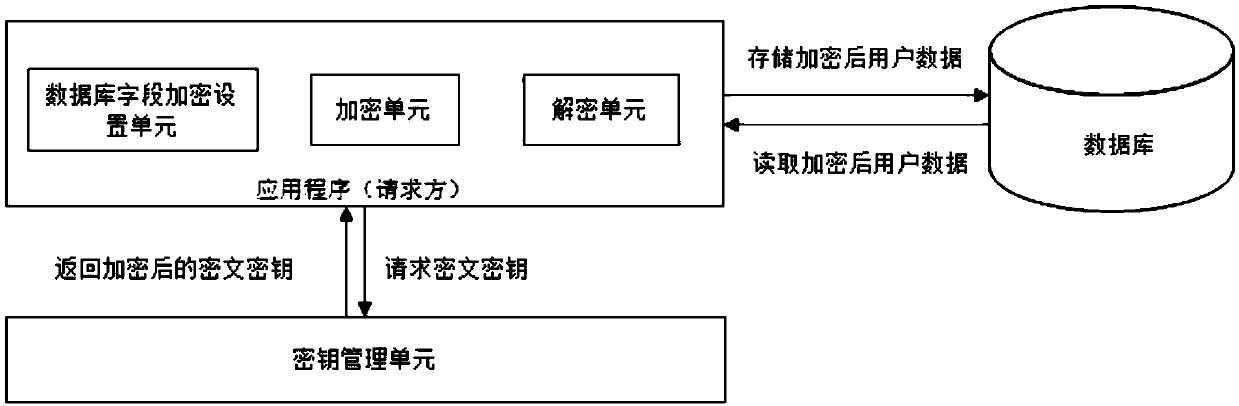
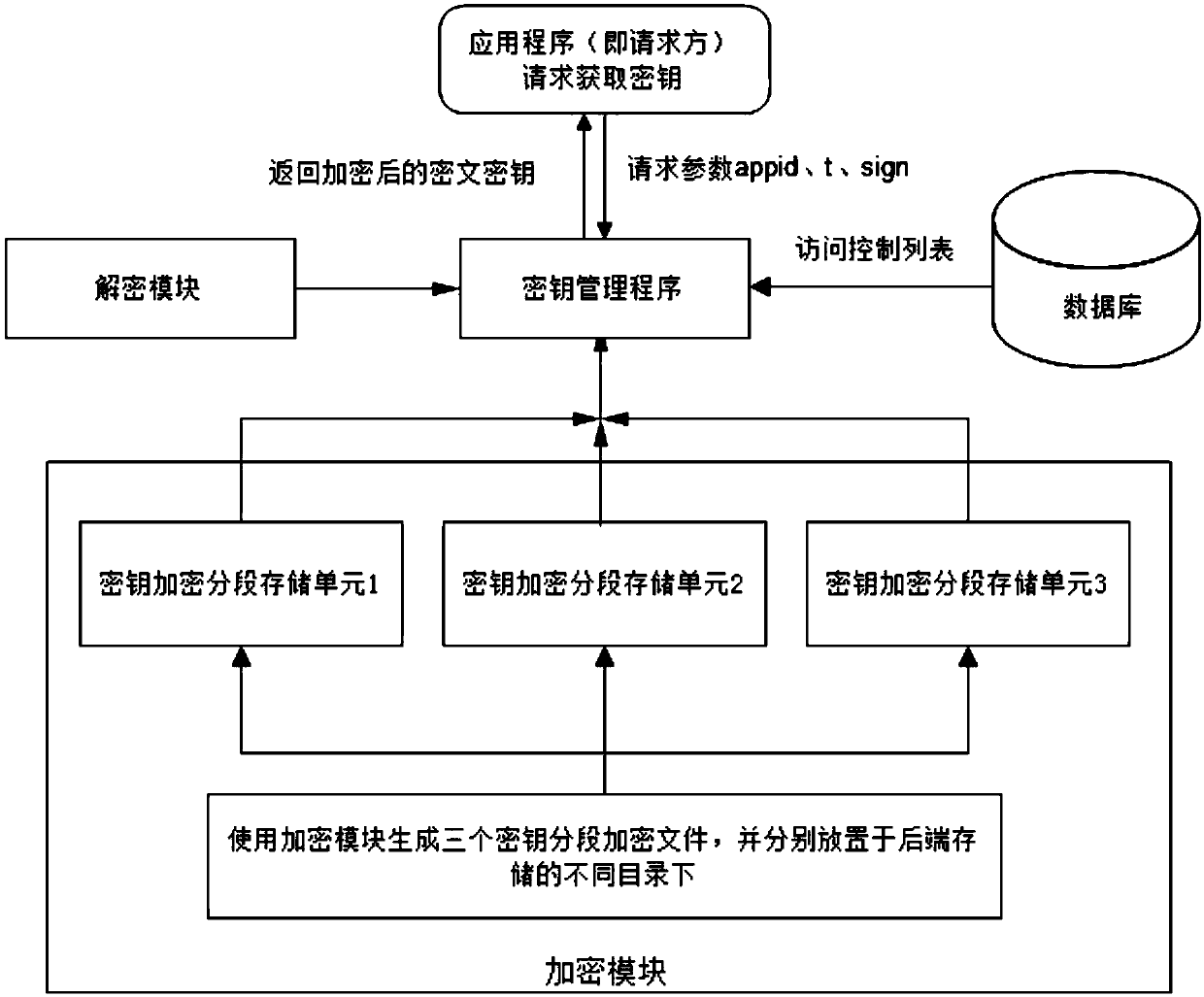
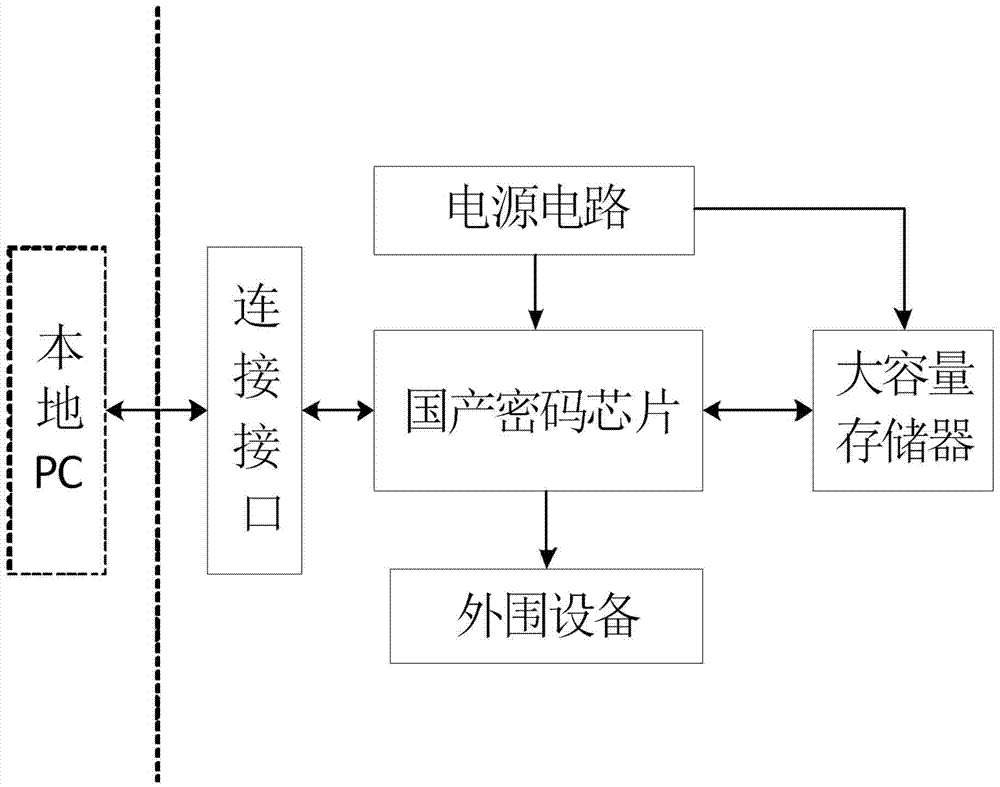
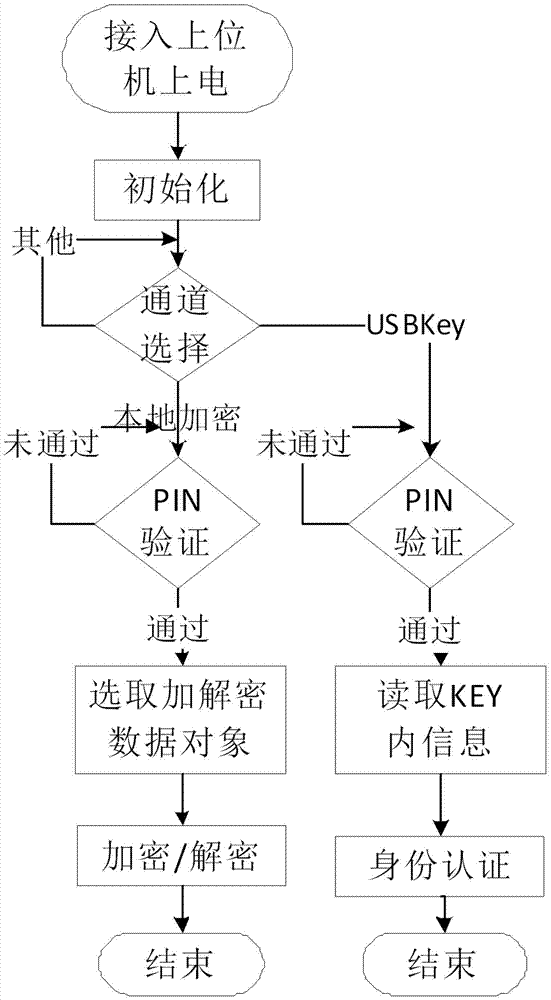
Patents
Literature
37results about How to "High encryption level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
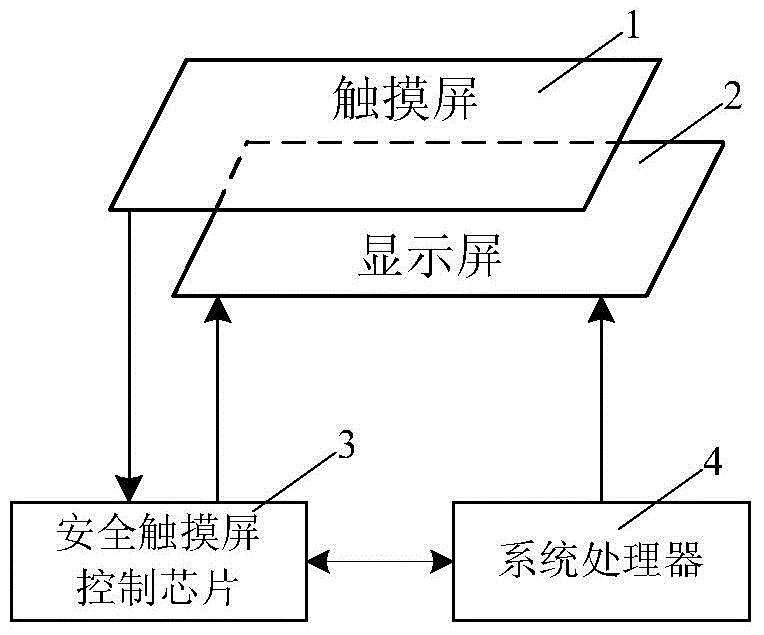
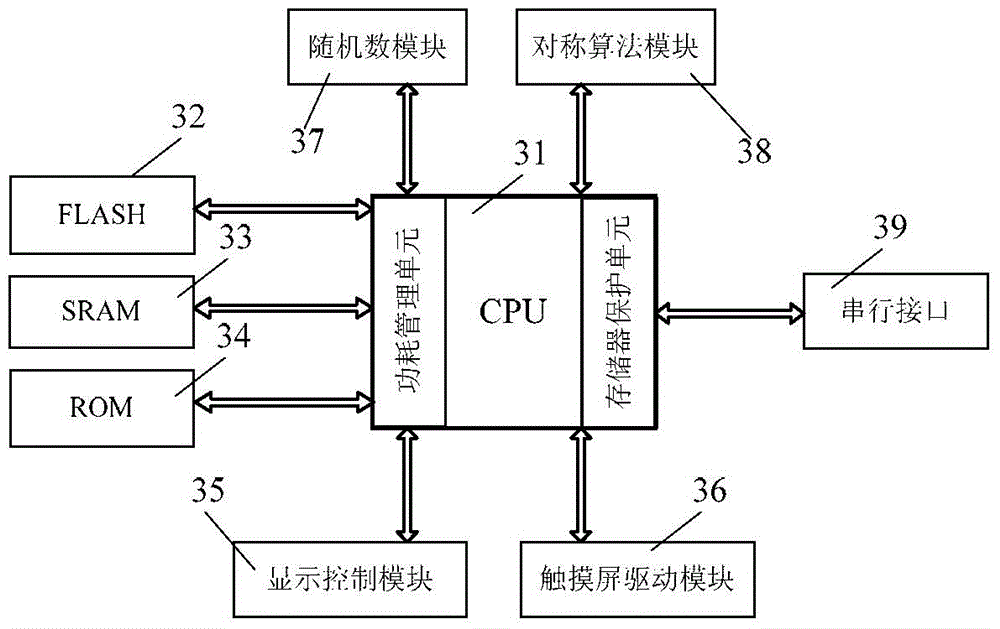
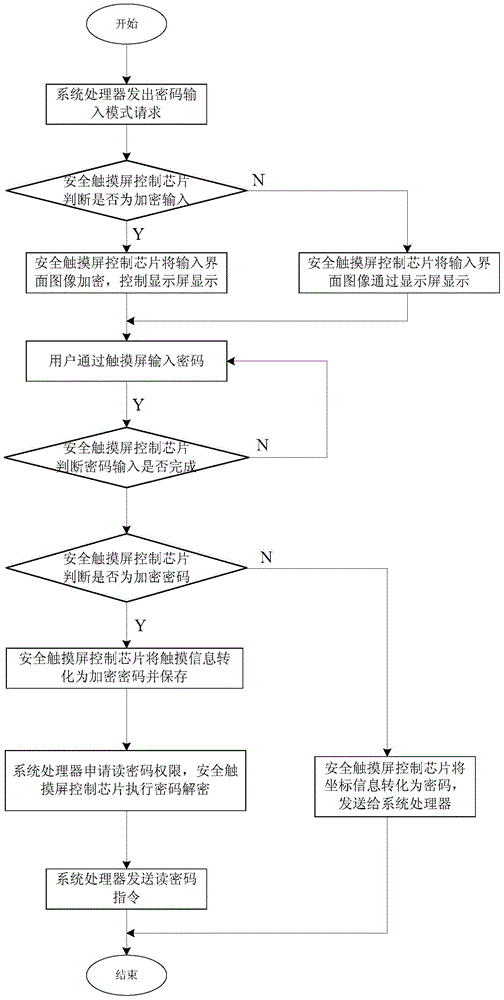
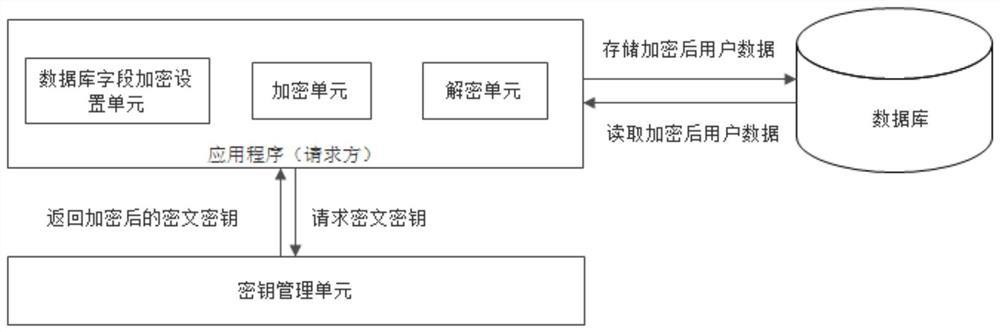
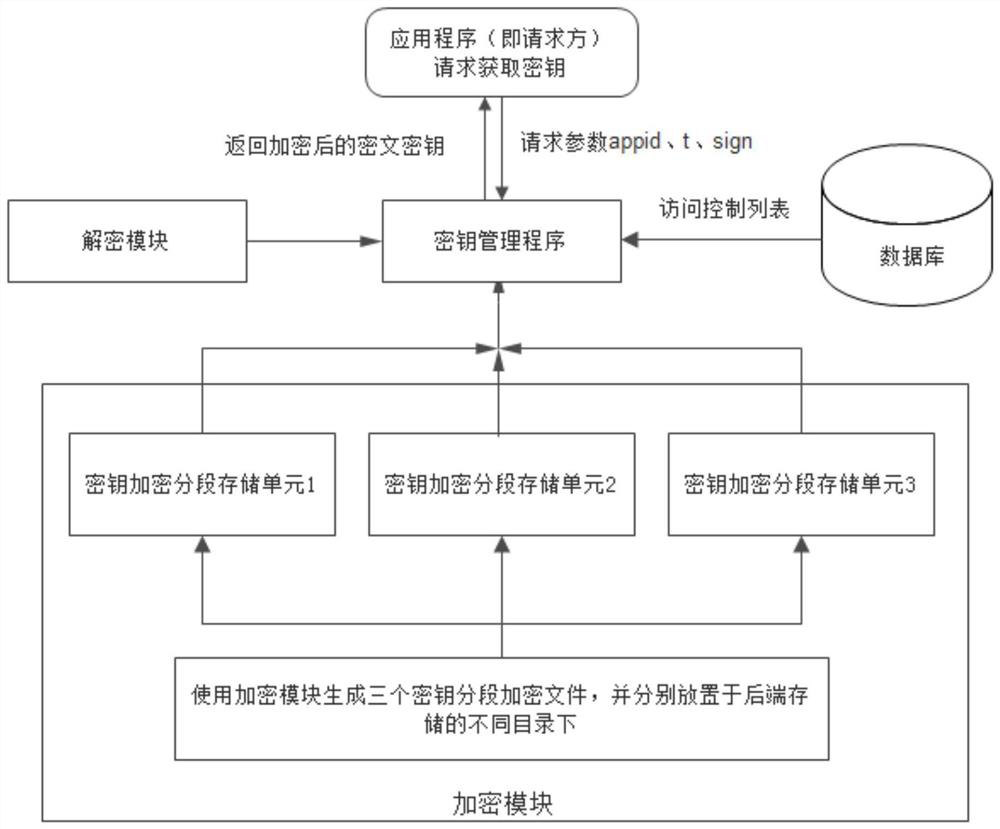
Security password input system and method based on security touch screen control chip
ActiveCN104156642AEasy to integratePrevent peepingDigital data authenticationInput/output processes for data processingStatic random-access memoryPassword
A security password input system based on a security touch screen control chip comprises a touch screen, a display screen, the security touch screen control chip and a system processor. The security touch screen control chip comprises a central processing unit. A FLASH memory, an SRAM (static random access memory), a display control module, a touch screen drive module, a random number module, a symmetric algorithm application module and a serial interface are connected to the central processing unit. The security touch screen control chip is used for encrypting an image of a password input interface, transmitting the image to the display screen for displaying, and encrypting and storing touch information generated by the touch screen; when the system processor sends out a command to read a password, the password is automatically decrypted and transmitted; the image of the password input interface is encrypted and decrypted both in the security touch screen control chip; the system processor is unable to acquire an encryption method of a password key pad, so that system Trojan programs still are unable to analyze the password through image recognition even after capturing the image of the password input interface.
