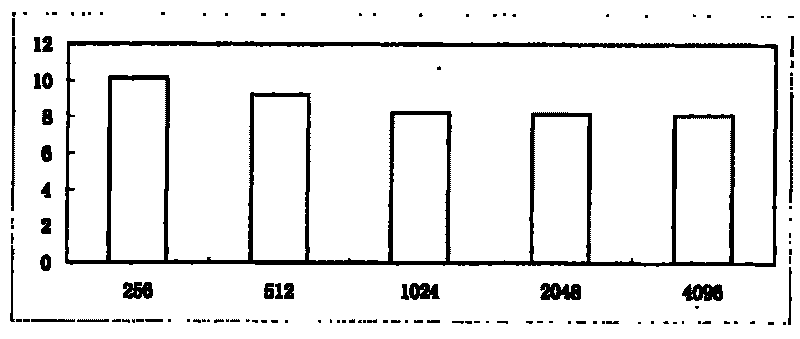
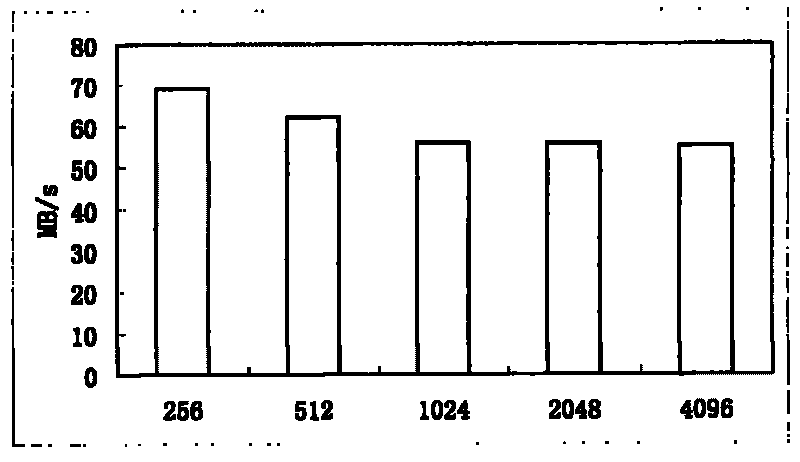
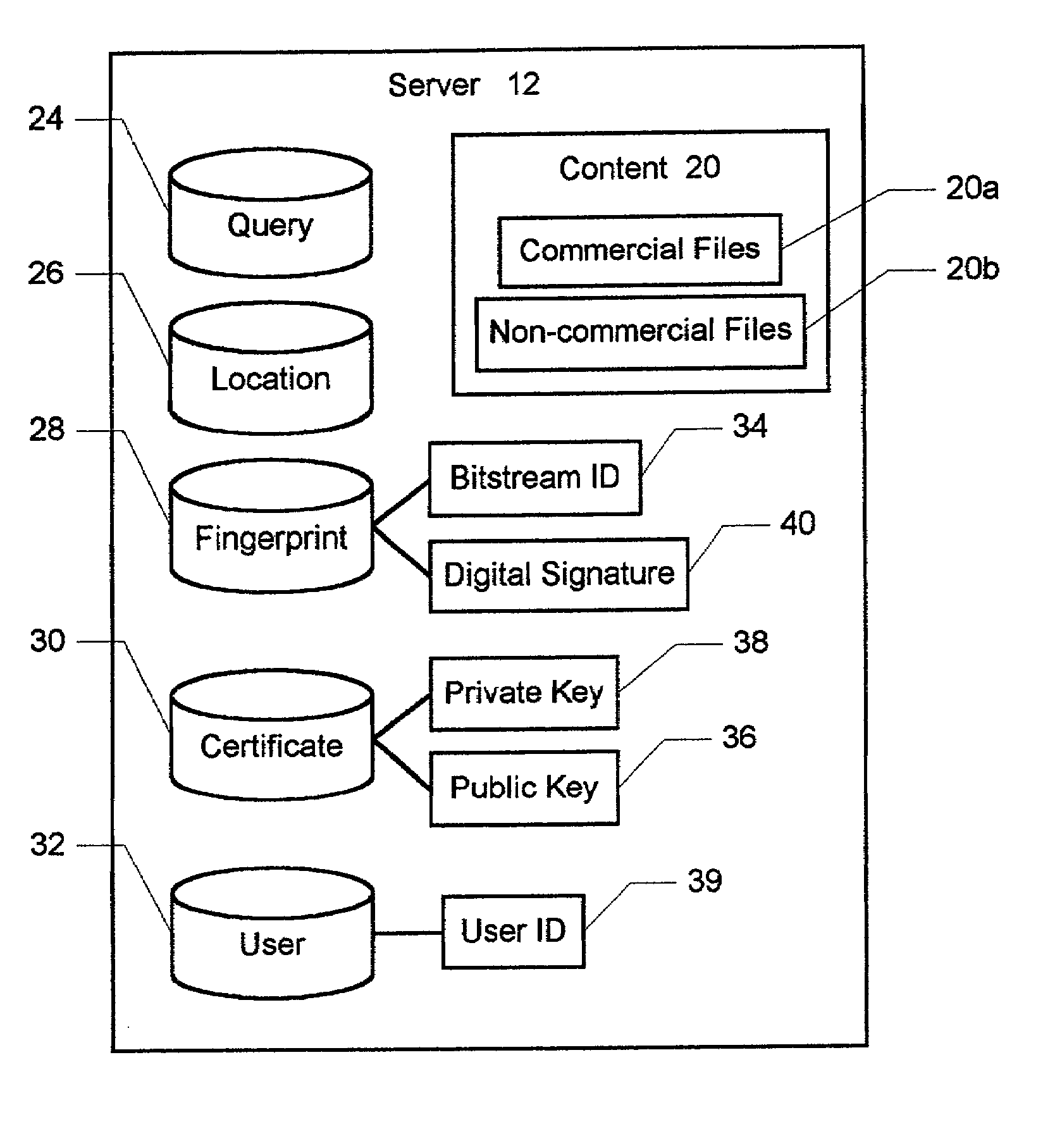
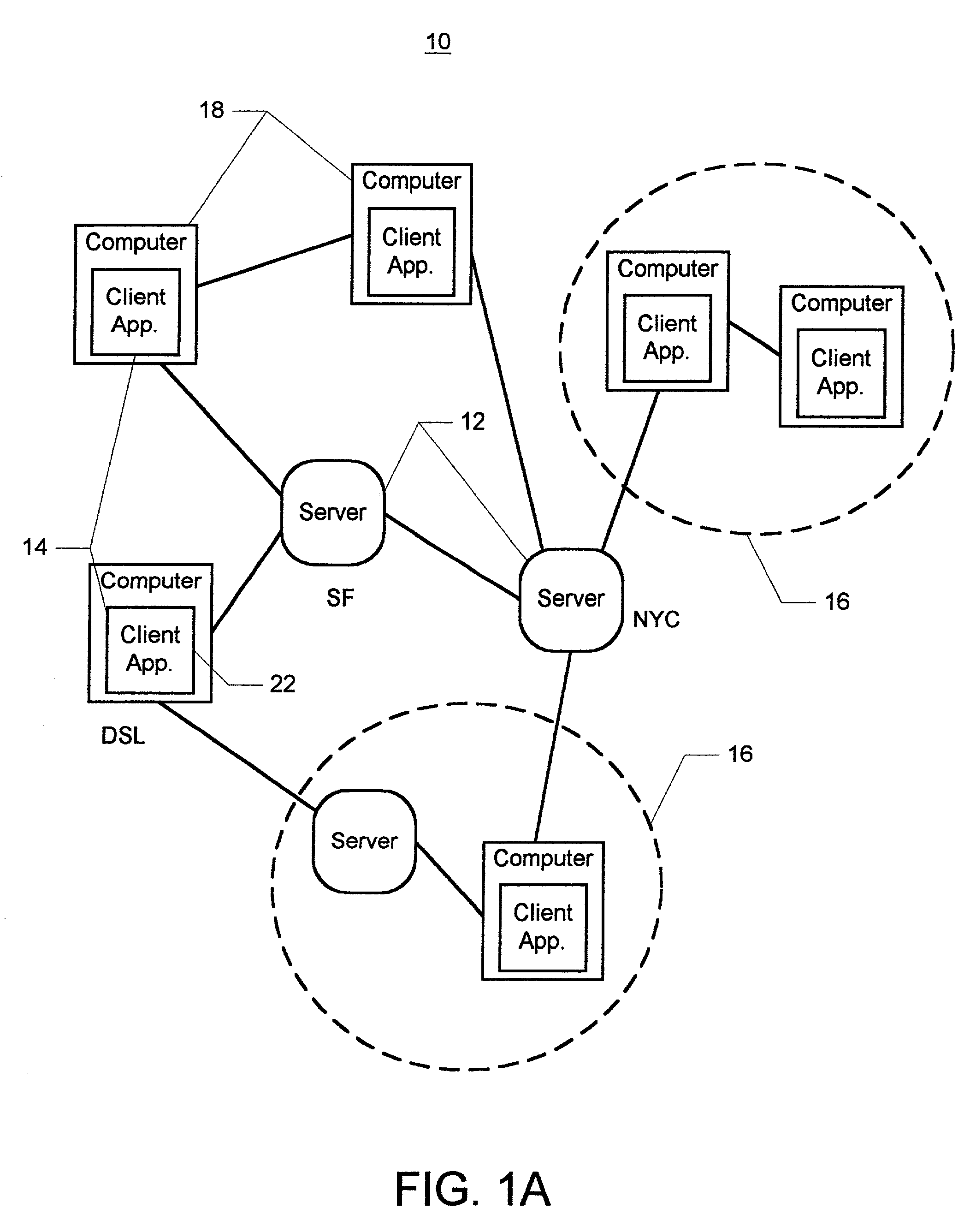
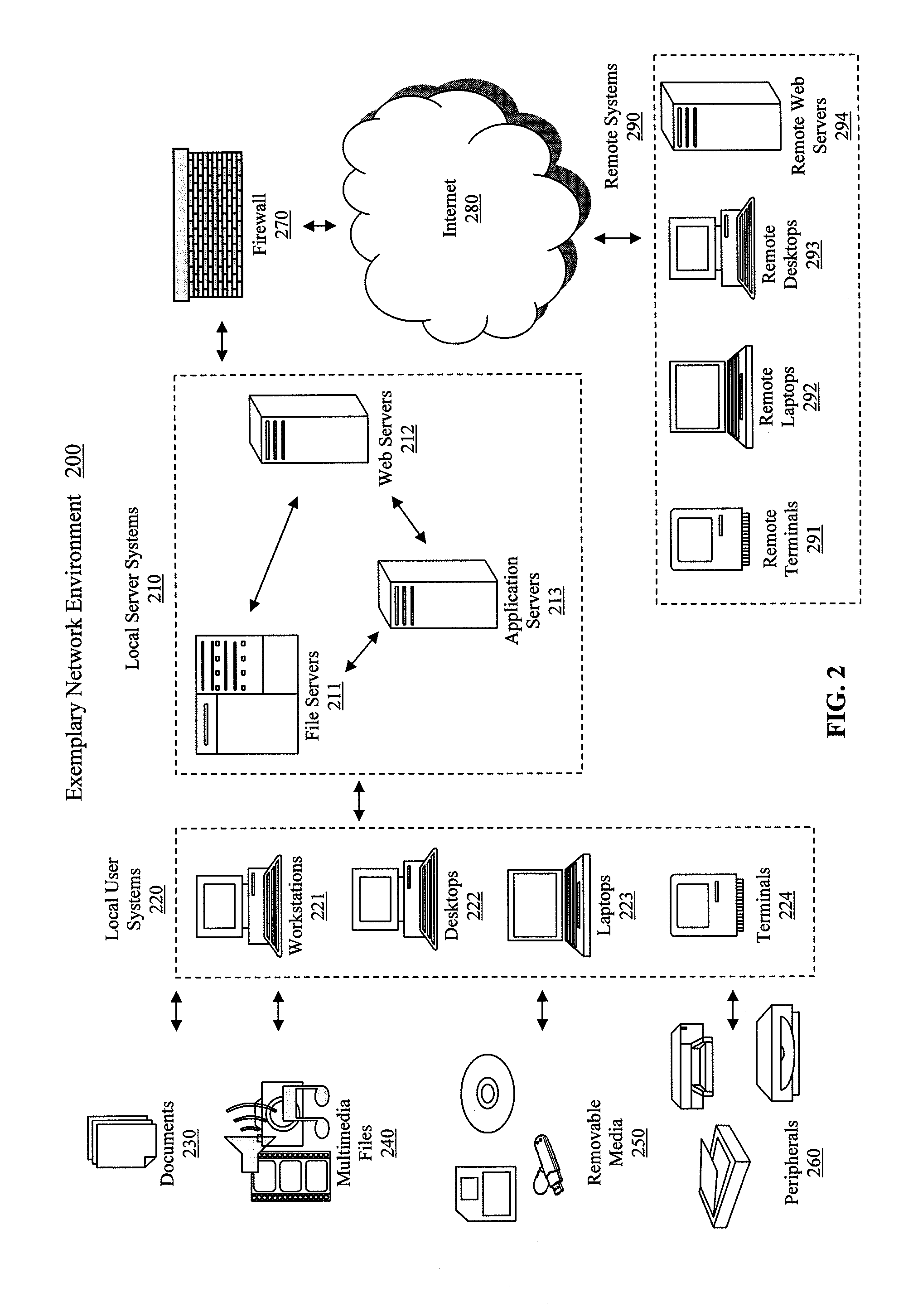
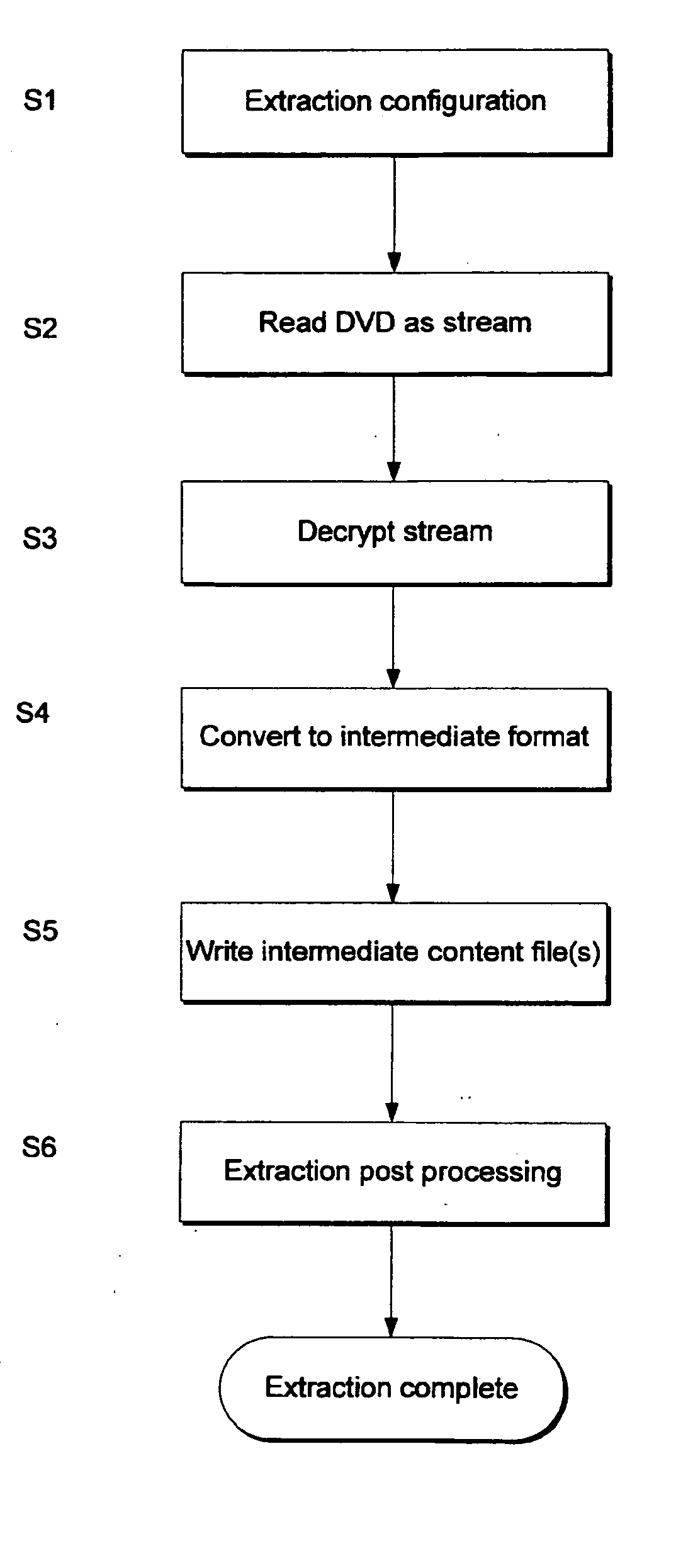
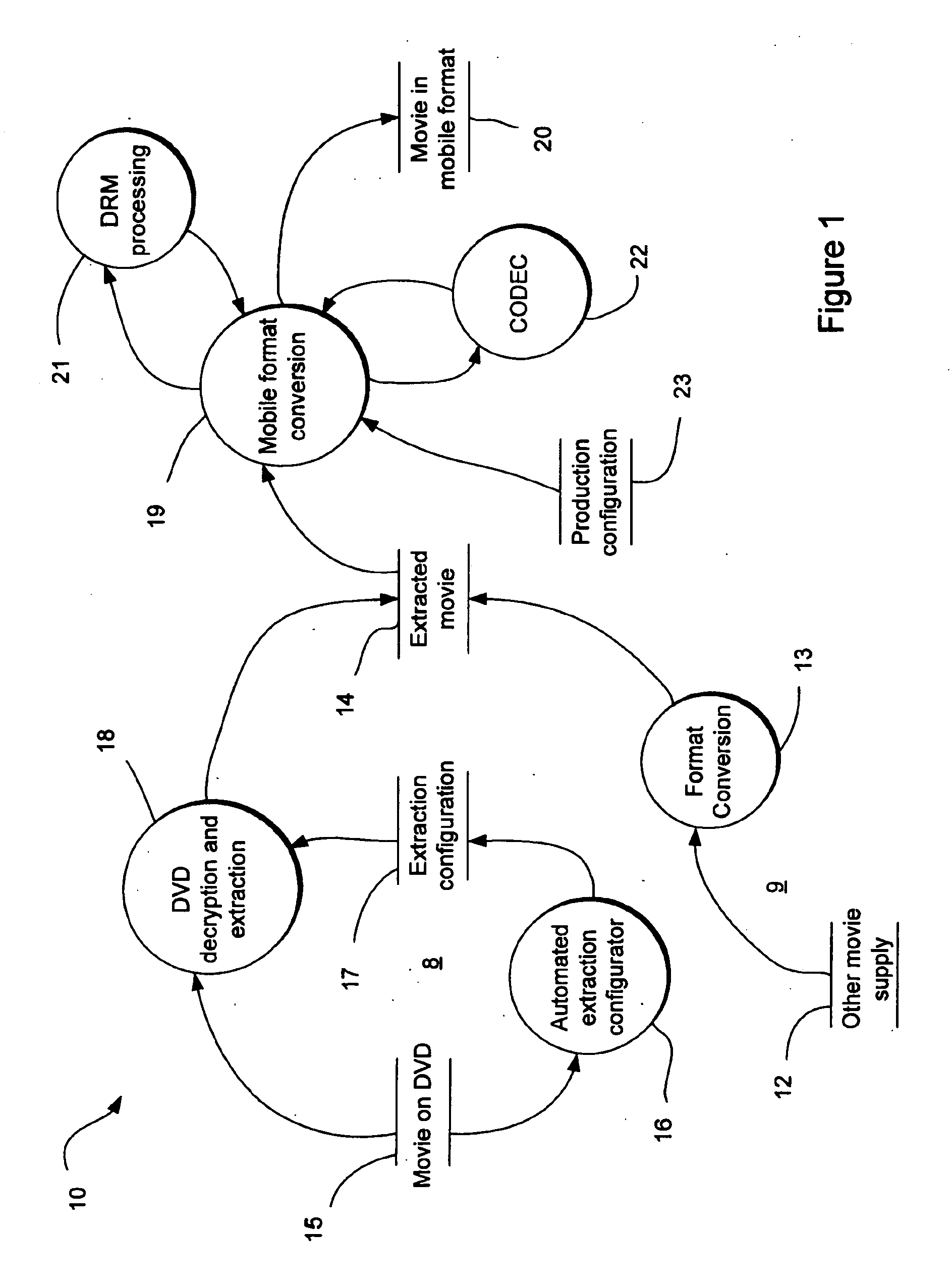
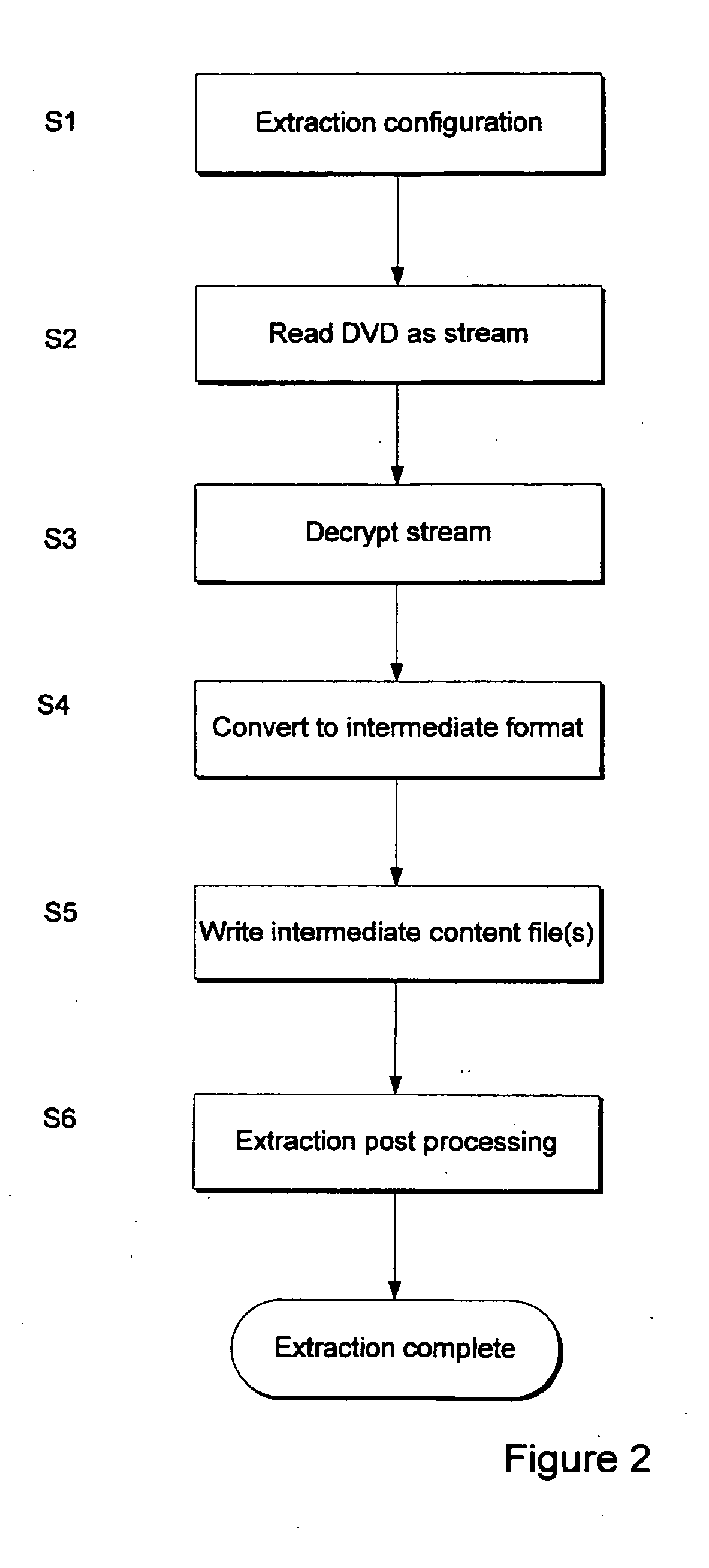
Patents
Literature
498 results about "Digital fingerprint" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
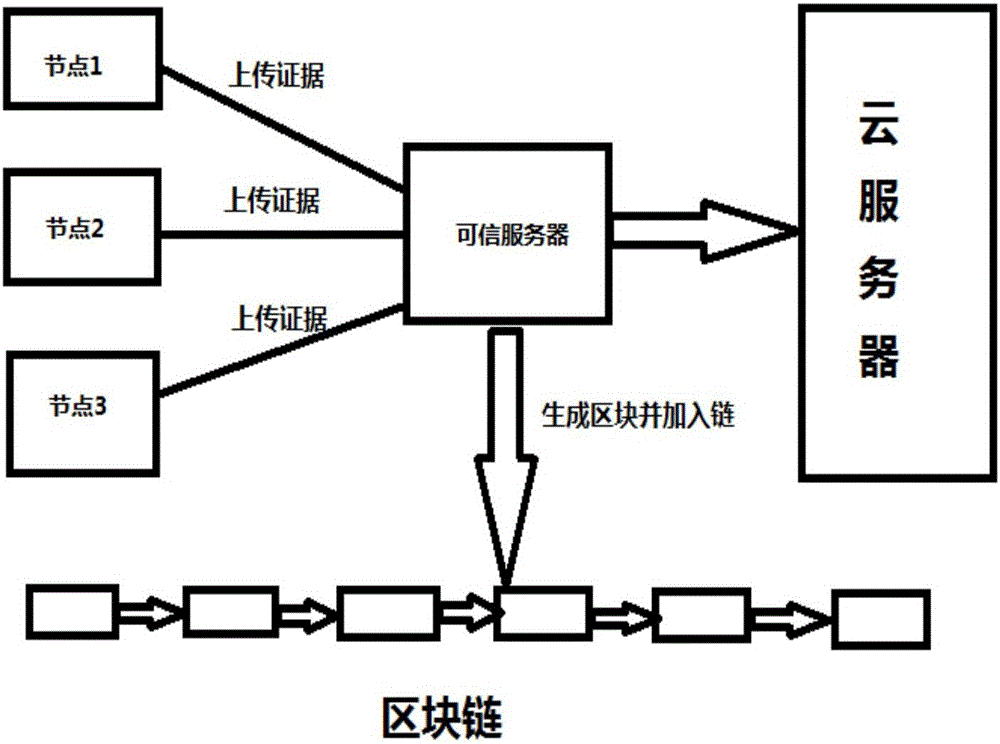
Block chain-based evidence preservation method and apparatus
InactiveCN105975868ASolve bulkyGuarantee authenticityDigital data protectionThird partyCloud storage
The invention discloses a blockchain-based evidence preservation method, which is applied to a network system with master nodes and slave nodes, including: each slave node performs identity verification to the master node, and assigns a pair of secret keys to the slave nodes that pass the identity verification. key, and write the registration information of the slave node into the blockchain; after the master node responds to the corresponding slave node with the evidence upload request received, the slave node signs the electronic evidence to be uploaded with the corresponding private key and sends To the master node; according to the registration information of each slave node in the blockchain, verify the legitimacy of the slave node and the authenticity of the signature of the corresponding electronic evidence, store the verified electronic evidence to the cloud storage server and generate the corresponding digital fingerprint, Write the generated digital fingerprint into the blockchain along with the corresponding timestamp. The evidence preservation method of the present invention has strong real-time performance, can save a lot of time, and does not require the participation of a third-party notary organization, thereby saving social resources.
Owner:HANGZHOU YUNXIANG NETWORK TECH
Watermarking with random zero-mean patches for printer tracking
InactiveUS6556688B1Efficient detectionUser identity/authority verificationCharacter and pattern recognitionVirtual cellControl signal
A steganographic method embeds hidden information like digital watermarks and digital fingerprints into an image by applying one or more zero-mean patches to a digital signal that conveys the image. Each zero-mean patch comprises elements having an average value substantially equal to zero. A printer tracking system is implemented by selecting a plurality of zero-mean patches according to a string of bits representing a printer serial number, and modifying printer control signals to embed the plurality of patches in each of a number of virtual cells within the image to be printed. The offset of the virtual cells with respect to the boundaries of the image and the location of the patches within each virtual cell are established in pseudo-random fashion. The printer tracking system further includes a technique for subsequently detecting the printer serial number by scanning the printed image and running a detection algorithm on the scanned data to recover the string of bits embedded in the zero-mean patches.
