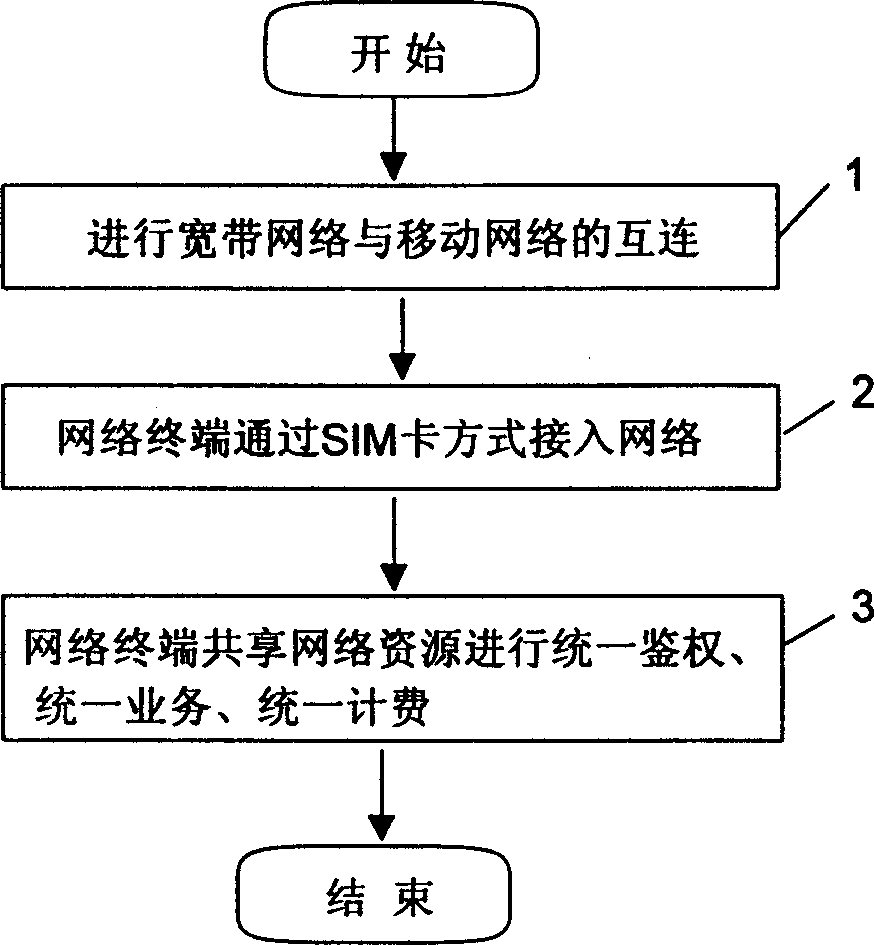
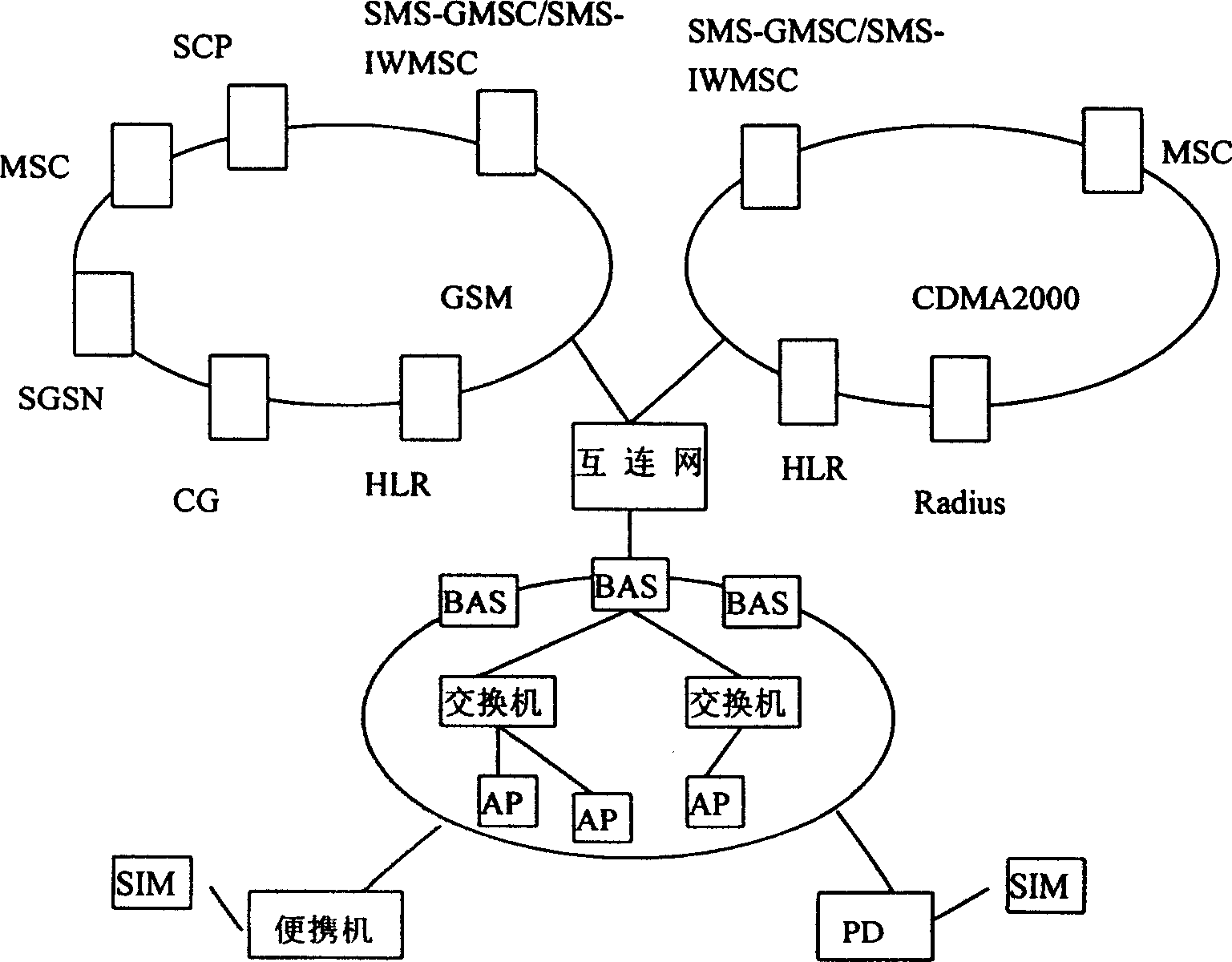
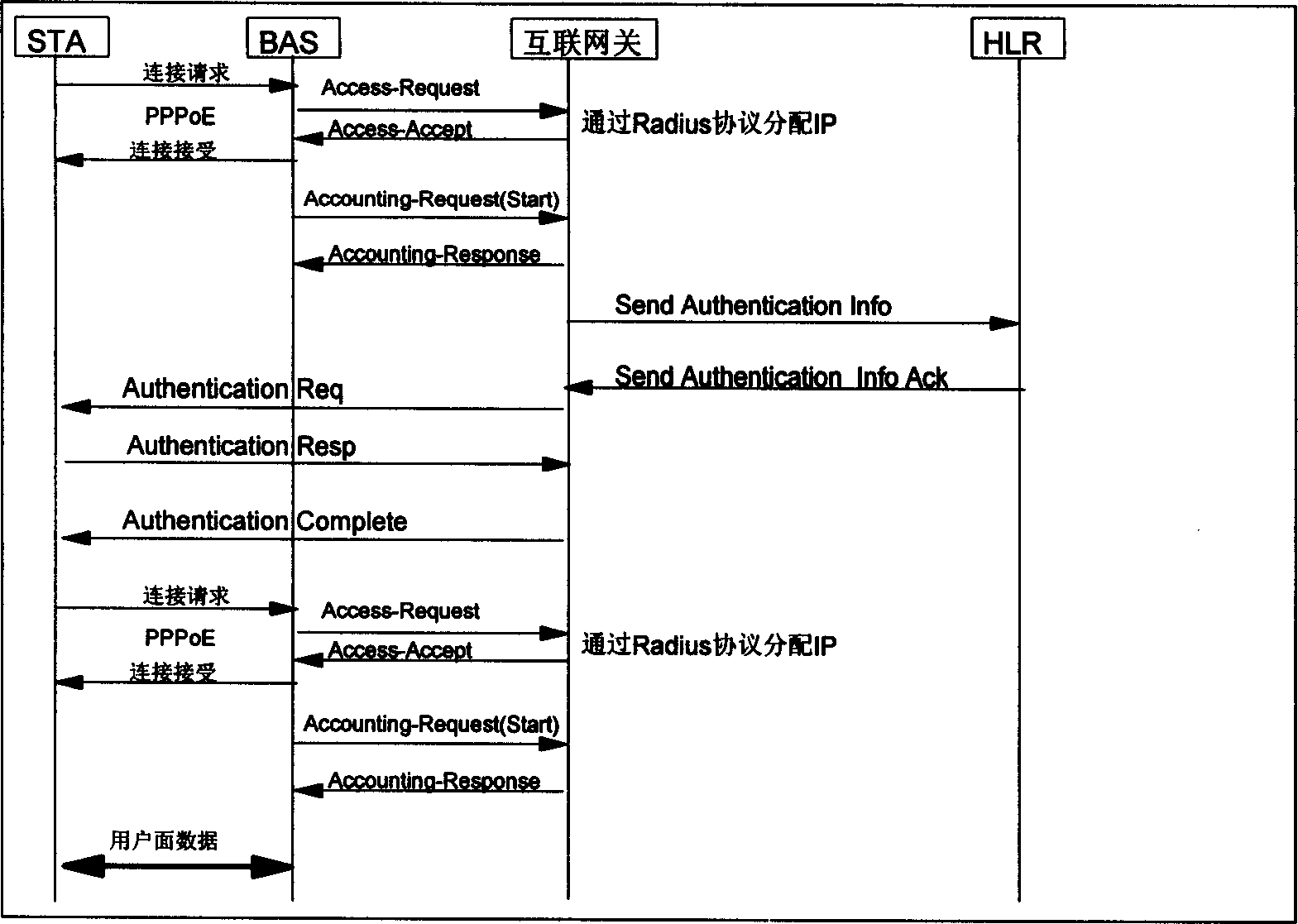
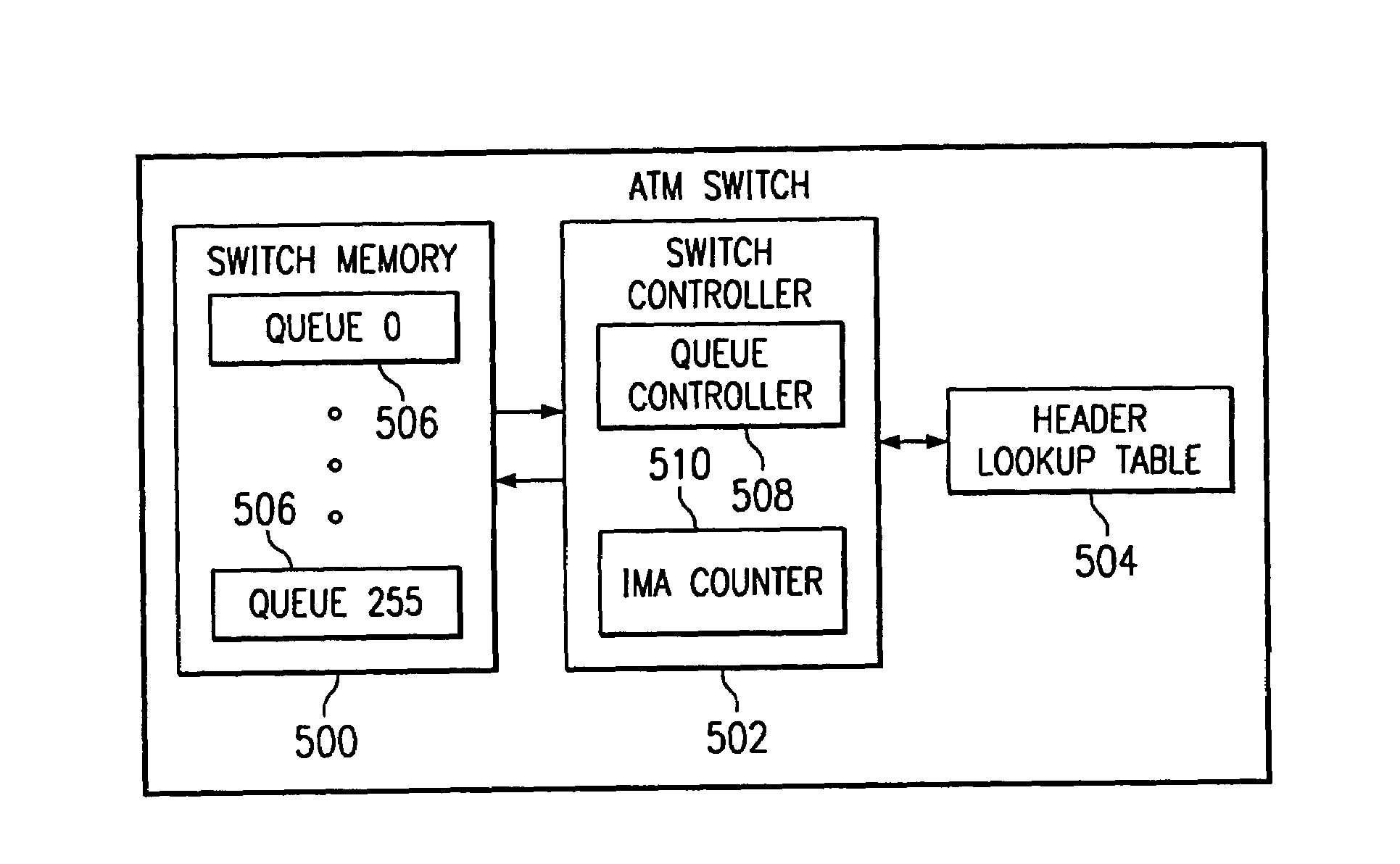
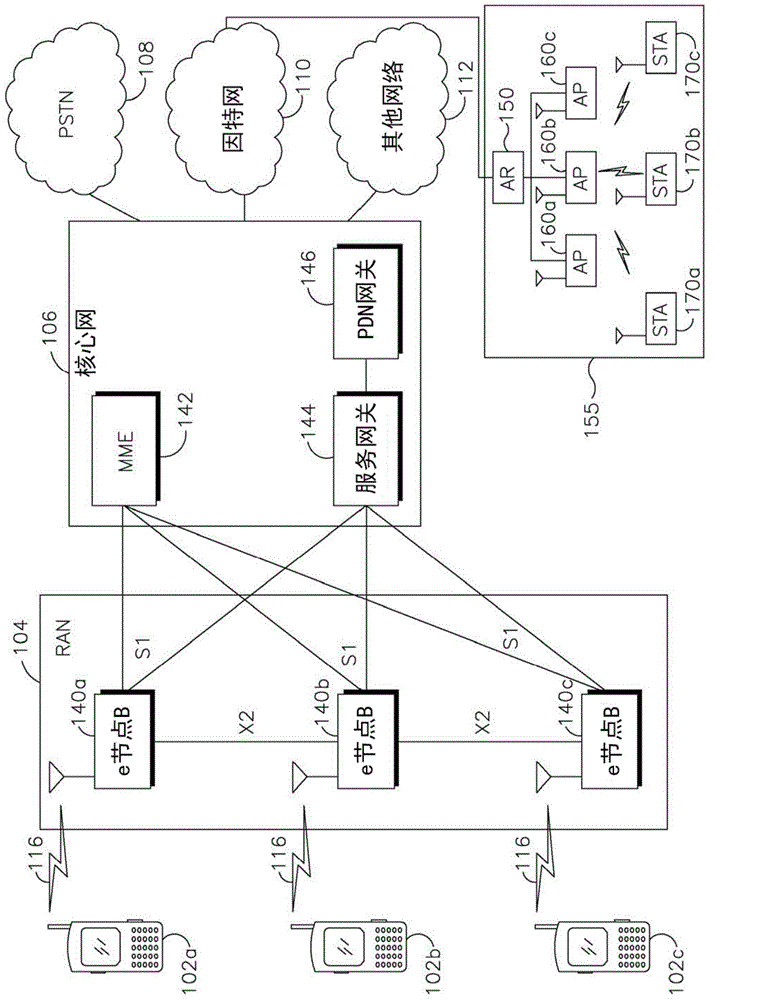
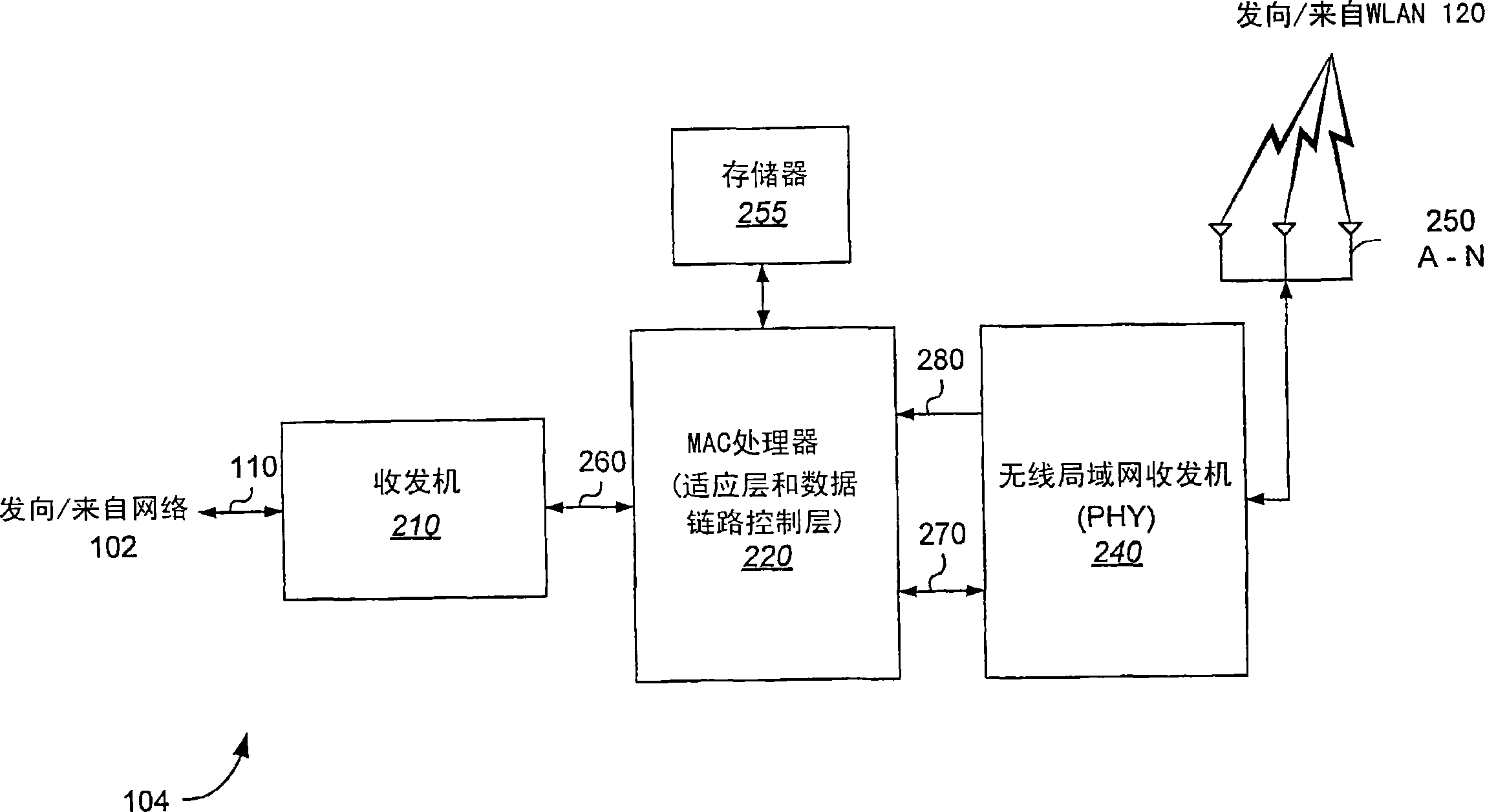
Patents
Literature
133results about "Answer-back mechanisms" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Security and privacy enhancements for security devices
InactiveUS20060288407A1Improve securityImprove privacyKey distribution for secure communicationPublic key for secure communicationInternet privacySubscriber identity module
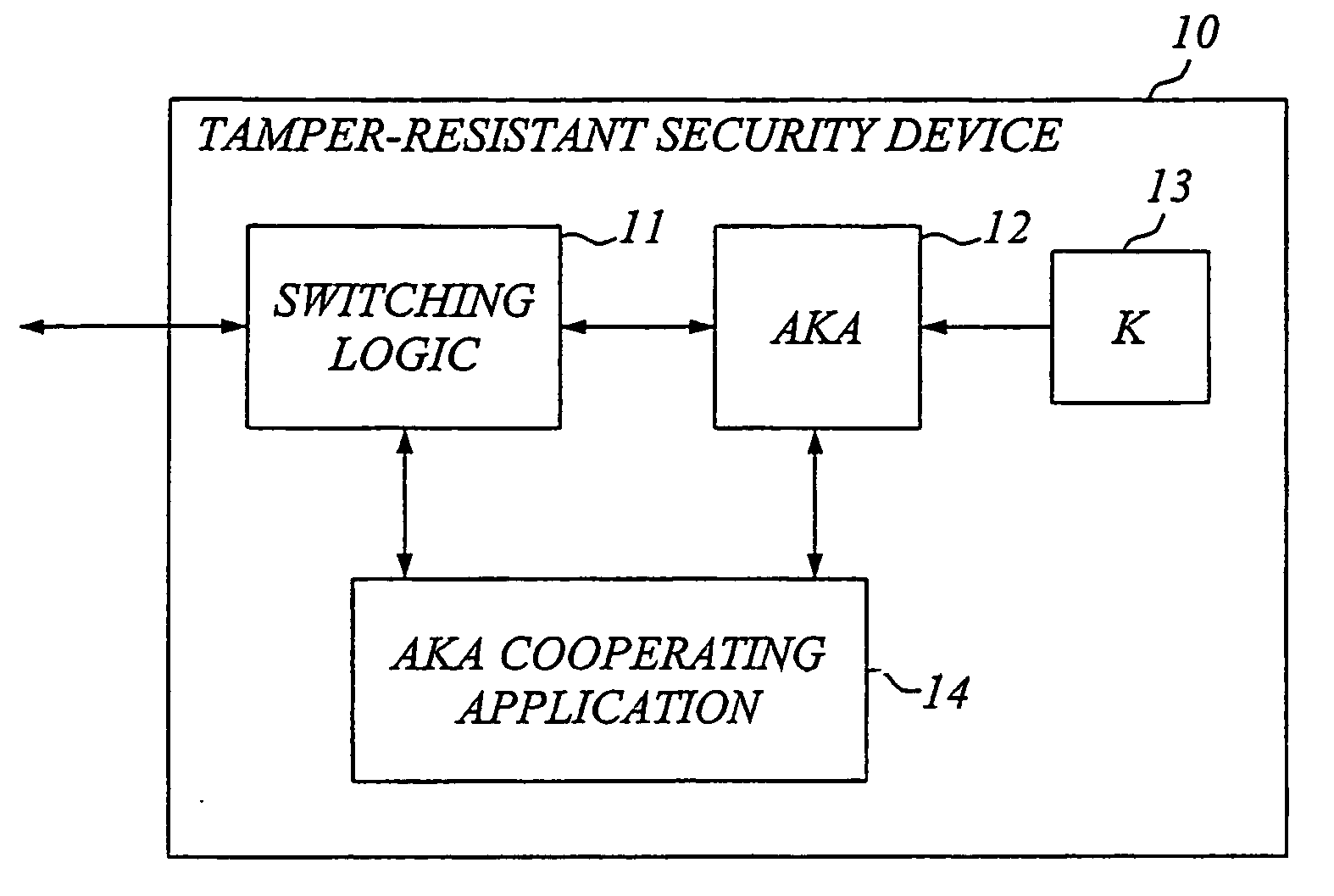
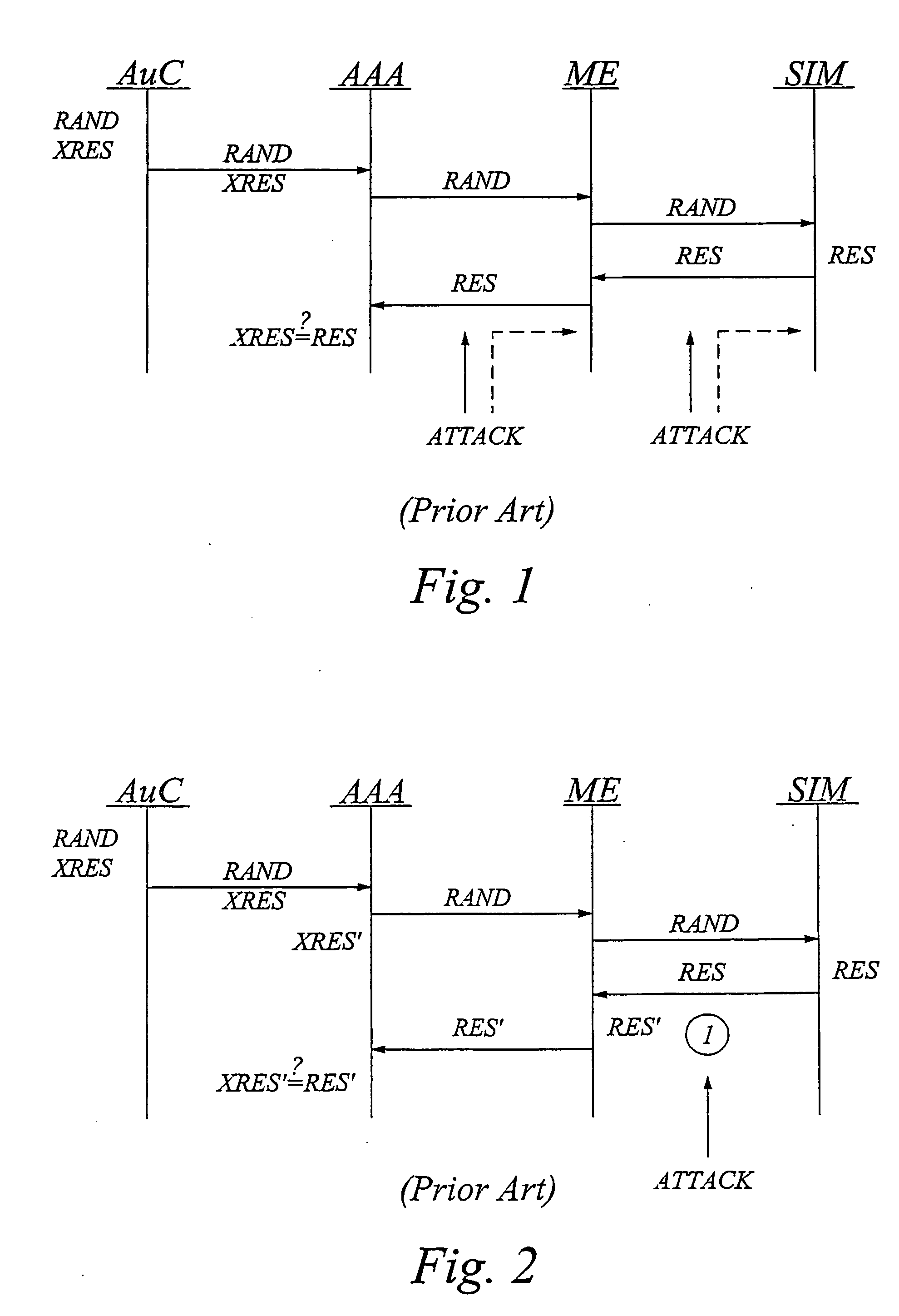
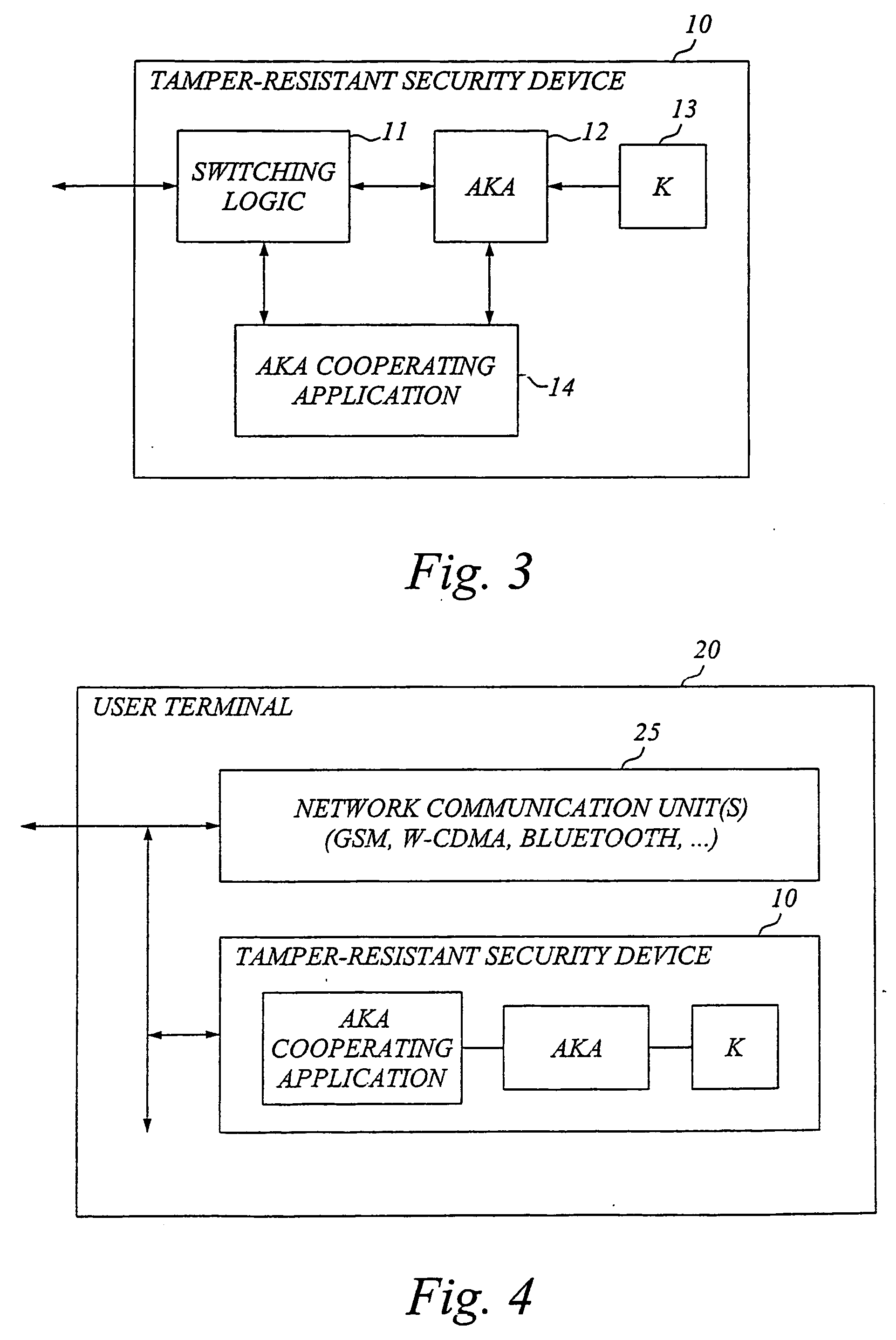
The invention generally relates to a tamper-resistant security device, such as a subscriber identity module or equivalent, which has an AKA (Authentication and Key Agreement) module for performing an AKA process with a security key stored in the device, as well as means for external communication. The idea according to the invention is to provide the tamper-resistant security device with an application adapted for cooperating with the AKA module and means for interfacing the AKA module and the application. The application cooperating with the AKA module is preferably a security and / or privacy enhancing application. The application is advantageously a software application implemented in an application environment of the security device. For increased security, the security device may also be adapted to detect whether it is operated in its normal secure environment or a foreign less secure environment, and set access rights to resident files or commands that could expose the AKA process or corresponding parameters accordingly.
