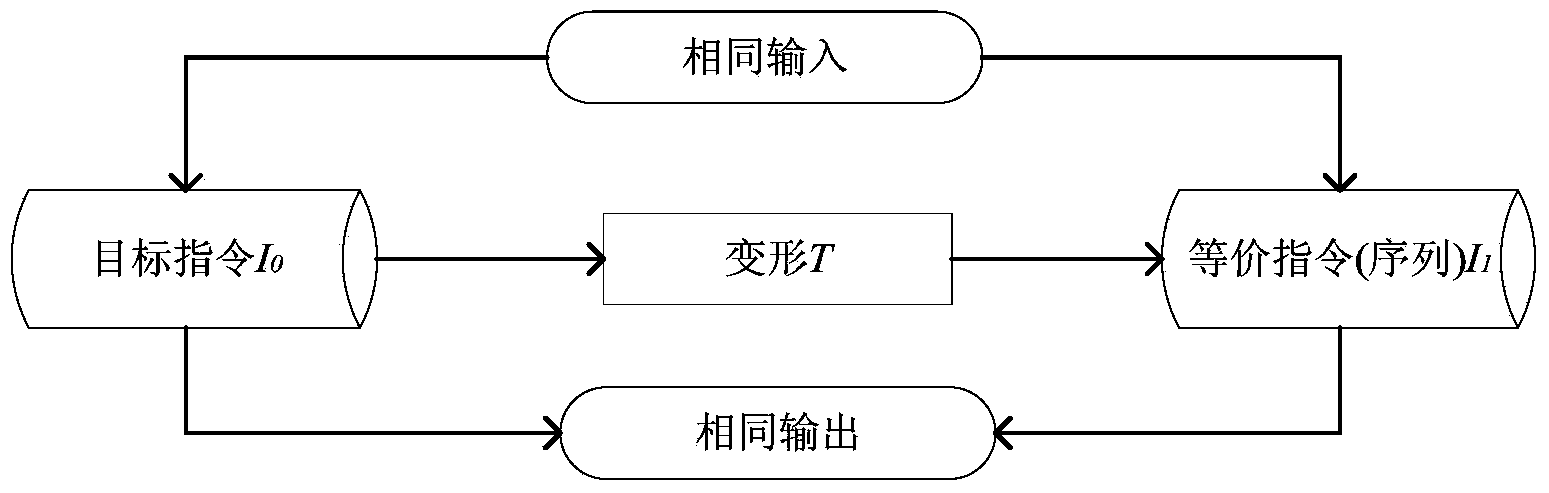
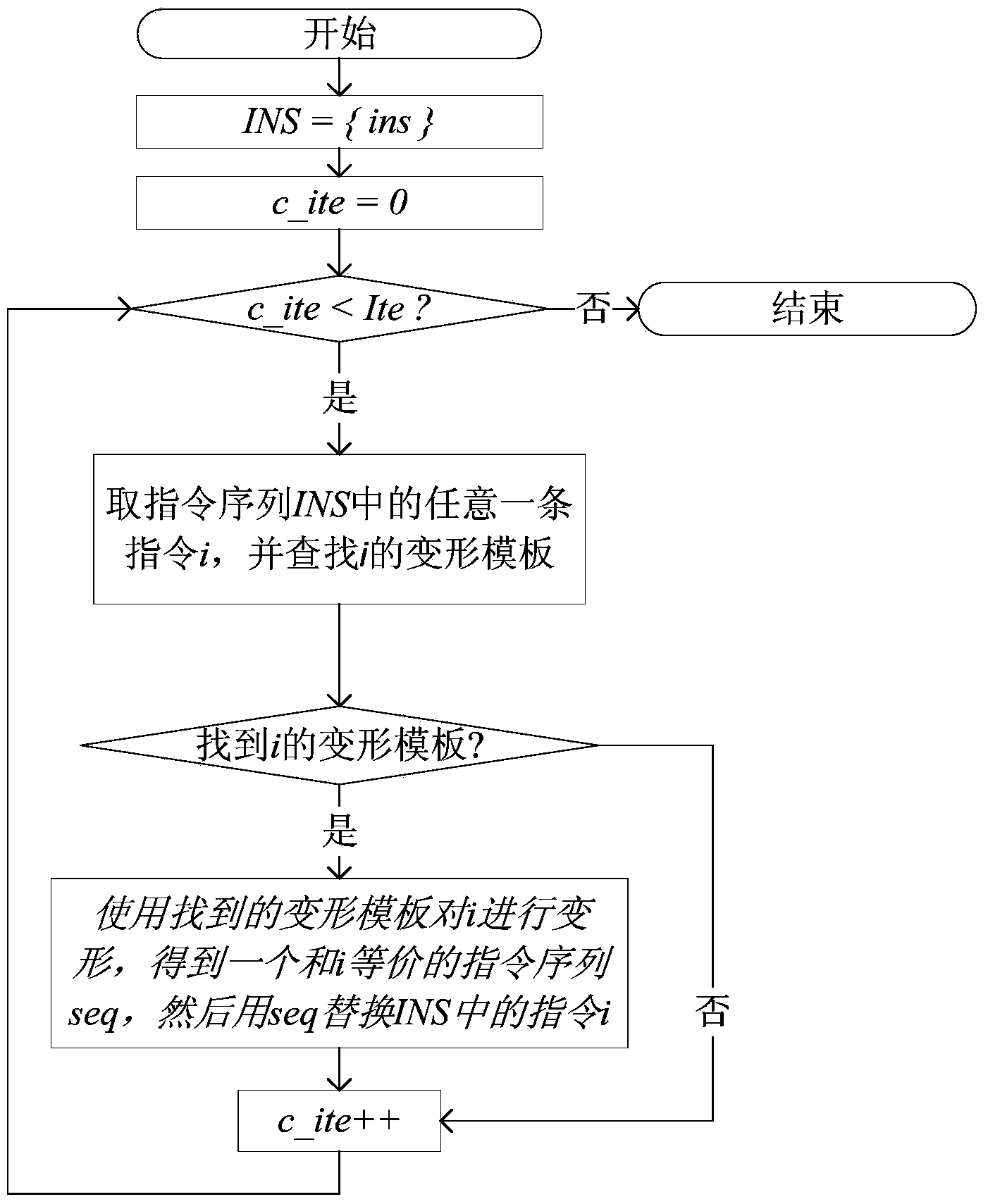
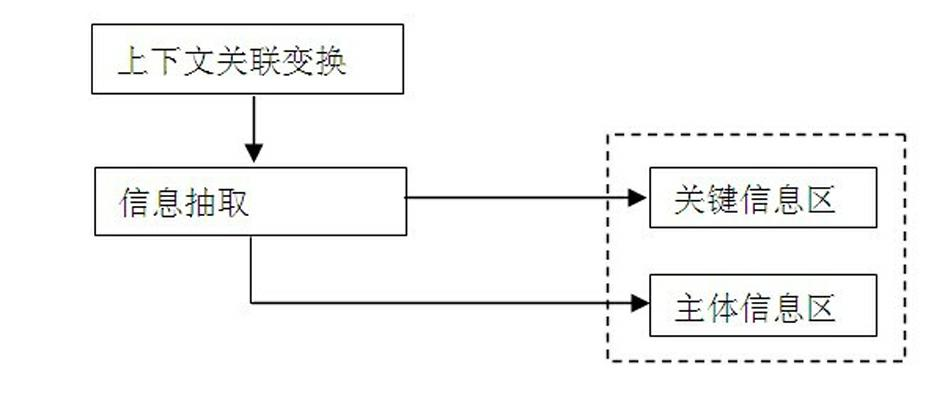
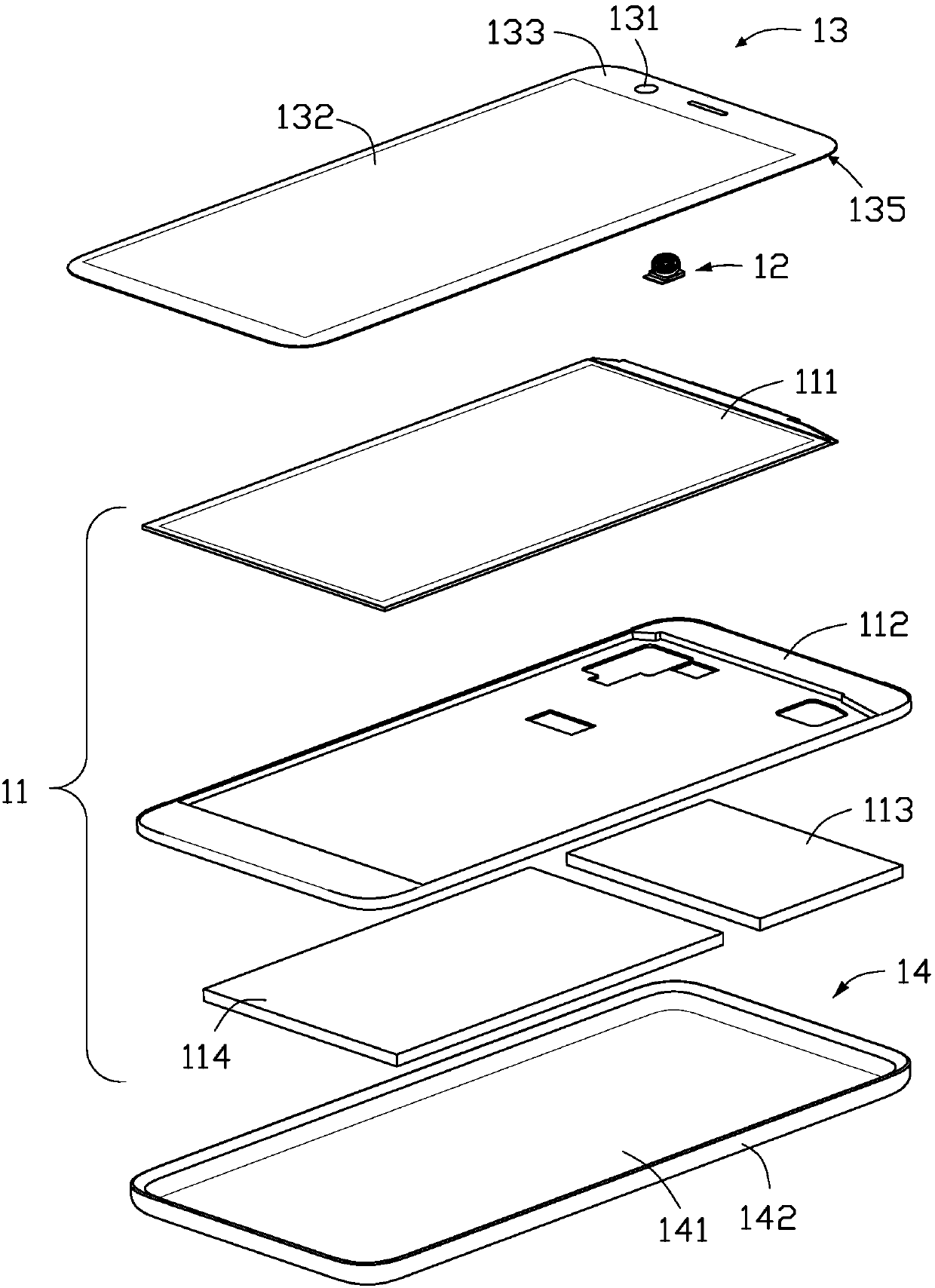
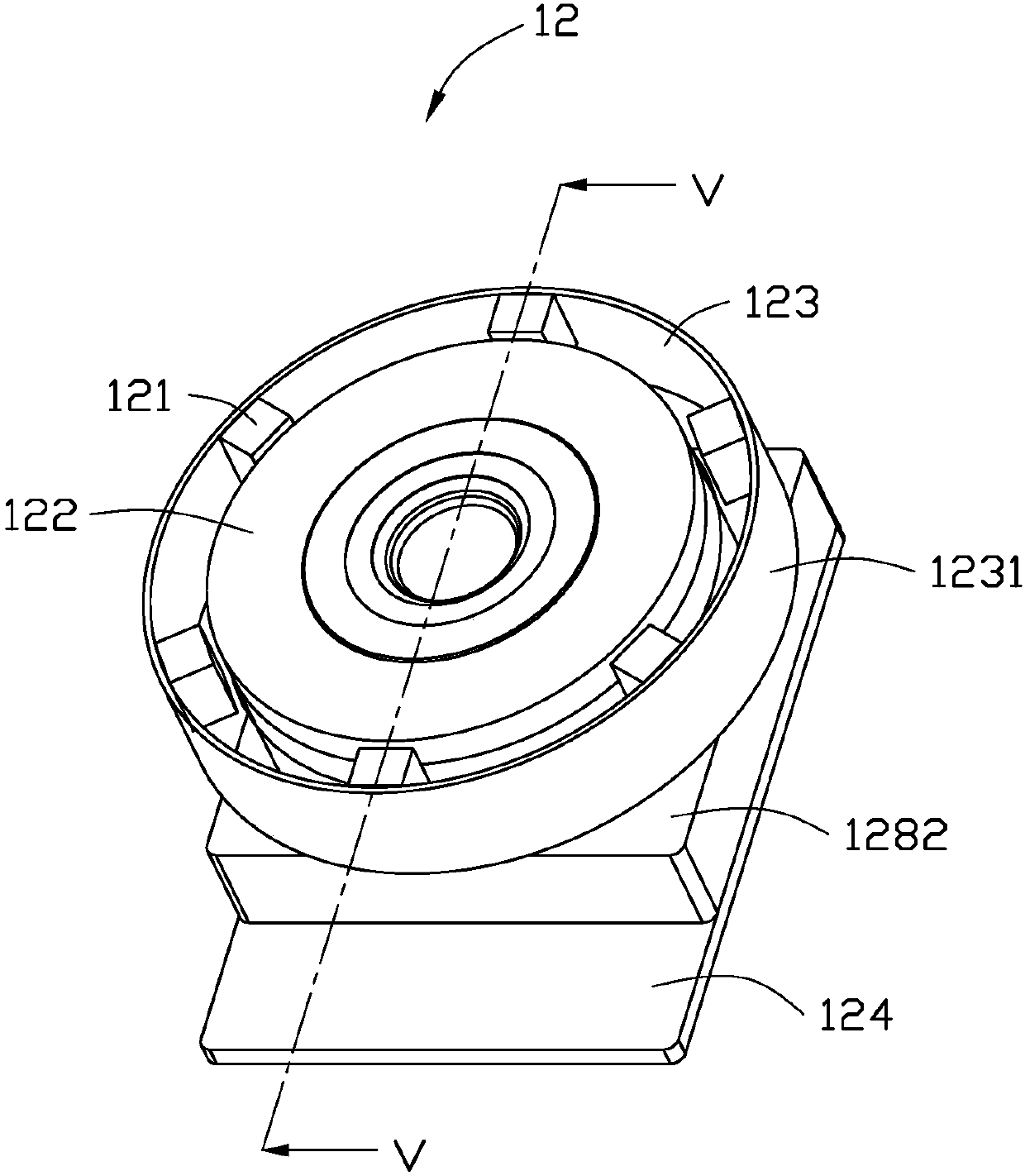
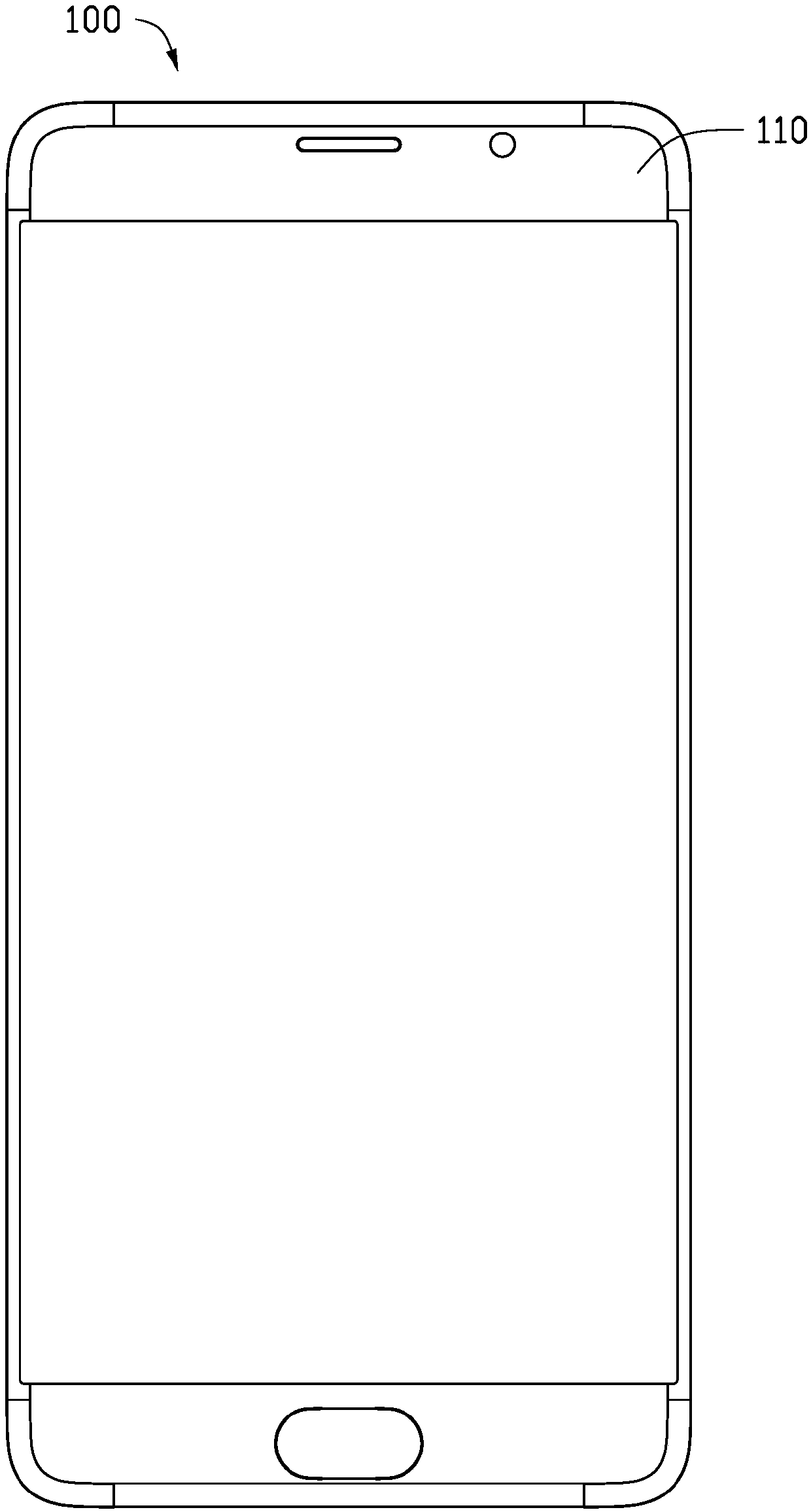
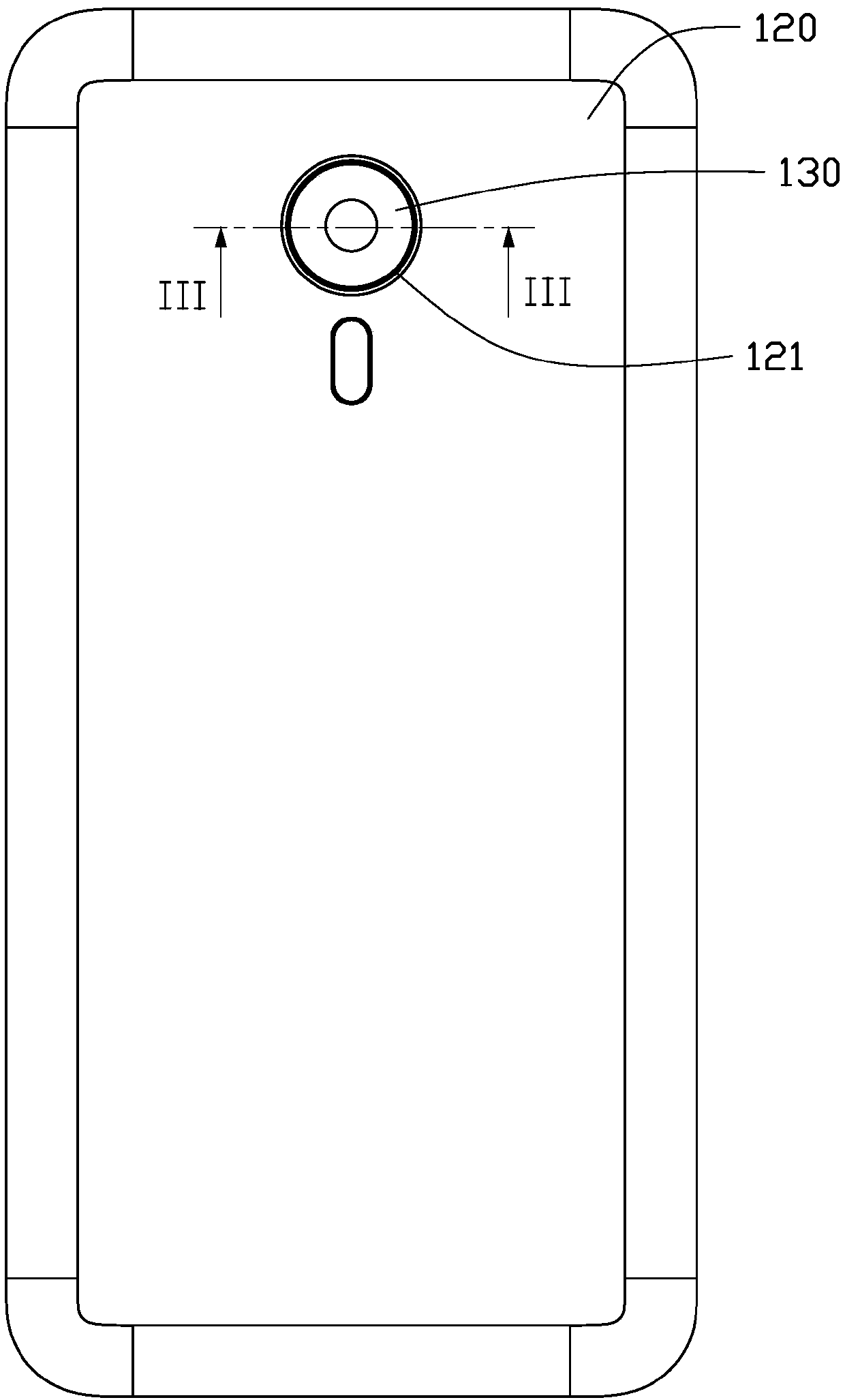
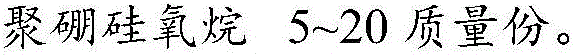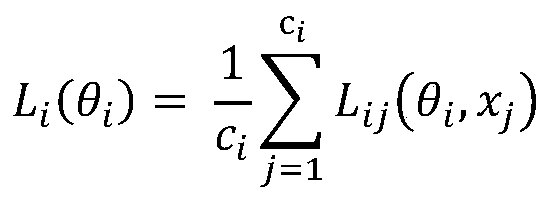Patents
Literature
261results about How to "Improve protection strength" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
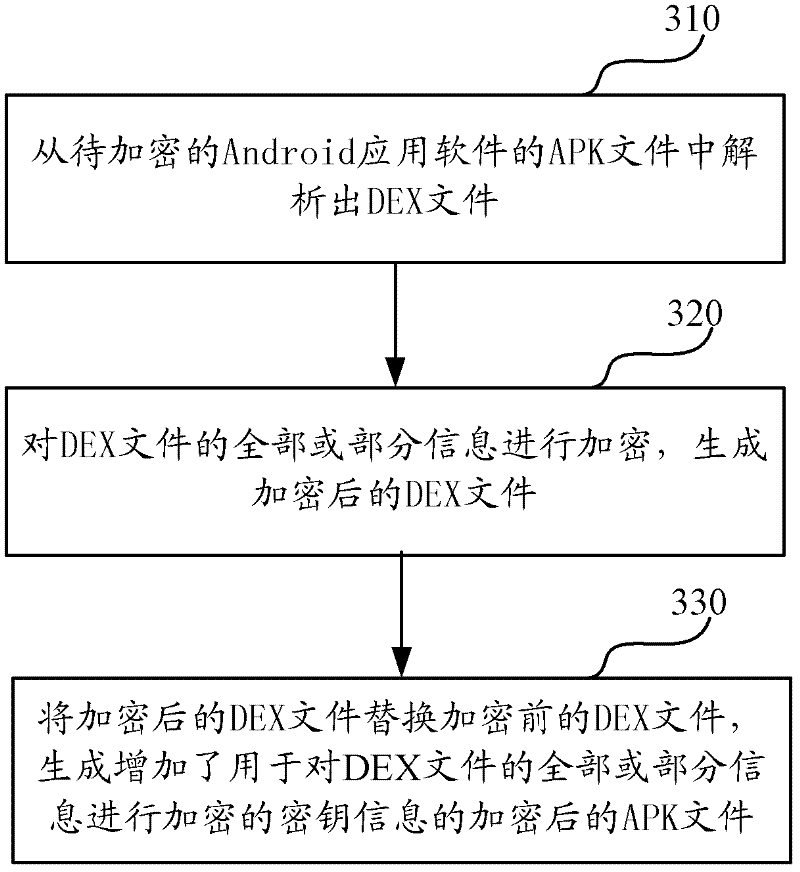
Software protection method and system applicable to Android system
InactiveCN102236757AImprove protectionImprove execution efficiencyProgram/content distribution protectionByteSoftware protection
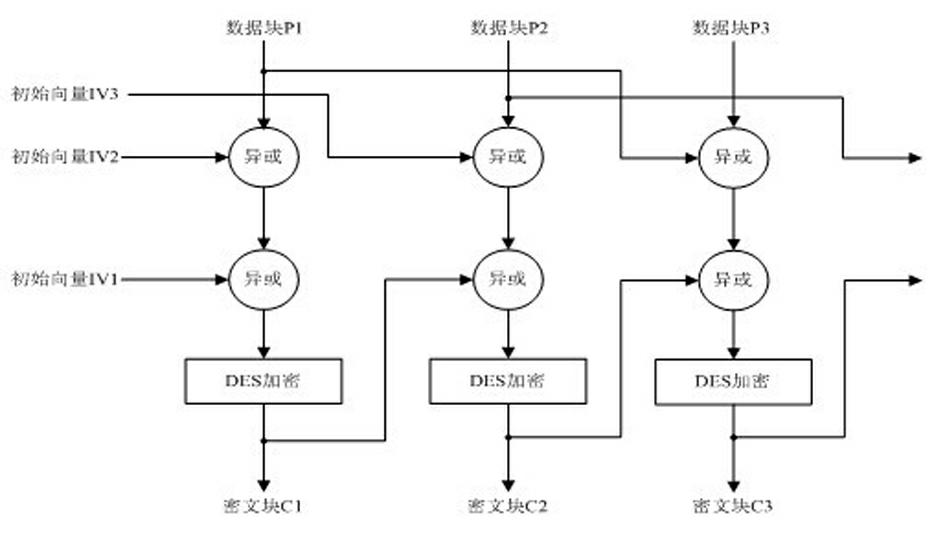
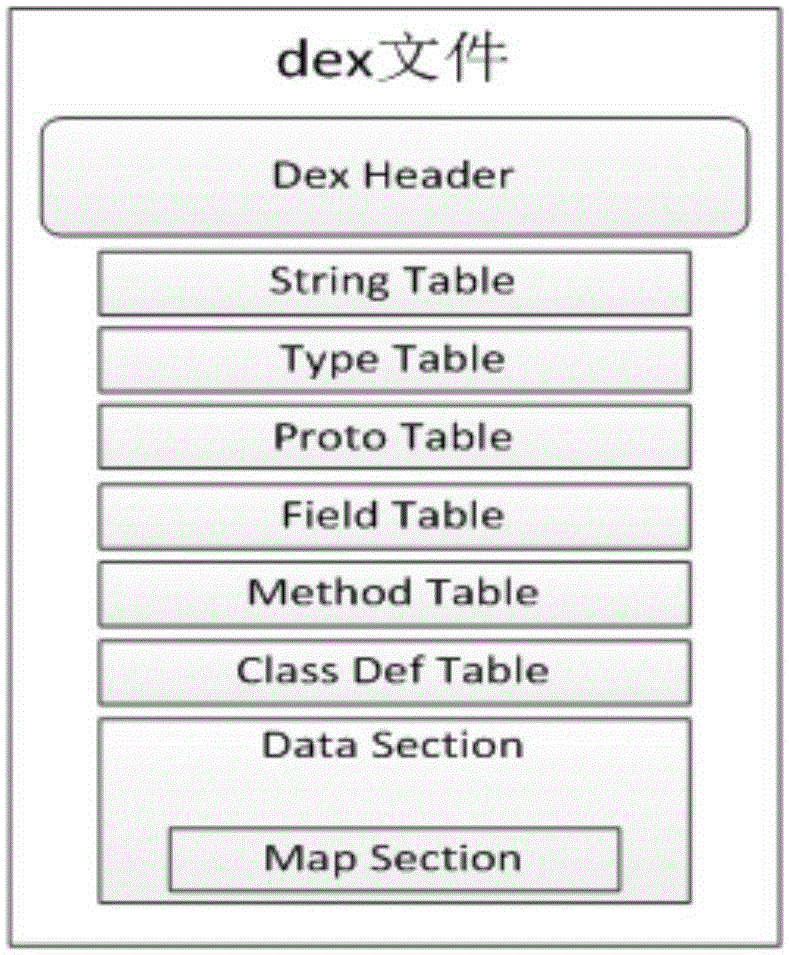
The invention discloses a software protection method and system applicable to an Android system. The method comprises the following steps of: analyzing: analyzing a DEX file from an APK (Android Package) file of Android application software to be encrypted; encrypting: encrypting all or a part of information of the DEX file to generate an encrypted DEX file; and generating, substituting the DEX file before encryption with the encrypted DEX file to generate the APK file formed by encrypting all or a part of the information of the DEX file and a digest file formed by performing MD5 (Message Digest 5) encryption on a key. Since the method only aims at the encryption protection of key information (such as a DEX file header, byte codes in the DEX file and the like) of the DEX file in the APK file, the execution efficiency of encryption and decryption is greatly increased.