Owner:SEIKO EPSON CORP
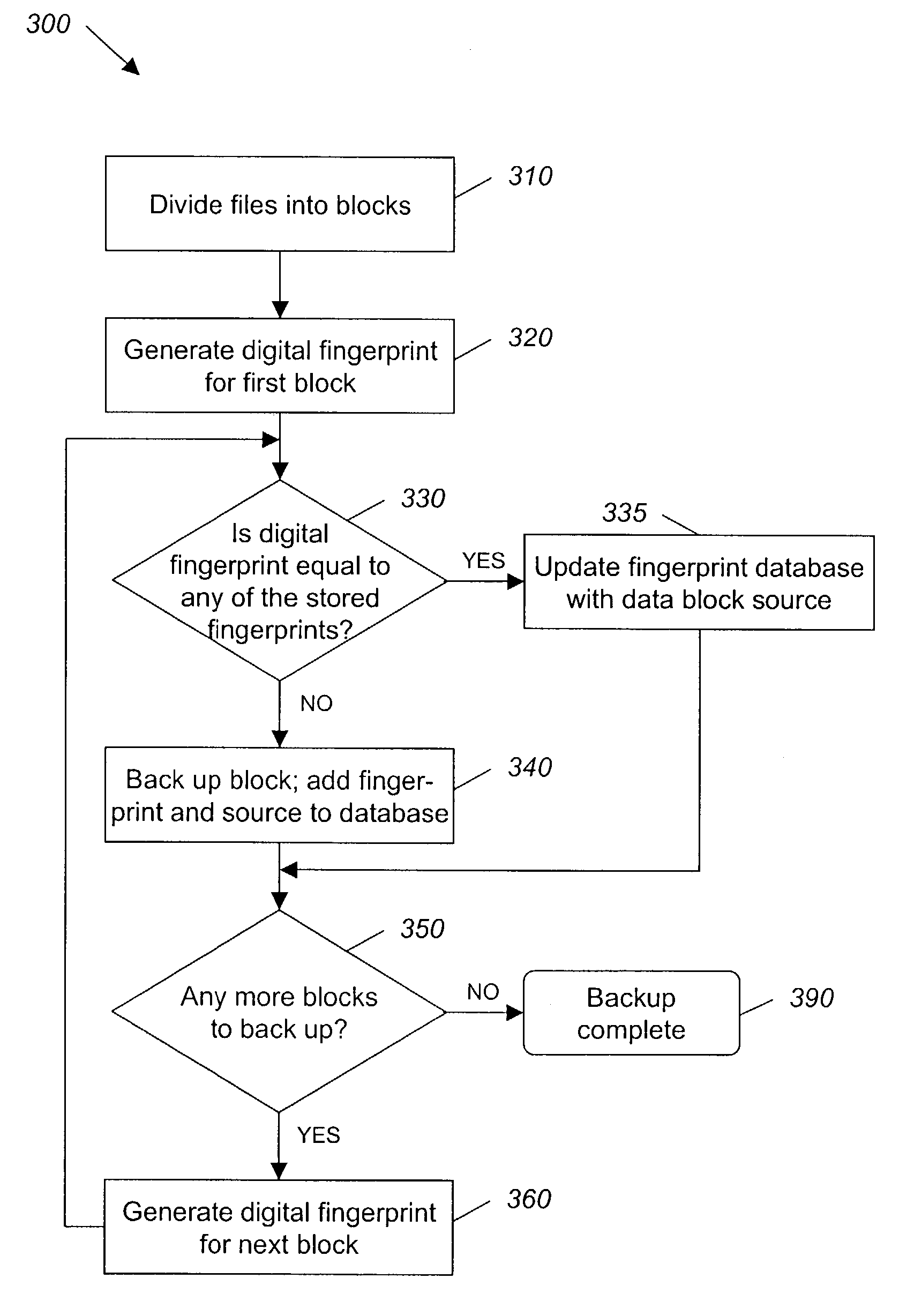
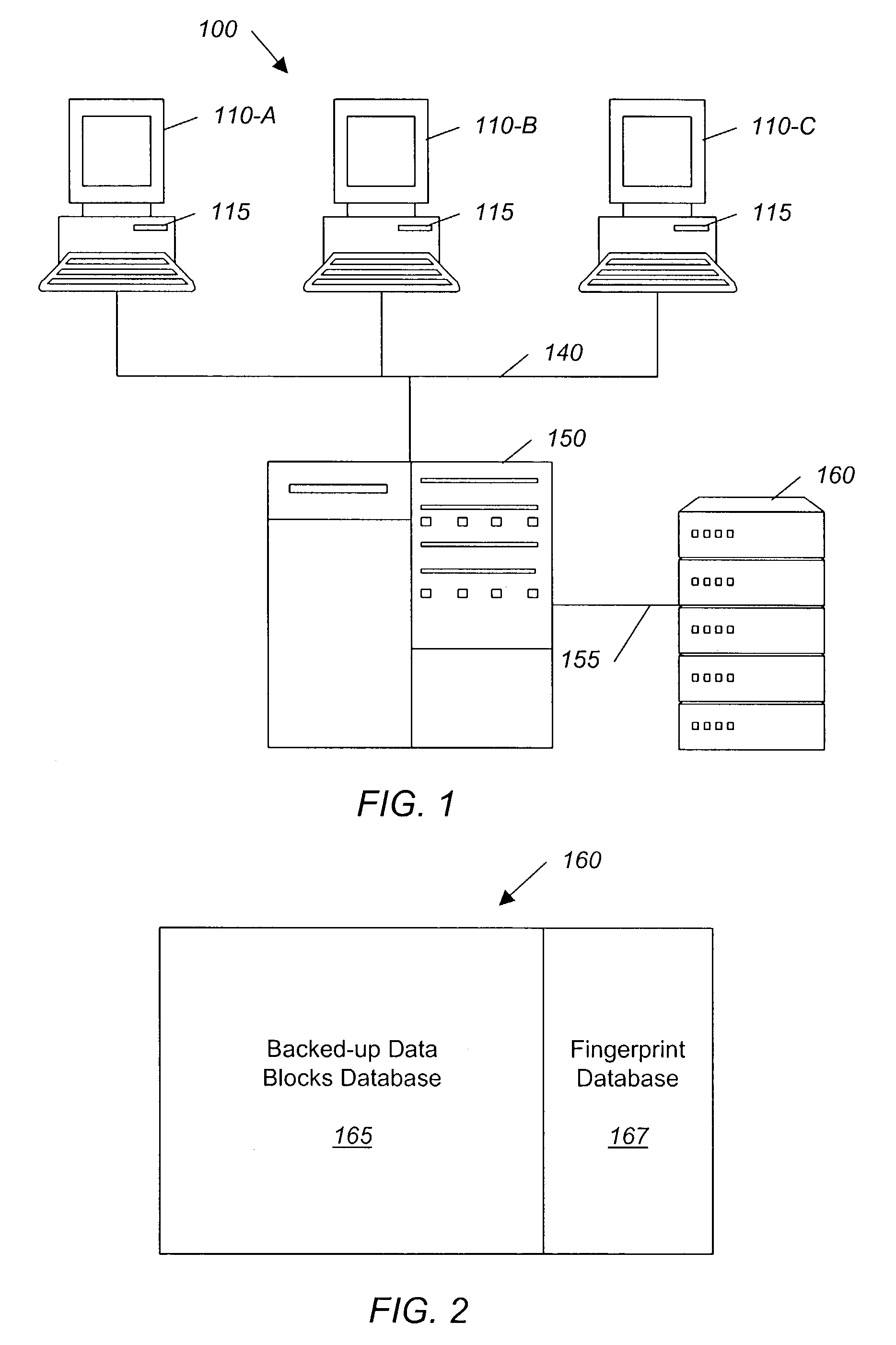
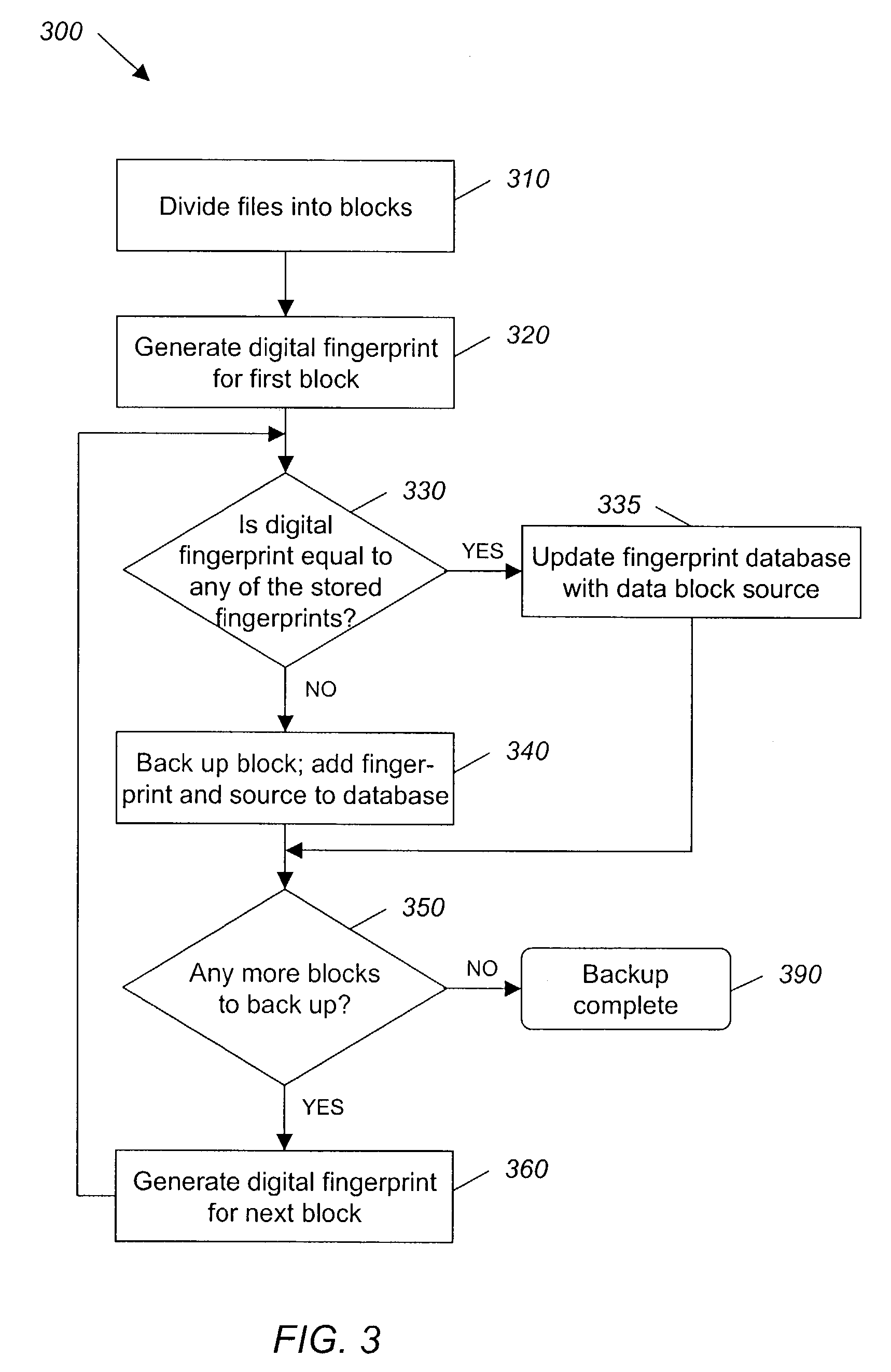
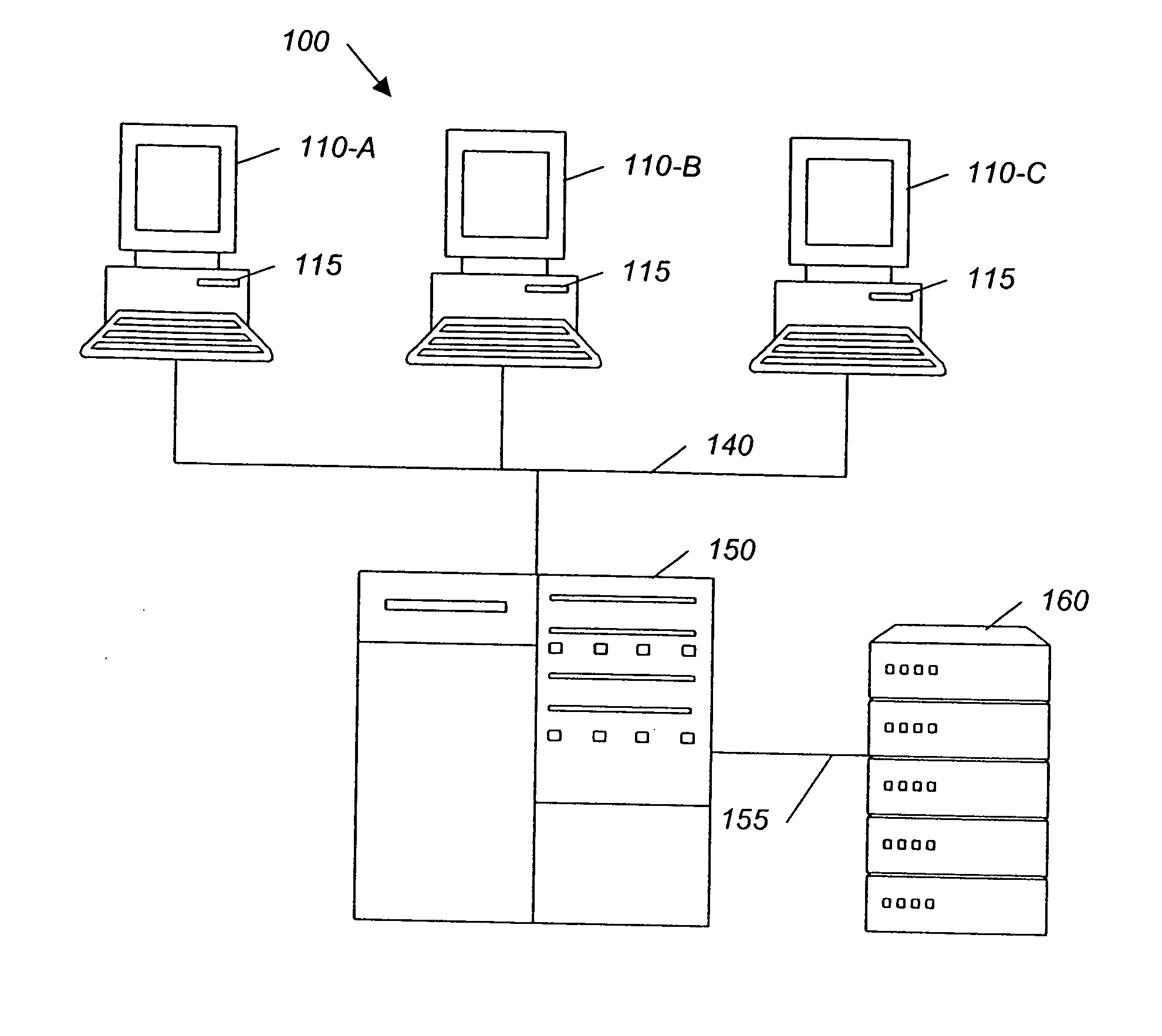
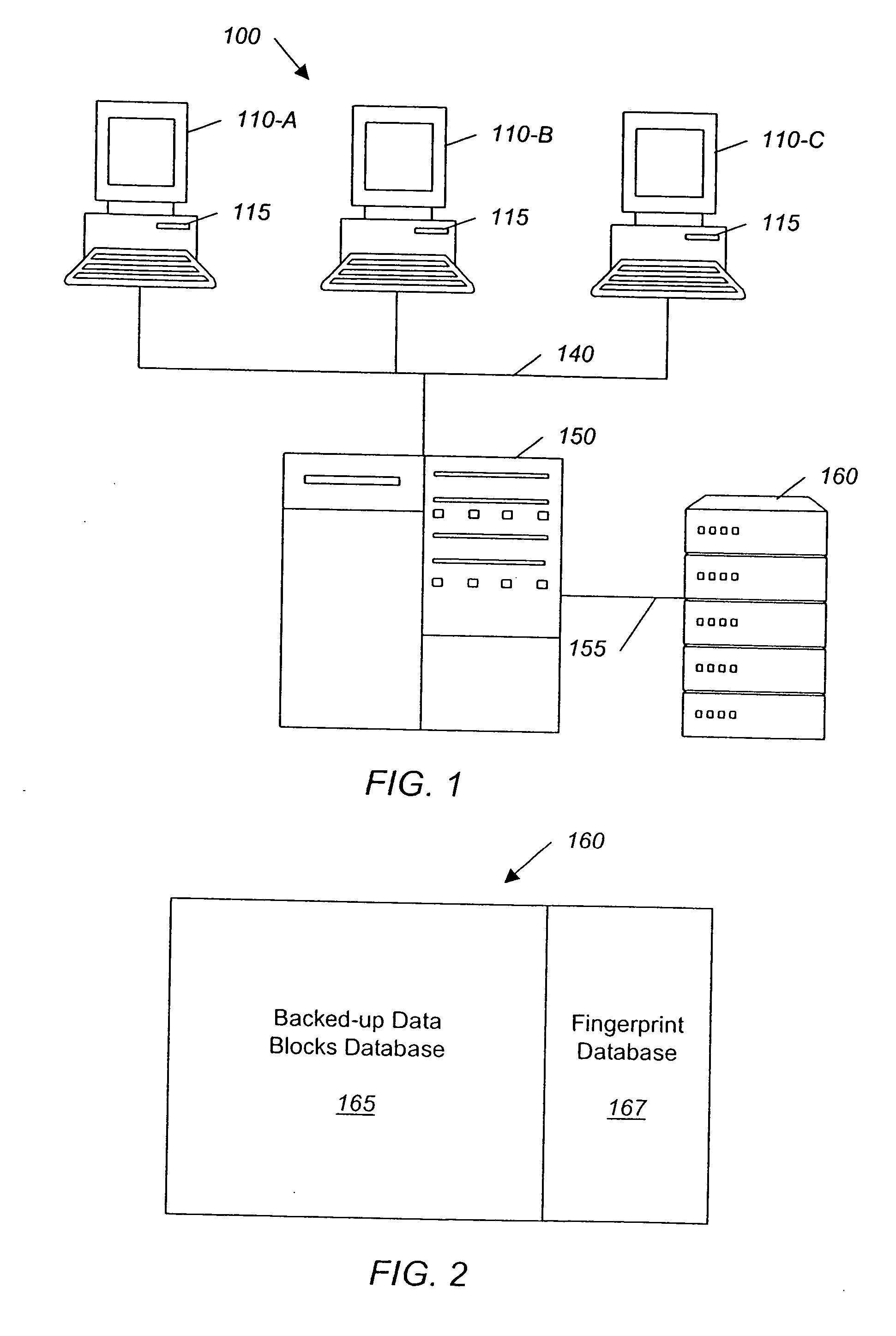
System and method for backing up data
ActiveUS7055008B2Avoid inefficiencyInefficiency of the Shnelvar patent can be avoidedCamera focusing arrangementPayment architectureSoftware licenseData content
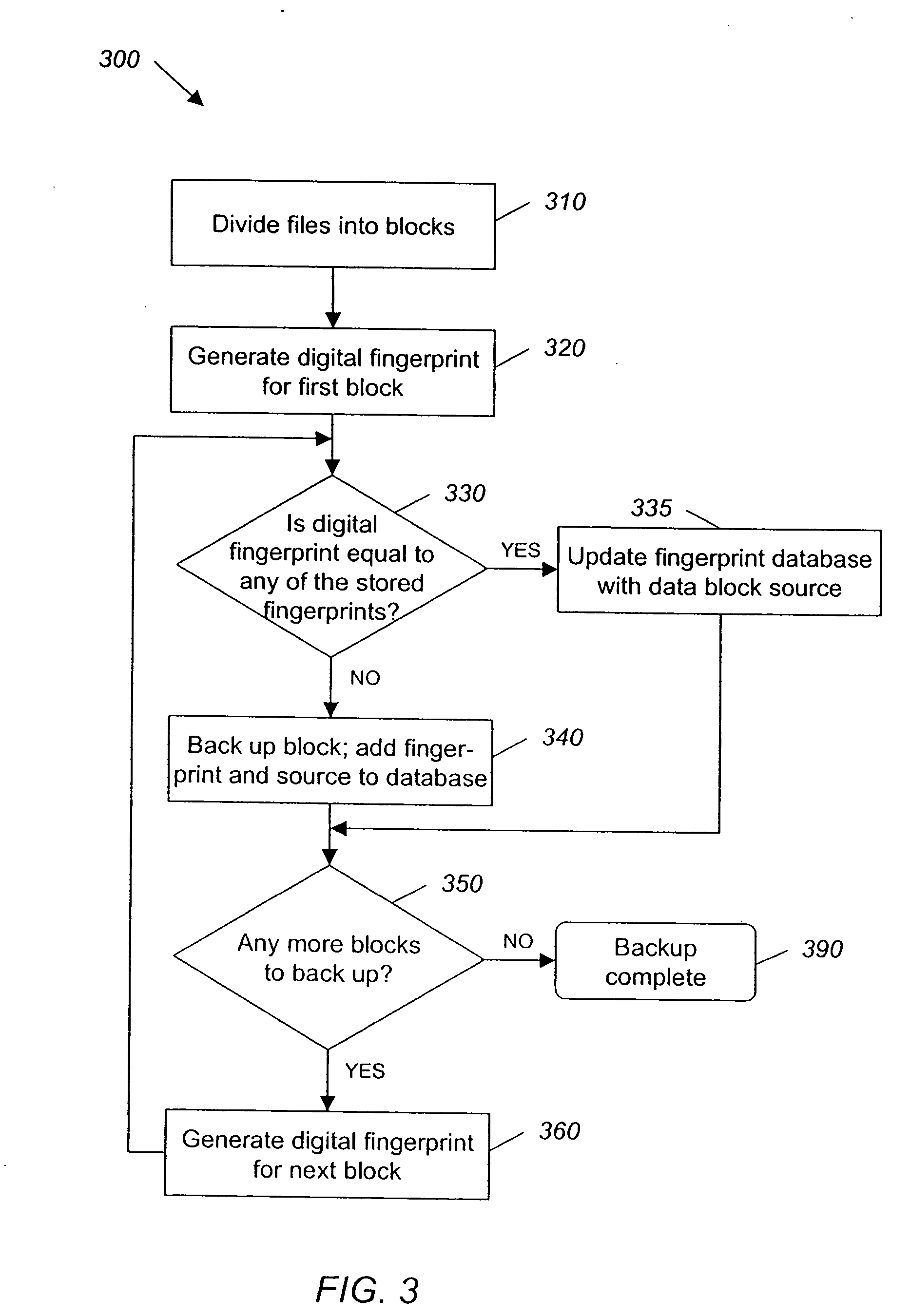
A hash-optimized backup system and method takes data blocks and generates a probabilistically unique digital fingerprint of the content of each data block using a substantially collision-free algorithm. The process compares the generated fingerprint to a database of stored fingerprints and, if the generated fingerprint matches a stored fingerprint, the data block is determined to already have been backed up, and therefore does not need to be backed up again. Only if the generated fingerprint does not match a stored fingerprint is the data block backed up, at which point the generated fingerprint is added to the database of stored fingerprints. Because the algorithm is substantially collision-free, there is no need to compare actual data content if there is a hash-value match. The process can also be used to audit software license compliance, inventory software, and detect computer-file tampering such as viruses and malware.
Owner:FALCONSTOR
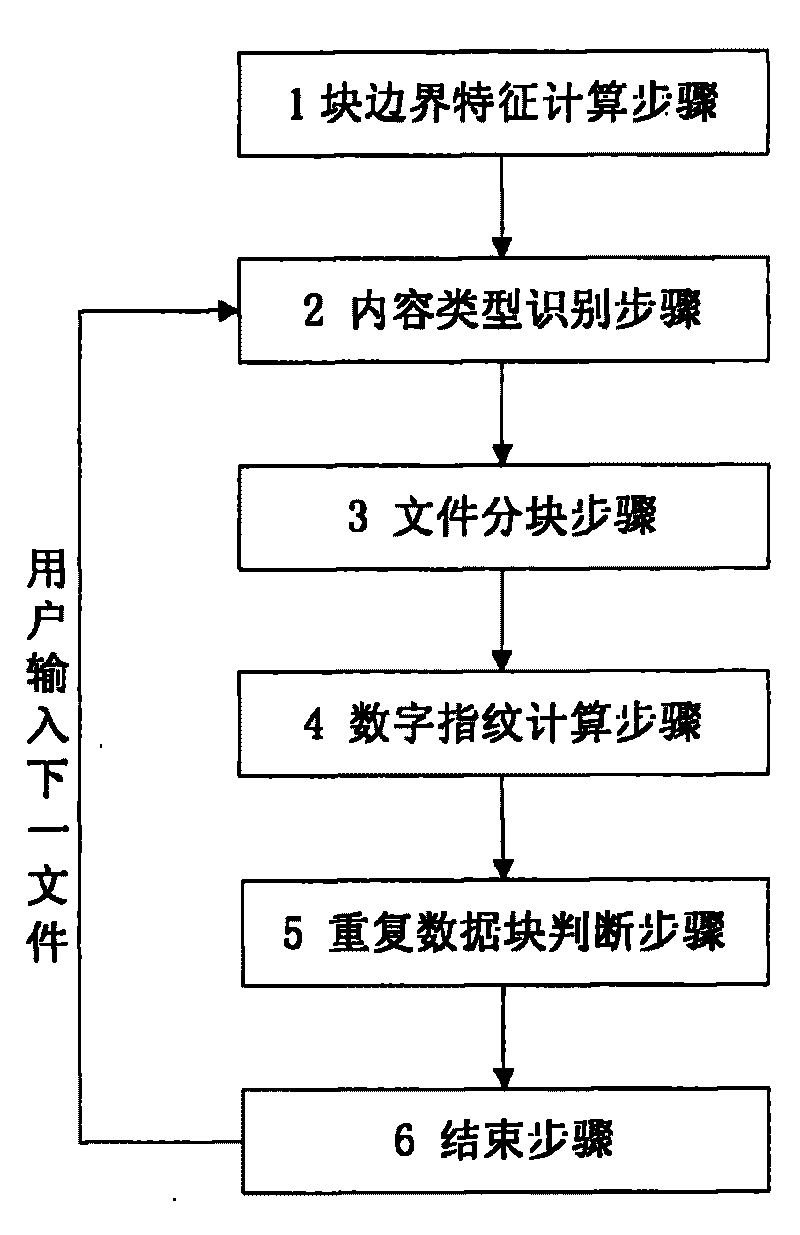
Replicated data deleting method based on file content types
InactiveCN101706825AAdd recognition stepsImprove performanceSpecial data processing applicationsRedundant operation error correctionDigital fingerprintContent type
The invention discloses a replicated data deleting method based on file content types, which belongs to the replicated data deleting method of computer data backup, is applicable to disk-based backup systems, and solves the problems that the existing replicated data deleting method is single in block strategies and can not carry out optimization according to the file content types. The deleting method carries out a block boundary characteristic calculation step in advance, and then comprises the following steps sequentially: content type identification, file blocking, digital fingerprint calculation, replicated data block judgment and ending. The deleting method carries out classification on backup files based on content types, computes the optimal block boundary characteristic value aiming at every content type; and when the backup files are processed, the file content type identification step is added, and the block boundary characteristic is selected according to identification result, therefore, the overall effectiveness of the replicated data deleting method is improved when the complex backup files are processed.
Owner:HUAZHONG UNIV OF SCI & TECH
Method and system for providing a secure peer-to-peer file delivery network
InactiveUS7047406B2Utilizes bandwidth efficientlyEffective bandwidthUser identity/authority verificationUnauthorized memory use protectionPublic networkClient-side
A method and system for electronically delivering files over a public network is disclosed. The network includes a plurality of computers including at least one server node and multiple client nodes. In a first aspect of the present invention, the method and system enable secure and reliable peer-to-peer file sharing between two client nodes. First, a digital fingerprint is generated and associated with a file in response to the file being selected for publication on a first client node. An entry for the file is then added to a searchable index of shared files on the server node, and the fingerprint for the file is also stored on the server. In response to a second client selecting the file from the search list on the server node, the file is automatically transferred from the first client node directly to the second client node. The second client node then generates a new fingerprint for the file and compares with the new fingerprint with the fingerprint from the server node, thereby verifying the authenticity of the file and publisher. In a second aspect of the present invention, the method and system also enable subscription-based decentralized file downloads to the client nodes. First, the client nodes are allowed to subscribe with the server node to periodically receive copies of one of the files. To provide a current subscribing client node with the file, the geographically closest client node containing the file is located, and the file is transferred from the closest node directly to the current subscribing node, thereby efficiently utilizing bandwidth.
Owner:QURIO HLDG
Interactive TV data track synchronization system and method
InactiveUS20080089551A1Easy to buyCharacter and pattern recognitionTelevision systemsThe InternetMobile device
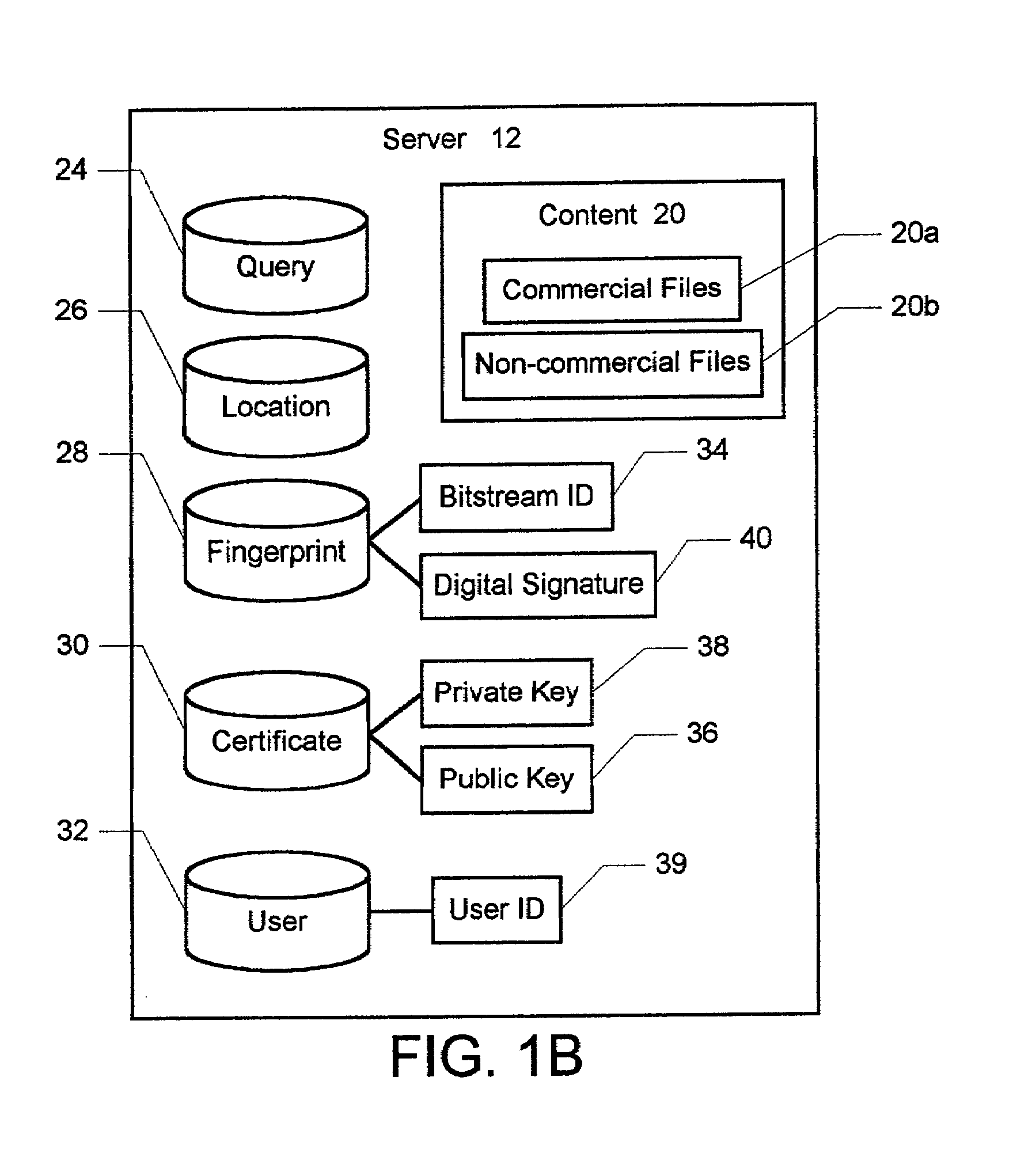
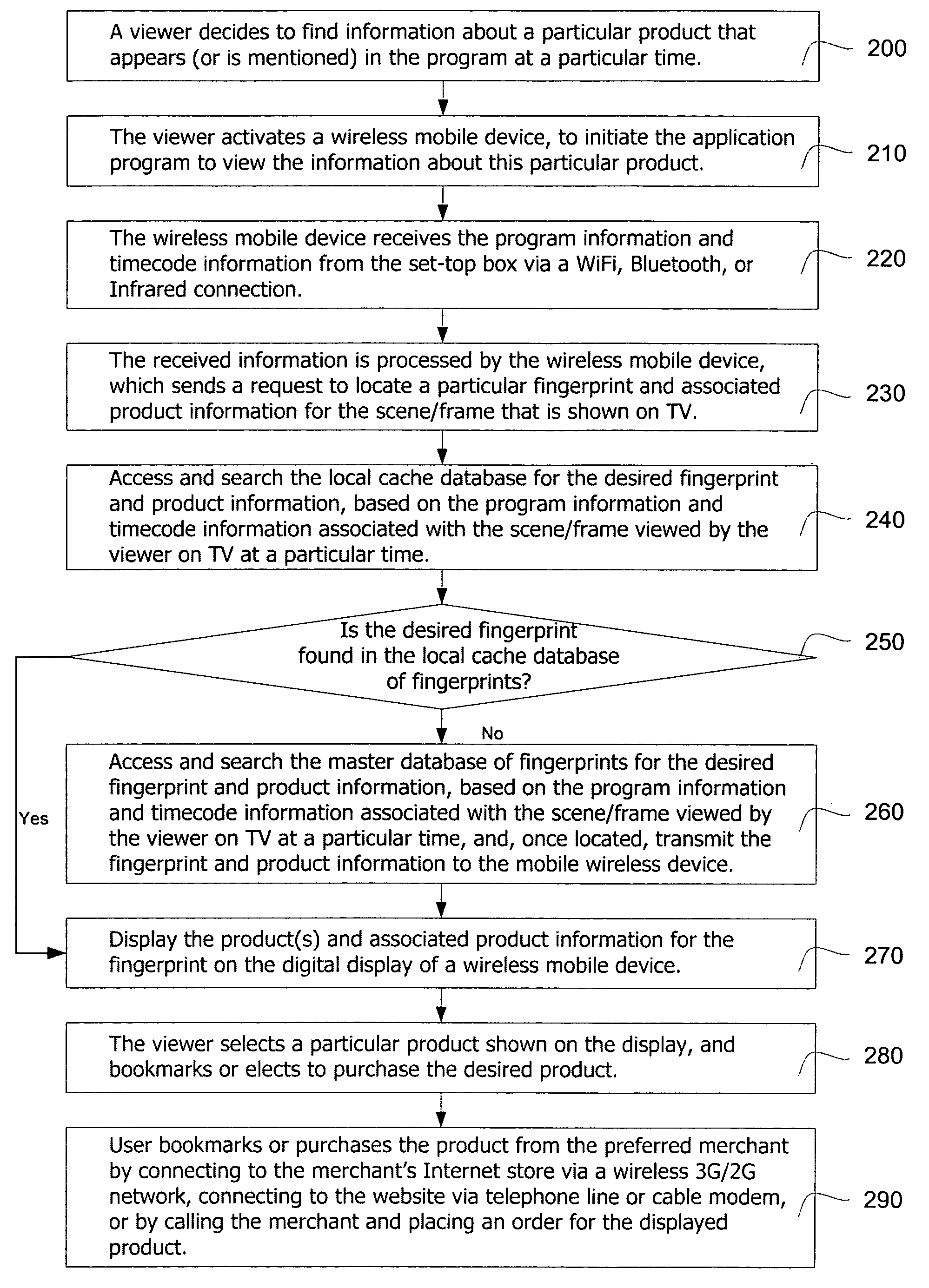
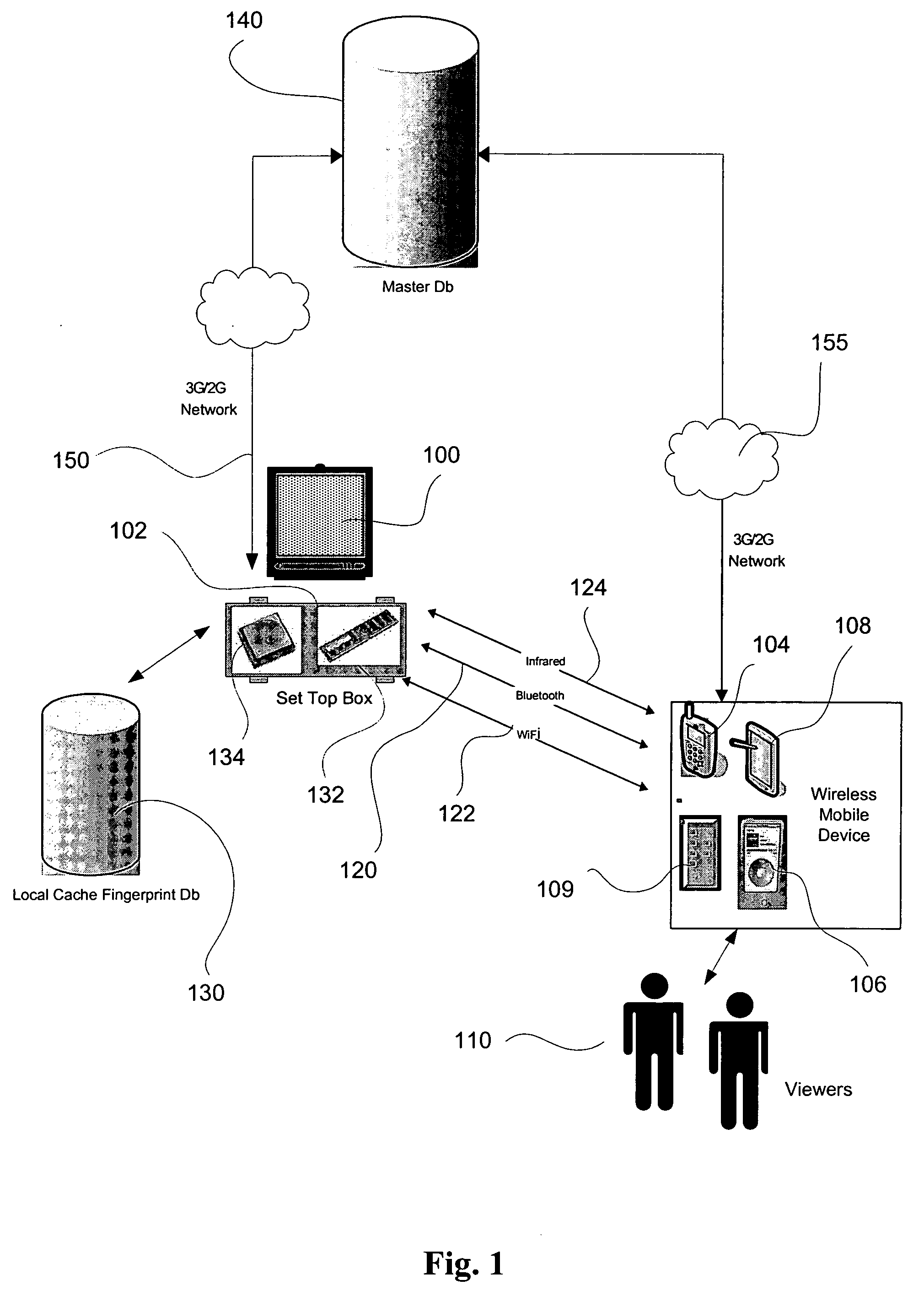
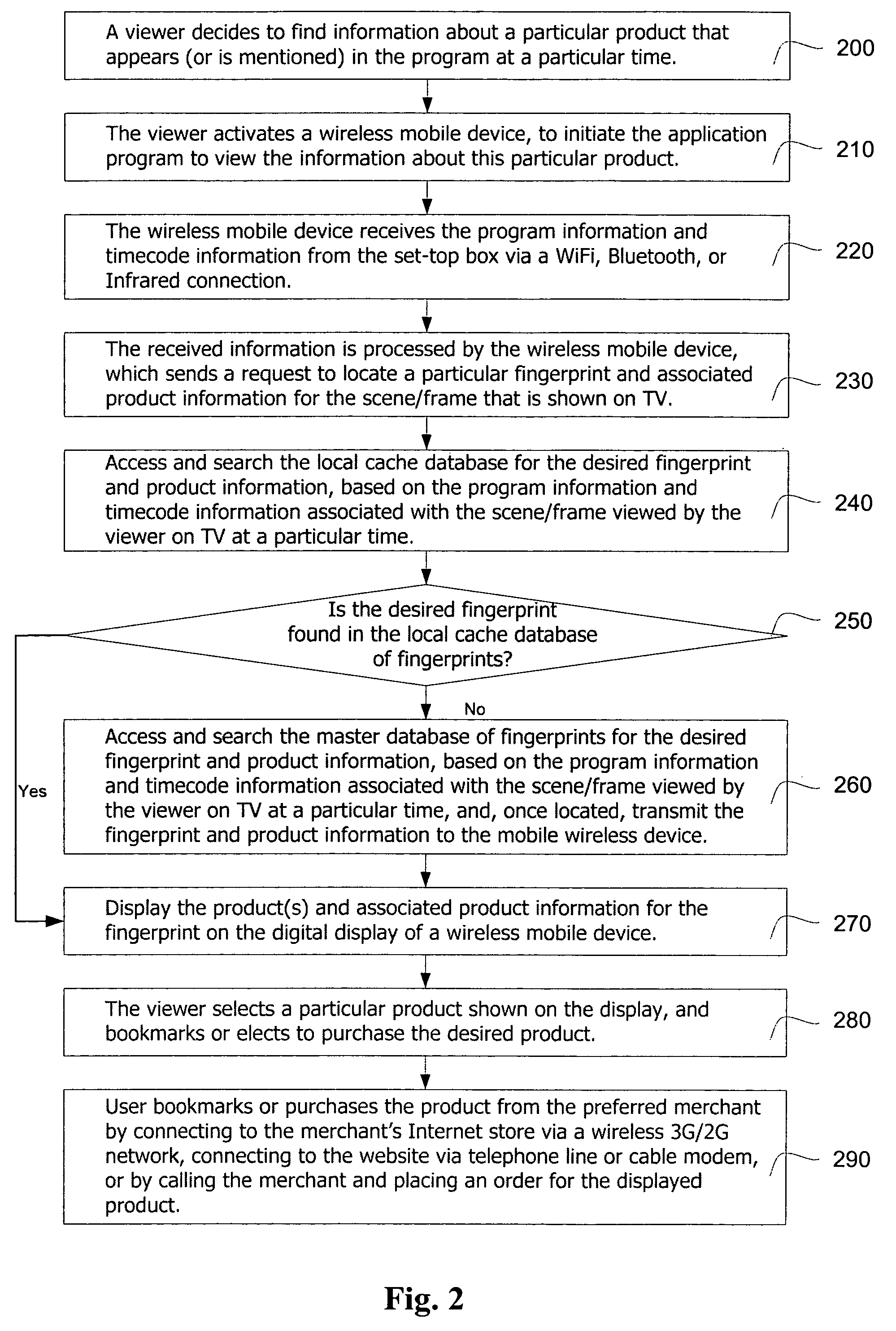
The present invention provides a system and method to allow product placement, i.e. showcasing products broadcast over TV, cable or similar media and to enable viewers to view, bookmark and purchase products placed within the program as they appear on the TV screen at a particular time. The present invention further provides a method and system for creating and identifying a digital fingerprint, which consists of a record of one or more frames in a program and associating information about products that appear in these frames to the digital fingerprint. The fingerprints are stored in a database of digital fingerprints, accessible via a wireless network and the Internet from the viewer's mobile wireless device. The mobile device submits a request to identify and locate the fingerprints corresponding to the program frame(s) being viewed, and it receives and displays the associated product information in order to facilitate the purchase of the featured products.