Owner:TELEFON AB LM ERICSSON (PUBL)
Apparatus and method for coordinately managing media content
InactiveUS20050135341A1Data processing applicationsDigital computer detailsComputer networkMedia server
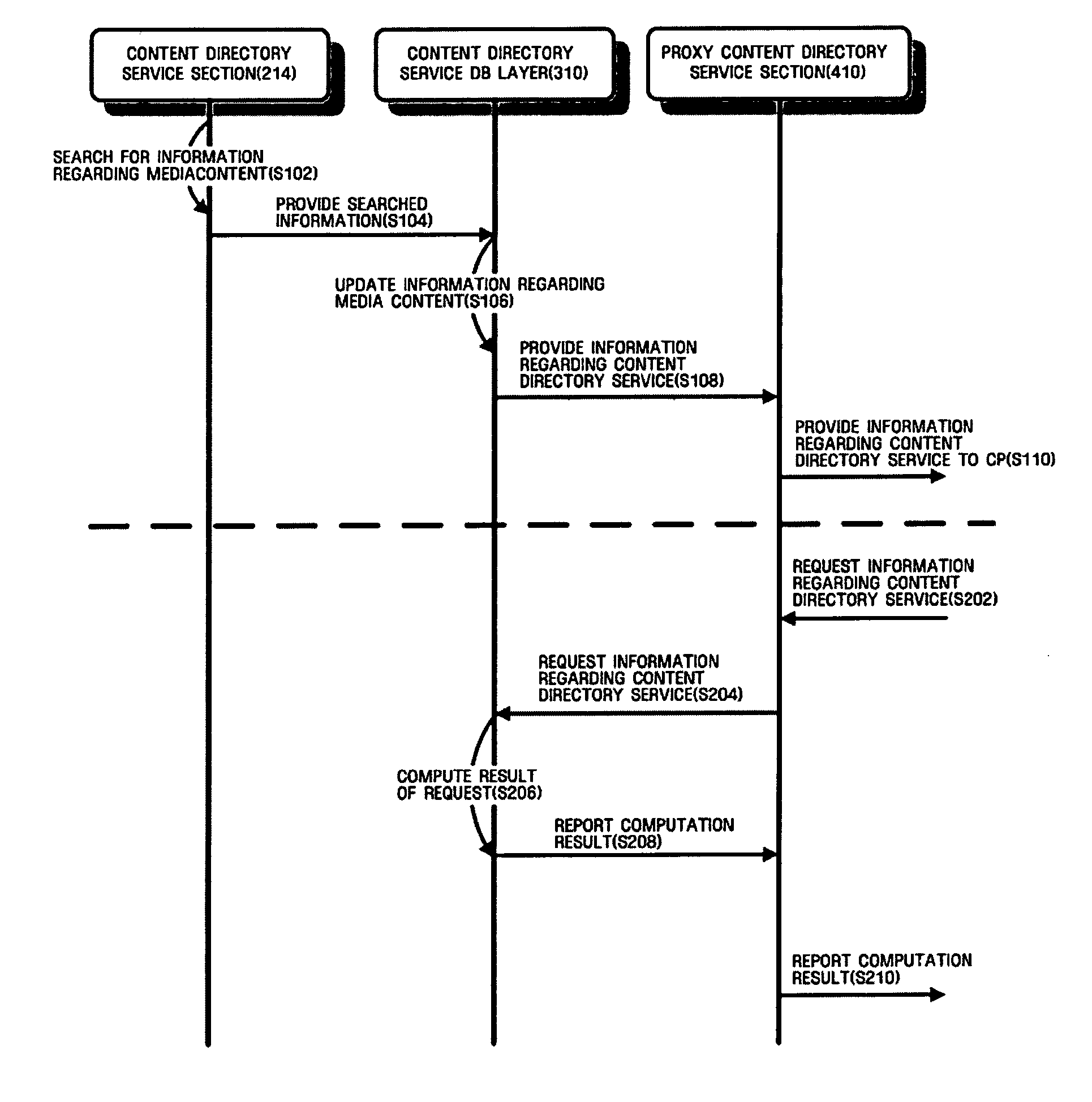
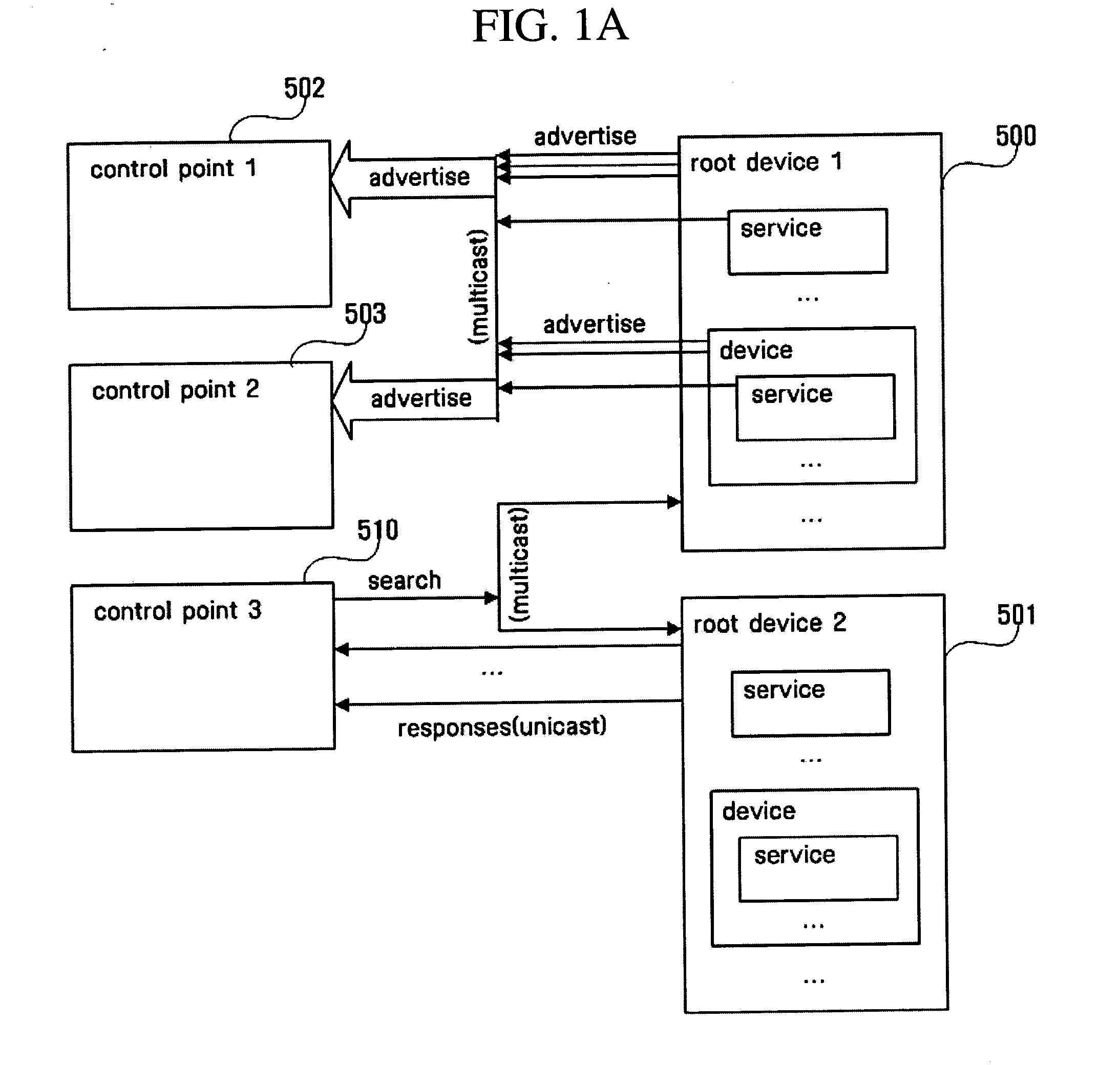
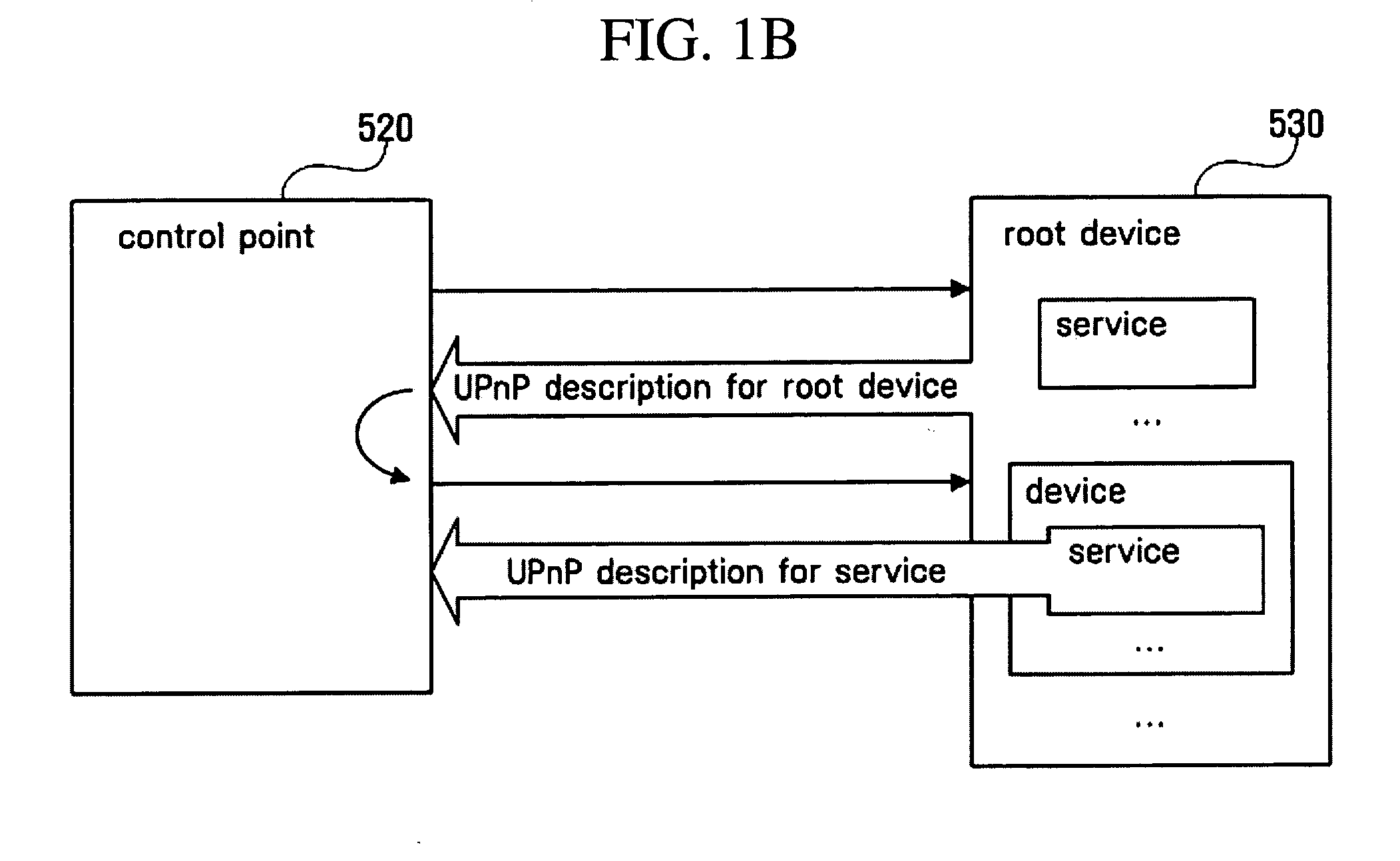
An apparatus that is connected to and controls a media server and a media renderer that is connected to a home network, stores and manages information regarding media content included in the media server, and provides a directory service with respect to all media content under a home network environment. The apparatus includes a media server directory module which stores and manages meta data of the media content comprised in all media servers existing under the home network environment and stores and manages connection information regarding the media servers. Also included is a proxy media server module which provides a content directory service, and a media server control point module which controls the media server directory module and the proxy media server module, searches for the media content, and brings and stores the meta data of the searched media content in the media server directory module.
Owner:SAMSUNG ELECTRONICS CO LTD
An online help platform system and its realization method
InactiveCN101237327AMeet the request for helpMeet special needsSpecial service provision for substationSpecial service for subscribersOnline helpComputer science
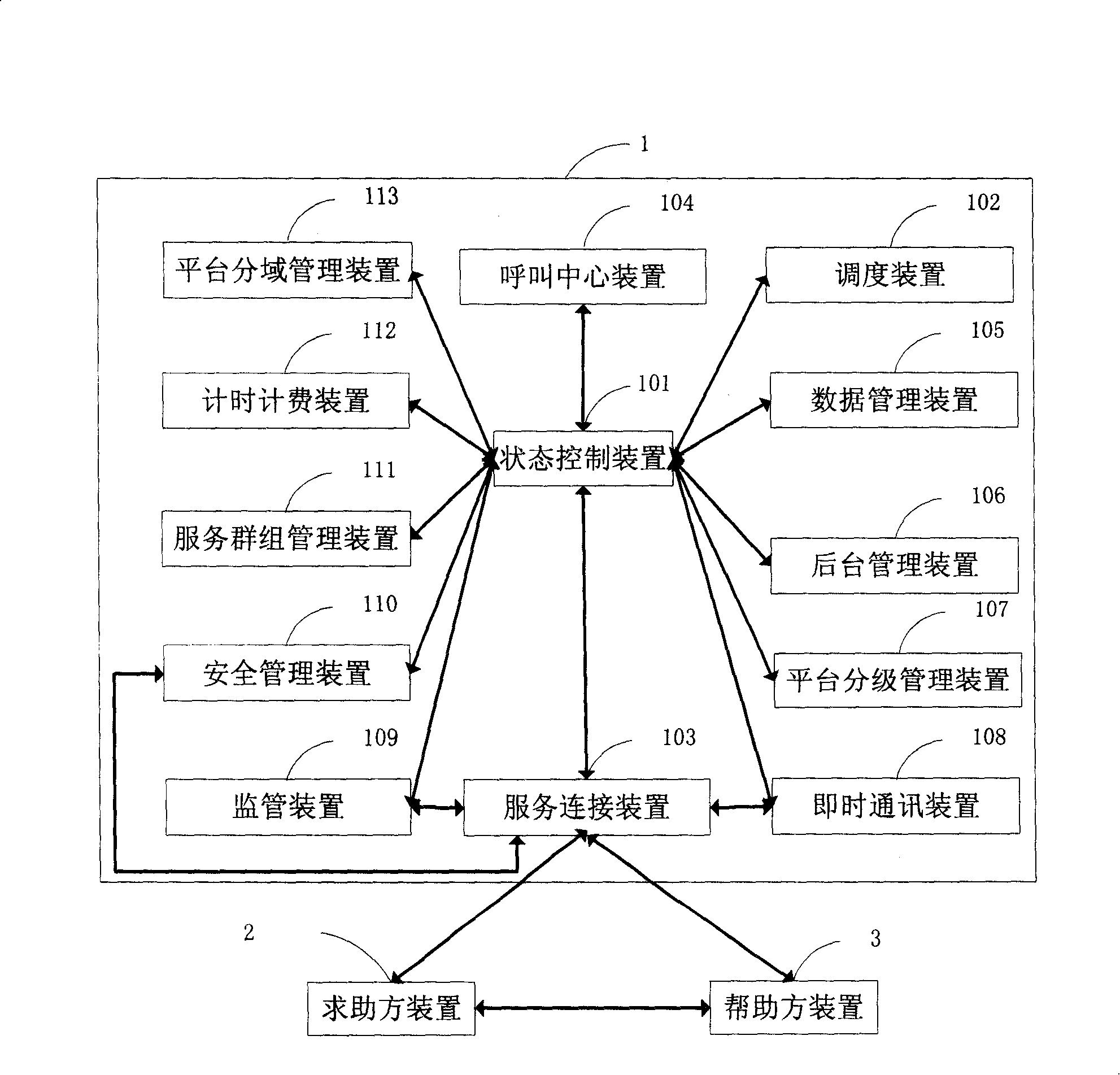
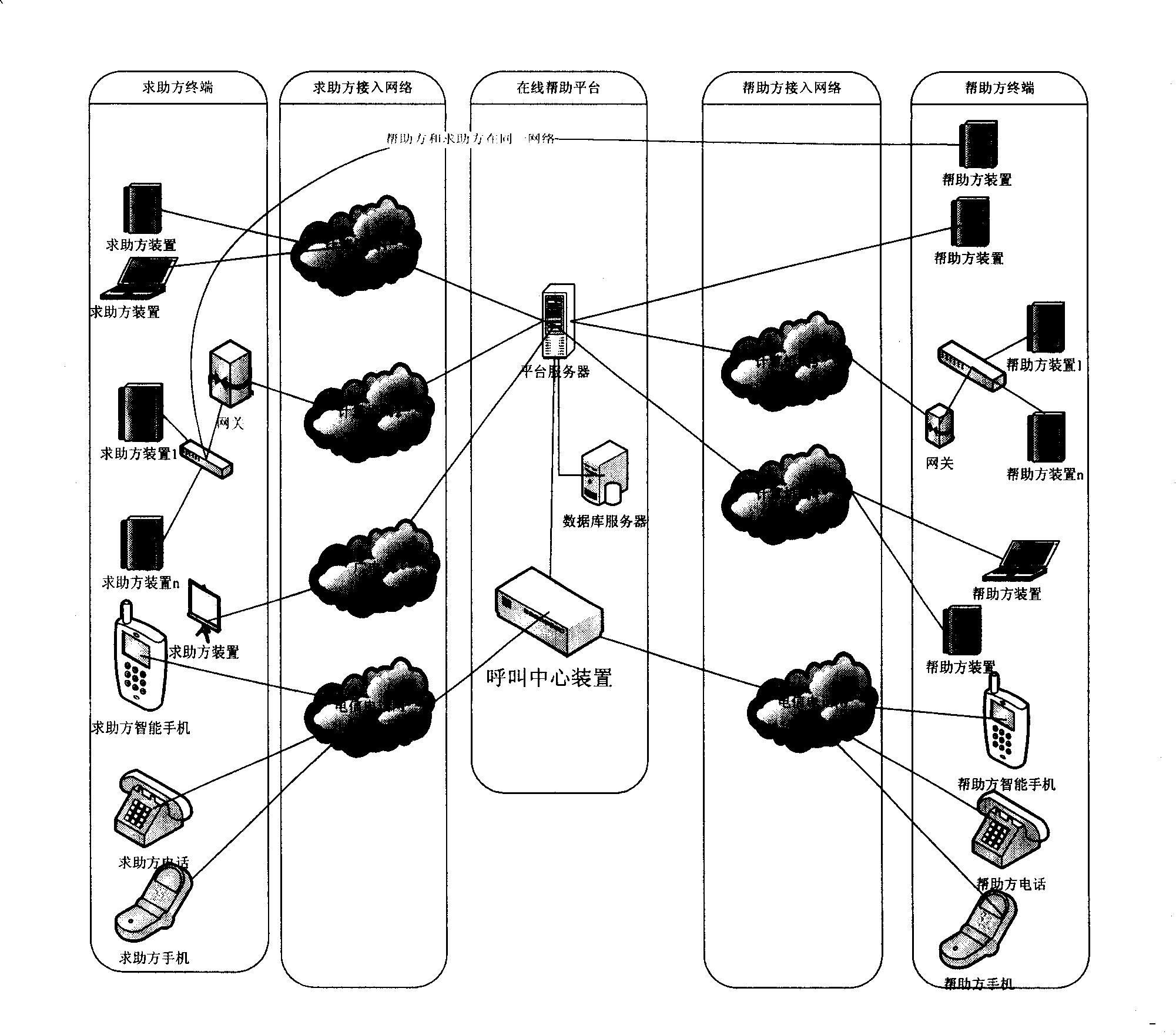
The invention relates to an online assistance platform system and a realization method thereof, wherein the platform system comprises an online assistance platform, at least one seeking-for-help party device and at least one help party device; the online assistance platform, which at least comprises a status management device, a dispatching device, a supervision device, an instant communication device, a calling center device, a timing charging device and a safety management device, etc., realizes management based on status and the dispatching of the seeking-for-help request of a seeking-for-help party. Moreover, the online assistance platform, which is based on a peripheral device management device, is another realizing mode of an online assistance platform system and ensures that the dispatching device and the instant communication device, etc. are allocated and connected outside the platform in a plurality of modes. The invention, which provides a status-based online assistance platform system of unified access, unified dispatching and unified management, provides a plurality of help parties and seeking-for-help parties with information services and technical supports including remote screen operation, audio, video and files, etc. by means of a network in the mode of direct connection or forwarding connection.
Owner:北京帮助在线信息技术有限公司
Method and system for managing access to information and the transfer thereof
InactiveUS7168094B1Digital data processing detailsAnswer-back mechanismsLibrary scienceAccess to information
The present invention relates to a method and system for managing access to information and the transfer thereof. More particularly, the present invention relates to a method and system for managing, via at least one intermediary server, access to information and the transfer thereof.
Owner:INTRALINKS
Method and apparatus for transferring data between IP network devices and SCSI and fibre channel devices over an IP network
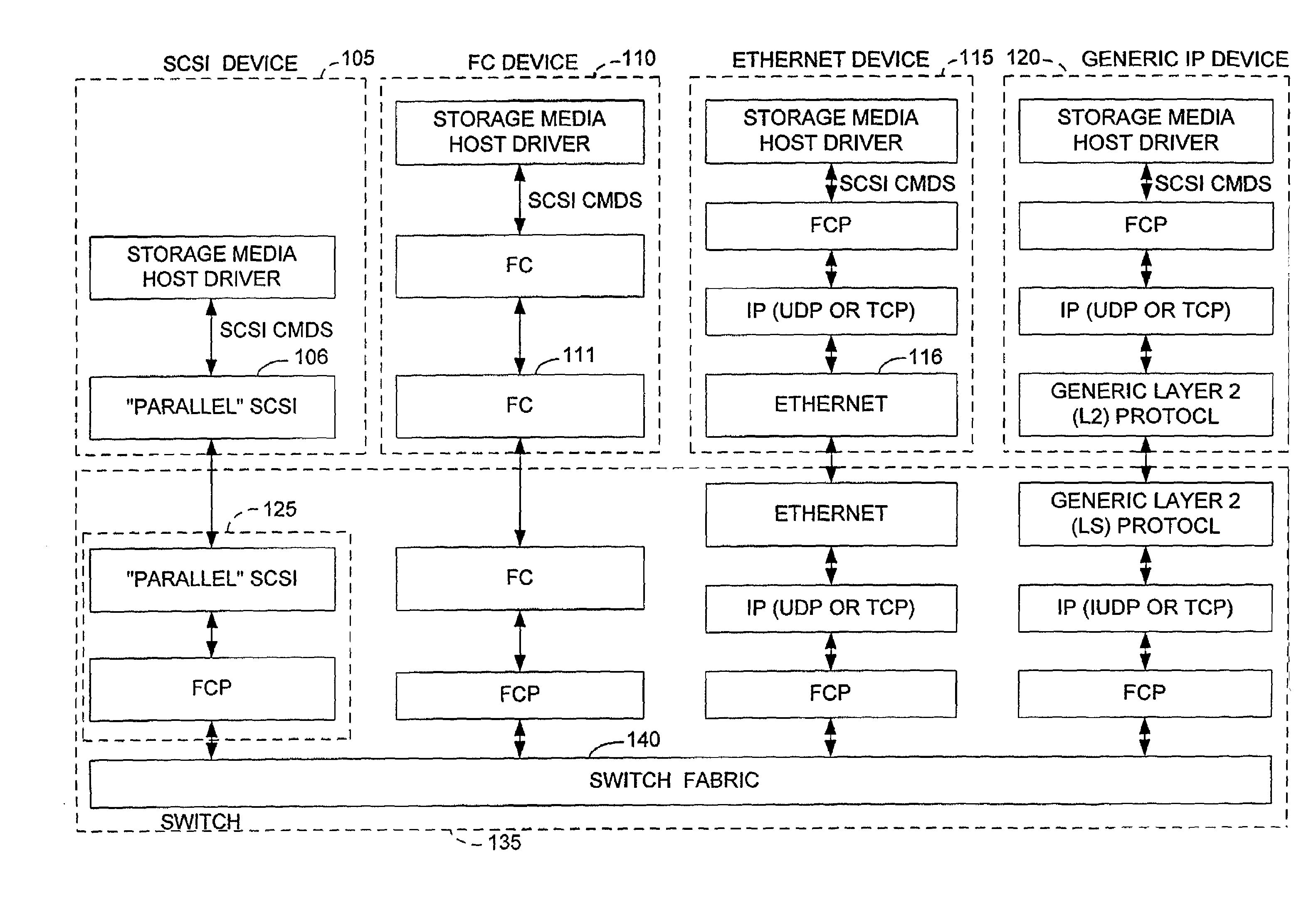
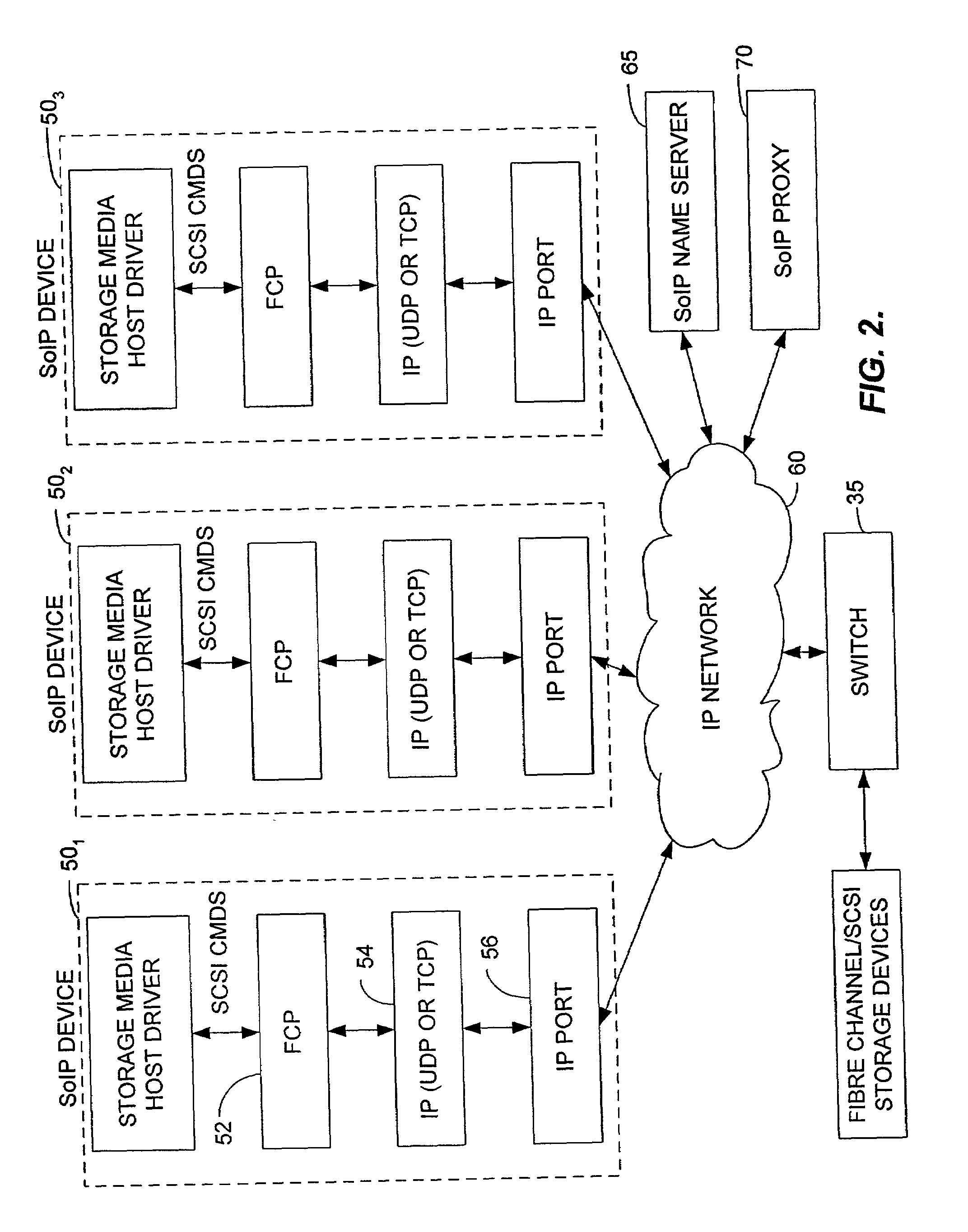
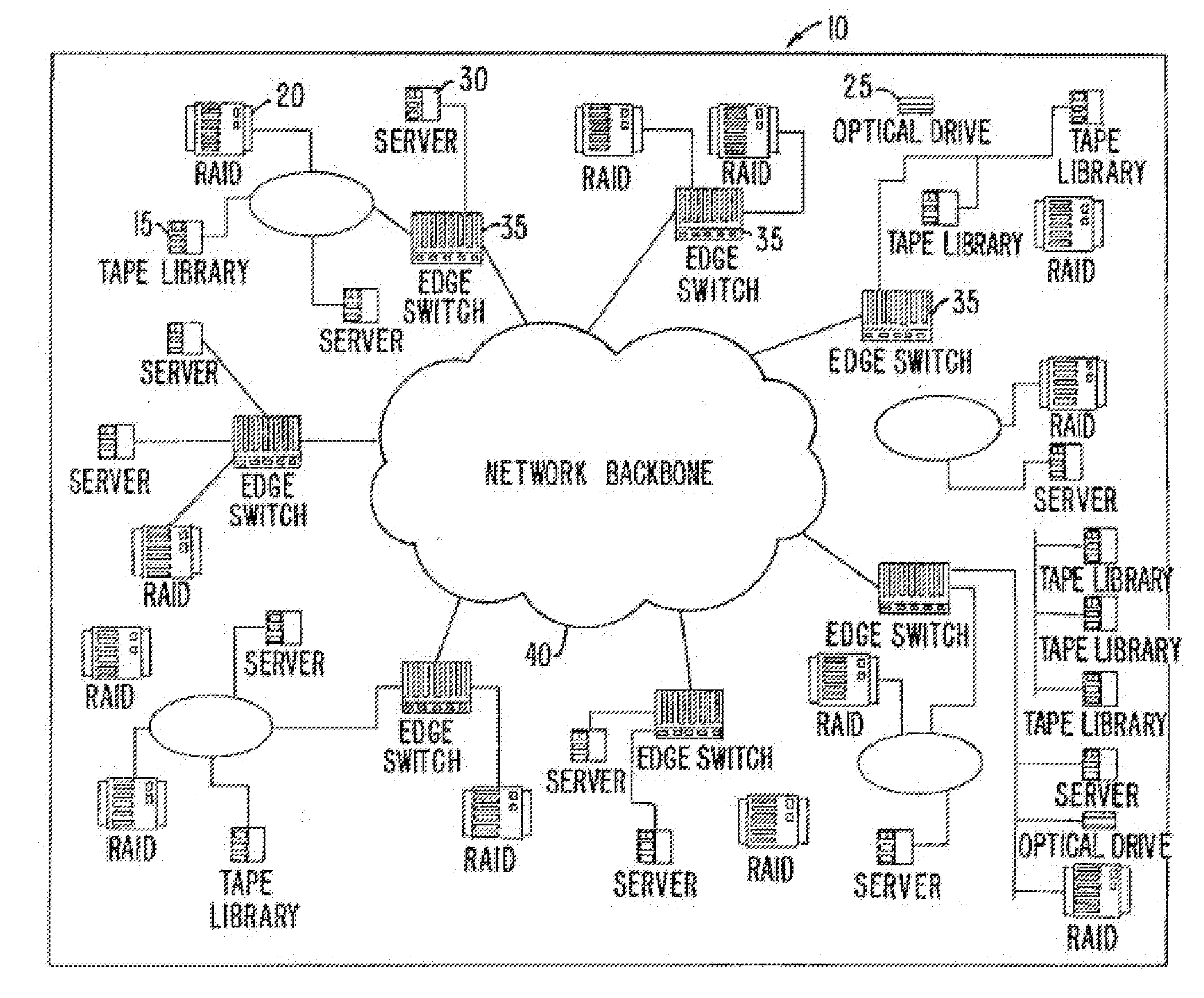
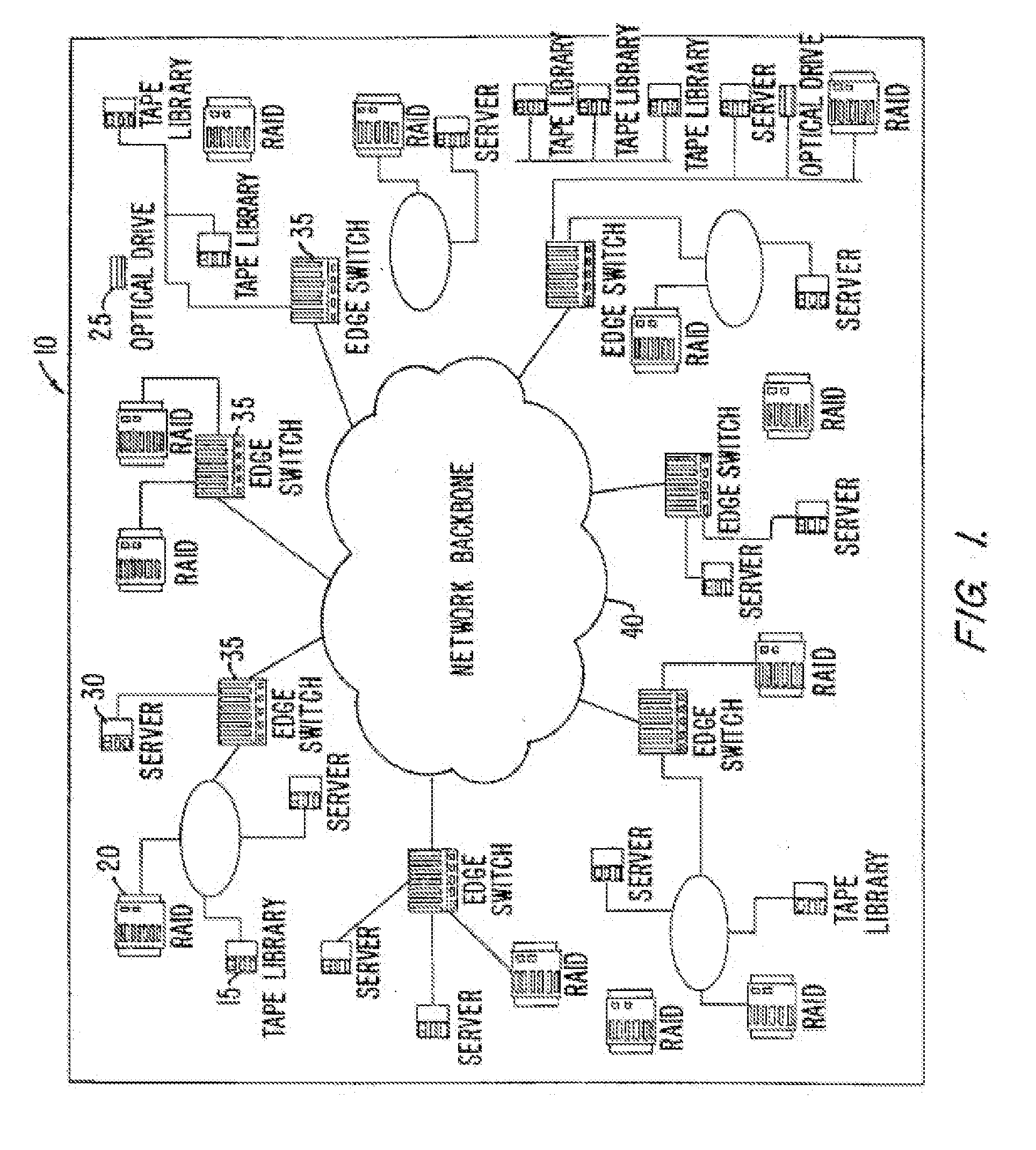
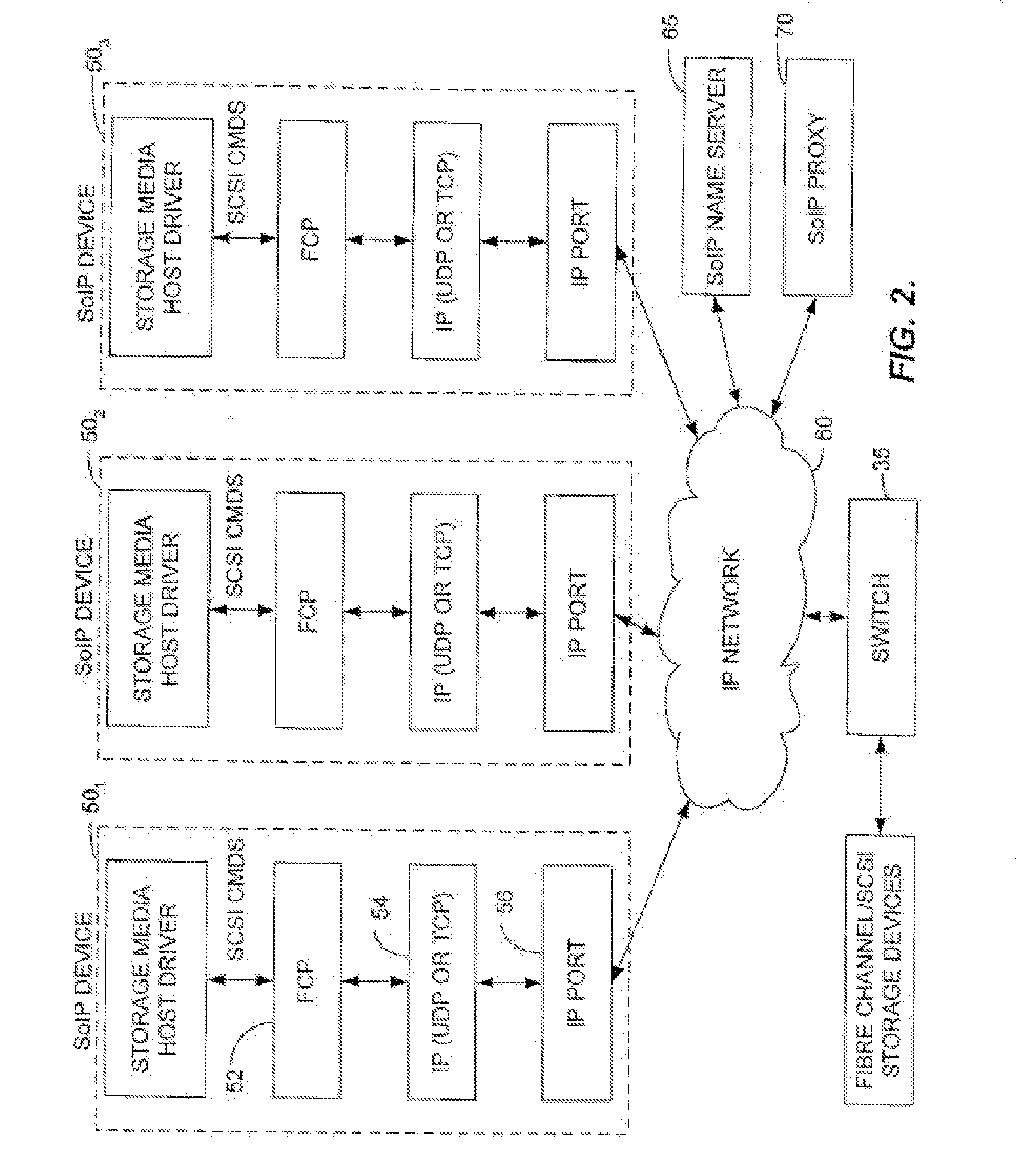
InactiveUS7197047B2Good conditionFast transferAnswer-back mechanismsTime-division multiplexSCSIFibre Channel
A method and apparatus for transferring data between IP devices (including, but not limited to, Gigabit Ethernet devices) and SCSI or Fibre Channel devices. The device interfaces may be either SCSI, Fibre Channel or IP interfaces such as Gigabit Ethernet. Data is switched between SCSI and IP, Fibre Channel and IP, or between SCSI and Fibre Channel. Data can also be switched from SCSI to SCSI, IP to IP and FC to FC. The port interfaces provide the conversion from the input frame format to an internal frame format, which can be routed within the apparatus. The amount of processing performed by each port interface is dependent on the interface type. The processing capabilities of the present invention permit rapid transfer of information packets between multiple interfaces at latency levels meeting the stringent requirements for storage protocols. The configuration control can be applied to each port on a switch and, in turn, each switch on the network, via an SNMP or Web-based interface, providing a flexible, programmable control for the apparatus.
