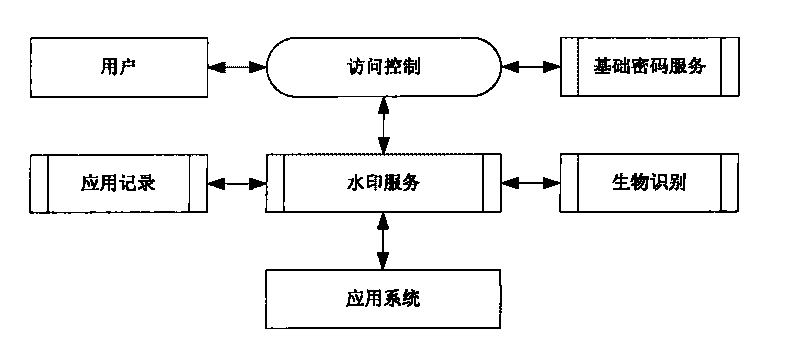
Patents
Literature
53results about How to "Avoid the risk of being stolen" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
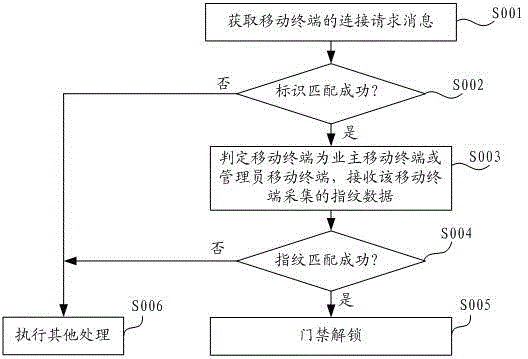
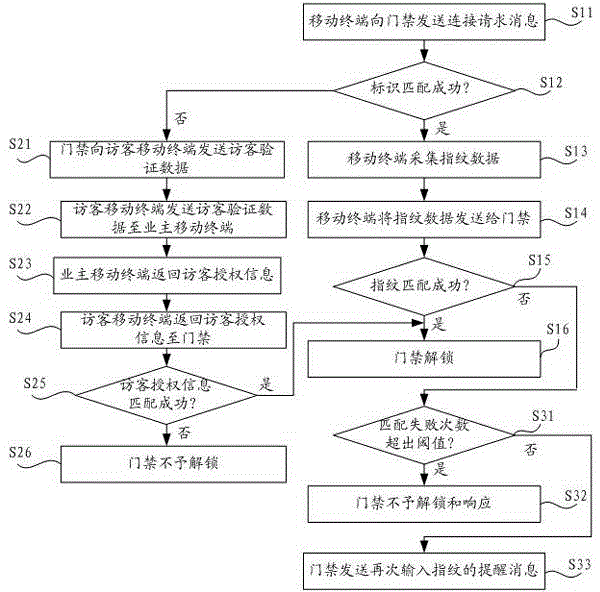
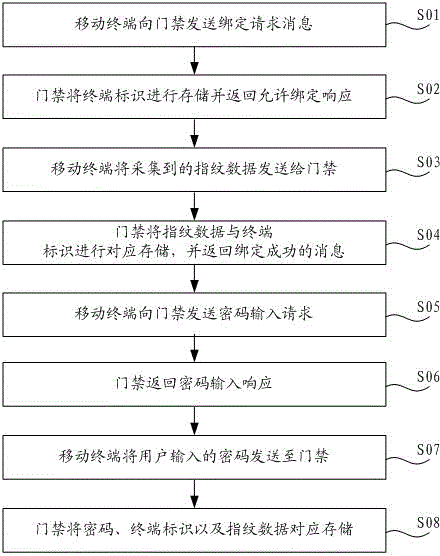
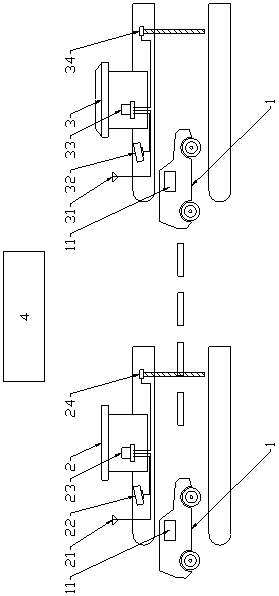
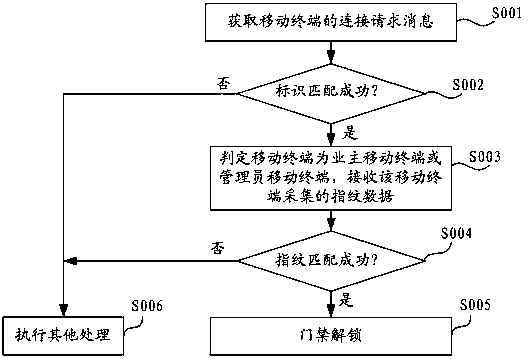
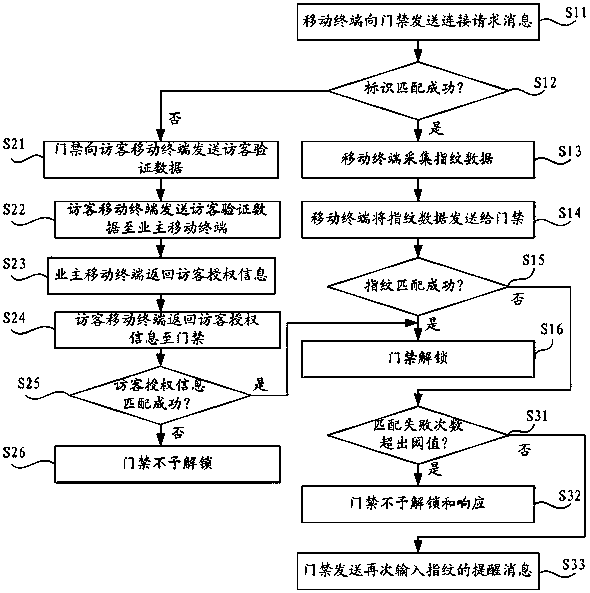
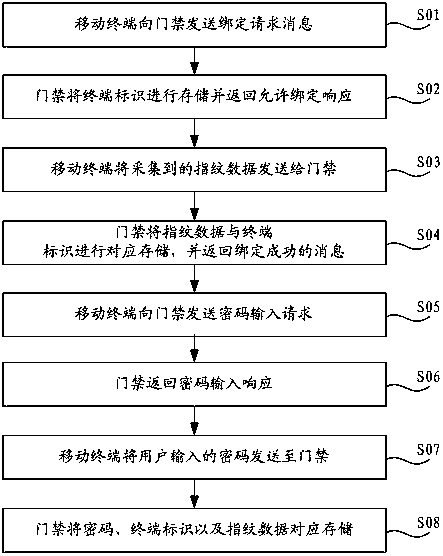
Entrance guard control method and control system thereof
ActiveCN105447928AAvoid the risk of being stolenImprove securityIndividual entry/exit registersControl systemMobile phone
The invention discloses an entrance guard control method and a control system thereof. The method comprises the following steps: acquiring connection requesting information of a mobile terminal, and judging whether a terminal marker carried by a connection requesting message is coupled with a pre-stored preset marker or not; determining the mobile terminal is an owner mobile terminal or an administrator mobile terminal if so; judging whether fingerprint data acquired by the mobile phone is coupled with preset fingerprint data corresponding the preset marker or not; and unlocking entrance guard if so. The method provided by the invention has high safety and great convenience, and realizes no staying of the fingerprint in a public area in order to avoid stole risk of the fingerprint.
Owner:QINGDAO HAIER INTELLIGENT HOME TECH CO LTD
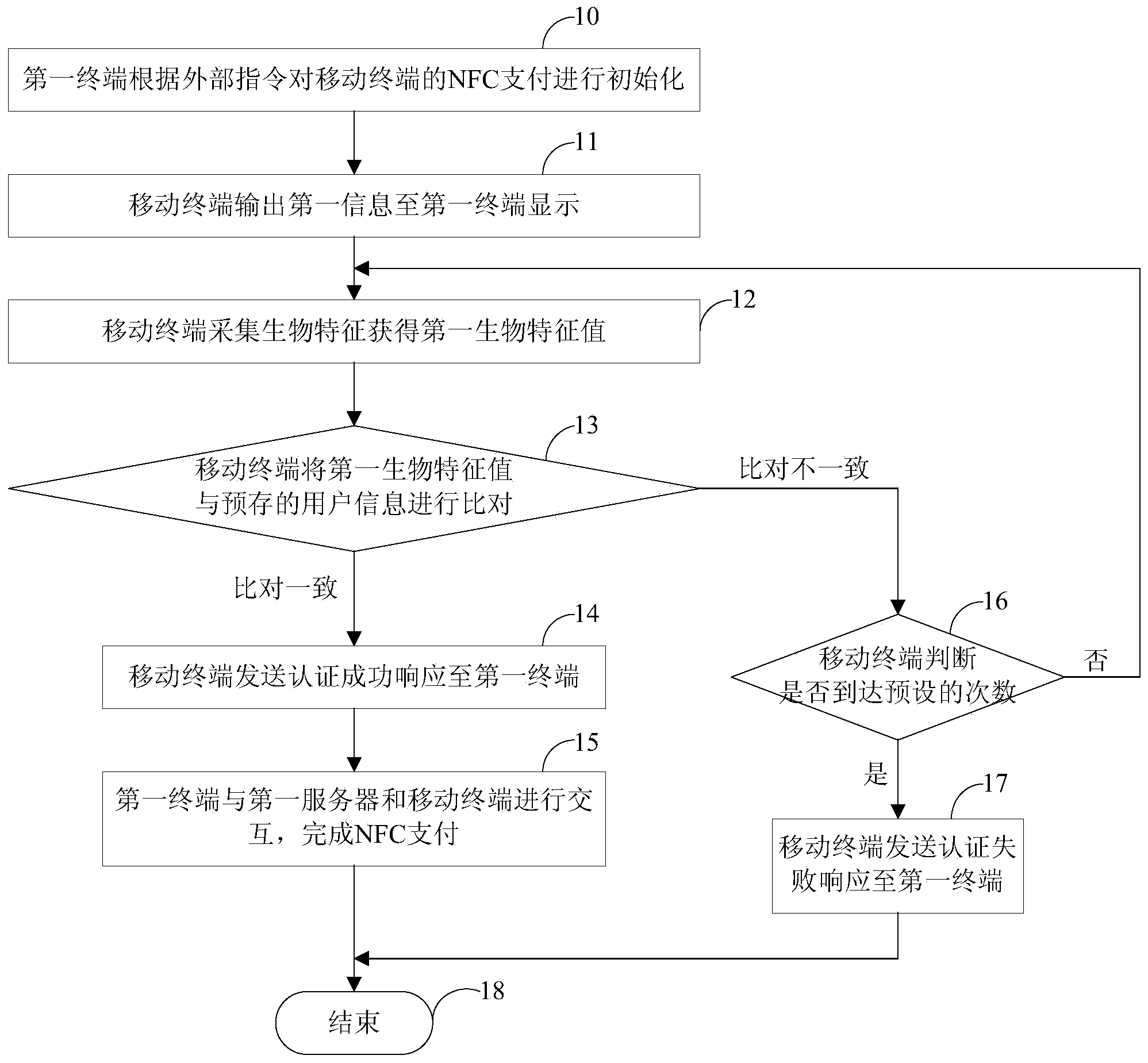
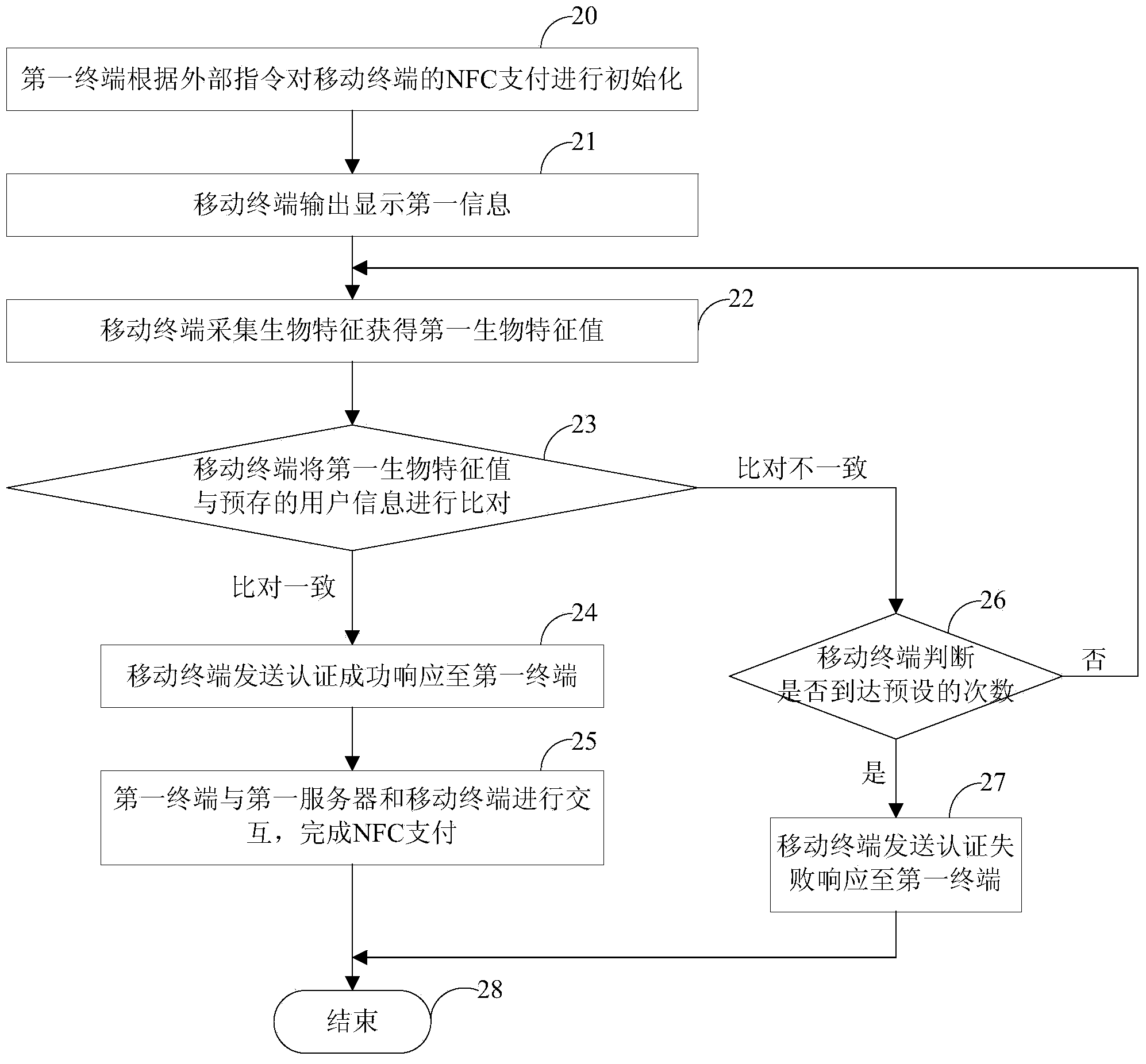
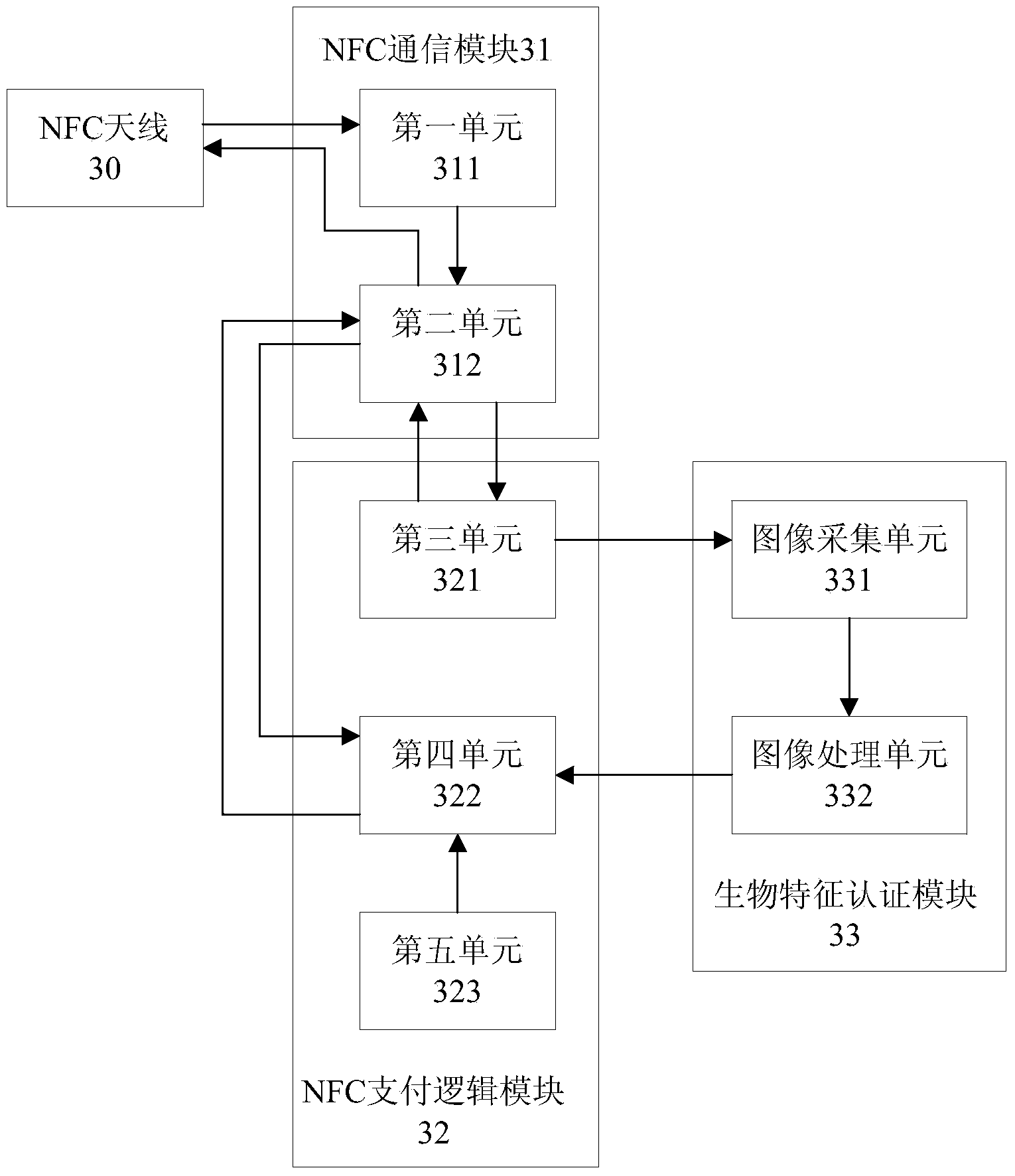
NFC payment method, device, system and mobile terminal
ActiveCN103455913AImprove securityAvoid the risk of being stolenProtocol authorisationPaymentRadio frequency signal
The invention discloses an NFC payment method. The method includes the steps that a first terminal receives input transaction data and NFC transaction instructions according to received outer instructions and outputs second information; a mobile terminal receives a radio frequency signal which is received from the first terminal and used for activating NFC payment; the mobile terminal is initialized according to initialization data from the first terminal, sends an initialization completion response to the first terminal and outputs first information; the mobile terminal collects biological characteristics of a user to obtain an image of the biological characteristics and carries out image process to extract first biological characteristic values; the mobile terminal compares the first biological characteristic values with second biological characteristic values included by pre-stored user information, and sends an authentication successful response to the first terminal when the first biological characteristic values are consistent with the second biological characteristic values; the first terminal interacts with a first server and the mobile terminal to complete NFC payment. According to the NFC payment method, the device, the mobile terminal and the system, safety can be improved.
Owner:TENDYRON CORP
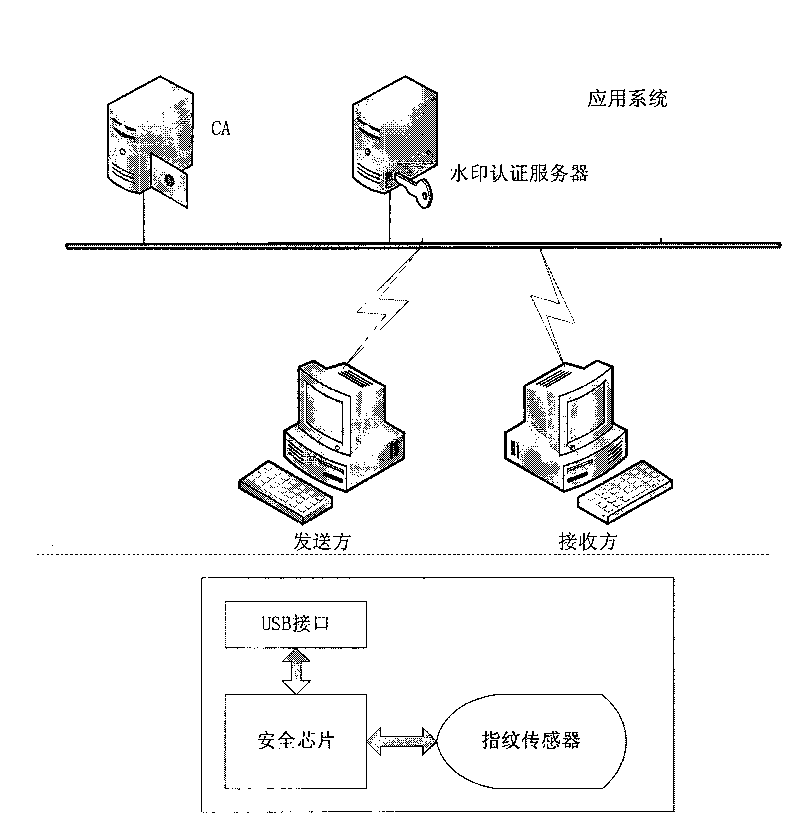
Security certificate method based on fingerprint, cryptographic technology and fragile digital watermark
ActiveCN101729256AAuthenticityAvoid the risk of being stolenUser identity/authority verificationImage data processing detailsDigital signatureSecure authentication
The invention discloses a security certificate method based on fingerprint, cryptographic technology and fragile digital watermark, comprising the following steps: a sender collects a fingerprint image, calculates summary information of the fingerprint image and inserts the summary information, a secret key and digital information which is digitally signed and encrypted into the fingerprint image as a watermark; the fingerprint of the sender is collected, the fingerprint image inserted with the watermark is sent to a receiver after the fingerprint of the sender is qualified; after receiving information, the receiver firstly detects and verifies whether the fingerprint image is inserted with the digital watermark and whether the digital watermark is right or not so as to indentify identity authenticity; digital watermark information is extracted from the received image; the summary information of the fingerprint image from which the watermark is extracted is calculated; and the summary information is compared with the summary information of the fingerprint image recorded in the watermark information to approve information authenticity. The invention can effectively overcome the defects that the existing digital signature security certificate can not approve the legal KEY holder and the fingerprint in the fingerprint certificate is easy to clone and embezzle.
