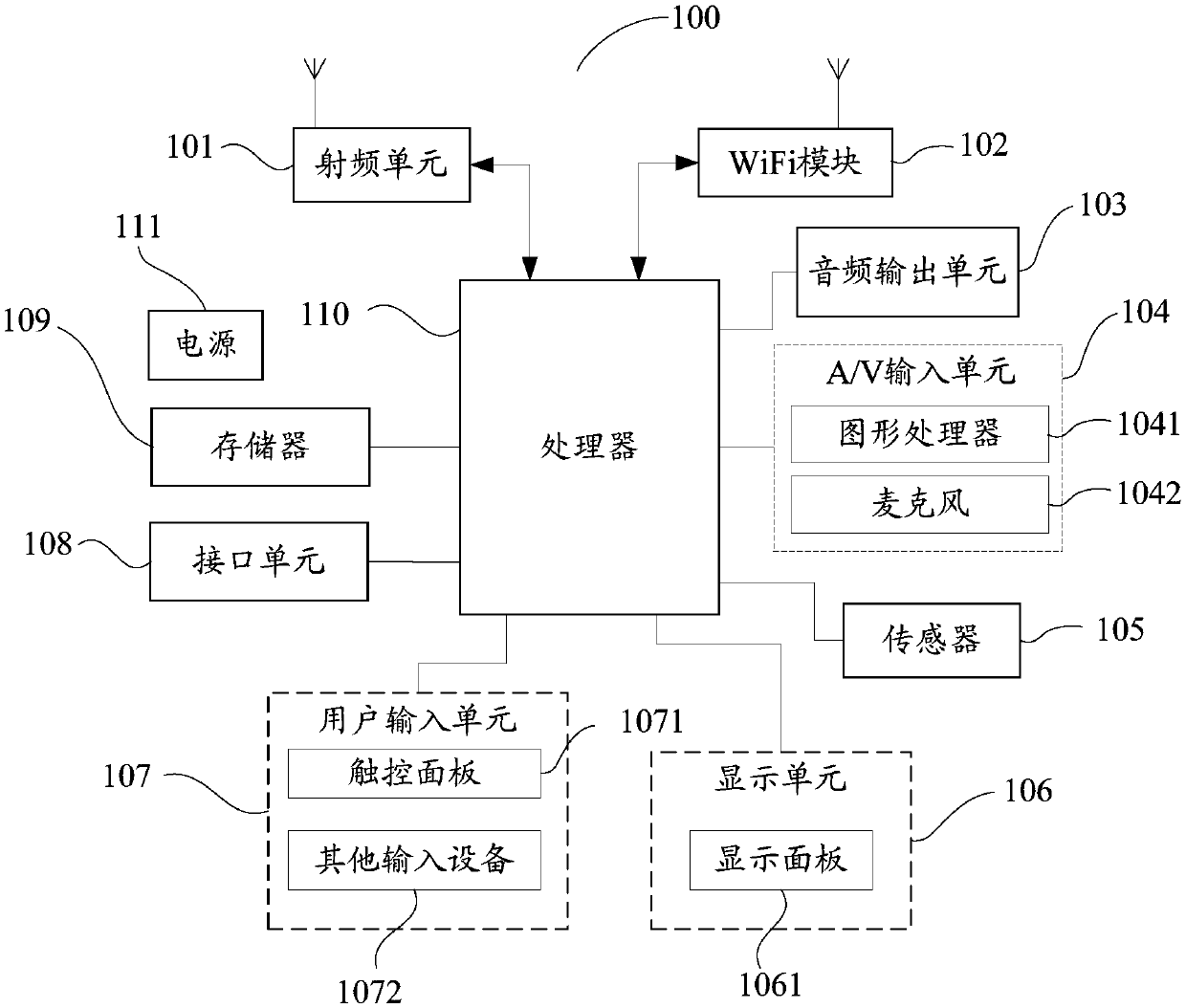
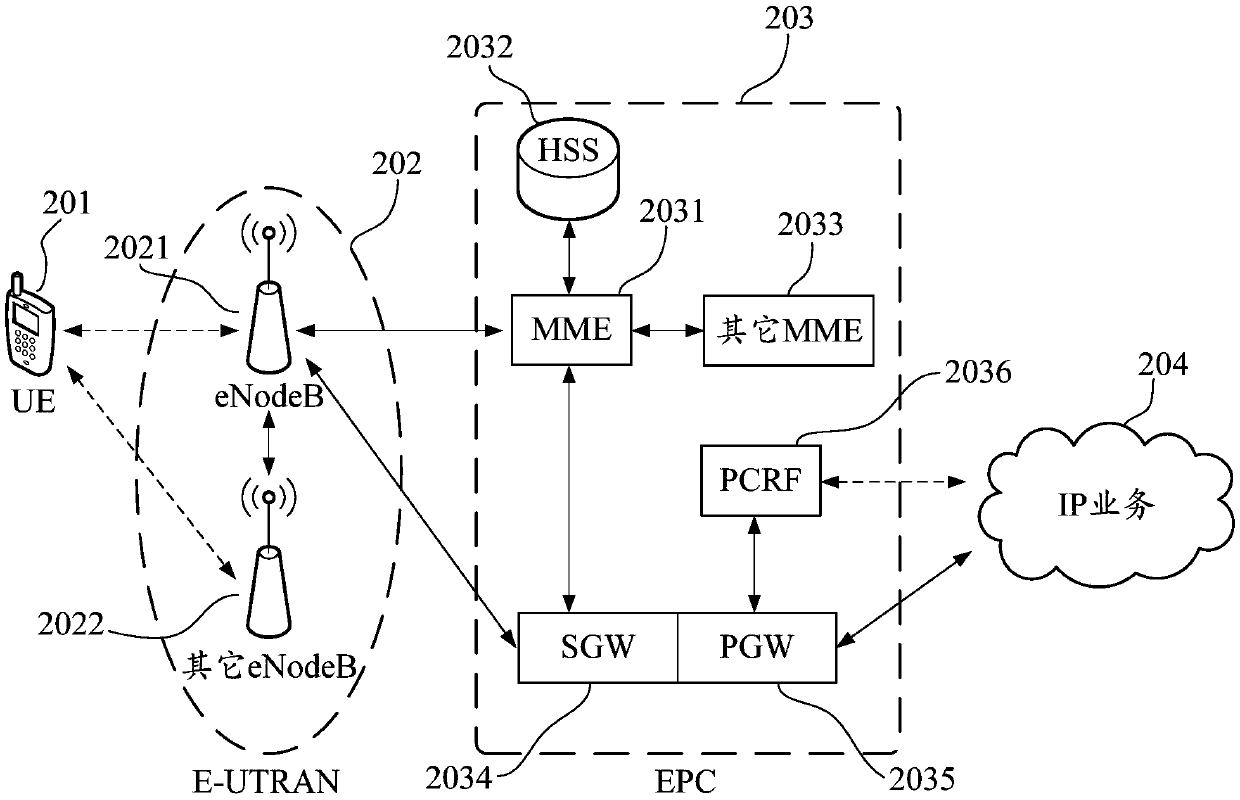
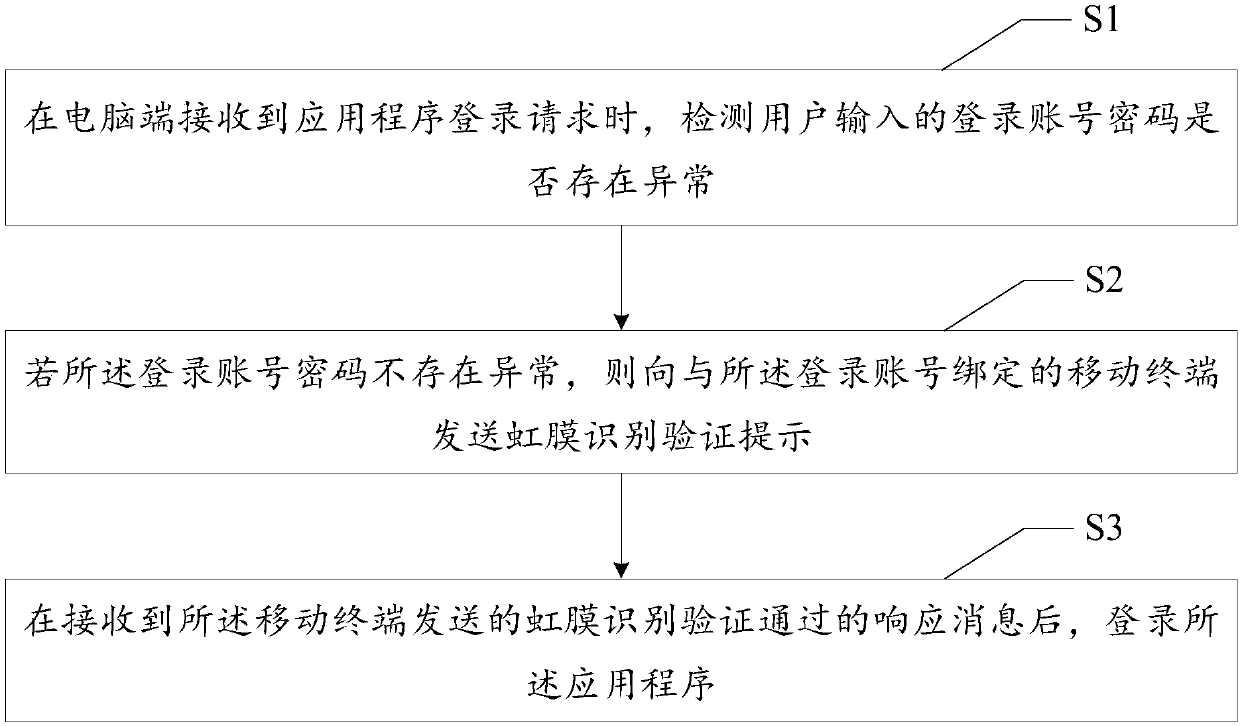
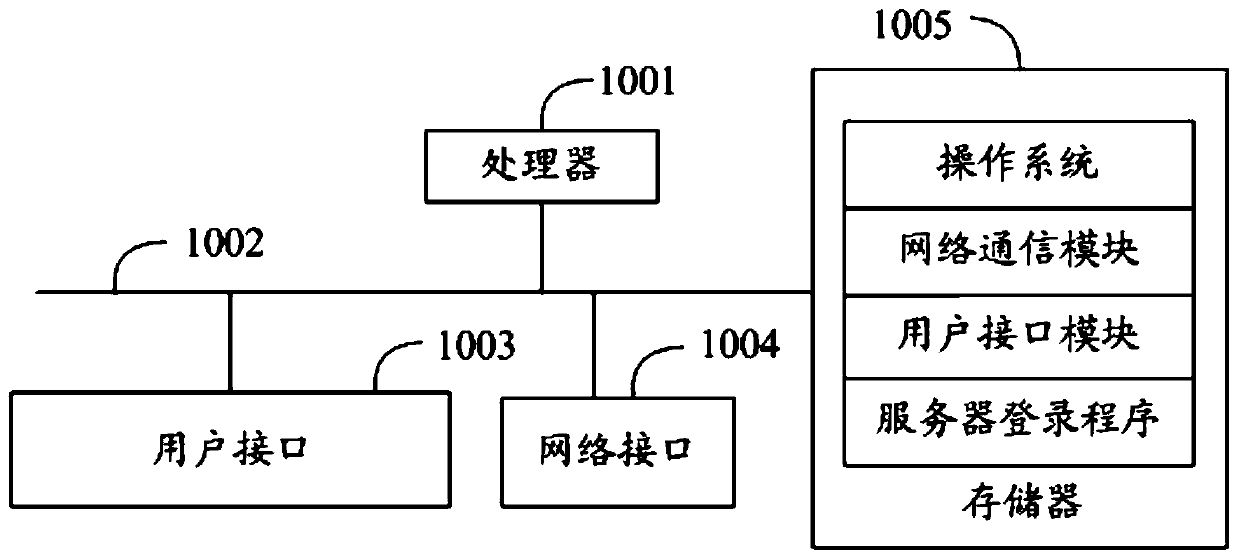
Patents
Literature
48results about How to "Improve login security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Login verification method, system and instant messaging (IM) server
ActiveCN102651739AImprove login securityEnsure safetyData switching networksValidation methodsWeb service
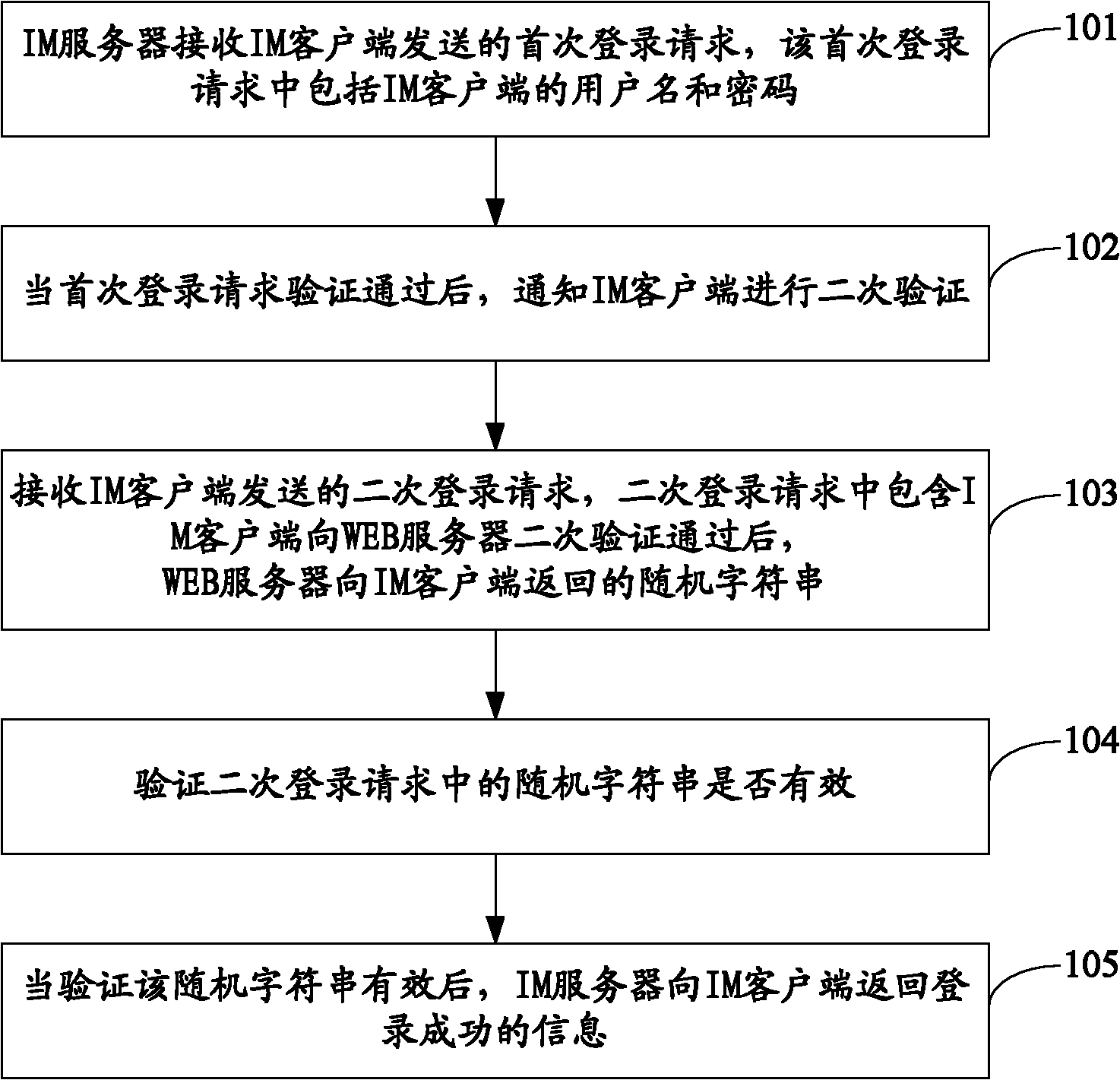
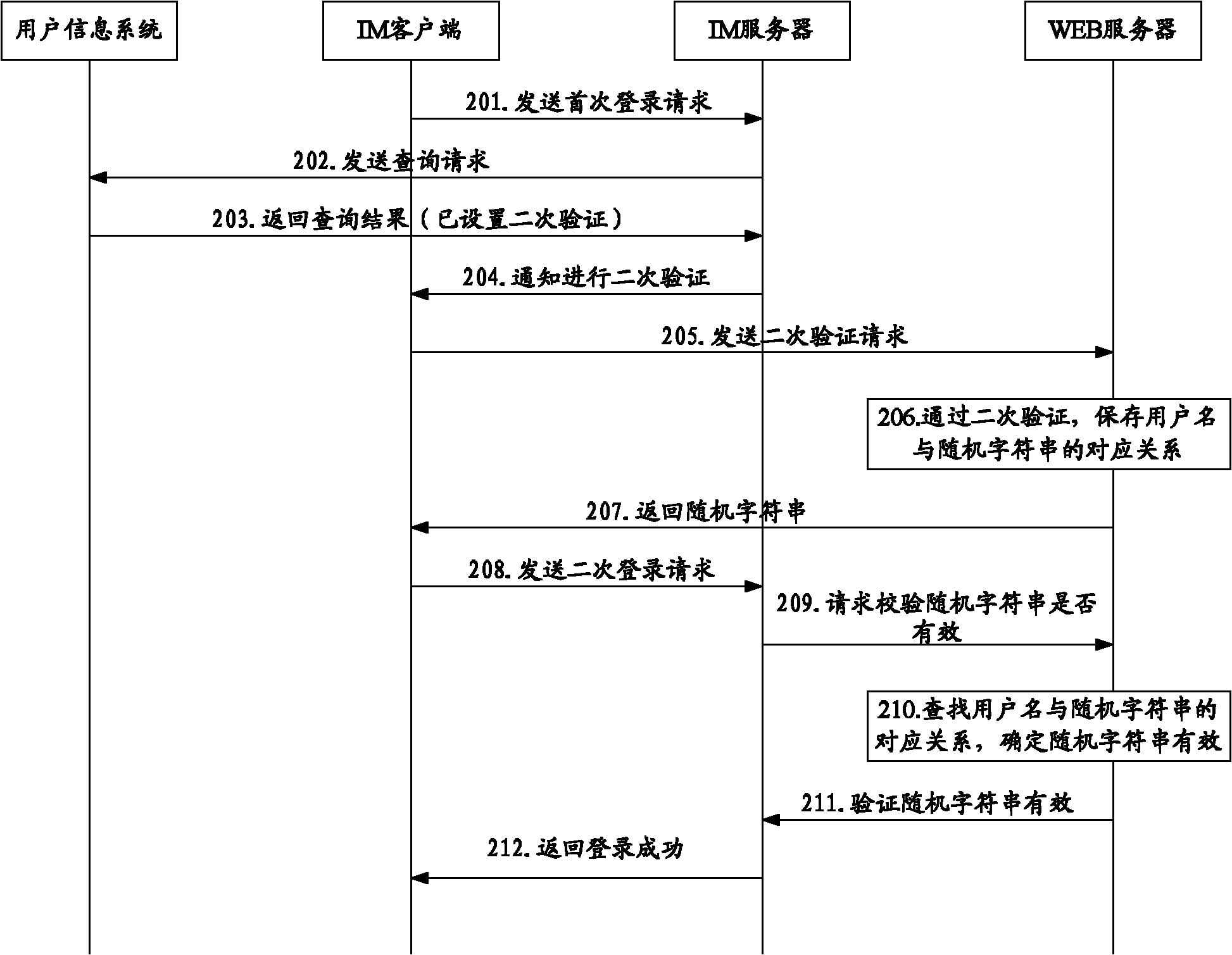
The embodiment of the invention discloses a login verification method, a system and an instant messaging (IM) server. The method comprises the following steps that: the IM server receives first-time login requests sent by an IM client, and the first-time login requests comprise user names and passwords of the IM client; when the first-time login request verification is passed, the IM client is notified to carry out second-time verification; the second-time login requests sent by the IM client is received, the second-time login requests comprise random character strings returned by a web server to the IM client after the second-time verification of the IM client to the web server is passed; whether the random character strings in the second-time login requests are valid or not is verified; and when verification results show that the random character strings are valid, the IM server returns the login successful information to the IM client. Because of the introduction of the second-time verification process in the embodiment of the invention, only the login security of users is improved.