Owner:BEIJING UNIV OF POSTS & TELECOMM
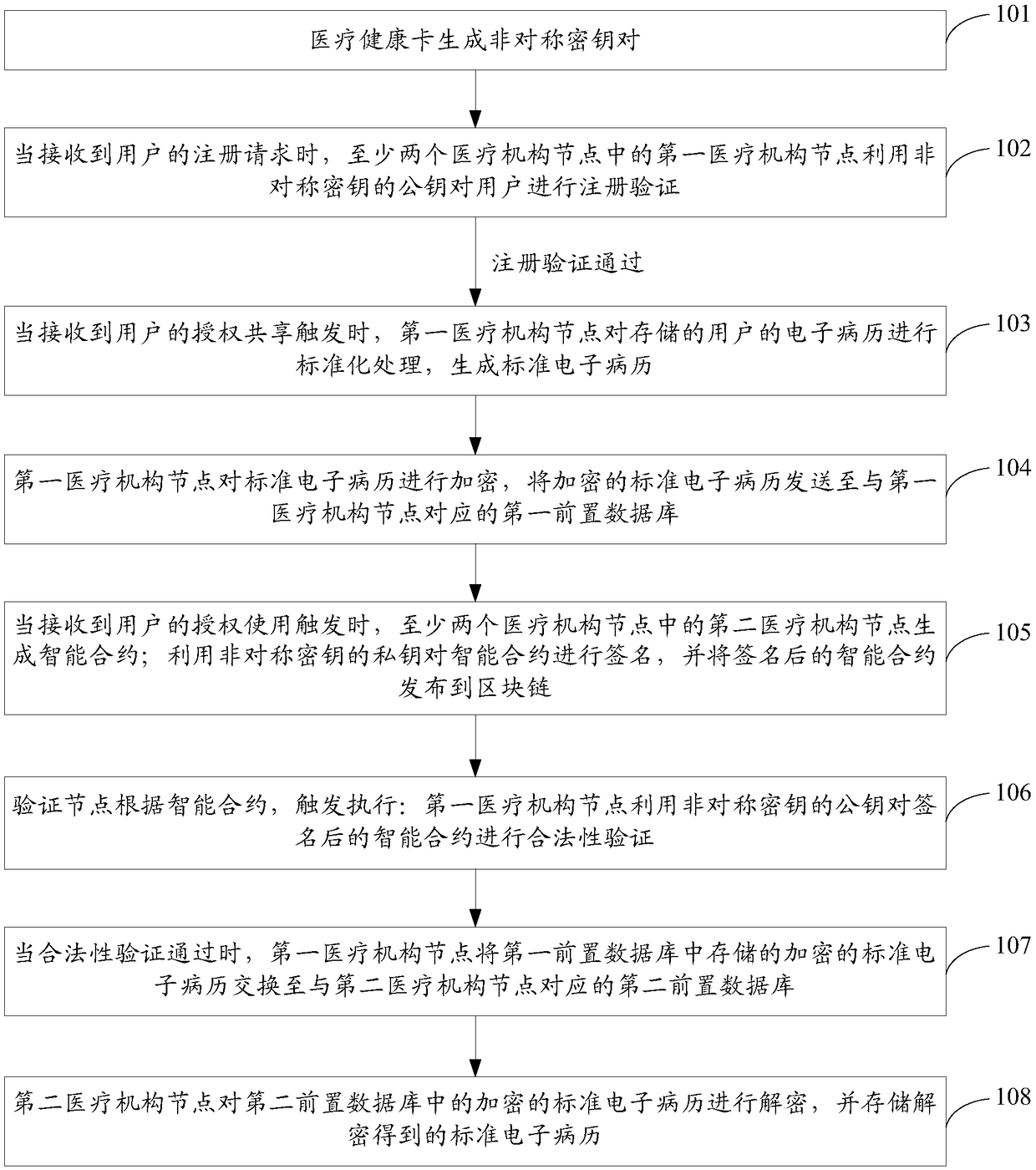
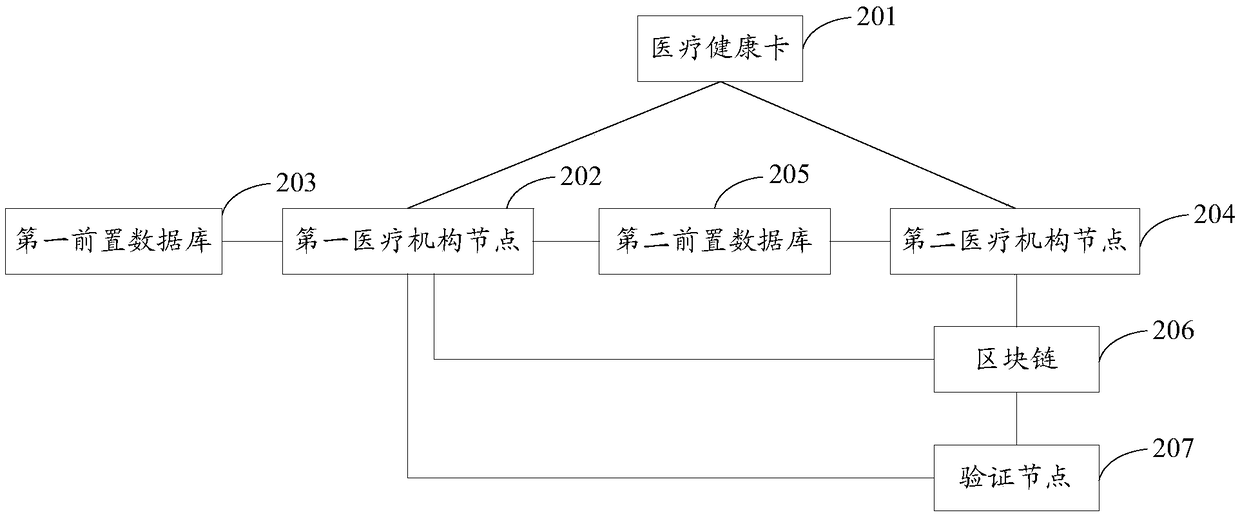
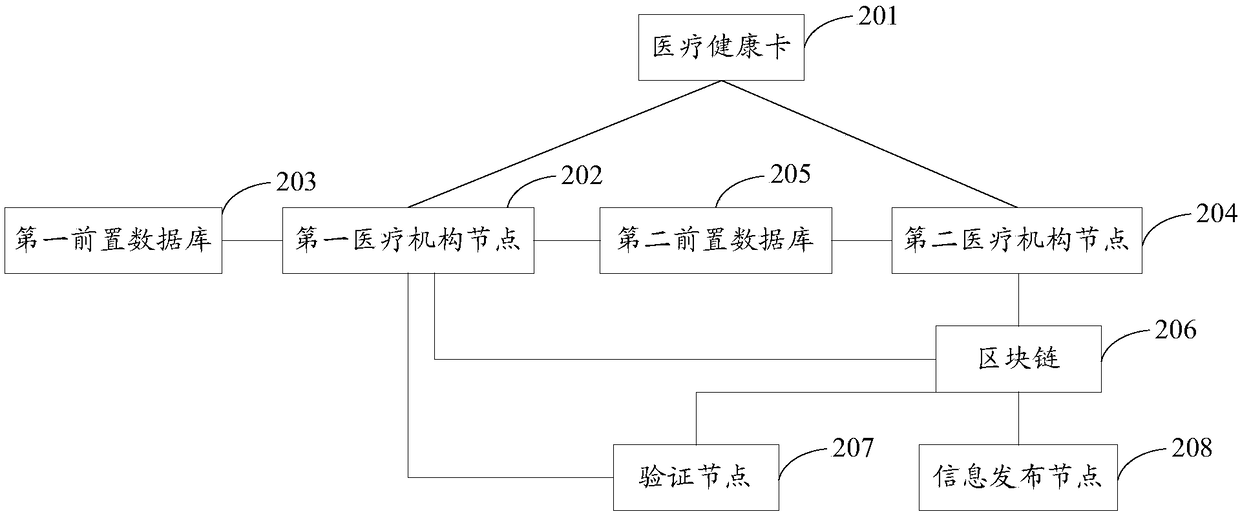
Electronic medical record sharing method and system based on block chain
InactiveCN108449359AProtect patient privacyImprove sharing efficiencyUser identity/authority verificationPatient-specific dataMedical healthSmart contract
The invention provides an electronic medical record sharing method and system based on a block chain, wherein the method comprises the following steps: a medical health card generates an asymmetric secret key pair; the first medical institution node performs registration verification on the user by utilizing the asymmetric secret key, and when the verification is passed, a first medical institution node uses the asymmetric secret key to perform registration verification on a user; when the verification is passed, the steps are carried out as follows: when an authorized sharing trigger is received, the first medical institution node performs standardized processing on the electronic medical record, and the encrypted standard electronic medical record is sent to a first front-loaded database; when an authorized use trigger of the user is received, the second medical institution node generates an intelligent contract and the signed intelligent contract is issued to a block chain; a verification node, according to the intelligent contract, triggers the execution as follows: the first medical institution node conducts validity verification on the signed intelligent contract; when the verification is passed, an encrypted standard electronic medical record is exchanged to a second front-loaded database; the second medical institution node decrypts the encrypted standard electronic medical record to obtain a standard electronic medical record. According to the scheme, the sharing process of the electronic medical record can be simplified.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
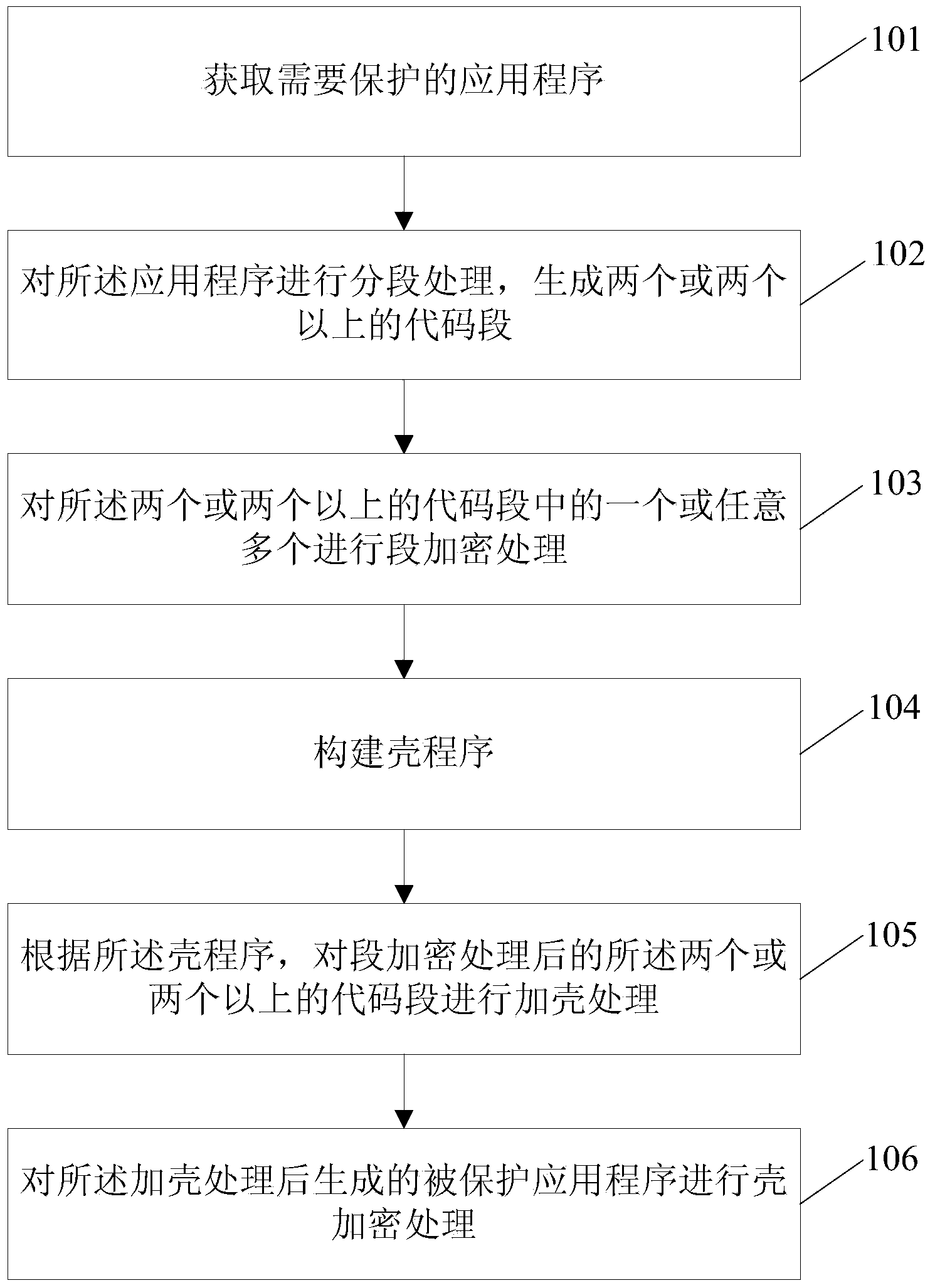
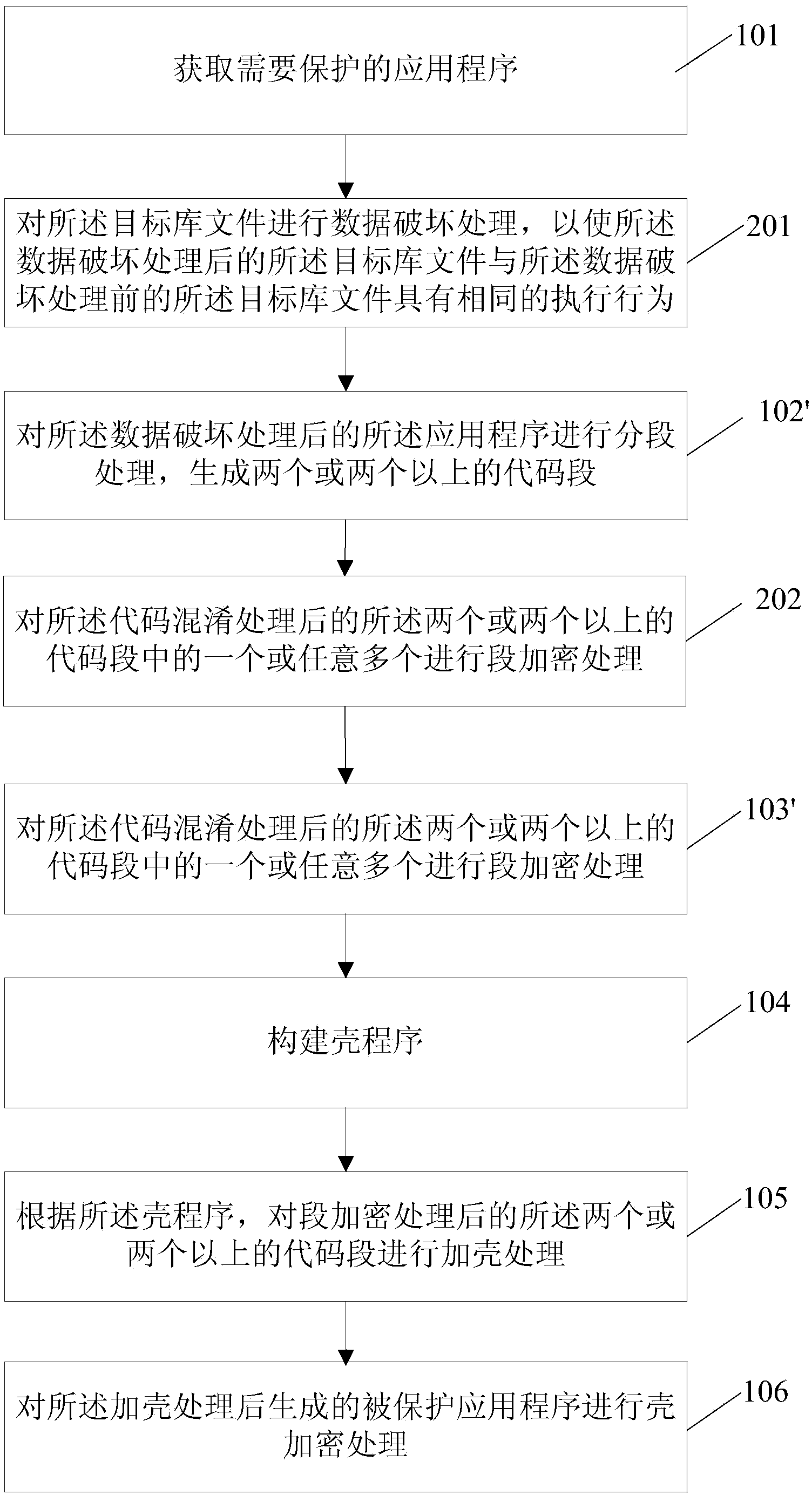
Protecting method and running method and device and system for Android platform application program
InactiveCN104102860AIncrease the difficulty of crackingImprove protection strengthProgram/content distribution protectionApplication softwareCode segment
The invention relates to a protecting method and a running method and device and system for an Android platform application program. The protecting method comprises the steps of obtaining an application program needing to be protected; performing segment handling on the application program and generating two or more code segments; performing segment encryption processing on one or random more of the two or more code segments; constructing a shell procedure; according to the shell procedure, performing shell adding processing on the two or more code segments having undergone segment encryption processing, and performing shell encryption processing on the protected application program generated after the shell adding processing. According to the technical scheme, the solving difficulty of the application program is increased, and protecting strength of the application program is further improved.
Owner:BEIJING QIHOO TECH CO LTD +1
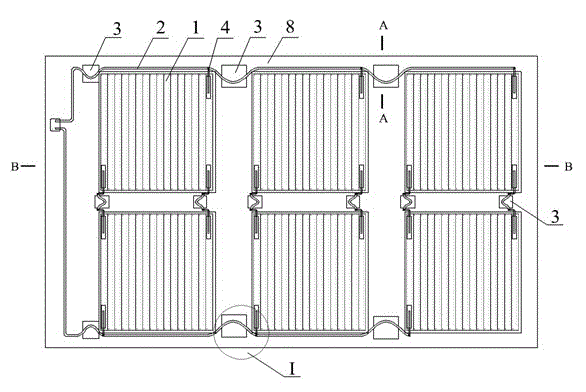
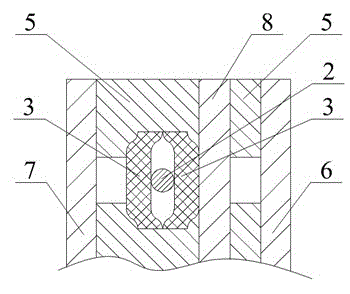
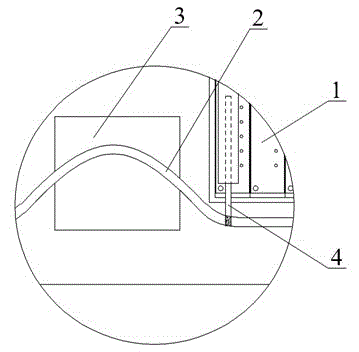
Multi-dimensional folded flexible solar battery pack and manufacturing method thereof
ActiveCN102945873AImprove protection strengthExtended service lifeFinal product manufacturePhotovoltaicsBackplaneEngineering
The invention relates to a multi-dimensional folded flexible solar battery pack and a manufacturing method thereof and belongs to the field of a solar photovoltaic technology. The technical problems that an interior metal lead in a flexible solar battery pack is easy to break and the like are solved. According to the multi-dimensional folded flexible solar battery pack, flexible solar battery chips are packaged between a front plate and a rear plate through an adhesive film; multiple flexible solar battery chips are in parallel connection through a lead string, so as to form a flexible solar photovoltaic array; an area for folding a battery pack is reserved between adjacent flexible solar battery chips; and an inner slot for storing the lead is arranged in the area for folding. The folding life of the multi-dimensional folded flexible solar battery pack designed by the invention is long; the folding times can reach above 4000 times, without the breaking condition of the metal lead; and the service life of the battery pack is ensured.
