Software shelling method based on software protection device, software shelling system and software protection method
A software protection device and software protection technology, applied in the fields of software packing, system and software protection, can solve the problems of easy cracking of the protected software, and achieve the effect of increasing the protection strength
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
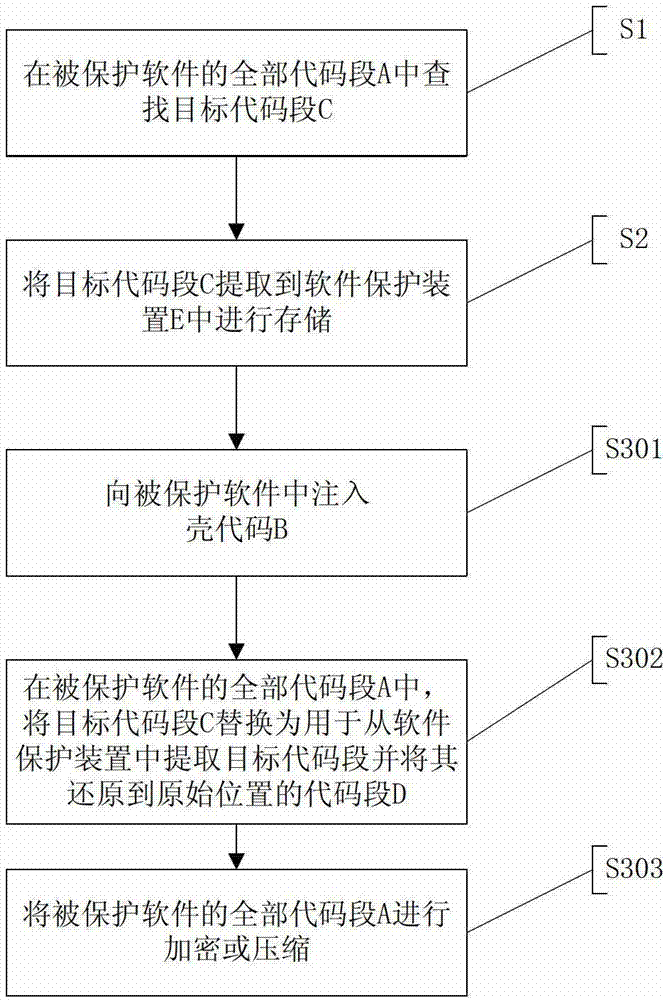
[0054] Such as figure 1 and figure 2 As shown, the software packing method based on the software protection device in Embodiment 1 includes the following steps:
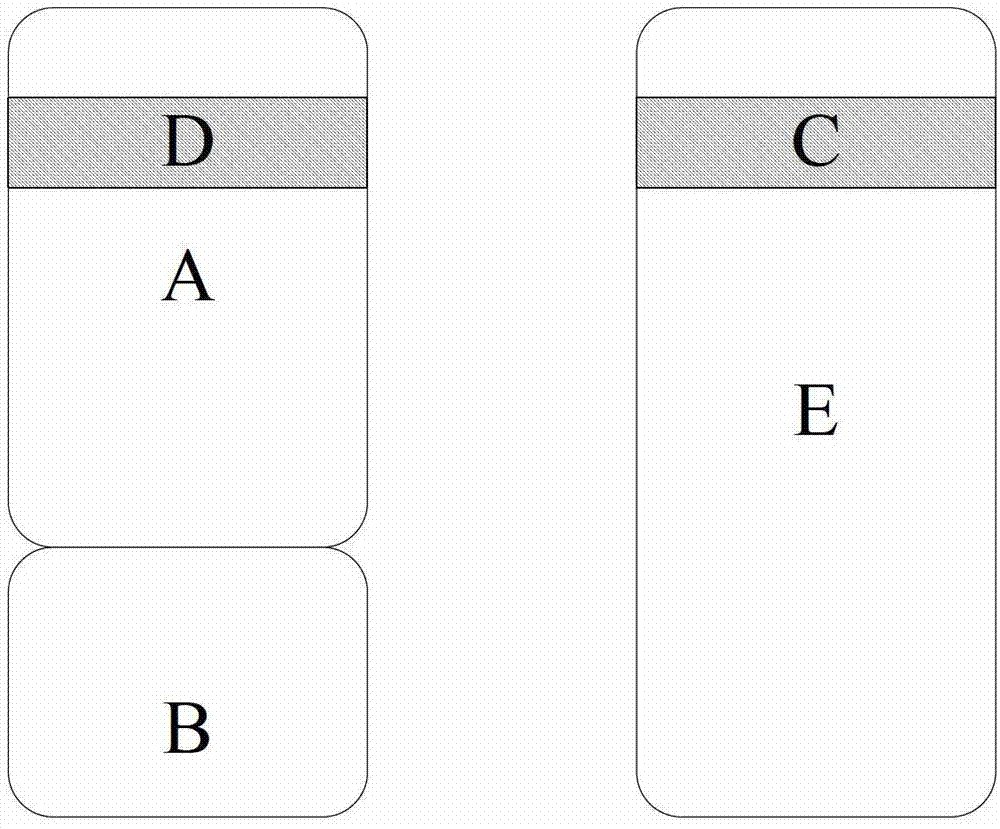
[0055] S1: Find the target code segment C in all code segments A of the protected software;
[0056] Since the target code segment C will be replaced with a section of other codes in the subsequent steps, the target code segment C will meet the following requirements: the protected software cannot jump to the inside of the target code segment C outside the target code segment C ( i.e. somewhere in the middle);
[0057] Since the target code segment C is to be extracted into the software protection device E, the target code segment C can only be executed from the first instruction. Therefore, in all the code segments A of the protected software, except for the target code segment C, no There are other codes that can jump directly to the middle of the target code section C. Limited to this condition, using the ent...
