Security and privacy enhancements for security devices
a security device and privacy enhancement technology, applied in the field of authentication and key agreement (aka) procedures in communication systems, can solve the problems of not even being able to achieve standardization, not being able to change the standard in time, and unable to achieve standardization efforts, etc., to achieve enhanced security and/or privacy, the effect of enhancing security and/or privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] Throughout the drawings, the same reference characters will be used for corresponding or similar elements.
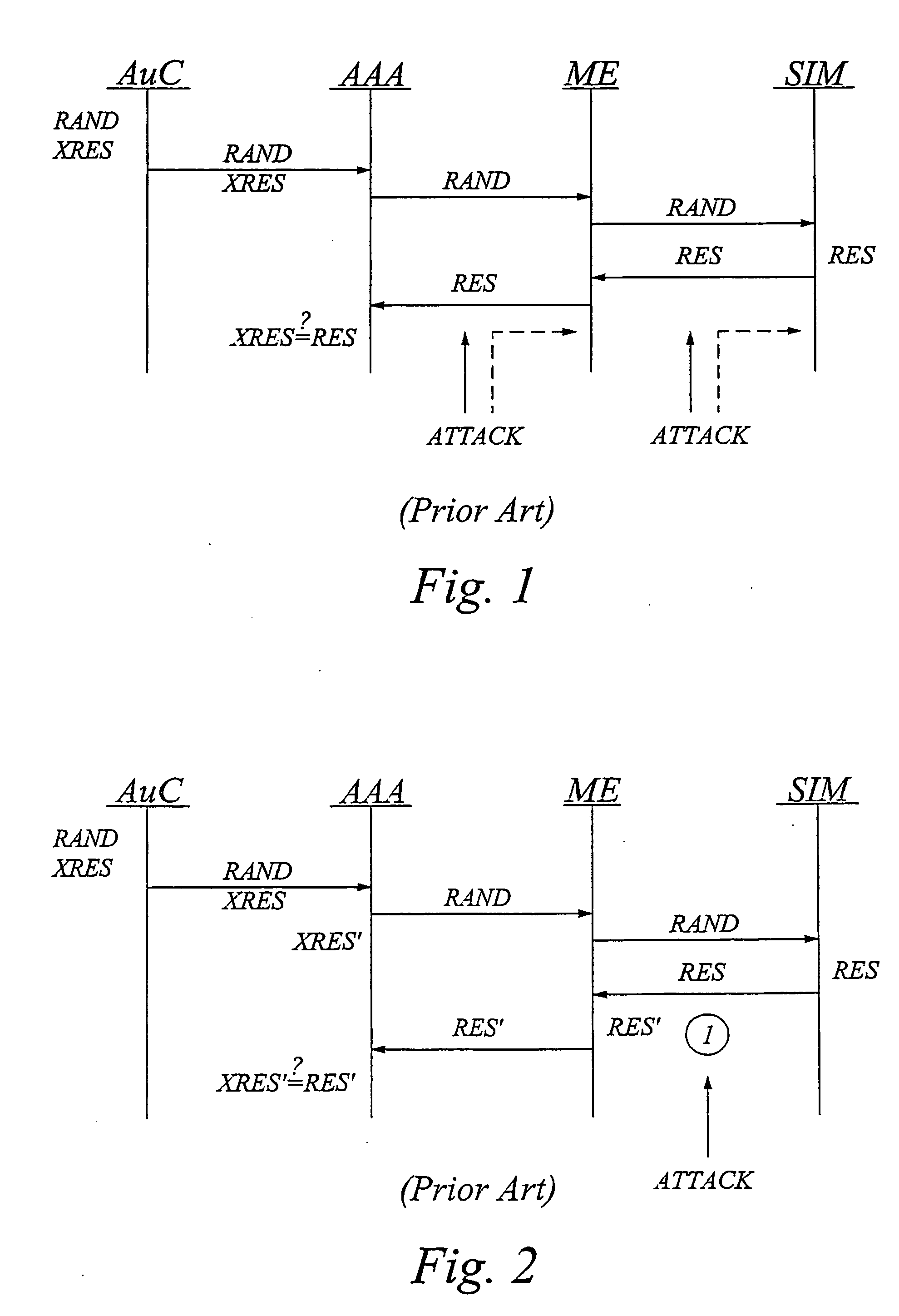
[0054] As will be described below, it is possible to obtain the above and other security goals in a way that can be used regardless of what algorithms that are currently implemented on the security device.
