Client authentication method, password agent device and system
An authentication method and technology of an agent device, applied in the fields of IP multimedia subsystem, client authentication method, password agent device and system, can solve the problems of being easily attacked by hackers, unable to guarantee information security, poor security level, etc., to improve experience , High login security, and the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
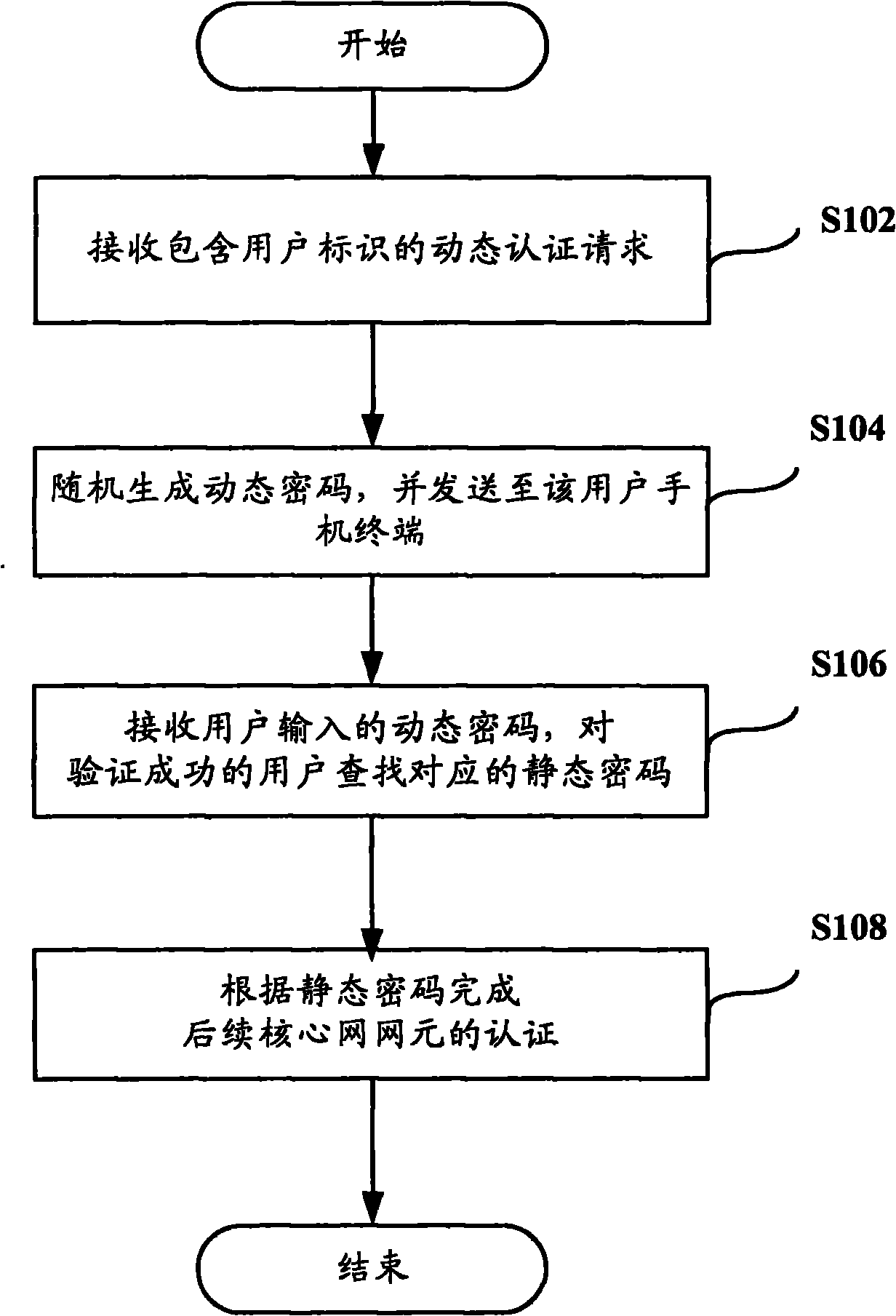
[0030] figure 1 It is a flow chart of Embodiment 1 of the client authentication method according to the present invention. Such as figure 1 As shown, this embodiment includes:
[0031] Step S102: receiving a dynamic authentication request including an IMS user ID;
[0032] Step S104: Generate a random dynamic password for the valid dynamic authentication request and send it to the IMS user; for example, verify whether the IMS user ID contained in the dynamic authentication request is legal;
[0033] Step S106: Receive the dynamic password input by the IMS user, and search for the corresponding static password for the successfully authenticated user;
[0034] Step S108: Use the static password to perform subsequent authentication of each network element of the IMS core network.