Owner:ALIBABA GRP HLDG LTD
Login credentials verifying method and apparatus
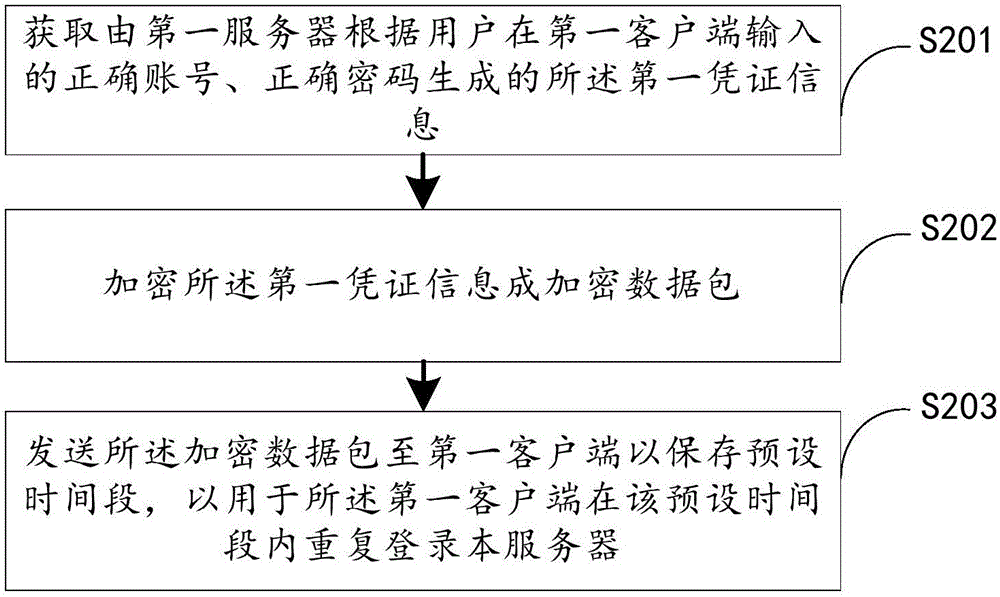
InactiveCN106790183AEnsure safetyAvoid cross-device loginsEncryption apparatus with shift registers/memoriesNetwork packetUser identifier
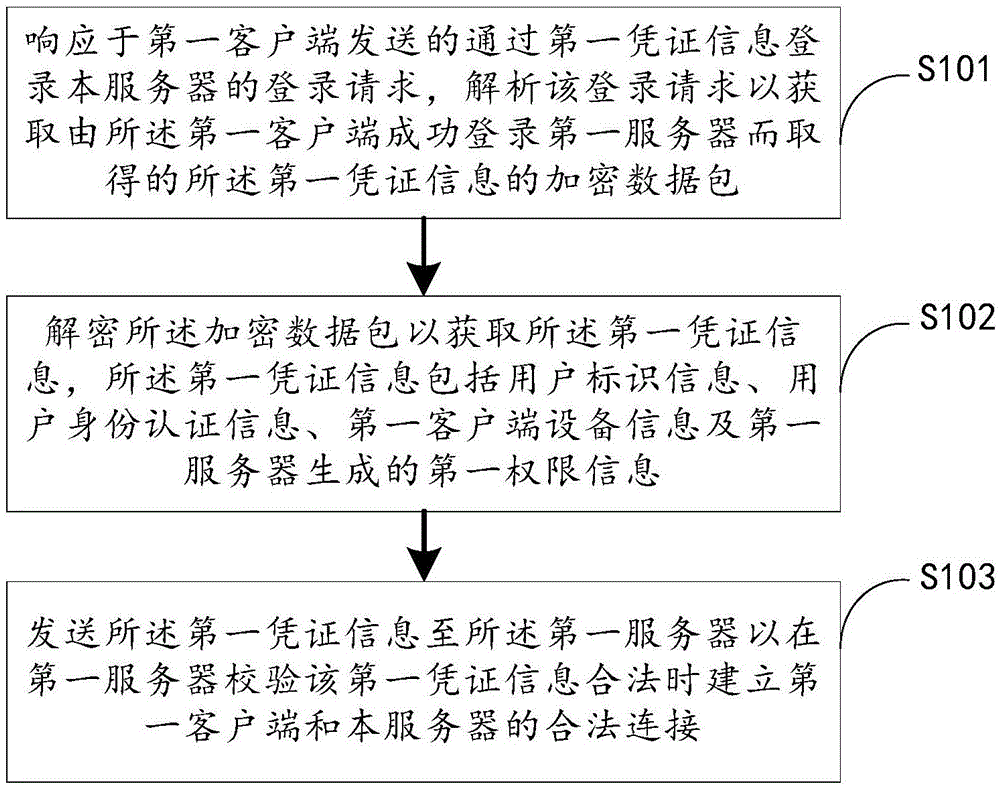
The invention discloses a login credentials verifying method and apparatus. The verifying method comprises the following steps: in response to a login request transmitted by a first client for logging in a local server by virtue of first credentials information, parsing the login request to acquire an encryption data packet of the first credentials information obtained when the first client successfully logs in a first server; parsing the encryption data packet to acquire the first credentials information, wherein the first credentials information comprises user identifier information, user identification information, first client device information and first permission information generated by the first server; and transmitting the first credentials information to the first server so as to verify a legal connection between the first client and the local server established when the first credentials information is legal at the first server. In addition, the invention also provides a login credentials verifying apparatus. By adopting the login credentials verifying method and apparatus, the automatic login of the client in a preset period of time can be realized, and the login security of the client is also ensured.
Owner:GUANGZHOU HUADUO NETWORK TECH
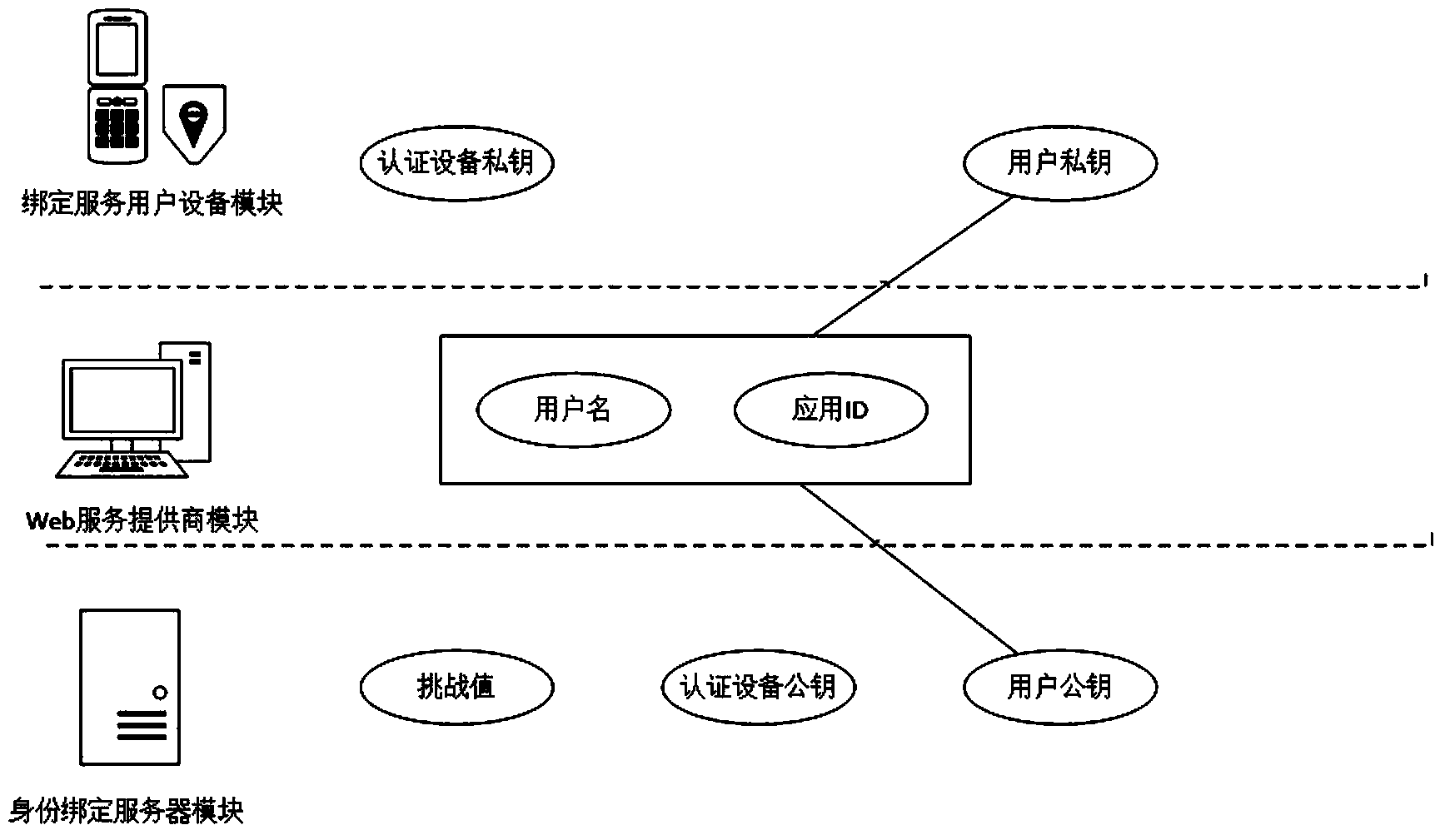
Multi-SP safety binding implementation method based on intelligent terminal local authentication
The invention relates to a multi-SP safety binding implementation method based on intelligent terminal local authentication. A trust presetting idea is introduced, public and private key certificates of an authentication device are preset, and the authentication device is bound with an identify authentication terminal. A user logs into SPs, a user public and private key UAuth for marking the authentication device is generated, and the UAuth is bound with a user account. A one-to-many bidirectional association is carried out on the safety authentication device held by the user and multiple accounts of the user in the same SP or accounts in multiple different SPs. By means of the multi-SP safety binding implementation method, a large amount of identify authentication can be successfully carried out through the unique safety device by the user, and a traditional user name password identify authentication mode is replaced to a great degree. In addition, under the condition that the convenient user identity authentication operation is guaranteed, the information safety in the authentication process is greatly improved.
Owner:INST OF INFORMATION ENG CAS
Mobile application unified login method and device
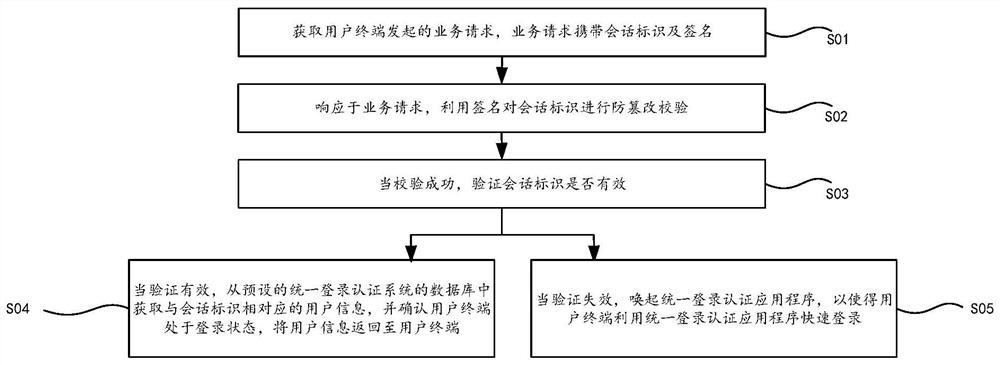
PendingCN111814133AImprove login securityQuick login succeededDigital data authenticationTamper resistanceSoftware engineering
The embodiment of the invention provides a mobile application unified login method and device, and relates to the technical field of base frame operation and maintenance. The method comprises the steps: obtaining a service request initiated by a user terminal, and enabling the service request to carry a session recognition and a signature; in response to the service request, performing tamper-proof verification on the session identifier by utilizing the signature; when the verification succeeds, verifying whether the session identifier is valid or not; when the verification is valid, obtaininguser information corresponding to the session identifier from a preset database of the unified login authentication system, confirming that the user terminal is in a login state, and returning the user information to the user terminal; and when the verification fails, evoking the unified login authentication application program, so that the user terminal quickly logs in by using the unified loginauthentication application program. According to the technical scheme provided by the embodiment of the invention, the problem of low login management safety in the prior art can be solved.
Owner:PINGAN INT SMART CITY TECH CO LTD
Instant communication service login method
ActiveCN102231716AReduce data interactionImprove login processing efficiencyUser identity/authority verificationData switching networksCommunications serverEngineering
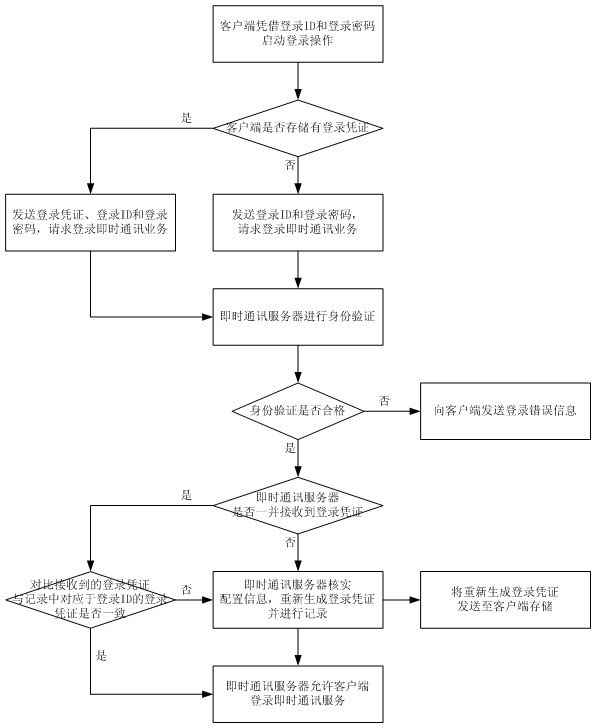
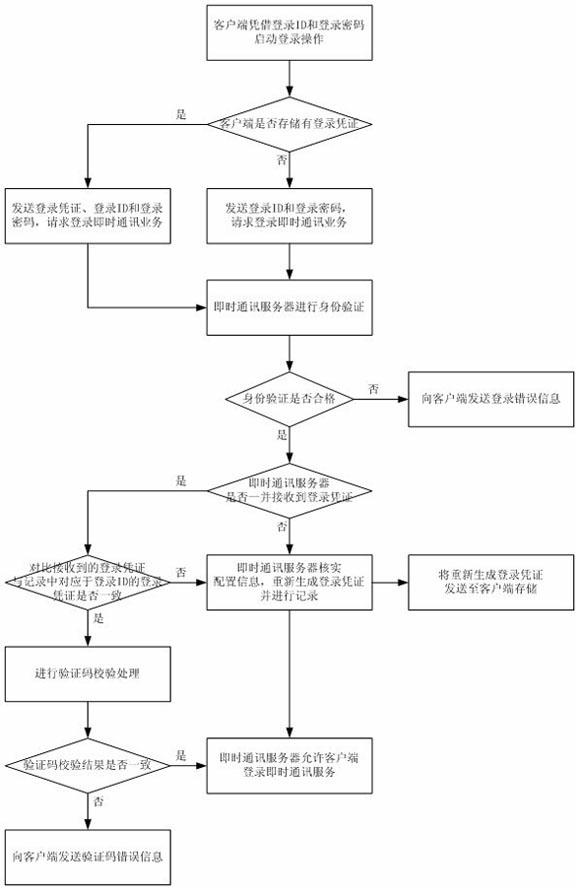
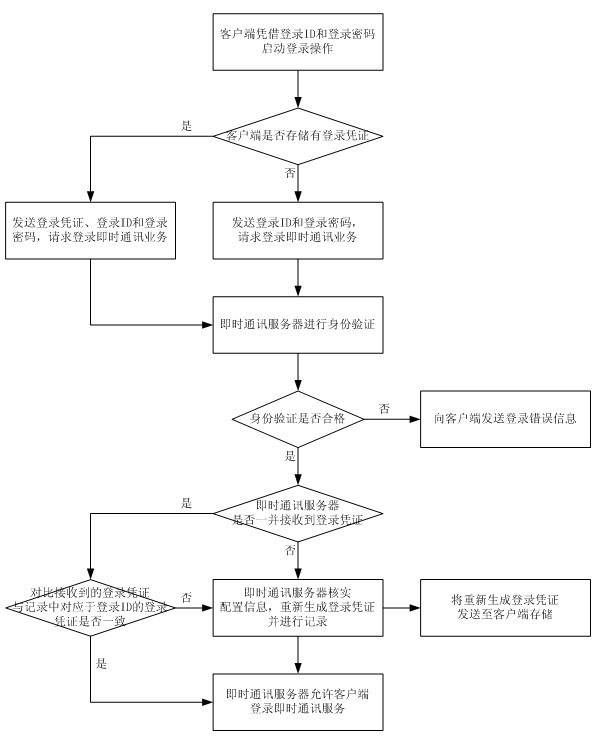
The invention provides an instant communication service login method. The technical scheme of the method is as follows: an instant communication server generates a corresponding login voucher of a login ID which has logged in an instant communication service successfully, records the login voucher in the instant communication server, and returns the login voucher to a client for storage; when the client logs in again with the login ID and a login code which have been successful in logging the instant communication service, the client sends the login voucher stored in the client, after successful identity verification of the login ID and the login code by the instant communication server, the instant communication server compares the received login voucher with the login voucher of the login ID recorded in the instant communication server, if the two login vouchers are consistent, then there is no need to verify configuration information and the client is allowed to login the instant communication service. Through the method in the invention, there is no need to verify the configuration information repeatedly in every login operation, thereby data interaction in a login process of the instant communication service is reduced, login processing efficiency is raised, and user experience is improved.
Owner:NEW SINGULARITY INT TECHN DEV
Application program login method, computer side, mobile terminal, system and storage medium
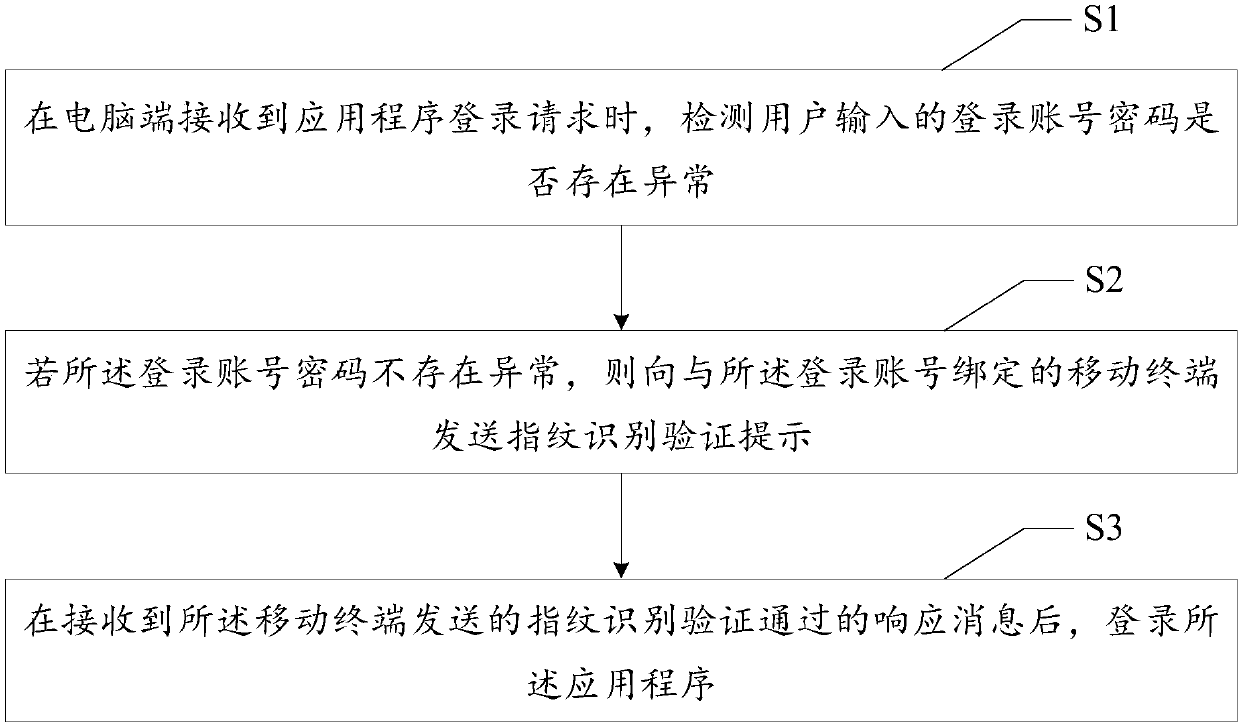
PendingCN109558718AEnsure information securityImprove login securityDigital data authenticationPasswordApplication software
The invention discloses an application program login method, a computer end, a mobile terminal, a system and a readable storage medium, and the method comprises the steps: detecting whether a login account password input by a user is abnormal or not when the computer end receives an application program login request; if the login account password is not abnormal, sending a fingerprint identification verification prompt to a mobile terminal bound with the login account; and logging in the application program after receiving a response message which is sent by the mobile terminal and passes thefingerprint identification verification. Through double verification of password verification and fingerprint verification, the identity and login safety of the user are authenticated, so that the login safety coefficient is improved, and the information safety of the user is ensured.
