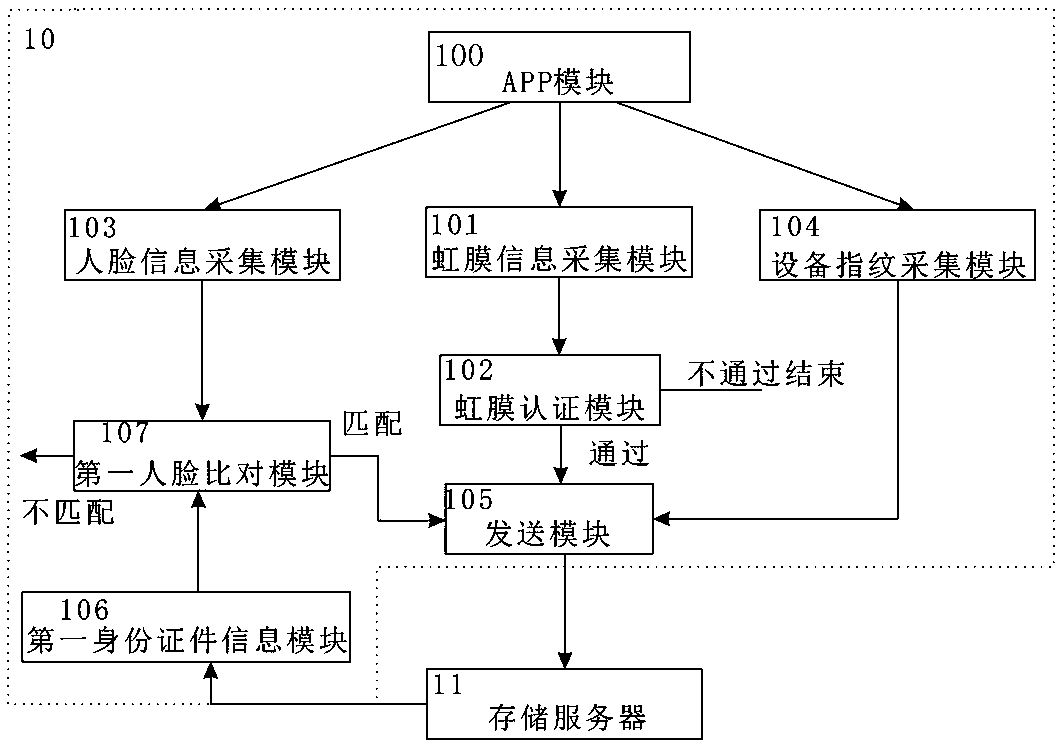
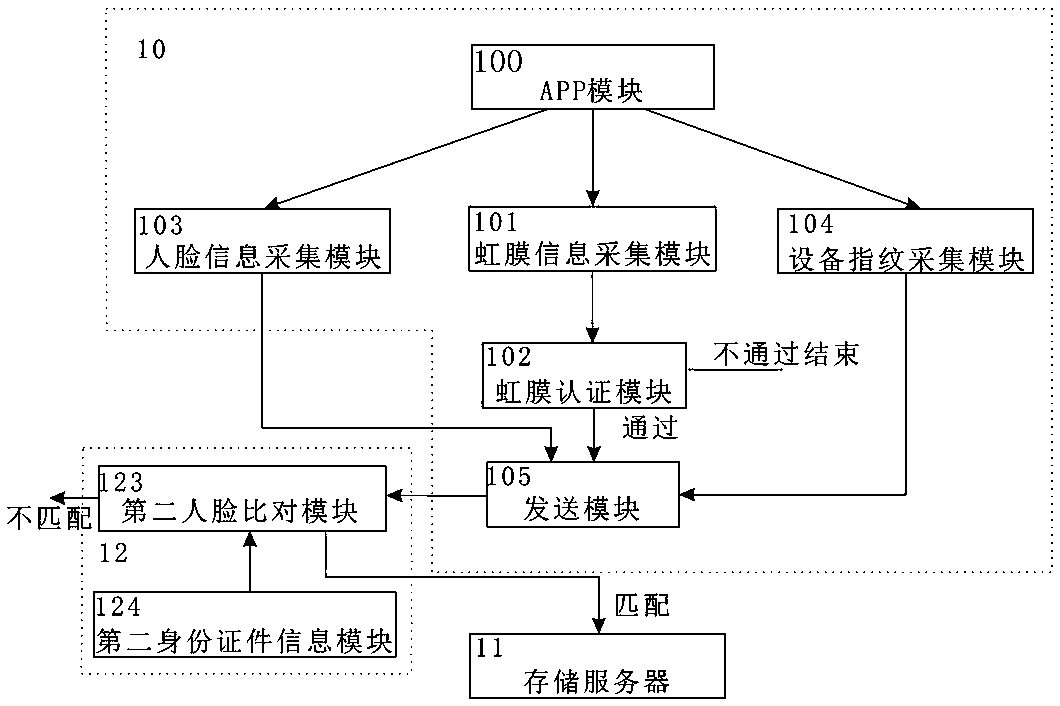
The present invention discloses an identity recognition method and system based on a multi-biometric feature in combination with a device fingerprint. The method comprises two main steps of registration authentication and user identification, and the system comprises a smart phone, a storage server and an authentication server; the smart phone is connected with an input end of the storage server, and an output end of the storage server is connected with the authentication server; and the smart phone is interconnected with the authentication server. The method disclosed by the present invention comprises two main sections of the registration authentication and the user identification, and by means of iris local authentication, the two main sections can confirm that an operator of a phone is an owner of the phone; human face information acquired at the same time as the iris local authentication can be confirmed as human face information of the owner of the phone, thereby ensuring accuracy of registered user information. According to the method and the system disclosed by the present invention, a smart phone iris recognition technology and a smart phone device fingerprint technology are combined, so that effects of network real person and real name authentication as well as high network account security and login convenience and the like are achieved.
Owner:SHANGHAI CHUANZHI FINANCE INFORMATION SERVICE CO LTD
Network identity document authentication method and system of block chain
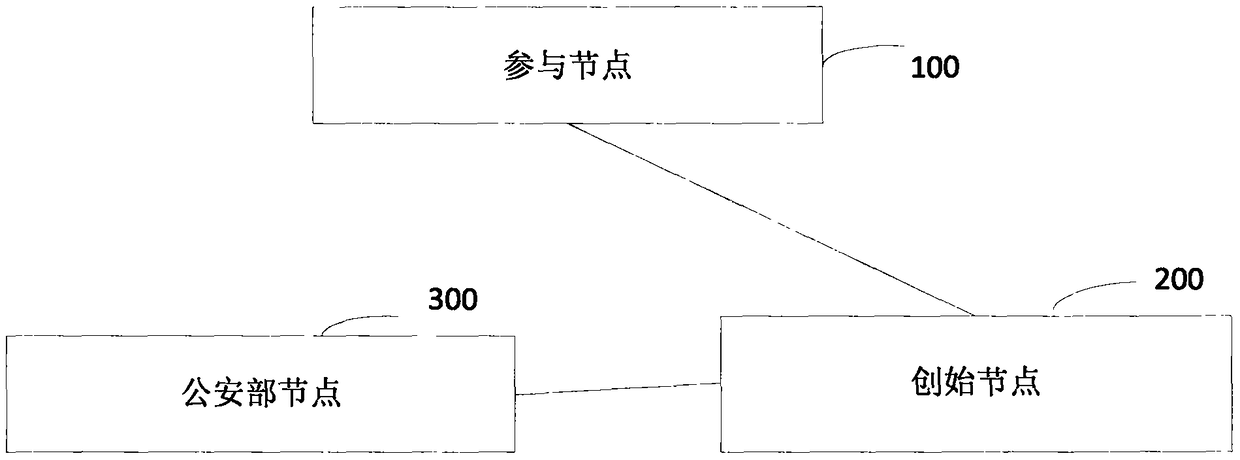
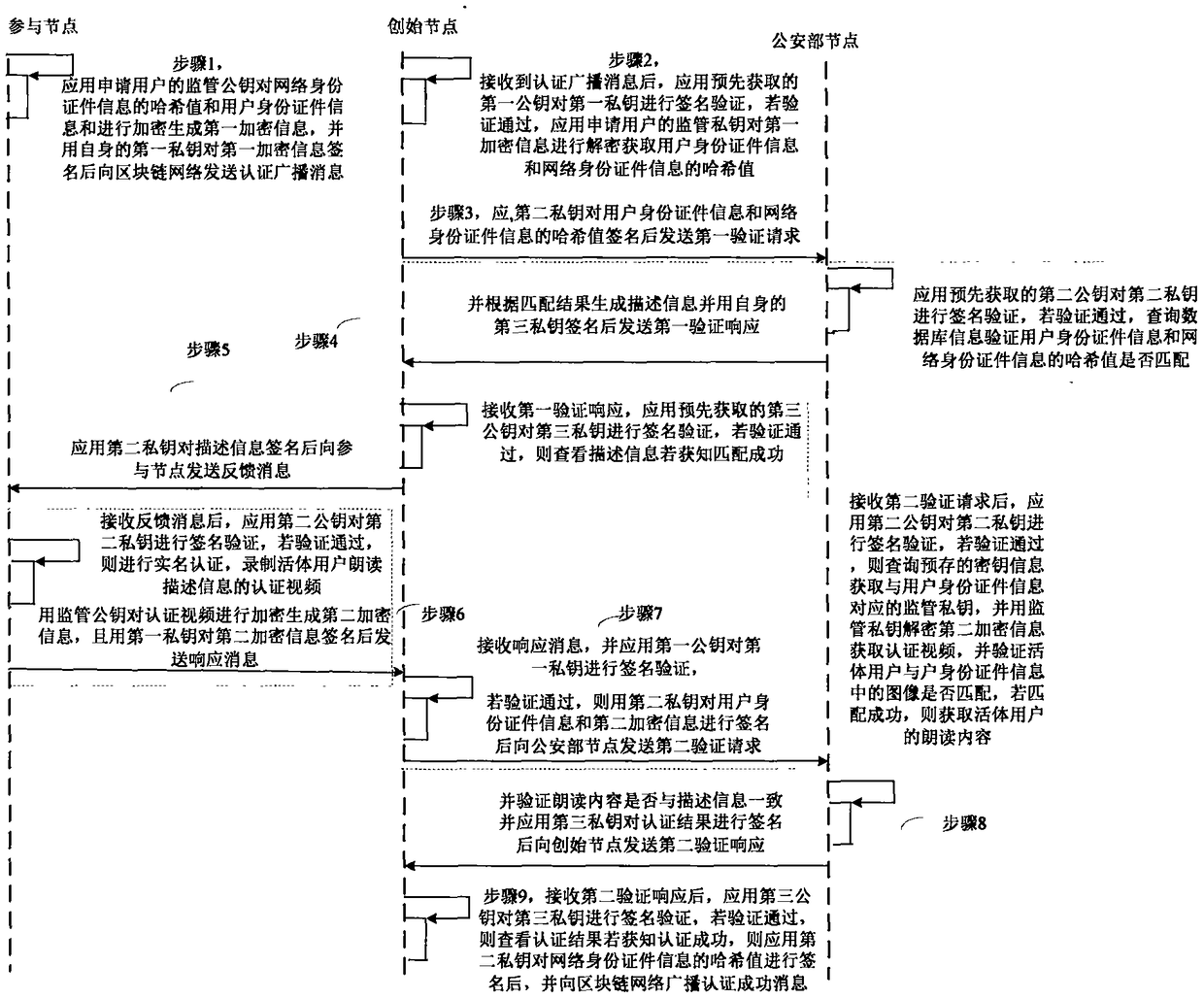
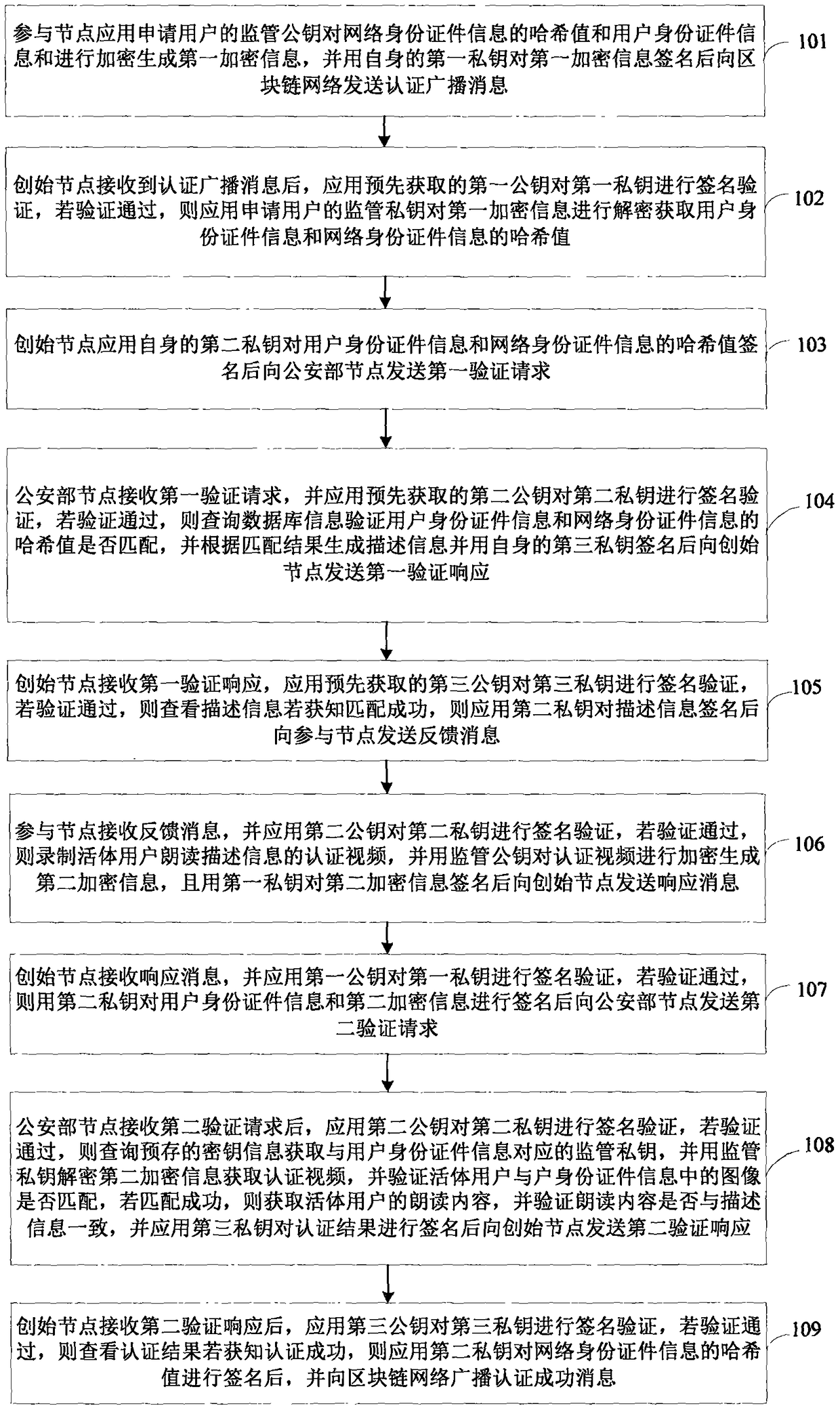
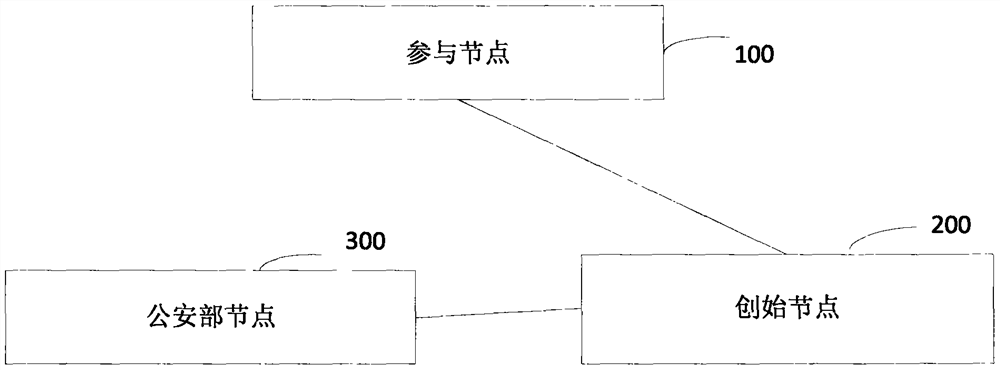
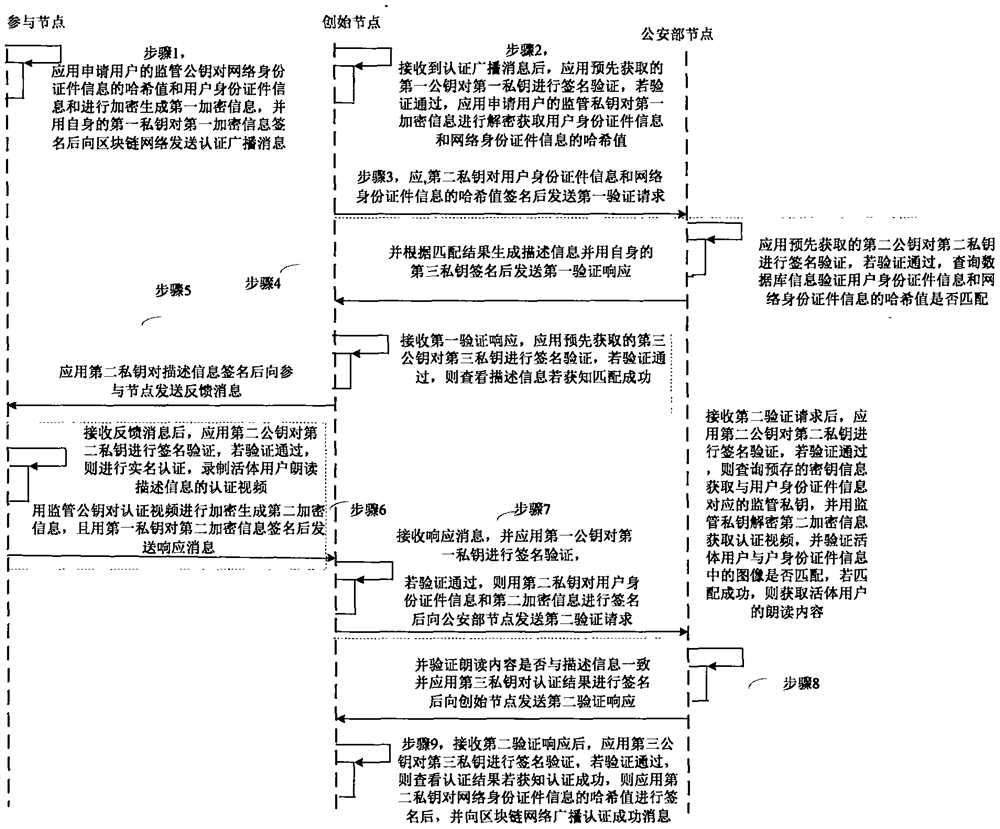
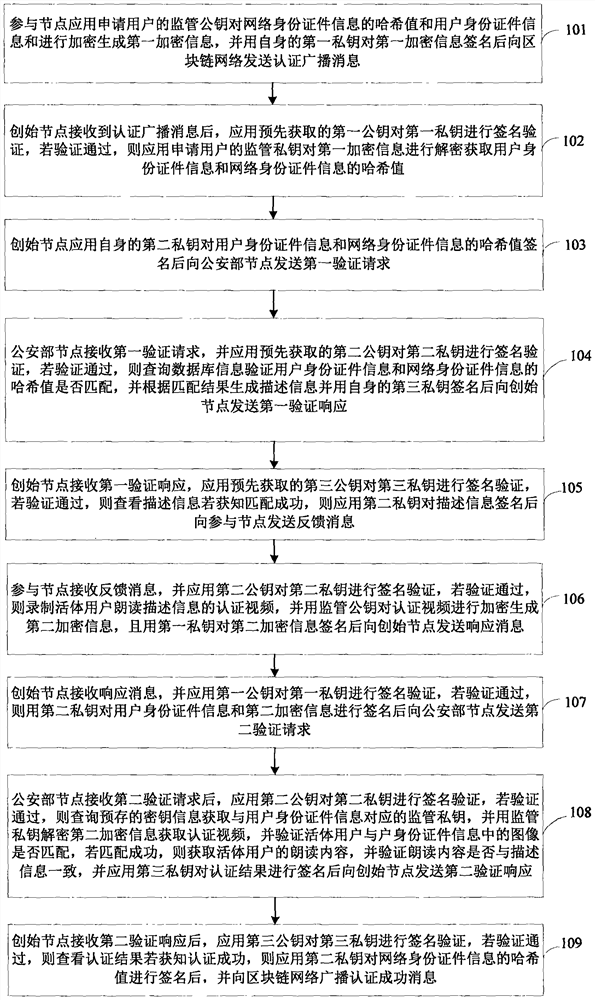
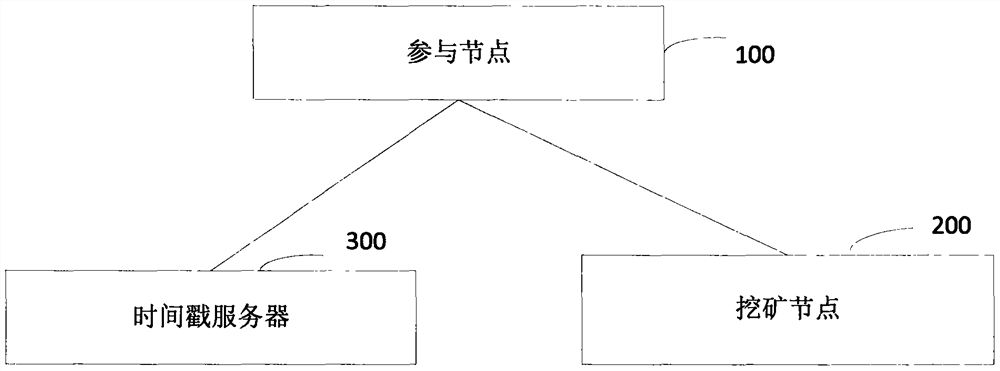
The invention discloses a network identity document authentication method and a system of a block chain, wherein the method comprises the following steps of: a participating node broadcasts application user network identity document information and user identity document information; obtaining the network identity document information and the user identity document information after a initiating node performs identity authentication on the participating node, and initiating verification to a Ministry of Public Security node; feeding back to the initiating node after the Ministry of Public Security node verifies that the network identity document information is consistent with the user identity document information; feeding back to the participant node after the initiating node verifies theMinistry of Public Security node, so as to perform application user real-name authentication. Thus, real-name authentication of nodes in the block chain is realized, nodes in the block chain networkare corresponding to the network identity document information which responds real user identity in real life, nodes are easy to manage and legitimacy to maintenance the block chain is facilitated.