Owner:AVAGO TECH INT SALES PTE LTD
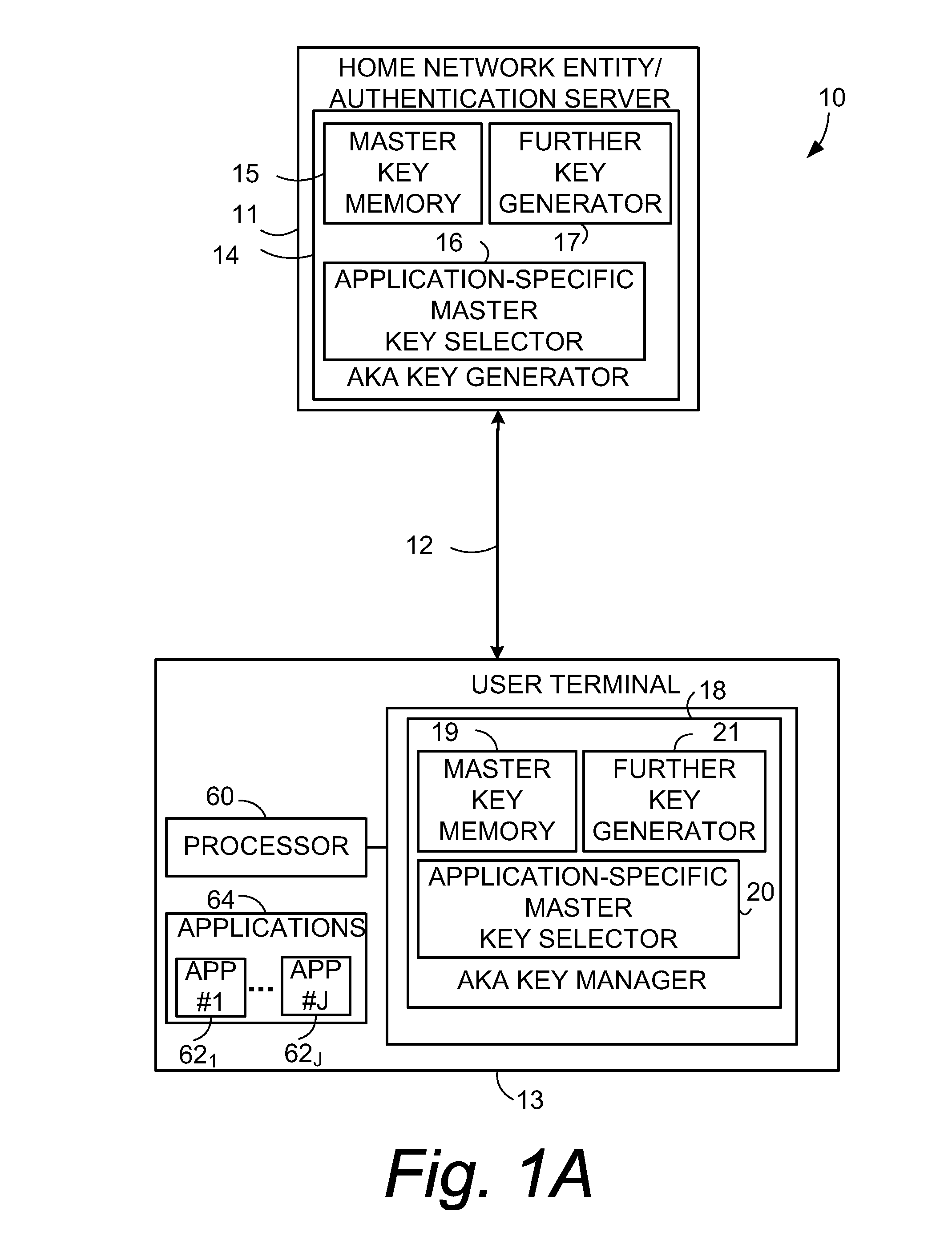
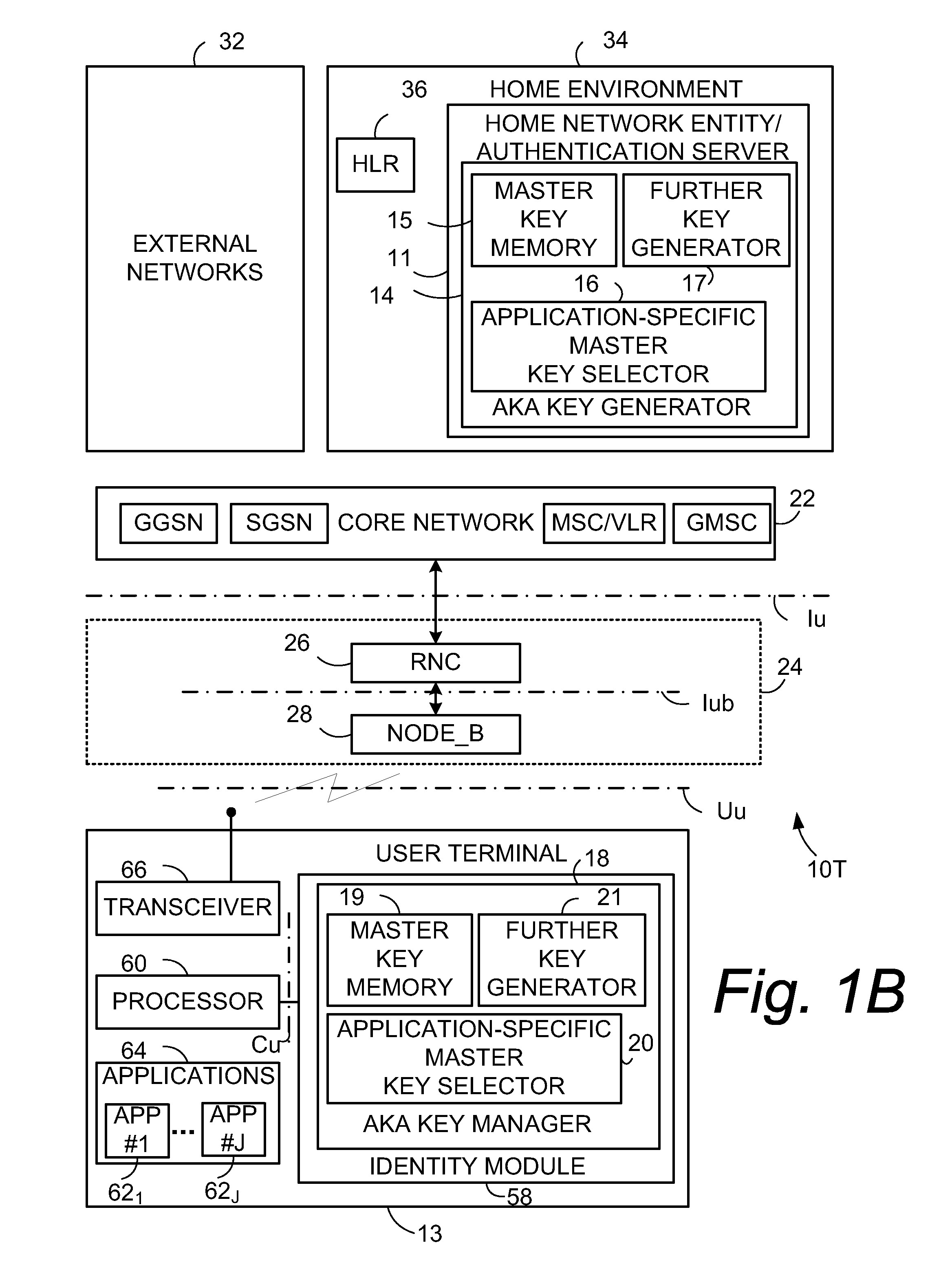
Application Specific Master Key Selection in Evolved Networks
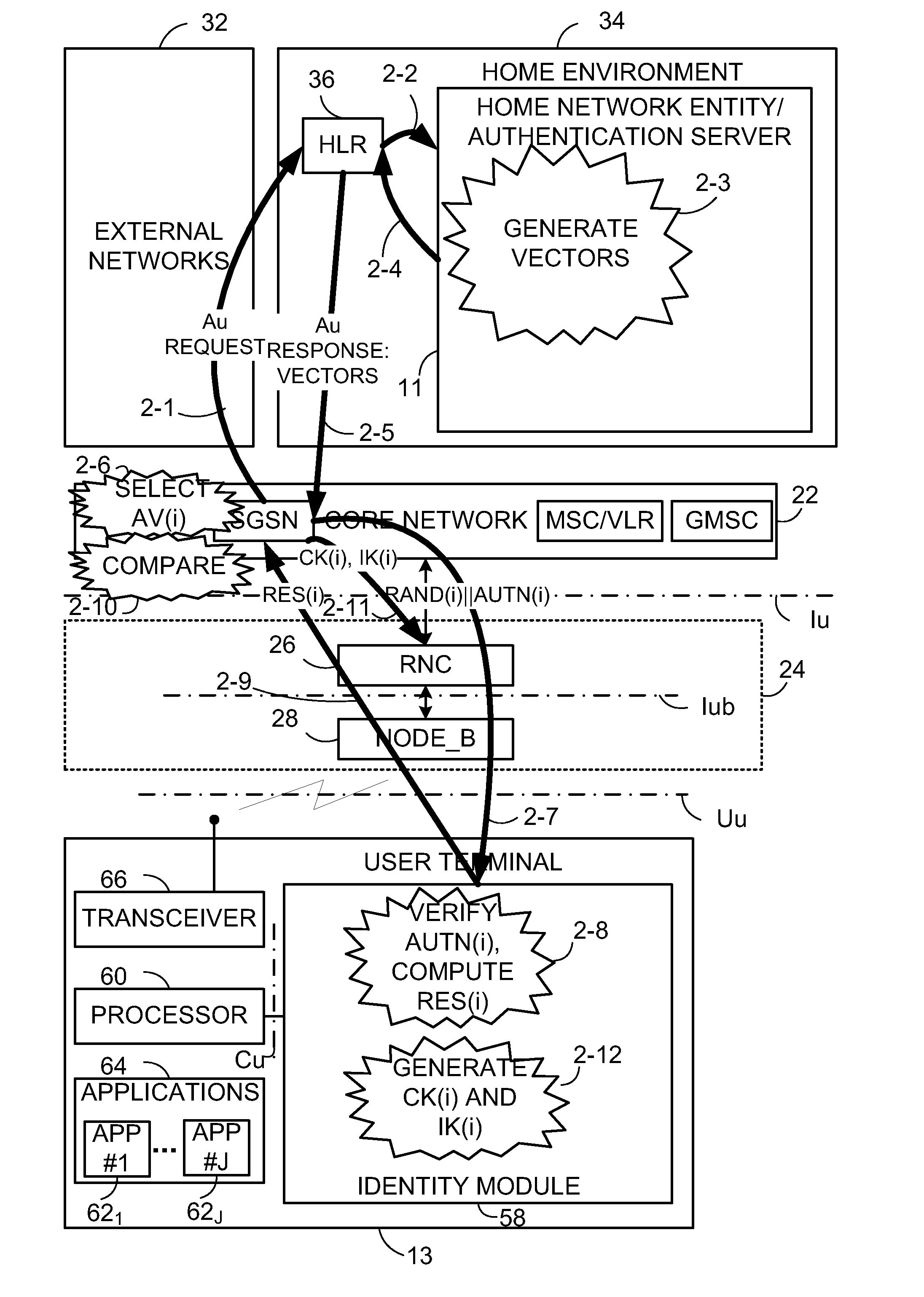
ActiveUS20110004758A1User identity/authority verificationAnswer-back mechanismsComputer terminalApplication specific
An authentication method comprises providing a set of N plural number of master keys both to a user terminal (13) and to home network entity (11) and, when performing an authentication key agreement (AKA) transaction for an application, selecting one of the N number of master keys to serve as a master key for use both at the user terminal and the home network entity for deriving further keys for the application. For example, when performing an authentication key agreement (AKA) transaction for a first application, the method involves randomly selecting one of the N number of master keys to serve as a first master key for use both at the user terminal and the home network entity for deriving further keys for the first application; but when 10 performing an authentication key agreement (AKA) transaction for another application, the method involves randomly selecting another one of the N number of master keys to serve as master key for use both at the user terminal and the home network entity for deriving further keys for the another application.
Owner:TELEFON AB LM ERICSSON (PUBL)
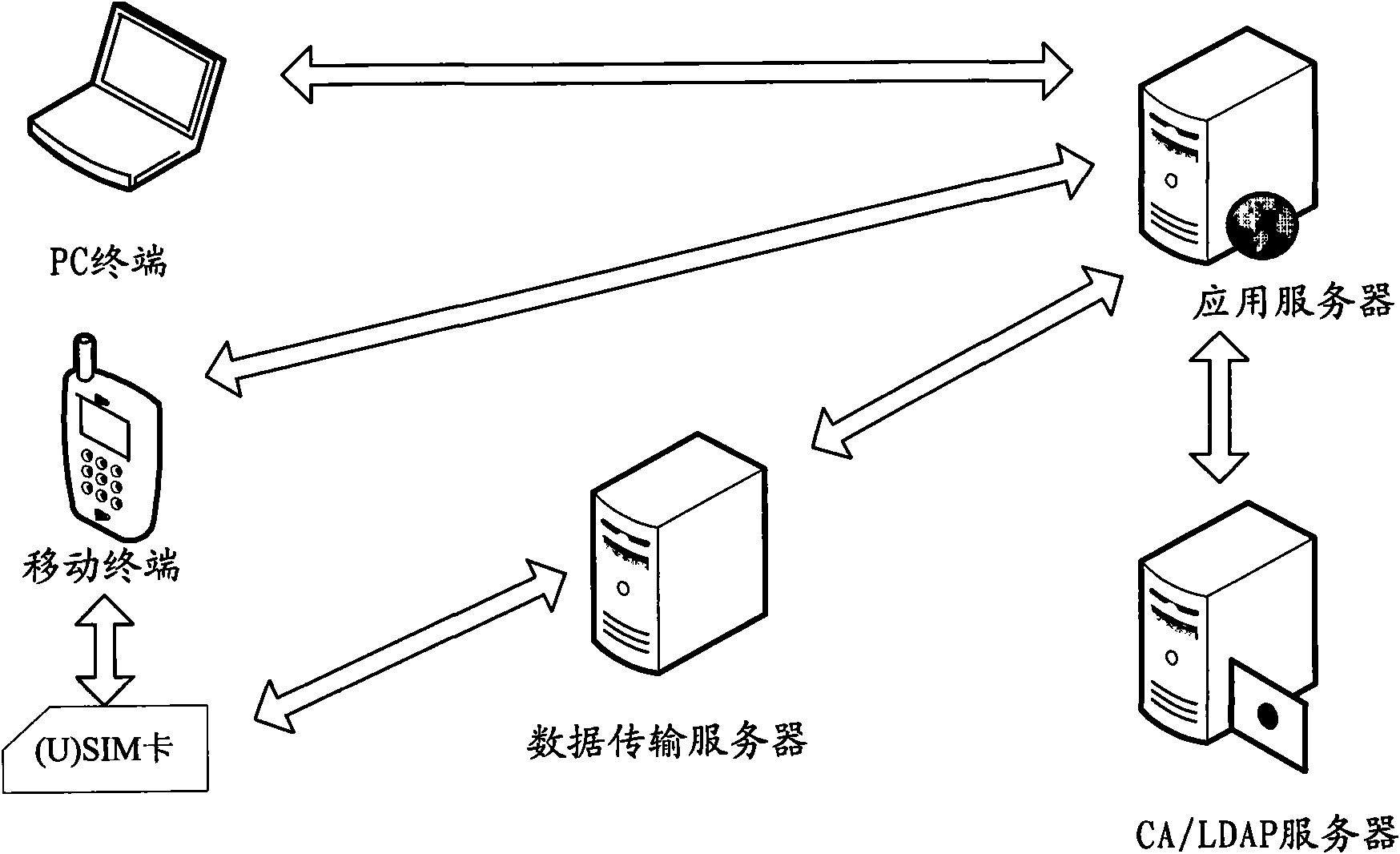
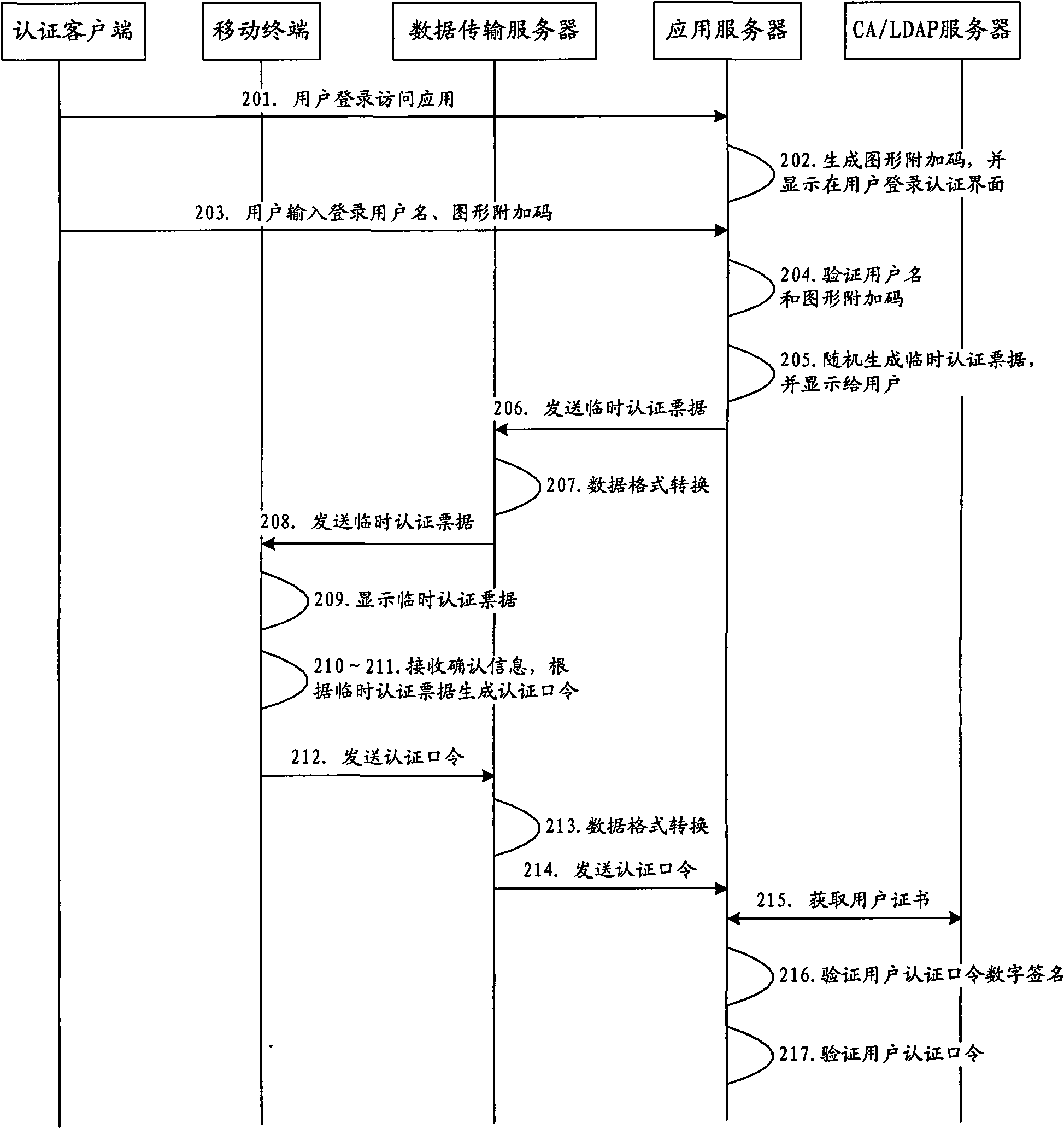
Identity authentication method based on mobile terminal as well as device and system thereof
ActiveCN101997824AAvoid lossPrevent theftUser identity/authority verificationInformation formatClient-sideAuthentication
The invention discloses an identity authentication method based on a mobile terminal as well as a device and a system thereof so as to solve the problems of poor security and limited use scene in the traditional identity authentication technology. The method comprises the following steps of: after a login identity submitted by a subscriber through an authentication client is verified to pass by a network side, generating first authentication data, providing the first authentication data to the authentication data client, and sending the first authentication data to the mobile terminal bound with the login identity; receiving second authentication data sent by the mobile terminal by the network side, wherein the mobile terminal generates and sends the second authentication data after confirming that the first authentication data received by the mobile terminal is consistent with that received by the authentication client; and verifying the second authentication data by the network side, and determining whether a subscriber identity is legal or not according to a verification result.