Owner:HANGZHOU SYNOCHIP DATA SECURITY TECH CO LTD
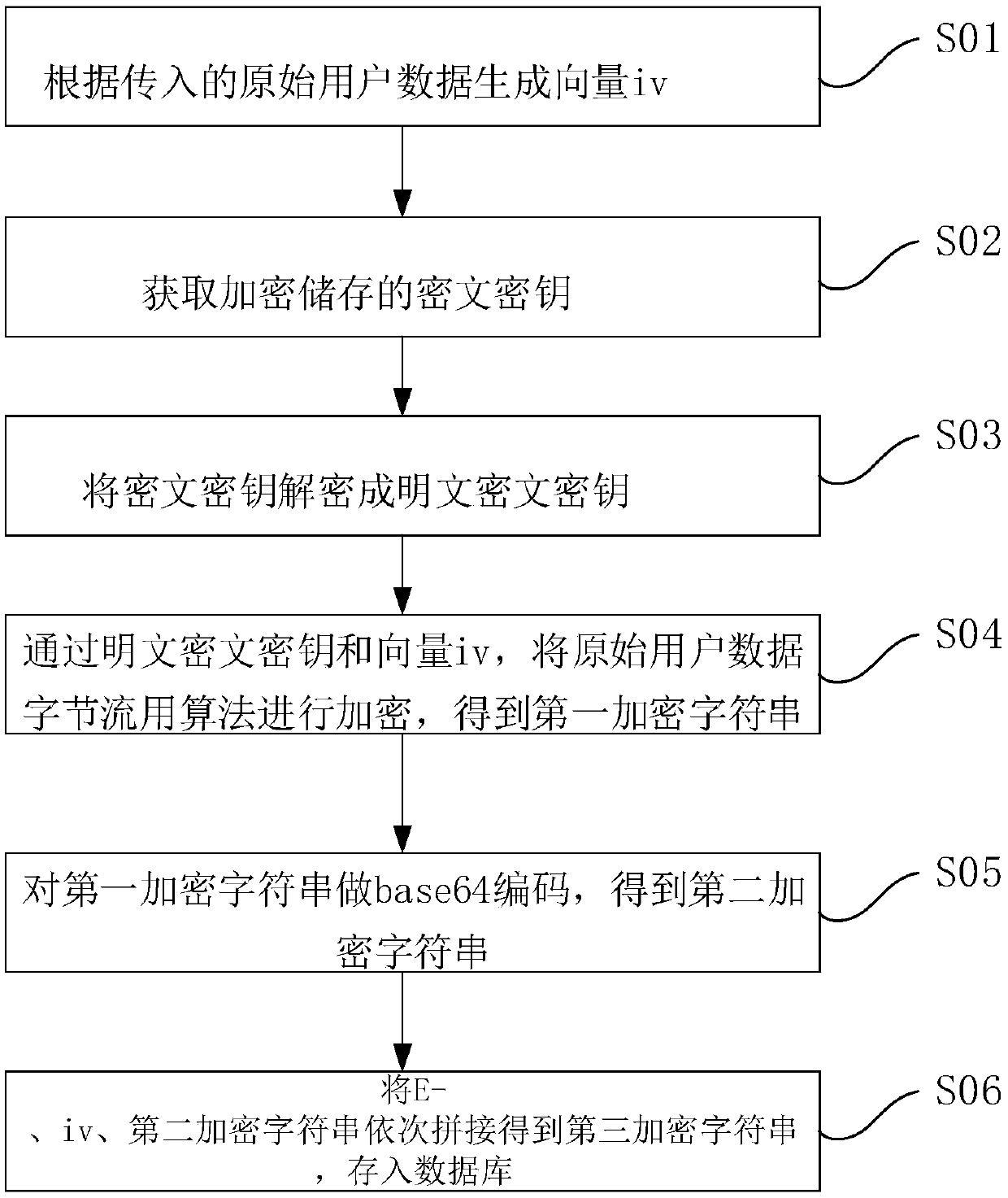
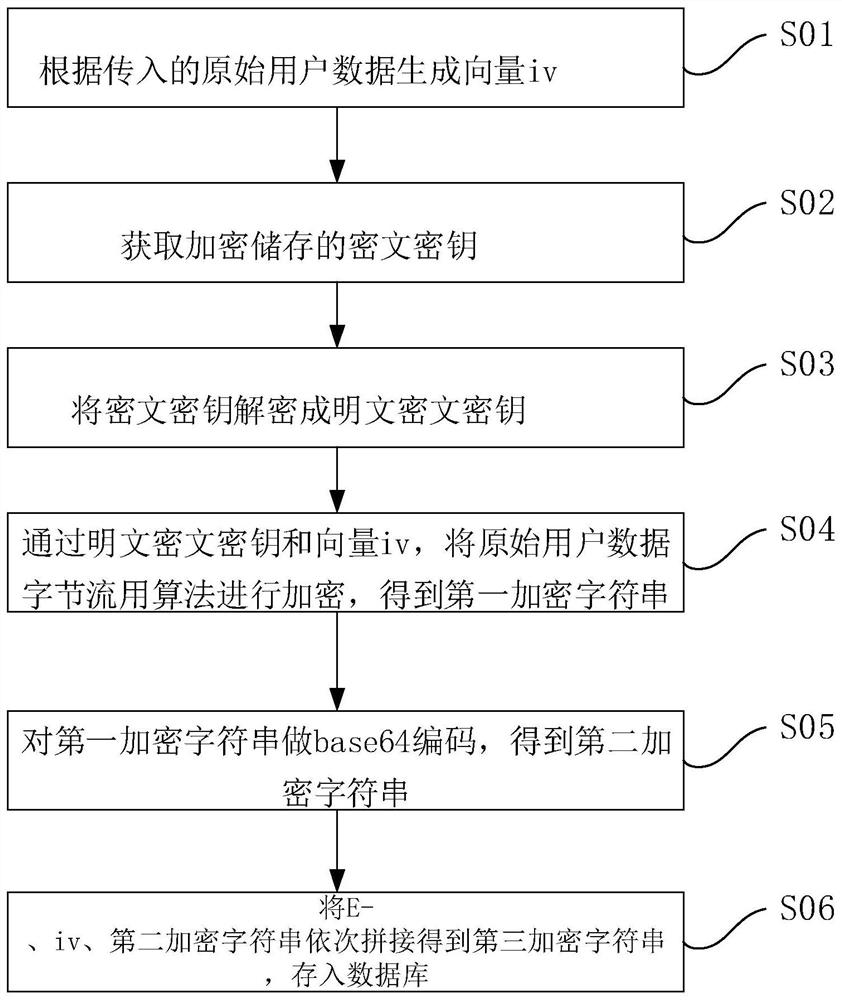
Internet e-commerce platform user privacy data encryption and decryption method
ActiveCN109583217AAvoid problemsAvoid gettingEncryption apparatus with shift registers/memoriesDigital data protectionPlaintextCiphertext
The invention discloses an Internet e-commerce platform user privacy data encryption method, which comprises the following steps of: encrypting and storing a ciphertext key, and generating a vector ivaccording to input original user data; Acquiring an encrypted and stored ciphertext key; Decrypting the ciphertext key into a plaintext ciphertext key; Encrypting the original user data byte stream by using an AES256 / CFB8 / NOPADDING algorithm through a plaintext ciphertext key and a vector iv to obtain a first encrypted character string; Carrying out Base64 coding on the first encrypted characterstring to obtain a second encrypted character string; connecting E-, iv and the second encrypted character string in sequence to obtain a third encrypted character string, and storing the third encrypted character string as encrypted data in a database. The user privacy data is encrypted, the user privacy data information of the database system is prevented from being leaked, and the processing efficiency is improved.
Owner:SHENZHEN YIXUNTIANKONG INTERNET TECH CO LTD
Intelligent password key with local data encryption function
ActiveCN105447394AAdd application functionsImprove practicalityDigital data protectionMass storagePassword
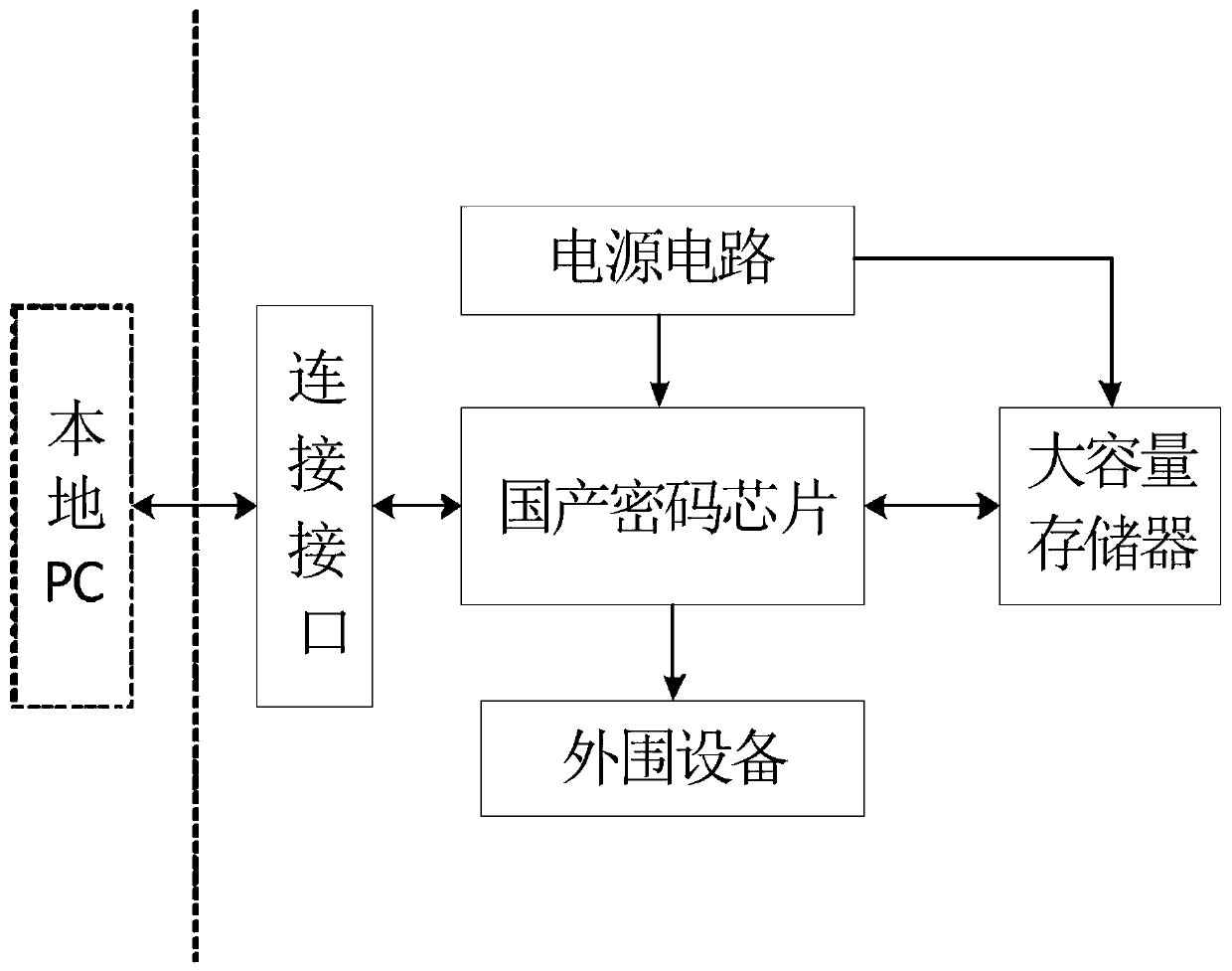
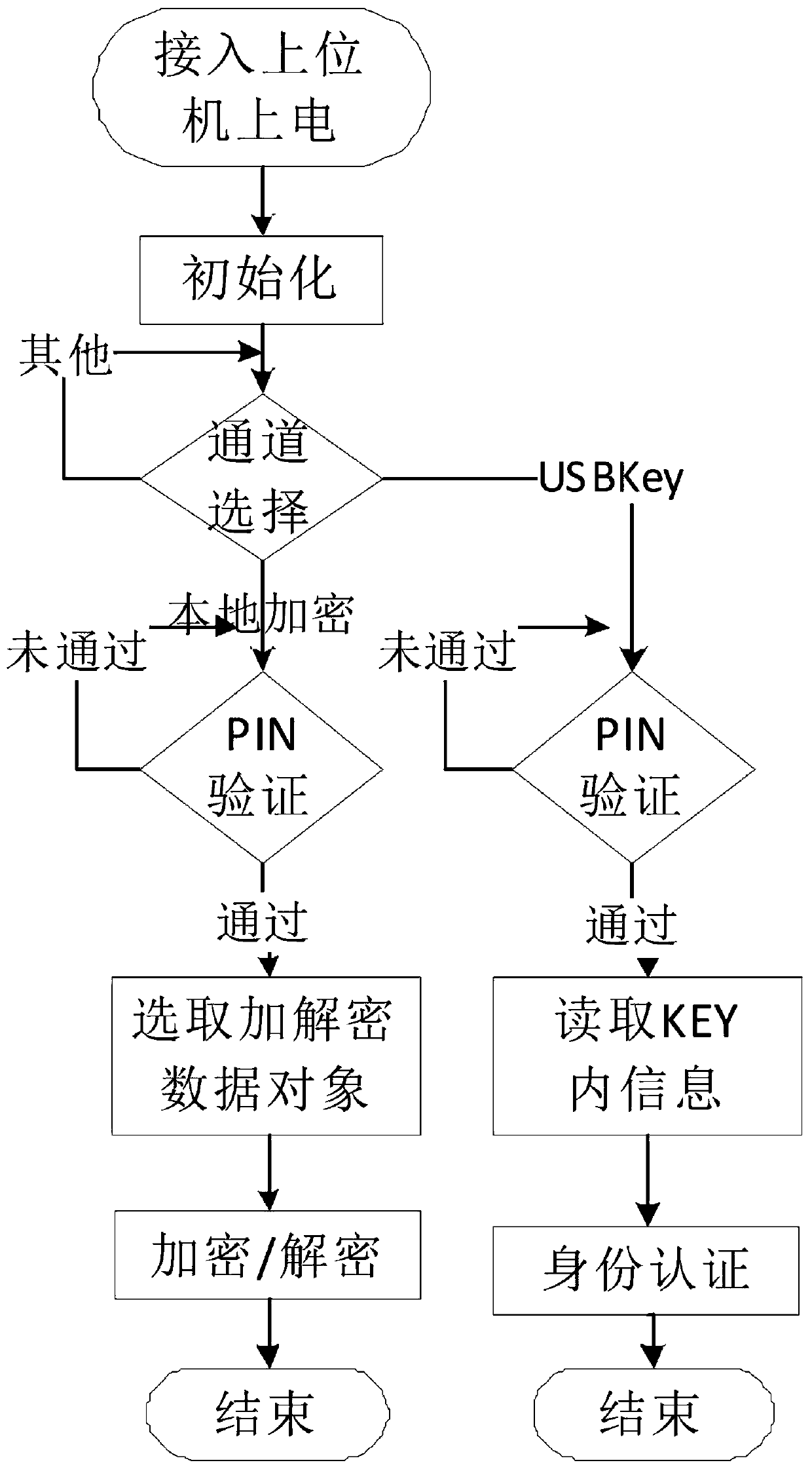
The invention discloses an intelligent password key with a local data encryption function. The intelligent password key comprises an encryption chip, a storage chip connected with the encryption chip, a power circuit, a connecting interface and a peripheral device, wherein the encryption chip is a microprocessor integrating a processor, input and output ports and a memory; the large-capacity storage chip is an NAND Flash chip, is provided with an NAND Flash controller and is connected with an external Flash to finish local data encryption storage; the power circuit is connected with a main control chip and the large-capacity memory, and monitors and provides a stable power supply; the connecting interface is connected with a local computer; and the peripheral device comprises an LED indication lamp and is connected with the encryption chip to indicate a working state of a USB Key. Compared with the prior art, the intelligent password key with the local data encryption function can serve as an encryption / decryption hardware key to encrypt / decrypt mass data of a PC end; and only a same encryption U disk can be used for encrypting / decrypting local data, so that the security is improved and the practicality is high.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
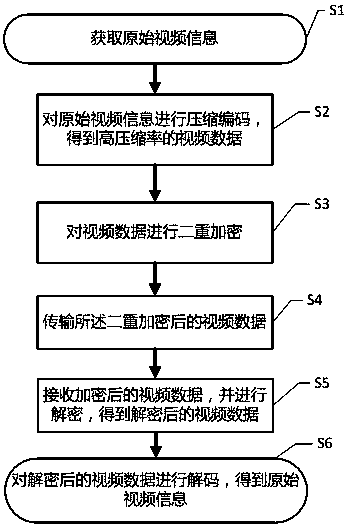
Computer video data processing method
InactiveCN108235022AIncrease the compression ratioTroubleshoot technical inefficienciesDigital video signal modificationTransmissionComputer hardwareCiphertext
The invention discloses a computer video data processing method. According to the computer video data processing method, the originally collected video information is compressed and encoded first to obtain the video data with high compression ratio; and dual encryption is carried out on the video data to be transmitted before the video data is transmitted, therefore, the cracking difficulty of a hacker is improved. In the first level encryption, the results of each unit on a nonlinear shifting register are obtained after performing a certain number of shifts and nonlinear transformations on the elements of the video data to be encrypted, and the first level encrypted output video data is obtained through a reversible transformation; and in the second level encryption, the last one ciphertext block in the generated first level encrypted output video data is used as a first target ciphertext block, the first target ciphertext block is decrypted to obtain the index value of the target ciphertext block, and second level encryption operation is performed on the index value of the first level encrypted output video data.