Owner:全链通有限公司
Methods and devices for sending and receiving instruction information
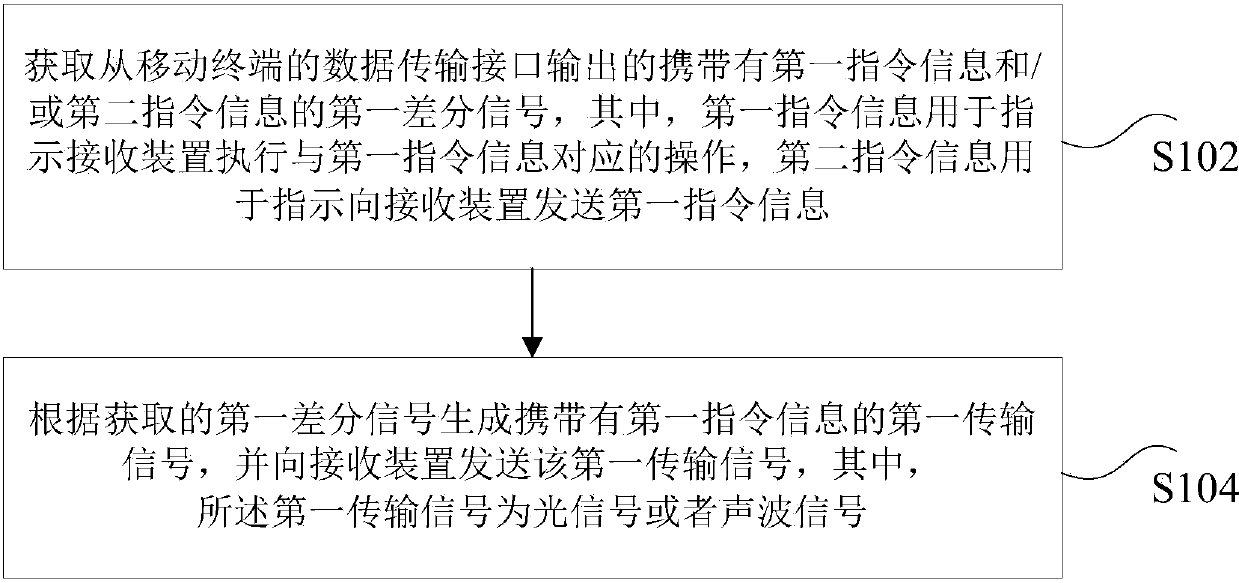
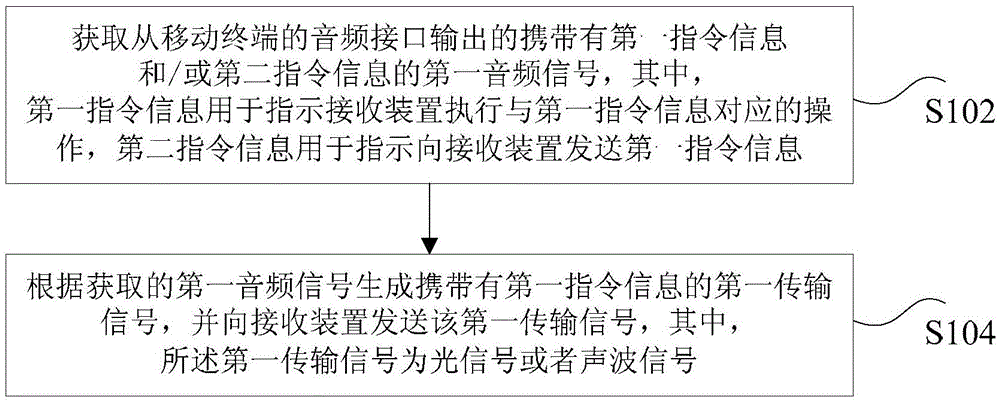
InactiveCN103793261AEnable two-way communicationRealize transmissionSoftware simulation/interpretation/emulationData transmissionOptical communication
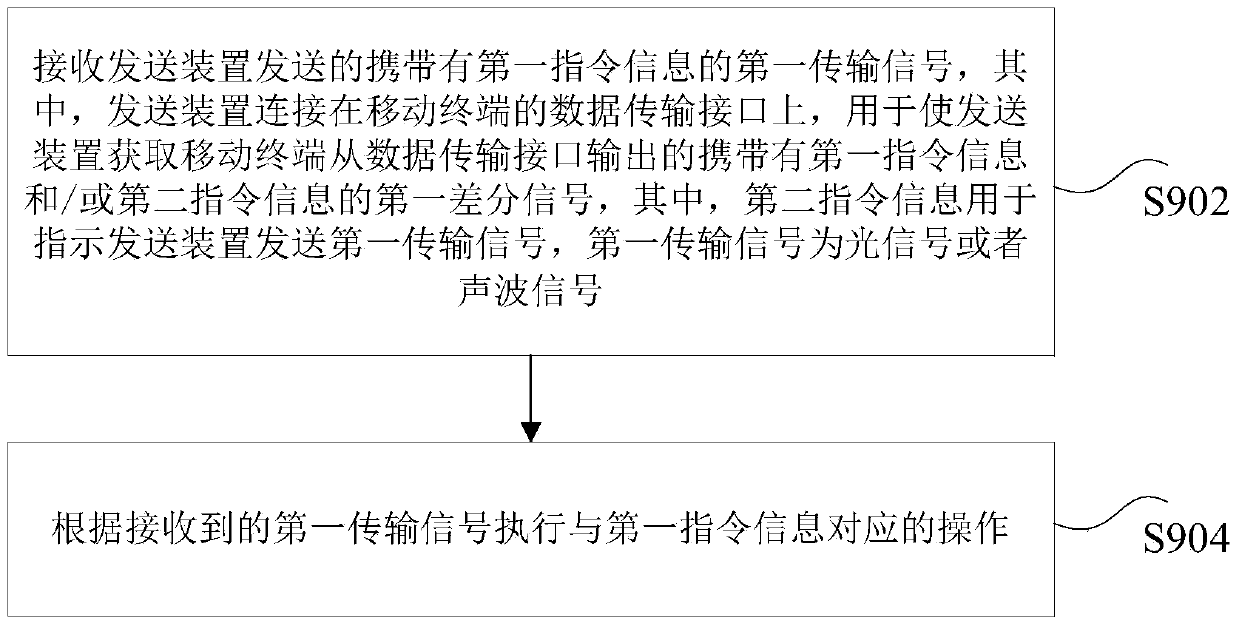
The invention discloses methods and devices for sending and receiving instruction information. The method for sending instruction information includes acquiring a first differential signal, carrying first instruction information and / or second instruction information, output from a data transmission interface of a mobile terminal, generating a first transmission signal carrying the first instruction information according to the acquired first differential signal and sending the first transmission signal to a receiving device. The first instruction information is used for indicating the receiving device to execute operations corresponding to the first instruction information, the second instruction information is used for indicating to send the first instruction information to the receiving device, and the first transmission signal is an optical signal or acoustic signal. With the methods and the devices for sending and receiving the instruction information, the technical problem that existing optical communication methods are difficult to be compatible with different types of mobile terminals is solved.
Owner:KUANG CHI INTELLIGENT PHOTONIC TECH
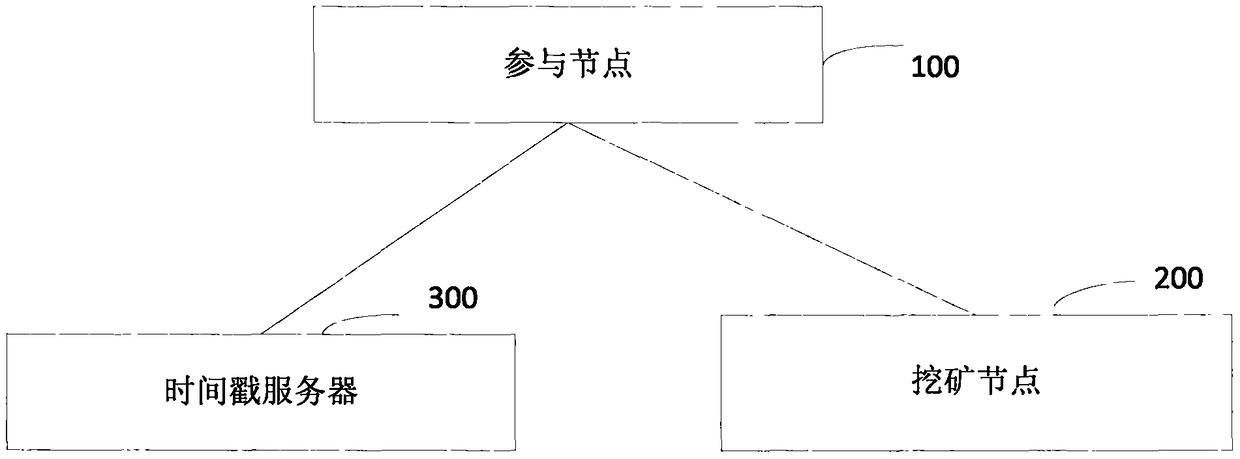
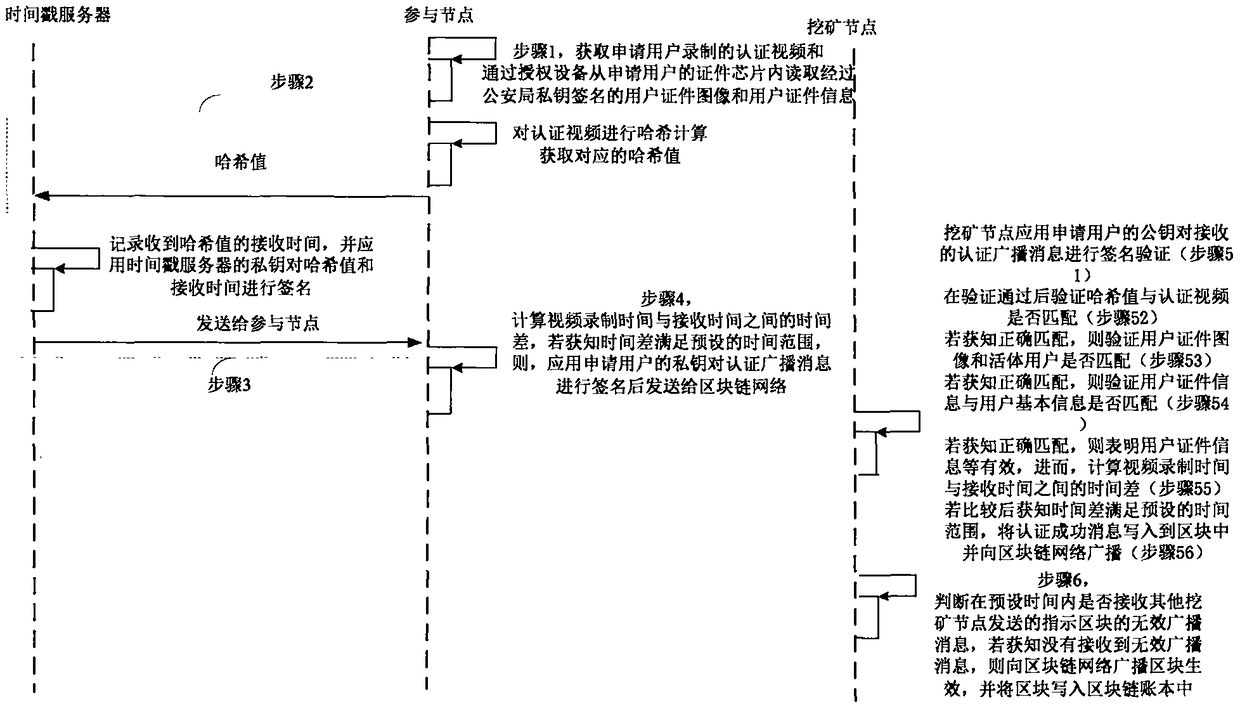
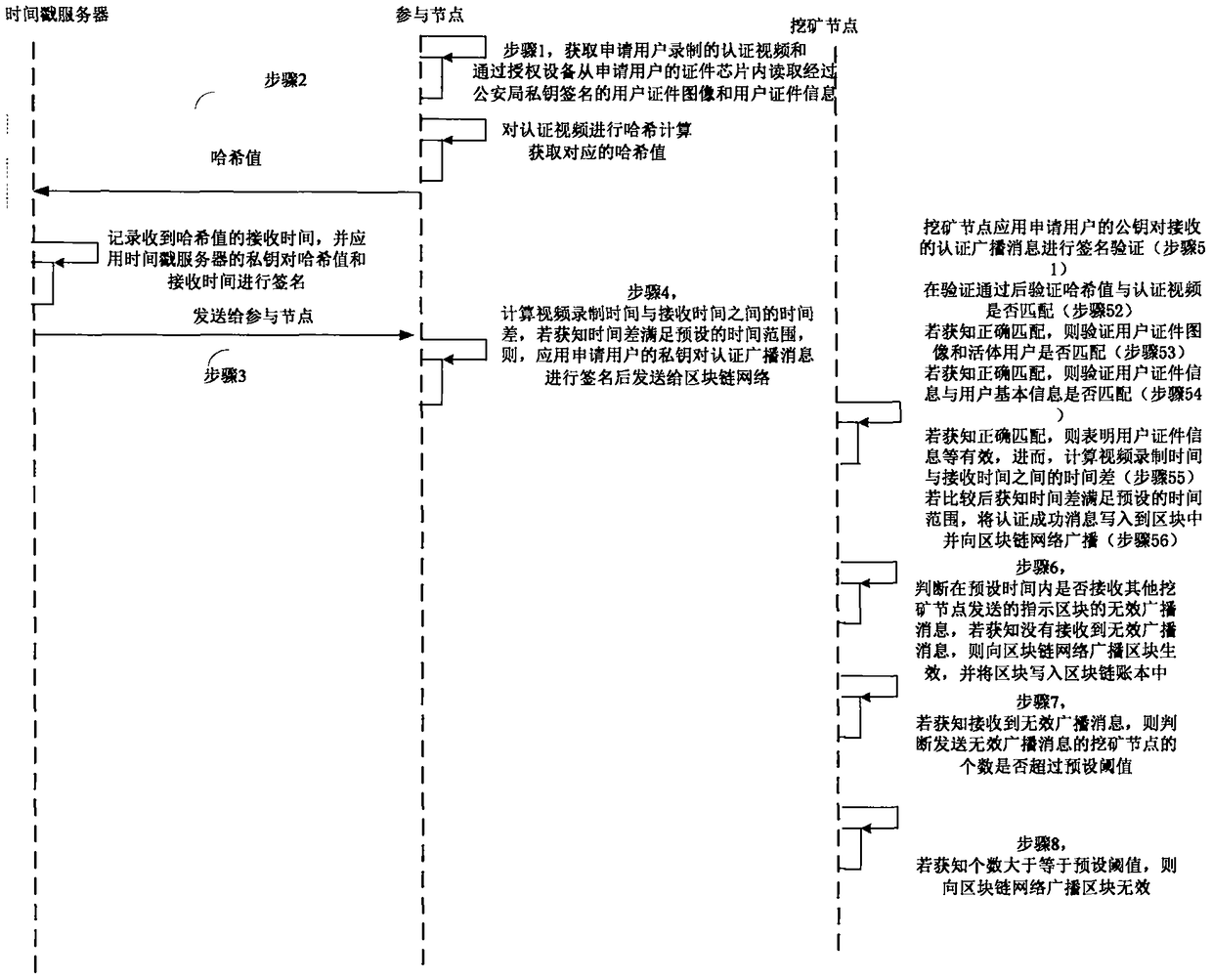
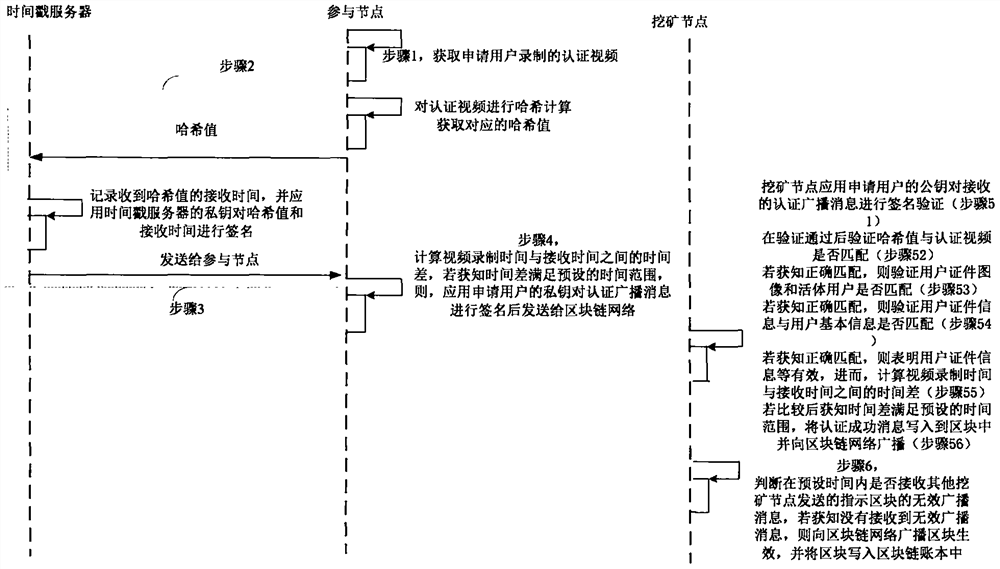
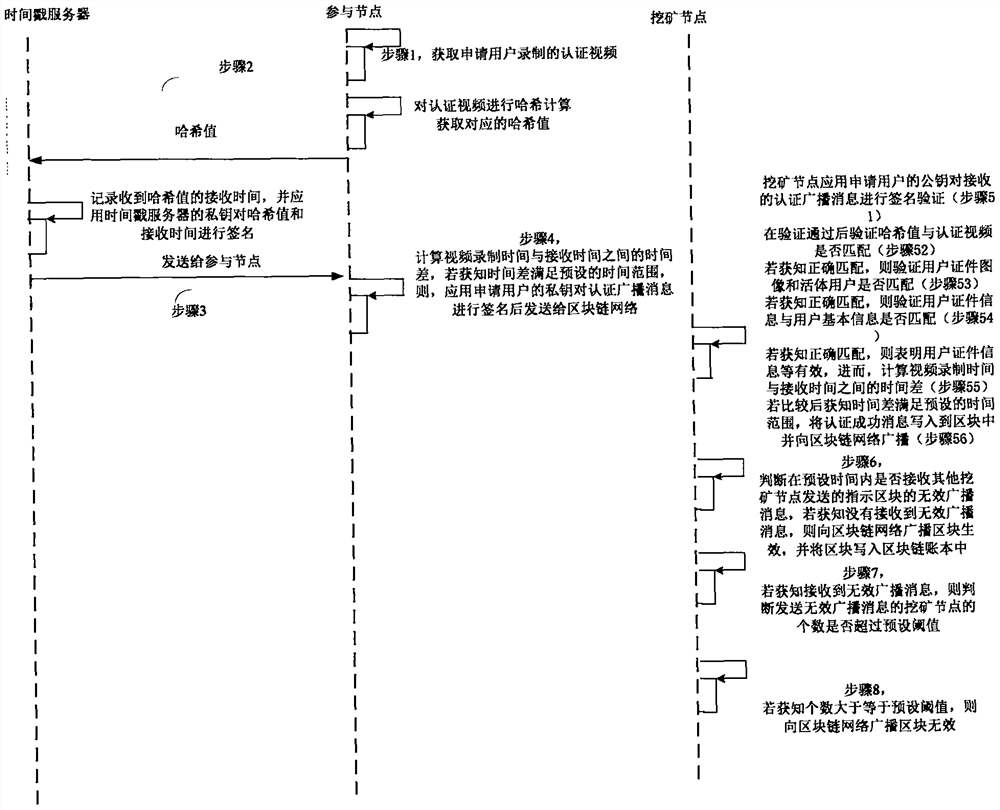
Block chain real-name participating method and system
InactiveCN108881253AGuaranteed accuracyGuaranteed reliabilityEncryption apparatus with shift registers/memoriesUser identity/authority verificationTime rangeChain network
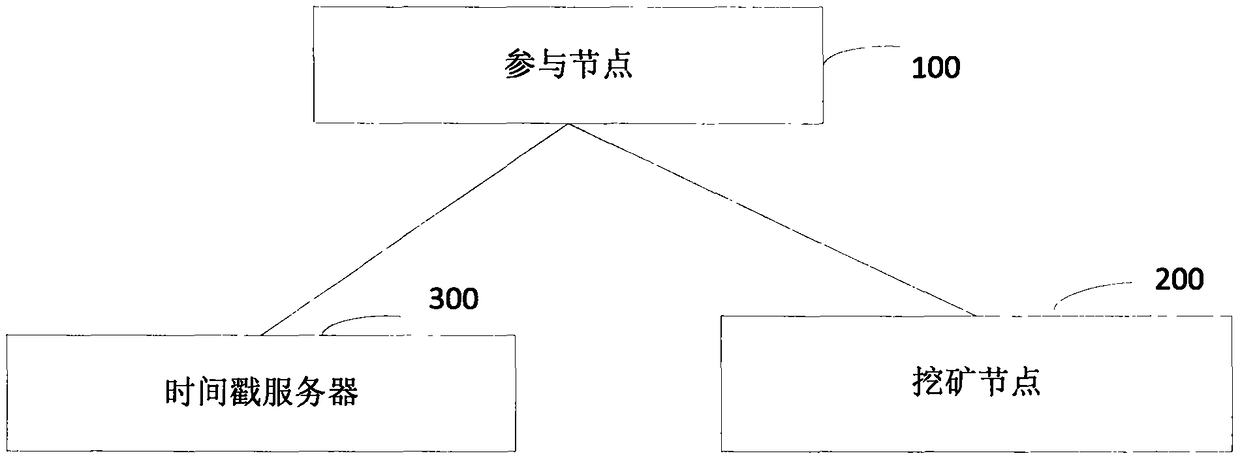
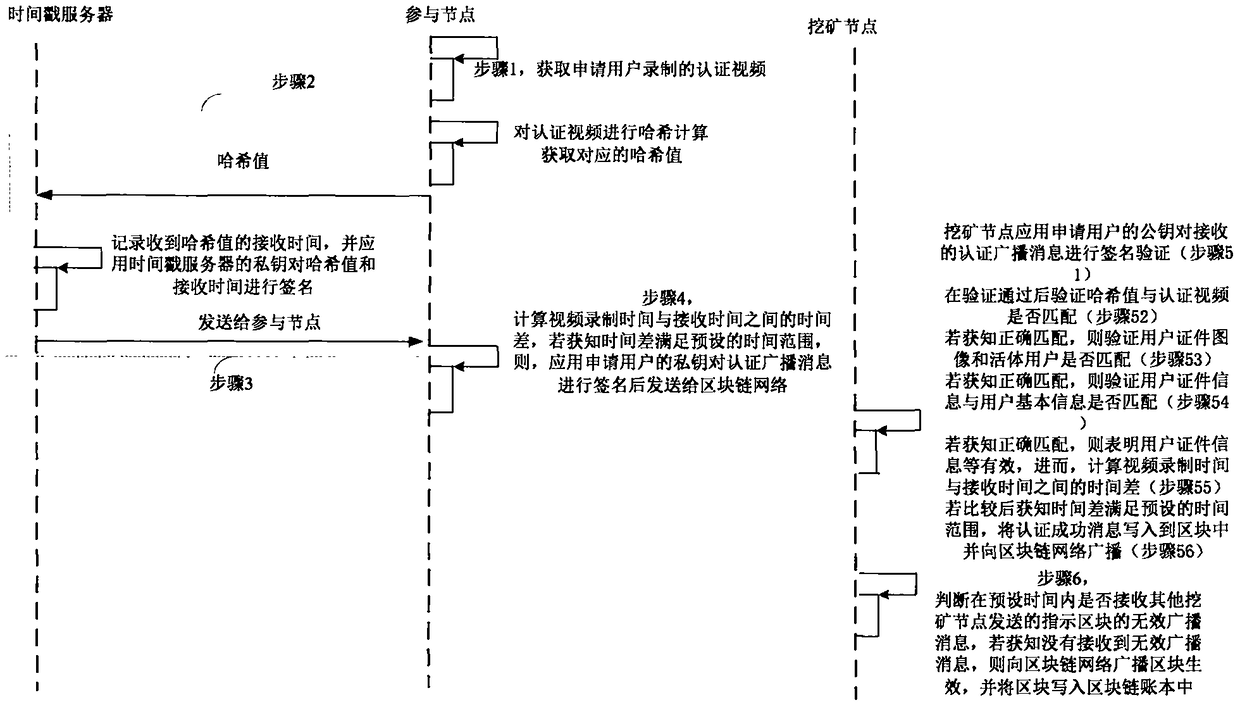
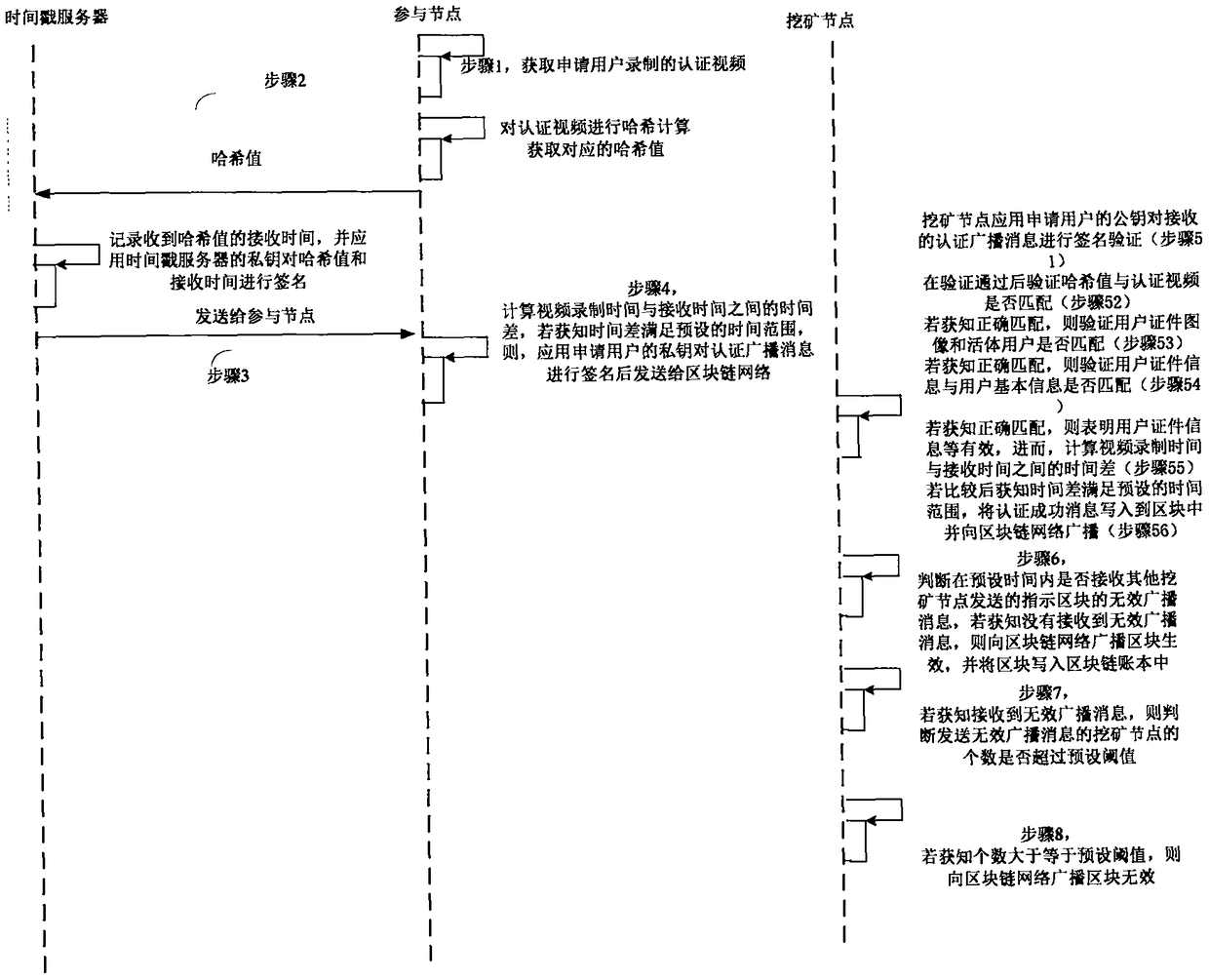
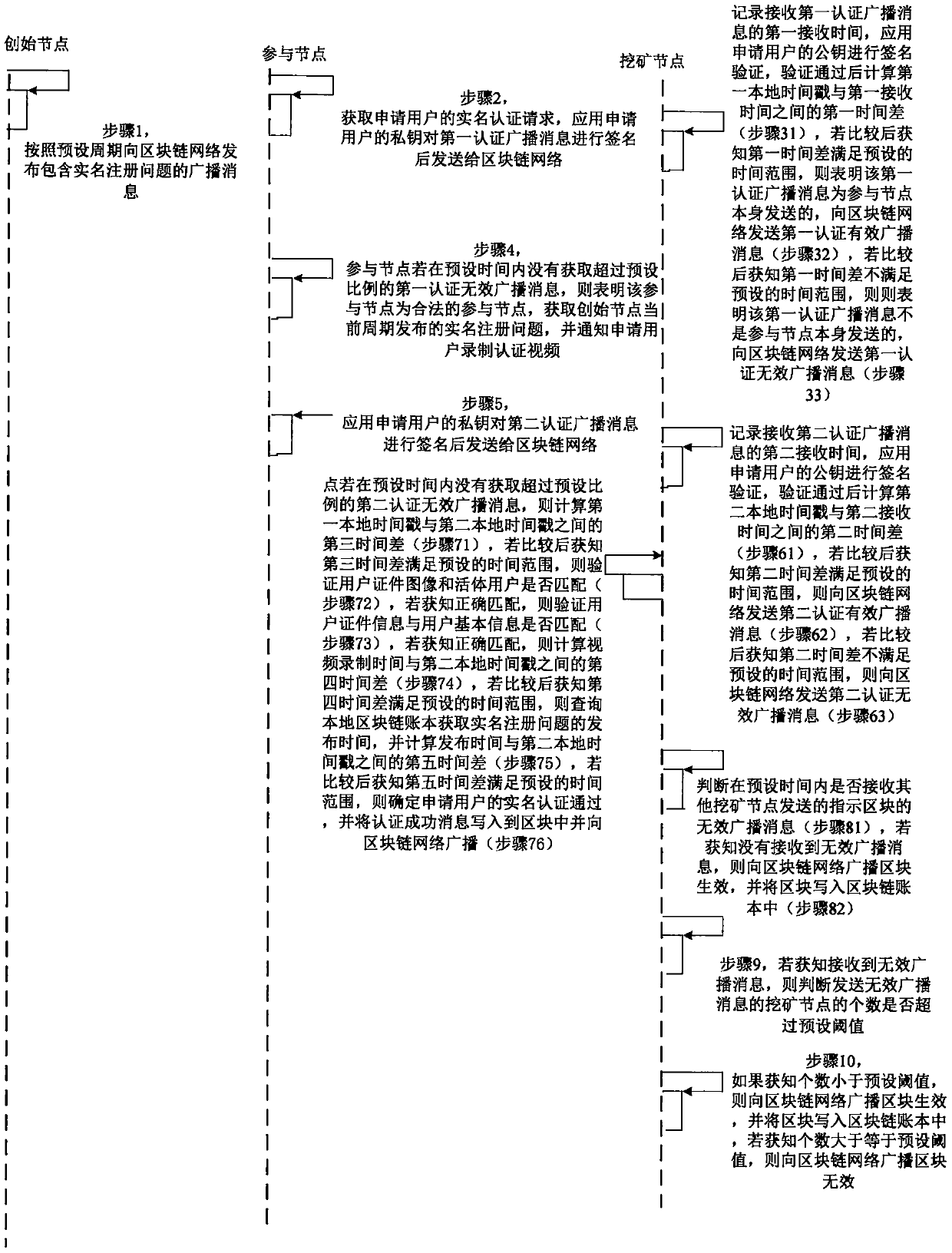
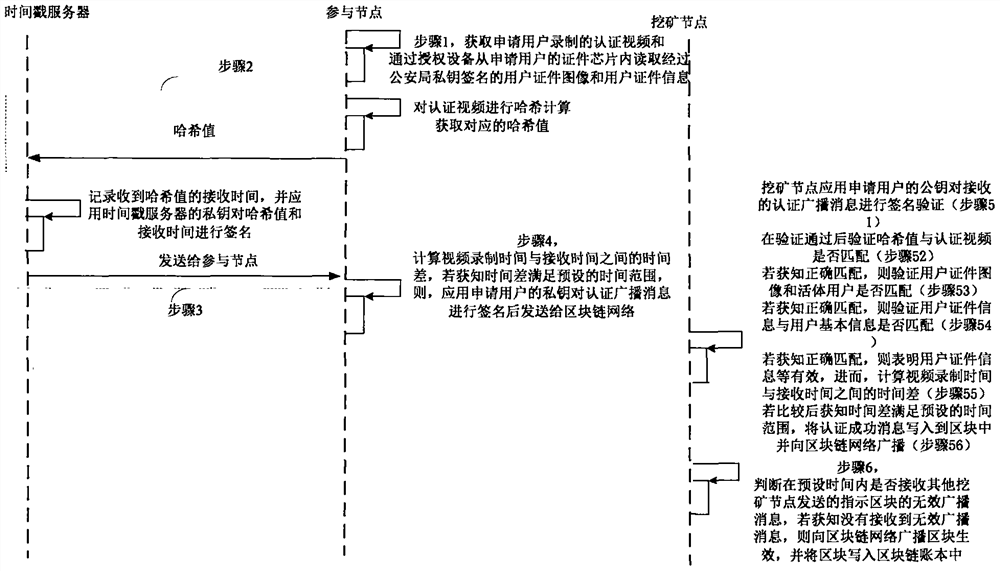
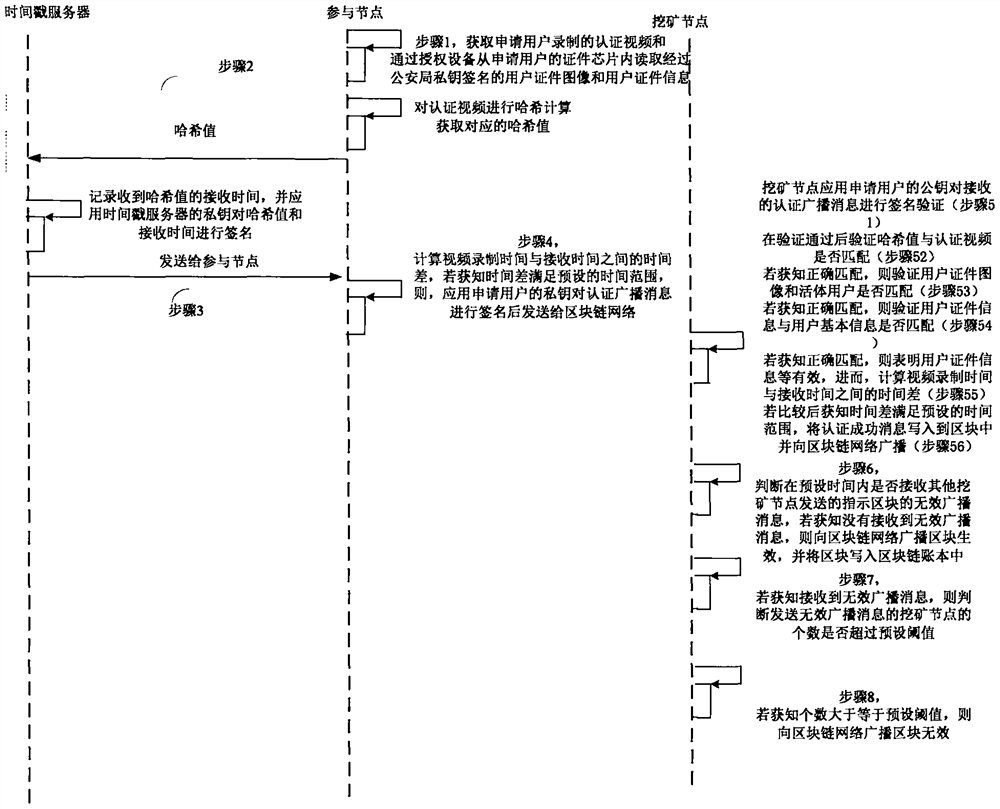
The invention provides a block chain real-time participating method and system. The method comprises the following steps: performing initial authentication according to an authentication video by a participating node; verifying whether a user certificate image is matched with a living user by a mining node after the initial authentication is passed, and verifying whether the user certificate information is matched with user basic information if the user certificate image is matched with the living user, wherein the user certificate image and the user certificate information are acquired and authenticated by the public security Bureau; if the user certificate information is matched with user basic information, computing the time difference between the video recording time and the receivingtime, and determining a fact that the real-name authentication of the application user is passed if the time difference satisfies the preset time range; and writing the block into a block chain into an account book if an invalid broadcast message is unreceived. Therefore, the real-name authentication of the node in the block chain is realized based on the user related information provided by the public security bureau, the accuracy of the real-time authentication is guaranteed; the node in the block chain network is corresponding to the real user identity in the reality, thereby facilitating the node management and block chain legality maintenance.
Owner:全链通有限公司
Artificial intelligence epidemic situation big data prevention and control early warning system
PendingCN111653368AReduce the pressure of screening workImprove the detection rateEpidemiological alert systemsSensing radiation from moving bodiesEarly warning systemEngineering
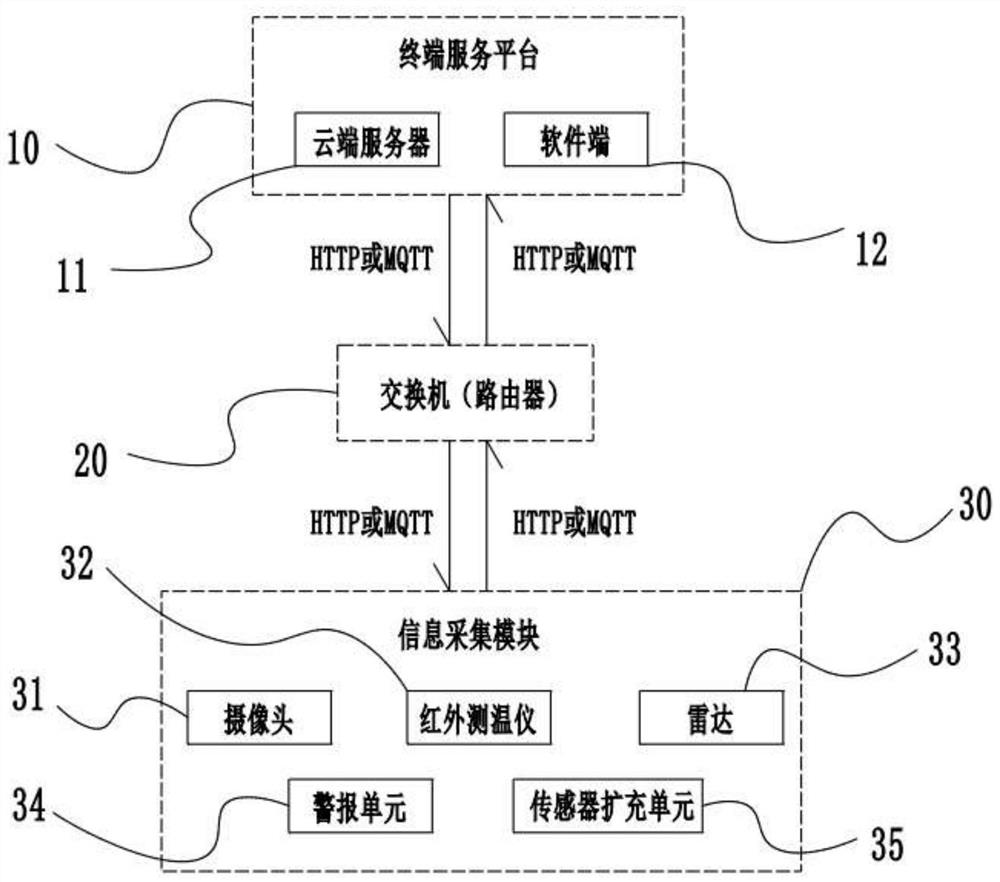
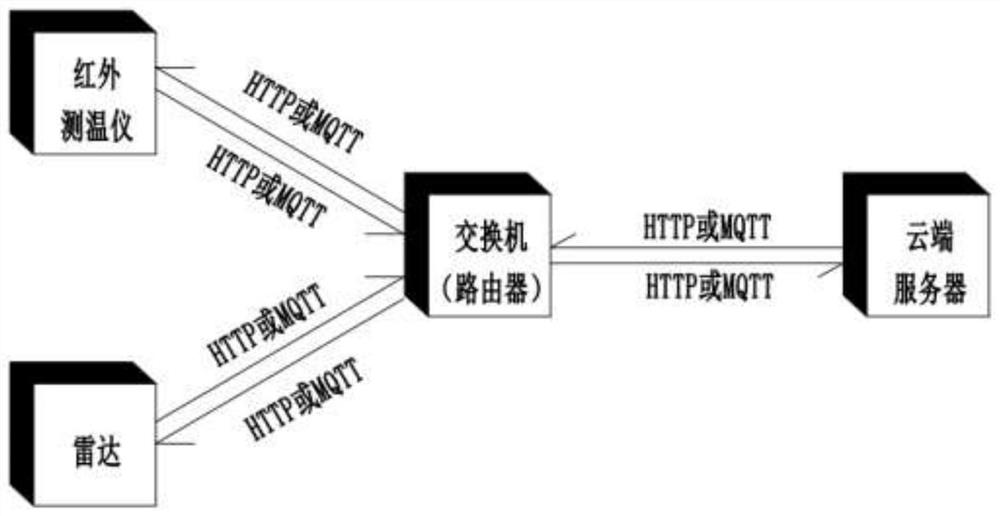
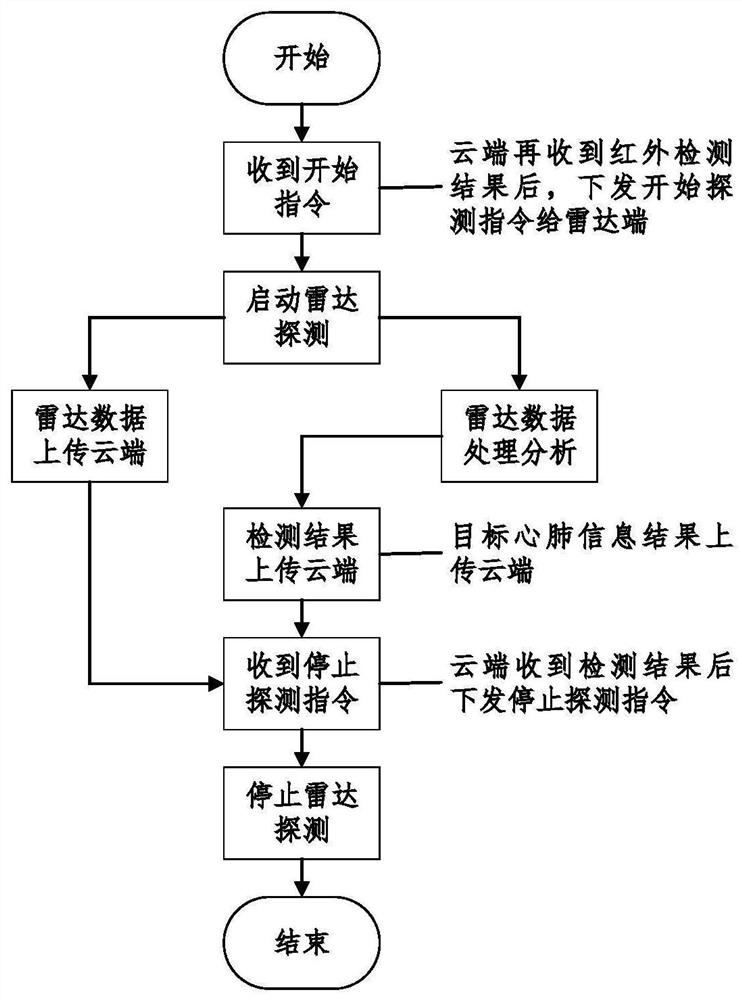
The invention discloses an artificial intelligence epidemic situation big data prevention and control early warning system, which comprises a terminal service platform, a plurality of information acquisition modules connected to the terminal service platform, and switches respectively connected between the plurality of information acquisition modules and the terminal service platform and used forbidirectional communication. According to the invention, face-body temperature-cardiopulmonary multi-mode recognition and intelligent analysis are carried out on a person, so that a traditional singleinfrared temperature measurement mode is broken through, non-contact accurate temperature measurement, cardiopulmonary signal measurement and abnormal alarm are achieved, screening, detection and alarm are mainly conducted on current corona virus disease 2019 patients, especially patients without symptoms, the screening work pressure of key public places can be greatly relieved, and the detectionprobability of suspected persons is increased; and an AI mathematical model algorithm is adopted, so that the system has the data deep mining capability, can perform deep learning by utilizing a neural convolutional network, can predict the epidemic situation development trend, and generates the epidemic situation monitoring and troubleshooting standard in real time.