Owner:CHINA MOBILE COMM GRP CO LTD
System and method for distributed multicast routing
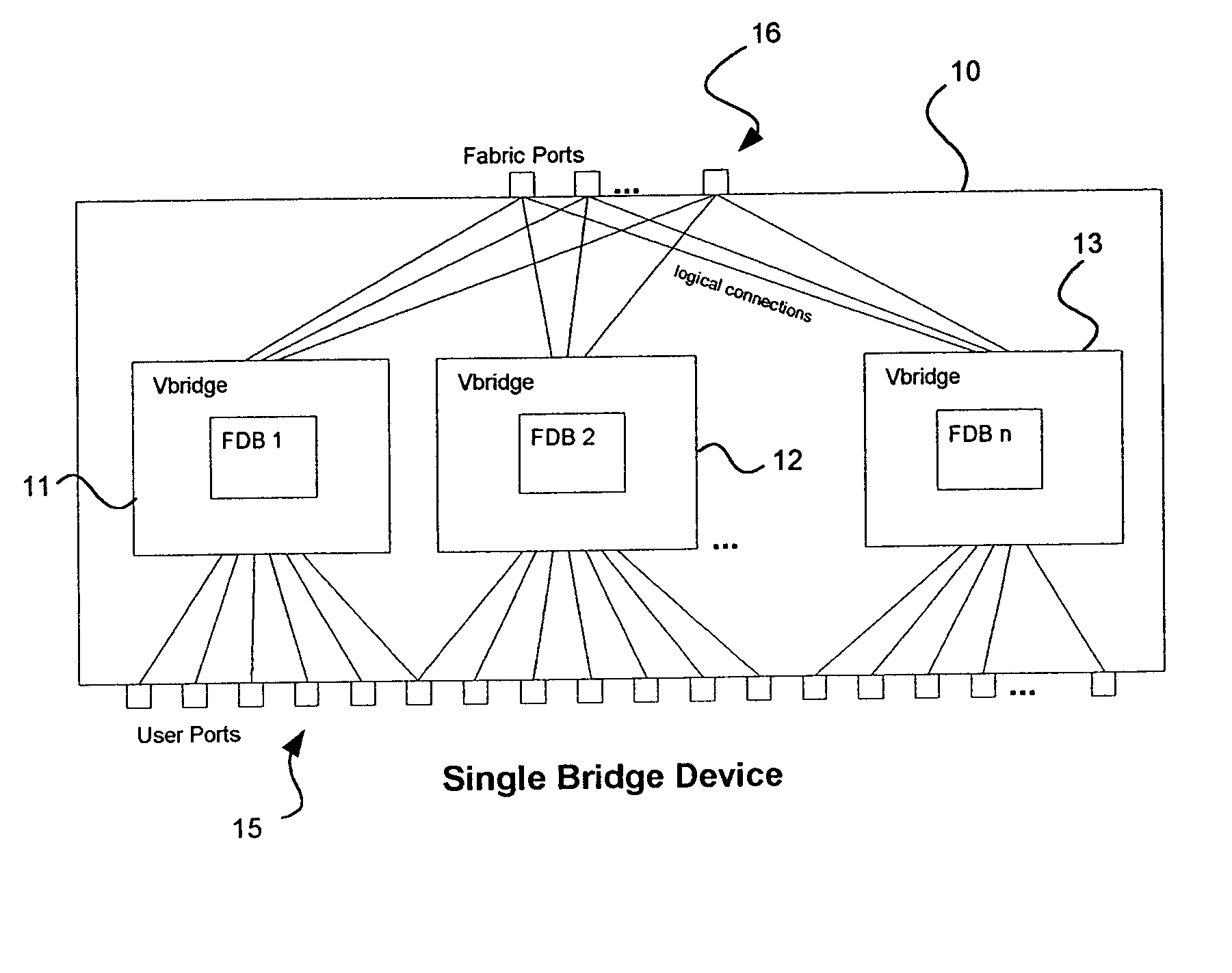
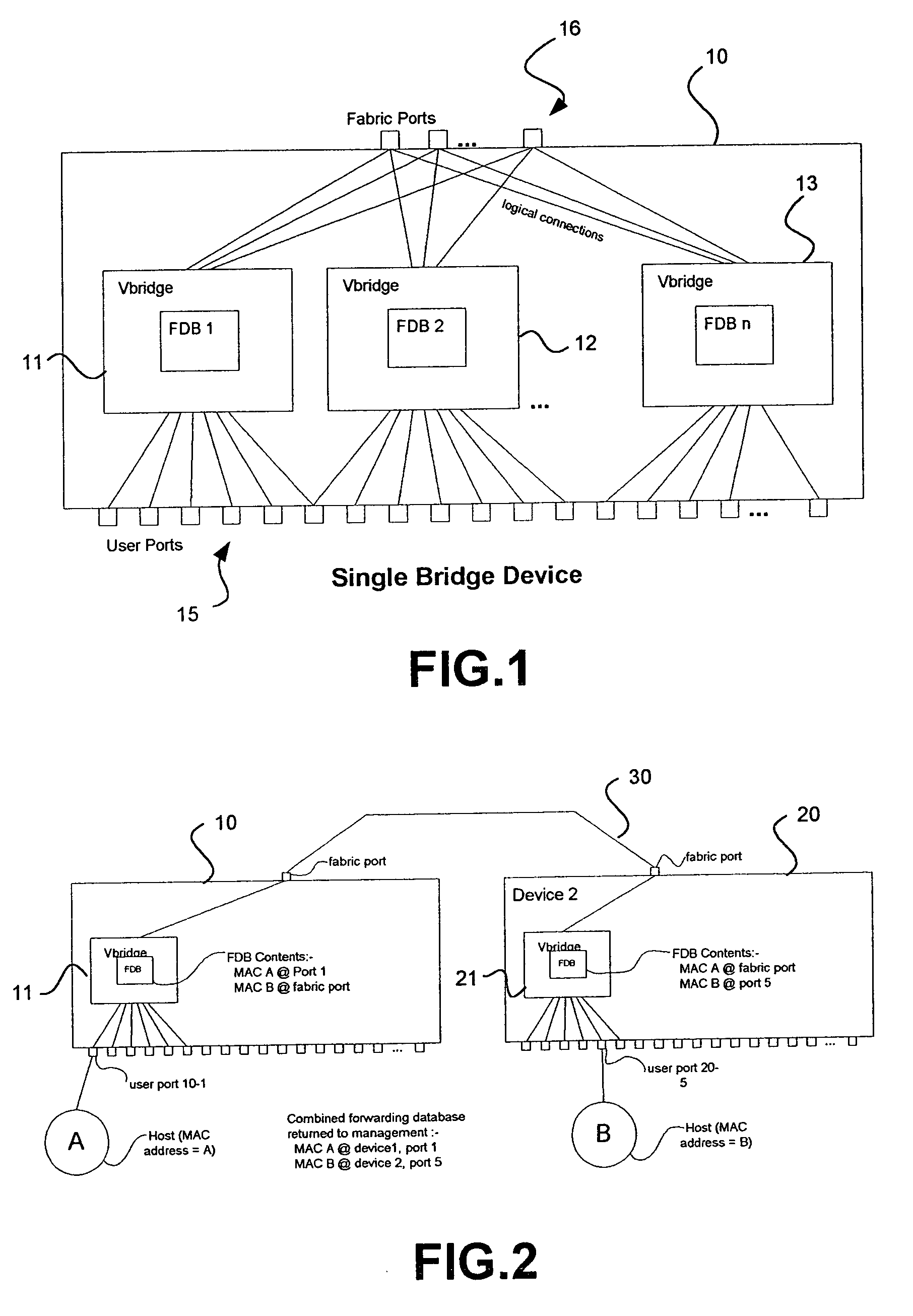
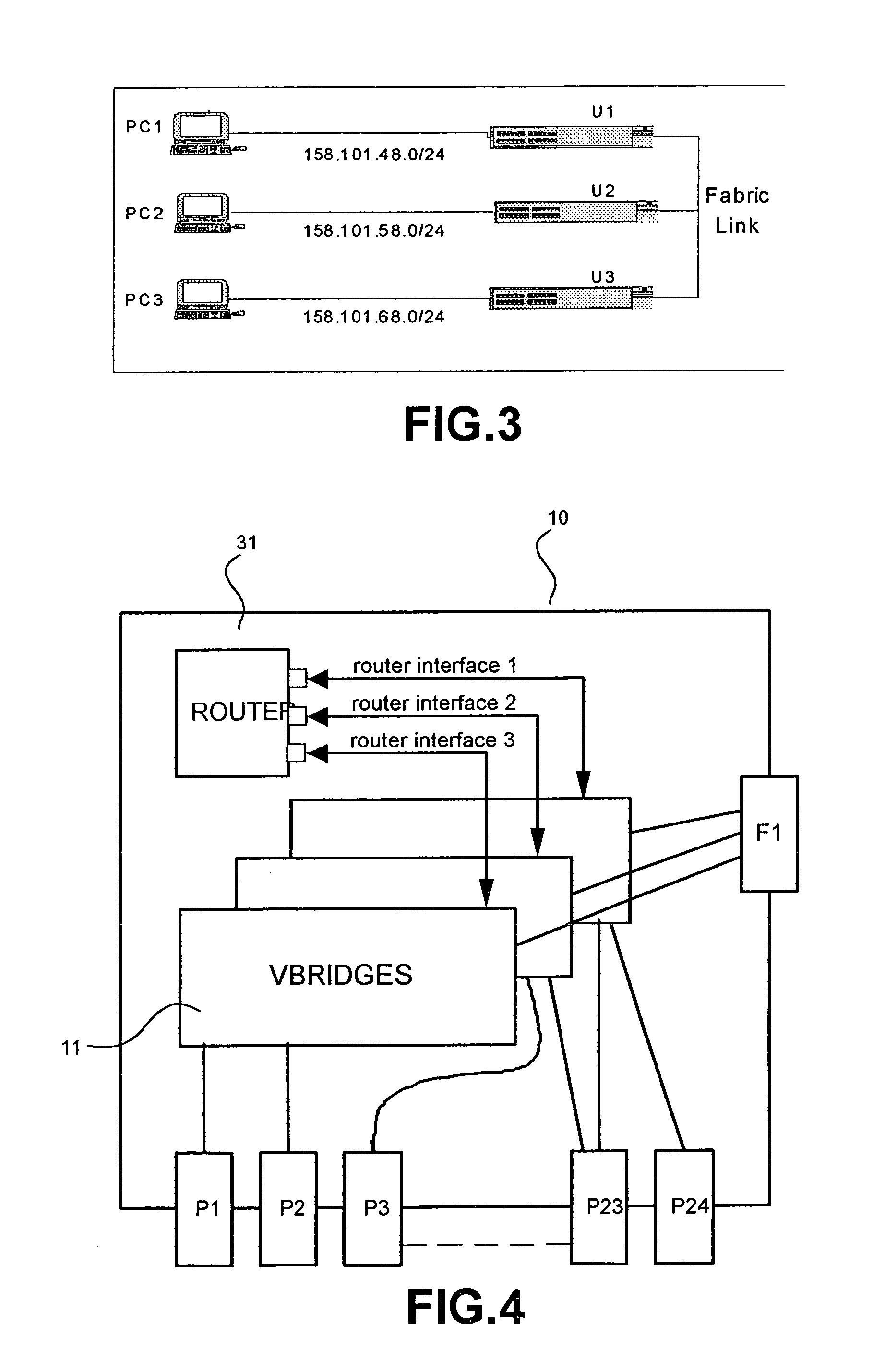
InactiveUS7317722B2Special service provision for substationAnswer-back mechanismsNetwork packetMulticast packets
A distributed router composed of individual units connected by links in a routing fabric which appears to be a single network entity routes multicast packets by bridging to the final unit in the fabric. At the final unit the packet is replicated as necessary and routed. The scheme avoids multiple transmission of the same packet across the fabric.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Monitoring a local area network
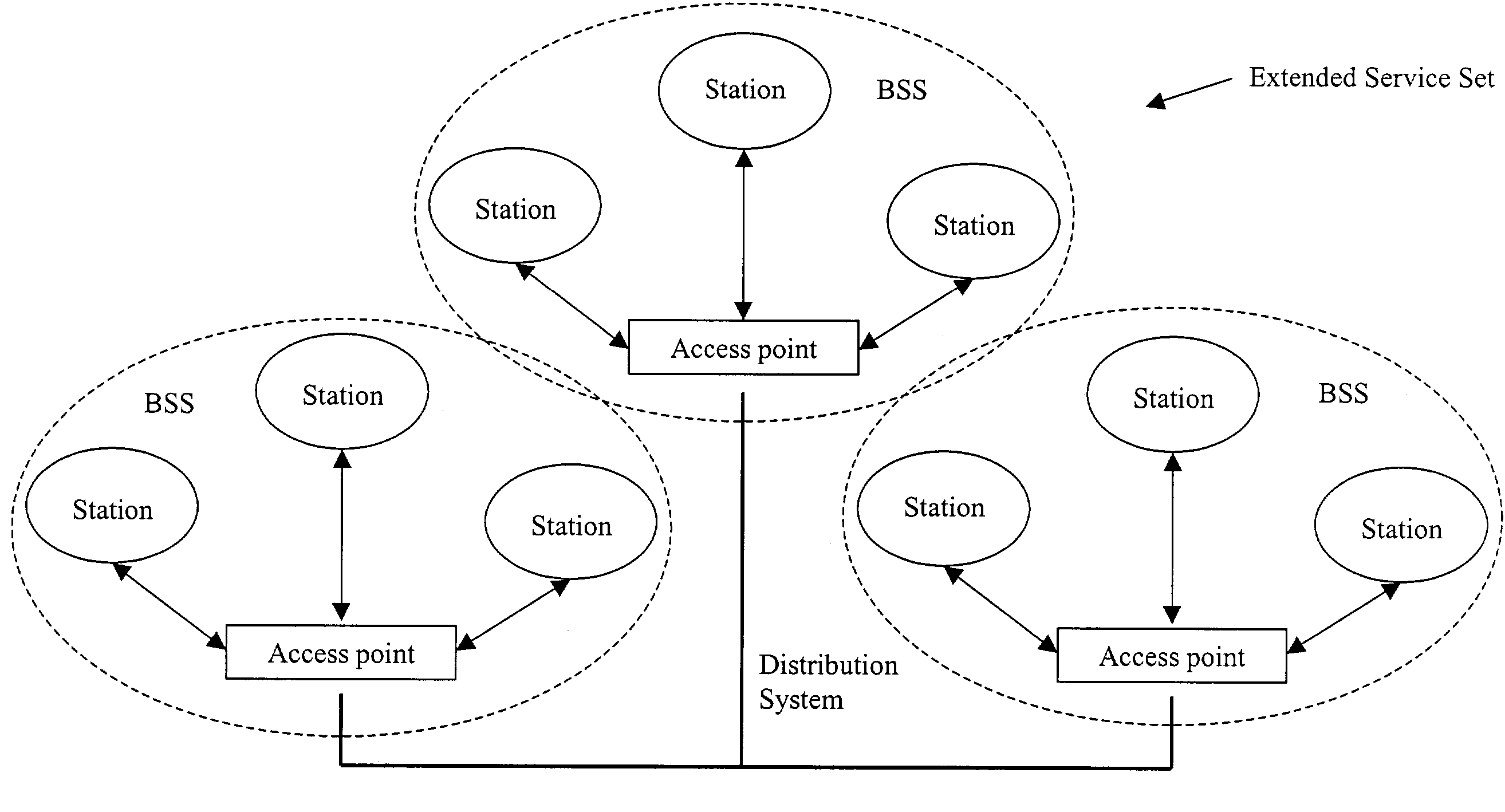
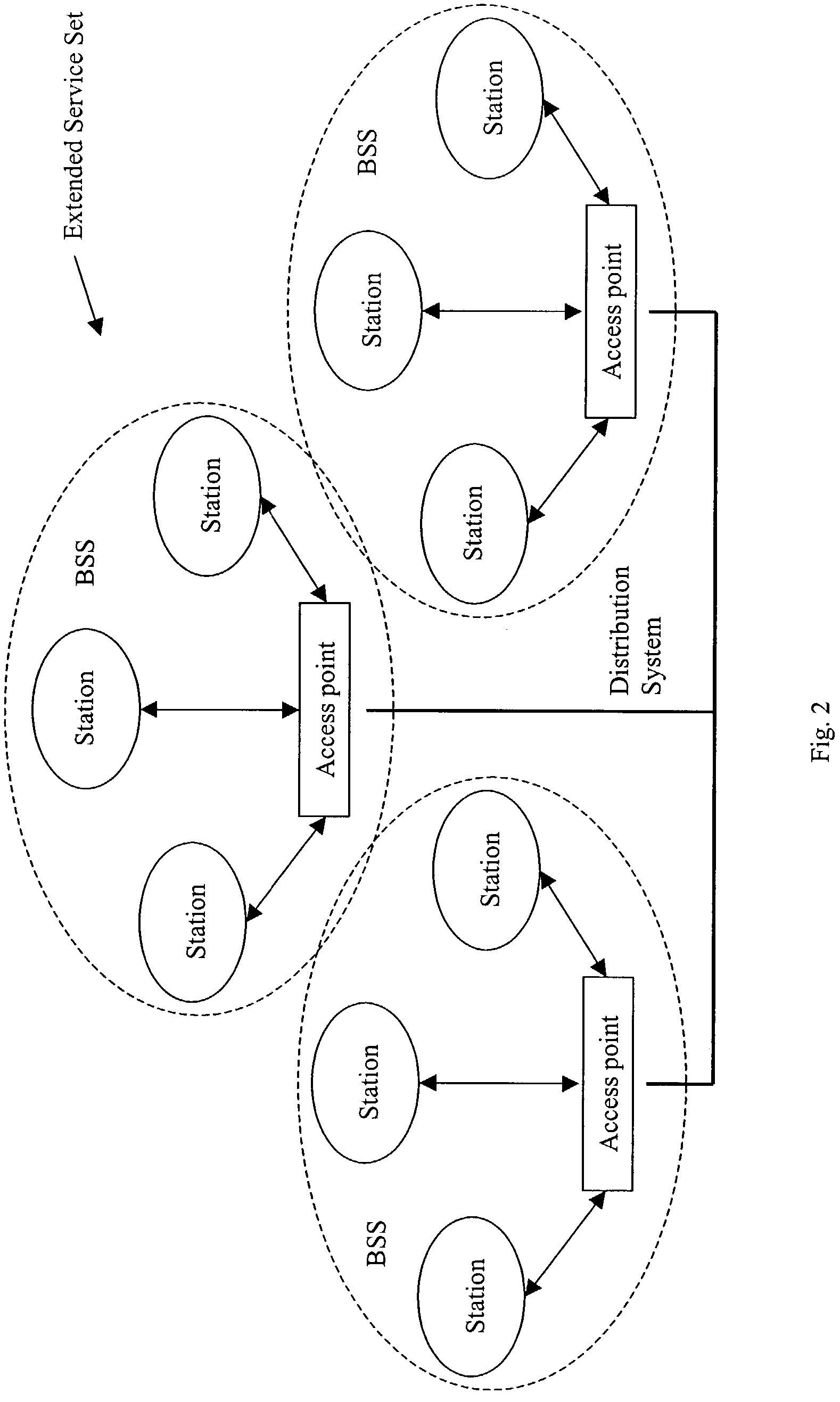
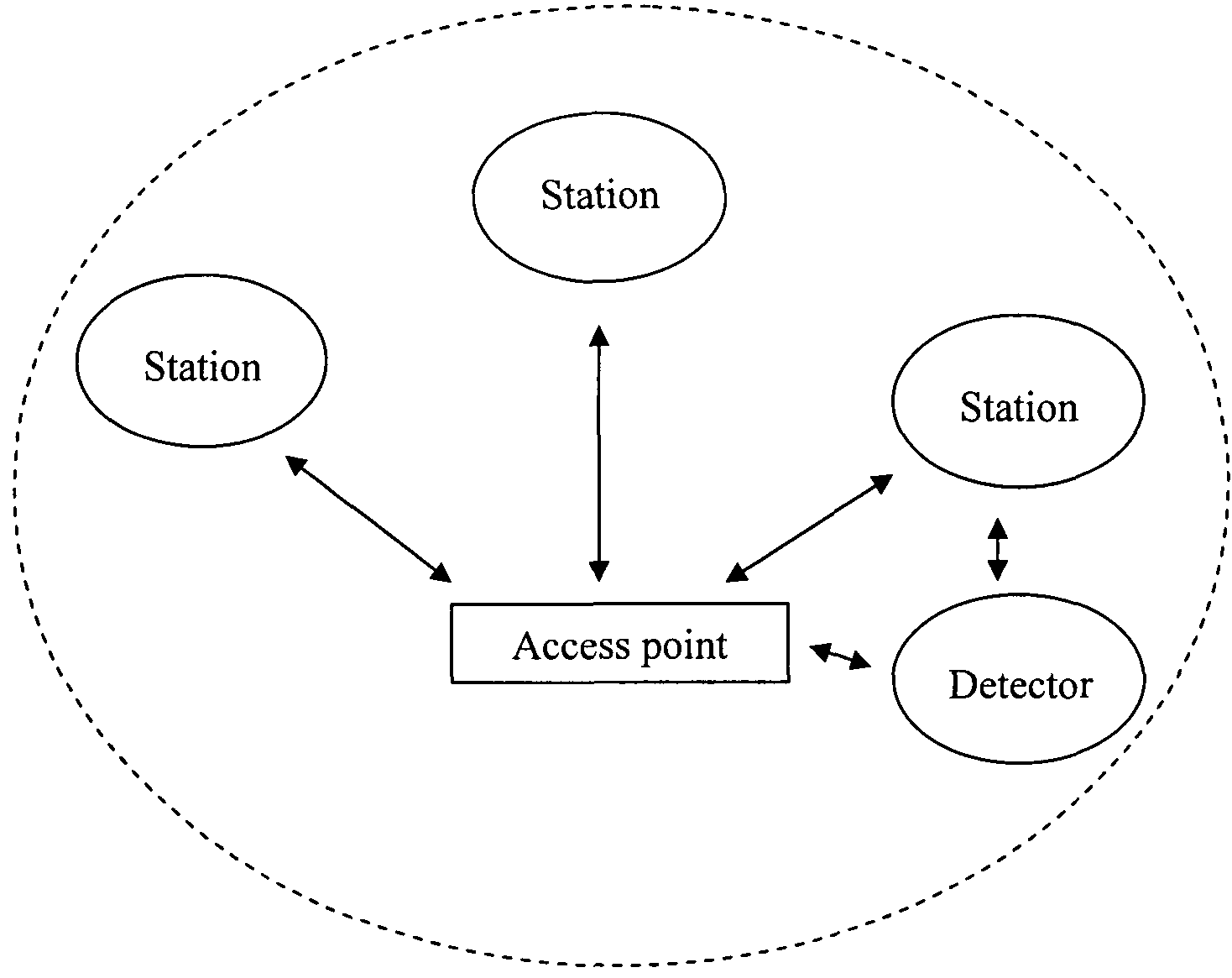
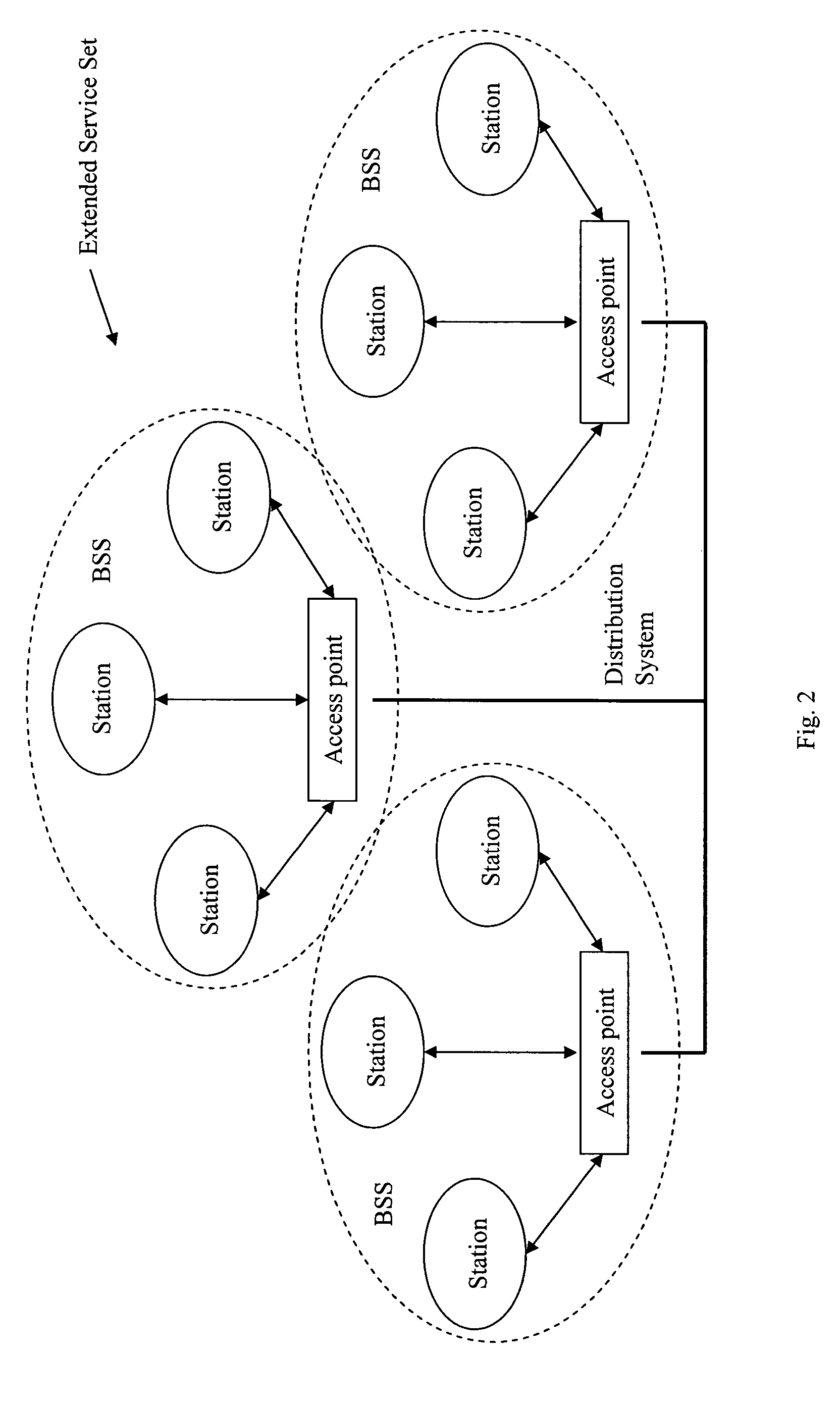
A wireless local area network (WLAN) is monitored by receiving transmissions exchanged between one or more stations and an access point (AP) in the WLAN using a detector located in the WLAN. A database is compiled based on the received transmissions. The received transmissions are analyzed to determine the state of a station. The compiled database and the determined state of the station are used to diagnose connectivity problems of the station.
Owner:AIRMAGNET
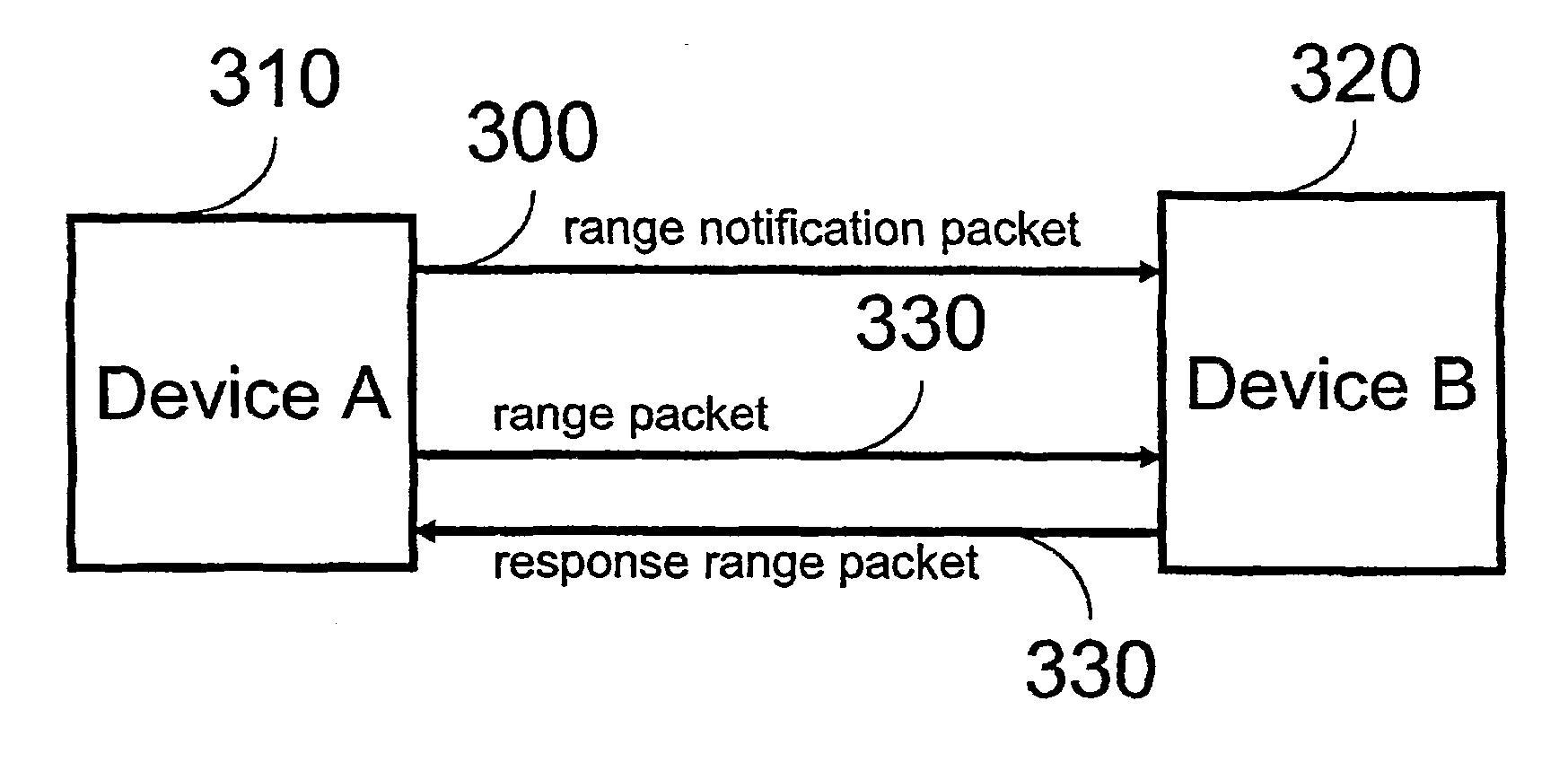
Device, method and protocol for private UWB ranging
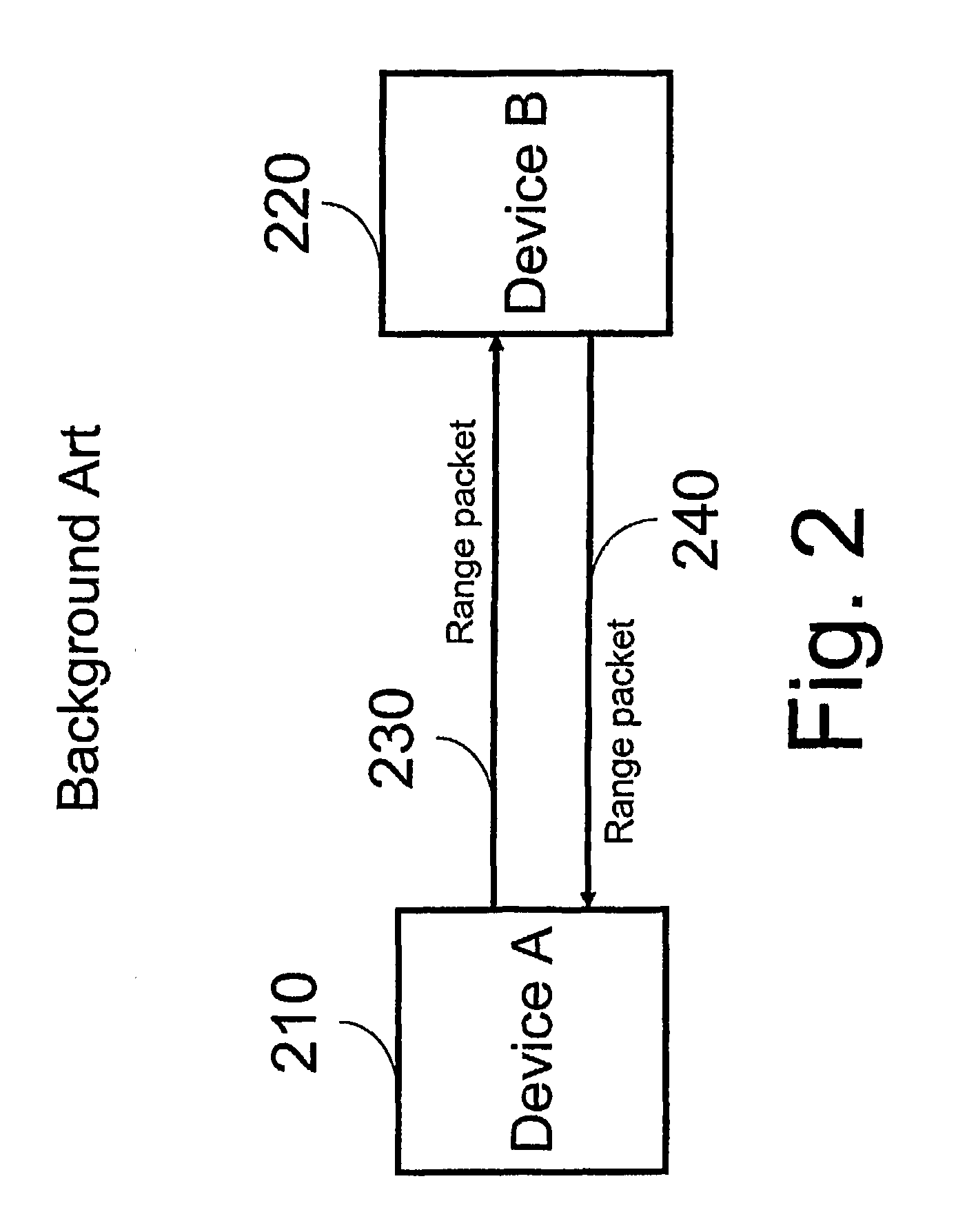
An apparatus, system, method and computer program product for secure ranging between at least two devices in radio communications with each other. In particular, an apparatus, system, method and computer program product for secure ranging between at least two devices communicating via ultra wideband (UWB) protocols. Either ternary-IR or time-hope-IR sequences are used for ranging and security. A first device transmits a range packet. A second device responds to the range packet after a delay time known only to the first and second devices. The delay time can be selected randomly by either to the first device or the second device and made known to the other device in an encrypted notification packet.
