Security certificate method based on fingerprint, cryptographic technology and fragile digital watermark
A technology of digital watermarking and security authentication, applied in the field of security authentication, can solve the problems of illegal embezzlement of fingerprint cloning and the inability to determine the legal holder of KEY, and achieve the effect of increasing sensitivity and preventing the risk of embezzlement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
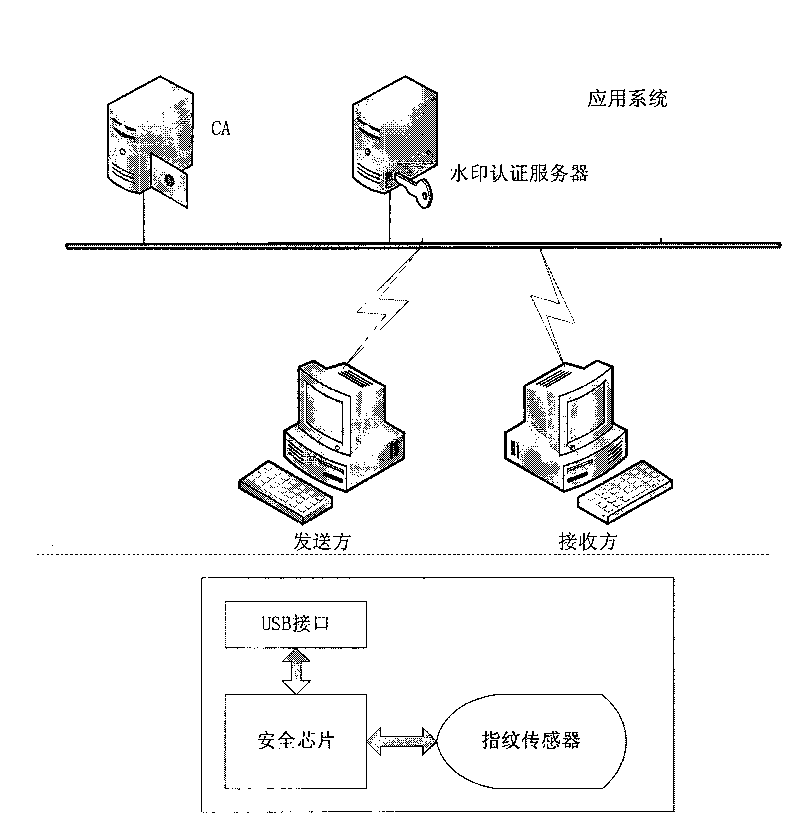
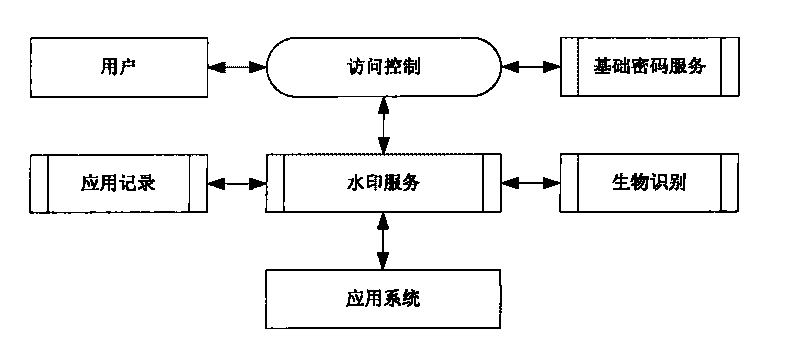
[0020] The present invention is based on the integer wavelet algorithm lossless digital watermark, uses the fingerprint image as the carrier, and at the same time binds the digital identity and the biological identity, embeds secret information or other information into the fingerprint image, and embeds the secret information or other information into the fingerprint image. Extraction and verification, effectively identify the authenticity of fingerprints, so as to confirm the authenticity of identity, effectively solve the defect that fingerprints can be cloned through computer systems, and effectively prevent the risk of fingerprints being stolen, so as to achieve true and unique identity Non-repudiation authentication goal.
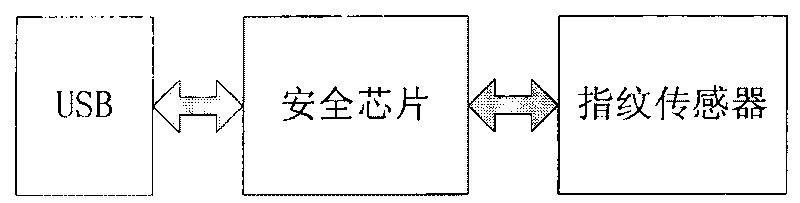
[0021] refer to figure 1 , the fingerprint USBKEY in the present invention adopts a domestic encryption chip, integrates watermark embedding, watermark extraction, fingerprint comparison, and basic cryptographic algorithms into the same chip, and is ex...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com