User authentication method and system
A user authentication and user technology, applied in the field of identity authentication, can solve the problems affecting the login security of industrial Internet systems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
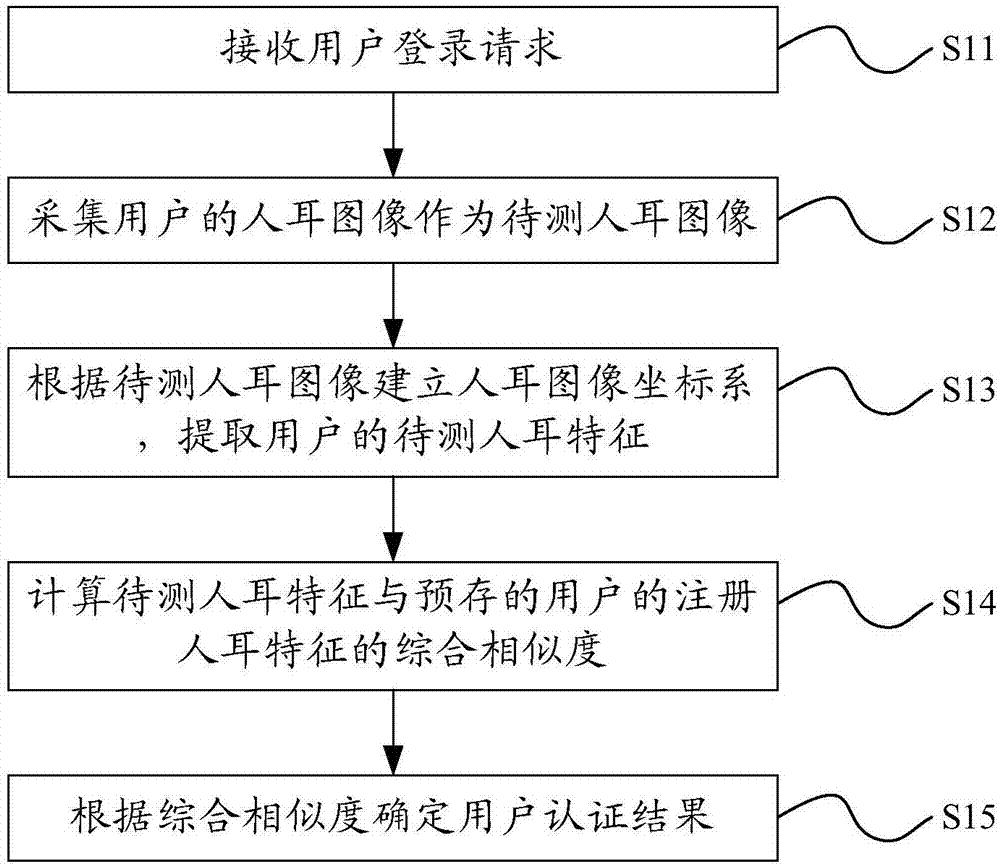
[0050] like figure 1 As shown, this embodiment provides a user authentication method, which is used to effectively authenticate the user when the user needs to identify the user, such as logging in to a website.
[0051] In this embodiment, the user authentication method authenticates the user by collecting the user's ear image. Since the human ear has a rich and stable structure and is similar to a rigid body, it is not easily affected by expression and age changes, so the human ear recognition has a wide range of applications. application prospects.
[0052] The user authentication methods include:
[0053] S11. Receive a user login request.
[0054] S12. Collect the human ear image of the user as the human ear image to be tested.