Owner:SHENZHEN TRONY SOLAR CORP +1
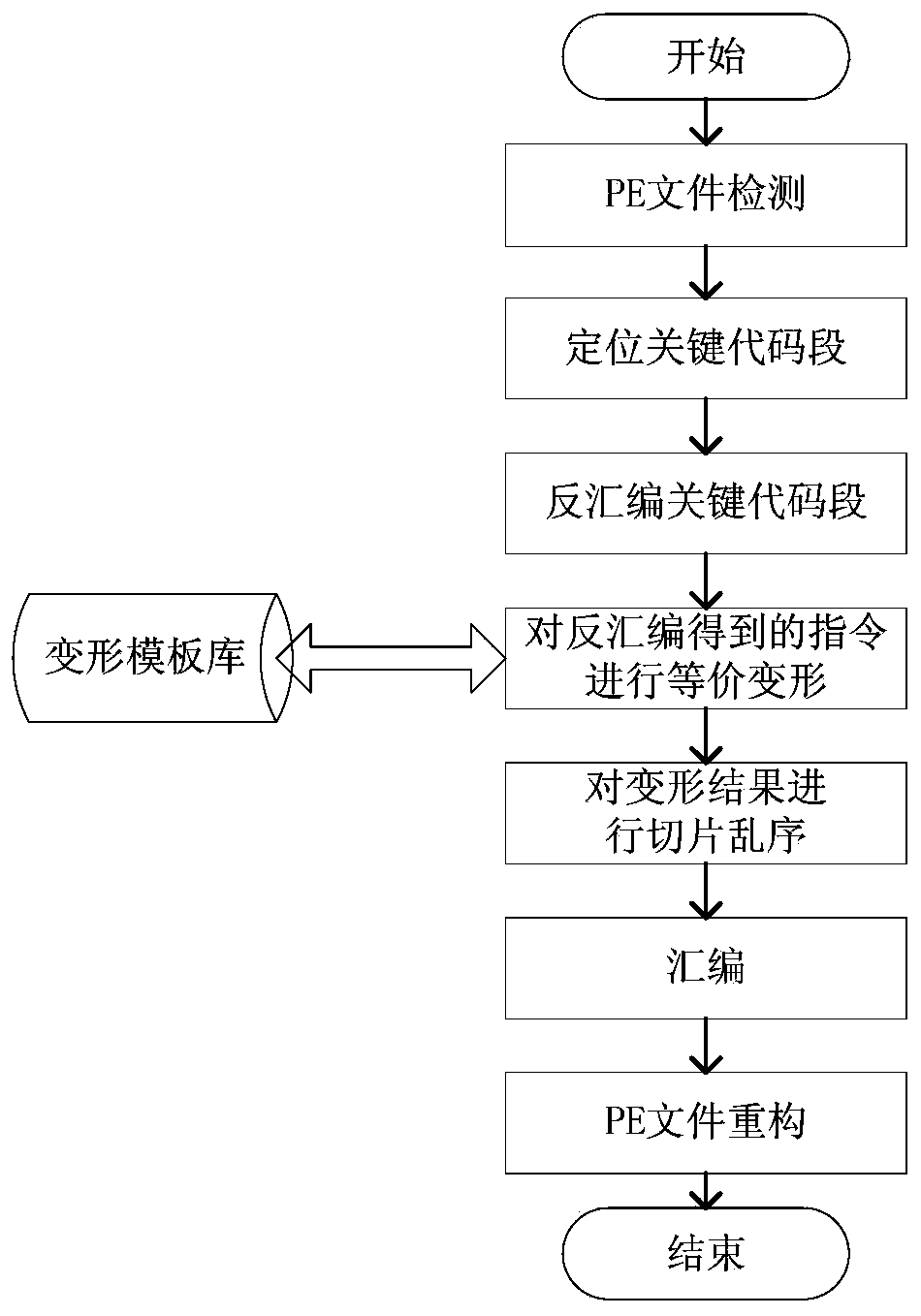
Code morphing-based binary code obfuscation method
InactiveCN103778355AWide applicabilityHave diversityProgram/content distribution protectionRe sequencingObfuscation
The invention discloses a code morphing-based binary code obfuscation method. The method comprises the following steps: 1, determining a morphing template library; 2, detecting a PE (Portable Execute) file; 3, locating a key code segment; 4, disassembling the key code segment to obtain an assembly instruction sequence, identifying a circular structure in the code segment, and calculating the weight of each instruction in the key code segment; 5, morphing all assembly instructions in the assembly instruction sequence; 6, slicing the assembly instruction sequence and re-sequencing; 7, assembling a new assembly instruction sequence generated in the step 6, and converting into a binary code; 8, reconstructing the PE file. In the method, a computer system is used for obfuscating the executable binary code file under a windows system, so that high protection strength is achieved, and extension becomes easy.
Owner:NORTHWEST UNIV
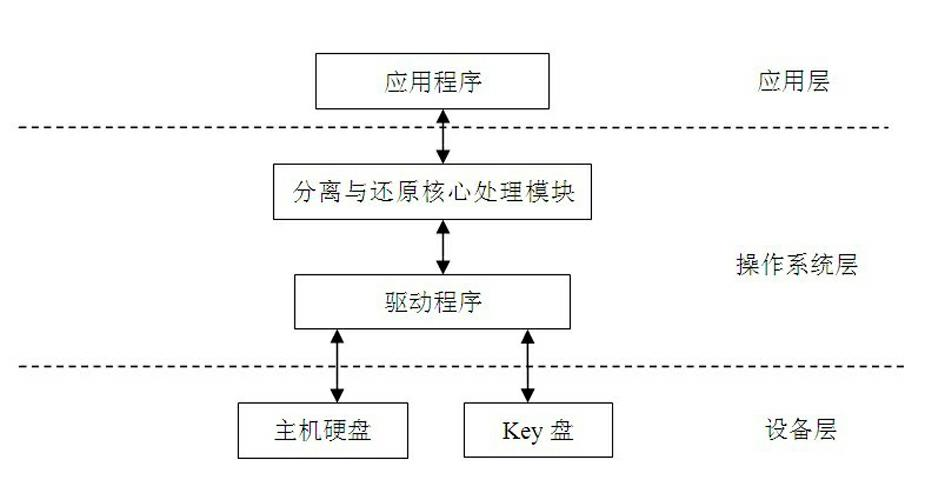
System and method for on-line separation and recovery of electronic documents
ActiveCN102693399APrevent leakageImprove protection strengthDigital data protectionElectronic documentManagement tool
The invention discloses a system and a method for on-line separation and recovery of electronic documents, and aims to realize automatic separation storage and recovery of electronic documents during the editing and using processes without any influence on thespecific document editing system. The method comprises the steps of binding a part storage area of a management terminal and a part storage area of a special key board (customized by the system) to form a logic storage space, namely, ''separation storage area''; when preserving the file in the separation storage area, effectively separating and storing information to two different mediums, namely, the management terminal and the special key board; when reading the file in the separation storage area, acquiring recovered original document by document fragment information on two mediums. Compared with the traditional encryption management, the method is more safe, convenient and reliable, so that the method can provide a safety management tool with super strength for terminal-level electronic documents.
Owner:南京伍安信息科技有限公司
Code fragmentization based Android application program packing protection method and apparatus
InactiveCN105184118AIncrease the difficultyReduce the possibilityDigital data protectionProgram/content distribution protectionProcess memoryApplication software
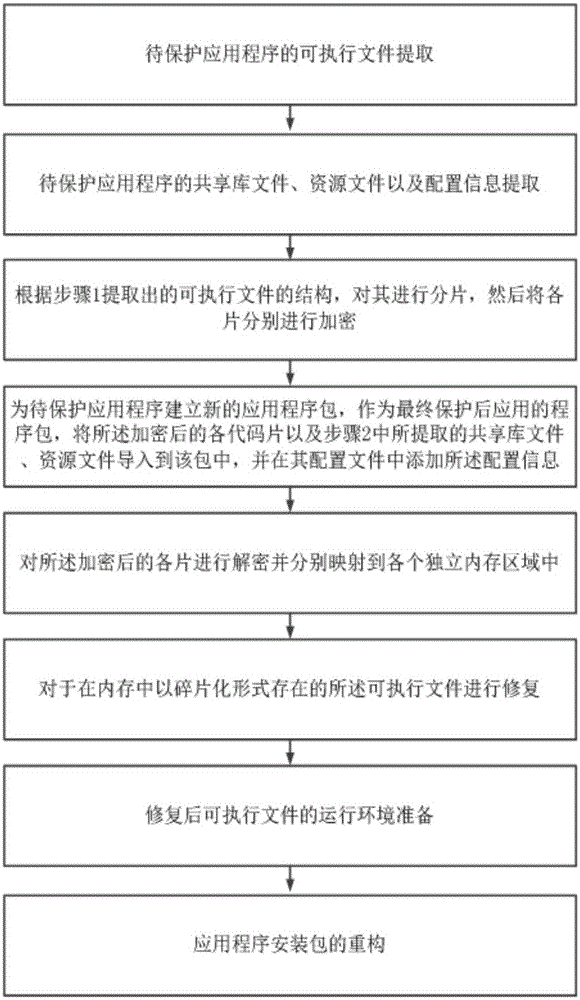
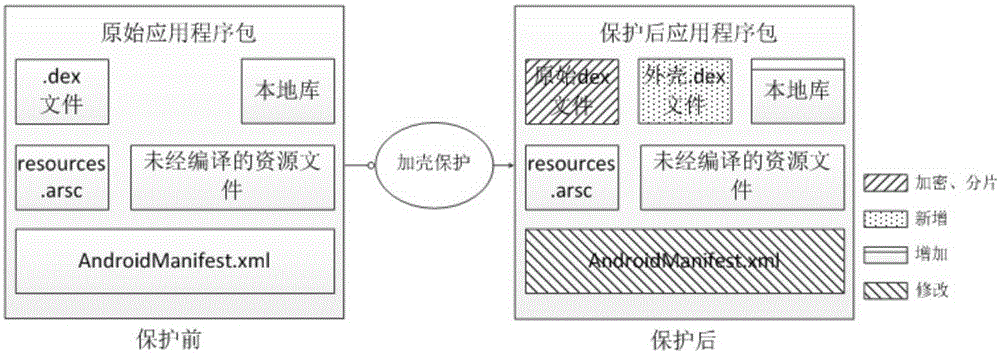
The invention discloses a code fragmentization based Android application program packing protection method and apparatus. The method comprises: extracting an executable file, a shared library file, resources, configuration information and the like from a to-be-protected application program first, then performing code fragmentization on the executable file, encrypting code fragments, importing the encrypted code fragments into a newly created application package, and adding the extracted configuration information; and decrypting the encrypted code fragments, allocating independent memory space, repairing and recombining the decrypted code fragments into the executable file, preparing a runtime environment and reconstructing an installation package. The method is high in protection intensity; and the executable file of the protected application program always exists in a fragmentization form in a process memory in the whole life cycle, so that the possibility of stealing the complete executable file by an attacker is greatly reduced and the difficulty of reversing, cracking, secondary packing and the like of the application program is greatly increased; and the protection intensity and the performance overhead can be balanced.
Owner:NORTHWEST UNIV(CN)
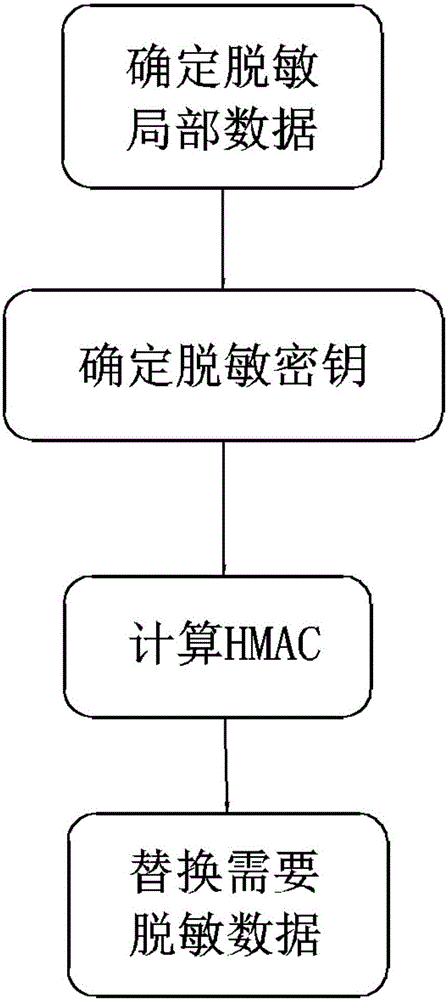
Method for local desensitization of data
InactiveCN106203139AImprove protection strengthEasy to analyzeDigital data protectionData needsData format
The invention discloses a method for local desensitization of data. The method comprises the steps of determining local data needing desensitization according to sensitive data format and significance; determining a desensitization key; performing a Hash message authentication code (HMAC) according to the desensitization key and the local data needing desensitization, and obtaining desensitized data. According to the method, the data format and part of significance are reserved while data protection strength is improved, and data is subject to analysis, statistics and processing easily.
