Authentication method based on geographic position information
A technology of geographic location information and authentication method, applied in electrical components, transmission systems, etc., to achieve the effect of improving login security and increasing protection strength
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
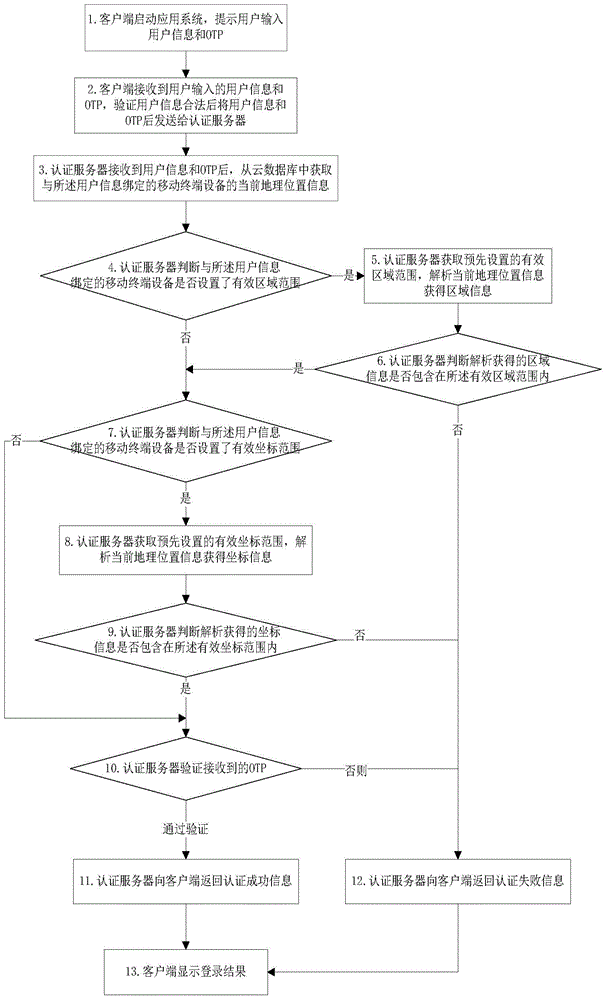
[0033] Embodiment 1 of the present invention provides an authentication method flow based on geographic location information, which is implemented based on an authentication system composed of a client, an authentication server, and a mobile terminal device. The OTP in this embodiment is generated at the mobile terminal and input by the user. to the client, and then sent to the authentication server by the client. The geographic location verification information in this embodiment is specifically the preset geographic location information.
[0034] Such as figure 1 As shown, the authentication method provided in Embodiment 1 includes the following steps:
[0035] Step 1: The client starts the application system and prompts the user to input user information and OTP;
[0036] Specifically, the user information may include a user name and a password, or only include a user name. In this embodiment, the user information only includes the user name as an example for introduction...
Embodiment 2
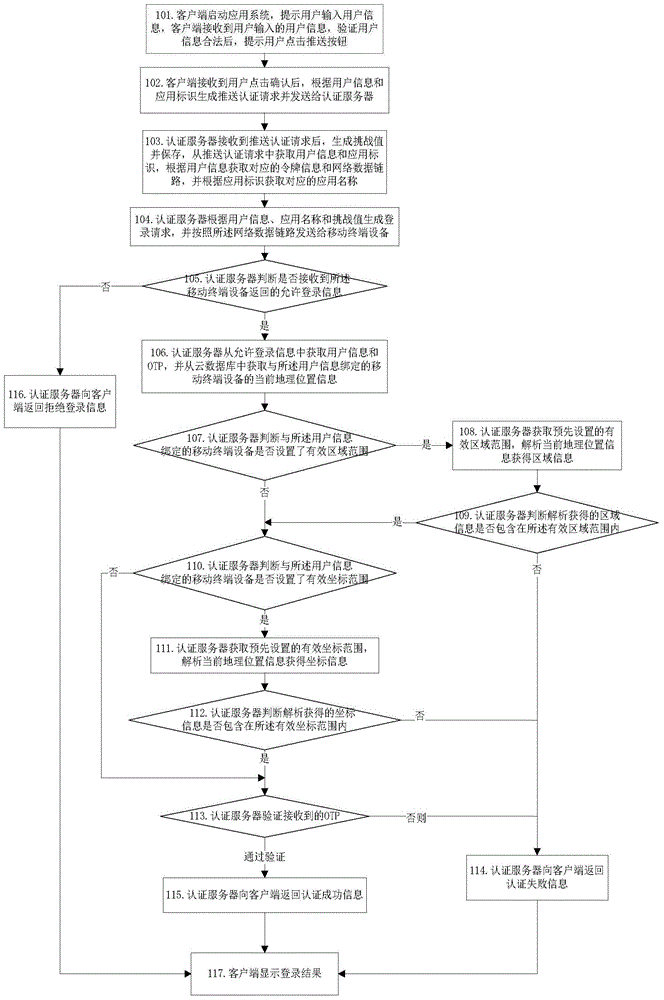
[0113] Embodiment 2 of the present invention provides an authentication method flow based on geographic location information, which is realized based on an authentication system composed of a client, an authentication server, and a mobile terminal device. The OTP in this embodiment is generated at a mobile terminal, and the mobile terminal sent to the authentication server, the geographic location verification information in this embodiment is specifically the preset geographic location information.