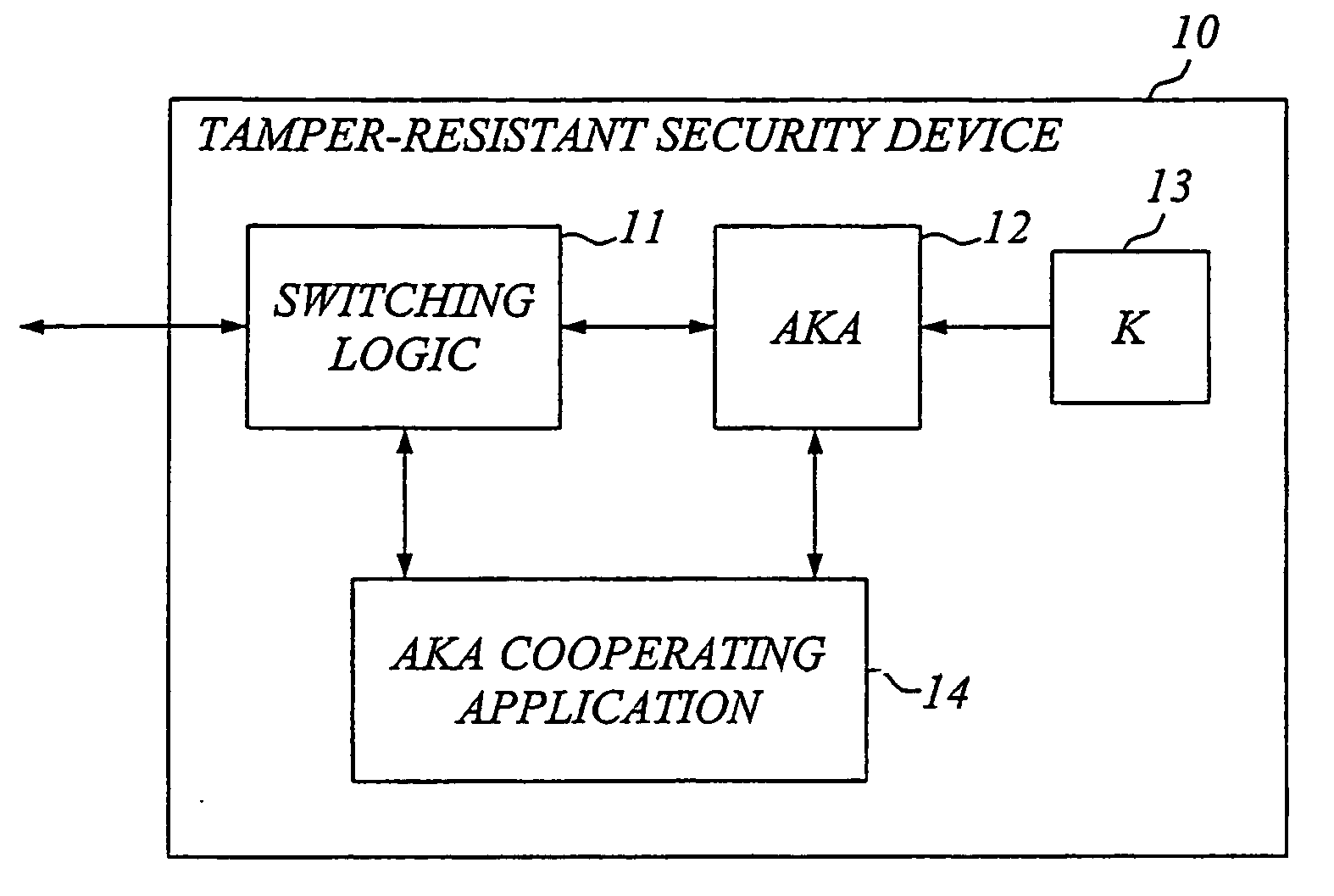
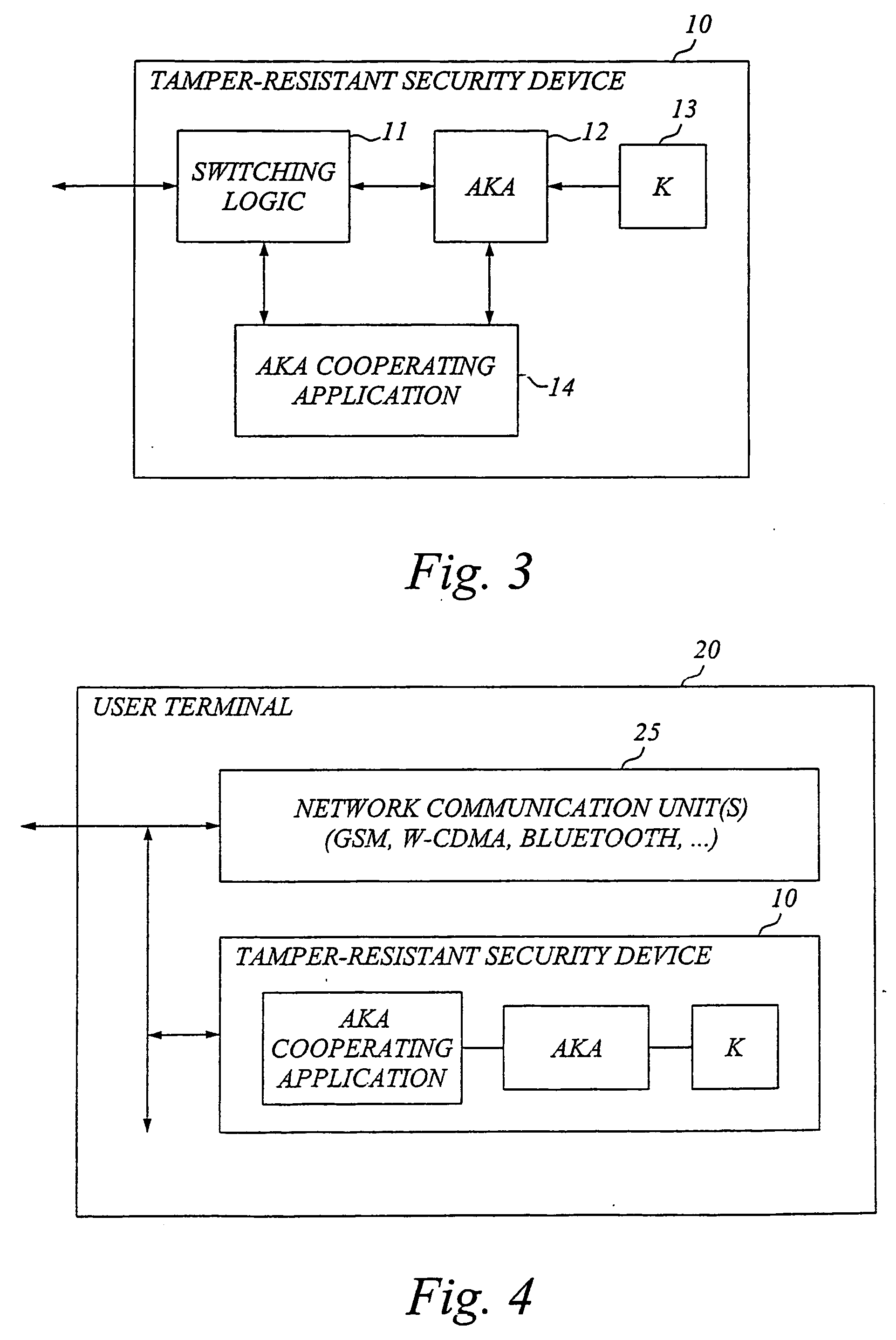
[0055] The basic idea according to a main aspect of the invention is to provide an application adapted for cooperating with the AKA module as well as an interface, for example an API or similar interface, between the AKA module and the application, as schematically illustrated in FIG. 3.
[0056]FIG. 3 illustrates an exemplary embodiment of a tamper-resistant security device according to the invention. The security device 10 basically comprises switching logic 11, an AKA module 12, securely stored user credentials 13 including at least a security key K (possibly also user identities and pseudonyms), an application 14 adapted for cooperating with the AKA module, and a mor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com