Patents
Literature
88results about How to "Prevent hacking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
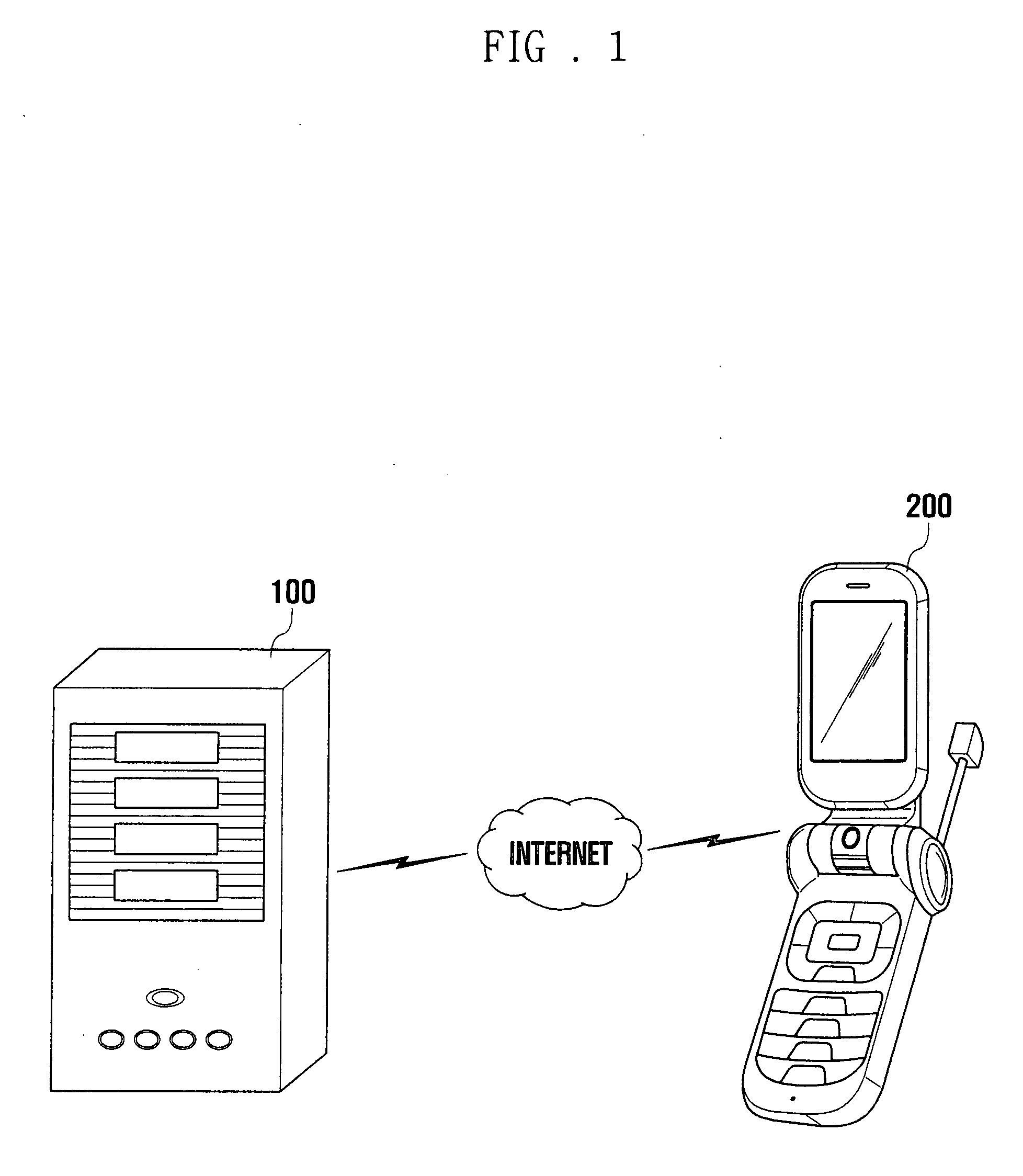
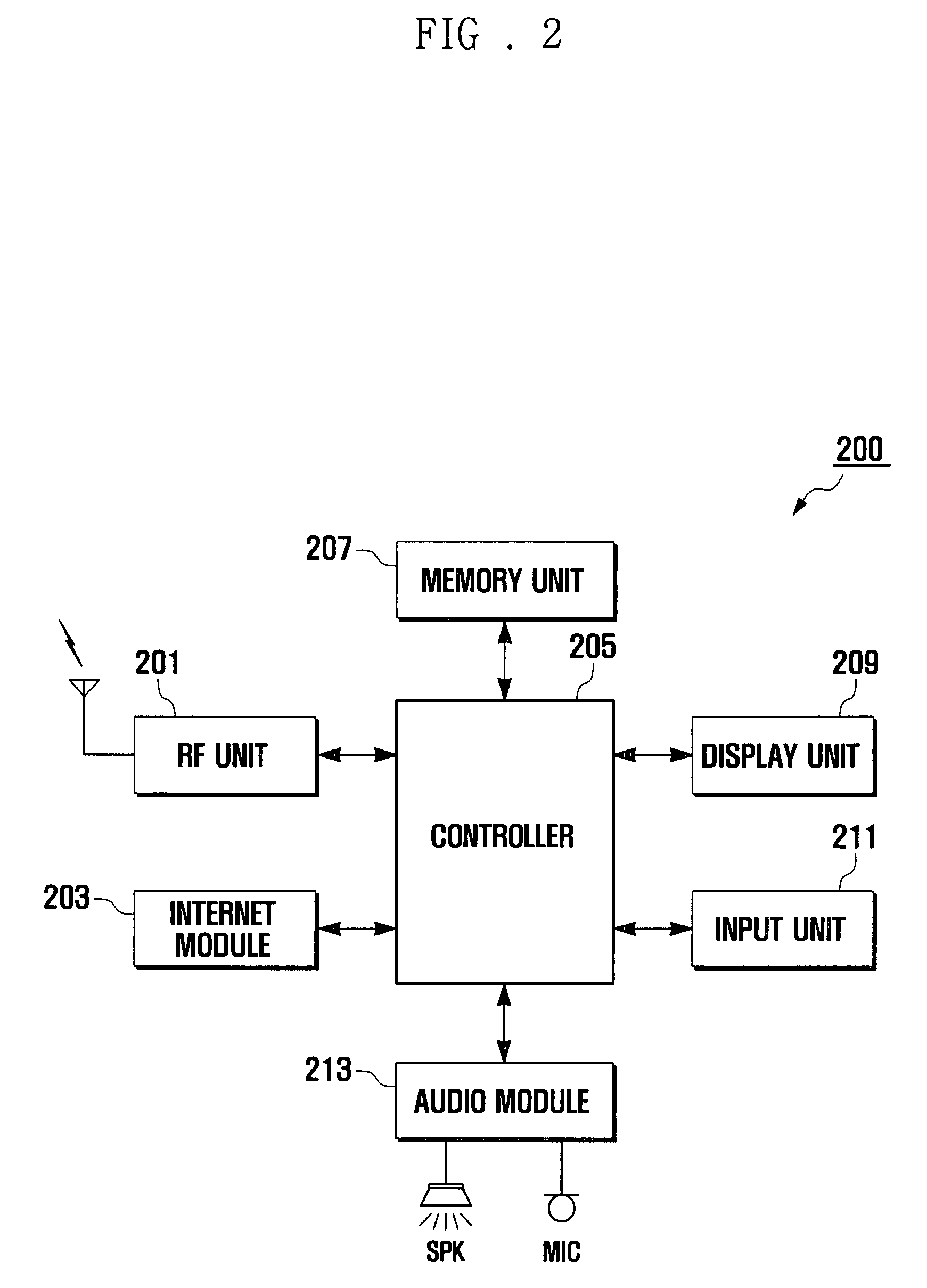
Preventive intrusion device and method for mobile devices
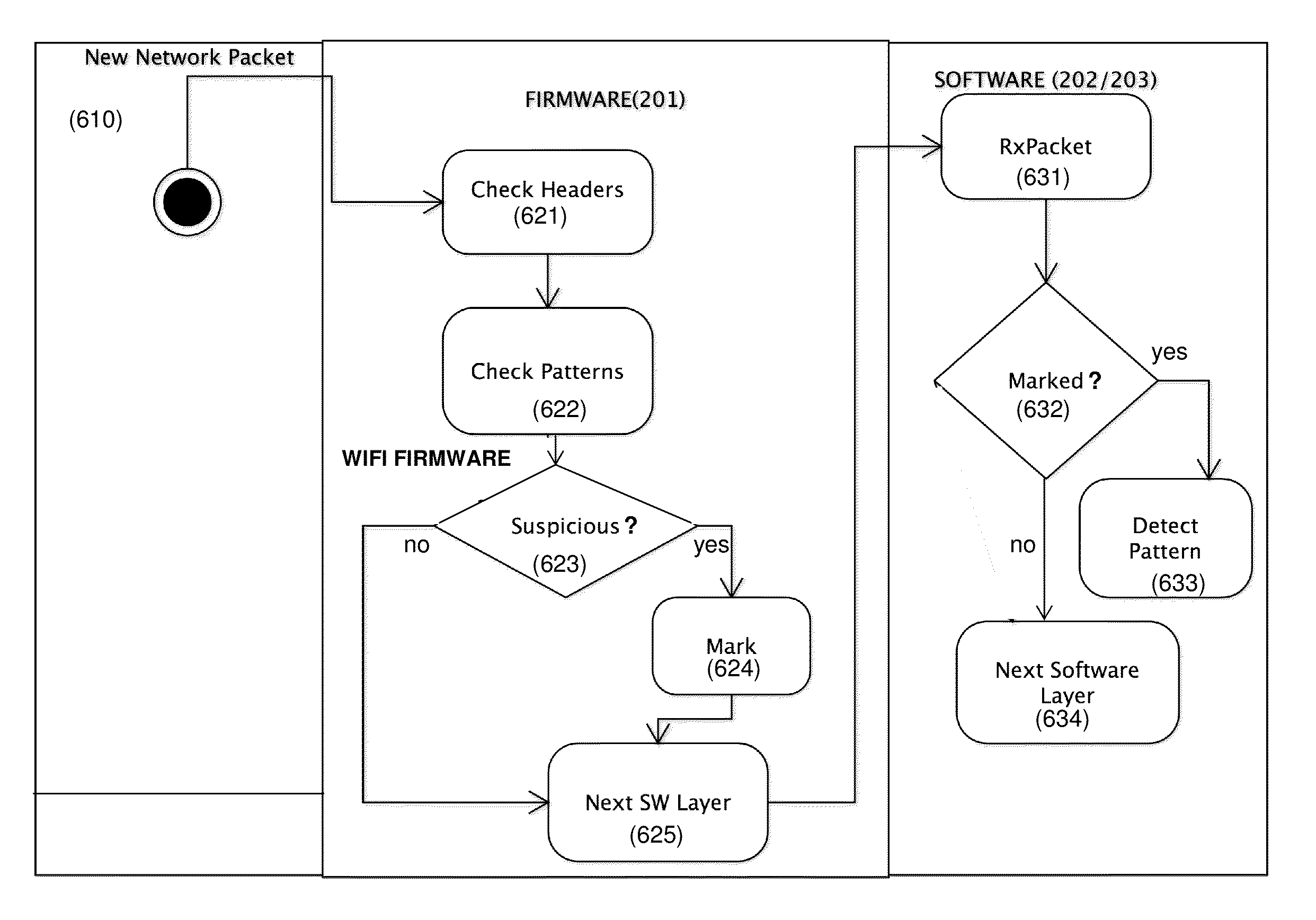
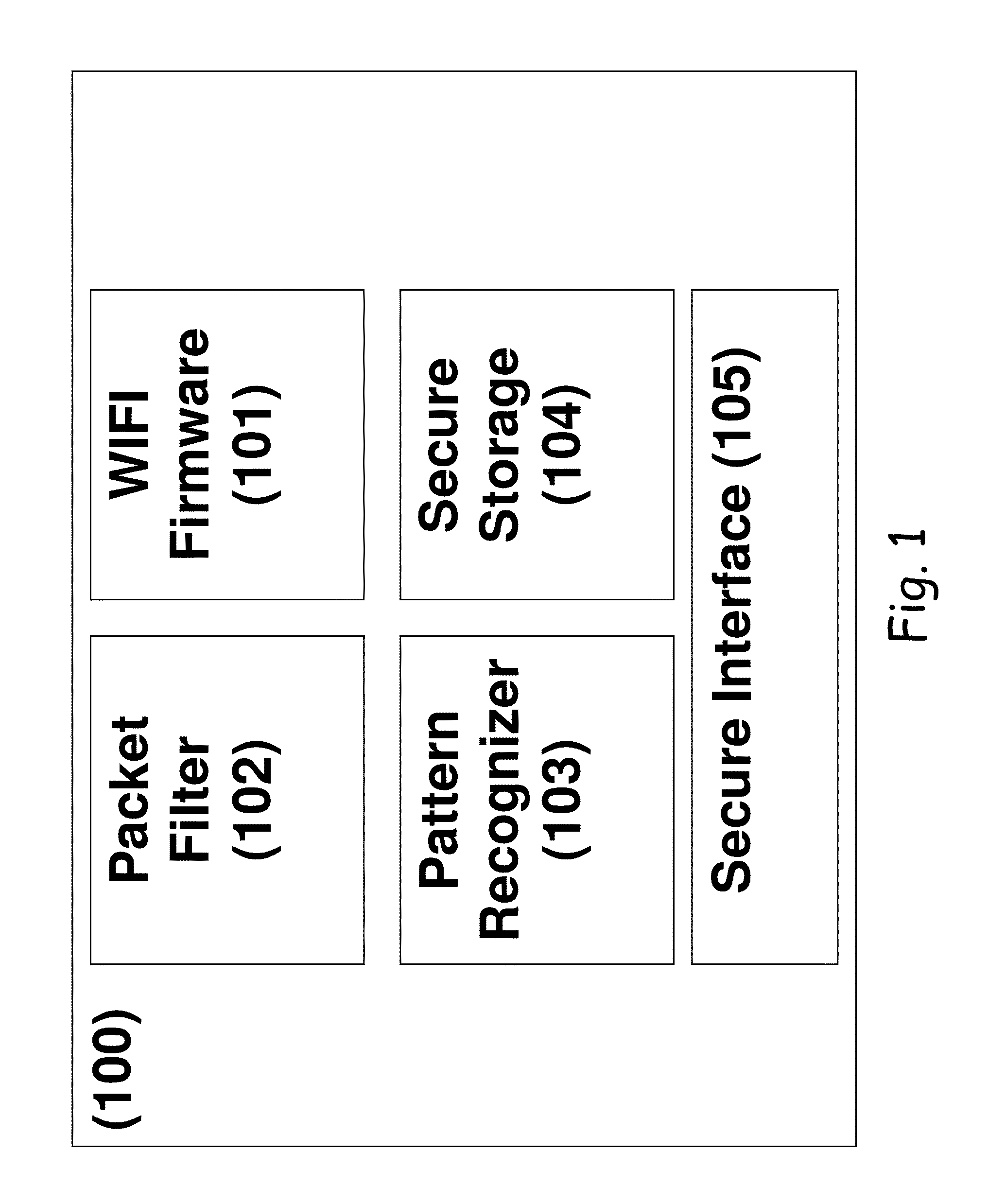
ActiveUS20140181972A1Improve securityPrevent hackingMemory loss protectionUnauthorized memory use protectionTraffic capacityNetwork packet
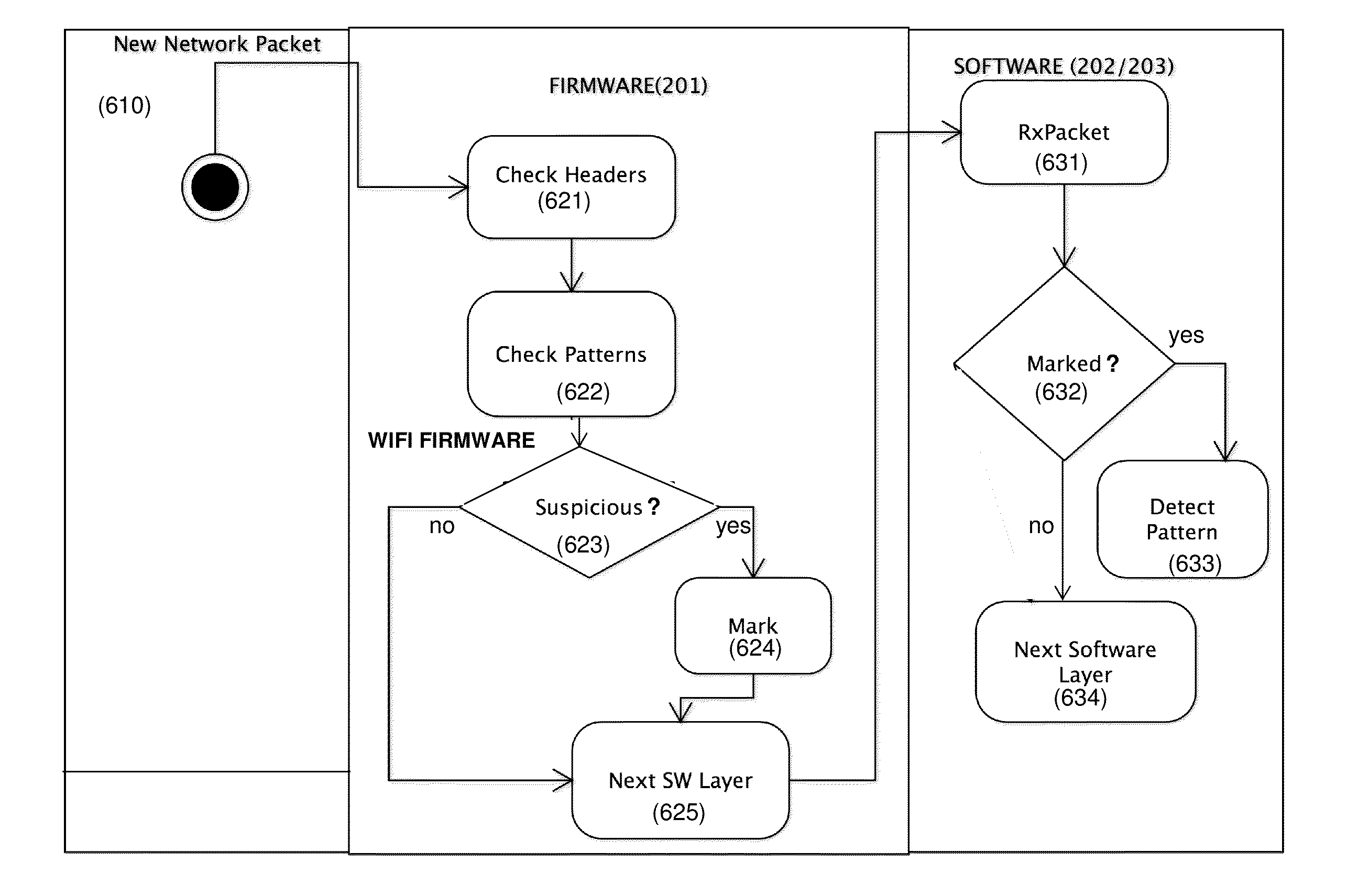
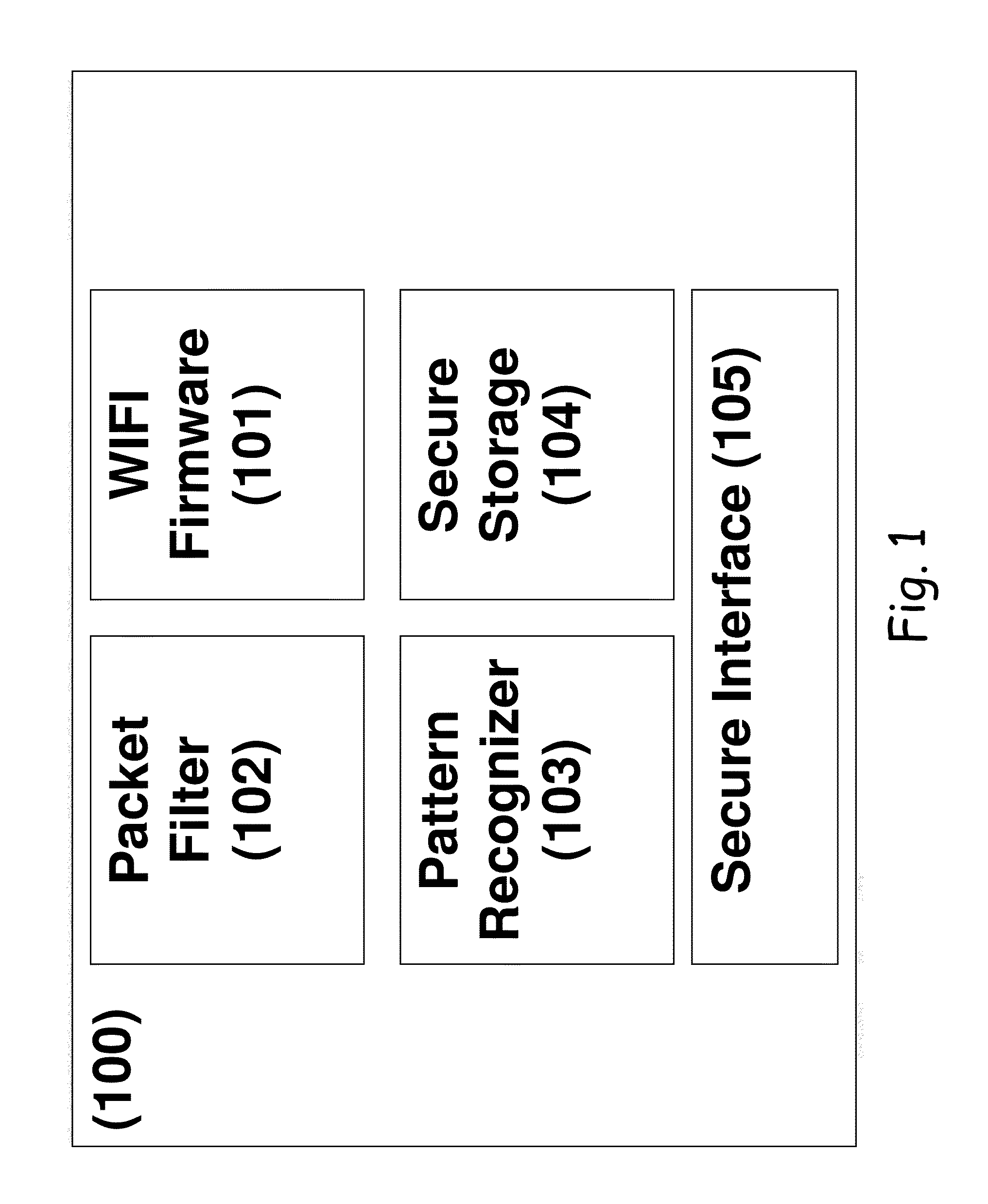
A method for providing an intrusion prevention system to prevent hacking into files located on enterprise users' endpoint devices functioning as mobile computing platforms. The method includes filtering low-level network packets for each of a plurality of received network packets, offloading the received packets to an inspecting processing module and marking suspicious packets based on at least one of a header and pattern of each of said received packets. The method also includes taking preventive measures by the system to ensure protection of the device and network, taking active steps by the system to block suspicious traffic and disconnecting the current connection by the system, when it detects suspicious traffic.