Owner:ENTERTAINMENT MEDIA WORKS
Data repository and method for promoting network storage of data
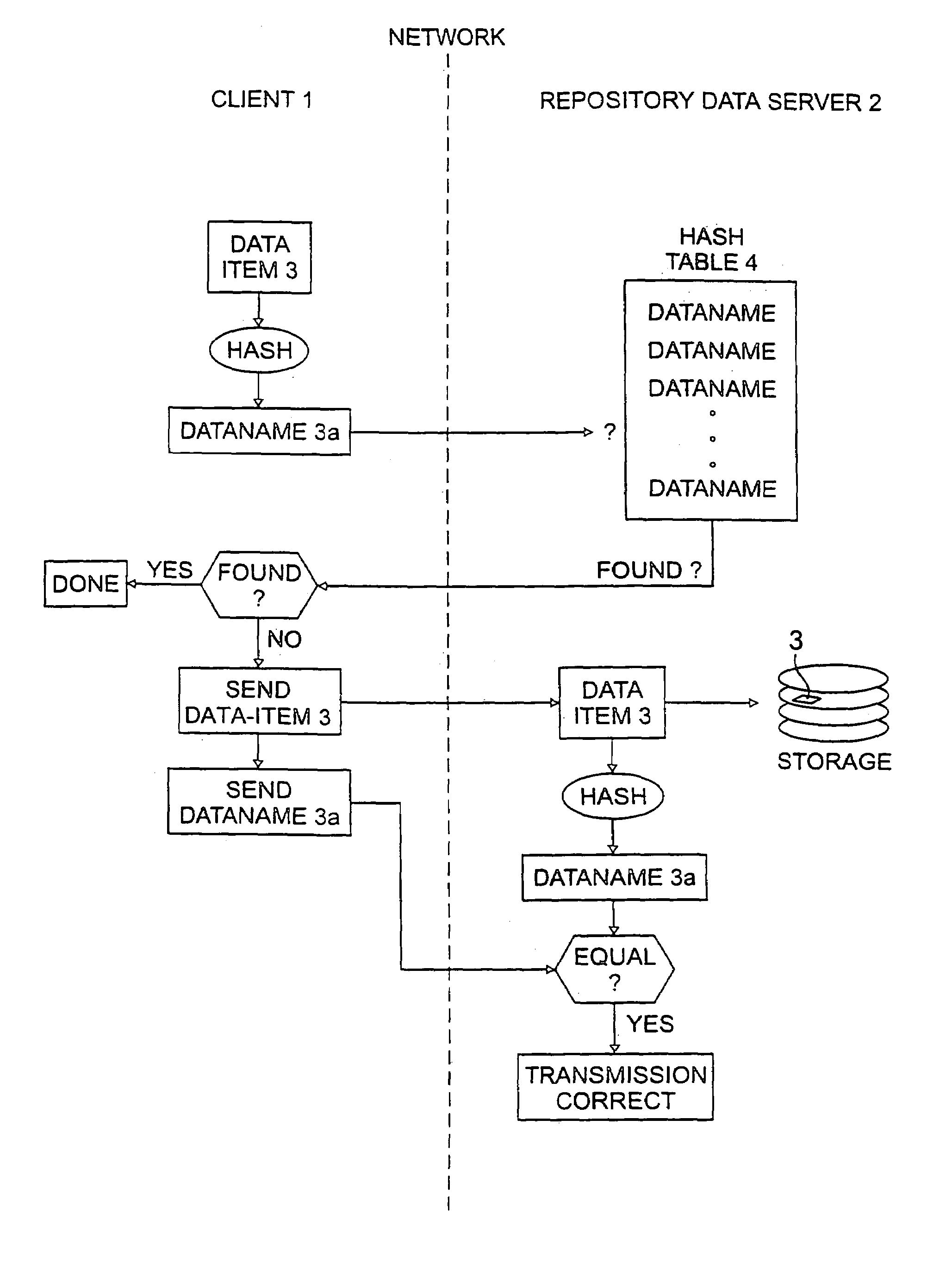
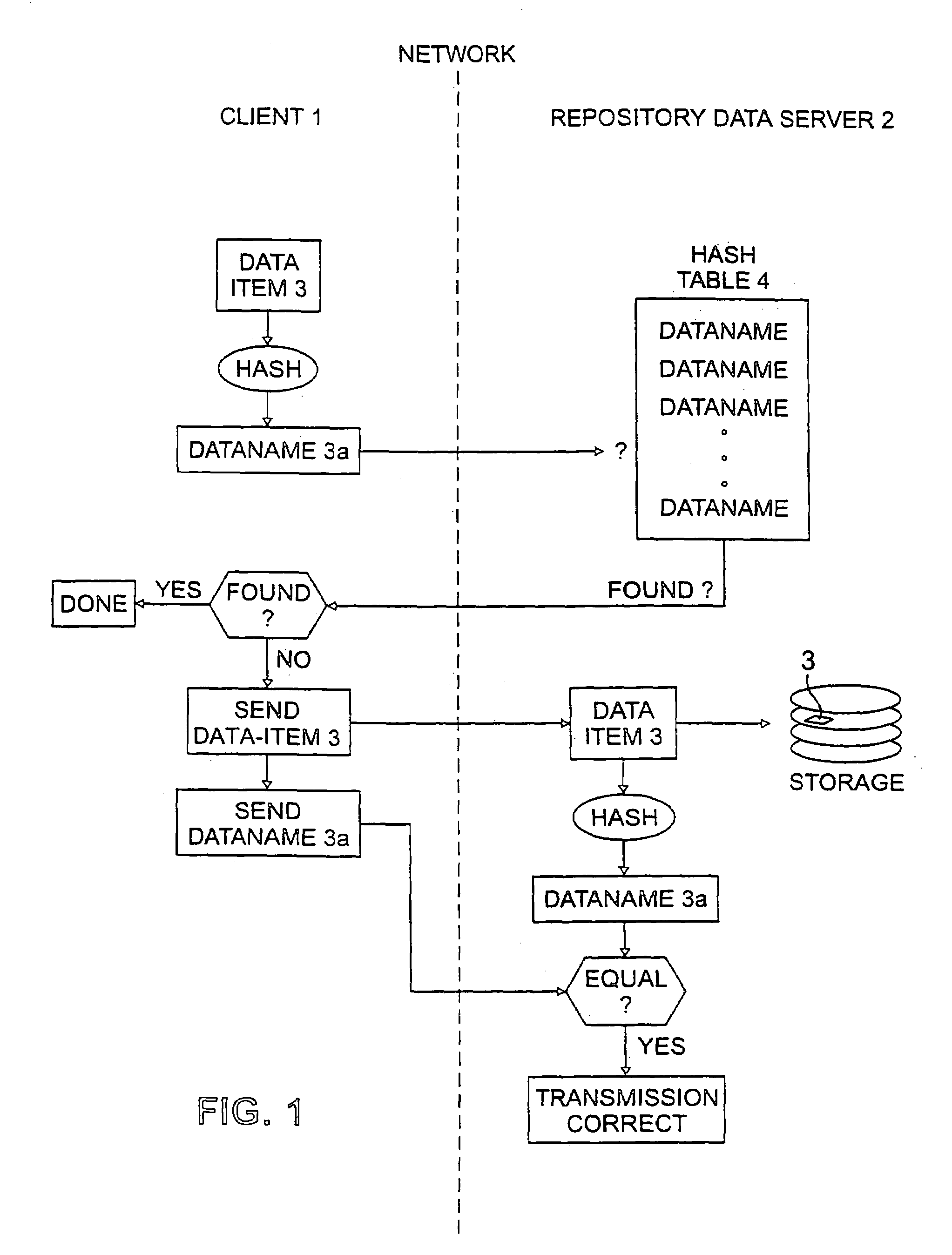
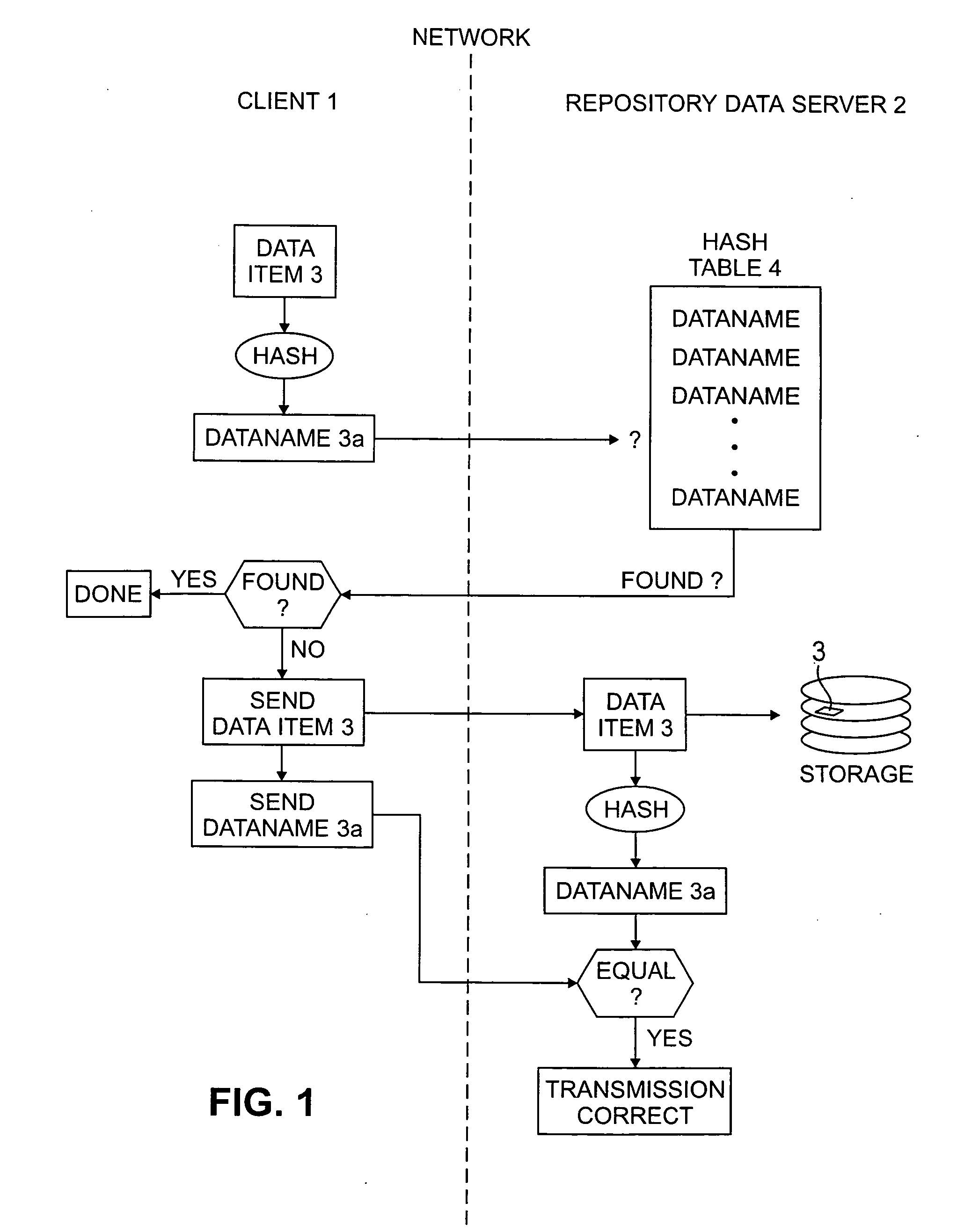
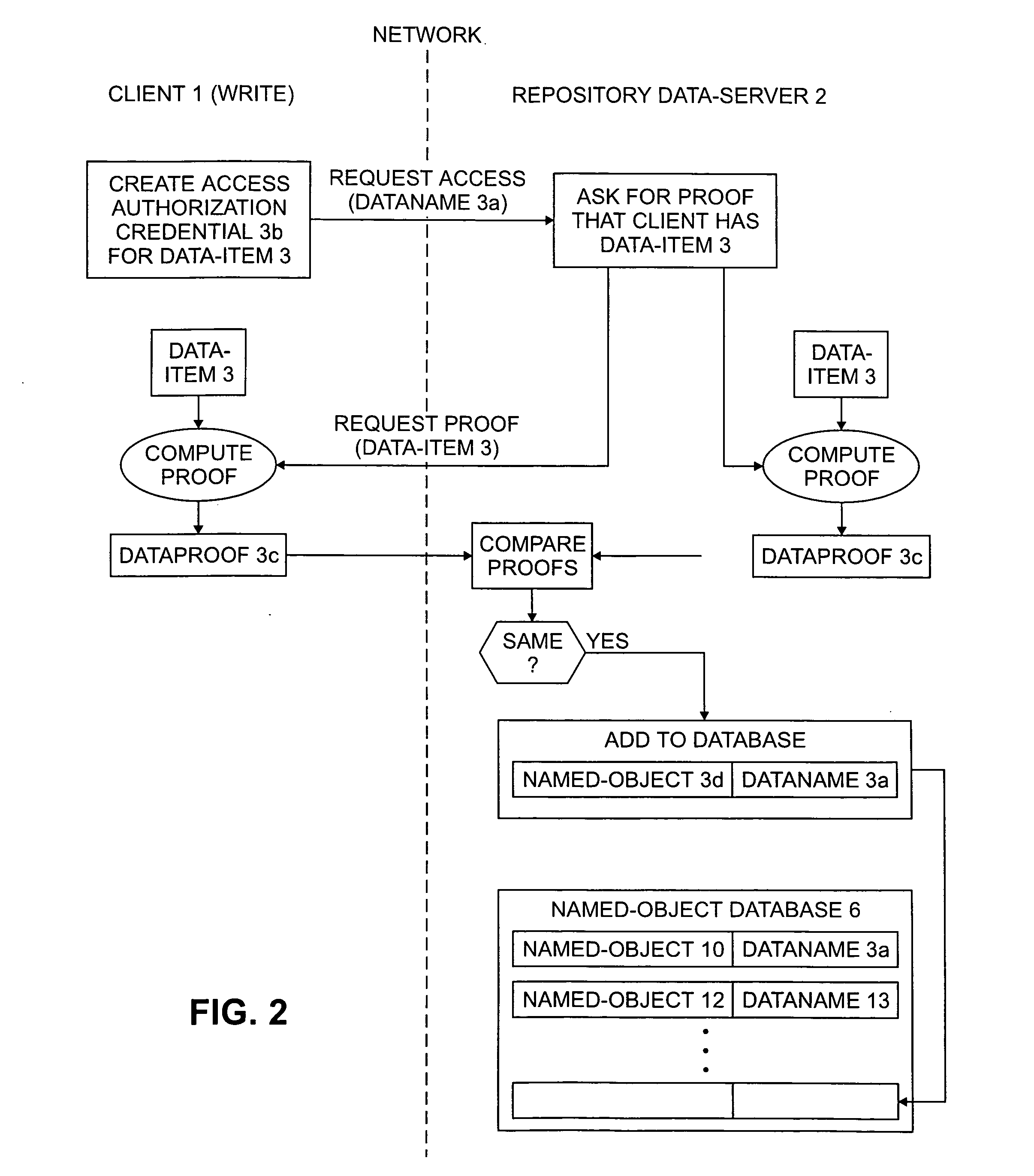
InactiveUS7124305B2Reduced likelihoodReduced versionDigital data information retrievalDigital data processing detailsFull dataClient-side
In general, the invention features methods by which more than one client program connected to a network stores the same data item on a storage device of a data repository connected to the network. In one aspect, the method comprises encrypting the data item using a key derived from the content of the data item, determining a digital fingerprint of the data item, and storing the data item on the storage device at a location or locations associated with the digital fingerprint. In a second aspect, the method comprises determining a digital fingerprint of the data item, testing for whether the data item is already stored in the repository by comparing the digital fingerprint of the data item to the digital fingerprints of data items already in storage in the repository, and challenging a client that is attempting to deposit a data item already stored in the repository, to ascertain that the client has the full data item.
Owner:RED HAT
Logistics tracking method based on block chain
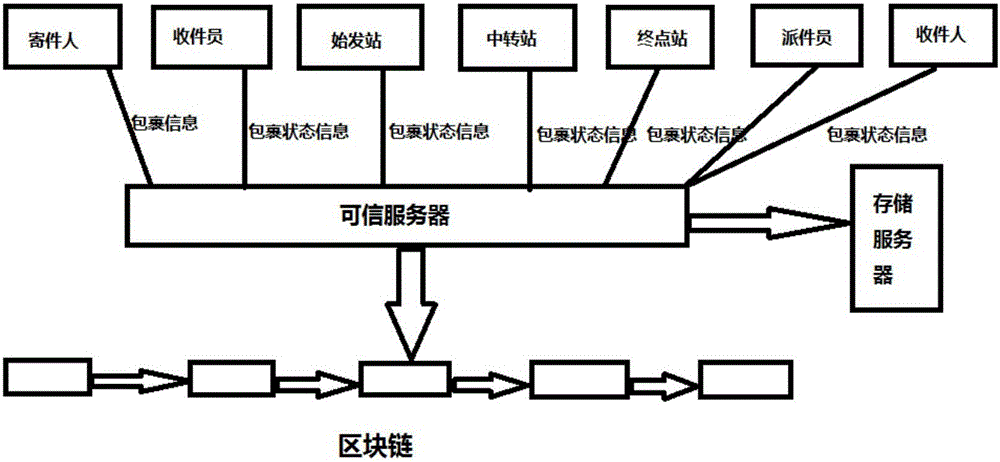
InactiveCN106022681ASolve the problem of real name systemGuarantee authenticityLogisticsPhysical spaceDigital fingerprint
The invention discloses a logistics tracking method based on a block chain. The method comprises steps that a user sending node uploads parcel information to a main node; the main node generates a digital fingerprint for the parcel information uploaded by the user sending node, writes the digital fingerprint and a corresponding time stamp into a block chain, broadcasts the block chain in all nodes; each logistics node generates parcel state information successively according to the digital fingerprint, the node information of the logistics node and the node information of a next logistics node in accordance with a parcel physical space transfer path; a corresponding user receiving node signs for the parcel, generates parcel receiving information and uploads the parcel receiving information to the main node in order for the main node to write the parcel receiving information into the block chain. The logistics tracking method applies the block chain technology to the logistics field, guarantees the traceability of the authenticity and the state of logistics information by using the unchangeable characteristic of the block chain, saves the logistics information and update state information fast and efficiently according to the characteristic of a private chain in order to satisfy a requirement for logistics instantaneity.
Owner:HANGZHOU YUNXIANG NETWORK TECH
Secure Transaction Authentication
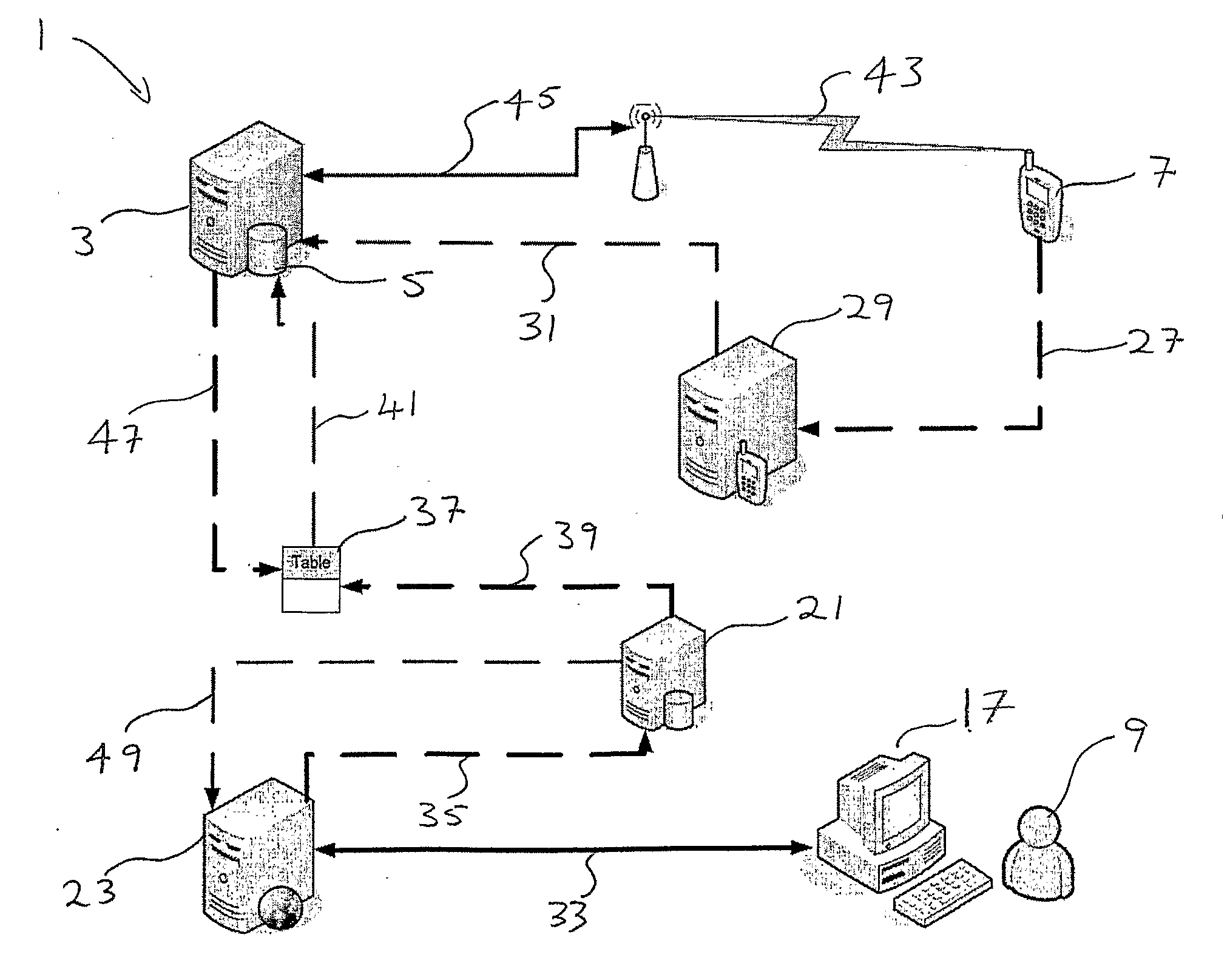
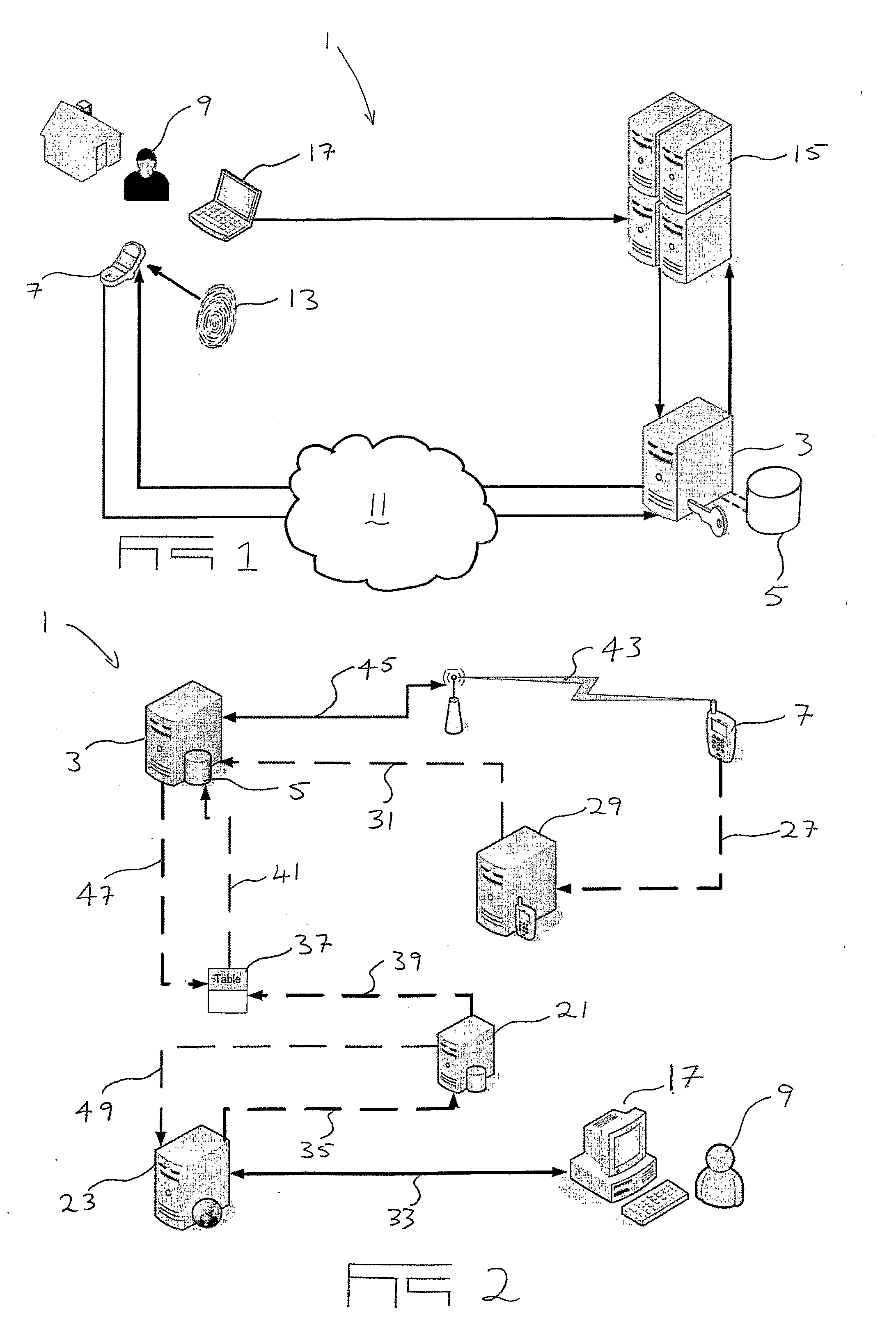
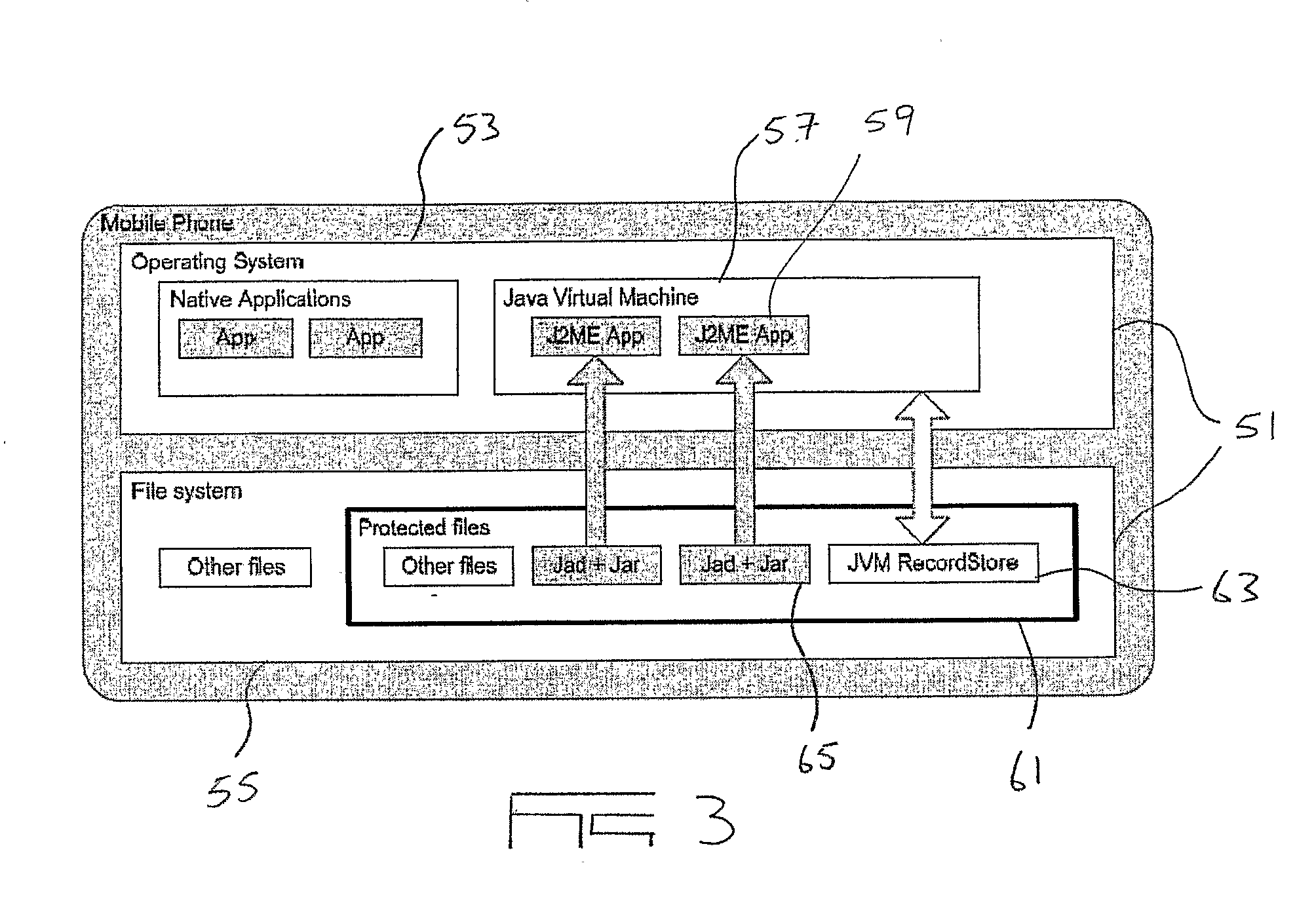
ActiveUS20110086616A1Reduce decreaseUnauthorised/fraudulent call preventionEavesdropping prevention circuitsFinancial transactionDigital fingerprint
A method and system for authenticating secure transactions between a transacting user (9) and a secure transaction host (15) is provided. The system includes a mobile phone software application (59) installed on a transacting user's mobile phone (7) which is configured to compose a digital fingerprint (13) uniquely associated with the specific mobile phone (7) on which it is installed. The system further includes an authentication service provider with which users of the system may be enrolled by registering at least the digital identifiers composed by the applications installed on their mobile communication devices in an authentication database (5). The authentication service provider is configured to authenticate secure transactions on request from secure transaction hosts by sending transaction confirmation requests to mobile phones of enrolled users requiring them to confirm or deny secure transactions before such transactions are allowed to be finalized.
