Related method for encrypting and storing files in trusted execution environment based on encryption chip
An encryption chip and file encryption technology, applied in the field of mobile information security to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
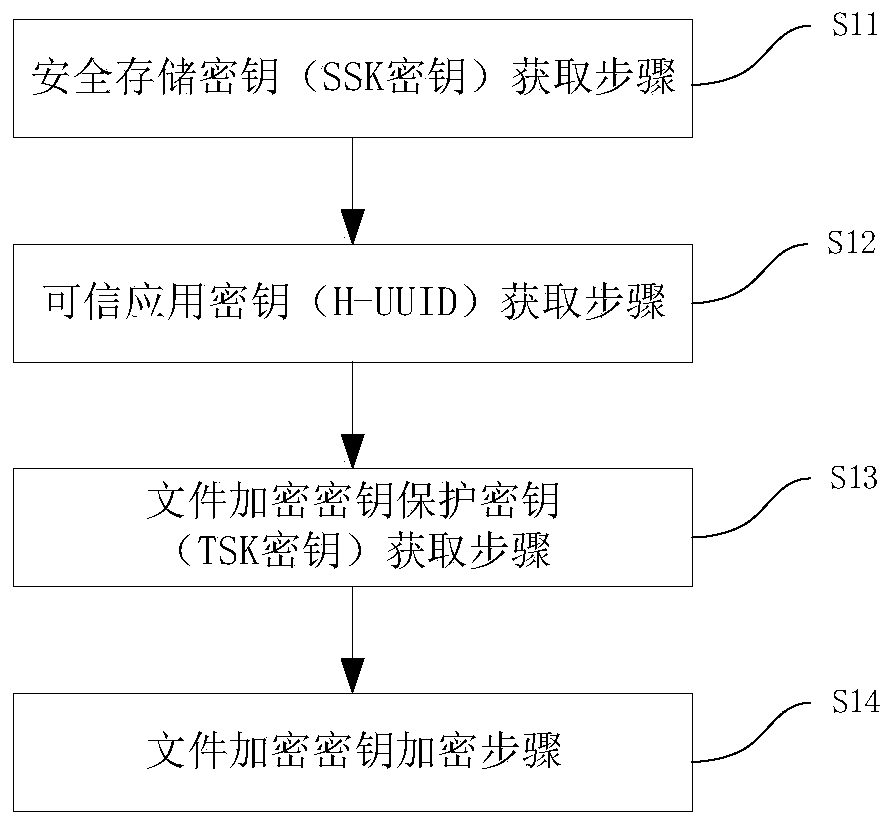
[0056] Embodiment 1 of the present invention provides a method for increasing the security of a file encryption key in a trusted execution environment based on an encryption chip. figure 1 An implementation flowchart of a method for increasing the security of a file encryption key in an encryption chip-based trusted execution environment provided by an embodiment of the present invention, as shown in figure 1 As shown, the method includes the following steps:
[0057] S11: Safe storage key (SSK key) acquisition step: refers to using the HUK key as the key through the first encryption algorithm to perform operations on the Message to generate the SSK key. The Message is composed of the main chip ID and the TEE String, wherein, The main chip ID is the serial number written into the chip after the main control chip of the terminal device leaves the factory. When the terminal system starts, it is obtained through the interface function of the TEE security environment and passed to...
Embodiment 2
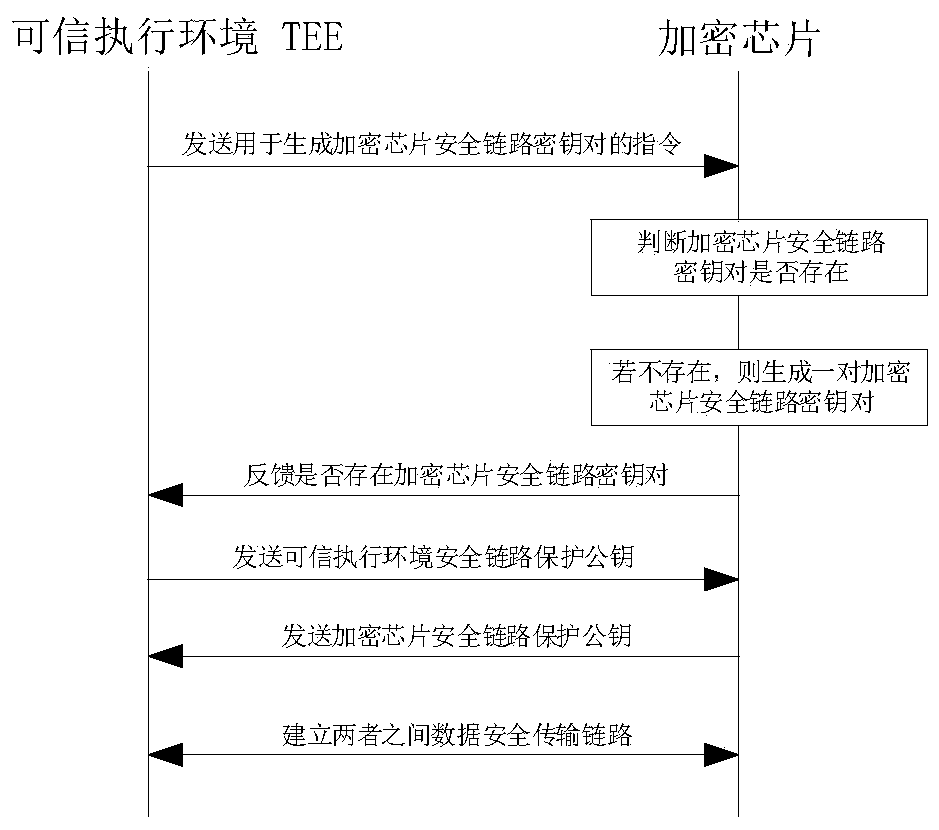
[0084] Embodiment 2 of the present invention provides a file encryption storage system in a trusted execution environment based on an encryption environment, such as Figure 5 As shown, it is a structural block diagram of a file encryption storage system under an encrypted environment-based trusted execution environment in Embodiment 2. It can be seen from the figure that this embodiment includes a TEE, an encryption chip, and a secure storage area.