Owner:SHENZHEN POKA ELECTRONICS EQUIP +1
Related method for encrypting and storing files in trusted execution environment based on encryption chip
ActiveCN110110548AGood encryptionImprove securityDigital data protectionInternal/peripheral component protectionPlaintextCiphertext
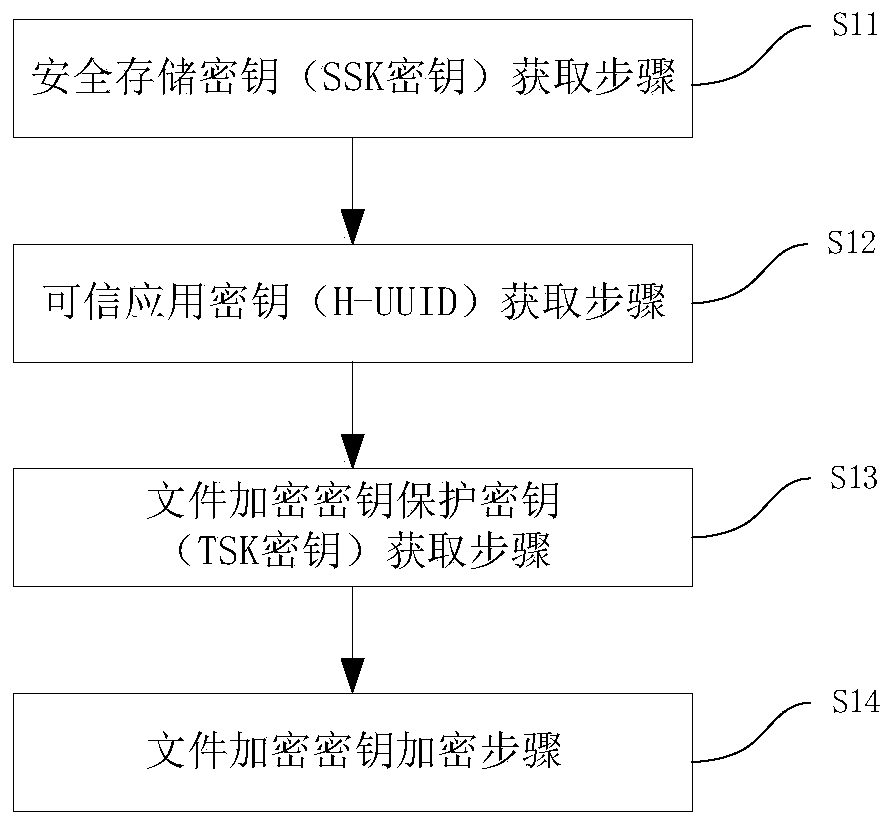
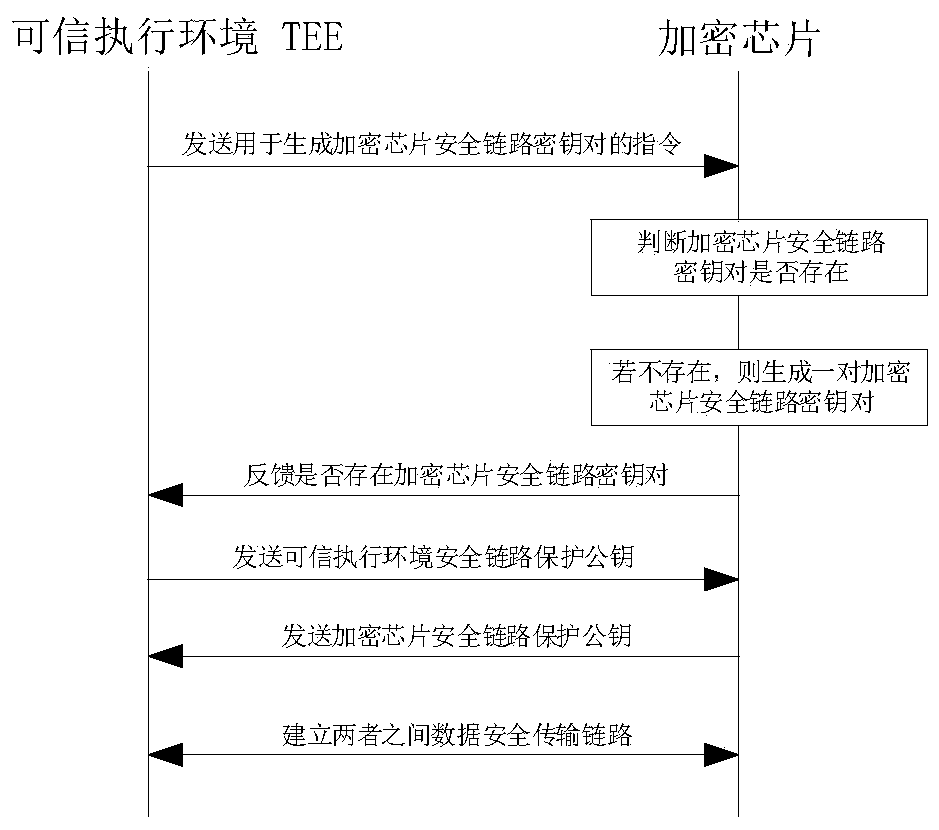
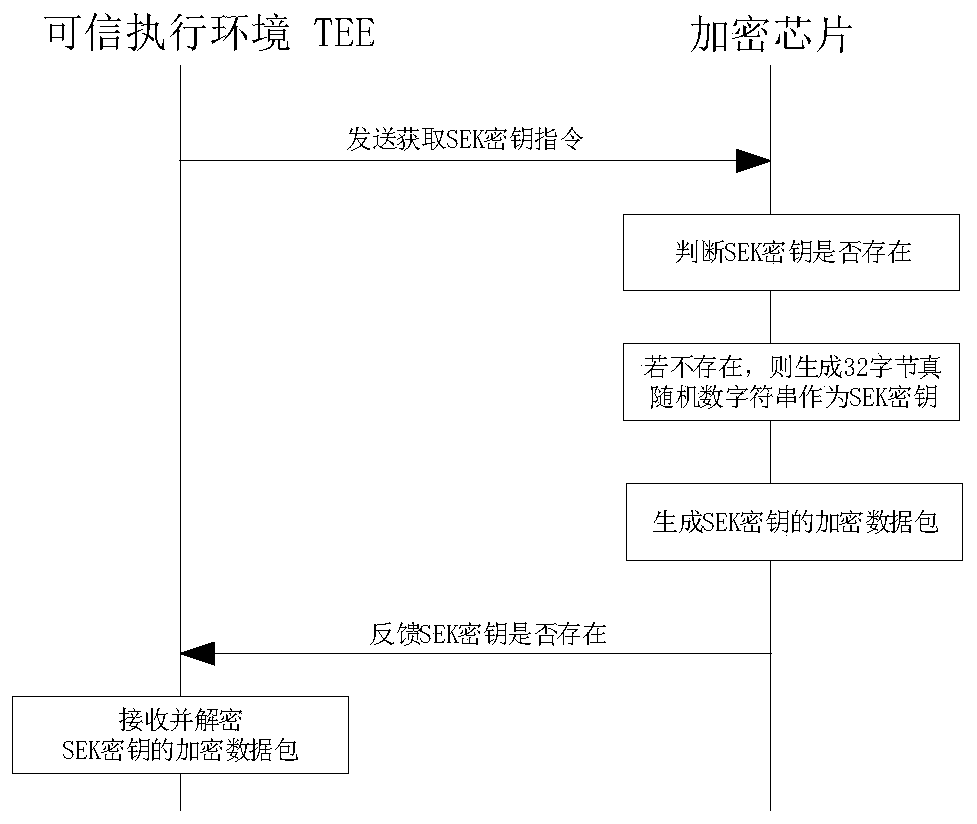
The invention discloses a method for increasing the security of a file encryption key in a trusted execution environment based on an encryption chip. The method comprises: integrating an encryption chip on a terminal device; controlling the encryption chip by a terminal device manufacturer to generate an encryption chip secret key as a secret key composition factor; generating a file encryption key protection key, used for protecting the file encryption key used when the file is encrypted in TEE service, and preventing problems that in the TEE service process, a chip manufacturer can completely decrypt the ciphertext data into a plaintext when leaving backdoor in the key generation process or performing inverse operation on the encryption key, and the sensitive data has the risk of being stolen. The security of the file encryption key is improved, and the autonomy and controllability of the terminal device manufacturer in encryption service are also improved. The embodiment is an improvement on the basis of an original TEE file encryption technology. The controllability of file encrypted storage and key algorithm is more conveniently realized under the condition that the encryptionand decryption efficiency of the original technology is not changed, and the security risk of key leakage is avoided.
Owner:深圳市中易通安全芯科技有限公司
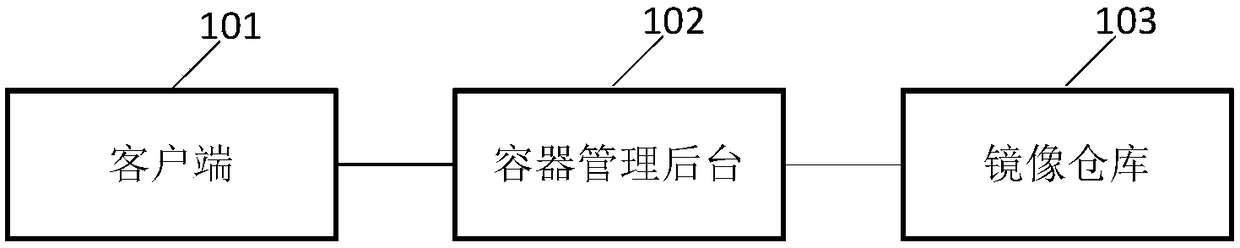
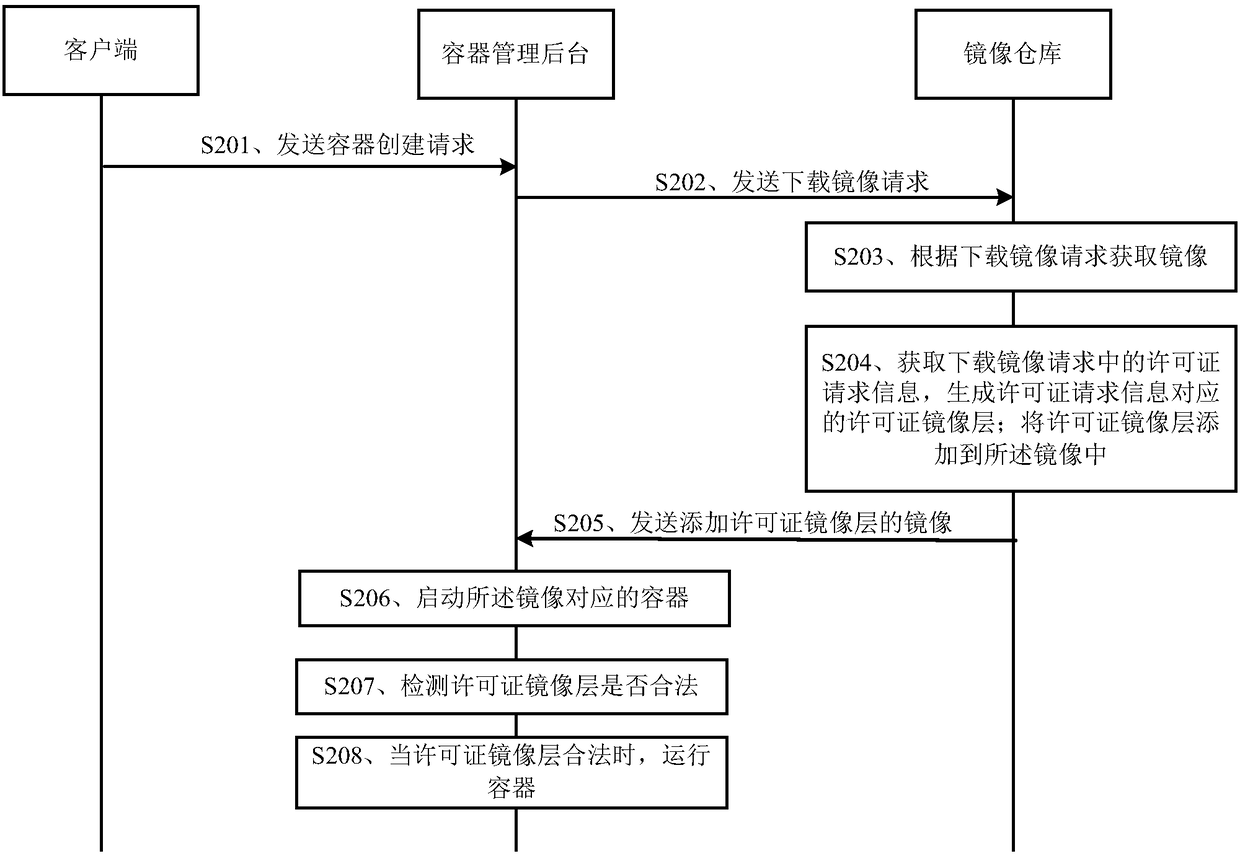
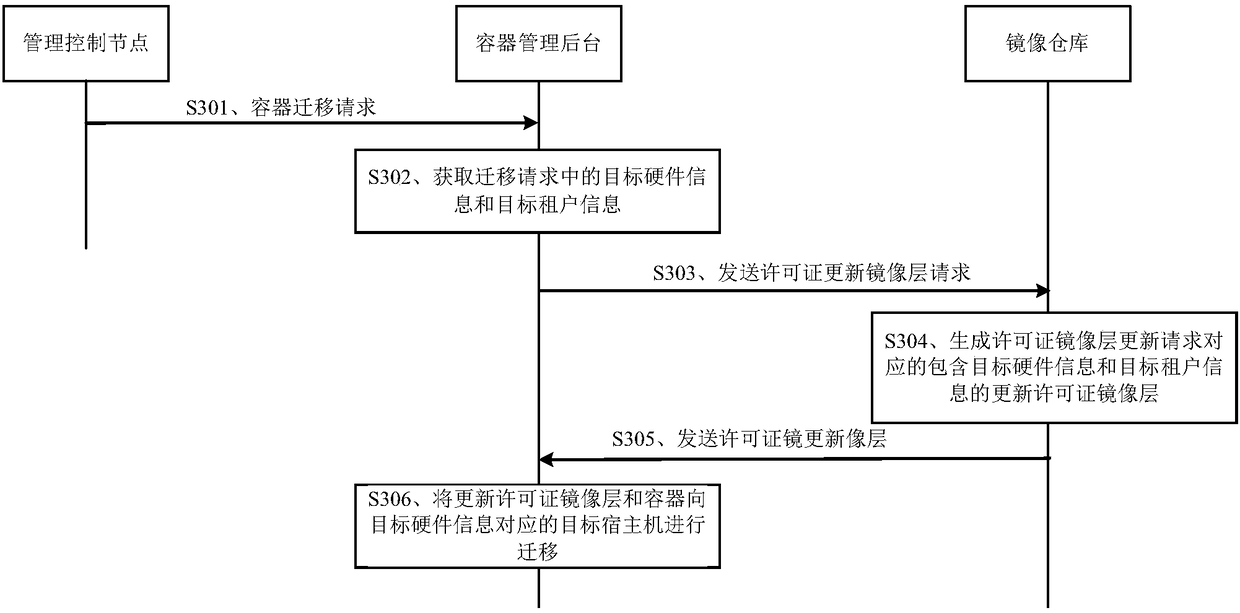
License managing method and device for containers
ActiveCN108628658AImprove management efficiencyImprove securityResource allocationComputer security arrangementsMirror imageComputer science
The embodiment of the invention discloses a license managing method and device for containers. The license managing method for the containers comprises the following steps of: receiving a mirror imagedownloading request containing information for requesting a license, which is sent by a container managing background; acquiring a mirror image according to the mirror image downloading request; acquiring the information for requesting the license in the mirror image downloading request and generating a license mirror image layer corresponding to the information for requesting the license; addingthe license mirror image layer to the acquired mirror image; and sending the mirror image added with the license mirror image layer to the container managing background to enable the container managing background to start a container corresponding to the mirror image and detect whether the license mirror image layer is legal or not. By adopting the method disclosed by the embodiment of the invention, the license managing efficiency of the container can be improved.
Owner:HUAWEI TECH CO LTD
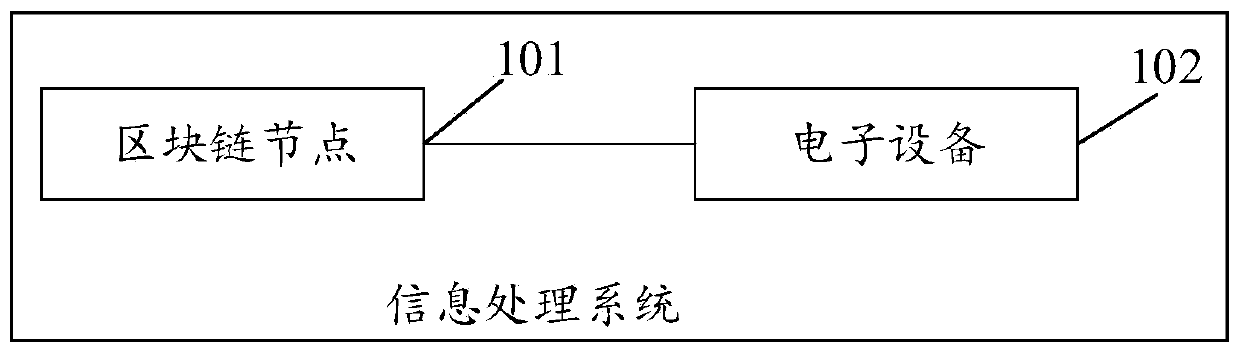
Information processing method, block chain node and electronic equipment
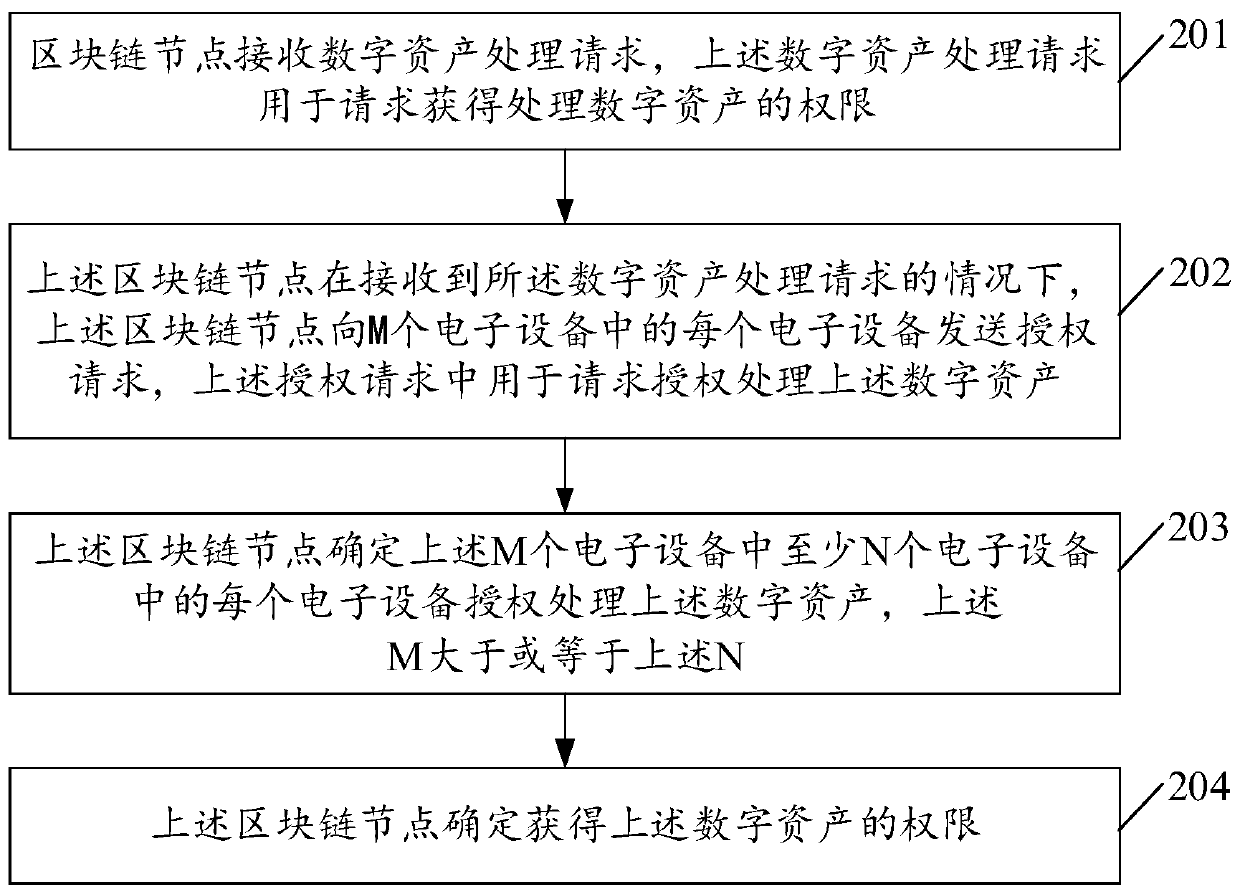
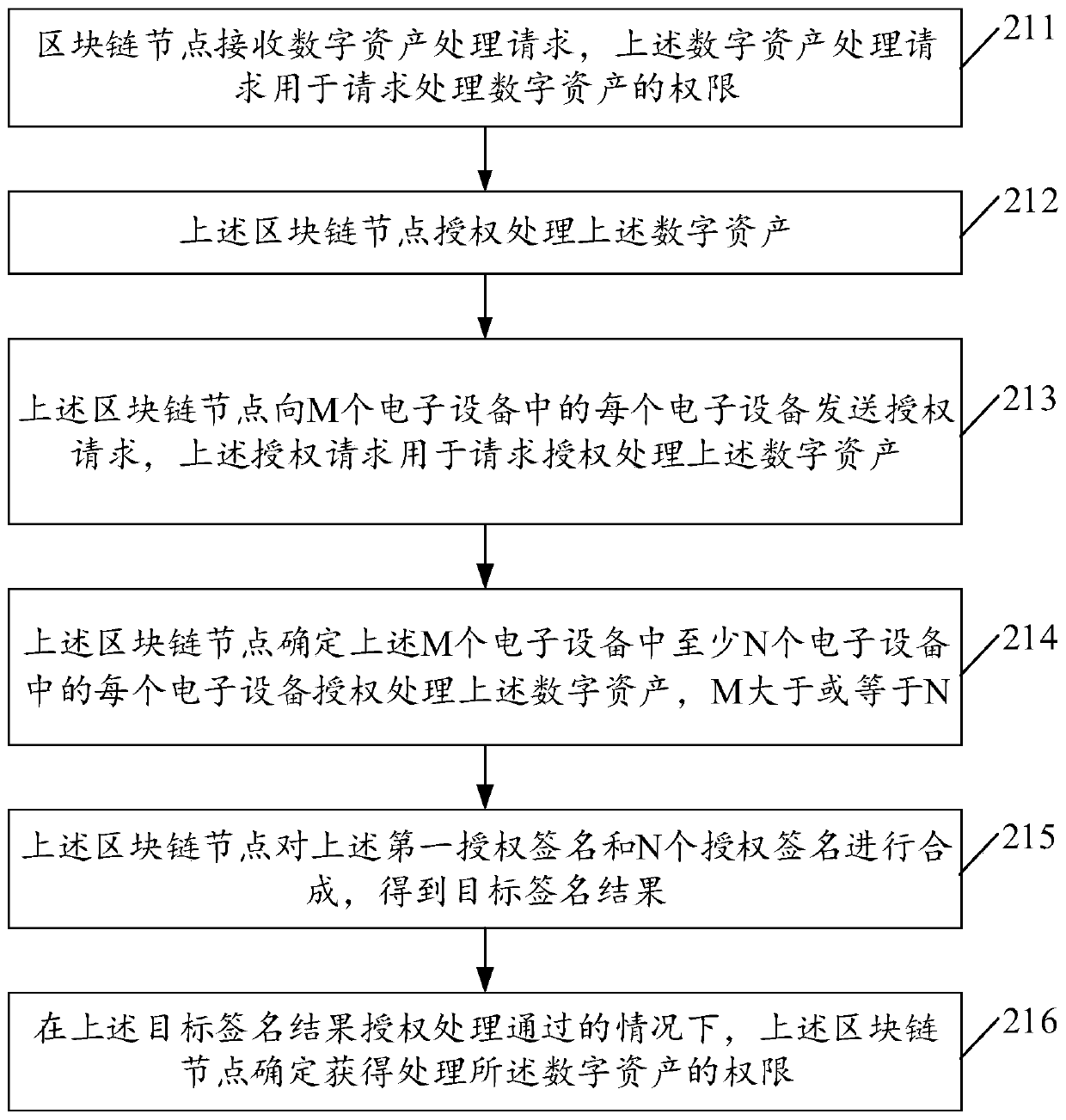
ActiveCN109697365AAvoid the risk of being stolenImprove securityMultiple keys/algorithms usagePublic key for secure communicationInformation processingAuthorization
The invention discloses an information processing method and device, and the method comprises the steps that a block chain node receives a digital asset processing request, and the digital asset processing request is used for requesting the authority of processing digital assets; under the condition that the block chain node receives the digital asset processing request, the block chain node sendsan authorization request to each electronic device in the M electronic devices, and the authorization request is used for requesting authorization processing of the digital asset; the blockchain nodedetermines that each electronic device in at least N electronic devices in the M electronic devices authorizes to process the digital asset, wherein M is greater than or equal to N; and the block chain node determines to obtain the authority of processing the digital asset. By adopting the method and the device, the efficiency of authorizing the digital assets can be effectively improved.
