Multi-layer data mapping authentication system
An authentication system, multi-layer technology, applied in the field of identity authentication system, can solve the problem of reducing the probability of real identity code being stolen, stealing card friends, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
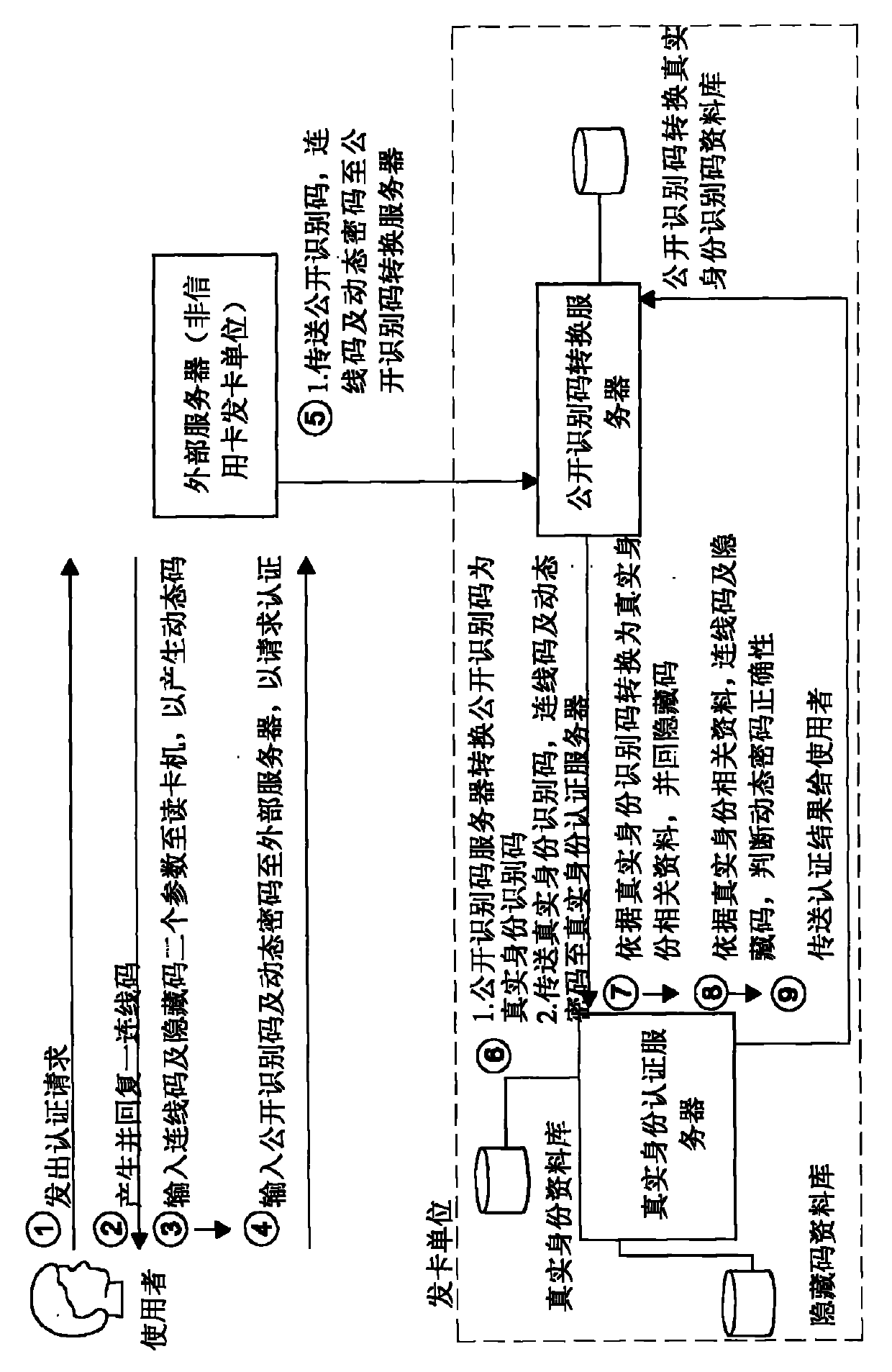
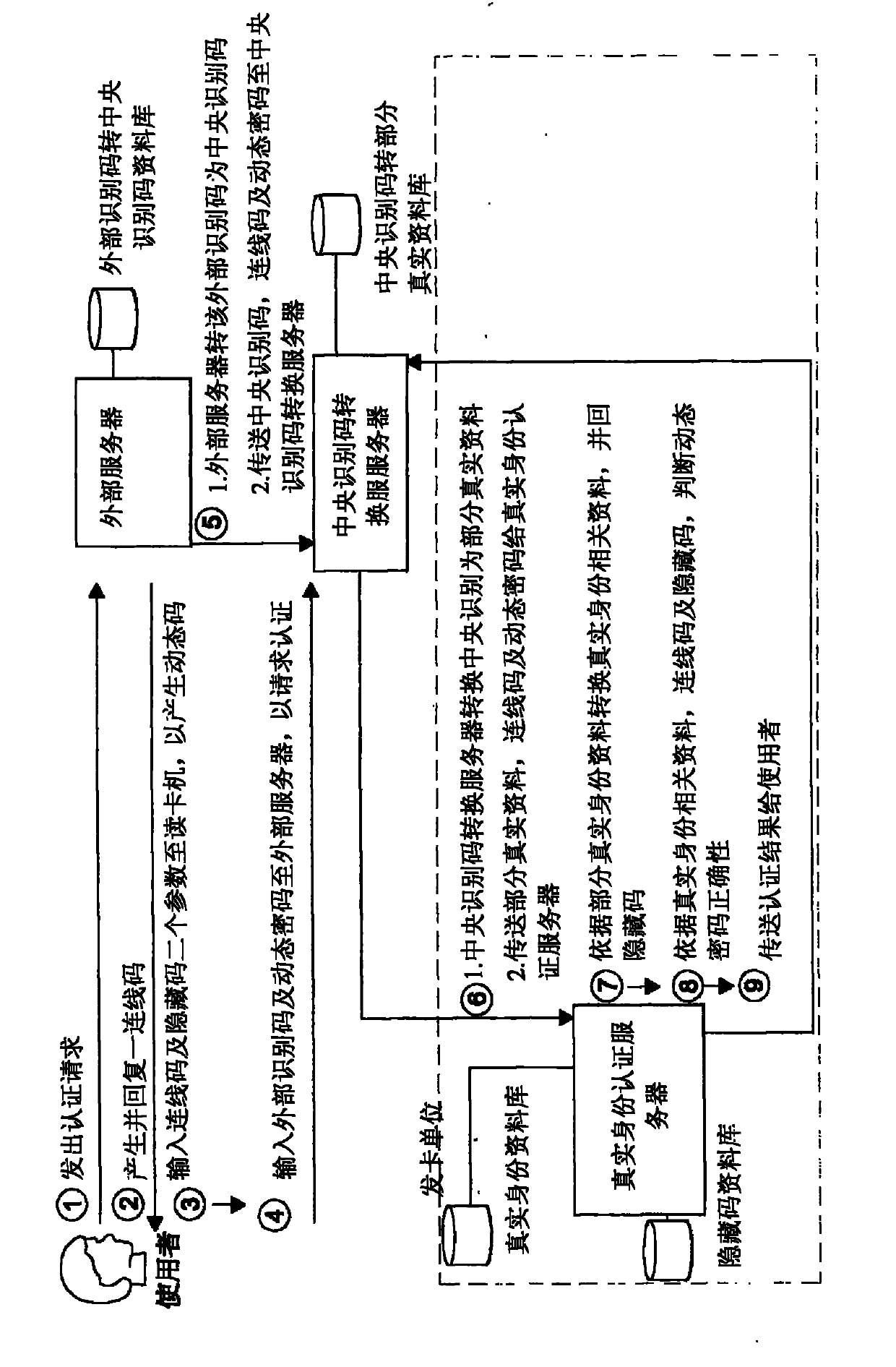
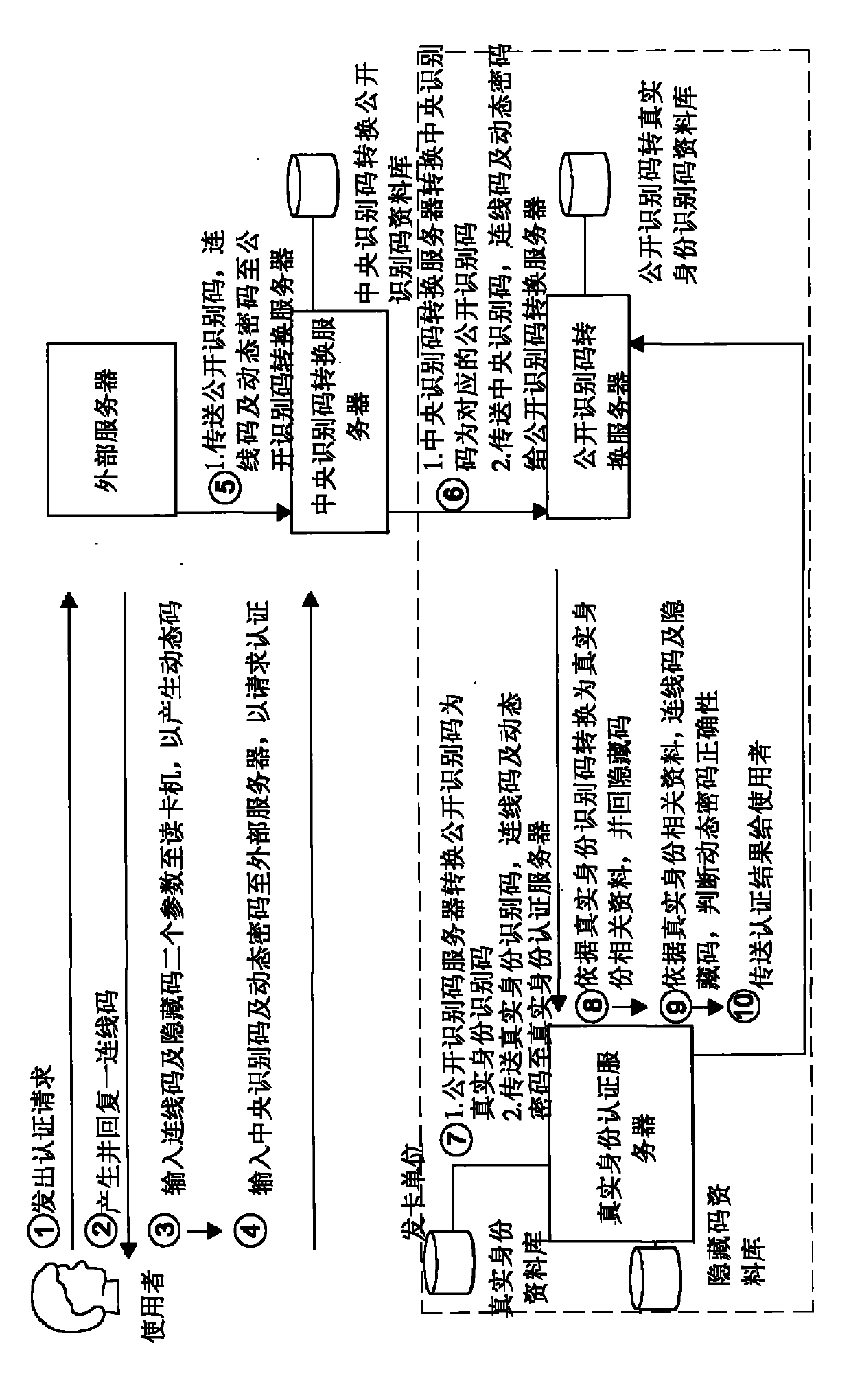
[0025] see figure 1 Shown is the first preferred embodiment of the multi-layer data mapping authentication system of the present invention, which includes a real identity authentication server, an intermediary data mapping server and a terminal data mapping server. Wherein the intermediary data mapping server is connected to the real identity authentication server and the terminal data mapping server.
[0026] The real identity authentication server is connected to the private network domain, and further includes at least one real identity database and a built-in third conversion program. In this embodiment, the real identity authentication server further includes a hidden code database for storing a plurality of hidden codes, and each hidden code corresponds to a unique real identity database.
[0027] In the first preferred embodiment, the intermediary data mapping server is connected to the real identity authentication server and has a built-in second conversion program. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com