Owner:SUZHOU NANER MATERIAL TECH CO LTD
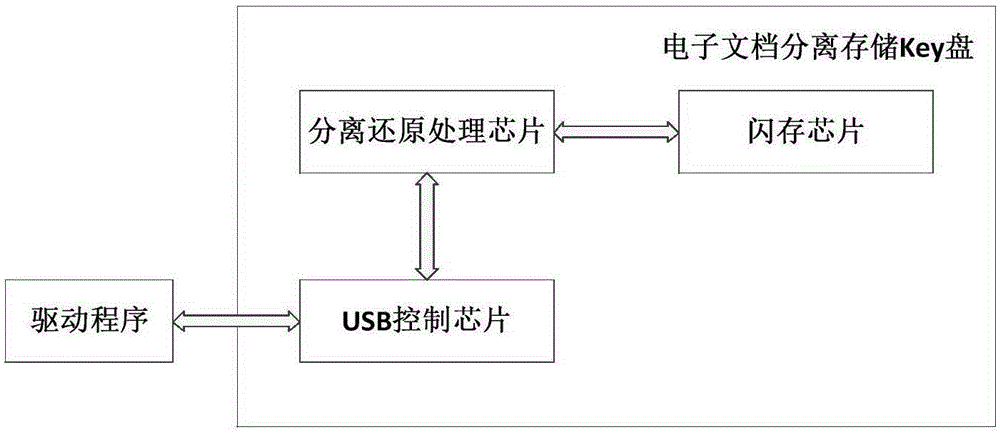
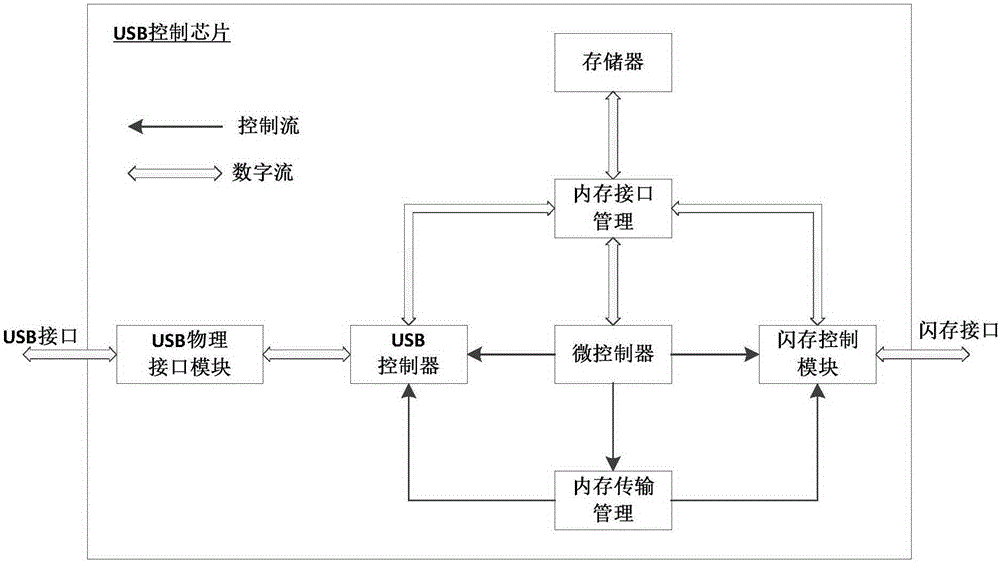
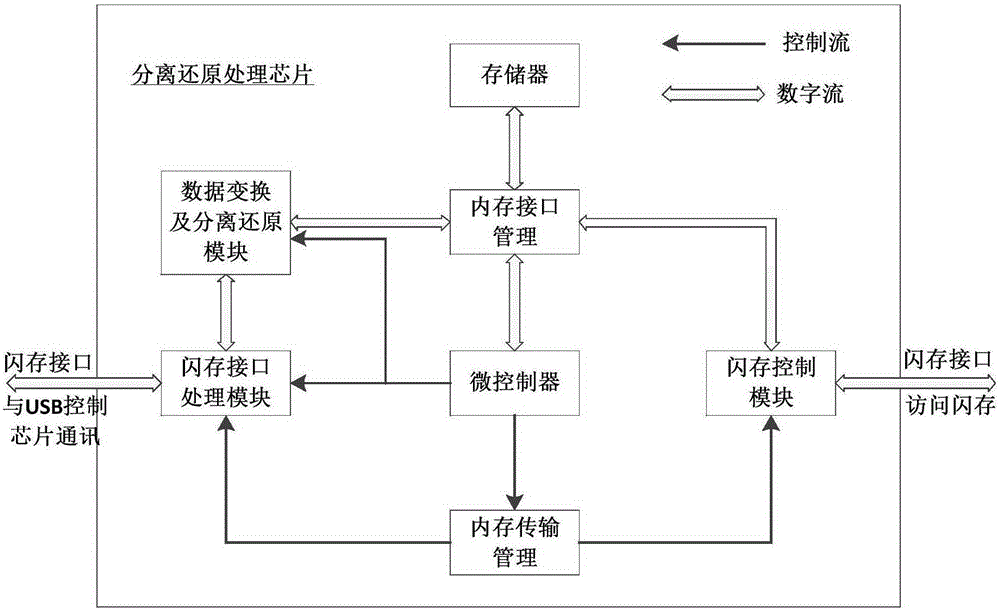
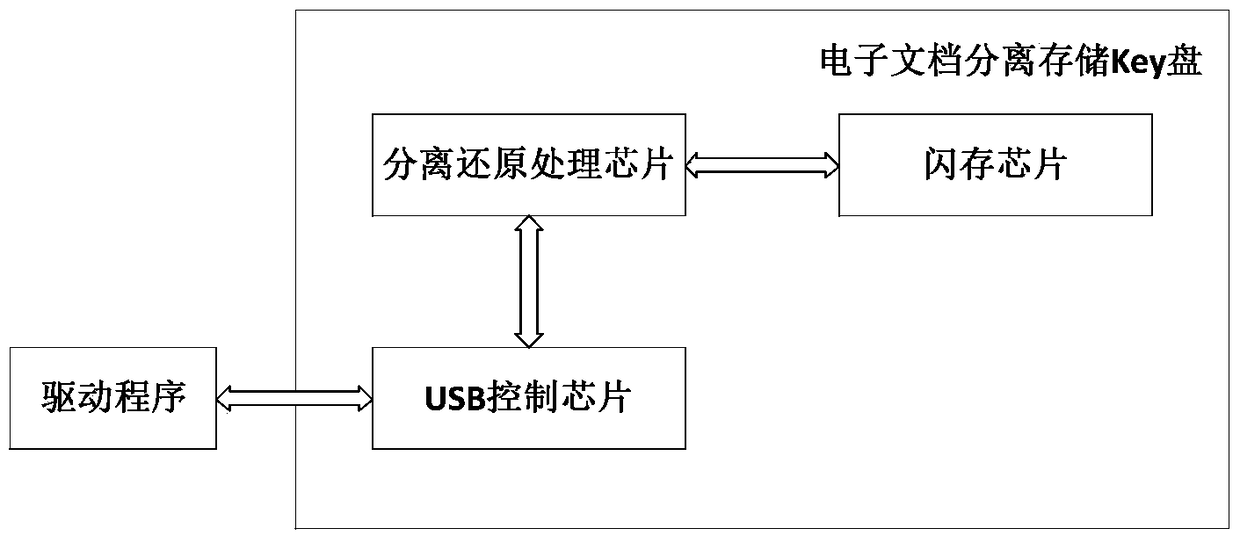
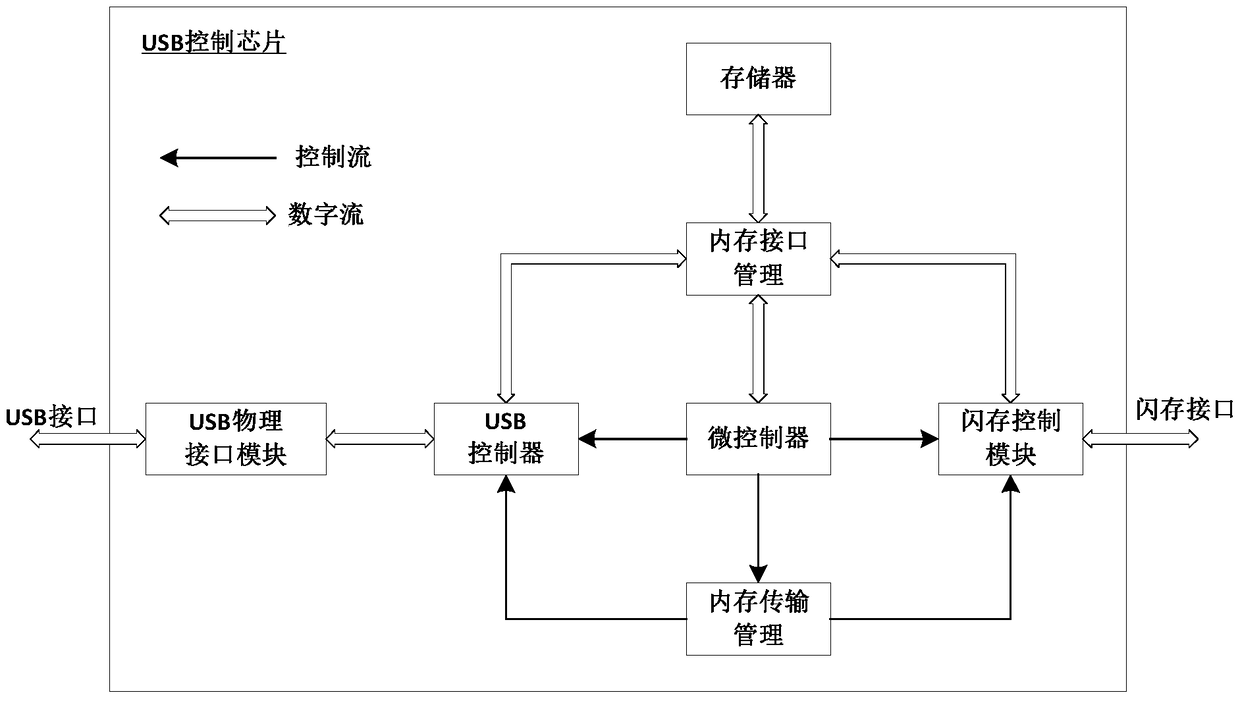
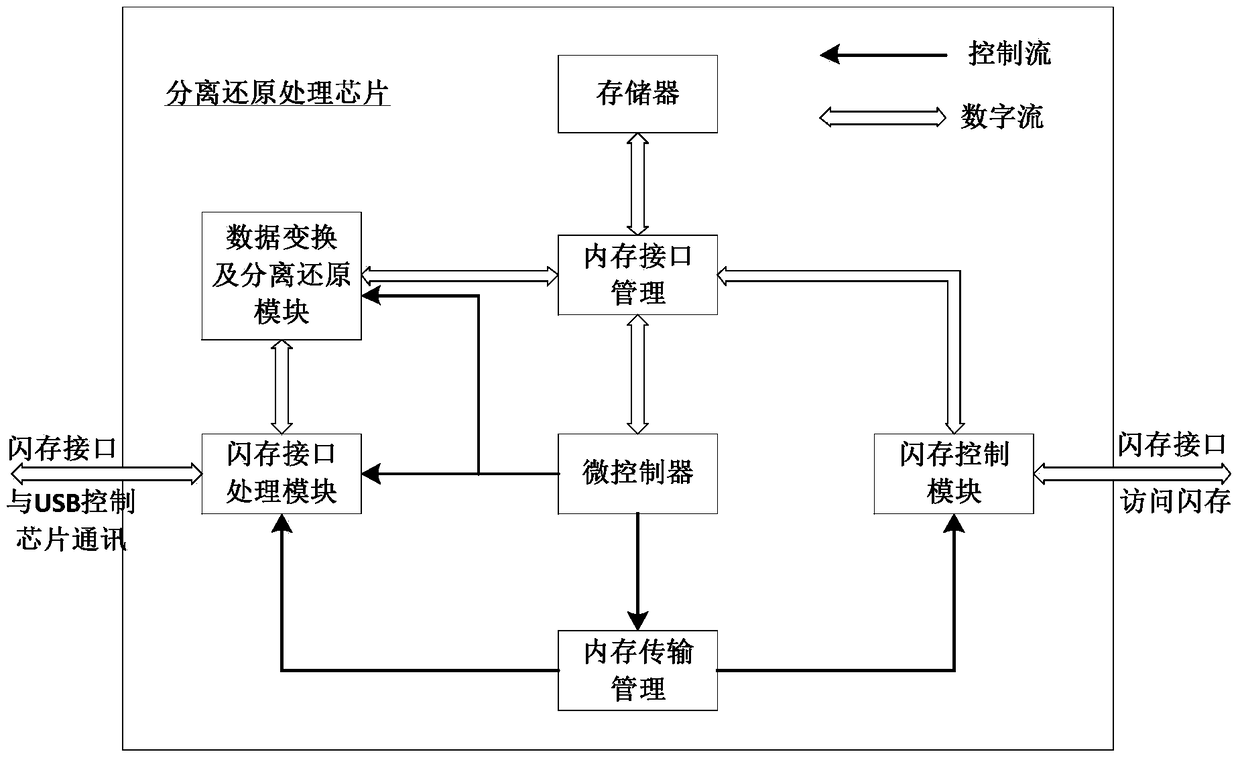
Data separate storage and reduction key disk and data separation and reduction method thereof
ActiveCN105184185APrevent leakageEffective Document Leakage Prevention Management MeasuresDigital data protectionElectronic documentUSB
The invention discloses a data separate storage and reduction key disk. The key disk comprises a USB control chip, a separation and reduction processing chip and a flash memory chip. The USB control chip receives and analyzes commands and data transmitted by a drive program through a USB port. The flash memory chip receives commands and data sent by the separation and reduction processing chip and stores the data. The separation and reduction processing chip is connected with the USB control chip and the flash memory chip and separates and reduces the data. An electronic document is separated step by step through the chips in the key disk, two data strings are generated finally, the two data strings are stored separately, a user can prevent the electronic document from being divulged just by ensuring the security of any data string, and therefore an effective document divulging prevention means is provided. The means has higher protection intensity than an existing security and secrecy system and is suitable for application and popularization.
Owner:丽水至行科技有限公司
Information transmission method
ActiveCN107294964AHigh encryption levelImprove the leakage levelKey distribution for secure communicationUser identity/authority verificationInformation transferInformation transmission
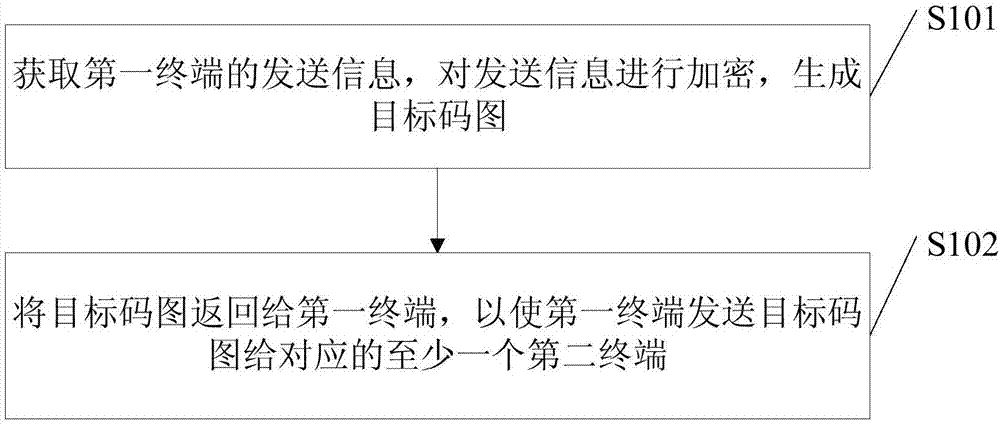
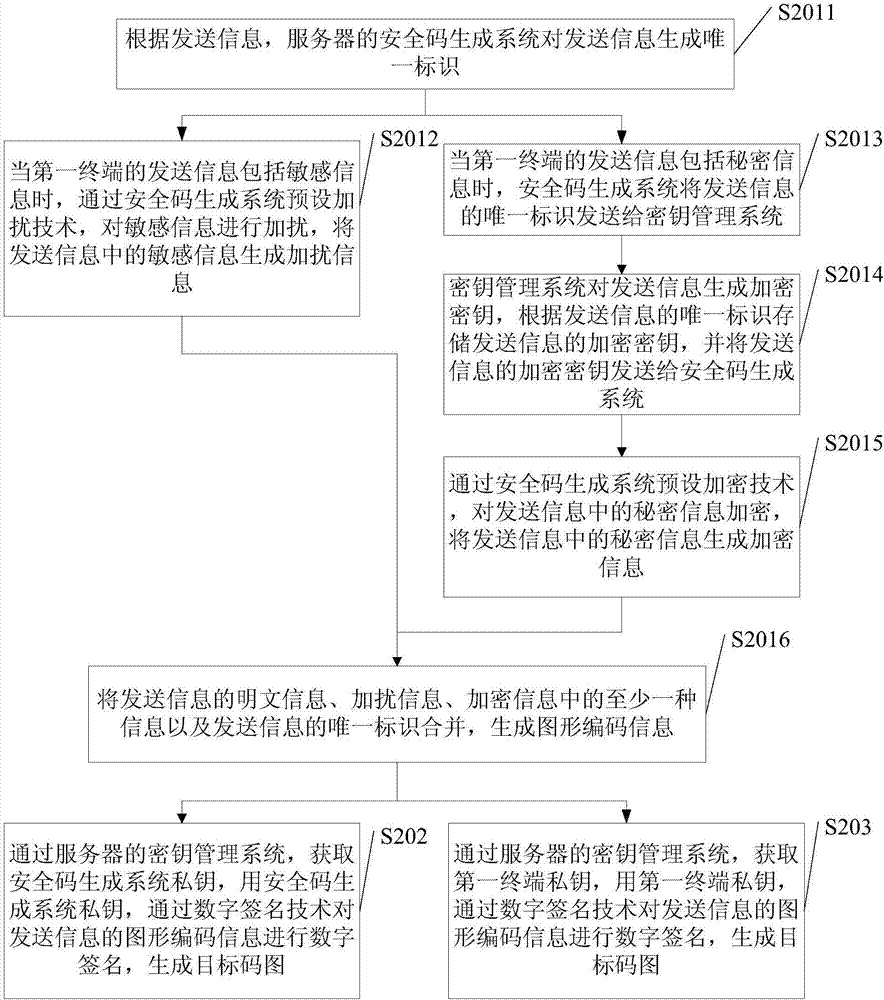
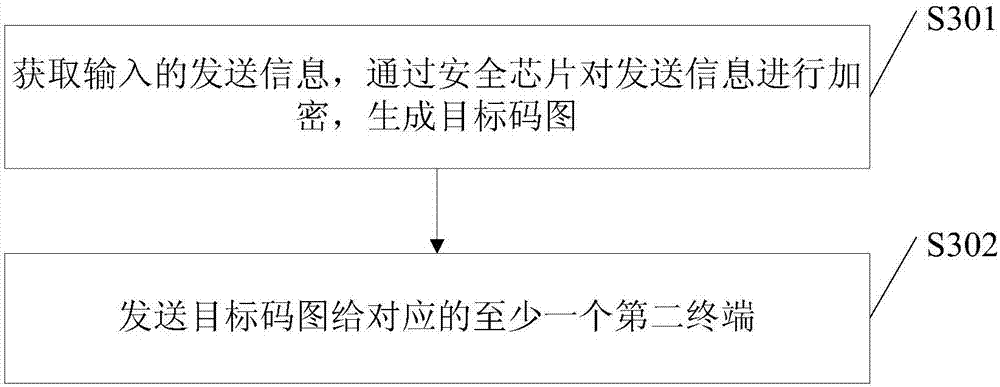
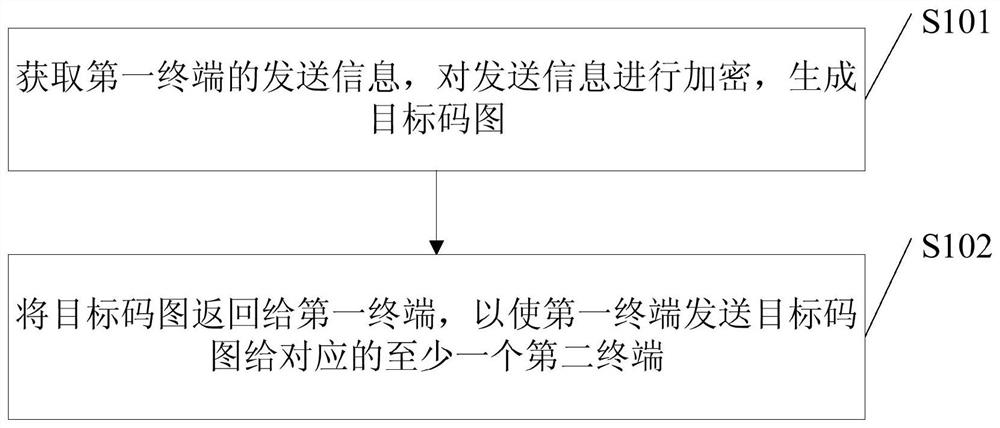
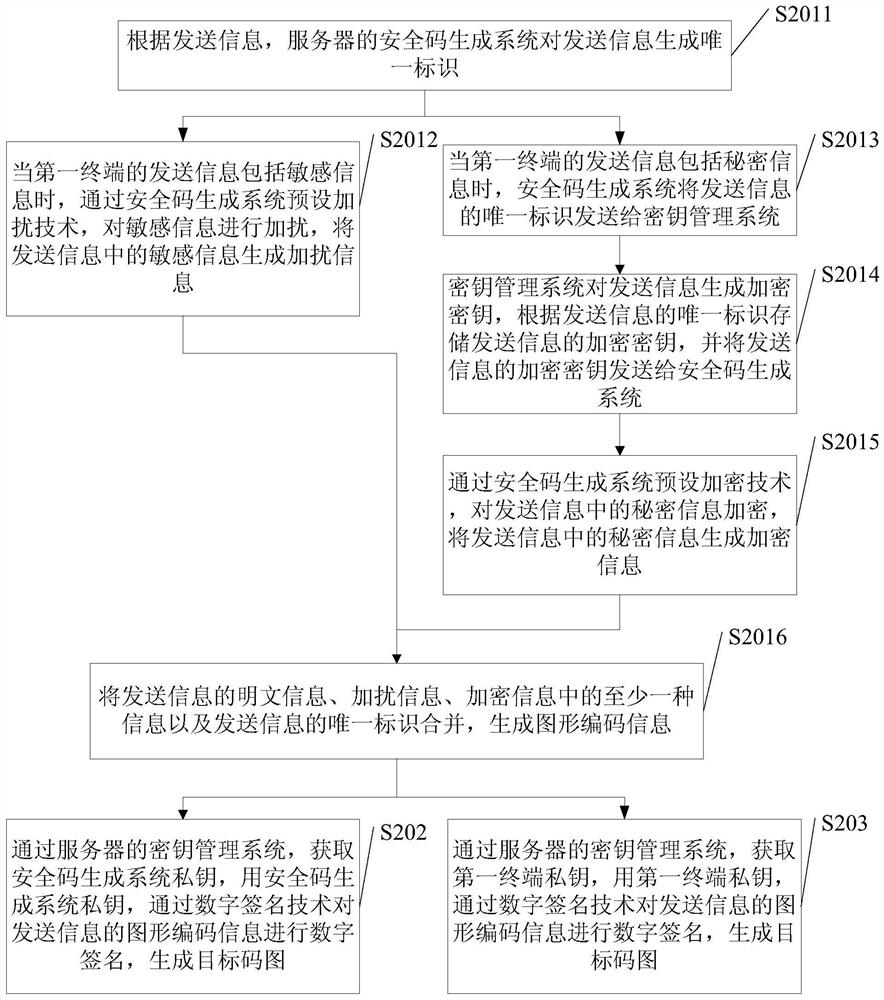
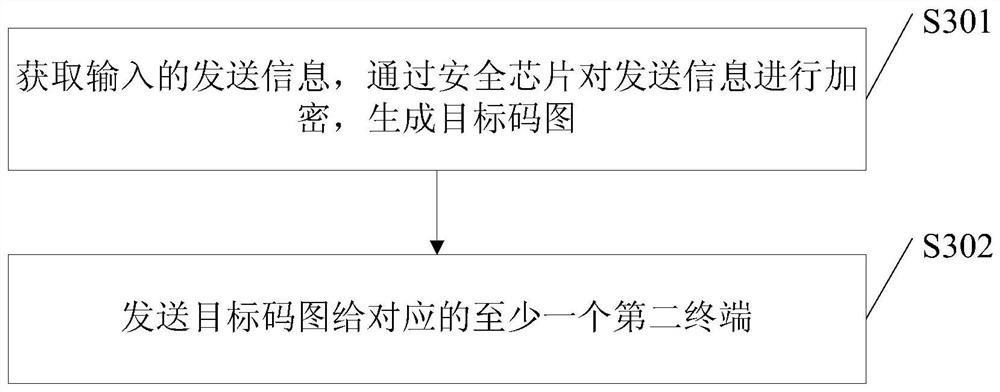
The embodiments of the invention disclose an information transmission method, wherein the information transmission method is applied to a server and comprises: obtaining the information transmitted from a first terminal, encrypting the transmitted information, and generating a targeted code graph, wherein the transmitted information comprises at least one of the following kinds of information: plaintext information, sensitive information or secrete information and the targeted code graph carries the graphic code information and the digital signature to the graphic code information by a security code generation system's private key or the digital signature to the graphic code information by a first terminal's private key; and returning the targeted code graph to the first terminal so that the first terminal transmits the targeted code graph to at least one corresponding second terminal. The information transmission method of the invention makes the information transmission more secure and more private.