Owner:ZIMPERIUM INC
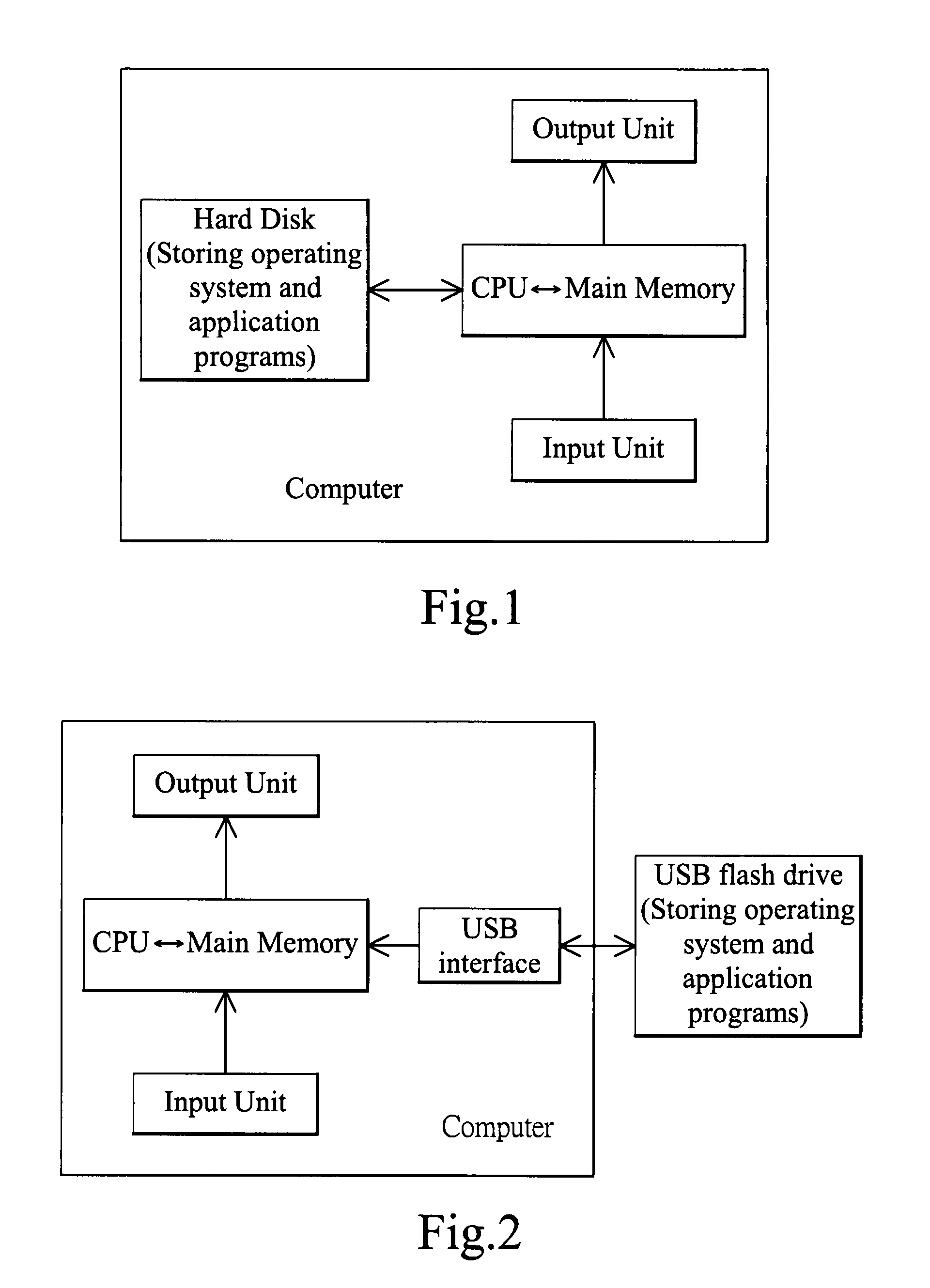
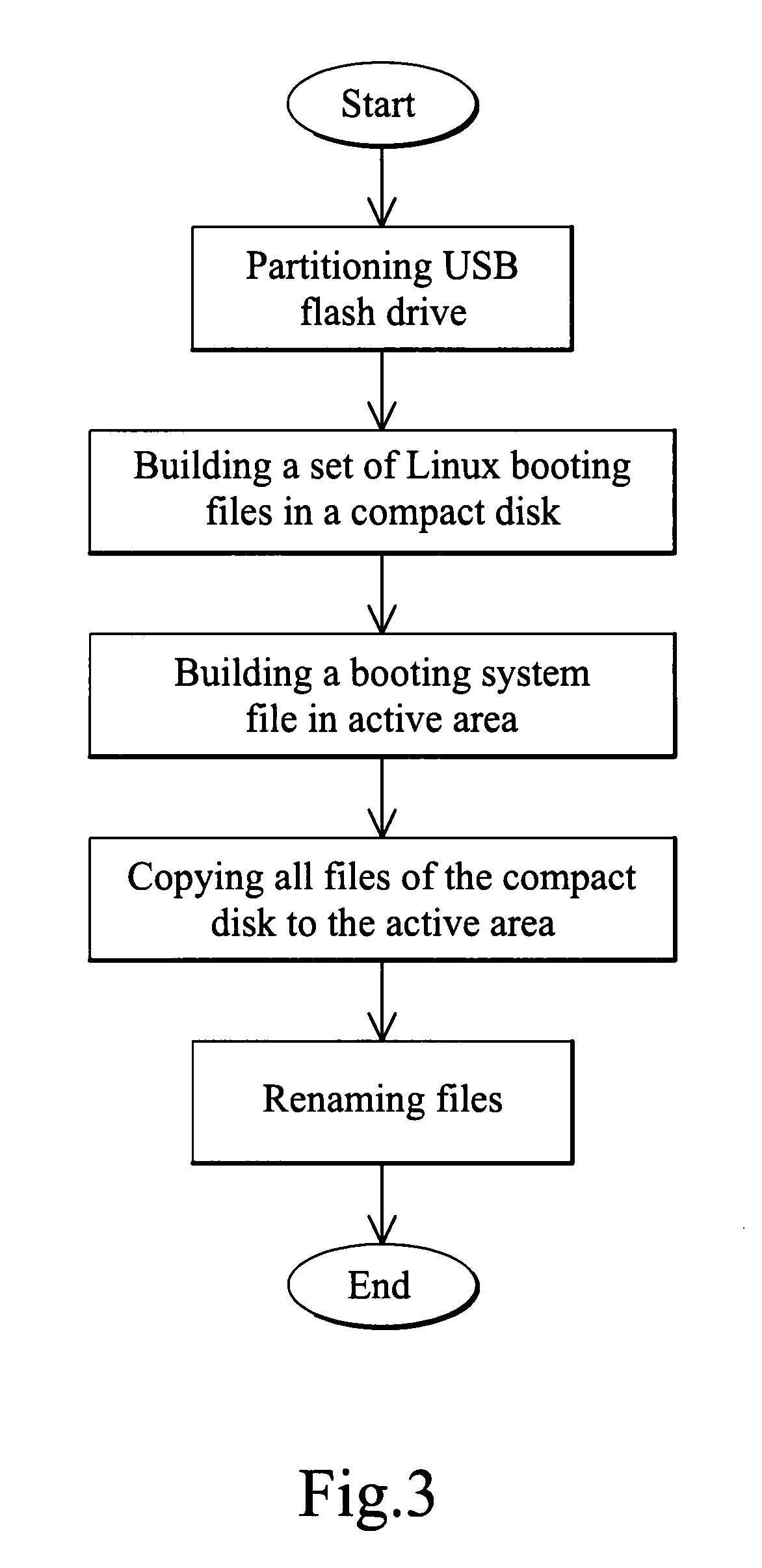
Universal serial bus flash drive for booting computer and method for loading programs to the flash drive
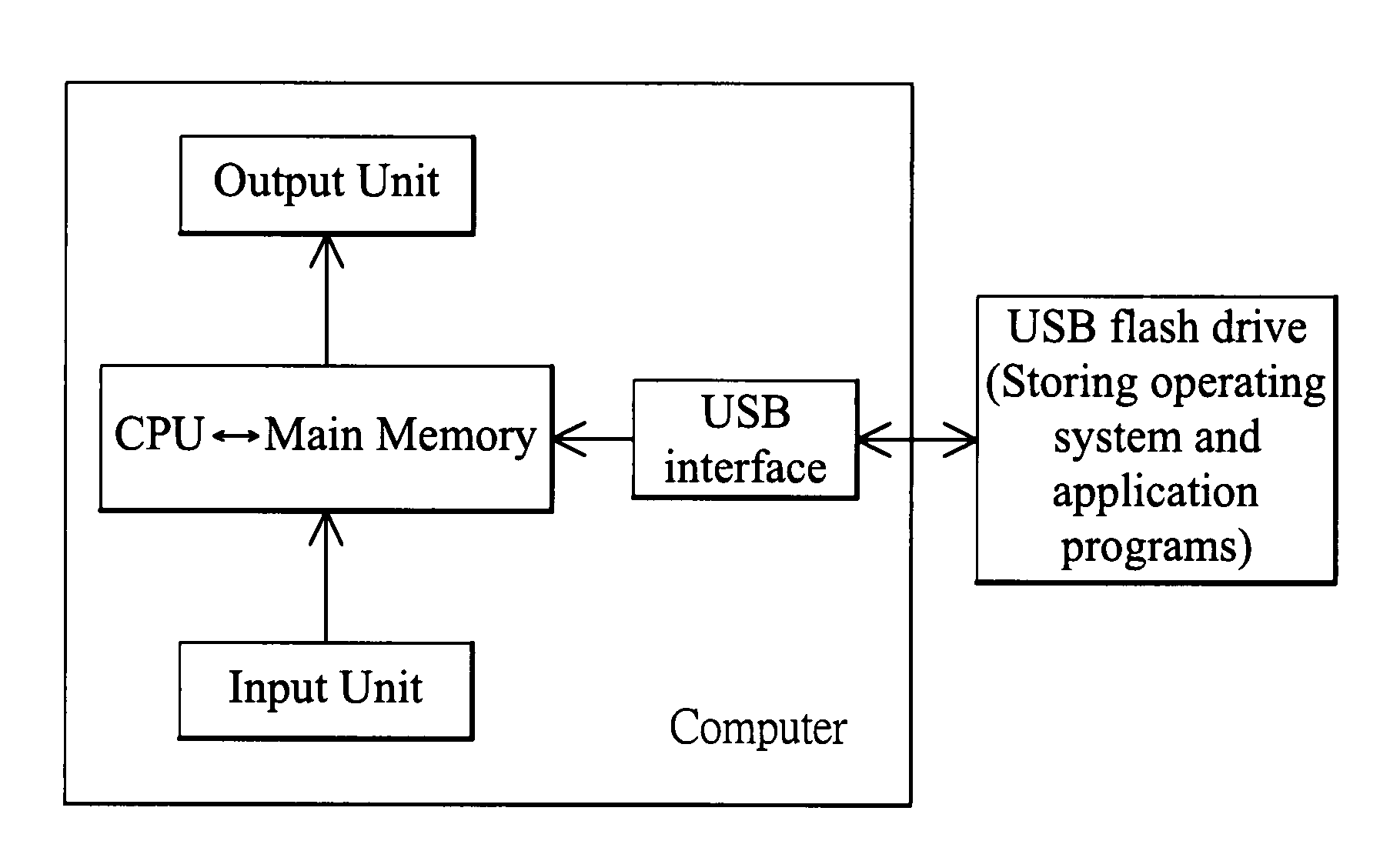
InactiveUS20090094447A1Prevent hackingNot easily hackDigital computer detailsBootstrappingBootingFlash drive
The present invention relates to a universal serial bus (USB) flash drive loaded with operating system and application programs for booting a computer when plugged into the computer, wherein memory of the flash drive is partitioned as a read-only active area and a writeable data storage area, and the operating system and application programs are stored in the active area; and the operating system is executed unrelated to hardware. The present invention also relates to a method for loading programs to the USB flash drive.
Owner:YANG JYH CHIANG +1
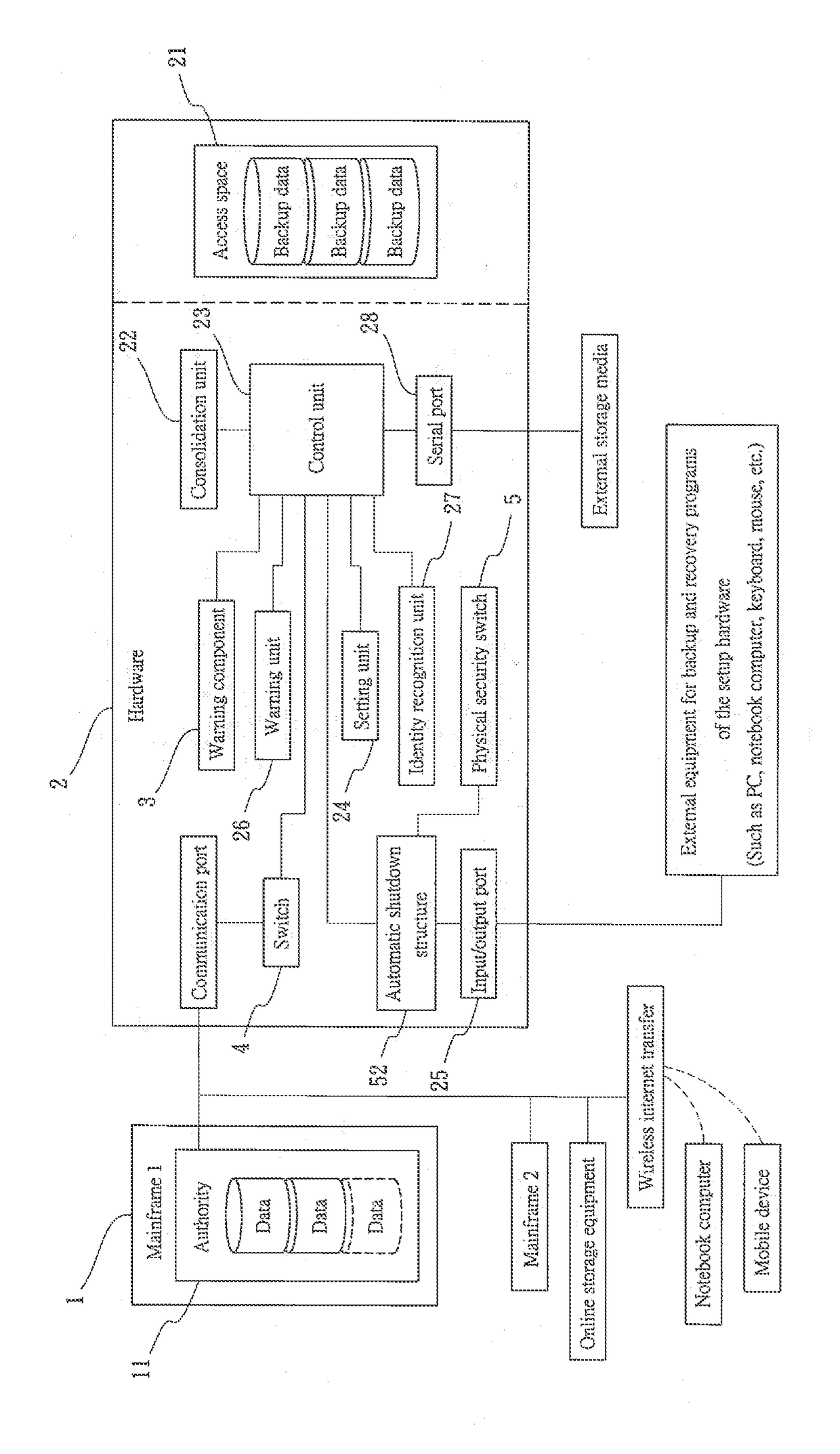
Active network backup device
InactiveUS20180375826A1Widely promotedEasily causes data corruption or blackmailInput/output to record carriersTransmissionRansomwareSoftware
An active network backup device includes at least a mainframe and a hardware. The mainframe and other network devices cannot log in, create settings and access data of the hardware. Hence, the hardware can practically prevent and block viruses, ransomware and attacks by hackers; moreover, the device has a physical security switch design for switching on and off a port to ensure personal operation of the administrator and prevent the hardware from being hacked by robot program. Most importantly, the hardware cannot execute destructive instructions and thereby viruses cannot be executed or run in the hardware, which also prevents accidental deletion due to setting errors, or any ransomware or malicious programs in the disguise of setting programs being downloaded and executed by careless users.
Owner:CHANG SHENG HSIUNG +1
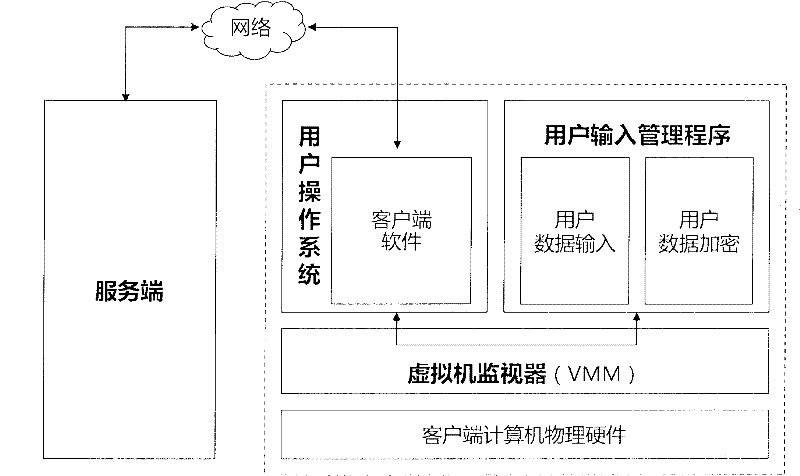
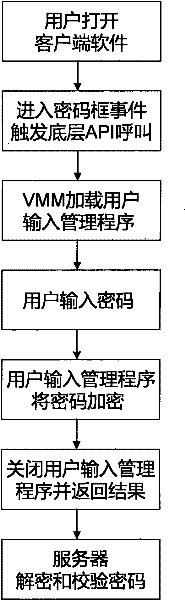
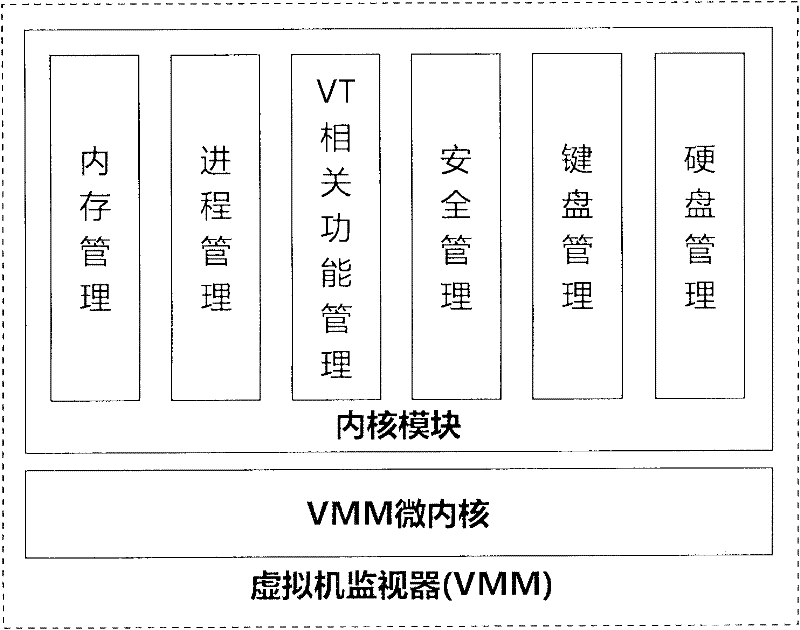
Virtual-machine-technology-based data security input and submission method and system
The invention relates to a virtual-machine-technology-based data security input and submission method and a virtual-machine-technology-based data security input and submission system. The system isolates a user input management programs and a user operating system into different hardware resource spaces by a virtual machine monitor (VMM), so that a user can securely input and submit data to a server in an environment inaccessible for Trojans without worrying that the data may be intercepted by the Trojans, and even though being intercepted, the intercepted data is encrypted. In other words, by the method and the system, a universal software solution is provided for the prevention of number stealing of the Trojans.
Owner:BEIJING SOFTLUMOS TECH
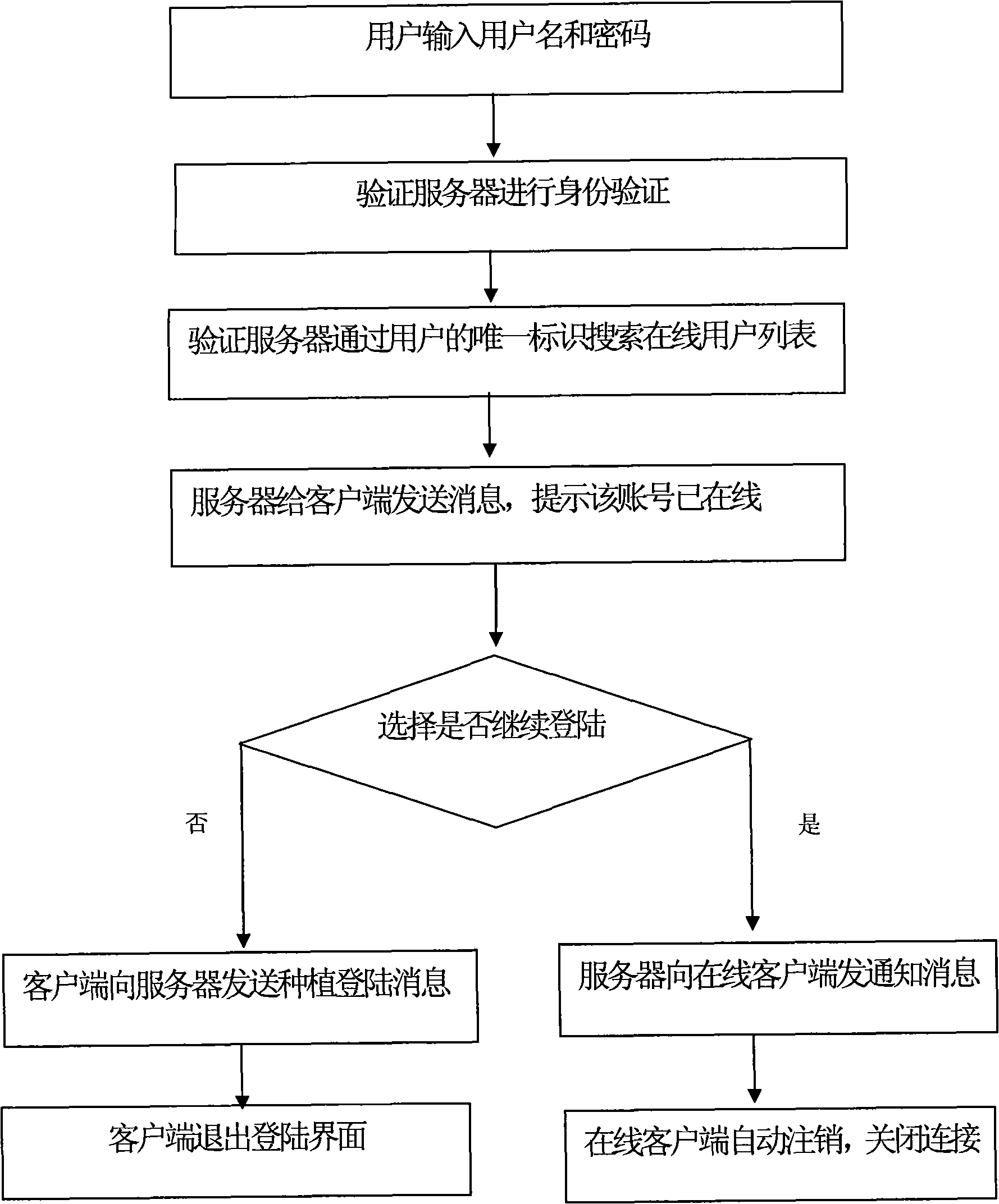
Method for dealing with repeat login
The invention provides a method for dealing with repeat login, aiming to solve the problem that when a user meets repeat login in during logging in an instant messaging system, the system simply kicks off the previous online user to allow the user to log in or directly prevents the user from logging in. The method for dealing with repeat login comprises the following steps: a server detects that a user name input by the user is online already; the server sends information to a client and prompts that the count number of the user is already online; and the client prompts the user to choose after receiving the information. The method can ensure that only one user can log in so as to prevent the occurrence of number stealing and can also provide the user logging in a chance to choose.