Owner:NUBIA TECHNOLOGY CO LTD
Client authentication method, password agent device and system
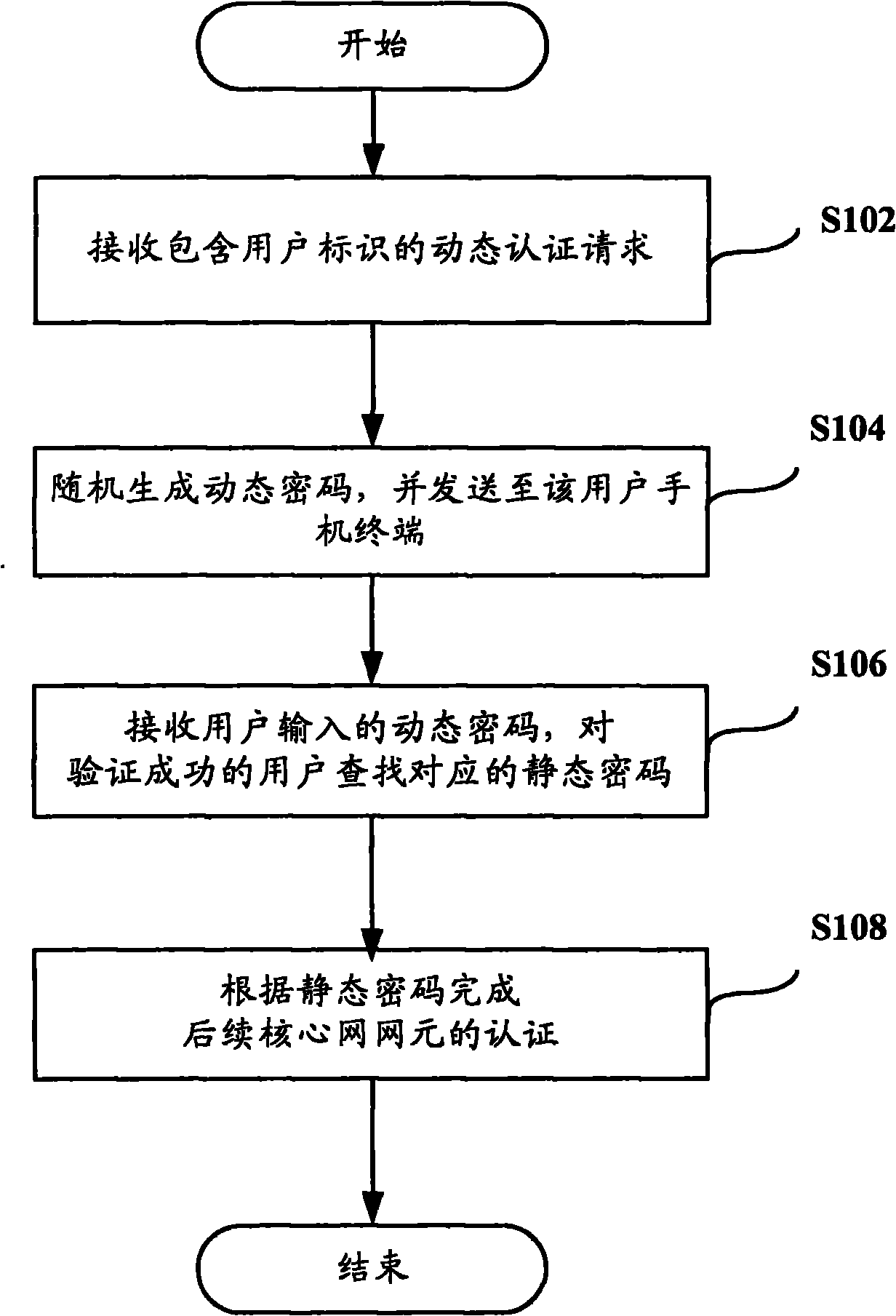
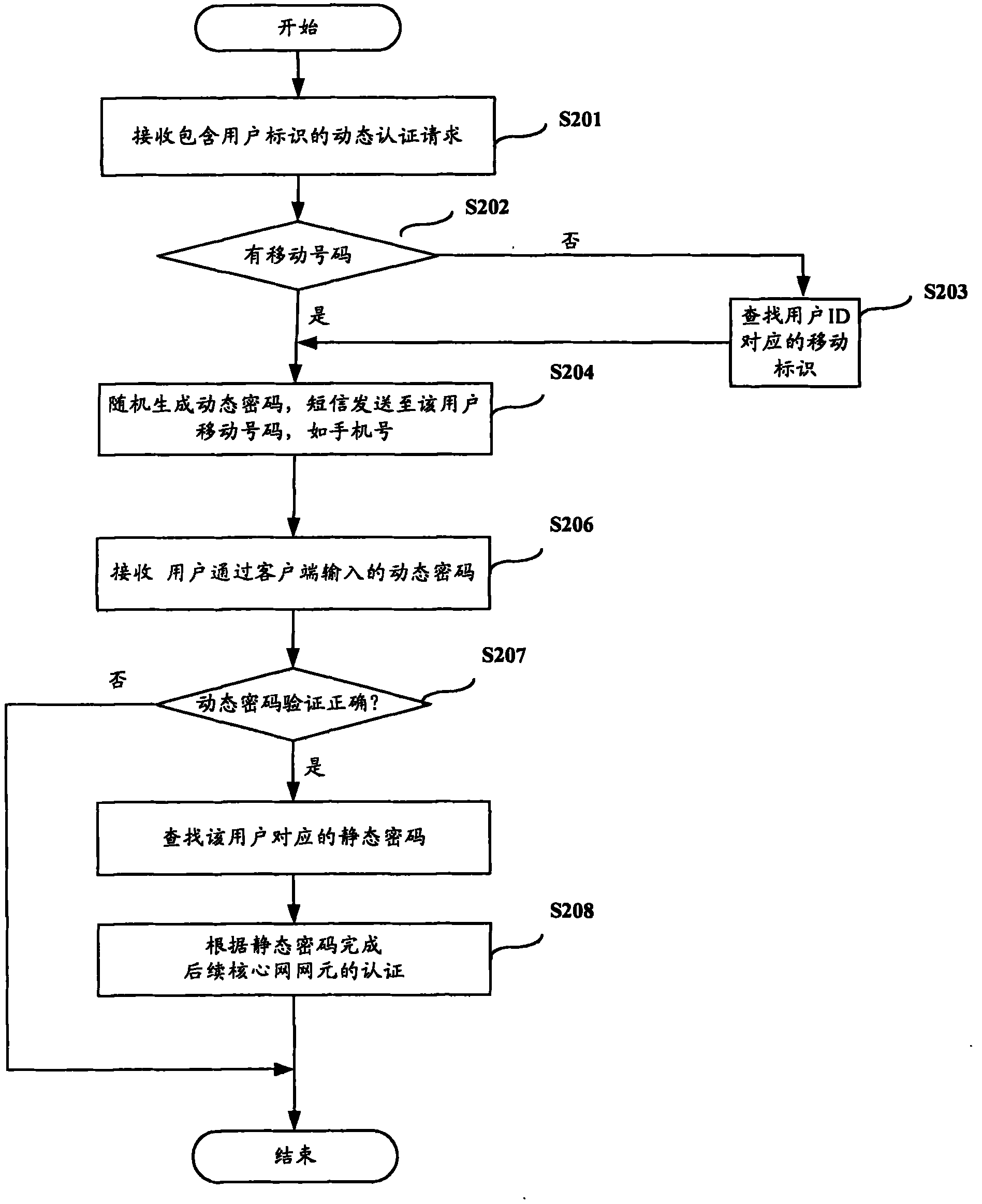
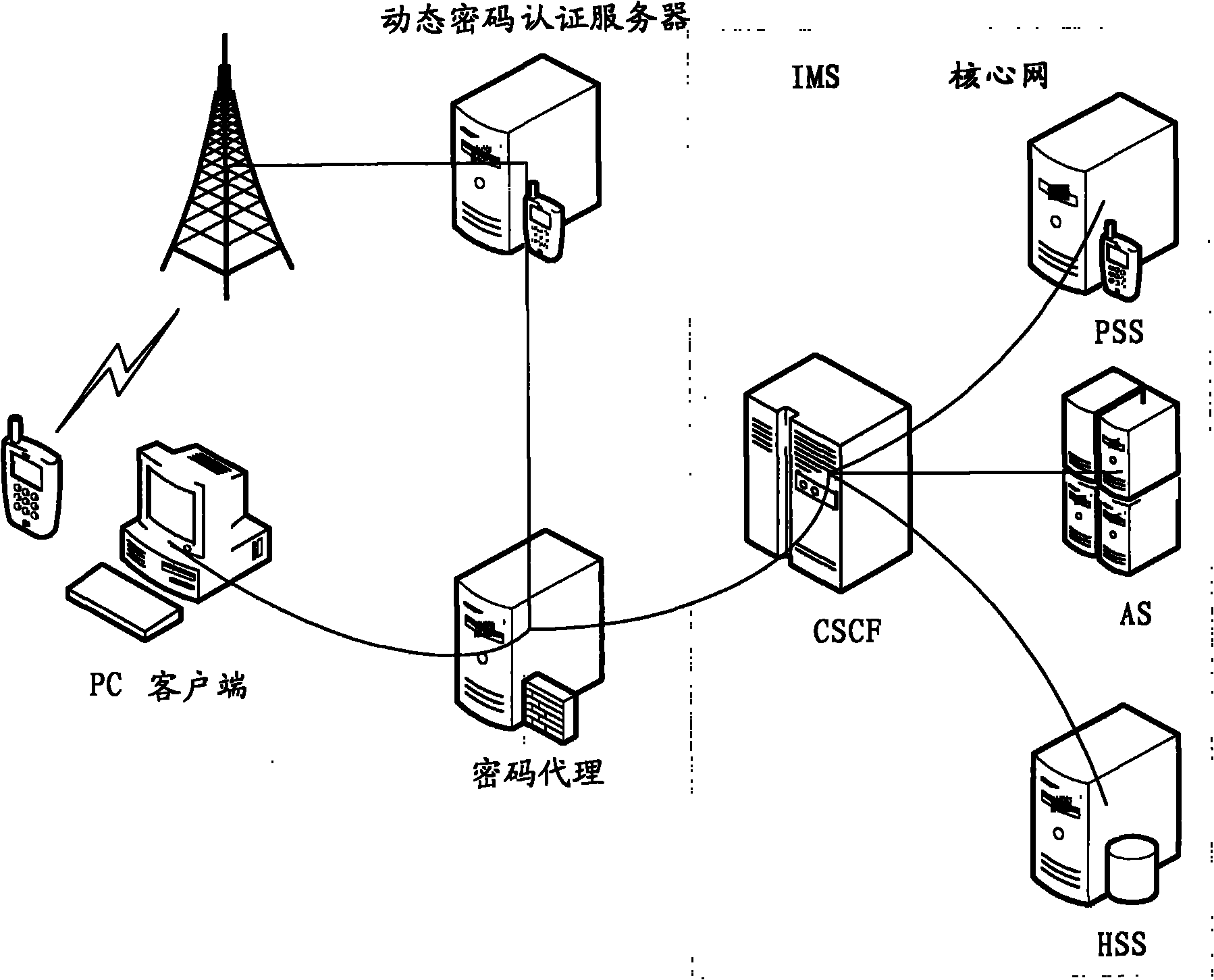
InactiveCN101998387AImprove login securityImprove securityAnswer-back mechanismsSecurity arrangementPasswordAuthentication
The invention discloses a client authentication method, a password agent device and a system. The method comprises the following steps of: receiving a dynamic authentication request containing user identification; generating a dynamic password according to the dynamic authentication request, and sending the dynamic password to the user; receiving the dynamic password of the user, and searching a corresponding static password for the user passing the verification; and performing authentication on a subsequent core network element according to the static password. The method can improve the security of client login, and overcomes the defect of low reliability in the IMS login mode in the prior art.
Owner:CHINA MOBILE COMM GRP CO LTD
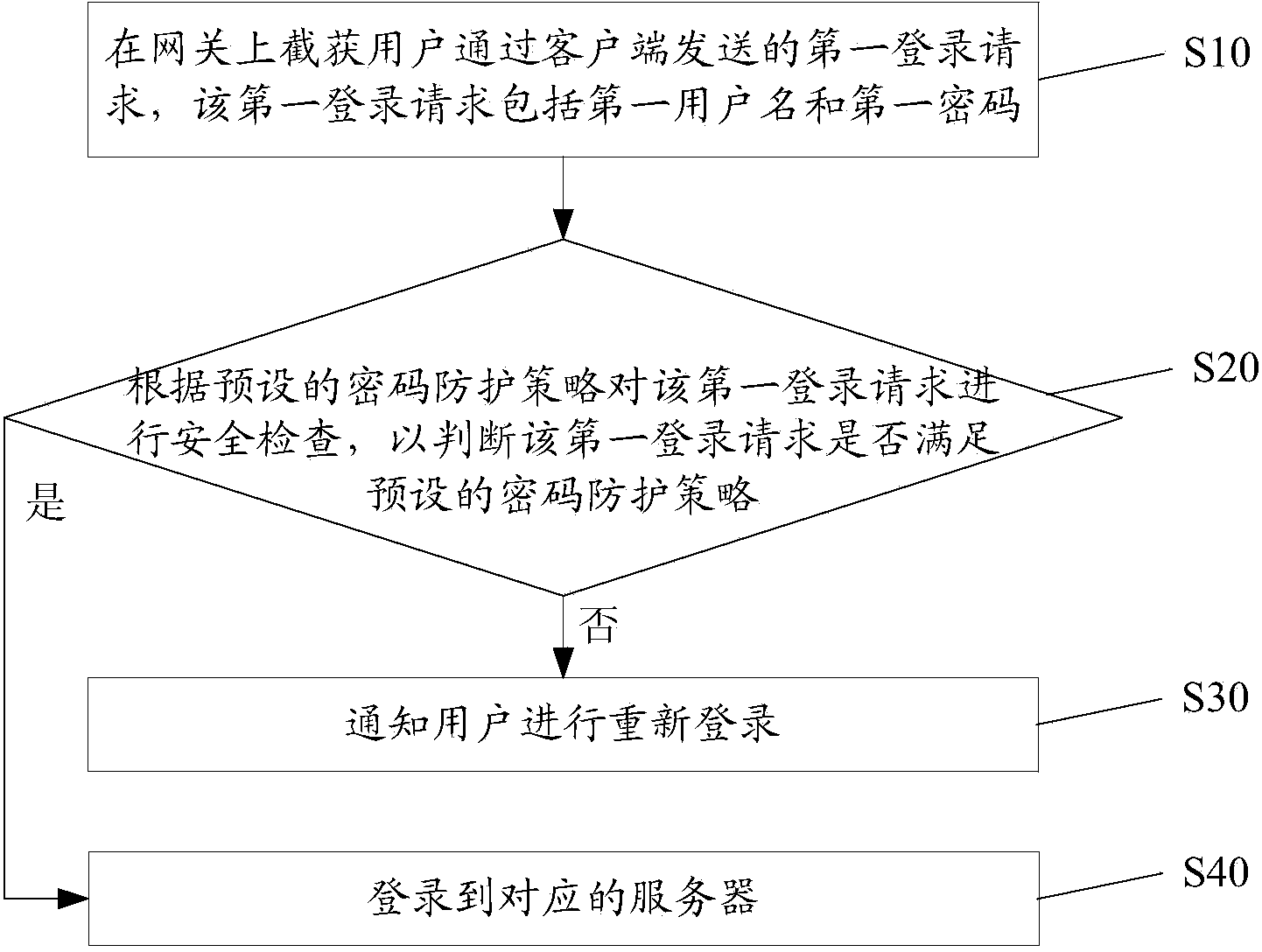
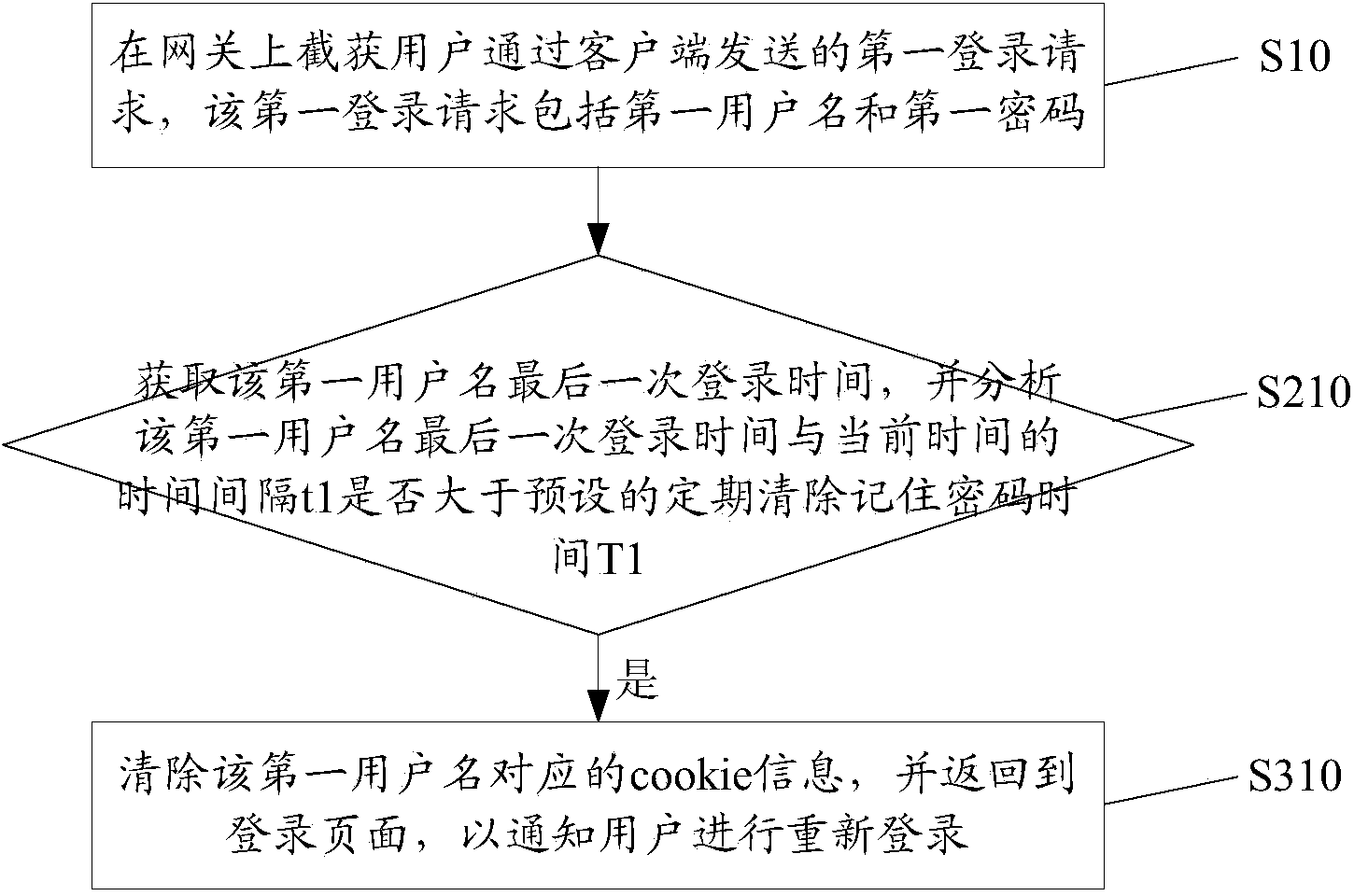
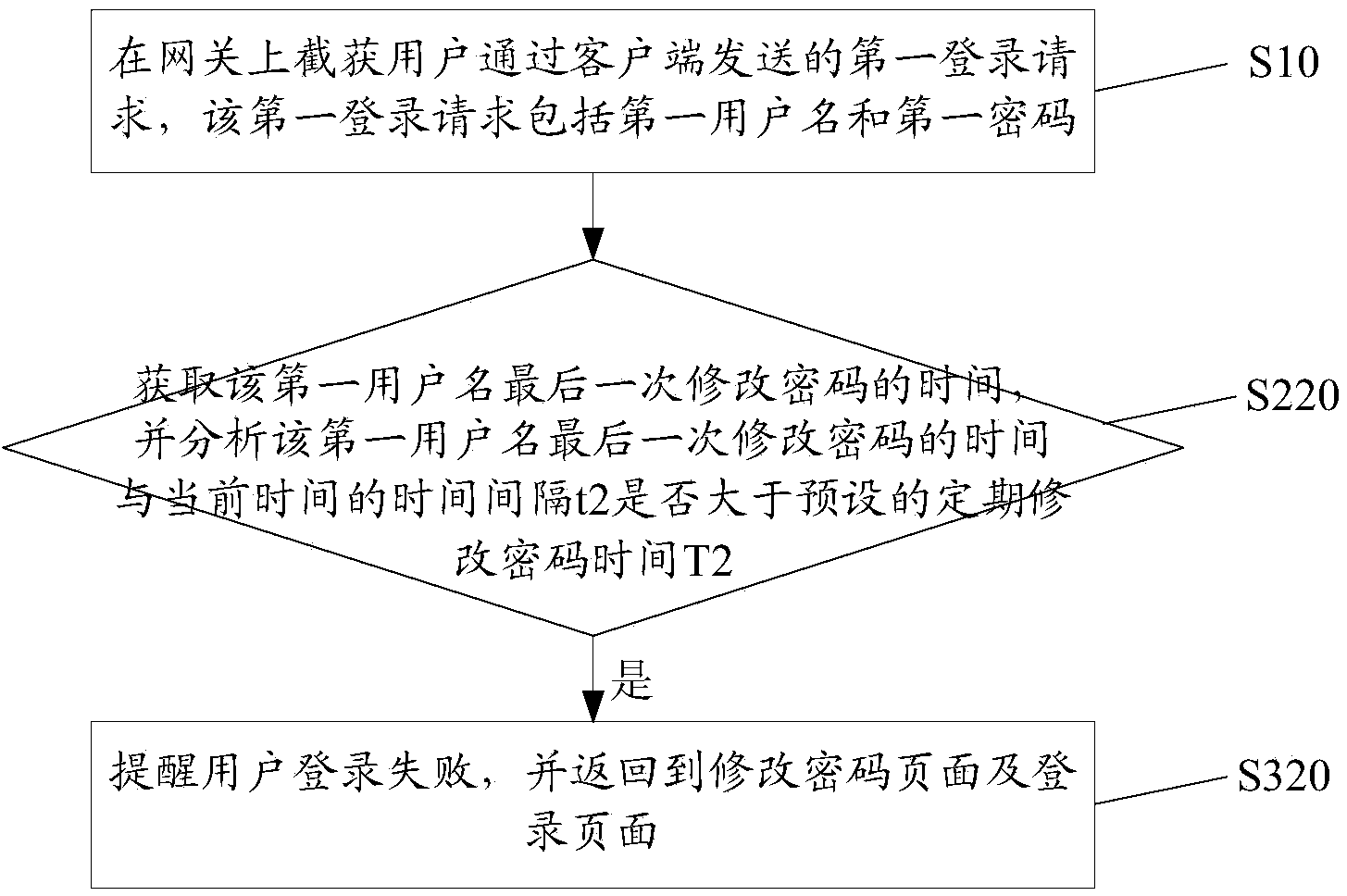
Method and system for improving login security
The invention discloses a method and system for improving login security. The method includes the steps that a first login request sent by a user through a client is intercepted on the gateway, and the first login request comprises a first user name and a first password; security check is conducted to the first login request according to the preset password protection strategy; if the first login request does not meet the preset password protection strategy, the user is informed to re-login. The invention further provides a system for improving login security. By the adoption of the method and system for improving login security, security check is conducted to the login request at the gateway, so that login security is improved.