Owner:梁步阁
Identity identification method and system based on combination of face characteristics and device fingerprint
PendingCN105488495AGuaranteed accuracyEnable login convenienceMatching and classificationSpoof detectionAuthentication serverTwo step
The invention discloses an identity identification method and system based on combination of face characteristics and a device fingerprint. The method includes two steps of registration certification and user identification. The system includes an intelligent mobile phone, a memory server for storing the device fingerprint information of the intelligent mobile phone and the user identity information, and a certificate server for identifying the face in-vivo information and the device fingerprint information of the intelligent mobile phone, the intelligent mobile phone is connected with the input end of the memory server, the output end of the memory server is connected with the certificate server, and the intelligent mobile phone is in interaction connection with the certificate server. Through the combination of intelligent face in-vivo identification technology and intelligent mobile phone fingerprint technology, the effects of network real-person and real-name certification, high network account security, and convenient logging are achieved.
Owner:SHANGHAI CHUANZHI FINANCE INFORMATION SERVICE CO LTD
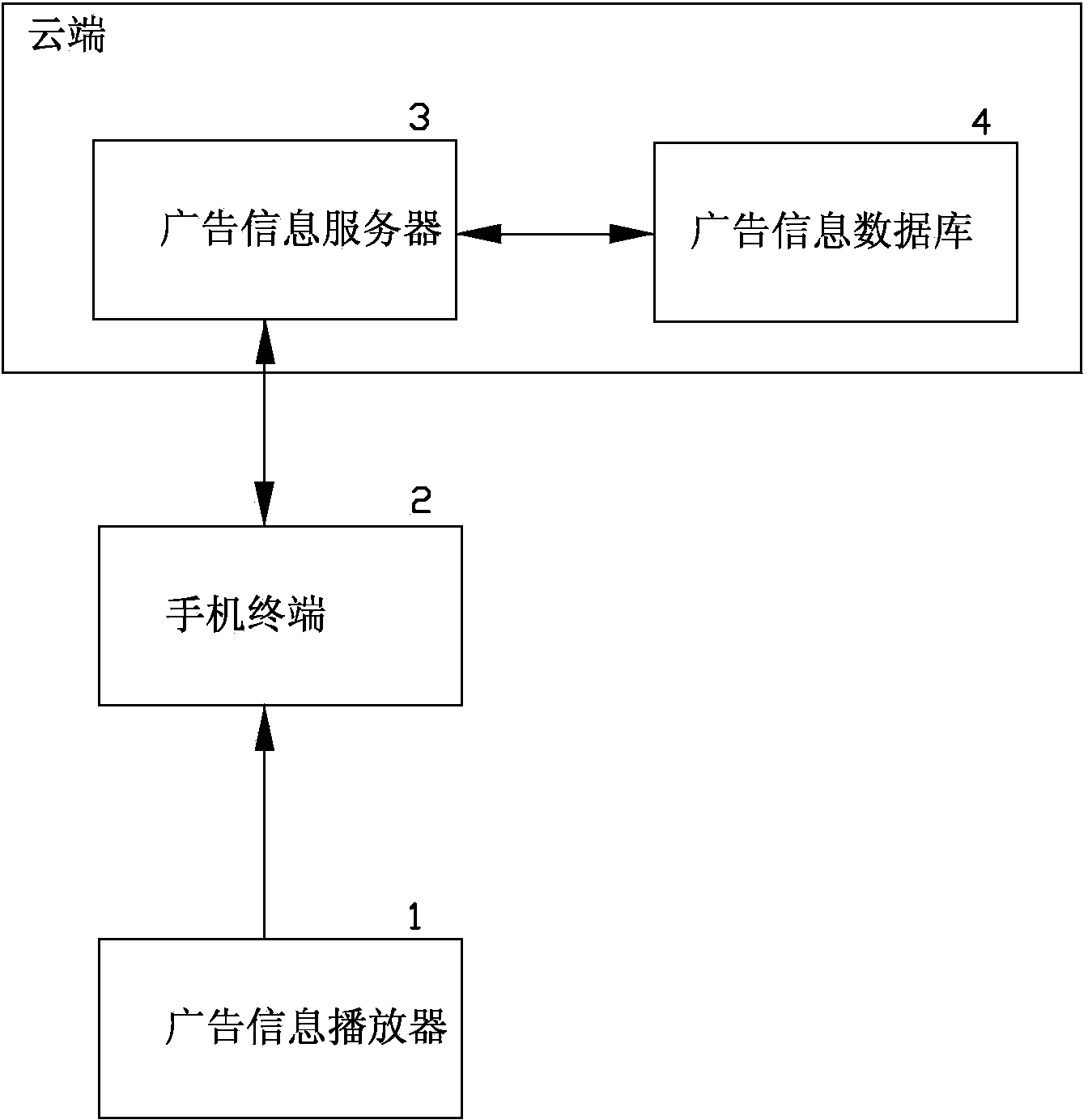
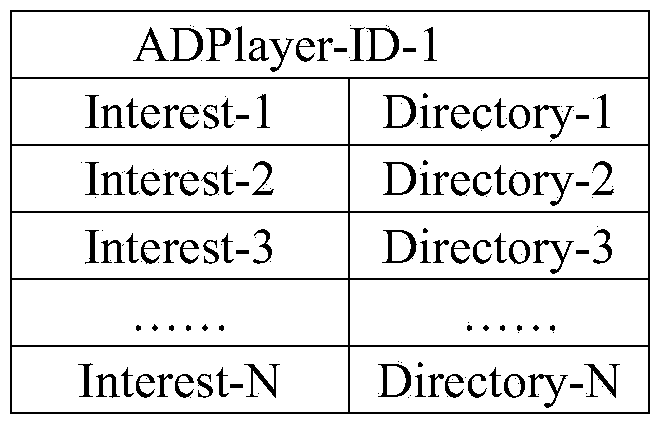
Mobile terminal interactive advertising message communication method
The invention discloses a mobile terminal interactive advertising message communication method. A smartphone is used as a mobile terminal; a played advertising message resource is provided by an advertising message server stored on the cloud; an advertisement player is similar to a miniature RFID card reader and plays ID index information of the station by a broadcasting mode; advertisement content information is downloaded to a mobile phone of a client through a cloud server; and a user can selectively play and read advertising messages. By an active push propagation mode and with the combination of setting advertisement interest focuses of clients in terminal client program APP, releasing of advertising messages has pertinency, and clients will not think of the advertising messages as spam advertisement. In addition, by a personal identity authentication mode, information such as negotiable securities provided by merchants is approved through the real-name system. Thus, for advertisers, propaganda effect of commercial advertisement can be raised, and true and safe business information also can be provided for consumers. Therefore, the purpose of mutual benefit can be achieved.
Owner:XIAMEN ELITE ELECTRIC
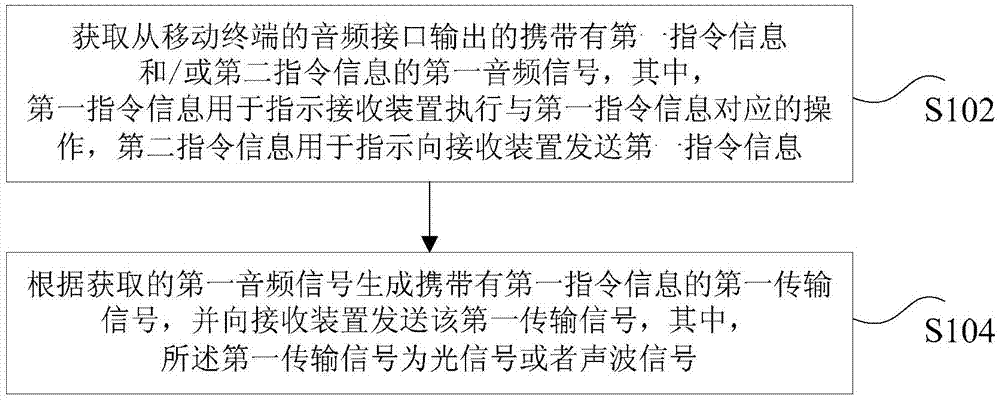
Method and device for sending and receiving command information
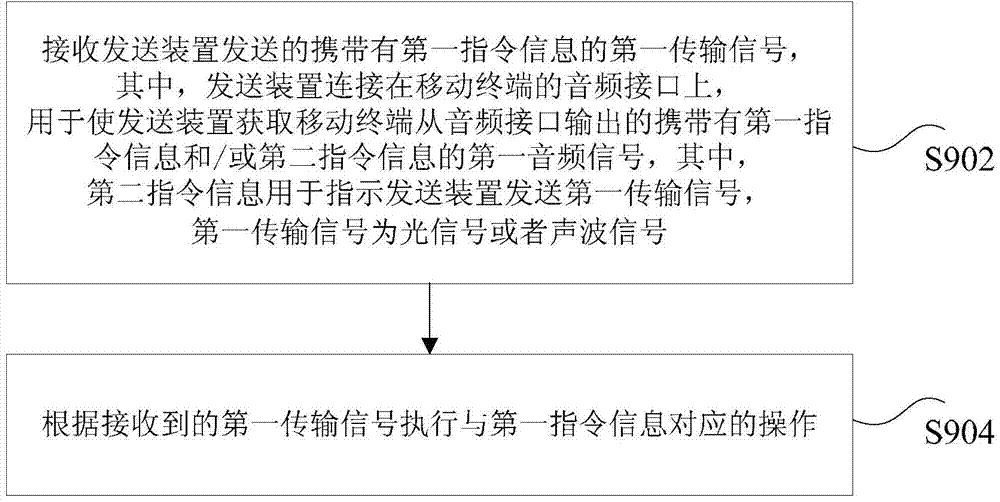
ActiveCN103810017AEnable two-way communicationRealize transmissionSoftware simulation/interpretation/emulationAcoustic waveOptical communication
The invention discloses a method and a device for sending and receiving command information. The method for sending the command information comprises the steps as follows: obtaining a first audio signal which carries first command information and / or second command information and is output by an audio interface of a mobile terminal, wherein the first command information is used for instructing a receiving device to execute an operation corresponding to the first command information, and the second command information is used for instructing sending of the first command information to the receiving device; according to the obtained first audio signal, generating a first transmission signal carrying the first command information and sending the first transmission signal to the receiving device, wherein the first transmission signal is an optical signal or an acoustic signal. According to the method and the device, the technical problem that existing optical communication methods are hard to be compatible with mobile terminals with different models is solved.