Owner:BEIJING YIQI TELECOMM TECH
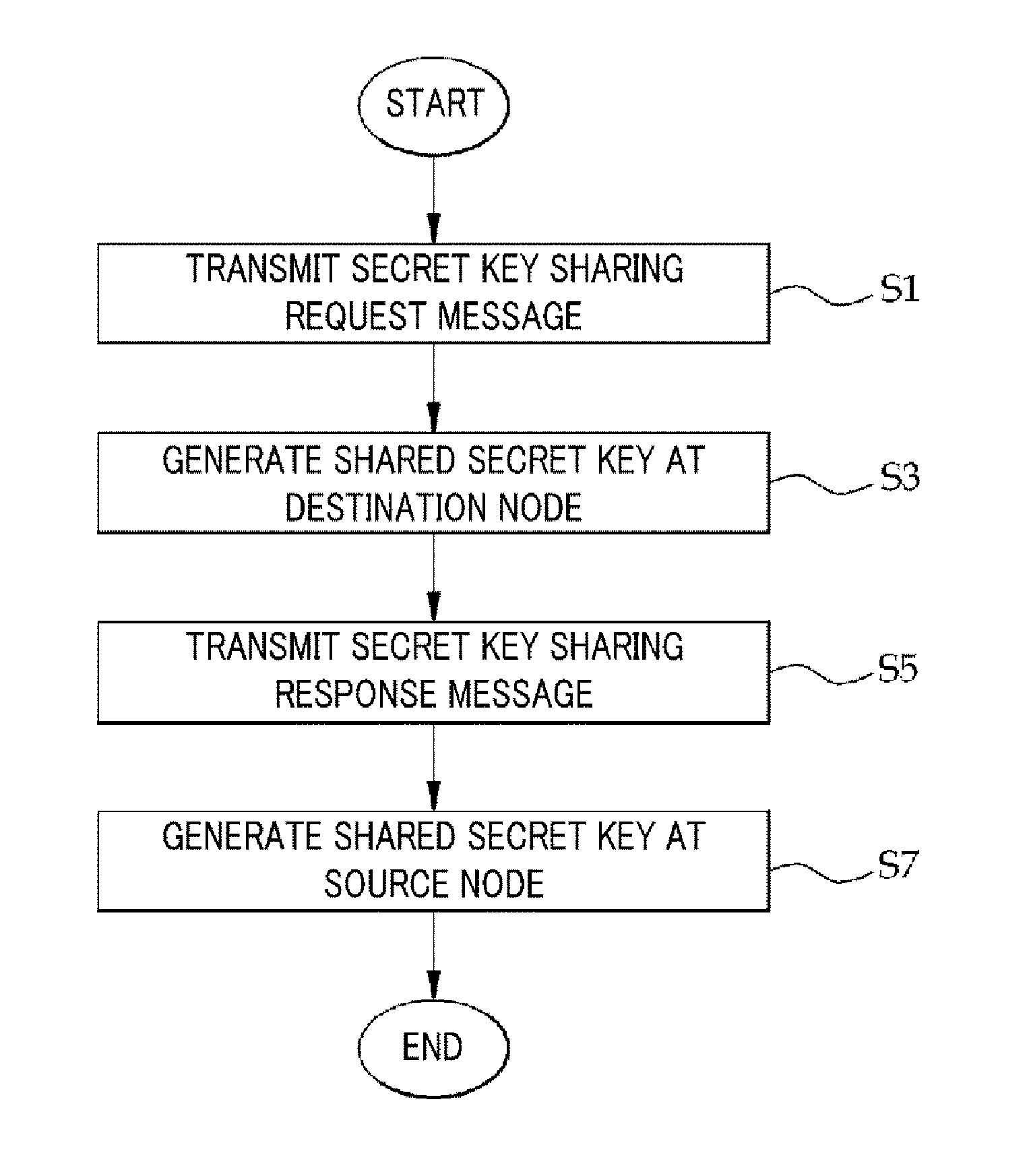
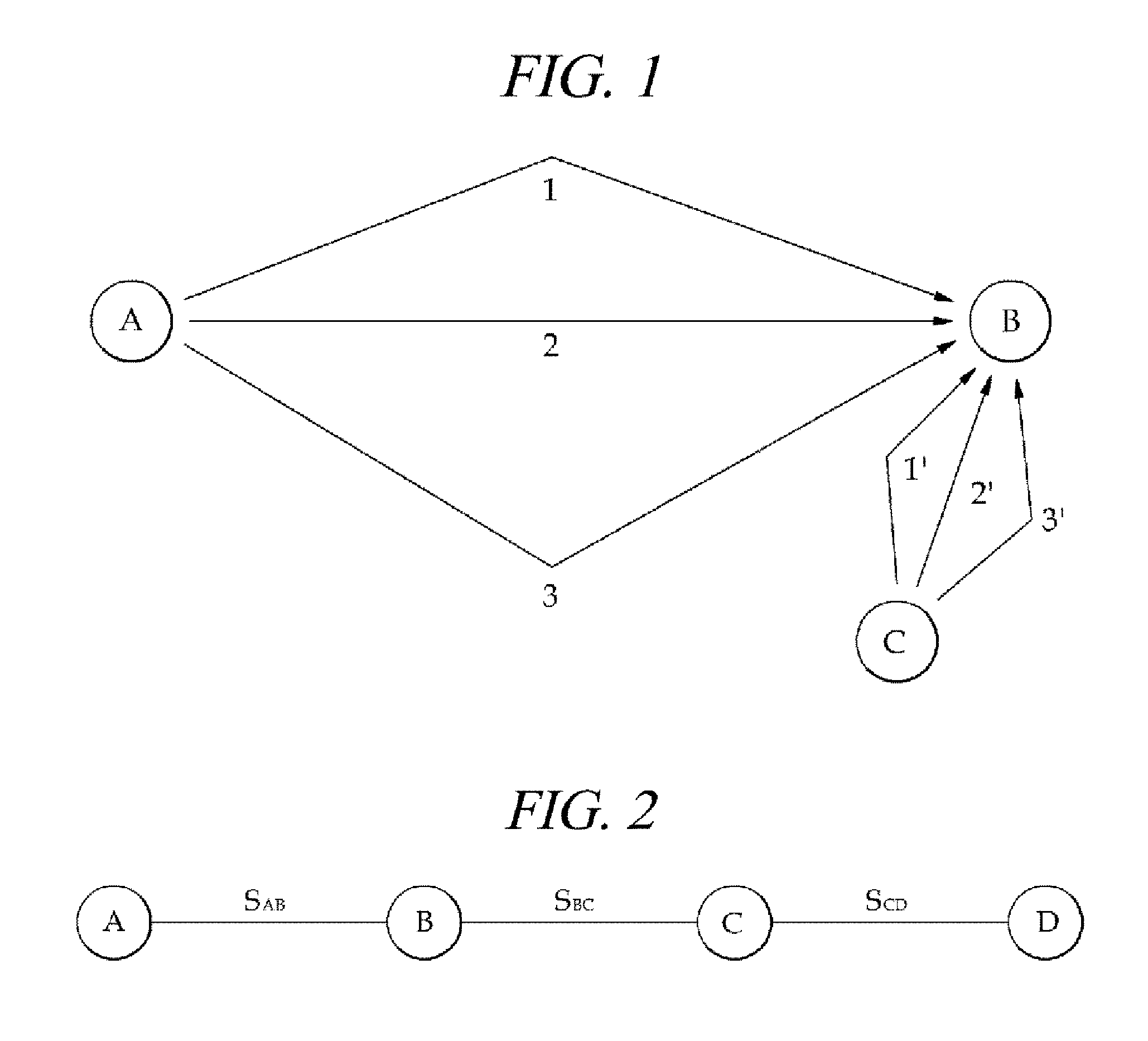
Method for sharing secret values between sensor nodes in multi-hop wireless communication network
InactiveUS20130173910A1Reduce energy consumptionPrevent hackingEnergy efficient ICTPower managementSensor nodeKey sharing
A method for sharing a secret key between a source node and a destination node includes (a) adding, at each forward intermediate node, a secret key between the forward intermediate node and a node before the forward intermediate node to the secret key sharing request message; (b) generating a shared secret key between the source node and the destination node from the secret key between the forward intermediate node and the node before the forward intermediate node added in the secret key sharing request message; (c) adding, at each backward intermediate node, a secret key between the backward intermediate node and a node before it to the secret key sharing response message; and (d) generating the shared secret key between the destination node and the source node from the secret key between the backward intermediate node and the node before it added in the secret key sharing response message.
Owner:INTELLECTUAL DISCOVERY CO LTD
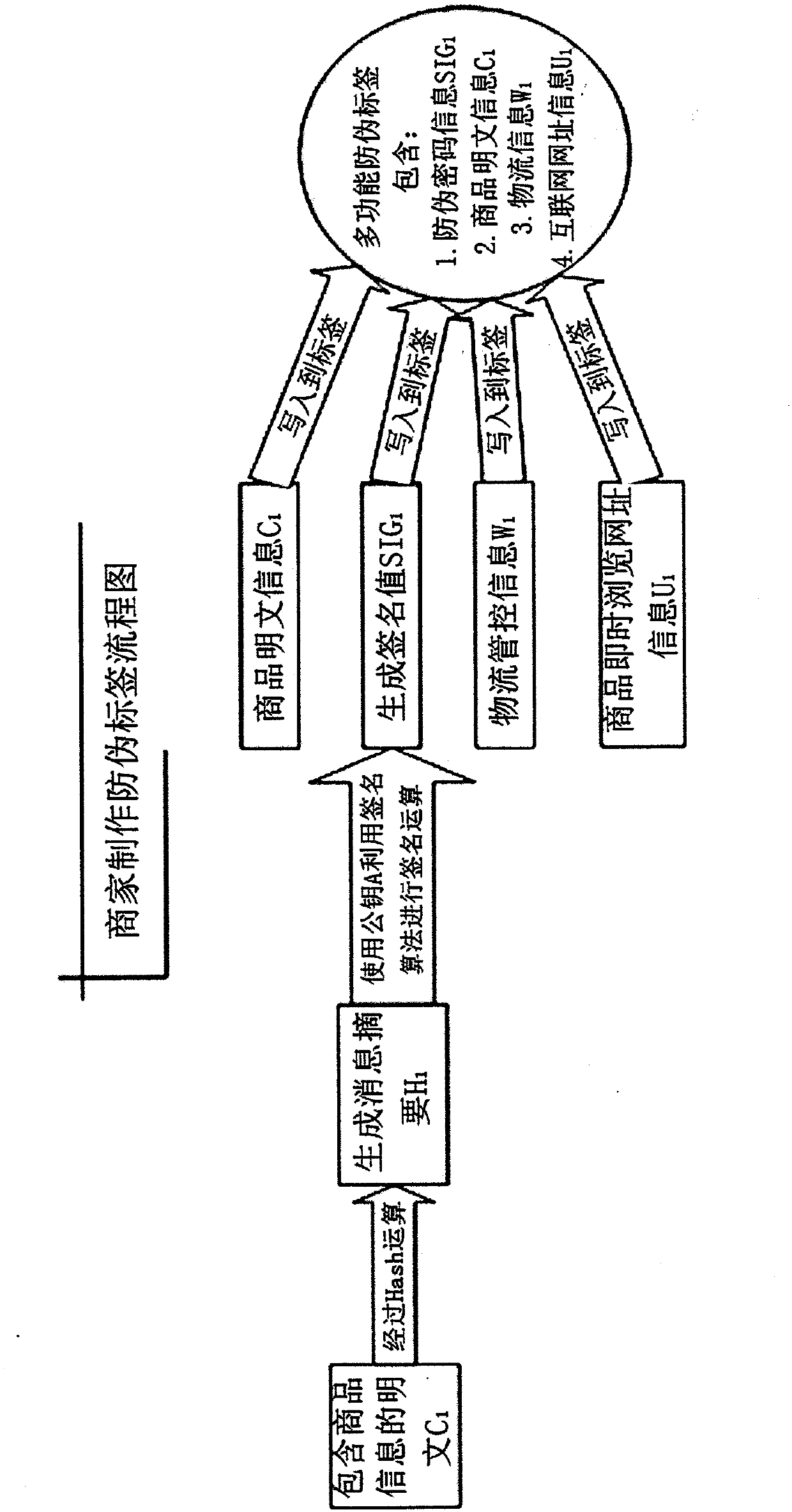
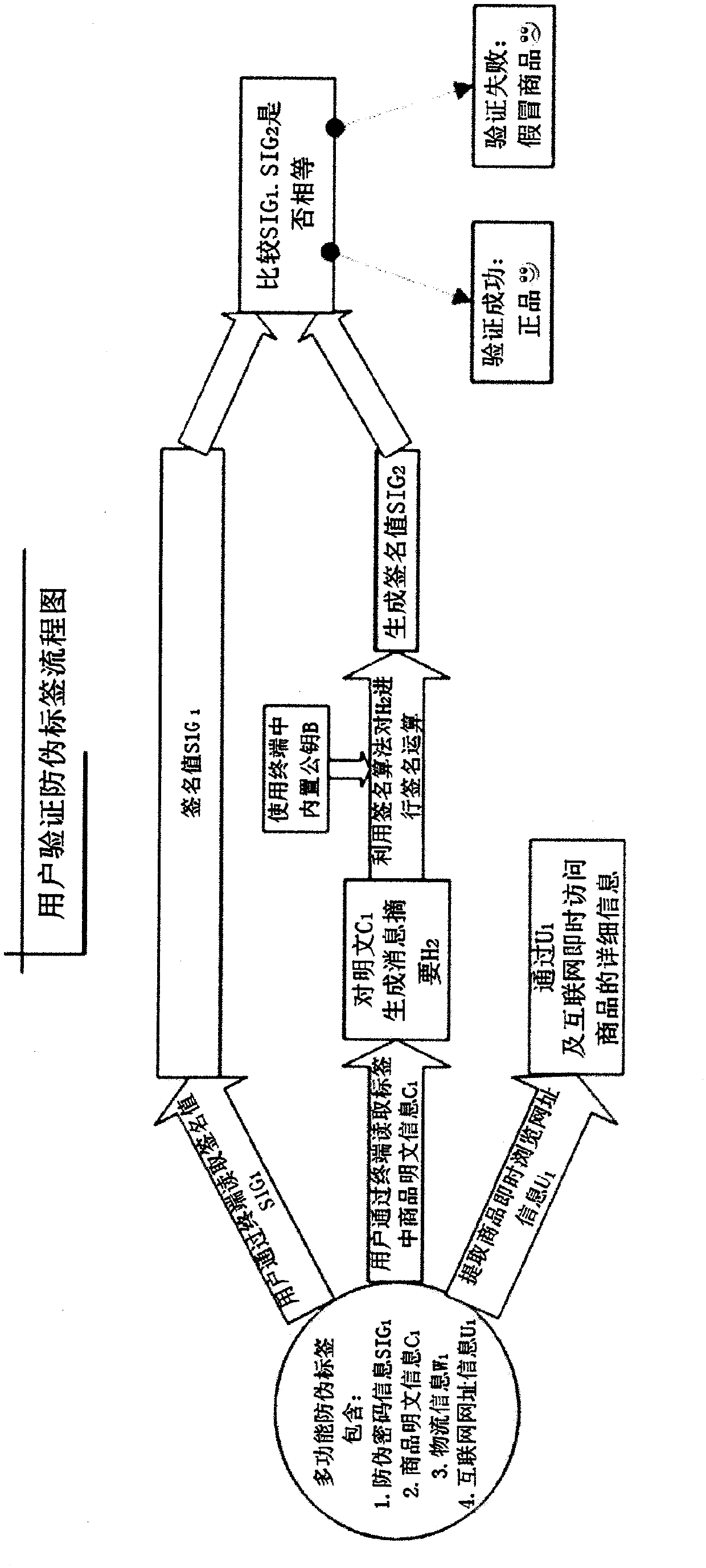
RFID (radio frequency identification device) label integrating comprehensive functions such as merchandise anti-counterfeiting, logistics control and the like
InactiveCN102779284AQuick identificationFix bugsRecord carriers used with machinesLogistics managementPassword
The invention discloses an RFID (radio frequency identification device) label integrating comprehensive functions such as merchandise anti-counterfeiting, logistics control and the like, and provides an anti-counterfeiting label identification method and data structure of an RFID label not based on password access control, namely that the password access control of the RFID label is not taken as the anti-counterfeiting core. The manufacturer manufactures the anti-counterfeiting information by use of a key A of a public key system in the anti-counterfeiting label database structure, and the anti-counterfeiting information of the merchandise, logistics control information and the website browsing information of the merchandise are written into the RFID anti-counterfeiting label attached to the merchandise at the same time; and before buying the merchandise, a user can check the identity of the merchandise and quickly browse the detailed information of the merchandise. Meanwhile, the manufacturer can perform logistics management by use of the RFID label.
Owner:张楠
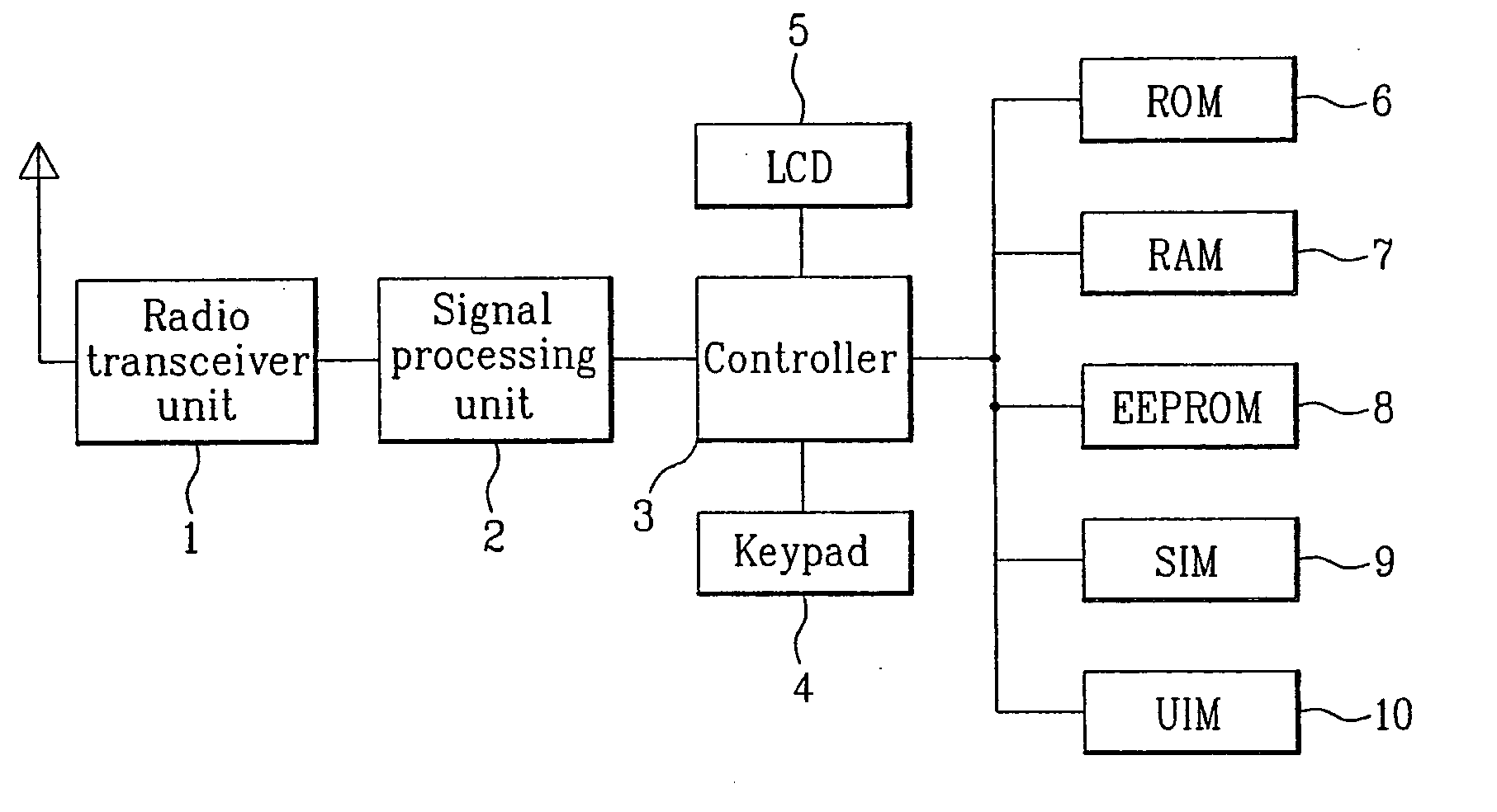
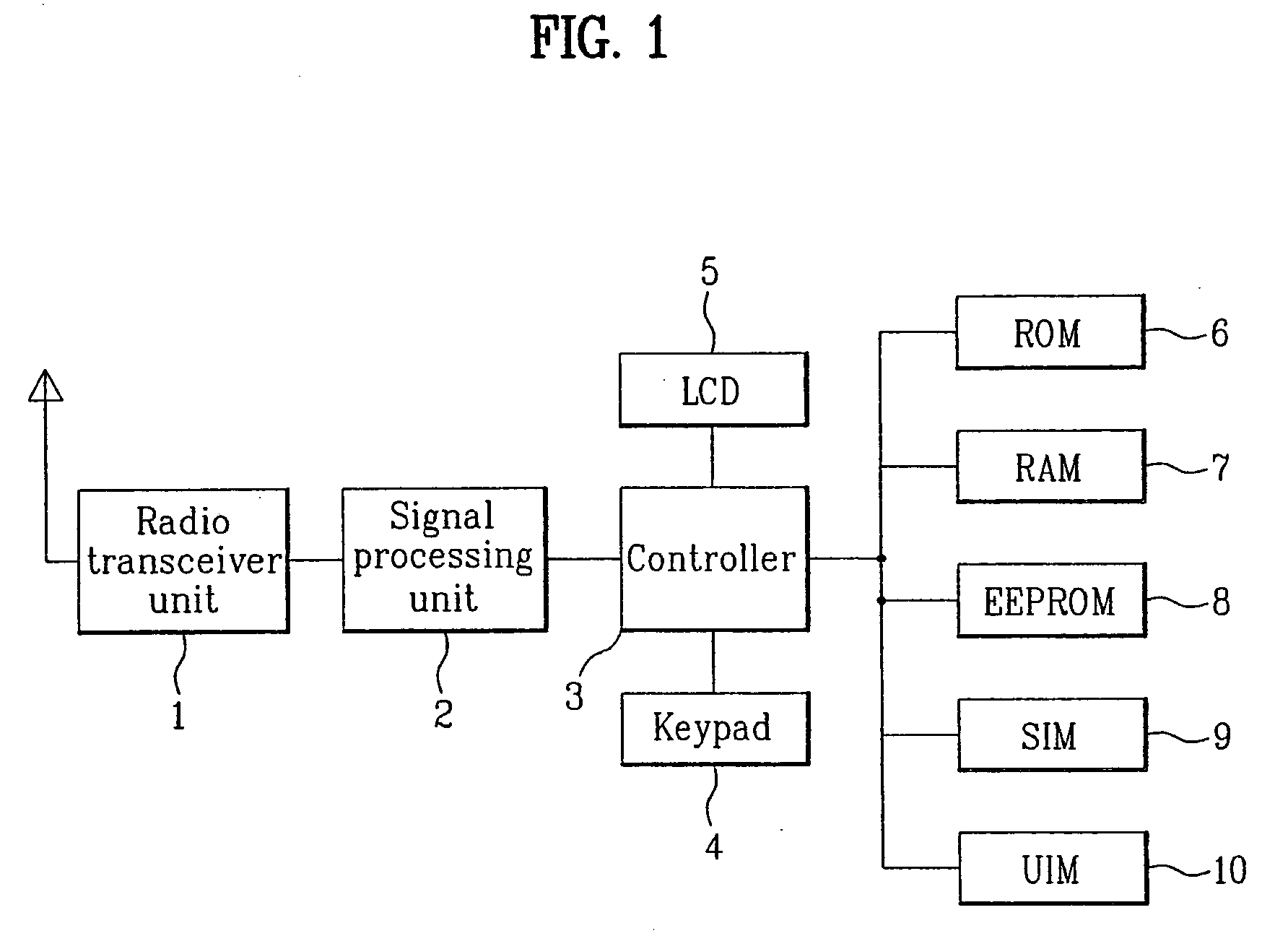
Method and apparatus for preventing hacking of subscriber identitification module in a mobile communication terminal
InactiveUS20060135208A1Prevent hackingSubstation equipmentTransmissionNon-volatile memorySubscriber identity module
An apparatus and method of preventing hacking of a subscriber identification module in a mobile communication terminal are disclosed. Hacking is prevented by storing a secret code in a hidden area of a writable non-volatile memory area and initializing a processor of the mobile communication terminal if the secret code matches a specified code.