Owner:BEIJING D9ING INST OF INFORMATION ENG CO LTD +1
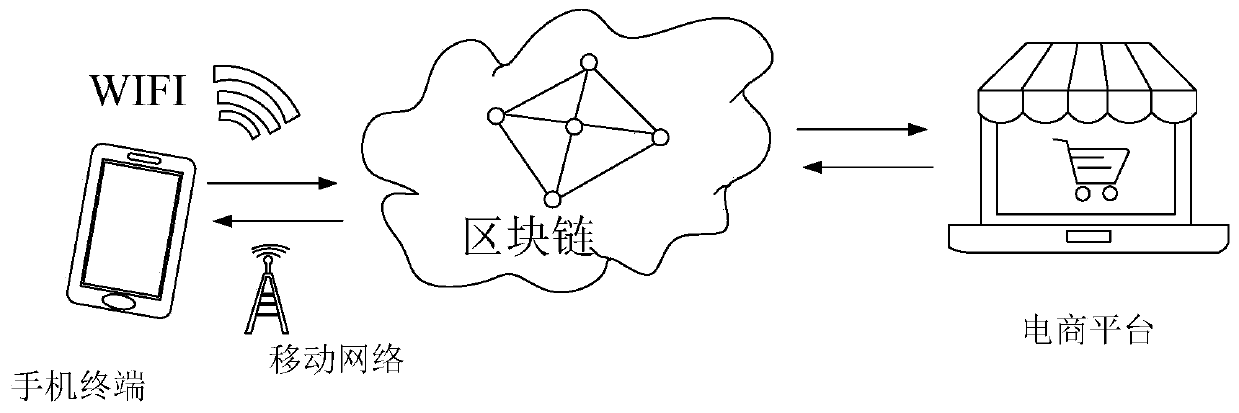
Mobile terminal e-commerce platform system based on block chain
InactiveCN110490709AReduce computing consumptionAchieve distributionFinanceBuying/selling/leasing transactionsEnd systemMobile end
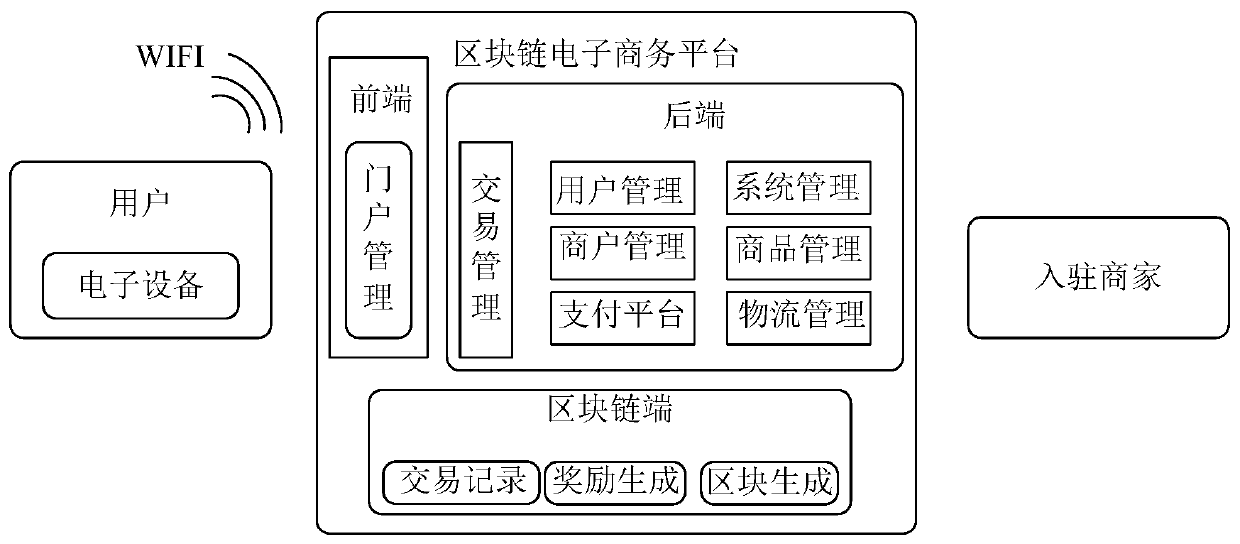
The invention provides a mobile terminal e-commerce platform system based on a block chain, and belongs to the technical field of e-commerce platforms. The mobile terminal e-commerce platform system based on the block chain specifically comprises an e-commerce platform user, a block chain e-commerce platform, a platform back-end system, a platform front-end system, a block chain end system and a check-in merchant. According to the mobile terminal e-commerce platform system based on the block chain, the block chain is combined with a traditional e-commerce platform, and information transmissionis established by utilizing a block chain technology, so that transaction records are recorded in the chain, non-tampering and distributed account books are ensured, the data encryption level is increased, and the security is enhanced. Simple distributed transaction processing can be realized, mining rewards are reasonably distributed, an e-commerce information block chain can be issued at a mobile terminal, and the use and propagation intention of a user is improved. Through centralization of the e-commerce platform based on the block chain, processing and storage of core data are ensured, and the safety performance and anti-risk capability of the system are improved.
Owner:SHANGHAI SUOBEI INFORMATION TECH CO LTD
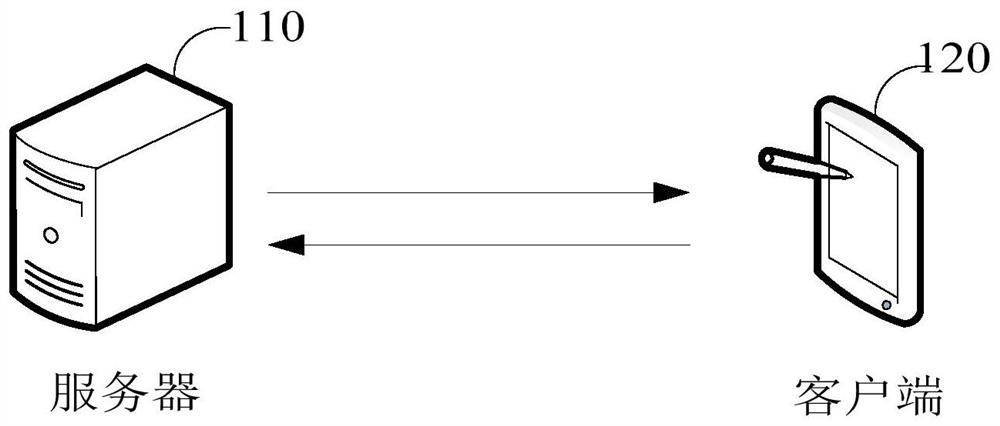
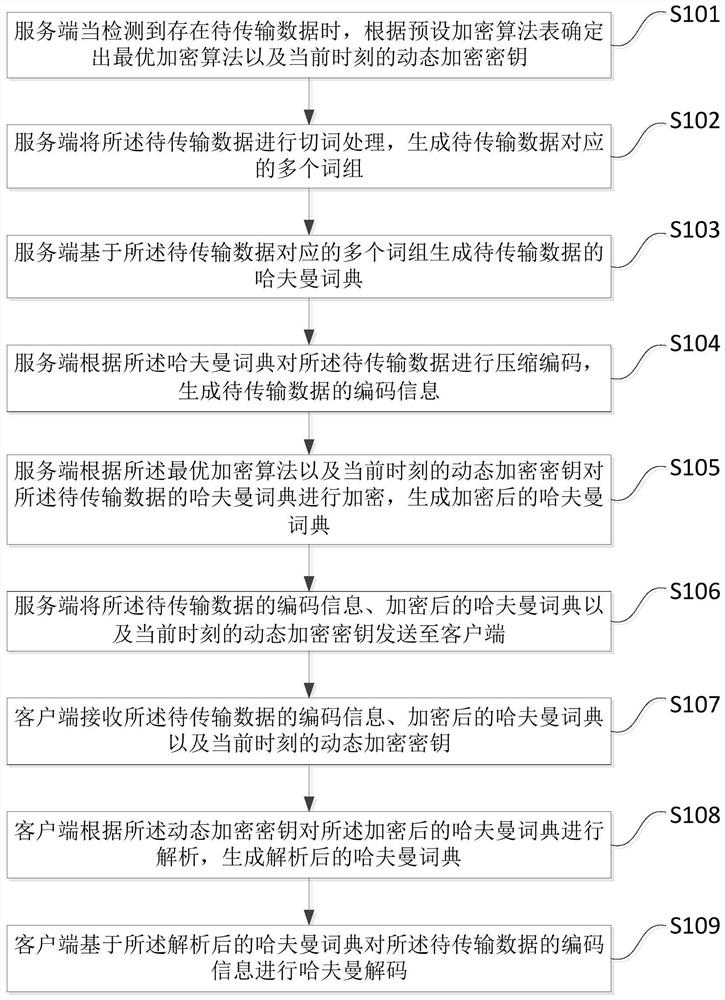
Data transmission method and device, computer equipment and storage medium
ActiveCN112437060AHigh encryption levelKey distribution for secure communicationError preventionAlgorithmTheoretical computer science
The invention discloses a data transmission method and device, computer equipment and a storage medium, and the method comprises the steps: determining an optimal encryption algorithm and a dynamic encryption key at a current moment according to a preset encryption algorithm table when a server detects that to-be-transmitted data exists; performing word segmentation processing on the to-be-transmitted data to generate a plurality of word groups corresponding to the to-be-transmitted data; generating a Huffman dictionary of the to-be-transmitted data based on the plurality of word groups corresponding to the to-be-transmitted data; compressing and encoding the to-be-transmitted data according to the Huffman dictionary to generate encoding information of the to-be-transmitted data; encrypting the Huffman dictionary of the to-be-transmitted data according to the optimal encryption algorithm and the dynamic encryption key at the current moment to generate an encrypted Huffman dictionary; and sending the coded information of the to-be-transmitted data, the encrypted Huffman dictionary and the dynamic encryption key at the current moment to the client. Therefore, by adopting the embodiment of the invention, the network broadband required to be consumed during data transmission can be reduced.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
Object antitheft system with data acquisition function and correlation method
InactiveCN104732687AConvenient verificationHigh encryption levelBurglar alarmManagement unitData acquisition
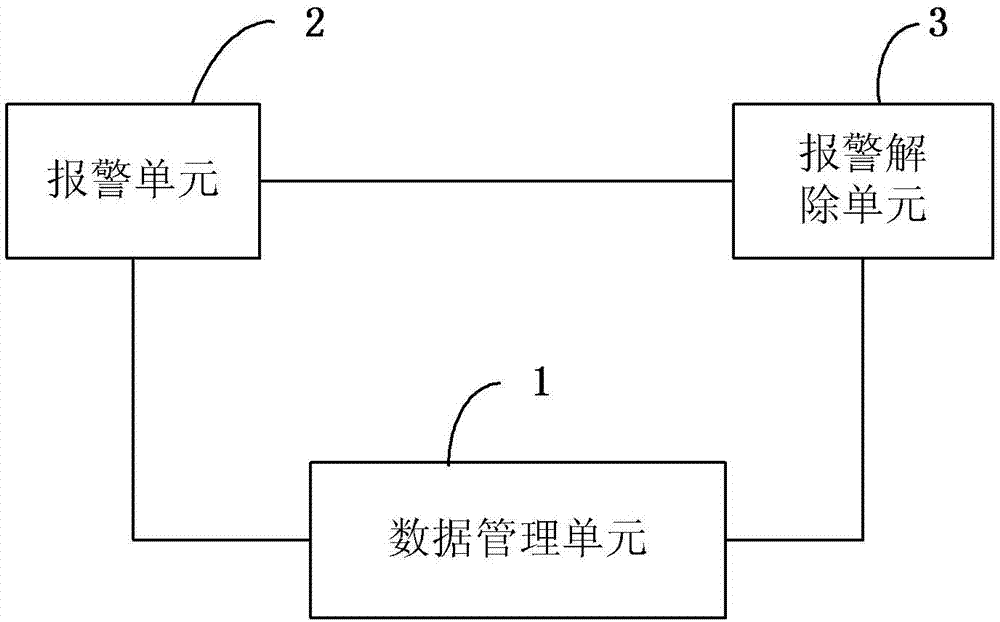
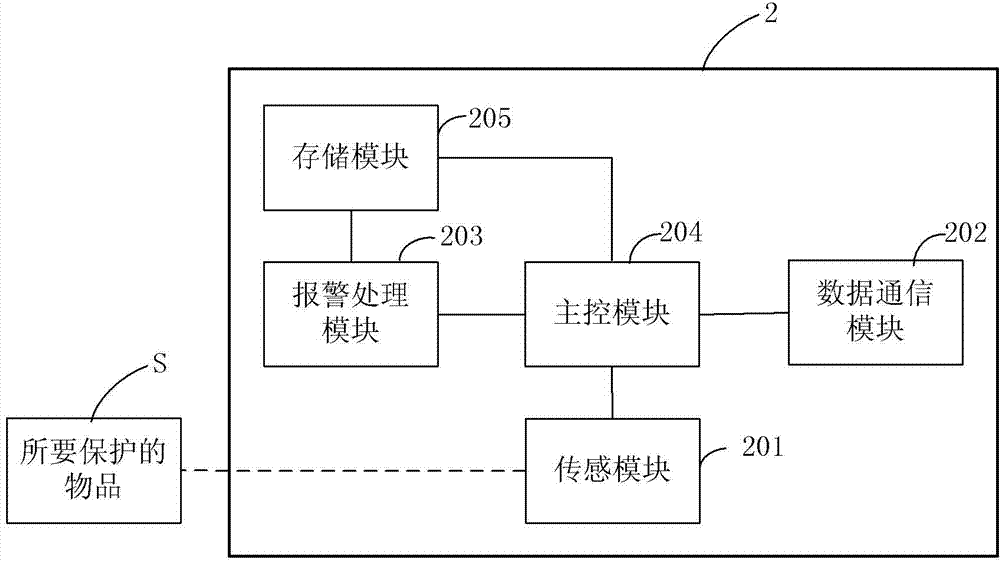
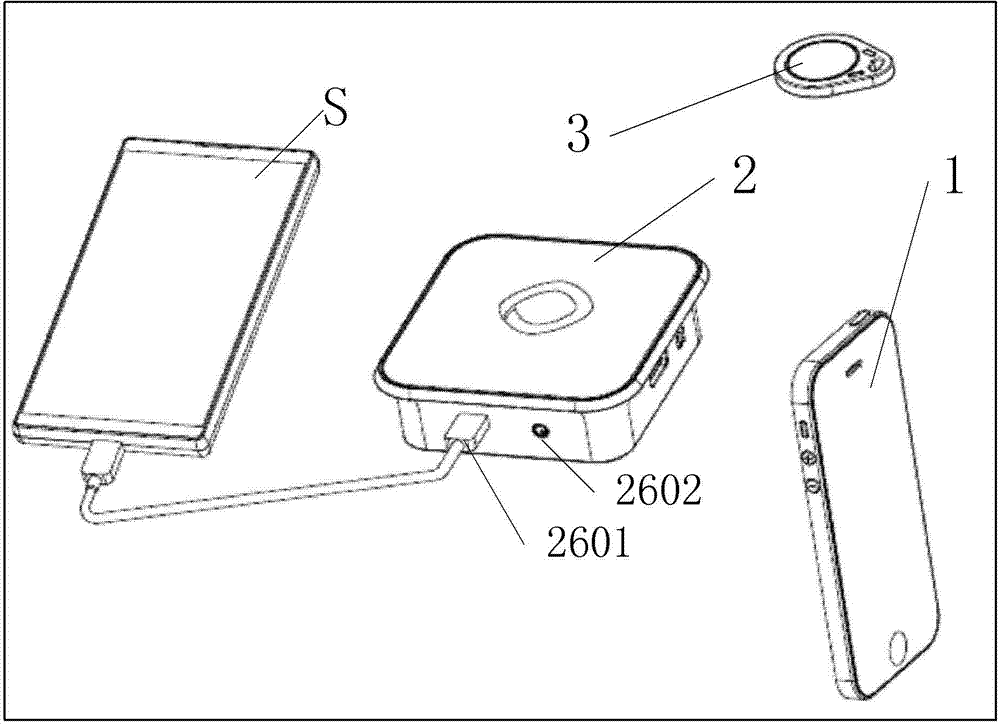