Owner:MITSUBISHI ELECTRIC RES LAB INC
Method and apparatus for accessing communication data relevant to a target entity identified by a number string
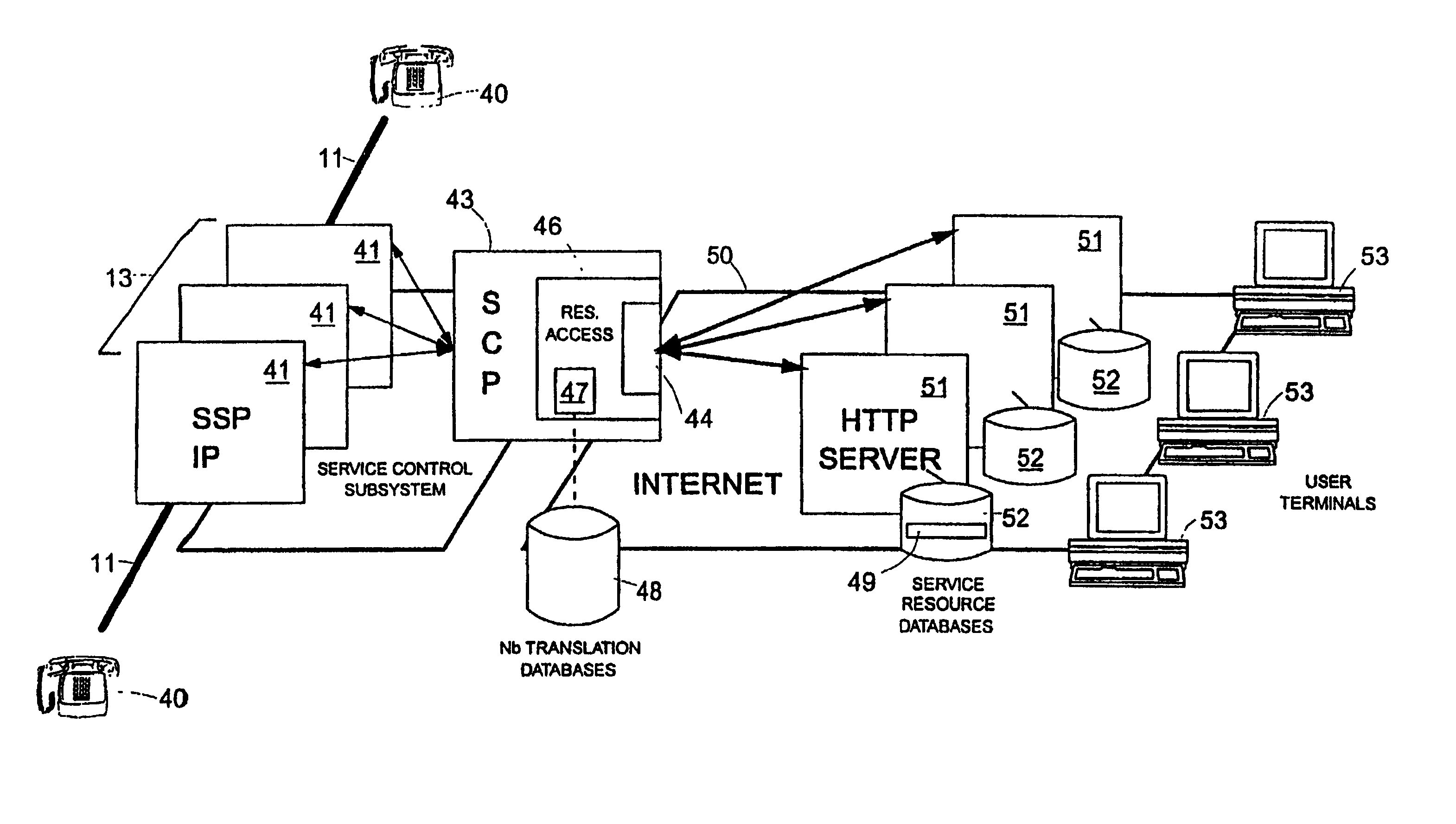
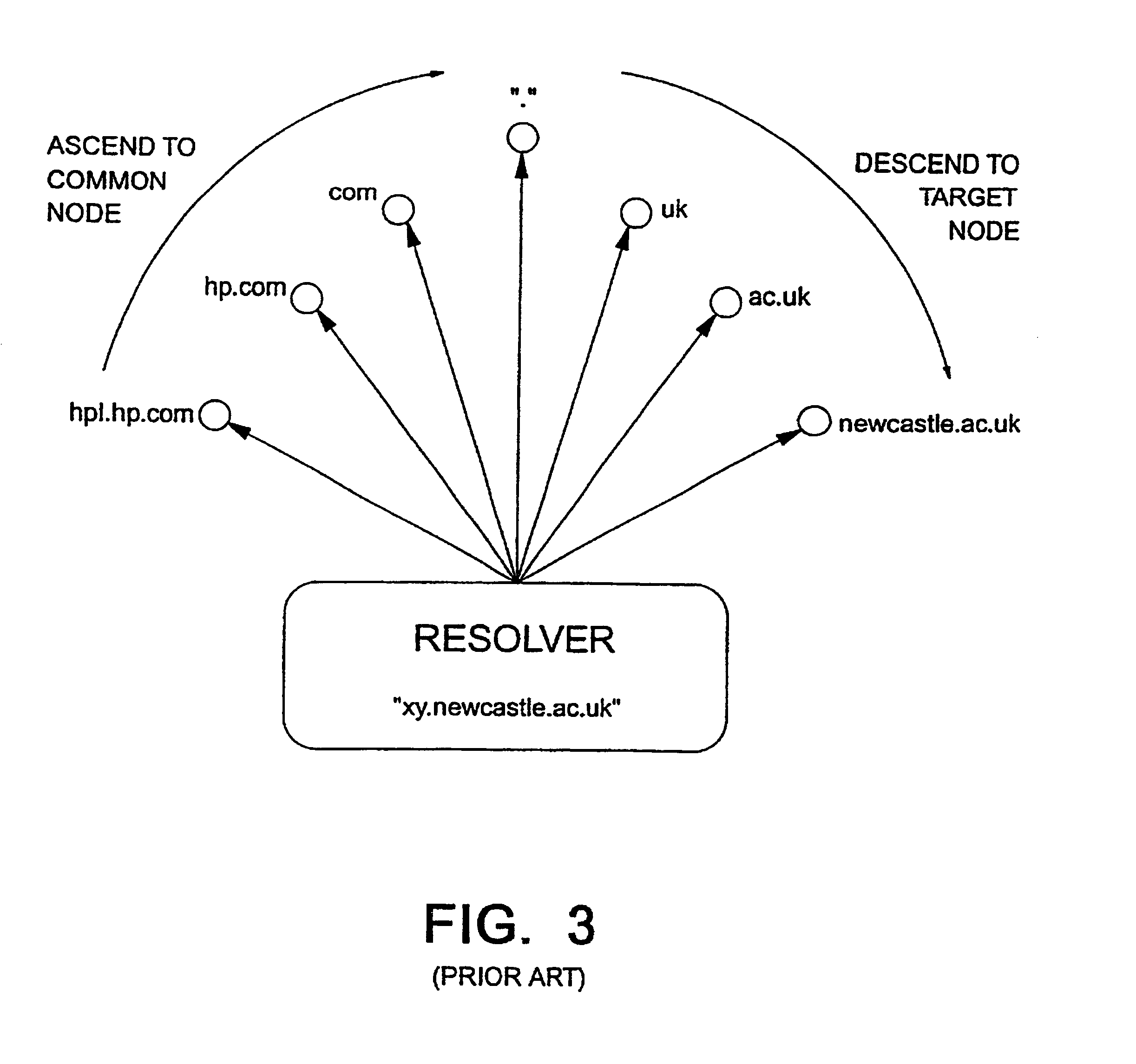
InactiveUS7012916B2Simple chaining together of the InternetMultiplex system selection arrangementsTelephone data network interconnectionsThe InternetCall setup
Service resource items (49) for use in call setup in a telephone system are held on servers (58) that are connected to a computer network which is logically distinct from the telephone system infrastructure; this computer network may, for example, make use of the Internet. Each service resource item (49) is locatable on the network at a corresponding URI and is associated with a particular telephone number. A mapping is provided between telephone numbers and the URIs of associated service resource items. When it is desired to access a service resource item (49) associated with a particular telephone number, this mapping is used to retrieve the corresponding URI (step 55) which is then used to access the desired service resource item (56, 57, 59).
Owner:COMCAST IP HLDG I
Method and Apparatus for Transferring Data Between IP Network Devices and SCSI and Fibre Channel Devices Over an IP Network
InactiveUS20070286233A1Good conditionFast transferAnswer-back mechanismsTime-division multiplexSCSIFibre Channel
A method and apparatus for transferring data between IP devices (including, but not limited to, Gigabit Ethernet devices) and SCSI or Fibre Channel devices. The device interfaces may be either SCSI, Fibre Channel or IP interfaces such as Gigabit Ethernet. Data is switched between SCSI and IP, Fibre Channel and IP, or between SCSI and Fibre Channel. Data can also be switched from SCSI to SCSI, IP to IP and FC to FC. The port interfaces provide the conversion from the input frame format to an internal frame format, which can be routed within the apparatus. The amount of processing performed by each port interface is dependent on the interface type. The processing capabilities of the present invention permit rapid transfer of information packets between multiple interfaces at latency levels meeting the stringent requirements for storage protocols. The configuration control can be applied to each port on a switch and, in turn, each switch on the network, via an SNMP or Web-based interface, providing a flexible, programmable control for the apparatus.
Owner:NISHAN SYST
Fusion method between radio LAN and mobile network
InactiveCN1453953AUnified authenticationUnauthorised/fraudulent call preventionUser identity/authority verificationNetwork terminationTerminal equipment
The method for mixing WLAN and mobile communication network together with each other through internet gateway first, then an access to SIM card is made by network terminal equipment through card reading device of SIM card. The network is switched in through WLAN card to share the signal contract information is the user in the mobile network and the signal contract information in the mobile network is used to carry on power identification through internet gateway. After the network is switched in, the service transmission is carried on by the network terminal equipment through internet gatewaybetween WLAN and the mobile network as well as charge information is sent through internet gateway to charge gateway of the mobile network. The resources of both networks can be shared by applying the abovesaid method.
Owner:BEIJING HUAWEI DIGITAL TECH
Asynchronous transfer mode (ATM) switch and method for switching ATM traffic
InactiveUS7636358B1Low costReduce processing requirementsAnswer-back mechanismsTime-division multiplexComputer networkAsynchronous Transfer Mode
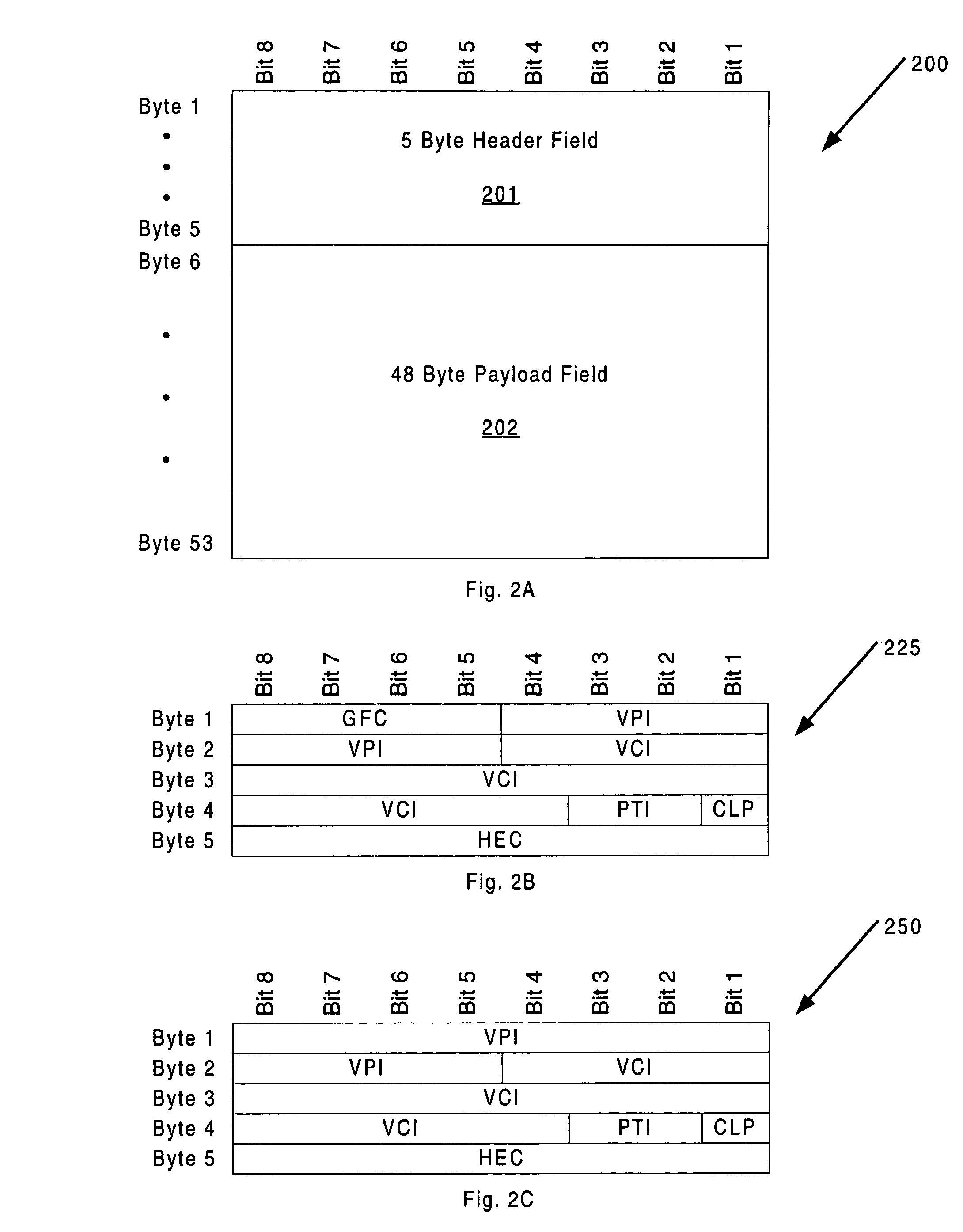
An asynchronous transfer mode (ATM) switch includes a switch memory having a plurality of discrete queues. A queue is dedicated to a connection in which a traffic stream is transmitted in cells and an inverse multiplex ATM (IMA) format. A switch controller is operable to receive a plurality of cells, to identify cells for the connection, to queue cells for the connection in the queue based on order information received with the cells, to reconstitute from the queue the traffic stream, and to switch the traffic stream and the ATM cells.
Owner:CISCO TECH INC
Method and apparatus for accelerated link setup between STA and access point of IEEE802.11 network
A methods and an apparatus may be used for accelerated link setup. The method may include a station (STA) and acquiring information about an access point of an institute of electrical and electronics engineers (IEEE) 802.11 network in advance through a previously connected IEEE 802.11 interface and / or an interface other than the IEEE 802.11 network. The STA may use the acquired information during a link setup procedure between the STA and the access point. The information may include a suggestion for a specific procedure to complete the link setup procedure between the STA and the access point.
Owner:INTERDIGITAL PATENT HLDG INC
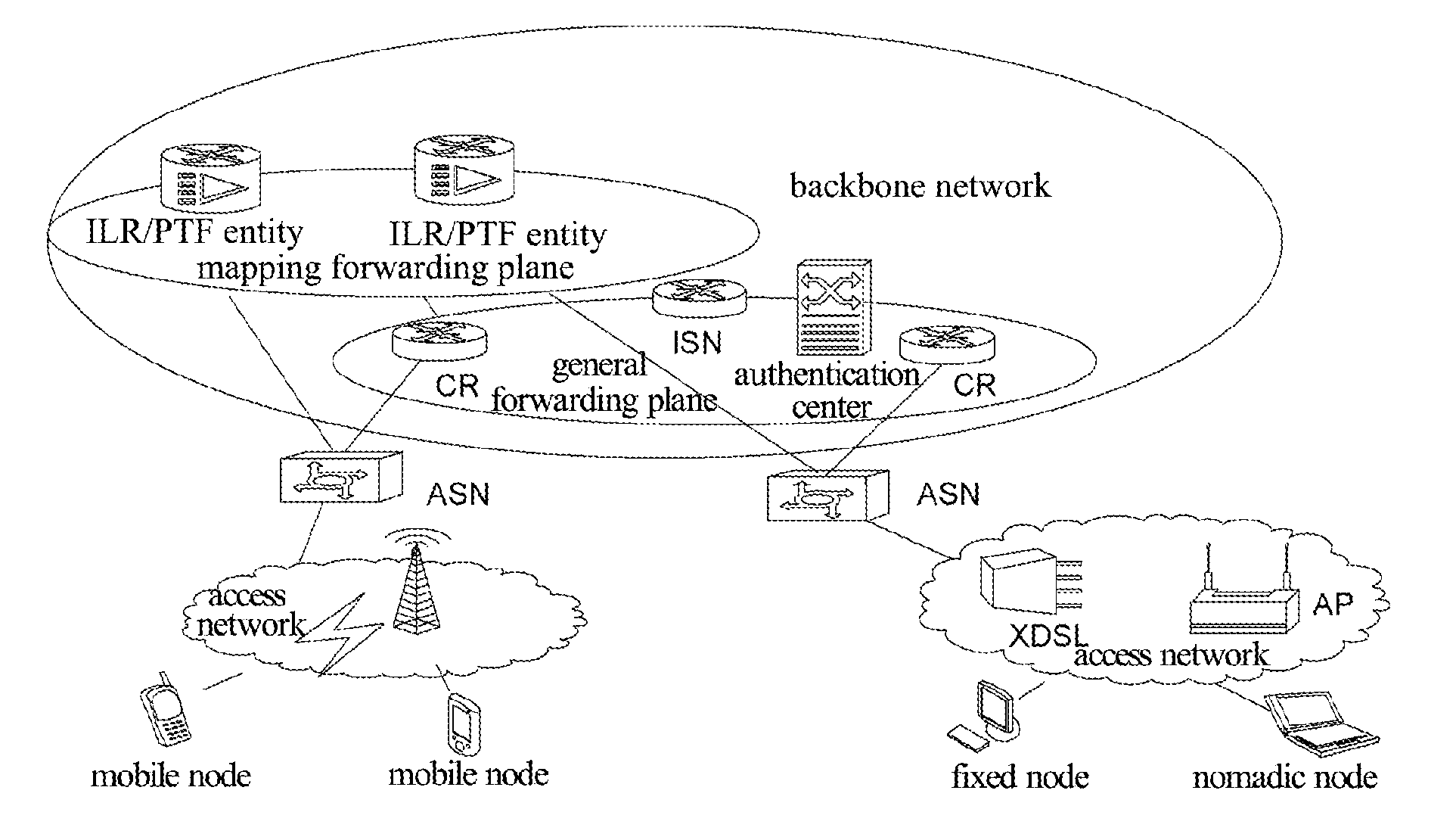
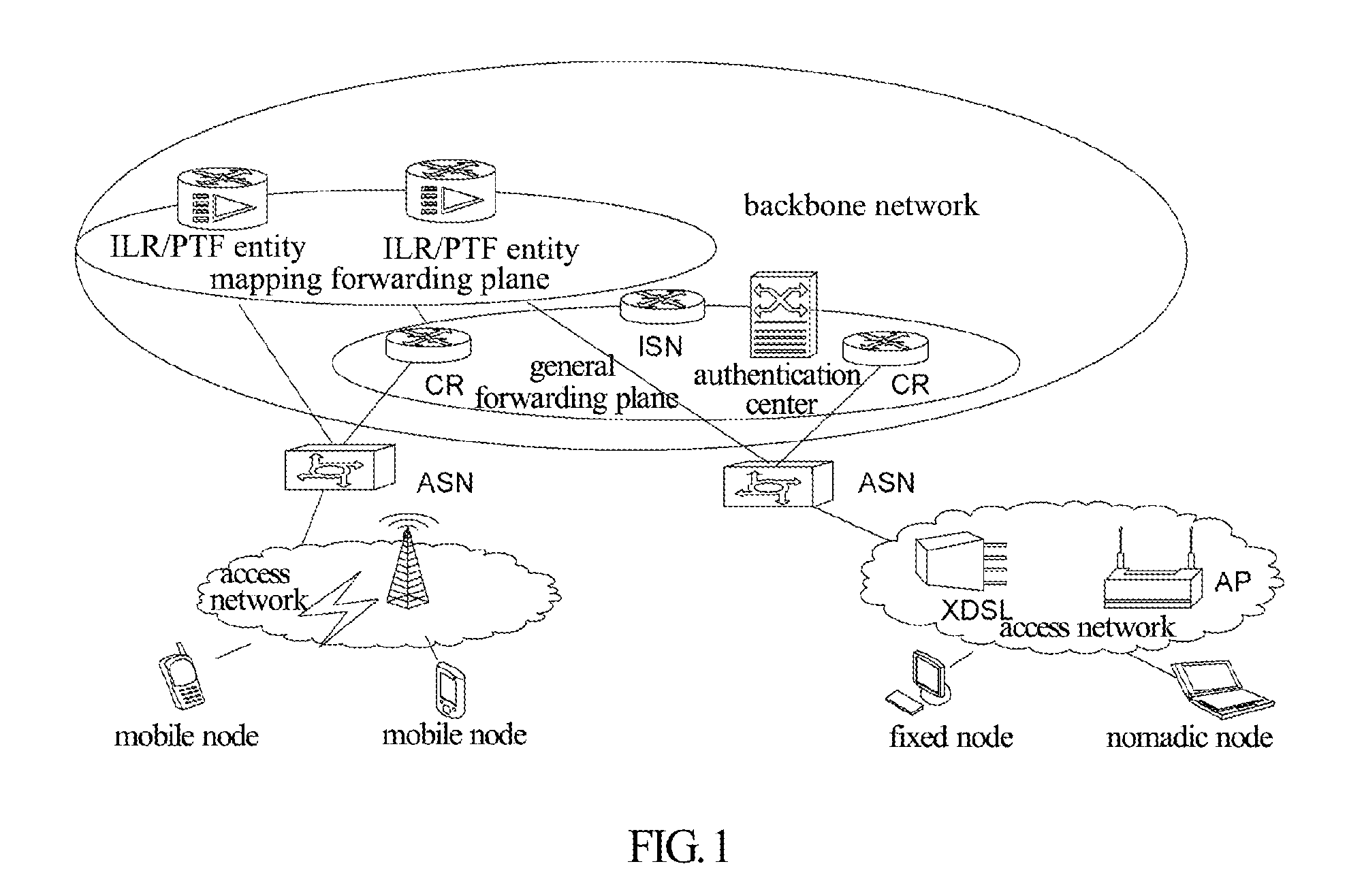
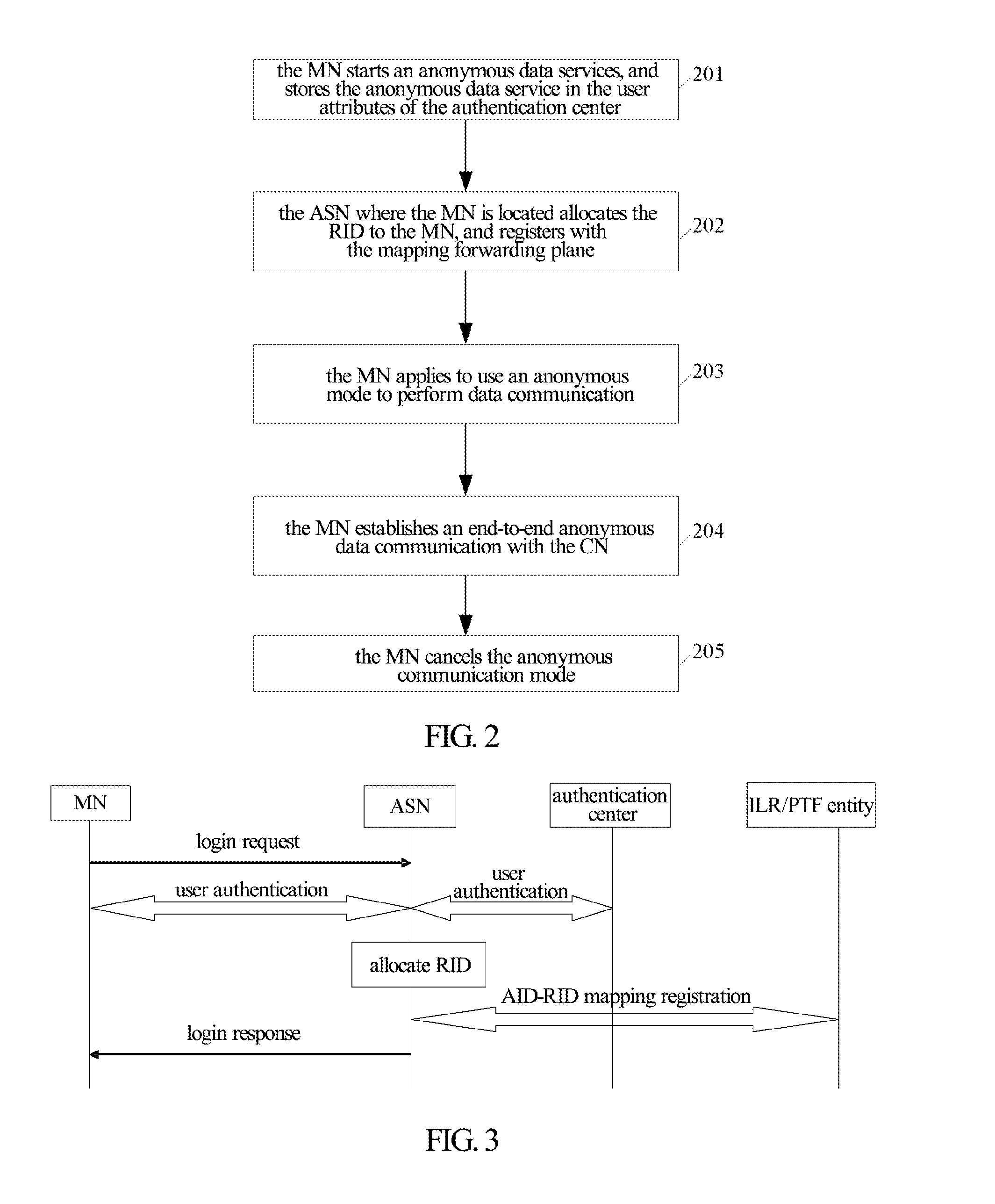
Method for anonymous communication, method for registration, method and system for transmitting and receiving information
ActiveUS20120203856A1Meet the requirementsAnswer-back mechanismsMultiple digital computer combinationsComputer scienceData messages
A method and a system for anonymous communication are disclosed in the present invention, which are applied in an architecture network with Identification (ID) identifier and locator separation. The method includes: after receiving an anonymous communication request initiated by a terminal, the network allocating an anonymous ID identifier to the terminal, and recording a state of the terminal as an anonymous communication state; when the terminal is in the anonymous communication state, an access gateway device where the terminal is located replacing a source access identifier in data message transmitted by the terminal with the anonymous ID identifier while receiving the data message; and replacing an anonymous ID identifier in data message transmitted to the terminal with the access identifier of the terminal while receiving the data message transmitted to the terminal.
Owner:ZTE CORP
Identity authentication method, device and system
ActiveCN105262779AImprove transfer safetyAvoid Illegal Value TransfersAnswer-back mechanismsDigital data authenticationComputer hardwareDigital fingerprint
The invention relates to an identity authentication method, a device and a system. The method comprises steps: a virtual resource data processing request sent by a mobile terminal is acquired, the virtual resource data processing request carries a pre-stored digital fingerprint, and the digital fingerprint is generated by using equipment information and user information; according to a prebuilt user numerical value transfer behavior model, virtual resource data processing authentication is carried out on the virtual resource data processing request; after the virtual resource data processing authentication is passed, according to the digital fingerprint, a numerical value transfer token is generated, and the numerical value transfer token is returned to the mobile terminal; a numerical value transfer request sent by the mobile terminal is received, and the numerical value transfer request carries the numerical value transfer token; and whether the numerical value transfer token is legal is checked, if yes, the identity authentication is passed, and if not, the identity authentication is not passed. Numerical value transfer safety can be improved, and numerical value transfer convenience is ensured.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
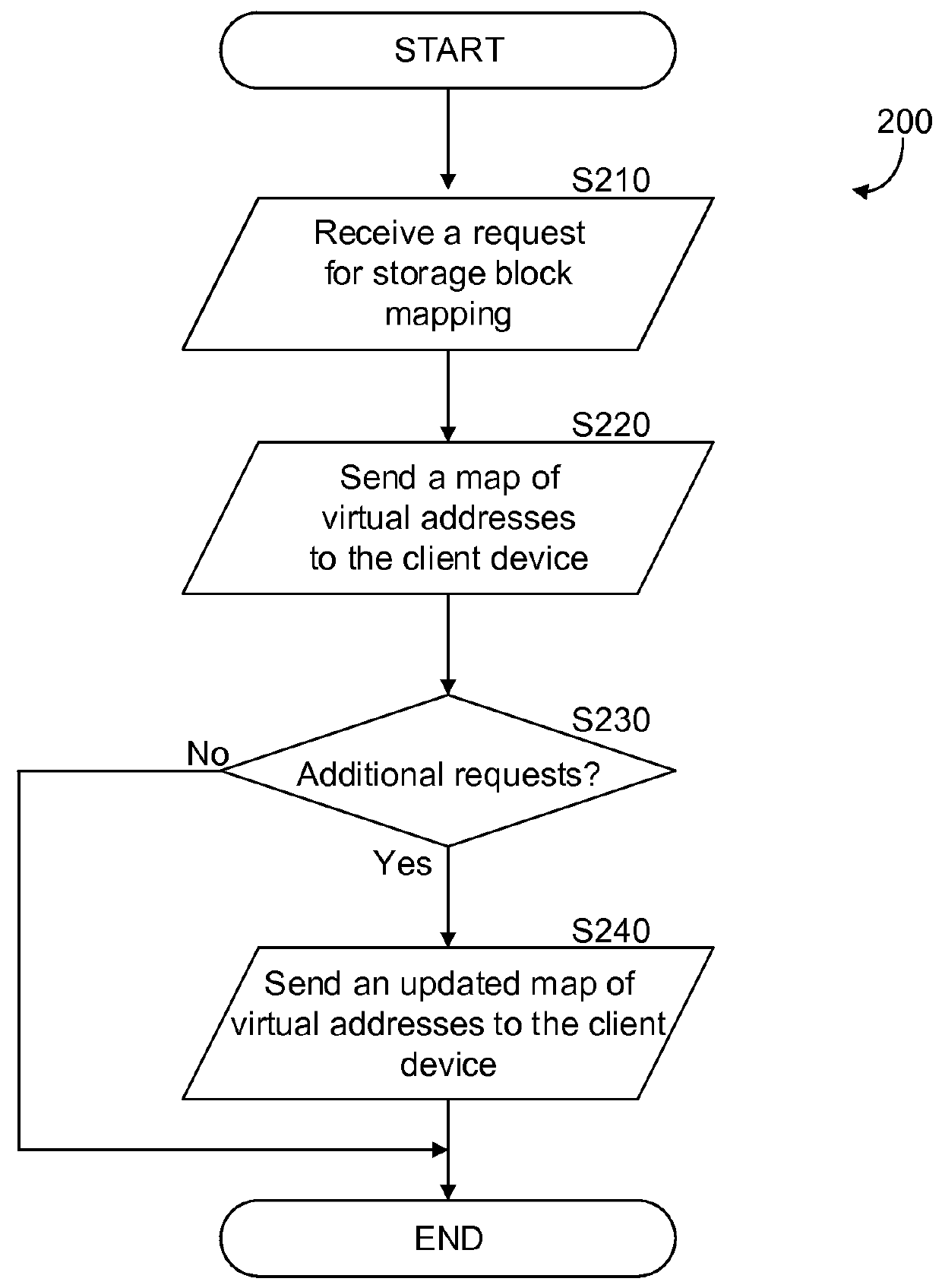
Method for providing a client device access to a plurality of remote storage devices
ActiveUS20160036913A1Input/output to record carriersMemory adressing/allocation/relocationClient-sideVirtual address space
A controller system allows direct access to a client device accessing remote data storage devices communicatively connected to the controller. A virtual block metadata (VBM) is generated by the controller system, the VBM including a plurality of maps. Each map includes a plurality of virtual addresses, each virtual address mapped to a physical address, each physical address on a remote storage device of the plurality of storage devices. The client device is sent a portion of the VBM, the portion including the map of the virtual addresses sent to the client. The controller receives, over a first network interface, read / write instructions from the client device for the a physical address corresponding to the virtual address allocated to the client device.