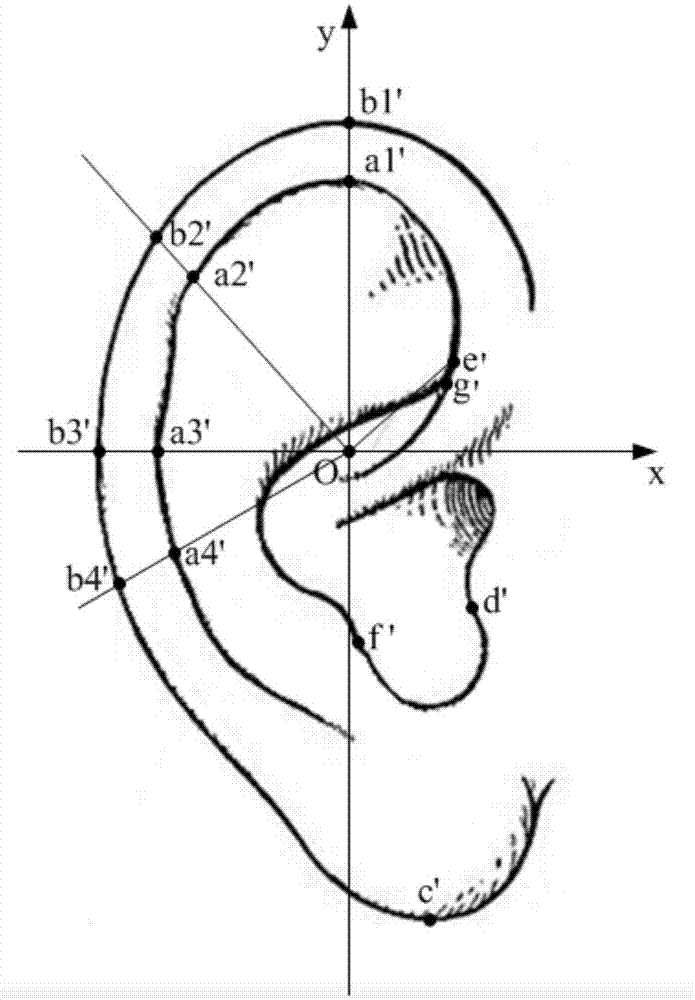
[0055] S13. Establish a human ear image coordinate system according to the human ear image to be tested, and extract the user's human ear feature r to be tested.
[0056] S14. Calculate the comprehensive similarity ρ between the human ear fea...
Embodiment 2
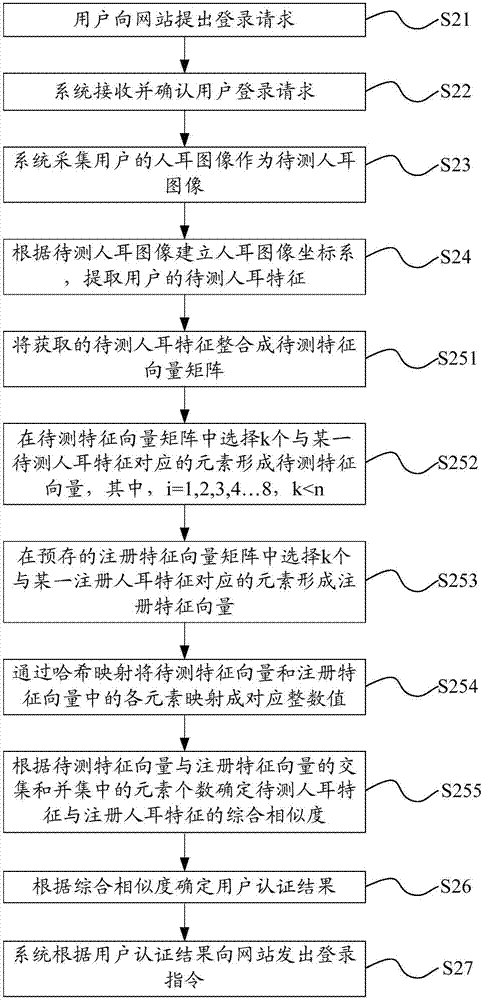
[0060] like Figures 2 to 4 As shown, this embodiment provides a user authentication method, which can effectively authenticate the user when the user needs to identify the user's identity when logging in to a website or the like.
[0061] In this embodiment, a user logging in to a website is taken as an example for illustration, and the user authentication method is implemented based on the following background.
[0062] The user submits a registration request to the website, and enters his own ear image as a registration sample (registered ear image); the system obtains and stores the user's registered ear feature r' (the user's ear feature when registering) according to the registration sample.
[0063] Wherein, when the user registers, he can specifically click on register on the website page and input a user name (such as a user name designed by himself, registered mobile phone number, email address, etc.) to apply for registration. Preferably, the user authenticates and...
Embodiment 3
[0126] like Figure 5 As shown, this embodiment provides a user authentication system, including a receiving unit, a collecting unit, an extracting unit, a calculating unit, and a judging unit.
[0127] Wherein, the receiving unit receives a user login request.
[0128] The acquisition unit acquires an image of the user's ear as the image of the ear to be tested.
[0129] The extraction unit establishes a human ear image coordinate system according to the human ear image to be tested, and extracts the user's human ear feature r to be tested.
[0130] The calculation unit calculates the comprehensive similarity ρ between the human ear feature r to be tested and the pre-stored user's registered ear feature r' r .
[0131] Preferably, the calculation unit includes a feature vector determination module and a comprehensive similarity ρ r Determine the module.
[0132] Wherein, the eigenvector determination module performs one or more eigenvector determinations according to the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com