Owner:SANGFOR NETWORK TECH SHENZHEN
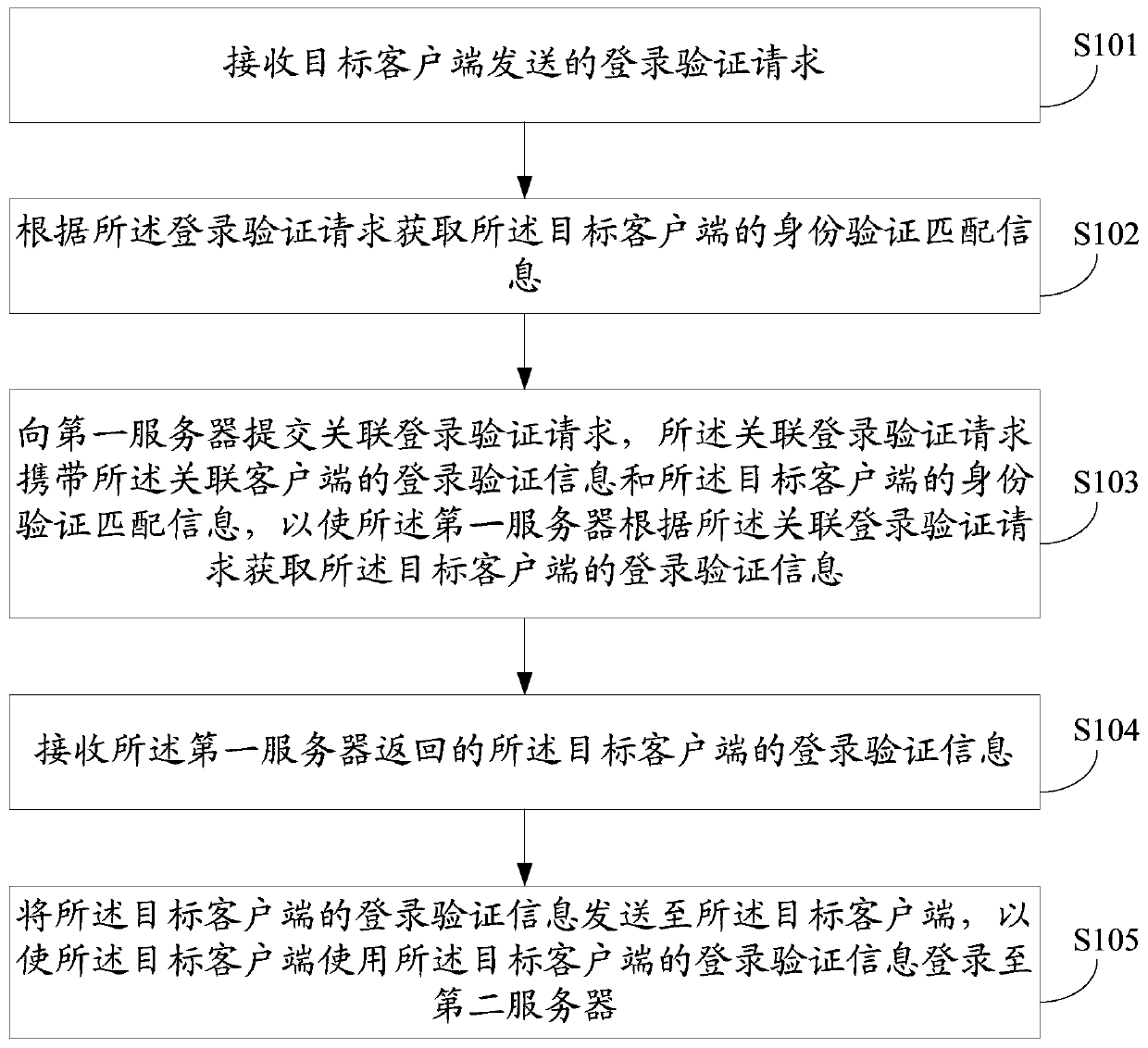
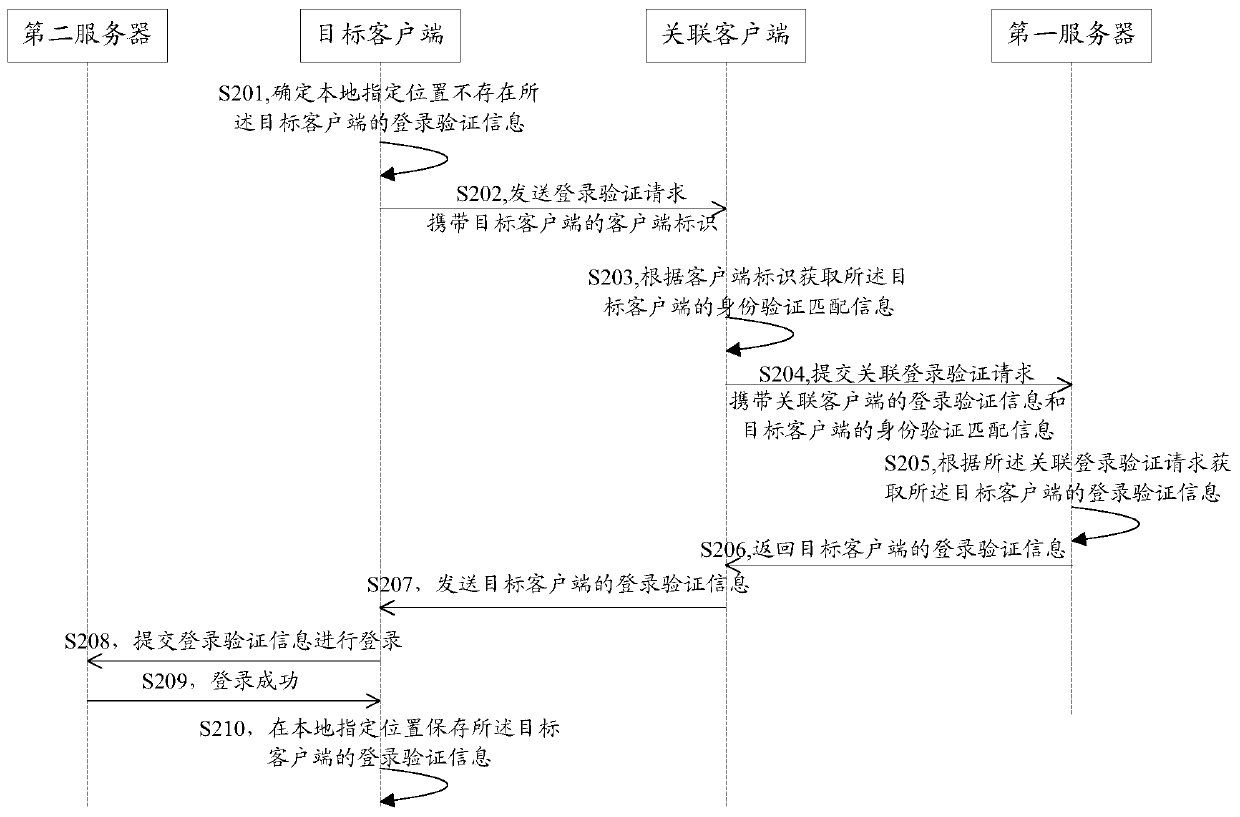
Method and system for logging in client and client
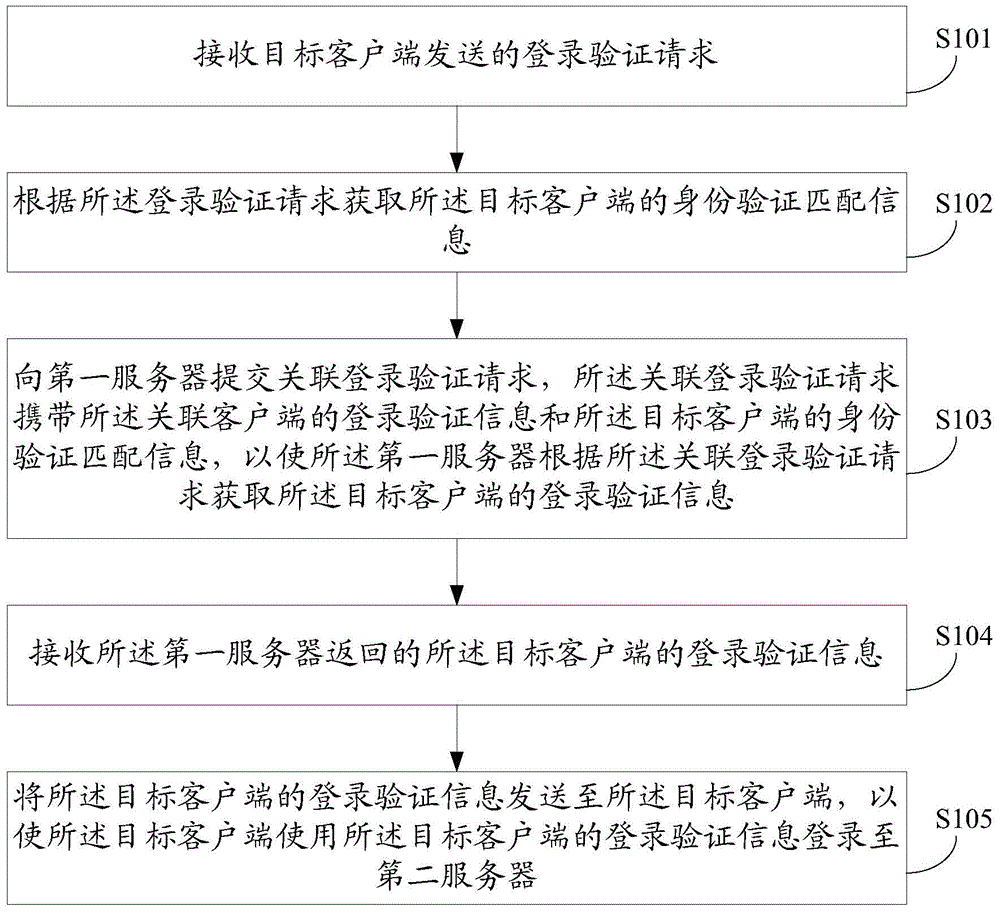
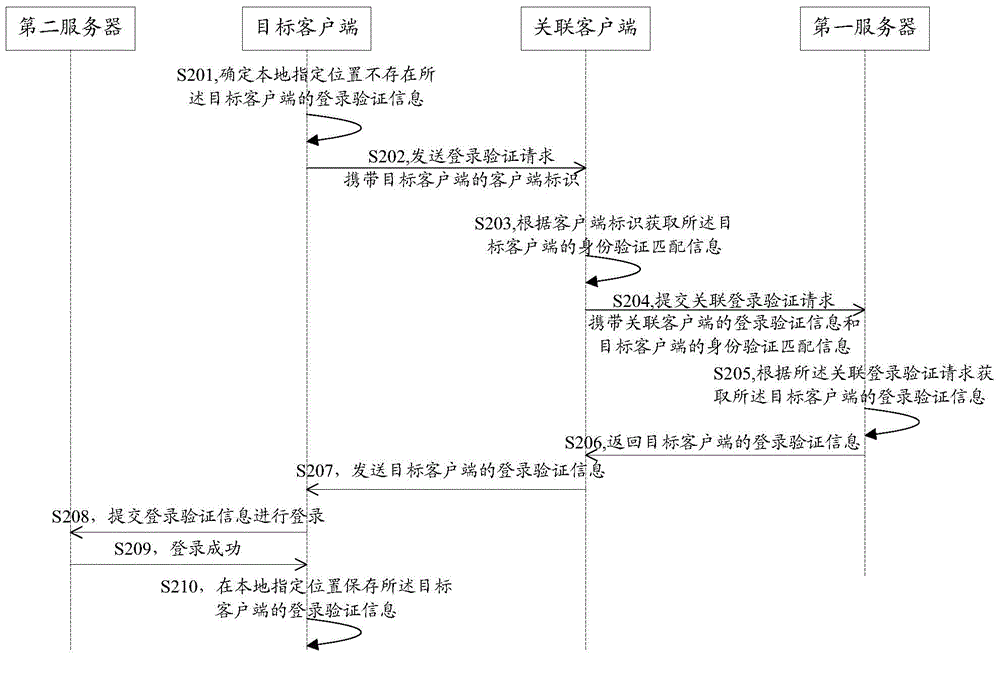
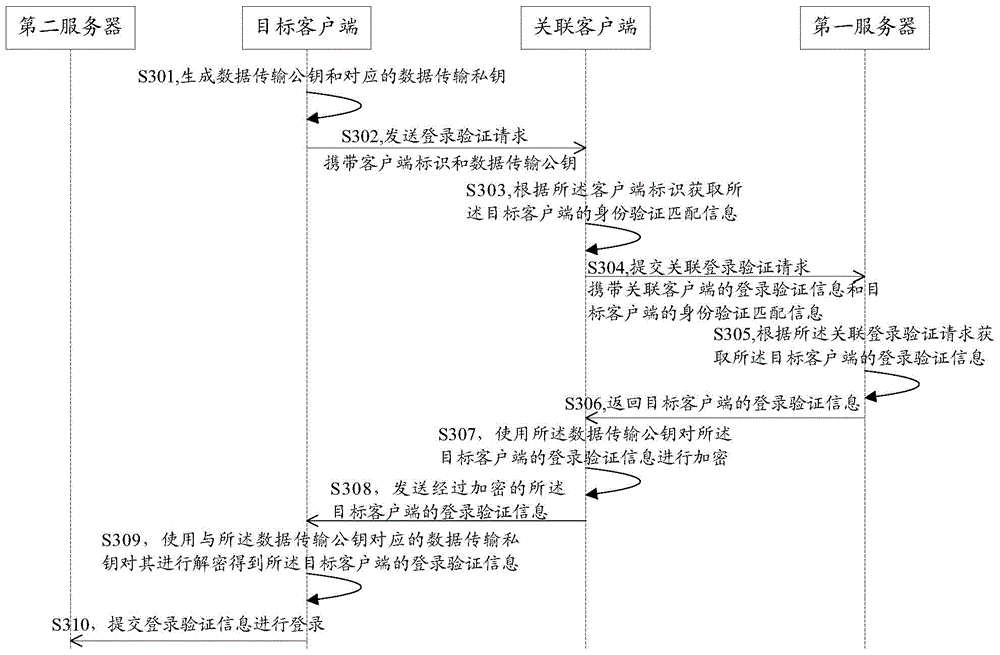
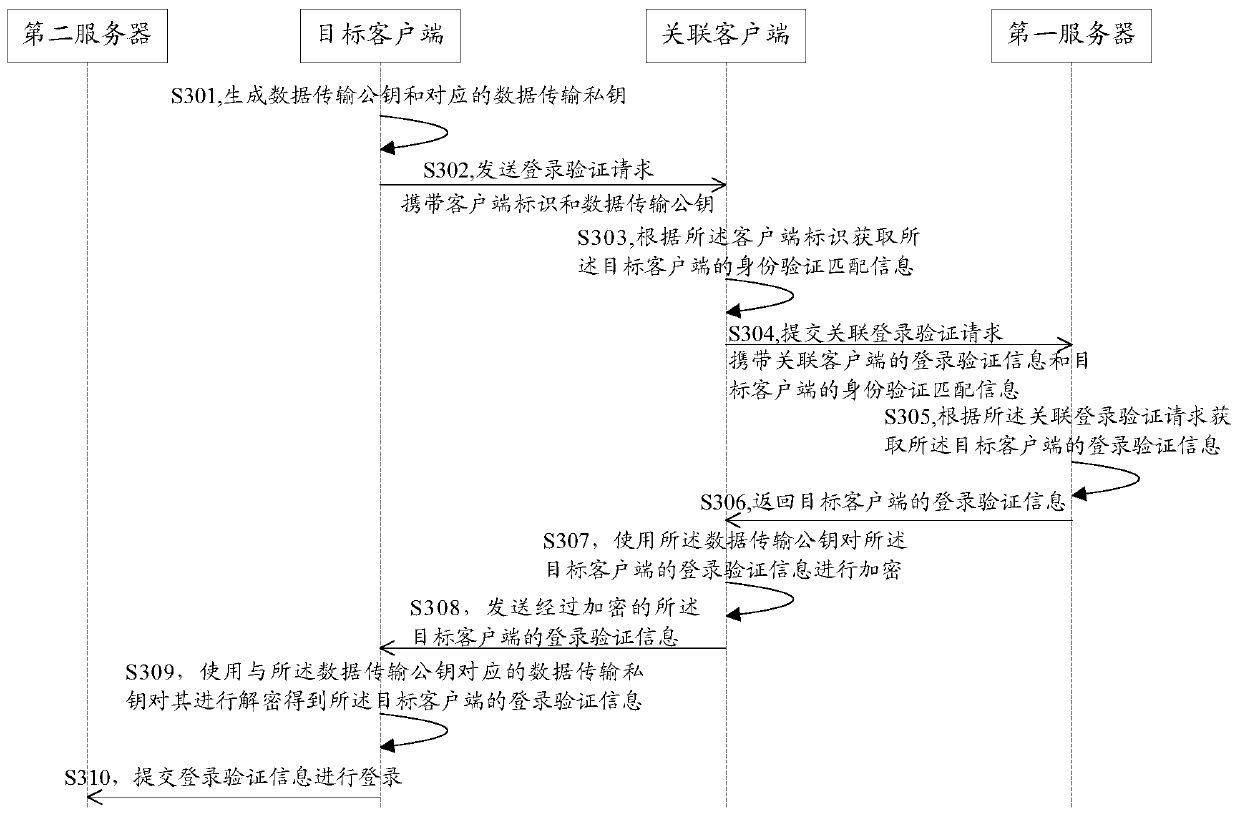
The embodiment of the invention discloses a method and system for logging in a client and a client. The method for logging in a client comprises: a logging-in verification request sent by a target client is received; according to the logging-in verification request, identity verification matching information of the target client is obtained; an associated logging-in verification request is submitted to a first server, so that the first server obtains logging-in verification information of the target client according to the associated logging-in verification request; the logging-in verification information, returned by the first server, of the target client is received; and the logging-in verification information of the target client is sent to the target client, so that the target client can log in a second server by using the logging-in verification information of the target client. According to the invention, rapid logging in of an application client can be realized and a risk of stealing logging-in verification information can be effectively eliminated, so that the logging-in security of the client can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method, device and system for establishing remote office operation and maintenance channel and storage medium
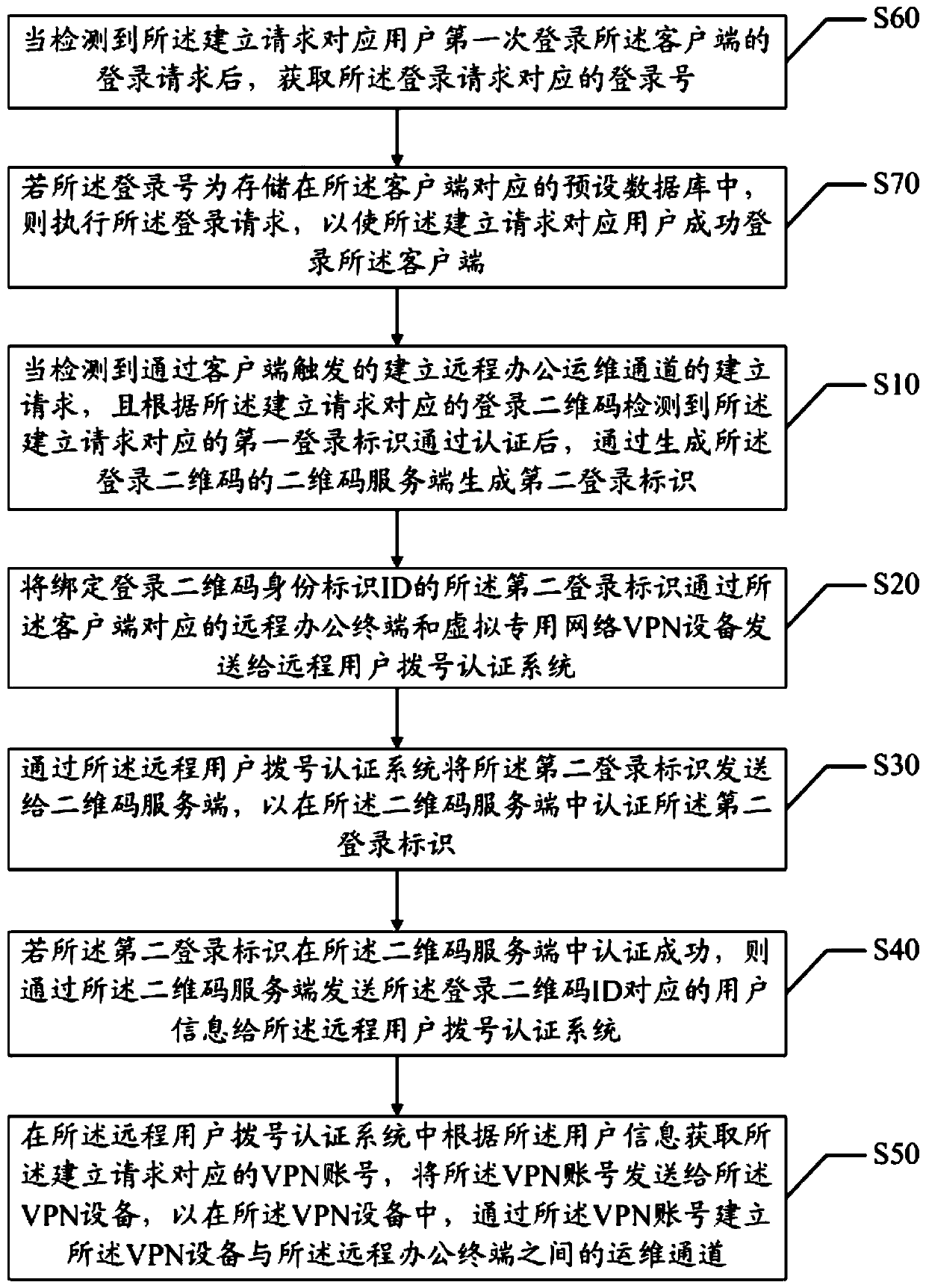
PendingCN110336870AImprove login success rateImprove login securityNetworks interconnectionSensing by electromagnetic radiationAuthentication systemUser information
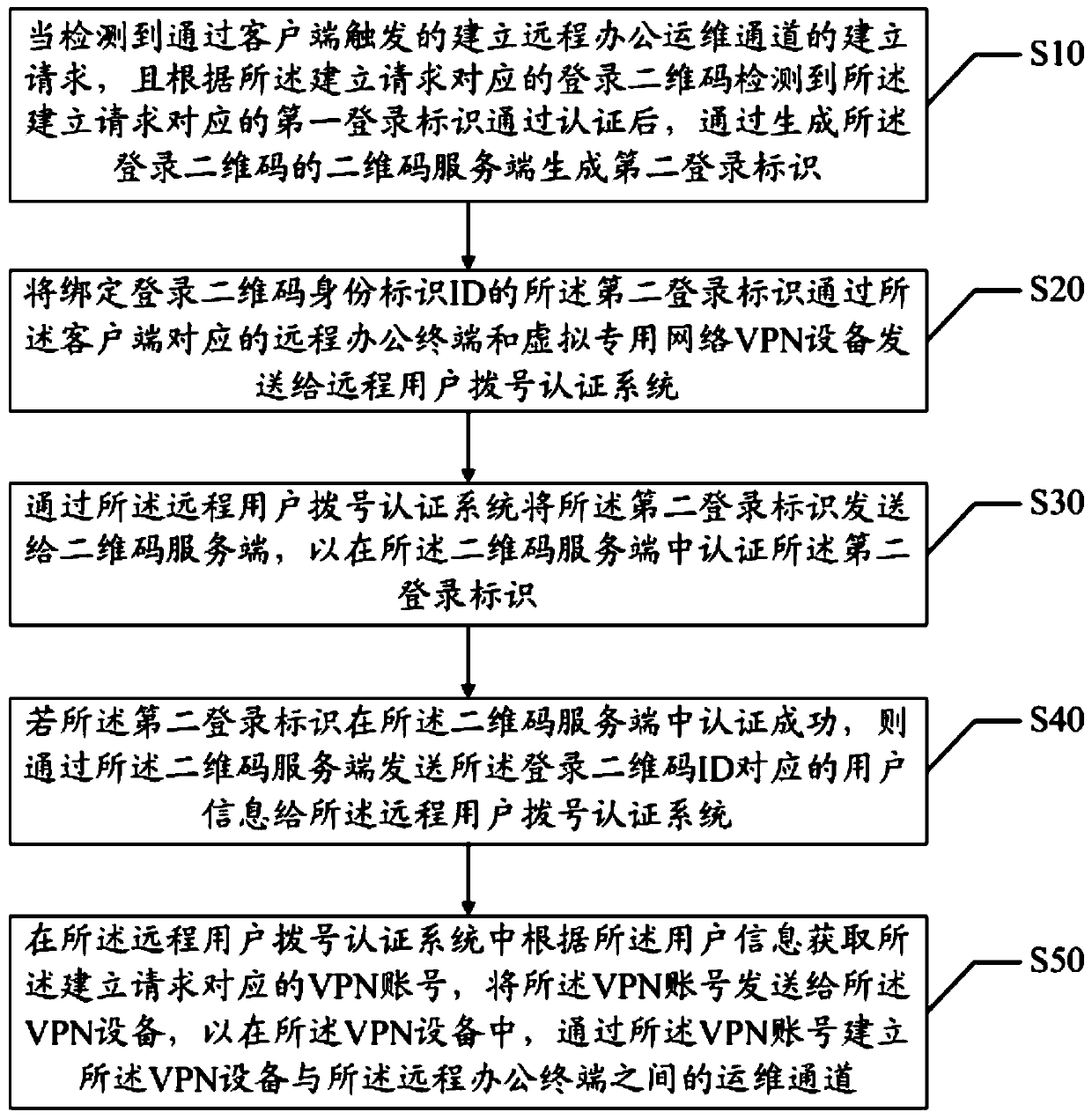
The invention discloses a method, device and system for establishing a remote office operation and maintenance channel and a storage medium, relating to the field of financial science and technology,the method comprises the steps: when an establishment request for establishing a remote office operation and maintenance channel is detected and the first login identifier passing the authentication is detected, generating a second login identifier through a two-dimensional code server, sending a second login identifier bound with the login two-dimensional code ID to a remote user dialing authentication system so as to send the second login identifier to the two-dimensional code server, and if the second login identifier is successfully authenticated in the two-dimensional code server, sendinguser information to the remote user dialing authentication system; and obtaining a VPN account corresponding to the establishment request according to the user information in the remote user dialingauthentication system, and establishing a remote office operation and maintenance channel through the VPN account. According to the invention, the login success rate of logging in the VPN equipment isimproved, and the login security of logging in the VPN equipment is improved.