Owner:NVIDIA CORP
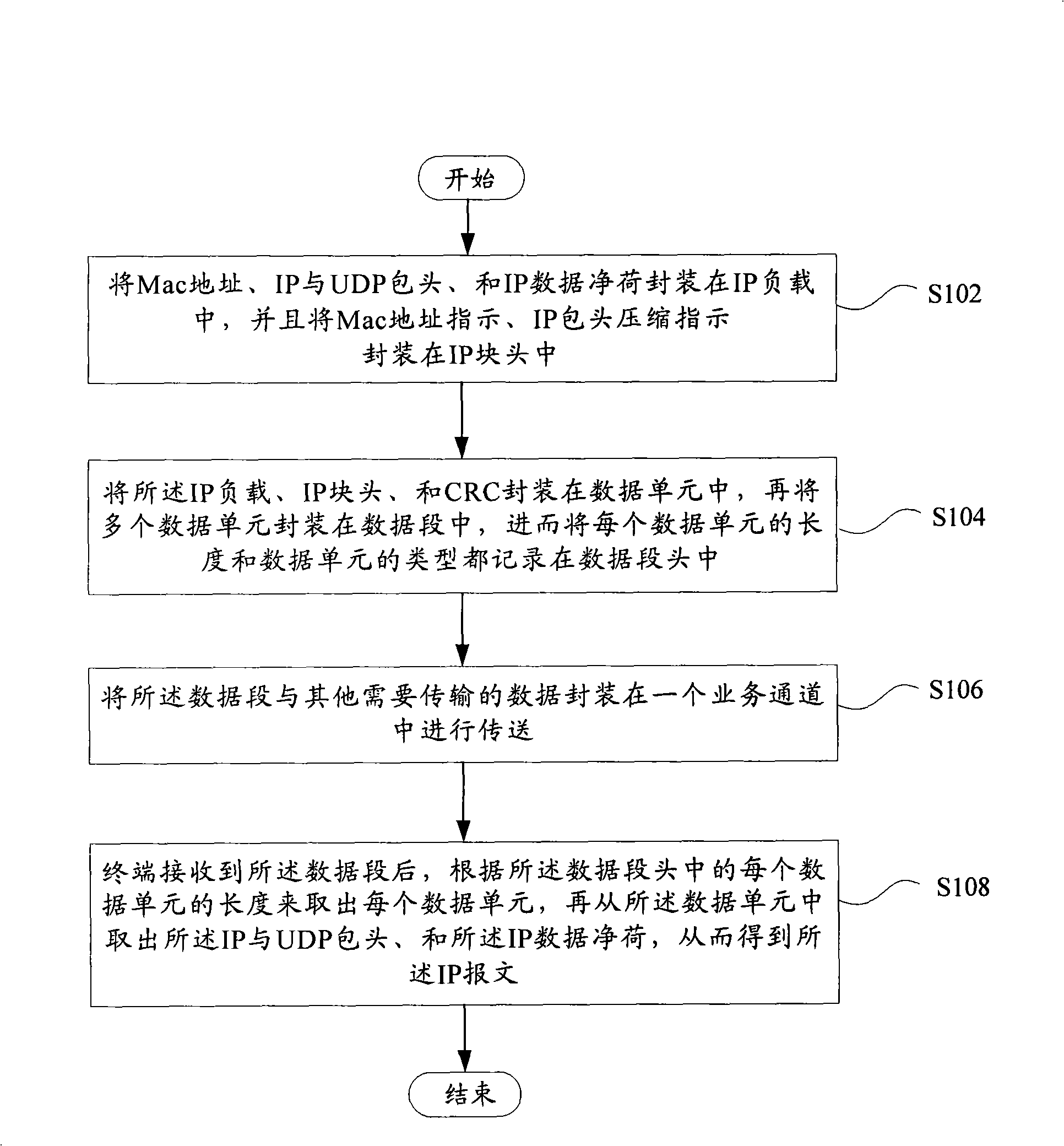
Method for conveying IP packet in broadcast network
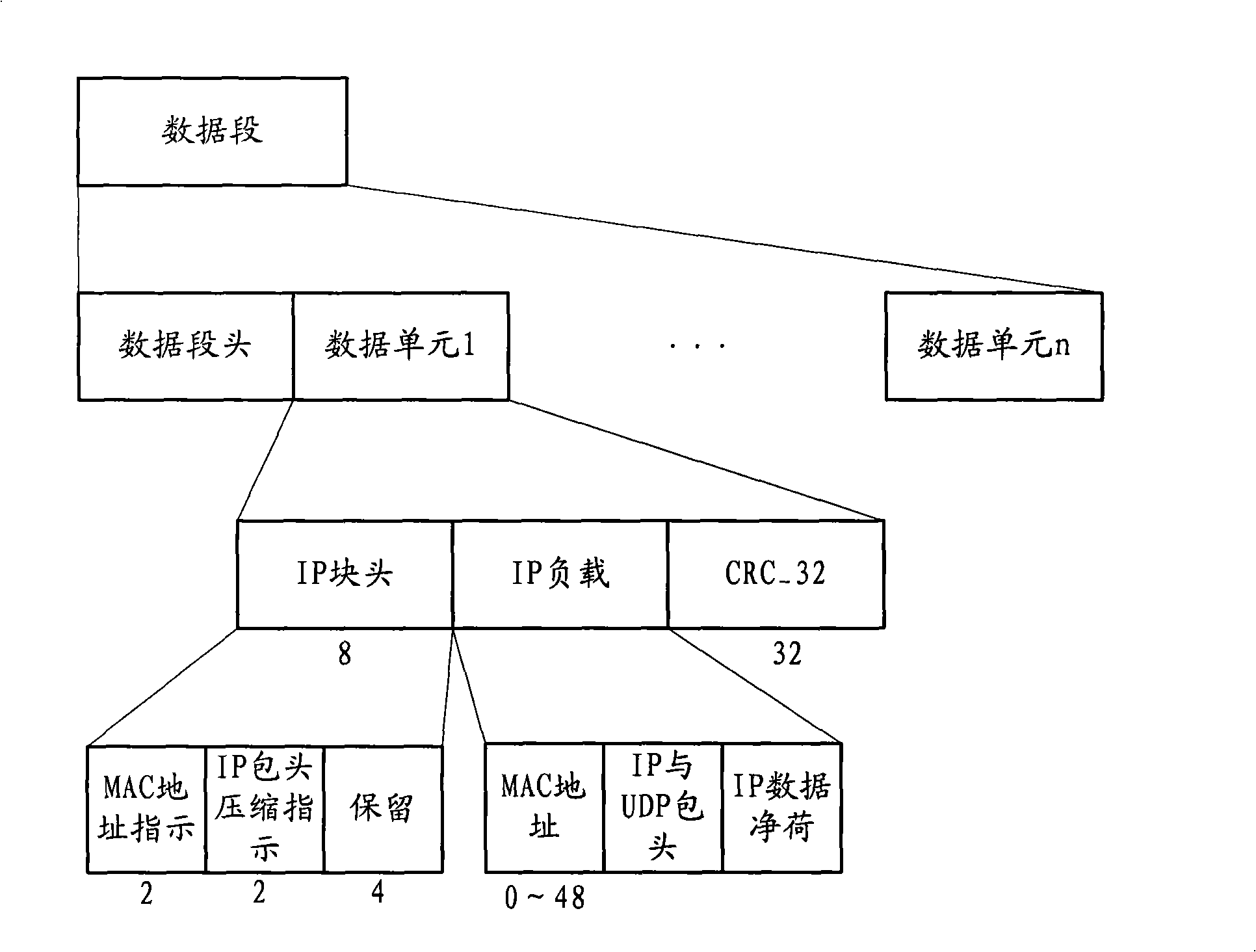
The present invention provides an IP message transmission method of broadcasting network, which can be used for effectively completing IP-based business in the multi-media broadcasting network, such as browsing, games and so on. In the method, the Mac address, IP and UDP header, and IP data payload are packaged in an IP load; the Mac address indication and IP header compression indication are packaged in an IP block head; the IP block head, the IP load and the CRC are packaged in a data unit; the length and the type of each data unit are recorded in a data segment head; a plurality of data units are packaged in the data segment; the data segment and other data to be transmitted are packaged and transmitted in a business channel; the terminal extracts each data unit after receiving the data segment, according to the length of each data unit in the head; the IP, the UDP header and the IP payload are extracted from the data unit so as to acquire the IP message. The length of the Mac address can be changed; the IP header can be compressed for transmission, thus the transmission efficiency is improved.
Owner:ZTE CORP
Method for authenticating a user
InactiveUS20150286811A1Biometric informationDigital data processing detailsAnswer-back mechanismsBiometric dataInternet privacy
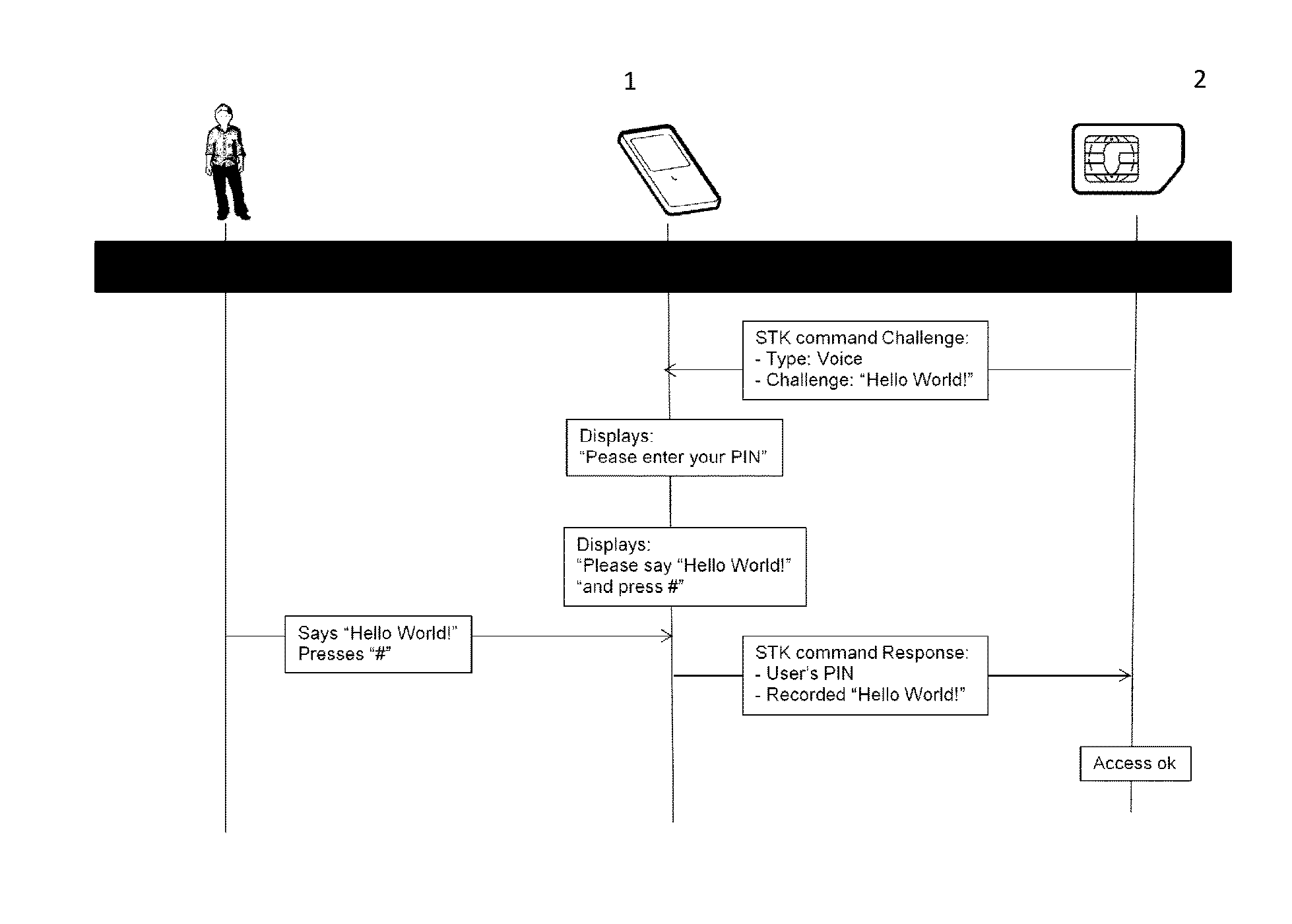
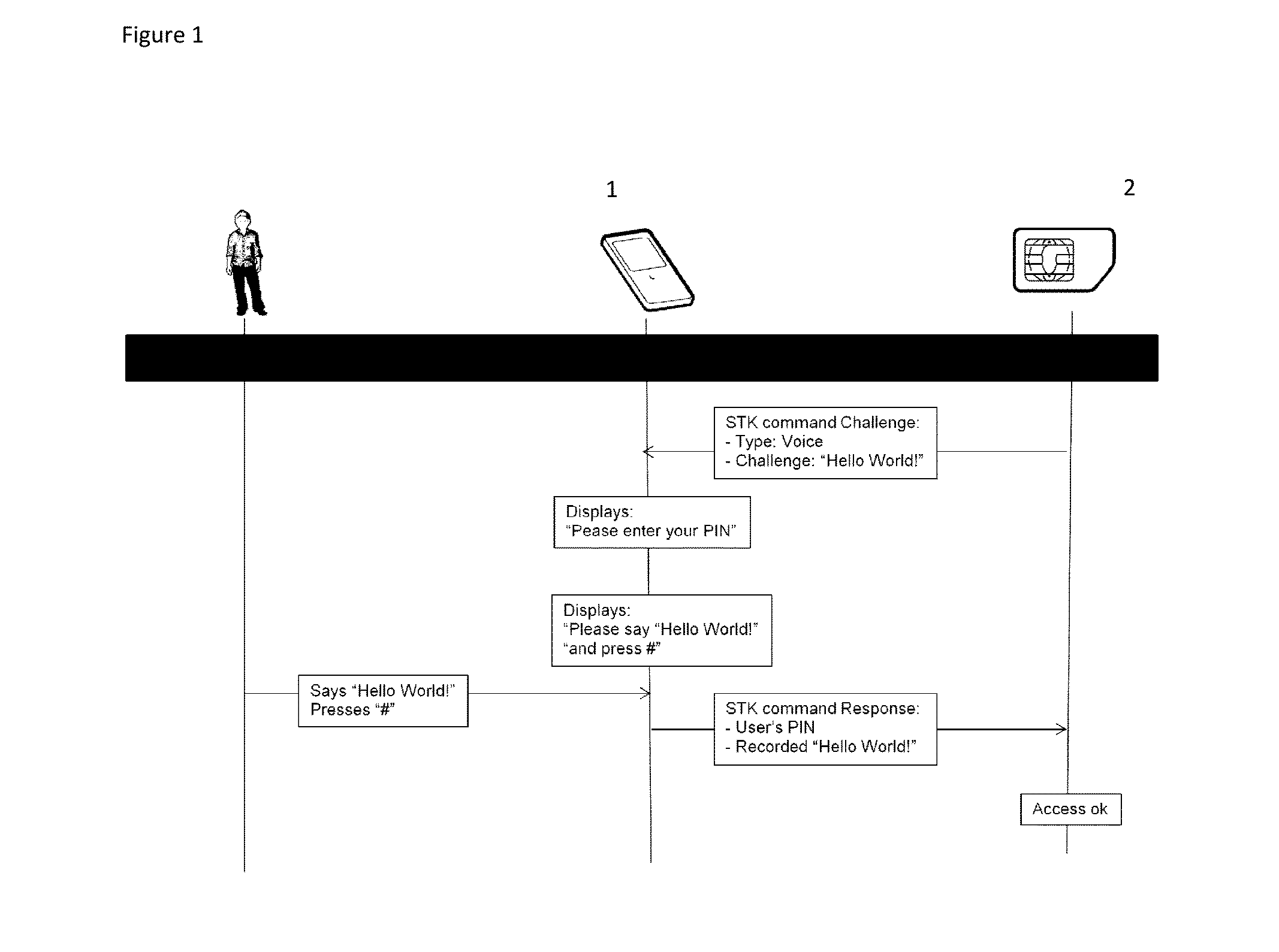
The invention relates to a method for authenticating a user when accessing to an application securely stored on a secure element of a portable device, said method comprising a step of authenticating the user via two authentication factors. The method comprises requesting a further authentication factor to said user, in a form of challenge-response based on a randomised request associated to a biometric data of said user.
Owner:GEMPLU
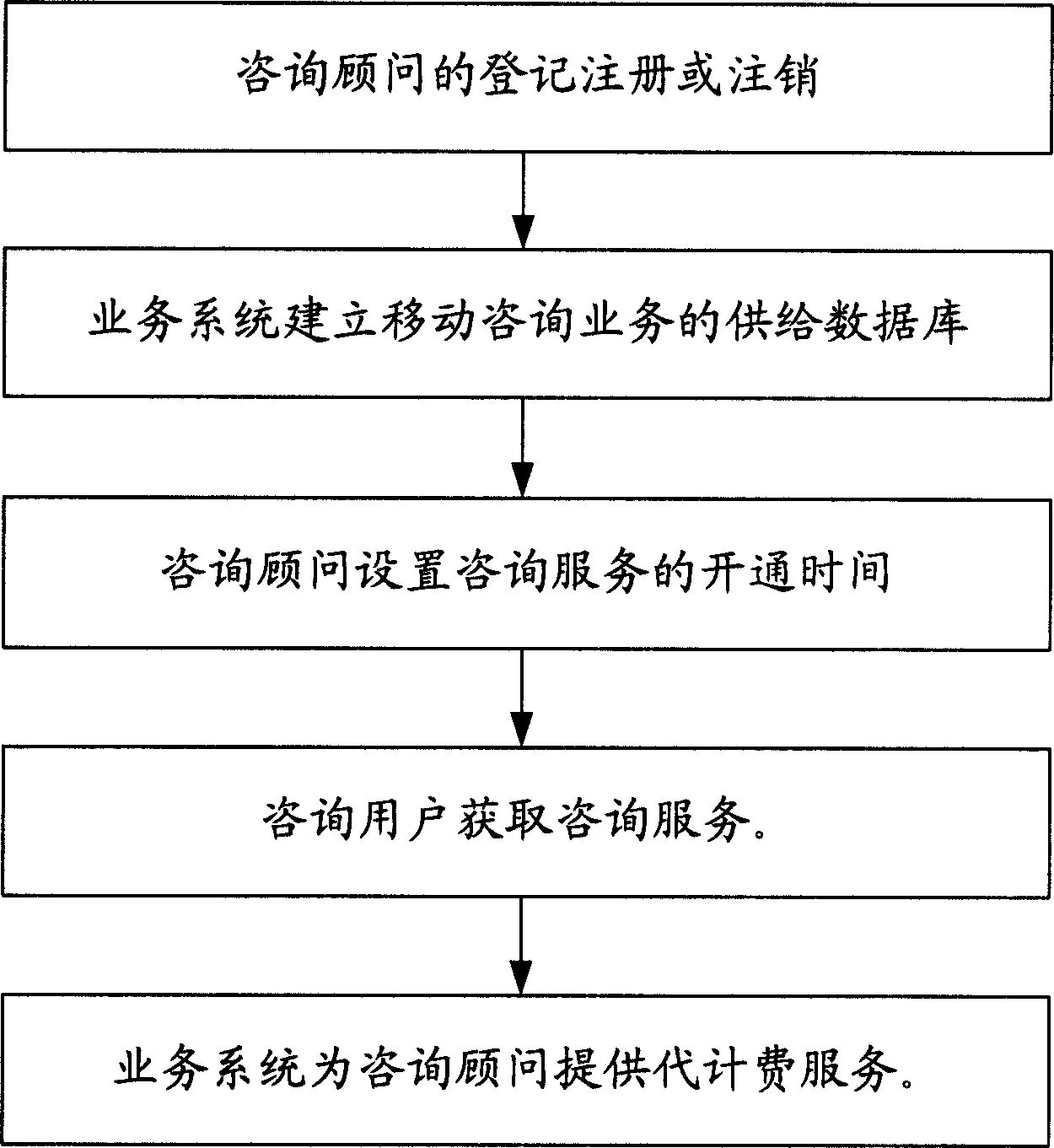
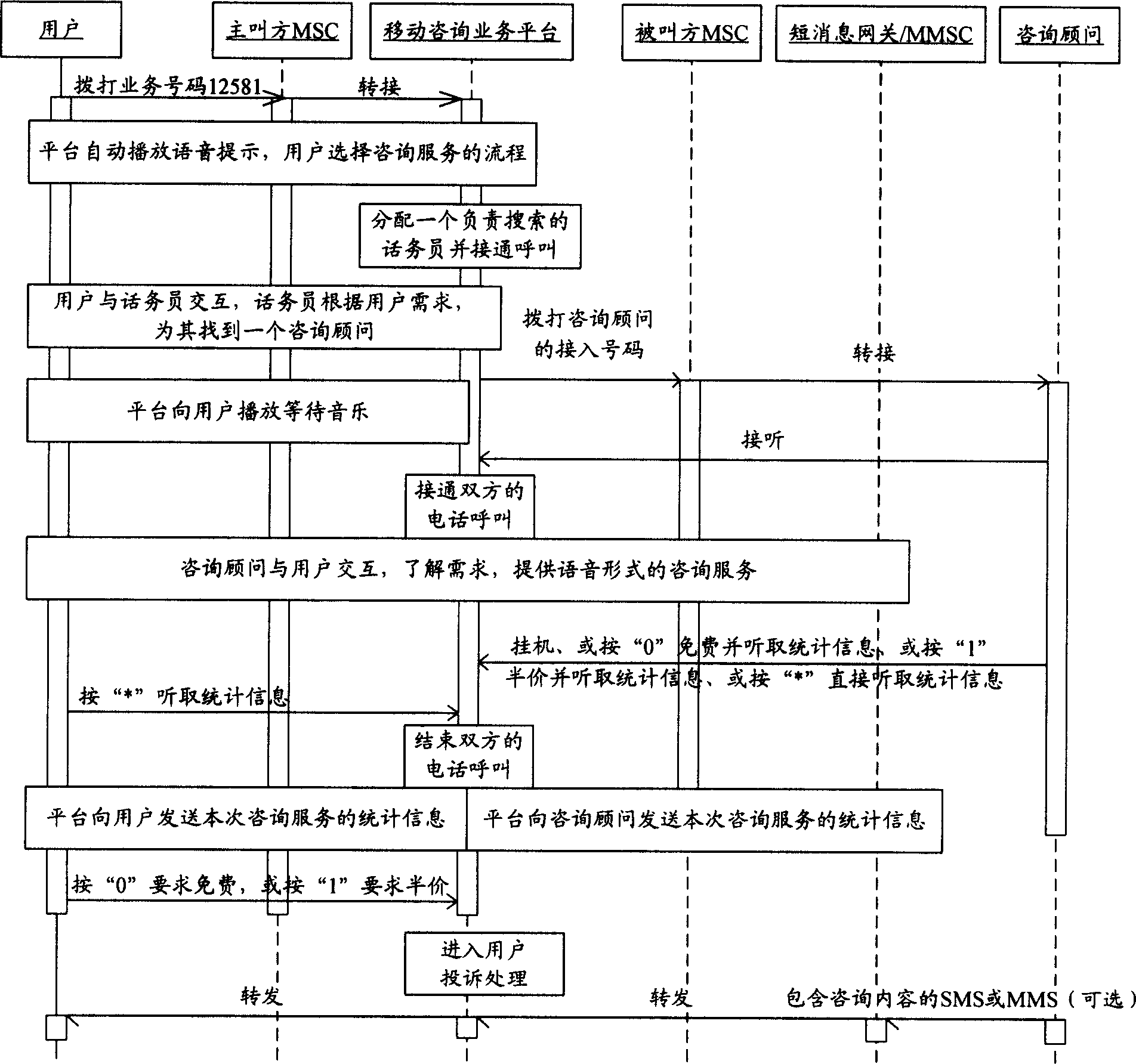
System and realization method for mobile consultation service between mobile users
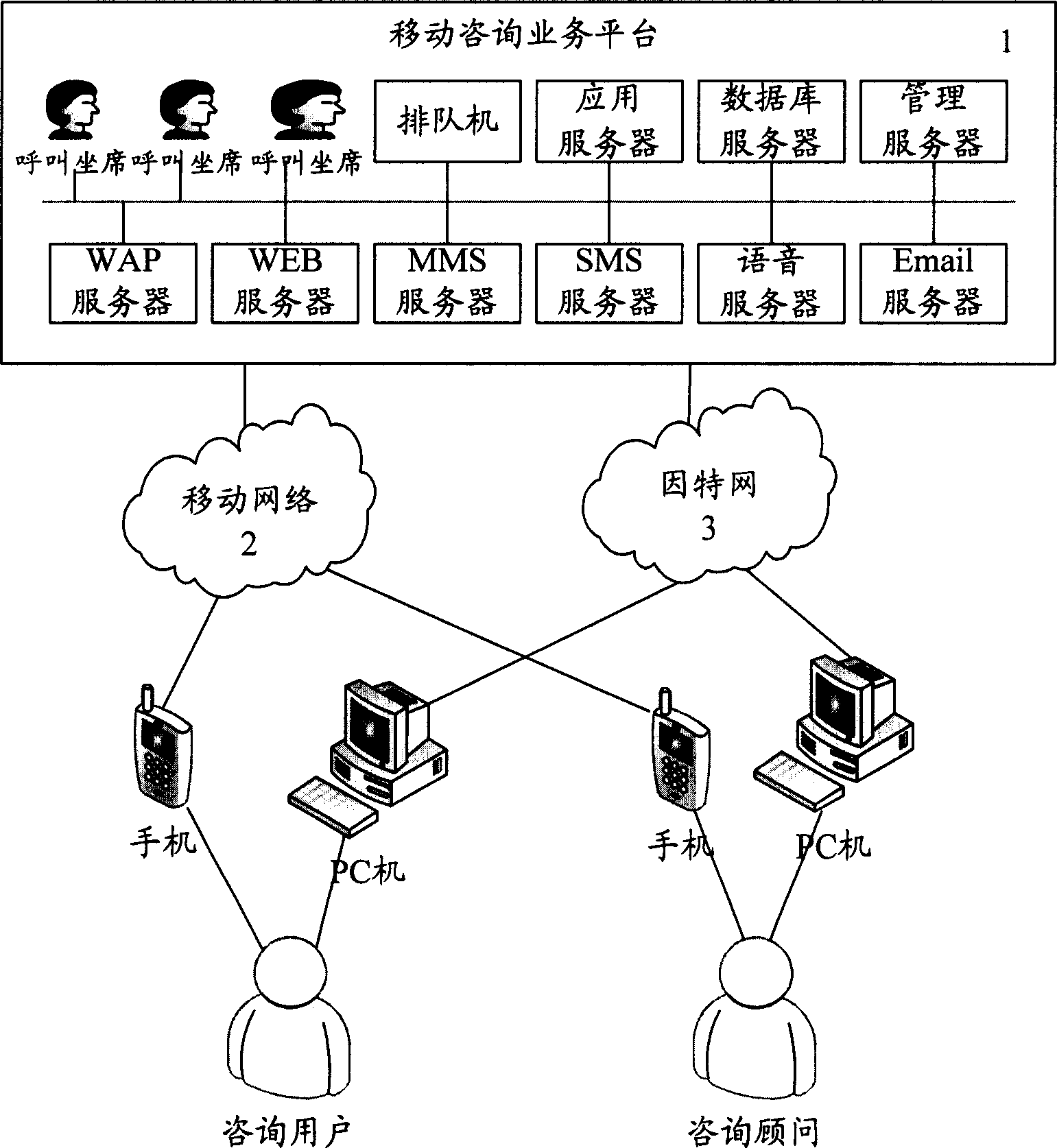
InactiveCN1845495AConsulting Business AssuranceSimple structureAnswer-back mechanismsData switching by path configurationInformation networksStructure of Management Information
The disclosed system for mobile consult business among mobile users comprises a mobile communication network, the Internet, mobile phone or PC, and the LAN-mobile consult business platform based on calling center technique. The corresponding method comprises: (1) registering or logging out; (2) building database for consult business; (3) setting turn-on time; (4) consulting user; (5) providing charge service. This invention is extendable and meets people requirement on information.
Owner:BEIJING UNIV OF POSTS & TELECOMM
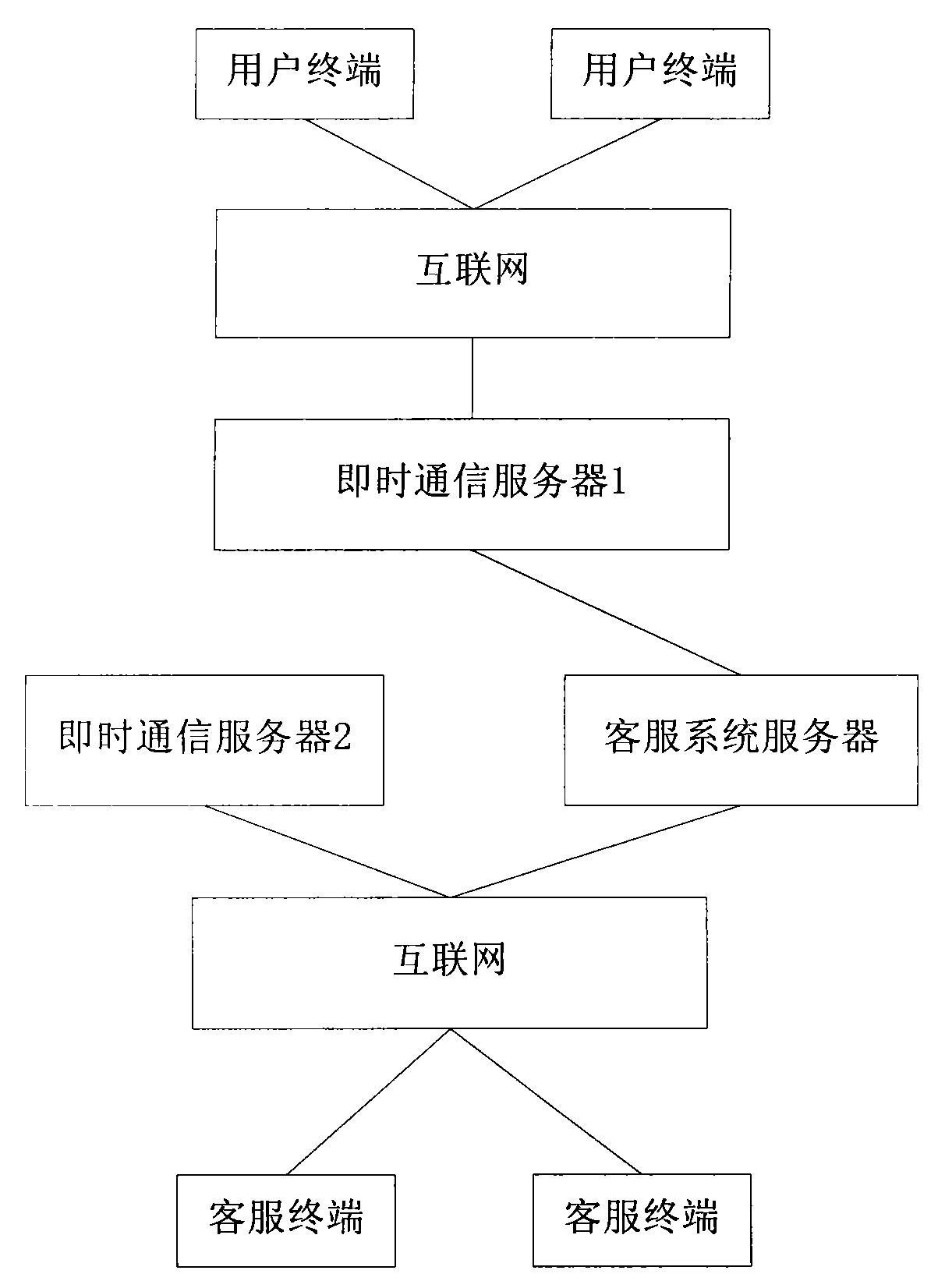
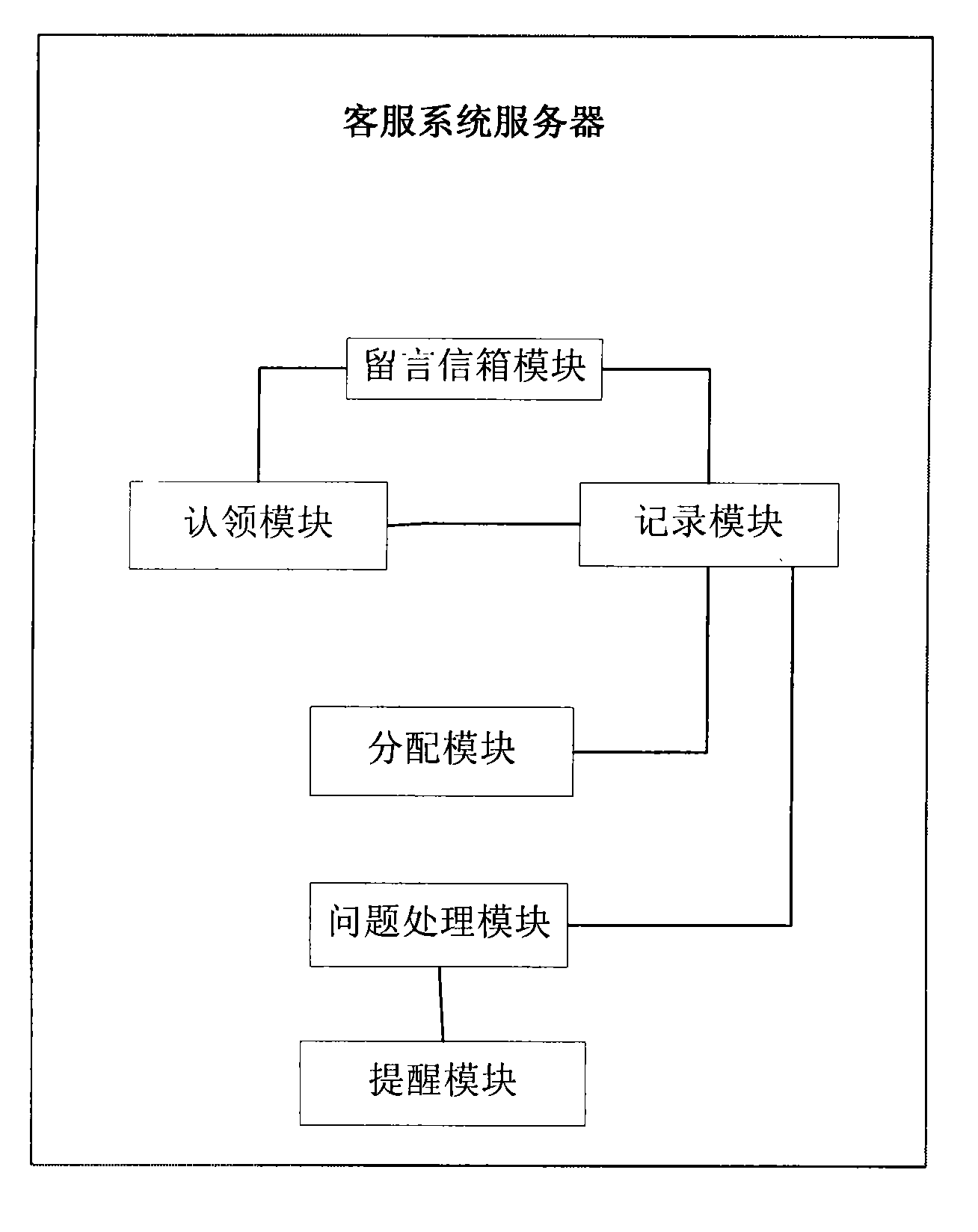
Method and system for submitting user questions through online customer service system
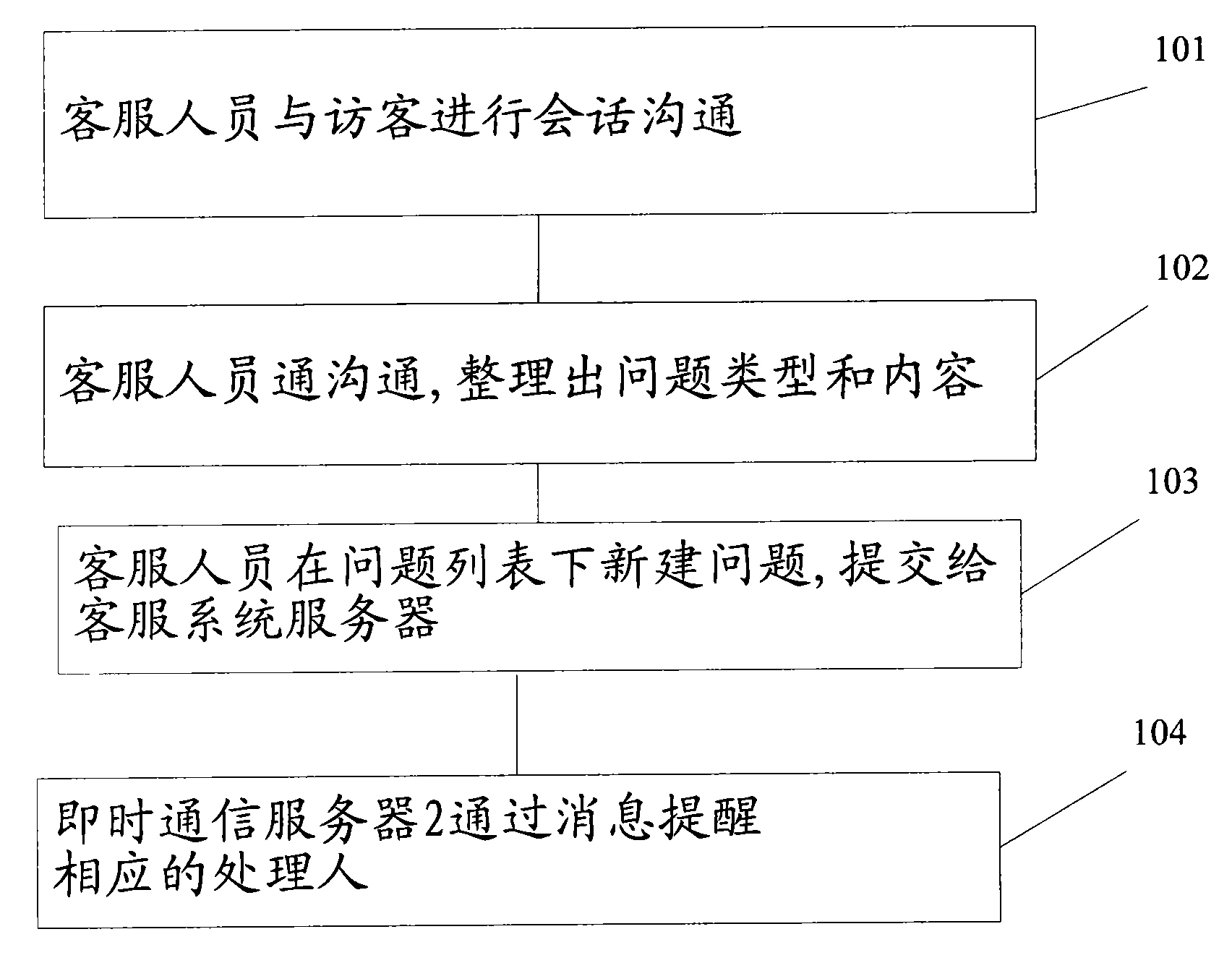
InactiveCN101588311AEasy to viewEasy to manageSpecial service for subscribersAnswer-back mechanismsService personnelThe Internet
The invention provides a method for submitting user questions through an online customer service system. The method comprises the following steps that: customer service personnel carry out session communication with a visitor, and sum up problem types and contents by chatting; customer service personnel establish a new problem under a problem list and select and submit a corresponding problem type, a dealing person and the priority to a customer service system server; the customer service system server sends the information to an instant communication server 2; and the instant communication server 2 generates an instant reminding message which is sent to a corresponding dealing person via the Internet. The method has the advantages that the problems of visitors are classified into different types under the problem list by the customer service personnel, so that other customer service personnel can look over identical problems conveniently, management and maintenance are convenient, and rapid feedback can be made; moreover, problem consultation and solving are facilitated.