Owner:成都知道创宇信息技术有限公司
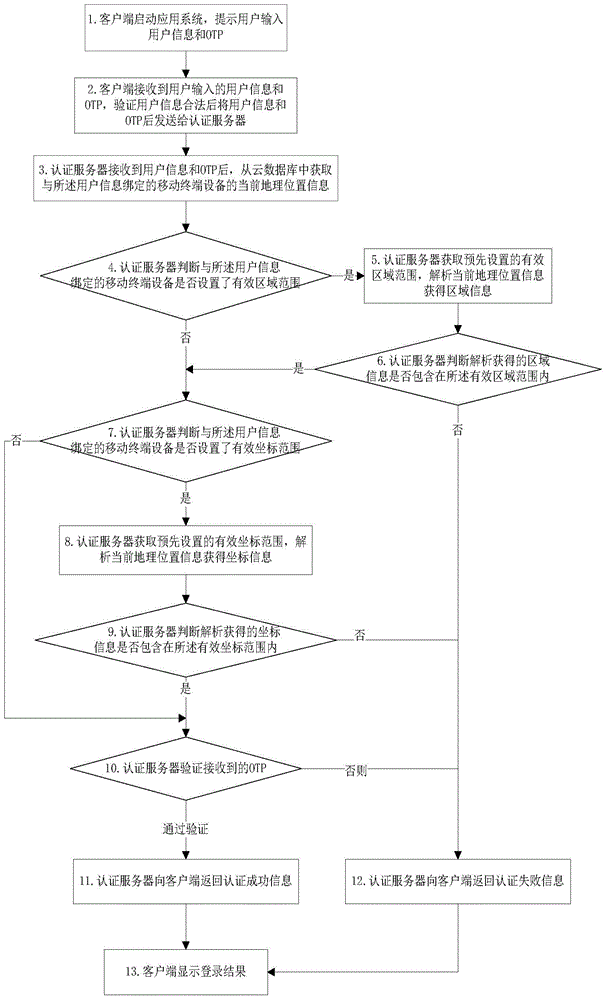
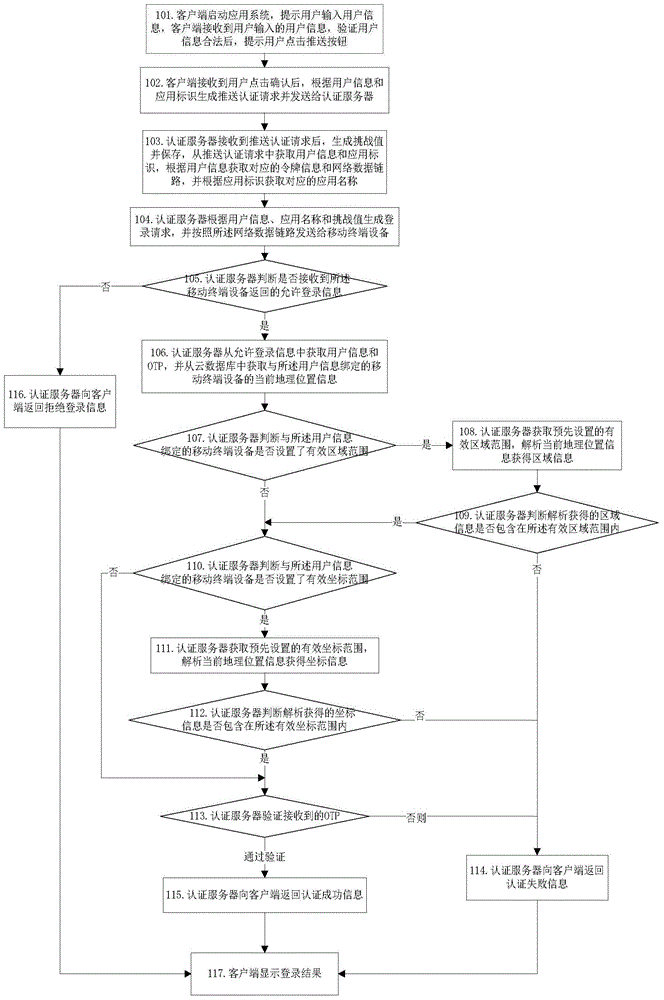
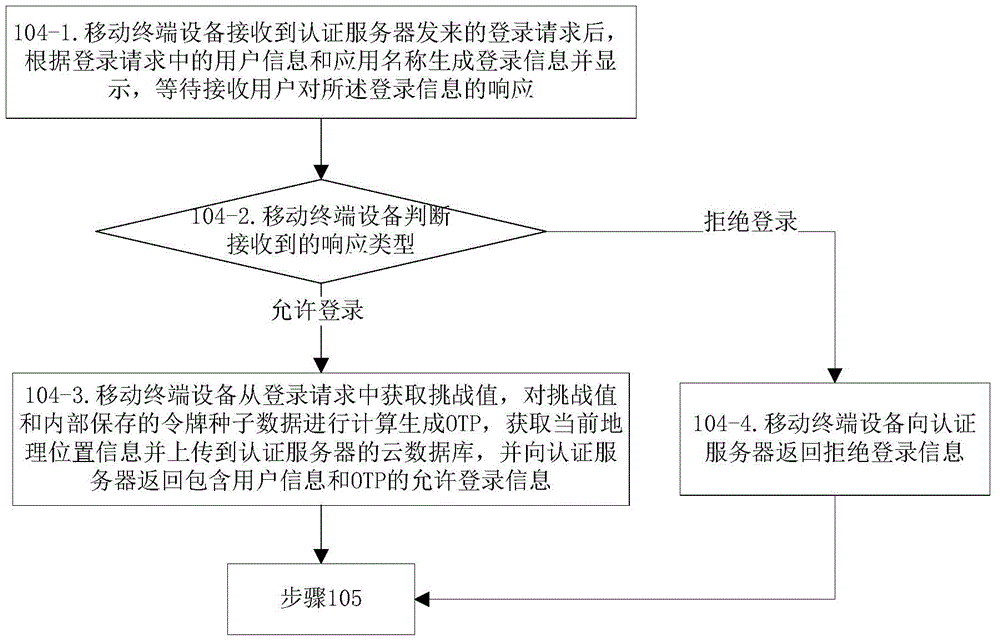
Authentication method based on geographic position information
ActiveCN104869124AImprove protection strengthAdd geographic location informationTransmissionClient-sideIp address
The invention discloses an authentication method based on geographic position information, and belongs to the field of information security. The authentication method disclosed by the invention comprises the following steps: verifying an OTP (One Time Password) and the current geographic position information of mobile terminal equipment bound with user information by an authentication server; and the authentication succeeds if both the OTP and the current geographic position information of the mobile terminal equipment pass verification, otherwise the authentication fails, wherein the verification of the current geographic position information of the mobile terminal equipment bound with the user information can be comparison with stored geographic position verification information or comparison with a geographic position corresponding to the IP (Internet Protocol) address of a client transmitting the user information. According to the authentication method provided by the invention, a plurality of authentication factors participate into an authentication flow, so that the protection intensity of application system login can be enhanced effectively, and the login security is enhanced.
Owner:FEITIAN TECHNOLOGIES
Binary software protection method by means of dynamic fine-grained code hiding and obfuscating technology
ActiveCN106650340AImprove securityResistance to static analysisProgram/content distribution protectionCoding blockRest position
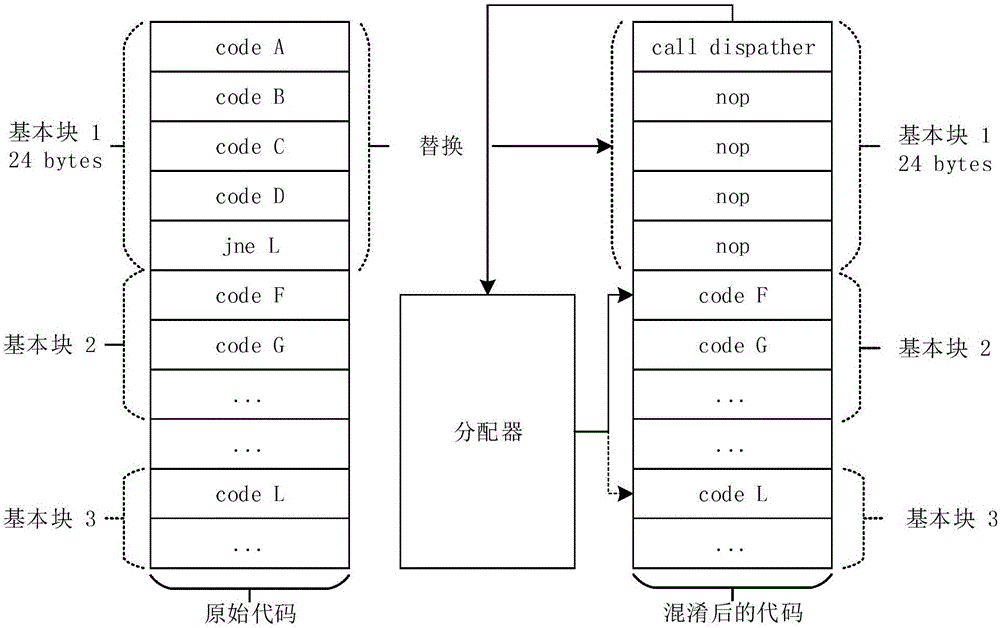
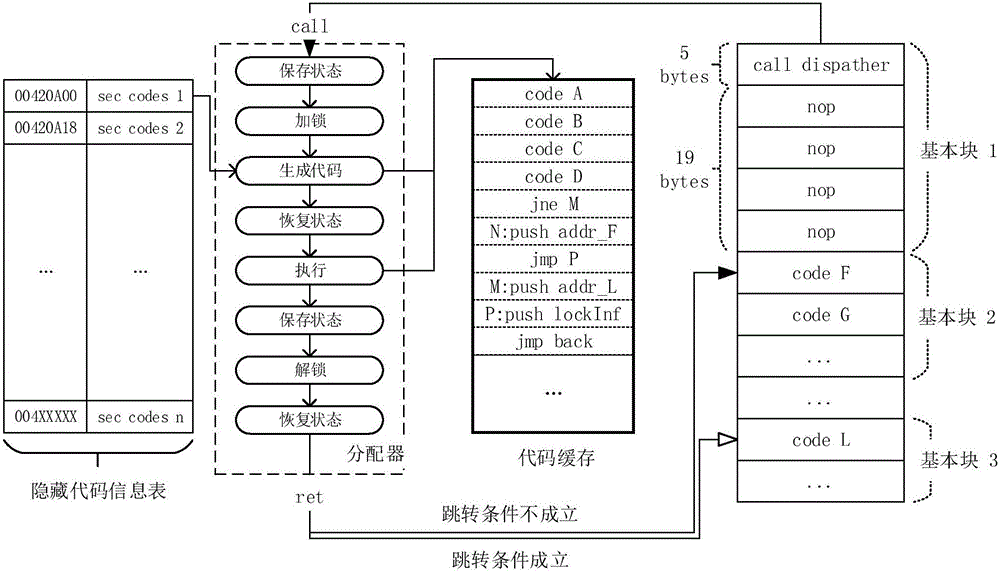
The invention discloses a binary software protection method by means of a dynamic fine-grained code hiding and obfuscating technology. The method comprises the steps that S1, a hidden target is selected, wherein a to-be-hidden code block is selected in a target program with a basic block as a unit; S2, the selected basic block is hidden, wherein according to each to-be-hidden basic block, an original code segment is replaced with a distributor function call, and other obfuscating instructions are filled in the rest positions; S3, the codes are packaged again, a new code segment is created so as to save all additional logic and data. The method has the advantages of being wide in application range, light in magnitude, extendable, high in safety and the like.
Owner:NAT UNIV OF DEFENSE TECH
Methods of utilizing coal combustion residuals and structures constructed using such coal combustion residuals
ActiveUS9790703B1Cost-effectiveLow facility requirementsSolid waste managementWallsCombustionEngineering
A process of fabricating a static structure including an interior volume that includes the steps of mixing coal combustible residual (CCR) with structural reinforcing materials to form a construction material and utilizing the construction material to fabricate exterior enclosure-forming components of the static structure. The enclosure-forming components are sufficiently reinforced, enhanced and / or thick to provide protection against exterior forces directed against the structure.
Owner:GO TEAM CCR LLC
Safety protecting mesh
InactiveCN101906880AImprove protection strengthHigh strengthBuilding material handlingPolyesterFiber
The invention discloses a safety protecting mesh which comprises a plastic mesh. A plurality of plastic reinforced ribs I are arranged in parallel on one surface of the plastic mesh along the longitudinal direction, a plurality of plastic reinforced ribs II are arranged in parallel on the other surface of the plastic mesh along the transverse direction, and a plurality of glassfibers or polyester fibers are both embedded in each plastic reinforced rib I and each plastic reinforced rib II. After adopting the structure, the invention can enhance the using period and increase the reusability, also lower the failure ratio and the use cost, enhance the construction safety, is convenient for construction and operation, also remarkably strengthens the protection strength after being enclosed in the construction field, at a danger area or at the periphery of a building, has good anti-beaten capability and has the advantages of large vigor and obvious effect when resisting and buffering a heavy.
Owner:刘明志
Novel protective shoe upper and production technique thereof
InactiveCN103271511AImprove protection strengthReduce collision damageUpperBootlegsSkin treatmentsFoaming agent
A process for manufacturing a novel protective shoe upper comprises the following steps: adding a processing adjuvant, a bridging agent, a foaming agent, an active agent, and pigment in EVA raw materials, forming EVA foaming body after fully mixing, finally cutting into an EVA foaming body layer; covering a bonding layer on the EVA foaming body layer, then blanking into a preset pattern modeling; placing the blanked EVA foaming body layer in a bottom die; coating a cloth-skin treatment agent on the bonding surface of the bottom layer of a shoe upper and placing on the bottom die of the die, closing a die cover, firstly pressurizing and heating and then pressurizing and cooling and fetching an end product. The protective shoe upper manufactured by the invention can effectively improve protective strength of the shoe upper, reduce collision harm from external impact force to an instep, and play a protective role for a user in outdoor activities.
Owner:泉州泰亚鞋业有限公司
Gangue stopping device
The invention discloses a gangue stopping device, which comprises a base, a first rotating oil cylinder, a rocker arm, a retractable sleeve, a retractable oil cylinder, a protection net, a face oil cylinder and a face guard, wherein one end of the first rotating oil cylinder is hinged with the base, the other end of the first rotating oil cylinder is hinged with the position of the rocker arm adjacent to the middle, one end of the rocker arm is hinged with the base and the first rotating oil cylinder is used for controlling the rocker arm to rotate within a horizontal plane; the retractable sleeve is sheathed on the rocker arm, one end of the retractable oil cylinder is connected with the rocker arm, the other end of the retractable oil cylinder is connected with the retractable sleeve and the retractable oil cylinder is used for controlling the retractable sleeve to extend and retract along the rocker arm; the face guard is hinged with the front end of the retractable sleeve, the upper side of the protection net is connected with the retractable sleeve and the lateral side of the protection net is connected with the face guard; and one end of the face oil cylinder is hinged with the position of the retractable sleeve adjacent to the front end and the other end of the face oil cylinder is hinged with the position of the face guard adjacent to the middle part. The gangue stopping device has the advantages that the automatic extension and the automatic retraction of the protection net can be realized, the protection strength is improved and the safety in mining operation is improved.
Owner:HUAINAN MINING IND GRP
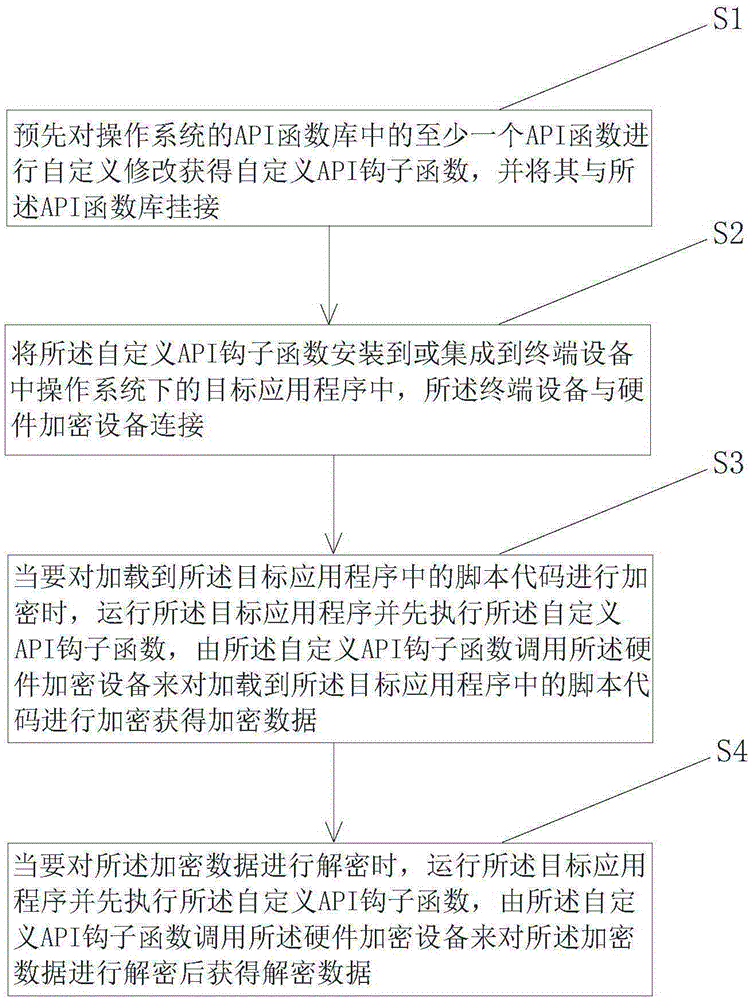
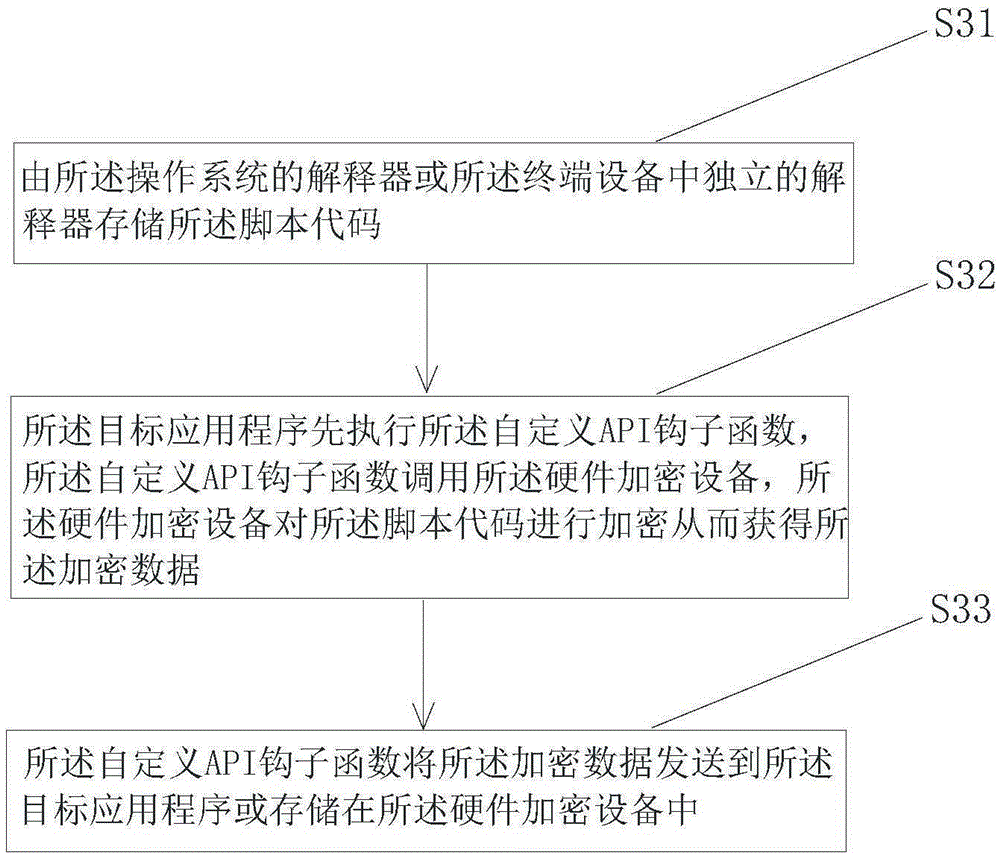
Protecting method for software codes
ActiveCN105303073AImprove protection strengthAvoid safety hazardsProgram/content distribution protectionOperational systemTerminal equipment
The invention discloses a protecting method for software codes. The protecting method comprises the following steps: S1) performing user-defined modification on at least one API (Application Program Interface) function in an API function library of an operation system in advance, and then acquiring a user-defined API hook function, linking the user-defined API hook function with the API function library; S2) installing or integrating the user-defined API hook function into a target application program under the operation system in terminal equipment which is connected with a hardware encrypting device; S3) while encrypting a script code loaded to the target application program, running the target application program, firstly performing the user-defined API hook function and then invoking the hardware encrypting device, thereby acquiring an encrypted data; S4) while decrypting the encrypted data, running the target application program, firstly performing the user-defined API hook function and then invoking the hardware encrypting, thereby acquiring a decrypted data. According to the protecting method for software codes, the poor safety and the potential safety hazard caused by the incapability of the shell to protect the script code in text form in the present software code protecting scheme are solved.