Owner:ENTERSECT INT
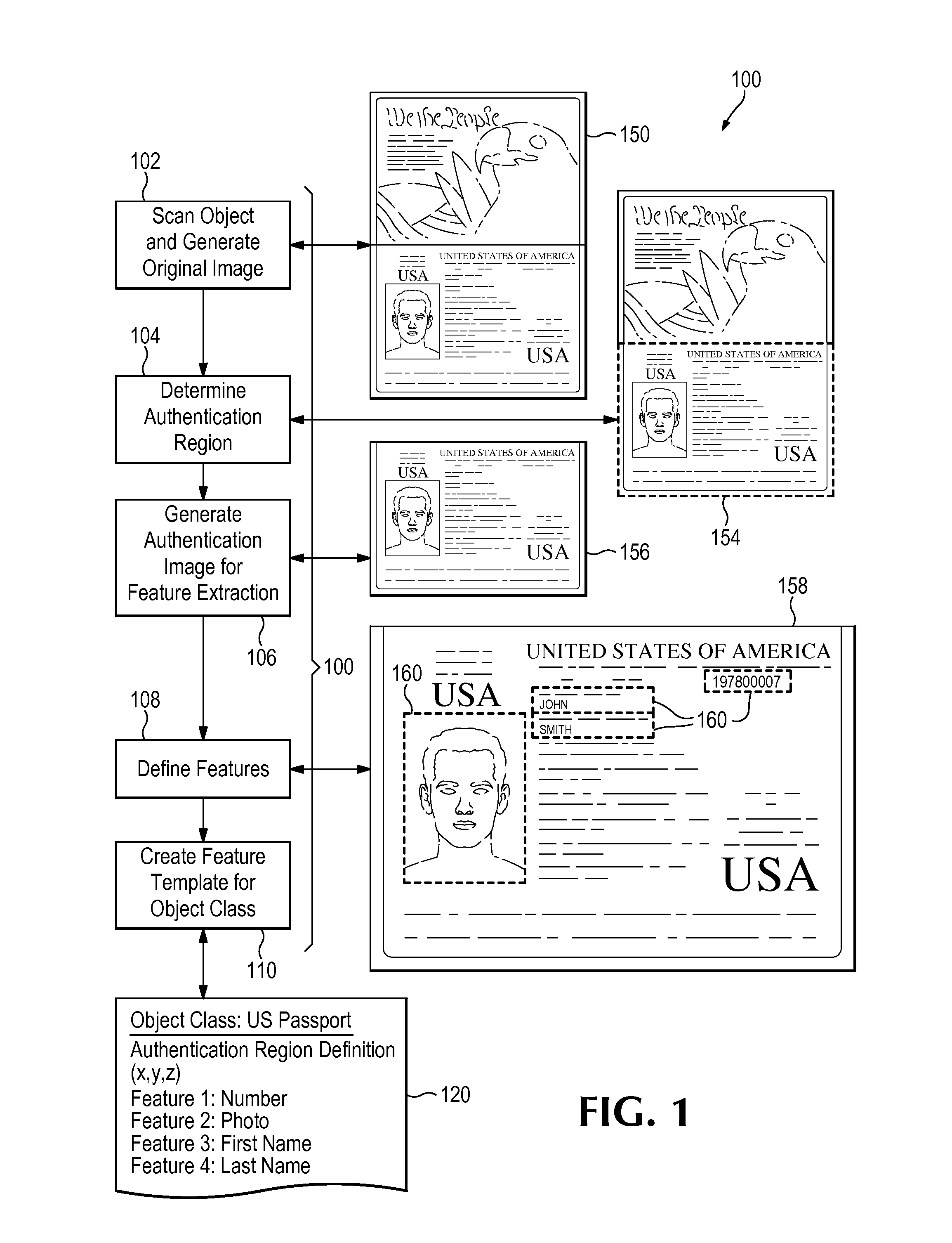
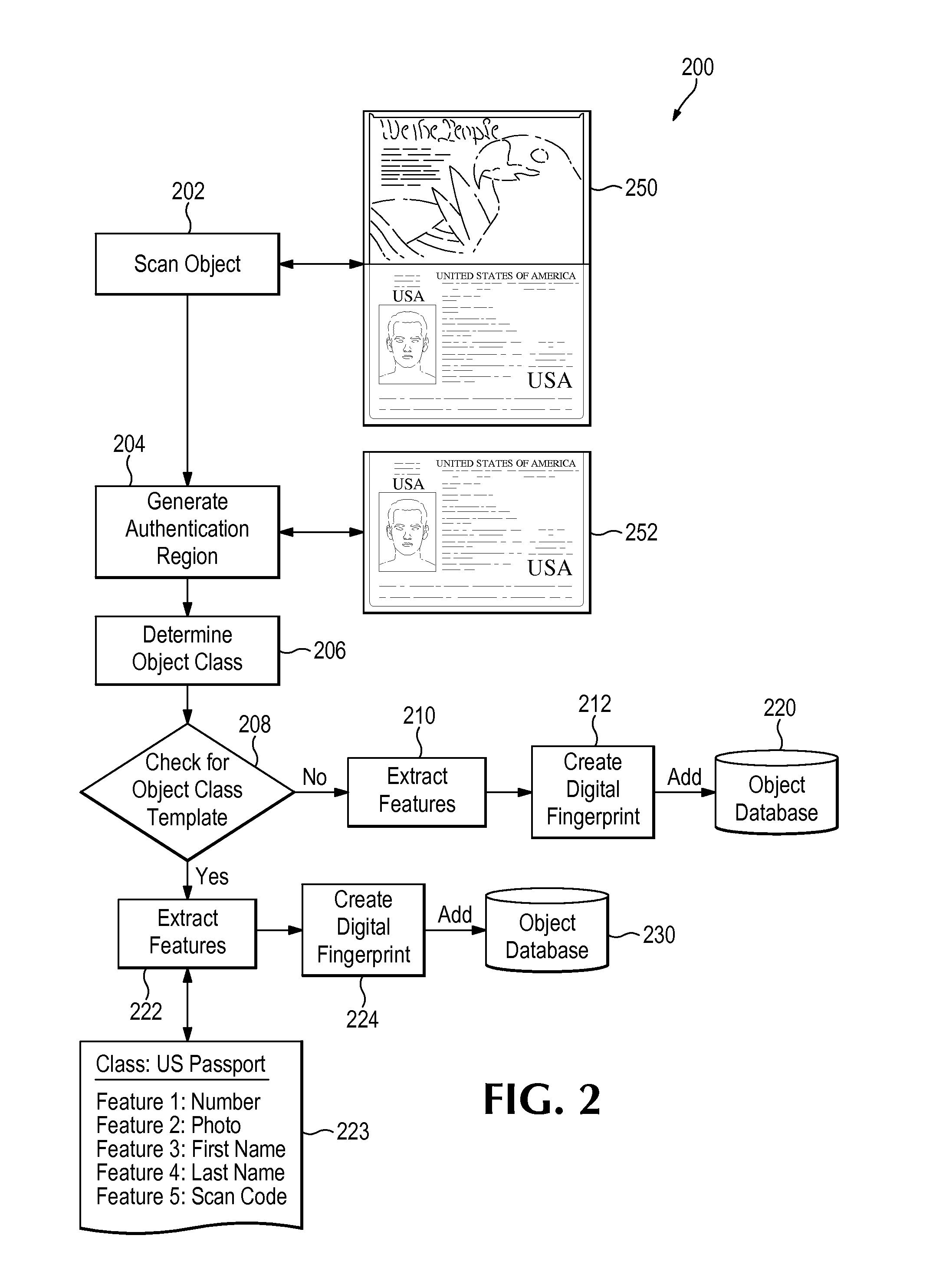
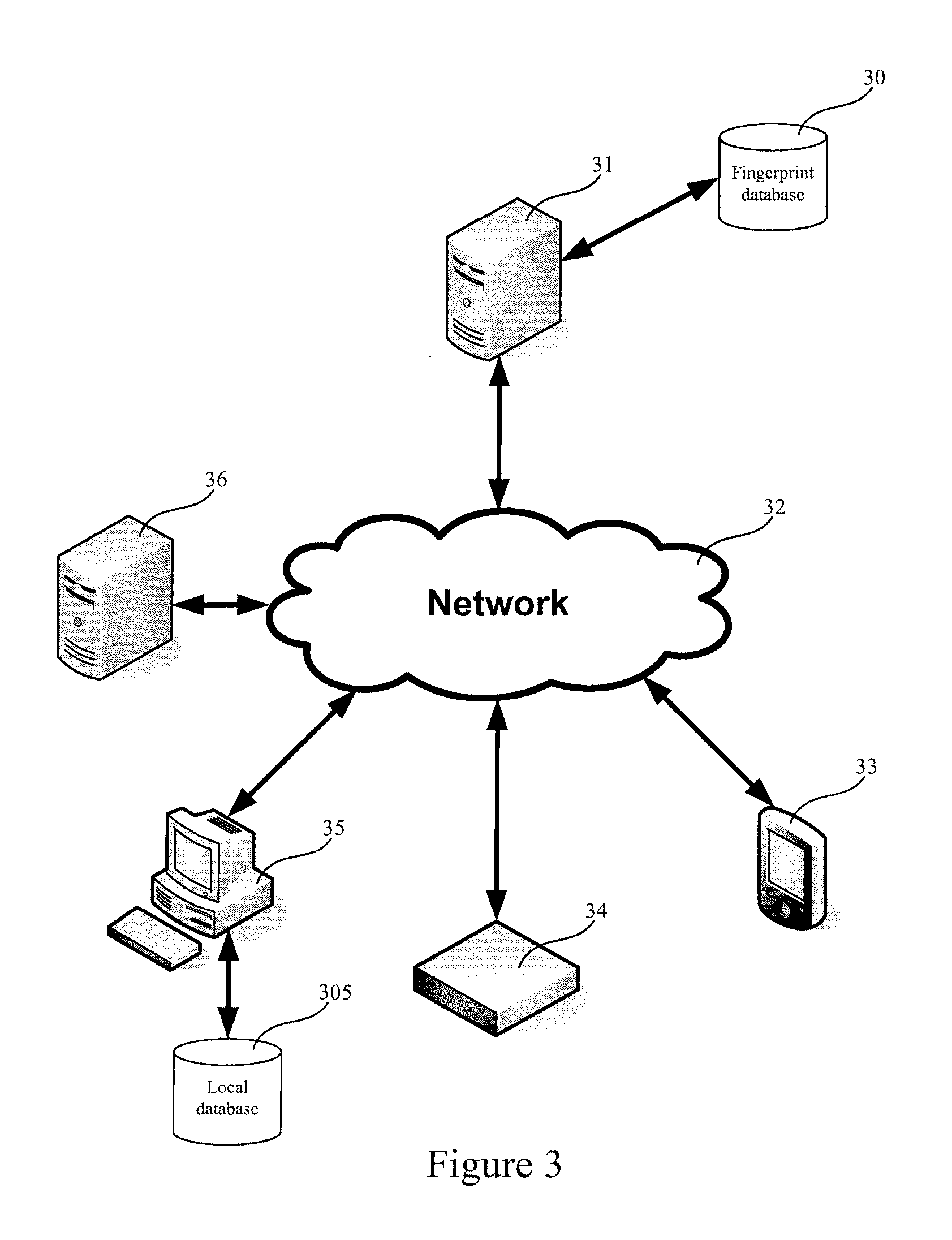
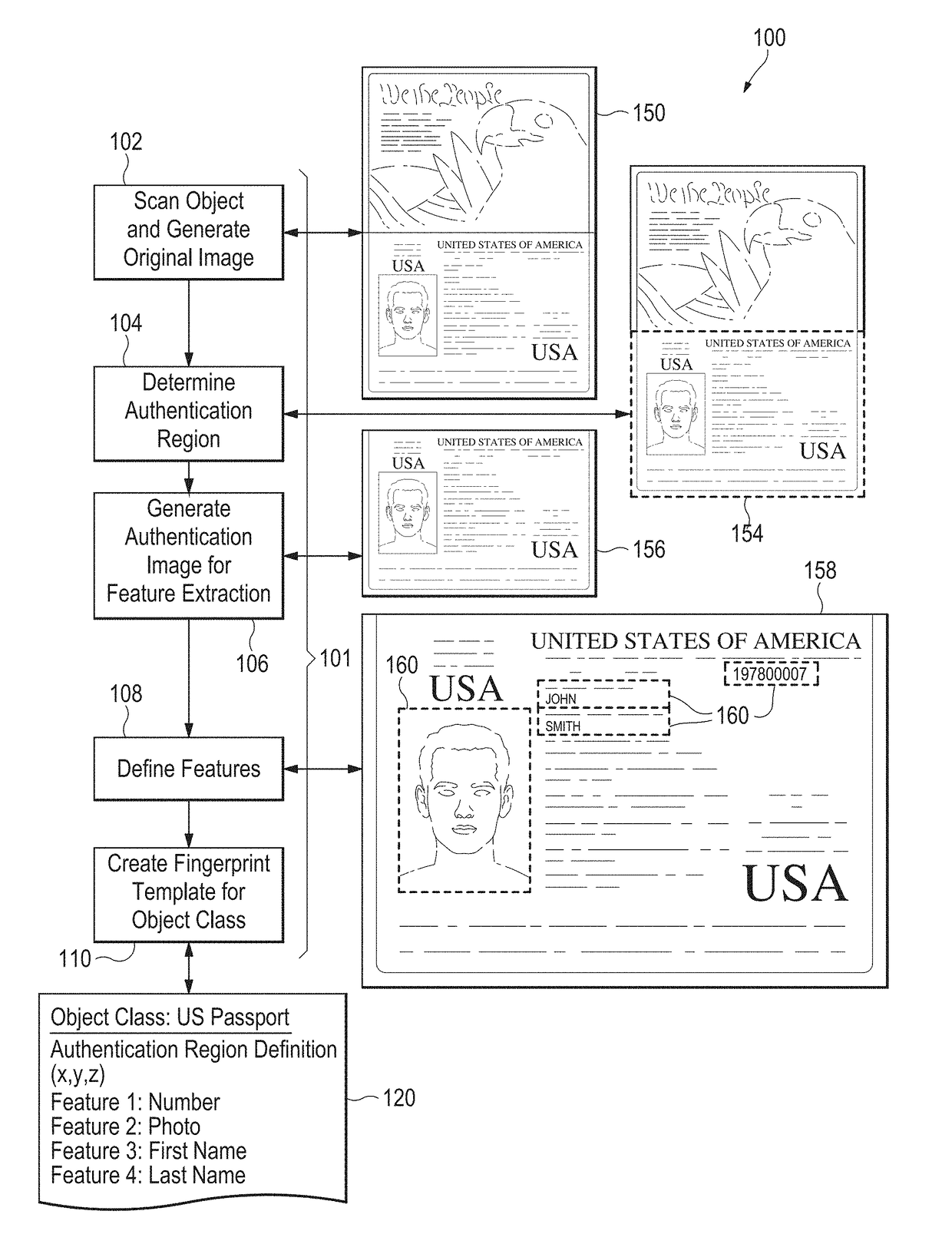
Digital fingerprinting object authentication and Anti-counterfeiting system
Improvements are disclosed for authentication of an object, verification of its provenance, and certification of the object as compliant with manufacturing standards. Or, an object may be reported as a suspected counterfeit. In one embodiment the system compares a digital fingerprint of the object, based in image capture, to digital fingerprints previously stored in a database and determines if the object has been registered before and is thus authentic. An object feature template may be created which has a list of features and attributes that are relevant for authenticating particular classes of objects. The object feature template can also be used to examine unregistered objects for signs of counterfeiting.
Owner:ALITHEON INC
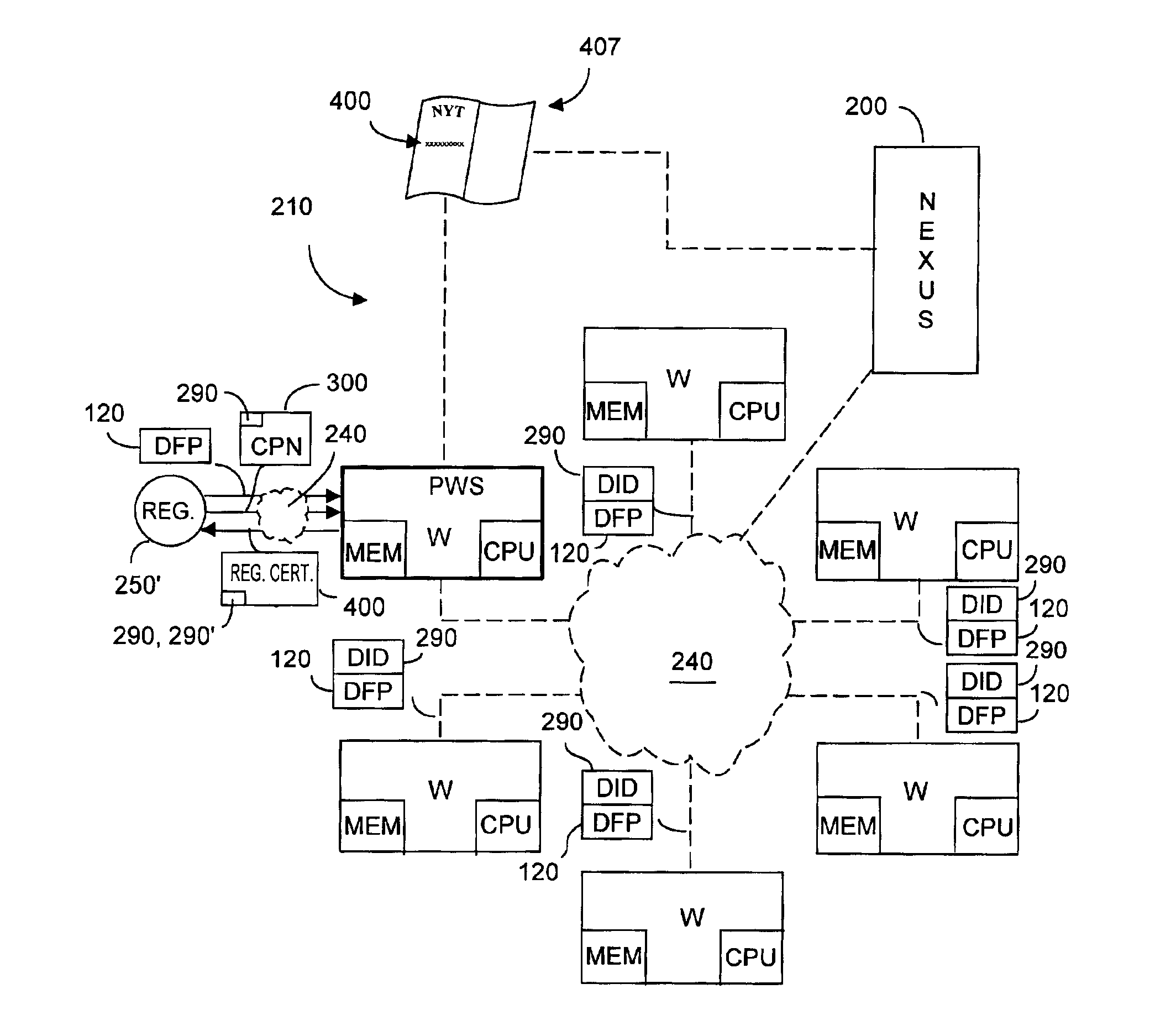
Distributed information system and protocol for affixing electronic signatures and authenticating documents
InactiveUS6938157B2System overhead associated with couponsImprove effectivenessUser identity/authority verificationUnauthorized memory use protectionCryptographic hash functionCryptogram
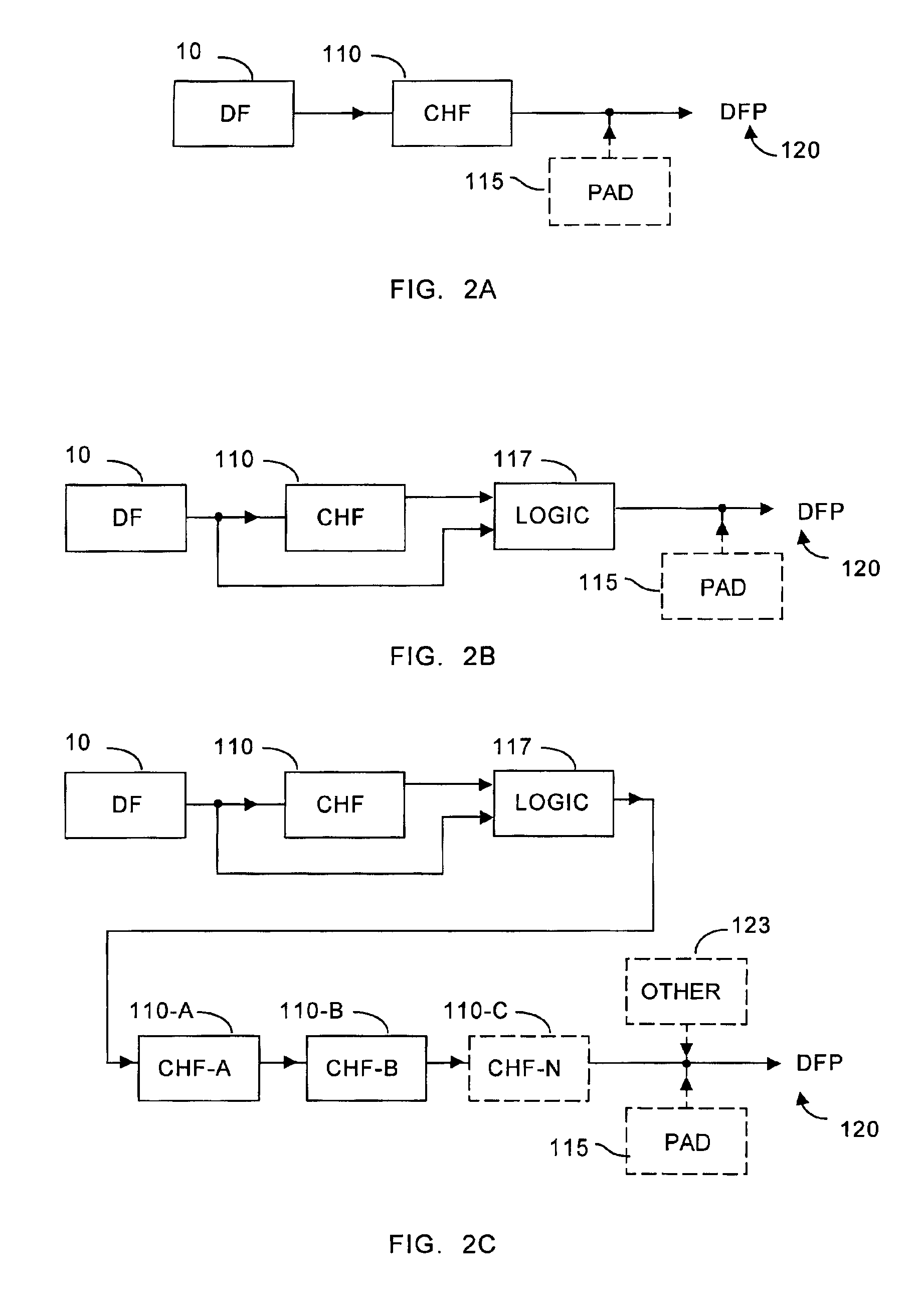
A system can process a digital representation (DF) of a document with a one-way cryptographic hash function (CHF) to yield a digital fingerprint (DFP) value that is associated with the DF. A document identification number (DID) is created, uniquely associated with the DFP, and with DID and DFP are associated optional credential information (C). A registration certificate DFC that represents an optional electronic signature associated with the document and that includes the DID and DFP is promulgated and archived at a plurality of storage locations. The system can authenticate whether a putative document is the original document by generating a digital fingerprint value for the putative document and comparing it to DFP retrieved from various of the storage locations. Authentication can confirm that the electronic signature is unaltered.
Owner:DISTRIBUTED TRUST MANAGEMENT
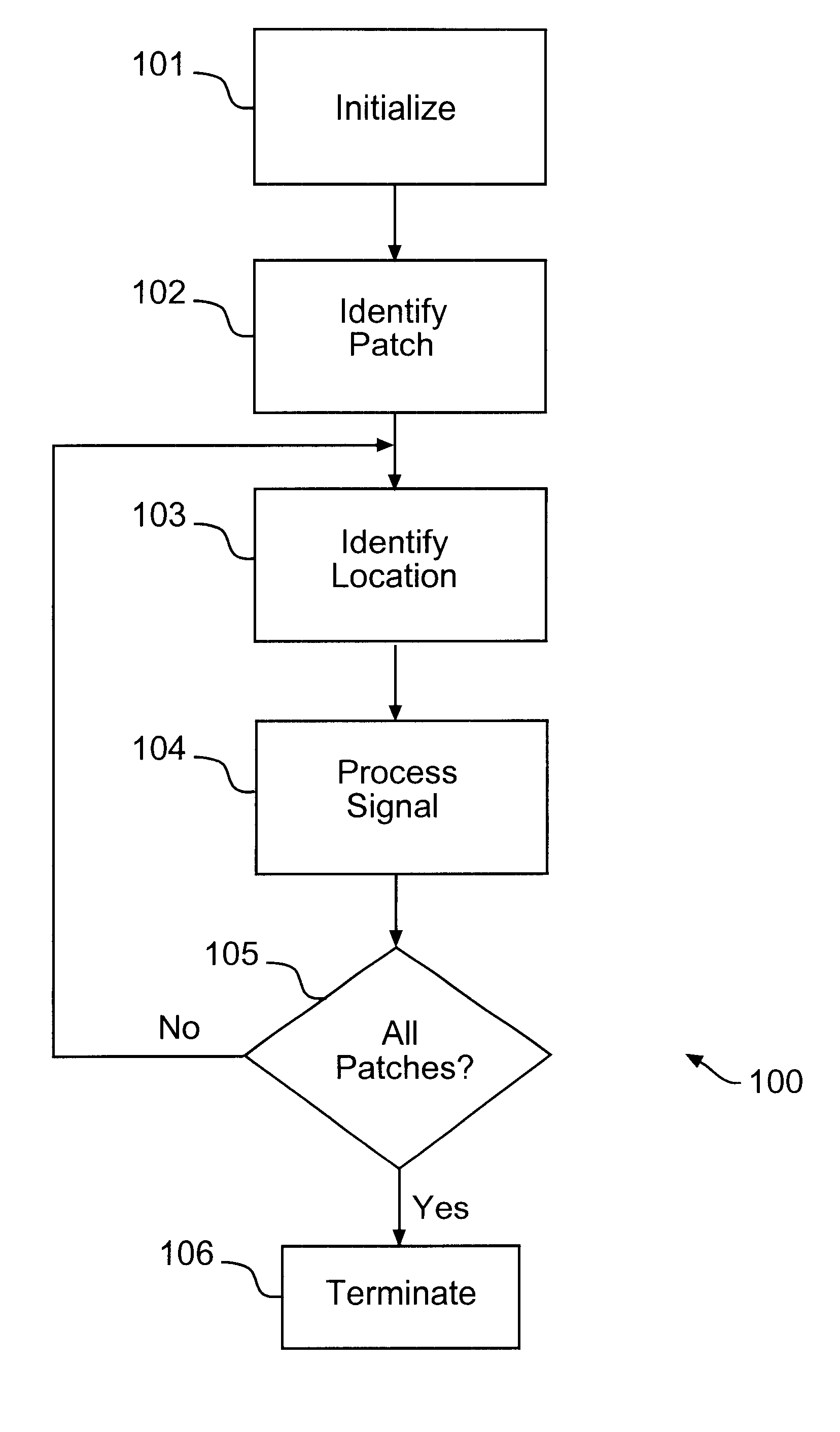
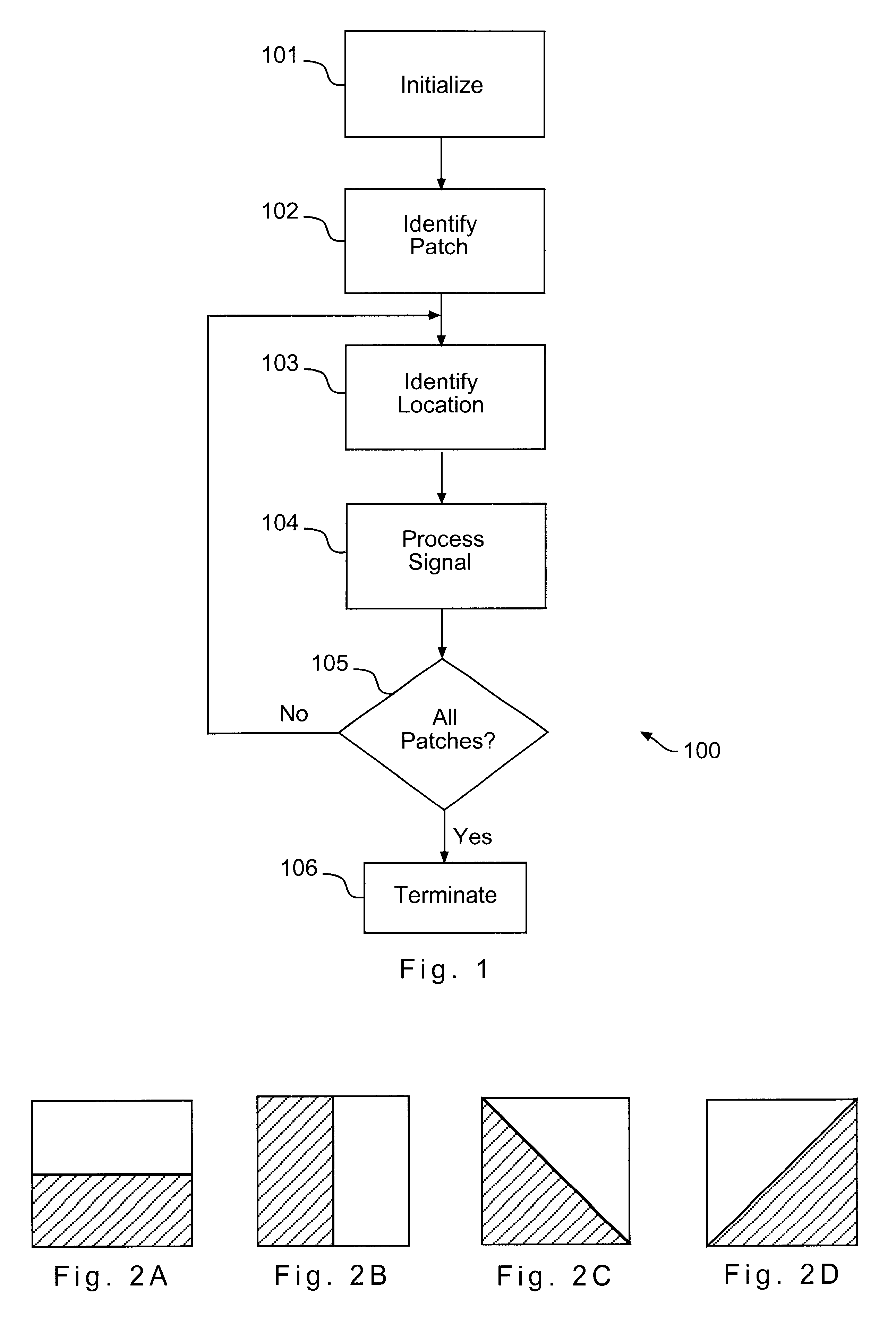
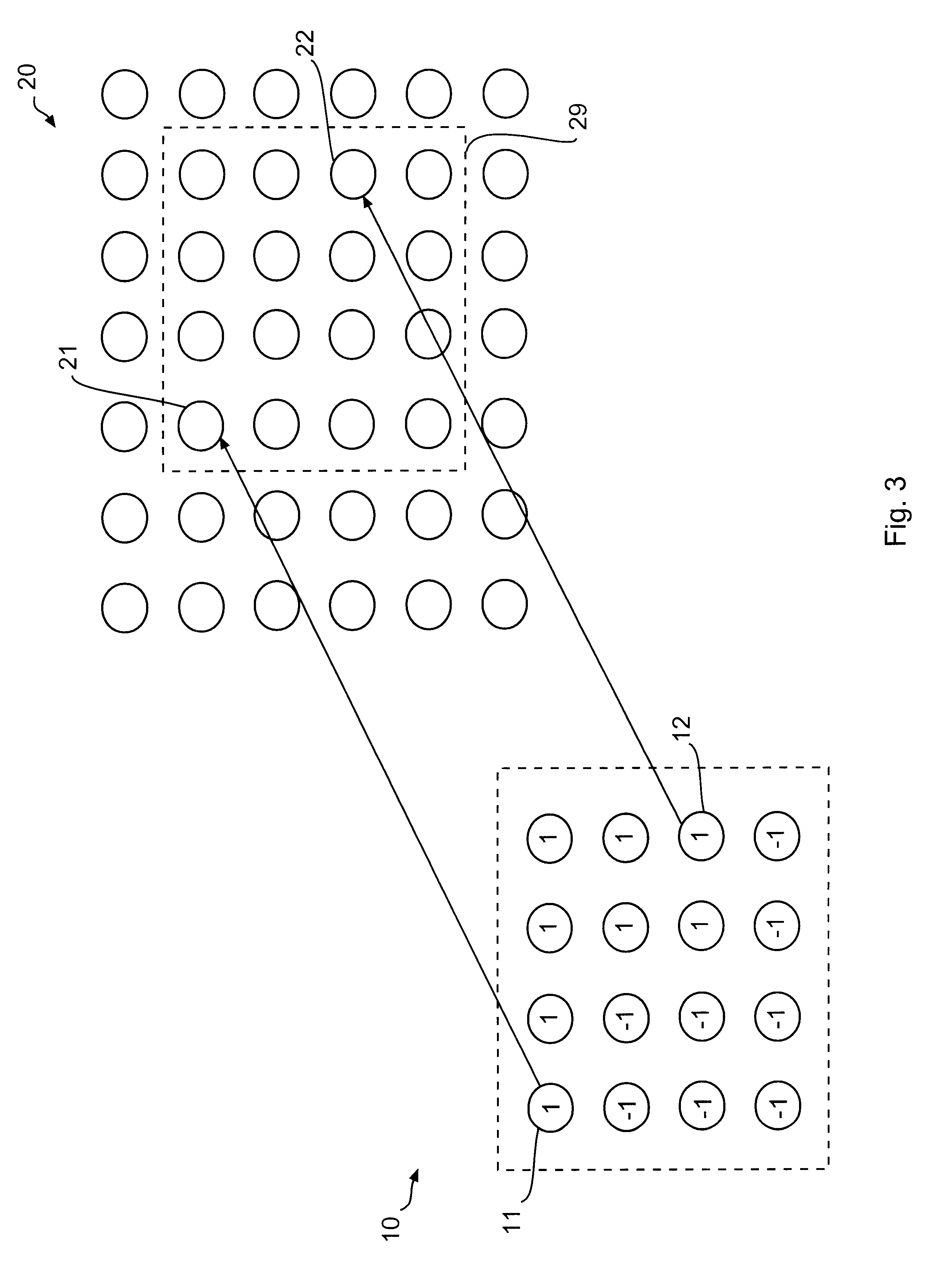
Method for fingerprinting multimedia content
InactiveUS20070180537A1Digital data processing detailsAnalogue secracy/subscription systemsDigital dataData segment
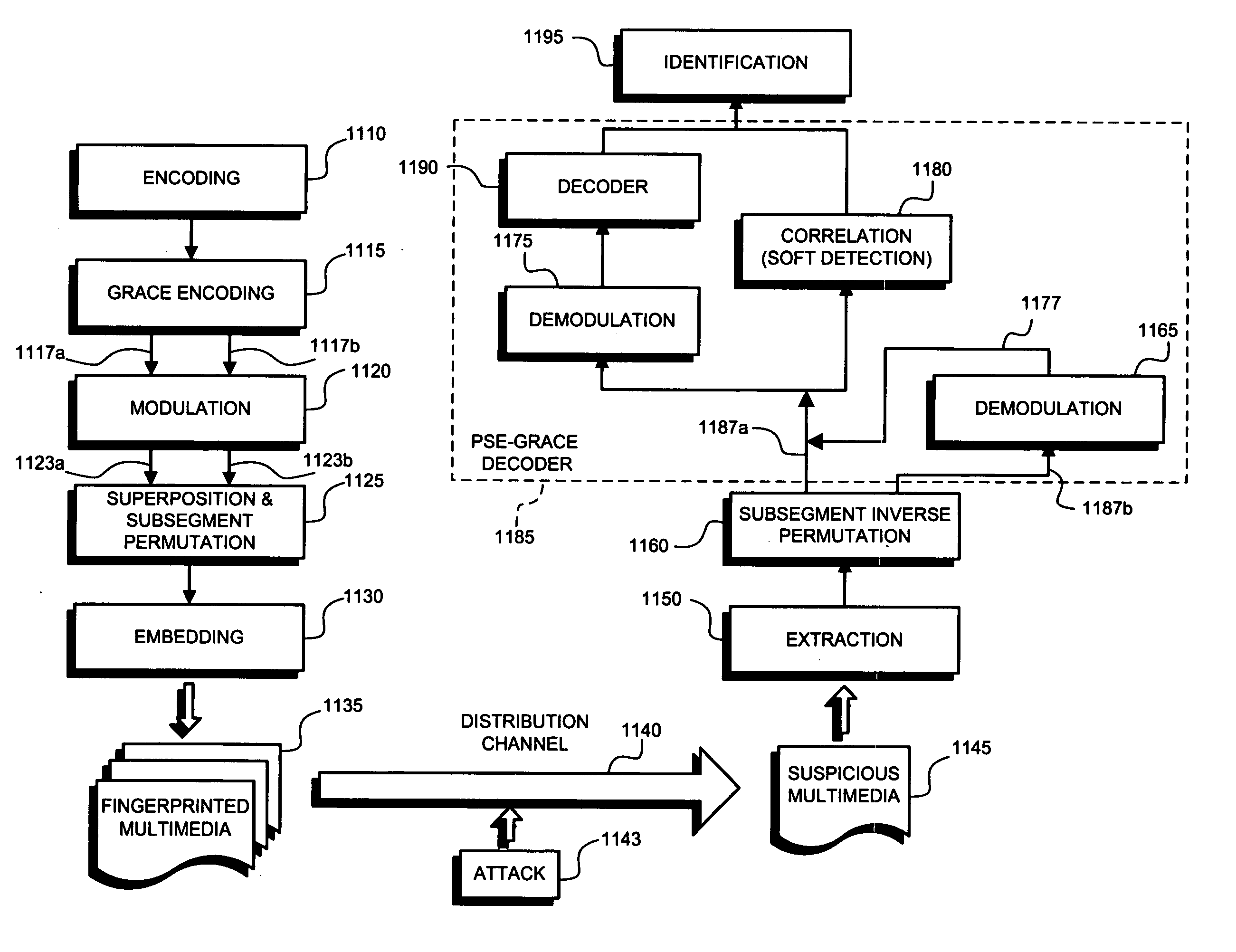
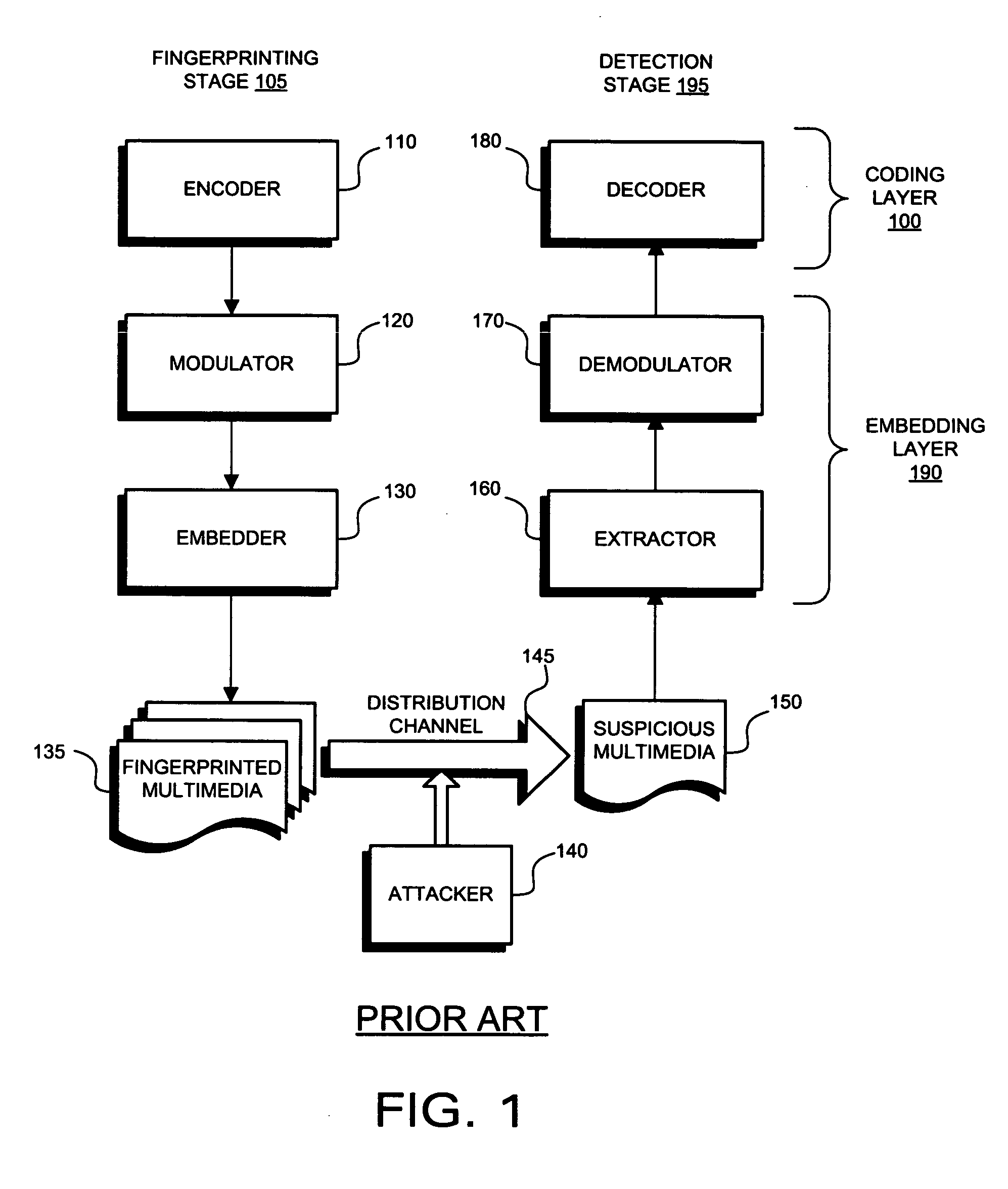
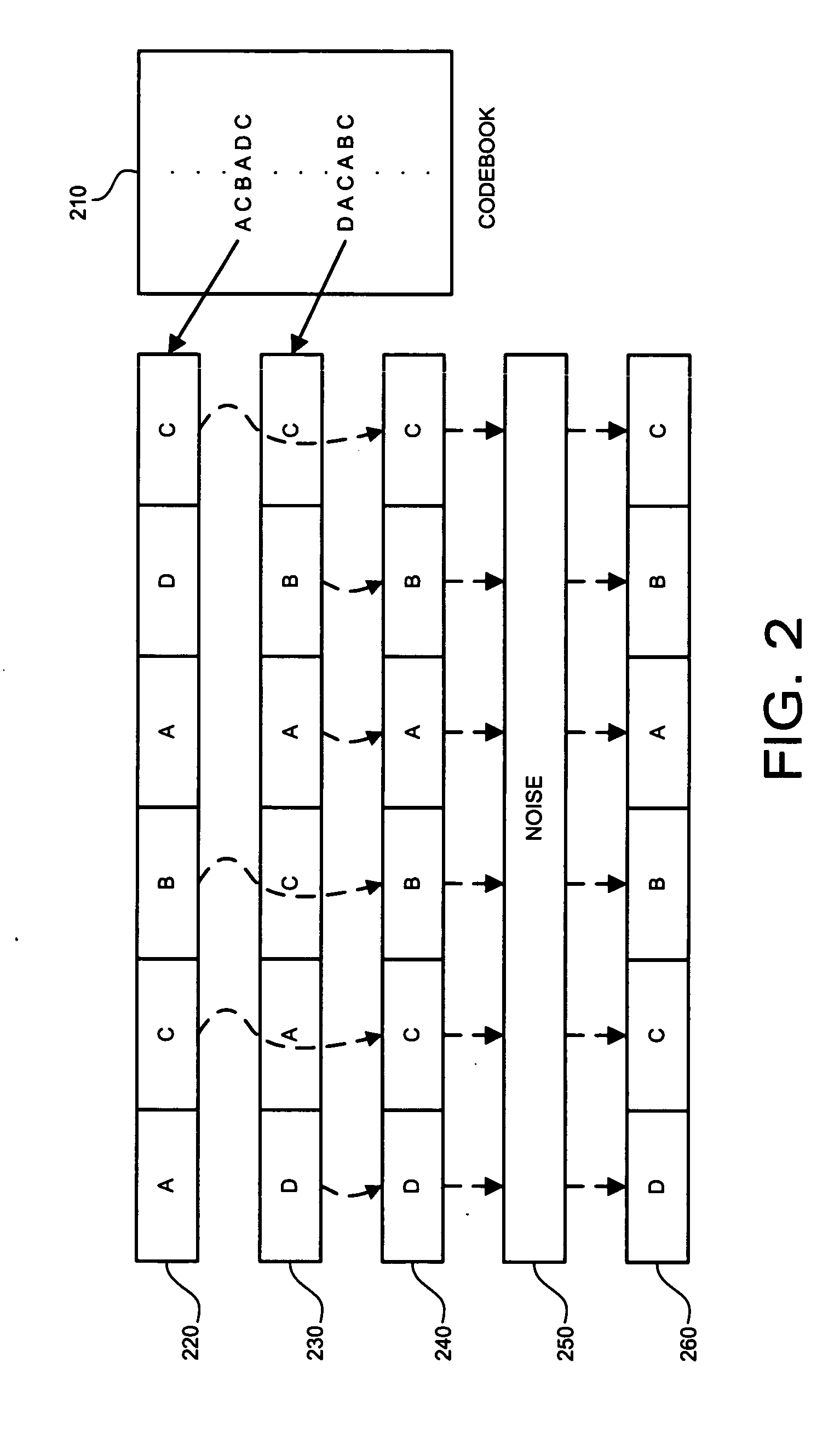
To identify participants in collusion directed to altering a digital fingerprint embedded in multimedia content, an ECC based fingerprinting technique establishes a code symbol for each of a plurality of segments of digital data forming the multimedia content. The code symbols are concatenated to form a fingerprint signal, which is subdivided into a plurality of subsegments for each segment in the digital data. The subsegments are permuted and embedded into the digital data. When a suspicious copy of the multimedia content is discovered, the permuted fingerprint signal is extracted from the content and inversely permuted to form a test fingerprint. The identity of one of the colluders is determined by correlation with characteristics of the codeword originally assigned to the user. The determination of identity may be enhanced by the addition of group data embedded as an additional fingerprint in the digital data. Joint consideration of coding and embedding provide benefits over previous fingerprinting techniques.