Owner:LG ELECTRONICS INC
Anti-hacking mechanisms for flash memory device
ActiveUS20190114097A1Enhanced securityImprove securityInput/output to record carriersSemiconductor/solid-state device detailsPassword protectionFlash memory
Multiple embodiments are disclosed for enhancing security and preventing hacking of a flash memory device. The embodiments prevent malicious actors from hacking a flash memory chip to obtain data that is stored within the chip. The embodiments include the use of fault detection circuits, address scrambling, dummy arrays, password protection, improved manufacturing techniques, and other mechanisms.
Owner:SILICON STORATE TECH INC
Network security architecture for power information acquiring system
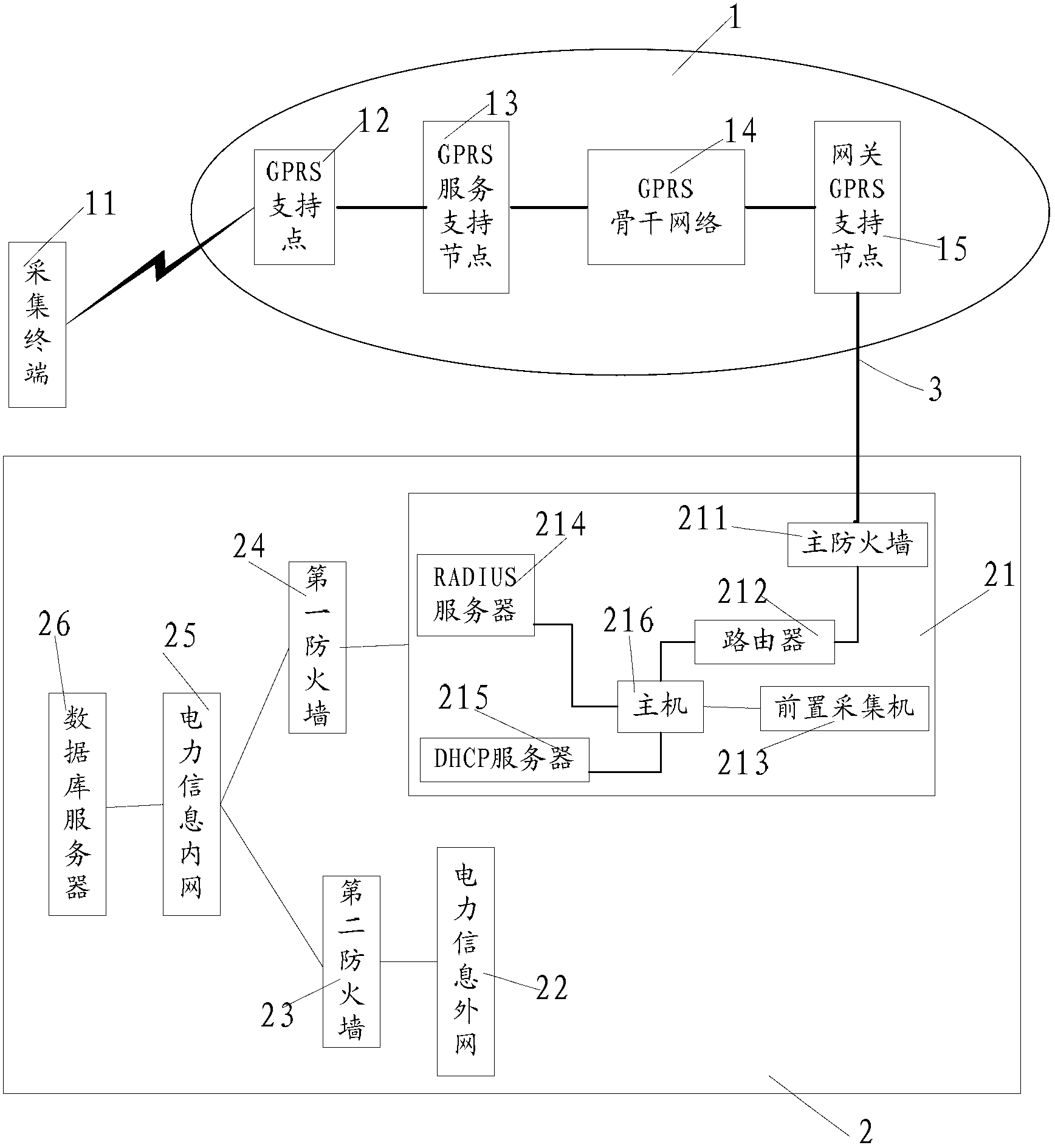
The invention discloses a network security architecture for a power information acquiring system in the field of intelligent power grids. The network security architecture comprises a client end and a host end, wherein the host end comprises a gateway GPRS support node, and also comprises a gateway and a database server which are connected through a power information intranet, the gateway comprises a router, a DHCP (Dynamic Host Configuration Protocol) server and a host, the router and the DHCP server are connected with a host, the gateway and the gateway GPRS support node through an APN (Access Point Name) special line, an IP address of the APN special line is allocated by the DHCP server, and the router is used for carrying out domain name analysis on the IP address corresponding to the APN special line. The network security architecture has the beneficial effects that hacker attack from a public network can be avoided, and the security of operation of the power information acquiring system is enhanced.
Owner:SHANGHAI MUNICIPAL ELECTRIC POWER CO +1
Method for locking application program
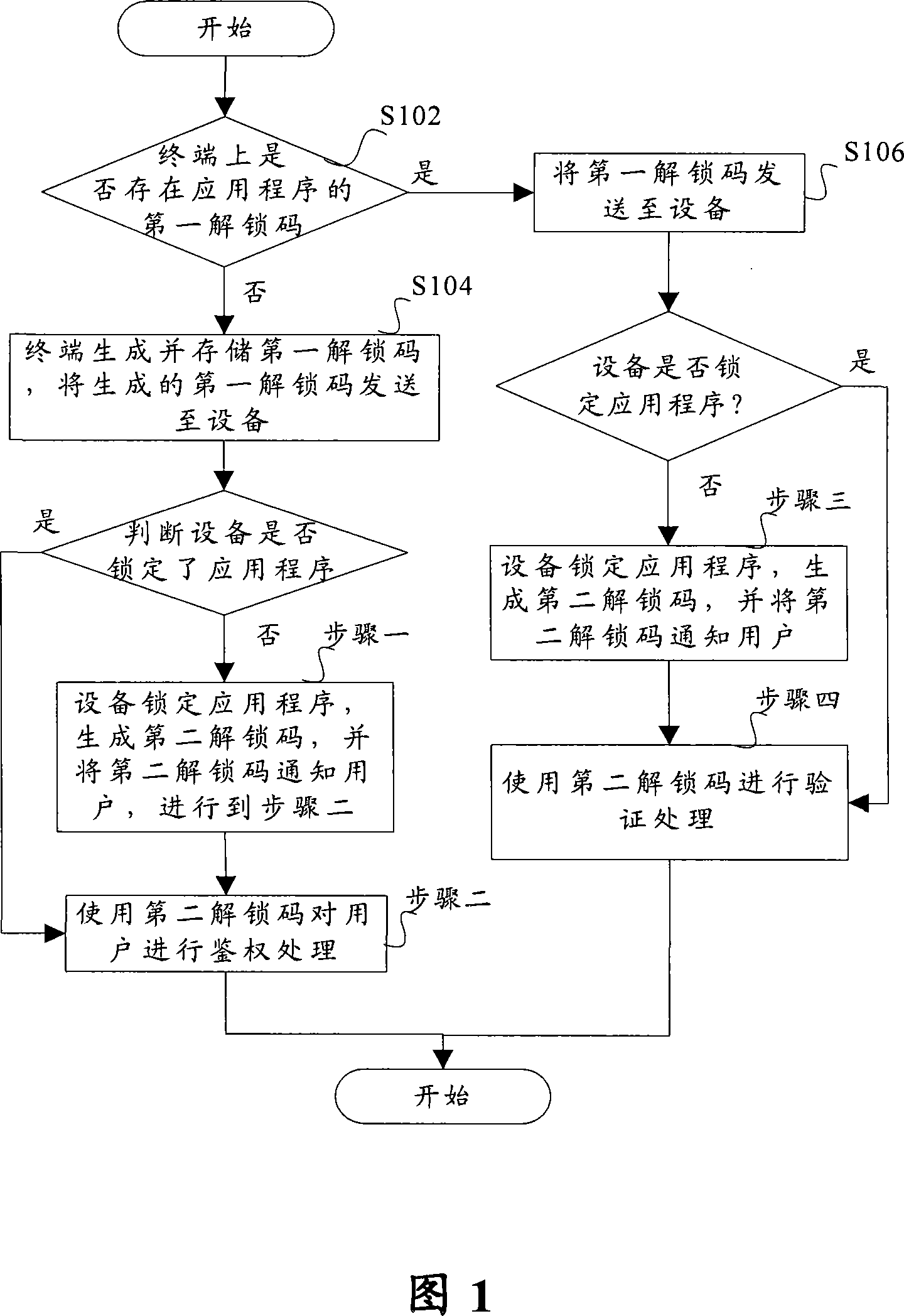
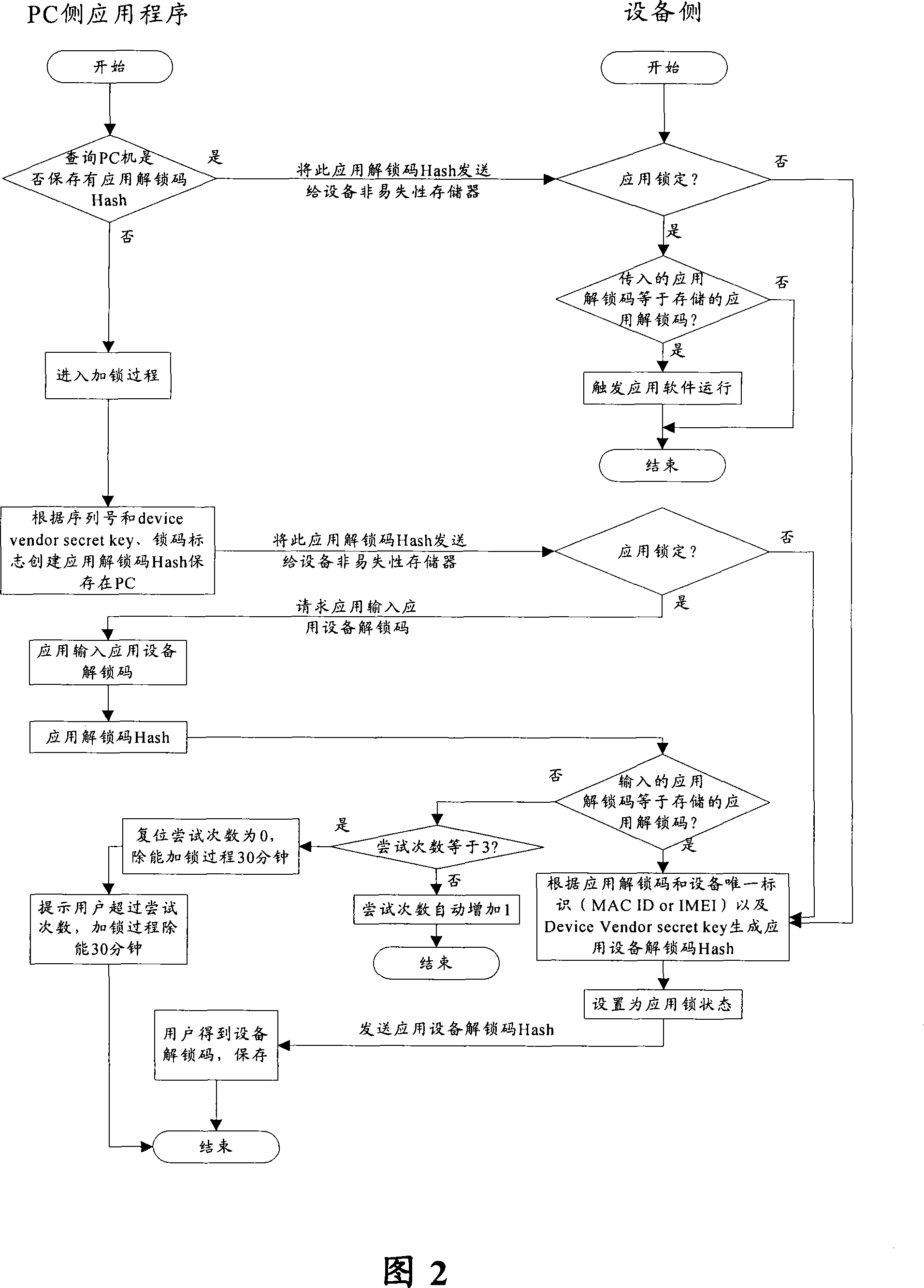
InactiveCN101226575APrevent hackingEffective protectionProgram/content distribution protectionEmbedded systemAuthentication
A locking method for application programs comprises judging whether the terminal is provided with a first unlocking code of an application program when running the application program stored in the terminal. If the first unlocking code is absent, the terminal produces and stores a first unlocking code which is then transferred to a device. The method further comprises judging whether the device locks the application program or not, if not, step one is carried out, otherwise step two is executed. Step one includes that the device locks the application program, produces a second unlocking code and informs the second unlocking code to users and executes step two. Step two comprises carrying out authentication treatment to users. If the terminal is provided with a first unlocking code, the method comprises sending the first unlocking code to the device, judging whether the device locks the application program or not, if not, executes step three, otherwise executes step four. Step three includes that the device locks the application program, produces the second unlocking code, informs the second unlocking code to users and executes step four. Step four includes identifying treatment.
Owner:ZTE CORP
Method for preventing illegal use of software
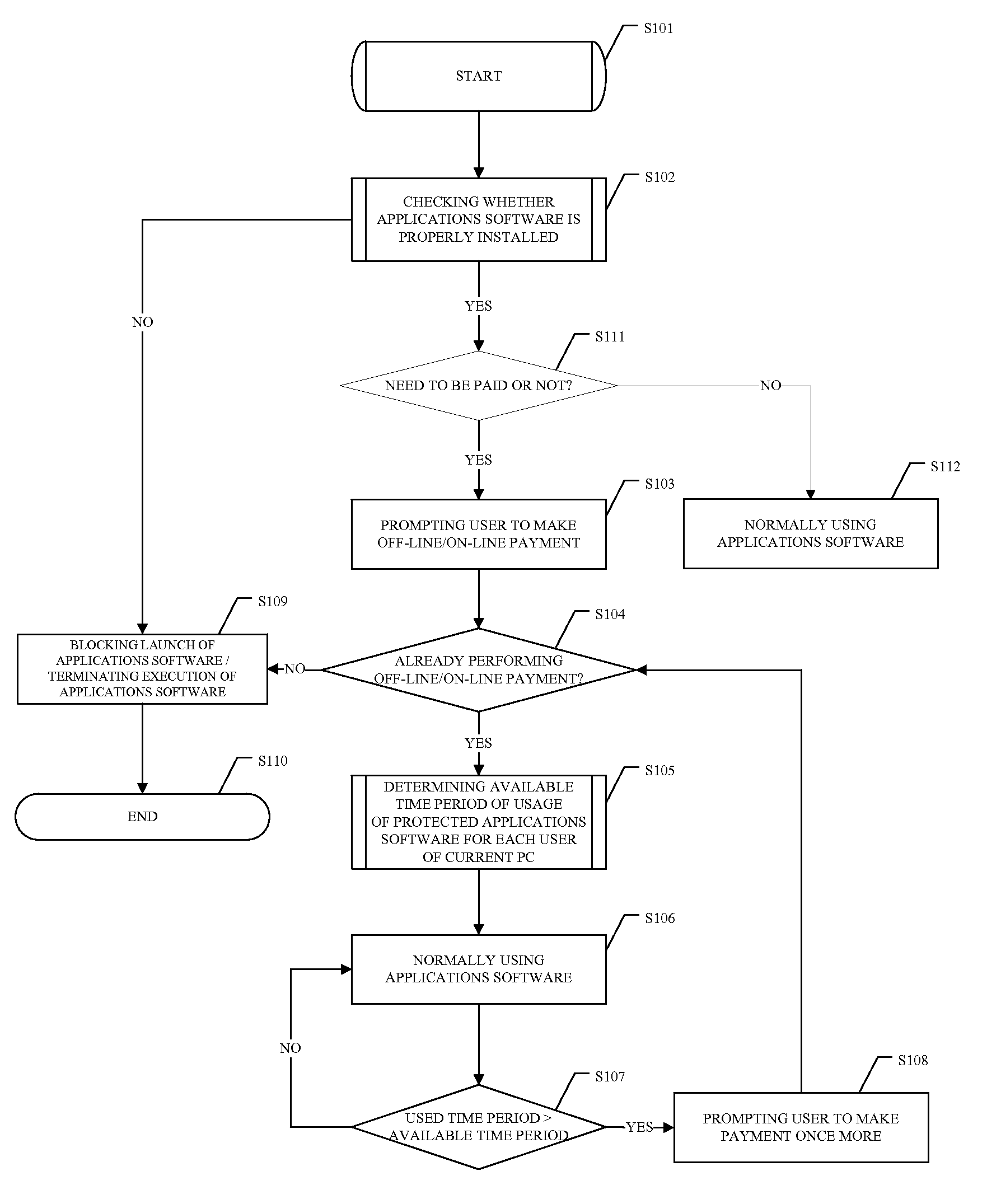
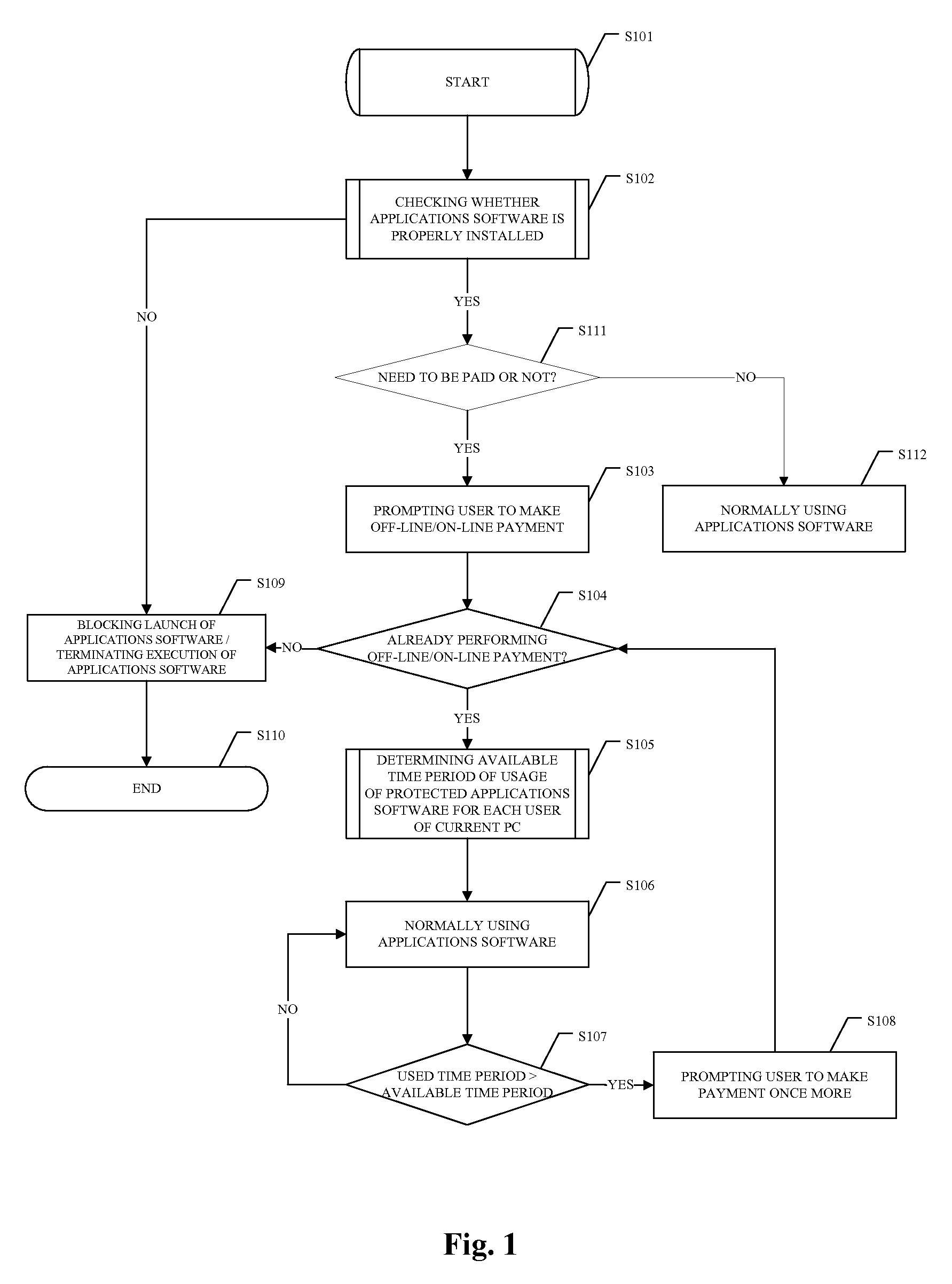
ActiveUS20070300308A1Prevent any harmful modifyingPrevent hackingDigital data processing detailsUser identity/authority verificationComputerized systemApplication software
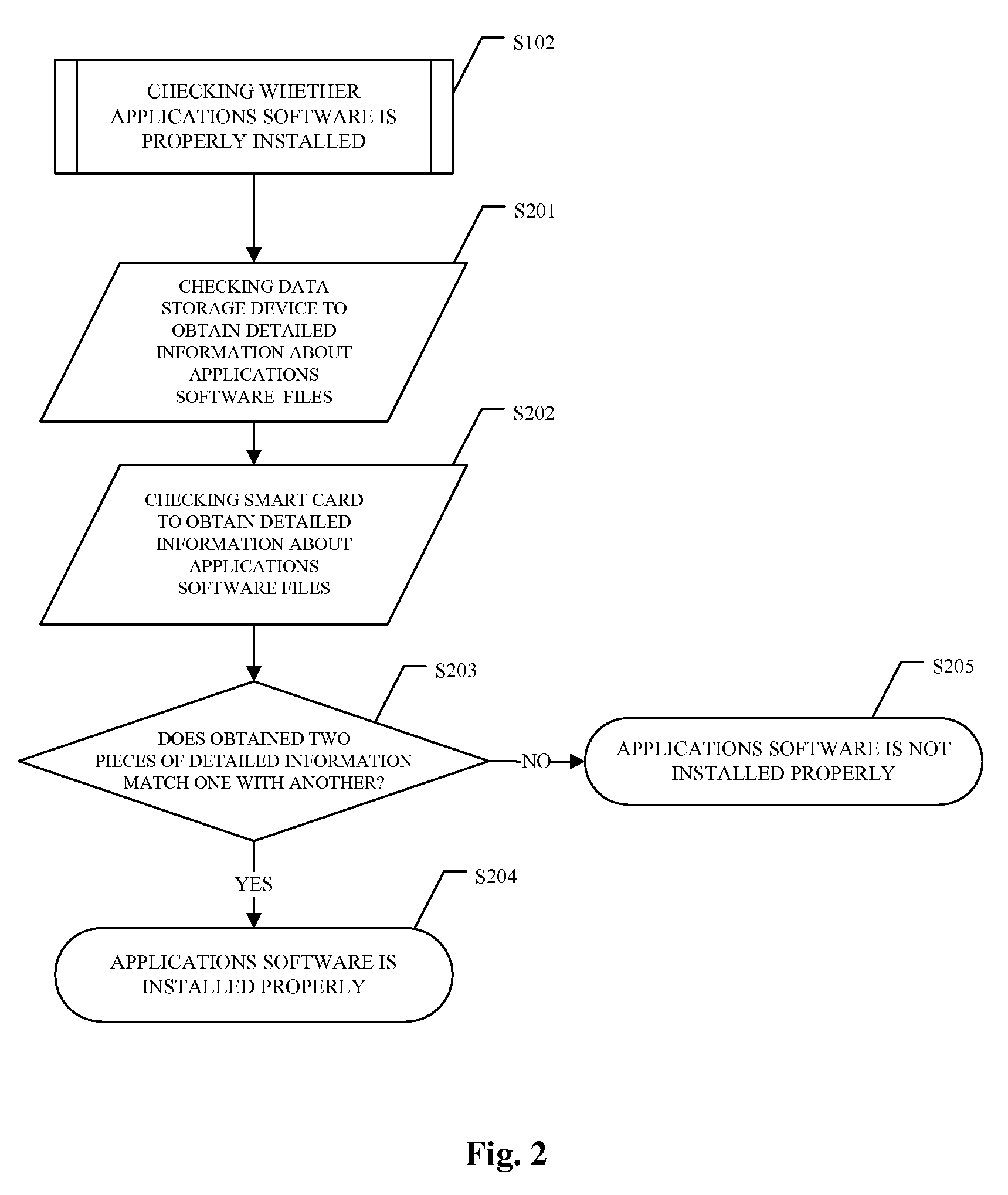
Apparatus, techniques and systems for preventing illegal use of software and other digital files based on operations of a data storage device controller in a computer or computer system. For example, a method for preventing illegal use of software includes: configuring a computer to use a data storage device controller to control use of each digital file stored on one or more data storage devices; before a use of each digital file, operating the data storage device controller to access a storage device on which the digital file is stored to check whether the digital file meets a condition for use; and operating the data storage device controller to block use of the digital file when the condition is not met and to allow execution of the digital file when the condition is met. The digital file can be an application software or other digital documents.