Owner:BEIJING YIQI TELECOMM TECH
Client authentication method, password agent device and system
InactiveCN101998387AImprove login securityImprove securityAnswer-back mechanismsSecurity arrangementPasswordAuthentication
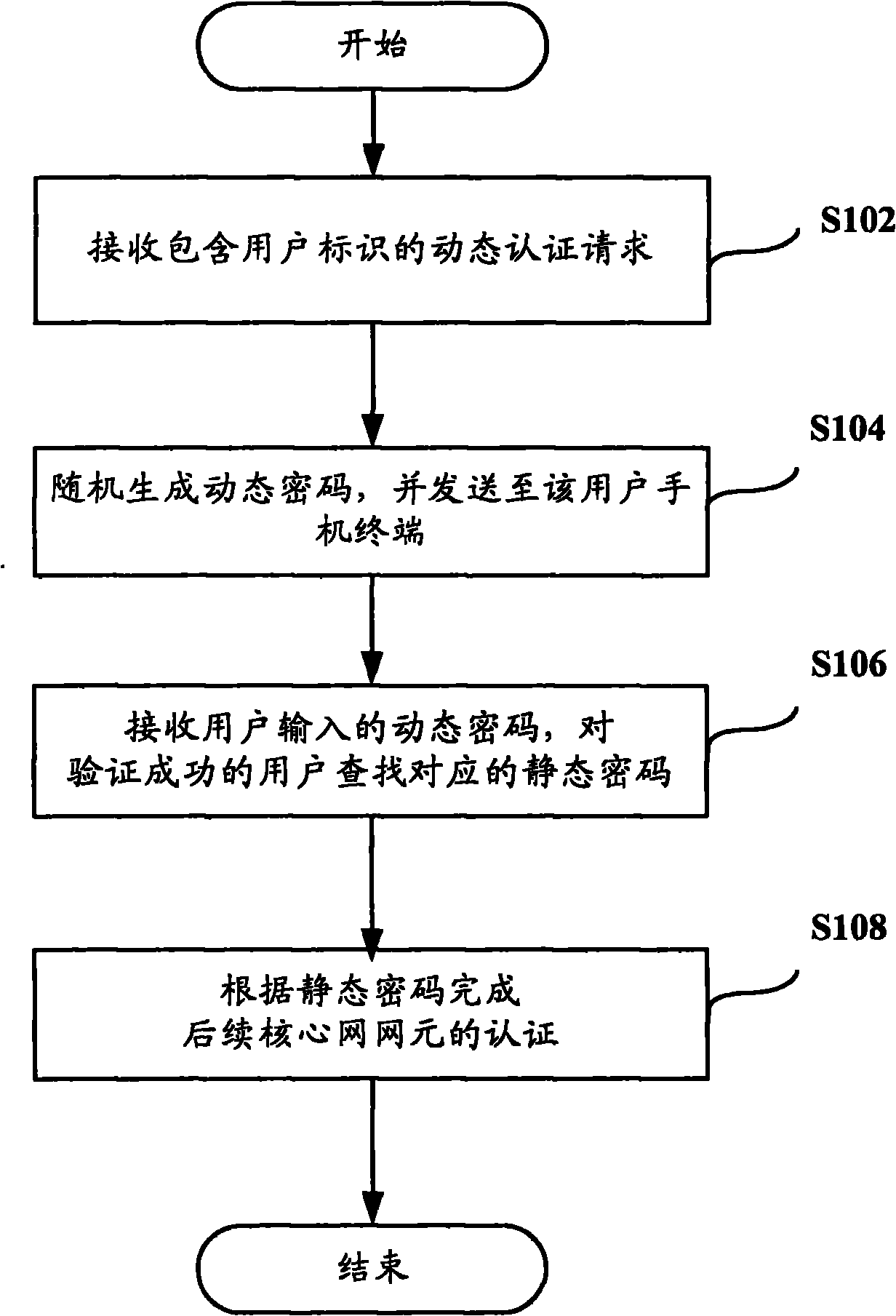
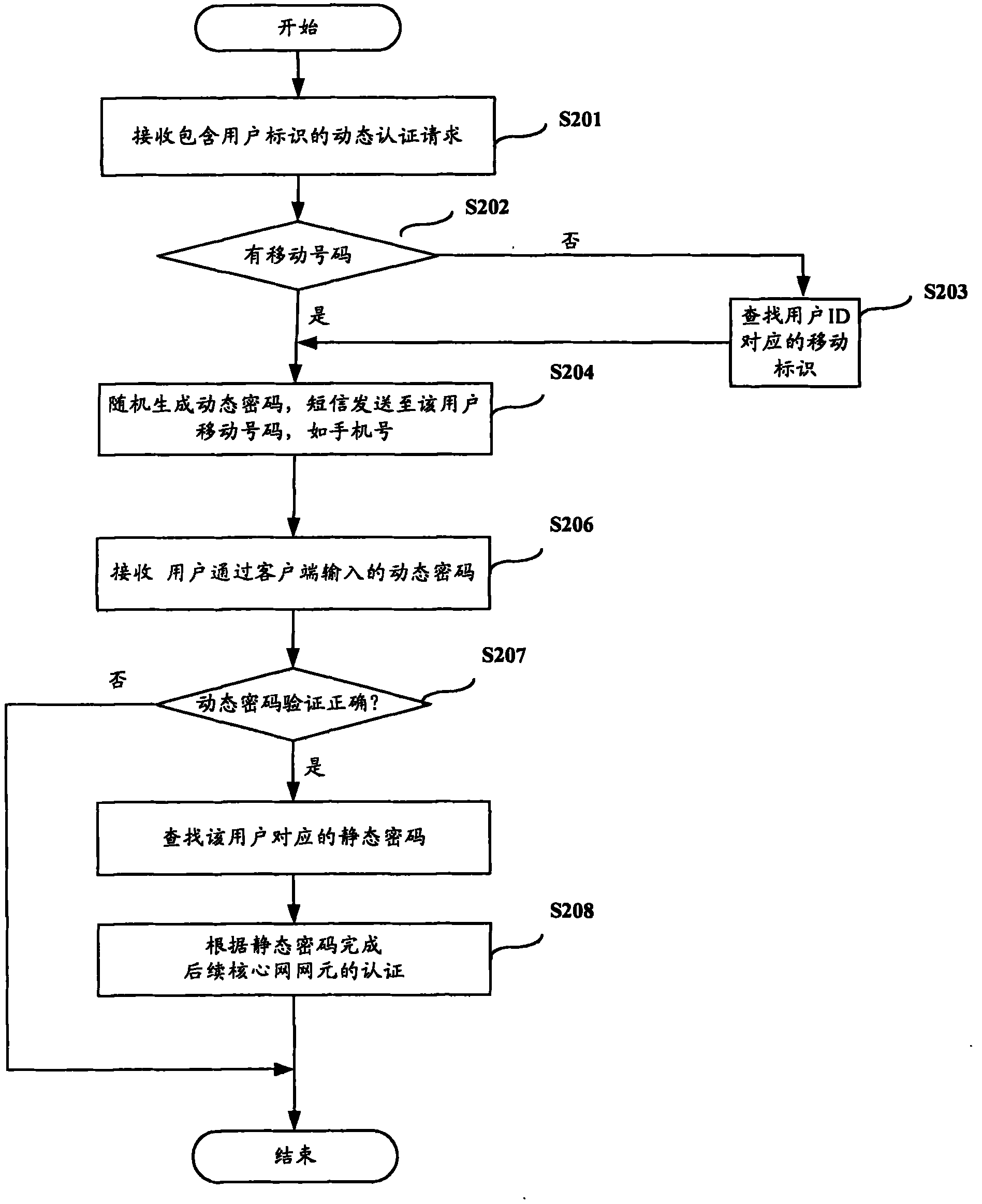
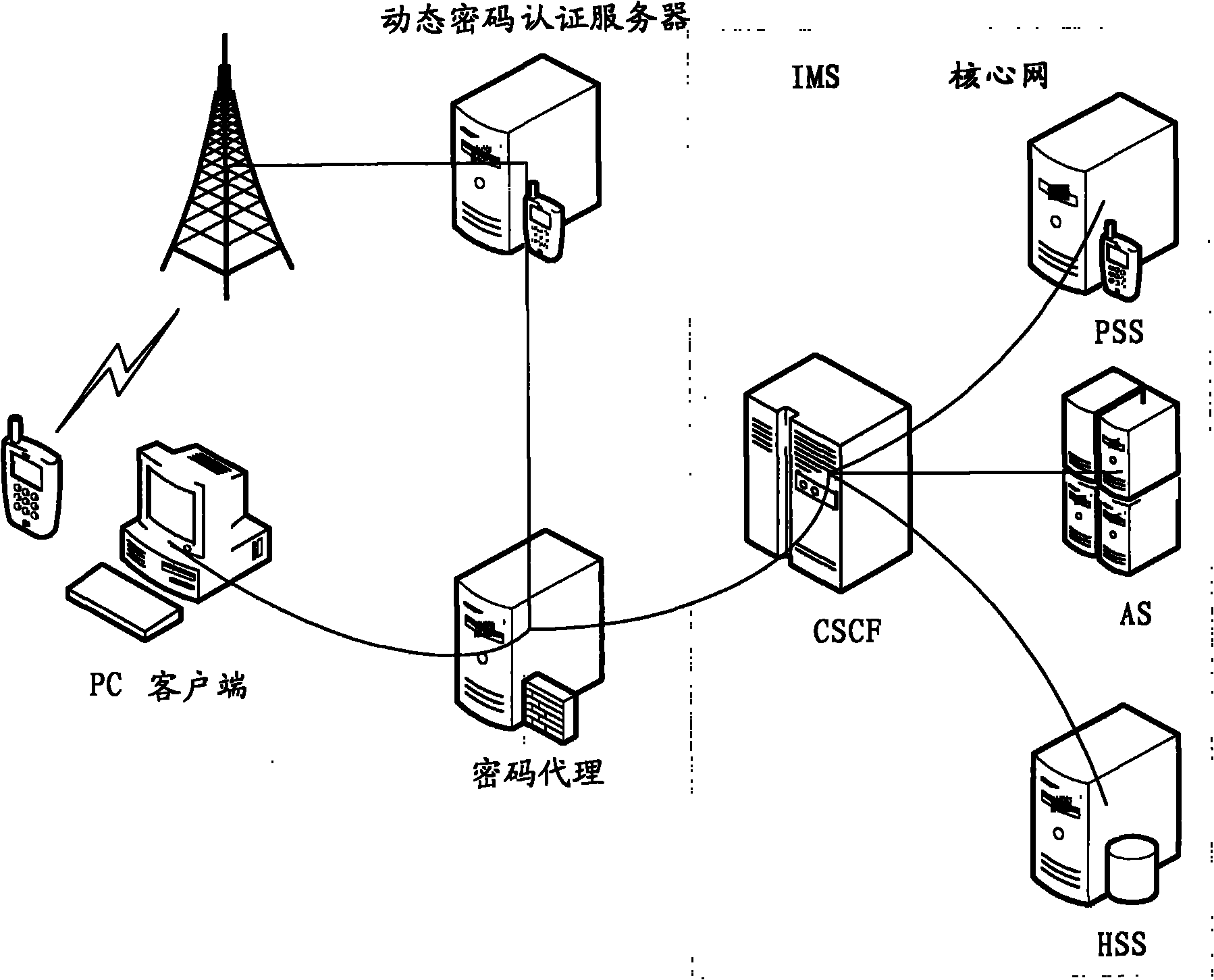
The invention discloses a client authentication method, a password agent device and a system. The method comprises the following steps of: receiving a dynamic authentication request containing user identification; generating a dynamic password according to the dynamic authentication request, and sending the dynamic password to the user; receiving the dynamic password of the user, and searching a corresponding static password for the user passing the verification; and performing authentication on a subsequent core network element according to the static password. The method can improve the security of client login, and overcomes the defect of low reliability in the IMS login mode in the prior art.
Owner:CHINA MOBILE COMM GRP CO LTD
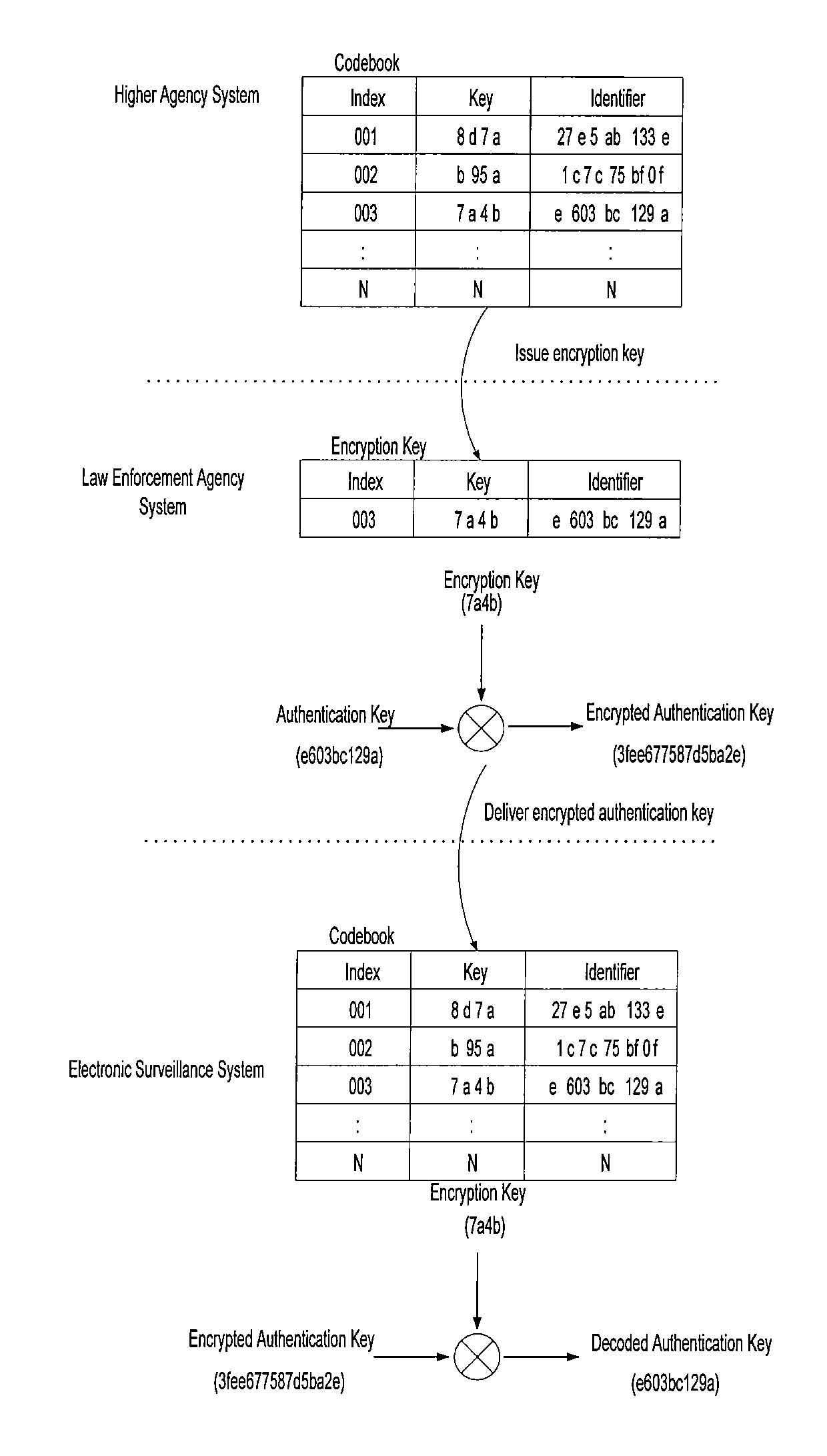
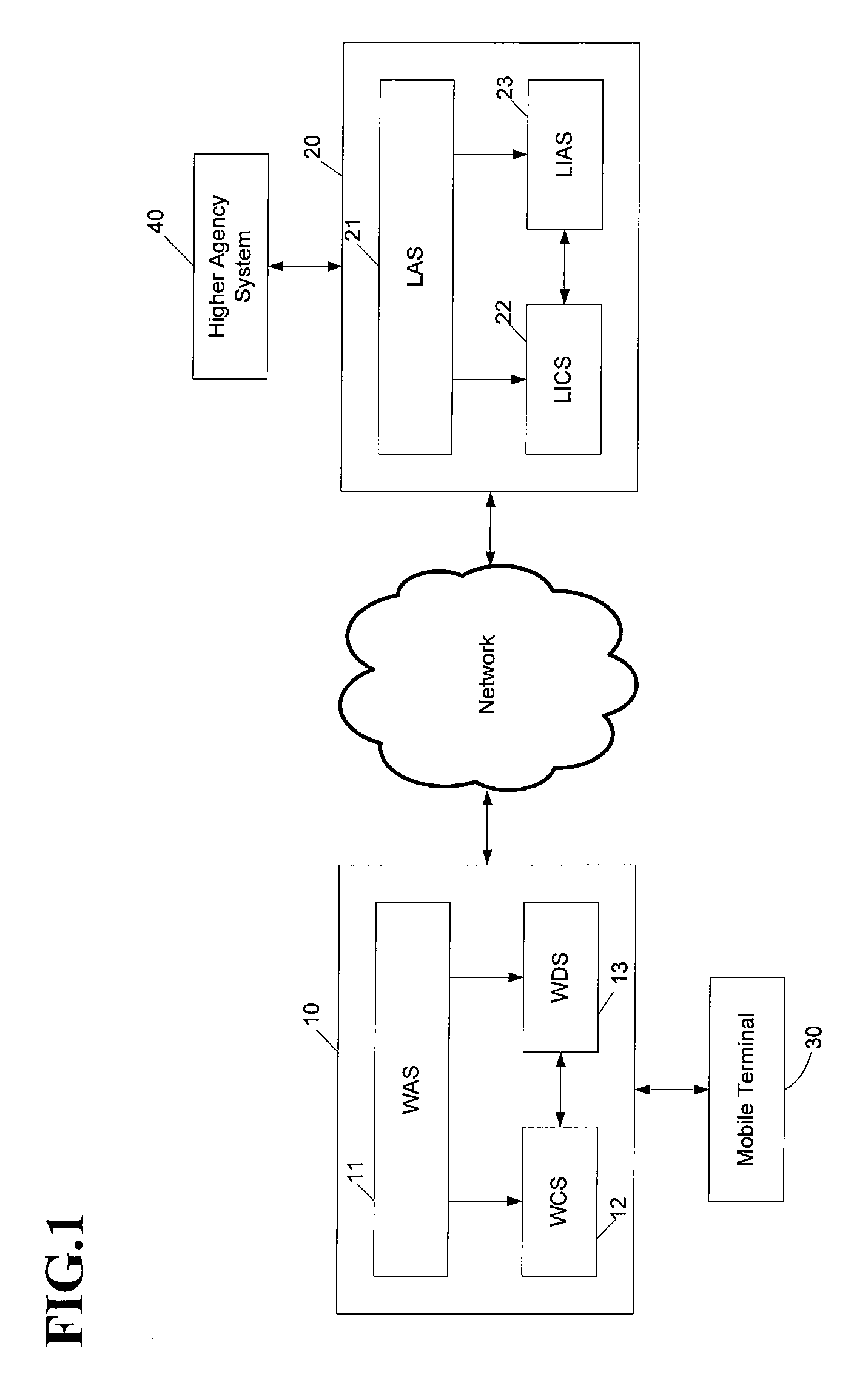
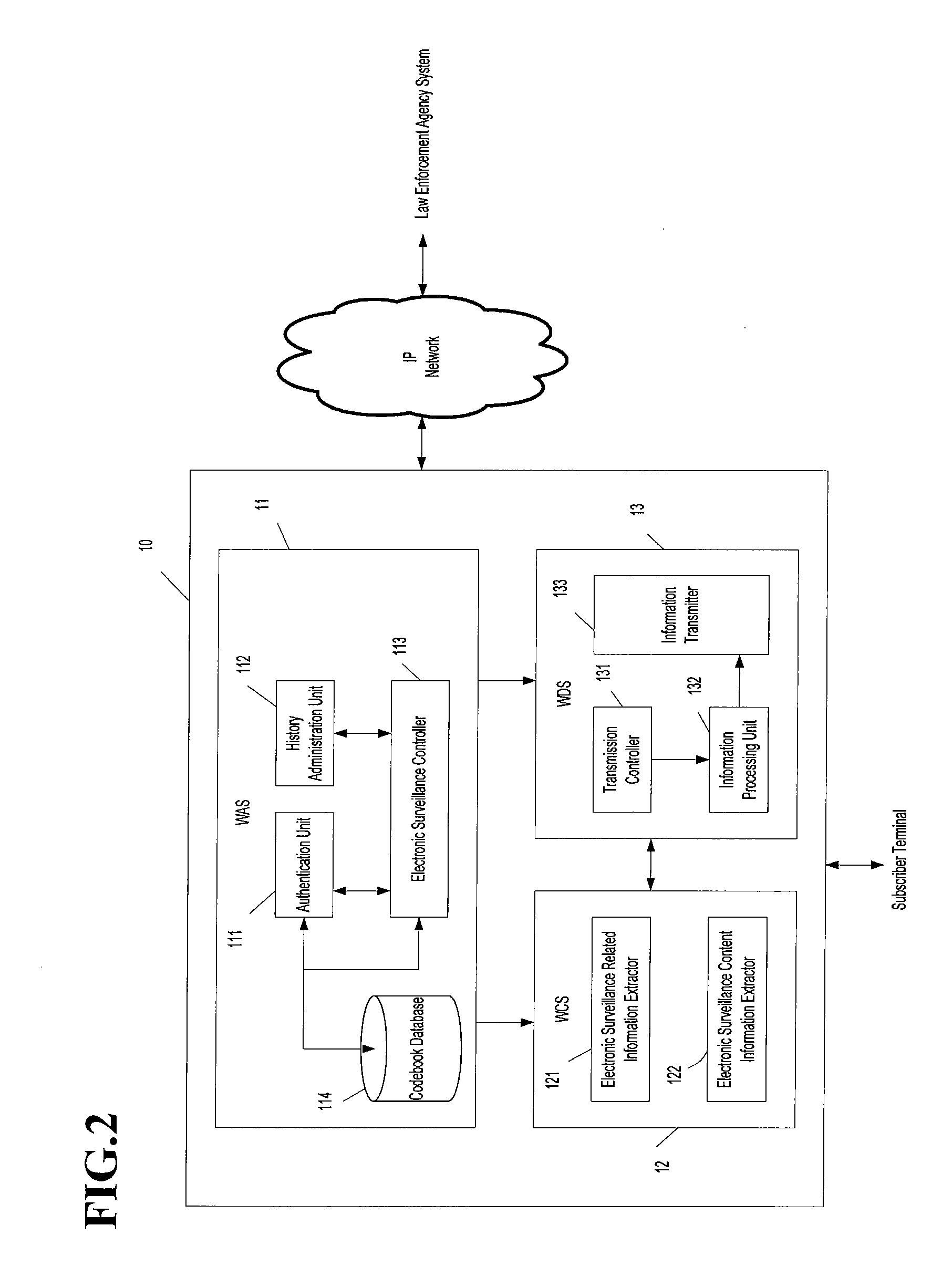
Electronic surveillance method and system
InactiveUS20080103973A1Improve safety and reliabilityKey distribution for secure communicationPublic key for secure communicationBroadbandEncryption
The present invention relates to an electronic surveillance method and system in a wideband wireless access system. If a law enforcement agency system requests electronic surveillance relative to a specified object, an electronic surveillance system first performs an authentication process using a codebook to authorize the electronic surveillance request. As the result of the authentication process, if it is judged that the electronic surveillance request of the law enforcement agency system is legal, the electronic surveillance system issues an encryption key required for encrypting communication contents with a law enforcement agency and electronic surveillance information. Thereafter, communication and message transmission / reception between the electronic surveillance system and the law enforcement agency system are encrypted and decoded using the encryption key. Accordingly, an illegal electronic surveillance request by an unauthorized user can be blocked, and an encryption key is issued to only an authorized user, such that the authorized user is authorized to access electronic surveillance information. With the authentication process and the encryption, the electronic surveillance information is protected doubly. Therefore, illegal access by an unauthorized user can be prevented.
Owner:ELECTRONICS & TELECOMM RES INST
High speed media access control and direct link protocol
Owner:QUALCOMM INC
Determining the service set identification of an access point in a wireless local area network
InactiveUS7836166B2Special service provision for substationError preventionBeacon frameLocal area network
The service set identification (SSID) of an access point (AP) in a wireless local area network (WLAN), where the AP suppresses its SSID in beacon frames broadcasted by the AP, is determined. At a detector located in the WLAN, a probe request broadcasted by a station through the WLAN is received. At the detector, a probe response sent by the AP to the station through the WLAN in response to the probe request broadcasted by the station is received. At the detector, the SSID of the AP is obtained from the received probe response.