Owner:BEIJING SENSESHIELD TECH
Packaging body for heating processing
InactiveUS6855356B2Low costEasily fabricatingReady-for-oven doughsVenting meansFilling materialsRoom temperature
A packaging body for heat processing a material retained therein is basically formed of a plastic base material having side joining sections, and end sides. The side joining sections and end sides are superposed and connected together to form a bag for filling the material. A sealant layer is deposited on at least one of the end sides to connect the end sides together through the sealant layer to thereby form a vapor communication joining section at the end sides. The sealant layer has a peeling off property from 0 to 1,200 gf / 15 mm at 90° C. and a peeling off property of equal to or more than 3 kgf / 15 mm at a room temperature. Thus, only when the packaging body is heated more than 90° C., the vapor communication joining section is only opened to release pressure inside the packaging body.
Owner:SUN A KAKEN
High-temperature resisting foundry sand and preparation method thereof
The invention aims to provide high-temperature resisting foundry sand. The high-temperature resisting foundry sand comprises the following components in parts by weight: 100 parts of bauxite by mass, 20-30 parts of zircon sand ores by mass, 10-20 parts of absorption fillers by mass, 10-30 parts of high-temperature fillers by mass, and 5-20 parts of polyborosiloxane by mass; and the prepared high-temperature resisting foundry sand is excellent in high-temperature resistance, is used for casting an alloy at a temperature of 2000-2500 DEG C, and obtains an excellent effect. The invention also aims to provide a preparation method of the high-temperature resisting foundry sand; and the preparation method comprises the following steps: (1) the fillers are pretreated; (2) a mixture after treatment in the step (1) and bauxite are put in a ball mill for mixing; (3) the mixture in the step (2) is put in a ball former; and a proper amount of water is added in the ball former to pelletize to obtain a ball-shaped blank; and (4) the ball-shaped blank in the step (3) is put in a graphite crucible for high-temperature sintering and cooling to obtain the high-temperature resisting foundry sand.
Owner:WENLING NEWIMPETUS CASTINGANDMACHINING CO LTD
Differentiated noise adding method and system in federated learning gradient exchange
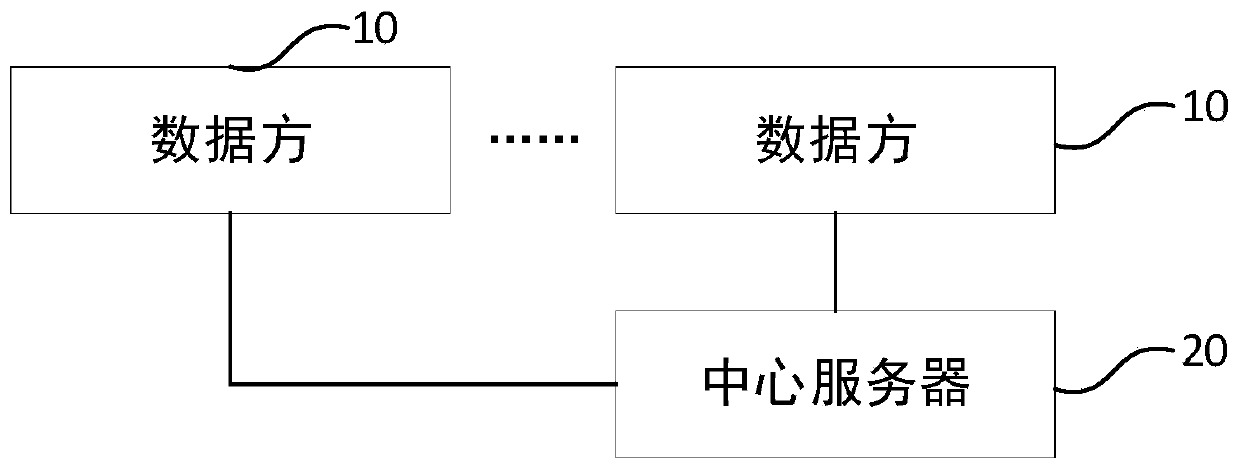
ActiveCN111260061AReduce overheadImprove protection strengthNeural learning methodsData setPrivacy protection
The invention discloses a differentiated noise adding method, medium and system in federated learning gradient exchange, and the method comprises the steps that a plurality of data parties obtain corresponding training data sets, and train a deep learning model according to the corresponding training data sets, so as to update the gradient of the deep learning model; each data party performs hierarchical processing on the corresponding gradient, calculates a two-norm corresponding to each layer of gradient, adds noise to each layer of gradient according to the two-norm, and sends the noise-added gradient to the central server; the central server aggregates the noise-added gradients and sends the aggregated gradients to each data party, so that each data party updates a local deep learningmodel according to the aggregated gradients; and according to the method, the privacy protection strength in the data exchange process of federated learning can be improved, and meanwhile, compared with an encryption algorithm in traditional federated learning, the overhead of data transmission can be reduced.
Owner:XIAMEN UNIV
Authentication method and device for reinforced software
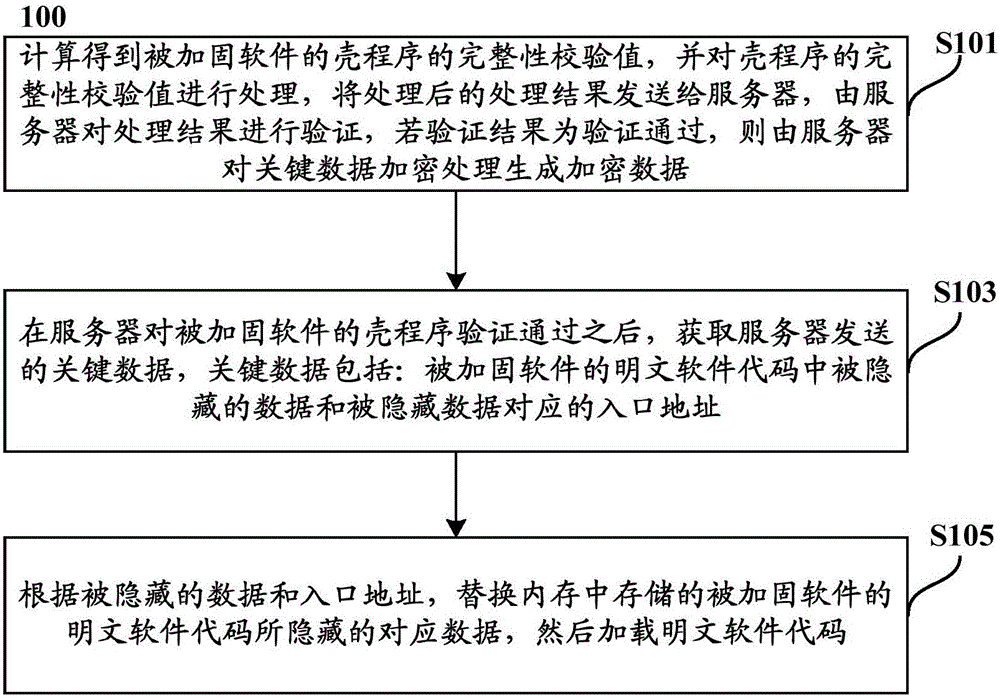
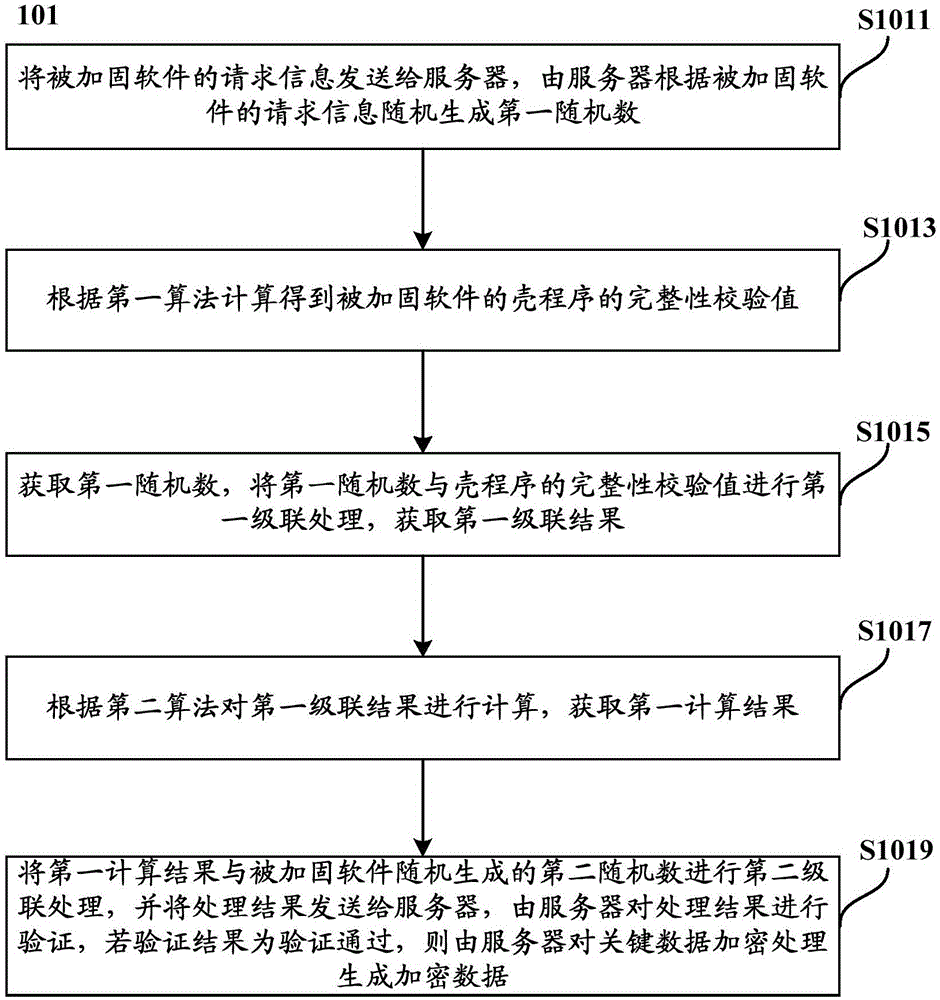
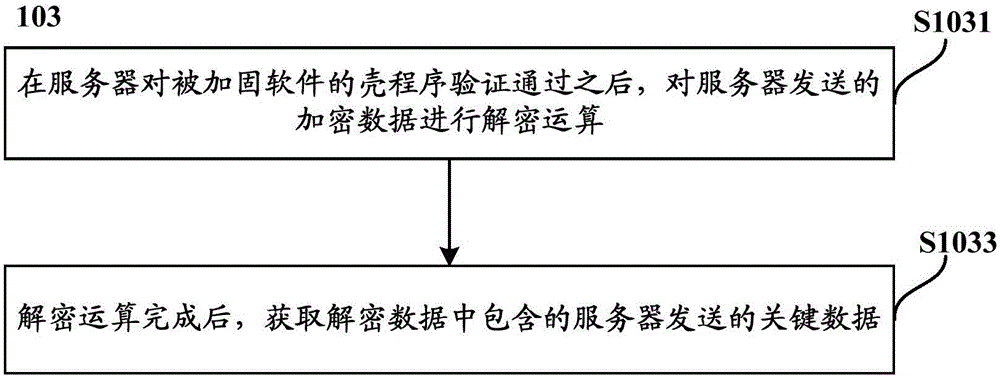
InactiveCN106295257AGuaranteed uptimeImprove protection strengthMultiple keys/algorithms usageDigital data protectionPlaintextComputer hardware
The invention provides an authentication method and device for reinforced software. The authentication method comprises the steps that after shell program verification of a server on the reinforced software is passed, key data sent by the server is acquired, wherein the key data comprises hidden data in plaintext software codes of the reinforced software and entry addresses corresponding to the hidden data; corresponding data which is stored in a memory and hidden by the plaintext software codes of the reinforced software is replaced according to the hidden data and the entry addresses, and then the plaintext software codes are loaded. According to the authentication method, the sources of service requests can be effectively distinguished, effective protection can be conducted when an malicious application requests service provision, the protection intensity of the reinforced software is greatly improved, attack of an attacker is effectively prevented, and it is guaranteed that the reinforced software can normally run.