Owner:MISHURA SERGII
Authenticating input in trusted execution mode
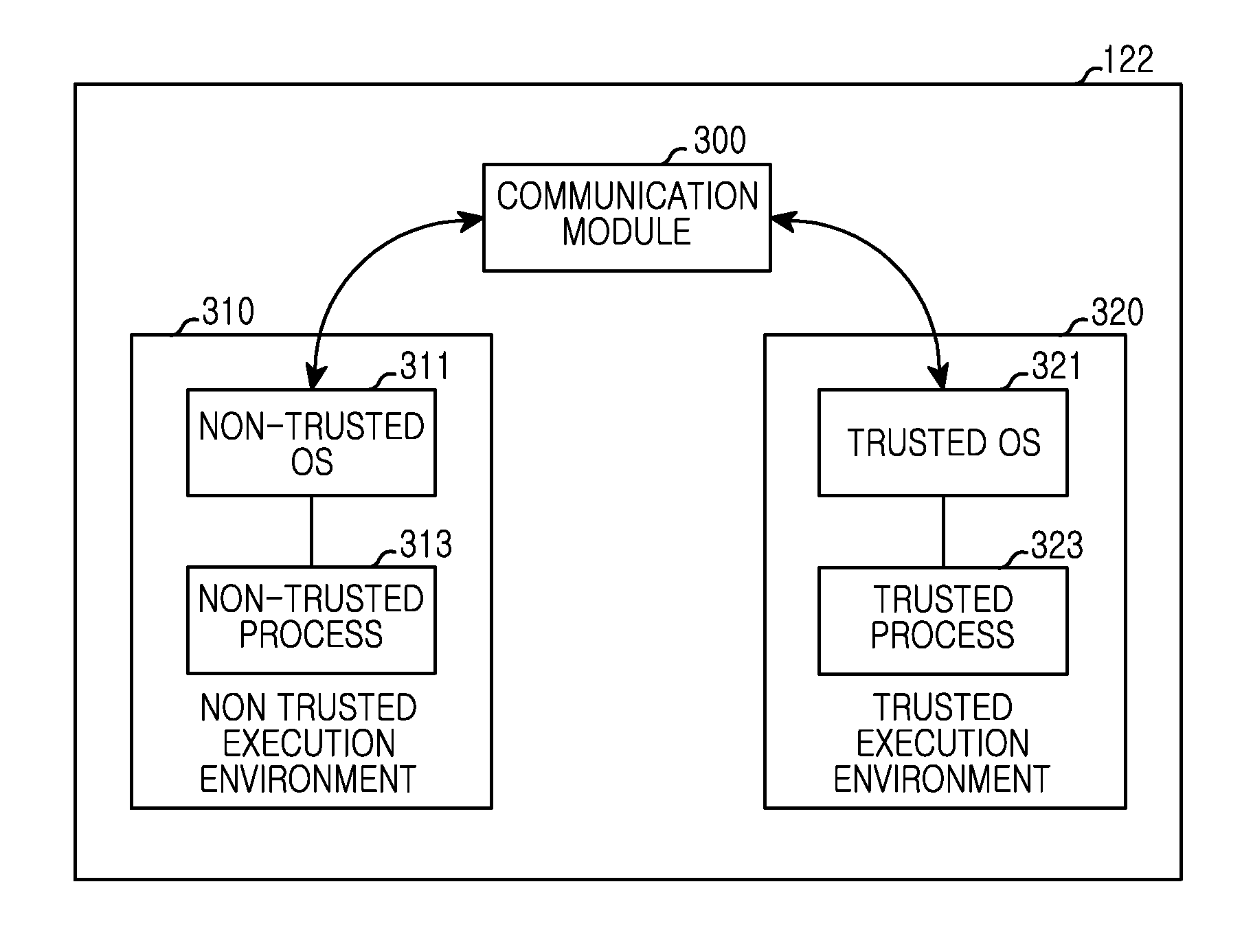
InactiveUS20150121516A1Prevent hackingDigital data processing detailsUnauthorized memory use protectionComputer hardwareSecurity authentication
Disclosed herein are a method and electronic device for enhancing security authentication. An execution mode may be changed from a non-trusted execution mode to a trusted execution mode. At least one input may be authenticated while in the non-trusted execution mode.
Owner:SAMSUNG ELECTRONICS CO LTD
Optical recording medium for retail activation
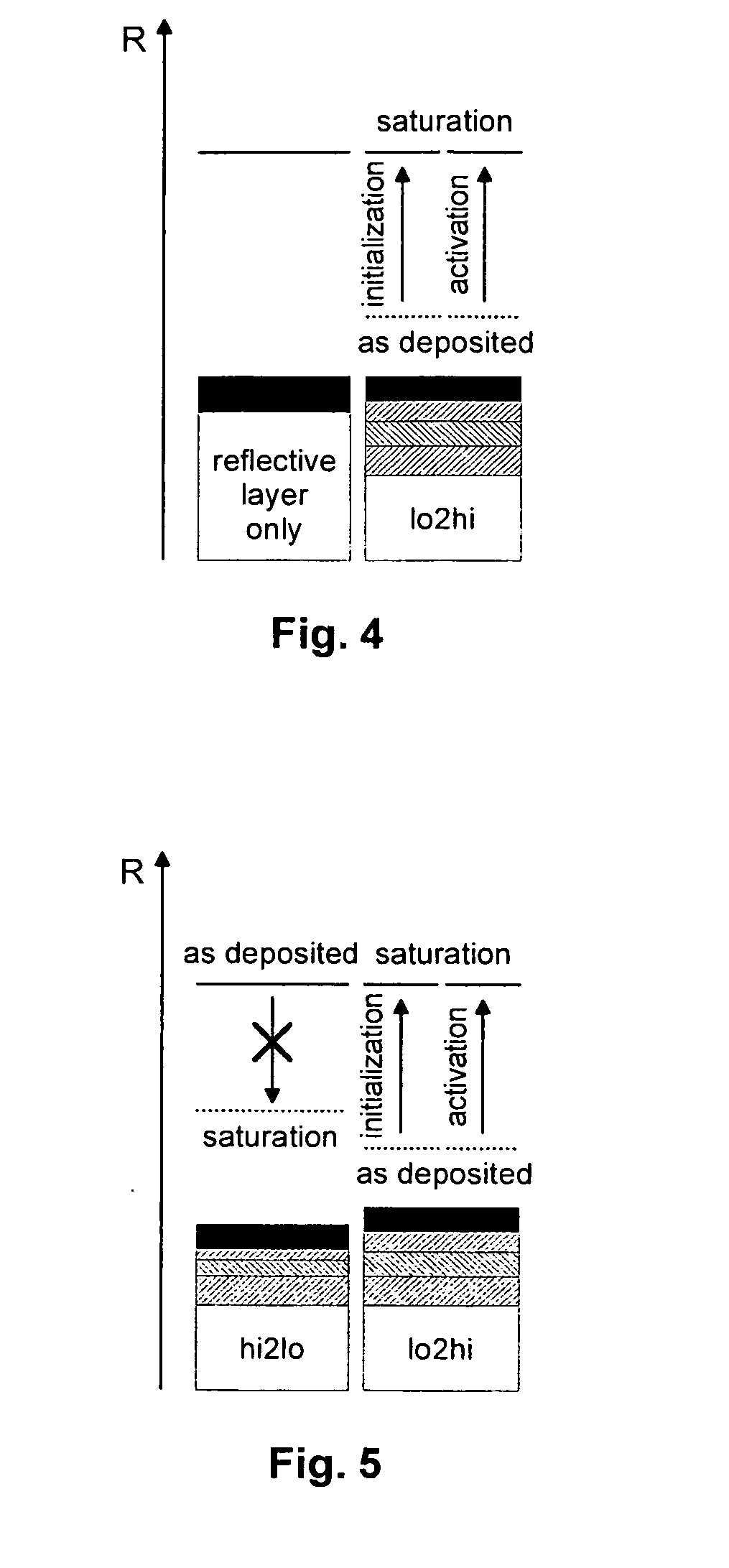
InactiveUS20100157769A1Improve securityPrevent counterfeitingMechanical record carriersRecord information storageComputer hardwareReflective layer
An optical recording medium to be used for a retail activation solution is proposed. The optical recording medium is a modified ROM disk that can only be played after the application of an activation process. For this purpose at least a part of a reflective layer of a read-only area of the optical recording medium is replaced by a light sensitive layer stack that changes its reflectivity upon illumination.Also proposed are a method for producing such an optical recording medium as well as methods and apparatuses for initializing and / or activating such an optical recording medium.
Owner:THOMSON LICENSING SA
Fingerprint-encryption-based electronic purse system payment method
ActiveCN104200363AEnsure safetyPrevent hackingDigital data authenticationProtocol authorisationData fileFingerprint
The invention is fingerprint-encryption-based electronic purse system payment method. The setting process of an electronic purse comprises a), connecting a device and running a program; b), setting character codes; c), collecting fingerprint information; d), encrypting the fingerprint information; e), encrypting the character codes; f), generating private data files; g), completing the setting process. The payment process of the electronic purse comprises 1), device connecting including connecting an USB (universal serial bus) flash disk with a PC (personal computer), running an electronic purse application in the USB flash disk to enter a transfer process; 2) code inputting; 3) code checking; 4) acquisition of the private data files; 5) payment initiating; 6) private key decryption; 7) transfer authorization; 8) transfer record storing; 9) payment completing. According to the fingerprint-encryption-based electronic purse system payment method, by setting the character codes and the fingerprint information, payment can be completed only when the fingerprint information input during the payment process and the setting process is from the same person, so that fund security can be guaranteed.
Owner:韩林
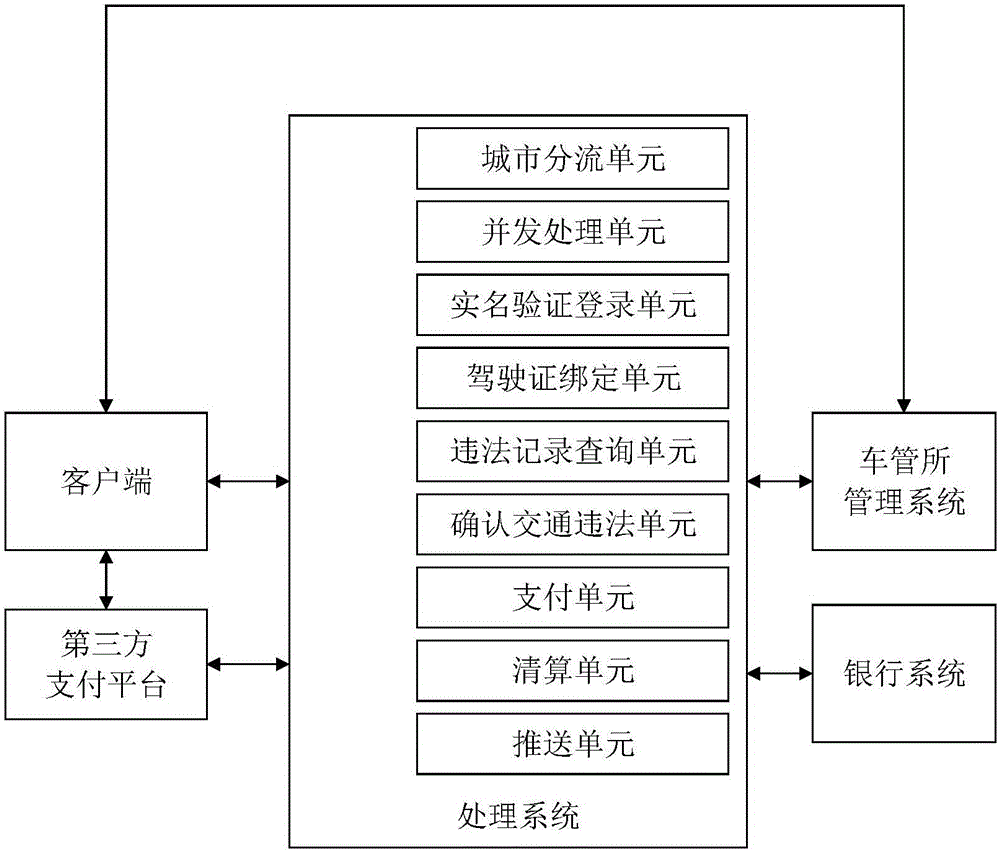
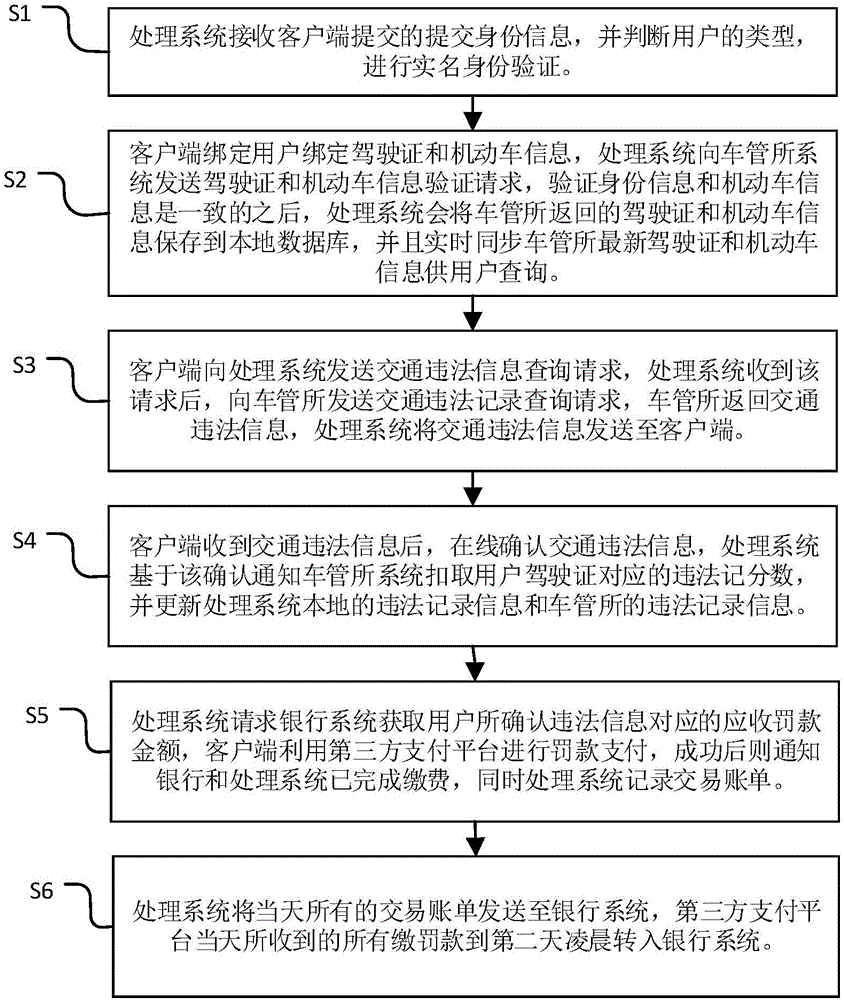
Traffic violation online processing system and method
InactiveCN106056512AEasy to useGuaranteed normal operationPayment architectureTransmissionThird partyTraffic violation
The invention provides a traffic violation online processing method. The method comprises the following steps: the step 1, a processing system receives a registration request submitted by a client side, and performs identity authentication; the step 2, the client side is bound with a user bound driving license and user bound motor vehicle information; the step 3, the client side sends a traffic offense information query request to the processing system; the step 4, after the client side receives traffic offense information, the traffic offense information is confirmed in an online manner; and the step 5, the processing system requests a bank system to obtain the amount of a receivable fine corresponding to the offense information confirmed by a user, and the client side performs fine payment by utilizing a third-party payment platform. The invention further correspondingly provides a traffic violation online processing system. A function that a traffic fine is handled through a third-party merchant platform is achieved.