Owner:WEBANK (CHINA)
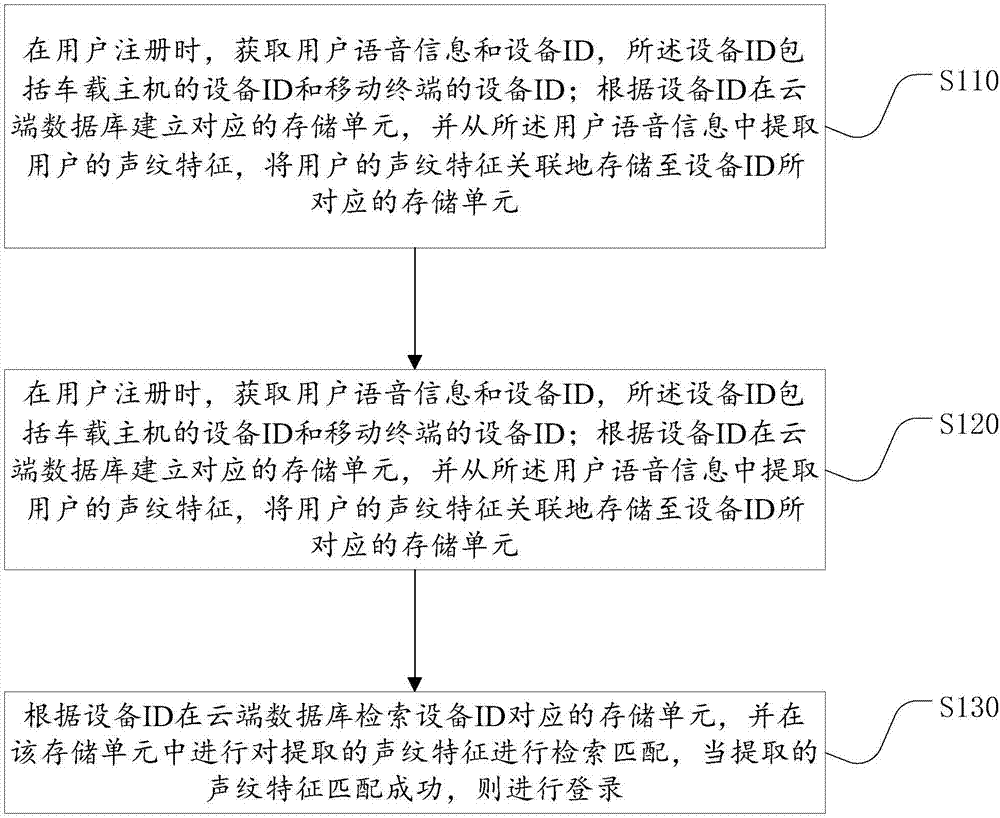
Method and device for quick voice login of intelligent vehicle
The invention relates to a method and a device for quick voice login of an intelligent vehicle. The method comprises the following steps of simultaneously obtaining vocal print features and a device ID of an on-board host computer or a device ID of a mobile terminal, which is provided by a user, when the user logs in; affirming a storage unit in a cloud database according to the device ID of the on-board host computer or the device ID of a mobile terminal, which is provided by the user; when the device ID is affirmed to be in the storage unit of the cloud database, carrying out matching and retrieval on the extracted vocal print features in the storage unit; and when the vocal print features are matched successfully, logging in successfully, otherwise failing to log in. The user information is classified and stored through the device ID, so that the time for matching and retrieval of the vocal print features is greatly reduced, and the login is realized through the vocal print features of the user while a username and a login password cannot be input, so that the login safety of vehicle-mounted terminals, such as an electronic control unit, is increased, the user login is greatly facilitated, and meanwhile, the user identity can be quickly identified to realize the quick login.
Owner:FJ MOTOR GRP YUDO NEW ENERGY AUTOMOBILE CO LTD
Application program login method, computer side, mobile terminal, system and storage medium
PendingCN109522695AEnsure information securityImprove login securityDigital data authenticationPasswordComputer terminal
The invention discloses an application program login method, a computer end, a mobile terminal, a system and a readable storage medium, and the method comprises the steps: detecting whether a login account password input by a user is abnormal or not when the computer end receives an application program login request; If the login account password is not abnormal, sending an iris recognition verification prompt to a mobile terminal bound with the login account; And after a response message which is sent by the mobile terminal and passes iris recognition verification is received, logging in theapplication program. The identity and login safety of the user are authenticated through double verification of password verification and iris verification, so that the login safety coefficient is improved, and the information safety of the user is ensured.
Owner:NUBIA TECHNOLOGY CO LTD
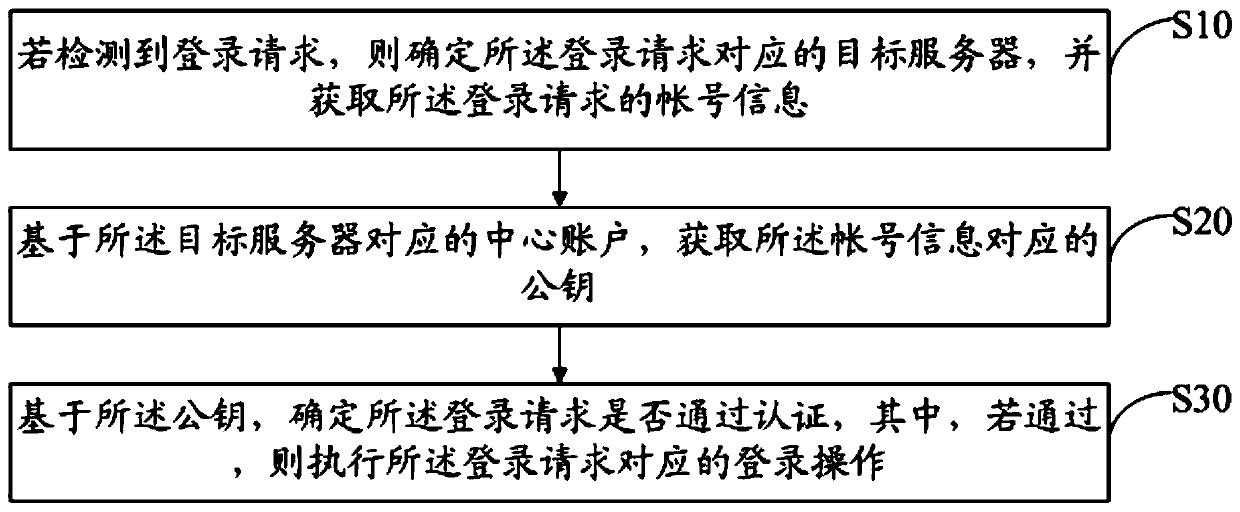
Server login method, device and system and computer readable storage medium
PendingCN111460410AImprove login securitySimplify the login processDigital data authenticationPasswordEngineering
The invention discloses a server login method which comprises the following steps: if a login request is detected, determining a daemon process corresponding to the login request, and determining account information of the login request; acquiring a public key corresponding to the account information based on a central account corresponding to the daemon process; and determining whether the loginrequest passes authentication based on the public key, If so, executing a login operation corresponding to the login request. The invention further discloses a server login device and system and a computer readable storage medium. Login method, account-free password, the method comprises the steps of detecting a login request; the login request is authenticated by determining the corresponding account information and the public key, if the authentication is passed, the current login request is determined to be trustworthy, login is allowed, Meanwhile, the responsibility attribution of subsequent operation can be determined according to the account information, so that the login safety is improved, the login process is simplified, and quick login is realized.
Owner:WEBANK (CHINA)
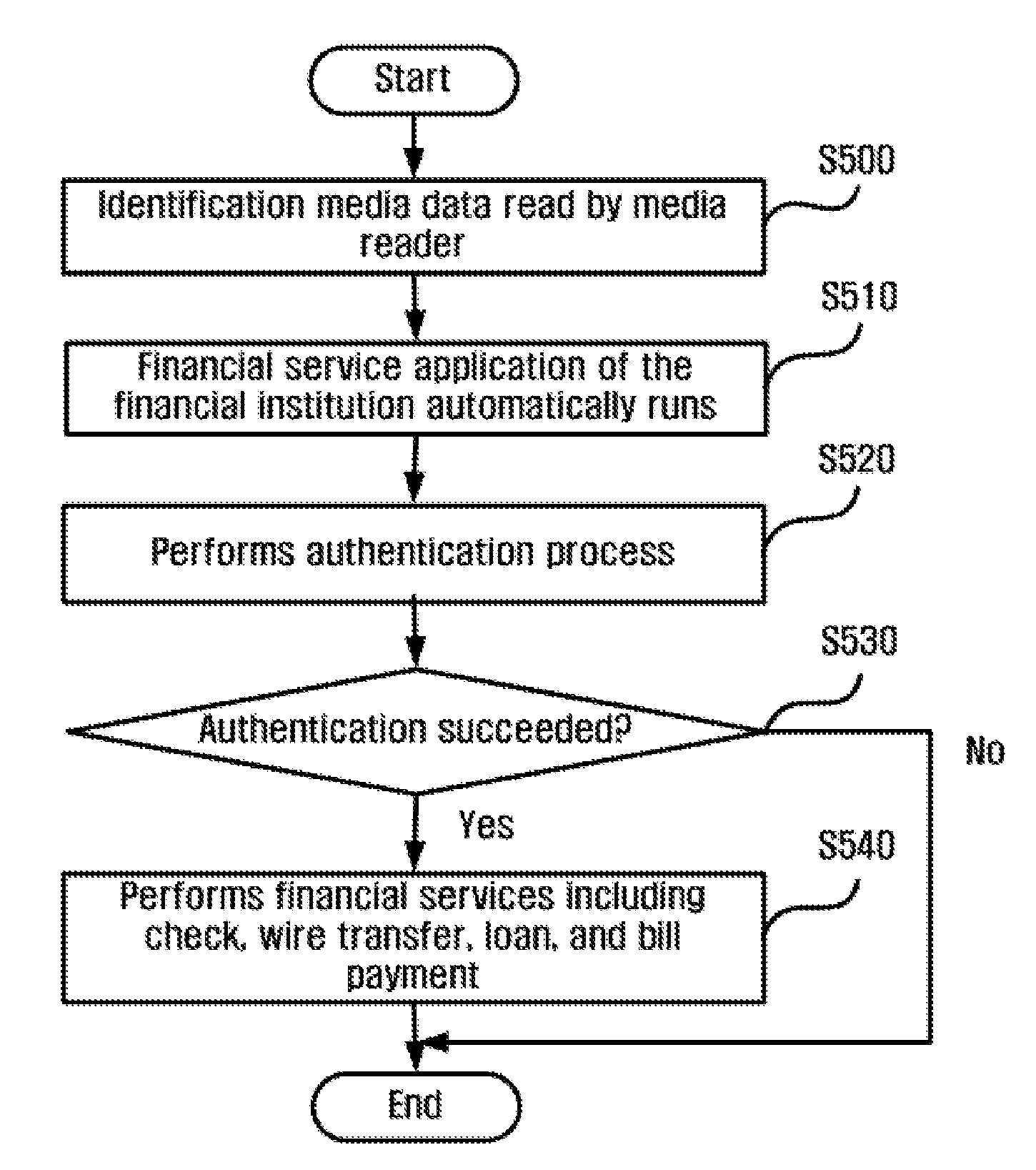
Online information input and financial transaction system using the personal identification media, methods to input information online and conduct financial transactions, and the storing media that stores the programs for the system
InactiveUS20120290476A1Shorten the timeImprove login securityFinanceProtocol authorisationWeb sitePayment
This invention is related to the online information input and financial transaction system using the personal identification media, which is intended to facilitate the information input process by utilizing the personal information registered with the personal information management institutions in signing up to be a member of, or logging in to, websites, and the methods to input information online and conduct financial transactions. In this invention, we intended the process of membership joining or logging-in to websites to be completed through transmitting the personal identification data read by the media reader to the personal information management institutions and then receiving the member's personal information or the personal authentication services, and also helped minimize the user's information input by integrating the log-in and payment processes. This invention has merits in that it facilitates the membership-joining, log-in and payment processes, and the amount of the information the user has to input is minimized.
Owner:YOO SEUNG HUN
Integrated cold chain vehicle temperature monitoring terminal
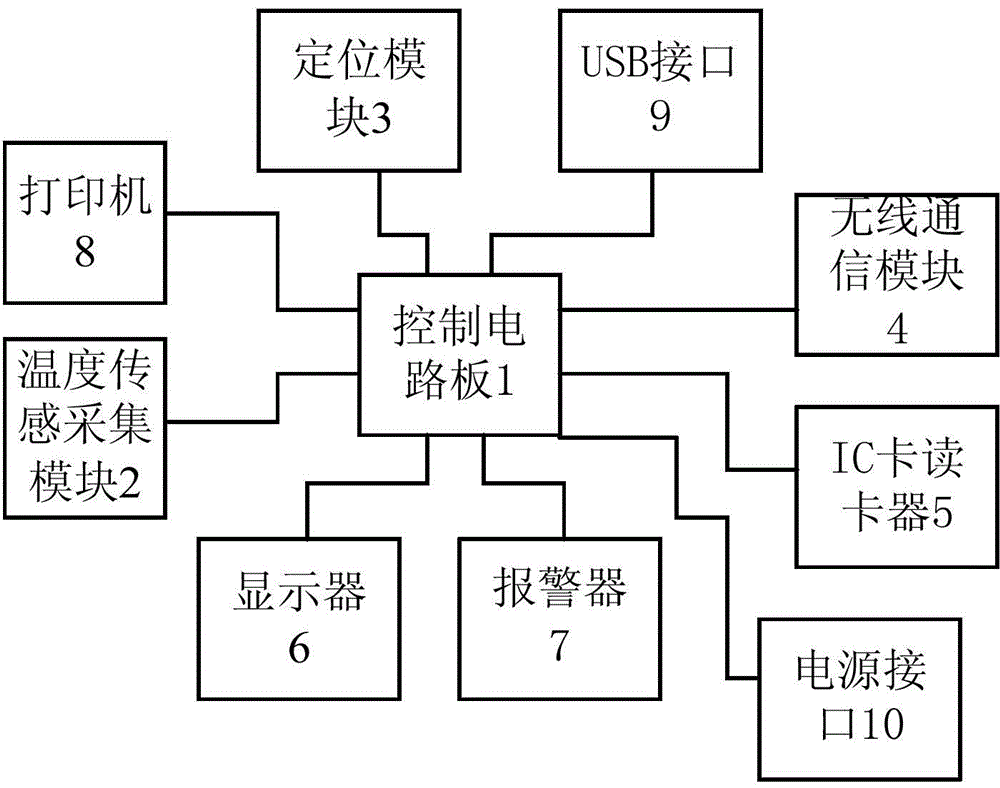
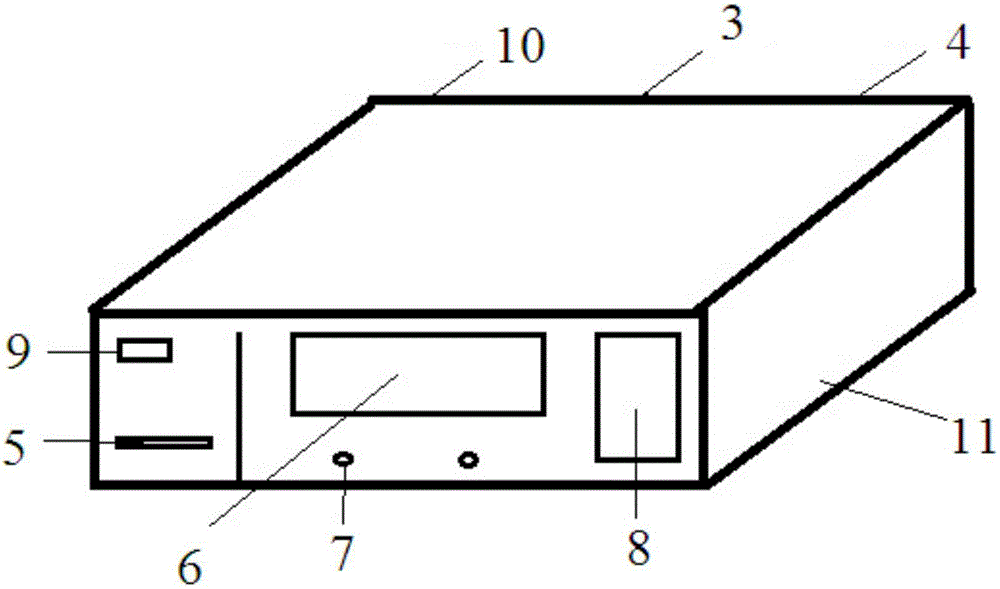
InactiveCN105444898AHighly integratedMeet the requirements of cold chain safetyThermometer detailsTransmission systemsCold chainComputer terminal
The present invention relates to an integrated cold chain vehicle temperature monitoring terminal. The integrated cold chain vehicle temperature monitoring terminal comprises a housing, a control circuit board, a temperature collection module, a location module, a wireless communication module, an IC card reader, a display, an alarm, a printer, a USB interface and a power interface, wherein the control circuit board, the temperature collection module, the location module, the wireless communication module, the IC card reader, the display, the alarm, the printer, the USB interface and the power interface are installed on the housing. The control circuit board is connected with the temperature collection module, the location module, the wireless communication module, the IC card reader, the display, the alarm, the printer, the USB interface and the power interface. Compared with the prior art, the integrated cold chain vehicle temperature monitoring terminal has the advantages of high integration level, good safety, wide application range and the like.