The invention discloses an object antitheft system and a correlation method thereof. The system comprises a data management unit, at least one alarm unit and at least one alarm relief unit. The data management unit is used for setting unlocking data in the alarm relief units and setting unlocking judgment data in the alarm unit. The alarm unit can detect whether an object needing to be protected is in a normal state or not under the alarm start state and send alarm signals when it is detected that the object needing to be protected is not in the normal state. The alarm unit judges whether the unlocking data are legal or not according to the stored unlocking judgment data and relieving the alarm start state when it is judged that the unlocking data are legal. Each unlocking judgment datum corresponds to one unique legal unlocking datum. The alarm unit can achieve the data acquisition function, and can acquire alarm start and alarm relief correlation information and other data correlated with user behaviors for later data analysis.
Owner:QUASION +1
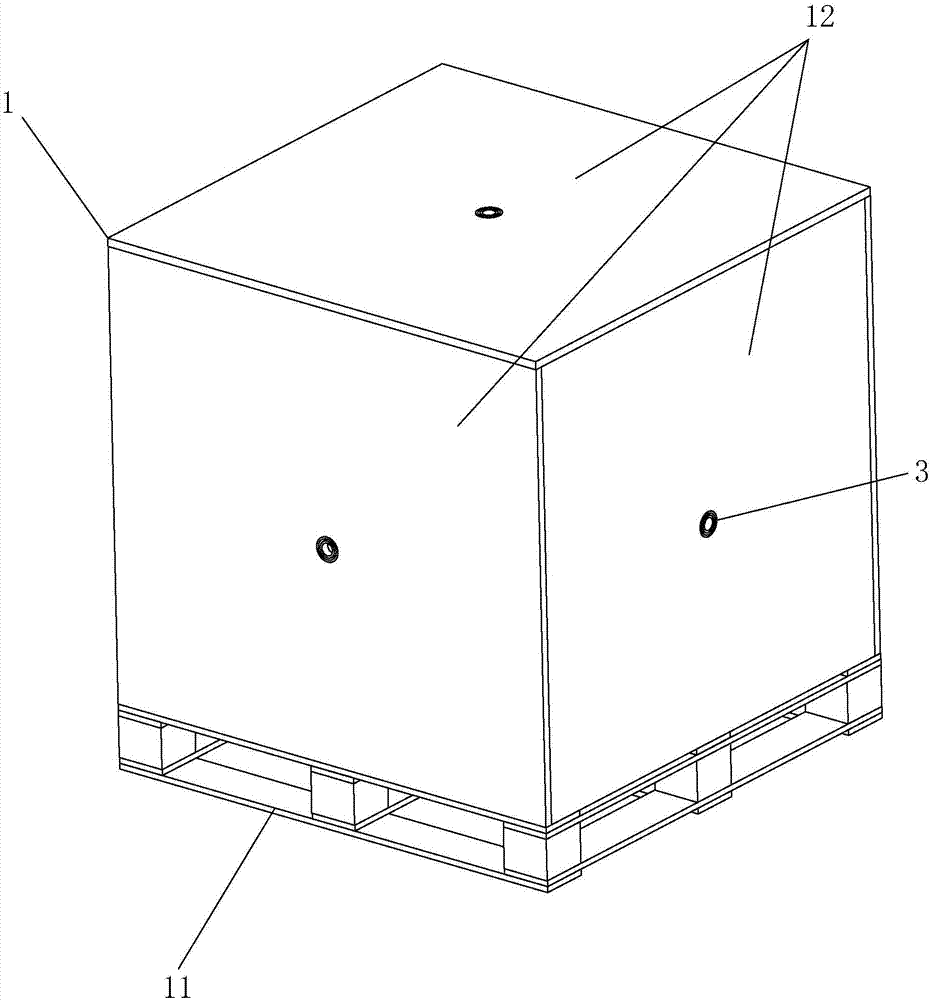
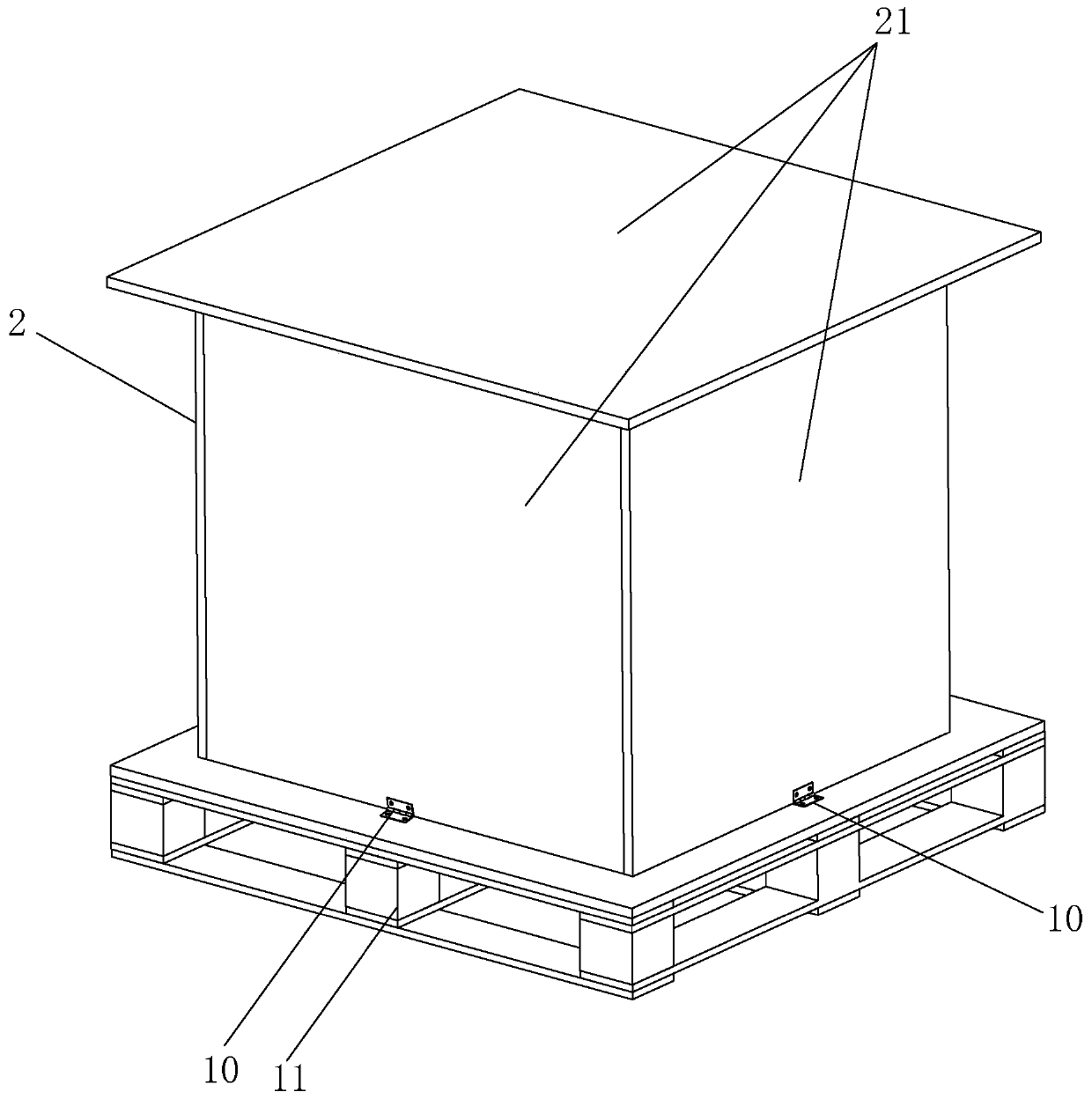
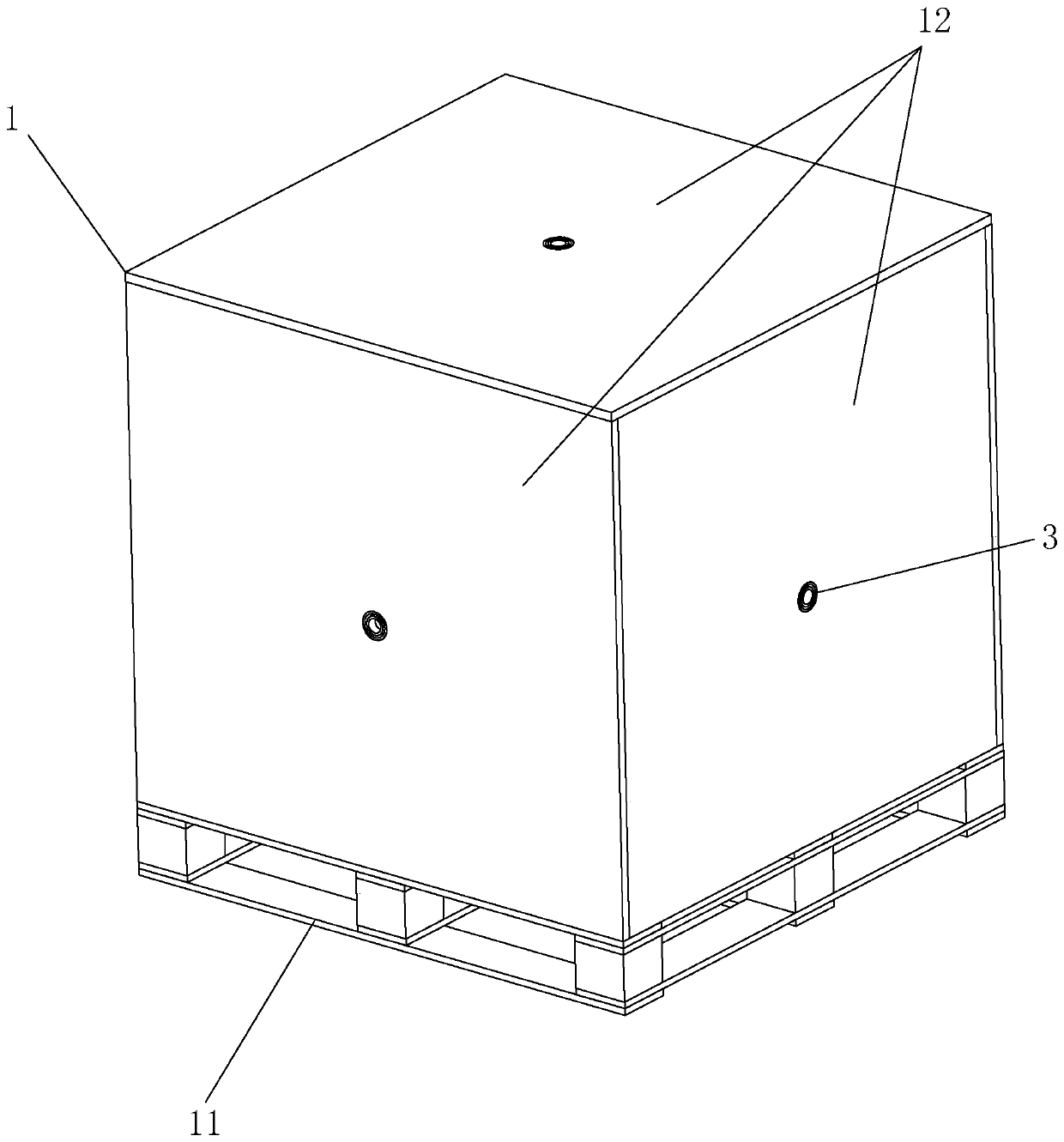
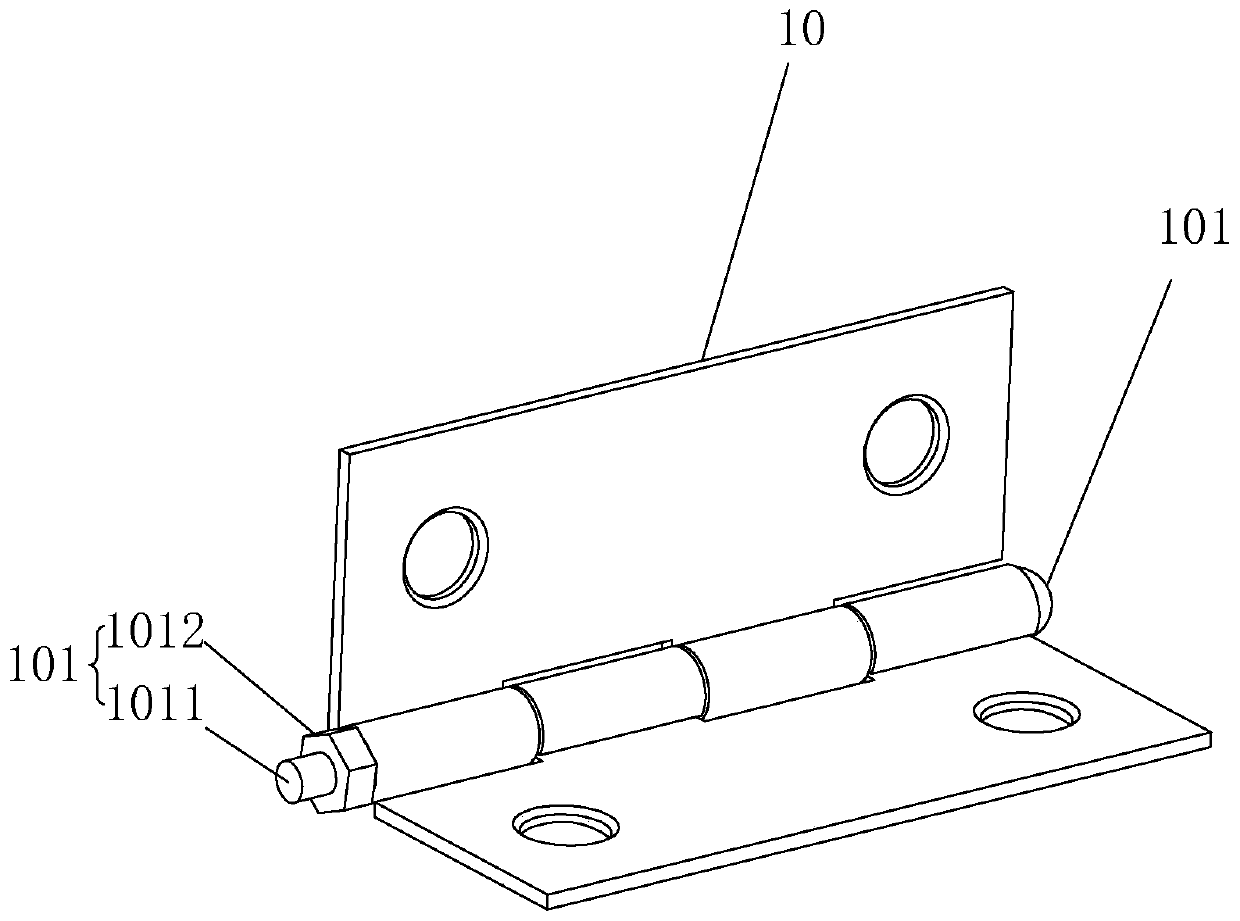
Combined stealing-disassembling-preventing packaging box and stealing-disassembling preventing method
InactiveCN107985727ALower success rateReduce theftRigid containersExternal fittingsEngineeringMechanical engineering
Owner:温胜洁
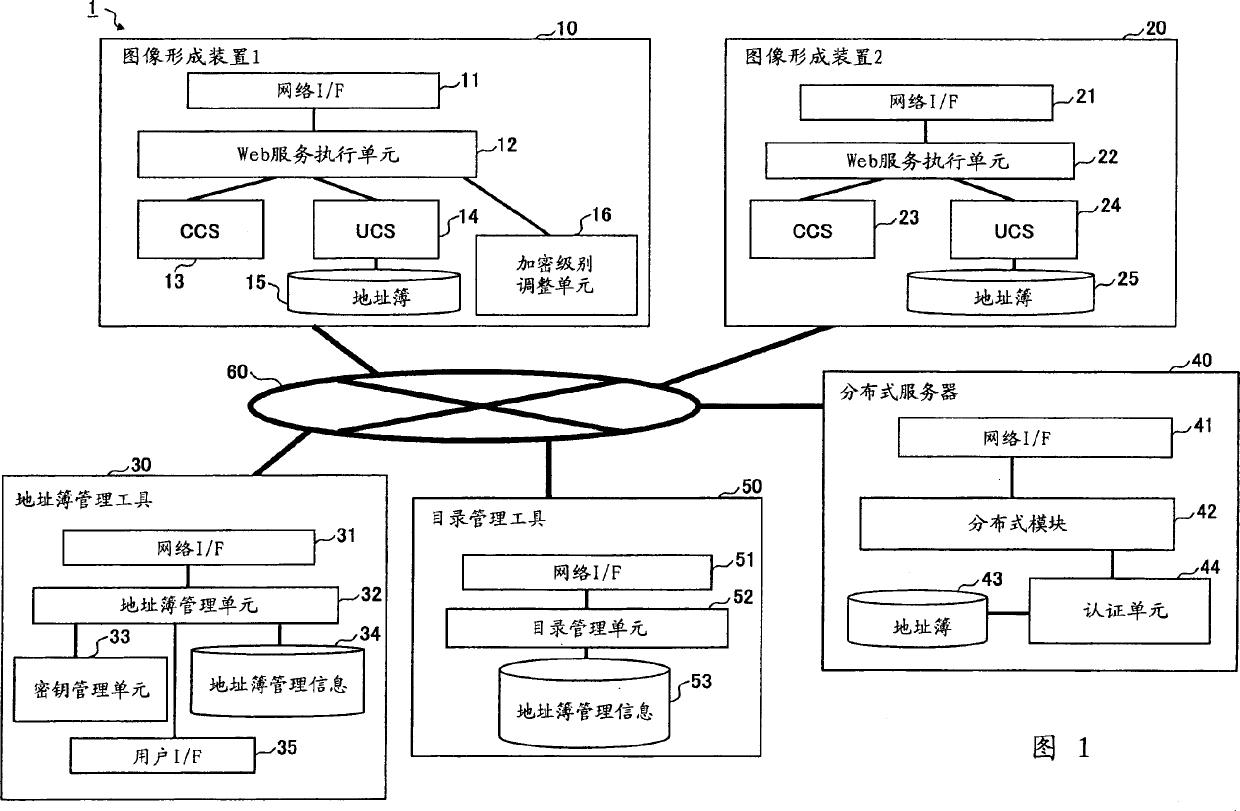
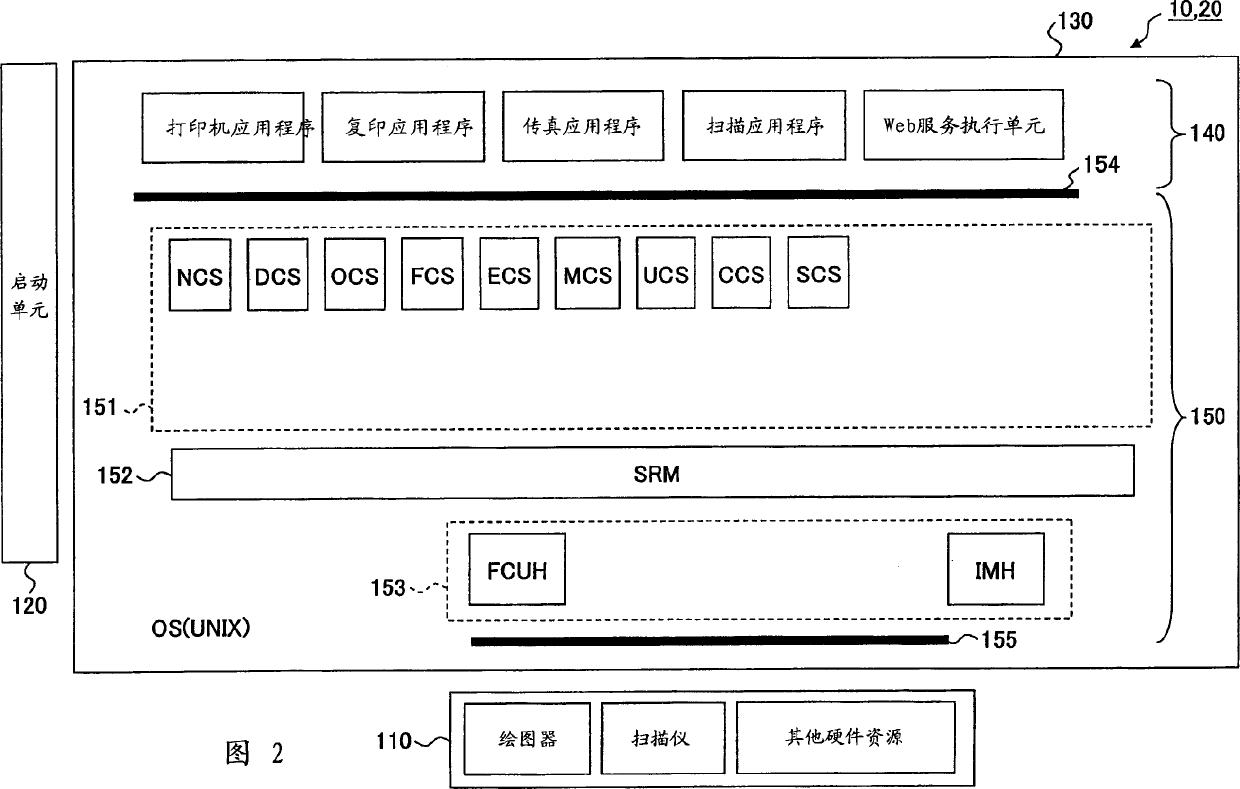
Information management system, information processor, and information management method
ActiveCN1783814AHigh encryption levelEncryption levels are assigned to include different levels of increased securityData switching networksInformation processorLibrary science
The invention discloses an information management system (1), information processors (10), (20), and an information management method. The information management system includes an information processor and an information management device (30) connected through a network (60). When storing information into the information management device, one of the information processors adjusts the encryption level of the information, the information including two or more items having different security levels, according to a predetermined degree of reliability.
Owner:RICOH KK
Set top box protection method and system, set top box and encryption device
InactiveCN103491439AHigh encryption levelPrevent from being copiedSelective content distributionPasswordSet top box
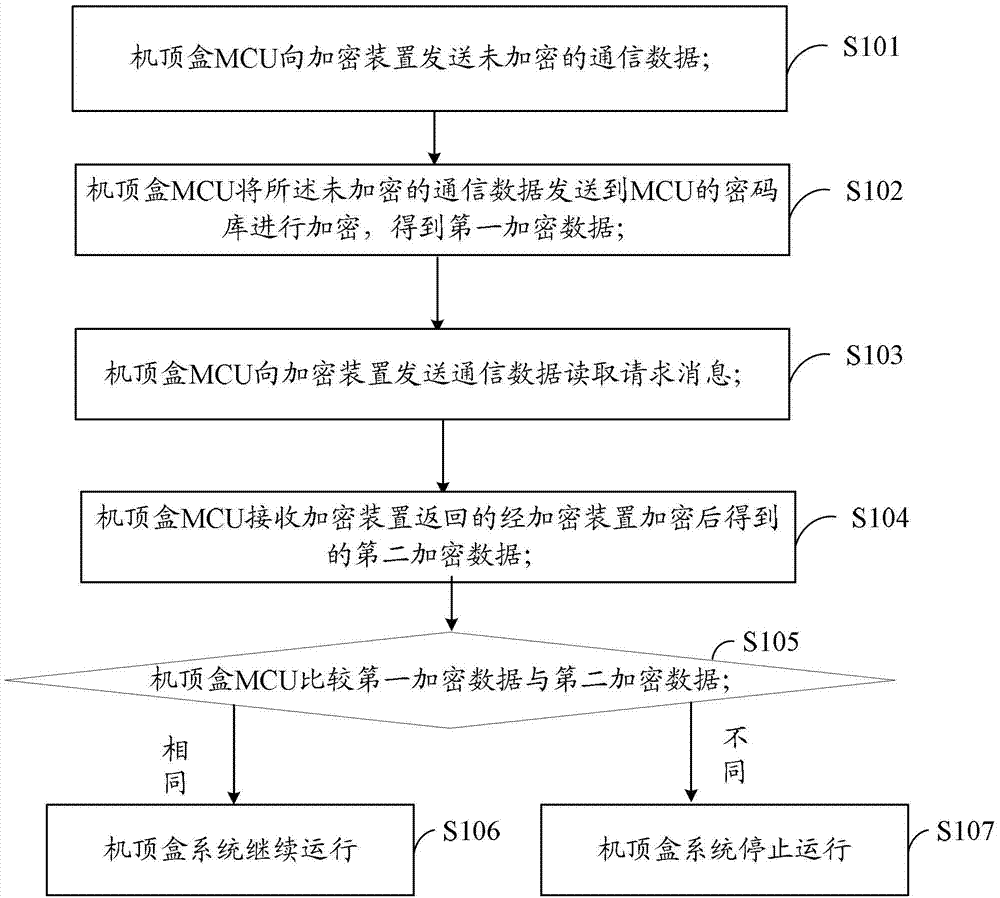
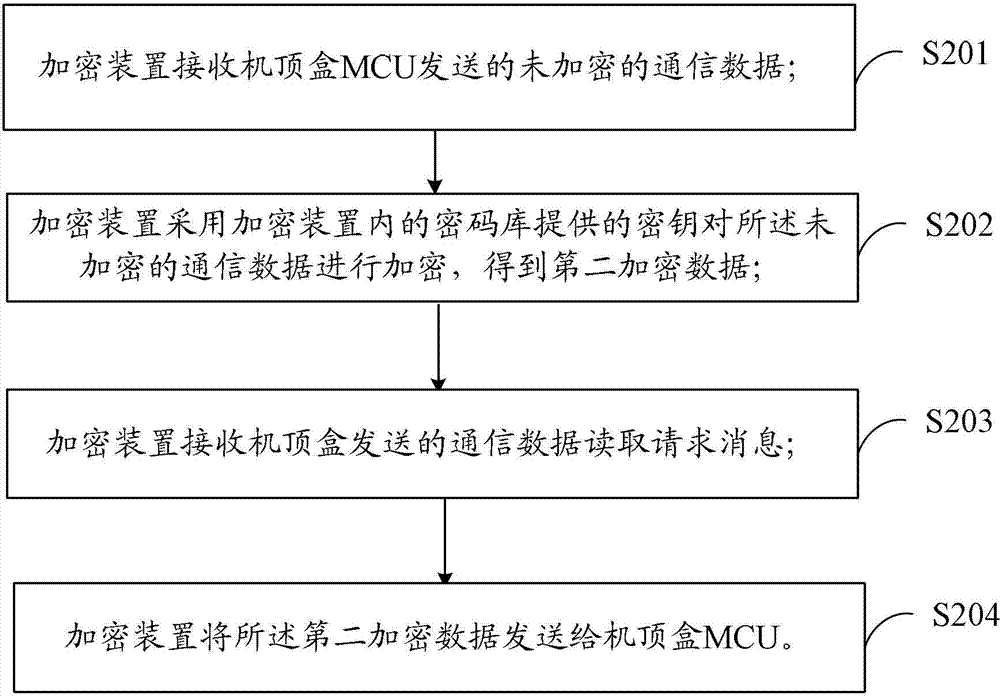
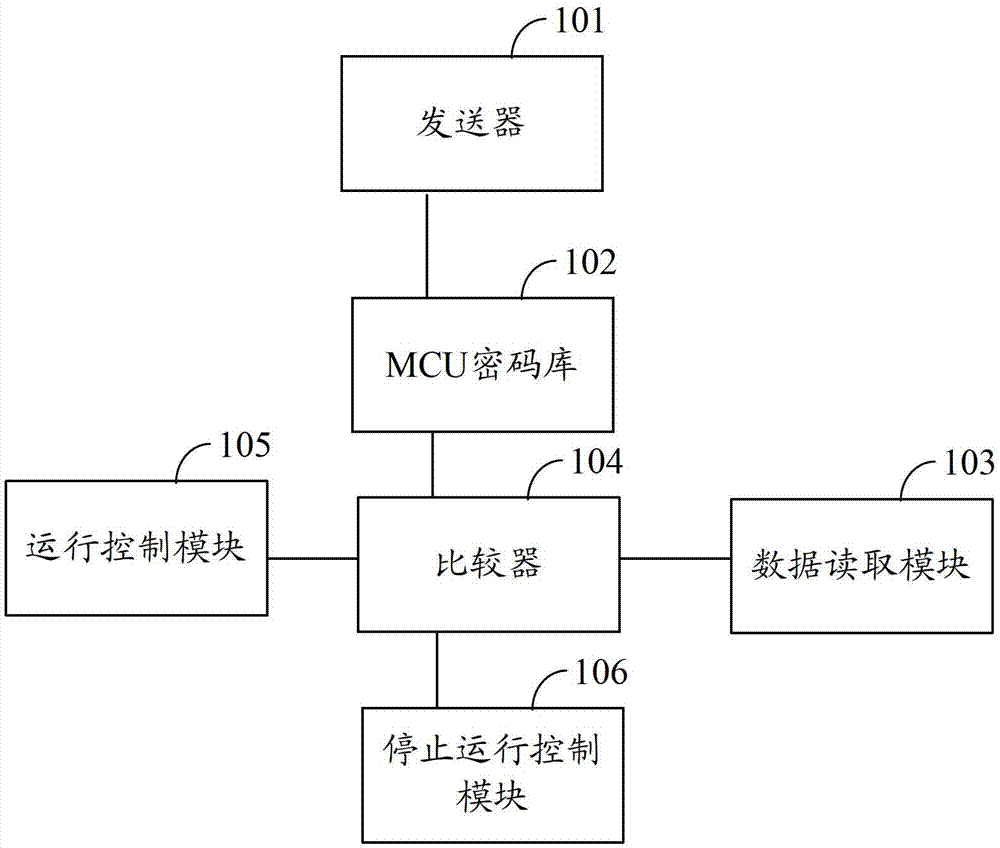
The invention belongs to the technical field of encryption, and provides a set top box protection method and system, a set top box and an encryption device. The set top box protection method comprises the following steps that a set top box MCU sends unencrypted communication data to the encryption device; the set top box MCU sends the unencrypted communication data to a password bank of the MCU to be encrypted, and first encrypted data are obtained; the set top box MCU sends a communication data reading request message to the encryption device; the set top box MCU receives second encrypted data returned and encrypted by the encryption device; the set top box MCU compares the first encrypted data with the second encrypted data; if after comparison, the first encrypted data are the same as the second encrypted data, a set up box system runs continuously; if after comparison, the first encrypted data are different from the second encrypted data, the set top box system stops running. By means of the set top box protection method and system and the encryption device, the encryption level of the set top box can be improved, and copy of software information can be prevented in the aspect of hardware.
