Login verification method, system and instant messaging (IM) server
A login verification and server technology, applied in the fields of login verification methods, systems and IM servers, can solve the problem of low security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
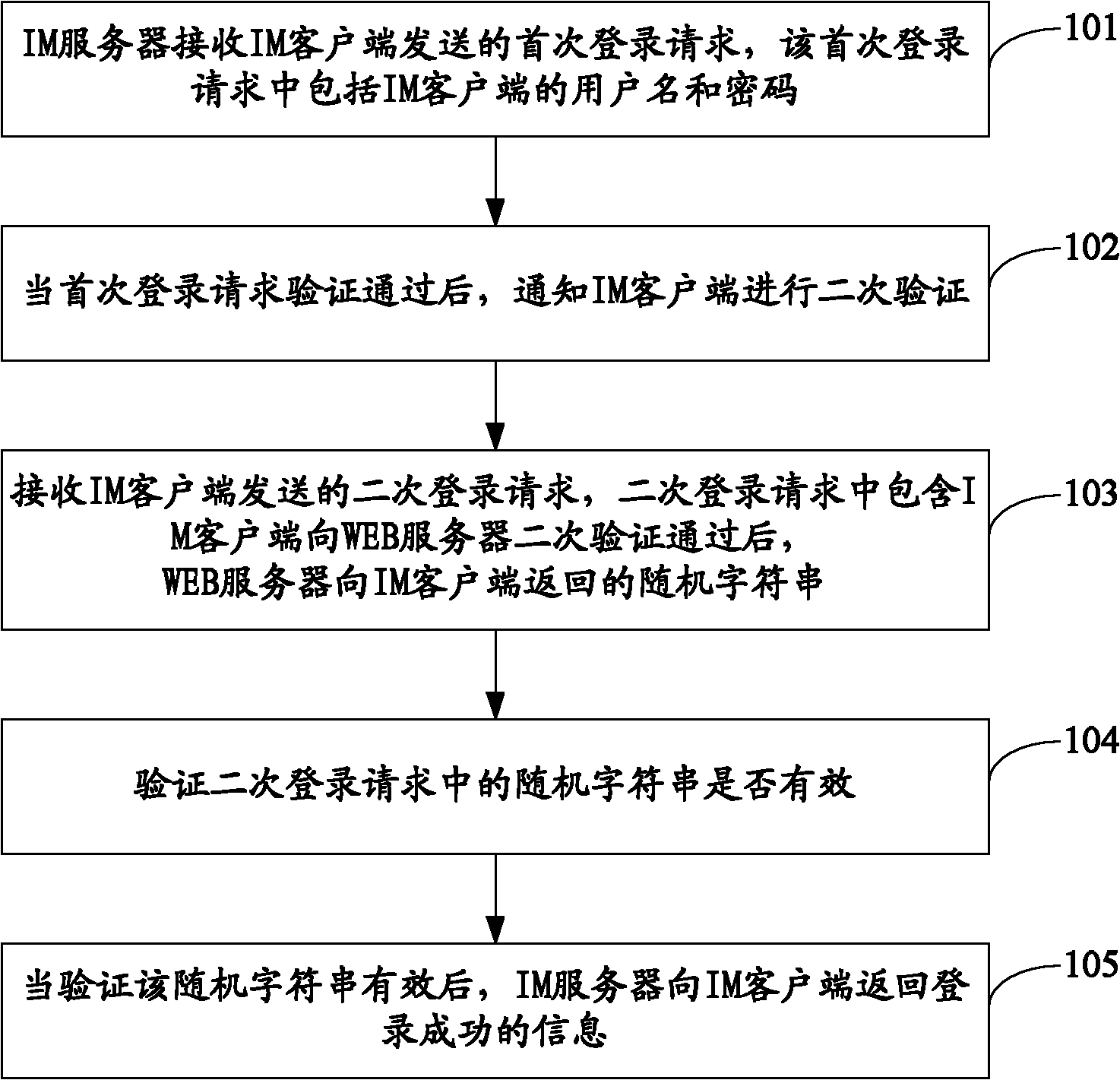
[0034] see figure 1 , which is the flow chart of the first embodiment of the login verification method of this application:
[0035] Step 101: The IM server receives the first login request sent by the IM client, and the first login request includes the user name and password of the IM client.
