Key encryption system constructed by means of multidirectional technology
A technology of key encryption and technology, applied in the field of information security, can solve problems such as the inability to meet the requirements of Internet data transmission security, the security can no longer be guaranteed, and the reliability of encryption algorithms. , the effect of high safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
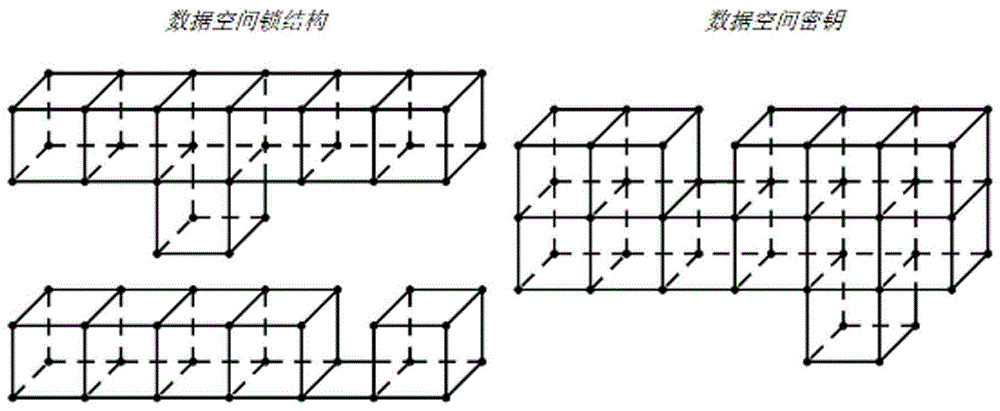
[0037] as attached figure 1 As shown, the present invention uses multi-dimensional technology to build a key encryption system, which completely disrupts the transmission rules of ordinary binary computer data streams through the original spatial geometric data structure, thereby fundamentally solving the problem of traditional key encryption methods. The problem of being easily cracked is an effective guarantee for the security of Internet data transmission.
[0038] Its specific structure includes:
[0039] Data space module, which is used to construct and sort the data to be encrypted and the geometric structure of the data space lock, as well as the relationship between the components;
[0040] The component association module uses the interactive interaction dimension to manage the operation and feedback between components;
[0041] The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com