Owner:SHENZHEN JIUZHOU ELECTRIC
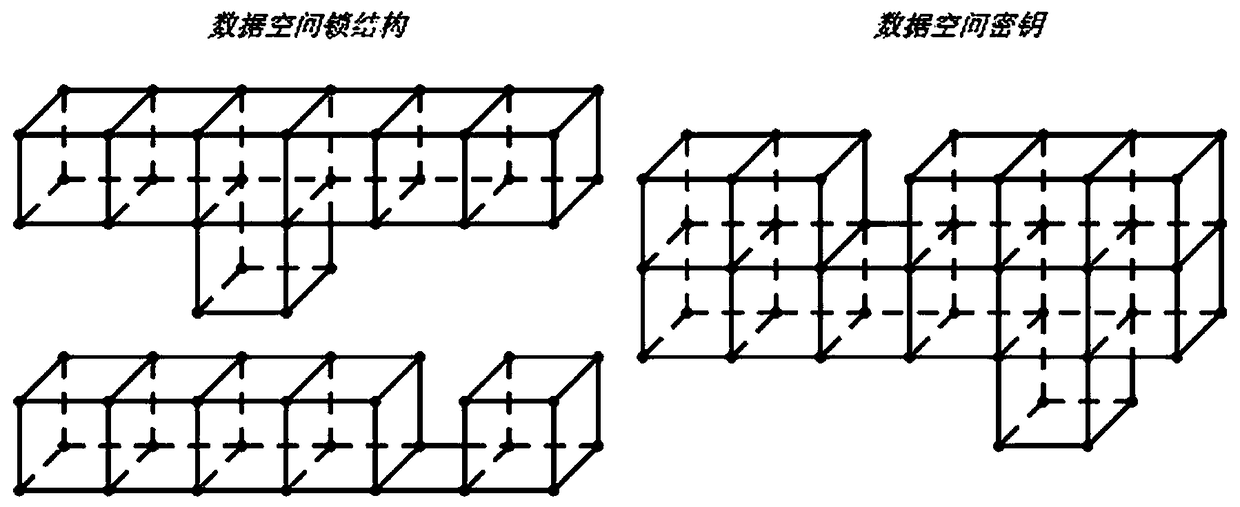
Key encryption system constructed by means of multidirectional technology
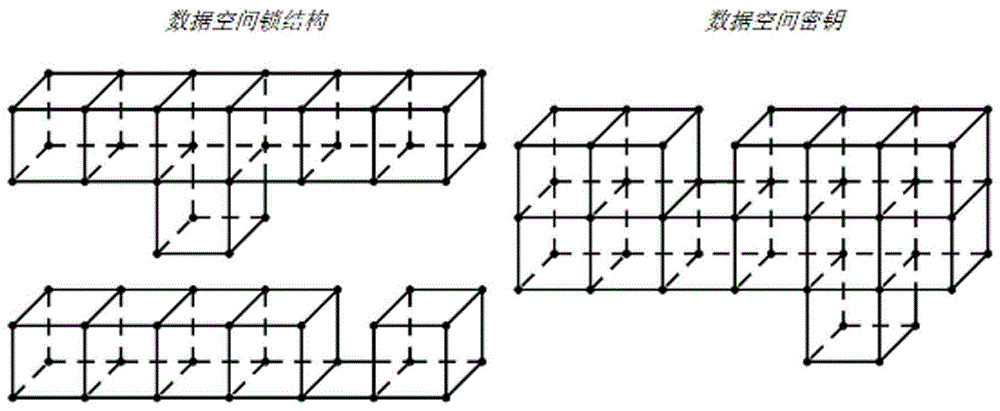
ActiveCN105959102AImprove securityEasy to operateKey distribution for secure communicationComputer hardwareData space
The invention discloses a key encryption system constructed by means of multidirectional technology. The key encryption system comprises the components of a data space module which is used for constructing and ordering to-be-encrypted data, the geometric structure of a data space lock and association among components; a component association module which utilizes interaction dimensions for managing operation and feedback among the components; a physical material module which manages the material and physical attribute of the component by means of the material physical dimension; and a decryption reduction module which starts a data decryption process when operation of the key satisfies an active state critical point rule of the data space lock, thereby rearranging the sequence of spatial data and realizing purposes of decryption and reducing original data. Compared with the prior art, the key encryption system which is constructed by means of the multidirectional technology has advantages of high safety degree, simple key memorization, convenient user operation, supporting user / manufacturer customizing of the encryption method, high encryption grade, cracking incapability, convenient use, high practicability and easy popularization.
Owner:INSPUR FINANCIAL INFORMATION TECH CO LTD
Remote encryption, decryption and writing processing method for MCU writer
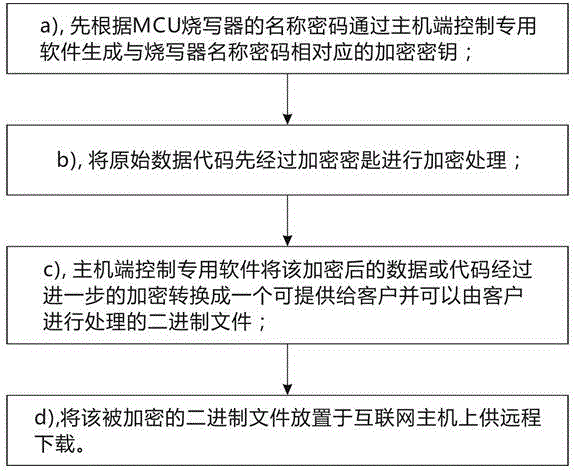
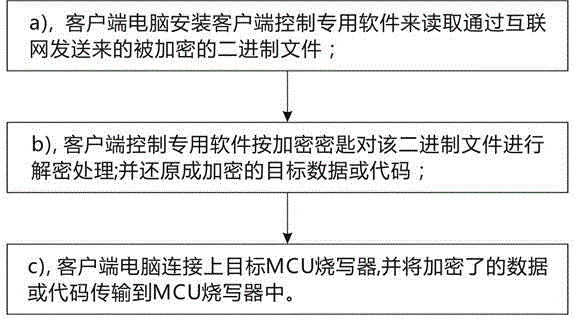
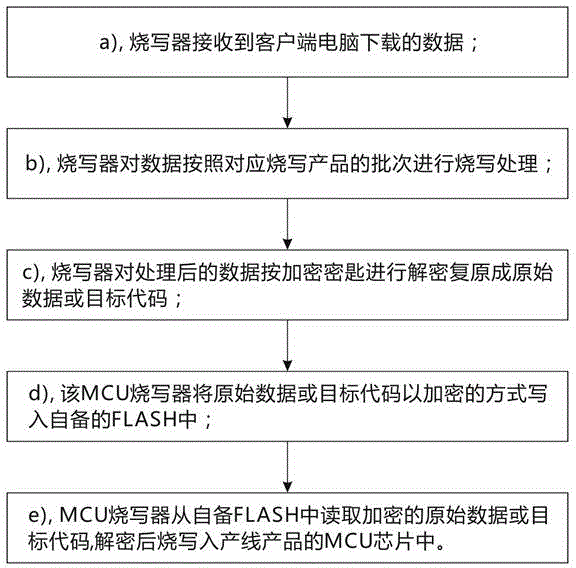
InactiveCN104683105AAvoid back-and-forth delivery of itemsImprove authorization operation efficiencyUser identity/authority verificationProgram/content distribution protectionOriginal dataPassword
The invention discloses remote encryption, decryption and writing processing methods for an MCU writer. The encryption method comprises the following steps: (a) generating an encryption key corresponding to a name password of the MCU writer by a host end special control software according to the name password of the writer; (b) firstly encrypting an original data code by the encryption key; (c) further encrypting the encrypted data or the code by the host end special control software, and converting into a binary file which can be provided for a client and can be processed by the client; (d) placing the encrypted binary file on an Internet host for remote downloading. By adoption of the host end special control software, a client end special control software and Internet transmission, remote encryption control of the MCU writer is realized; back-and-forth object express delivery of the MCU writer is avoided, and the authorization operating efficiency of the data code is greatly improved.
Owner:深圳市迈斯威志科技有限公司
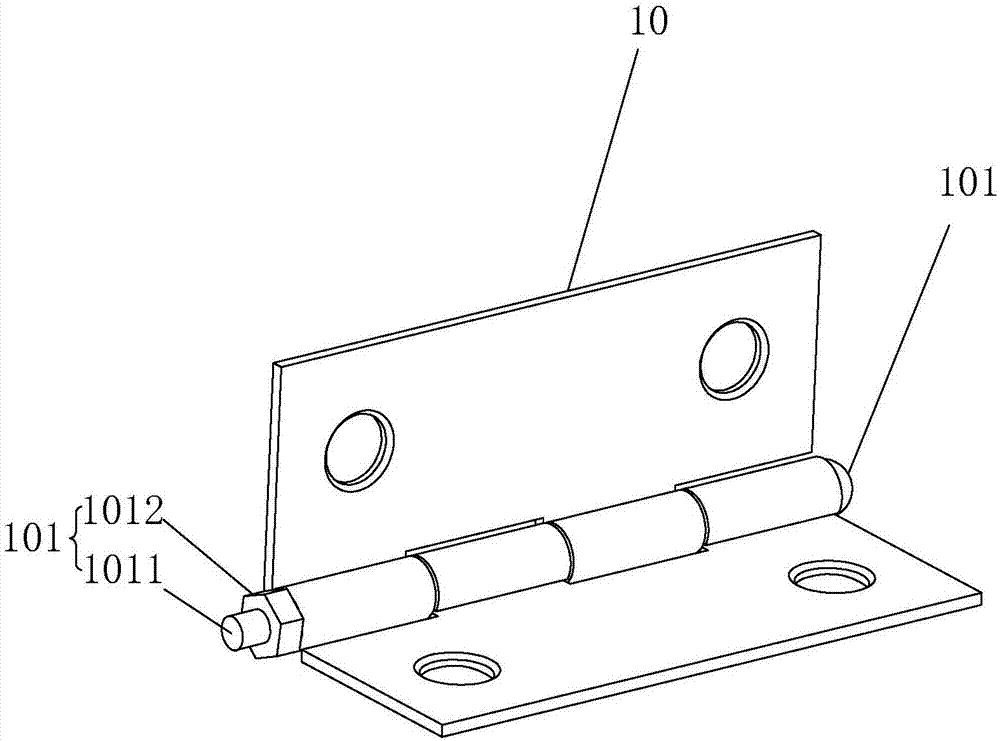
Combined anti-theft unpacking box and anti-theft unpacking method
InactiveCN107985727BCompact structureSimple structurePuzzle locksPermutation locksEngineeringStructural engineering
Owner:温胜洁
A method for encrypting and decrypting user privacy data on an Internet e-commerce platform
ActiveCN109583217BAvoid problemsAvoid gettingEncryption apparatus with shift registers/memoriesDigital data protectionPlaintextCiphertext
The invention discloses a method for encrypting privacy data of users on an Internet e-commerce platform, wherein a ciphertext key is encrypted and stored, comprising the following steps: generating a vector iv according to incoming original user data; The key is decrypted into a plaintext ciphertext key; through the plaintext ciphertext key and vector iv, the original user data byte stream is encrypted with the AES256 / CFB8 / NOPADDING algorithm to obtain the first encrypted string; base64 encoding to obtain the second encrypted string; concatenate E-, iv, and the second encrypted string in sequence to obtain the third encrypted string, and store the third encrypted string as encrypted data in the database. The invention encrypts the user privacy data, prevents leakage of the user privacy data information of the database system and improves processing efficiency.
Owner:SHENZHEN YIXUNTIANKONG INTERNET TECH CO LTD
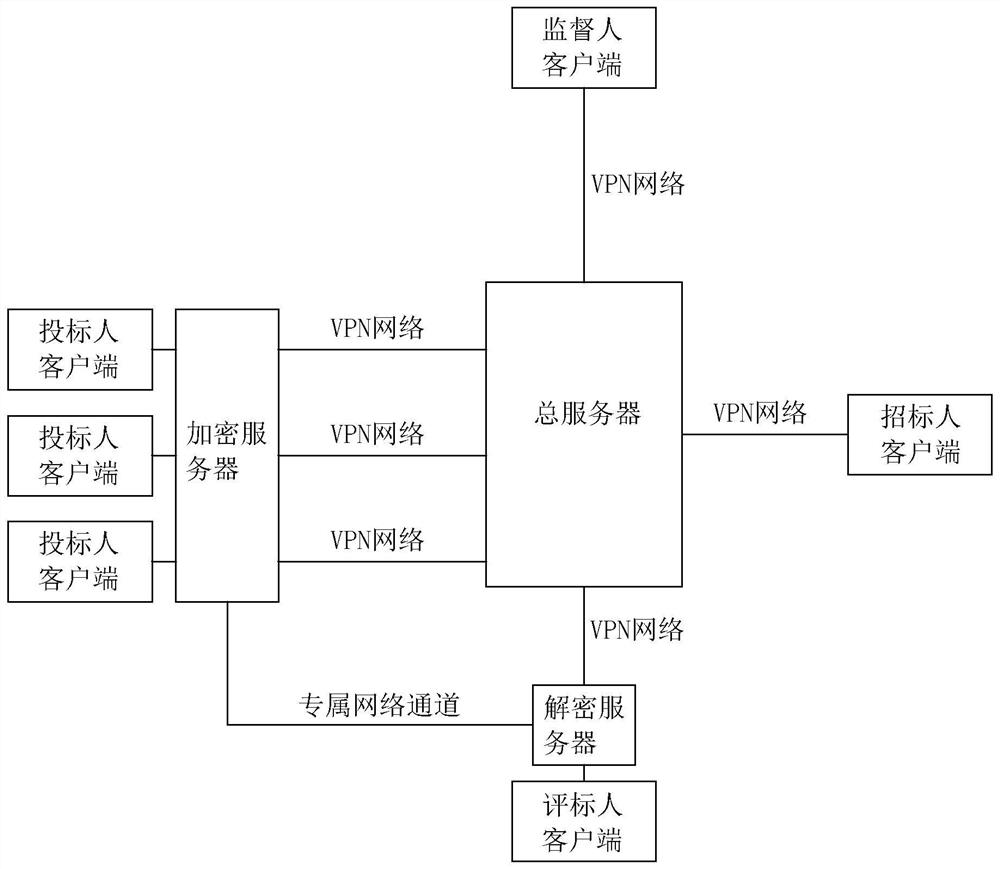
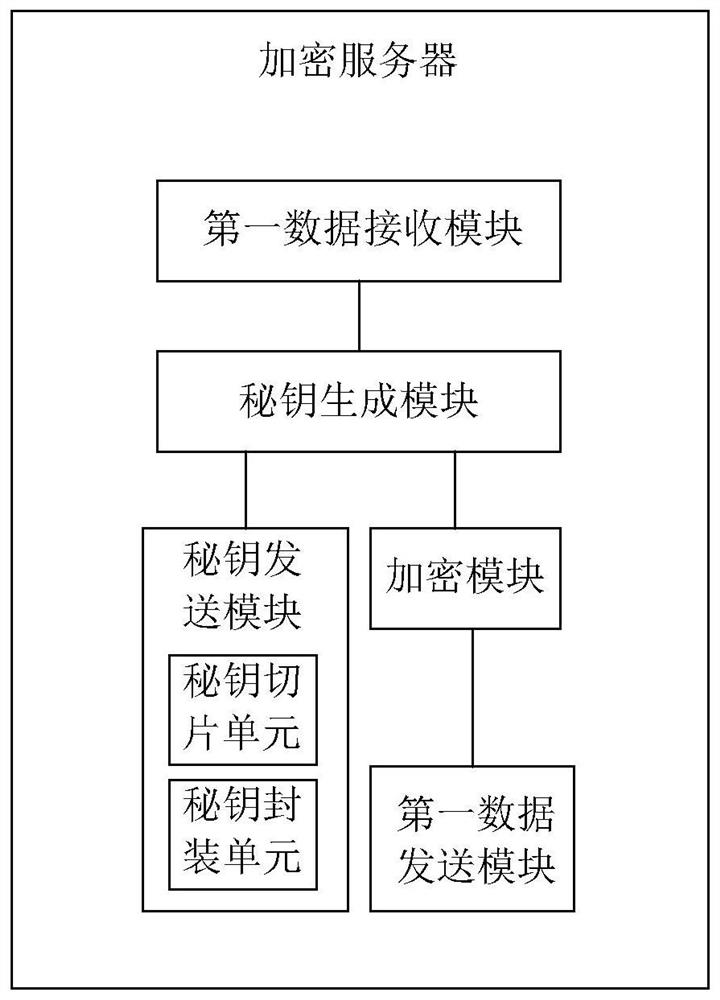
System and method for realizing electronic bidding and tendering encryption in VPN
InactiveCN112468514AImprove securityHigh encryption levelKey distribution for secure communicationBuying/selling/leasing transactionsInternet privacyNetwork connection
The invention relates to a system and a method for realizing electronic bidding and tendering encryption in a VPN, and relates to the field of electronic bidding and tendering, the system comprises atotal server, a bidder client, a bidder client, a bidder evaluator client and the VPN; the bidder client, the bidder client and the bidder evaluator client are connected to the VPN, and the VPN is connected to the total server; the system further comprises an encryption server and a decryption server, the encryption server is connected to the bidder client, the decryption server is connected to the bidder client, and the encryption server is used for generating an encryption key for the bidding file; the decryption server is used for decrypting the encrypted bidding file; and a transmission channel for transmitting a secret key is connected between the encryption server and the decryption server. The data transmission method and device have the effect of improving the safety of the data inthe transmission process.
Owner:天津普泽工程咨询有限责任公司
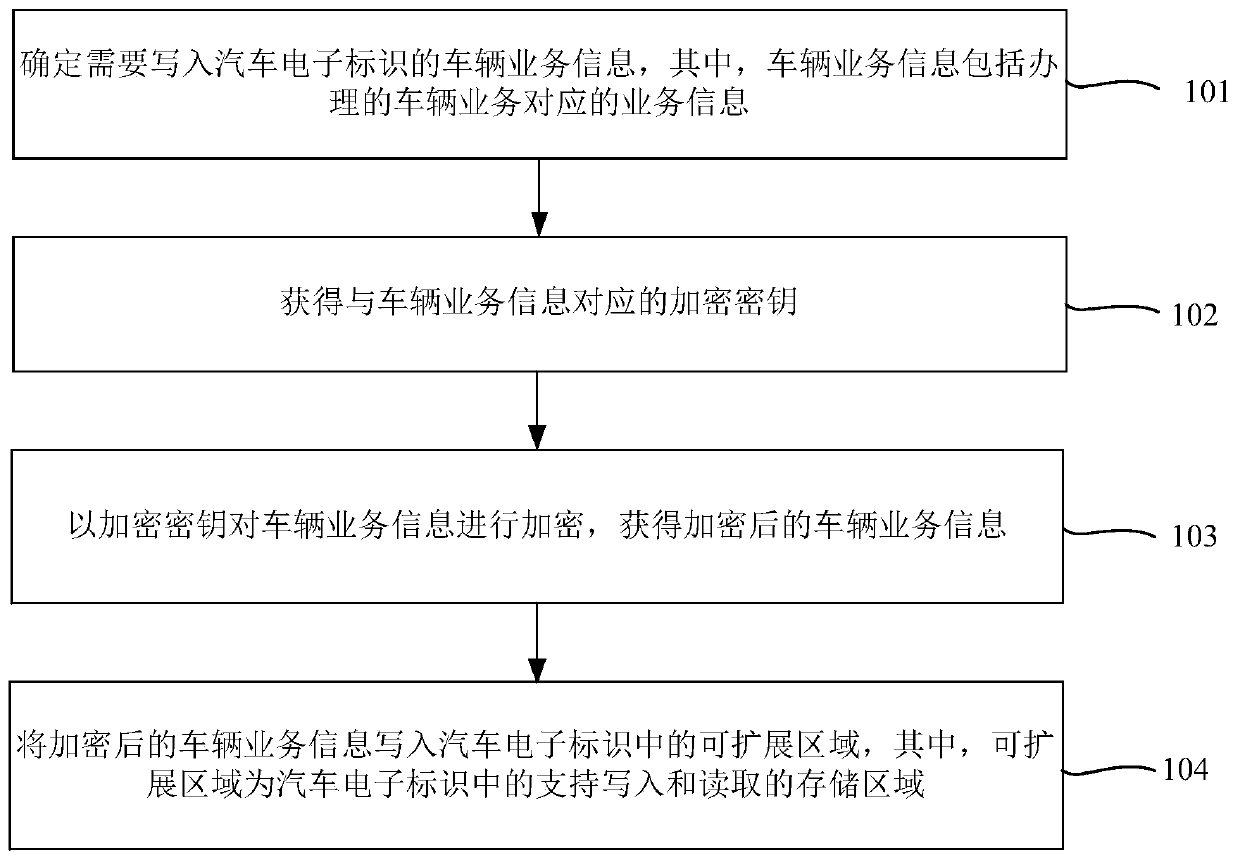
Method and device for writing vehicle service information and computing equipment
PendingCN111324896AReduce the possibility of leaksImprove securityDigital data protectionService informationEngineering
The invention discloses a method and a device for writing vehicle service information and computing equipment, which are used for improving the safety of the vehicle service information stored in an automobile electronic identifier. The method comprises the steps that vehicle service information needing to be written into an automobile electronic identifier is determined, and the vehicle service information comprises service information corresponding to a handled vehicle service; obtaining an encryption key corresponding to the vehicle service information; encrypting the vehicle service information by using the encryption key to obtain encrypted vehicle service information; and the encrypted vehicle service information is written into an extensible area in the automobile electronic identifier, and the extensible area is a storage area supporting writing and reading in the automobile electronic identifier.