Owner:LAUNCH TECH CO LTD
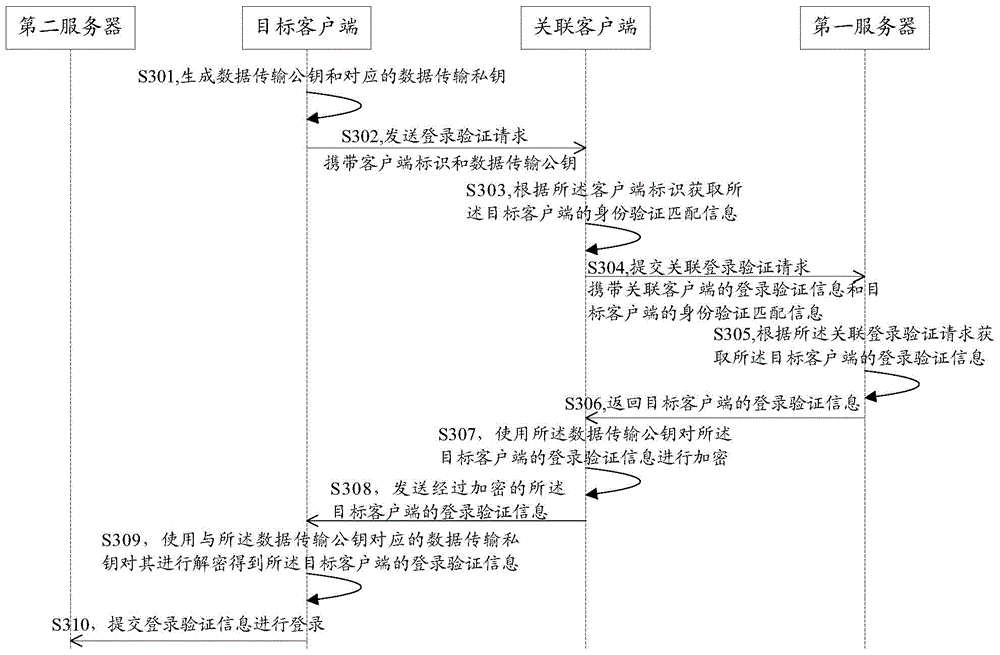
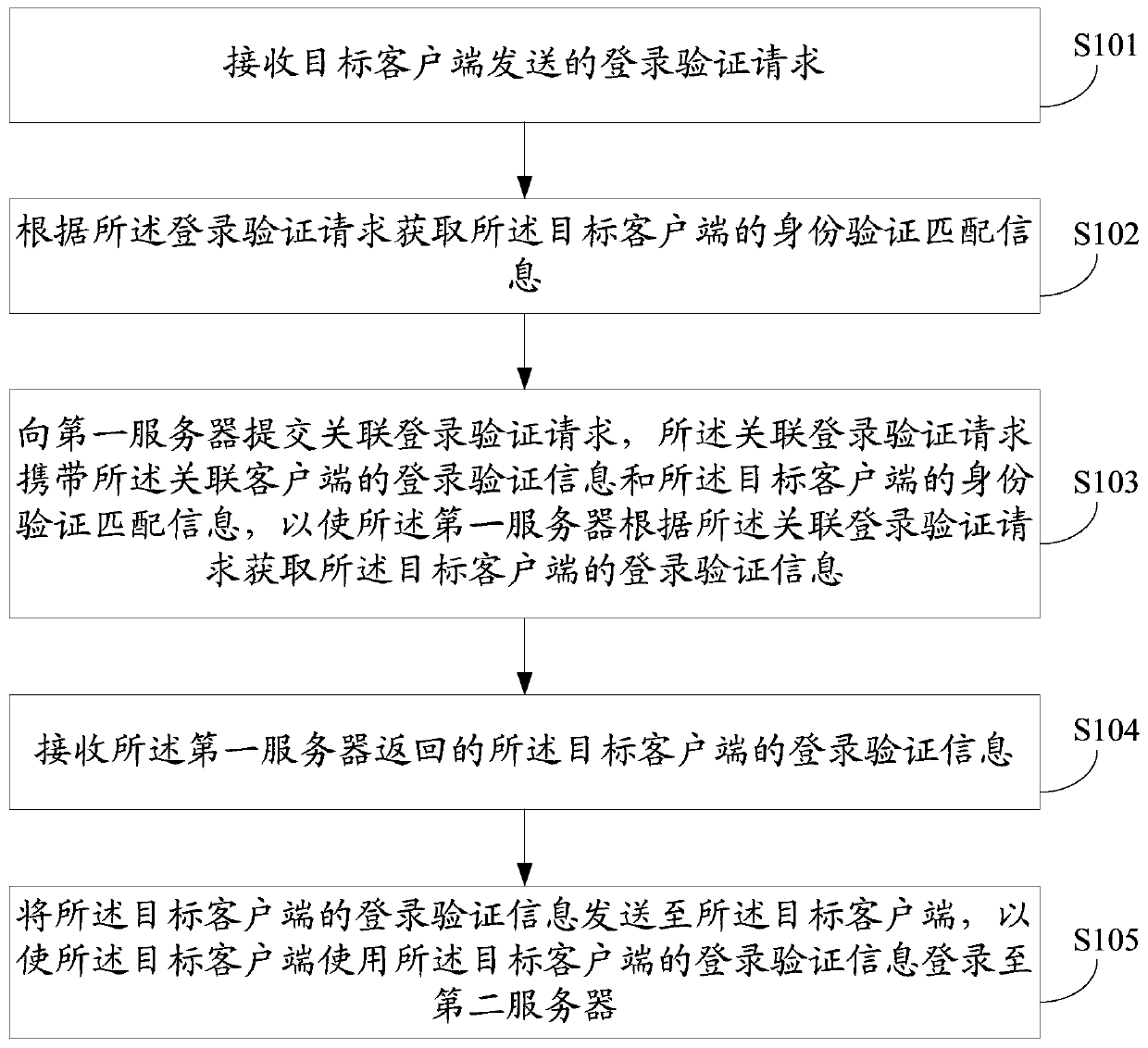
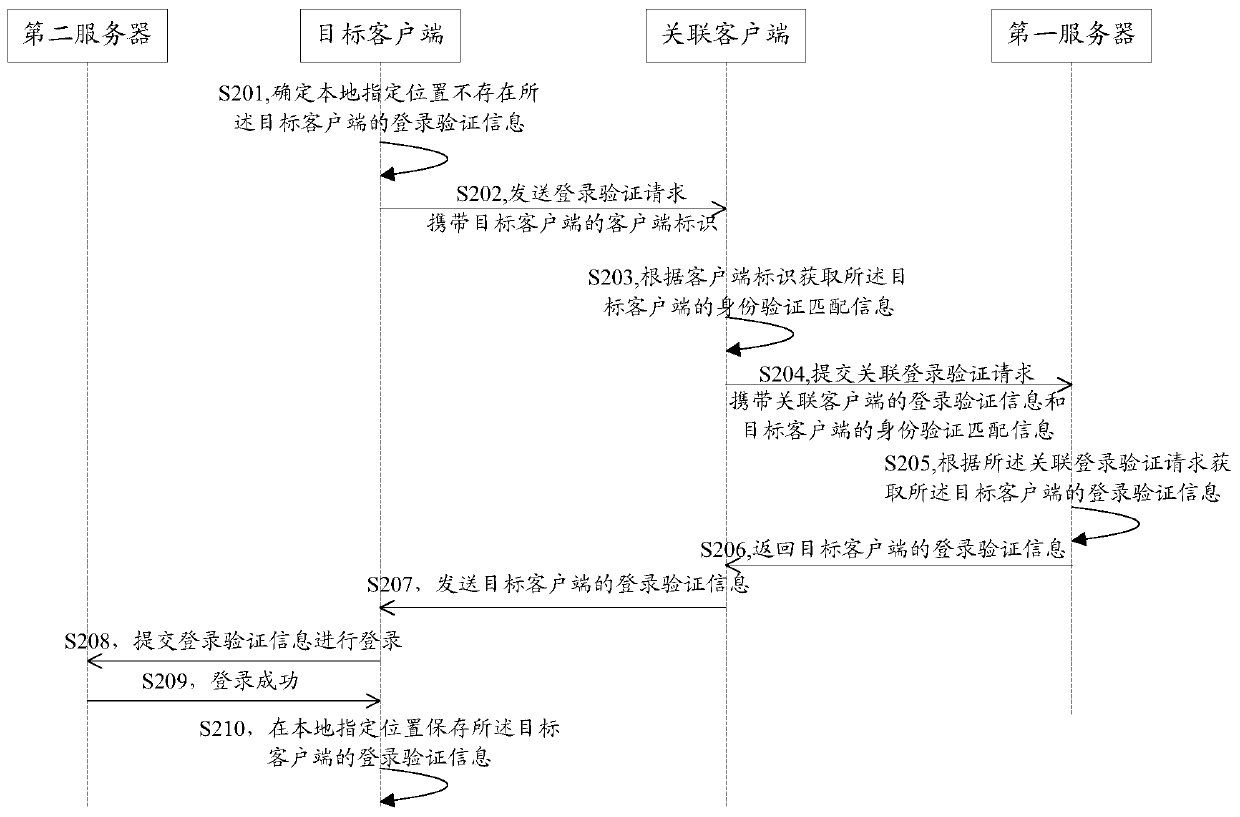
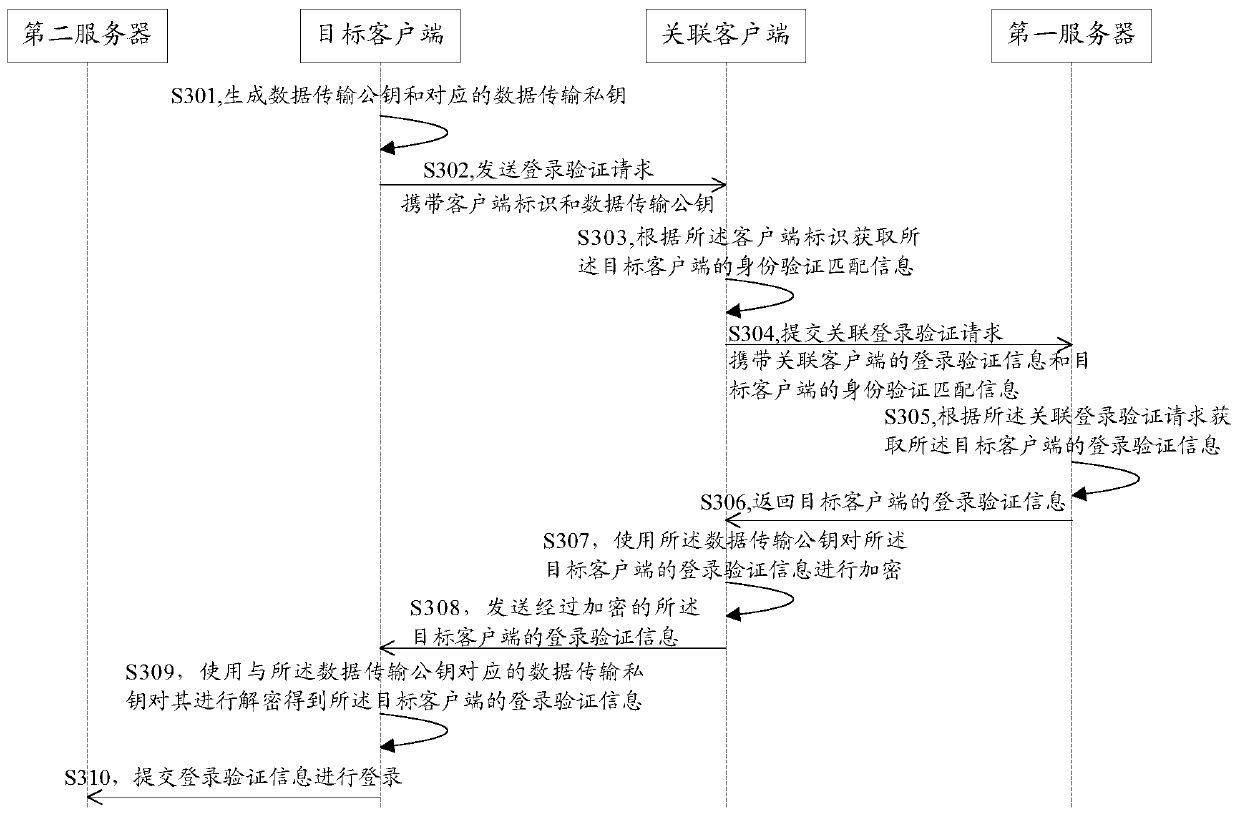
Method and system for logging in client and client
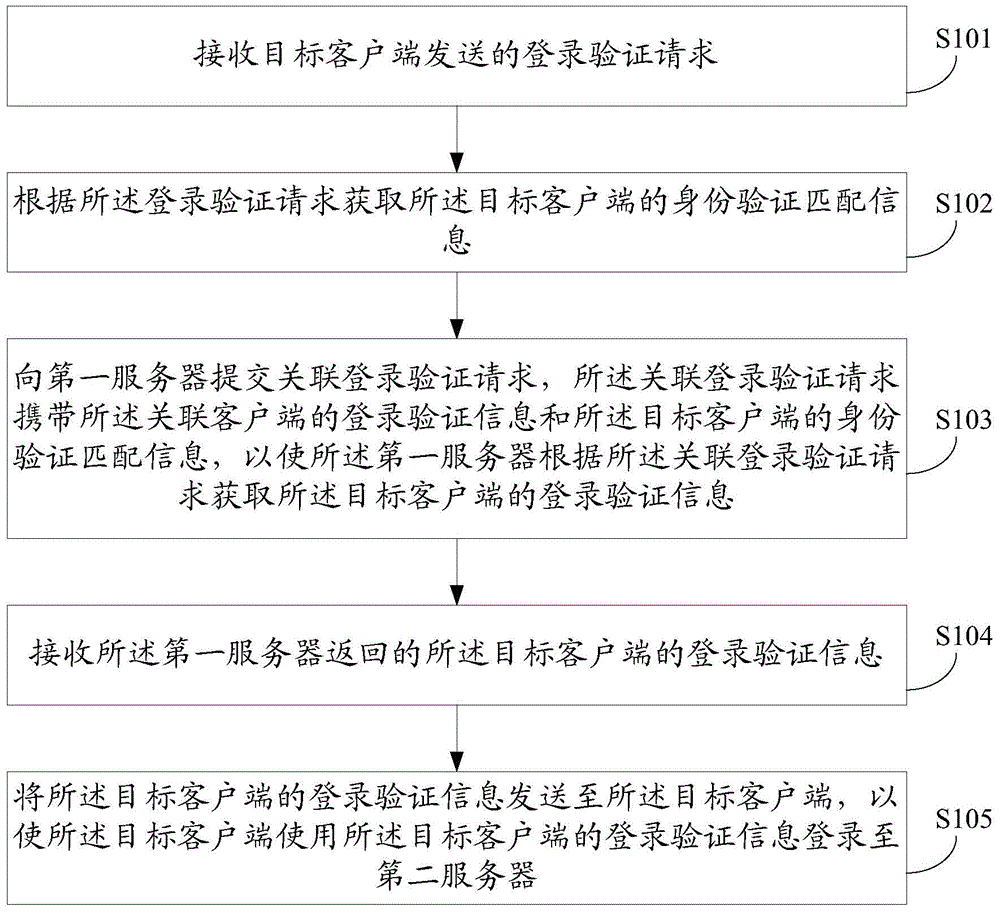
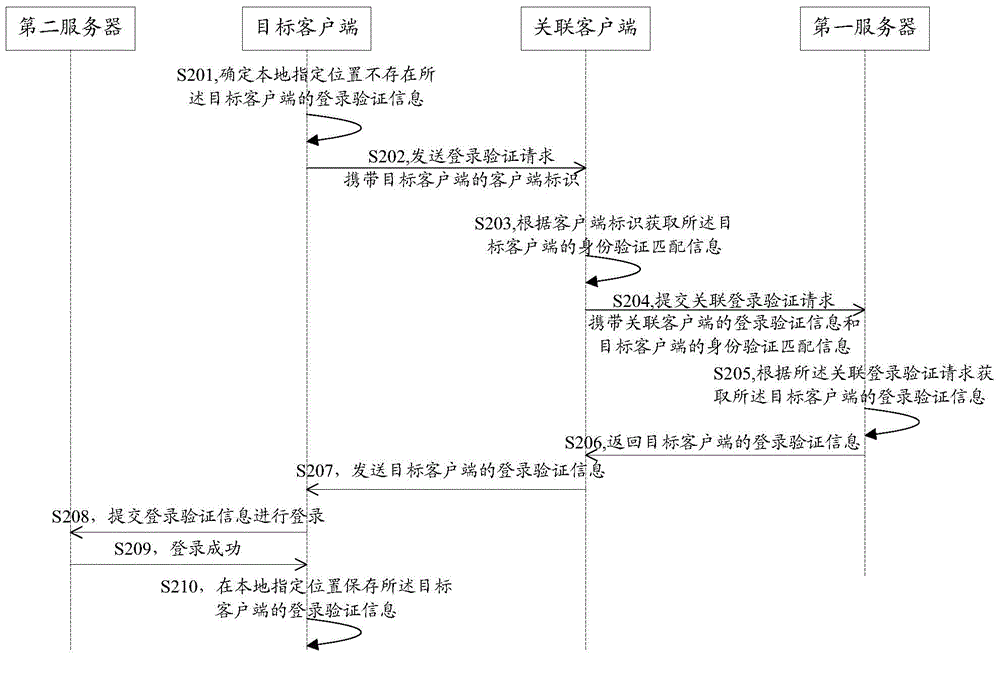
The embodiment of the invention discloses a method and system for logging in a client and a client. The method for logging in a client comprises: a logging-in verification request sent by a target client is received; according to the logging-in verification request, identity verification matching information of the target client is obtained; an associated logging-in verification request is submitted to a first server, so that the first server obtains logging-in verification information of the target client according to the associated logging-in verification request; the logging-in verification information, returned by the first server, of the target client is received; and the logging-in verification information of the target client is sent to the target client, so that the target client can log in a second server by using the logging-in verification information of the target client. According to the invention, rapid logging in of an application client can be realized and a risk of stealing logging-in verification information can be effectively eliminated, so that the logging-in security of the client can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
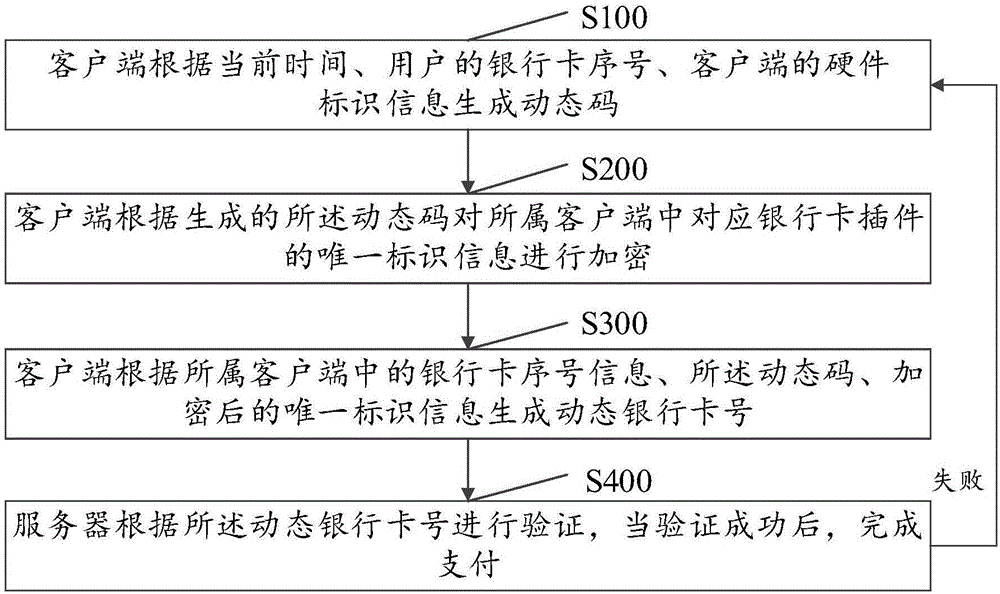
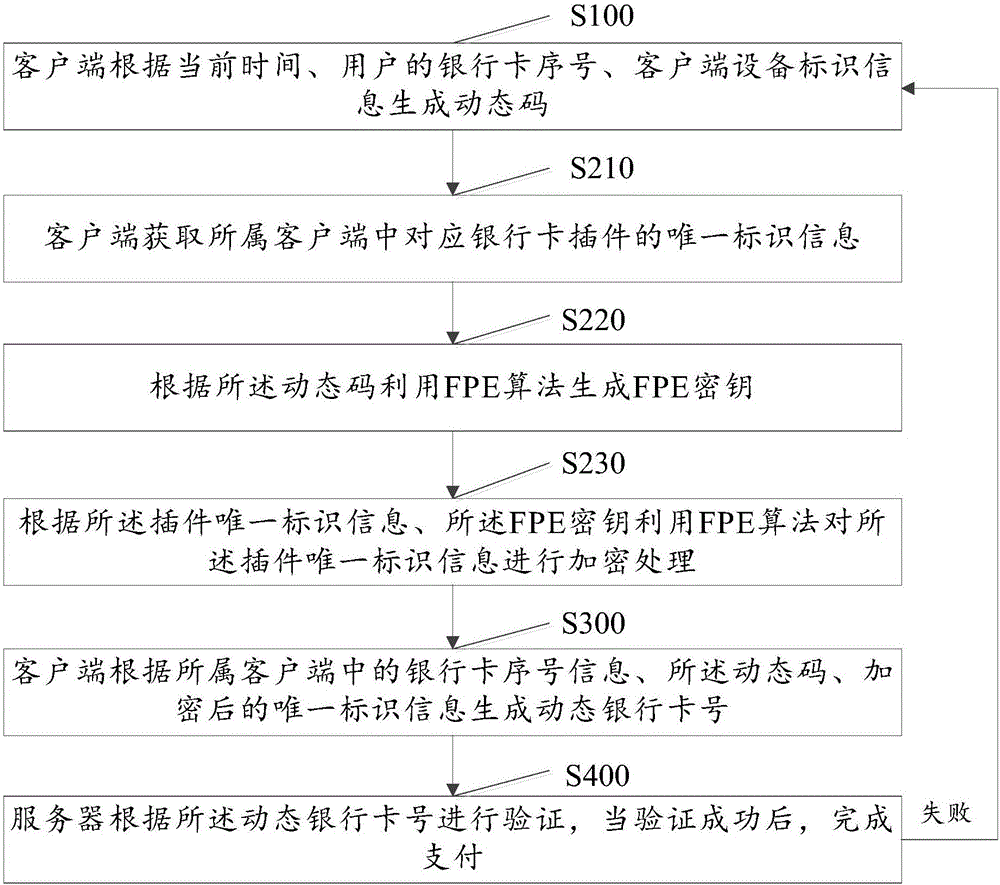
Dynamic payment method and system
The invention discloses a dynamic payment method and system. The method comprises the steps that S100, a client generates a dynamic code according to current time, a bank card serial number of a user and device identifier information of a client; S200, the client encrypts unique identifier information corresponding to a bank card plug-in in the client according to the generated dynamic code; S300, the client generates a dynamic bank card number according to the bank card serial number information in the client, the dynamic code and the encrypted unique identifier information in the step S200; and S400, a server performs verification according to the dynamic bank card number, and finishes payment when the verification succeeds, otherwise, returns to and executes the step S100. The purpose of the method is to generate the dynamic bank card number, and an offline authentication mode is adopted, so that the payment efficiency is improved and the use convenience is brought for users.