Owner:UNIV OF MARYLAND
System and method for backing up data
InactiveUS20060218644A1Inefficiency of the Shnelvar patent can be avoidedAvoid inefficiencyDigital data processing detailsCamera focusing arrangementEnterprise computingTheoretical computer science
A method is provided to audit license restrictions of a computer program in an enterprise computing environment. In one example, a digital fingerprint is generated of at least one file in the computer program using a substantially collision-free algorithm, and a digital fingerpring is generated for each file on each computer in the enterprise using the substantially collision-free algorithm. The digital fingerprints from the enterprise files are compared with the digital fingerprint of the computer program file, and the number of fingerprint matches is counted. Another method is provided for inventorying a computer program in an enterprise computing environment. In examples of both methods, a file may be divided into data blocks and a digital fingerprint may be generated for each data block.
Owner:FALCONSTOR
Sharing query method of electronic medical records based on block chain technology
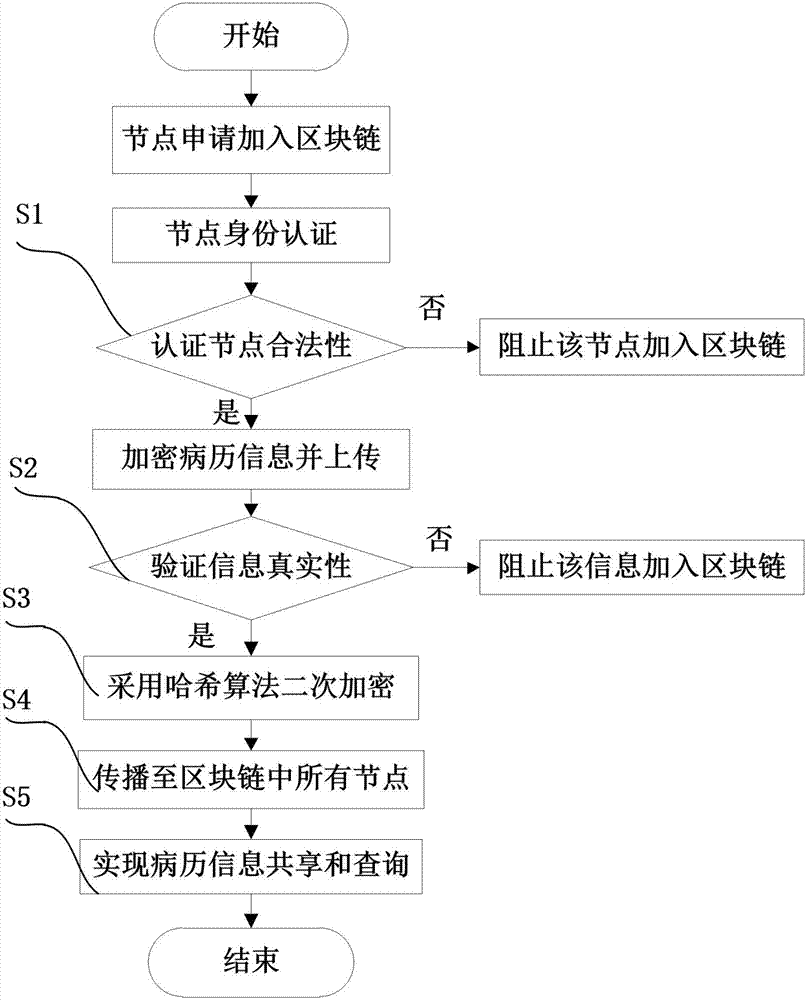
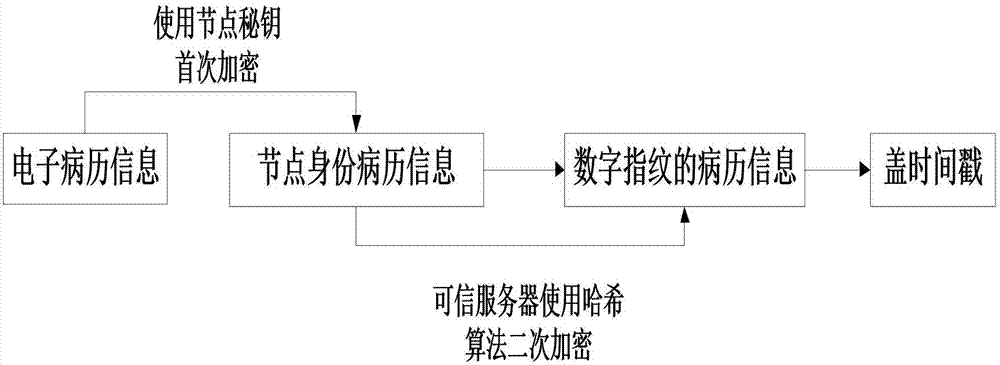
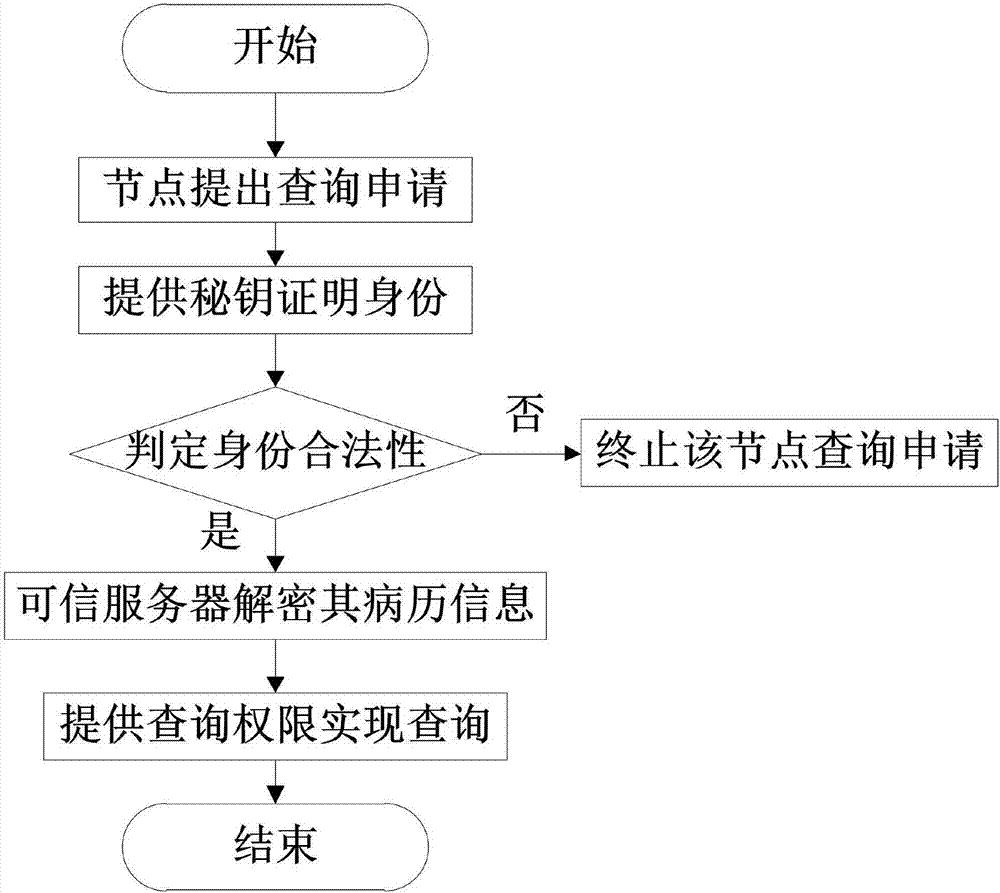
InactiveCN107579979AAchieve sharingShared query implementationUser identity/authority verificationSpecial data processing applicationsMedical recordTimestamp
The invention discloses a sharing query method of electronic medical records based on block chain technology. The method comprises the following steps: a user node applies to join a block chain and sends identity authentication information, registers the identity information and allocates a pair of keys for encrypting electronic medical record information after legal authentication; meanwhile performing bidirectional verification on the encrypted electronic medical record information, and uploading the electronic medical record information passing the bidirectional verification to the block chain for the sharing query of the whole electronic medical record information; performing SHA256 hash algorithm secondary encryption on the real electronic medical record information by a trusted server to generate a segment of uploaded digital fingerprint of electronic evidence, and adding a corresponding timestamp for preventing electronic medical record tampering or information leakage; and storing the electronic medical records after twice encryption in the sharing query block chain, and uploading the same to the cloud; and providing a key by a remote node for identity proving, obtaining the electronic medical records in the sharing query block chain, and decrypting the electronic medical records by the trusted server.
Owner:CHENGDU UNIVERSITY OF TECHNOLOGY
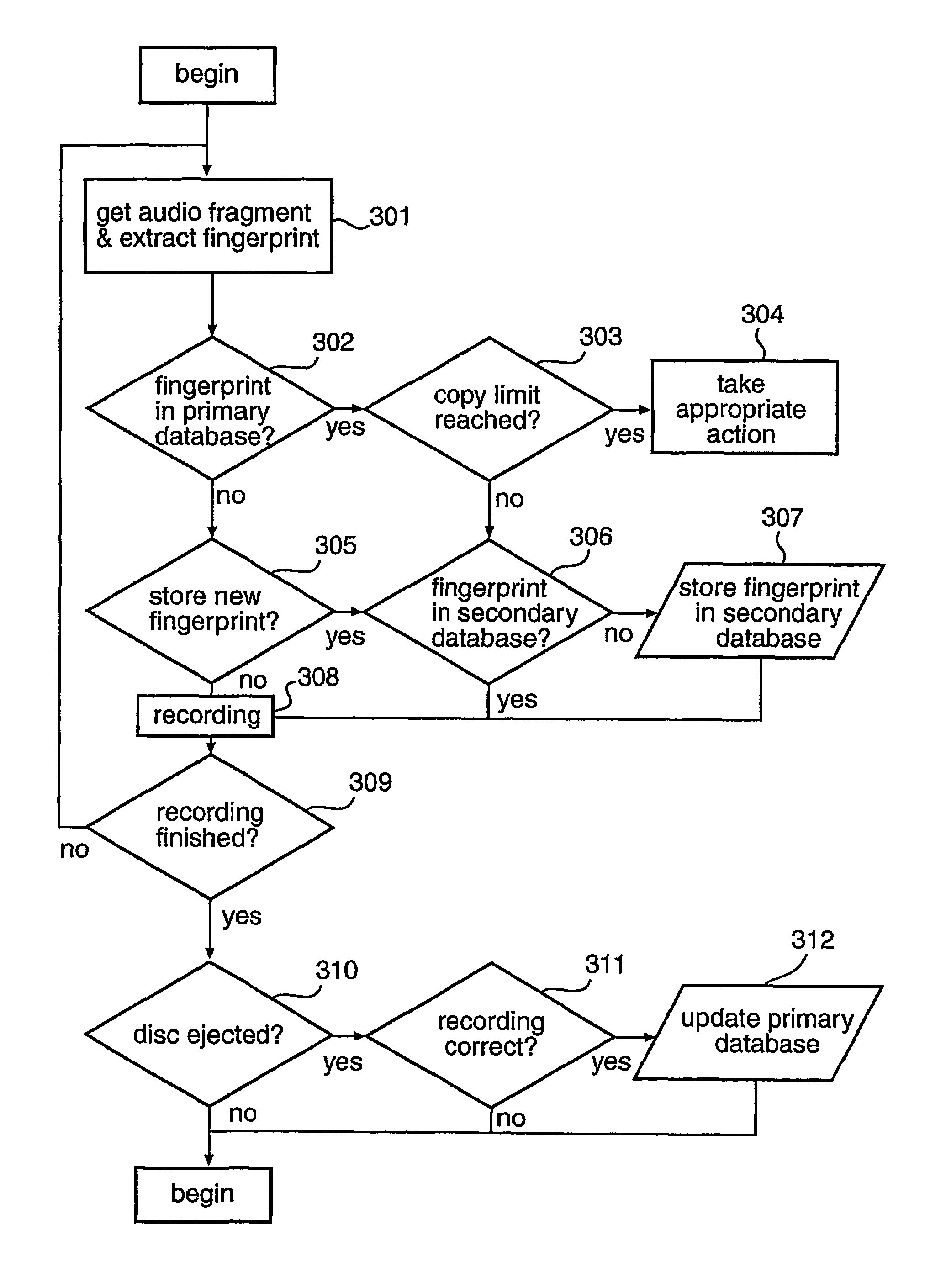
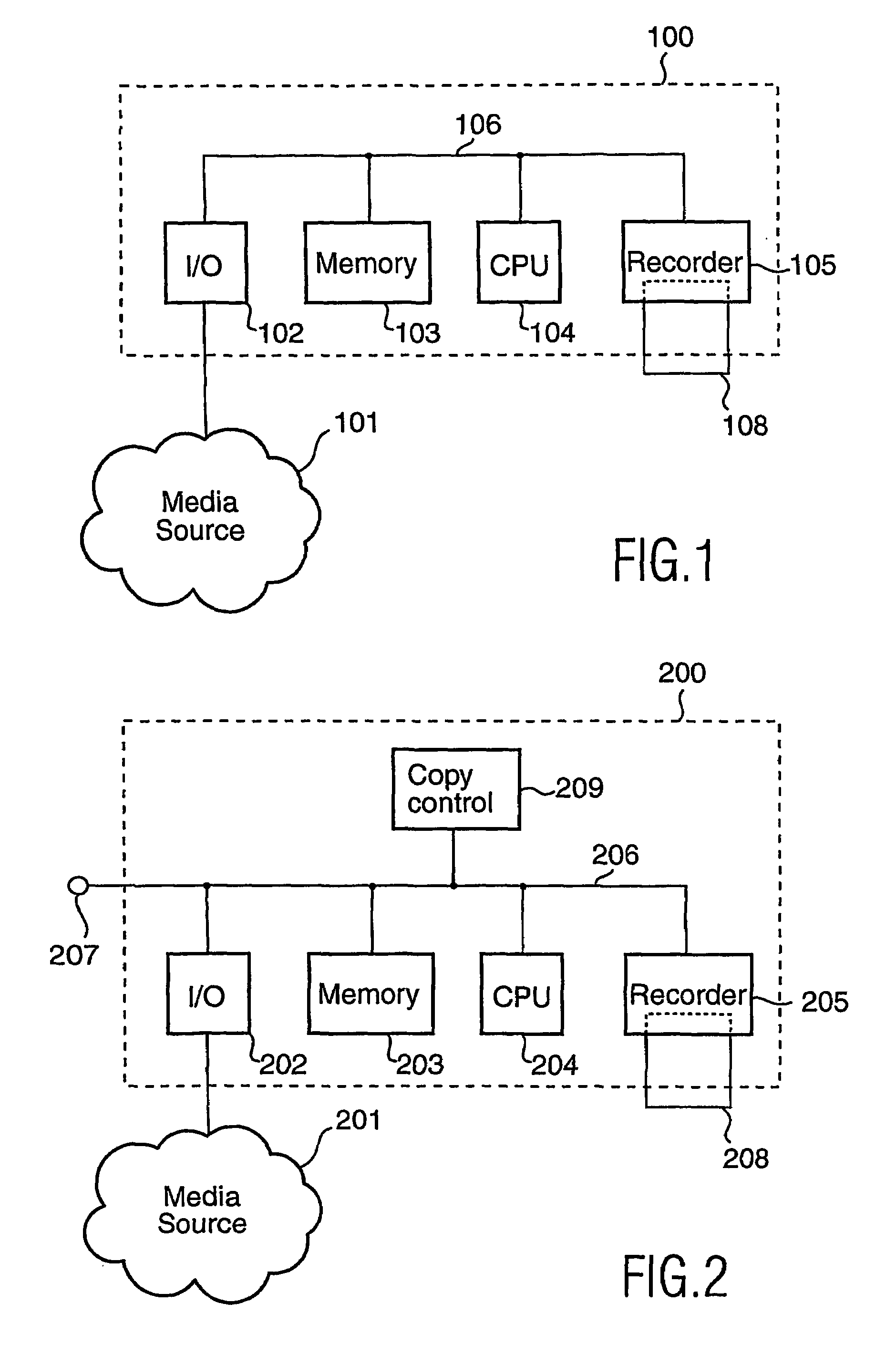
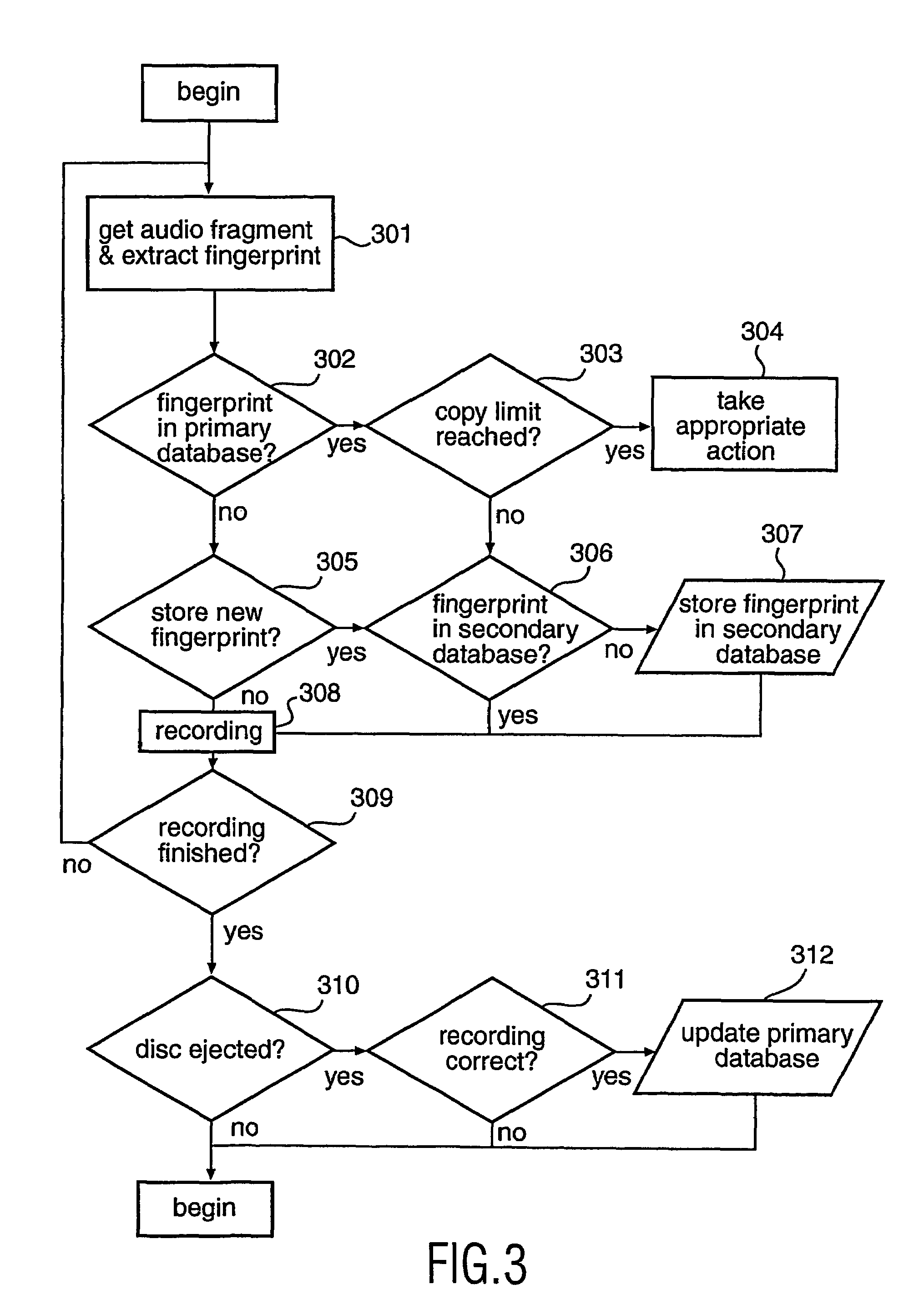
Copy control using digital speed bumps
A digital media recorder and a method of controlling such are provided. During attempts to copy media content, sub-sequences are extracted from an input media sequence. A digital fingerprint of the sub-sequence is calculated and compared with at least one first reference fingerprint from a database. The outcome of the comparison determines the action to take in the further processing. Recording of the input media sequence on a media carrier is either allowed or obstructed, e.g. disallowed. In the case recording of the sequence is allowed, the database is updated with information that the digital media sequence has been recorded.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Method and system for recognizing video program
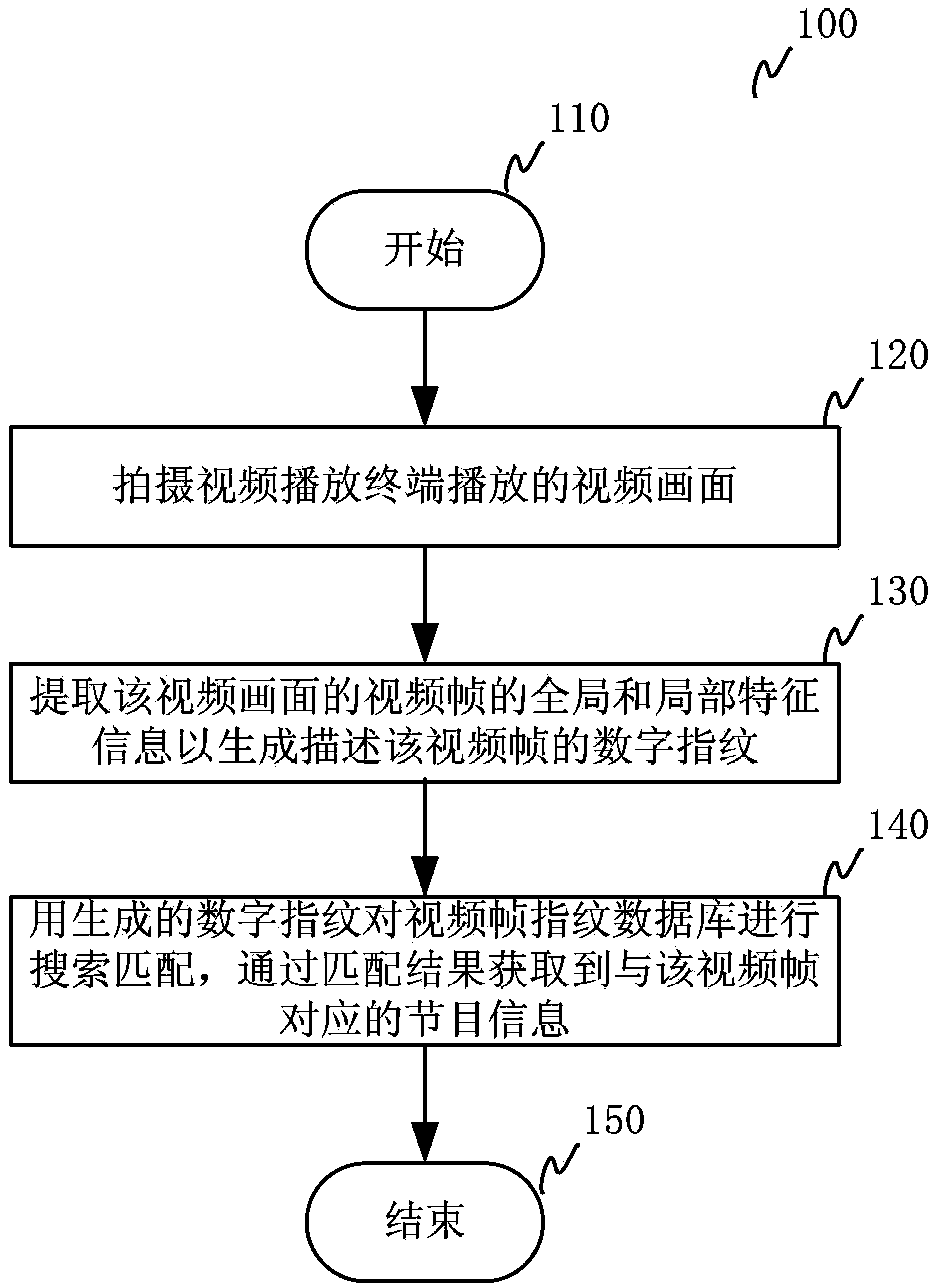
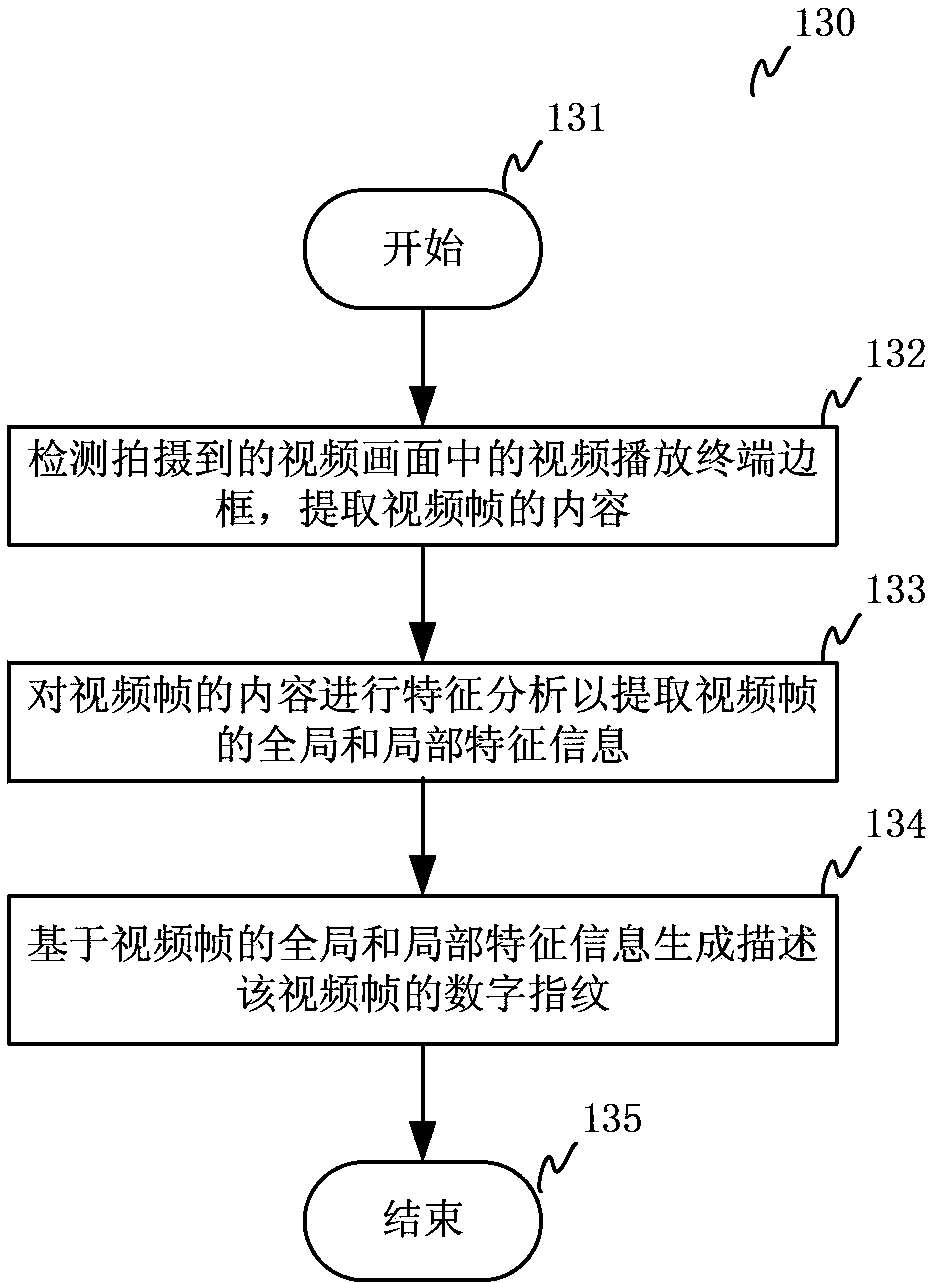
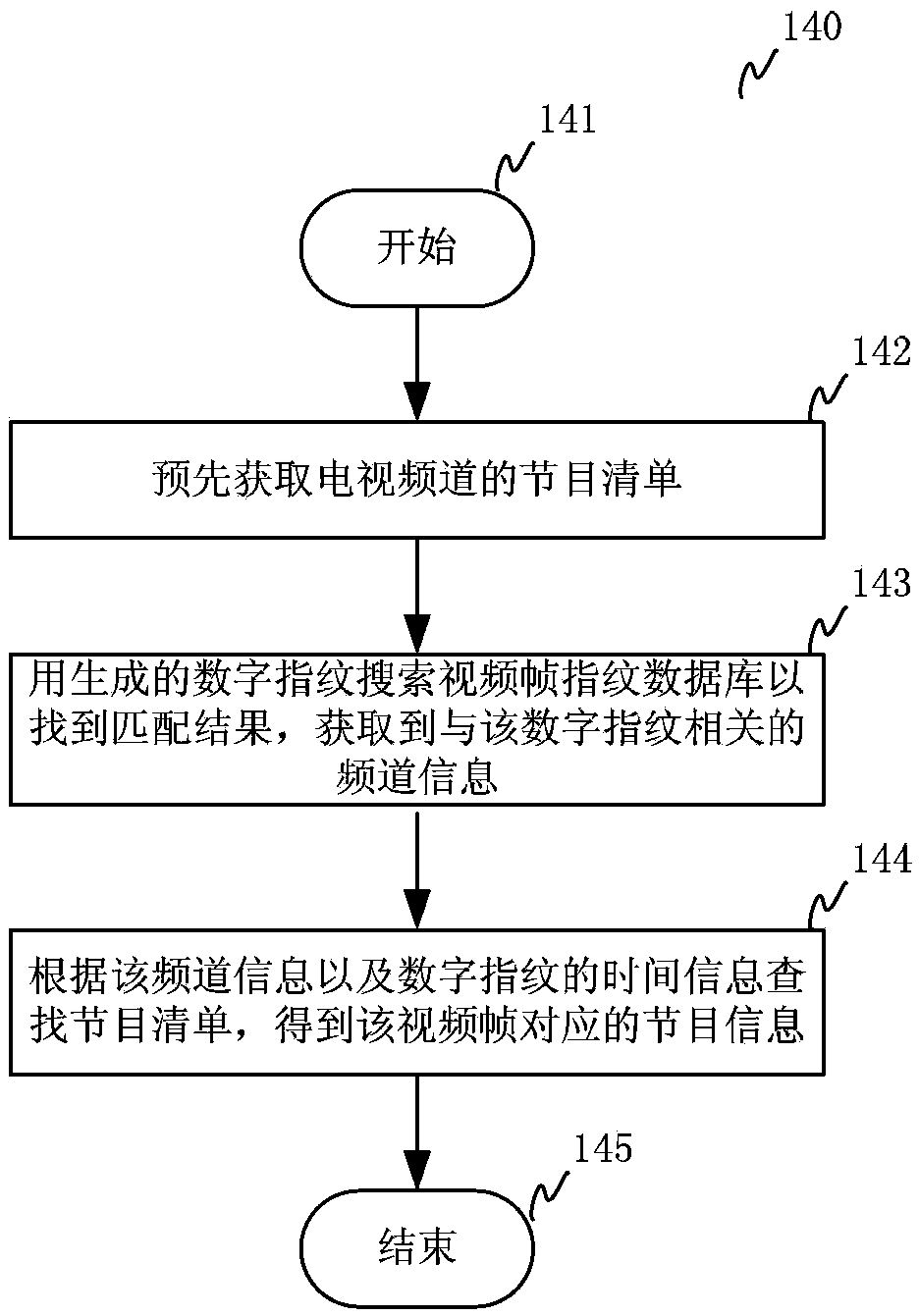
InactiveCN103581705AImprove experienceFast recognitionSelective content distributionSpecial data processing applicationsPattern recognitionRelevant information
The invention relates to a method and system for recognizing a video program. The method comprises the steps that S1, video pictures played by a video play terminal are shot; S2, the overall or local feature information of video frames in the video pictures is extracted to generate digital fingerprints describing the video frames; S3, search matching is carried out on a video frame fingerprint database through the generated digital fingerprints, and program information corresponding to the video frames is acquired through a matching result. The video frame digital fingerprints are generated through the shot video pictures of the video play terminal, the search matching is carried out in the video frame fingerprint database to obtain the corresponding program information, and therefore recognition speed is high, the precision degree is high, and real-time requirements are met. Related information resources on a network are searched for and obtained through the recognized program information and are returned to a mobile communication terminal, a user can acquire the related information of a television program being watched by the user conveniently and fast when watching the video program, the operation is simple, real-time performance is strong, and the user experience effect is good.
