Method and system for improving login security
A login request and re-login technology, applied in the field of communication, can solve problems such as login insecurity, and achieve the effect of improving login security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
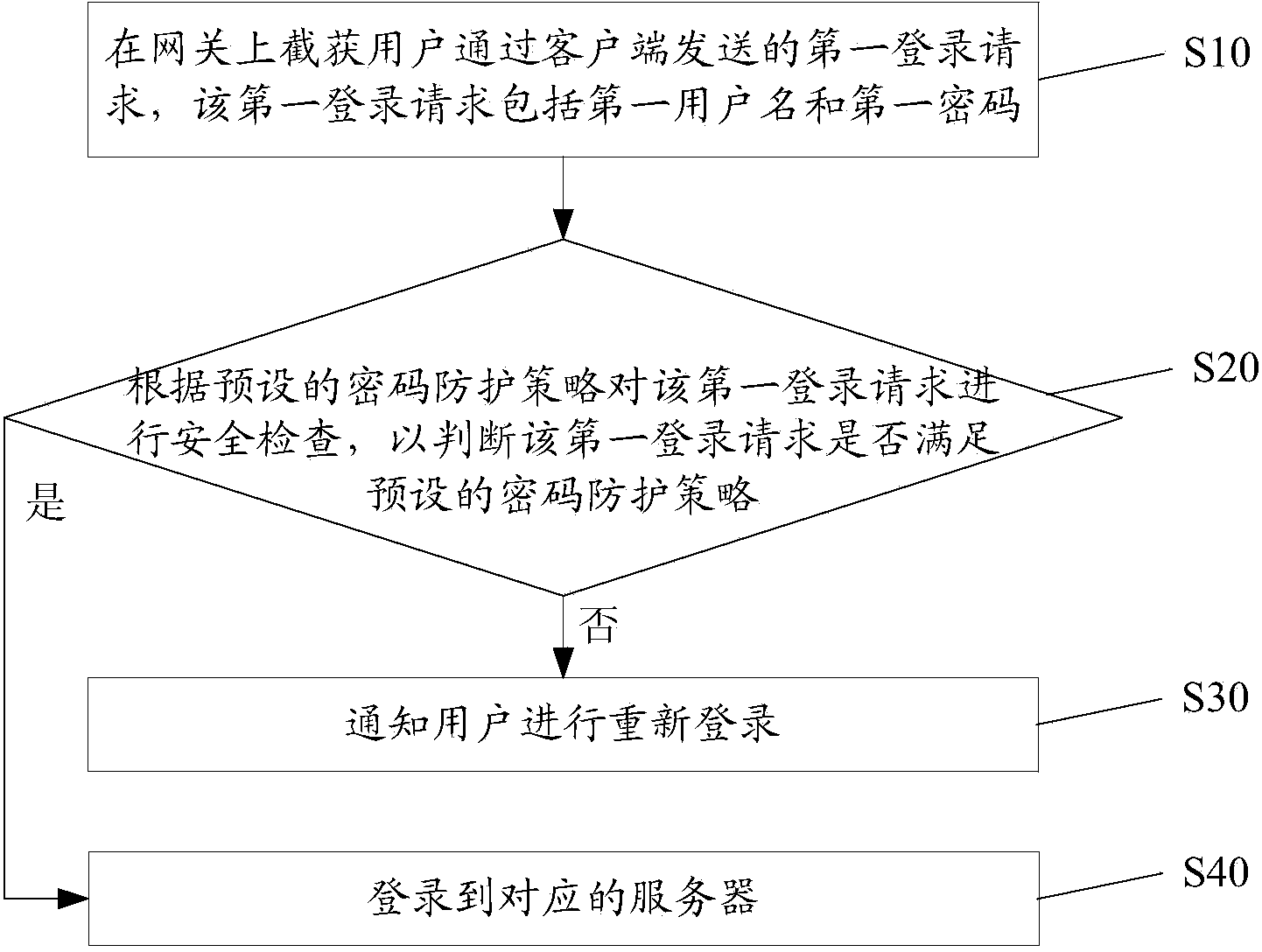
[0051] refer to figure 1 , figure 1 It is a schematic flow chart of the first embodiment of the method for improving login security in the present invention, the method includes:
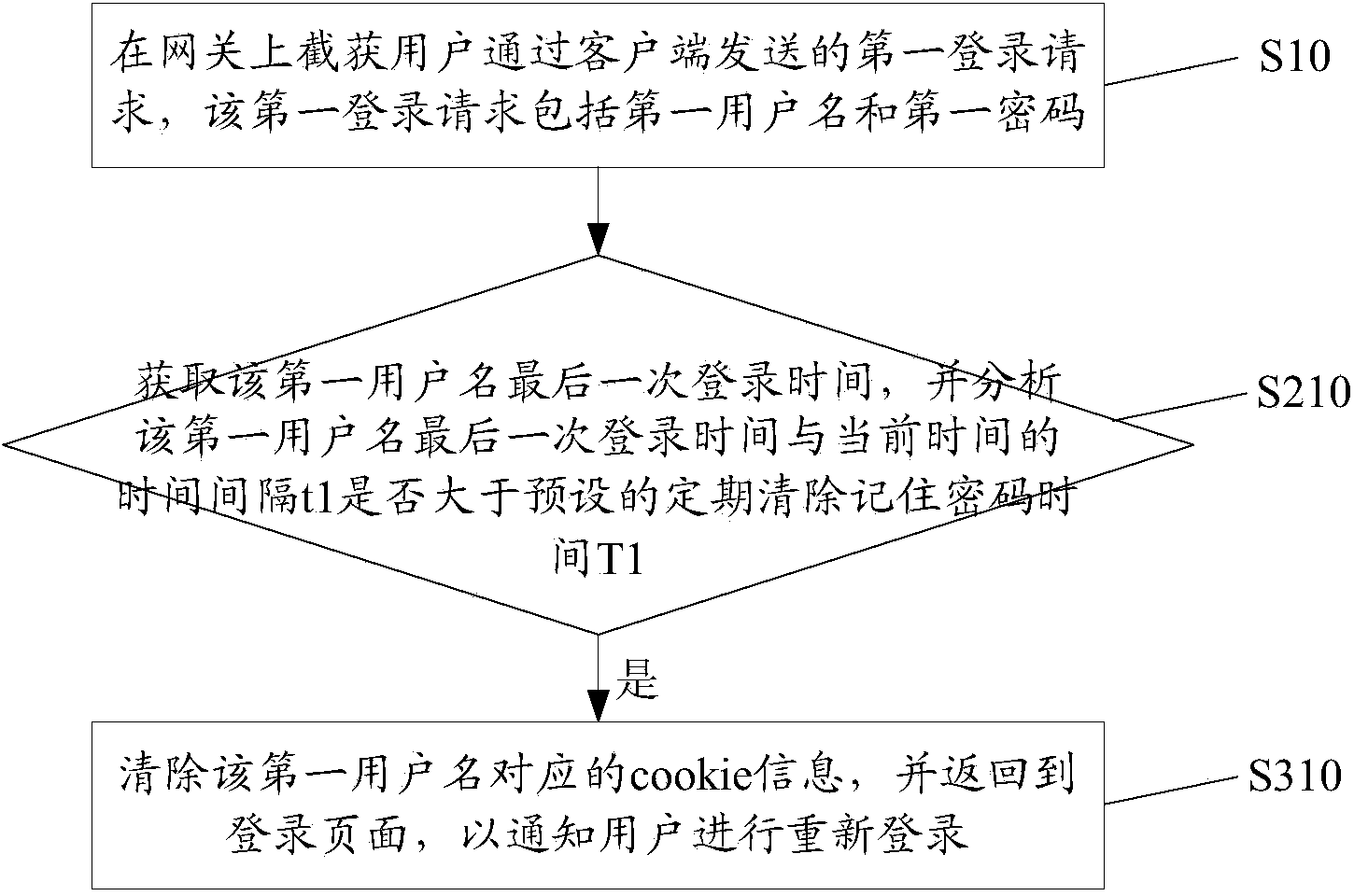
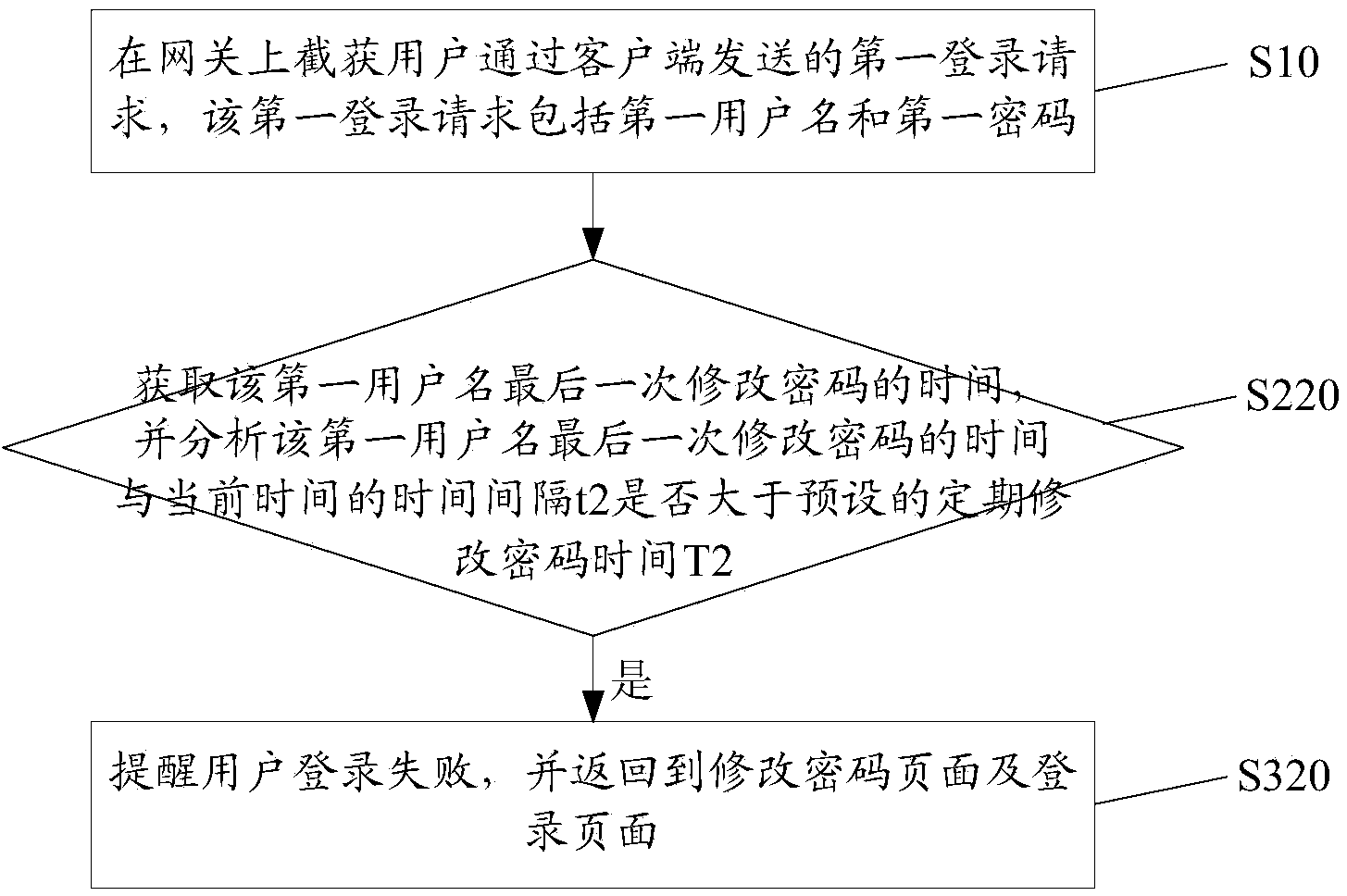
[0052] S10. On the gateway, intercept the first login request sent by the user through the client, where the first login request includes a first user name and a first password.
[0053] The gateway (Gateway) is also called an Internet connector and a protocol converter. The gateway is at the network layer to realize network interconnection. It is the most complex network interconnection device and is only used for the interconnection of two networks with different high-level protocols. The gateway can be used for both wide area network interconnection and local area network interconnection. In this embodiment, the gateway may be a firewall, an online behavior management device, a flow control management device, and the like.
[0054]The first login request may be a request to log in to an http s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com