Owner:AEROSPACE INFORMATION
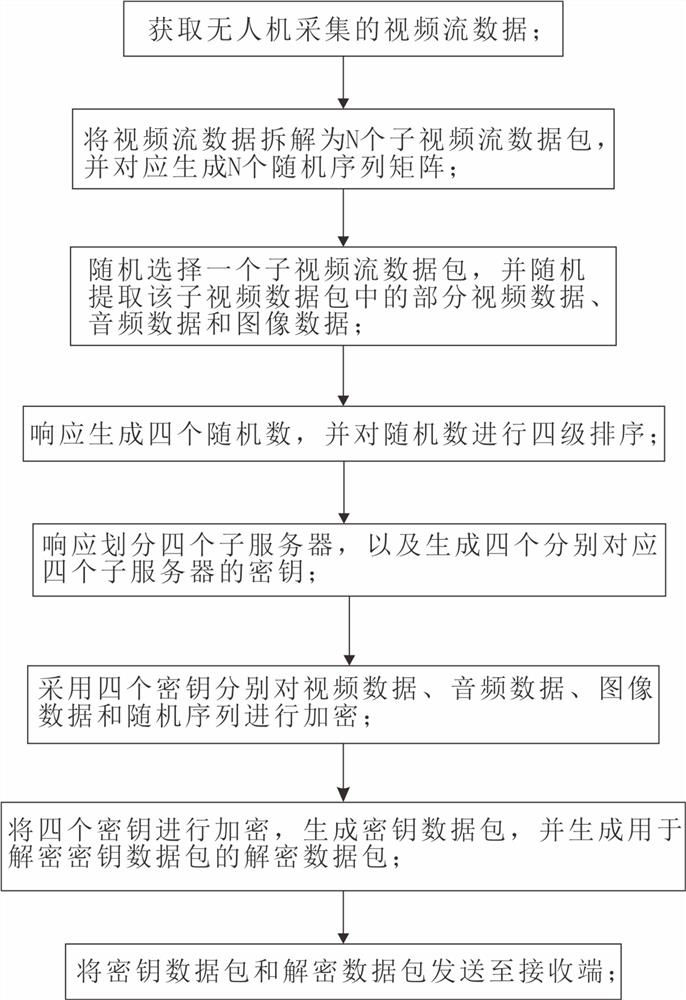
Encryption and multistage calibration method for streaming media of unmanned aerial vehicle
ActiveCN113783900AHigh encryption levelKey distribution for secure communicationStreaming dataData pack
The invention discloses an unmanned aerial vehicle streaming media encryption and multi-level calibration method; the method comprises the steps: carrying out the disassembly and packaging of video streaming data based on the video streaming data collected by an unmanned aerial vehicle, randomly extracting one sub-video transmission data package, and extracting a part of video data A1, audio data A2 and picture data A3 in the sub-video transmission data package; then correspondingly generating, by the server, a random sequence matrix Wn containing sub-video transmission data packet information, responding to generate random numbers of four levels and four sub-servers corresponding to the four levels, performing encryption on the four sub-servers according to the level arrangement, so that the current sub-server is removed only by adopting a secret key during decryption, and the next sub-server starts the unlocking state and can continue to decrypt by using the secret key. That is to say, the multi-level encryption and decryption operation is adopted, and the sub-video transmission data packets are in a random sequence, so that the encryption level is further enhanced.
Owner:四川格锐乾图科技有限公司
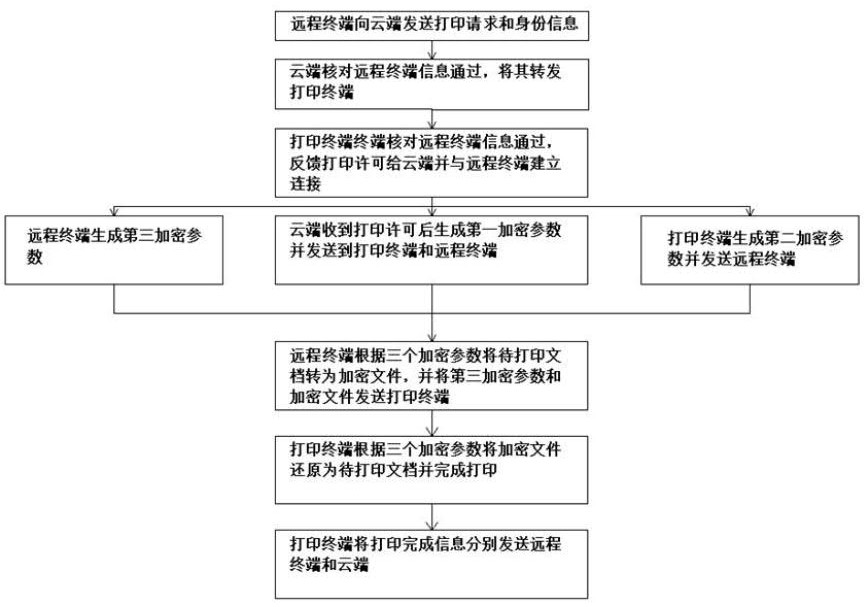
Cloud printing method, system and storage medium
Owner:北京辰光融信技术有限公司
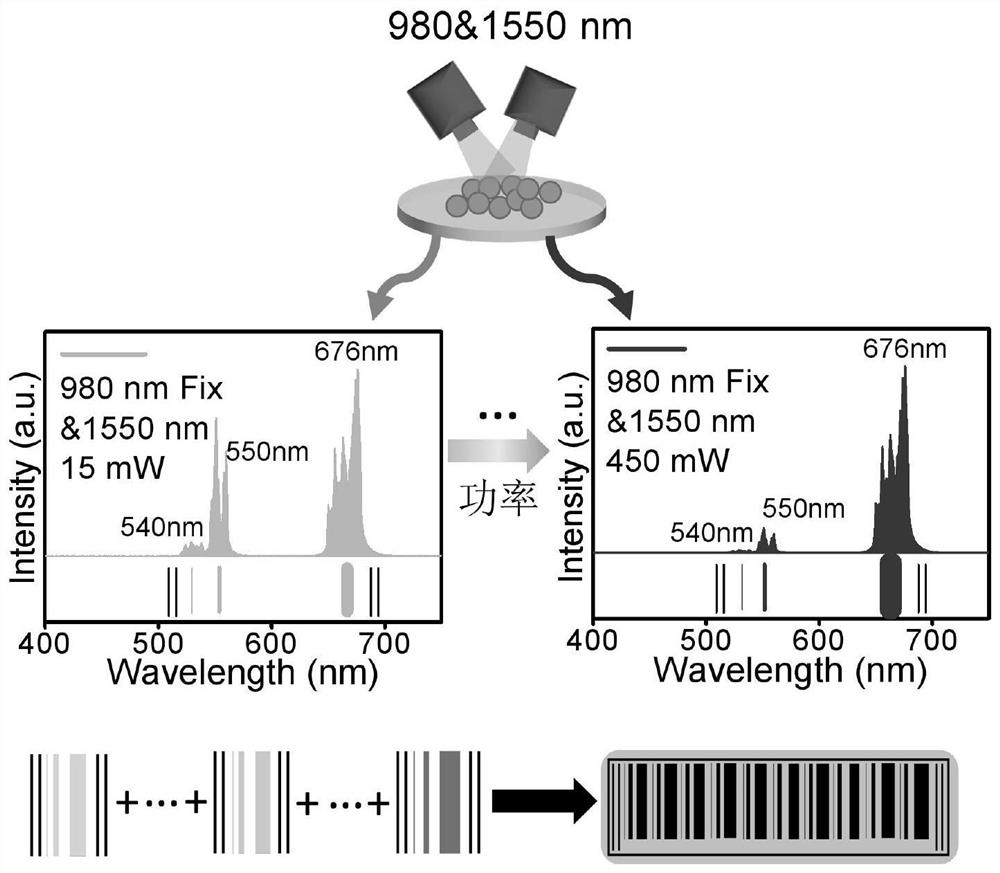
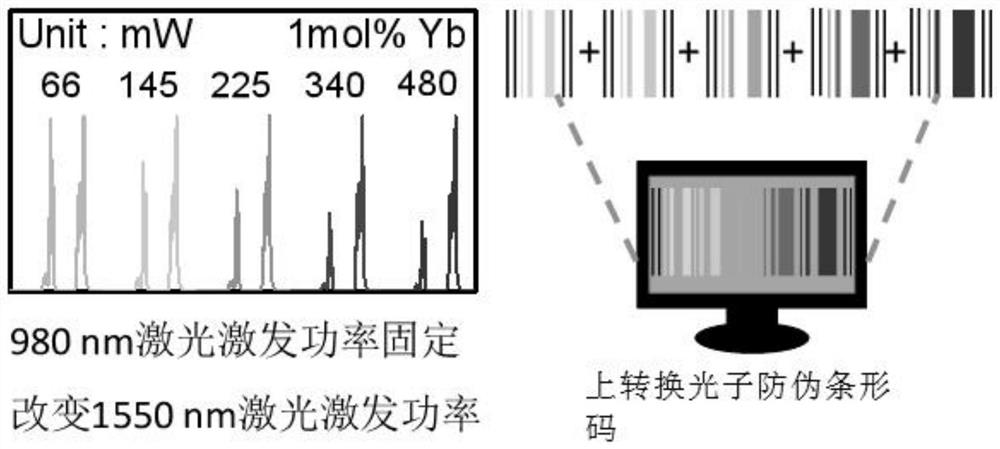
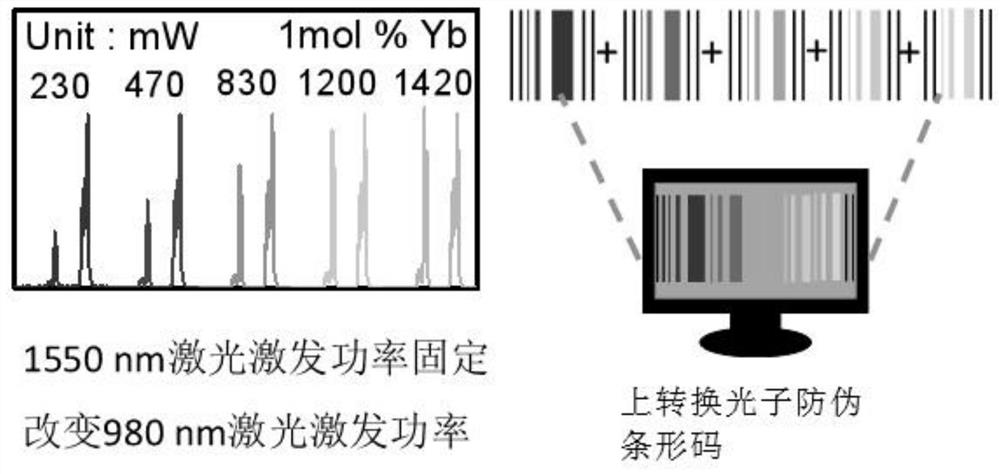
An anti-counterfeiting barcode based on dual-wavelength response up-conversion photons and its construction method and application
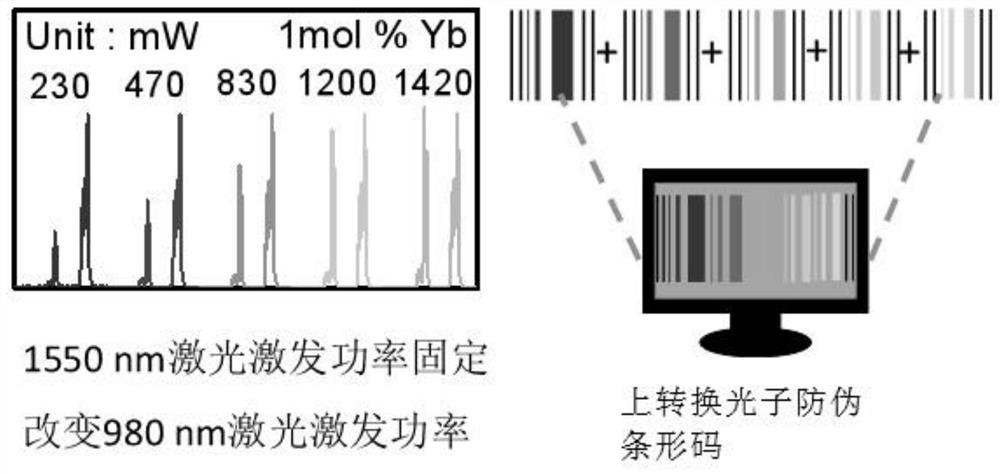
ActiveCN113255861BIncreased complexityLarge storage capacityRecord carriers used with machinesLuminous intensityEngineering
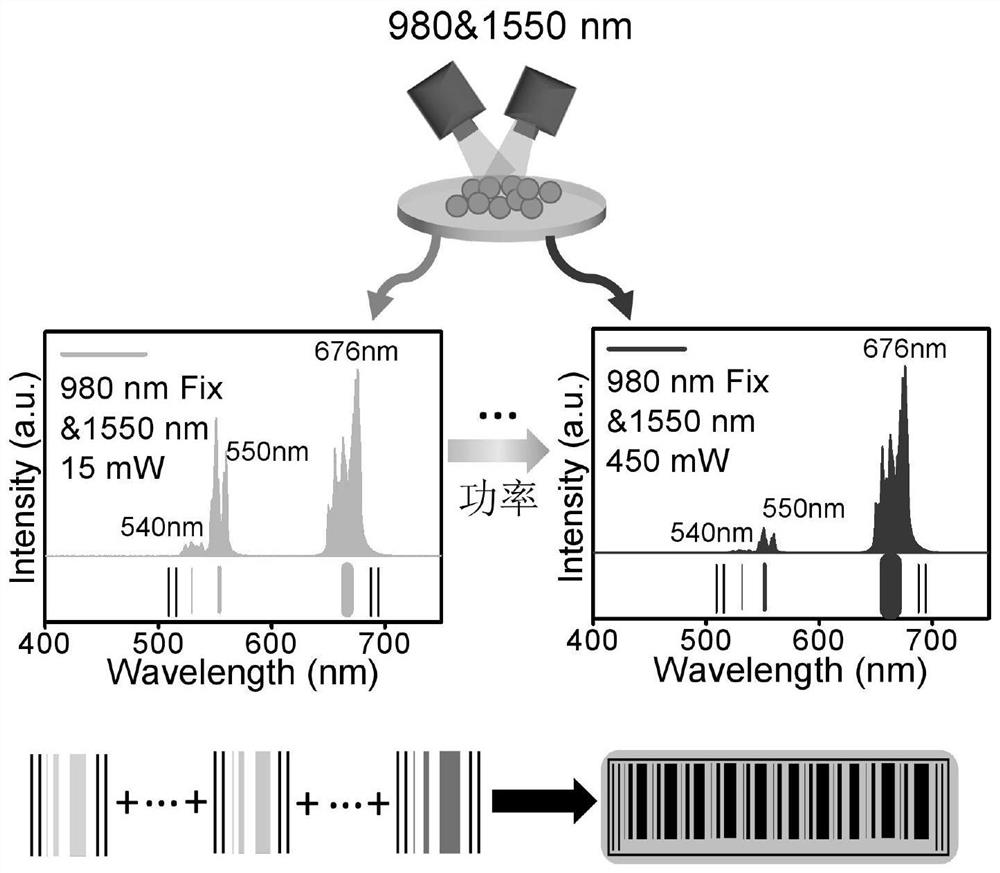
The invention provides an up-conversion photon anti-counterfeiting barcode based on dual-wavelength response, a construction method and application thereof, and belongs to the technical field of up-conversion anti-counterfeiting. The present invention adopts dual-wavelength near-infrared laser to jointly excite rare earth-doped up-conversion luminescent materials, and regulates the transition process of electrons in rare-earth ions by changing the excitation power of near-infrared laser to produce different luminous colors and luminous intensities. The luminous color and luminous intensity information of hybrid up-conversion luminescent materials are encoded as identification codes. Due to the fine and flexible adjustment of excitation power, rich spectral information can be obtained, and the corresponding up-conversion sub-barcode can be constructed from the obtained large amount of spectral information. , random combination of up-conversion sub-barcodes to obtain a complete up-conversion photonic anti-counterfeiting barcode, which can increase the complexity of information and bring greater flexibility to advanced anti-counterfeiting, large information storage capacity, high encryption level, greatly improving the coding ability and Security level.
Owner:YANSHAN UNIV
Data stream encryption method, data stream decryption method
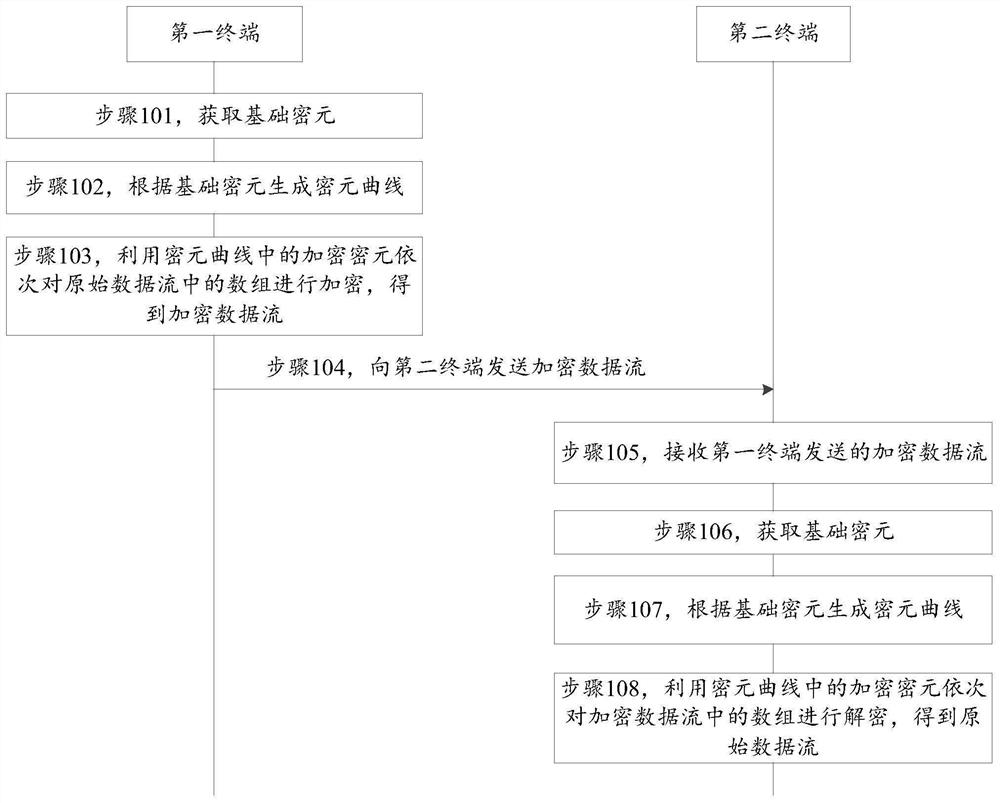
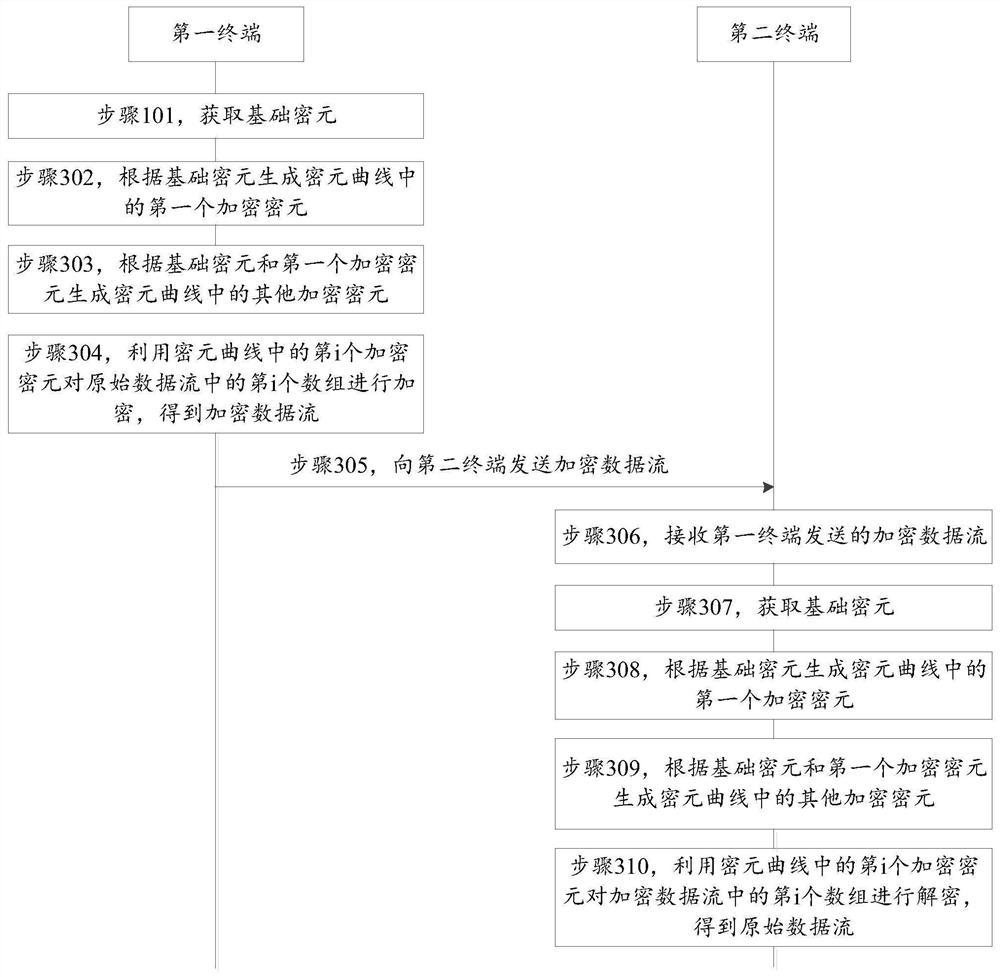
The present invention discloses a data stream encryption method, and a data stream decryption method, belonging to the field of information safety. The data stream decryption method comprises the steps of: obtaining basic encrypted elements; according to the basic encryption elements, generating an encrypted element curve, wherein the encrypted element curve comprises a plurality of encryption encrypted elements, the number of the encryption encrypted elements is identical with the number of arrays in the original data stream, and the first encryption encrypted element in the encrypted elementcurve is not a square number; employing the encryption encrypted elements to perform encryption of the arrays in the original data stream to obtain an encryption data stream; and sending the encryption data stream, allowing a first terminal and a second terminal to use the same basic encrypted elements. The problem is solved that the encryption speed is low or safety is not high when the data stream is encrypted, different encryption encrypted elements are used for each digit in the data stream to perform encryption, each encryption encrypted element is determined according to the basic encrypted elements so that a known encryption encrypted element is employed not to obtain other encryption encrypted elements, and therefore, the encryption grade can be improved while reduction of the operation data size, and the safety of the data stream is ensured.