[0035] This embodiment aims at the combination of dynamic password authentication, a strong authentication method, and IMS users, and provides a reliable authentication method for the user side to ...
Embodiment 2
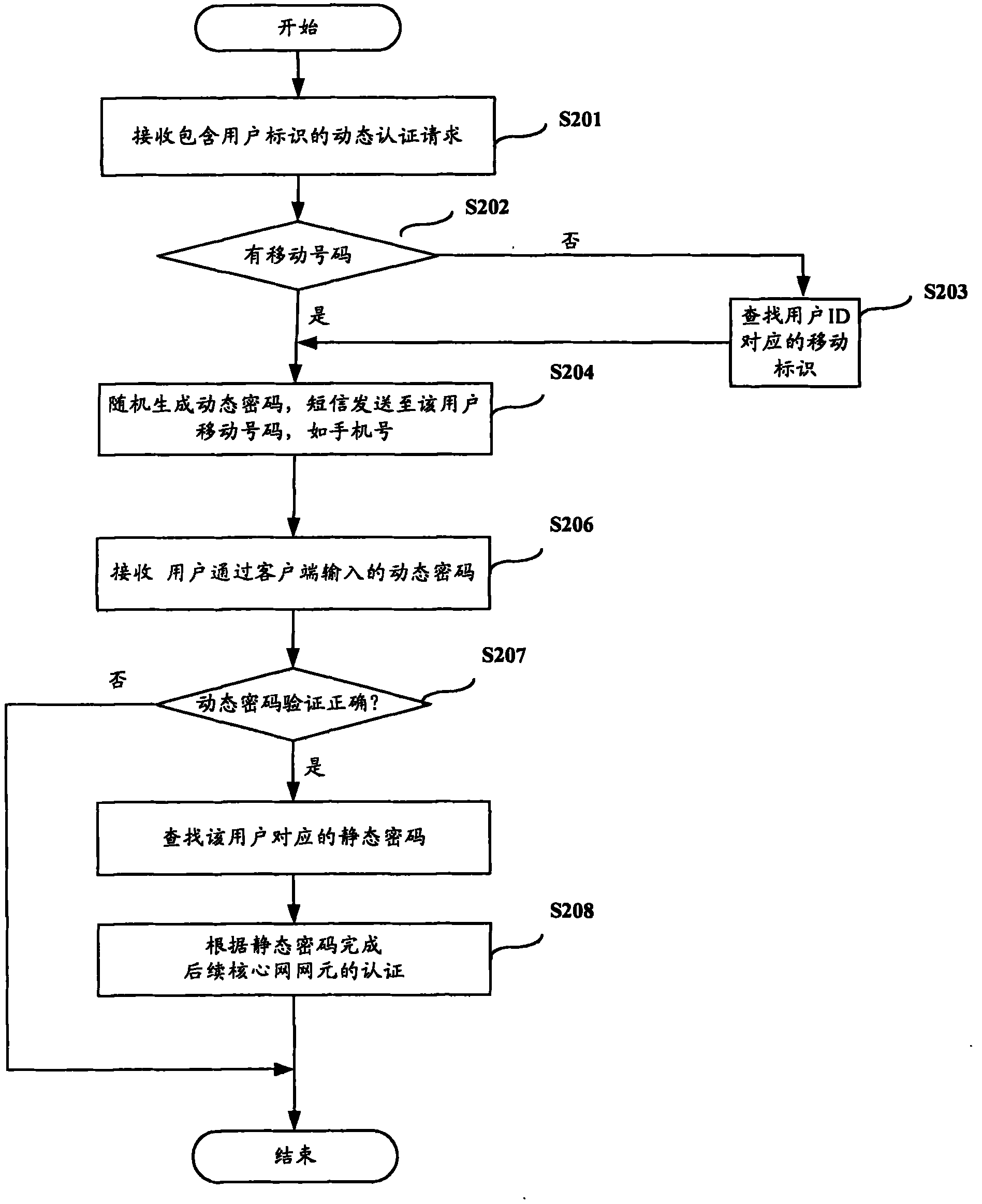
[0037] figure 2 It is a flow chart of Embodiment 2 of the client authentication method according to the present invention. Such as figure 2 As shown, this embodiment includes:
[0038] Step S201: Receive the dynamic authentication request containing the user ID, and perform the following steps on the verified legal authentication request, otherwise, the dynamic authentication requester "illegal user" can be returned directly;
[0039] Step S202: Determine the type of the user identifier, such as: the user's identity identifier (user ID), or the user's mobile number, such as a mobile phone number. If it is a mobile number, then step S204 is performed, and if it is a user ID number, then step S203;
[0040] Step S203: Search for the mobile terminal identification (such as: mobile phone number) corresponding to the user ID. Generally, the corresponding relationship between users and their identifications will be stored, as shown in Table 1
[0041] Table 1 Correspondence be...