Owner:广州大白互联网科技有限公司
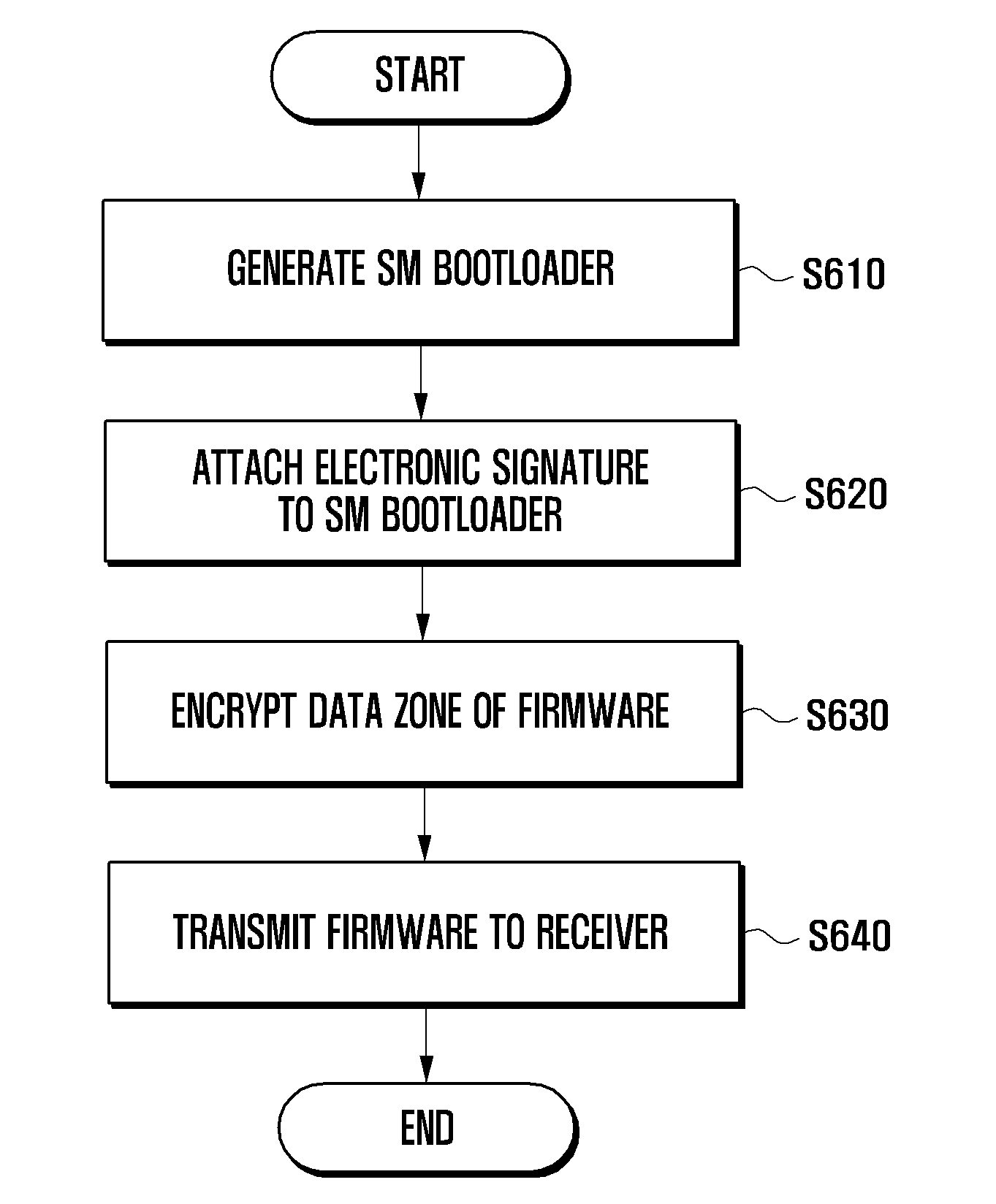
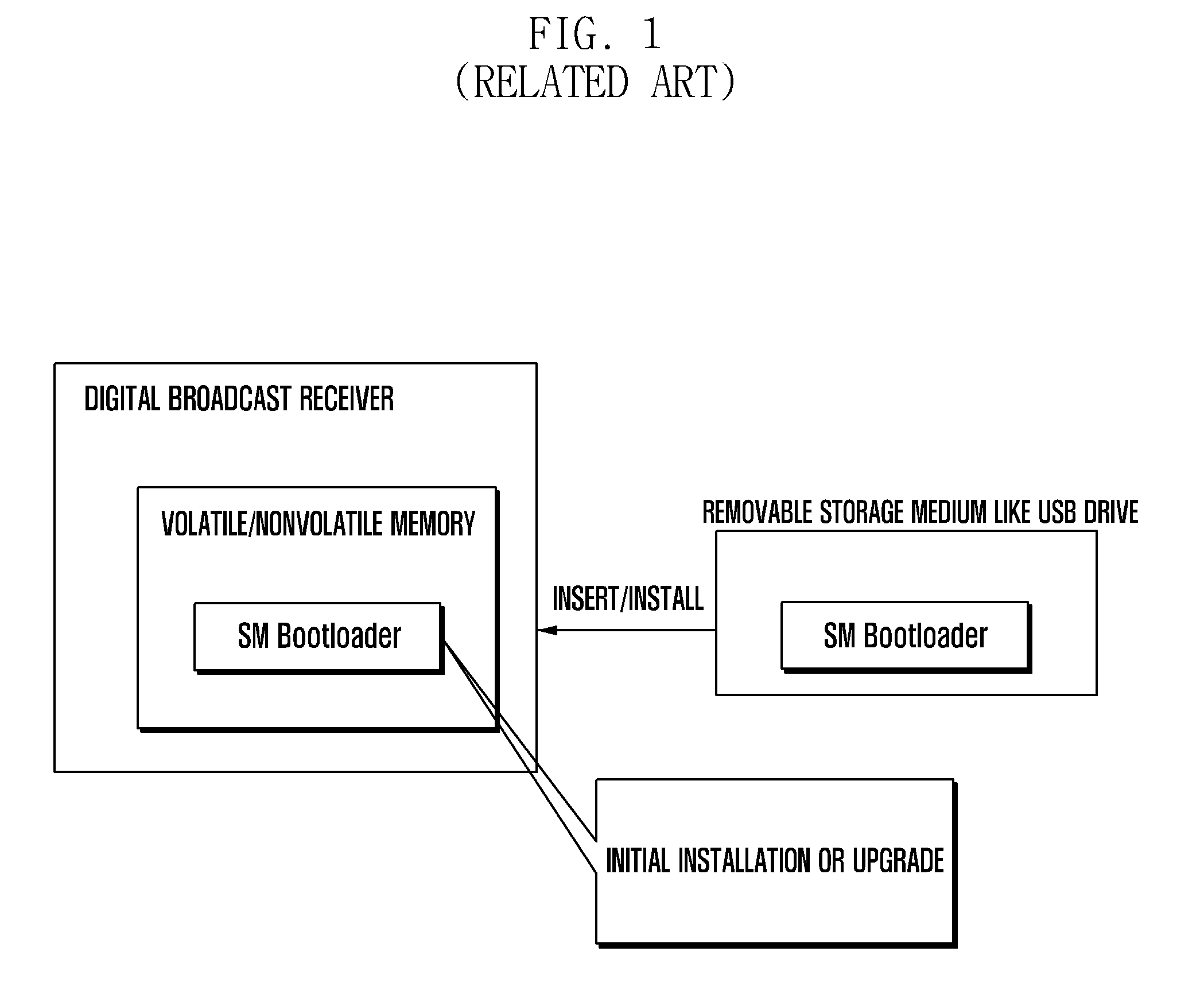
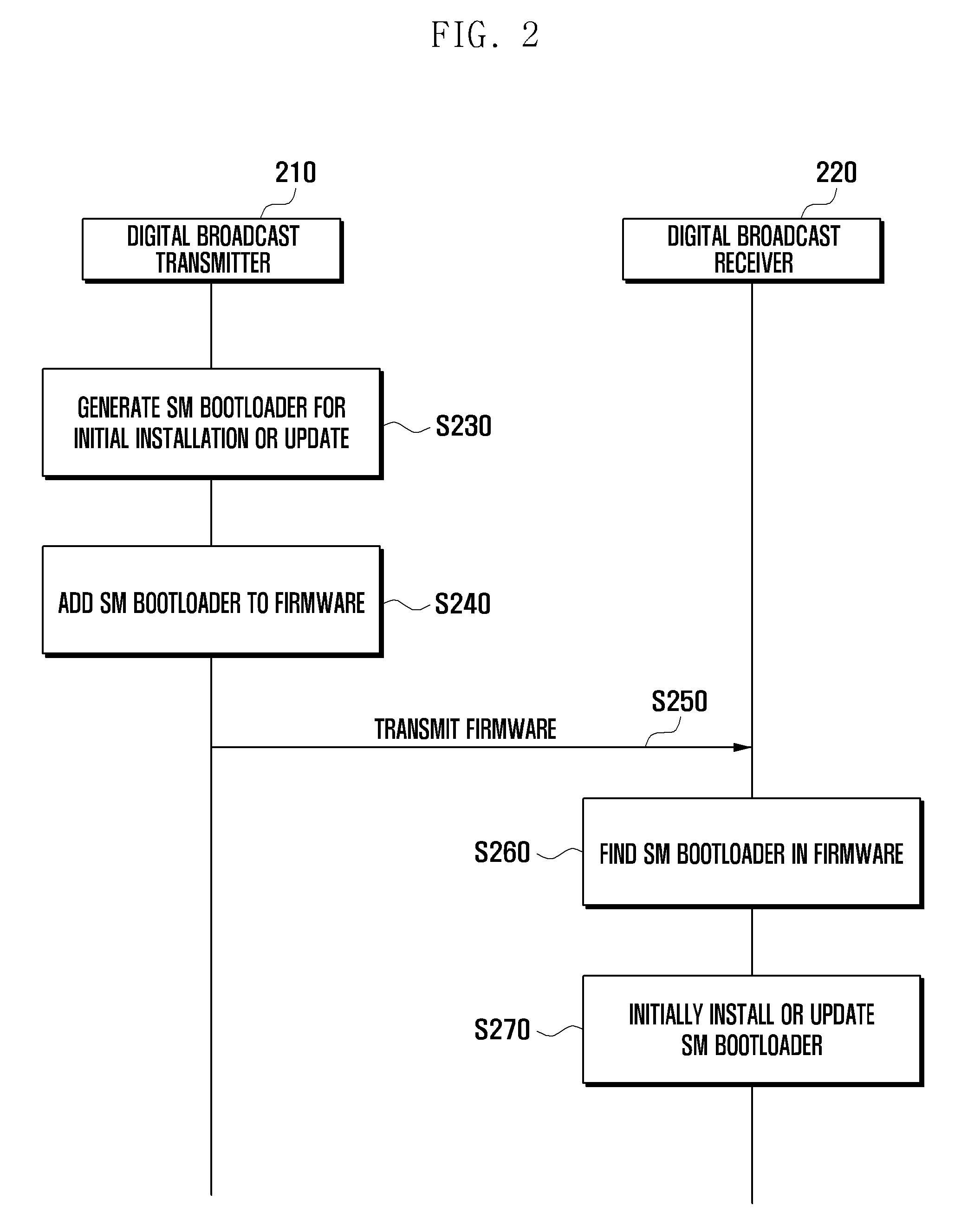
Method and apparatus for downloading secure micro bootloader of receiver in downloadable conditional access system
InactiveUS20110125995A1Simple to manufacturePrevent hackingSynchronising transmission/receiving encryption devicesUser identity/authority verificationDownloadable Conditional Access SystemTransmitter
A method and apparatus for downloading a Secure Micro (SM) bootloader of a receiver in a Downloadable Conditional Access System (DCAS) is provided. The method includes generating, by a transmitter, an SM bootloader for the receiver and adding the generated SM bootloader to firmware to be transferred to the receiver, sending, by the transmitter, the firmware to the receiver, and performing, by the receiver, registration by receiving the firmware, locating an SM bootloader in the firmware, and registering the located SM bootloader. In the DCAS, a receiver may download or install an SM bootloader through an online or offline procedure.
Owner:SAMSUNG ELECTRONICS CO LTD
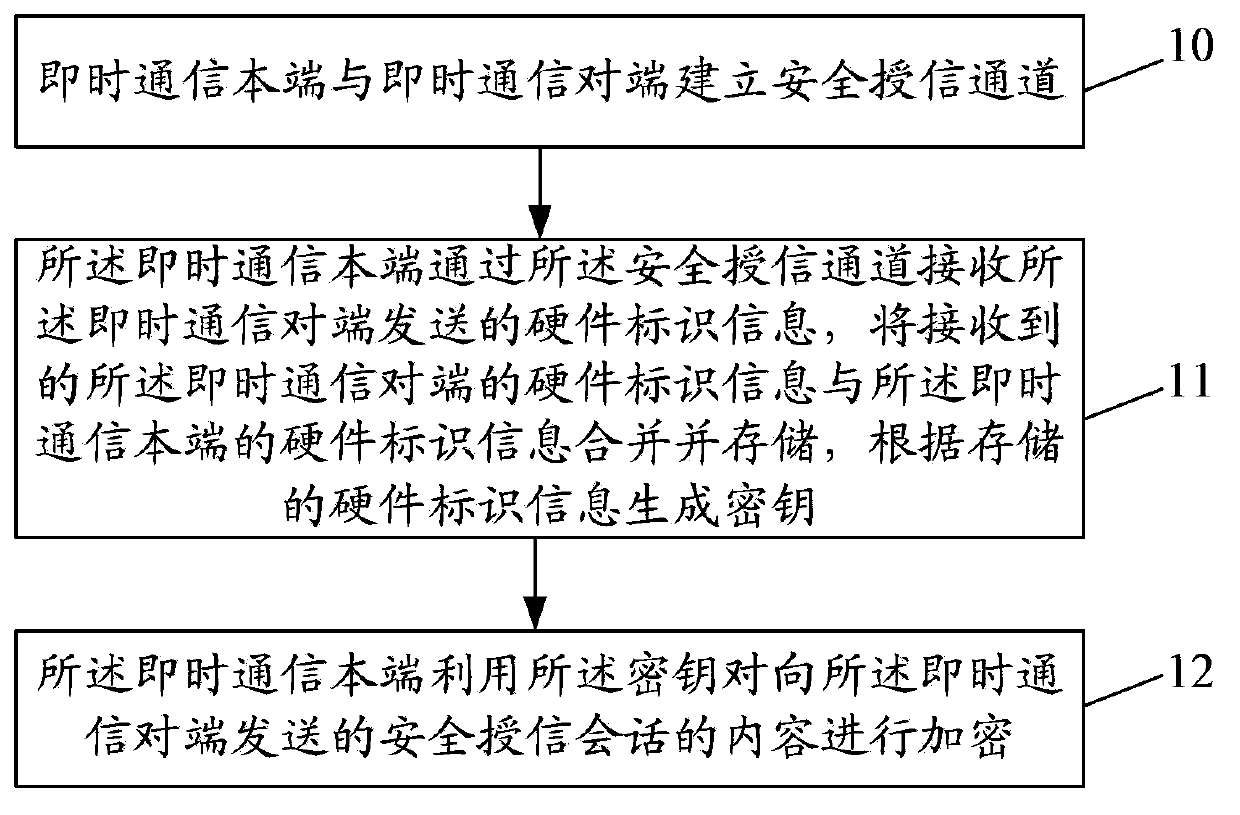
Method and device for instant messaging
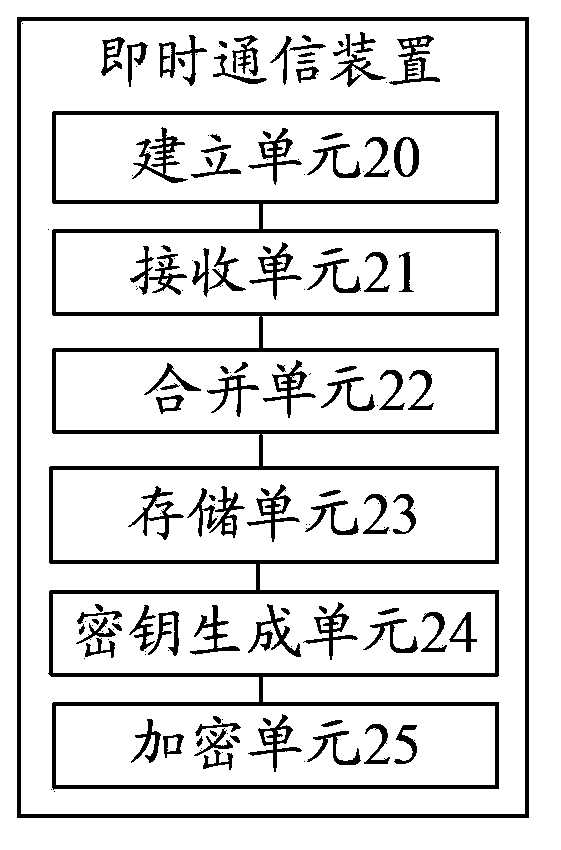
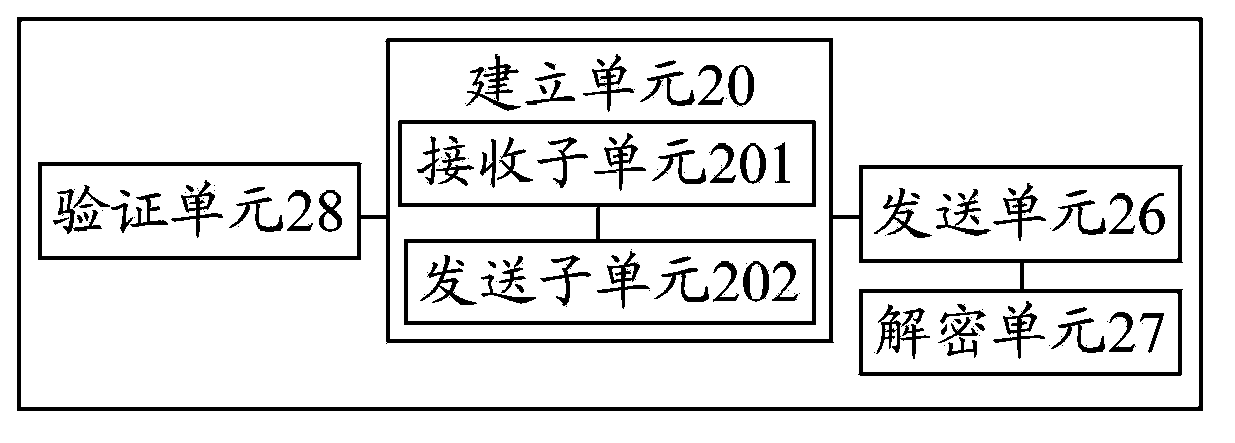
ActiveCN103973543AAvoid security issuesNot easy to be stolenData switching networksTelecommunications equipmentInstant messaging
The invention discloses a method for instant messaging. The method includes establishing a safe credit channel between an instant messaging home terminal and an instant messaging opposite terminal, subjecting the instant messaging home terminal to receiving a hardware identification information sent by the instant messaging opposite terminal through the safe credit channel, combining and storing the received hardware identification information of the instant messaging opposite terminal with hardware identification information of the instant messaging home terminal and producing a key according to the stored hardware identification information, and subjecting the instant messaging home terminal to encrypting content of a safe credit conversation sent by the instant messaging opposite terminal by the aid of the key. The invention further discloses a device for instant messaging. The method and the device for the instant messaging are safe in instant messaging.
Owner:CHINA MOBILE COMM GRP CO LTD
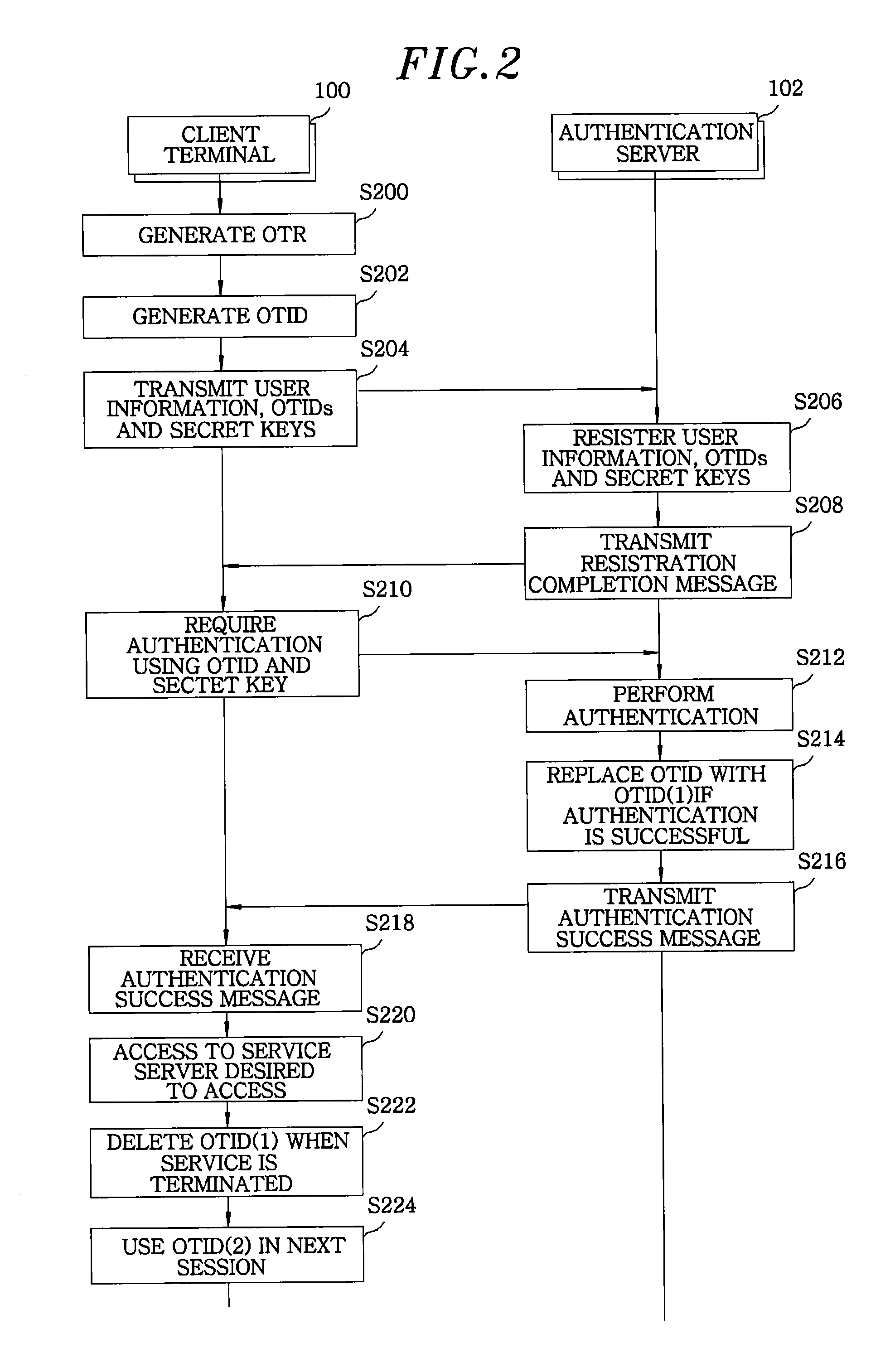
System and method for user authentication using one-time identification
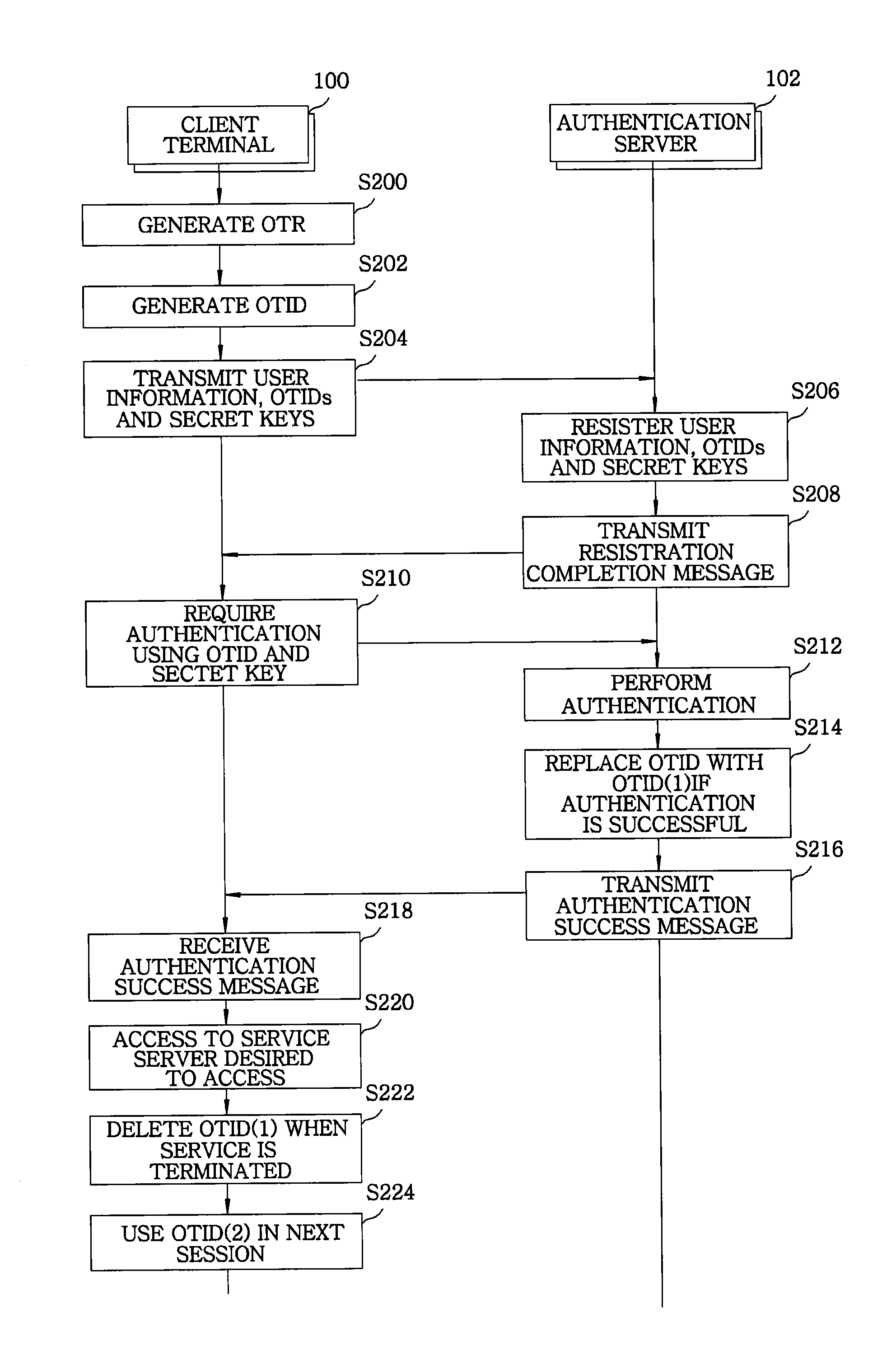
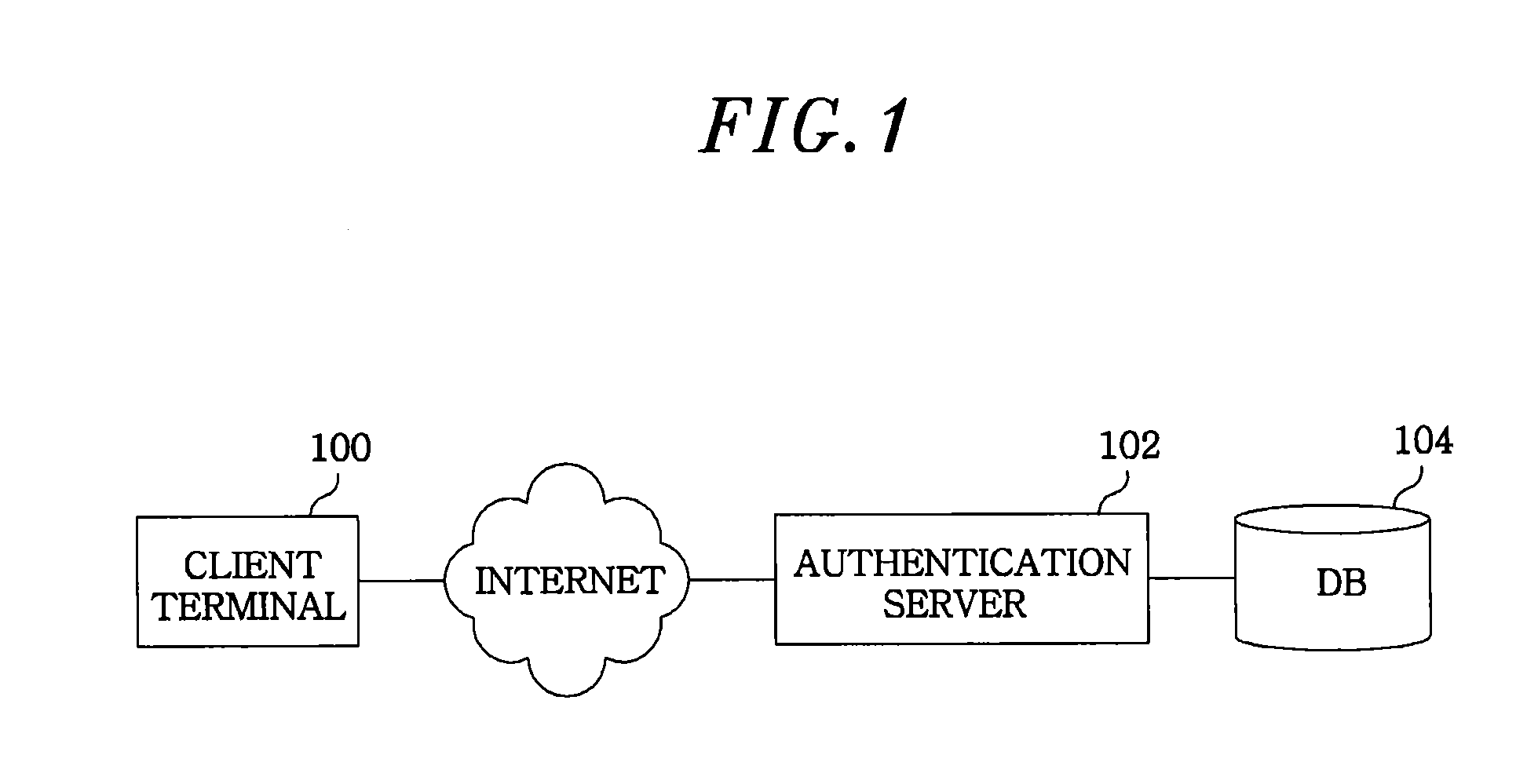
InactiveUS20130152179A1Validity time is shortenedObviates advantageDigital data processing detailsUser identity/authority verificationUser authenticationAuthentication server
A system for user authentication using OTIDs (one-time identifications), includes a client terminal configured to generate n number of OTIDs which is used in the user authentication, and sequentially select one of the generated n number of OTIDs to use the selected OTID as a user identification in each authentification session. Further, the system includes an authentication server configured to receive the generated n number of OTIDs from the client terminal to store same, when the one OTID selected from the n number of OTID and a secret key are transmitted, inquire the OTID in a DB (database), and determine whether a secret key which is associated with the inquired OTID and stored in the DB and the received secret key is matched to performing the user authentication.