Owner:KUANG CHI INTELLIGENT PHOTONIC TECH
Data processing method and apparatus of mobile communication electronic SIM card
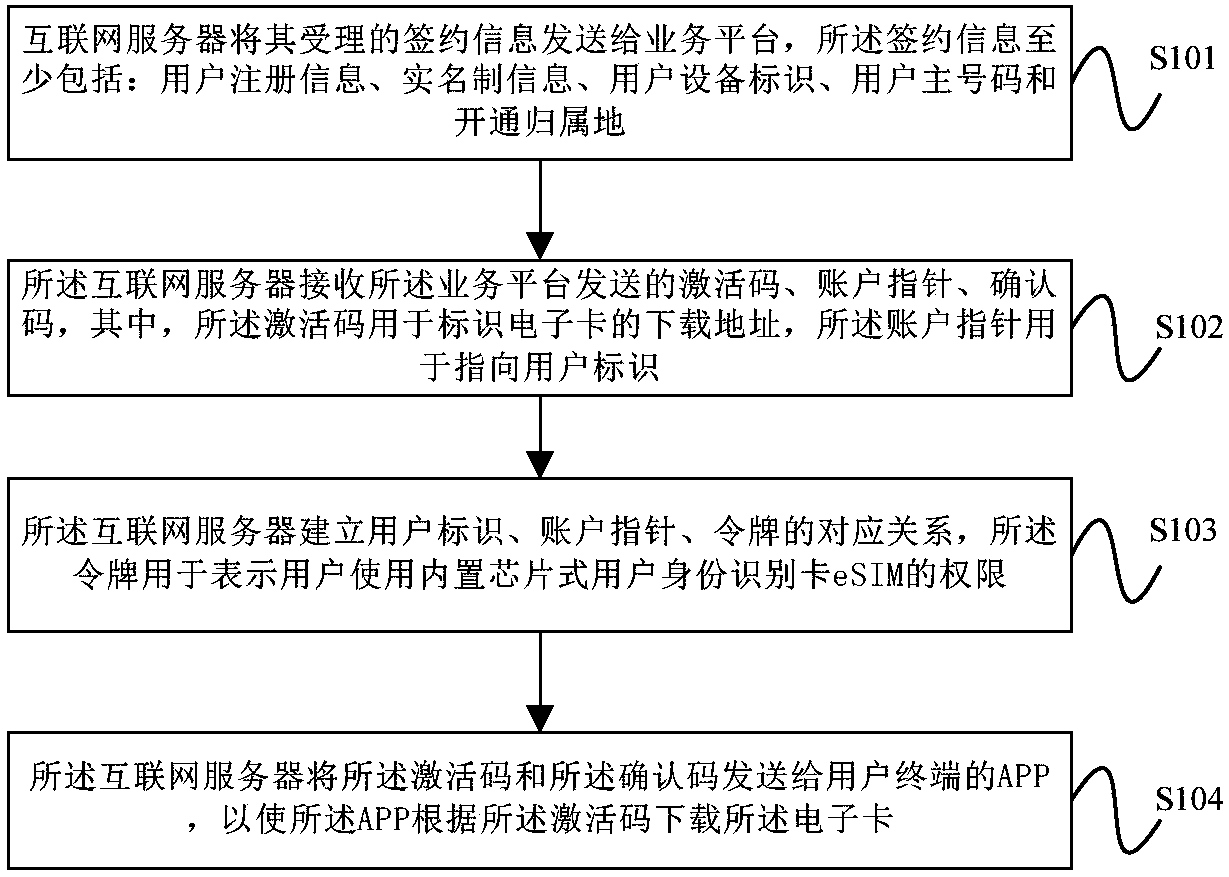
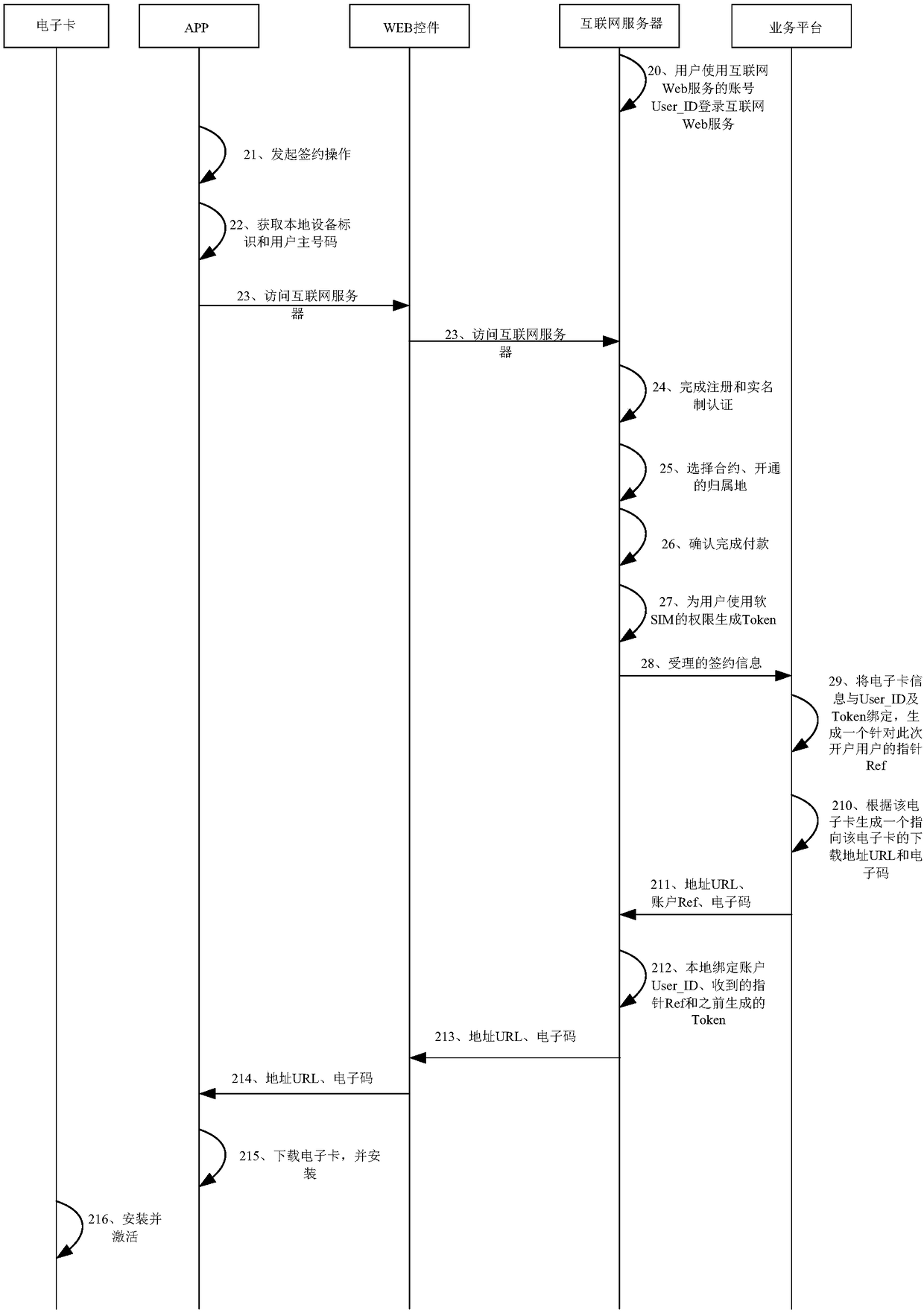
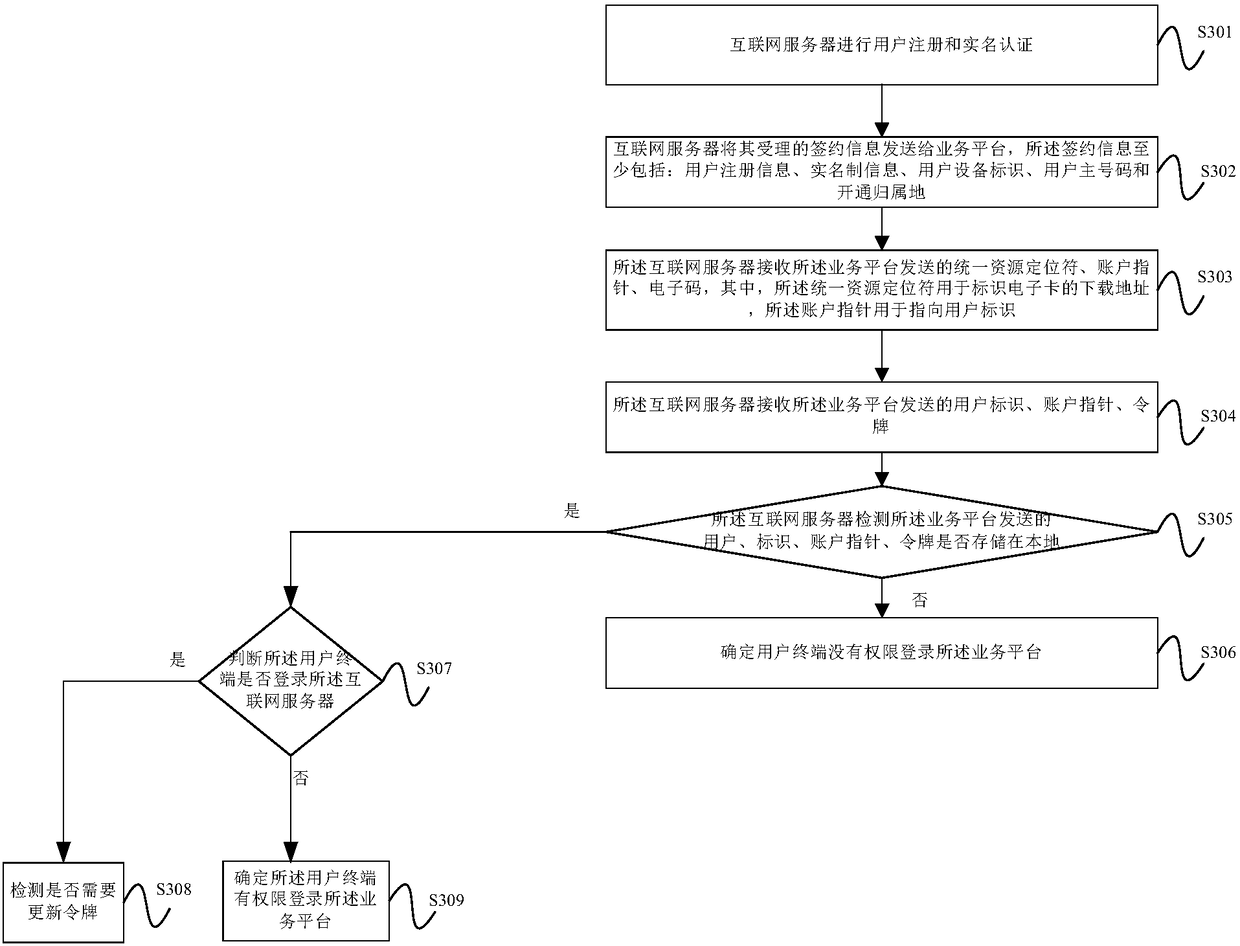
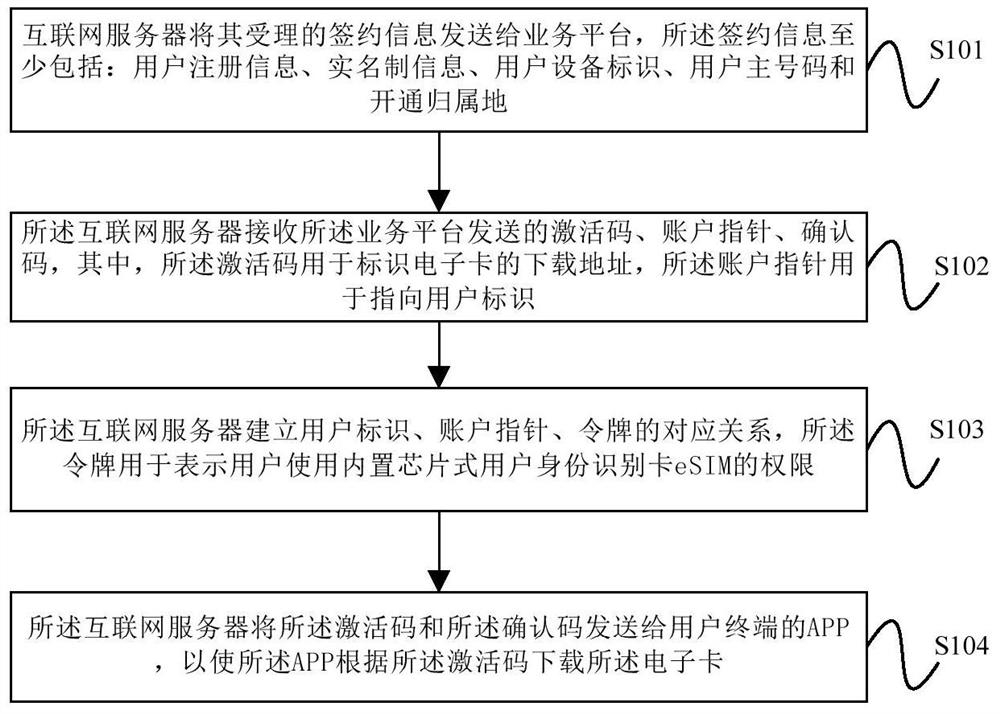
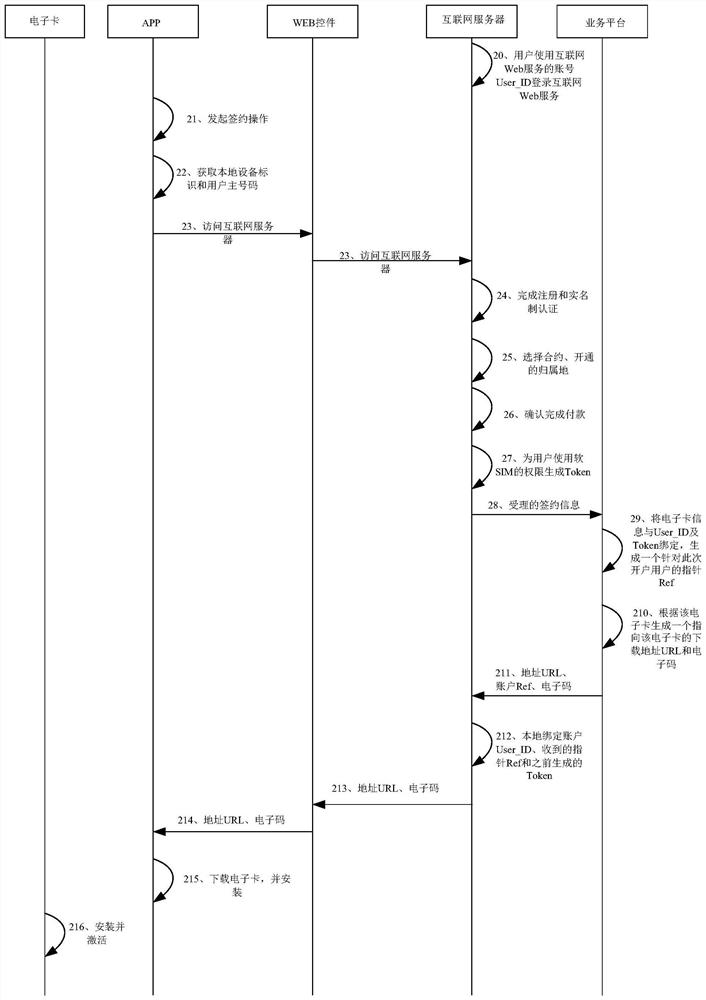
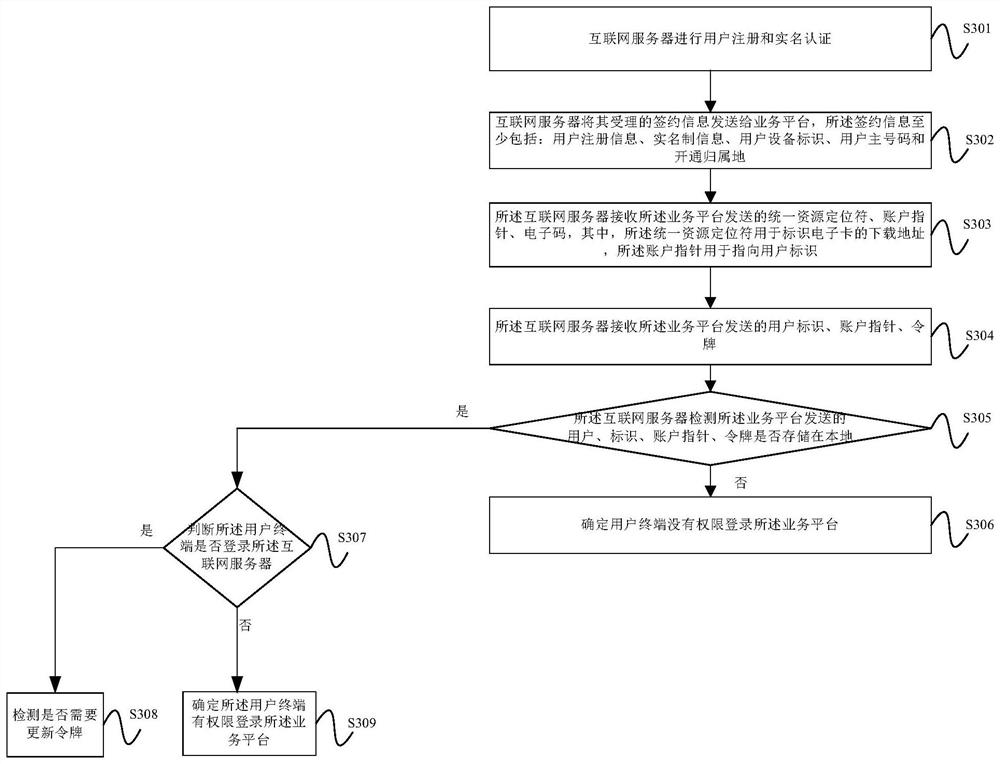
ActiveCN108200568ARealize real-name authenticationImplement identity authenticationNetwork data managementComputer terminalUser identifier
The embodiment of the invention provides a data processing method and apparatus of a mobile communication electronic SIM card. The method comprises the following steps: sending, by an Internet server,accepted subscription information to a service platform; receiving an activation code, an account pointer and a confirmation code sent by the service platform; establishing a corresponding relationship between a user identifier, the account pointer and a token; and sending the activation code and the confirmation code to an APP of a user terminal. In the embodiment of the invention, the acceptedsubscription information is sent to the service platform by the Internet server, the activation code, the account pointer and the confirmation code sent by the service platform are received, the corresponding relationship between the user identifier, the account pointer and the token is established, and the activation code and the confirmation code are sent to the APP of the user terminal, so thatthe APP downloads the electronic card according to the activation code, and real name authentication and user identity authentication in mobile communication are achieved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Block chain real name participation method and system
InactiveCN108876375ARealize real-name authenticationFacilitate legalitySecuring communicationProtocol authorisationTime rangeChain network
The invention provides a block chain real name participation method and a system, wherein the method comprises: participating node performs preliminary authentication according to time difference between authentication video recording time and receiving time; mining node verifies whether user document image matches living user, after the preliminary authentication is passed; if it matches, verifywhether user document information matches user's basic information; if it matches, calculating the time difference between the video recording time and the receiving time; if the time difference satisfies preset time range, it is determined that application user real name authentication is passed; if no invalid broadcast message is received, writing block to block chain ledger. Thereby, the real name authentication of nodes in the block chain is realized, and the nodes in the block chain network are associated with real user identity in real life, which facilitates the management of the nodesand maintains the legitimacy of the block chain.
Owner:全链通有限公司
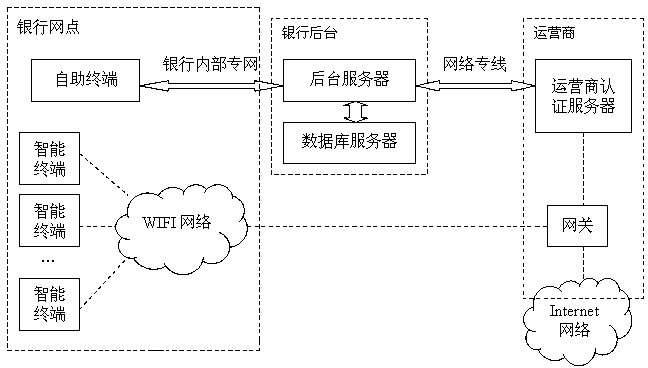
Business outlet Internet WIFI access system and method thereof
ActiveCN103327490AEasy to superviseRealize real-name authenticationNetwork topologiesSecurity arrangementResource informationDatabase server
The invention discloses a business outlet Internet WIFI access system and a method thereof. The system comprises a plurality of intelligent terminals, a self-service terminal, a background server, an operator certification server, a database server, a Portal server and a gateway. The self-service terminal is connected with the background server through a bank internal special network. The background server is connected with the operator certification server through a network special line. The operator certification server is respectively connected with each intelligent terminal through a WIFI network. The WIFI network is connected with the Internet, the operator certification server and the Portal server through the gateway. The business outlet Internet WIFI access system is provided with real name authentication and Internet behavior tracing functions, bank self-service equipment and the operator certification server are organically combined, combined with bank customer resource information, the safety of a bank network and the high efficiency and flexibility of an Internet environment provided by an operator are taken into consideration at the same time, and a safe Internet environment is provided for customers.