Owner:ZTE CORP
Private key storage and reading method and device and hardware device
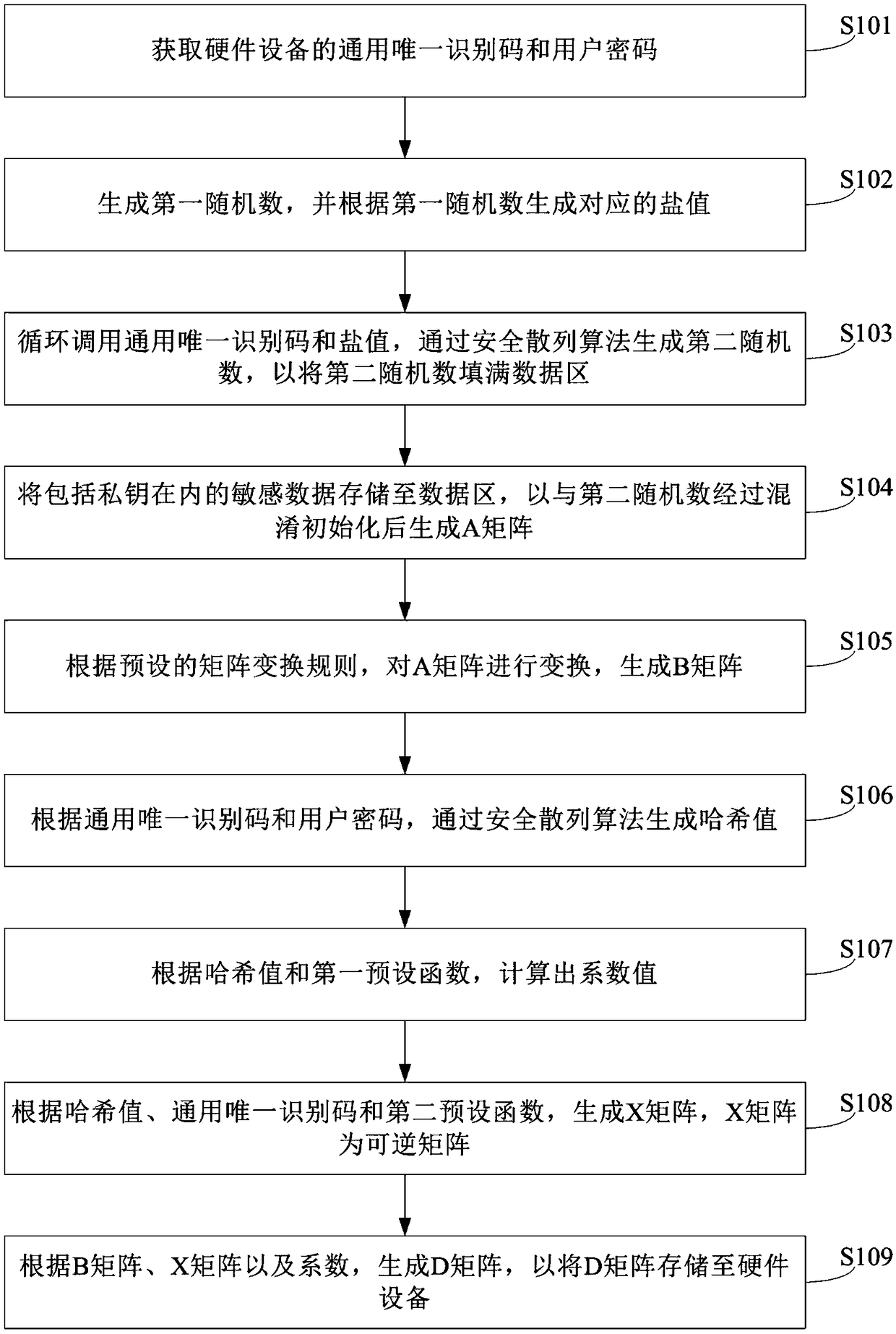
ActiveCN108833117AImprove protection strengthSmall amount of calculationKey distribution for secure communicationUser identity/authority verificationComputer hardwareUniversally unique identifier
An embodiment of the invention discloses a private key storage and reading method and device and a hardware device. According to the private key storage and reading method and device and the hardwaredevice, confusion is carried out on sensitive data comprising private key and the like according to universal unique identification code of the hardware device and user passwords and the like to obtain matrix data for storage and reading; according to the scheme, confusion is only carried out in the aspect of data storage, so that computation amount is small; data is not encrypted, so that users can integrate any encryption algorithm based on the scheme to enhance protection of the private key; and the scheme is not limited by the data structure, can be applied to private key storage of various currencies, and is high in university.
Owner:成都同创佳联科技有限公司
Electronic lock
InactiveCN105781239AReduce wasteAvoid damageNon-mechanical controlsLock casingsEffective lengthEngineering
The invention discloses an electronic lock. The electronic lock comprises a linking rod, an inner lever handle and an outer lever handle, wherein the linking rod is inserted into a lock body to act on a lock tongue; both two ends of the linking rod extend out of the lock body; the locking rod comprises an inner end and an outer end; the inner lever handle comprises a combining end; the combining end of the inner lever handle and the inner end of the linking rod form synchronous rotary combination in the rotating direction; the outer handle lever handle comprises a combining end; the combining end of the outer lever handle and the outer end of the linking rod form synchronous rotary combination or separation in the rotating direction through an engagement and disengagement device; an accommodation hole is formed in one of the combining ends of the inner lever handle and the outer lever handle or two accommodation holes are respectively formed in the two combining ends; the inner end or the outer end of the linking rod can extend into the corresponding accommodation hole, thereby adjusting the length of the linking rod between the combining end of the inner lever handle and the combining end of the outer lever handle, wherein the length is defined as an effective length; and therefore, the effective length can be adjusted by the linking rod according to the thicknesses of panel bodies of different door panels. In addition, an existing traditional lock body can be reformed into the electronic lock.
Owner:谢祥令
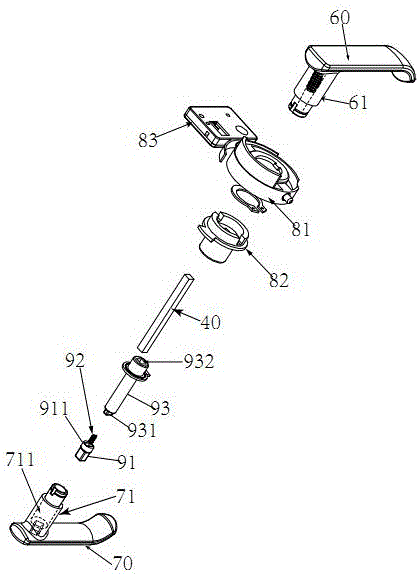
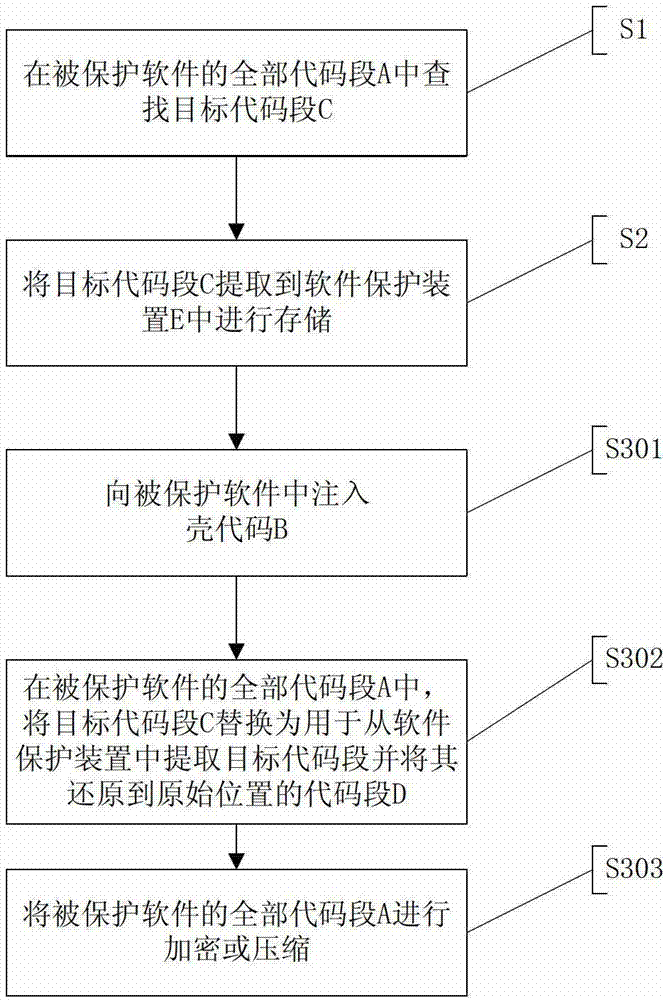
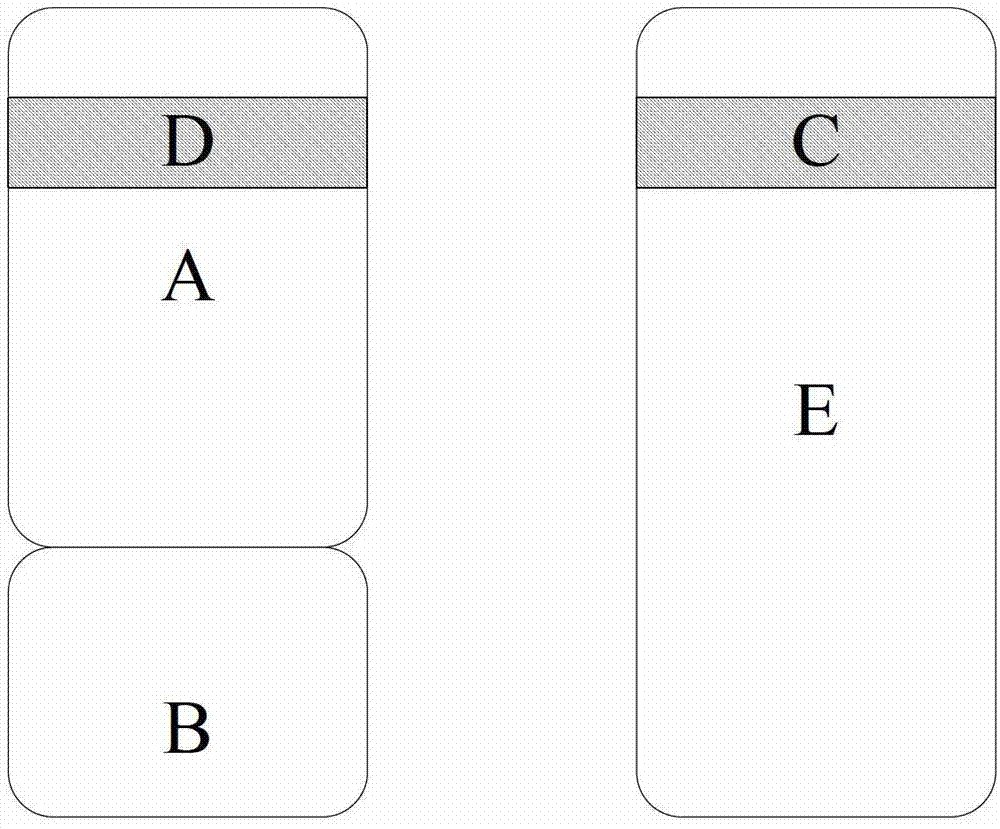
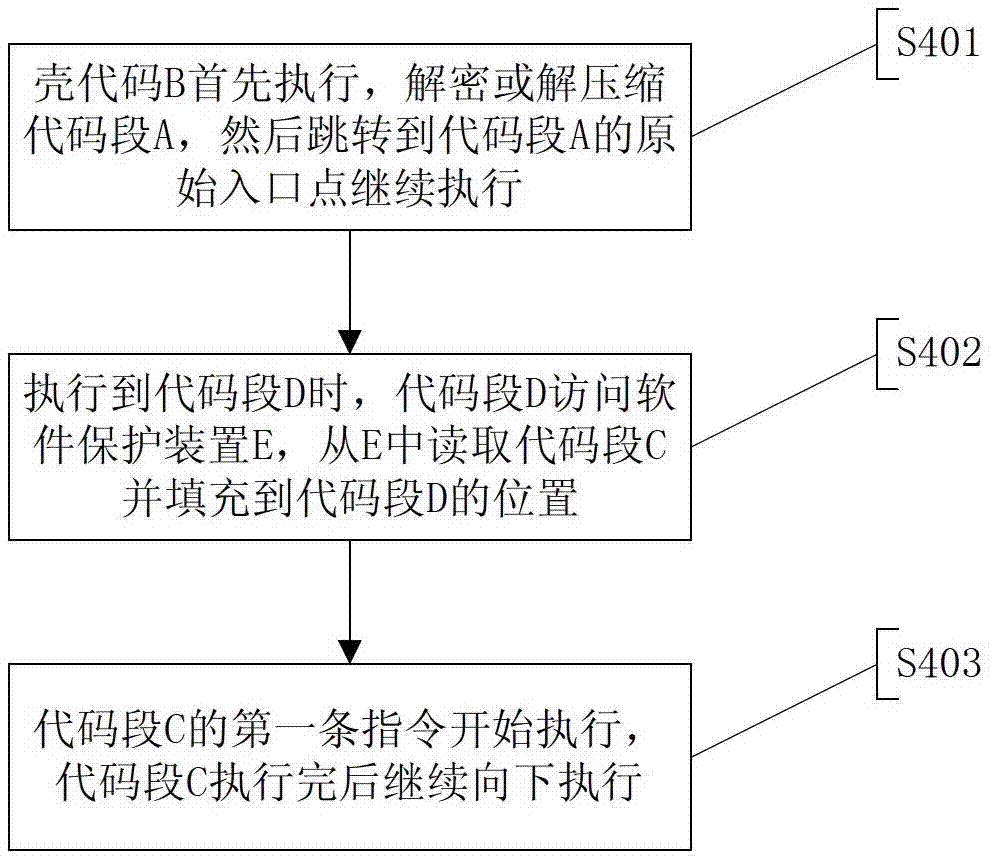
Software shelling method based on software protection device, software shelling system and software protection method
ActiveCN102930204AImprove protection strengthPlatform integrity maintainanceInternal memoryObject code
The invention discloses a software shelling method based on a software protection device, and the software shelling method comprises the following steps of S1 searching a target code segment in all code segments of protected software; S2, extracting the target code segment to be stored in the software protection device; and S3, replacing the target code segment with a code segment comprising a jump instruction or extracting the target code segment from the software protection device, restoring the target code segment to the code segment of an original position in all code segments of the protected software, and shelling the protected software. The invention also discloses a software shelling system and a software protection method. When the shelled software is run, since the target code segment is stored in the software protection device, all codes and data of the protected software are not exposed in an internal memory, and the protection strength of the software is enhanced.
Owner:BEIJING SENSESHIELD TECH
Fingerprint detection and control method and terminal
InactiveCN107784274AImprove securityImprove reliabilityDigital data authenticationMatching and classificationPattern recognitionComputer vision
The invention provides a fingerprint detection and control method and a terminal. The fingerprint detection and control method comprises the following steps of receiving a fingerprint detection signaldetected by a fingerprint sensor annularly arranged at the periphery of a camera shooting module; receiving a fingerprint image signal shot by the camera shooting module; and storing the fingerprintdetection signal and the fingerprint image signal into a preset fingerprint template or comparing the fingerprint detection signal and the fingerprint image signal with the preset fingerprint template.
Owner:MEIZU TECH CO LTD
Tree insulation, disinsection and insect prevention method
ActiveCN103548629AImprove protection strengthAnimal repellantsPlant protective coveringsMedicineOverwintering
A tree insulation, disinsection and insect prevention method is characterized by comprising the following steps: (1) coating a trunk with a layer of straw mat, and binding the straw mat on the trunk by using bondages; (2) binding a circle of insect-proof medicine bags around the upper part or the middle part of the straw mat; (3) wrapping the straw mat where the insect-proof medicine bags are bound with a layer of degradable protective layer, and uniformly distributing a plurality of short branches on the circumference between the lower end of the protective layer and the straw mat. The method has the benefits that the straw mat for coating the trunk is protected by the protective layer, so that the moisture-holding and heat-insulating effects are realized, and the protection strength is enhanced; the insect-proof medicine bags are bound on the straw mat, pests get into the straw mat for overwintering or pupation, pests which realize mating for laying eggs in the trunk lay eggs in laying egg intervals, when plastic bag bodies of the insect-proof medicine bags are degraded after a predetermined time, insect-proof medicine in the bags plays a role in the protective layer, and the protective layer has a sealing function, so that the pests entering the straw mat are all be killed.
Owner:QINGDAO HOUKE INFORMATION ENG
Combined portable electronic equipment protection device
InactiveCN110203538AEasy to moveImprove practicalityLidsNon-removalbe lids/coversEngineeringElectric equipment
The invention discloses a combined portable electronic equipment protection device which comprises a base and a protection box. A box cover is hinged to the top of the protection cover through a hinge. Sliding blocks are fixedly connected to an inner cavity of the protection box, and sliding rods are connected to the tops of the sliding blocks in a sliding manner. The bottom ends of the sliding rods penetrate the tops of the sliding blocks and extend to inner cavities of the sliding blocks. Reset springs are fixedly connected to the bottoms of the inner cavities of the sliding blocks, and in addition, the top ends of the reset springs are fixedly connected with the bottom ends of the sliding rods. The combined portable electronic equipment protection device relates to the technical field of electronic equipment protection. By means of the combined portable electronic equipment protection device, push rods are pulled to drive the sliding rods to extrude the reset springs to move downwards, clamping blocks are pulled out from the interiors of limiting holes, the box cover can be rapidly and conveniently opened so that electronic equipment can be stored or taken out, the box cover canbe fixed and opened without taking too much time, in addition, operation is simple, the electronic equipment can be rapidly and conveniently moved, and practicability of the electronic equipment protection device is improved.
