Distributed frequency data collection via DNS
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
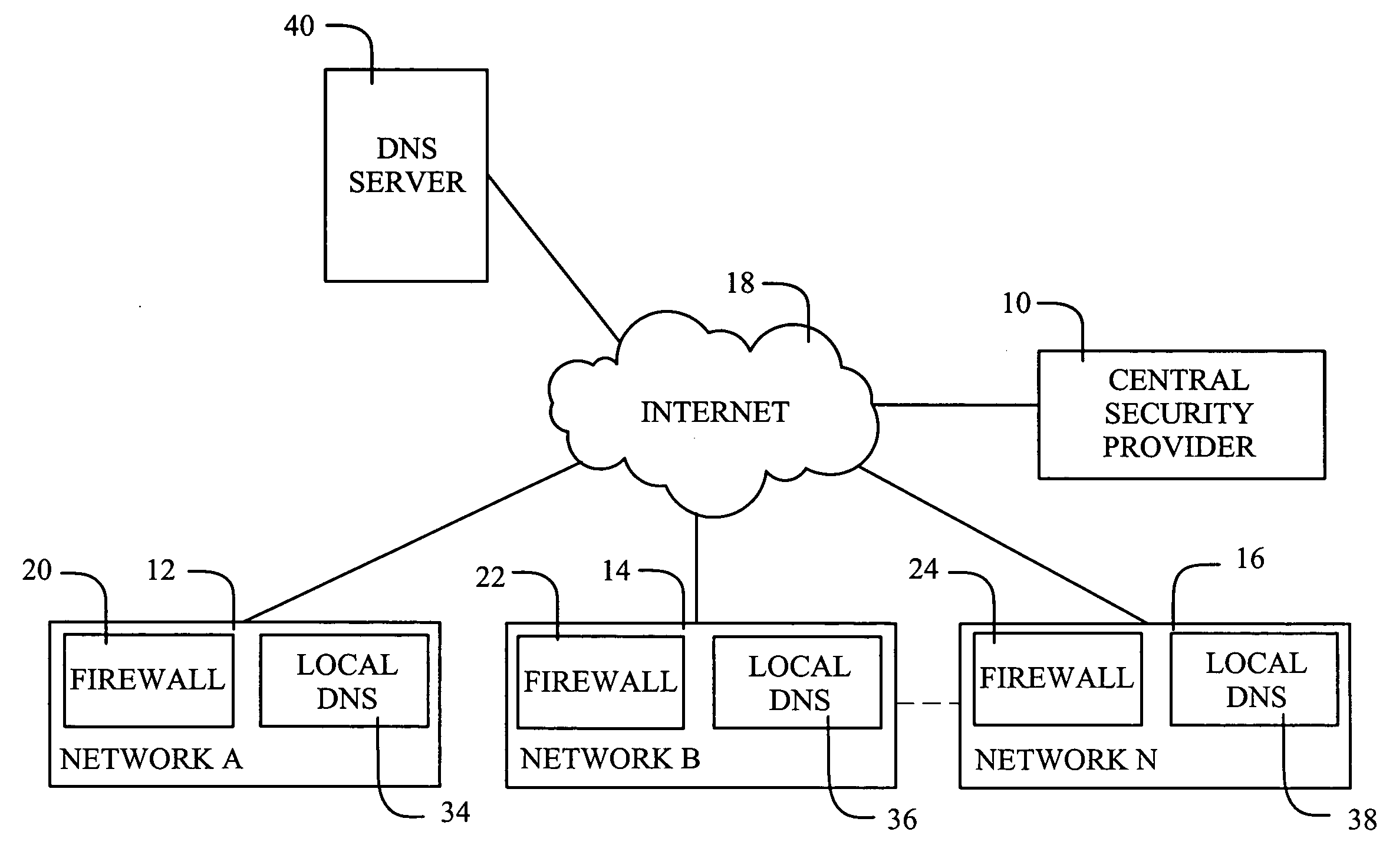
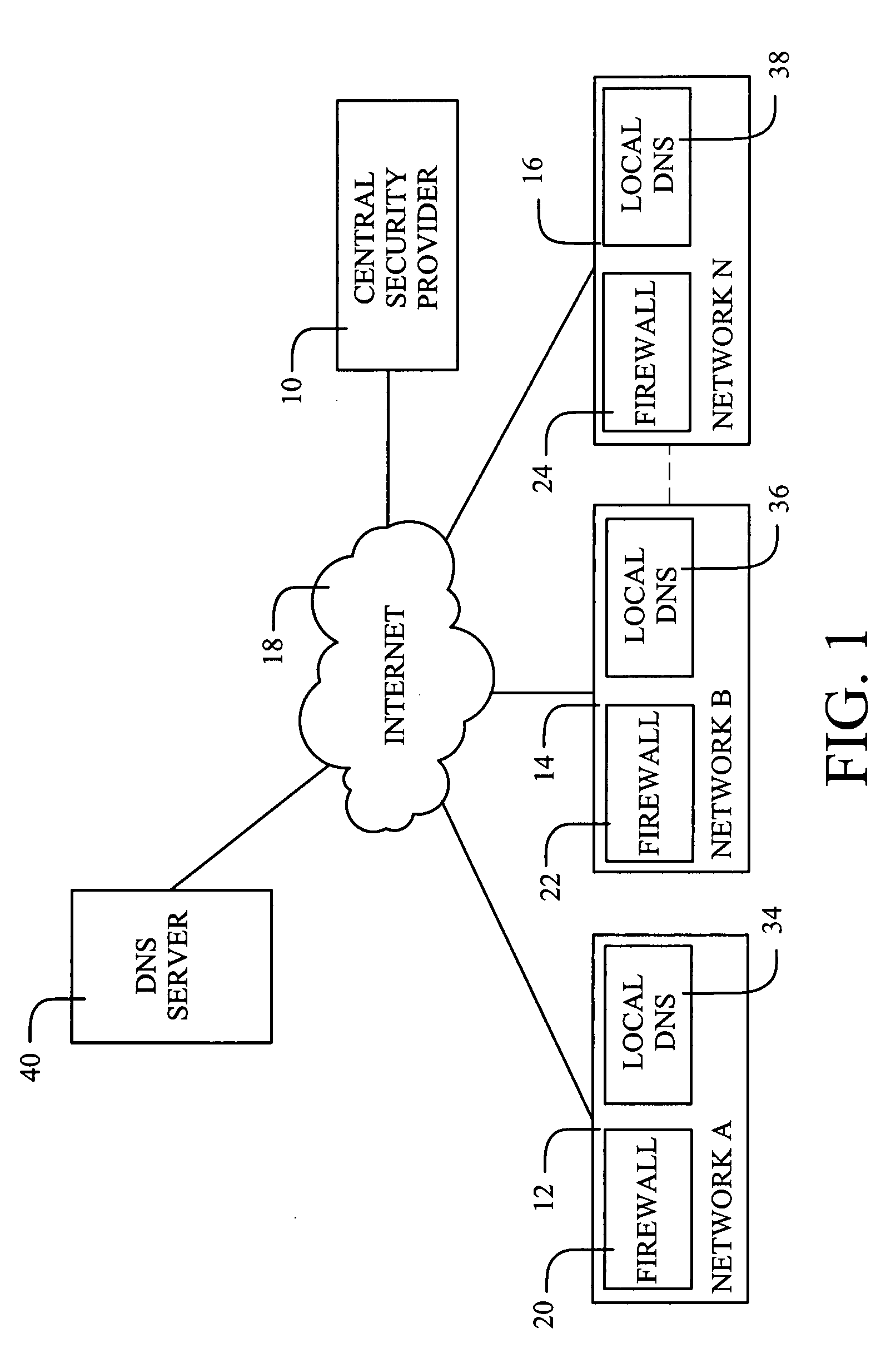
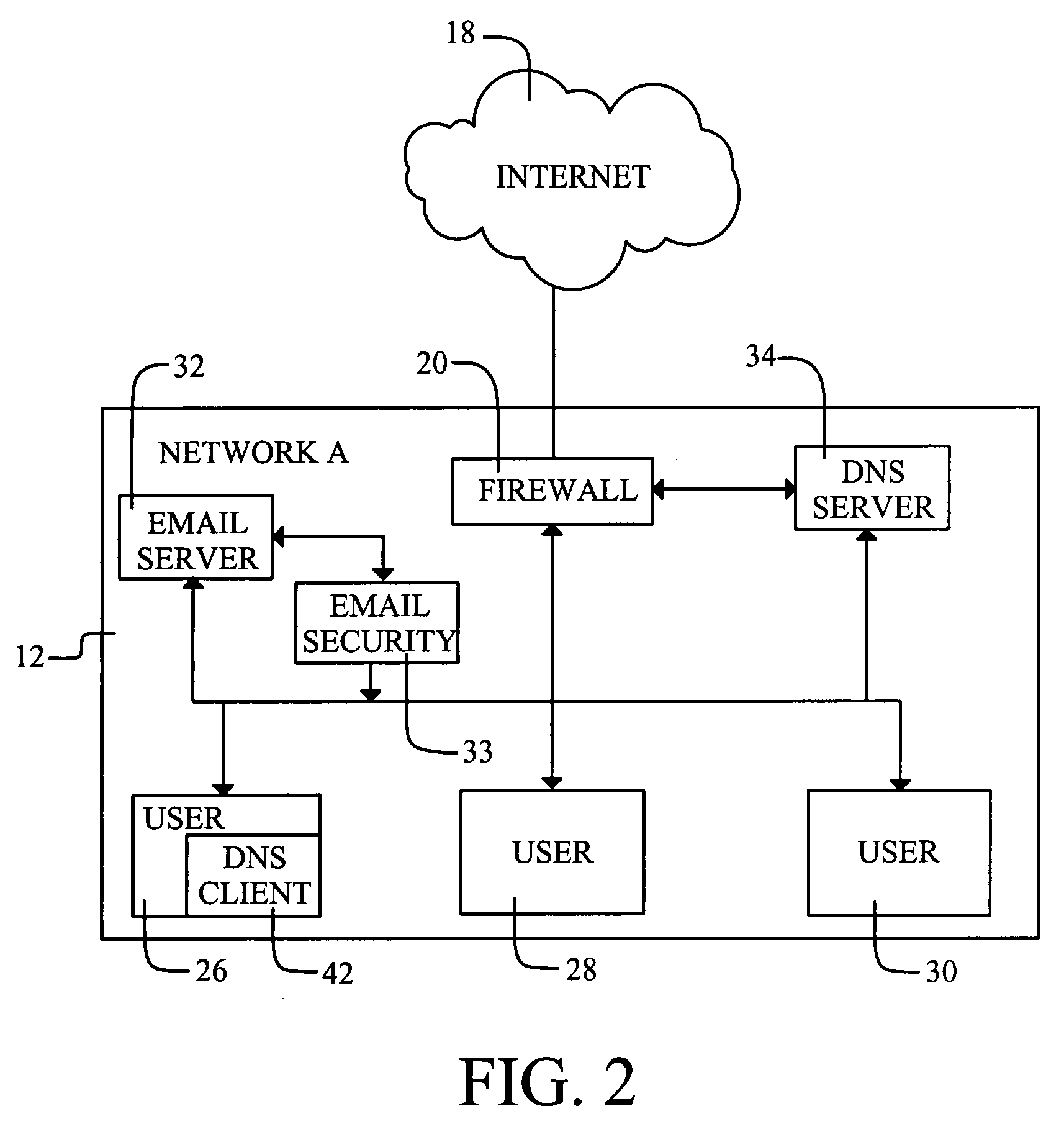
[0024]With reference to FIG. 1, a single security provider 10 may be enabled to provide Internet security for a number of different autonomous networks 12, 14 and 16. While the networks are related with respect to connection to the same security provider, the networks are “autonomous” with respect to network management. For example, each network may be specific to a business or an educational facility. The term “network” is used herein in its conventional definition as an organization of data processing nodes that are interconnected for the purpose of data communication. Typical nodes include computers.
[0025]The central security provider 10 is connected to the different networks 12,14 and 16 via the global communications network referred to as the Internet 18, so as to allow updates in response to detecting new security breaches. The invention will be described with reference to its application via the Internet, but may be used within connectivity environments (e.g., WANs) that incl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com