Owner:中国农业银行股份有限公司四川省分行
Information transmission method
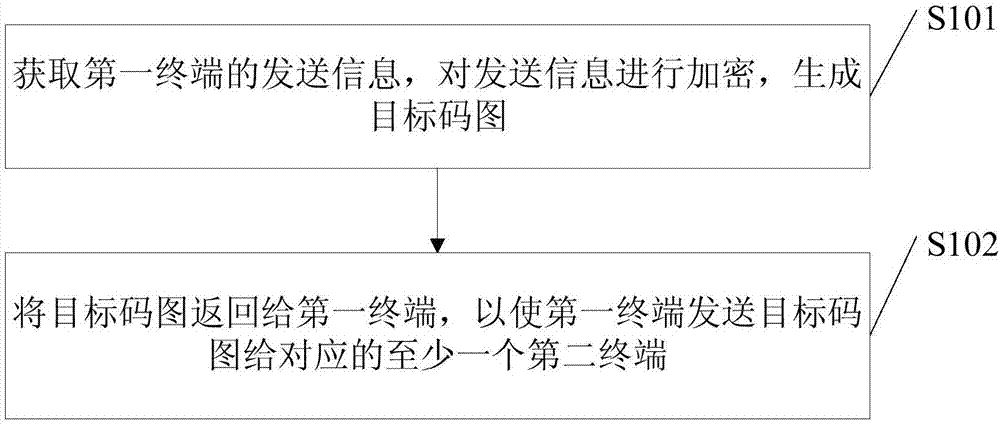
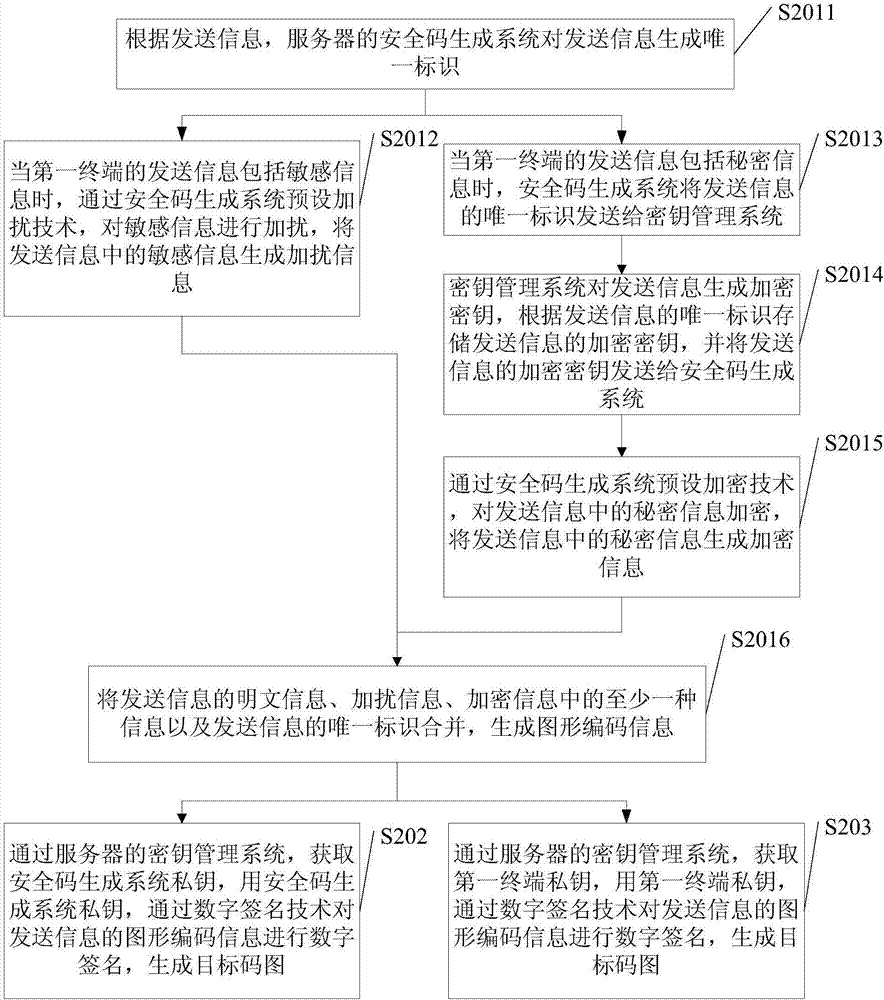
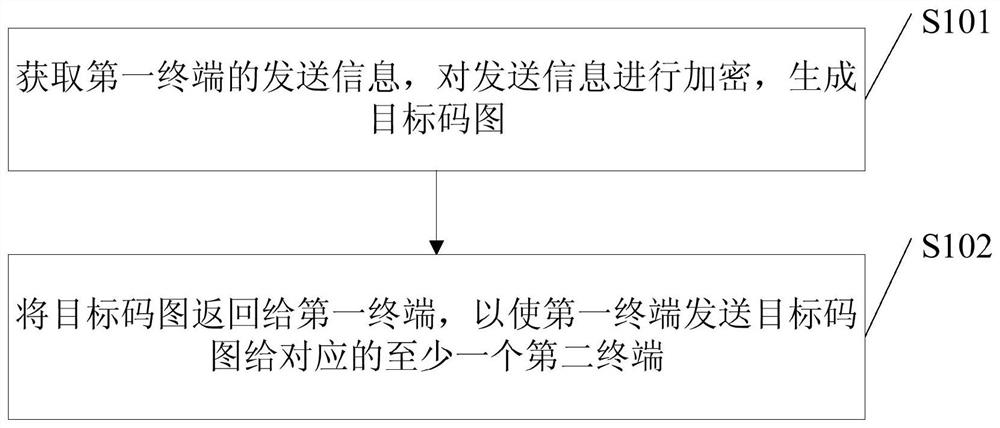
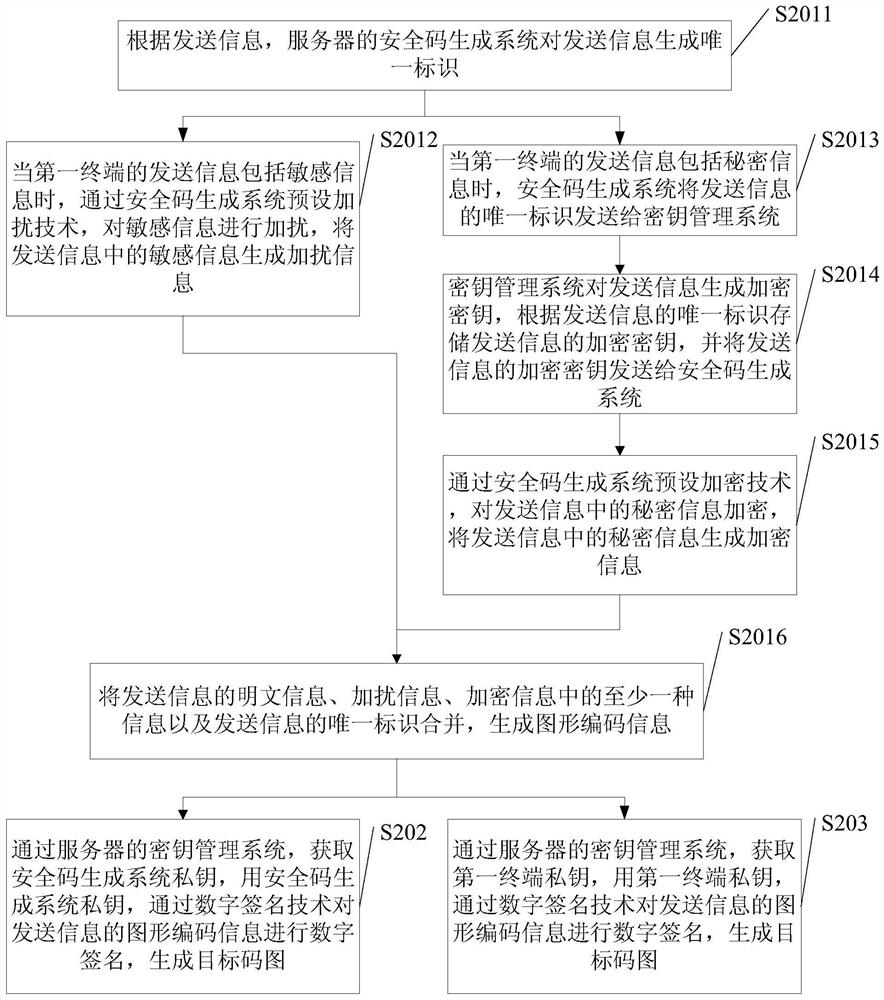
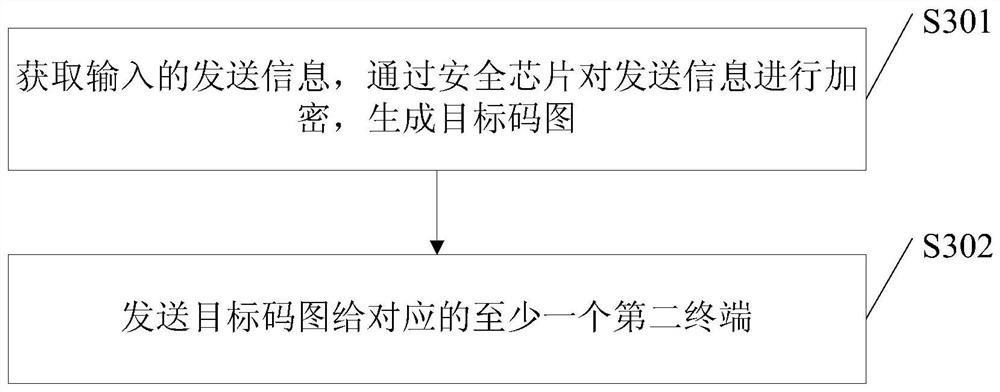
ActiveCN107294964AHigh encryption levelImprove the leakage levelKey distribution for secure communicationUser identity/authority verificationInformation transferInformation transmission
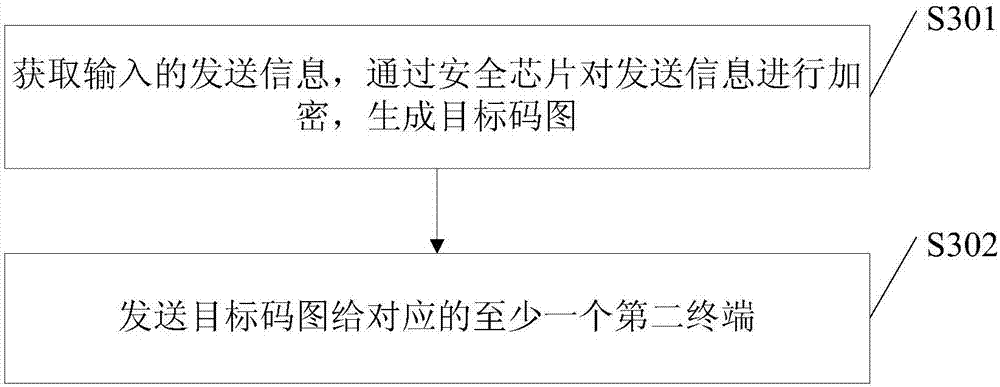
The embodiments of the invention disclose an information transmission method, wherein the information transmission method is applied to a server and comprises: obtaining the information transmitted from a first terminal, encrypting the transmitted information, and generating a targeted code graph, wherein the transmitted information comprises at least one of the following kinds of information: plaintext information, sensitive information or secrete information and the targeted code graph carries the graphic code information and the digital signature to the graphic code information by a security code generation system's private key or the digital signature to the graphic code information by a first terminal's private key; and returning the targeted code graph to the first terminal so that the first terminal transmits the targeted code graph to at least one corresponding second terminal. The information transmission method of the invention makes the information transmission more secure and more private.
Owner:BEIJING D9ING INST OF INFORMATION ENG CO LTD +1
Real-name authentication method and device
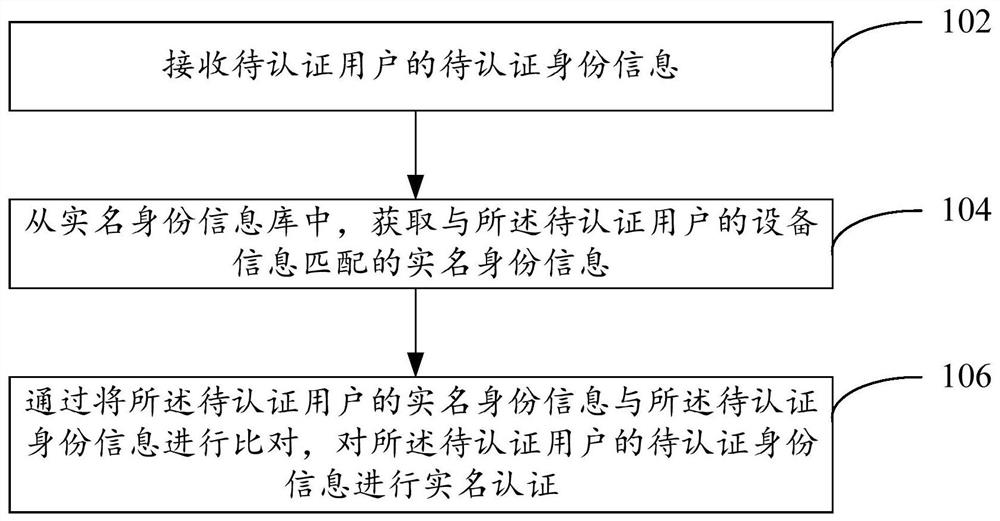
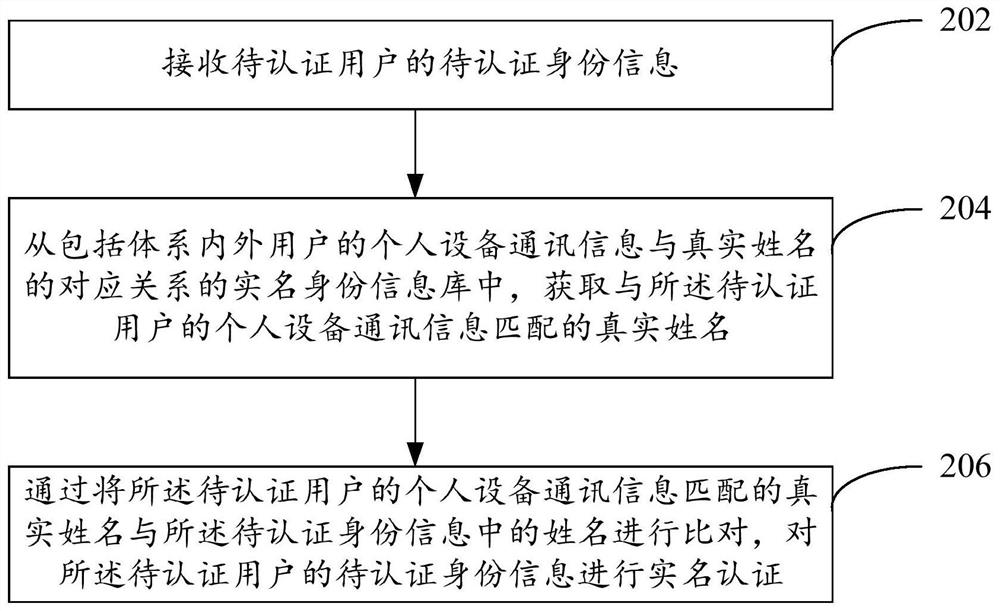
ActiveCN110808978AReduce stepsImprove experienceData processing applicationsDigital data authenticationInformation repositoryInternet privacy
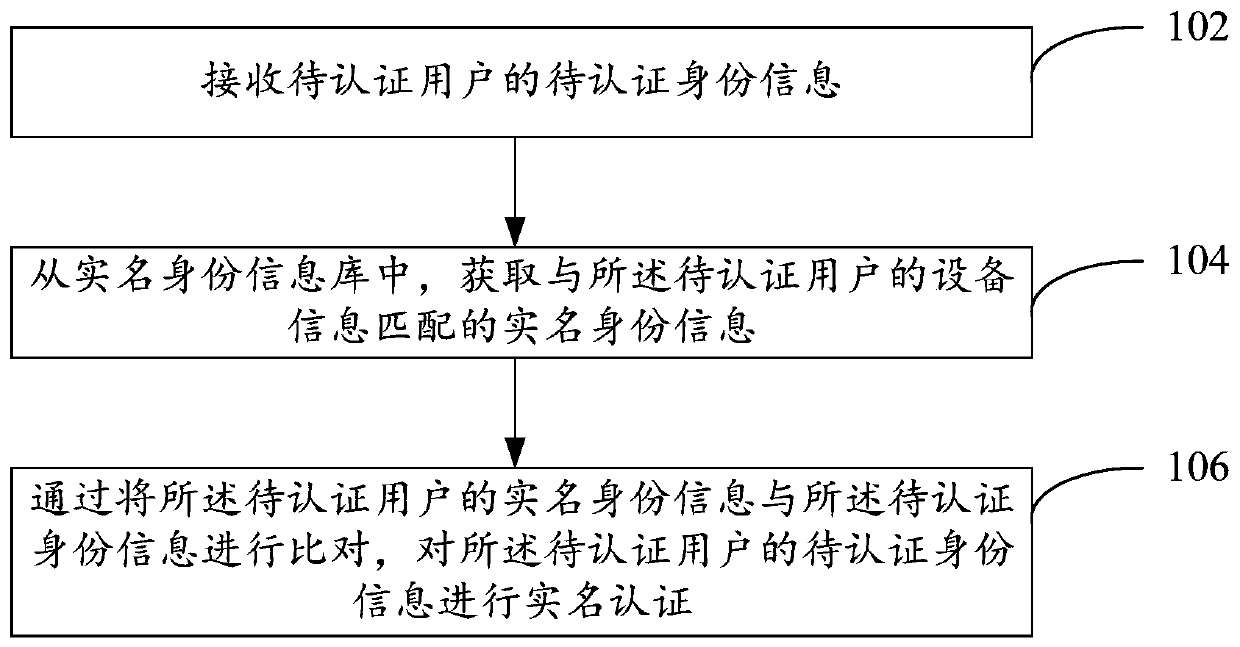
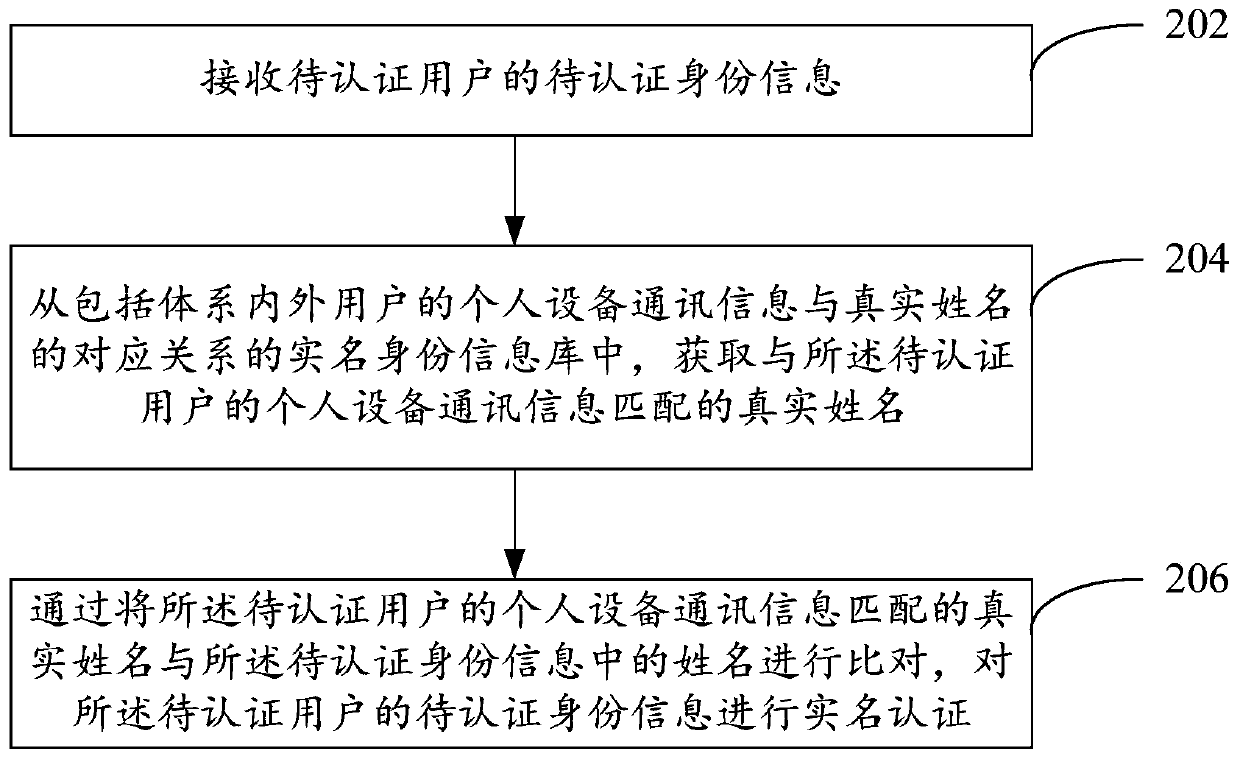
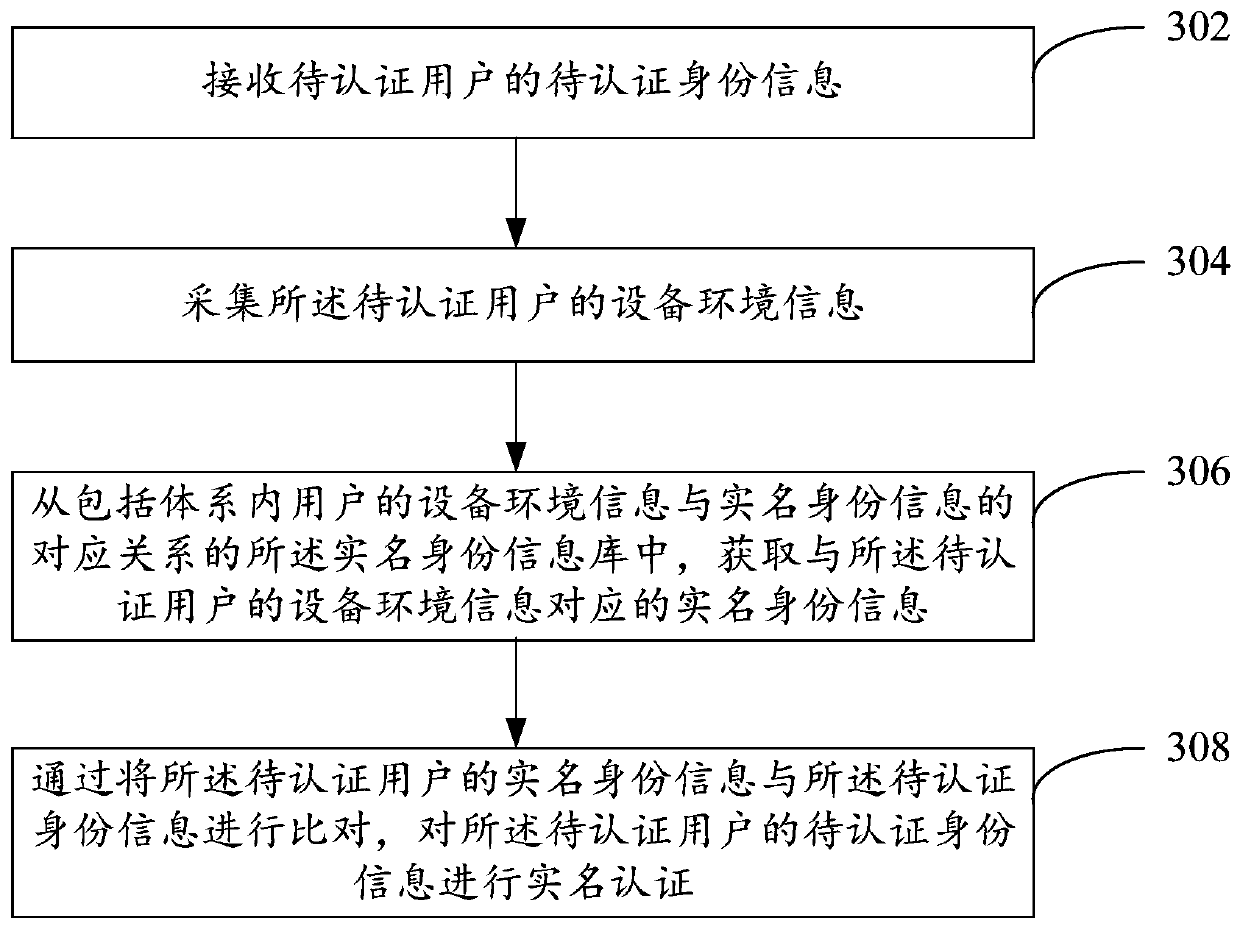
Embodiments of the invention provide a real-name authentication method and device. The real-name authentication method comprises the steps of receiving to-be-authenticated identity information of a to-be-authenticated user; obtaining the real-name identity information from a real-name identity information base; acquiring real-name identity information matched with the equipment information of theto-be-authenticated user, the real-name identity information library comprising a corresponding relationship between the equipment information of the users inside and outside the system and the real-name identity information, and the corresponding relationship being mined based on a relationship between real-name behavior data of the users inside and outside the system and the equipment information; and comparing the real-name identity information of the to-be-authenticated user with the to-be-authenticated identity information, and performing real-name authentication on the to-be-authenticated identity information of the to-be-authenticated user.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Identification method and system based on multiple biological features combined with device fingerprints
ActiveCN105279416BGuaranteed accuracyReal personDigital data authenticationIdentity recognitionAuthentication server
Owner:SHANGHAI CHUANZHI FINANCE INFORMATION SERVICE CO LTD
Real-name authentication method and device
ActiveCN110808978BReduce stepsImprove experienceData processing applicationsDigital data authenticationInformation repositoryInternet privacy
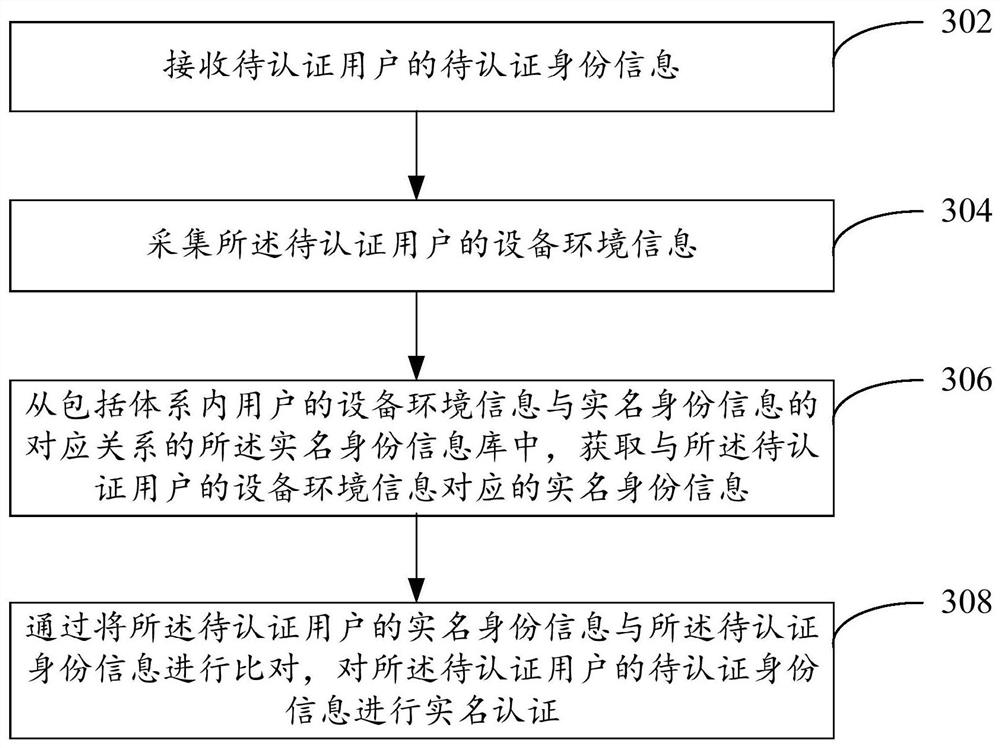
The embodiment of this specification provides a real-name authentication method and device, wherein the real-name authentication method includes: receiving the identity information to be authenticated of the user to be authenticated; obtaining the real-name identity matching the device information of the user to be authenticated from the real-name identity information database information, wherein the real-name identity information database includes the corresponding relationship between the equipment information of users inside and outside the system and the real-name identity information, and the corresponding relationship is mined based on the relationship between the real-name behavior data and equipment information of users inside and outside the system; through Comparing the real-name identity information of the user to be authenticated with the identity information to be authenticated, and performing real-name authentication on the identity information to be authenticated of the user to be authenticated.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Detection and maintenance evaluation system based on JSP development
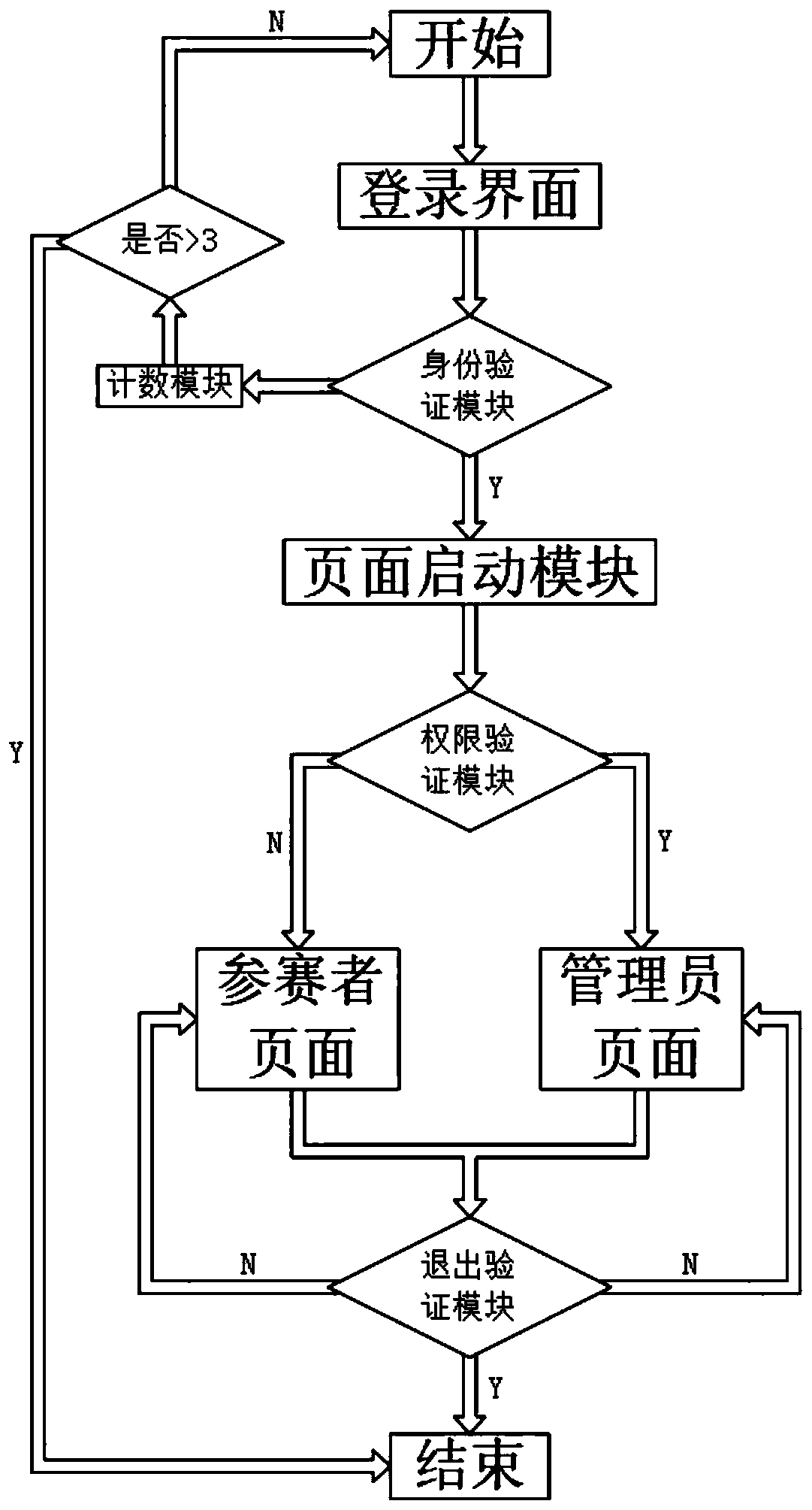
PendingCN111260247AReasonable allocation settingsVersatilityResourcesSoftware engineeringVerification