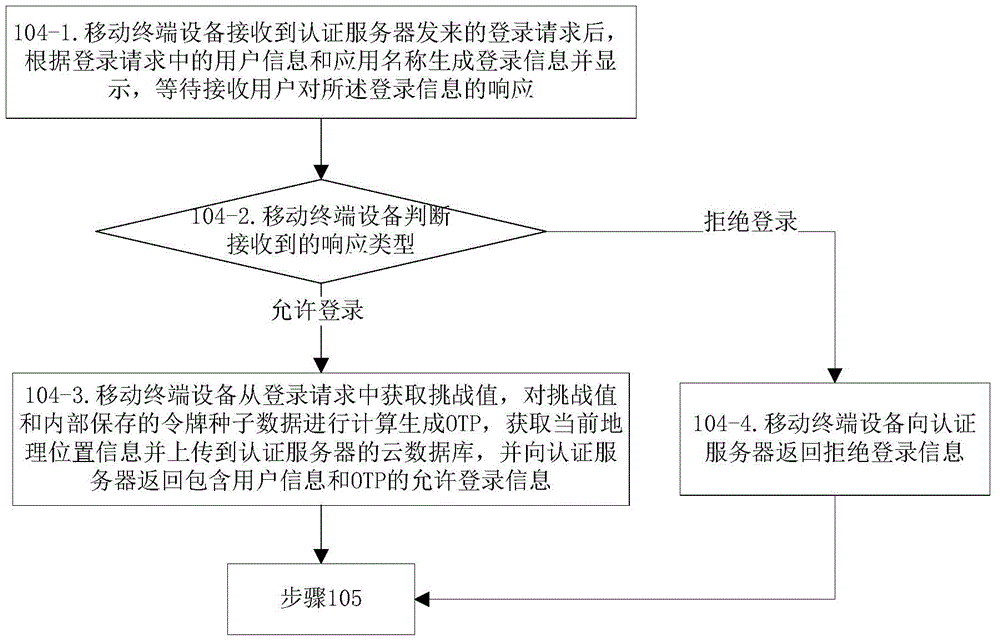
[0114] Such as figure 2 As shown, the authentication method provided in Embodiment 2 includes the following steps:
[0115] Step 101: the client starts the application system, prompts the user to input user information, the client receives the user information entered by the user, and after verifying that the user information is legal, prompts the user to click a push button;
[0116] Specifically, the user information may be a user name, or a user name and a password. In this...
Embodiment 3
[0170] Embodiment 3 of the present invention provides an authentication method flow based on geographic location information, which is implemented based on an authentication system composed of a client, an authentication server, and a mobile terminal device. The OTP in this embodiment is generated at the mobile terminal and input by the user. to the client, and then sent to the authentication server by the client. In this embodiment, the verification of the current geographic location information is to compare it with the geographic location corresponding to the IP address of the client.
[0171] Such as Figure 4 As shown, the authentication method provided in Embodiment 3 includes the following steps:
[0172] Step 1: The client starts the application system and prompts the user to input user information and OTP;
[0173] Specifically, the user information may include a user name and a password, or only include a user name.
[0174] After this step, it also includes: when ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com