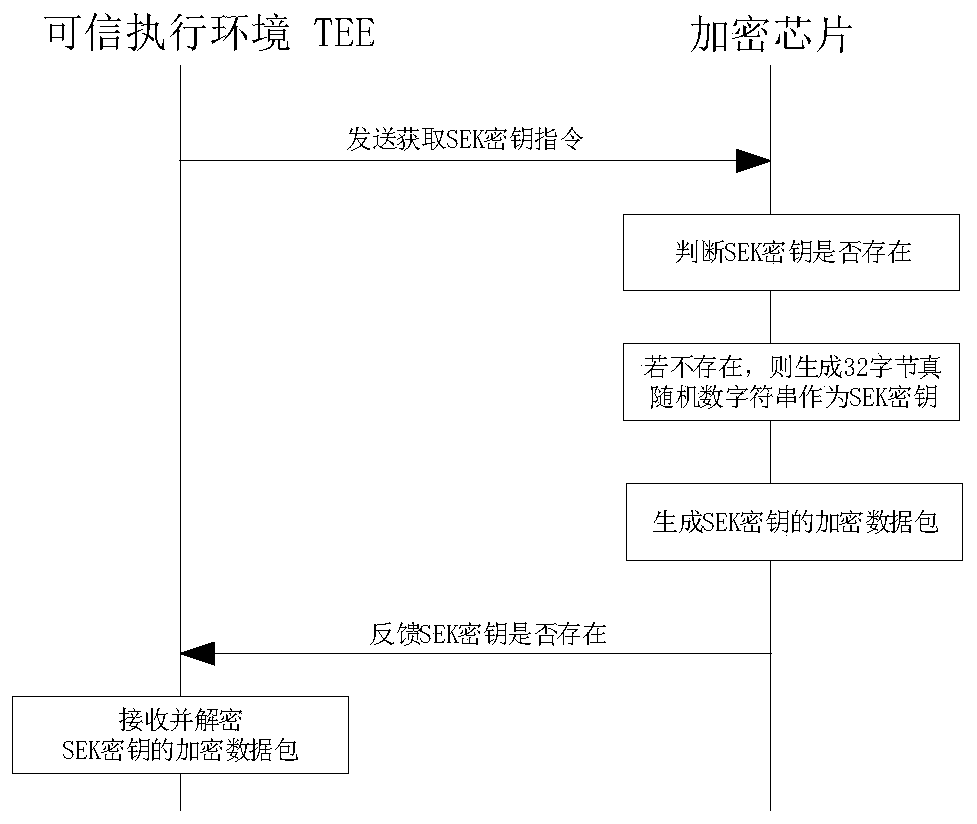
[0085] As described in Embodiment 1: the encryption chip is used to generate and store the SEK key, and key components include the SEK key, HUK key, TEE String, main chip ID, and UUID.
[0086] The TEE OS runs in the TEE, and includes an encryption and decryption module and files. The encryption and decryption module is implemented by TEE codes in the TEE environment, and is used to obtain key composition factors and increase the security of the file encryption key according to Embodiment 1. The method obtains the TSK key, and th...
Embodiment 3
[0091] Embodiment 3 of the present invention provides a file encryption storage structure in a trusted execution environment based on an encryption environment, such as Figure 6 As shown, it is a block diagram of file encryption storage structure composition in an encrypted environment-based trusted execution environment in Embodiment 3. The encrypted file in this embodiment is like the encrypted encrypted file in Embodiment 2. It can be seen from the figure that this implementation The encrypted file in the example includes file header, node attribute block and data segment.
[0092] The file header includes Encryption FEK, Meta IV, Tag1 and file node information ciphertext. Specifically, in the process of generating Encryption FEK in Embodiment 1, TEE OS will generate Meta IV as the encryption vector of Meta Data, and then according to the third encryption algorithm, Using Meta IV as the key vector, use the FEK key to encrypt Meta Data to generate Tag1 and file node informa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com