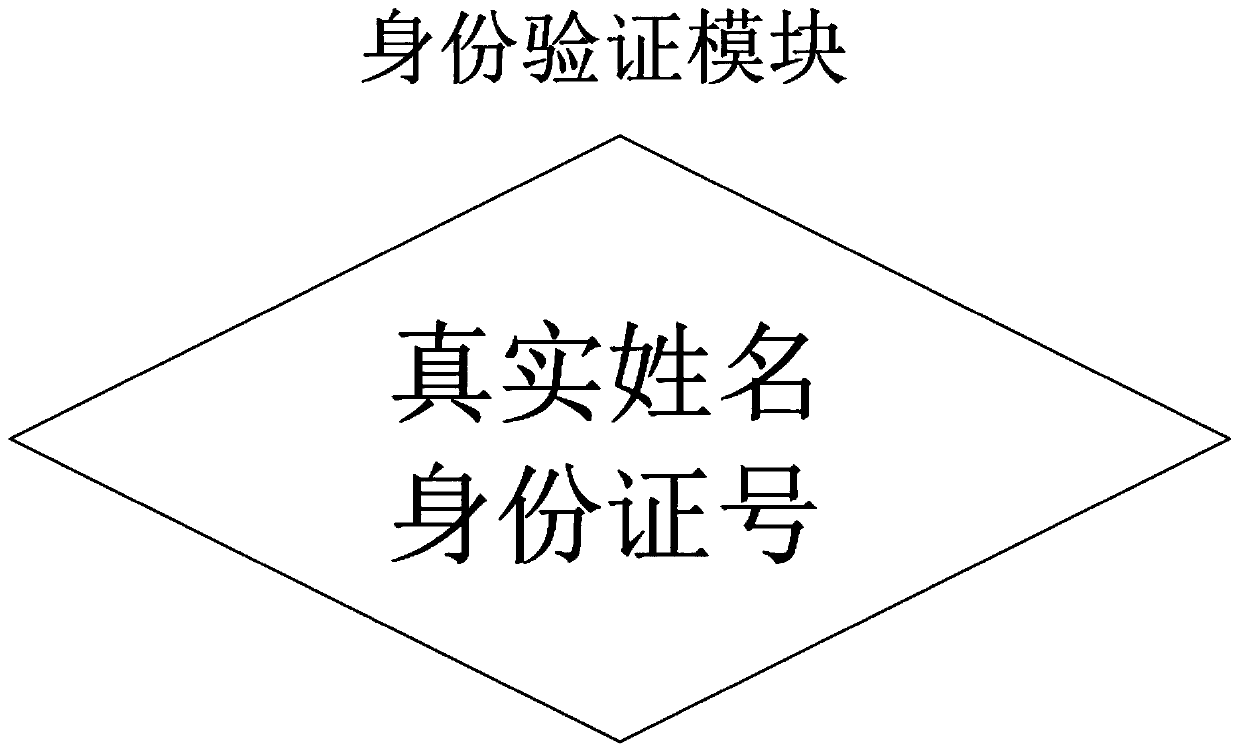
The invention discloses a detection and maintenance evaluation system based on JSP development, relates to the technical field of databases, and aims at solving the problems that an existing detectionand maintenance evaluation system does not have a set of relatively complete scoring system, the scoring standard difference between different devices is relatively large, and the universality is low. The starting output end is connected with the input end of the login interface; the input end of the login interface is connected with the input end of the identity verification module; the identityverification module is connected with the page starting module when verification succeeds; the identity verification module is connected with the counting module when verification fails; the output end of the page starting module is connected with the input end of the authority verification module; the authority verification module is connected with the administrator page when verification succeeds, the authority verification module is connected with the participant page when verification fails, the output end of the administrator page and the output end of the participant page are both connected with the exit verification module, and the exit verification module is connected with the end when confirmation succeeds.
Owner:南京米好信息安全有限公司
Public security management lock and system based on identity card unlocking and using method thereof
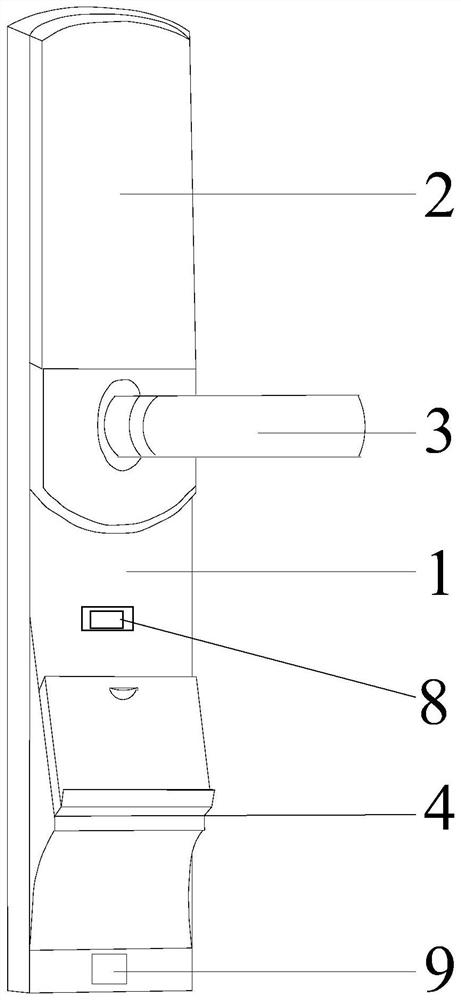
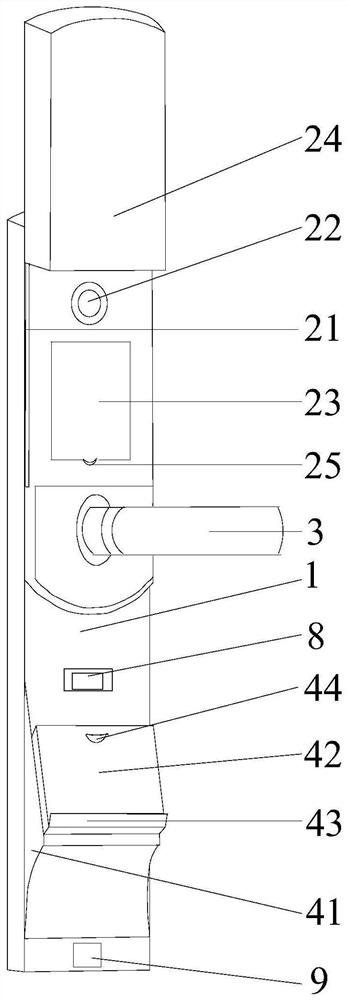
PendingCN111798596AEasy accessReduce safety incidentsNon-mechanical controlsElectric permutation locksComputer hardwareEmbedded system
The invention belongs to the technical field of intelligent door locks, and particularly relates to a public security management lock and system based on identity card unlocking and a using method thereof. The system comprises a lock shell, and an upper end unlocking area, a handle and a lower end unlocking area which are sequentially arranged on a front panel of the lock shell from top to bottom.The upper end unlocking area comprises a sliding groove formed in the front panel of the lock shell and a sliding cover arranged on the front panel of the lock shell and matching the sliding groove.The lower end unlocking area comprises a landslide protruding block arranged on the front panel of the lock shell and an identity card recognition area fixedly installed on the landslide protruding block, and a baffle is arranged below the identity card recognition area. A face recognition detector and an identity card recognition module are adopted to perform dual detection on a user, it is guaranteed that unlocking can be performed only after simultaneous detection of a person and an identity card is passed, and therefore it is guaranteed that unlocking can be performed only by a person whocan input unlocking information, and safety accidents are reduced. And a fingerprint identification module is further arranged, so that the user can enter a room under the condition that the identitycard is lost.
Owner:江苏先驰物联网技术有限公司
Mobile social platform interaction control method for LED landscape lighting system
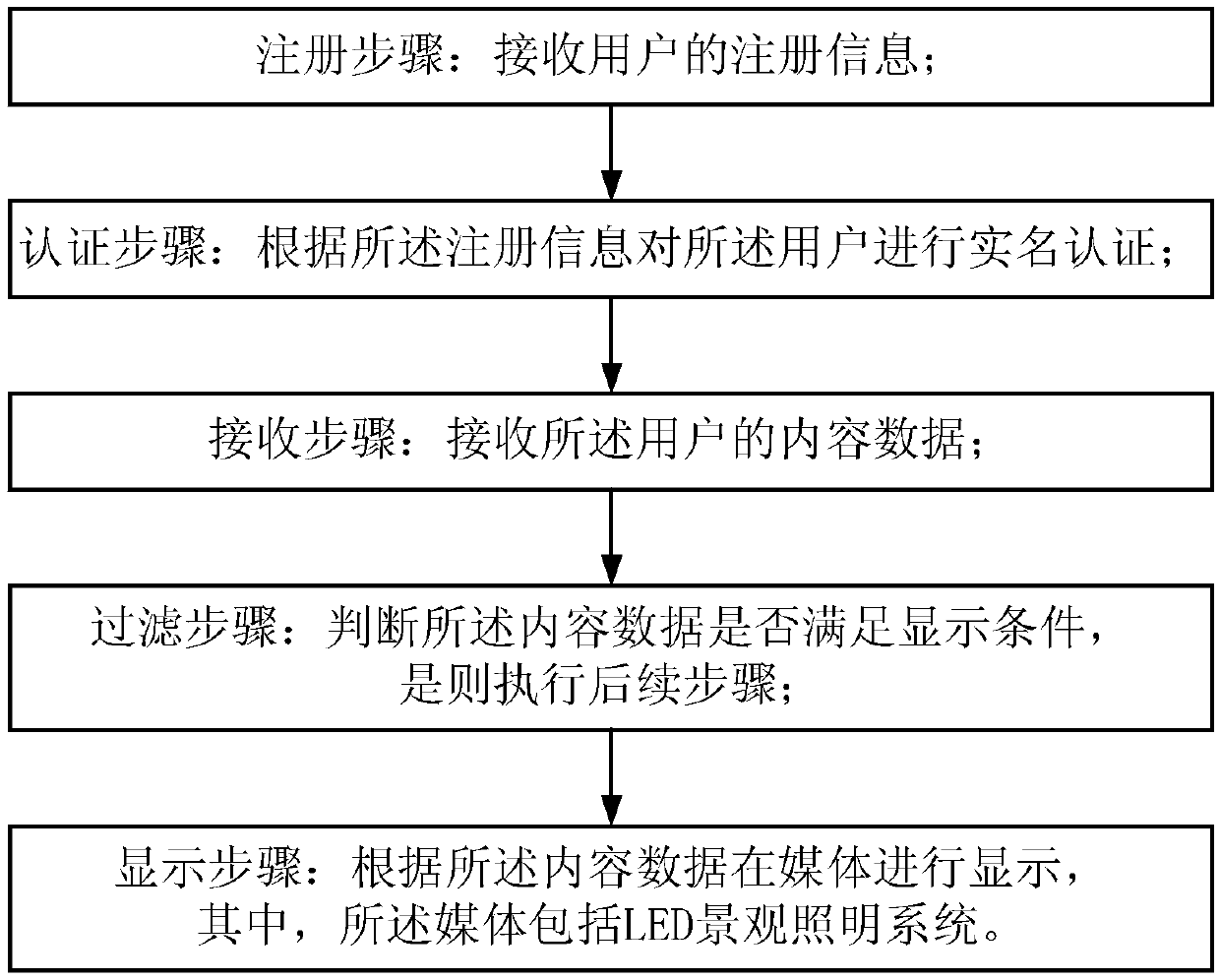
InactiveCN109561206ARealize real-name authenticationSimplify launch promotionSubstation equipmentTransmissionSocial platformLighting system
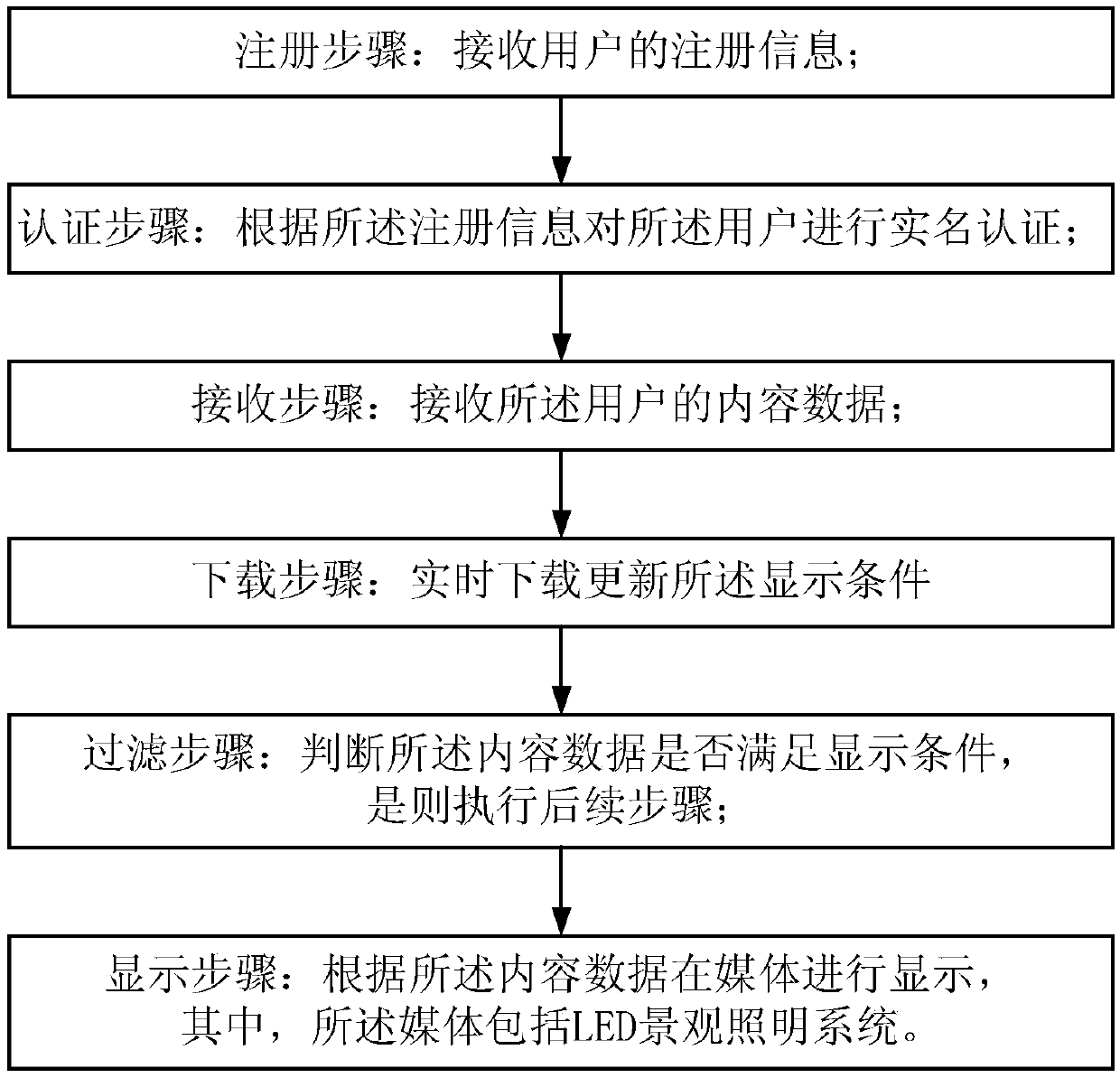
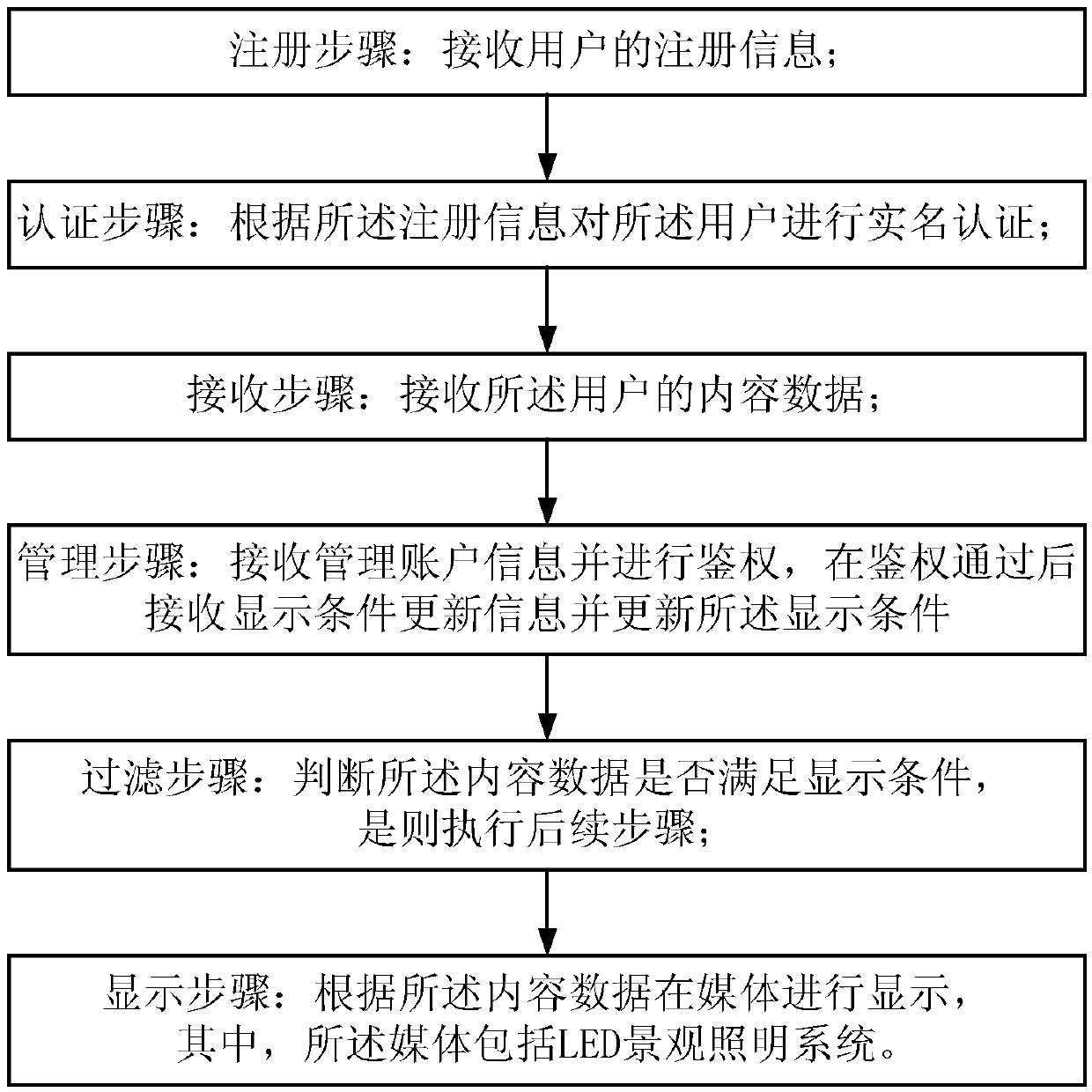
The invention discloses a mobile social platform interaction control method for an LED landscape lighting system. The mobile social platform interaction control method comprises the steps of: a registration step, which is implemented by receiving registration information of a user; an authentication step, which is implemented by performing real-name authentication on the user according to the registration information; a receiving step, which is implemented by receiving content data of the user; a filtering step, which is implemented by determining whether the content data satisfies a display condition and then executing a subsequent step if so; and a display step, which is implemented by displaying the data on a medium according to the content data, wherein the medium comprises the LED landscape lighting system. The mobile social platform interaction control method realizes the real-name authentication of the audiences and simplifies the release and promotion of the LED landscape lighting system, realizes a more convenient and safer public media interaction platform, can effectively control the displayed content interactively published to the outdoor medium, can better filter bad information, and can track a publisher according to the real-name information, thereby realizing more abundant content presentation and safer and more harmonious interaction control of the mobile social platform.