Owner:SHENZHEN XINGAN YISOU NETWORK TECH
Authentication-triggered processes
ActiveUS20170300905A1Well formedDigital data information retrievalCharacter and pattern recognitionDigital fingerprintAuthentication
Digital fingerprints (FIG. 1B), are used to authenticate an item. Authentication attempts (730), for a physical item or items, may automatically trigger actions or processes (FIG. 7) related to the attempted item or item or to other items. Different processes may take place depending on whether the authentication was successful (732, 912, 1012). The additional process(es) may be computer-implemented, for example, using executable scripts (740). The triggered action(s) may be immediate (“real-time”), or delayed, deferred, or batched, etc. At least one additional action or process is triggered or initiated, locally or remotely, by at least one affirmative authentication result (730) or at least one additional action or process is triggered or initiated, locally or remotely, by a least one unsuccessful authentication attempt (917, 1020). In one example, methods and systems are disclosed to realize a combination of purchase and authentication of an item into a single action (842).
Owner:ALITHEON INC
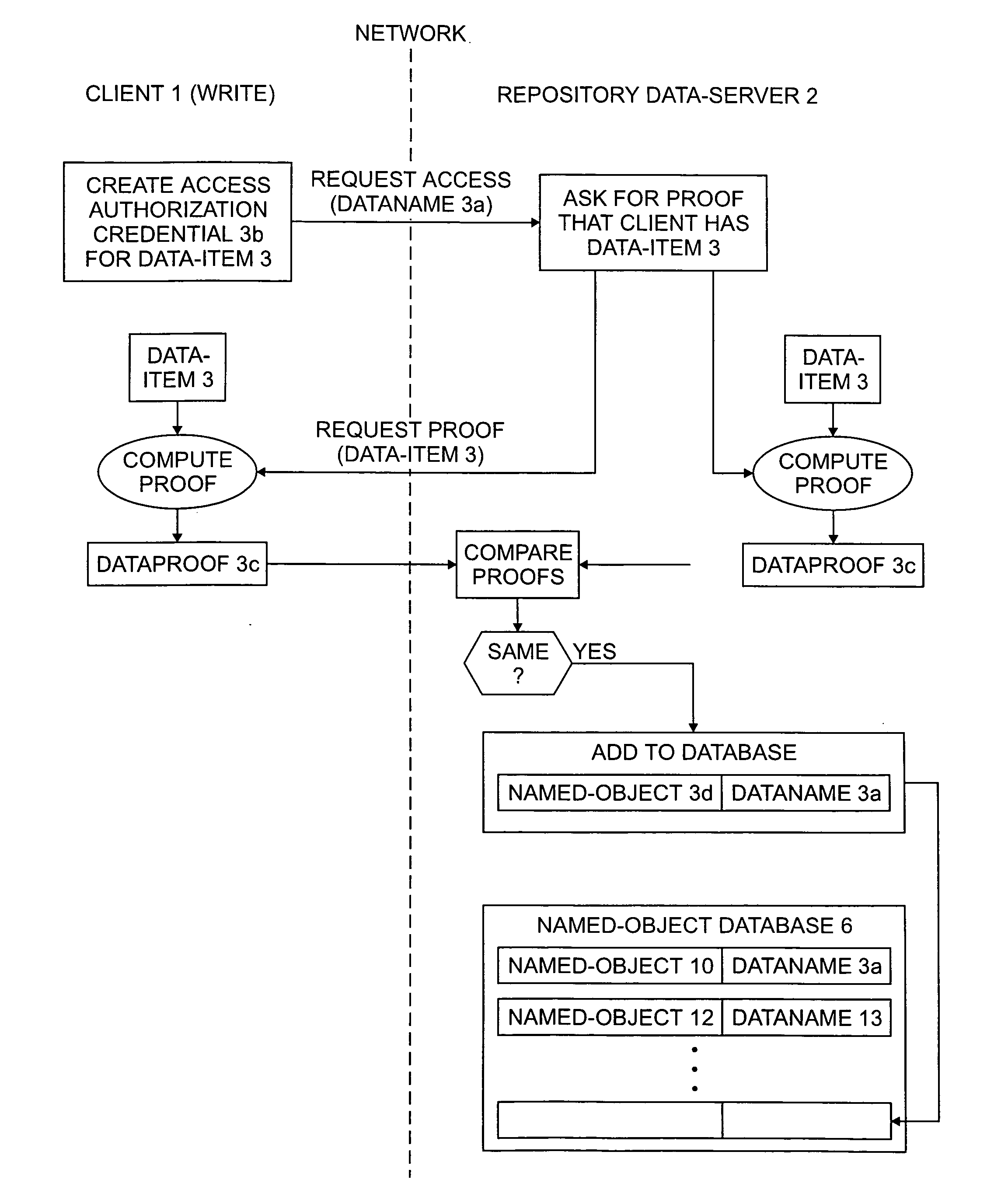
Data repository and method for promoting network storage of data
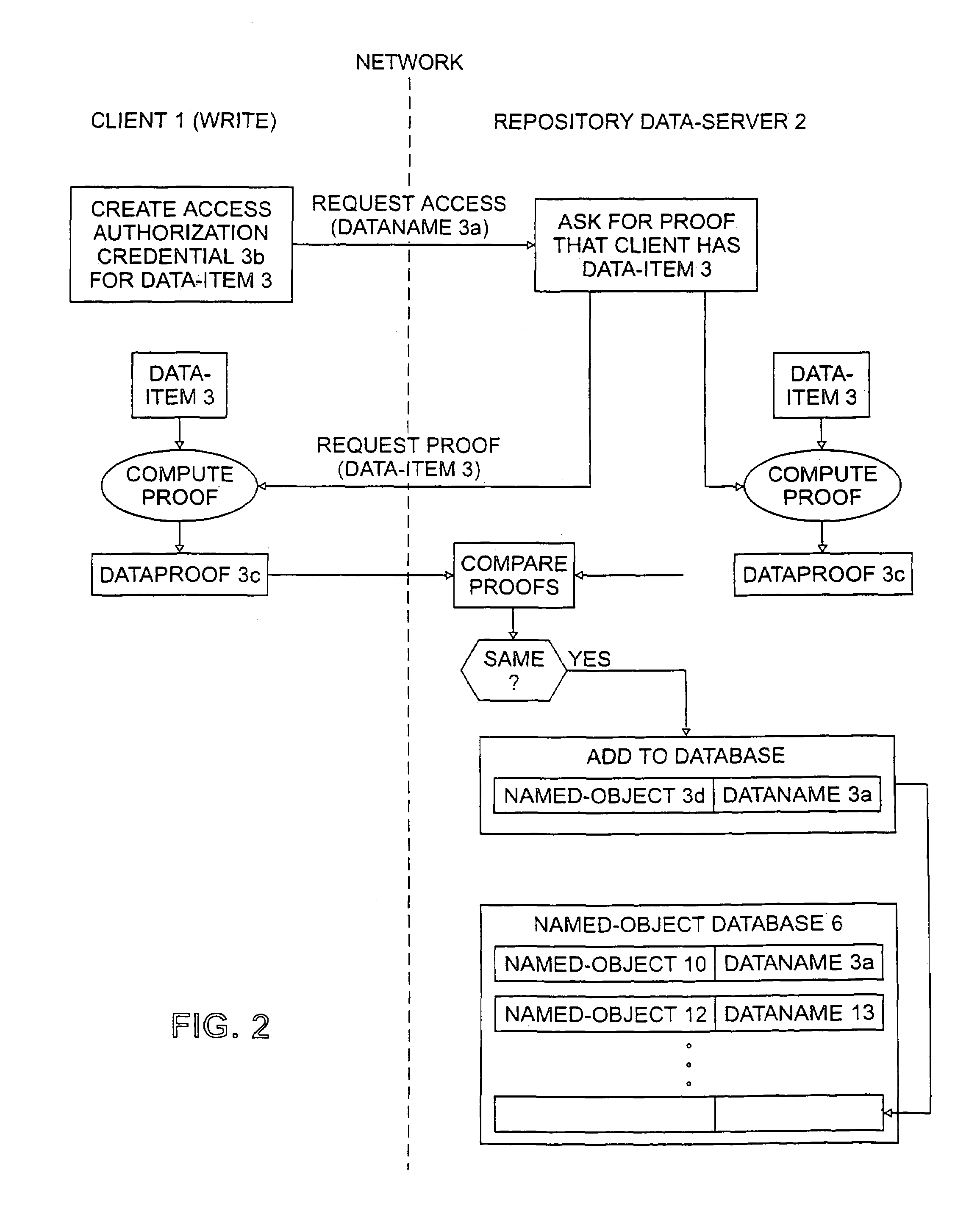
InactiveUS20050131905A1Digital data information retrievalDigital data processing detailsClient-sideDigital fingerprint
A method by which more than one client program connected to a network stores the same data item at the same location or locations in a data repository connected to the network, the method comprising having a first client program deposit a first data item in a data repository, the depositing including determining a digital fingerprint from the data item using a reproducible pseudorandom process that produces digital fingerprints having a pseudorandom distribution, storing the data item in the data repository at a location or locations associated with the digital fingerprint, and associating a deletion permission token with the data item, and storing this association in the data repository, having a second client program initiate a process for depositing a second data item in the data repository, wherein the second data item is identical to the data item stored by the first client program, the process including determining a digital fingerprint from the second data item using the reproducible pseudorandom process, determining from the digital fingerprint that a data item identical to the second data item is already stored in the data repository, relying on the data item already stored in the data repository for storage of the second data item rather than storing a separate copy of the second data item, and associating a second deletion permission token with the data item already stored, and storing this association in the data repository, having a client program initiate a process for deleting the data item already stored in the repository, wherein a deletion permission token associated with the data item is deleted from the repository, but the data item itself is not deleted.
Owner:RED HAT
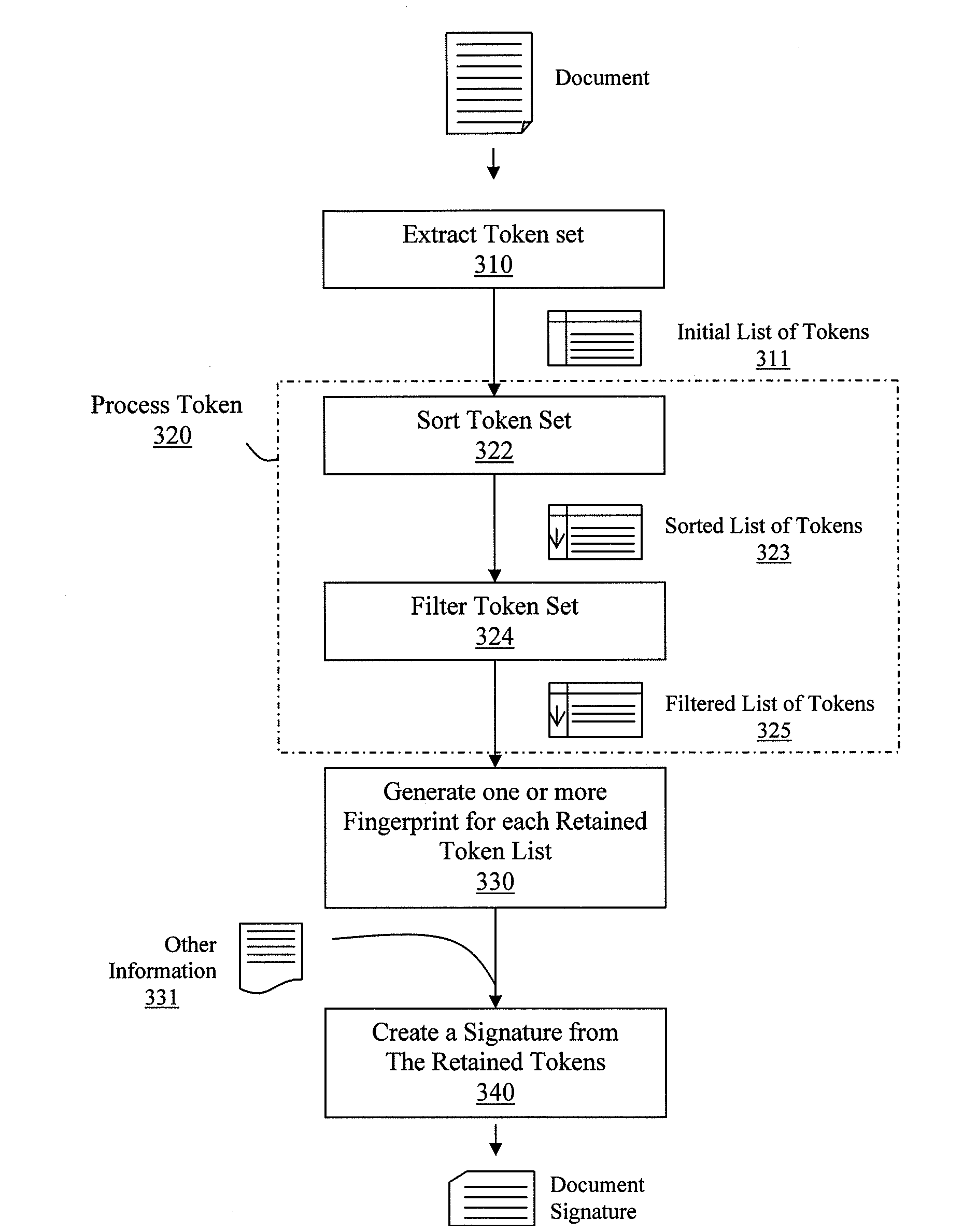
Automated forensic document signatures
ActiveUS20100287196A1Facilitate methodDigital data processing detailsPlatform integrity maintainanceDocument preparationDigital fingerprint
Owner:GEORGETOWN UNIV
Media player operable to decode content data
InactiveUS20060195909A1Simple authorisation processFunction increaseTelevision system detailsPulse modulation television signal transmissionObfuscationData content
Content is provided on a medium or is transmitted, for example streamed, with in-built protection against unauthorised playback or copying. Video content data is provided in content blocks, each of which relates to a video frame and has a corresponding header. Some content clocks have an excess data item, such as a digital fingerprint, interposed somewhere in the data comprising that content block. Thus, the amount of the data in the content block is increased by the addition of the digital fingerprint. Information identifying the length of the content block in the corresponding header is not altered. Some or all content blocks are obfuscated following the additional of the digital fingerprints. In a media player, de-obfuscation is performed, and digital fingerprints then removed before the resulting content blocks are decoded. Without de-obfuscation and removal of the digital fingerprints, correct decoding would not occur. Thus, playback of the content is limited to a media player that knows the de-obfuscation scheme used and knows the locations of the digital fingerprints.
Owner:ROK PROD LTD
Distributed frequency data collection via DNS
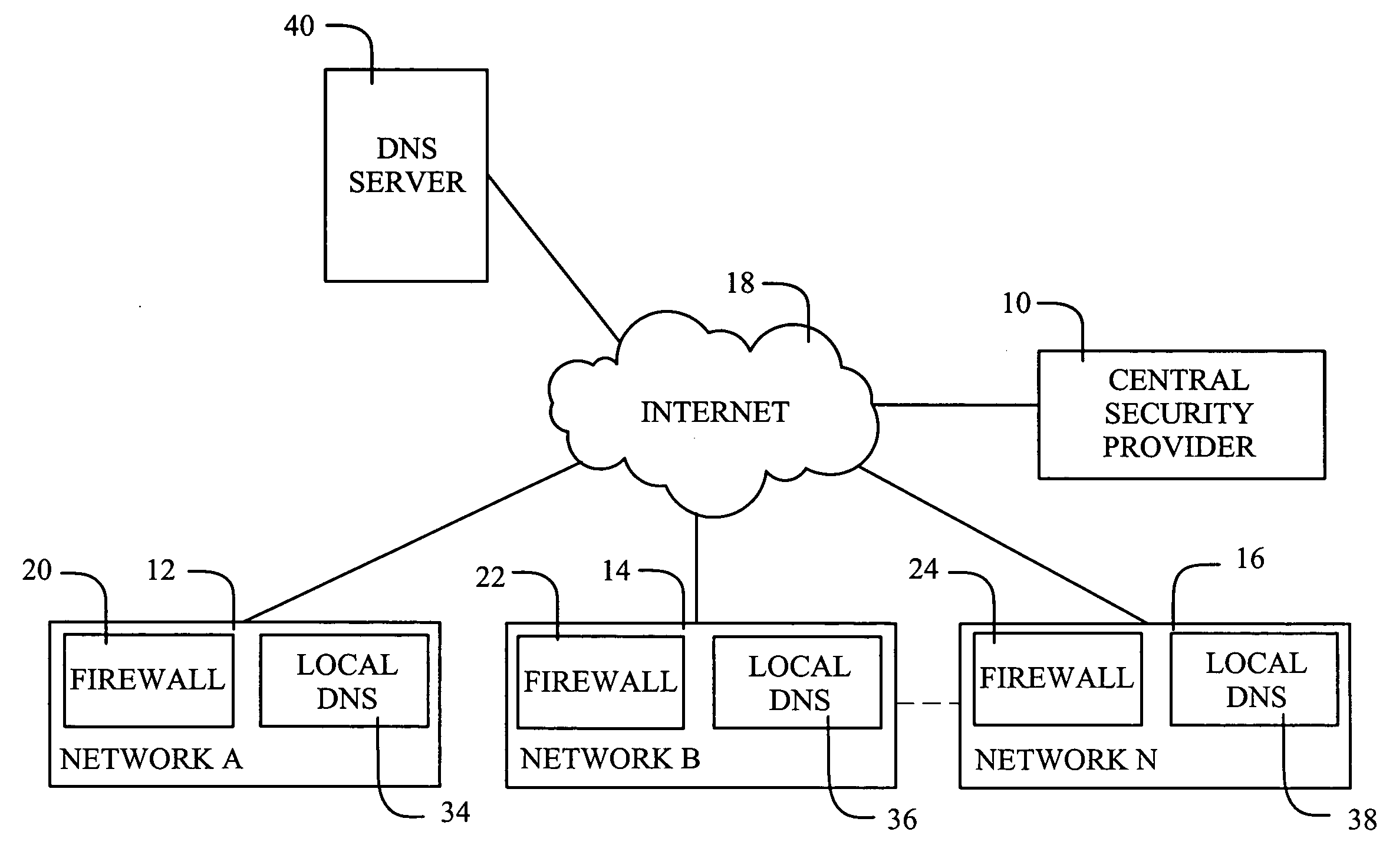
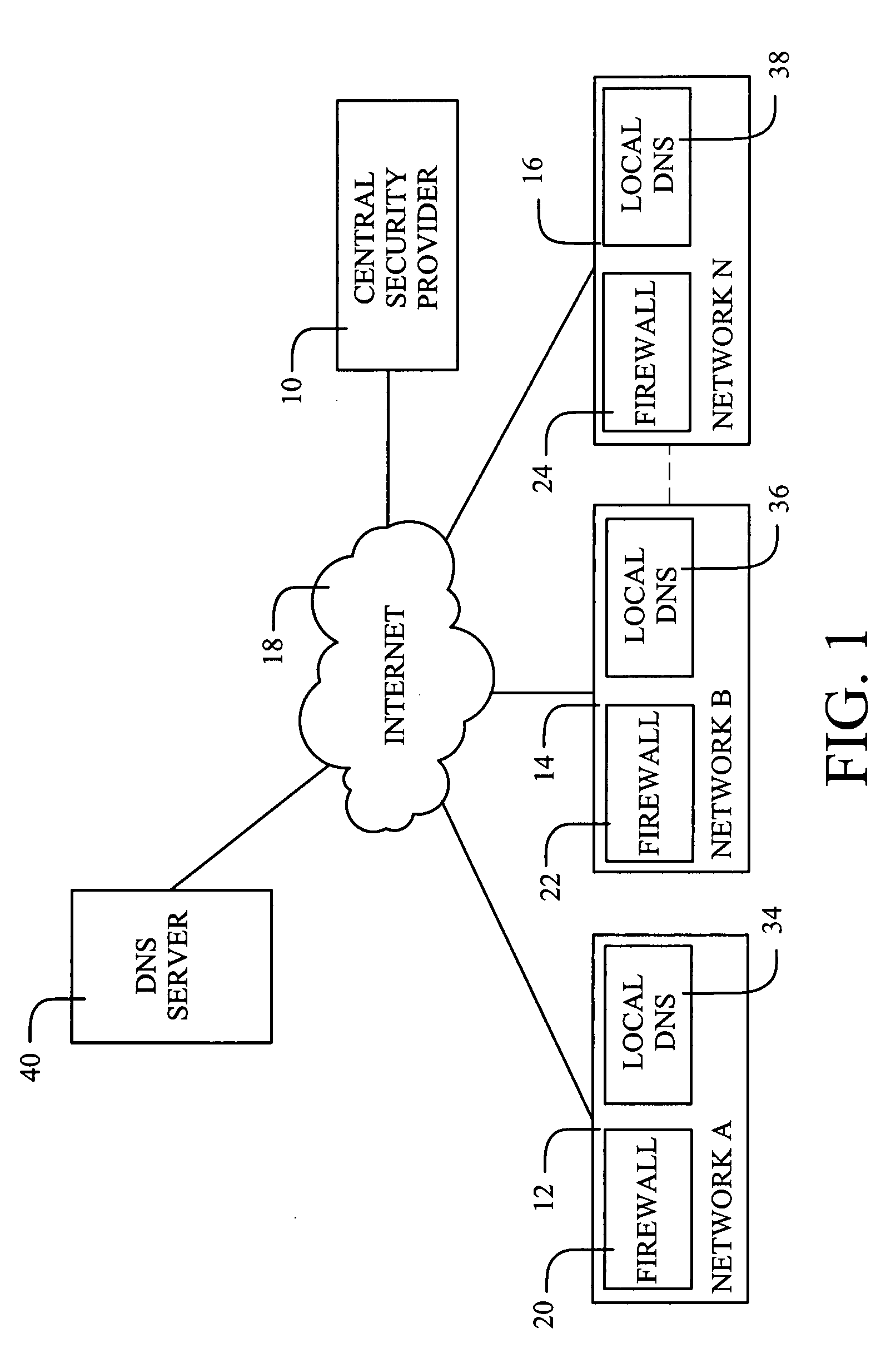
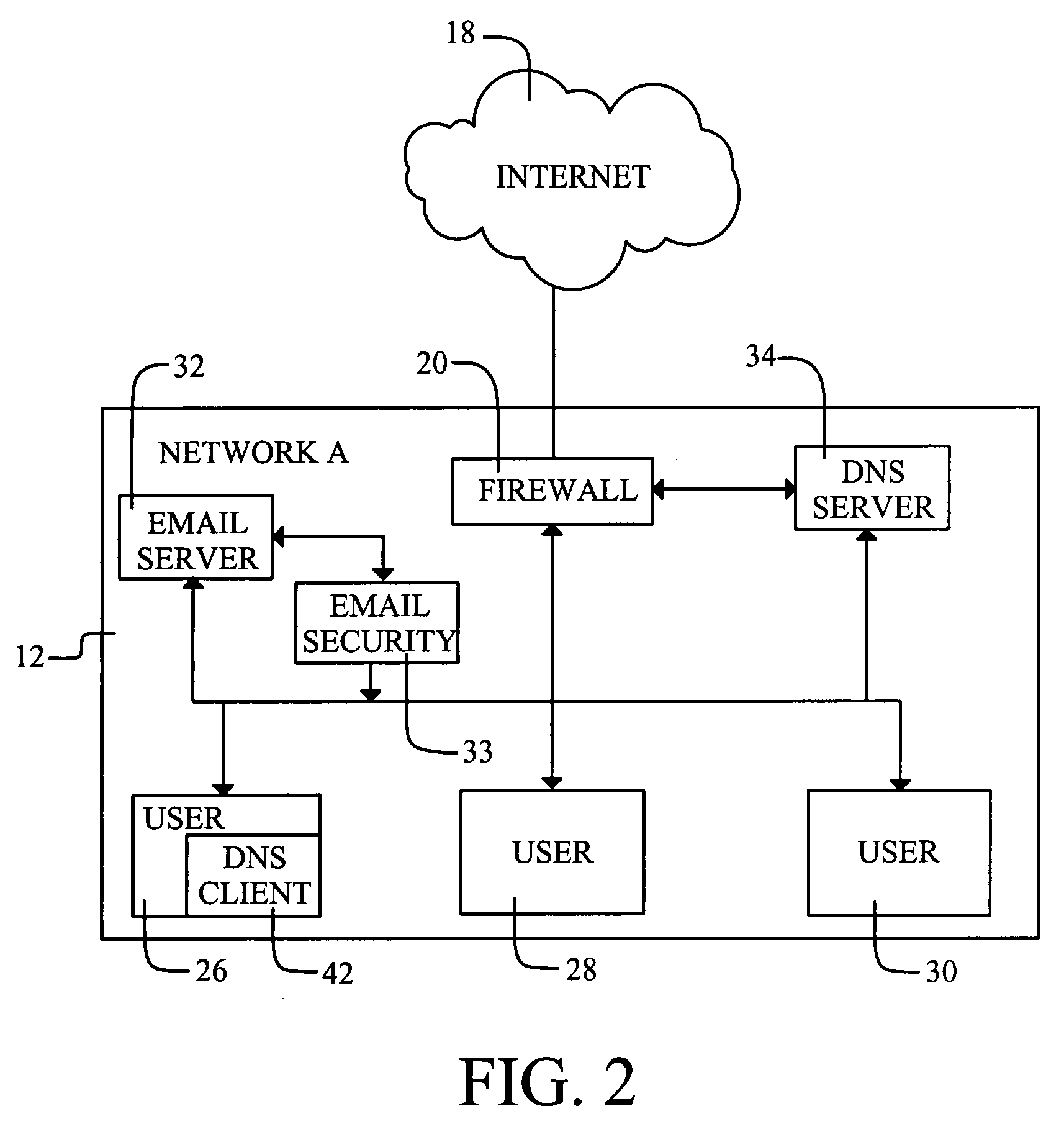
InactiveUS20090083413A1Digital data processing detailsUser identity/authority verificationDomain nameNetworked Transport of RTCM via Internet Protocol
Domain Name Service (DNS) requests are used as the reporting vehicle for ensuring that security-related information can be transferred from a network. As one possibility, a central facility for a security provider may maintain a data collection capability that is based upon receiving the DNS requests containing the information being reported. In an email application, if a data block is embedded within or attached to an email message, an algorithm is applied to the data block to generate an indicator that is specifically related to the contents of the data block. As one possibility, the algorithm may generate a hash that provides a “digital fingerprint” having a reasonable likelihood that the hash is unique to the data block. By embedding the hash within a DNS request, the request becomes a report that the data block has been accessed.
Owner:BARRACUDA NETWORKS
System and method to validate and authenticate digital data
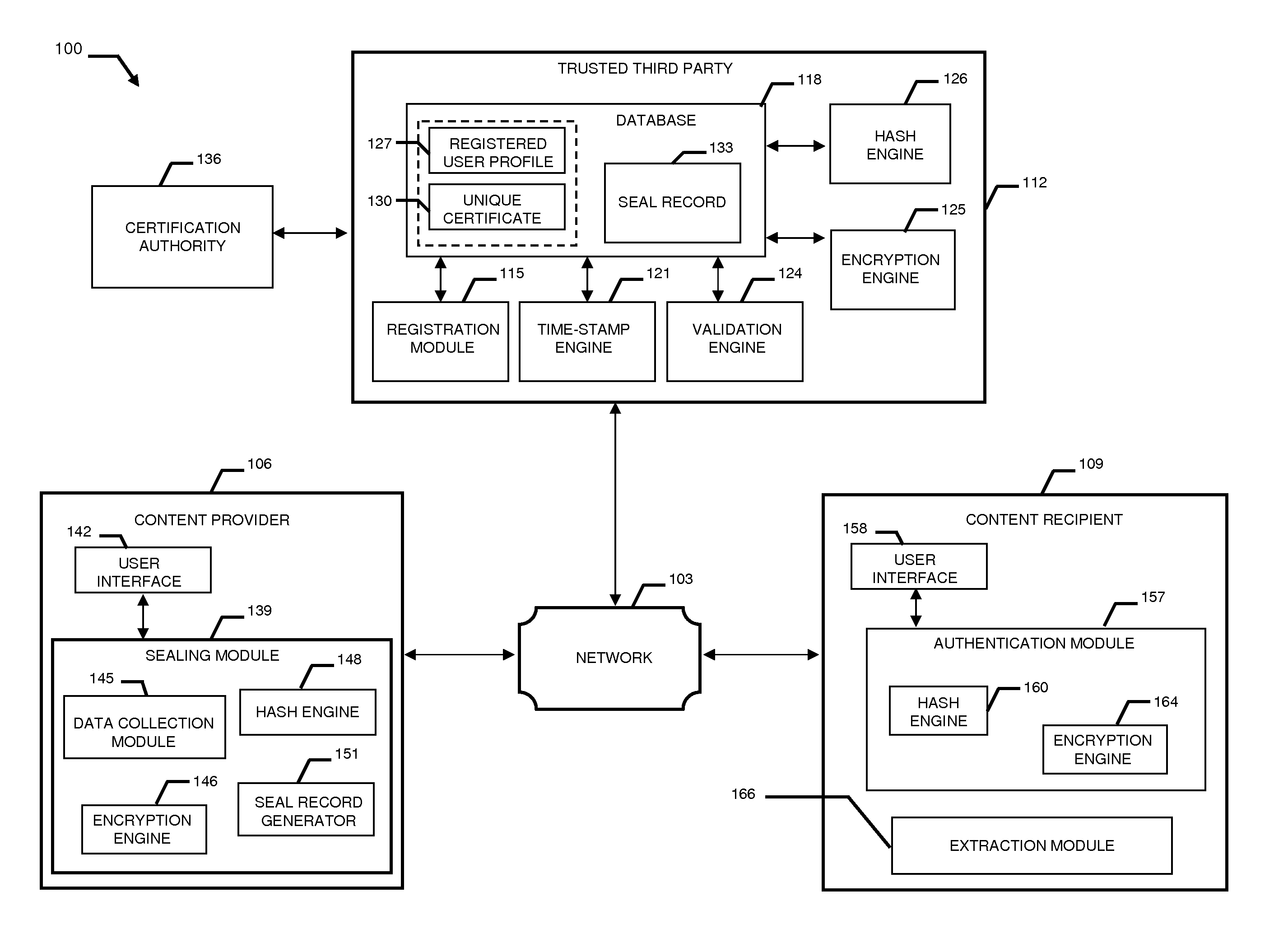
InactiveUS20110231645A1Data can be securedDigital data processing detailsUser identity/authority verificationDigital dataDocument Identifier
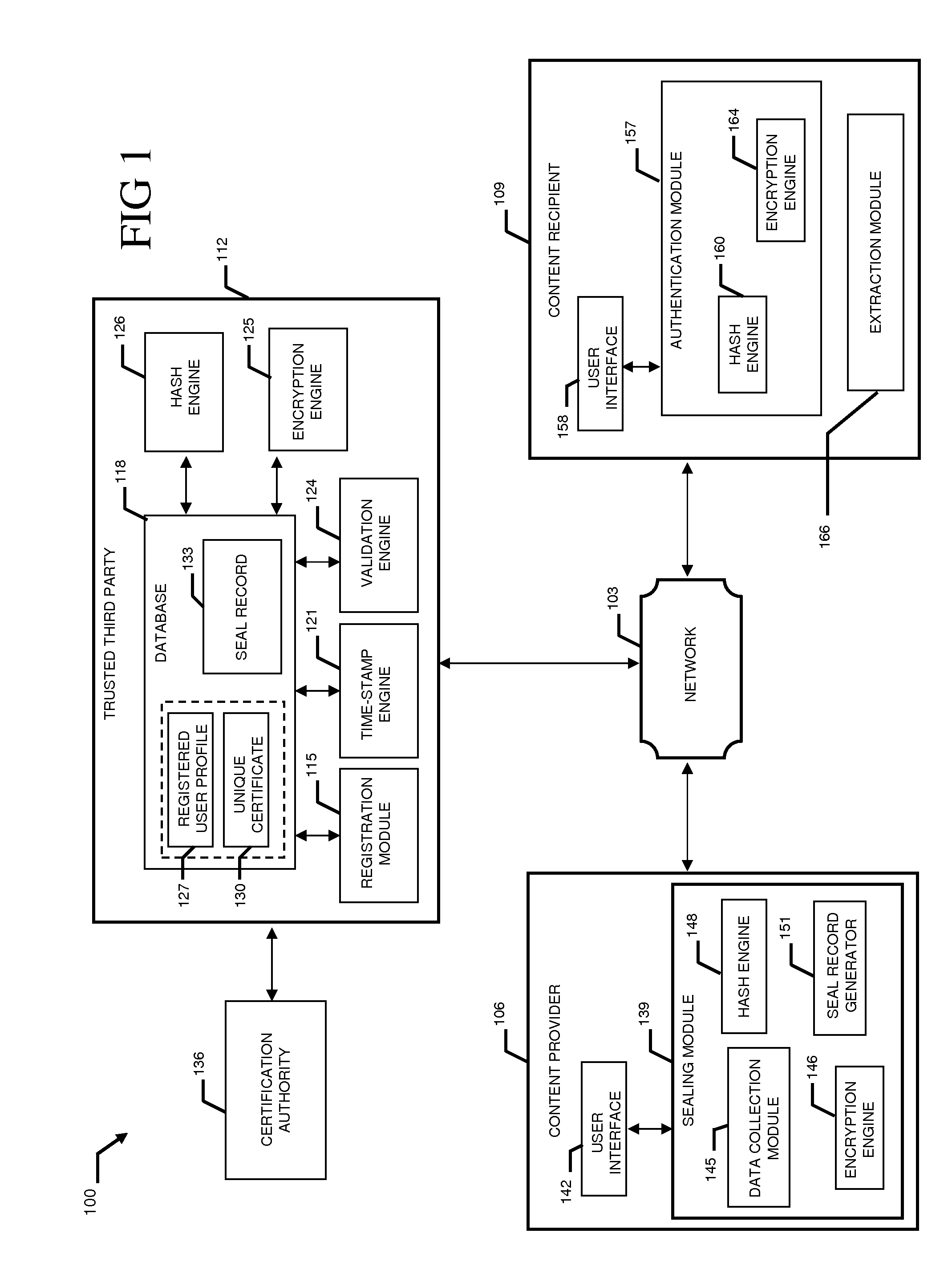
A system and method combining registration with a trusted third party, certificate generation, hashing, encryption, customizable file identification fields, and time-stamping technology with recognized “best practice” procedures to achieve the legal admissibility and evidential weight of any form of digital file or collection of digital files. Generally, the originator of the file (the first party) and the originator's employing organization are registered with a Trusted Third Party. The originator reduces the file, by means of a hashing algorithm, to a fixed bit length binary pattern. This provides a unique digital fingerprint of the file. The resultant hash value, the originator's identity details, the employing organization details associated and securely linked to the digital certificate, the title of the file, customizable file identification fields, and other relevant data are forwarded to a Trusted Third Party where the date and time from a known and trusted time source are added. The customizable file identification fields can provide the originator with a mechanism for configuring the seal to incorporate as much additional information as deemed necessary to prove the authenticity of the digital content and / or provide data for the purposes of adding value in functions such as source identification, sorting, analysis, investigation, and compliance. Such information could include, but would not be limited to, location / GPS coordinates, machine id, biometric information, smart-card data, reason for sealing. The original file does not leave the control of the originating party. When combined, the forwarded details and date and time create a Seal Record. The Seal Record is encrypted and hashed. The Seal Record along with all other relevant information are retained on a central secure server. The recipient of the file (the second party) can confirm the file has been received in an unaltered state with integrity retained and it is the authentic version by validating the file.
