Mobile security settlement network construction system and use method thereof
A security and network technology, applied in transmission systems, payment systems, electrical components, etc., can solve the problems of low security, difficult deployment, and easy to break the defense line, and achieve the effect of ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
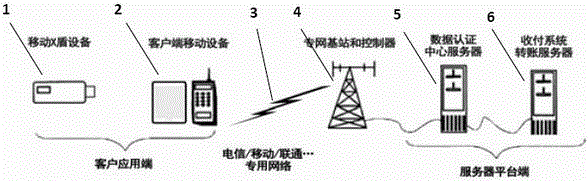
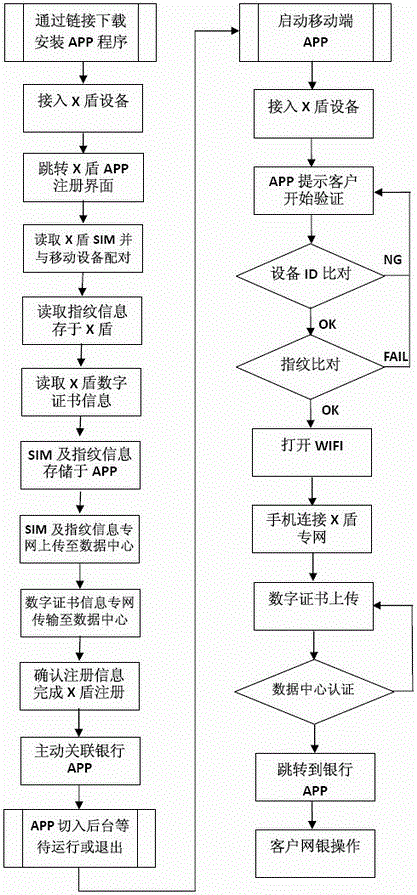
[0032] The invention provides a construction system of a mobile security settlement network, which is provided with an embedded system, and the embedded system is integrated with five modules, namely, a SIM card identification module, a WIFI module, a mobile communication module, a digital certificate module and a fingerprint identification module, and becomes The intermediate key is X-shield, which is an intelligent key system. Embedded systems have OTG or Lightning standard interfaces on the embedded motherboard.
[0033] The function of the digital encryption (digital certificate) module is to pair with the certificate of the designated address of the data authentication center to confirm the legitimacy of the certificate.
[0034] The function of the fingerprint identification module is: to scan the pre-stored fingerprint of the X-shield user in real time, compare it with the pre-stored fingerprint identification code of the APP and the data authentication center, and rece...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com