Owner:安徽银点电子科技有限公司
Fingerprint identification method and terminal
InactiveCN107798229AImprove reliabilityEasy to assembleTelevision system detailsColor television detailsFingerprintLight source
The invention provides a fingerprint identification method and a terminal. The fingerprint identification method comprises the following steps of controlling an auxiliary light source arranged in an adjacent camera module to be switched on for emitting auxiliary light rays; controlling the camera module to shoot a fingerprint image; receiving a signal of the fingerprint image shot by the camera module; and storing the fingerprint image signal as a preset fingerprint template or comparing the fingerprint image signal with the preset fingerprint template.
Owner:MEIZU TECH CO LTD
Photographing and fingerprint identification device and terminal
InactiveCN107563358AImprove aestheticsMiniaturizationCharacter and pattern recognitionComputer graphics (images)Identification device
The invention provides a photographing and fingerprint identification device and a terminal. The photographing and fingerprint identification device includes a photographing module and a fingerprint module. The photographing module includes a first area. The photographing module receives light of a photographed scene via the first area. The fingerprint module includes a fingerprint sensor. When viewed in a direction perpendicular to the photographing module, the fingerprint sensor is disposed around the periphery of the first area.
Owner:MEIZU TECH CO LTD
Novel temperature measuring cable
InactiveCN103576268AHigh strengthIncrease the speed of heat transferFibre mechanical structuresSolid structureRefractive index
A novel temperature measuring cable sequentially comprises a core layer, a cladding, a coating, a buffering layer, a metal armor cladding, a reinforcing layer and an outer protective layer from inside to outside. The core layer is of a solid structure, the outer wall of the core layer is wrapped by the cladding, the outer wall of the cladding is wrapped by the coating, the outer wall of the coating is wrapped by the buffering layer, the outer wall of the buffering layer is wrapped by the metal armor cladding, the outer wall of the metal armor cladding is wrapped by the reinforcing layer, and the outer wall of the reinforcing layer is wrapped by the outer protective layer. The core layer and the cladding are made of a homogeneous material doped with silica glass or pure silica glass. The refractive index of the core layer is larger than that of the cladding. The buffering layer is filled with an aramid fiber in a knitting mode. According to the novel temperature measuring cable, high-precision, quick-response and high-strength optical fiber temperature measurement can be achieved, and the novel temperature measuring cable is simple in structure and long in service life.
Owner:WUHAN XINGUANGNIAN PHOTOELECTRIC TECH
Illumination unit for endoscope and endoscope
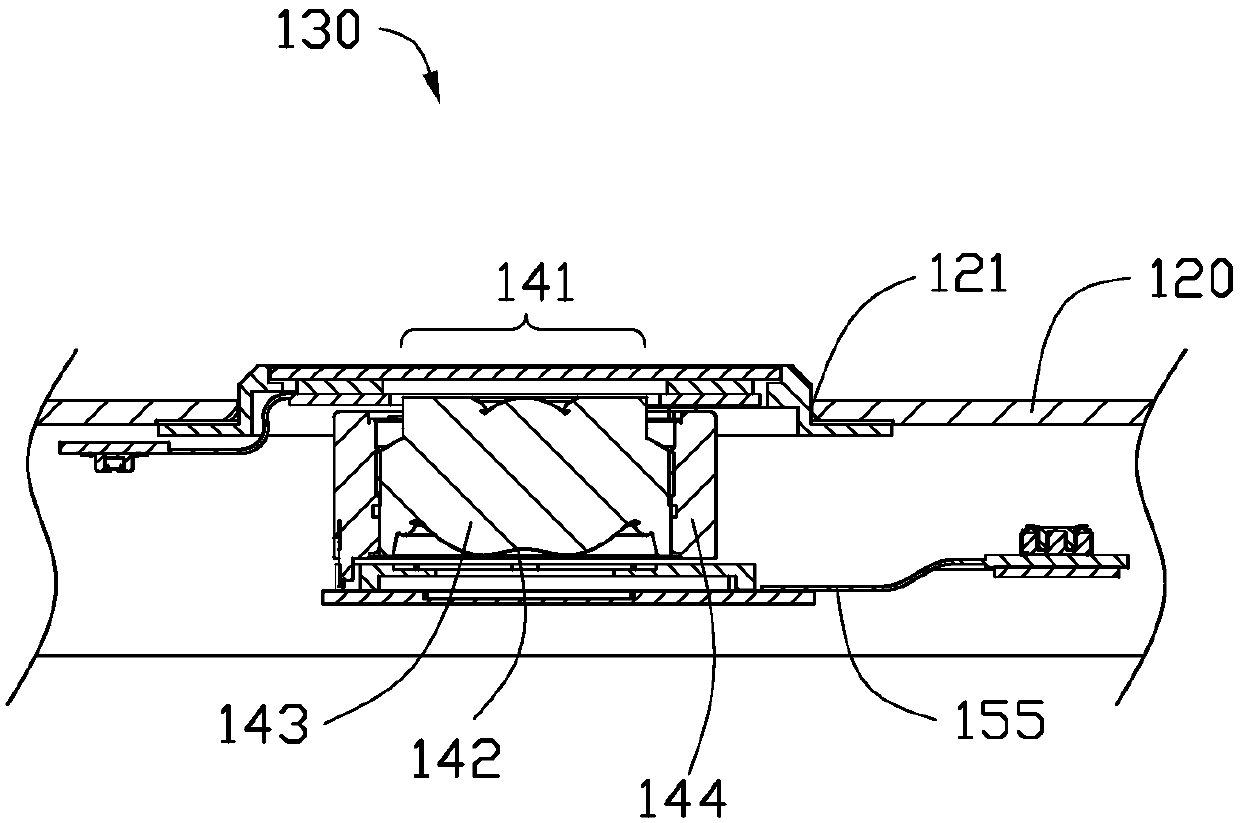
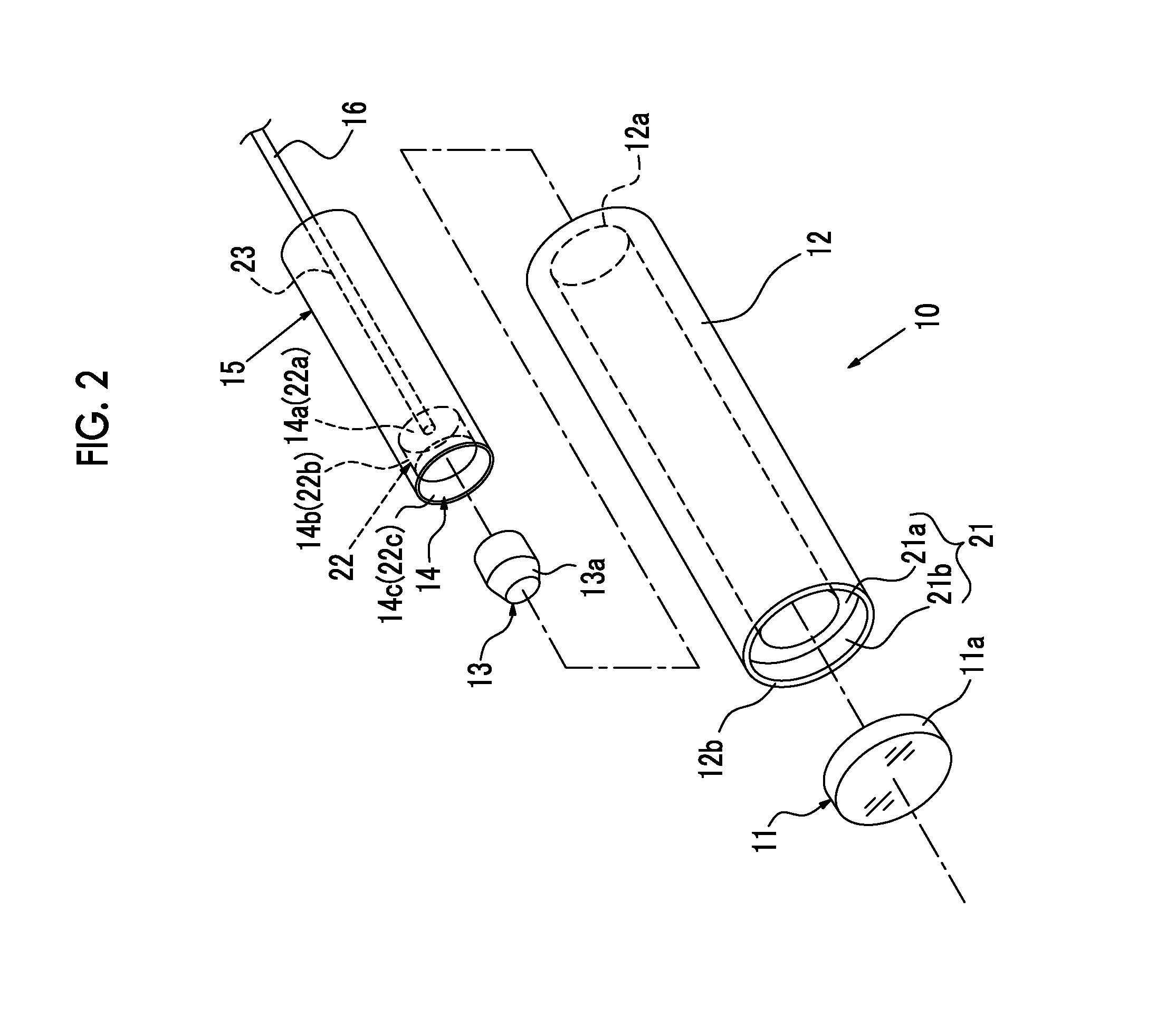
An illumination unit for an endoscope, which does not increase in diameter and has high emission intensity, is provided. A fluorescent body-holding portion 22 is formed at a tip of the ferrule 15, and a metal reflective film 14 is formed on an inner peripheral surface of the fluorescent body-holding portion 22. The fluorescent body 13 is irradiated with blue laser light emitted from a tip of the optical fiber 16 and the blue laser light and excitation light of the fluorescent body are mixed, so that pseudo white light is obtained. When the fluorescent body 13 is formed in a substantially columnar shape, an emission diameter of the fluorescent body is denoted by D1, a thickness of the protective cover 11 is denoted by t1, and an effective diameter of the protective cover is denoted by D2, “0.7 mm≦D1≦0.9 mm”, “0.4 mm≦t1≦0.59 mm”, and “1.3 mm≦D2≦1.5 mm” are satisfied.
Owner:FUJIFILM CORP
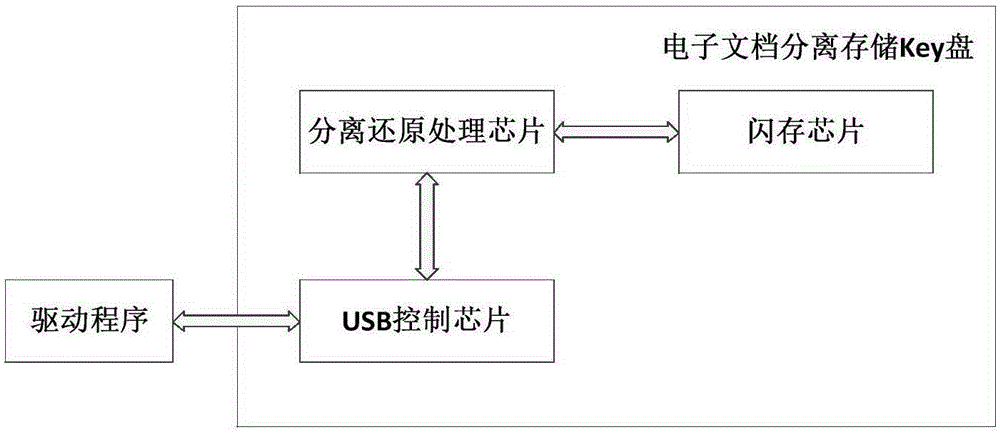
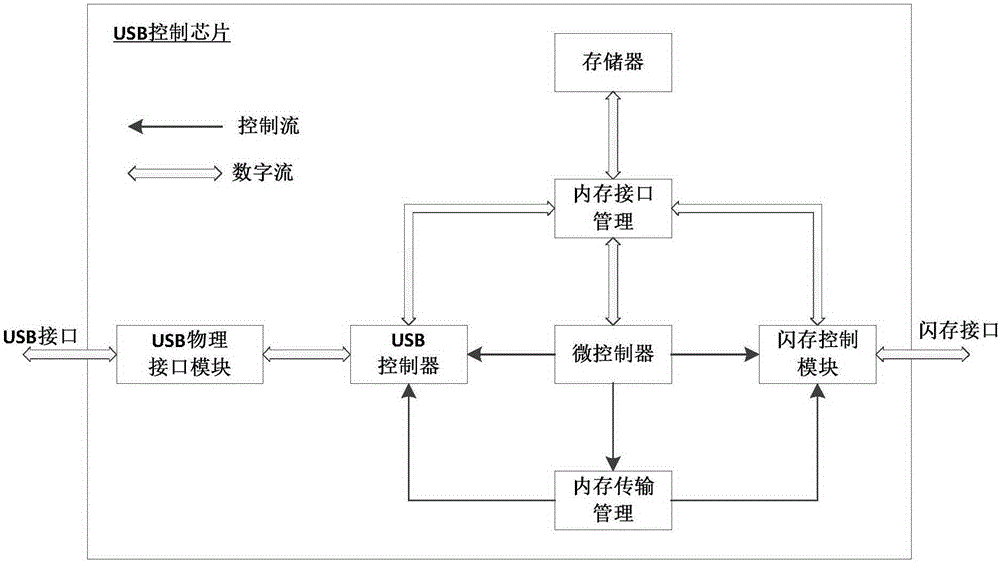
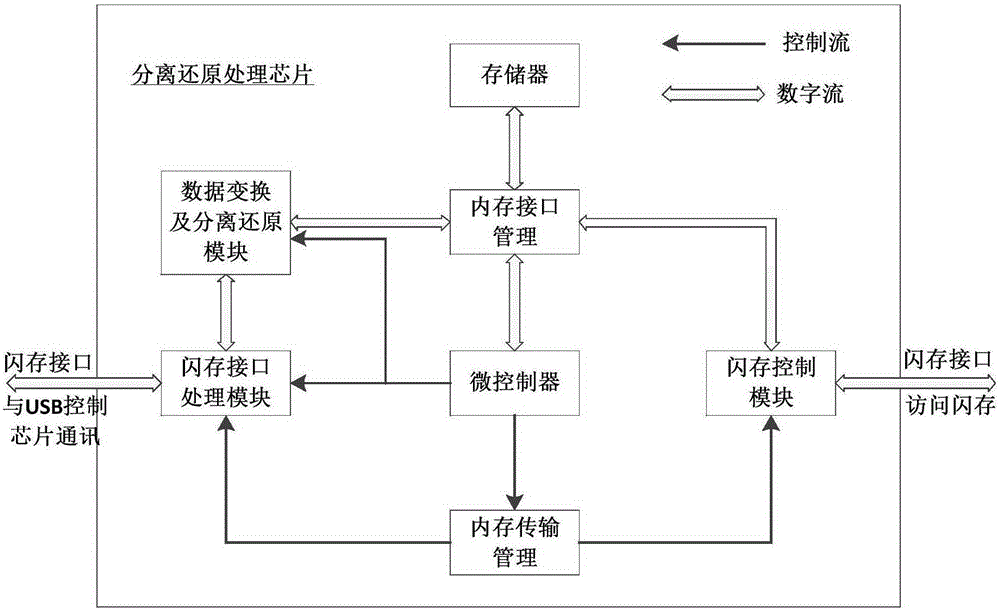
Data separate storage and reduction key disk and data separation and reduction method thereof
ActiveCN105184185APrevent leakageEffective Document Leakage Prevention Management MeasuresDigital data protectionElectronic documentUSB
The invention discloses a data separate storage and reduction key disk. The key disk comprises a USB control chip, a separation and reduction processing chip and a flash memory chip. The USB control chip receives and analyzes commands and data transmitted by a drive program through a USB port. The flash memory chip receives commands and data sent by the separation and reduction processing chip and stores the data. The separation and reduction processing chip is connected with the USB control chip and the flash memory chip and separates and reduces the data. An electronic document is separated step by step through the chips in the key disk, two data strings are generated finally, the two data strings are stored separately, a user can prevent the electronic document from being divulged just by ensuring the security of any data string, and therefore an effective document divulging prevention means is provided. The means has higher protection intensity than an existing security and secrecy system and is suitable for application and popularization.
Owner:丽水至行科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com