Owner:NEWLAND DIGITAL TECH CO LTD
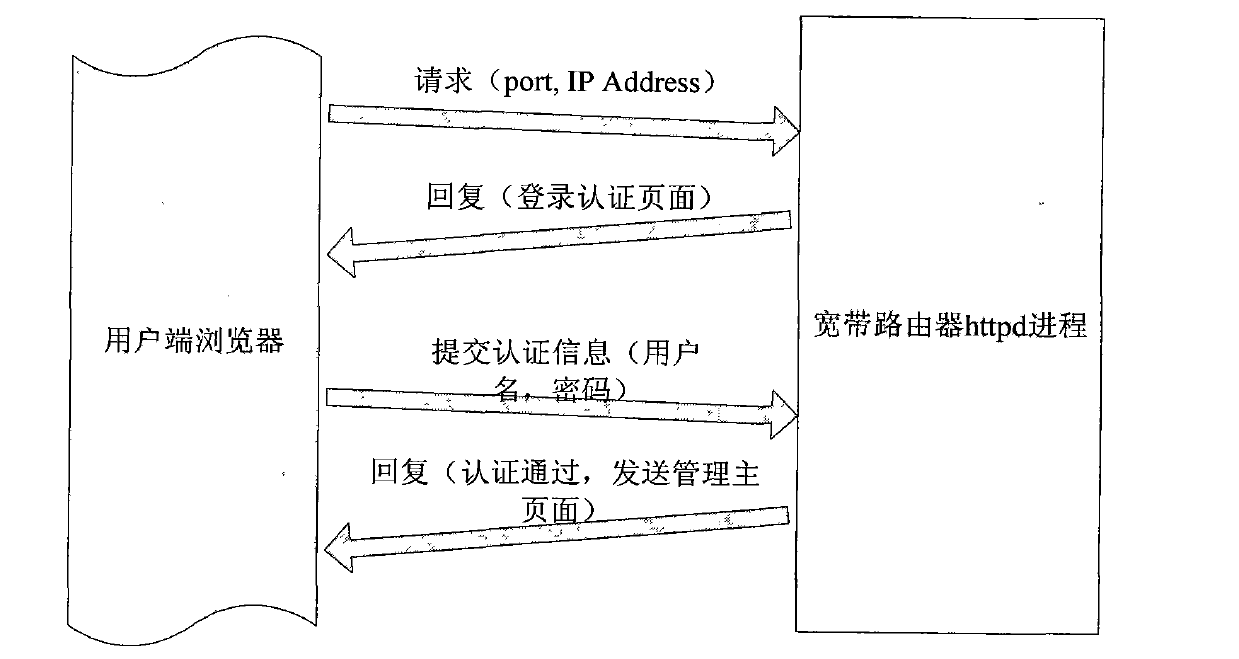
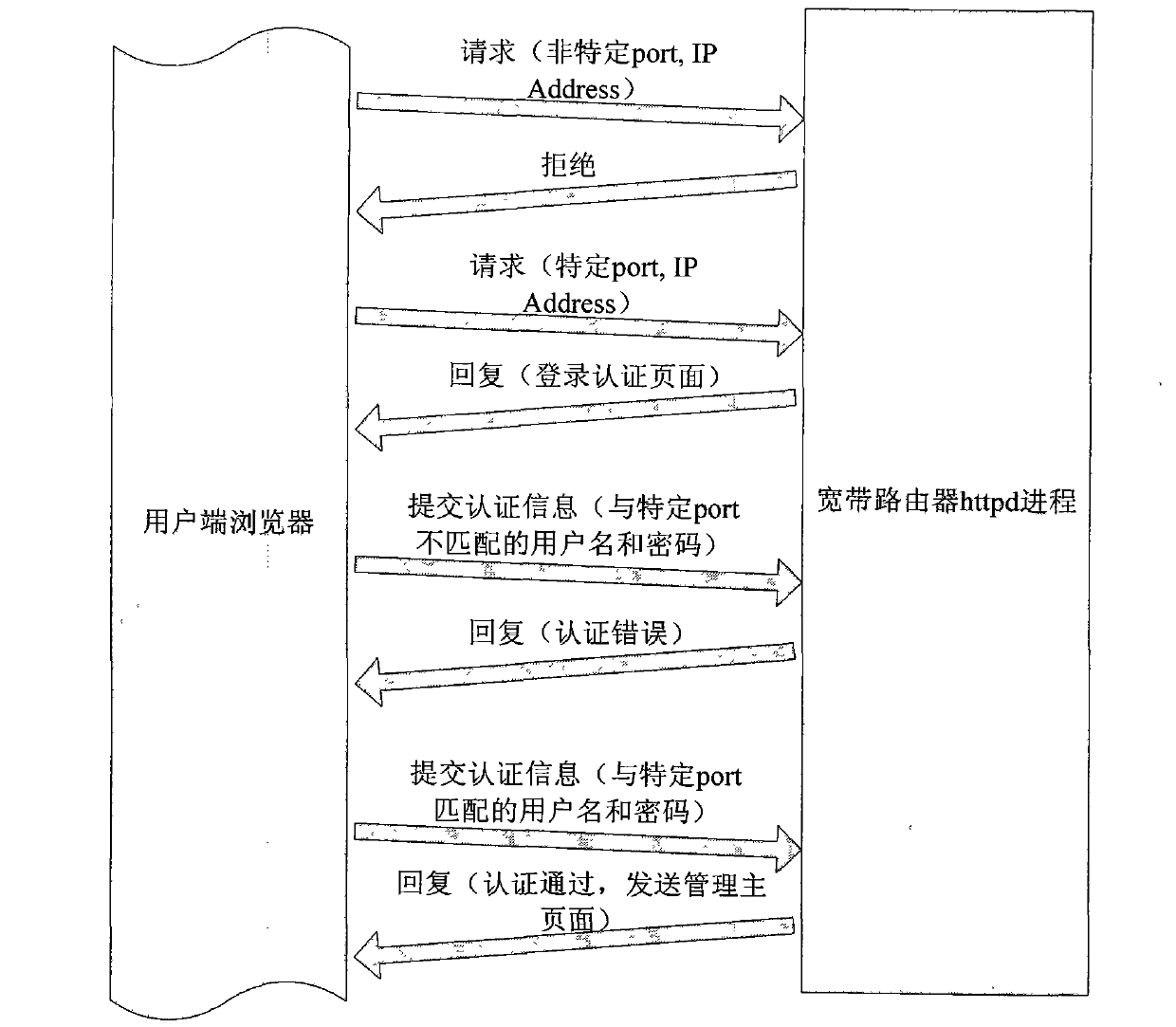
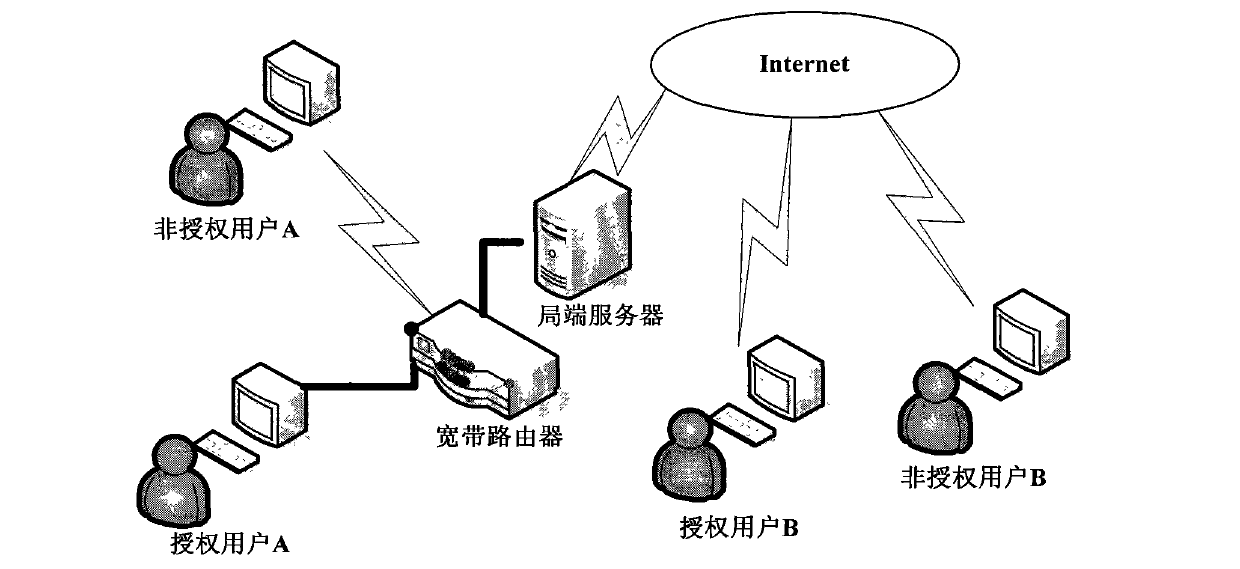
Method for improving managing page login security of broad band router
The invention relates to a router, in particular to a method for improving managing page login security of a broad band router. The method includes two methods of using port 80 and using port 800, wherein the method of using the port 80 includes that when a browser requests the broad band router for connecting, the request is accepted, and a hyper text transfer protocol daemon (httpd) process of the broad band router feeds back a login authentication page to the browser. The method for improving the managing page login security of the broad band router has the functions of improving the managing page login security of a broad band router system, preventing unauthorized users from using an exhaustion method to crack a login account number effectively, and reducing a possibility of login of the unauthorized users when an authorized user uses a simple login password.
Owner:SHENZHEN GONGJIN ELECTRONICS CO LTD
User login authentication system based on online banking security management
InactiveCN111274572AImprove login securityKey distribution for secure communicationFinanceInternet privacyEngineering
The invention relates to the technical field of online banking user login authentication, and discloses a user login authentication system based on the online banking security management, which comprises a local server Si running bank APP system software, a PC terminal Ci running the bank APP system software and / or a mobile terminal MTi, and the bank APP system comprises a user login authentication system body. The PC terminal Ci and / or the mobile terminal MTi are / is in communication connection with the local server Si through network communication equipment; and when the login user on the PCterminal Ci and / or the mobile terminal MTi sends a login request to the bank APP system, the user login authentication system of the bank APP system performs identity authentication on the login useron the PC terminal Ci and / or the mobile terminal MTi by adopting a user authentication method based on zero knowledge proof. According to the invention, the technical effect of further improving the login security of the online banking user is achieved.
Owner:周正达
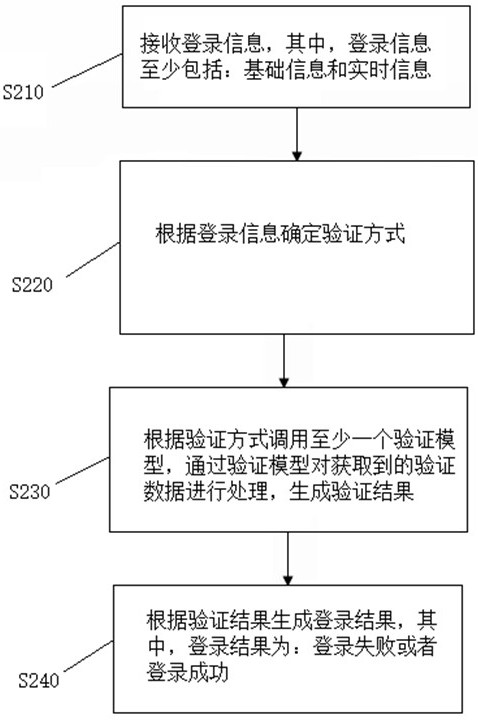
Login method and system
InactiveCN112532655AImprove login securityUser identity/authority verificationTime informationService Interface for Real Time Information
The invention discloses a login method and system, and the system comprises at least one client and a server. At least one client is used for sending login information, receiving and executing a verification data acquisition instruction, and sending the acquired verification data to the server; the server is used for executing the following steps: receiving the login information, wherein the logininformation at least comprises basic information and real-time information; determining a verification mode according to the login information; calling at least one verification model according to the verification mode, and processing the obtained verification data through the verification model to generate a verification result; and generating a login result according to the verification result,the login result being login failure or login success. The method and the device have the technical effects that the login risk is dynamically recognized, and further management and control measuresare realized according to the login risk, so that the login security is improved.
Owner:北京英迈琪科技有限公司
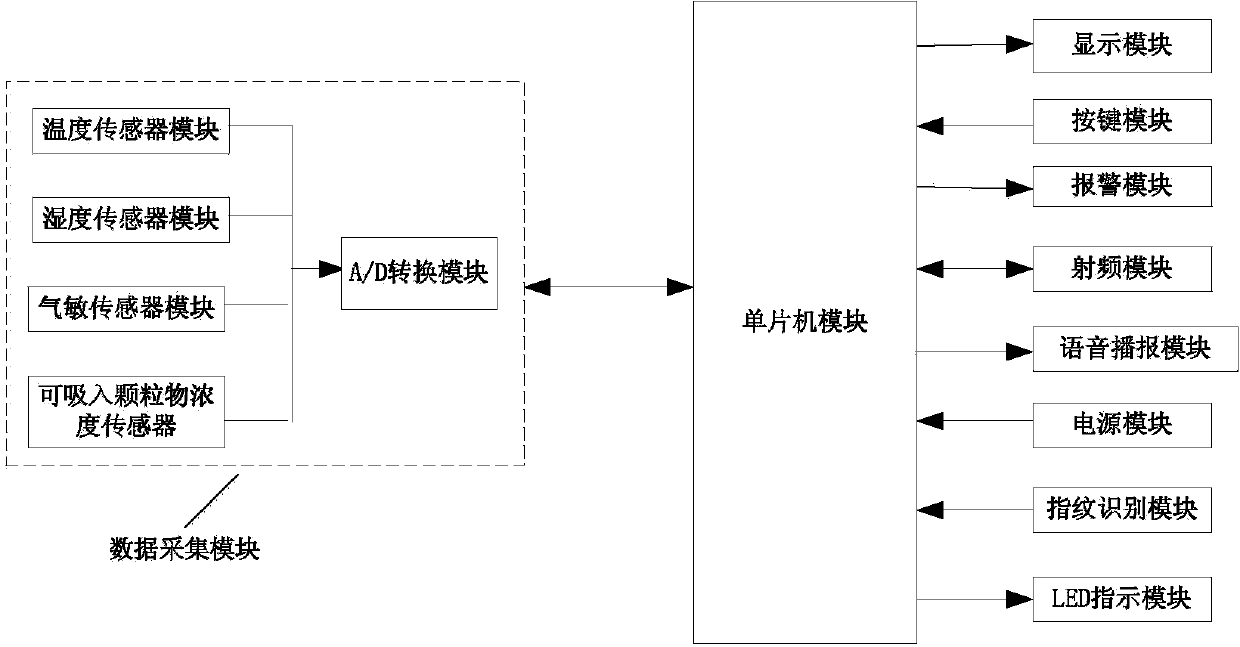
Environment monitoring system
The invention discloses an environment monitoring system comprising a shell, a data collecting module, a single chip microcomputer module, a display module, a key module, an alarm module, a radio frequency module, a voice broadcast module, a power module, a fingerprint recognition module and a remote control center. The data collecting module, the single chip microcomputer module, the alarm module, the radio frequency module, the voice broadcast module and the power module are mounted in the shell. The display module, the key module and the fingerprint recognition module are electrically connected with the single chip microcomputer module respectively and further mounted on the outer surface of the shell. An output end of the power module is connected with a power input end of the single chip microcomputer module. A data transmission end of the radio frequency module is connected with a data transmission end of the single chip microcomputer module. An output end of the single chip microcomputer module is connected with an input end of the alarm module and an input end of the voice broadcast module respectively. The radio frequency module is connected with the remote control center through the wireless network. The environment monitoring system is simple in structure and low in cost and allows convenient remote transmission, control and operation.
Owner:NANTONG BEICHENG SCI & TECH ENTREPRENEURIAL MANAGEMENT +1
Electric power operation and maintenance multi-level network security monitoring and early warning system
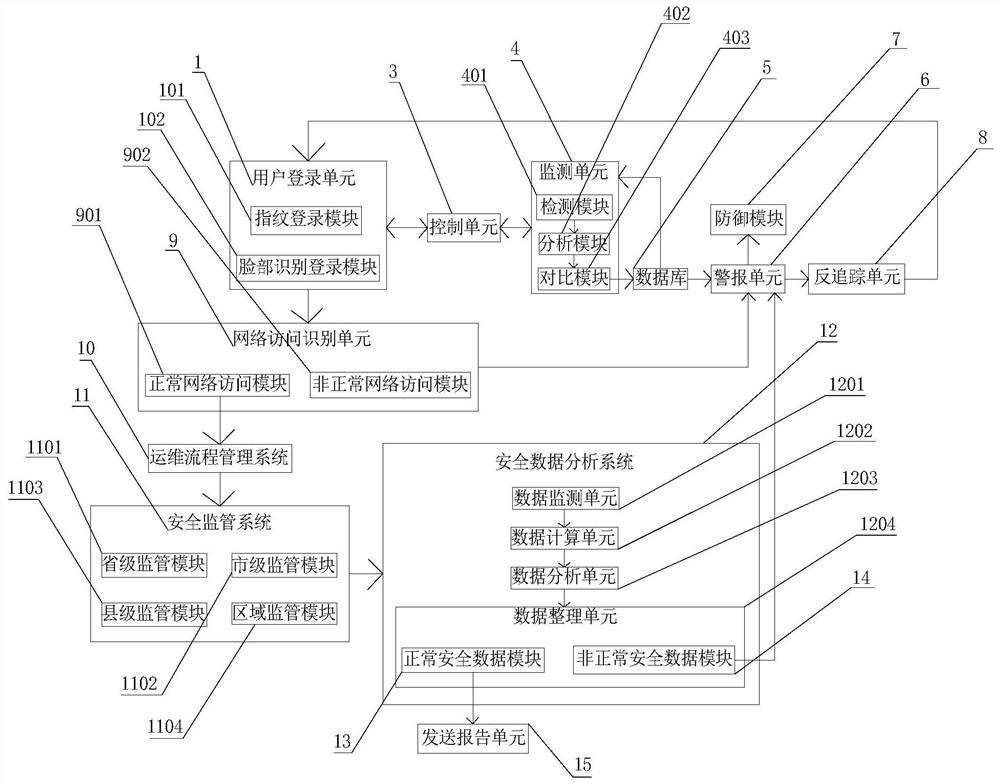
PendingCN112953891AEnhanced login securityImprove the effectData switching networksEmbedded systemManagement system
The invention discloses an electric power operation and maintenance multi-level network security monitoring and early warning system, which comprises a user login unit, an operation and maintenance process data management system, a security supervision system and a security data analysis system, and is characterized in that the user login unit is in double-signal connection with a control unit, and the control unit is connected with a monitoring unit; and the monitoring unit comprises a detection module, an analysis module and a comparison module. According to the electric power operation and maintenance multi-level network security monitoring and early warning system, the login security can be enhanced through a fingerprint login module and a face recognition login module which are arranged in the user login unit; and a normal network access module and an abnormal network access module are arranged in the network access identification unit, and a normal security data module, an abnormal security data module, an alarm unit and a defense module are arranged, so that the network security monitoring effect can be greatly enhanced.
Owner:CHINA SOUTHERN POWER GRID DIGITAL GRID RES INST CO LTD +1
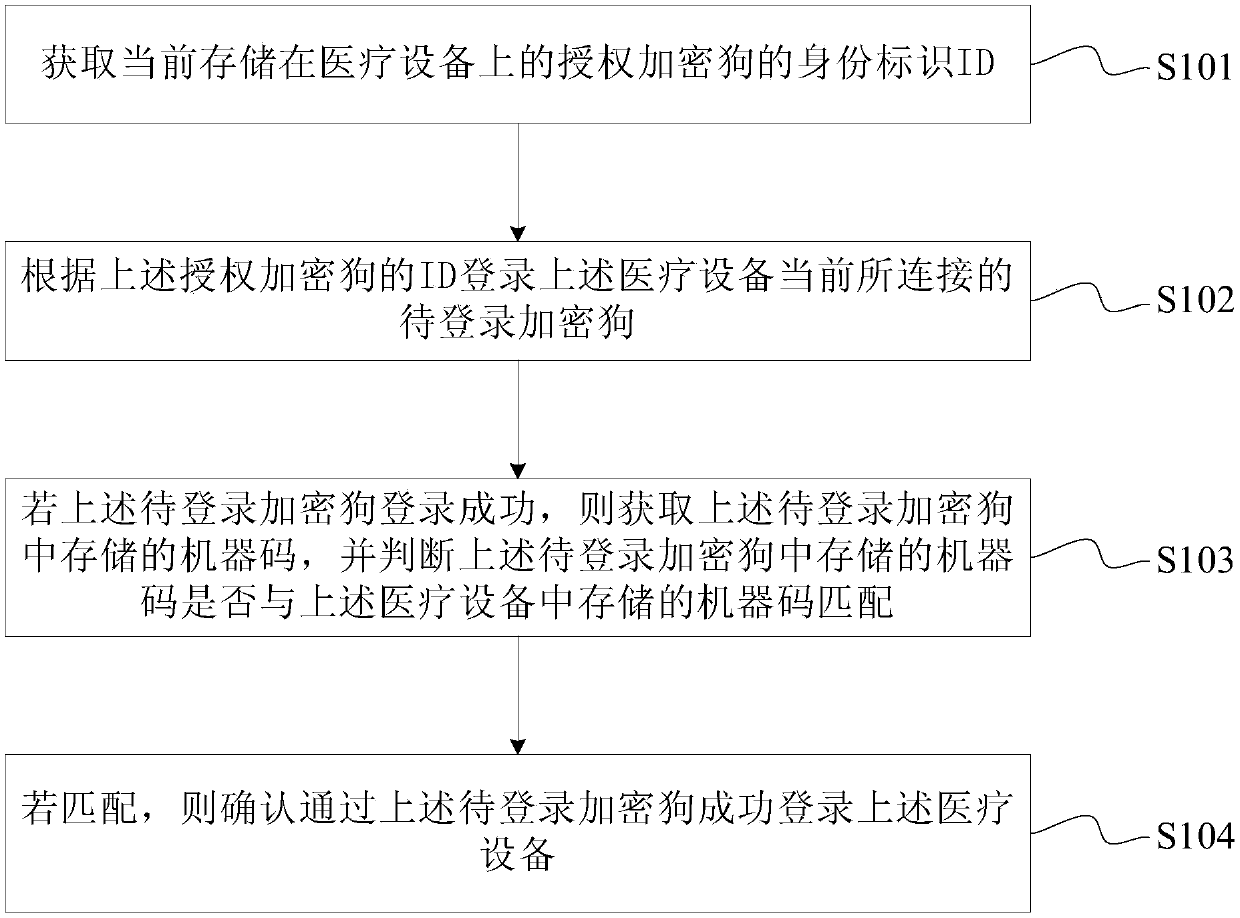
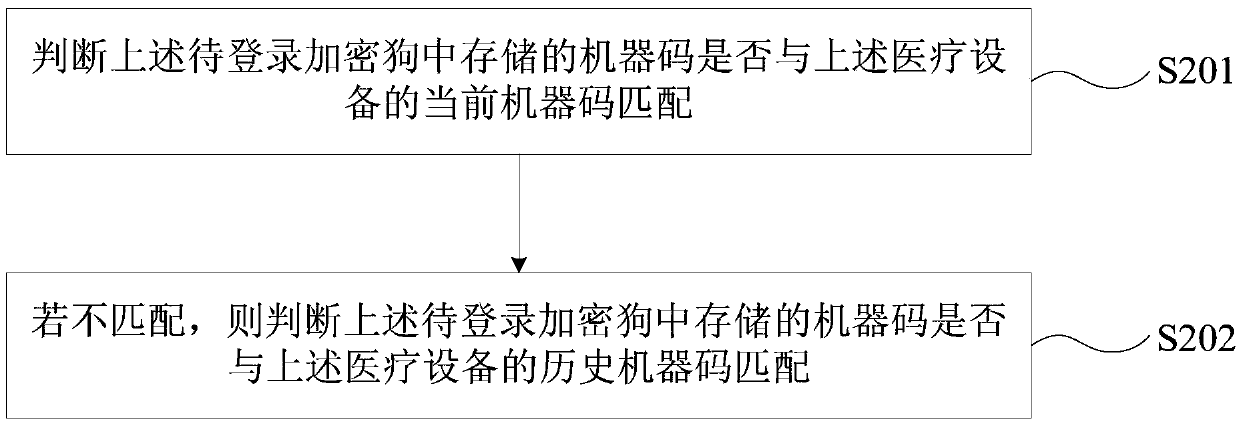
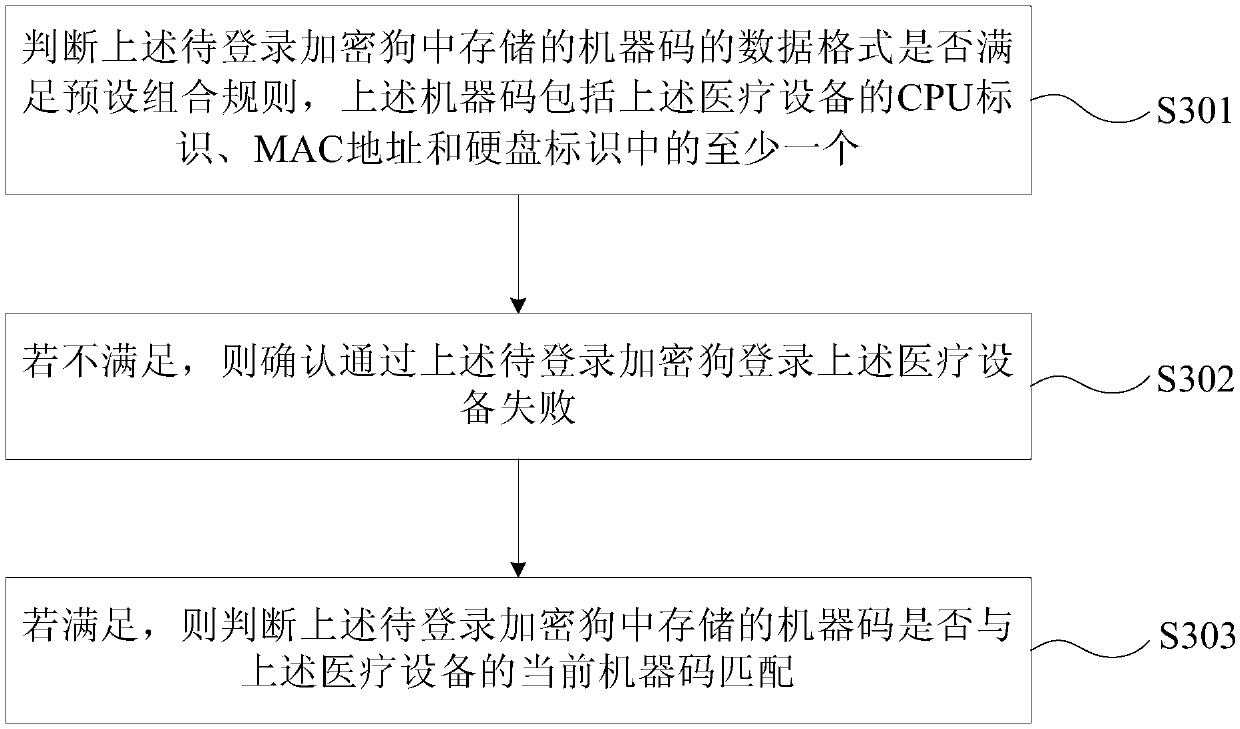
Medical device logging-in method and apparatus
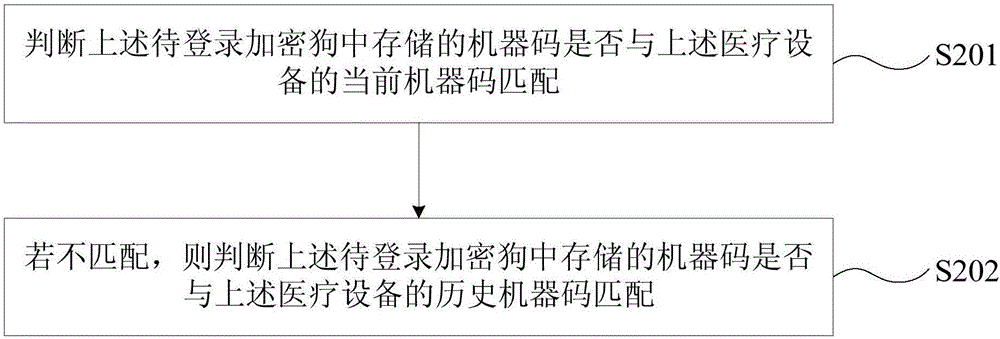
ActiveCN106529237AImprove login securityPrevent malicious tamperingDigital data authenticationMedical equipmentAuthorizationMachine code
The invention provides a medical device logging-in method and apparatus. The medical device logging-in method includes: acquiring an identity identification ID of an authorization dongle currently stored in a medical device; logging in a dongle to be logged which is currently connected to the medical device according to the ID of the authorization dongle; acquiring a machine code of the dongle to be logged if the dongle to be logged is logged successfully, and determining whether or not the machine code of the dongle to be logged matches a machine code stored in the medical device; and confirming the fact that the dongle to be logged successful logs in the medical device if so. The medical device logging-in method and apparatus can improve the logging-in security of the medical device, can avoid illegal logging-in of the medical device, and can avoid the problem the data of the medical device is lost due to illegal logging-in of the medical device.