Embodiment 3
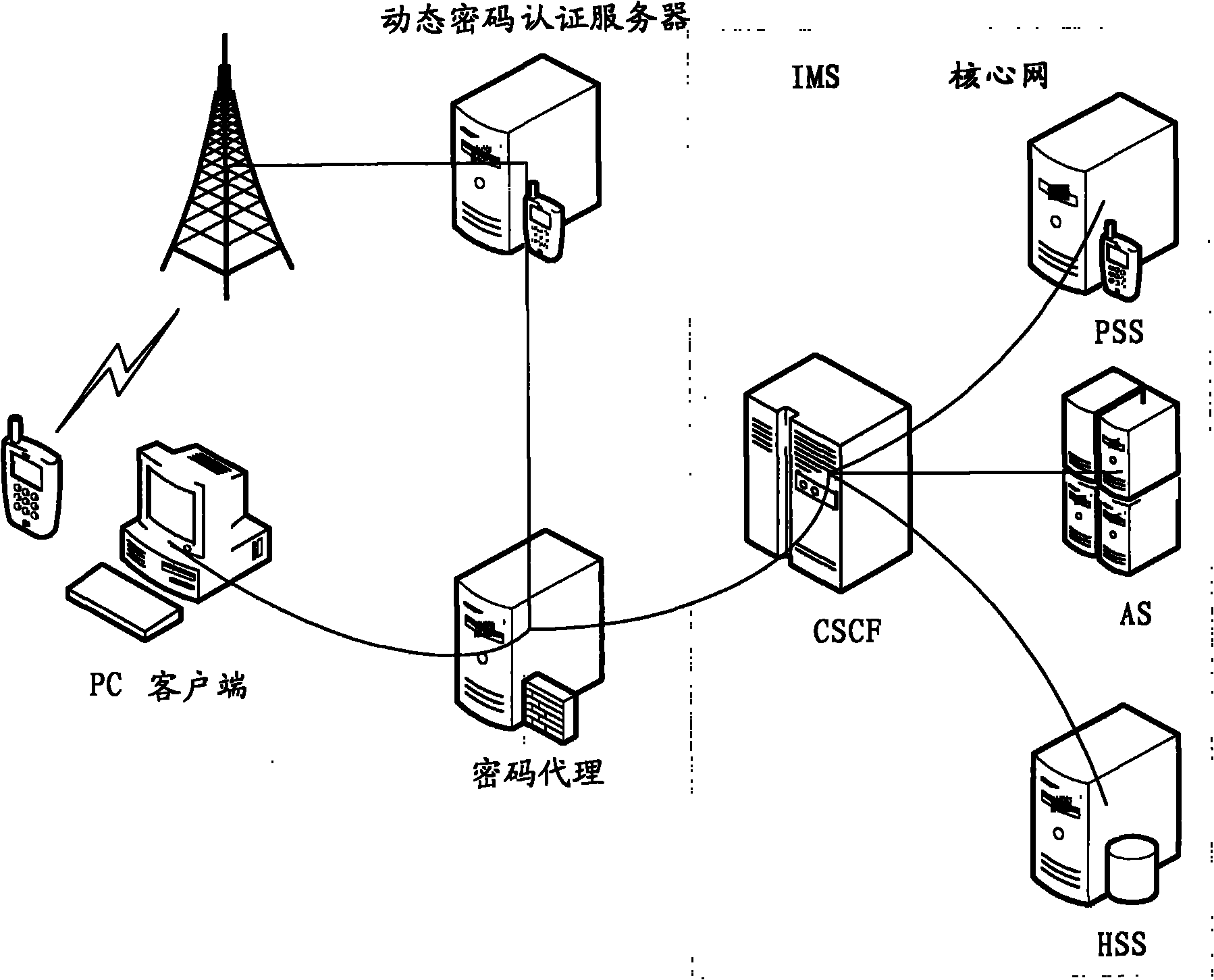
[0050] according to the above figure 1 and figure 2 According to the description of the method embodiment, those skilled in the art know that the strong authentication method of dynamic password authentication is used to assist in completing the IMS client authentication login. The user does not need to remember the static password, and only needs to enter the received dynamic password when logging in. However, in actual application, when the dynamic authentication method is adopted, the following problems may be encountered:
[0051]At present, when an IMS user logs in, although the user only needs to enter a password once, the IMS core device side needs to complete such as home subscriber server (Home Subscriber Server, HSS for short), application server (Application Server, AS for short), fixed network simulation service ( PSTN / ISDN Simulation Services (PSS for short) and other multiple network elements authentication and authentication, because these network elements all...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com