Owner:SHANGHAI PEOPLENET SECURITY TECH
Data encryption method, user terminal, server and system
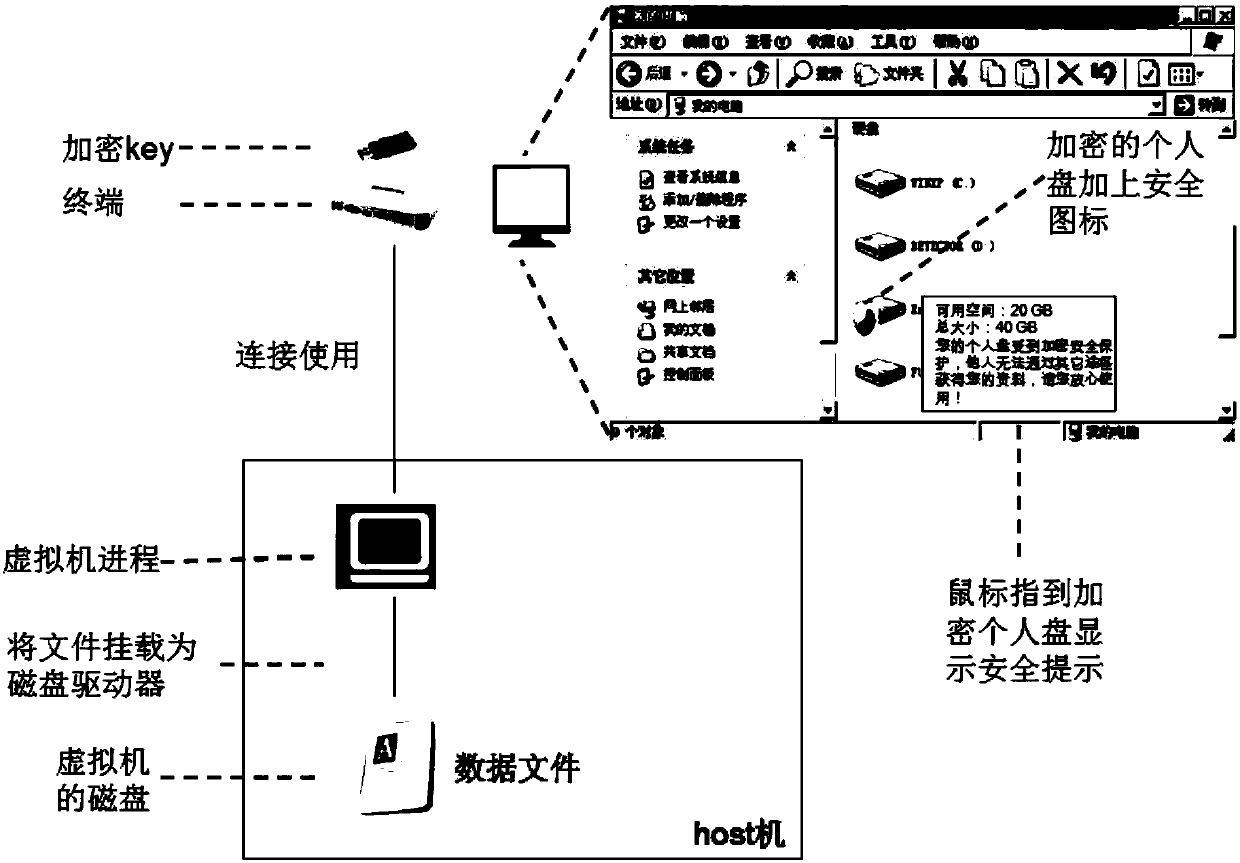
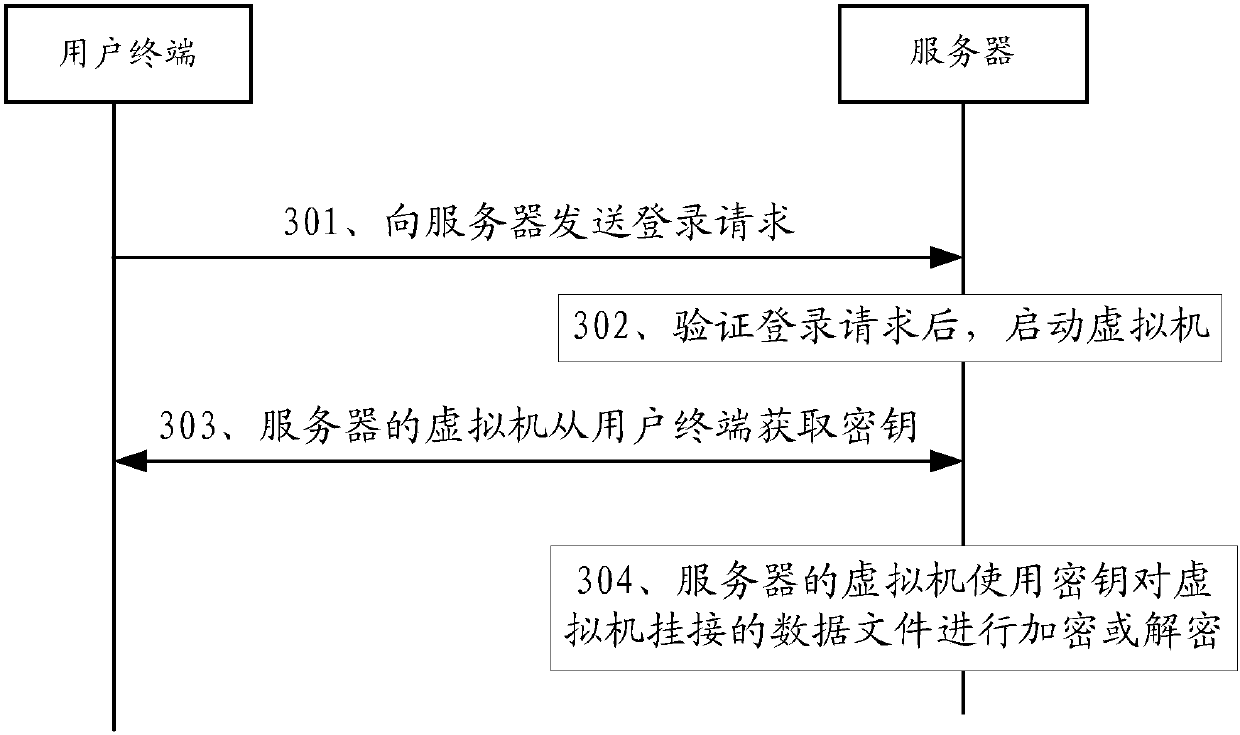
ActiveCN107689943AImprove securityImprove experienceTransmissionSoftware simulation/interpretation/emulationVirtual desktopData file
The embodiment of the invention discloses a data encryption method, a user terminal, a server and a system, and aims to enhance the security of data storage. The method is applied to a virtual desktopinfrastructure (VDI); the VDI comprises a user terminal and a server; and a virtual machine runs on the server. The method in the embodiment of the invention comprises the following steps that: the server receives a login request of the user terminal; the server verifies the login request, and launches the virtual machine; and the virtual machine of the server acquires a key from the user terminal, and encrypts or decrypts a data file which is mounted on the virtual machine. Through adoption of the data encryption method, the user terminal, the server and the system, encryption and decryptionof a virtual desktop personal disk can be controlled through a key on the terminal, and the key used for encrypting and decrypting the data file does not exist in the server, so that an administratorcan be prevented from letting out a secret by taking away a disk storing data and keys, and the security of data storage is enhanced.
Owner:SANGFOR TECH INC
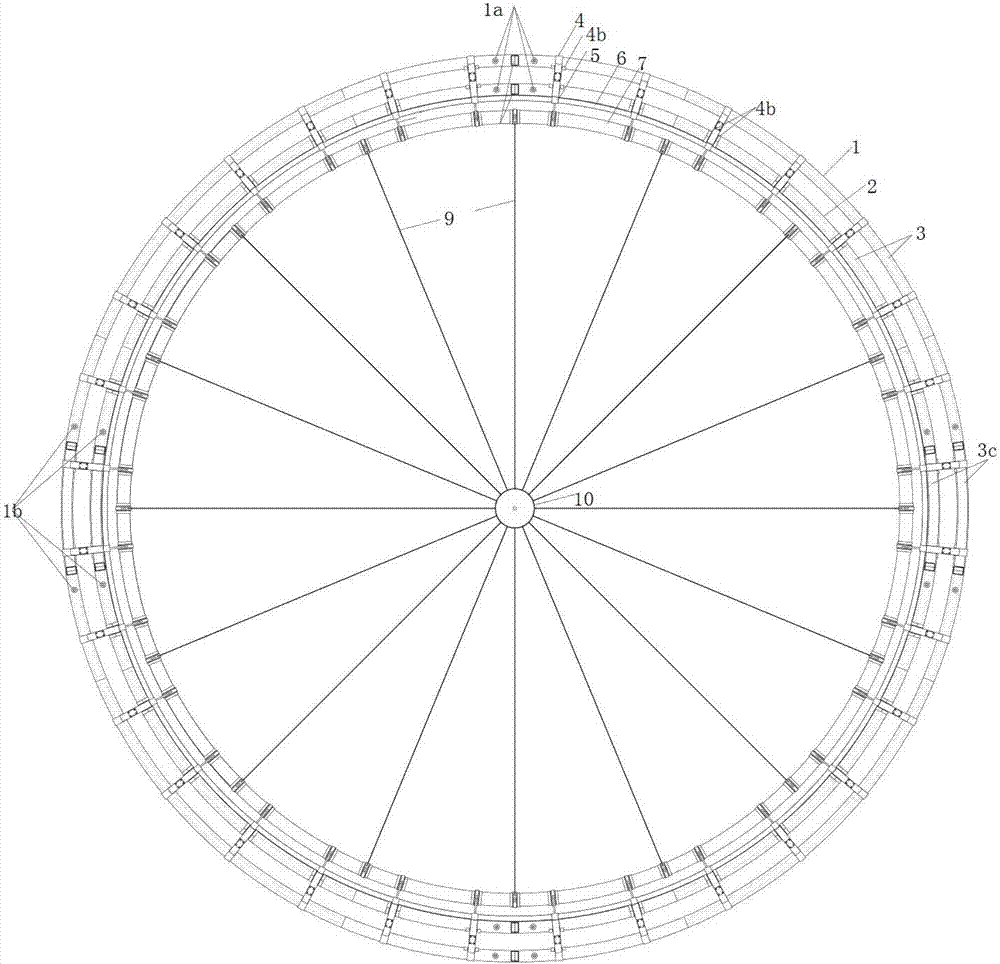
Sinking and floating type net cage
ActiveCN107148930AEasy accessAvoid destructionClimate change adaptationPisciculture and aquariaWater flowEngineering
The invention relates to a sinking and floating type net cage. The sinking and floating type net cage comprises at least two floating pipes, multiple floating pipe connection pieces, multiple handrails, at least one set of net, at least one net base rack, at least one sinker, at least one wire collector, at least one anchor, multiple sets of chains or ropes and at least one pipe-in-pipe. The floating pipes are used as floating bodies of the sinking and floating type net cage and are enclosed into two circles. The floating pipe connection pieces are used for fixing the floating pipes together. The handrails are arranged on the floating pipe connection pieces in an inward manner. The at least one sinker is arranged under the net base racks. The wire collectors are arranged between the net base racks and the sinkers. The anchors are arranged at the bottom of the sea and are used for fixing the net cage so that the net cage will not move along with the water flows. The chains or the ropes are used for connecting the floating pipe connection pieces to the net base racks, connecting the net base racks to the wire collectors, connecting the wire collectors to the sinkers and connecting the sinkers to the anchors. The pipe-in-pipes are sealed and filled with gas and arranged in the floating pipes. Adjusting assemblies are arranged on the floating pipes and / or the wire collectors, and are used for adjusting the sinking and floating of the net cage.
Owner:崔文亮
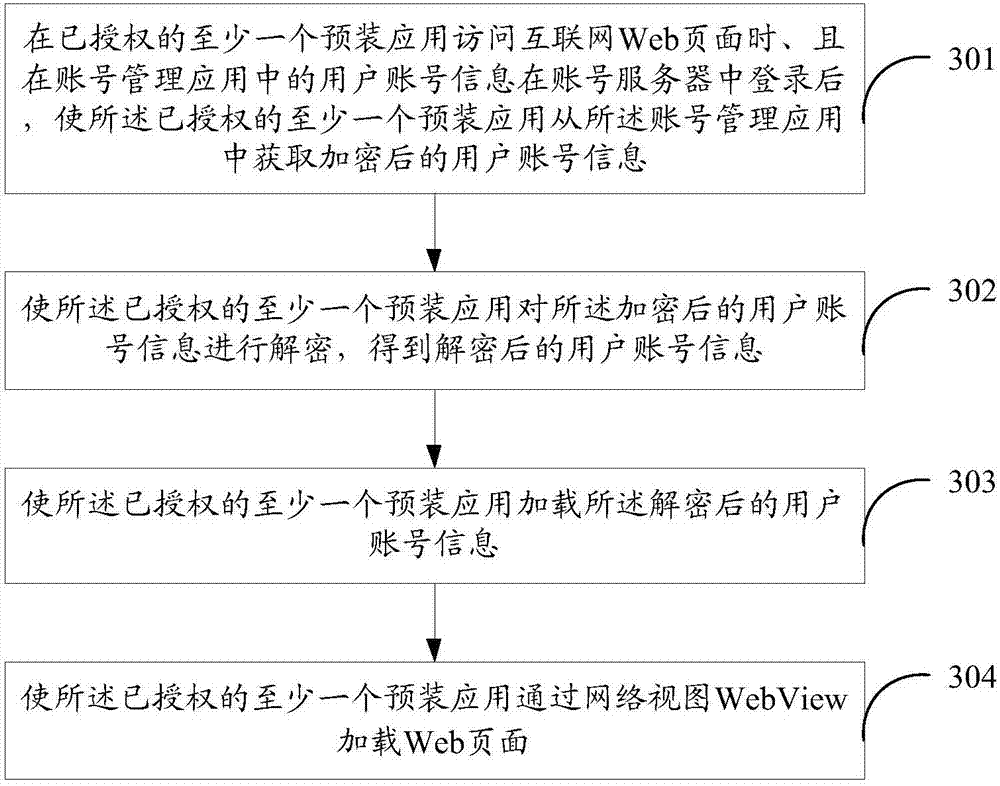
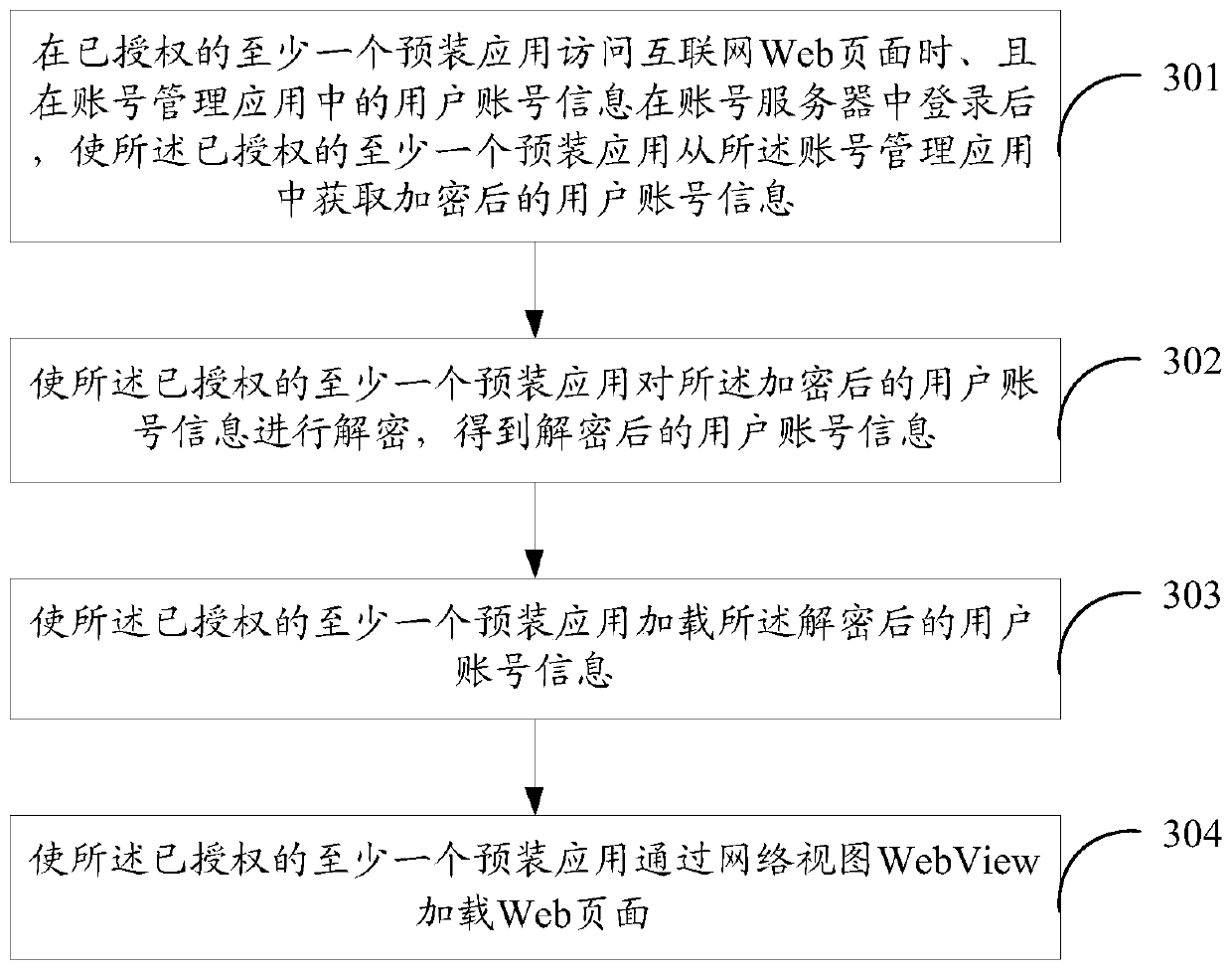
Method and equipment for loading Web page, and computer-readable storage medium
ActiveCN107276991AAvoid the risk of being stolenImprove securityTransmissionSpecial data processing applicationsWorld Wide WebComputer science
The invention discloses a method for loading a Web page. The method comprises the steps of: when at least one authorized pre-installed application accesses a Web page and after the user account information in an account management application is logged in an account server, enabling the at least one authorized pre-installed application to obtain encrypted user account information from the account management application; enabling the at least one authorized pre-installed application to decrypt the encrypted user account information, so that the decrypted user account information is obtained; enabling the at least one authorized pre-installed application to load the decrypted user account information; and enabling the at least one authorized pre-installed application to load the internet Web page through a WebView. The invention also discloses equipment for loading the Web page and a computer-readable storage medium. When the Web page is loaded in the pre-installed application through the WebView, the login state of the Web page is kept; and thus, the security of the user account information when the Web page is loaded is improved.
Owner:BEIJING GREATMAP TECH
Road charging system and operating method thereof
InactiveCN108765605ALower initial installation costsAvoid the risk of being stolenTicket-issuing apparatusCo-operative working arrangementsAuthorizationImage identification
The embodiment of the invention discloses a road charging system and an operating method thereof. The road charging system includes a vehicle-mounted identity electronic label, computer control unitsarranged at the entrance and exit fee collection counters, a road side reading antenna unit, an image identification unit, a lane equipment unit and a network background, wherein the road side readingantenna unit, the image identification unit, the lane equipment unit and the network background are communicated with the computer control units. The operating method of the road charging system utilizes the vehicle-mounted identity electronic label and image identification mode to verify a target vehicle. In the road charging system and the operating method thereof, a new charging mode is used,thus avoiding cumbersome process of mounting OBU equipment, and reducing the initial mounting cost of the vehicle; avoiding the risk that the OBU equipment bank card is swiped without authorization; and by comparing the vehicle-mounted identity electronic label information with the vehicle number information, improving the safety of charging and avoiding fake plates.