Owner:WUXI HISKY MEDICAL TECH
A device for logging in a railway special system based on face recognition
InactiveCN109818924APrevent theftAchieve uniquenessCharacter and pattern recognitionTransmissionInformation resourceComputer vision
The invention discloses a device for logging in a railway special system based on face recognition. The device comprises: an obtaining module which can acquire user's face image when a user logs in arailway special system; a detection module which detects whether the user logs in for the first time according to the acquired user face image; a Login module which verifies whether the acquired facial image of the user is associated with the identity authentication when it is detected that the user is not initial login according to the detection result whether the user is initial login, and detects that the user is an authenticated user, when it is detected that the acquired user face image is subjected to associated identity authentication, and allows the user to log in to the railway dedicated system and update the user login data.. Through the mode, the uniqueness of the biological characteristics based on the human face can be realized, the login safety can be improved through the login mode of human face recognition, and the information resource space of the railway special system owned by a user is prevented from being stolen.
Owner:SHENZHEN KEANDA ELECTRONICS TECH
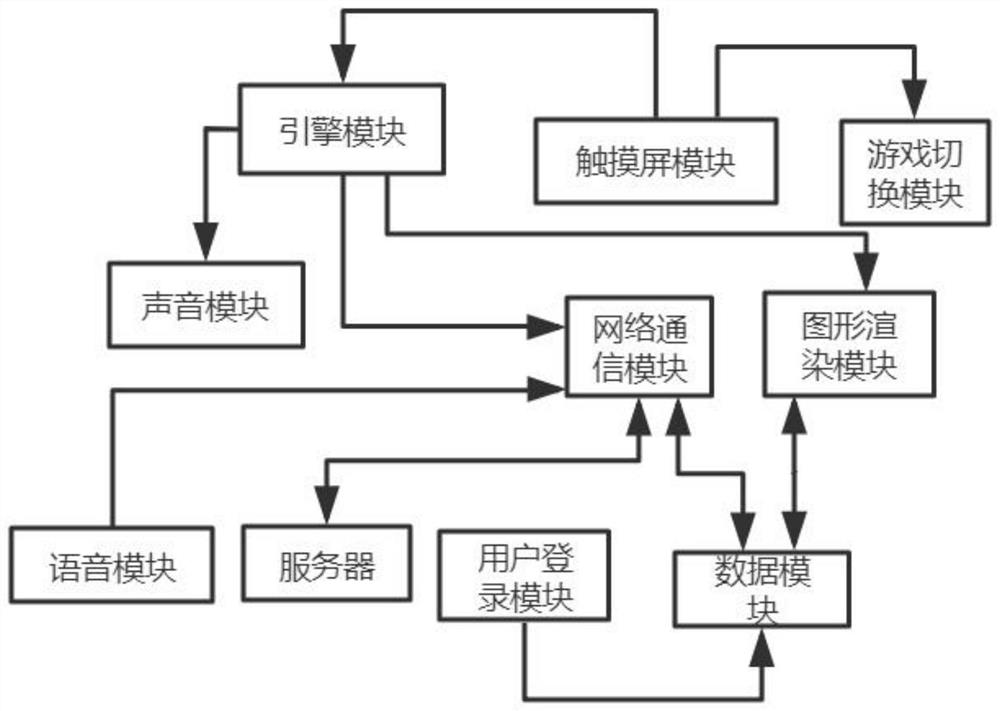
Multi-player online game APP based on mobile phone
The invention discloses a multi-player online game APP based on a mobile phone. The game APP comprises an engine module, a wireless network communication module, a data storage module, a graphic rendering module, a voice module, a sound module, a touch screen module, a server, a user login module and a game switching module, by setting a delayed login instruction input unit in the user login module, a user can set the verification information of the next login by himself / herself so that login security of the user is improved; by setting the operation method of the game switching module, a user is prevented from being in a waiting state in the switching process of multiple games, and seamless connection of switching is achieved; by improving the rendering method of the graphic rendering module and optimizing the rendering mode of the rendering module, mobile phone parameters of the user can be monitored in real time to adjust the rendering level in the running process of the game APP in real time, other APPs are selectively and preferentially closed according to the calorific value, and the user experience of game players is ensured.
Owner:海南神爱网络科技有限公司
User authentication method and system
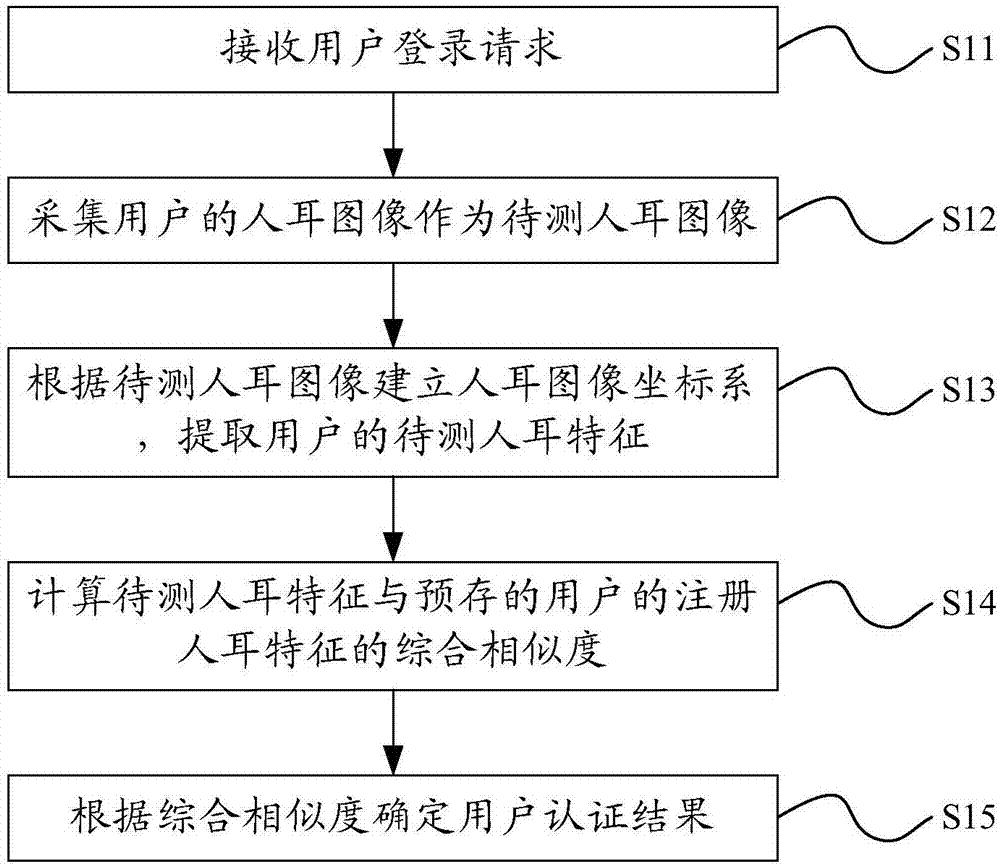
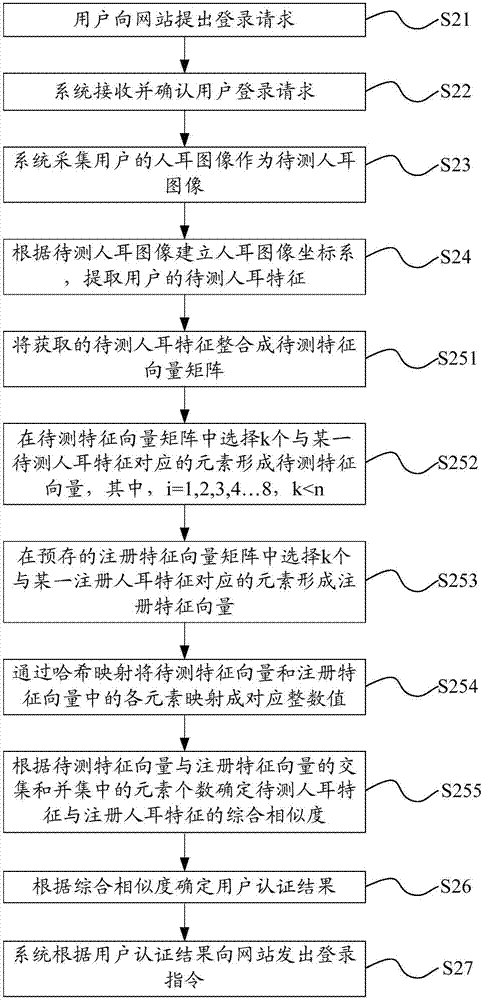
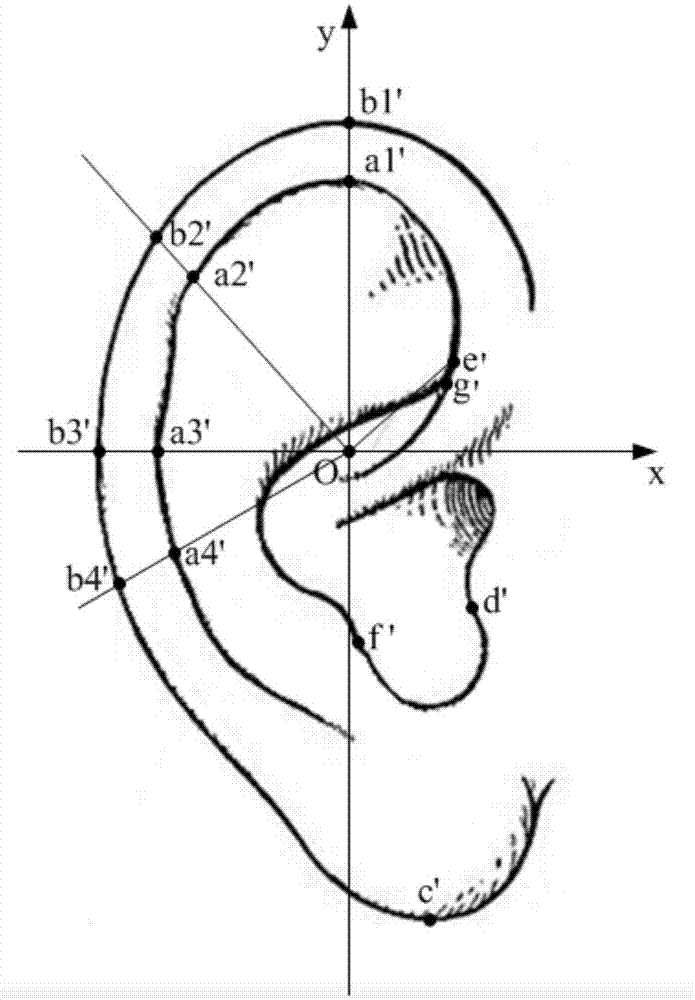
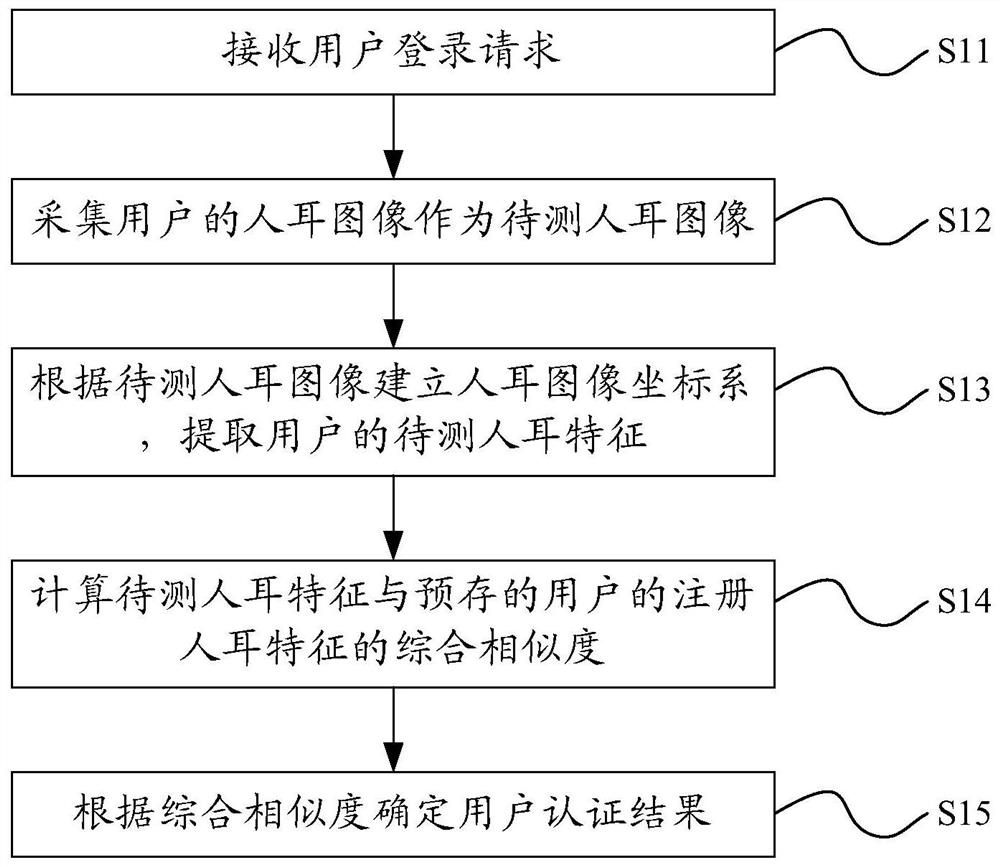
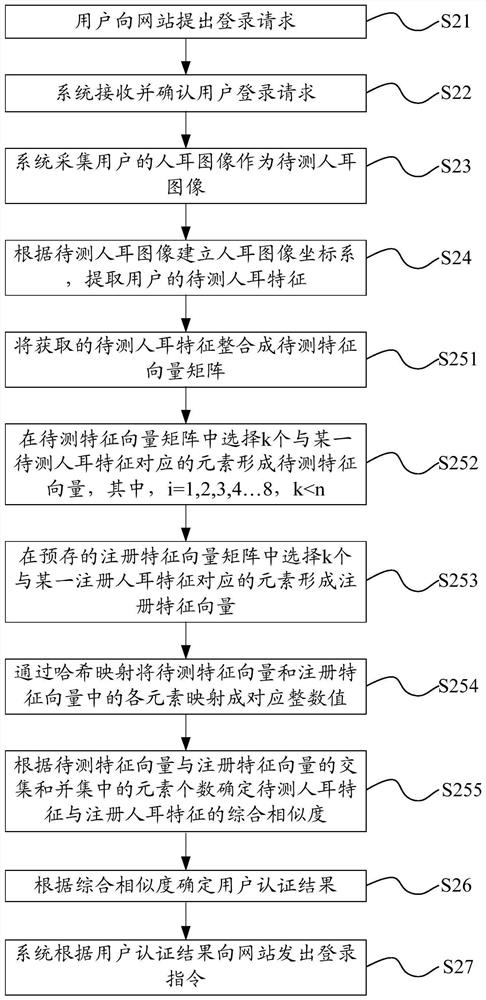
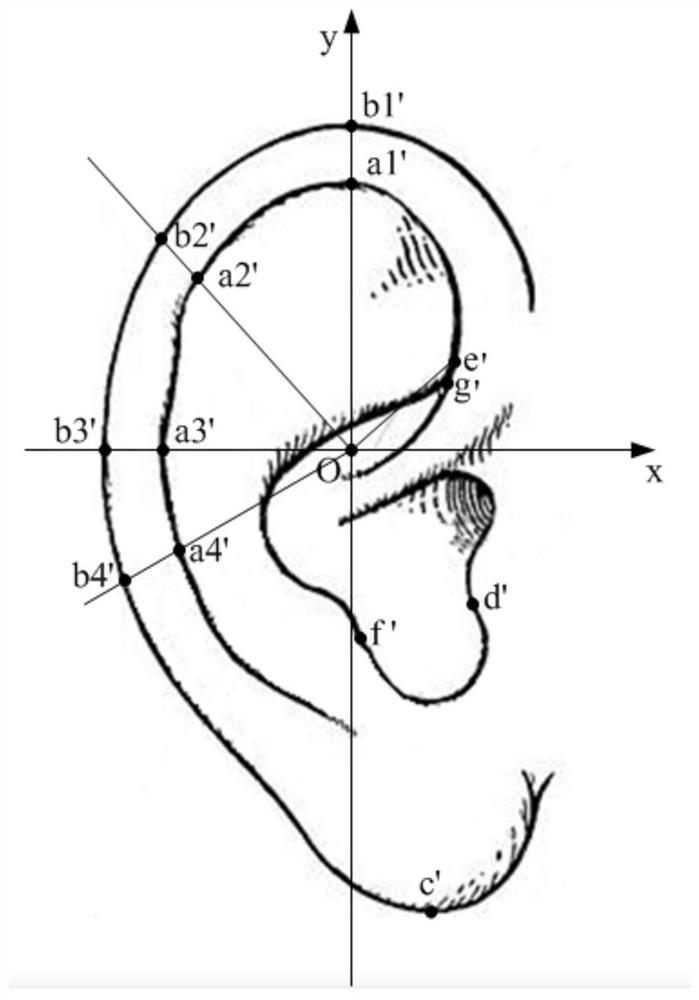
ActiveCN107370769AImprove login securityImage analysisTransmissionUser authenticationComputer science
The invention provides a user authentication method and system, belongs to the technical field of identity authentication, and is intended to solve the problem that as existing user login has poor security, login by thefts easily occurs. The user authentication method comprises: receiving a user login request; acquiring an ear image of a user as an ear image to be detected; establishing an ear image coordinate system according to the ear image to be detected, and extracting the user's ear characteristics r to be detected; calculating integrated similarity Rho r between the ear characteristics r to be detected and the user's registered ear characteristics r' prestored; determining user authentication results according to the integrated similarity Rho r.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Application login verification method, device, equipment and storage medium
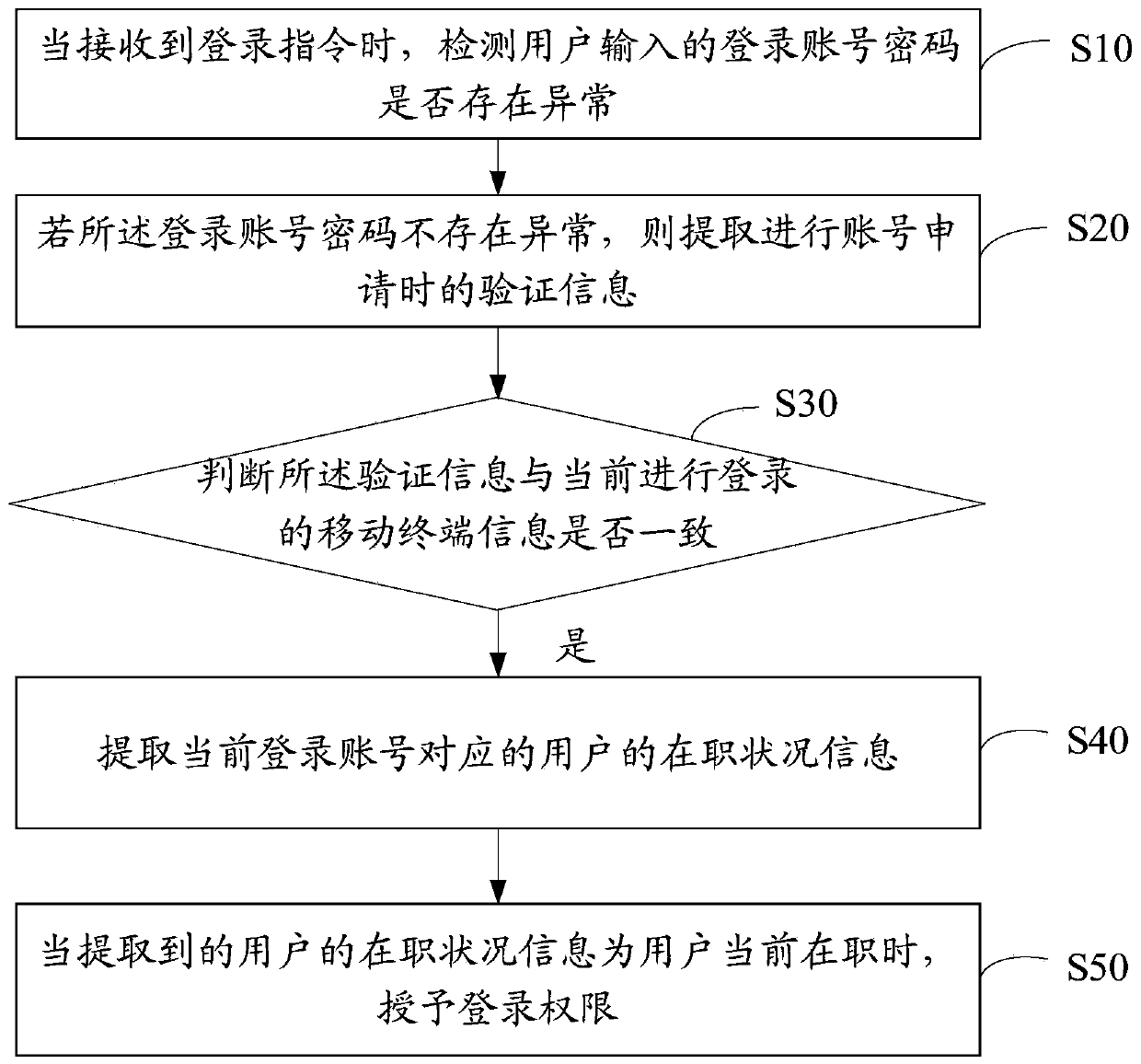
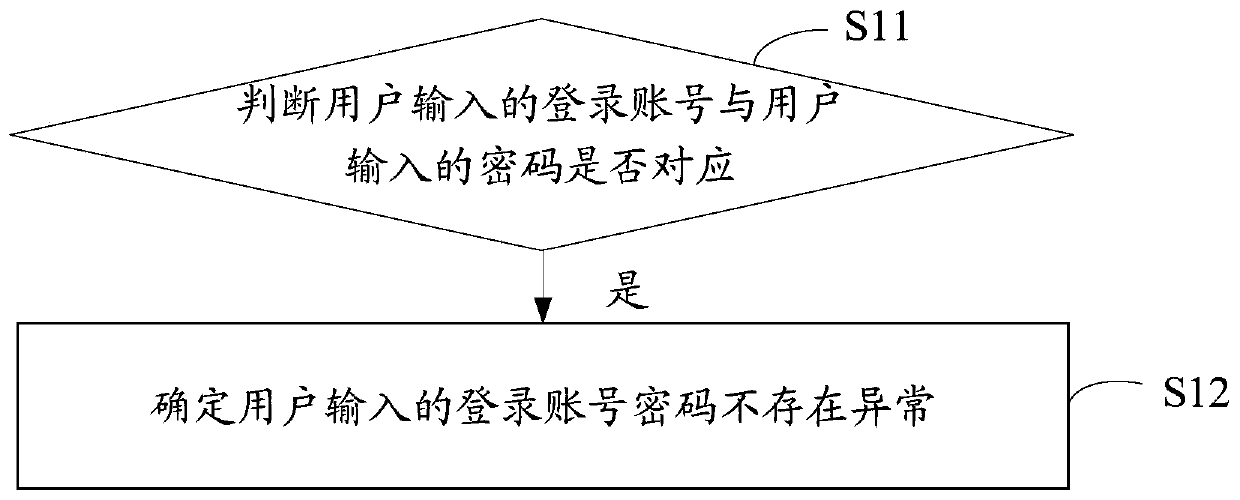
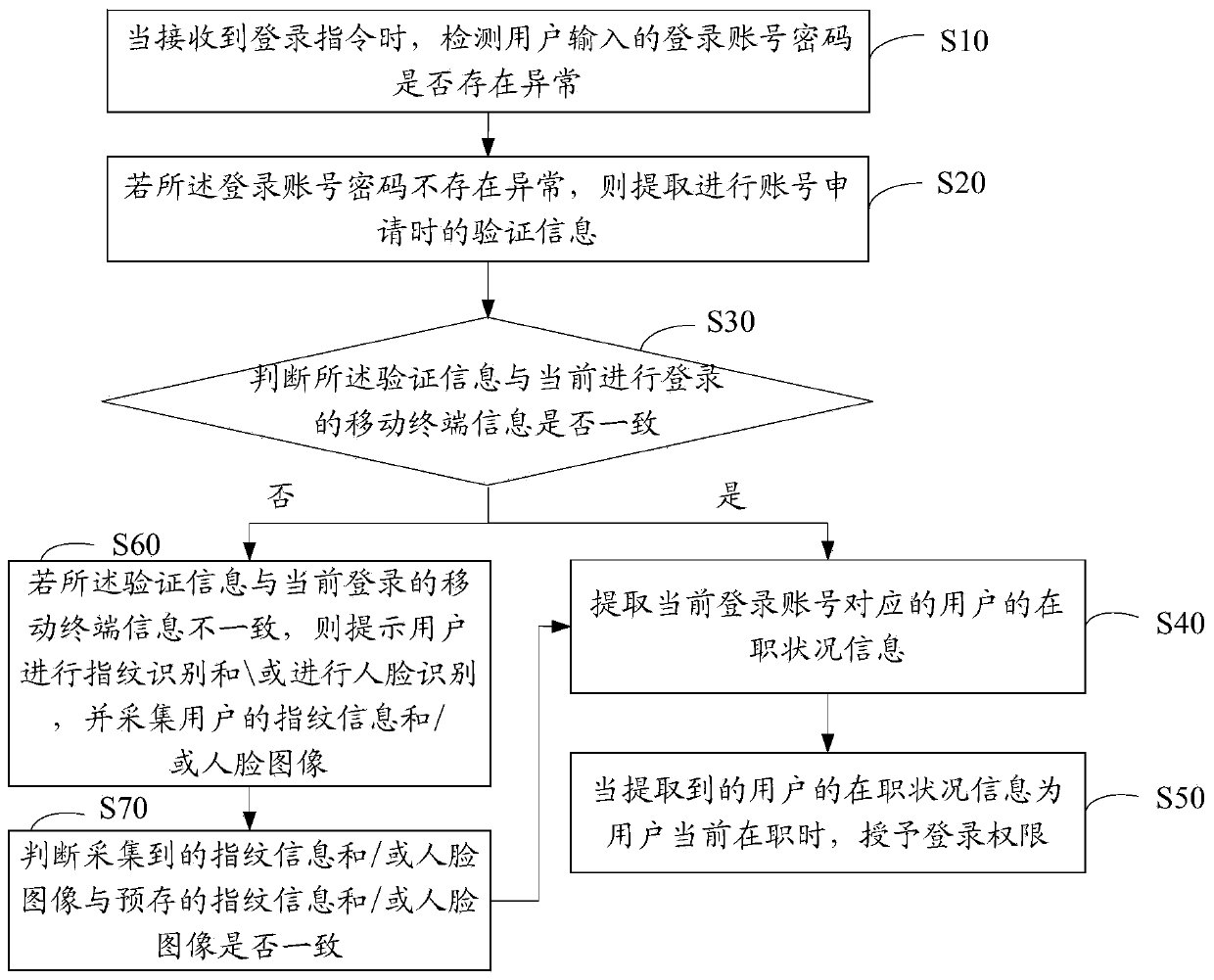
ActiveCN107911340BGuarantee property securityGuarantee the safety of lifeTransmissionPasswordEngineering
The invention discloses an application login authentication method. The method includes the following steps that: when a login instruction is received, whether an account login password inputted by auser is abnormal is detected; if the account login password is normal, authentication information generated when an account is applied is extracted; whether the authentication information is consistent with the information of a currently logged-in mobile terminal is determined; if the authentication information is consistent with the information of the currently logged-in mobile terminal, the employment status information of the user corresponding to the current logged-in account is extracted; and when the extracted employment status information of the user indicates that the user is employed,a login permission is granted. The invention also discloses an application login authentication device, an application login authentication apparatus, and a storage medium. With the application loginauthentication method, device, apparatus, and storage medium of the invention adopted, the security of application login can be improved.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