Owner:AIRMAGNET
Data cell traffic management
InactiveUS7072302B1Reduce processing latencyCalculation is complexError preventionFrequency-division multiplex detailsTraffic capacityControl cell
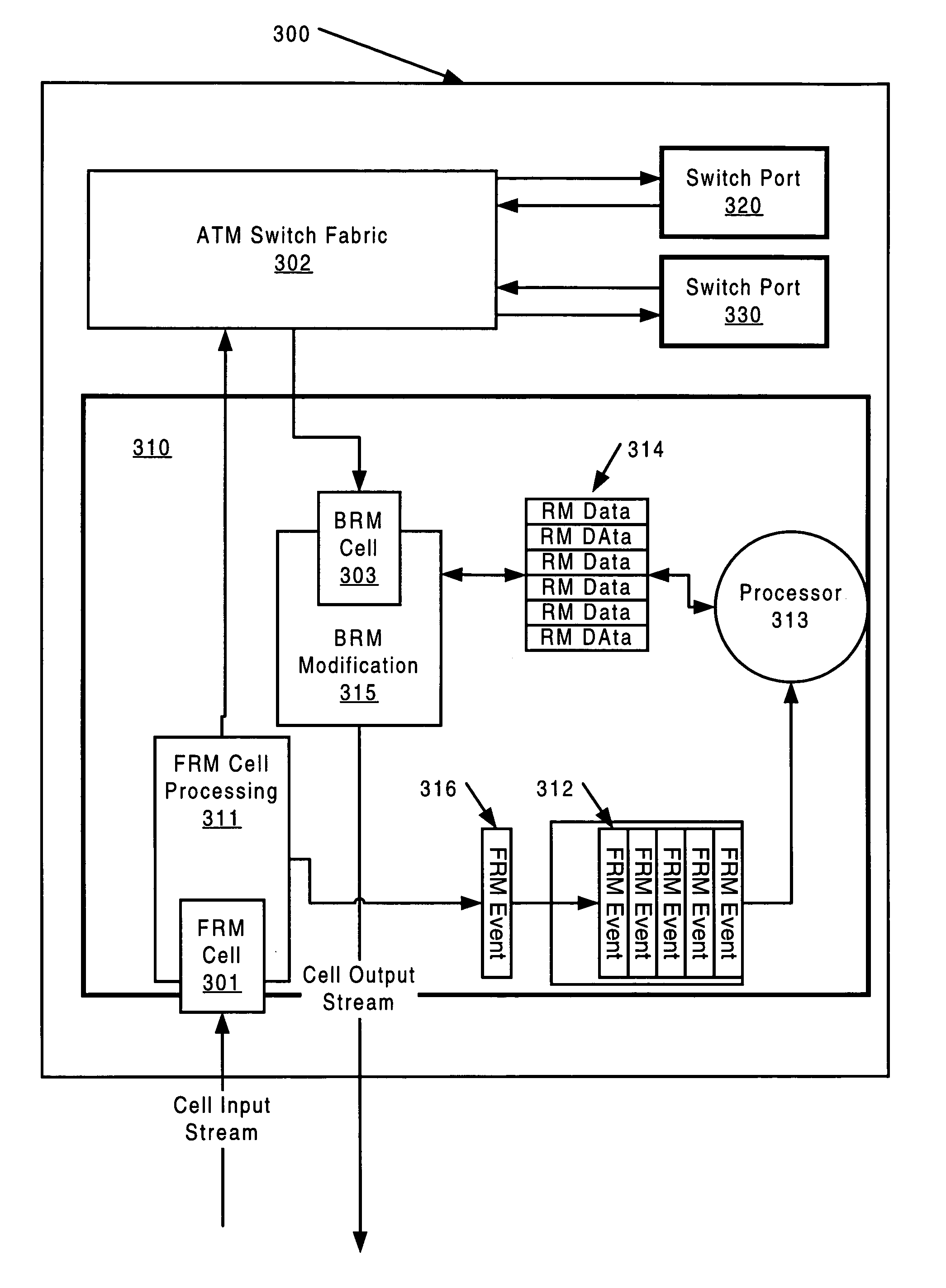
A method for controlling data cell transmission in a network can be implemented at a network element through which data cells are transferred between source and destination nodes. The method includes receiving a control cell on a virtual channel from a source node, generating a management event upon receipt of the control cell, and processing the management event to compute resource management data. Upon the subsequent receipt of a control cell on a virtual channel from a destination node, the control cell from the destination node is modifying using the computed resource management data and transmitted over the first virtual channel toward the source node. In another aspect, a data transmission apparatus regulates the transmission of data and control cells. The apparatus includes source and destination port circuitry, switching circuitry, management event circuitry, and return cell circuitry. The port circuitry couples the apparatus to links over which source and destination virtual channels can be established. The switching circuitry interconnects port circuitry and can exchange data and control cells between source and destination virtual channels. The management event circuitry is coupled to the source port circuitry to receive control cells from the source virtual channel and to compute resource management data. The return cell circuitry is coupled to the source and destination port circuitry and to the management event circuitry and can receive control cells from the destination port circuitry, modify control cells based on the resource management data computed by the management event circuitry, and provide the modified control cells to the source port circuitry for transmission over source virtual channels.
Owner:INTEL CORP
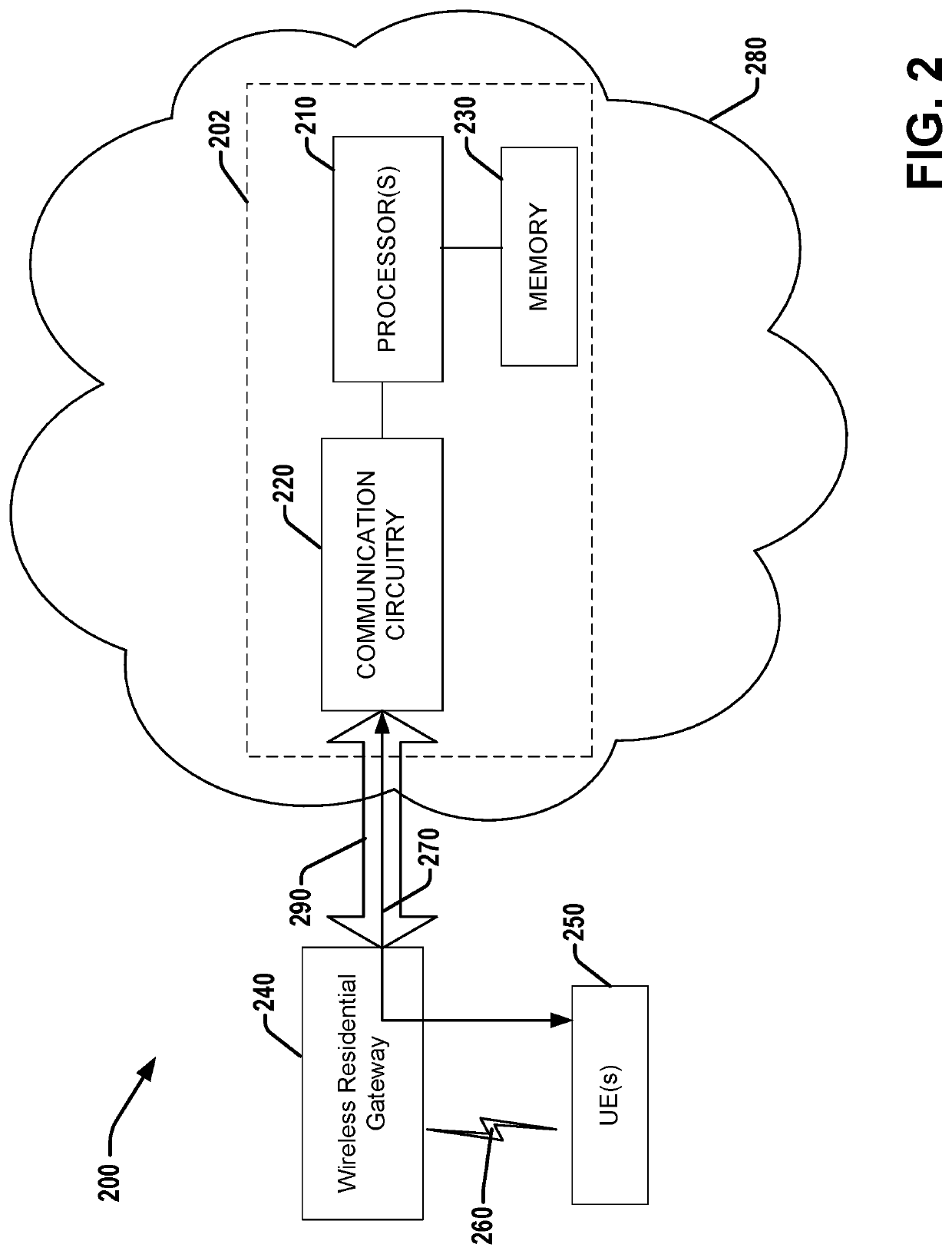
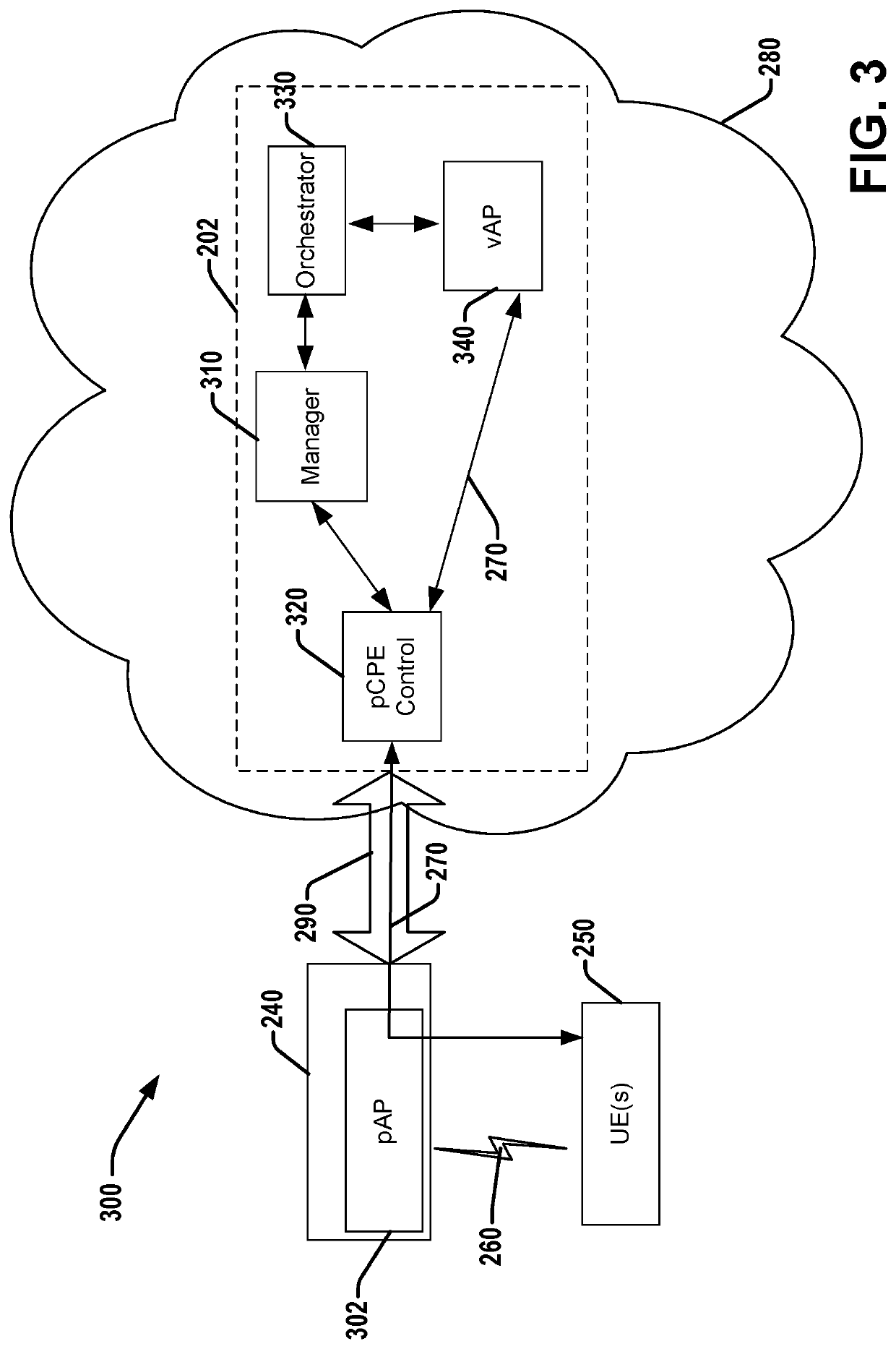
COMMUNITY WiFi ACCESS POINT (AP) VIRTUAL NETWORK FUNCTION (VNF) WITH WiFi PROTECTED ACCESS 2 (WPA2) PASS-THROUGH
ActiveUS20200028700A1Encryption apparatus with shift registers/memoriesNetwork topologiesCommunity settingUser equipment
A service provider (SP) network device or system can operate to enable a WiFi protected access 2 (WPA2) pass-through with a user equipment (UE). The WPA2 pass-through can be an interface connection that passes through a computer premise equipment (CPE) or wireless residential gateway (GW) without the CPE or GW modifying or affecting the data traffic such as by authentication or security protocol. The SP network device can receive traffic data from a UE through or via the WPA 2 pass-through from a UE of a community Wi-Fi network at a home, residence, or entity network. Regardless of whether the UE is connected to any other home network at the CPE or is a subscriber to the SP network, the UE can communicate transparently by the WPA 2 pass-through with the SP network device to establish a secure initial access process with the SP network.
Owner:MAXLINEAR INC
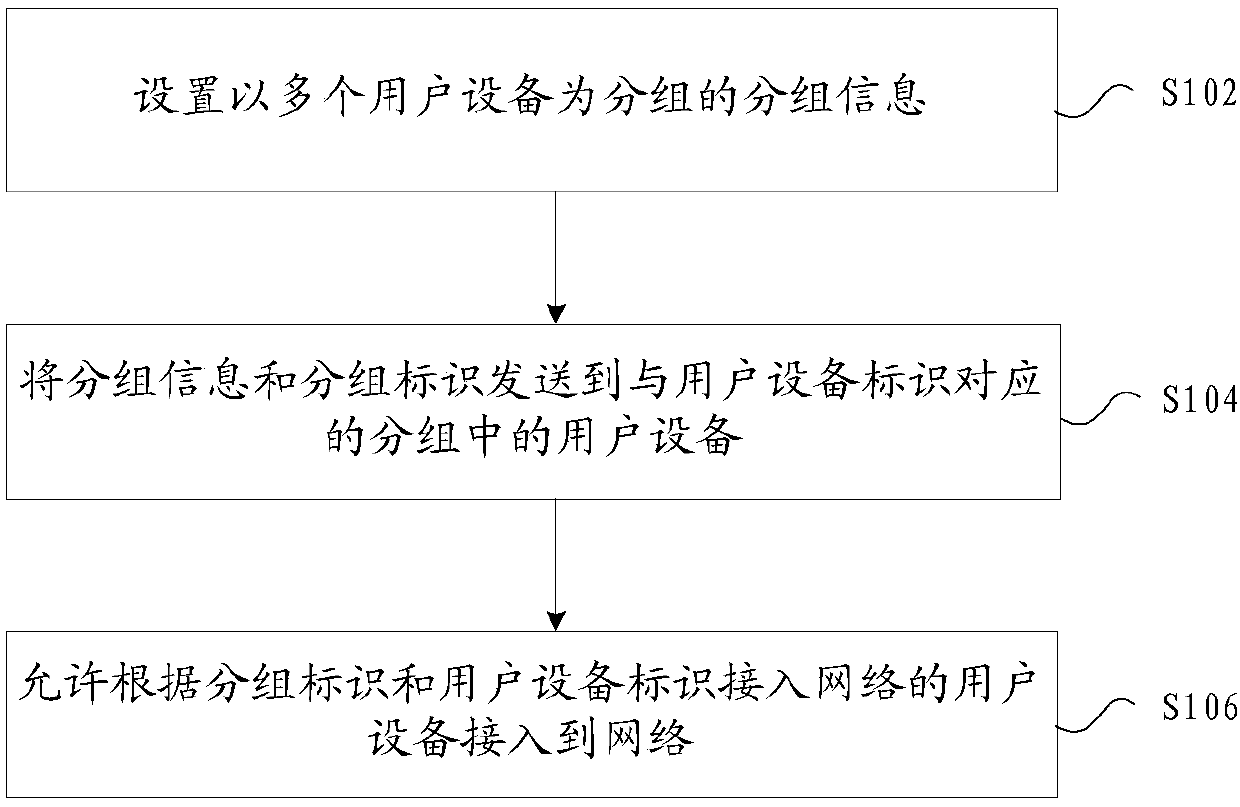
Method and device for achieving access to network
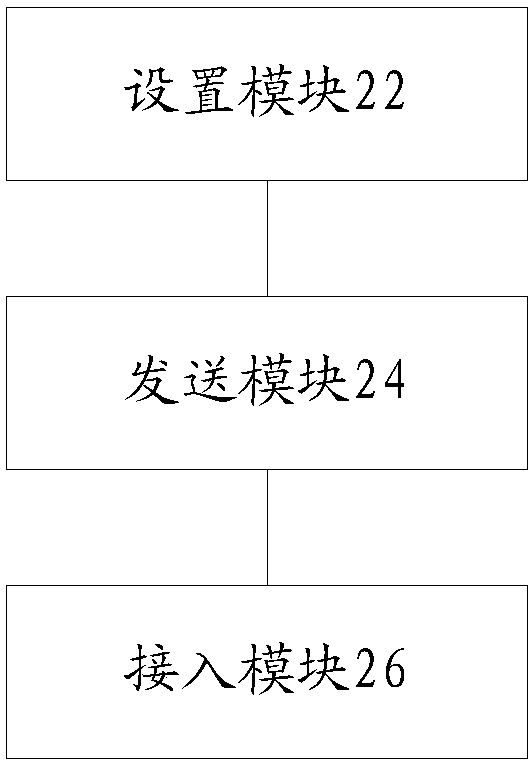
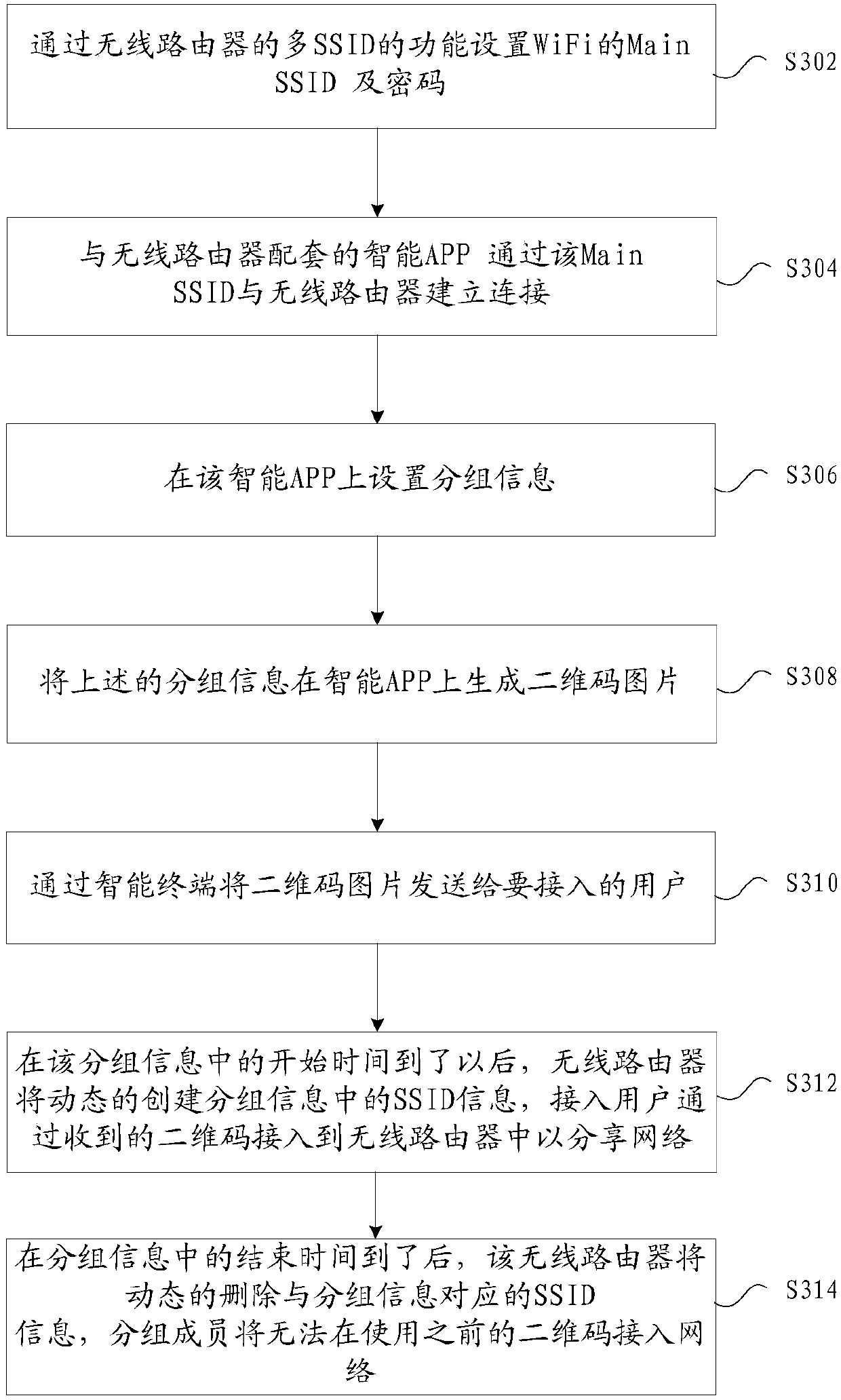
InactiveCN107566325AImprove securityAnswer-back mechanismsSecurity arrangementUser deviceUser identifier
The invention provides a method and a device for achieving access to a network. The method comprises steps of setting grouping information about grouping of multiple user devices, wherein the groupinginformation comprises grouping identifiers used for identifying groups and user device identifiers used for identifying user devices in the groups; sending the grouping information and the grouping identifiers to user devices in the groups corresponding to the user device identifiers; and allowing user devices accessed to the network according to the grouping identifiers and the user device identifiers to be accessed to the network. According to the invention, a problem is solved that users who are not in the groups can be also accessed to the network through information shared by the users in the groups in the prior art, and an effect of improving network safety is achieved.
Owner:ZTE CORP
Method and device for processing communication business
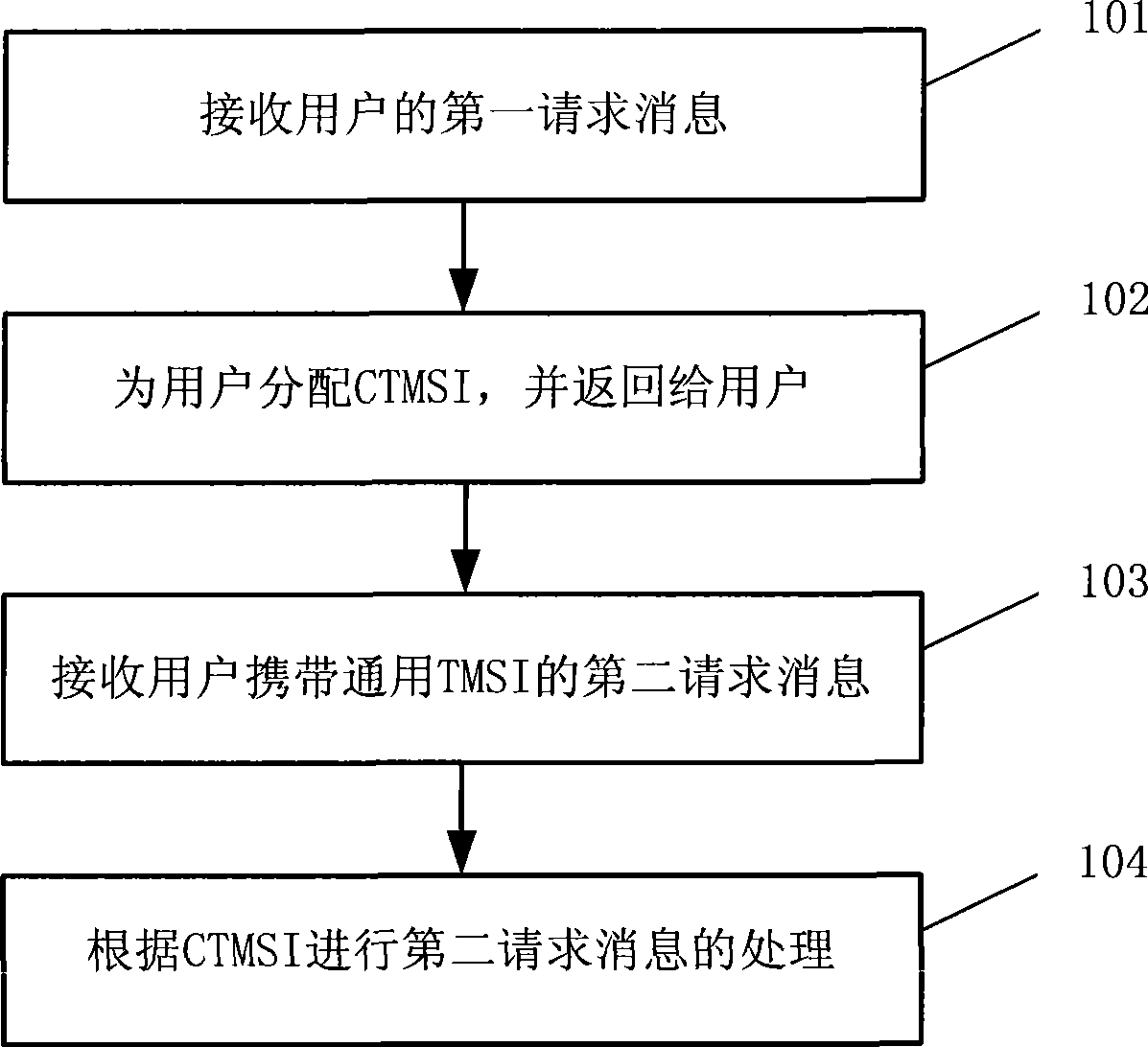
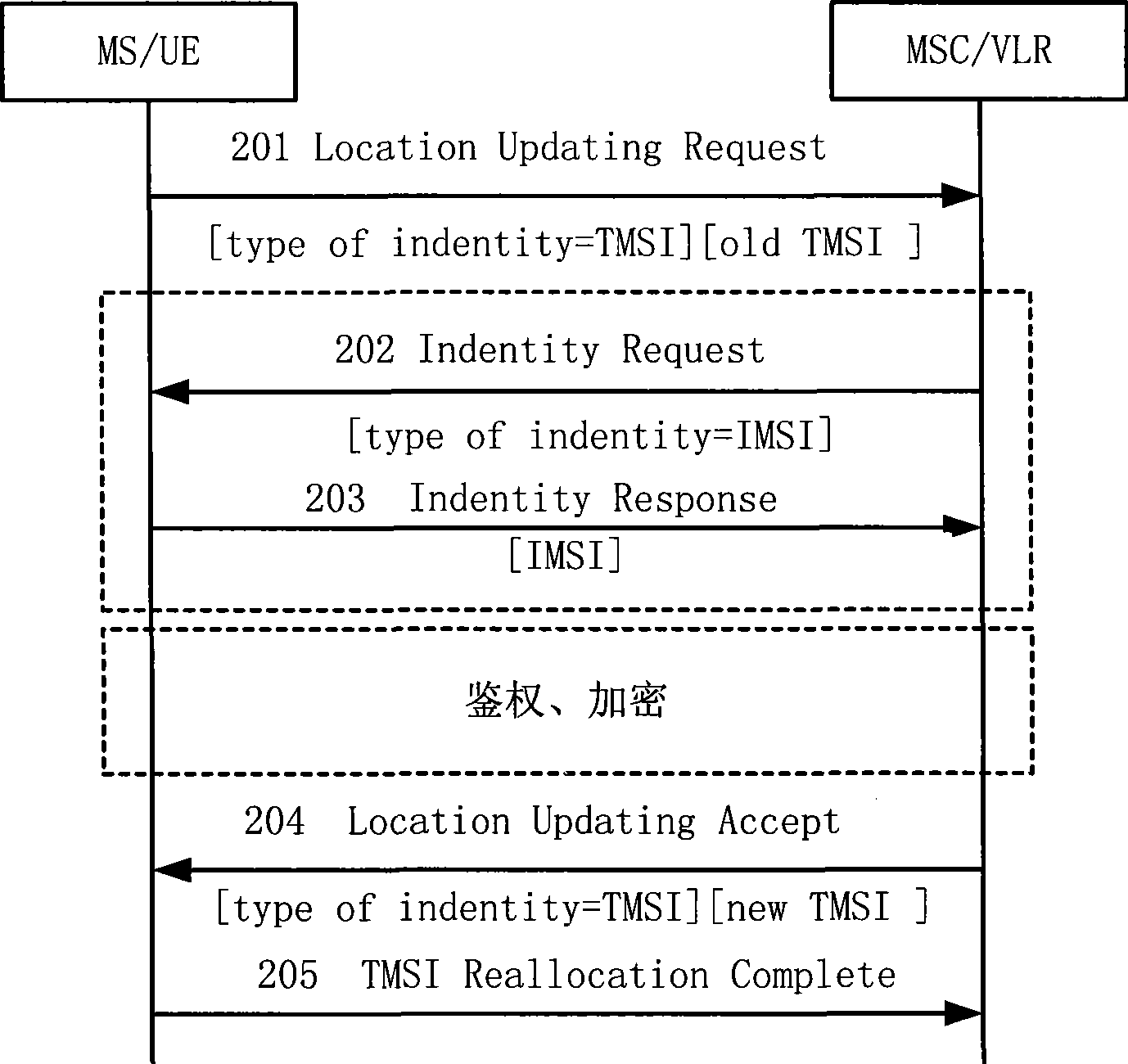
ActiveCN101466093AAllocation successfulAnswer-back mechanismsNetwork data managementProcess communicationWorld Wide Web
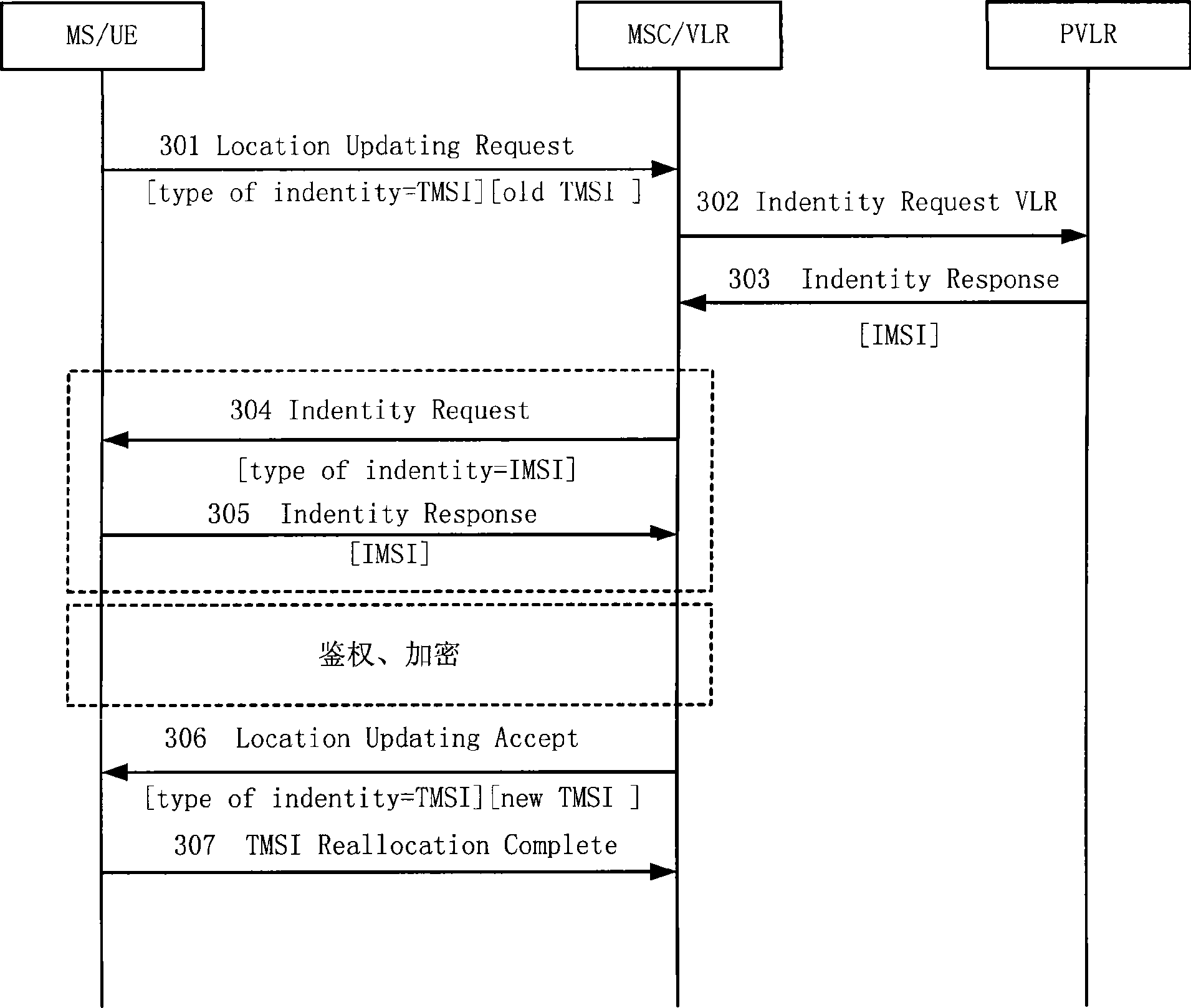
The embodiment of the invention discloses a processing method for communication service and a device thereof. The method includes that first user request information is received, and a conventional temporary mobile subscriber identity (CTMSI) can be allocated for users; second user request information carrying the CTMSI is received, and the second request information is processed according to the CTMSI. In the method and the device of the embodiment, by allocating the CTMSI for the users, the flow process of allocating the CTMSI for the users can not be limited by the CTMSI resource, so as to ensure the successful CTMSI allocation for the users; and the following users can process the following business according to the CTMSI.
Owner:HUAWEI TECH CO LTD
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com