Owner:苏州八股网络科技有限公司
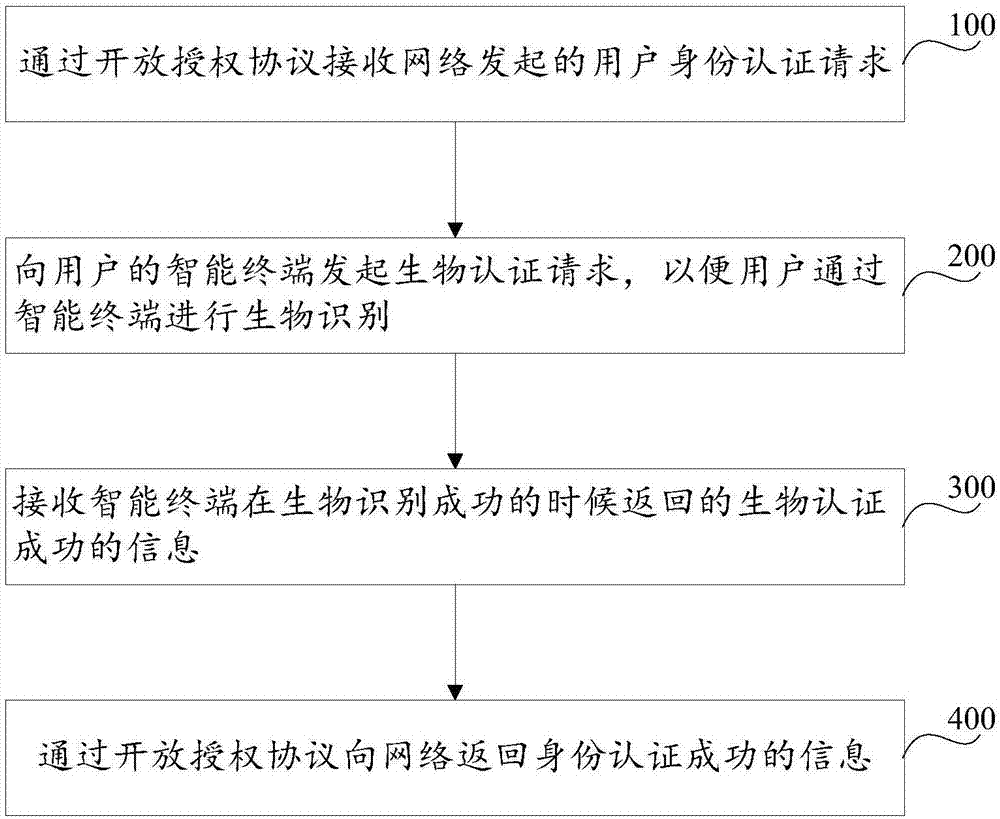
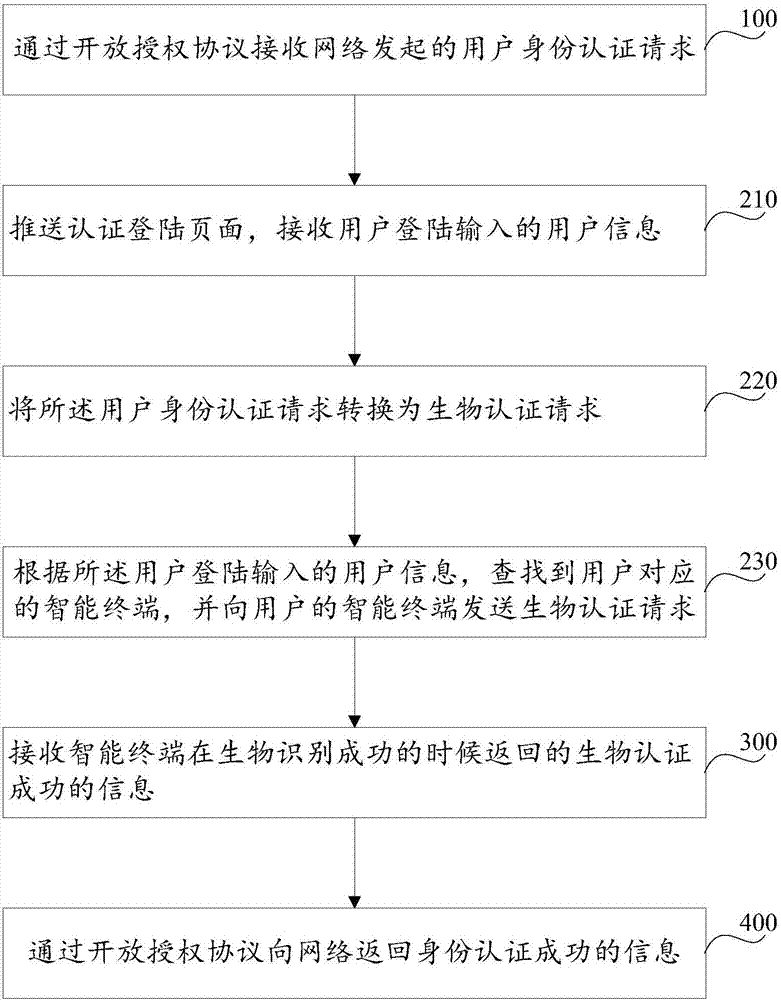
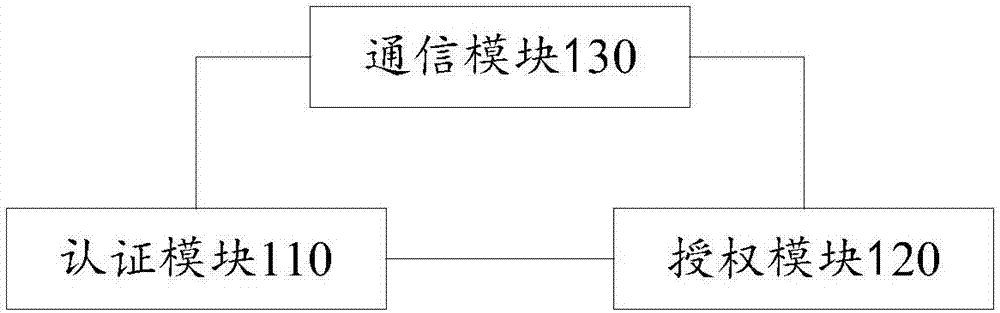
Network identity authentication method, system and intelligent terminal
InactiveCN106982221AEasy to implementEasy to understandTransmissionInternet Authentication ServiceThe Internet
The invention discloses a network identity authentication method. The method comprises the following steps: S100, receiving a user identity authentication request initiated by a network through an open license agreement; S200, initiating a biometric authentication request to an intelligent terminal of a user so that the user can perform the biometric recognition through the intelligent terminal; S300, receiving biometric authentication success information returned by the intelligent terminal when the biometric recognition is successful; and S400, returning the identity authentication success information to the network through the open license agreement. Furthermore, the invention further discloses a network identity authentication system and the intelligent terminal. By combining the biometric authentication and the open license agreement standard, the user identity authentication service is provided for the internet online resource, and the security and the reliability of performing the identity authentication in the internet by the user are improved.
Owner:PHICOMM (SHANGHAI) CO LTD
Multi-layer data mapping authentication system
InactiveCN101771696AAvoid the risk of being stolenSensing record carriersTransmissionPrivate networkAuthentication server
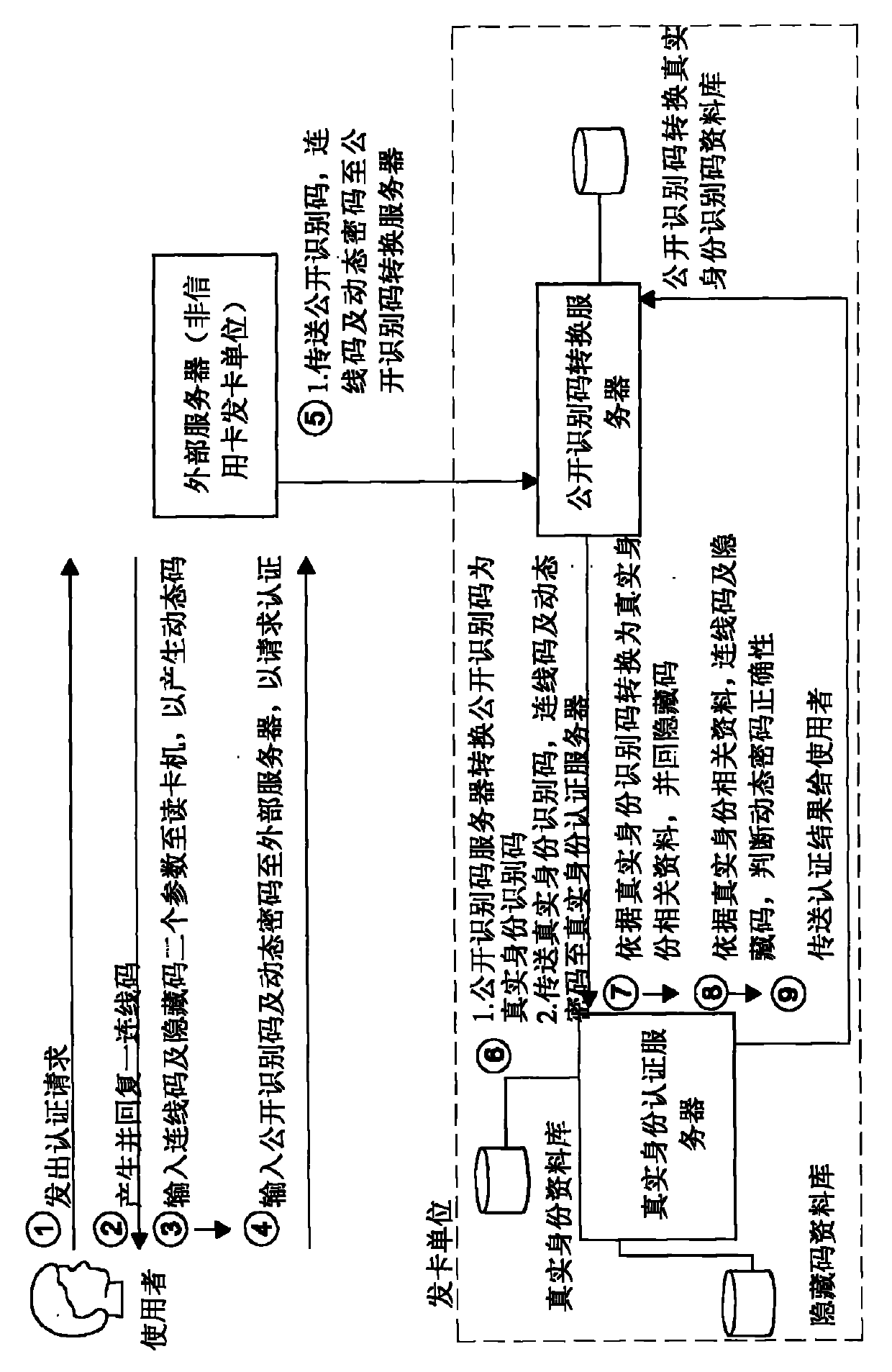
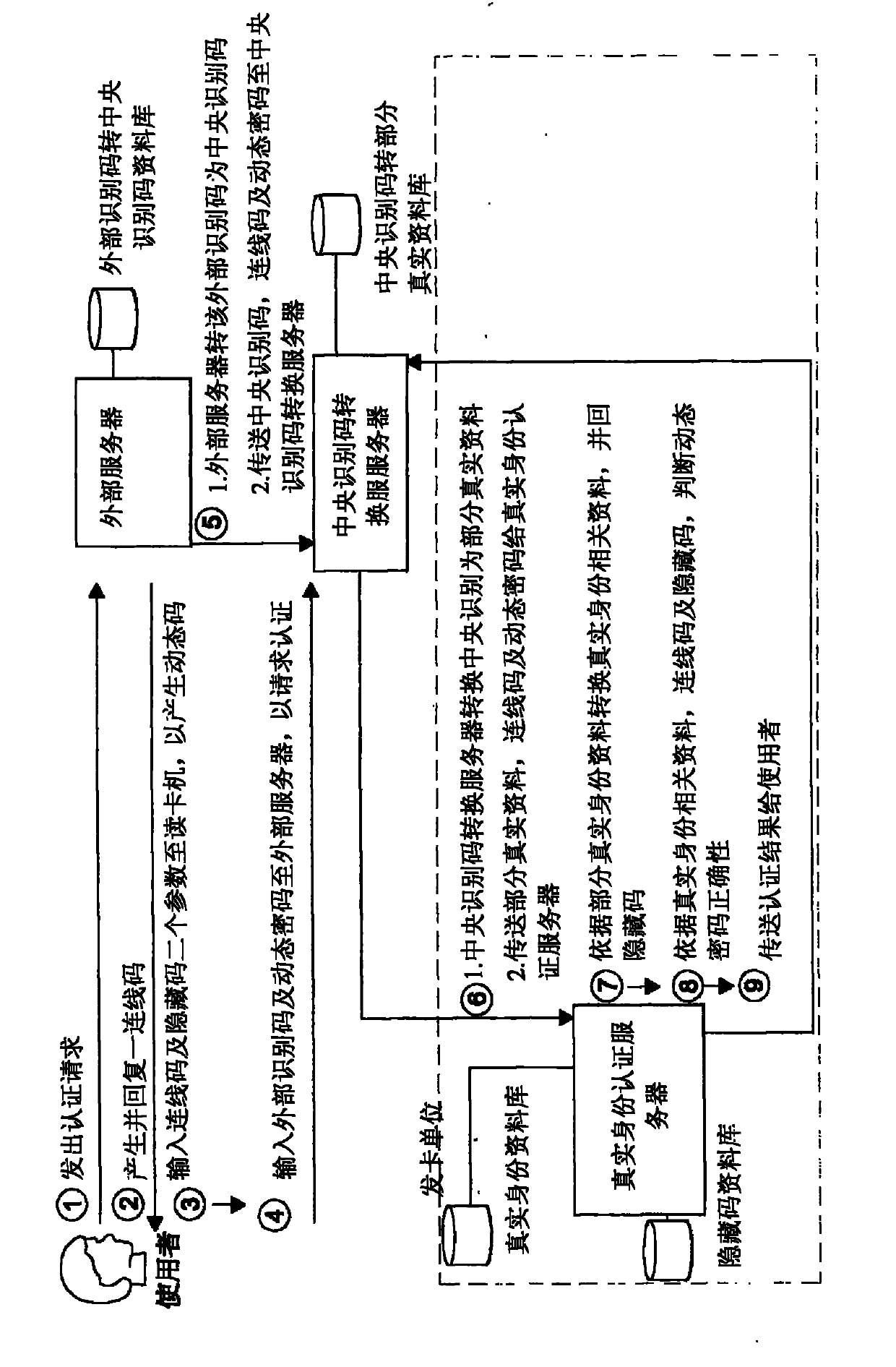
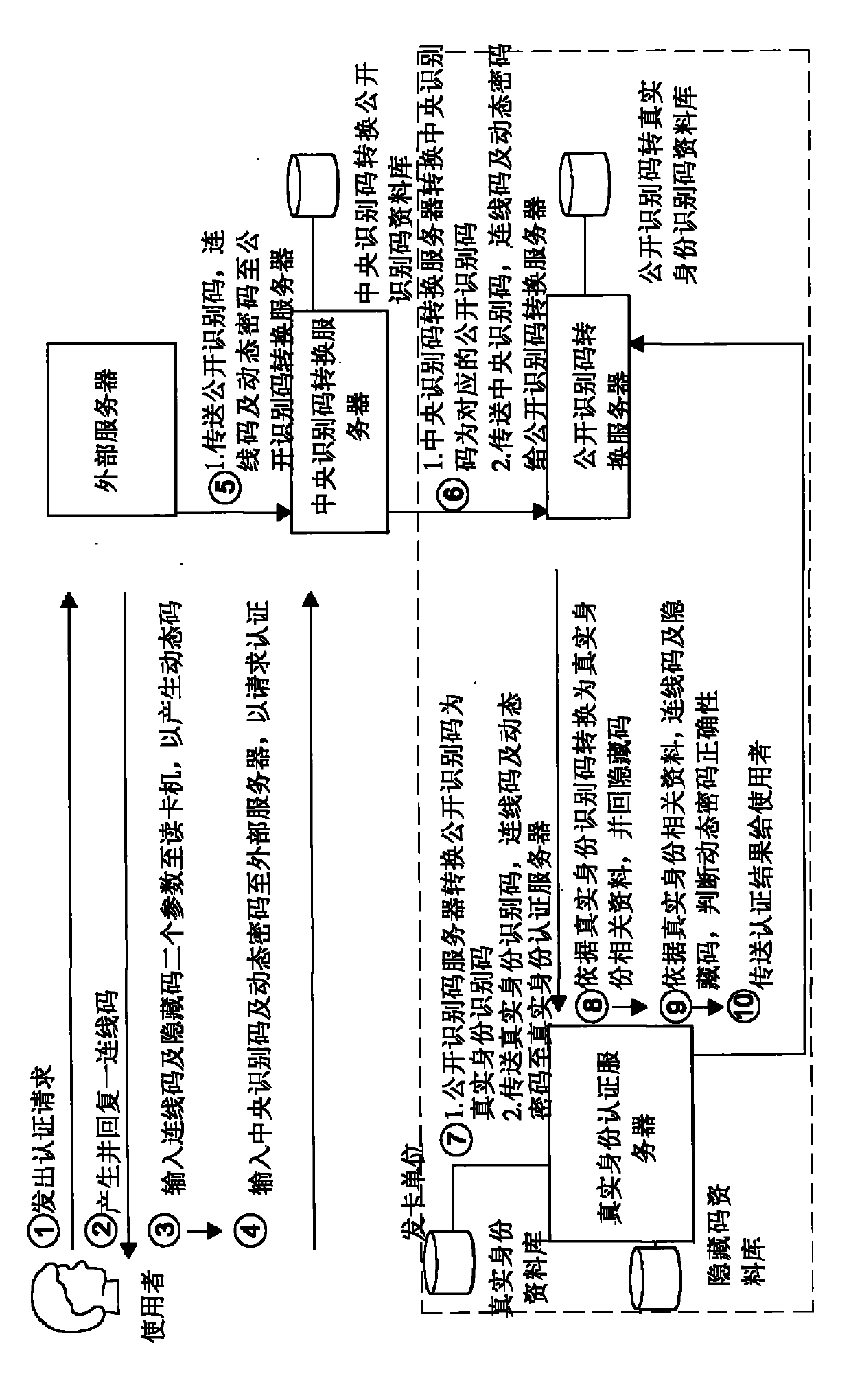
A multi-layer data mapping authentication system has a real ID authentication server, a middle data mapping server and a terminal data mapping server. The real ID authentication server links to a private network and stores real IDs and the hidden codes, each of which corresponds to a unique real ID. The terminal data mapping server links to a public network and allows an end user to link so that the end user sends the terminal data mapping server a user's code and an one-time-password (OTP). Since the middle data mapping server links between the real ID authentication server and the terminal data mapping server, the end user only uses hidden code to generate the OTP and sends the user's code and the OTP to the public network. The terminal and middle data mapping servers are converts the user's code to the corresponding real ID of the end user in the private network to complete the authentication procedure. The real ID and hidden code is not sent at the public network and is not stolen.
Owner:田种楠
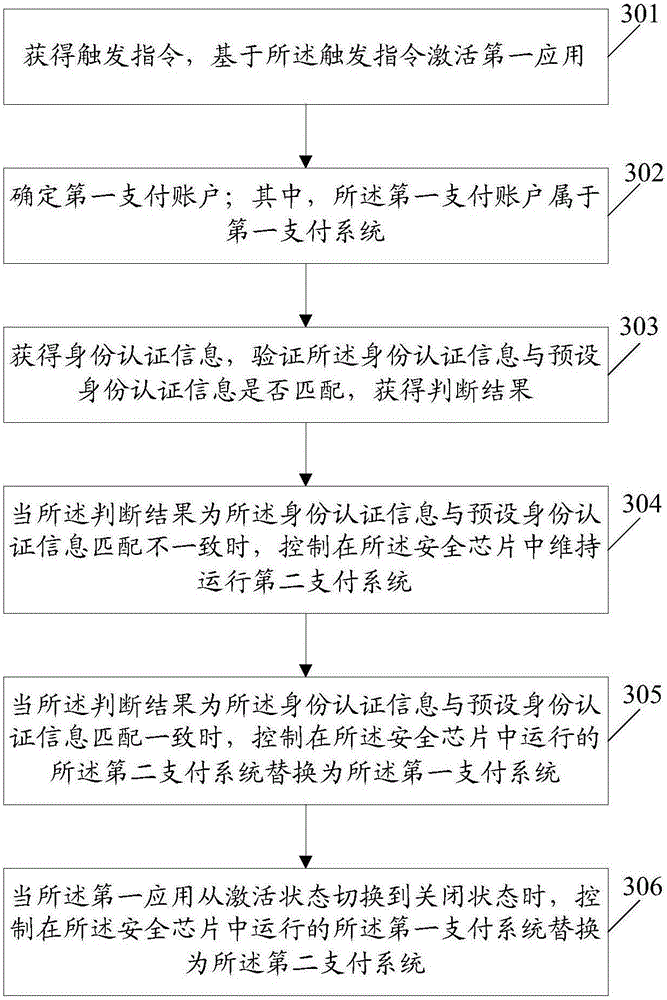
Information processing method and electronic device
ActiveCN105225113AAvoid the risk of being stolenImprove experienceProtocol authorisationInformation processingCard reader
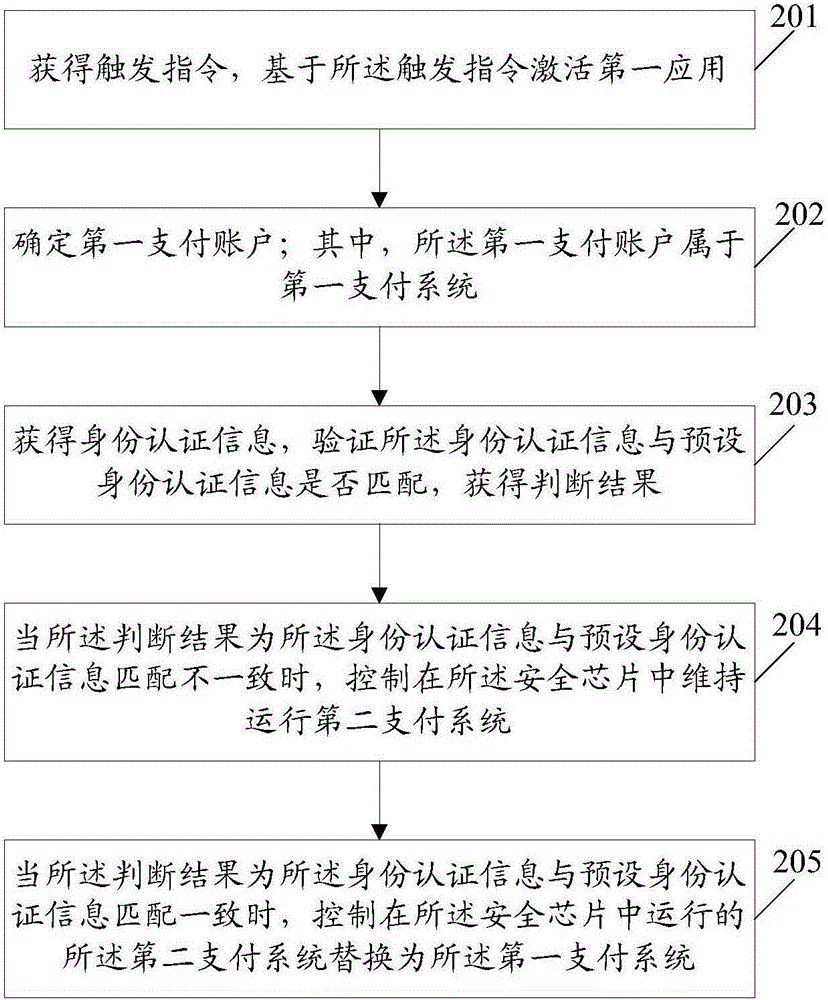
Embodiments of the present invention disclose an information processing method and an electronic device. The method comprises: acquiring a trigger instruction; activating a first application based on the trigger instruction, wherein the first application supports at least two payment accounts that can be supported in a security chip that manages the electronic device, and the at least two payment accounts correspond to at least two payment systems, and the security chip is connected to a near field communication device of the electronic device; determining a first payment account, wherein the first payment account belongs to a first payment system; acquiring identity authentication information; verifying whether the identity authentication information matches preset identity authentication information, and acquiring a determination result; and when the determination result is that the identity authentication information matches the preset identity authentication information, controlling to run the first payment system in the security chip, so that when the electronic device approaches a card reader, first payment account information of the first payment system is read by the card reader by means of the near field communication device.