Owner:ELECTRONICS & TELECOMM RES INST
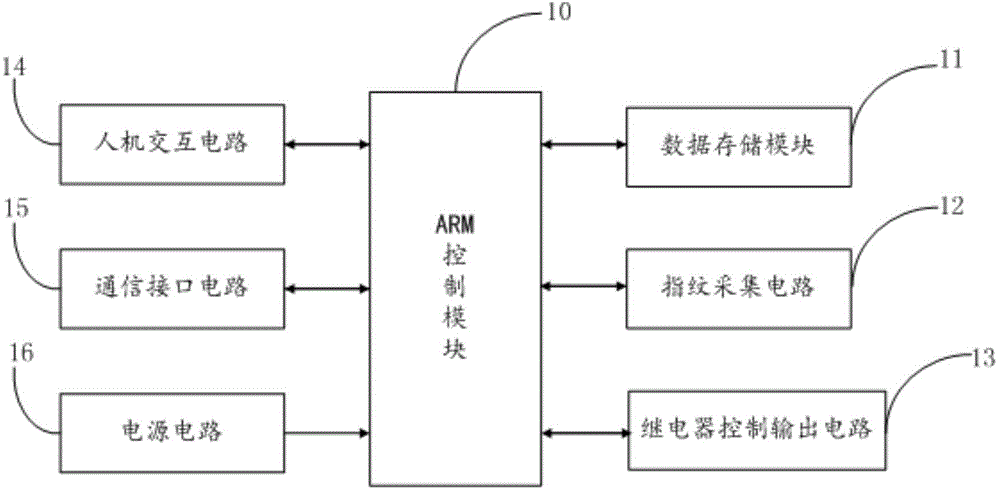
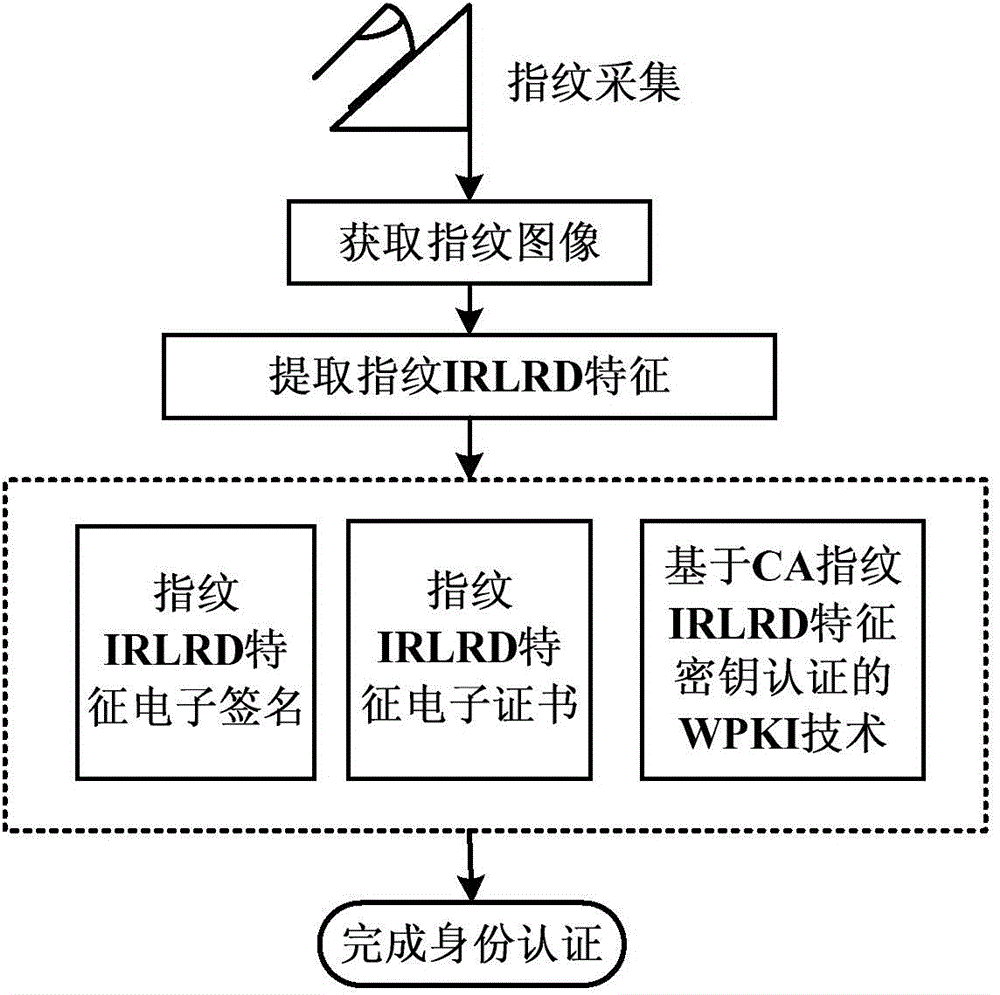
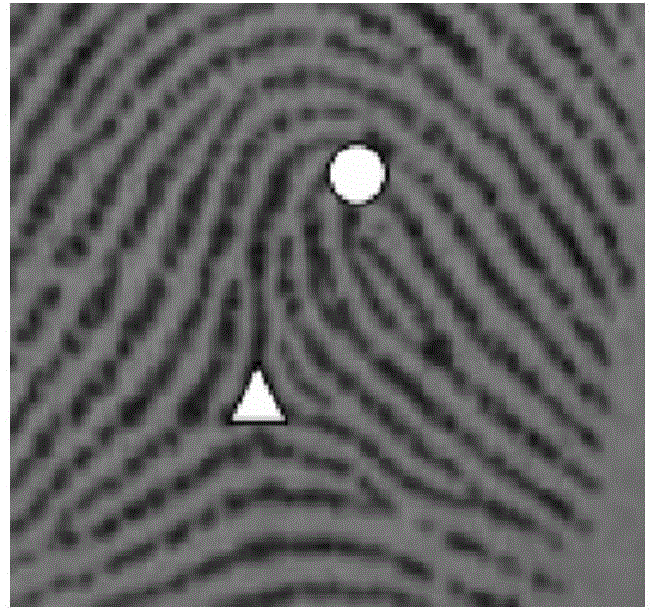
Fingerprint IRLRD characteristic encryption method, and mobile payment system and method based on encryption method
InactiveCN104899737ASolve the problem of self-certificationEnsure safetyProtocol authorisationCommunication interfaceMobile payment
The present invention discloses a fingerprint IRLRD characteristic encryption method, a mobile payment system and a mobile payment method based on the fingerprint IRLRD characteristic encryption method. The mobile payment system comprises an ARM control module, a data storage module, a fingerprint collection circuit, a human-machine interaction circuit, a communication interface circuit, a relay control output circuit, and a power supply circuit for supplying power to all the circuits. The ARM control module implements fingerprint IRLRD characteristic encrypted identity authentication by encrypting an ARM fingerprint IRLRD characteristic. Compared with the prior art, the invention has the following advantages: the mobile payment system obtains a user fingerprint image and extracts a fingerprint IRLRD characteristic as a key; implements secure transaction of mobile payment by multiple identity authentication protection; prevents payment information from being attacked and broken by a hacker; stops a security crisis that payment information is tampered, leaked or falsified during mobile payment, and ensures orderly proceeding of the mobile payment.
Owner:ANHUI XINHUA UNIV
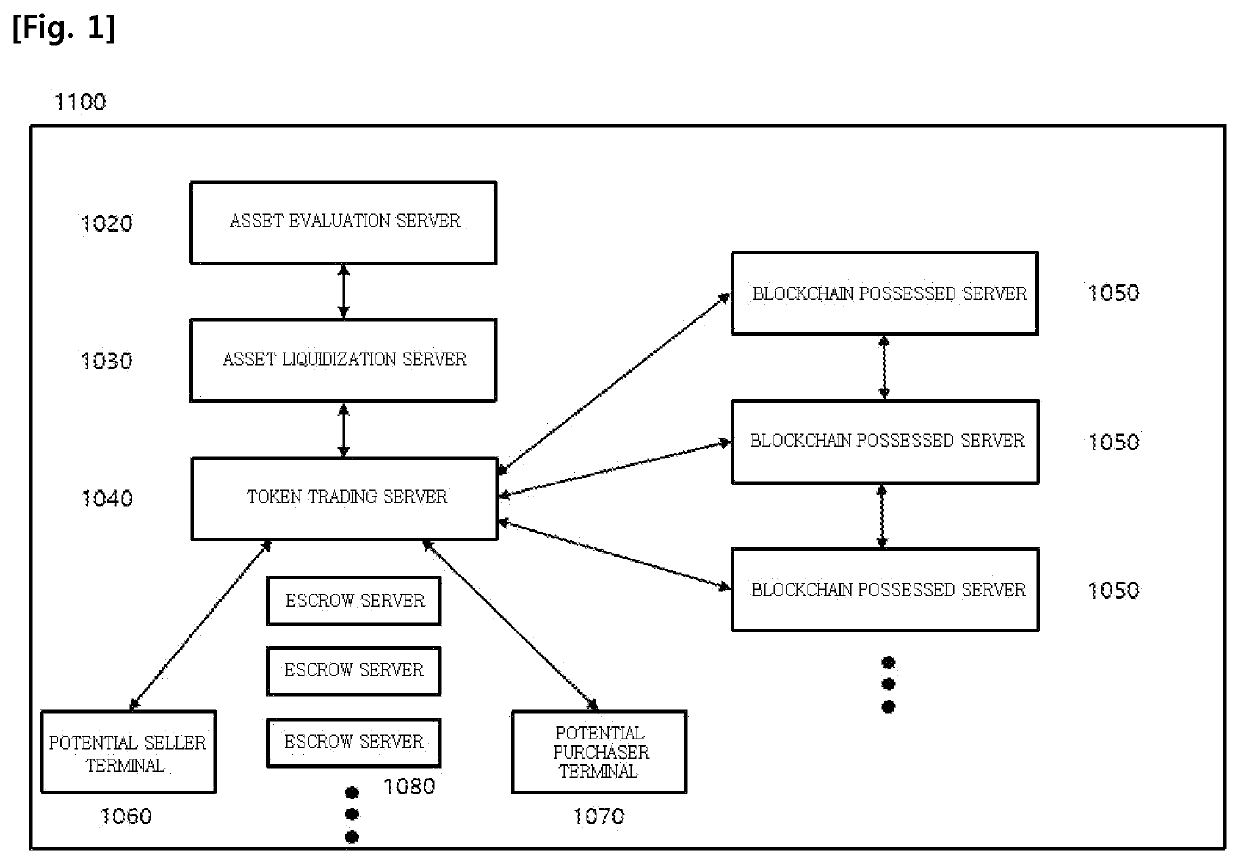
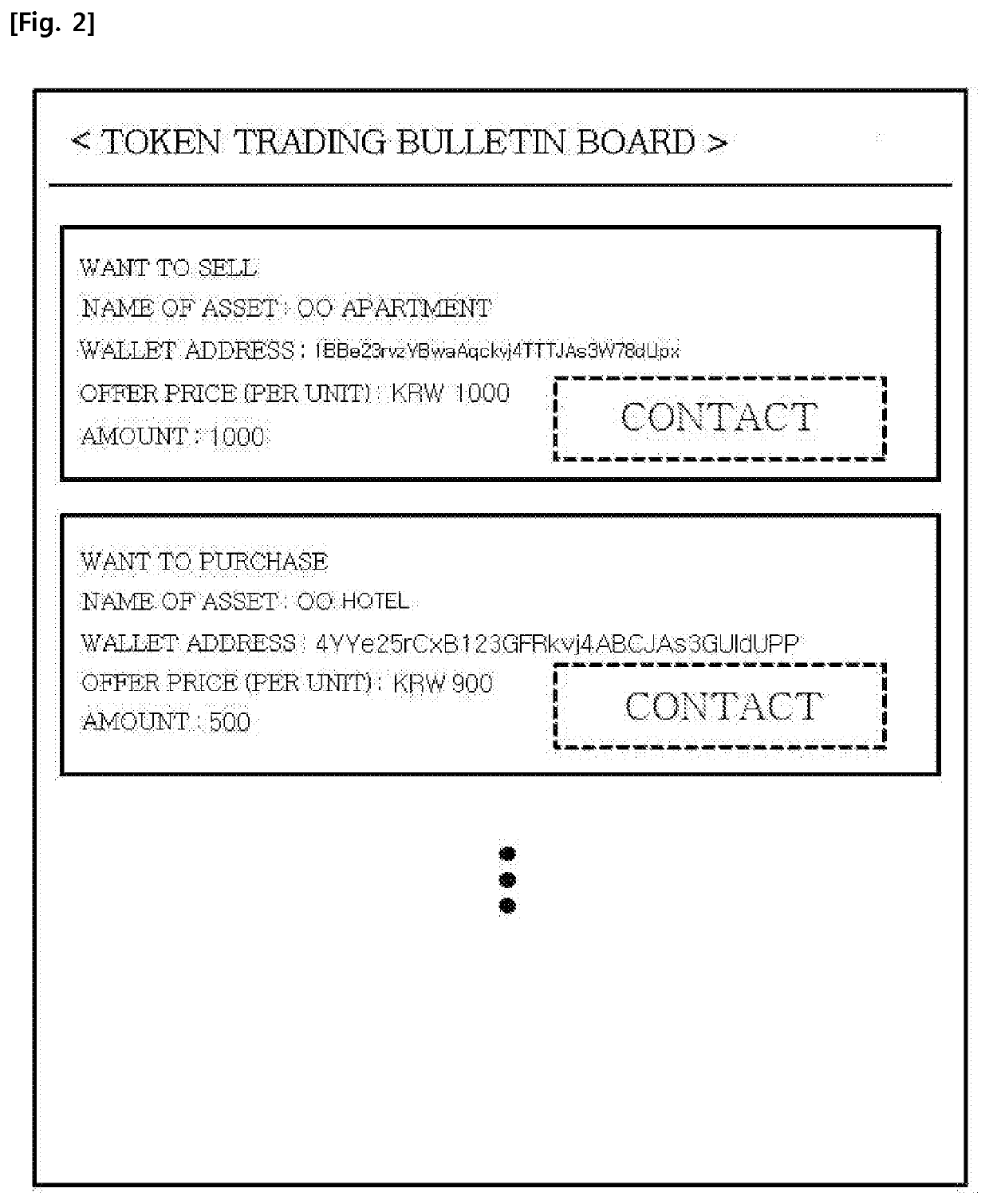
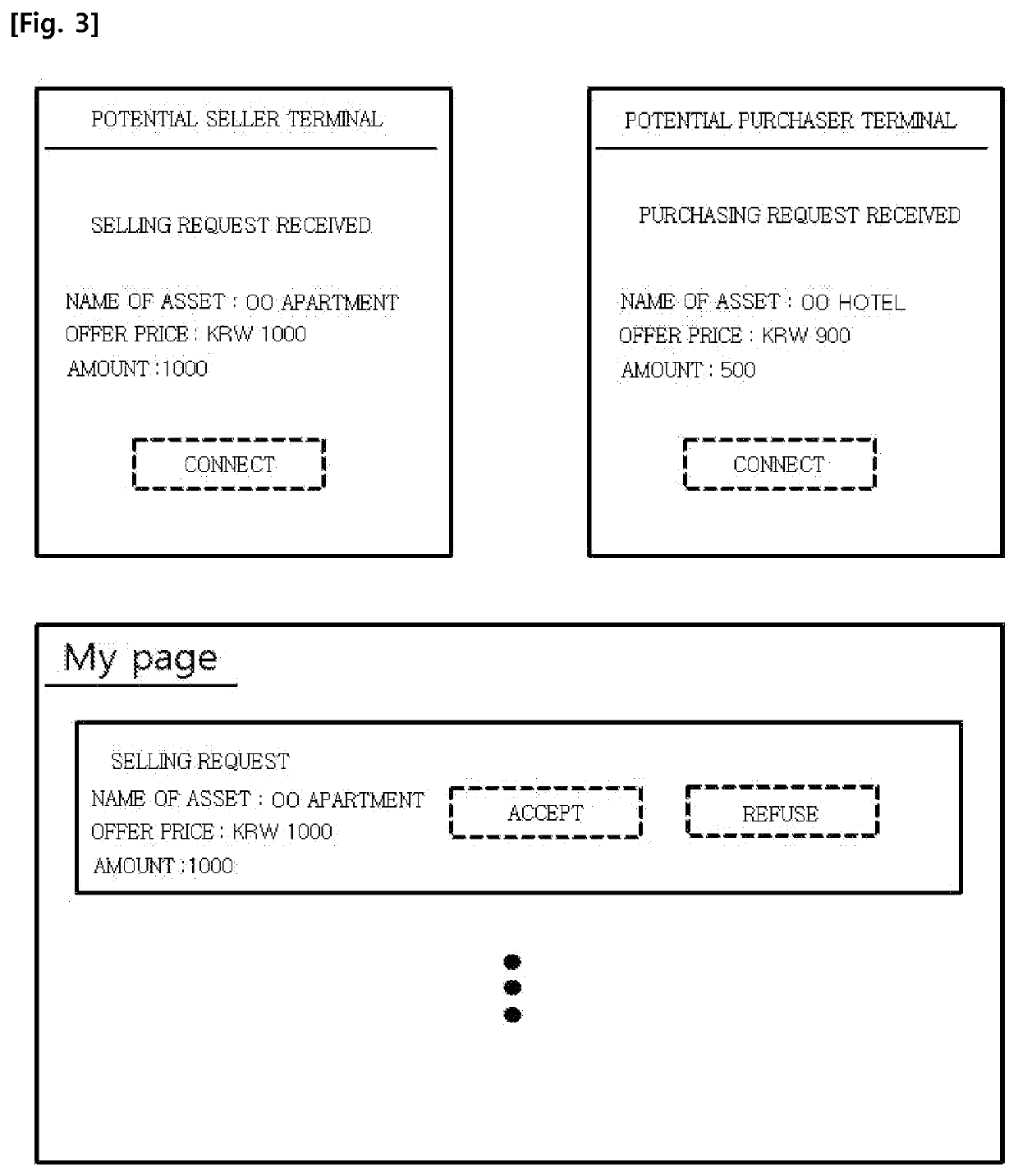
System and method for trading assets among parties through tokenization of assets
InactiveUS20200051166A1Ensure reliabilityPrevent hackingFinanceEncryption apparatus with shift registers/memoriesBlockchainInternet privacy
The present disclosure relates to an assets trading system among parties through tokenization of assets including an asset evaluation server for evaluating a value of an asset and computing an evaluated amount of the asset; an asset liquidization server for issuing a token corresponding to the computed evaluated amount, and managing rights and dividends regarding the issued token; a token trading bulletin board providing a token trading bulletin board where a seller intending to sell the issued token and a purchaser intending to purchase the issued token can directly trade with each other; an escrow server for mediating sales of the token between the potential seller and the potential purchaser; and a blockchain possessed server having a blockchain for certifying trading of the token and where trading information regarding the certified trade is recorded.
Owner:TICKETSOCKET KOREA CO LTD
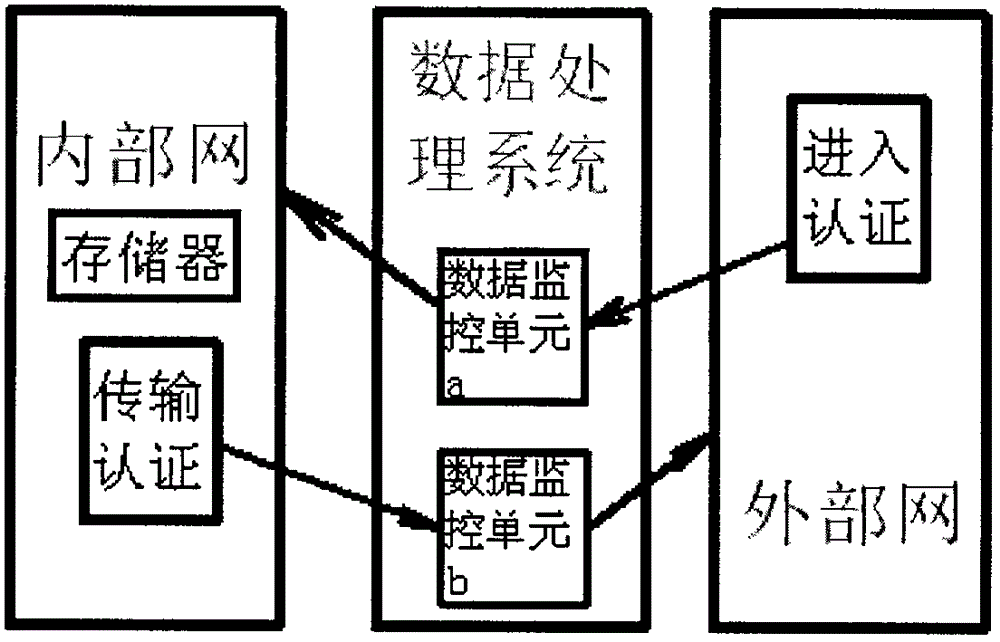
Network isolation system
InactiveCN102752286AAchieve security isolationPrevent infiltrationTransmissionData processing systemNetwork isolation
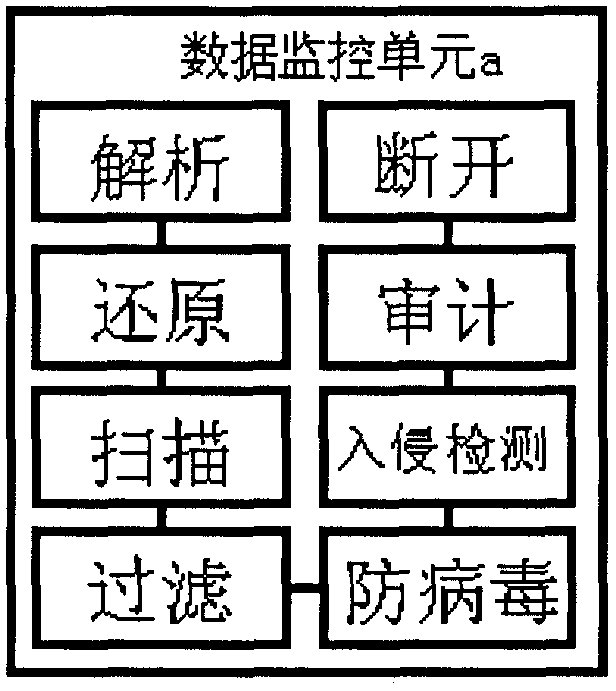
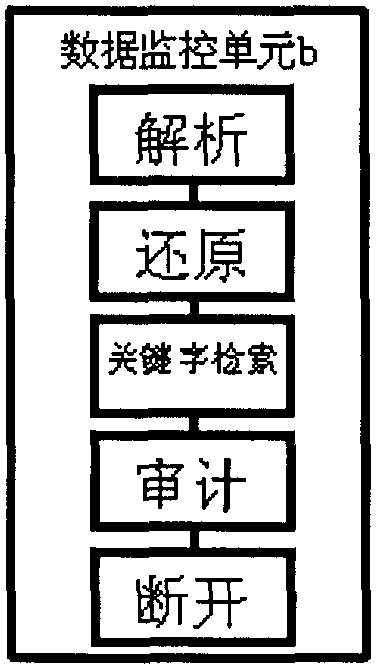
The invention discloses a network isolation system. The network isolation system comprises a data processing system used for transmitting data between an internal network and an external network, wherein the internal network is provided with a memory and transmission certificate; the external network is provided with access certificate; the data processing system consists of a data monitoring unit a and a data monitoring unit b; the transmission certificate performs one-way data transmission with the data monitoring unit b and the external network in sequence; the access certificate performs one-way data transmission with the data monitoring unit a and the internal network in sequence; the information of an internal network user is certificated by utilizing the transmission certificate; the information of an external network user is certificated by utilizing the access certificate; the memory of the internal network automatically records the information such as transmission data and user; a series of safe processing is performed by utilizing the data monitoring unit a and the data monitoring unit b; the potential safety hazard such as hacker attack, infiltration of malice code and virus and information leakage can be prevented effectively; and the safe isolation and the safe information exchange of the internal network and the external network are realized.