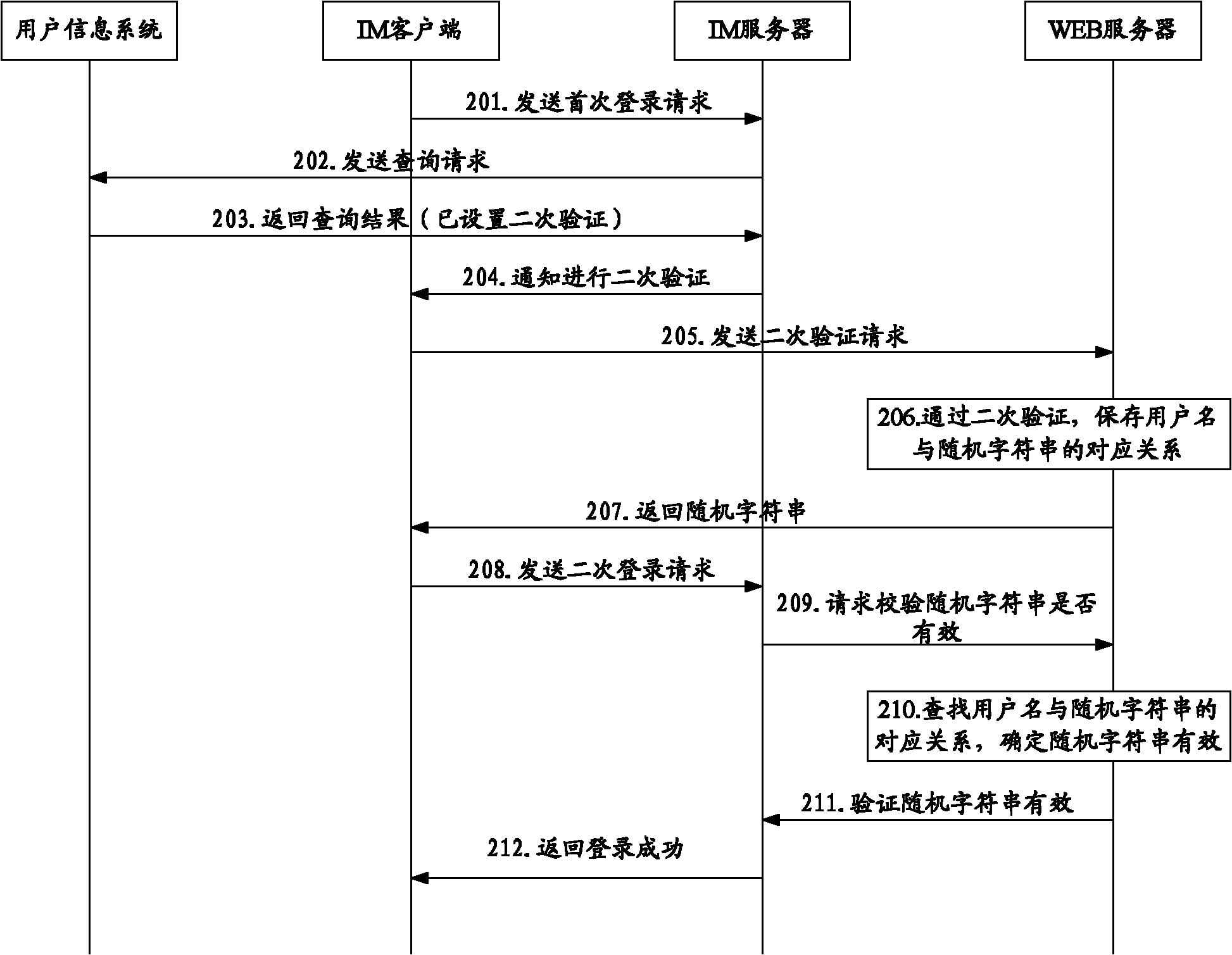
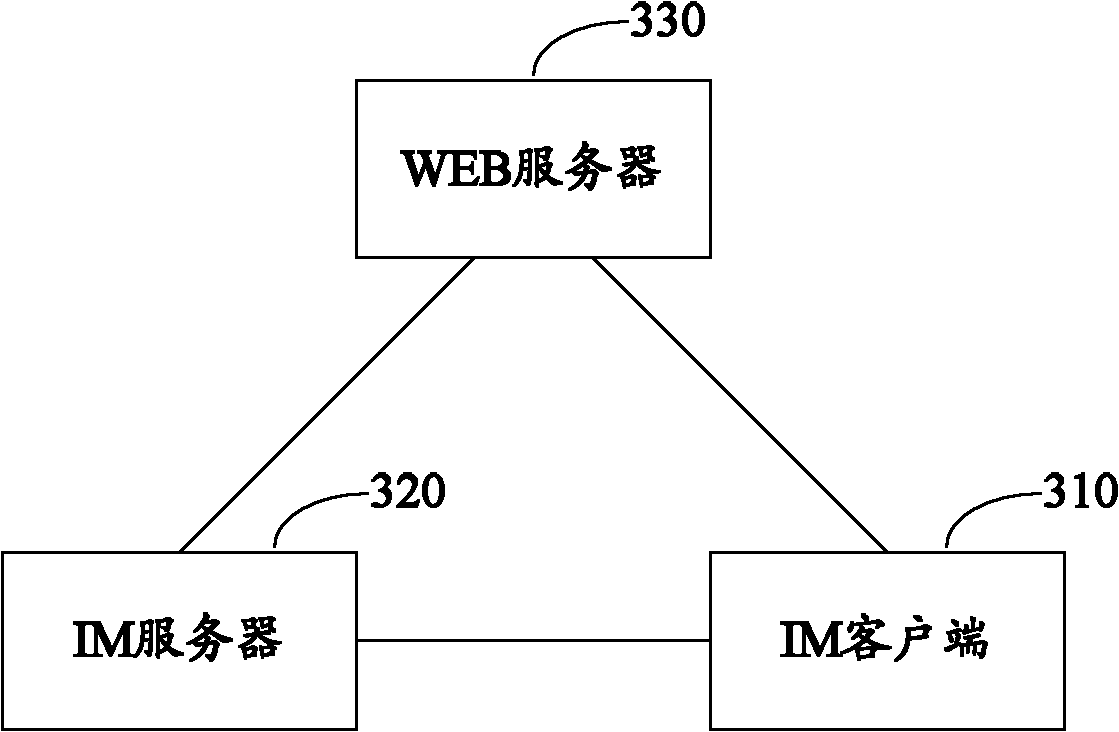
[0036] If a traditional IM client wants to log in to the IM server, the IM client user will register on the IM server in advance, and the user name and password of the user login account are set during the registration process, and the IM server can save the corresponding relationship between the user name and the password, so that When the user logs in through the IM client, the user account is verified. Usually the IM server can store the corresponding relationship between the user name and the password in a separate UIC (User Information Centre, User Information Center). When the user logs in through the IM client, the IM server can communicate with the UIC to verify the user name ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com