Owner:LENOVO (BEIJING) LTD
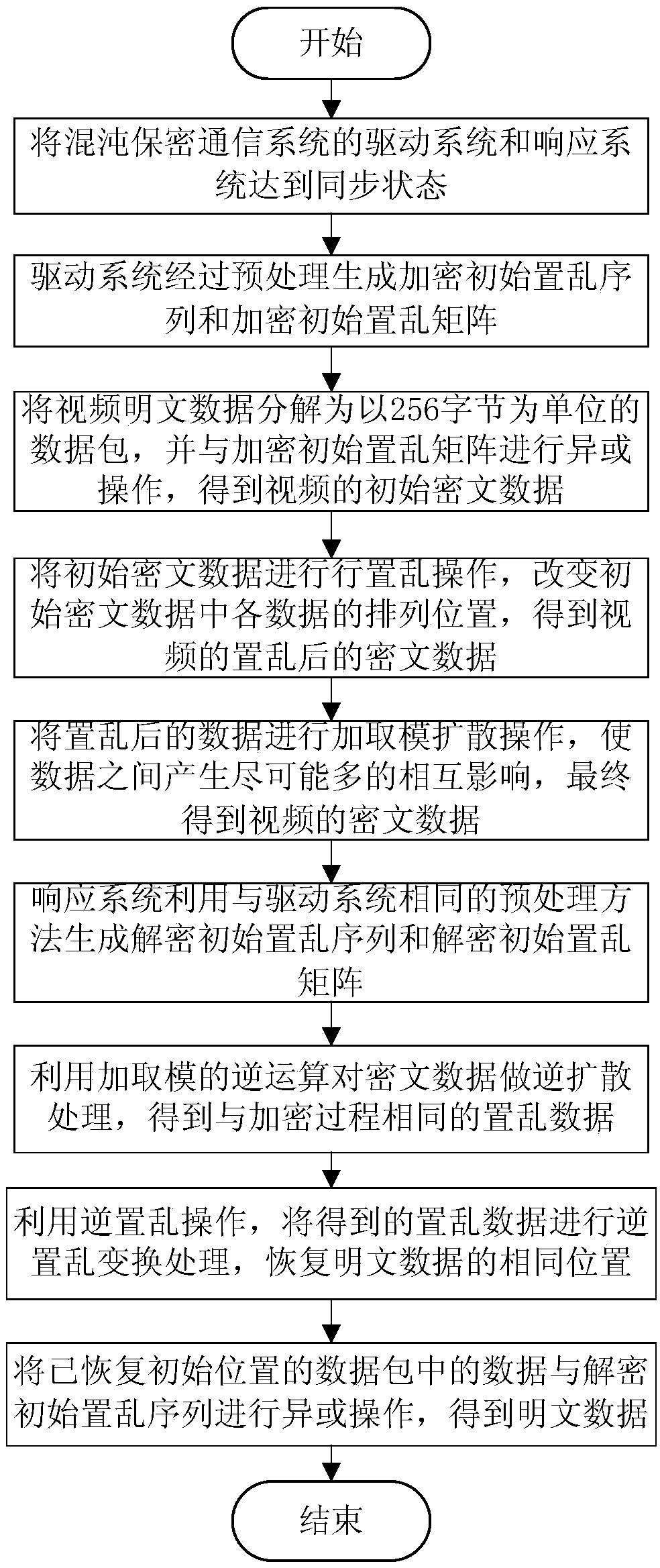
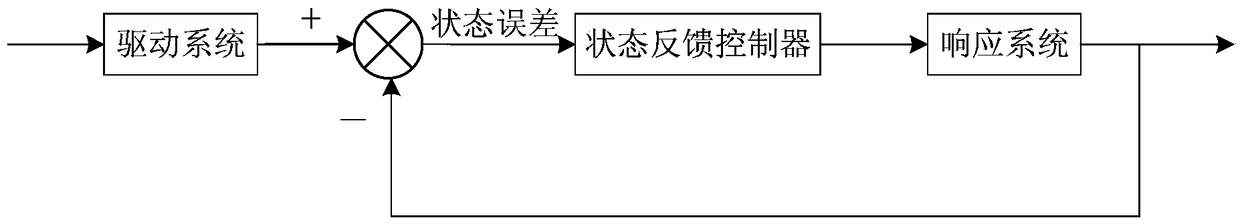
Video encryption method based on hyper-chaos system
InactiveCN108924594AAvoid the risk of being stolenOvercoming VulnerabilitiesSelective content distributionComputer hardwarePlaintext
The invention provides a video encryption method based on hyper-chaos system, and relates to the technical field of the image processing and secret communication. The method comprises the encryption process and the decryption process; the encryption process comprises the following steps: enabling a chaos secret communication system to achieve a synchronization state, and driving the system to generate an encryption initial scrambling sequence and an encryption initial scrambling matrix, and then decomposing video plaintext data into a data packet, performing XOR operation on the data packet and the encryption initial scrambling matrix to obtain initial cipherext data, and performing line scrambling operation on the initial ciphertext data; and finally performing adding module diffusion operation on the scrambled data to obtain the final video ciphertext data; the decryption process of the video is the inverse process of the encryption process. Through the video encryption method basedby the hyper-chaos system provided by the invention, the key can be transmitted without using a specific channel, and the risk that the key is stolen in the transmission process is avoided; the disadvantage that the low-dimension chaos system is easy to be attacked can be effectively overcome, the security is higher, and the realization is easy.
Owner:NORTHEASTERN UNIV
Safe payment system and method based on finger vein recognition and blockchain technology
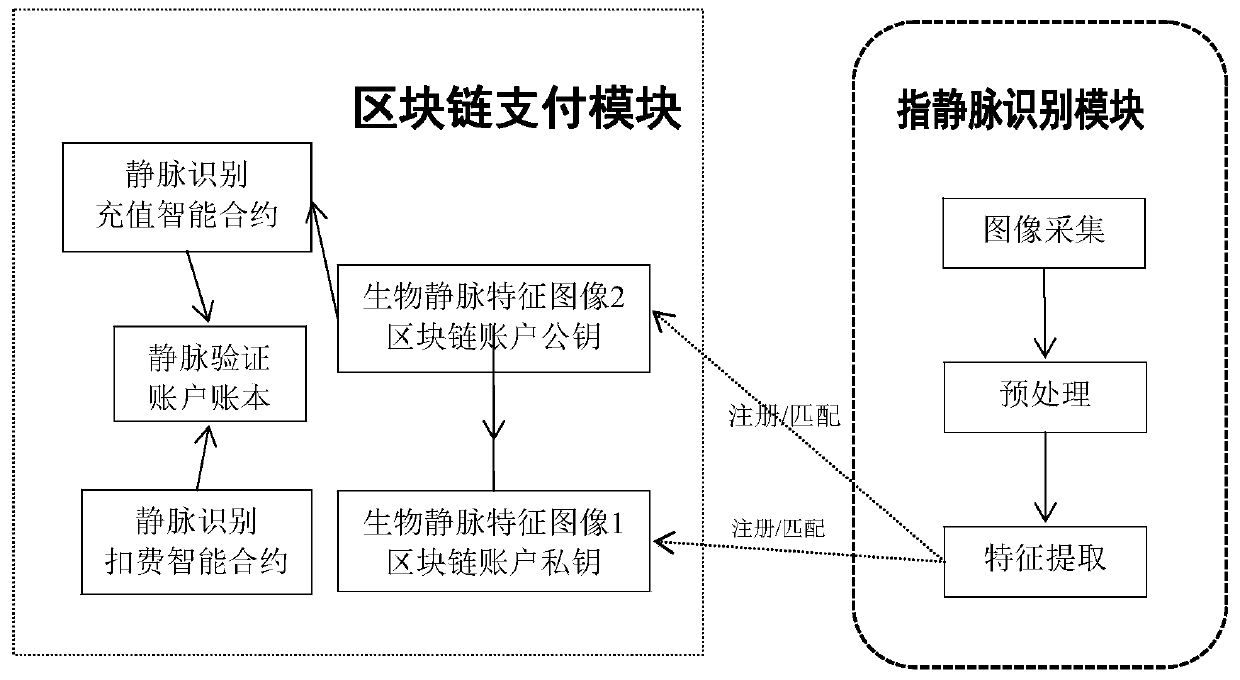
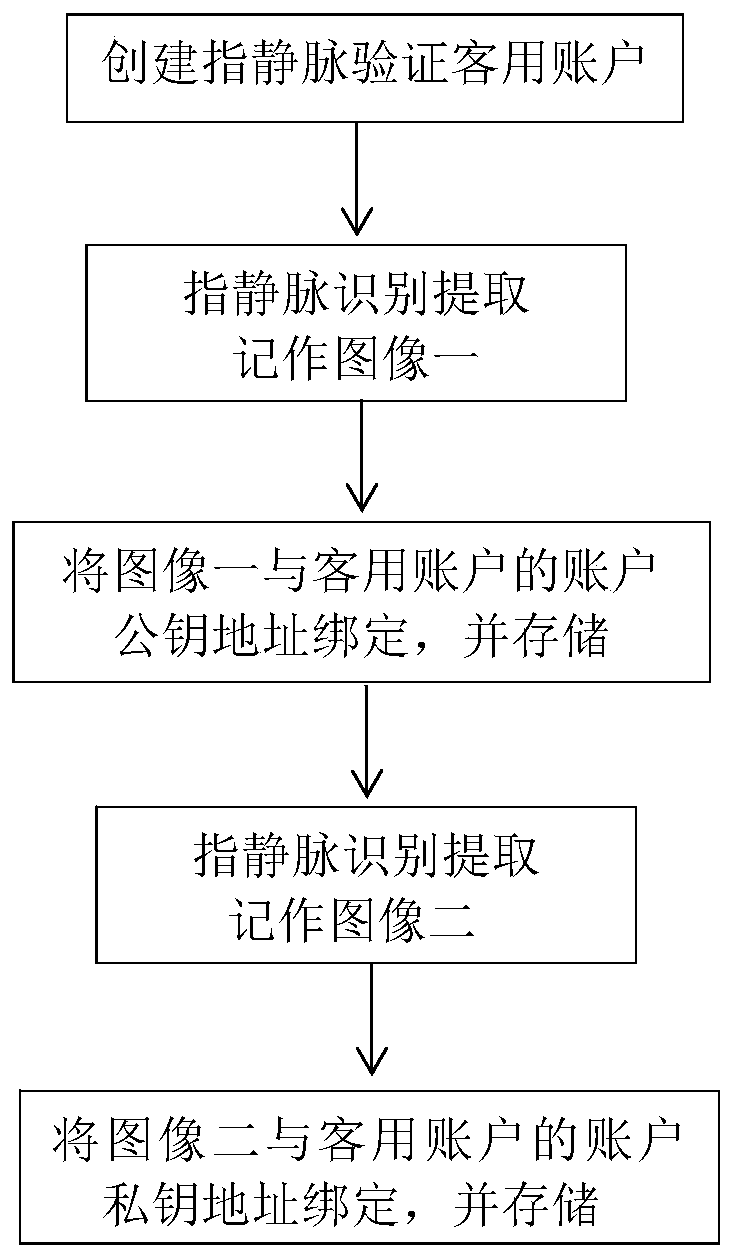
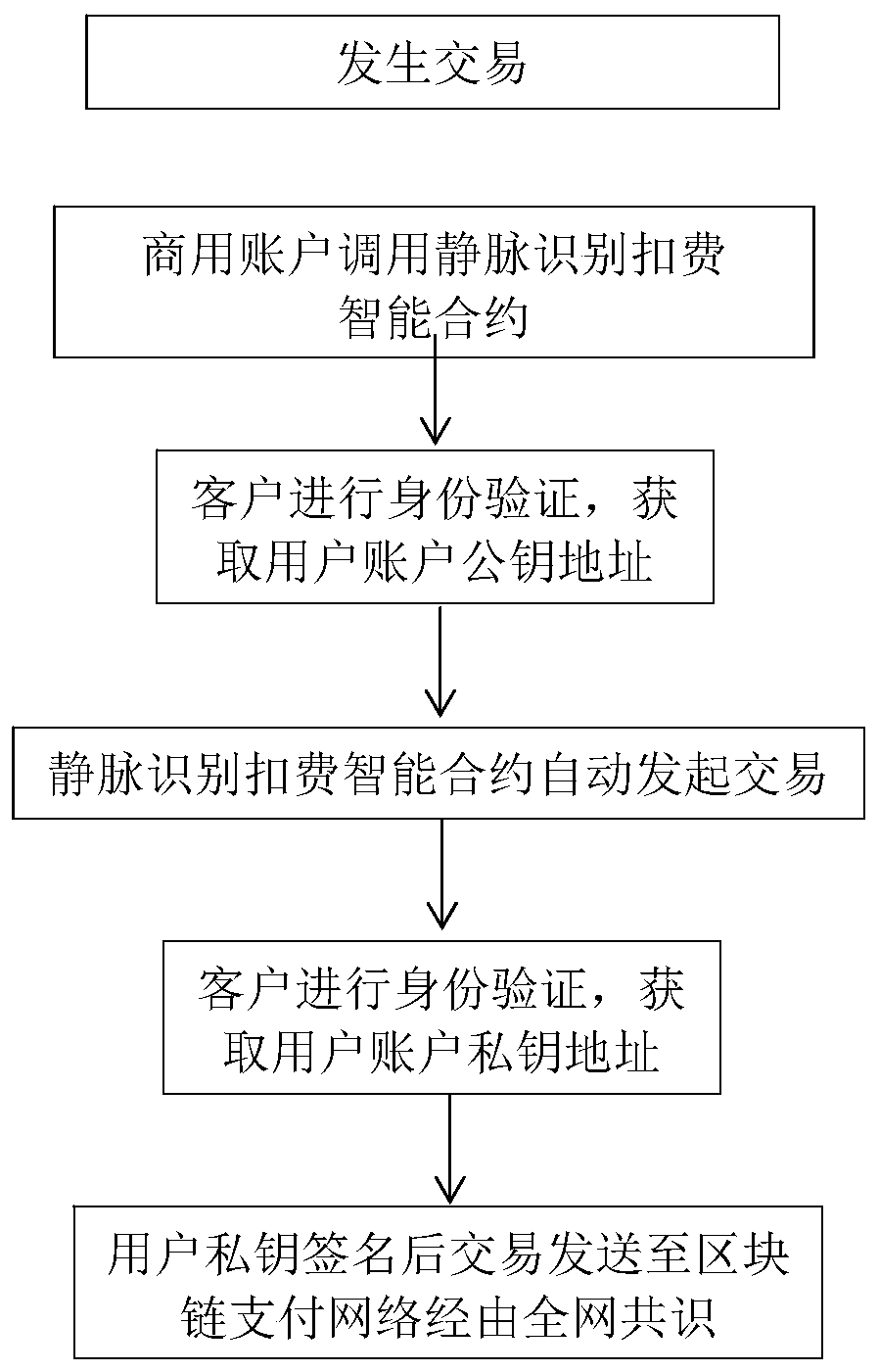
ActiveCN110992053ASolve the problem that the transaction cannot be completed normallyAvoid the risk of being stolenFinanceProtocol authorisationComputer hardwareFinger vein recognition
The invention discloses a safe payment system based on finger vein recognition and blockchain technology. The safe payment system comprises a finger vein recognition module and a regional chain payment module, the finger vein recognition module is used for performing finger vein image acquisition, preprocessing and feature extraction on a finger when a user is verified; the regional chain paymentmodule comprises a finger vein verification account and a finger vein recognition intelligent contract; the invention also discloses a safe payment method based on the finger vein recognition and blockchain technology. The method comprises the following steps: 1) constructing a blockchain payment network; 2) performing finger vein recognition payment operation; and 3) performing finger vein recognition recharging operation. According to the method, the problem that trade cannot be normally completed when a traditional mobile device is in abnormal states such as shutdown and no signal is provided is solved, the risk that a payment password of the mobile terminal is possibly stolen is avoided, and the use convenience of a user and the safety of a payment network are improved.
Owner:国科火炼(杭州)数字科技有限公司
Non-contact card type fingerprint identification automobile sensor key chip
PendingCN110264604AKeep safe from being stolenEnsure safetyIndividual entry/exit registersEmbedded systemFingerprint
The invention discloses a non-contact card type fingerprint identification automobile sensor key chip which comprises a chip body. The chip body further comprises a battery, a micro processing chip, a circuit board, a wireless communication chip and a fingerprint chip. The battery output end is in electrical signal connection with the input end of the micro processing chip. According to the invention, the micro processing chip, the wireless communication chip and the fingerprint chip are arranged in the chip body, so that the chip body can send data information to the cloud when a user passes; when information is acquired through the operation of the cloud, the user identity is identified, and the user and the user's vehicle can be paired; after the pairing is successful, the vehicle can be unlocked; and when the user's key is stolen or the user identity information is stolen, the vehicle matching the user cannot be opened, which effectively ensures the safety of the user's vehicle, avoids the risk of being stolen, and effectively makes up for the prior art.
Owner:东莞精旺电子有限公司
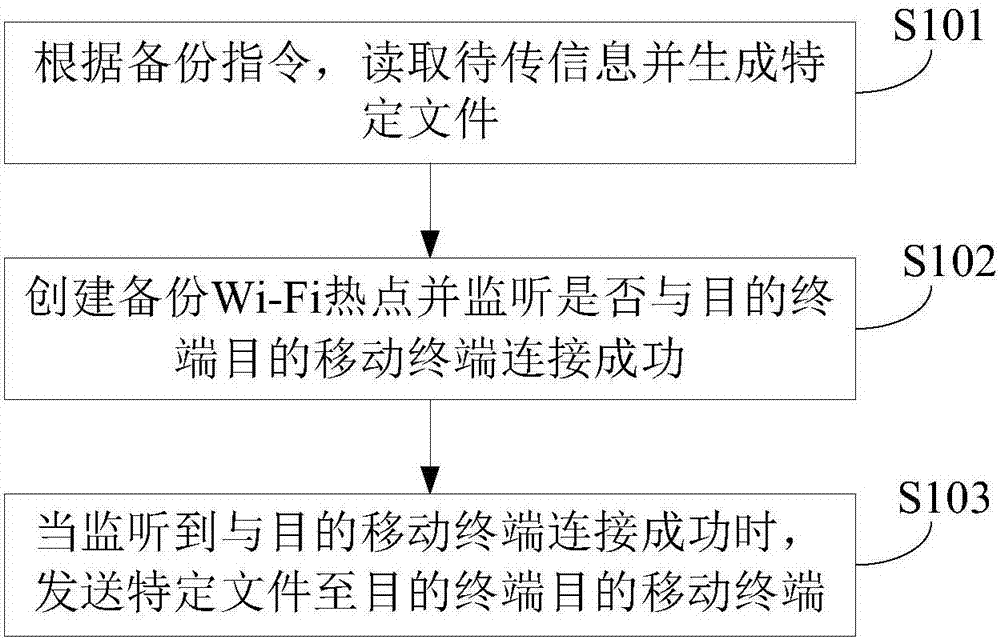
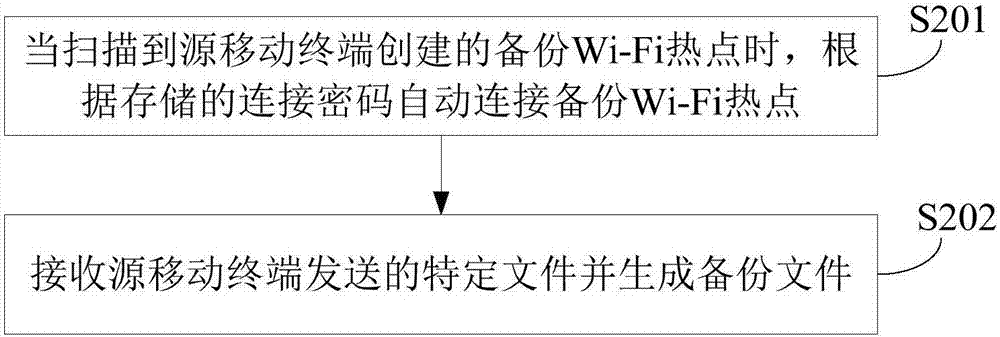
Mobile terminal data backup method and device
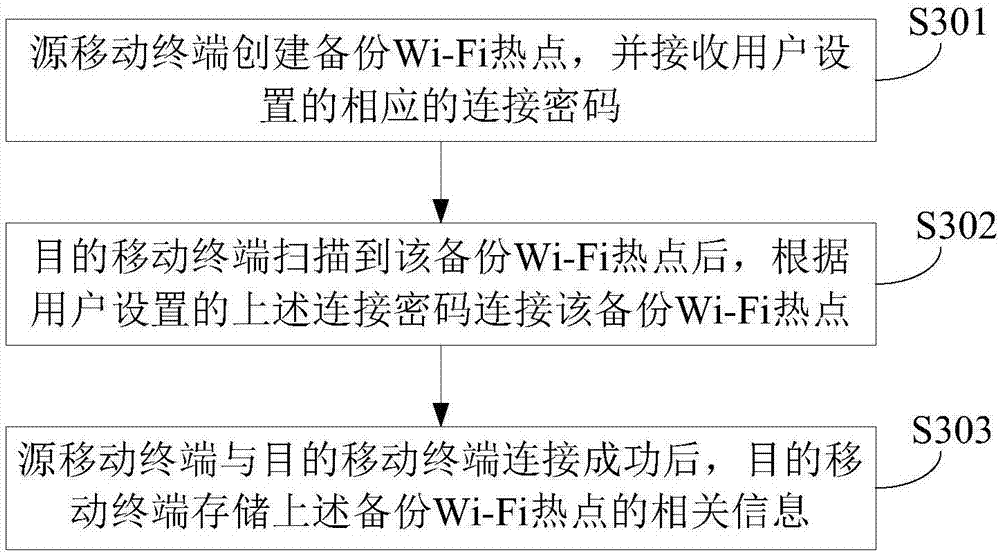
InactiveCN107291578AImprove securityAvoid the risk of being stolenAssess restrictionConnection managementWi-FiComputer terminal
The invention provides a mobile terminal data backup method and device, and relates to the technical field of mobile communication. The mobile terminal data backup method is applied to a source mobile terminal and includes the steps: reading information to be transmitted to generate a specific file according to a data backup instruction; building a backup Wi-Fi (wireless fidelity) hotspot and monitoring whether the Wi-Fi hotspot is successfully connected with a target mobile terminal or not; transmitting the specific file to the target mobile terminal when successful connection of the Wi-Fi hotspot and the target mobile terminal is monitored. The information to be transmitted includes complete information or modified information, the modified information comprises modified data generated between previous backup and current backup, the specific file includes a complete file when the information to be transmitted includes the complete information, and the specific file includes a modified file when the information to be transmitted includes the modified information. According to the mobile terminal data backup method and device, personal privacy stealing risks can be effectively avoided, and security of backup storage is improved.