Owner:CYBERCUBE
Systems and methods of fingerprinting and identifying digital versatile disc
ActiveUS20080040807A1Digital data processing detailsRecord information storageObject basedDigital fingerprint
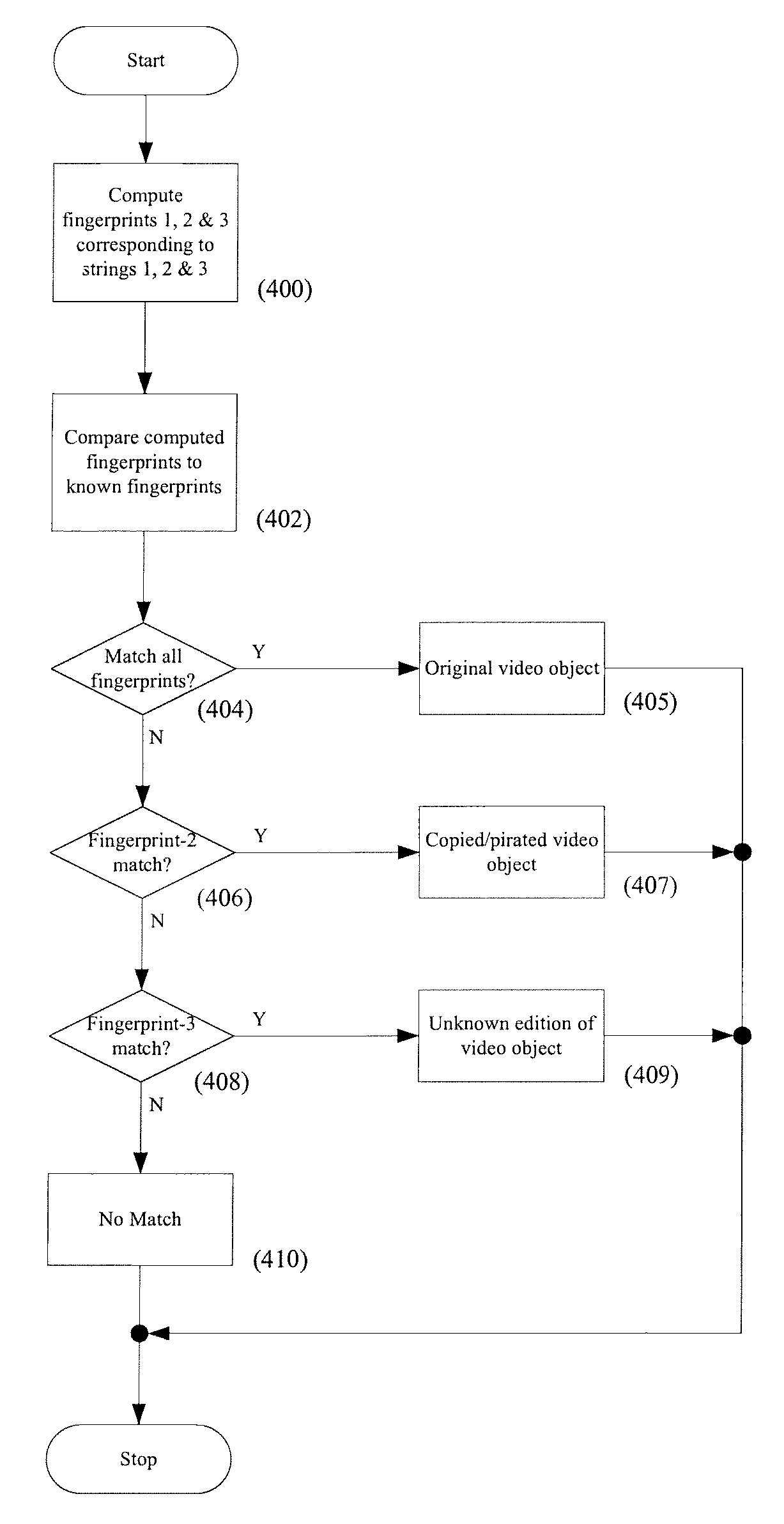
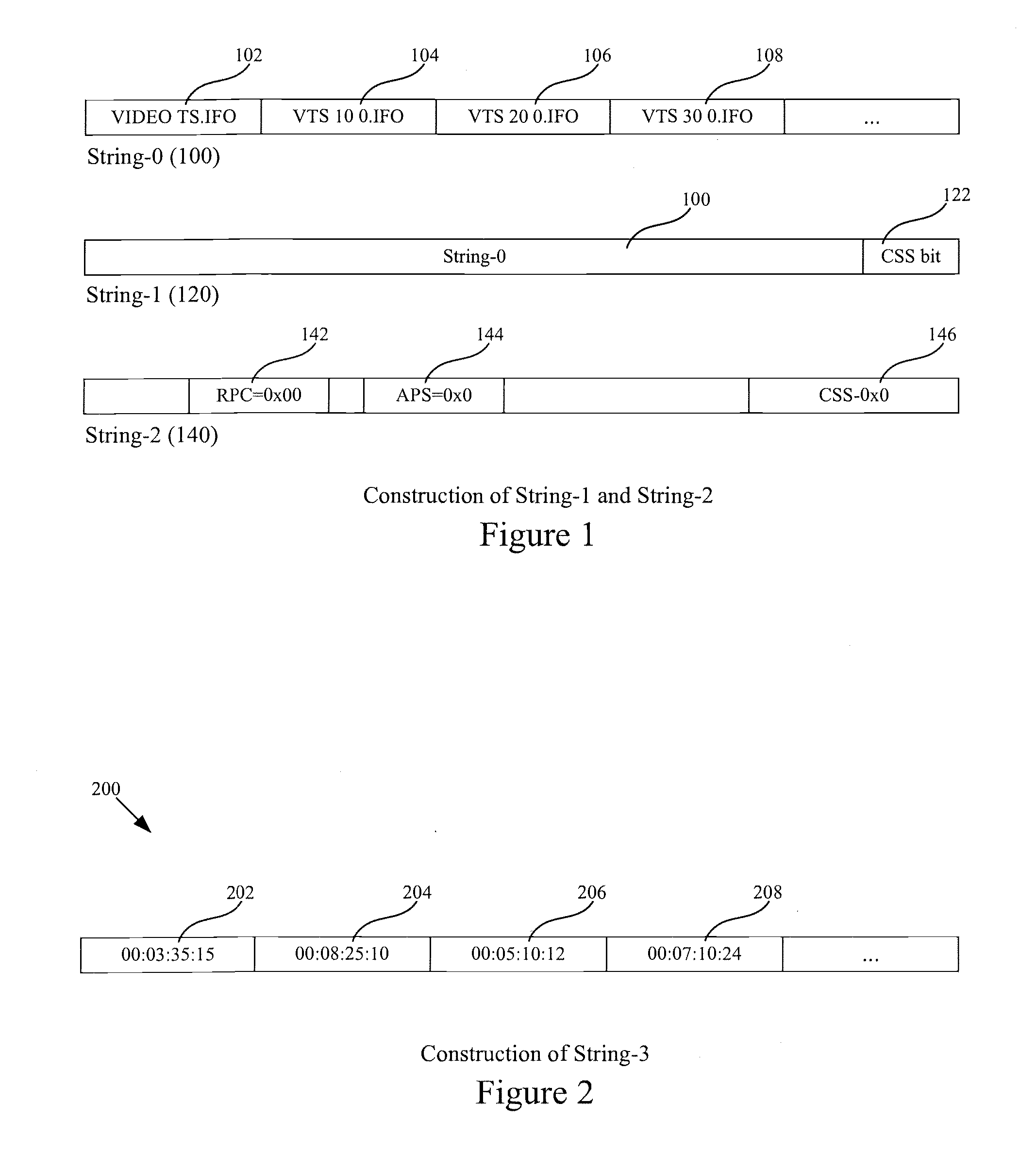
Systems and methods are provided for identifying a video object using digital fingerprints. The digital fingerprints are generated from information extracted from the video object including encoded video. The digital fingerprints can be calculated in a manner that permits identification of both the video object and operational characteristics of the video object based on matching calculated digital fingerprints with known fingerprints of known video objects. Systems and methods are described that allow a DVD to be uniquely identified and identify whether the DVD is original, copied or pirated. Systems and methods are described for computing digital fingerprints from strings of bits in which certain additional data is optionally embedded. Systems and methods are described that permit media players to access known signatures of known video objects maintained on one or more databases and to identify video objects presented for playing on the media player.
Owner:VOBILE
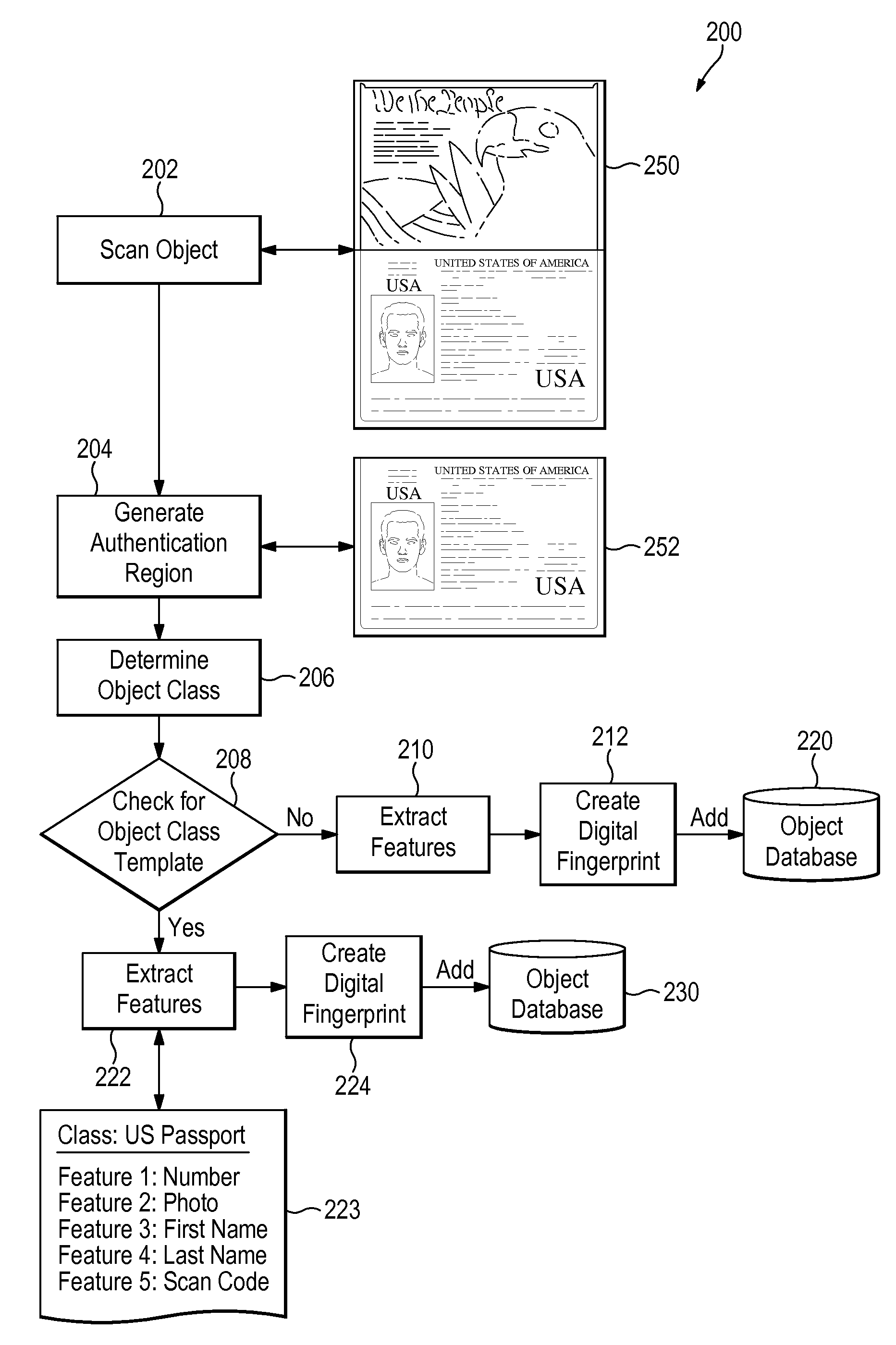
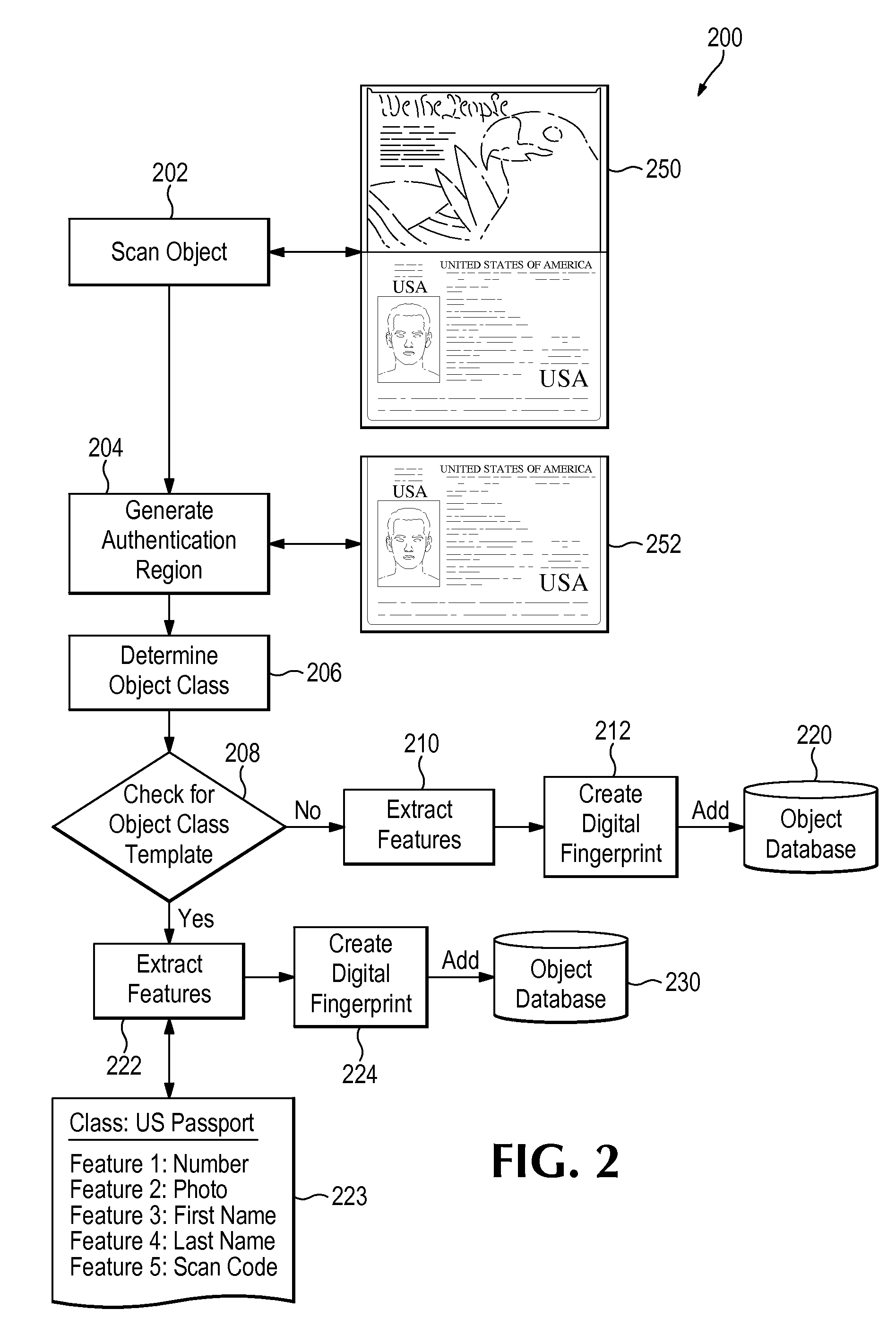
Digital fingerprinting object authentication and anti-counterfeiting system
Improvements are disclosed for authentication of an object, verification of its provenance, and certification of the object as compliant with manufacturing standards. Or, an object may be reported as a suspected counterfeit. In one embodiment the system compares a digital fingerprint of the object, based in image capture, to digital fingerprints previously stored in a database and determines if the object has been registered before and is thus authentic. An object feature template may be created which has a list of features and attributes that are relevant for authenticating particular classes of objects. The object feature template can also be used to examine unregistered objects for signs of counterfeiting.
Owner:ALITHEON INC
Fingerprint collection system and fingerprint information collection method
ActiveCN103810479ARefuse to cheatImprove securityCharacter and pattern recognitionCollection systemMode control
The invention relates to a fingerprint collection system comprising a fingerprint sensor, a scanning controller, a sensing unit driving circuit, an image output unit and a mode control circuit. The fingerprint sensor comprises a fingerprint sensing unit array, an antenna metal frame and a radiofrequency driving circuit; the fingerprint sensing unit array includes multiple sensing units, and the radiofrequency driving circuit drives the antenna metal frame to transmit radiofrequency signals. The scanning controller is used for selecting at least part of the sensing units of the fingerprint sensing unit array to serve as effective sensing units for sensing fingerprints and converting the same into electric signals. The sensing unit driving circuit is used for providing time-sequence signals needed for work of the effective sensing units. The image output unit is used for converting electric signals into digital fingerprint image information and outputting the information. The mode control circuit is used for controlling the sensing unit driving circuit to send different time-sequence signals to change working modes of the fingerprint collection system. The working modes at least include a capacitive collection mode and a radiofrequency collection mode. The fingerprint collection system has wide application range and has good collection and recognition effects in various application fields.
Owner:成都费恩格尔微电子技术有限公司 +1
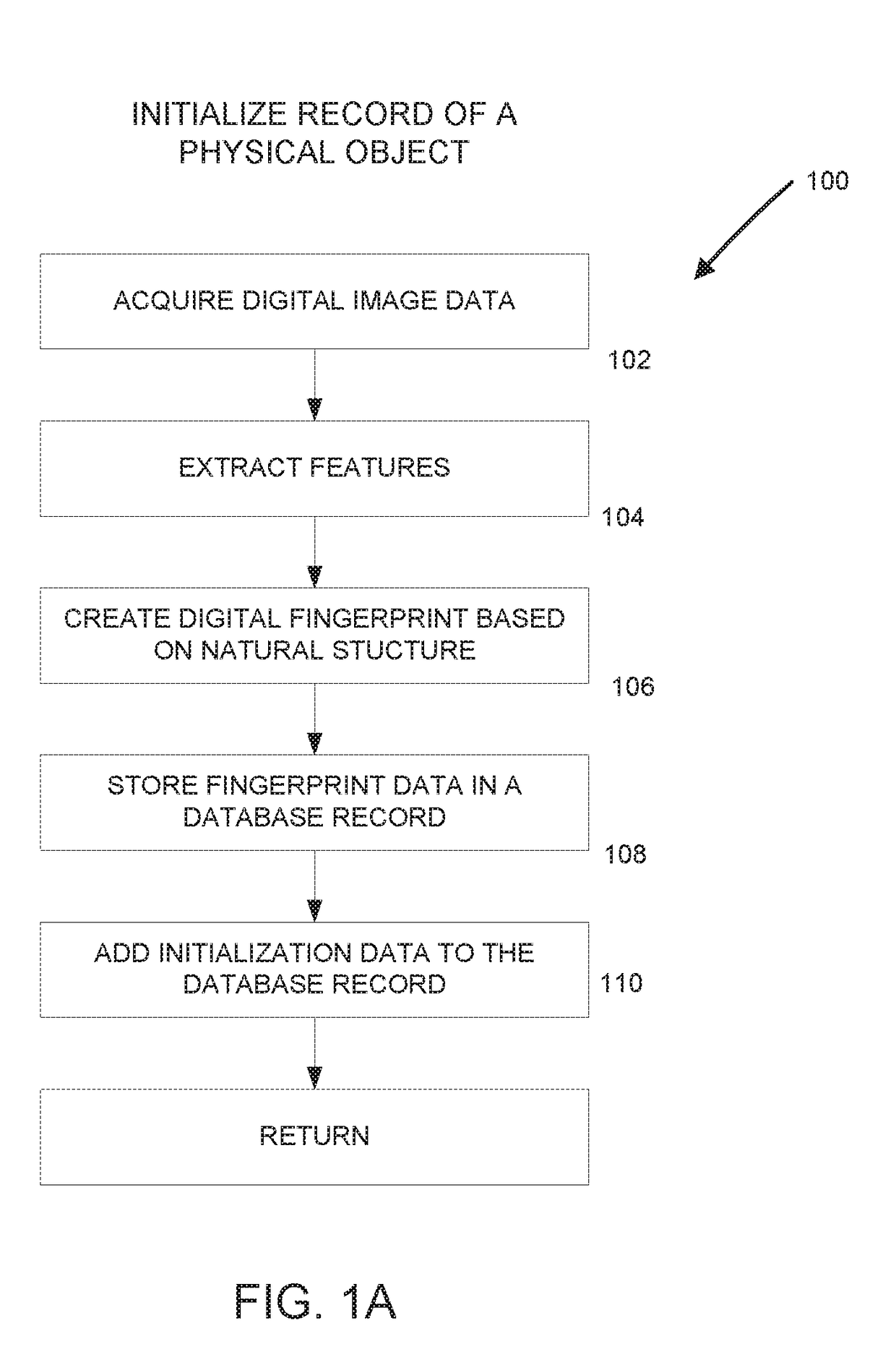
Digital fingerprinting track and trace system
ActiveUS20150067346A1Well formedDigital data information retrievalData processing applicationsPaper documentDigital image
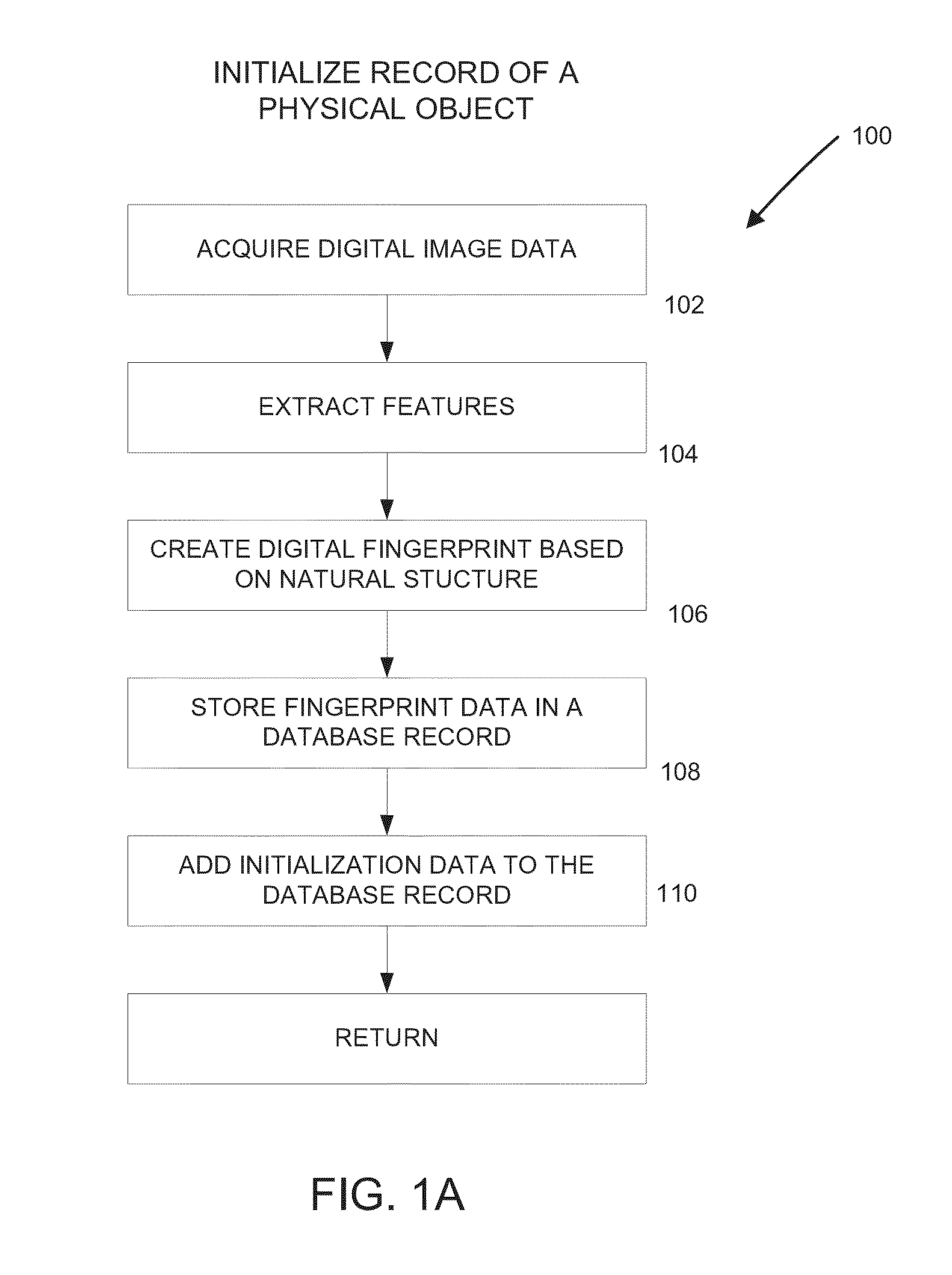
Methods and systems for tracking a physical object to identify or authenticate it utilizing digital fingerprints which are based on natural features extracted from a digital image of the object. Digital fingerprints do not require or rely on any labels, tags, integrated materials, unique identification characters, codes or other items that may be added to the object specifically for the purpose of identification. Consequently, the disclosed digital fingerprint techniques help to detect or prevent unauthorized alterations of documents, apparel, drugs and pharmaceuticals, etc. Further digital fingerprints can be used to better track and trace a wide variety of objects throughout the distribution chain to demonstrate their provenance and to detect counterfeit objects.
Owner:ALITHEON INC
Method for Analyzing Activities Over Information Networks
InactiveUS20080162397A1Knowledge representationData switching networksLawful interceptionInformation networks
The present invention is a method for analyzing large volumes of network information for the purpose of identifying particular patterns of behavior in a plurality of connections. It enables identifying unique digital fingerprints of particular users, be it individuals, groups or organizations, and tracks their activities in large scale information networks such as corporate wide area networks or the public internet despite attempts on the part of the users to hide their identity. By recognizing unique identifiers and distinguishing patterns of behavior the method may differentiate between different users all using a single connection, or identify a single entity across multiple connections. The method may be applicable for tracking hostile entities inside an organizational network. Advertisers may uniquely and anonymously track the activities of users. The method may also be used to track and identify suspicious activities by law enforcement agencies via lawful interception of network data.