Owner:北京明瑞之光科技有限公司
Blockchain real-name authentication method and system
InactiveCN108880832BImprove reliabilityEasy to manageSpecial service provision for substationEngineeringVideo recording
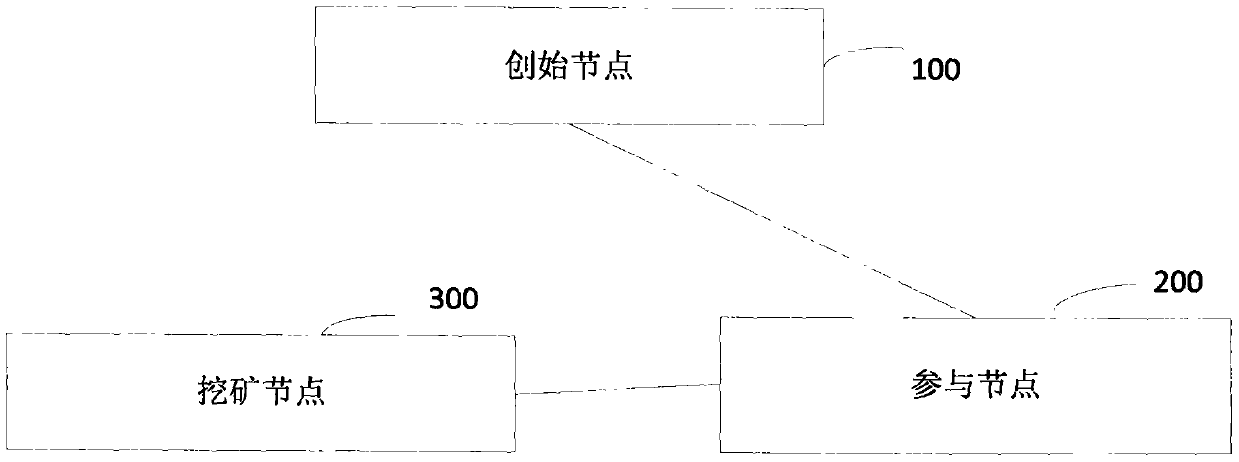
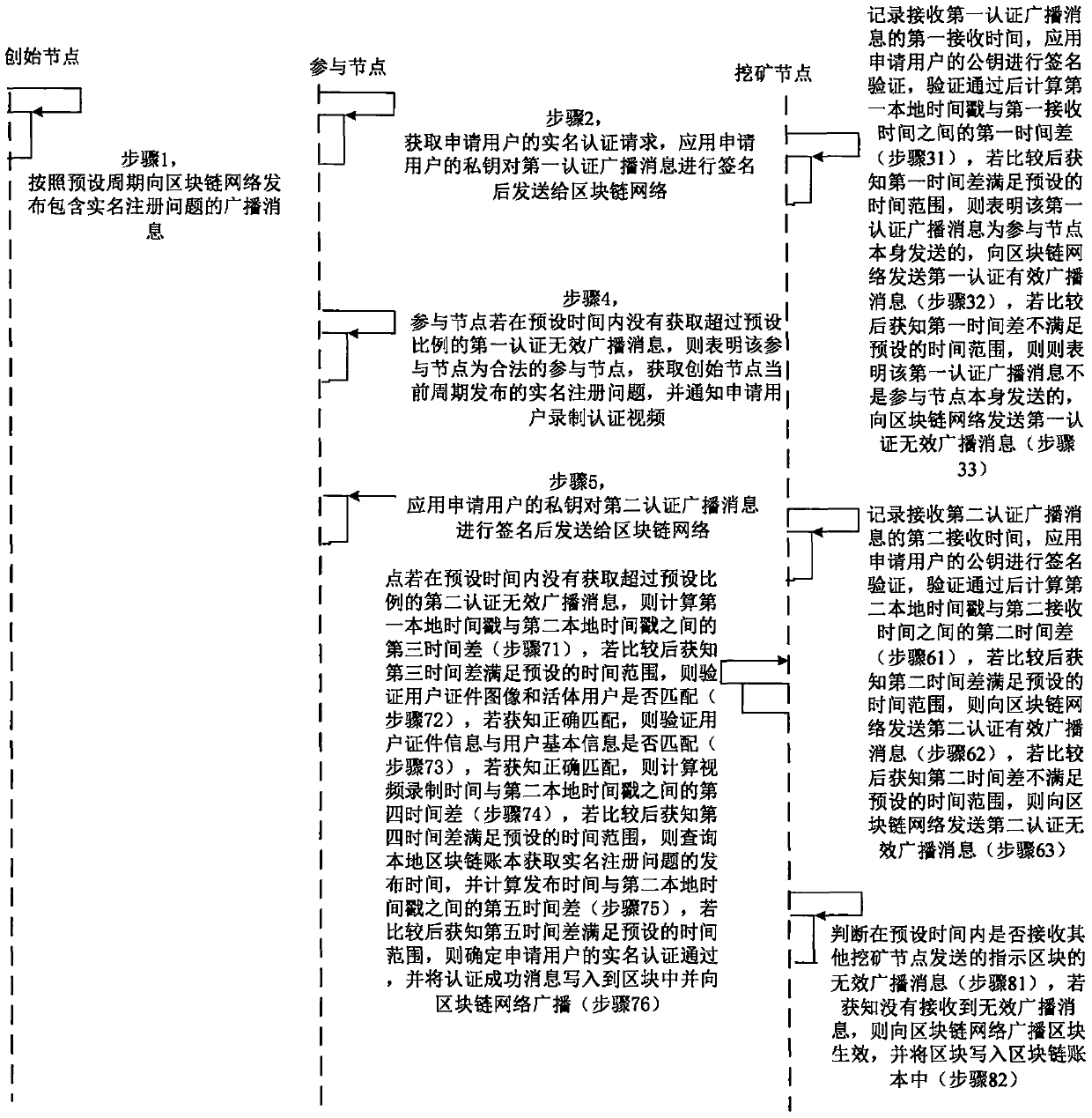
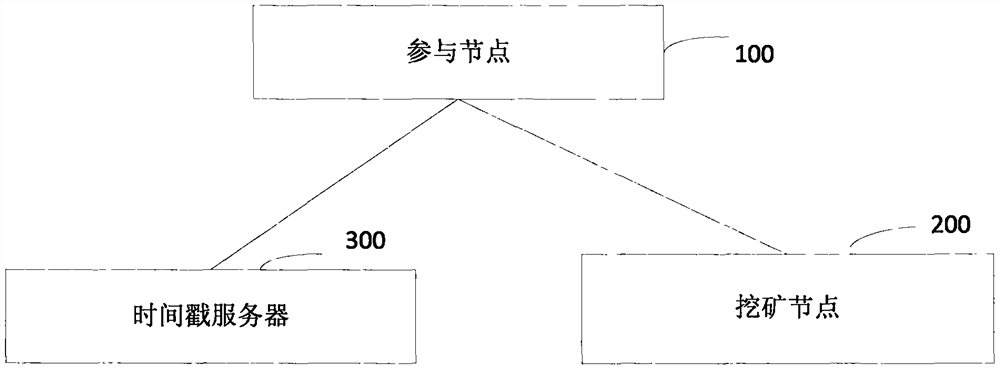
The invention provides a block chain real-name authentication method and system. The method comprises the following steps: publishing a broadcast message including a real-name registration problem toa block chain network by a founding node; acquiring a real-name authentication request by a participating node, signing the first authentication broadcast message, and then sending to the block chainnetwork; verifying whether a user certificate image is matched with a living user by a mining node, and verifying whether the user certificate information is matched with user basic information if theuser certificate image is matched with the living user; if the user certificate information is matched with user basic information, computing the time difference between the video recording time andthe receiving time, and determining a fact that the real-name authentication is passed if the time difference satisfies the preset time range; and writing the block into a block chain into an accountbook if an invalid broadcast message is unreceived. Therefore, the real-name authentication of the node in the block chain is realized, the node in the block chain network is corresponding to the realuser identity in the reality, the misjudgment on the time in the authentication process is avoided, and the reliability of the real-name authentication is improved.
Owner:全链通有限公司
Method and system for network identity certificate authentication of block chain
InactiveCN108876374BRealize real-name authenticationDigital data authenticationProtocol authorisationInternet privacyEngineering
The invention discloses a network identity document authentication method and a system of a block chain, wherein the method comprises the following steps of: a participating node broadcasts application user network identity document information and user identity document information; obtaining the network identity document information and the user identity document information after a initiating node performs identity authentication on the participating node, and initiating verification to a Ministry of Public Security node; feeding back to the initiating node after the Ministry of Public Security node verifies that the network identity document information is consistent with the user identity document information; feeding back to the participant node after the initiating node verifies theMinistry of Public Security node, so as to perform application user real-name authentication. Thus, real-name authentication of nodes in the block chain is realized, nodes in the block chain networkare corresponding to the network identity document information which responds real user identity in real life, nodes are easy to manage and legitimacy to maintenance the block chain is facilitated.
Owner:全链通有限公司
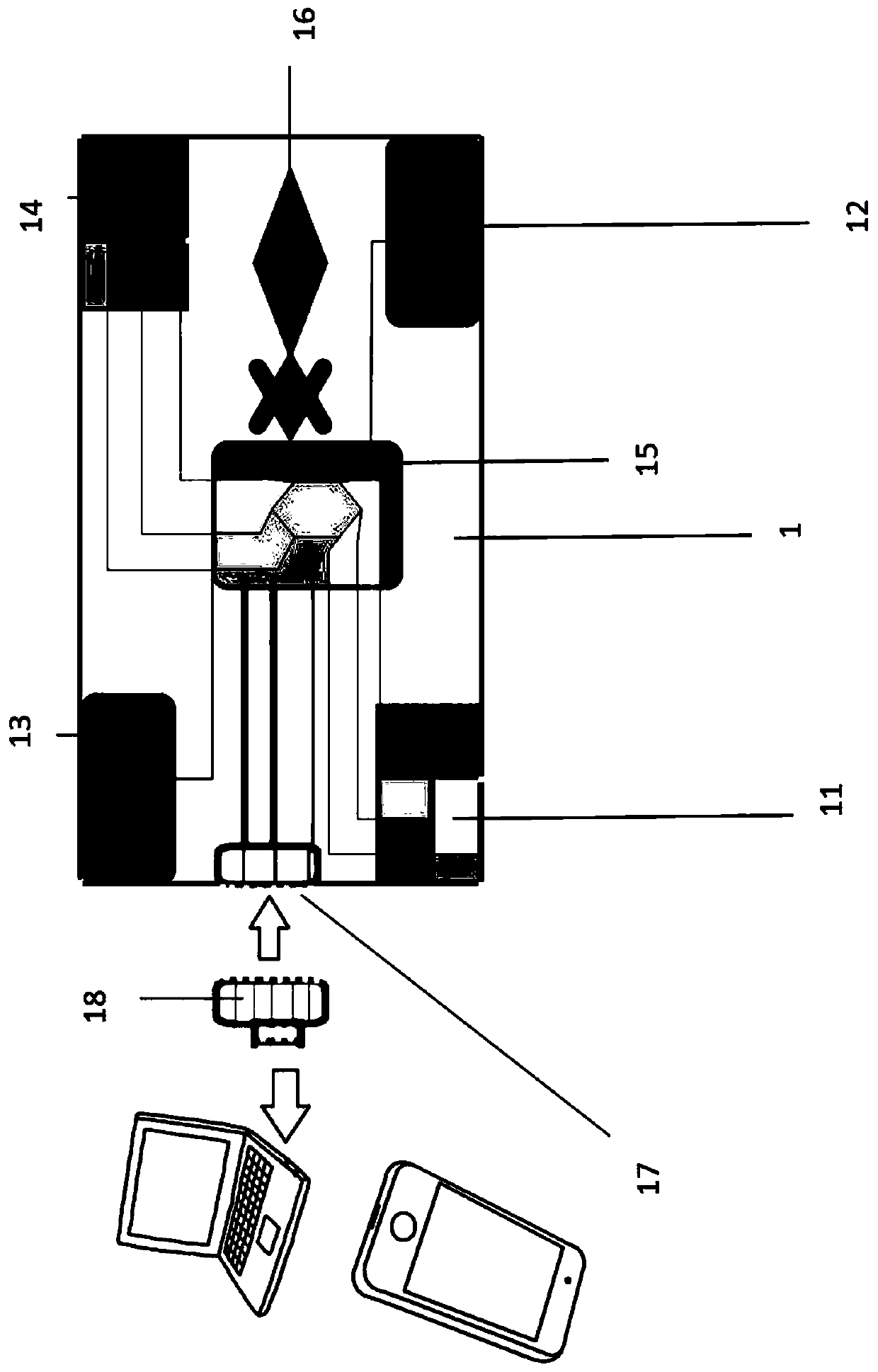
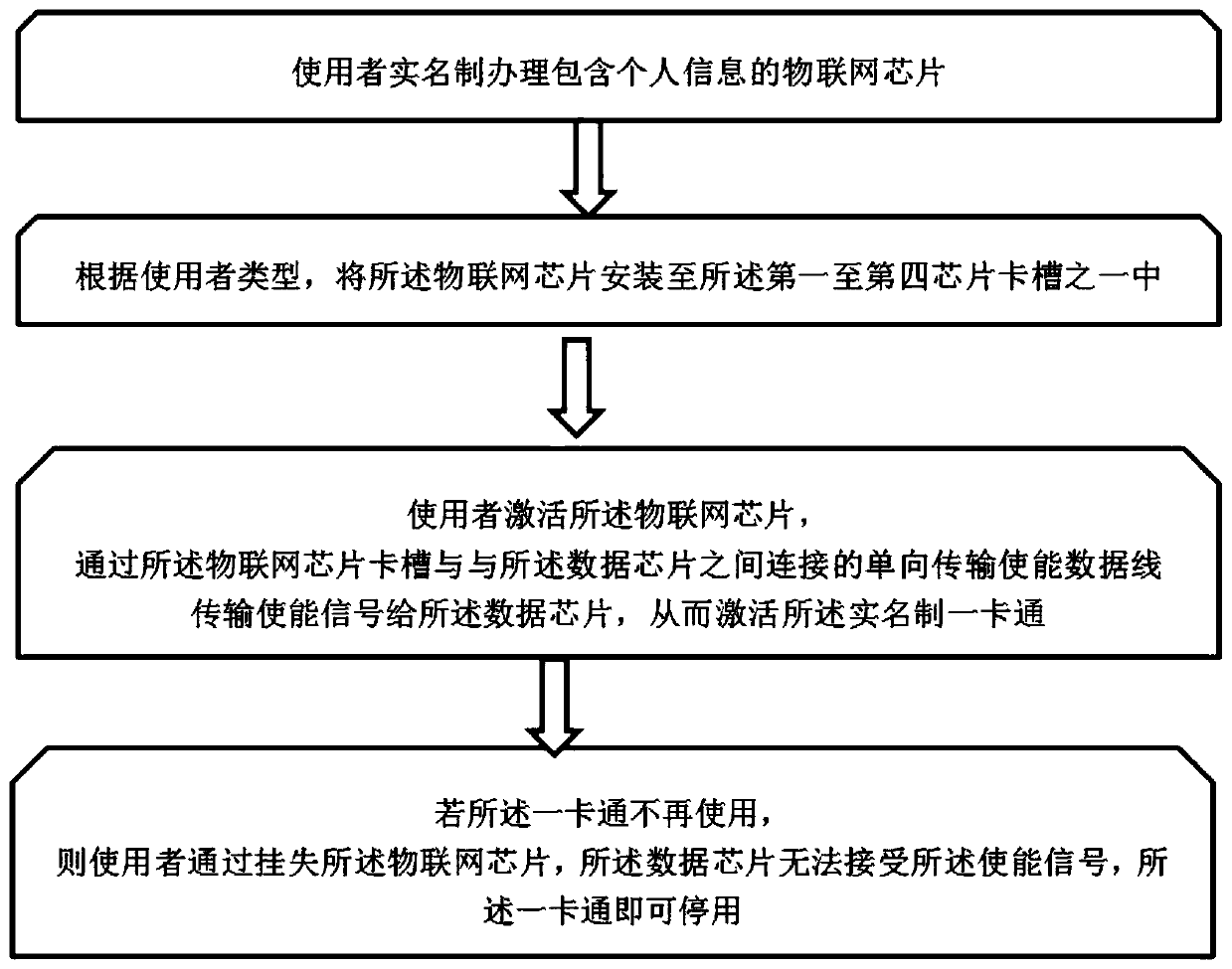
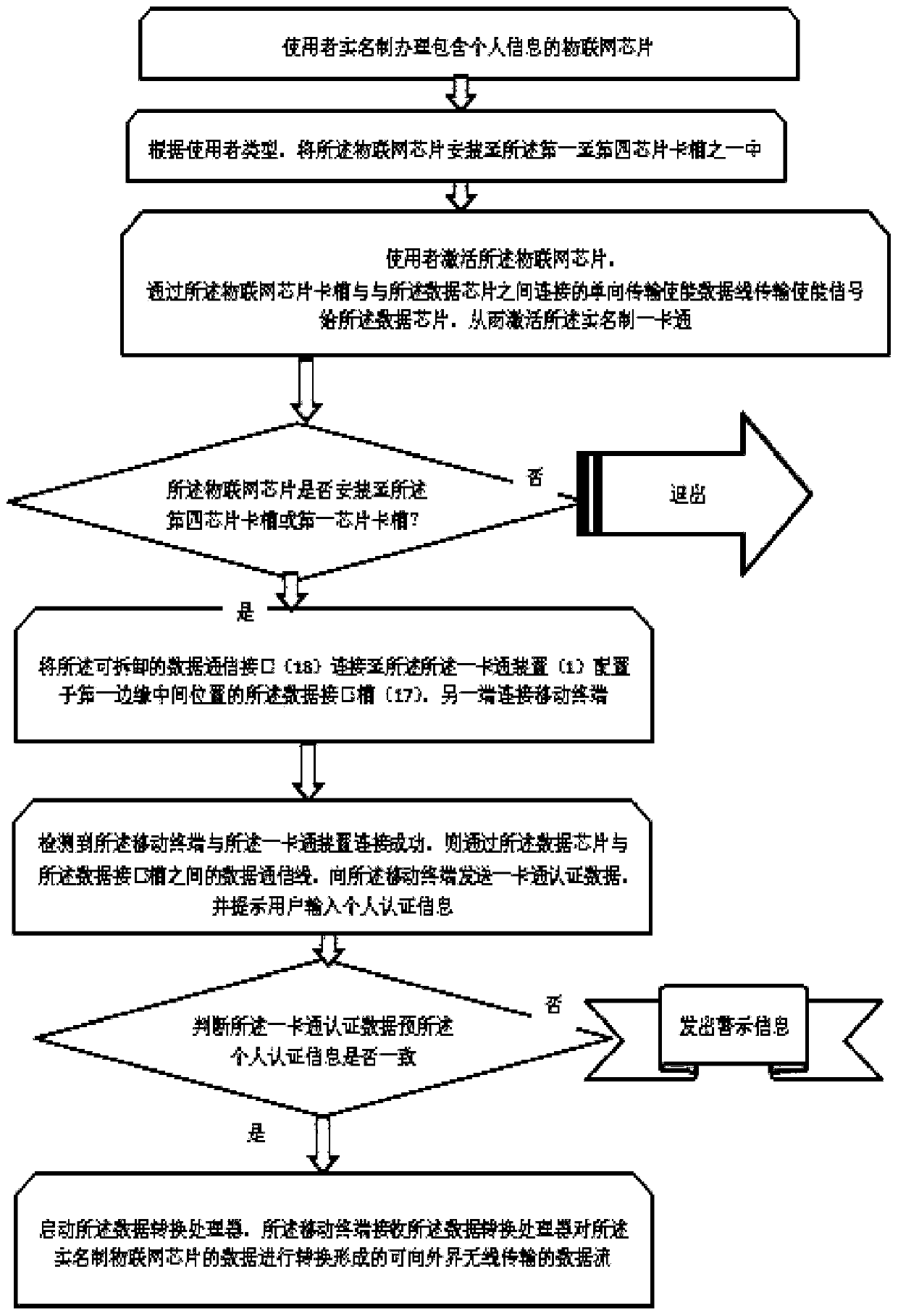
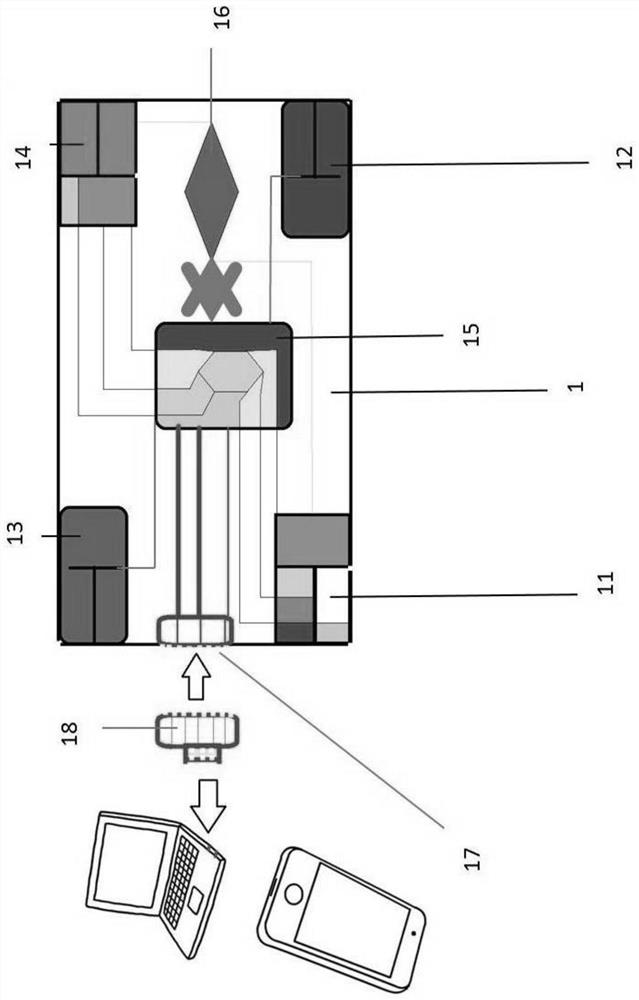
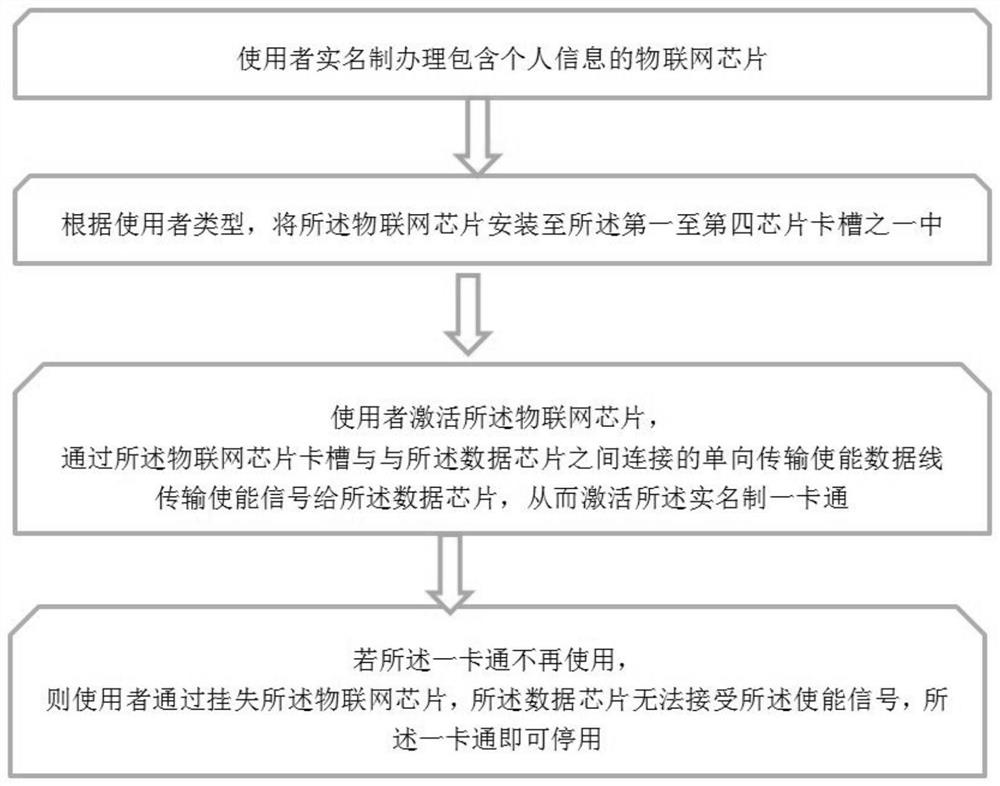
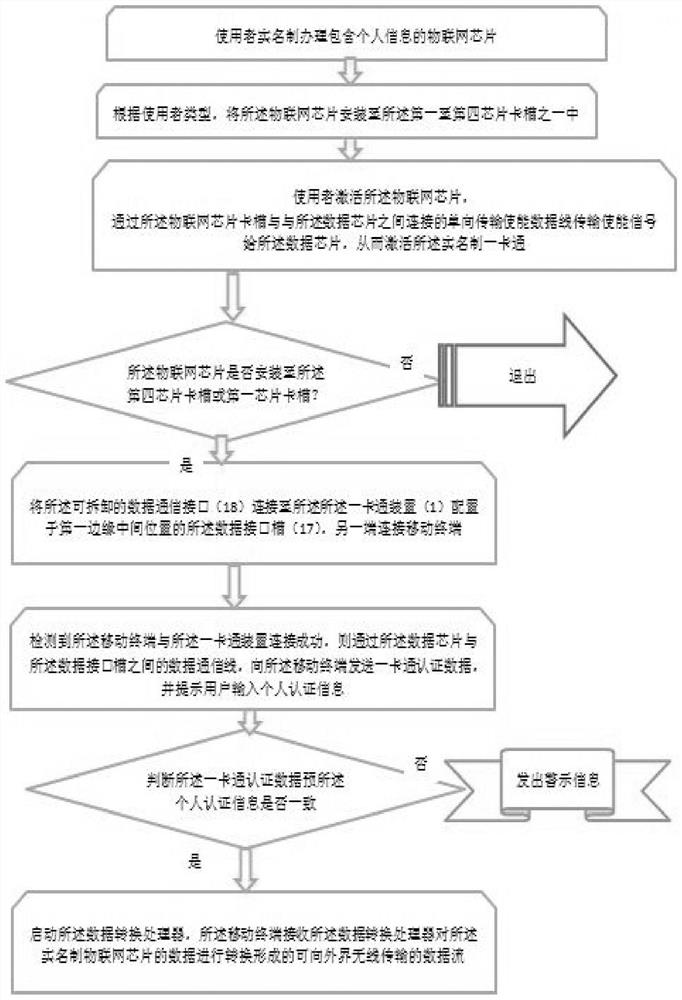
Real-name system all-in-one card suitable for different crowds
ActiveCN110782250ARealize real-name authenticationRealize customizationPayment architectureRecord carriers used with machinesData streamWireless transmission
According to the real-name system all-in-one card suitable for different crowds provided by the invention, a plurality of chip card slots are configured, and the card slots selected by the different crowds are different in configuration function, so that customization can be realized according to the function requirements of the different crowds; the card slots comprise a first chip card slot, a second chip card slot, a third chip card slot and a fourth chip card slot. When the Internet of Things chip is placed in the second chip card slot or the third chip card slot, the all-purpose card device achieves basic functions, and the all-purpose card device can be started or lost through the Internet of Things chip. When the Internet of Things chip is placed in the first chip card slot or the fourth chip card slot, the Internet of Things chip is inserted. The all-purpose card device not only realizes basic functions, but also can be connected with a mobile terminal through a data interfaceso as to read data, and can convert the data of the real-name system Internet of Things chip based on the data conversion processor to form a data stream capable of being wirelessly transmitted to theoutside, so that the data stream can be used by the mobile terminal.