Medical equipment login method and device
ActiveCN106529237BImprove login securityPrevent malicious tamperingDigital data authenticationMedical equipmentAuthorizationComputer science
The invention provides a medical device logging-in method and apparatus. The medical device logging-in method includes: acquiring an identity identification ID of an authorization dongle currently stored in a medical device; logging in a dongle to be logged which is currently connected to the medical device according to the ID of the authorization dongle; acquiring a machine code of the dongle to be logged if the dongle to be logged is logged successfully, and determining whether or not the machine code of the dongle to be logged matches a machine code stored in the medical device; and confirming the fact that the dongle to be logged successful logs in the medical device if so. The medical device logging-in method and apparatus can improve the logging-in security of the medical device, can avoid illegal logging-in of the medical device, and can avoid the problem the data of the medical device is lost due to illegal logging-in of the medical device.
Owner:WUXI HISKY MEDICAL TECH
A client login method, client and system
The embodiment of the invention discloses a method and system for logging in a client and a client. The method for logging in a client comprises: a logging-in verification request sent by a target client is received; according to the logging-in verification request, identity verification matching information of the target client is obtained; an associated logging-in verification request is submitted to a first server, so that the first server obtains logging-in verification information of the target client according to the associated logging-in verification request; the logging-in verification information, returned by the first server, of the target client is received; and the logging-in verification information of the target client is sent to the target client, so that the target client can log in a second server by using the logging-in verification information of the target client. According to the invention, rapid logging in of an application client can be realized and a risk of stealing logging-in verification information can be effectively eliminated, so that the logging-in security of the client can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
User authentication method and system
The invention provides a user authentication method and system, belongs to the technical field of identity authentication, and is intended to solve the problem that as existing user login has poor security, login by thefts easily occurs. The user authentication method comprises: receiving a user login request; acquiring an ear image of a user as an ear image to be detected; establishing an ear image coordinate system according to the ear image to be detected, and extracting the user's ear characteristics r to be detected; calculating integrated similarity Rho r between the ear characteristics r to be detected and the user's registered ear characteristics r' prestored; determining user authentication results according to the integrated similarity Rho r.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Authorization code generation method, identity authentication method, terminal, server and medium
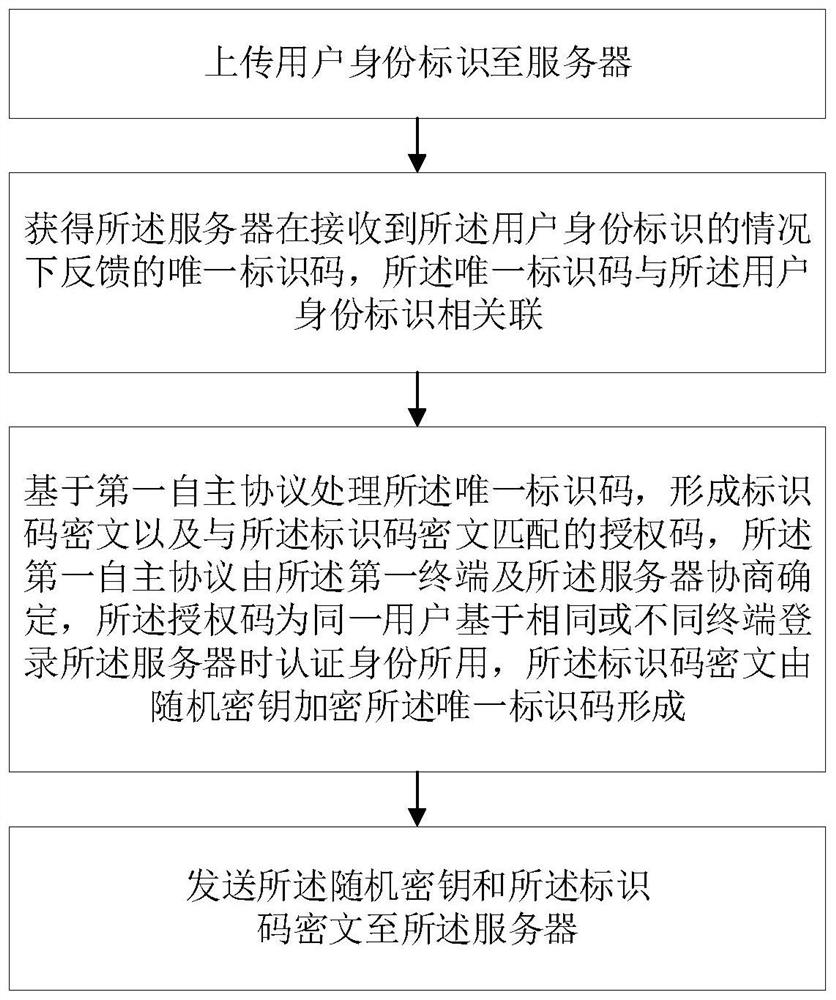
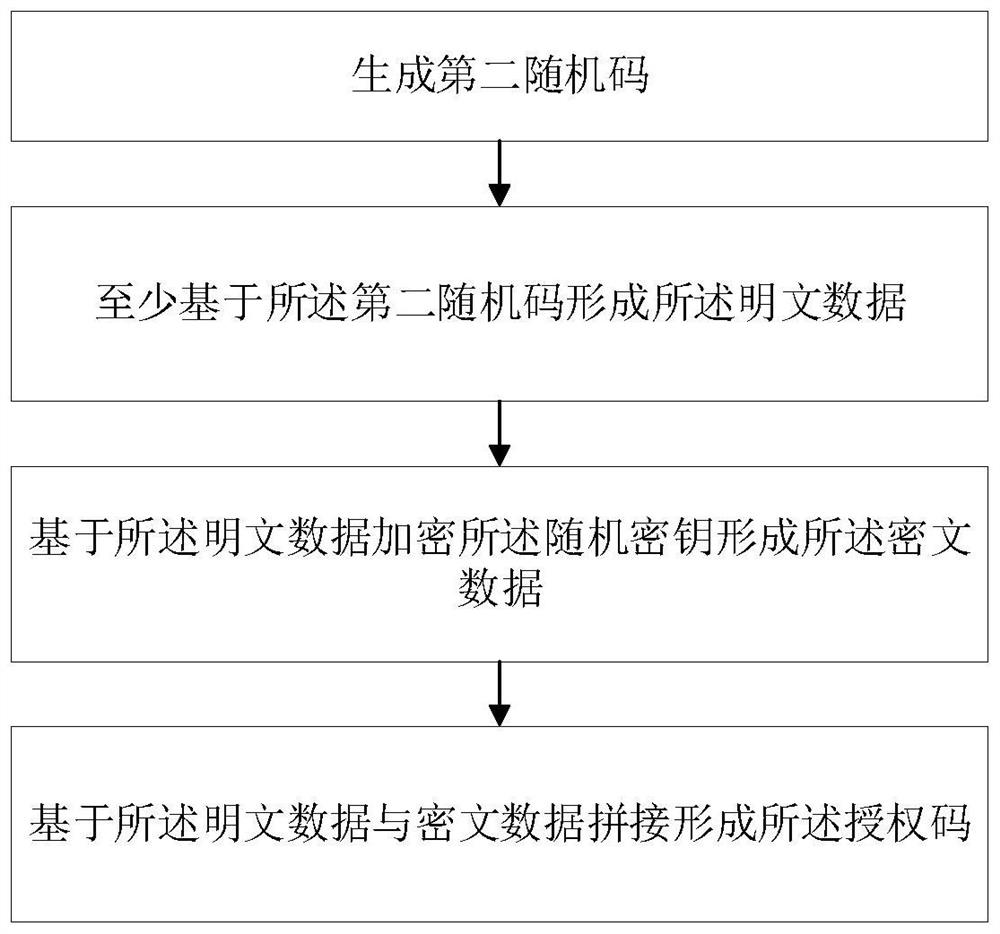
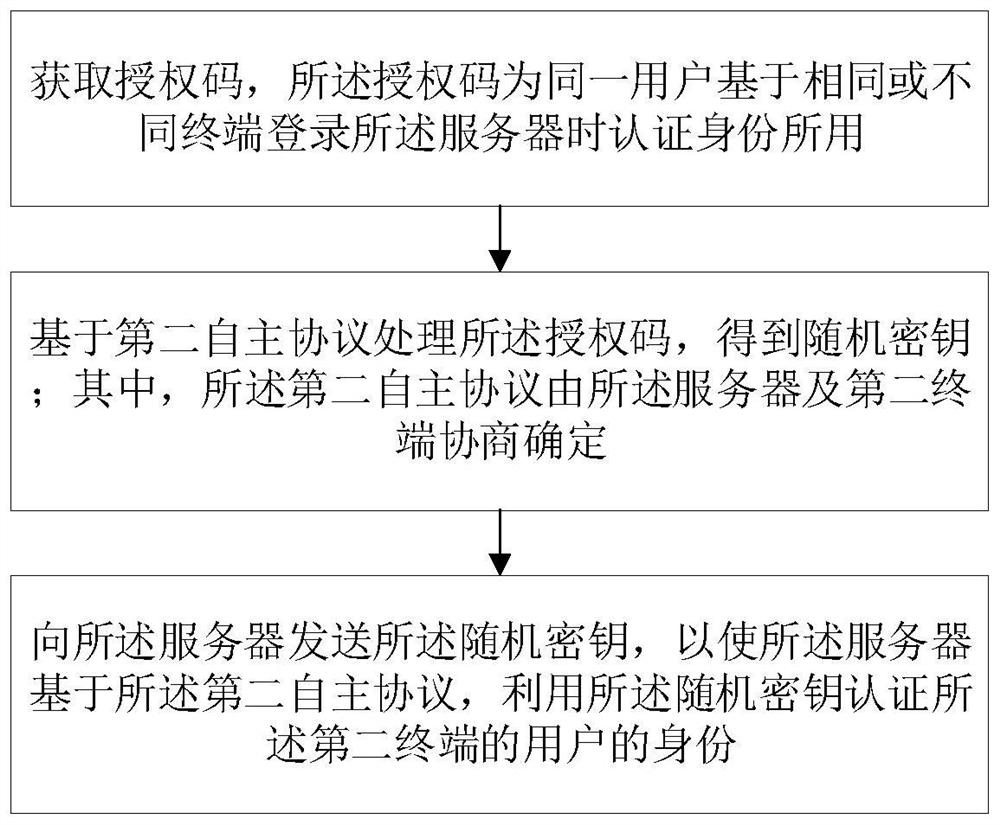
PendingCN114297618AImprove securityRealize multi-terminal loginDigital data authenticationSecuring communicationTerminal serverProtocol processing
The embodiment of the invention provides an authorization code generation method, an identity verification method, a terminal, a server and a storage medium, the authorization code generation method is applied to a first terminal, and the method comprises the following steps: uploading a user identity identifier to the server; obtaining a unique identification code fed back by the server under the condition that the server receives the user identity identifier, wherein the unique identification code is associated with the user identity identifier; the unique identification code is processed based on a first autonomous protocol to form an identification code ciphertext and an authorization code matched with the identification code ciphertext, the first autonomous protocol is determined by negotiation of the first terminal and the server, and the authorization code is used for identity authentication when the same user logs in the server based on the same or different terminals. The identification code ciphertext is formed by encrypting the unique identification code by a random key; and sending the random key and the identification code ciphertext to the server.
Owner:BEIJING SENSESHIELD TECH
A realization method of one-to-many account mapping and binding for multi-screen multi-factor convenient web identity authentication
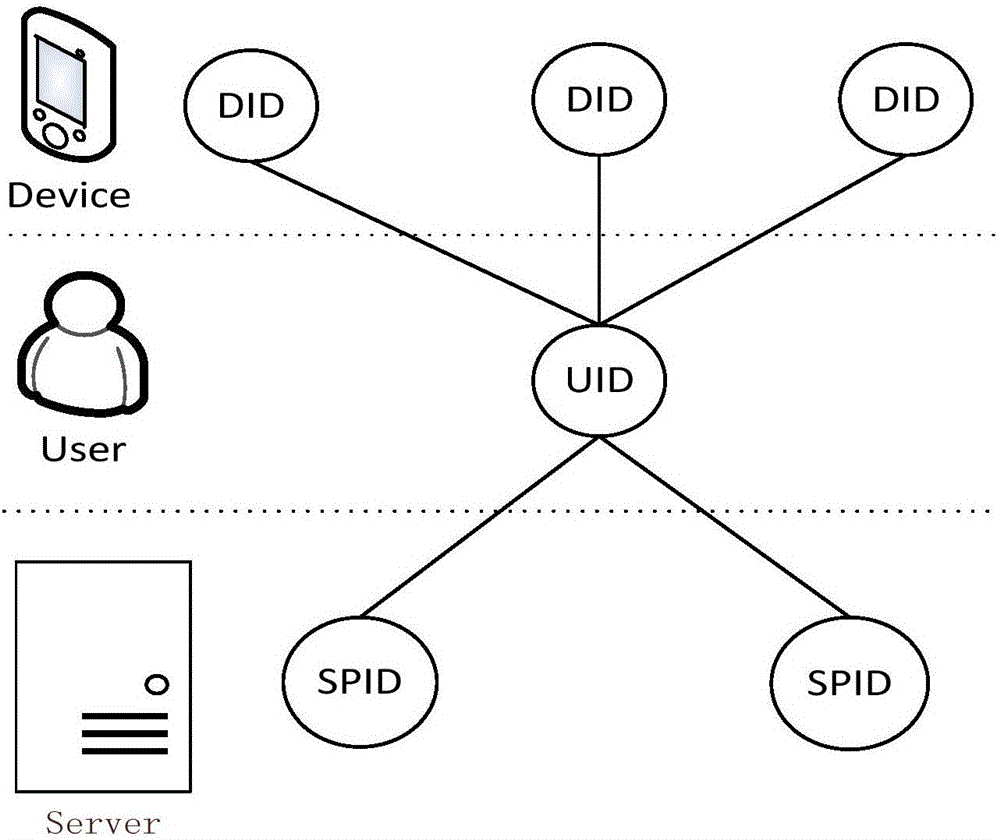
InactiveCN103856332BImprove login securityEnsure safetyUser identity/authority verificationIdentity providerInformation security
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com