Owner:SHANGHAI WINGTECH ELECTRONICS TECH
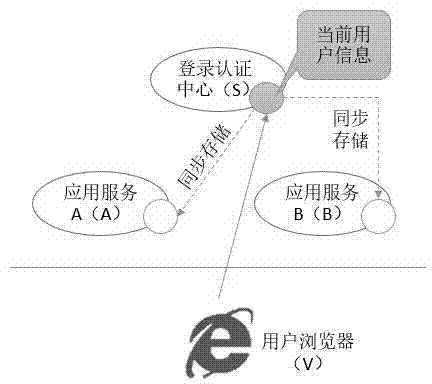
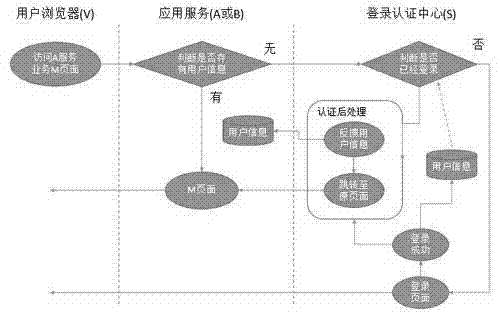
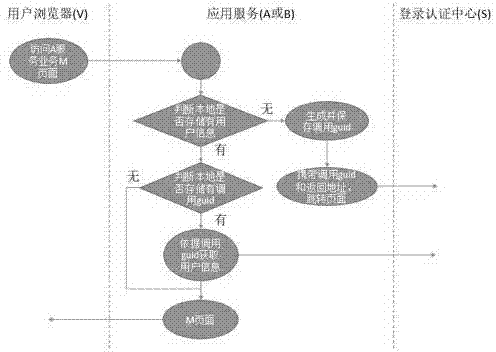
Client zero-storage single sign-on method
InactiveCN104506555ASimplify the development processImprove securityTransmissionSystem safetyAuthorization
The invention discloses a client zero-storage single sign-on method. The method is that sign-on pages of all application systems are provided by a sign-on authorization center; the information of user signing on the system is stored by the sign-on authorization center and synchronized to a server of each application system at the same time, so that the user information and session ID (or bills) are not stored in the client. By adopting the client zero-storage single sign-on method, the user information can be stored, transmitted and synchronized in the sign-on authorization center and application service, thus that unnecessary information is transmitted to other sides from the client can be avoided, and moreover, the risk that the session ID (or bill) is embezzled can be prevented; the development process of a single sign-on application system is simplified, and the safety performance of the system is improved.
Owner:北京艾力泰尔信息技术股份有限公司
Method and system for realizing safety payment
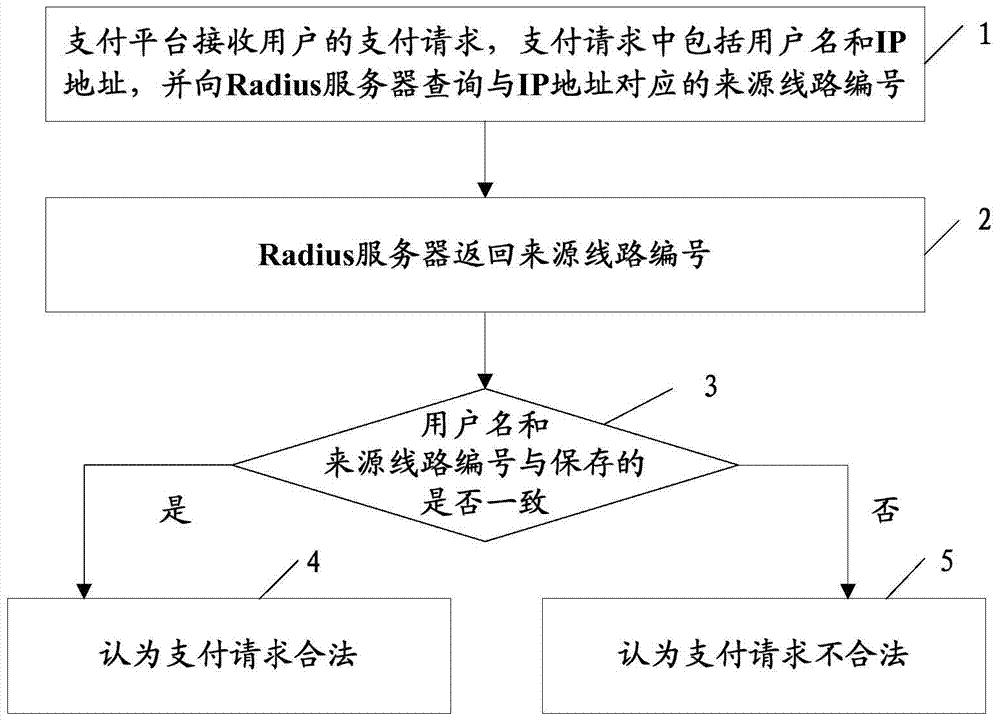
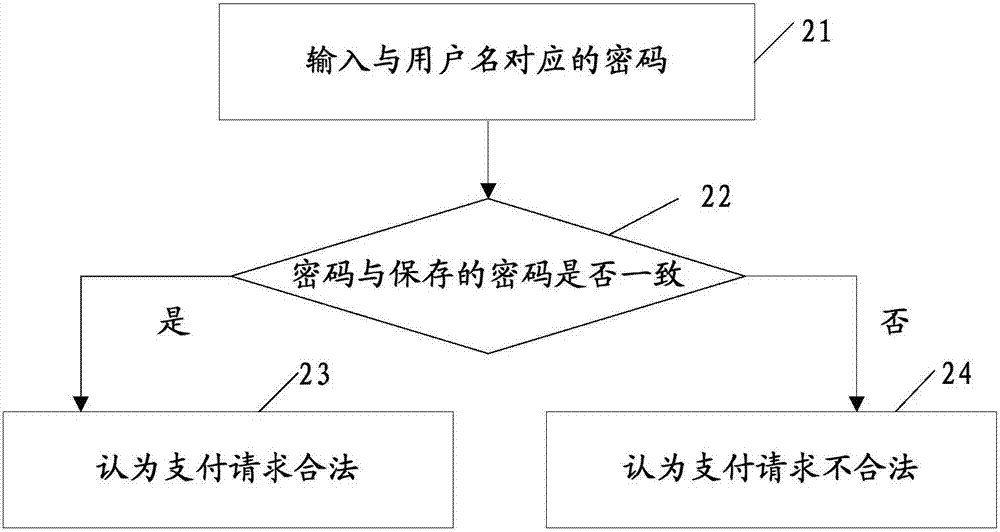
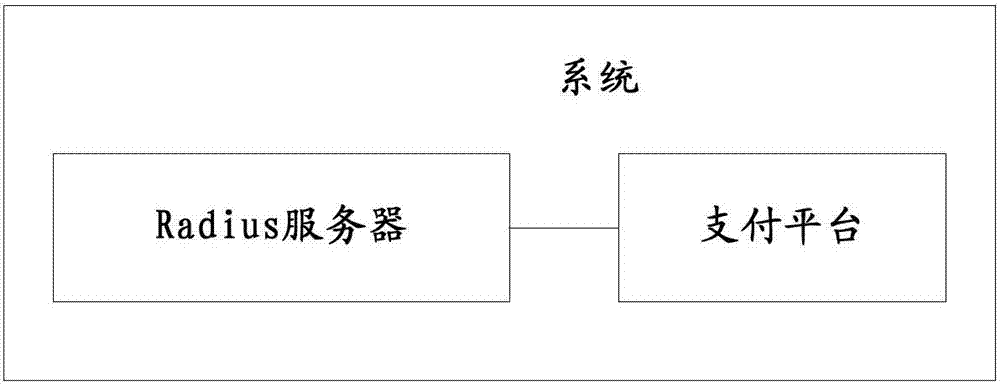
InactiveCN104519015AAvoid the risk of being stolenMeet the need to simplify configuration deployment workPayment protocolsTransmissionPaymentIp address
The invention discloses a method and a system for realizing safety payment. The method comprises: a payment platform receiving a payment request of a user, the payment request including a username and an IP address, and inquiring a source line number corresponding to the IP address in a Radius server; the Radius server returning the source line number; the payment platform storing the corresponding relations of the username and the source line number, and determining whether the received username and the obtained source line number are consistent with the stored corresponding relations, if yes, regarding as legal. The method and the system can realize a safe and convenient payment process.
Owner:CHINA TELECOM CORP LTD
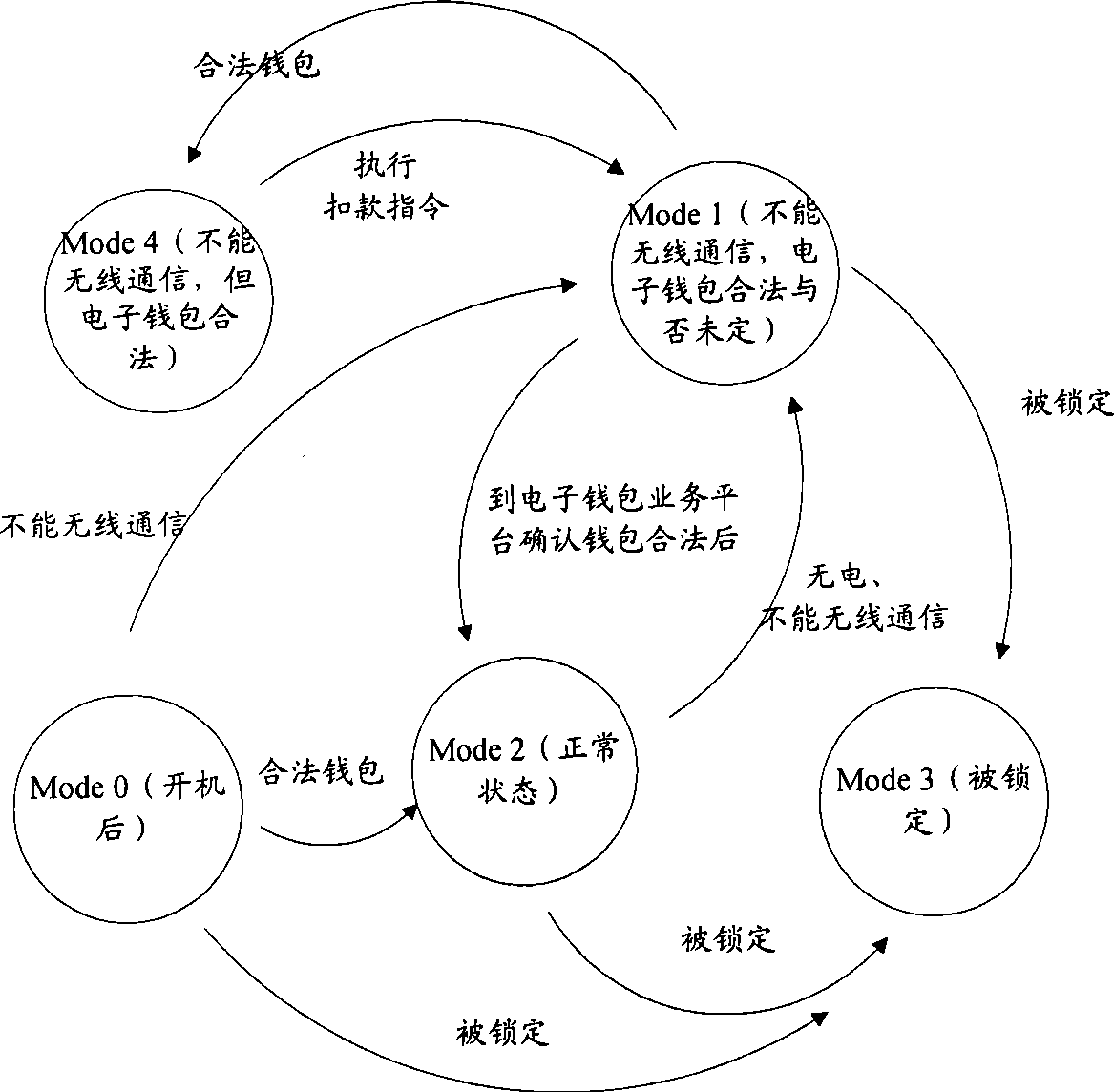
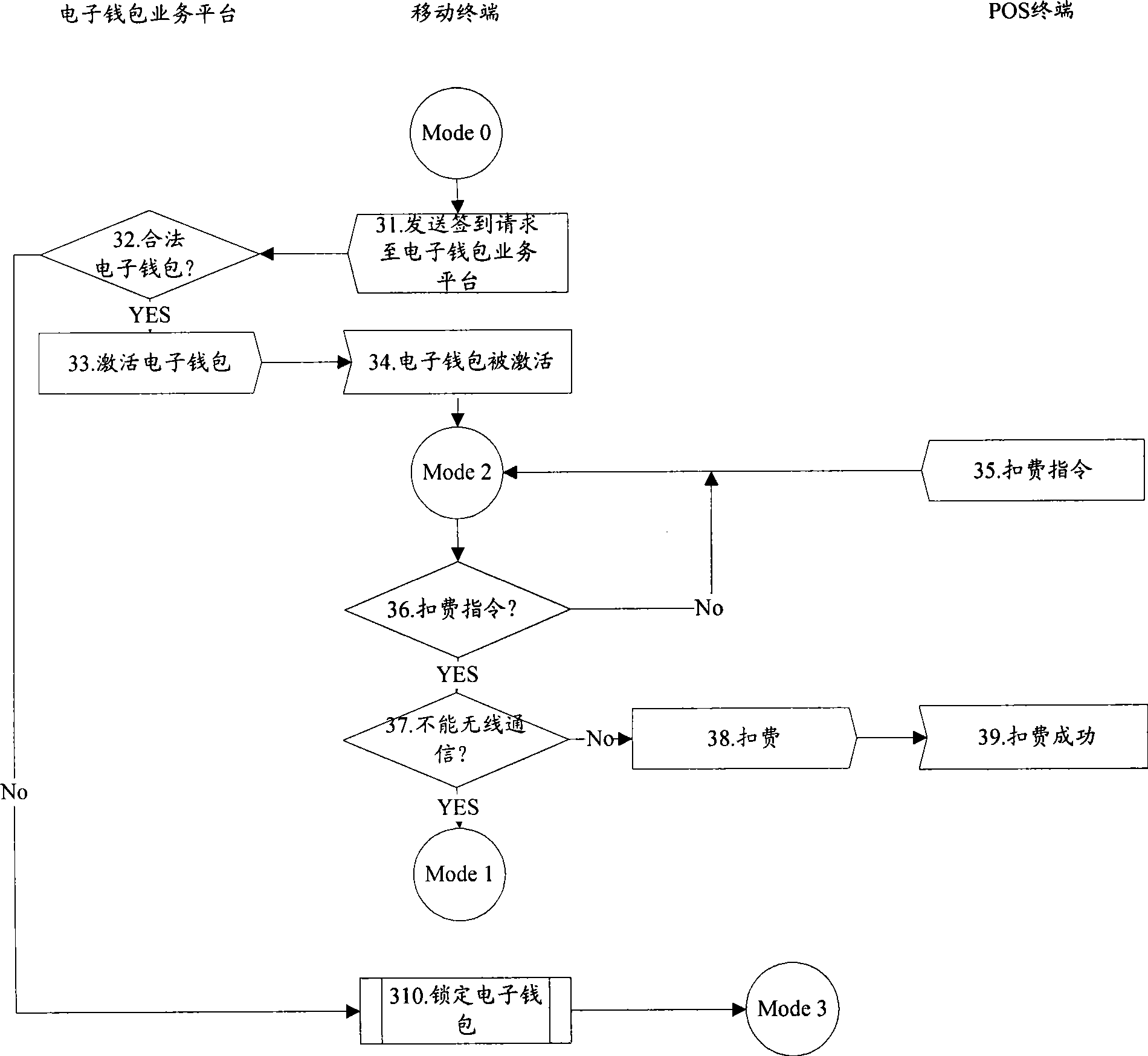
Fee deducting method, device and system for electronic purse
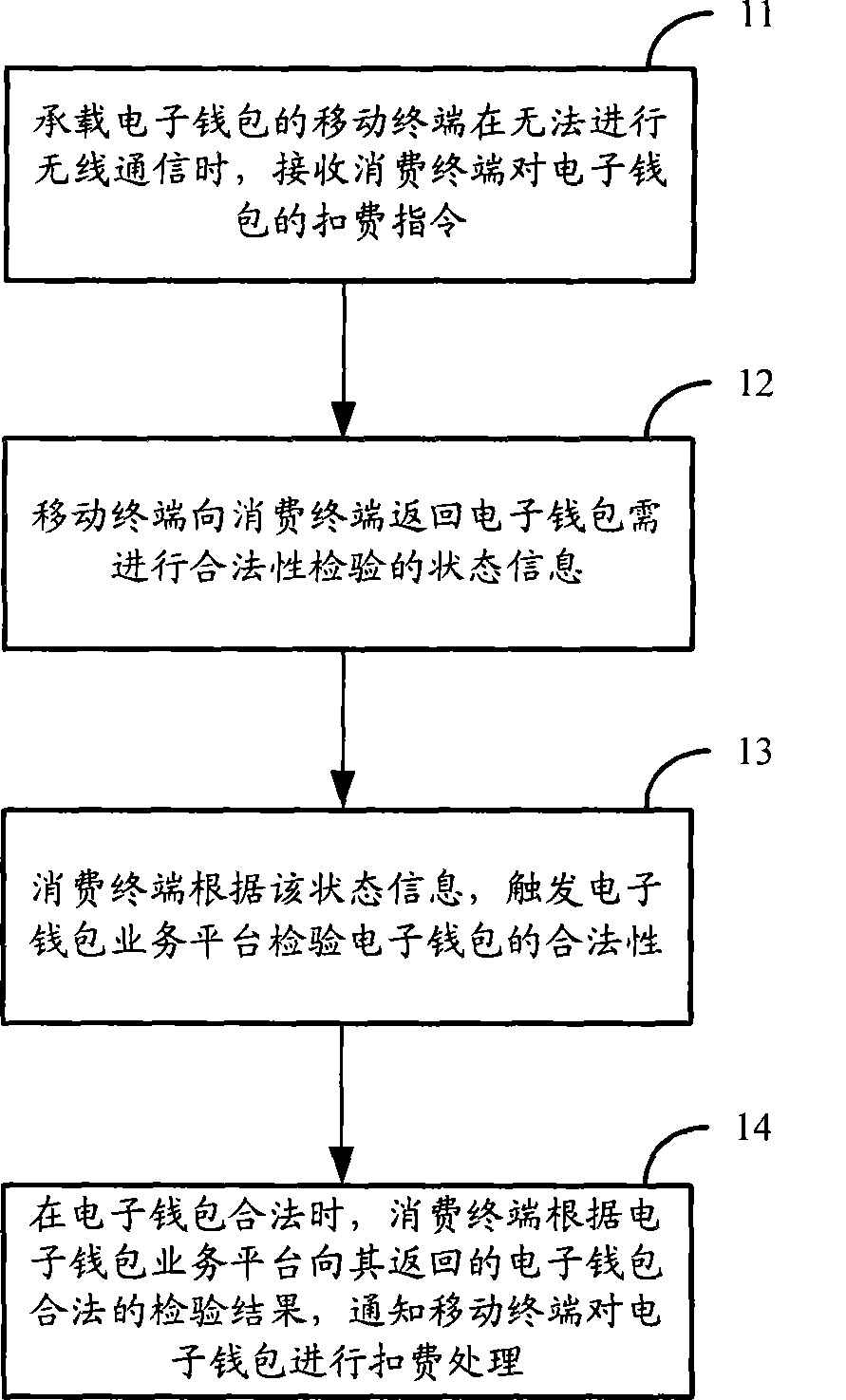
ActiveCN101504783AImprove convenienceAvoid the risk of being stolenPayment architectureCoded identity card or credit card actuationSafety management systemsComputer terminal
The invention discloses a fee deduction method for an E-wallet. The method comprises that: a mobile terminal for bearing the E-wallet receives a fee deduction instruction of the E-wallet given by a consumer terminal when wireless communication cannot be performed; the mobile terminal returns state information for the requirement of validity verification of the E-wallet to the consumer terminal; the consumer terminal triggers an E-wallet service platform to verify the validity of the E-wallet according to the state information; and the consumer terminal notifies the mobile terminal of performing fee deduction on the E-wallet according to the verification result which is returned by the E-wallet service platform to the consumer terminal and proves the validity of the E-wallet when the E-wallet is valid. The invention simultaneously discloses the mobile terminal for bearing the E-wallet, the consumer terminal and a safety management system of the E-wallet. The invention can improve the convenience and the safety of the use of the E-wallet through the mobile terminal.
Owner:CHINA MOBILE COMM GRP CO LTD
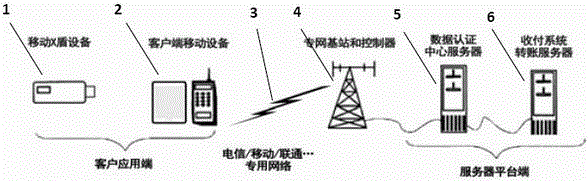
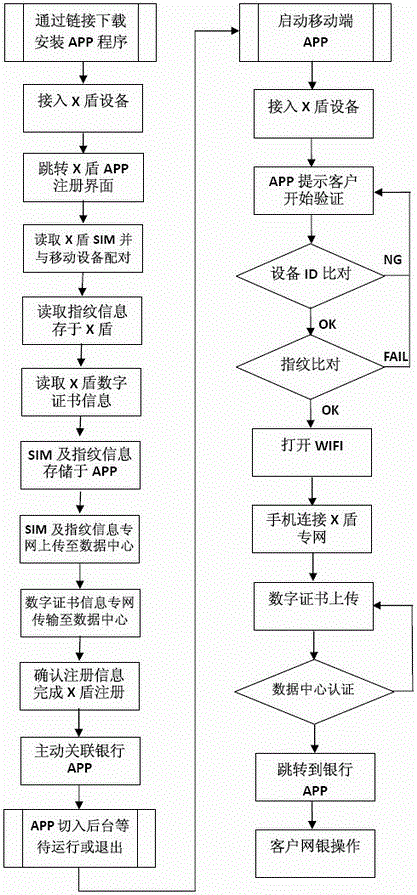
Mobile security settlement network construction system and use method thereof
InactiveCN106651374AAvoid the risk of being stolenOperational securityTransmissionProtocol authorisationPaymentPrivate network
The invention relates to a mobile security settlement network construction system. The mobile security settlement network construction system consists of an embedded system comprising an intermediate key, namely, an X shield, a mobile X shield device, a client mobile device, a mobile private network, private network base station and controller, a data authentication center platform server and a receipt and payment settlement system operation platform server, and a mobile security settlement network is constructed. An X shield APP is installed in the client mobile device, bound with the client mobile device and associated with an APP of a receipt and payment settlement system; when a client performs receipt and payment settlement, the X shield APP is actively connected to the mobile private network of mobile security settlement, transmits private encrypted data and is intelligently connected with a back-end system server platform database; after an identity is confirmed to be correct through multiple comparison, a connection permission signal is released, so that the system can be securely connected with the private network, and secure system operation is ensured; and when the identity is abnormal through comparison, the system refuses a connection and gives an alarm signal to a client APP, so that the payment settlement is refused, and the private network connection is cut off.