Owner:ZALTZMAN ORI
Method of processing postal items including management of digital fingerprints of the postal items
InactiveUS7674995B2Limited spaceEasy to implementSeparation devicesCharacter and pattern recognitionDigital imageDigital fingerprint
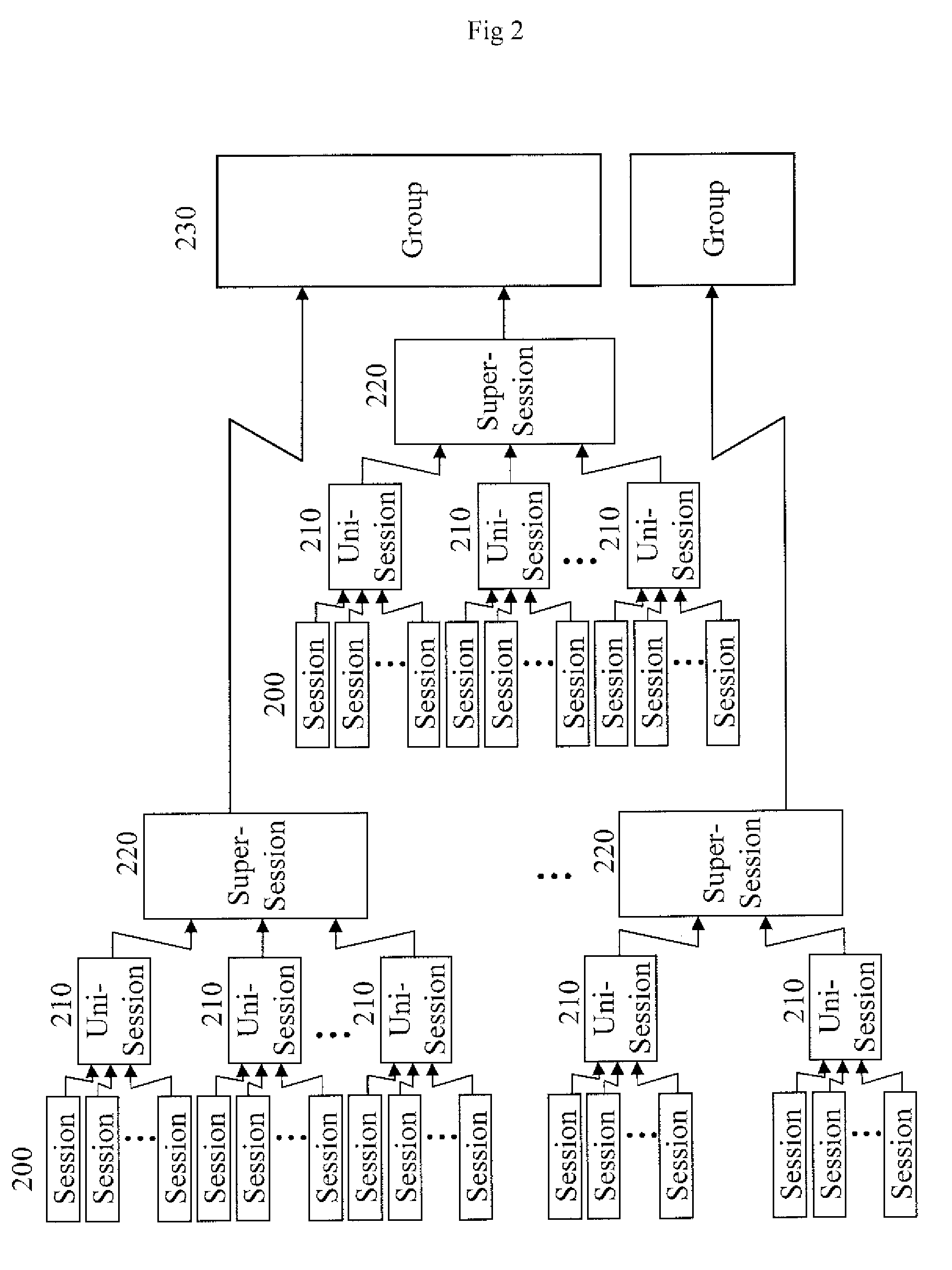
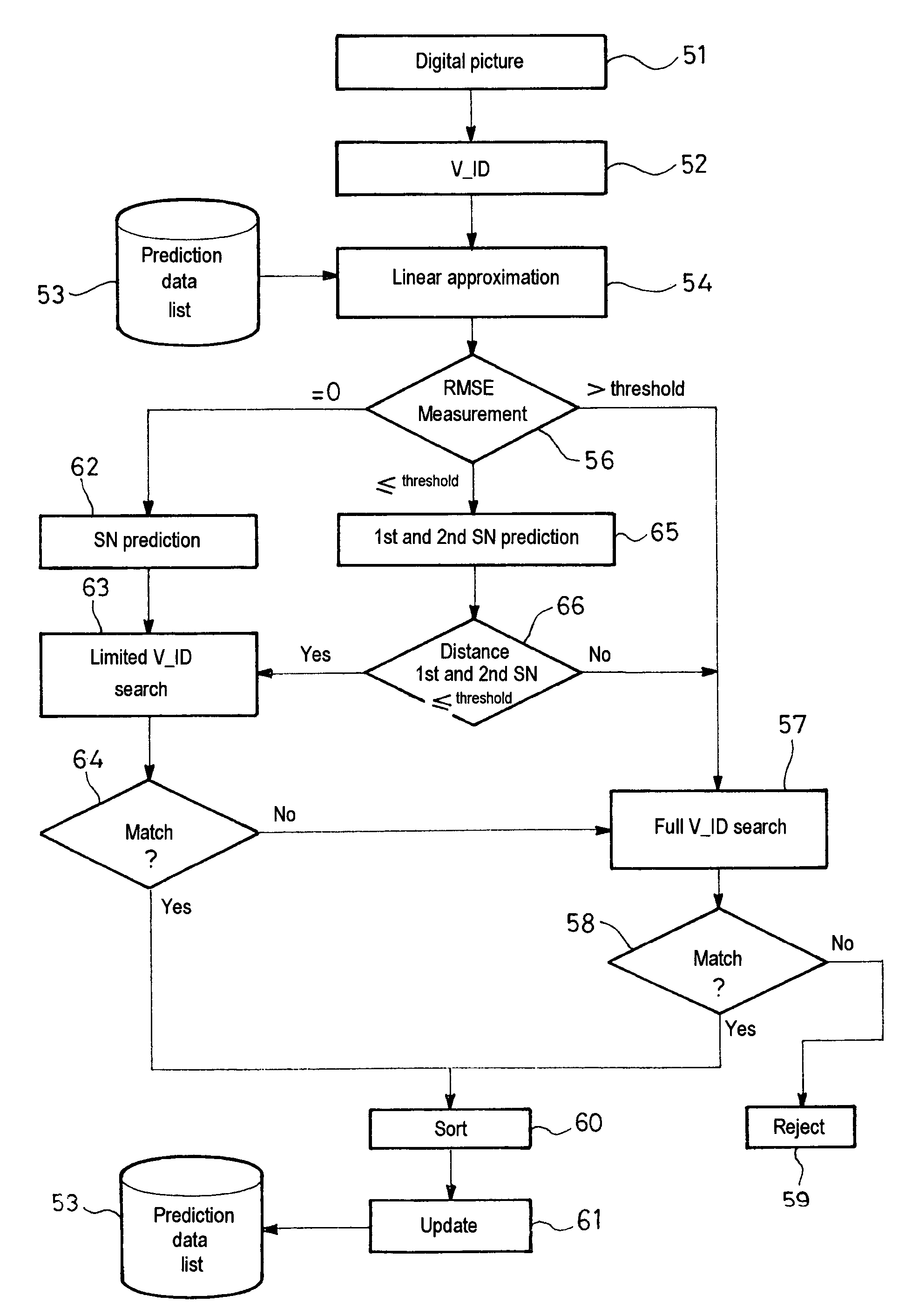
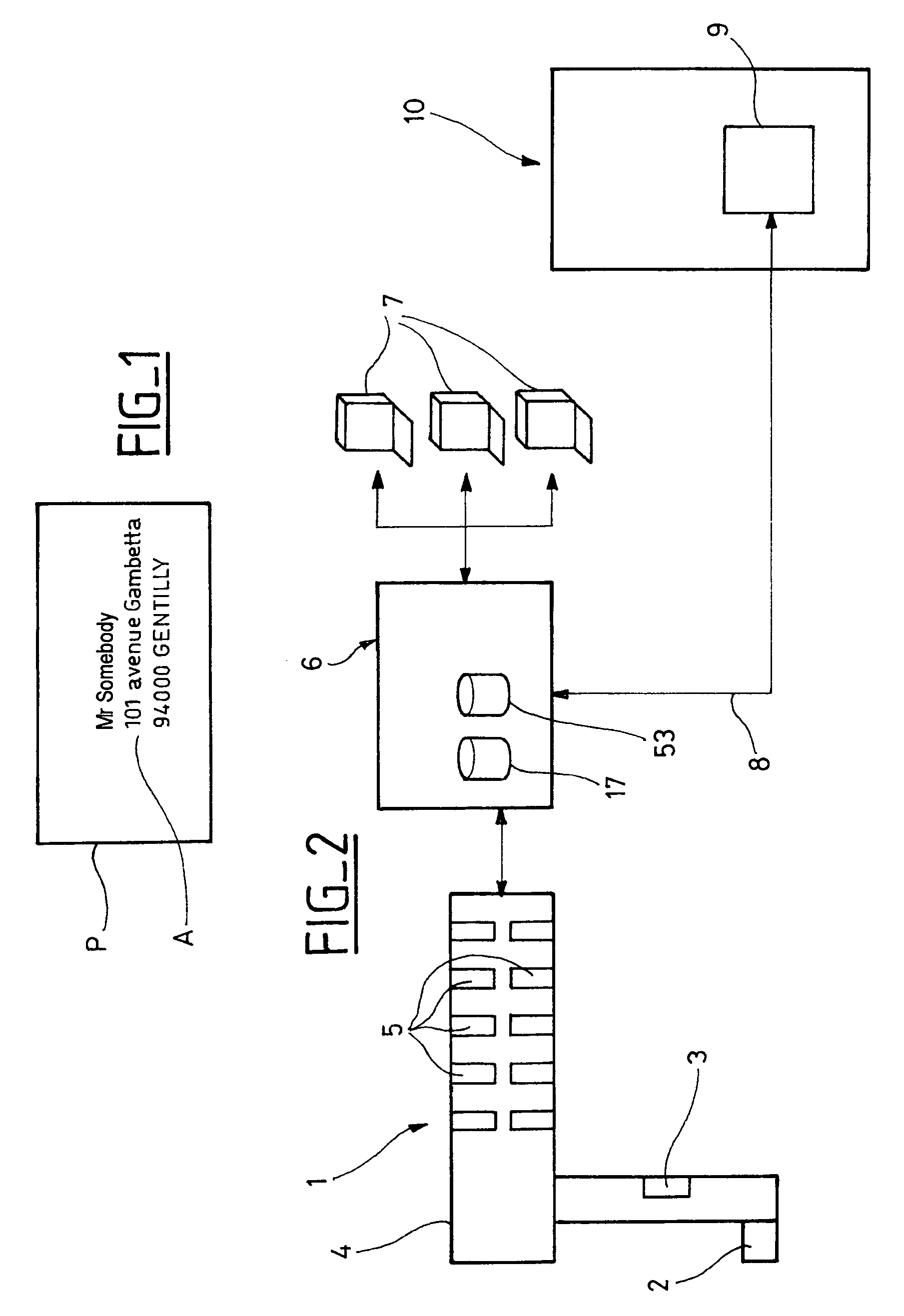
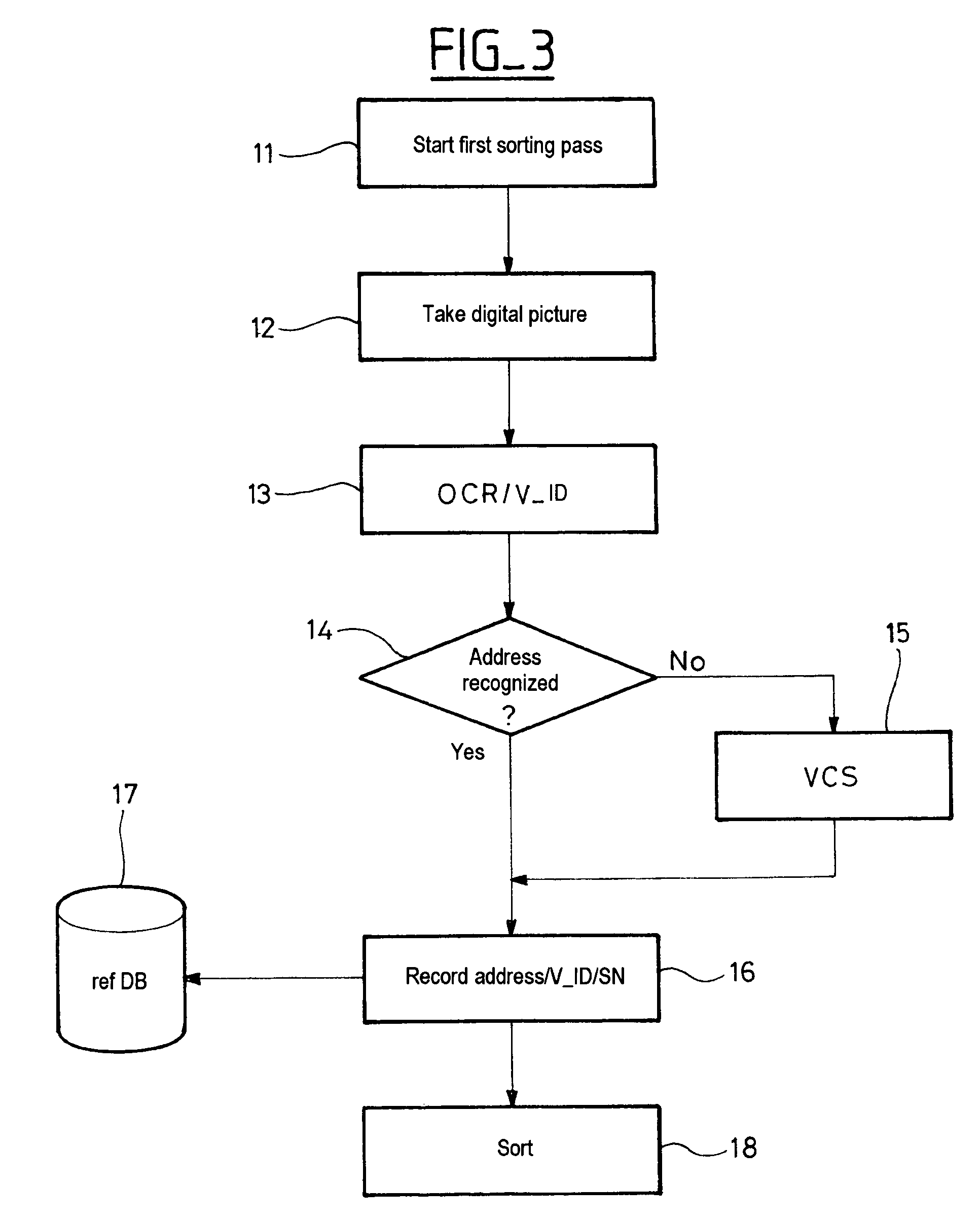
The invention concerns a method for processing postal packets including managing digital impressions of the postal packets. In a method for processing postal packets, during a preliminary sorting of the packets, a digital image of a packet comprising an address information is formed, a digital impression (V-Id) is derived from said image which constitutes a logical identifier for the packet and the packet impression is recorded in memory corresponding to data indicating the packet address information, and during a second sorting of the packets, a digital image of a current packet is formed again (51) comprising an address information, a digital impression for the current packet is derived (52) from said image and a search is performed among the recorded impressions in the preliminary sorting for a match with the current packet impression.
Owner:SOLYSTIC
Generating statistics of popular content
ActiveUS8959202B2Reduce data transferIncrease speedUser identity/authority verificationDigital computer detailsThe InternetDigital fingerprint
Client terminals report an easy-to-calculate identifier such as the Internet URL or a cryptographic hash of the content to a server. The server collects and counts the reported identifiers so as to obtain preliminary statistics. By aggregating these reported identifiers into the preliminary statistics, identifiers are revealed that are likely popular content. The server selects one or more identifiers from the preliminary statistics and makes these available to at least a subset of clients. The clients that obtain these one or more identifiers then access content and compute the easy-to-calculate identifiers as usual. If the computed identifier matches one of the identifiers obtained from the server, the client will additionally extract a watermarked identifier or compute a digital fingerprint of the content in question and report this to the server. The server then uses the received identifier or fingerprint to create final statistics by aggregating the preliminary statistics.
Owner:KANTAR SAS
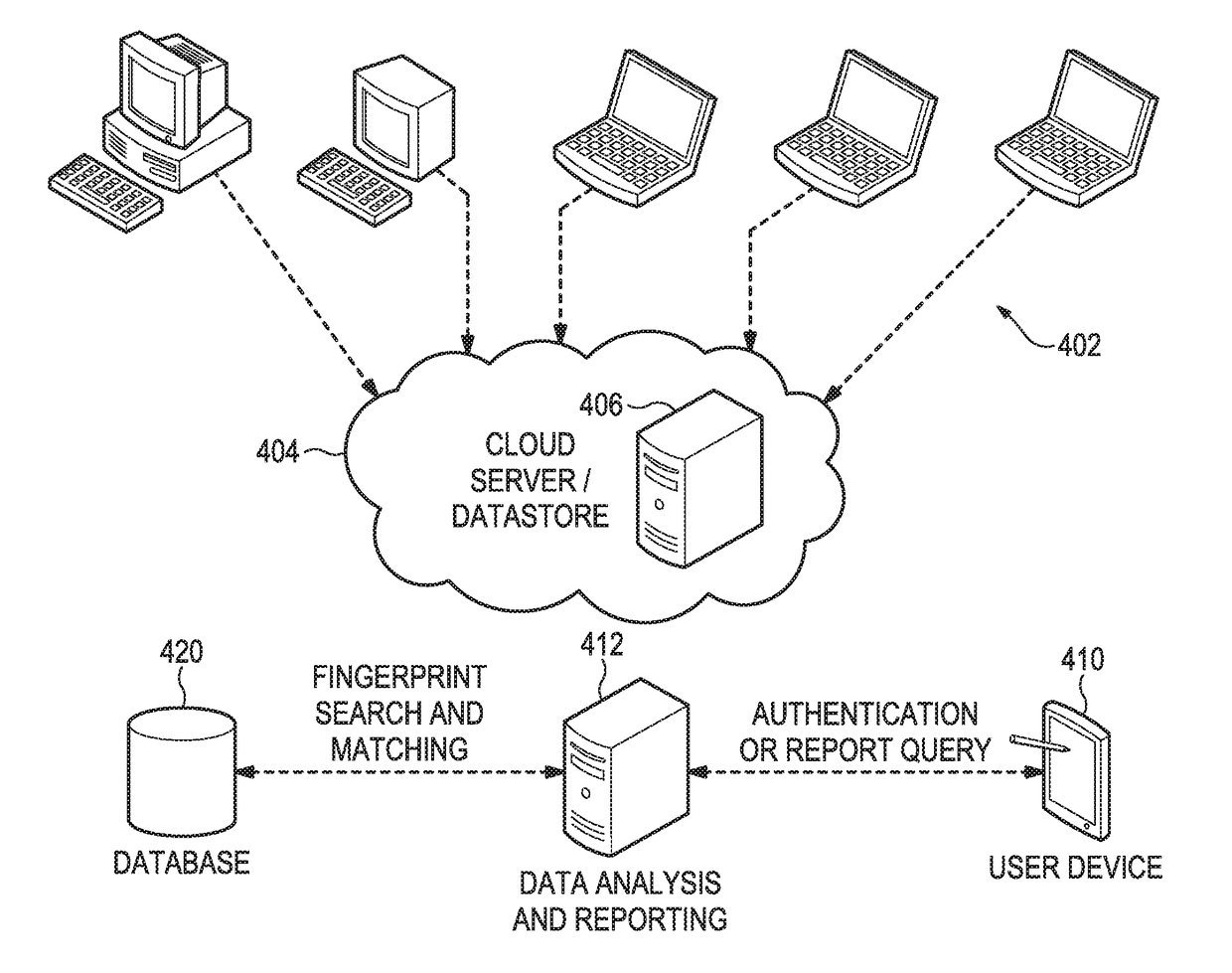
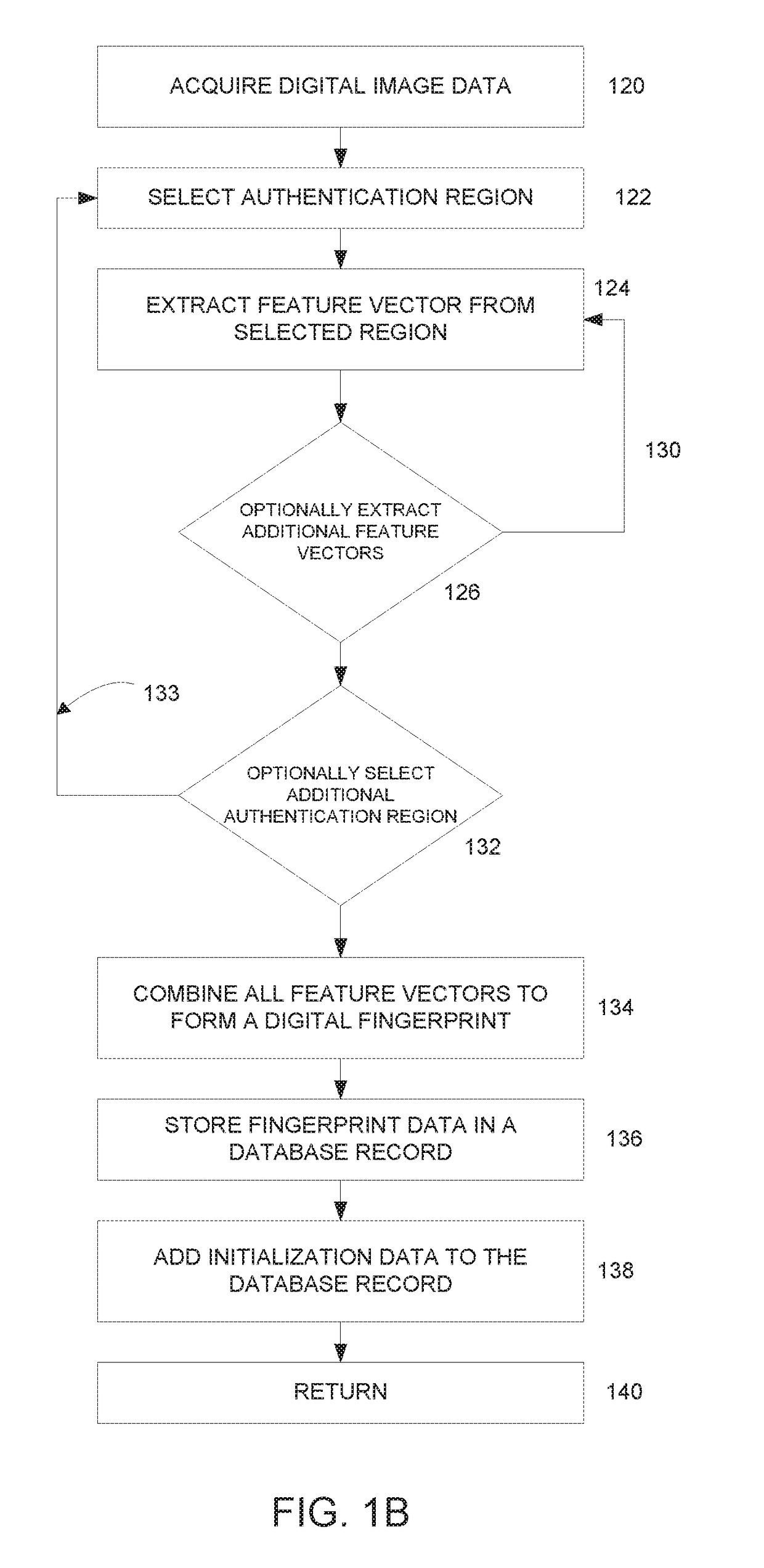
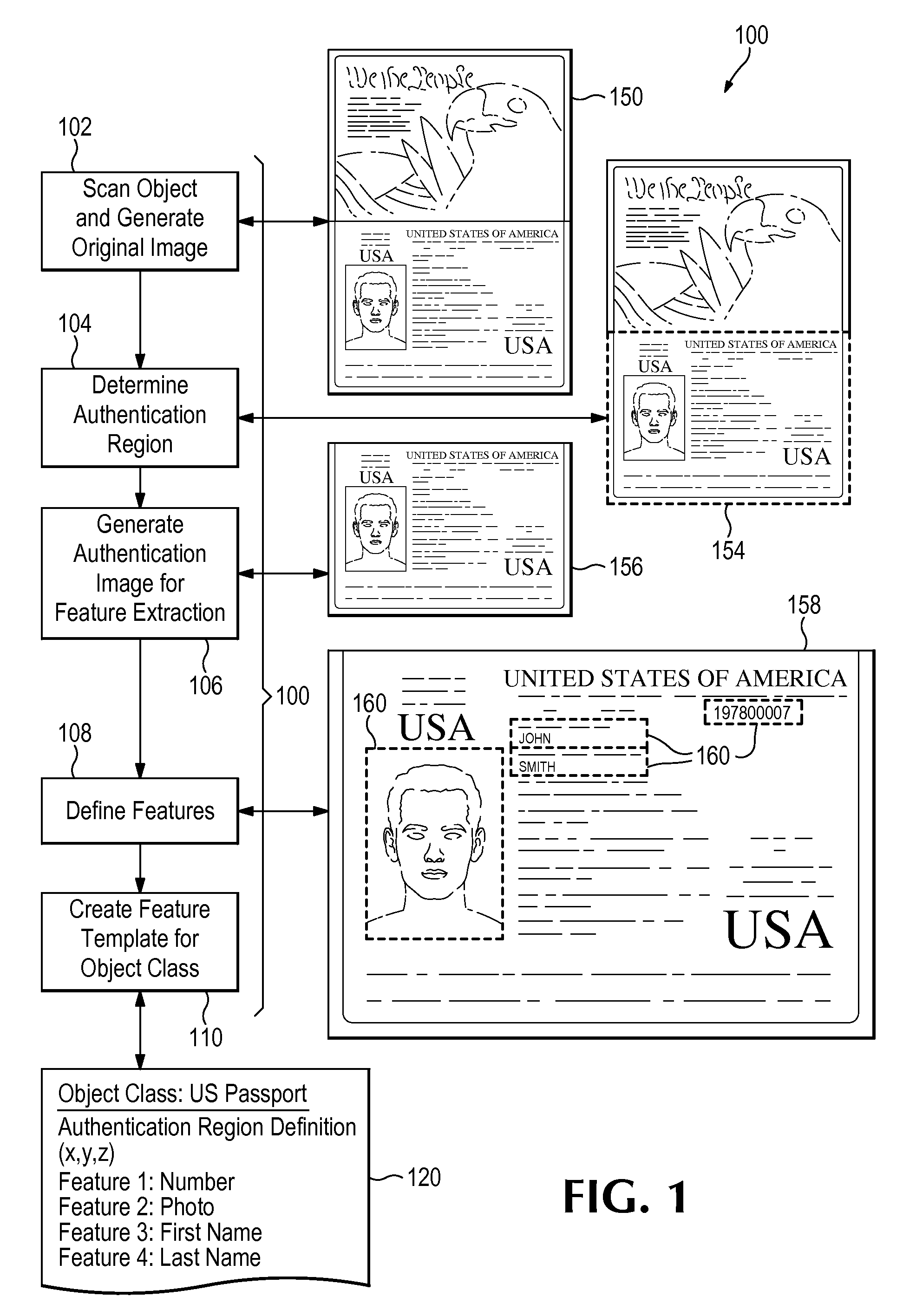
Controlled authentication of physical objects
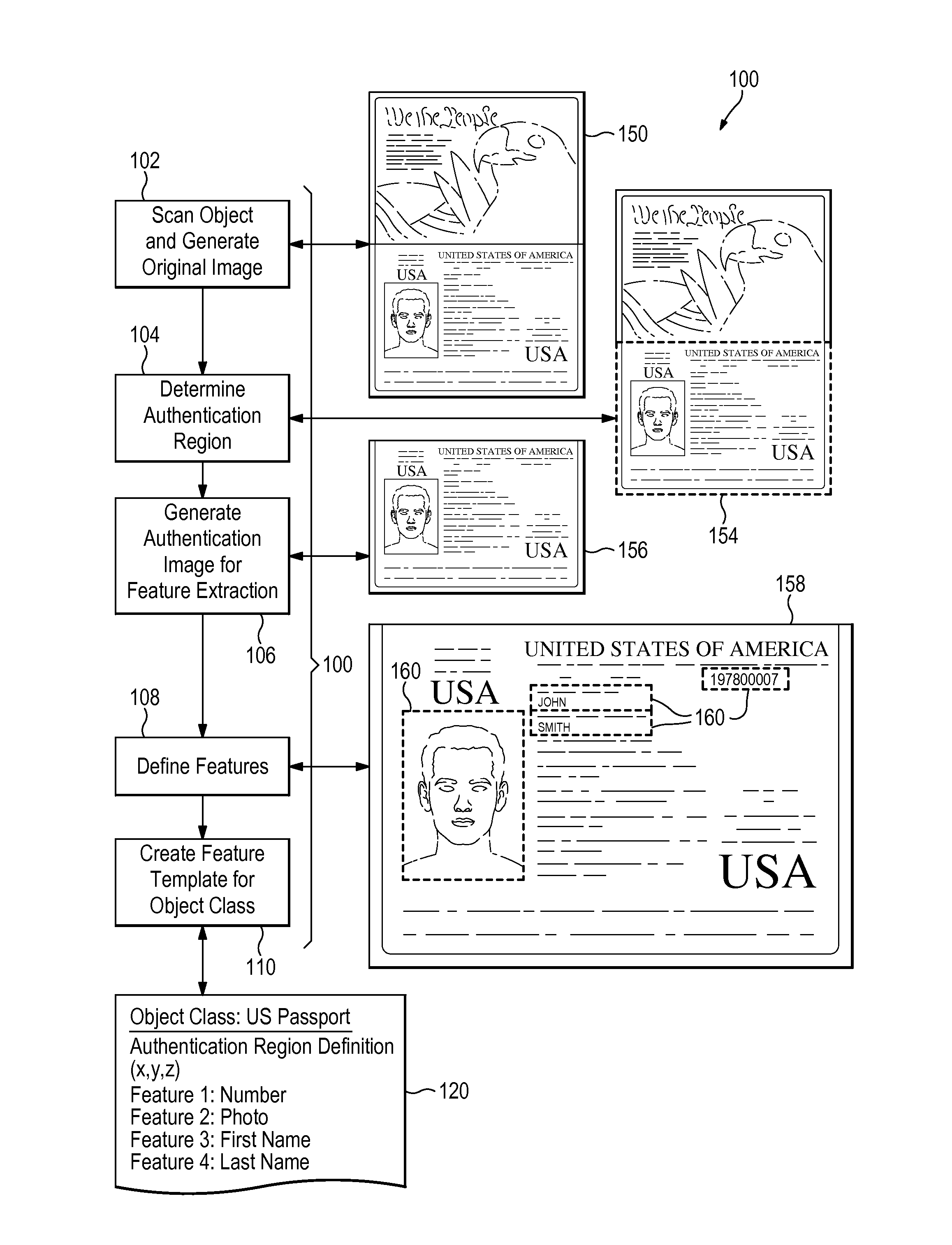
ActiveUS20170344823A1Improve securityQuick searchStill image data indexingCharacter and pattern recognitionFeature vectorUnique identifier
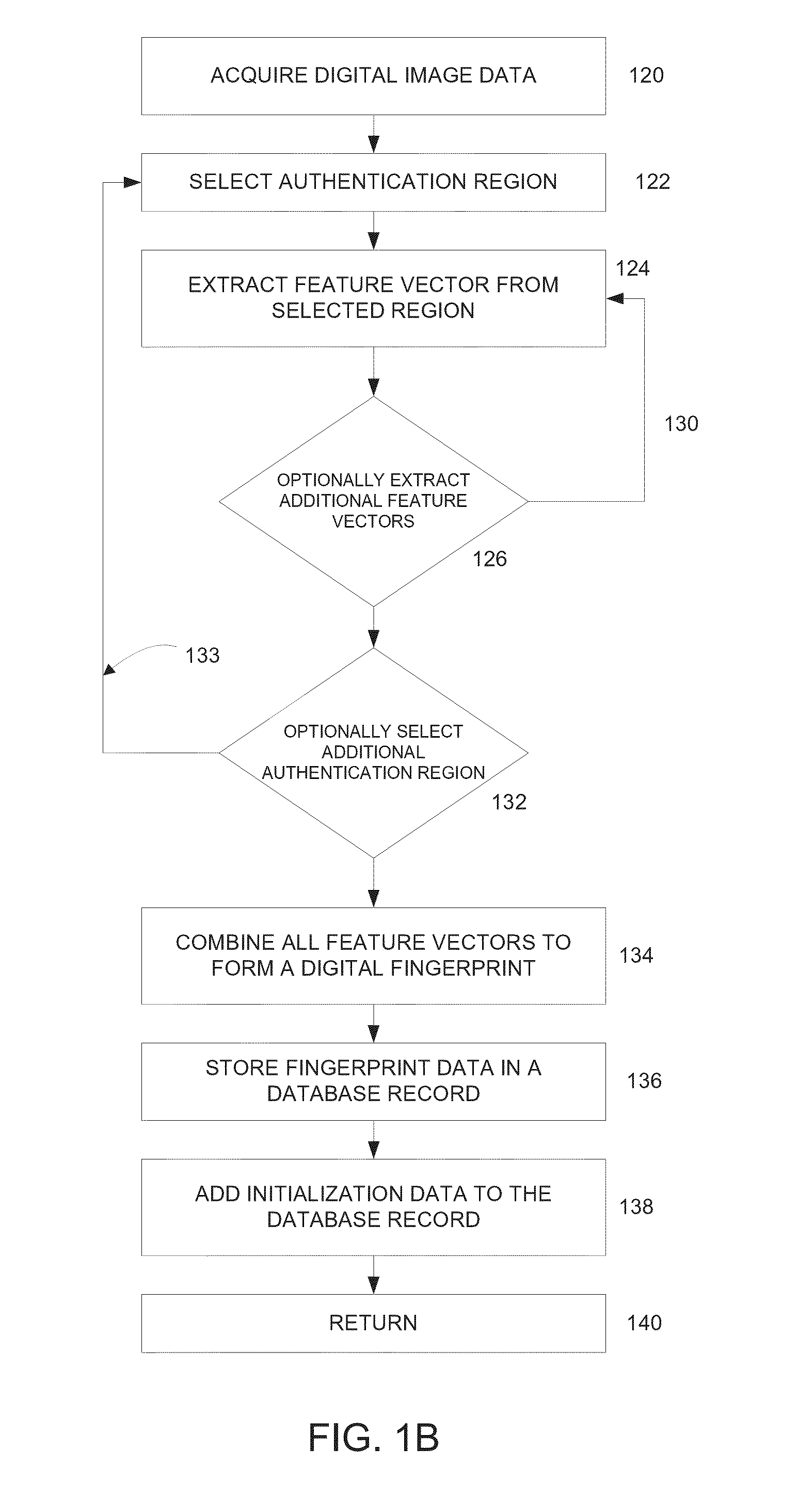
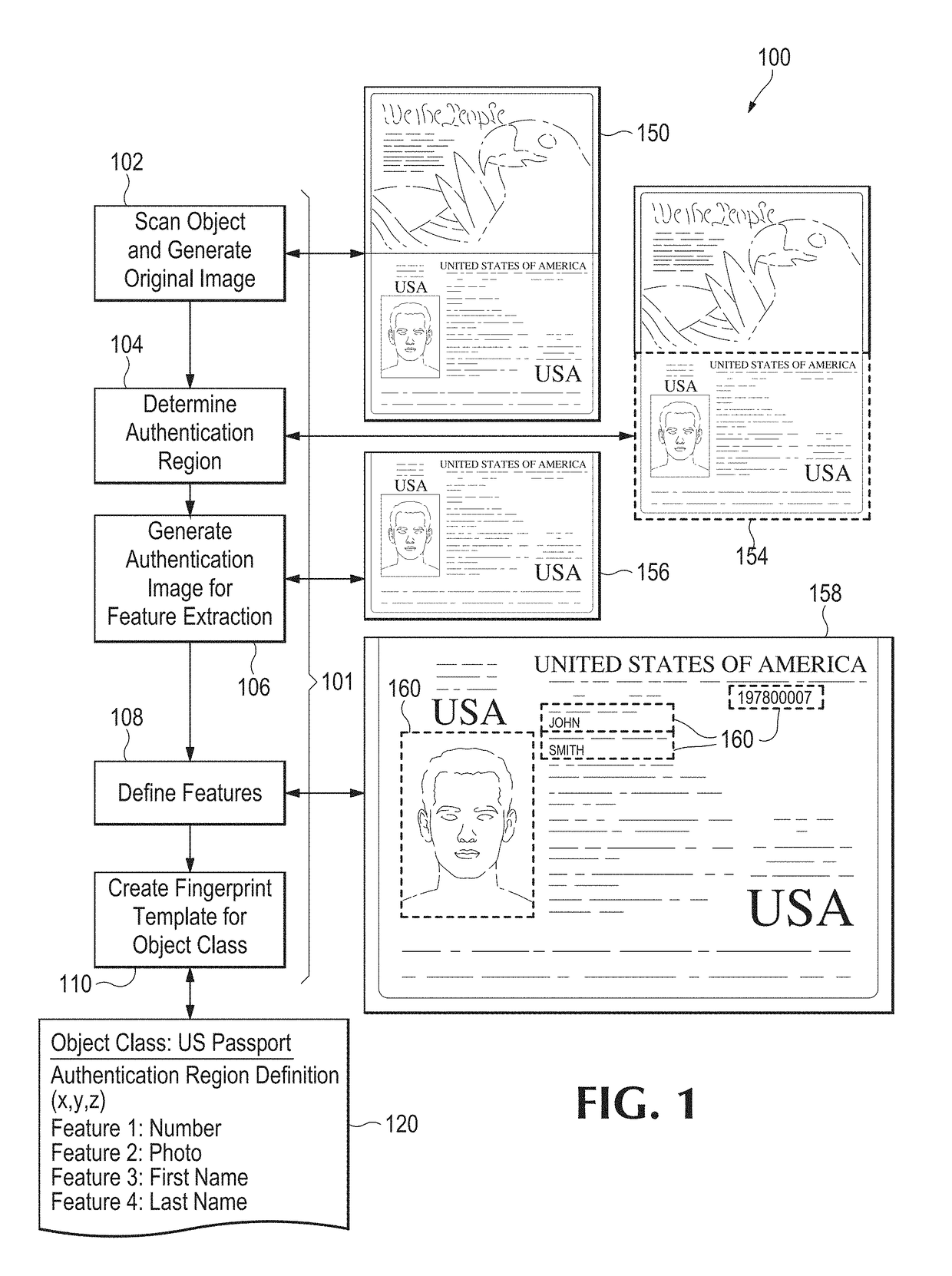
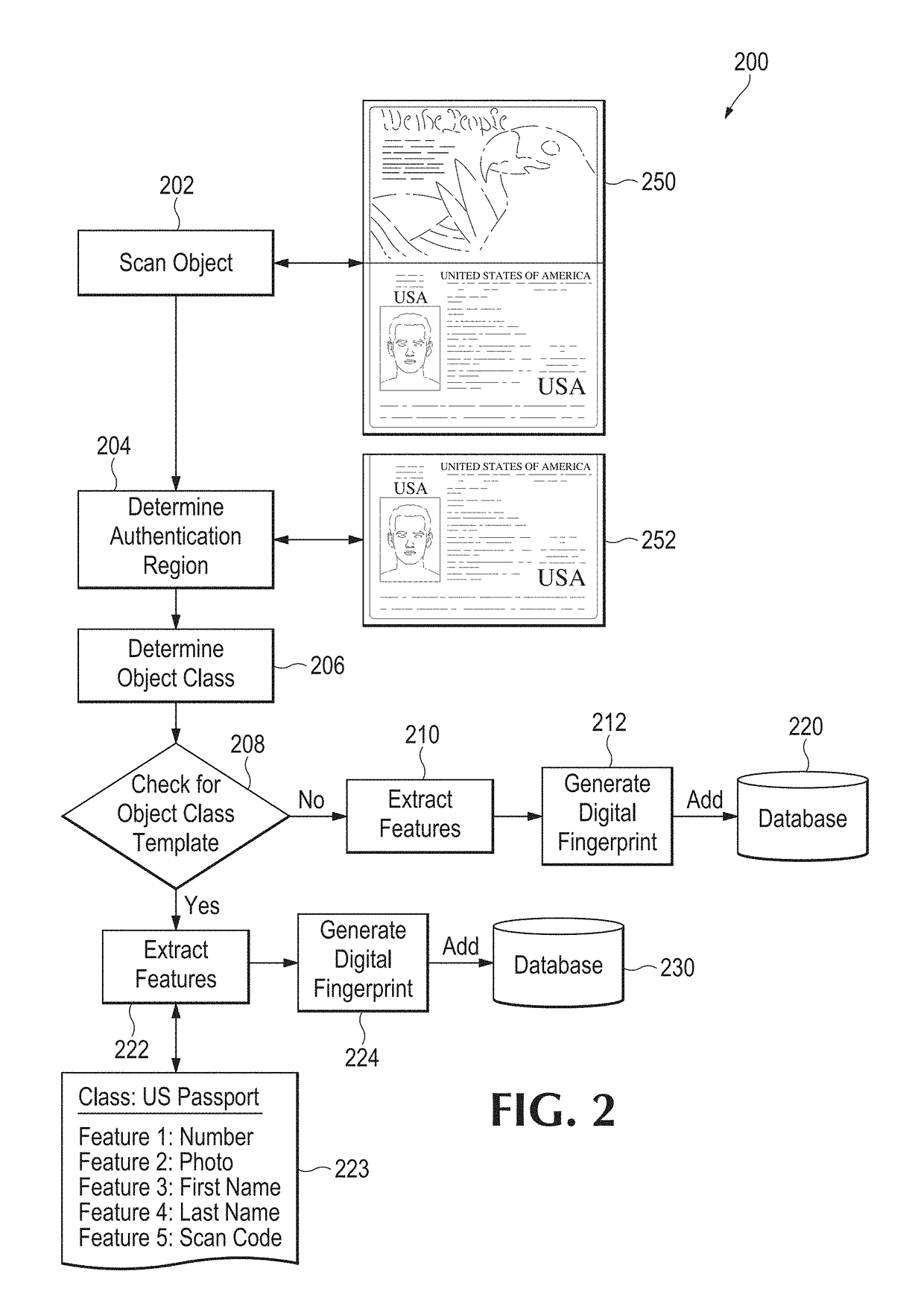
A physical object is scanned and a digital image of the object is generated from the scan. At least one subset of the image, known as an “authentication region” is selected. A plurality of feature vectors, arising from the physical structure of the object, are extracted from certain locations of interest within an authentication region and combined to generate a unique identifier or “digital fingerprint” for that object. Preferably, authentication regions for feature vector extraction are automatically selected by a software process. To identify or authenticate an object, a system may compare a digital fingerprint of an object to digital fingerprints previously stored in a database. Digital fingerprint data may specify a set of features (also termed “locations of interest”) which may be referenced in the creation of a “fingerprint template” which is a template of certain locations of interest and / or attributes selected for authenticating a particular class of objects.
Owner:ALITHEON INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com