Owner:无锡润盟软件有限公司
a method of information transmission
ActiveCN107294964BHigh encryption levelImprove the leakage levelKey distribution for secure communicationUser identity/authority verificationComputer hardwareGraphics
The embodiment of the present invention discloses an information transmission method, wherein the information transmission method is applied to a server, including: obtaining the sending information of the first terminal, encrypting the sending information, and generating an object code map, wherein the The sent information includes at least one of plaintext information, sensitive information, and secret information, and the object code map carries graphic encoding information and a digital signature of the graphic encoding information with the private key of the security code generation system, or the first Digitally signing the graphic encoding information with the terminal private key; returning the object code map to the first terminal, so that the first terminal sends the object code map to at least one corresponding second terminal. An information transmission method in an embodiment of the present invention realizes the improvement of security and privacy of information transmission.
Owner:BEIJING D9ING INST OF INFORMATION ENG CO LTD +1
Safe Box Based on Network Intelligent Wireless Control System
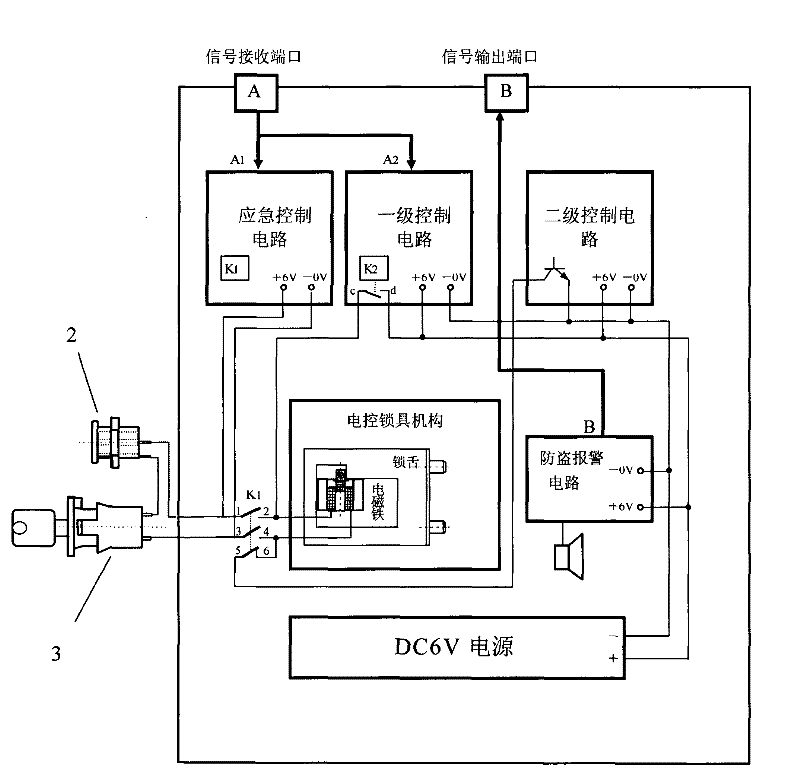
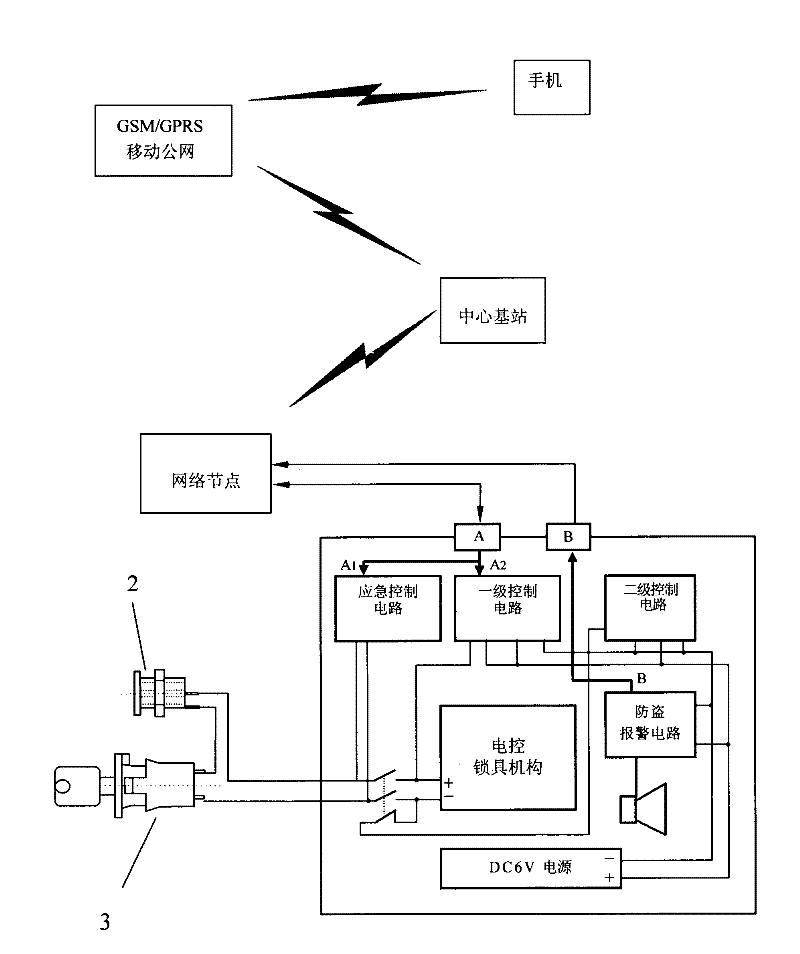
InactiveCN101775942BHigh encryption levelImprove securityNon-mechanical controlsElectric permutation locksIntelligent NetworkWireless control
The invention relates to a safe based on a network intelligent wireless control system, which includes a signal receiving port capable of receiving control signals, a primary control circuit, a secondary control circuit, an electronically controlled lock mechanism, an emergency control circuit, an emergency power socket and a power supply Lock and power supply, the signal receiving port is respectively connected with the primary control circuit and the emergency control circuit, the primary control circuit is connected with the power supply and the electric control lock mechanism respectively, the secondary control circuit is connected with the power supply and the electric control lock mechanism respectively, and the emergency control circuit It is connected with the electric control lock mechanism, one end of the emergency power socket is connected with one end of the power lock, the other end is connected with the emergency control circuit through the connection line, and the other end of the power lock is connected with the emergency control circuit through the connection line. This kind of safe based on the network intelligent wireless control system has high encryption level and good security.
Owner:邱柏康
Key disk for separating storage and restoring data and method for separating and restoring data
ActiveCN105184185BPrevent leakageEffective Document Leakage Prevention Management MeasuresDigital data protectionElectronic documentUSB
Owner:丽水至行科技有限公司
A Key Encryption System Using Multidimensional Technology
ActiveCN105959102BImprove securityEasy to operateKey distribution for secure communicationComputer hardwareData space
The invention discloses a key encryption system constructed by means of multidirectional technology. The key encryption system comprises the components of a data space module which is used for constructing and ordering to-be-encrypted data, the geometric structure of a data space lock and association among components; a component association module which utilizes interaction dimensions for managing operation and feedback among the components; a physical material module which manages the material and physical attribute of the component by means of the material physical dimension; and a decryption reduction module which starts a data decryption process when operation of the key satisfies an active state critical point rule of the data space lock, thereby rearranging the sequence of spatial data and realizing purposes of decryption and reducing original data. Compared with the prior art, the key encryption system which is constructed by means of the multidirectional technology has advantages of high safety degree, simple key memorization, convenient user operation, supporting user / manufacturer customizing of the encryption method, high encryption grade, cracking incapability, convenient use, high practicability and easy popularization.
Owner:INSPUR FINANCIAL INFORMATION TECH CO LTD
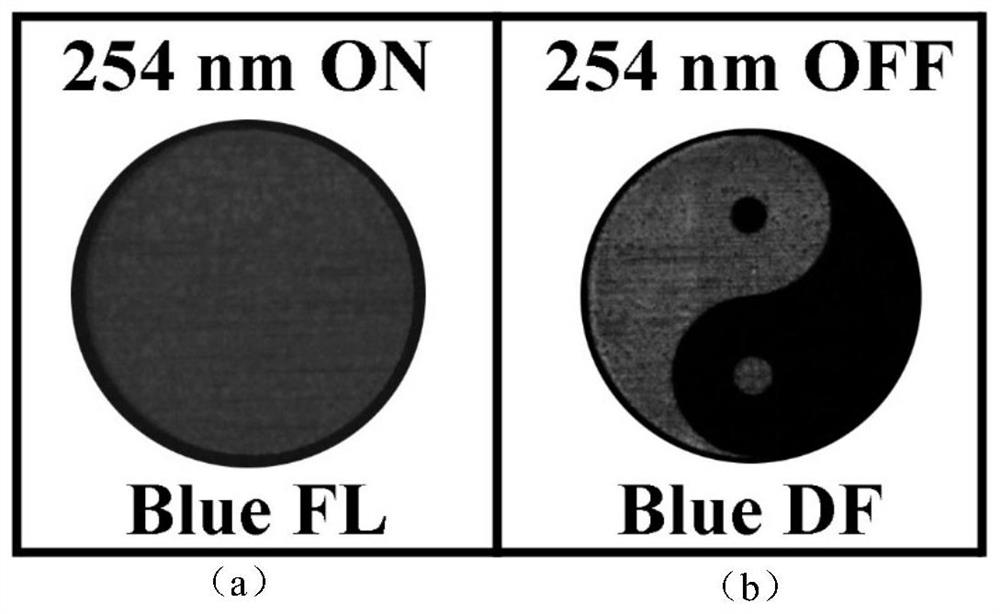
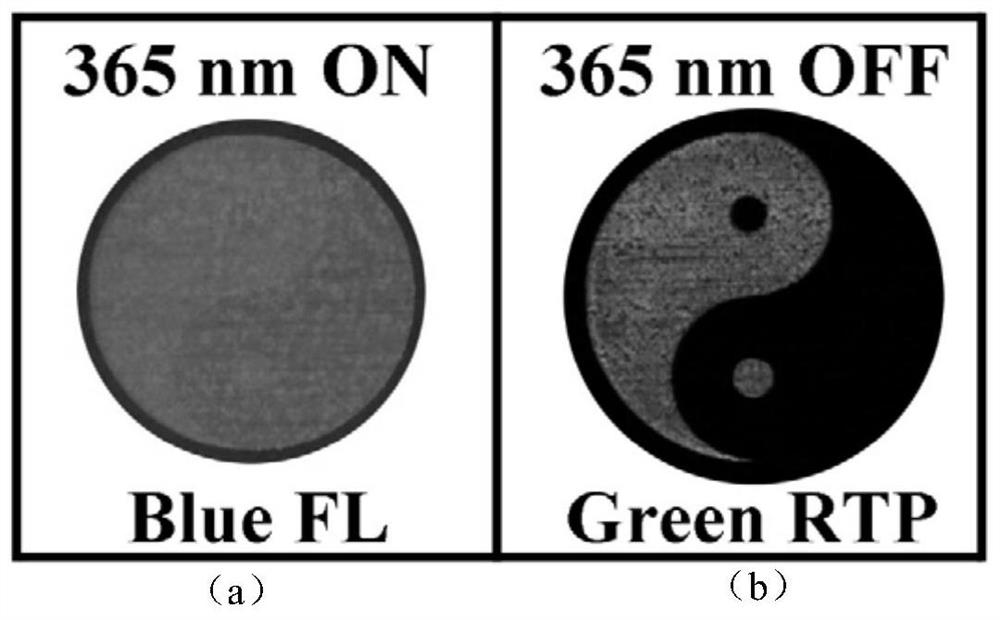
Triple optical anti-counterfeiting ink with fluorescence, delayed fluorescence and room temperature phosphorescence and anti-counterfeiting method and application
InactiveCN109294331BImprove anti-counterfeitingGood dispersionStampsInksOrganic solventComputer printing
Owner:XIAMEN UNIV
Database data encryption and decryption method and system based on database connection pool
ActiveCN109960942BStrong expandabilityImprove efficiencyDigital data information retrievalDigital data protectionTheoretical computer scienceConnection pool
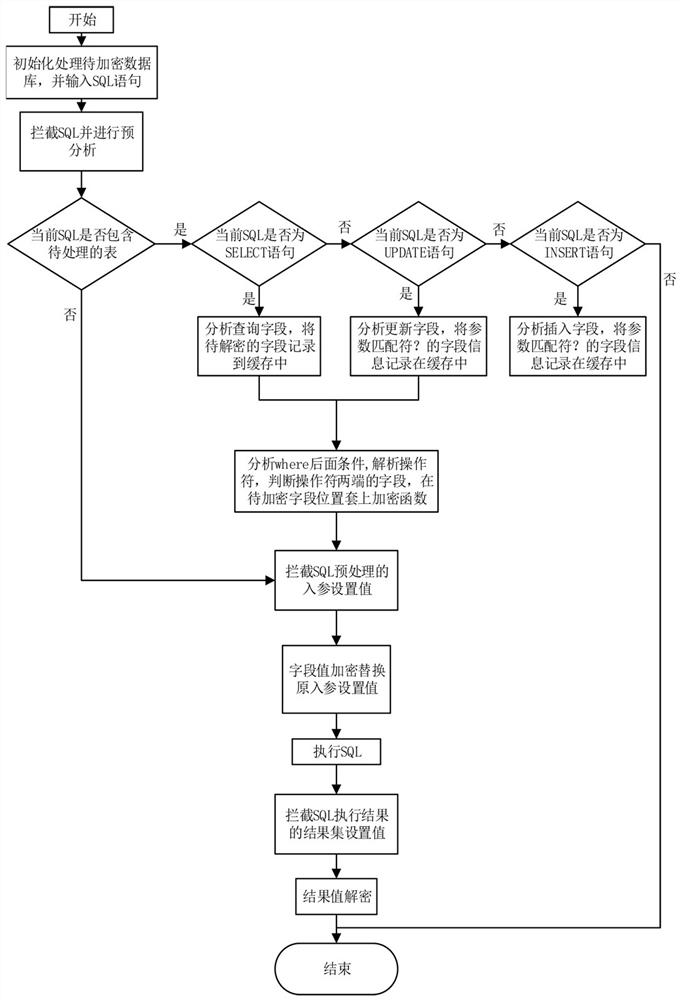
The present invention relates to a database data encryption and decryption method and system based on a database connection pool. By directly performing encryption and decryption on the data access layer (JDBC), the characteristics of SQL to be executed and input parameters can be obtained in the JDBC layer, and SQL execution can be automatically analyzed. Statements, interception, encryption, decryption, and conversion of statements, and execution of SQL actions. In this way, the function of embedding encryption and decryption of sensitive data into the system can be realized without manually modifying the original SQL in a large area. And it is similar to the SQL execution statement, no need to repeat the test, as long as there is a correct analysis, it can be considered that the similar SQL can also be executed correctly, high efficiency, small changes to the original system, and less workload.
Owner:厦门商集网络科技有限责任公司
A smart password key with local data encryption function
ActiveCN105447394BAdd application functionsImprove practicalityDigital data protectionMass storagePassword
The invention discloses an intelligent password key with a local data encryption function. The intelligent password key comprises an encryption chip, a storage chip connected with the encryption chip, a power circuit, a connecting interface and a peripheral device, wherein the encryption chip is a microprocessor integrating a processor, input and output ports and a memory; the large-capacity storage chip is an NAND Flash chip, is provided with an NAND Flash controller and is connected with an external Flash to finish local data encryption storage; the power circuit is connected with a main control chip and the large-capacity memory, and monitors and provides a stable power supply; the connecting interface is connected with a local computer; and the peripheral device comprises an LED indication lamp and is connected with the encryption chip to indicate a working state of a USB Key. Compared with the prior art, the intelligent password key with the local data encryption function can serve as an encryption / decryption hardware key to encrypt / decrypt mass data of a PC end; and only a same encryption U disk can be used for encrypting / decrypting local data, so that the security is improved and the practicality is high.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
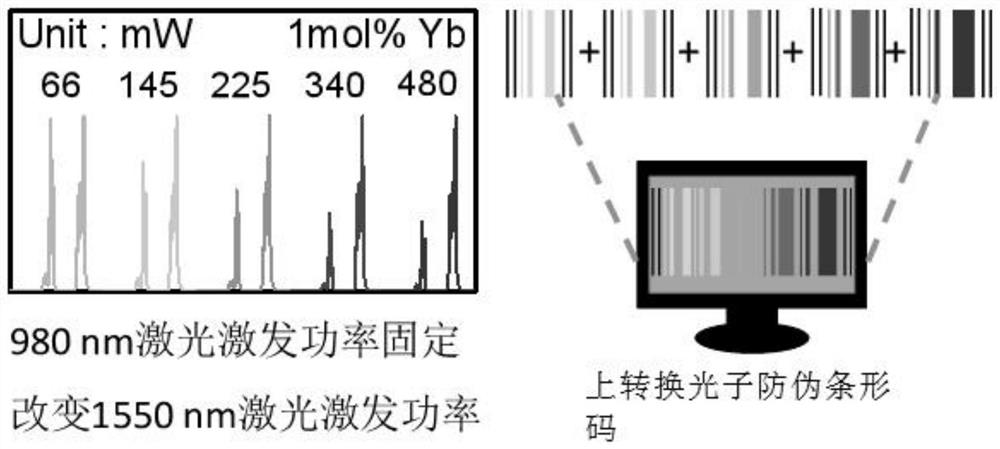
Upconversion photon anti-counterfeiting bar code based on dual-wavelength response and construction method and application thereof
ActiveCN113255861AIncreased complexityLarge storage capacityRecord carriers used with machinesLuminous intensityEngineering
The invention provides an up-conversion photon anti-counterfeiting bar code based on dual-wavelength response and a construction method and application thereof, and belongs to the up-conversion anti-counterfeiting technical field. According to the present invention, a near-infrared laser dual-wavelength is adopted to jointly excite a rare earth doped up-conversion luminescent material, and the transition process of electrons in rare earth ions is regulated and controlled by changing the excitation power of the near-infrared laser, so that different luminescent colors and luminescent intensities are generated; and the luminescent color and the luminescent intensity information of the rare earth doped up-conversion luminescent material are used as the identification codes for coding. Due to fine and flexible adjustment of excitation power, rich spectral information can be obtained; and by constructing a large amount of obtained spectral information into the corresponding up-conversion sub-bar codes, the up-conversion sub-bar codes are randomly combined to obtain the complete up-conversion photon anti-counterfeiting bar codes, so that the complexity of information can be increased, higher flexibility is brought to advanced anti-counterfeiting, the information storage capacity is large, the encryption level is high, and the coding capacity and the anti-counterfeiting level are greatly improved.
Owner:YANSHAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com