Embodiment 2
[0073] Such as Figure 4 As shown, the software packing method based on the software protection device of the second embodiment includes the following steps:
[0074] S1: Find the target code segment C in all code segments A of the protected software;
[0075] S2: Extract the target code segment C into the dongle E for storage;
[0076] S311: In all code segments A of the protected software, replace the target code segment C with a code segment D for extracting the target code segment C from the software protection device E and restoring it to the original position;
[0077] S312: Inject shell code B into the protected software;
[0078] S313: Encrypt or compress all code segments A of the protected software.
[0079] It can be seen that the difference between the software packing method in Embodiment 2 and the software packing method in Embodiment 1 is that the execution order of the third and fourth steps is swapped.
[0080] The steps during the operation of the softwar...
Embodiment 3
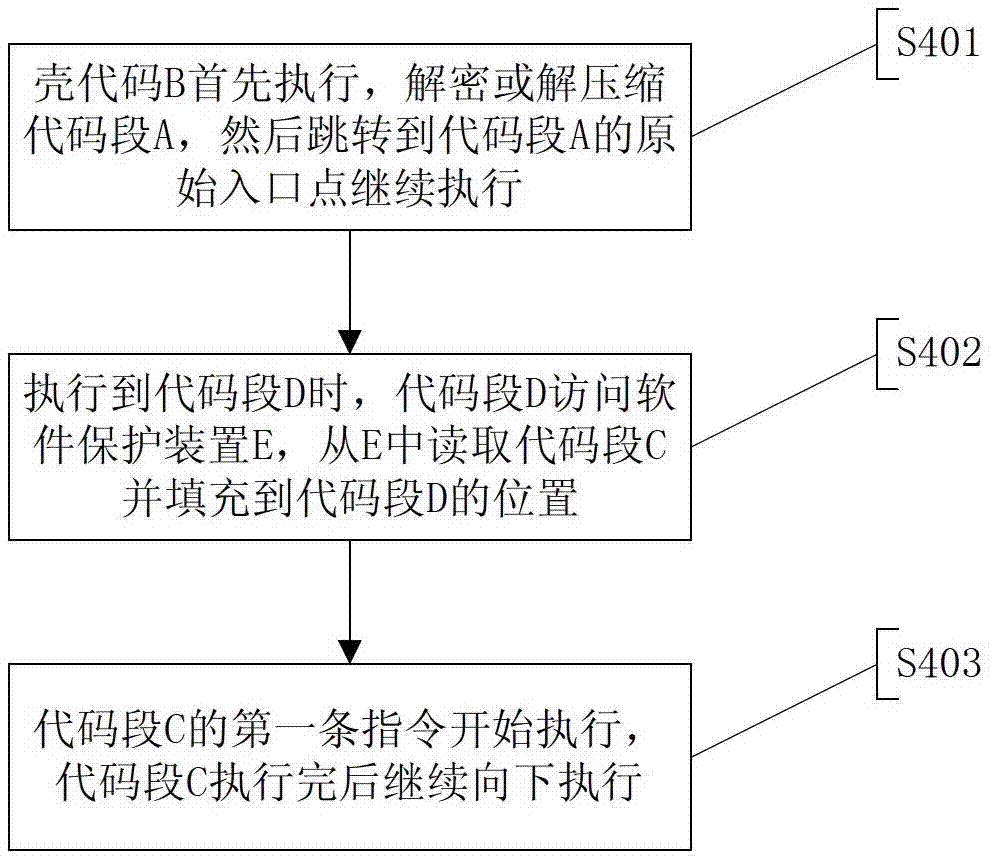
[0085] Such as Figure 5 and Figure 6 As shown, the software packing method based on the software protection device of the third embodiment includes the following steps:
[0086] S1: Find the target code segment C in all code segments A of the protected software;
[0087] Since the target code segment C will be replaced with a section of other codes in the subsequent steps, the target code segment C will meet the following requirements: the protected software cannot jump to the inside of the target code segment C outside the target code segment C ( i.e. somewhere in the middle);
[0088] Since the target code segment C is to be extracted into the software protection device E, the target code segment C can only be executed from the first instruction. Therefore, in all the code segments A of the protected software, except for the target code segment C, no There are other codes that can jump directly to the middle of the target code section C. Limited to this condition, usin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com