Owner:SHANGHAI CHENGYE INTELLIGENT TECH CO LTD
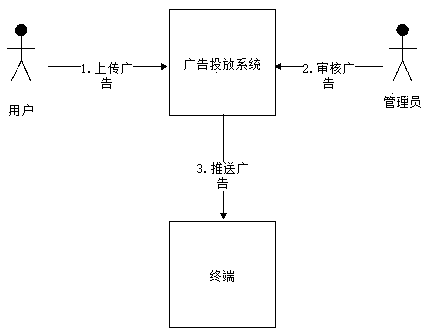
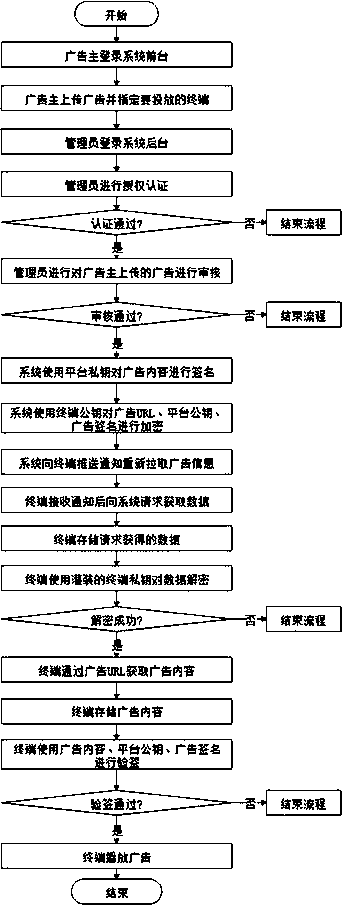
Advertisement putting system for guaranteeing safety of advertisement putting process
PendingCN110572454AAvoid the risk of being stolenNot be hijacked and tampered withUser identity/authority verificationTerminal equipmentUniform resource locator
The invention discloses an advertisement putting system capable of guaranteeing the safety of an advertisement putting process. A typical advertisement putting process in the advertisement putting system comprises the following steps that: 1) an advertiser uploads an advertisement to the system through the foreground of the advertisement putting system and designates terminal equipment of which the advertisement content is to be played; 2) the system administrator audits the advertisement content uploaded by the advertiser; 3) the system signs the audited advertisement by using a platform private key; 4) the system encrypts the platform public key, the advertisement signature and the advertisement URL by using the terminal public key; 5) the system pushes the encrypted content to terminalequipment to be played; 6) after receiving the push, the terminal decrypts the push by using the filled private key; 7) the terminal downloads the advertisement content to be played according to the advertisement URL; 8) the terminal performs signature verification on the advertisement; and 9) the terminal plays the advertisement passing the signature verification. Based on the system disclosed bythe invention, the security problems that an advertiser maliciously uploads bad advertisements, the operation security is audited, the advertisement content is tampered during network transmission, the advertisement content is tampered at the advertisement terminal and the like can be effectively solved.
Owner:SHENZHEN BAIYUN INFORMATION TECH CO LTD
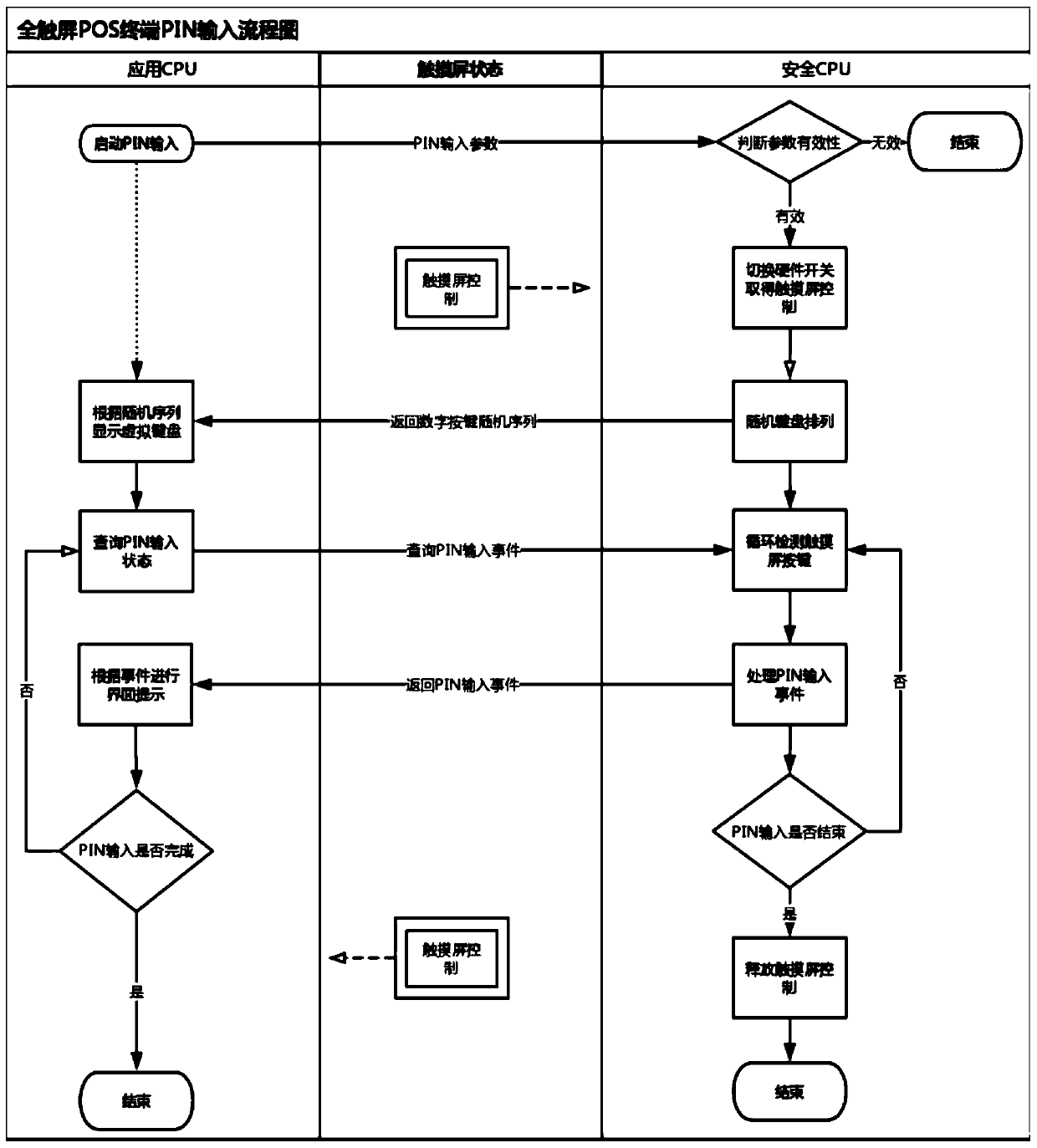
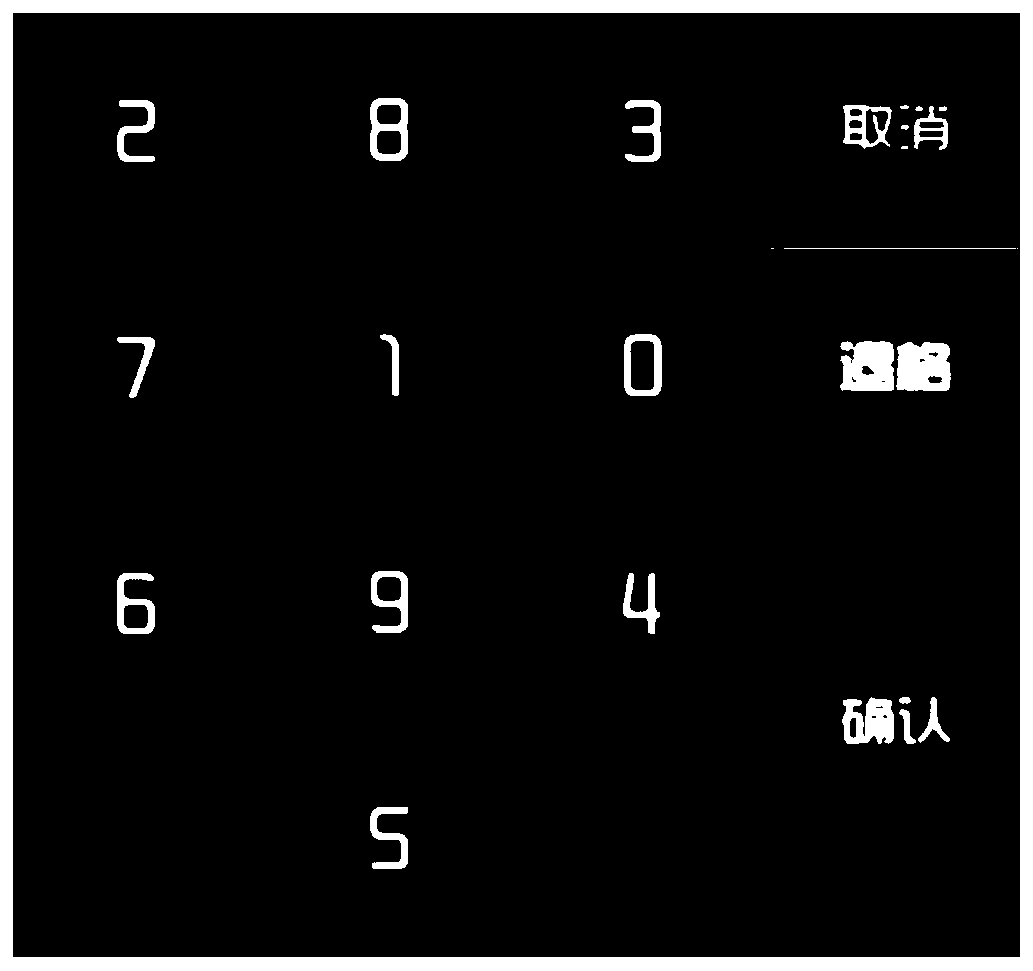
PIN safety input method of full-touch-screen POS terminal
PendingCN110992047AGuarantee the safety of fundsAvoid the risk of being stolenCash registersProtocol authorisationComputer hardwareControl signal
The invention belongs to the technical field of POS terminal security. The invention relates to a POS terminal, in particular to a PIN safety input method of a full-touch-screen POS terminal. The method specifically comprises the following steps that S1, after a terminal is started, an application CPU controls a touch screen in a default mode, and when an application program requires to execute PIN input, the application CPU informs a safety CPU and sends parameters related to PIN input to the safety CPU; s2, the safety CPU receives a PIN input request sent by the application CPU, and immediately switches the touch screen control signal from the application CPU to itself; S3, the safety CPU circularly detects and processes PIN input on the touch screen, and when PIN input is finished, a PIN secret key preinstalled by the safety CPU is used for encrypting the PIN, and then the ciphertext PIN is returned to the application CPU, and a touch screen control signal is switched to the application CPU; and S4, the application CPU packages the ciphertext PIN acquired from the security CPU into transaction data and then sends the transaction data to a transaction background, so that one financial transaction is completed.
Owner:FUJIAN NEWLAND PAYMENT TECH
Truck fuel tank based on fuel type recognition machine
InactiveCN111703297AAvoid the risk of being stolenReduce the risk of adding errorsUnderstructuresFuel supplyFuel tankFuel type
The invention discloses a truck fuel tank based on a fuel type recognition machine. The truck fuel tank comprises a placement block; a placement cavity is formed in the placement block; a recognitionmechanism is arranged in the placement cavity; the recognition mechanism comprises an auxiliary oil tank; an auxiliary oil tank cavity is formed in the auxiliary oil tank; a first sliding rail is fixedly arranged on the inner wall of the right side of the auxiliary oil tank cavity; a first sliding block is arranged on the first sliding rail in a sliding manner; a floating ball is fixedly arrangedat the left end of the first sliding block; and a first contact plate bracket is fixedly arranged on the upper end surface of the first sliding block. According to the truck fuel tank, the type of fuel added into the fuel tank can be recognized, only when correct fuel is added, a switch is turned on, the fuel enters the fuel tank, if the type of the fuel is added by mistake, the switch cannot be turned on, the risk that the type of the fuel is added by mistake can be reduced; and the risk that the fuel in the truck fuel tank is stolen can be effectively prevented through an automatically-opening-and-closing fuel cover.
Owner:广州欧享科技有限公司
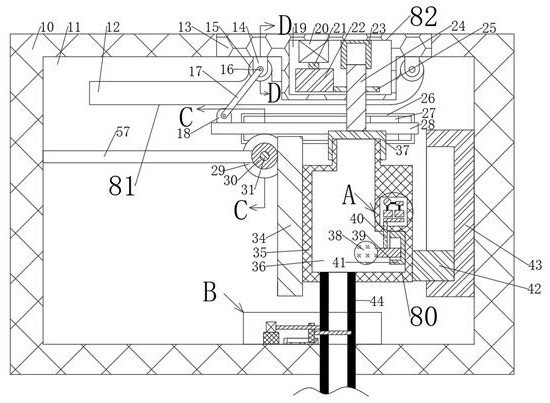
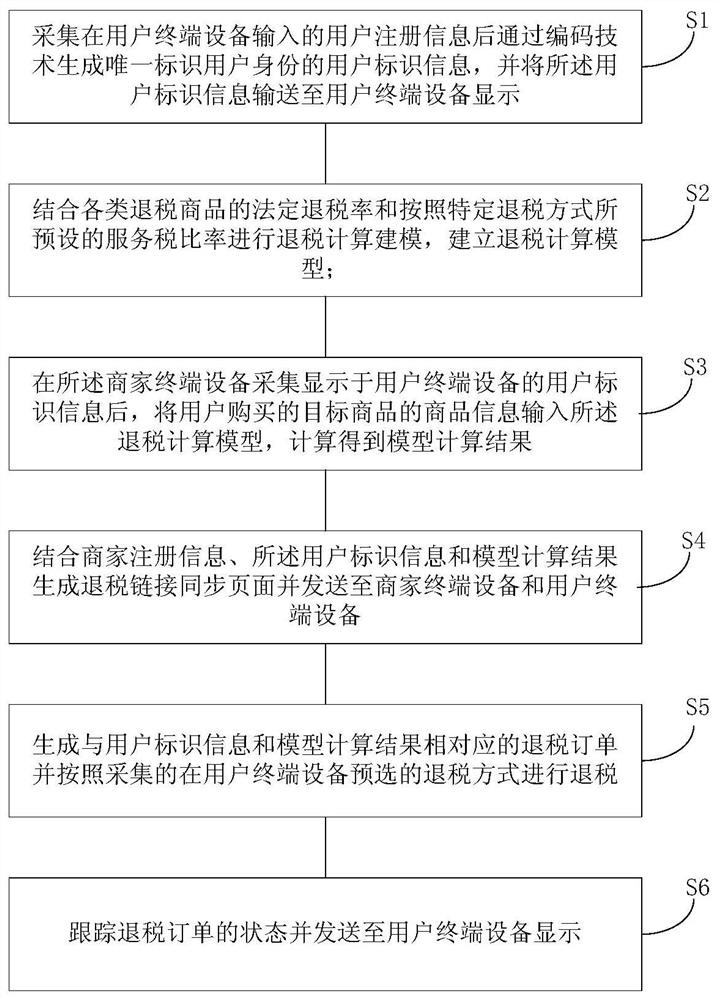
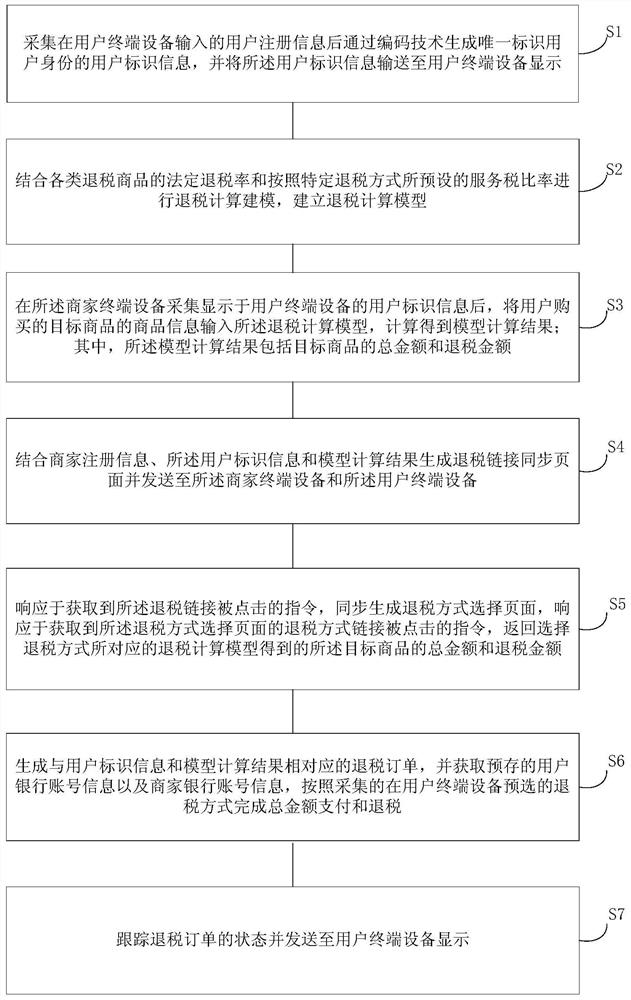
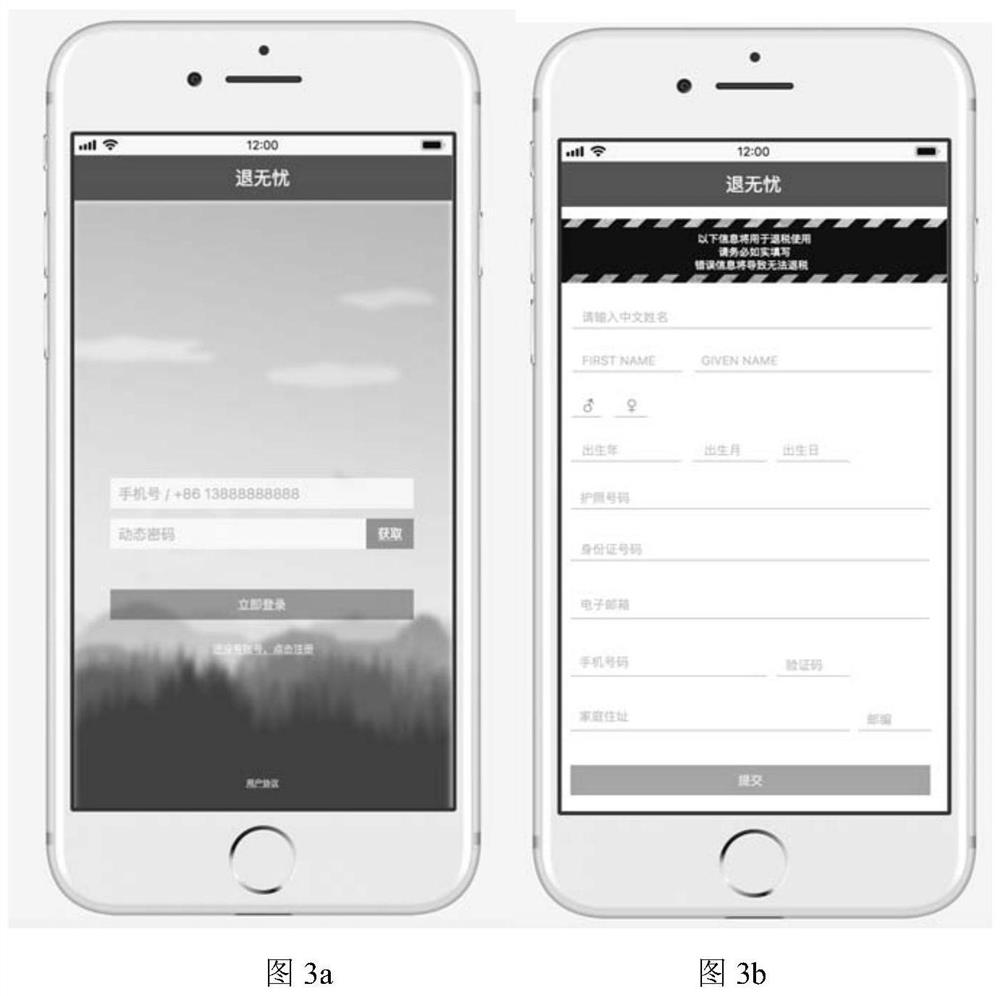
A tax refund method, tax refund platform and tax refund system
ActiveCN109146657BAvoid lostImprove experienceFinancePayment architectureTerminal equipmentFinancial transaction
The invention provides a tax refund method, a tax refund platform and a tax refund system. The tax refund method includes a user identification information generation step to generate user identification information and send it to a user terminal device for display; The preset service fee ratio of the tax refund method is used to model the tax refund calculation; after the merchant terminal device collects the user identification information, the product information of the target product is input into the tax refund calculation model, and the calculation result of the model is calculated; the synchronous information generation step generates a tax refund link synchronization page And send it to the merchant's terminal device and the user's terminal device; the tax refund order generation processing step generates a tax refund order corresponding to the user identification information and model calculation results, and performs tax refund according to the collected tax refund method pre-selected in the user's terminal device. The method is quick and easy, and the working efficiency is improved. All tax refund work is done online, which saves a lot of space rent and personnel costs.
Owner:曹宝妹
Access control method and control system
ActiveCN105447928BAvoid the risk of being stolenImprove securityIndividual entry/exit registersControl systemComputer terminal
The invention discloses an entrance guard control method and a control system thereof. The method comprises the following steps: acquiring connection requesting information of a mobile terminal, and judging whether a terminal marker carried by a connection requesting message is coupled with a pre-stored preset marker or not; determining the mobile terminal is an owner mobile terminal or an administrator mobile terminal if so; judging whether fingerprint data acquired by the mobile phone is coupled with preset fingerprint data corresponding the preset marker or not; and unlocking entrance guard if so. The method provided by the invention has high safety and great convenience, and realizes no staying of the fingerprint in a public area in order to avoid stole risk of the fingerprint.
Owner:QINGDAO HAIER INTELLIGENT HOME TECH CO LTD
Method, device, and computer-readable storage medium for loading web pages
ActiveCN107276991BAvoid the risk of being stolenImprove securityTransmissionSpecial data processing applicationsThe InternetEngineering
The invention discloses a method for loading a Web page. The method comprises the steps of: when at least one authorized pre-installed application accesses a Web page and after the user account information in an account management application is logged in an account server, enabling the at least one authorized pre-installed application to obtain encrypted user account information from the account management application; enabling the at least one authorized pre-installed application to decrypt the encrypted user account information, so that the decrypted user account information is obtained; enabling the at least one authorized pre-installed application to load the decrypted user account information; and enabling the at least one authorized pre-installed application to load the internet Web page through a WebView. The invention also discloses equipment for loading the Web page and a computer-readable storage medium. When the Web page is loaded in the pre-installed application through the WebView, the login state of the Web page is kept; and thus, the security of the user account information when the Web page is loaded is improved.
Owner:BEIJING GREATMAP TECH
A client login method, client and system
The embodiment of the invention discloses a method and system for logging in a client and a client. The method for logging in a client comprises: a logging-in verification request sent by a target client is received; according to the logging-in verification request, identity verification matching information of the target client is obtained; an associated logging-in verification request is submitted to a first server, so that the first server obtains logging-in verification information of the target client according to the associated logging-in verification request; the logging-in verification information, returned by the first server, of the target client is received; and the logging-in verification information of the target client is sent to the target client, so that the target client can log in a second server by using the logging-in verification information of the target client. According to the invention, rapid logging in of an application client can be realized and a risk of stealing logging-in verification information can be effectively eliminated, so that the logging-in security of the client can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com