Owner:CHINA UNIV OF GEOSCIENCES (BEIJING)
a method of information transmission
ActiveCN107294964BHigh encryption levelImprove the leakage levelKey distribution for secure communicationUser identity/authority verificationComputer hardwareGraphics
The embodiment of the present invention discloses an information transmission method, wherein the information transmission method is applied to a server, including: obtaining the sending information of the first terminal, encrypting the sending information, and generating an object code map, wherein the The sent information includes at least one of plaintext information, sensitive information, and secret information, and the object code map carries graphic encoding information and a digital signature of the graphic encoding information with the private key of the security code generation system, or the first Digitally signing the graphic encoding information with the terminal private key; returning the object code map to the first terminal, so that the first terminal sends the object code map to at least one corresponding second terminal. An information transmission method in an embodiment of the present invention realizes the improvement of security and privacy of information transmission.
Owner:BEIJING D9ING INST OF INFORMATION ENG CO LTD +1
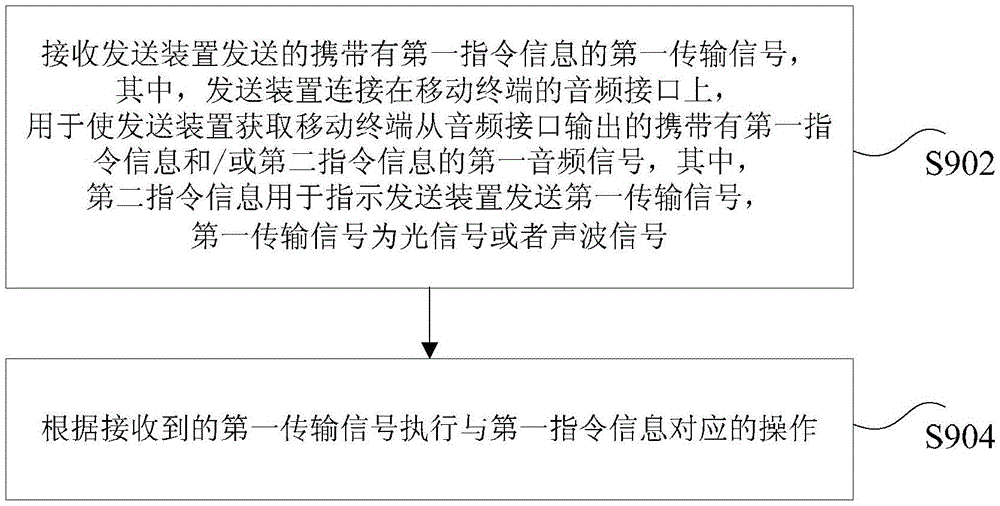
Method and device for sending and receiving instruction information
ActiveCN103810017BEnable two-way communicationRealize transmissionSoftware simulation/interpretation/emulationAcoustic waveOptical communication
The invention discloses a method and a device for sending and receiving command information. The method for sending the command information comprises the steps as follows: obtaining a first audio signal which carries first command information and / or second command information and is output by an audio interface of a mobile terminal, wherein the first command information is used for instructing a receiving device to execute an operation corresponding to the first command information, and the second command information is used for instructing sending of the first command information to the receiving device; according to the obtained first audio signal, generating a first transmission signal carrying the first command information and sending the first transmission signal to the receiving device, wherein the first transmission signal is an optical signal or an acoustic signal. According to the method and the device, the technical problem that existing optical communication methods are hard to be compatible with mobile terminals with different models is solved.
Owner:KUANG CHI INTELLIGENT PHOTONIC TECH
A method for generating admission tickets for public places
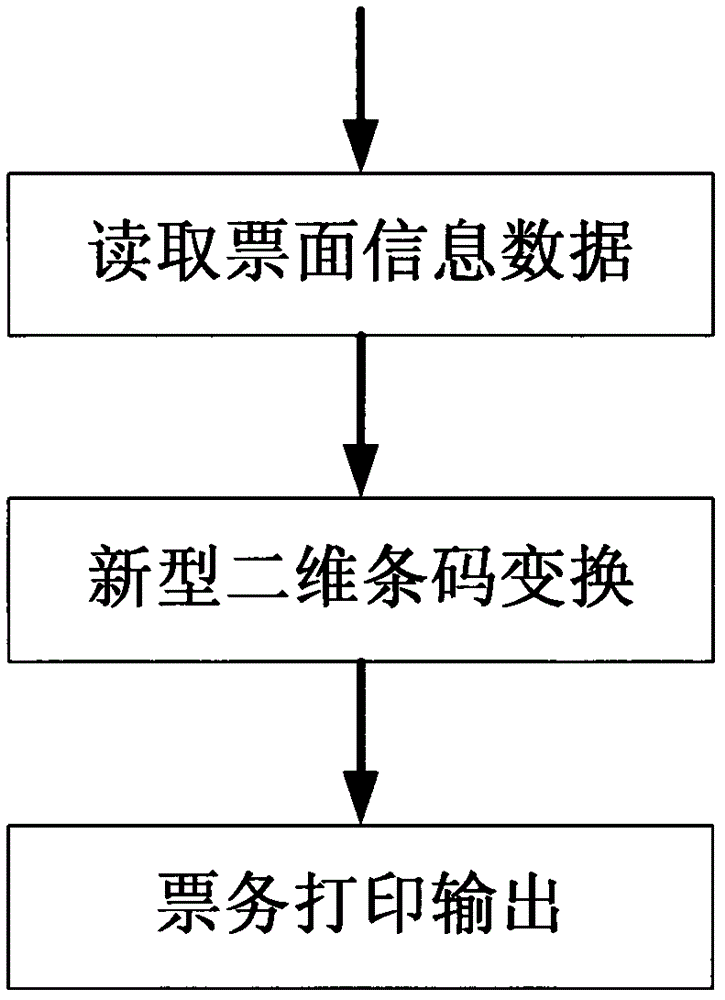
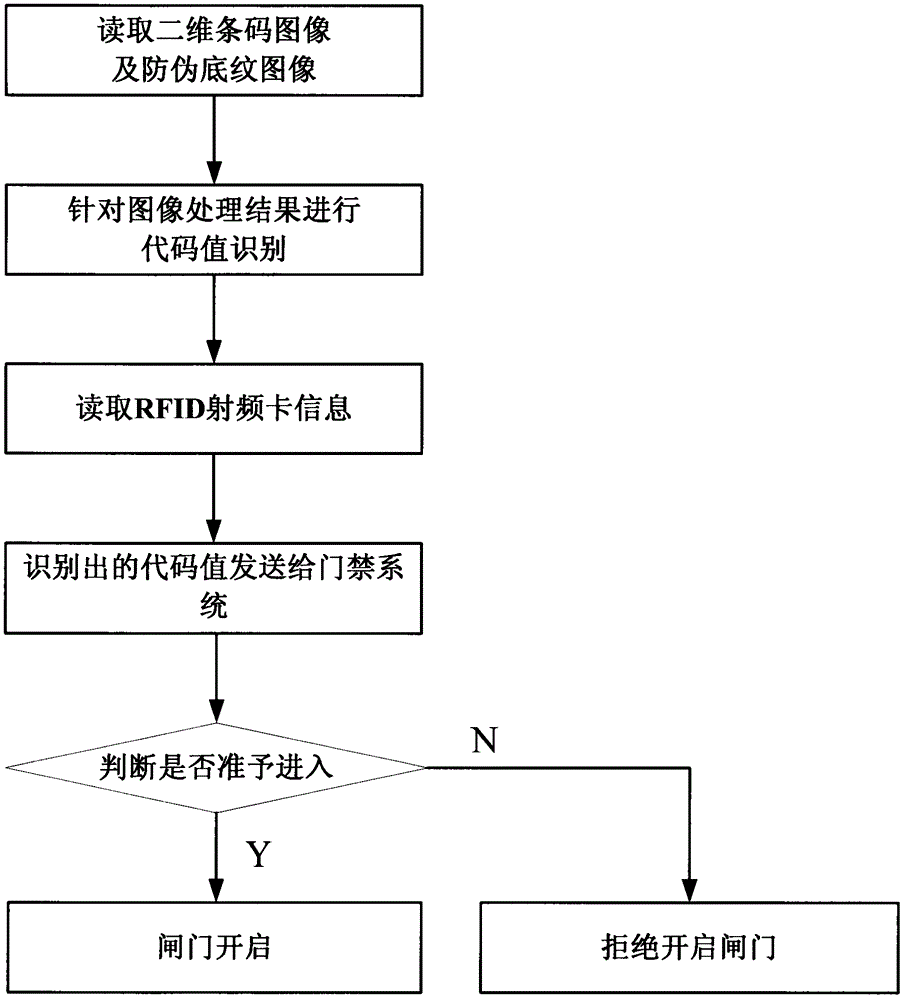
ActiveCN103035032BDoes not affect aestheticsWith decorative effectIndividual entry/exit registersRecord carriers used with machinesInformation processingPublic place
The invention relates to a method for generating an admission ticket for a public place in the field of information processing, and is characterized in that it proposes a method for printing an admission ticket using a low-precision printer, which can embed ticket face information on a paper-medium ticket , without destroying the beauty of the face, but also has a high degree of anti-counterfeiting features, can be directly used in the access control system of automatic gates, and can be identified by point-reading pens, and can also be used with RFID cards. The introduction of this technology can solve the problems of high cost of tickets using magnetic media, complex structure of automatic gates, and frequent maintenance. The problem of inspection plays a role in promoting the technological development of modern transportation and access control management of large public places.
Owner:天津市阿波罗信息技术有限公司
Blockchain real-name participation method and system
InactiveCN108876375BRealize real-name authenticationFacilitate legalitySecuring communicationProtocol authorisationInternet privacyEngineering
The present invention provides a blockchain real-name participation method and system, wherein the method includes: the participating nodes perform preliminary authentication according to the time difference between the authentication video recording time and the receiving time; after the preliminary authentication is passed, the mining node verifies the user certificate image Whether it matches with the live user, if it matches, verify whether the user certificate information matches the user's basic information, if it matches, calculate the time difference between the video recording time and the receiving time, if the time difference meets the preset time range, then determine the application user If the real-name authentication is passed, if no invalid broadcast message is received, the block will be written into the blockchain ledger. As a result, the real-name authentication of nodes in the blockchain is realized, and the nodes in the blockchain network are associated with real user identities in real life, which facilitates the management of nodes and maintains the legitimacy of the blockchain.
Owner:全链通有限公司
A real-name card for different groups of people
ActiveCN110782250BRealize real-name authenticationRealize customizationPayment architectureRecord carriers used with machinesWireless transmissionData stream
The real-name all-in-one card proposed by the present invention is suitable for different groups of people. By configuring multiple chip card slots, the functions of the card slots selected by different groups of people are different, and can be customized according to the functional requirements of different groups of people; the card slots include the first Chip card slot, second chip card slot, third chip card slot, fourth chip card slot. When the Internet of Things chip is placed in the second chip card slot or the third chip card slot, the one-card device realizes basic functions, and the enabling or reporting of the loss of the one-card device can be realized by the Internet of Things chip; when the Internet of Things chip is placed in the first When the chip card slot or the fourth chip card slot, in addition to realizing the basic functions, the all-in-one card device can also be connected with the mobile terminal through the data interface to read the data, and the real-name Internet of Things can be processed based on the data conversion processor. The data of the chip is converted to form a data stream that can be wirelessly transmitted to the outside world, so that it can be used by mobile terminals.
Owner:CHINA UNIV OF GEOSCIENCES (BEIJING)
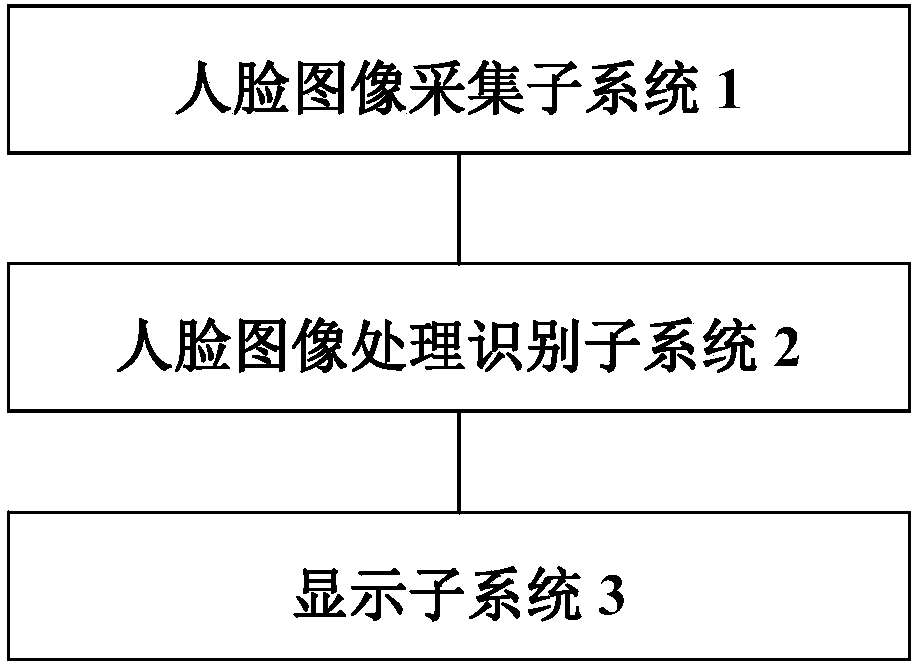
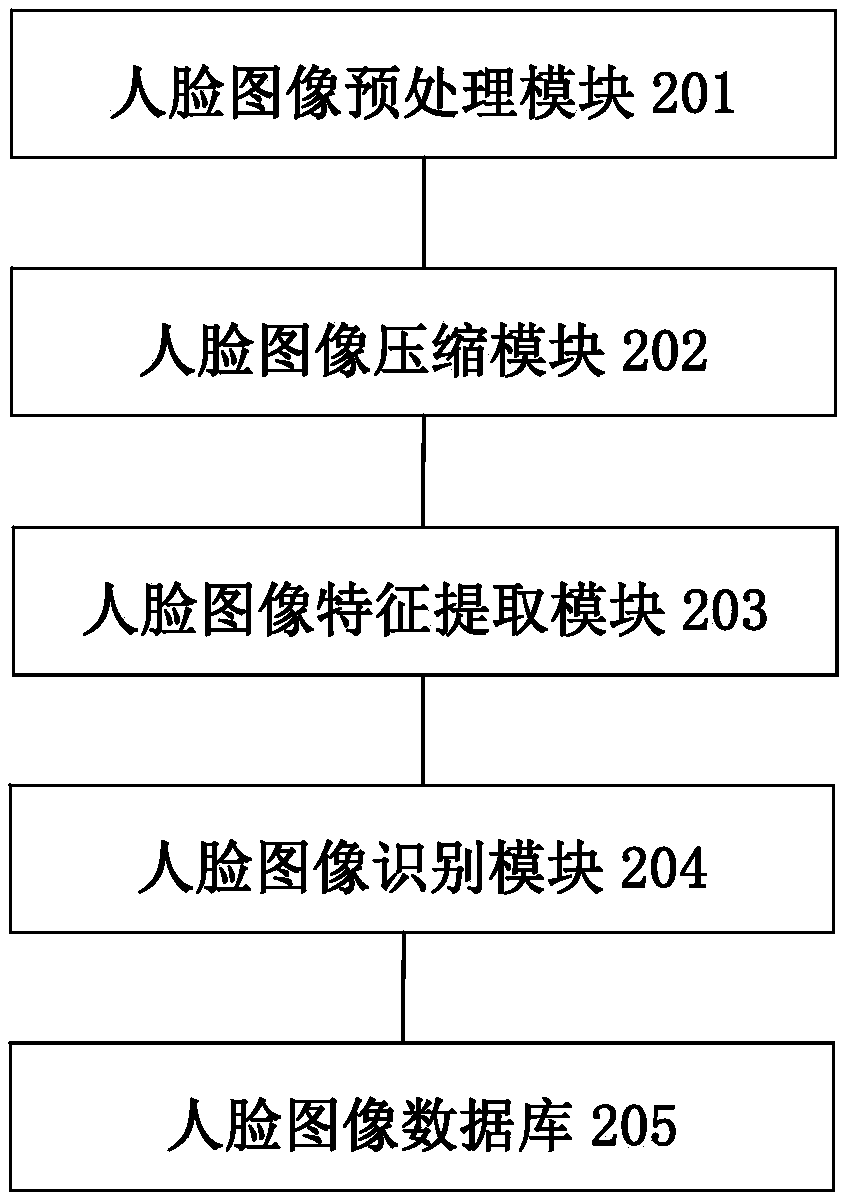
An Identity Recognition System Based on Face Image
ActiveCN107133590BAchieving Valid AuthenticationImprove securityCharacter and pattern recognitionDigital data authenticationImaging processingIdentity recognition
The invention provides an identity recognition system based on a face image, comprising a face image acquisition subsystem, a face image processing recognition subsystem, and a display subsystem connected in sequence; the image acquisition subsystem is used to collect and store the face image to be identified, The face image processing and recognition subsystem is used to recognize the collected and stored face images to be recognized, obtain the identity recognition result, and display the identity recognition result through the display subsystem. The beneficial effects of the present invention are: when the face image needs to be recognized, the face image to be recognized is collected and stored by the face image collection subsystem, and then the collected and stored face image to be recognized is processed and stored by the face image processing and recognition subsystem The face image is recognized to obtain the identification result, and the display subsystem displays the identification result, which can realize the effective authentication of the identity, so as to realize real-name authentication, network account security, account login convenience, and improve the security of identity authentication .
Owner:上海天使印记信息科技有限公司
Blockchain real-name participation method and system
InactiveCN108881253BGuaranteed accuracyGuaranteed reliabilityEncryption apparatus with shift registers/memoriesUser identity/authority verificationEngineeringVideo recording
The invention provides a block chain real-time participating method and system. The method comprises the following steps: performing initial authentication according to an authentication video by a participating node; verifying whether a user certificate image is matched with a living user by a mining node after the initial authentication is passed, and verifying whether the user certificate information is matched with user basic information if the user certificate image is matched with the living user, wherein the user certificate image and the user certificate information are acquired and authenticated by the public security Bureau; if the user certificate information is matched with user basic information, computing the time difference between the video recording time and the receivingtime, and determining a fact that the real-name authentication of the application user is passed if the time difference satisfies the preset time range; and writing the block into a block chain into an account book if an invalid broadcast message is unreceived. Therefore, the real-name authentication of the node in the block chain is realized based on the user related information provided by the public security bureau, the accuracy of the real-time authentication is guaranteed; the node in the block chain network is corresponding to the real user identity in the reality, thereby facilitating the node management and block chain legality maintenance.
Owner:全链通有限公司
Mobile communication electronic sim card data processing method and device
ActiveCN108200568BRealize real-name authenticationImplement identity authenticationNetwork data managementEngineeringUser identifier
The embodiment of the invention provides a data processing method and apparatus of a mobile communication electronic SIM card. The method comprises the following steps: sending, by an Internet server,accepted subscription information to a service platform; receiving an activation code, an account pointer and a confirmation code sent by the service platform; establishing a corresponding relationship between a user identifier, the account pointer and a token; and sending the activation code and the confirmation code to an APP of a user terminal. In the embodiment of the invention, the acceptedsubscription information is sent to the service platform by the Internet server, the activation code, the account pointer and the confirmation code sent by the service platform are received, the corresponding relationship between the user identifier, the account pointer and the token is established, and the activation code and the confirmation code are sent to the APP of the user terminal, so thatthe APP downloads the electronic card according to the activation code, and real name authentication and user identity authentication in mobile communication are achieved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
A wireless router access control method
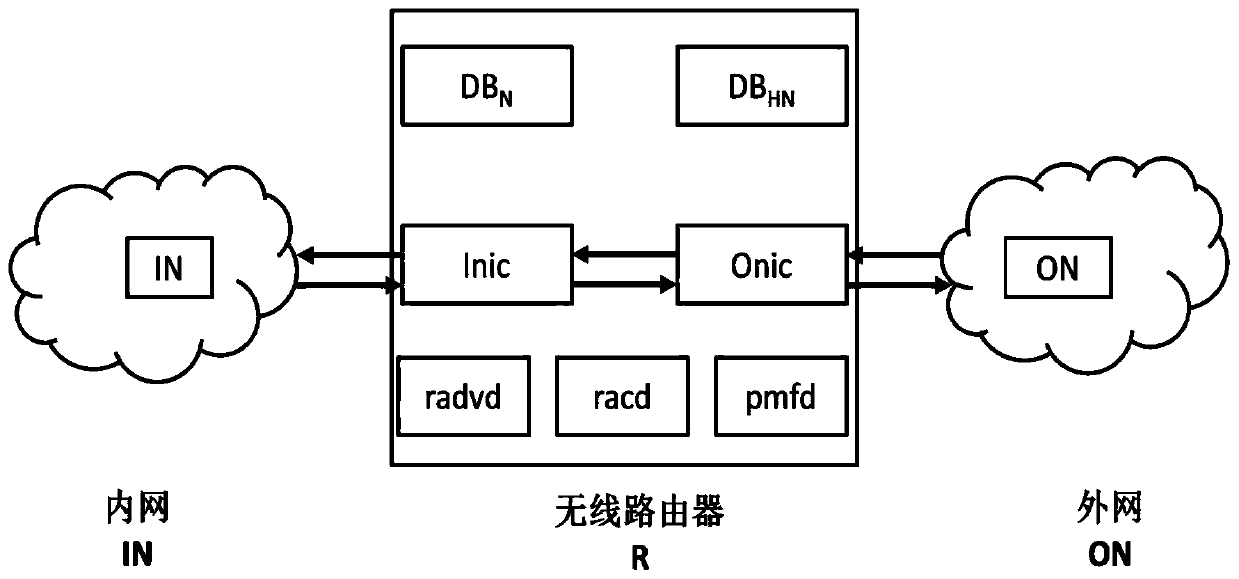
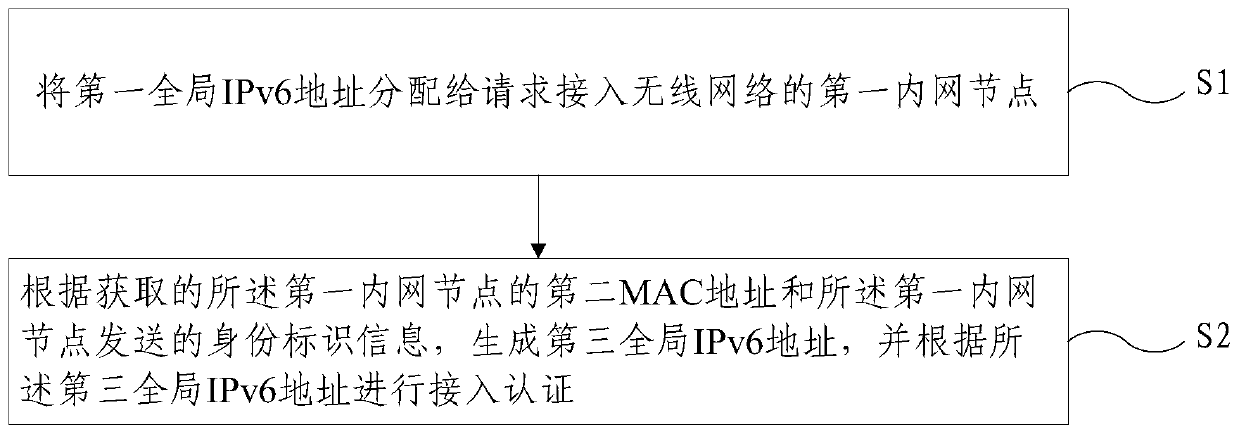
ActiveCN107707685BRealize real-name authenticationAvoid safety hazardsTransmissionWireless routerCommunications security
The present invention provides a wireless router access control method, comprising: S1, assigning the first global IPv6 address to the first intranet node requesting to access the wireless network; S2, according to the acquired second MAC address of the first intranet node and the identity information sent by the first intranet node to generate a third global IPv6 address, and perform access authentication according to the third global IPv6 address and the first global IPv6 address. The access control method of a wireless router provided by the present invention performs access control through the global IPv6 address generated based on the identity information of the node and the MAC address, realizes the real-name authentication of the node identity, and effectively prevents potential safety hazards in the IPv6 network. Improved security for IPv6-based wireless router communications.
Owner:TSINGHUA UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com