Owner:DONGGUAN BOSHENG ELECTRONICS TECH
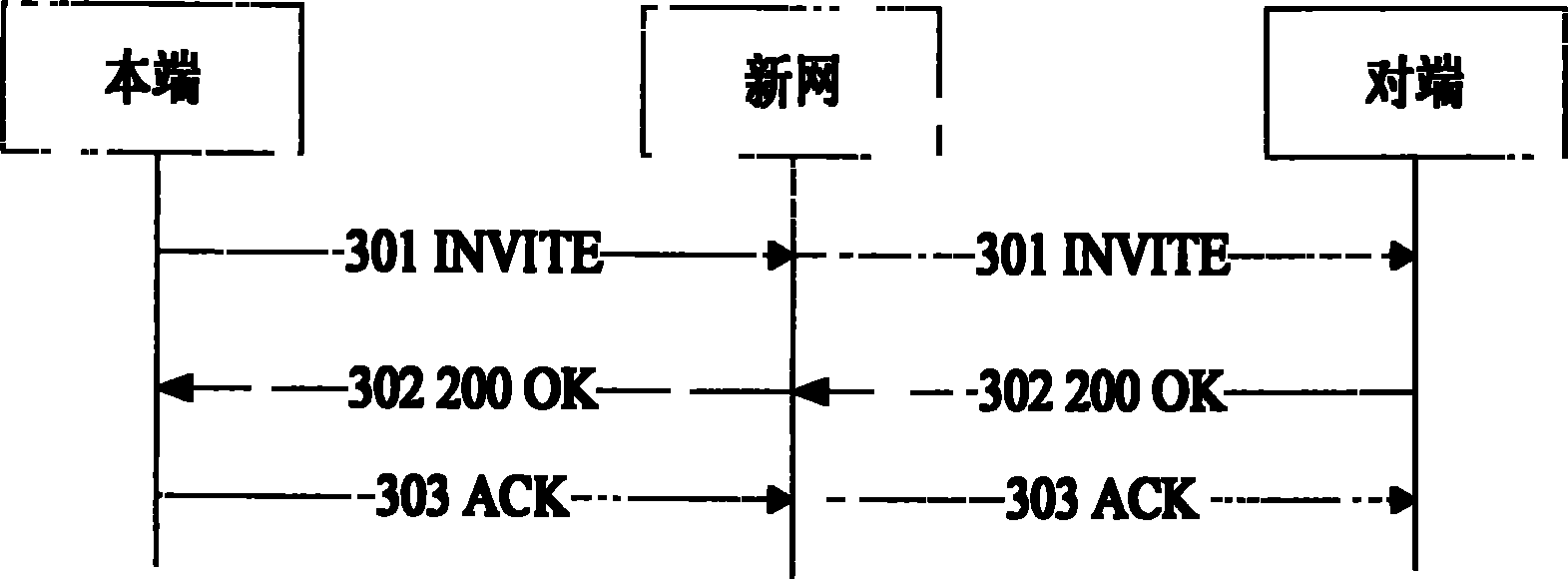
End-to-end call realizing method, end-to-end call terminal and system
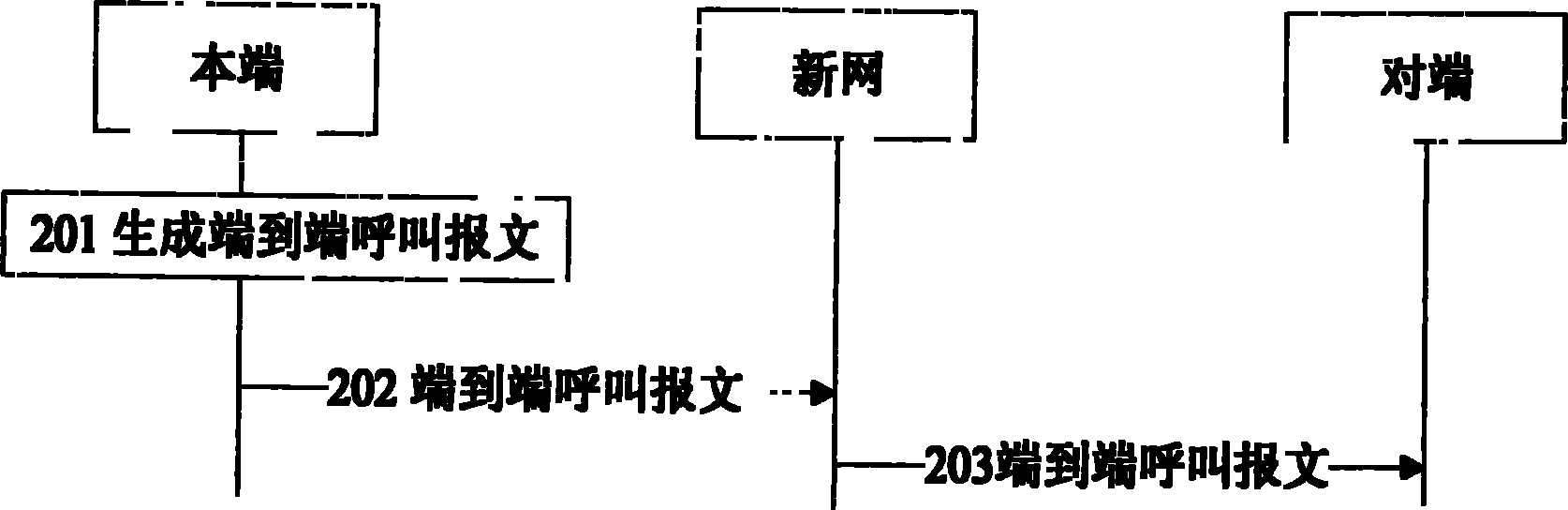
ActiveCN102035813AAvoid reliability risks of single point of failurePrevent hackingSpecial service provision for substationUser identity/authority verificationTelecommunicationsComputer terminal
The invention discloses an end-to-end call realizing method, which comprises an end-to-end call establishment flow, wherein the end-to-end call establishment flow does not need an end-to-end call service server and comprises the steps that: a local end sends a call establishment request after receiving input call initiating operation, wherein source and target addresses are identifiers of the local end and an opposite end, and a new network forwards the call establishment request to the opposite end in a routing way according to the mapping relationship between the identifiers and a route identifier respectively; and the opposite end receives the call establishment request, relies a call establishment response, and the new network forwards the call establishment response to the local end in a routing way according to the mapping relationship between the identifiers and the route identifier, wherein the source and target addresses are the identifiers of the opposite end and the local end respectively. The method, terminal and system can realize the end-to-end call and simplify the flow and system of the end-to-end call.
Owner:ZTE CORP
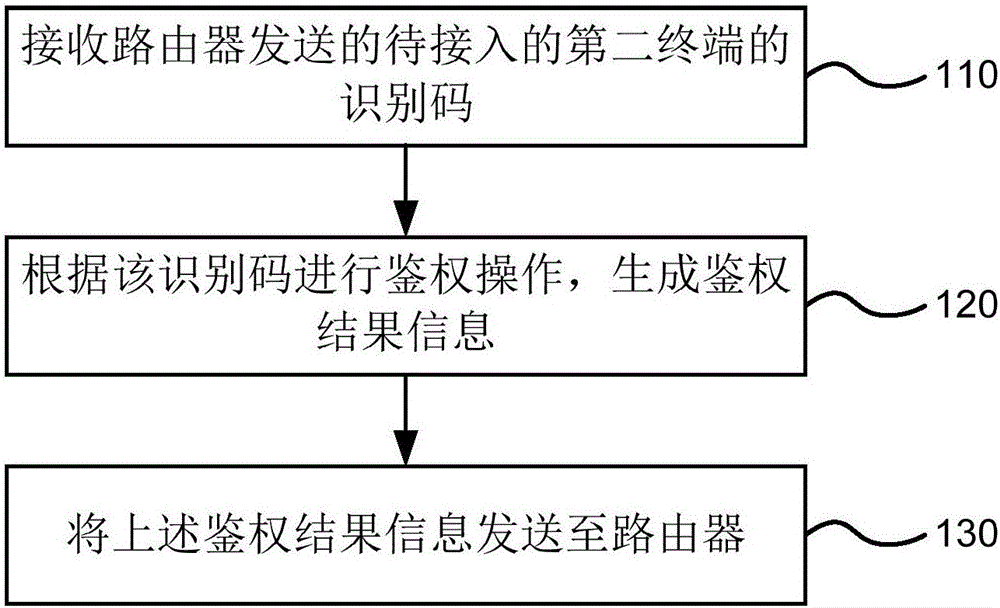
WIFI connection method, terminal and router
InactiveCN105848148AAvoid WIFI StealingProtect network bandwidth resourcesNetwork topologiesConnection managementUser authenticationPassword
An embodiment of the invention provides a WIFI connection method, a terminal and a router and relates to the field of communication technology. The method is applied to a first terminal and includes receiving an identification code of a to-be-accessed second terminal sent by the router; performing authentication operation according to the identification code and generating authentication result information; sending the authentication result information to the router. According to the embodiment of the invention, a new user authentication process is transferred to the terminal having administrator authority from the router, so that illegal WIFI connection caused by password divulgence can be avoided, network bandwidth resources can be protected, normal network use is ensured and user experience is improved.
Owner:LETV HLDG BEIJING CO LTD +1
Preventive intrusion device and method for mobile devices
ActiveUS8997231B2Improve securityPrevent hackingMemory loss protectionUnauthorized memory use protectionTraffic capacityNetwork packet
A method for providing an intrusion prevention system to prevent hacking into files located on enterprise users' endpoint devices functioning as mobile computing platforms. The method includes filtering low-level network packets for each of a plurality of received network packets, offloading the received packets to an inspecting processing module and marking suspicious packets based on at least one of a header and pattern of each of said received packets. The method also includes taking preventive measures by the system to ensure protection of the device and network, taking active steps by the system to block suspicious traffic and disconnecting the current connection by the system, when it detects suspicious traffic.
Owner:ZIMPERIUM INC
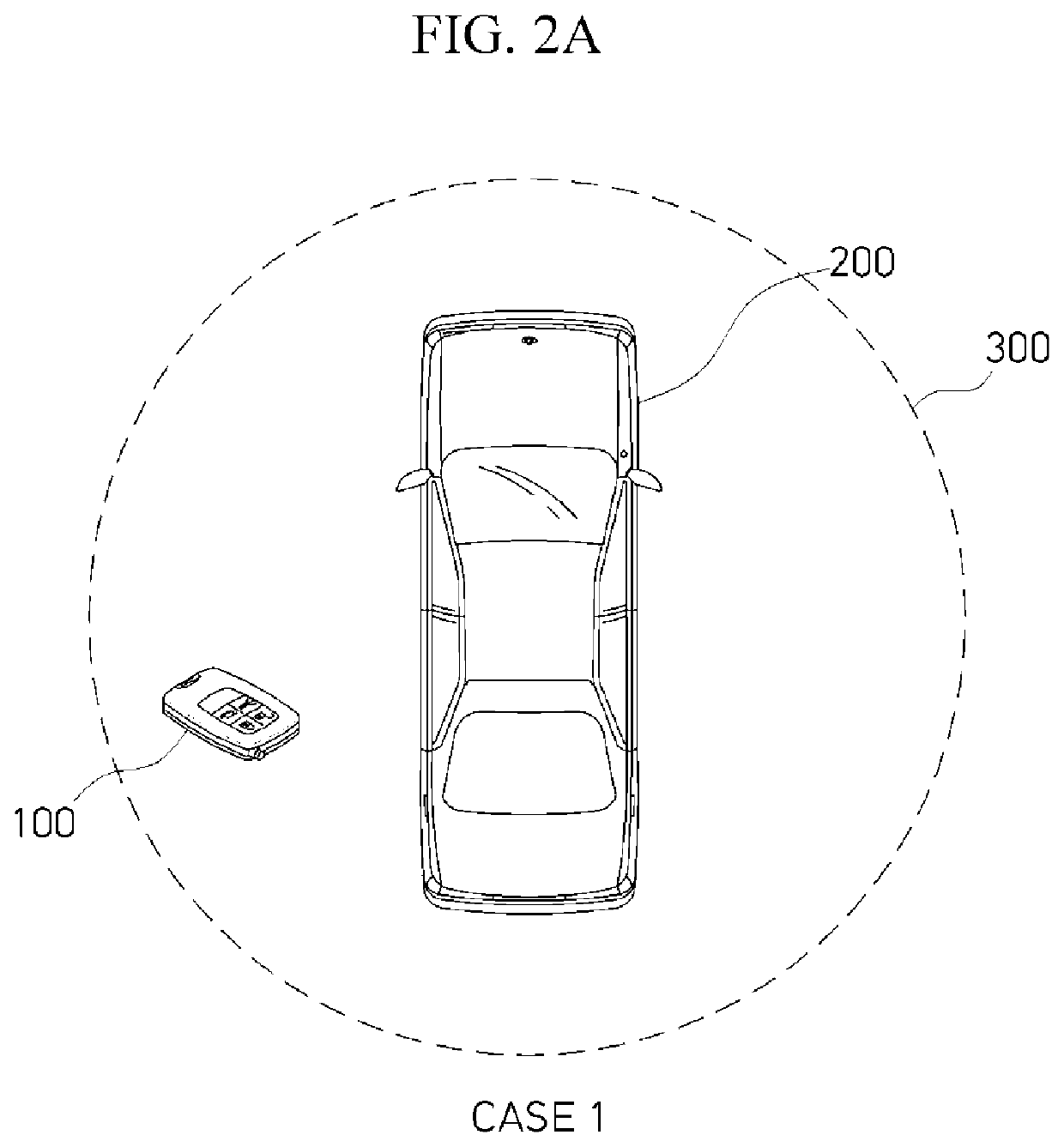
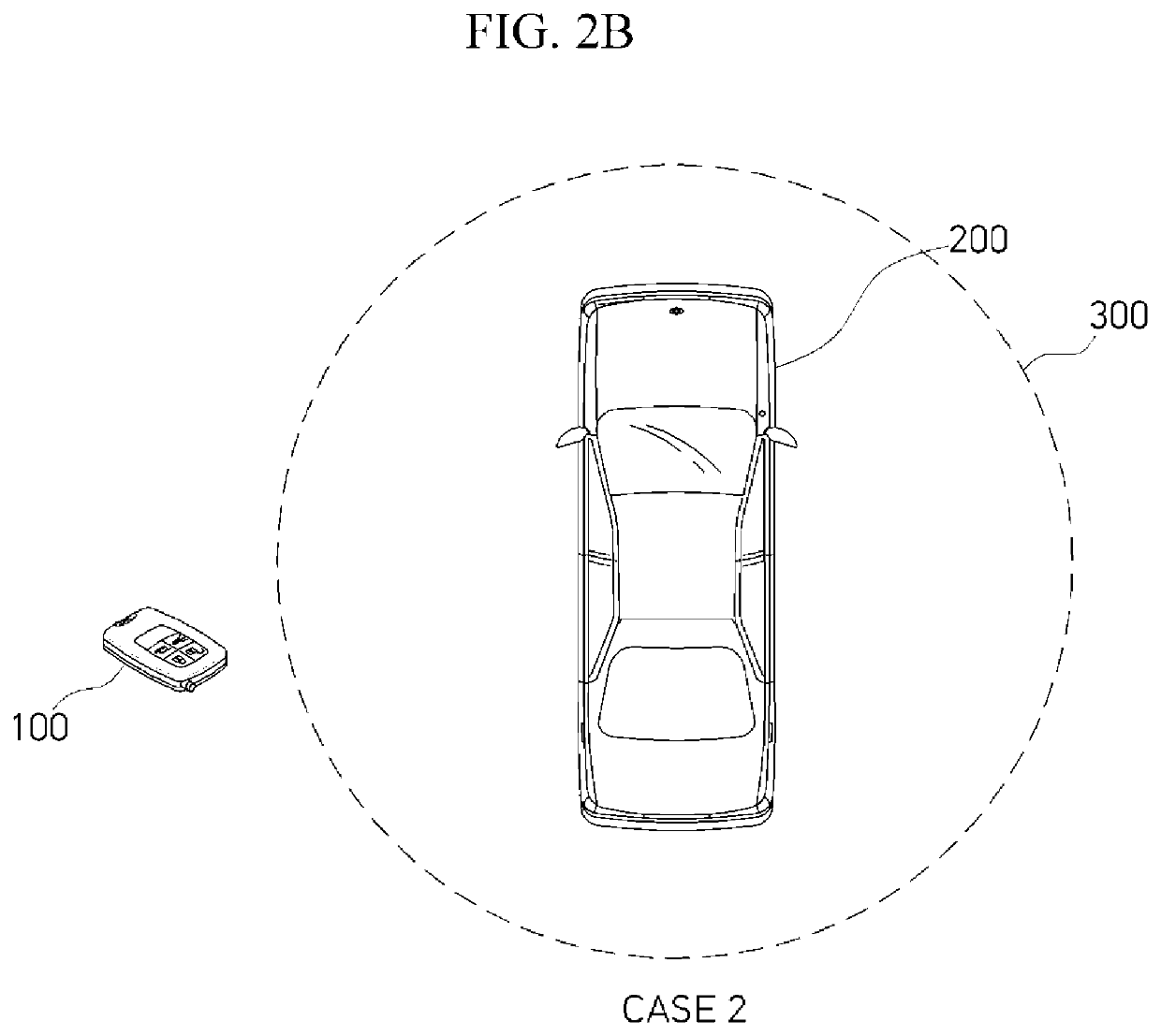
Method of controlling smart key
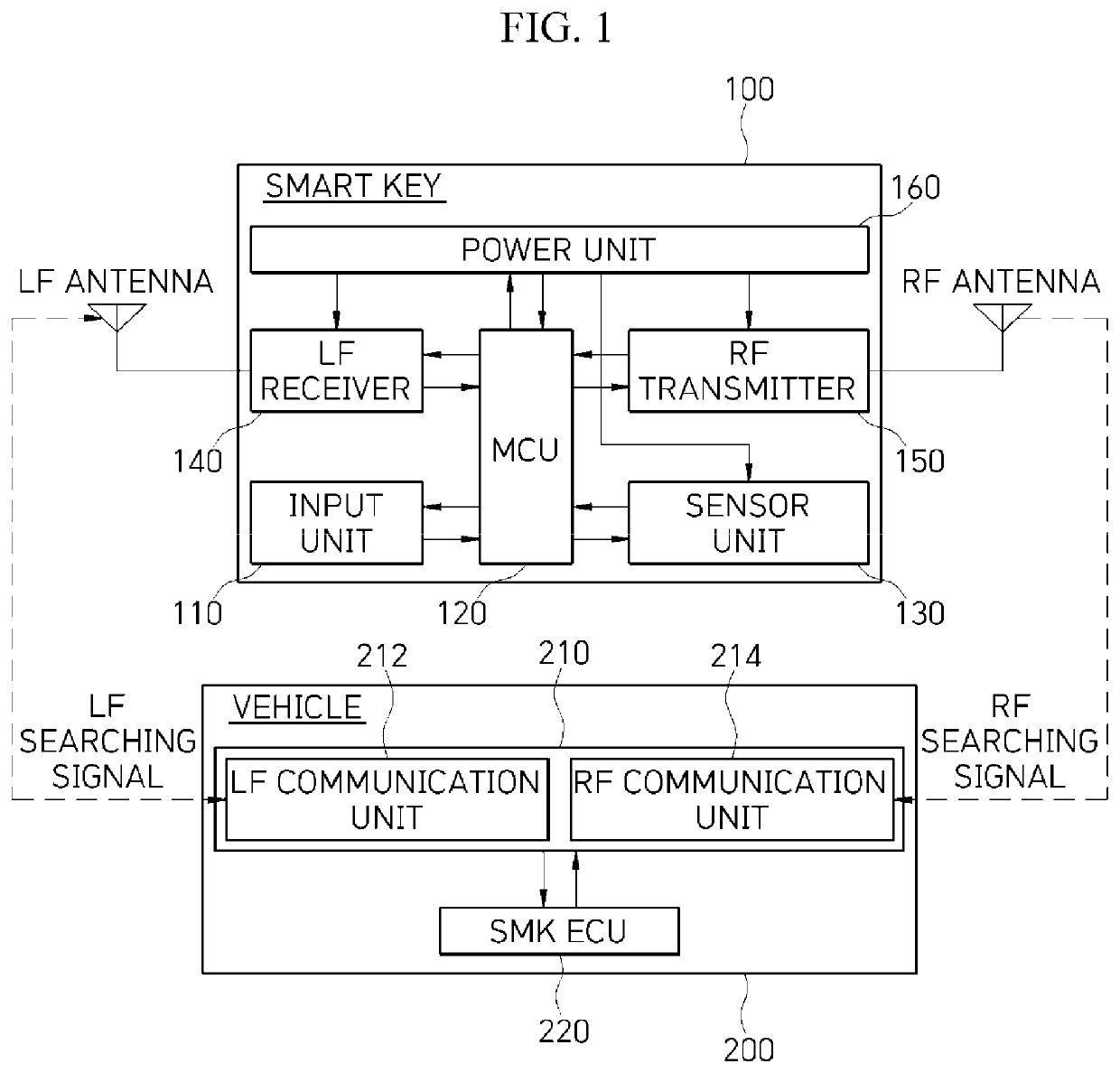
ActiveUS20200339066A1Maximize battery efficiencyPrevent hackingParticular environment based servicesAnti-theft devicesControl engineeringControl cell
A method of controlling a smart key, including a low frequency (LF) receiver receiving an LF signal from a vehicle, a radio frequency (RF) transmitter transmitting an RF signal to the vehicle in response to the LF signal, a sensor unit sensing a motion, and a micro control unit controlling operations of the LF receiver, the RF transmitter, and the sensor unit, includes receiving, by the LF receiver, the LF signal from the vehicle and controlling, by the micro control unit, a turn-on / off operation of each of the LF receiver, the RF transmitter, and the sensor unit on the basis of the received LF signal.
Owner:HYUNDAI MOBIS CO LTD
Smart home early warning system, method and device
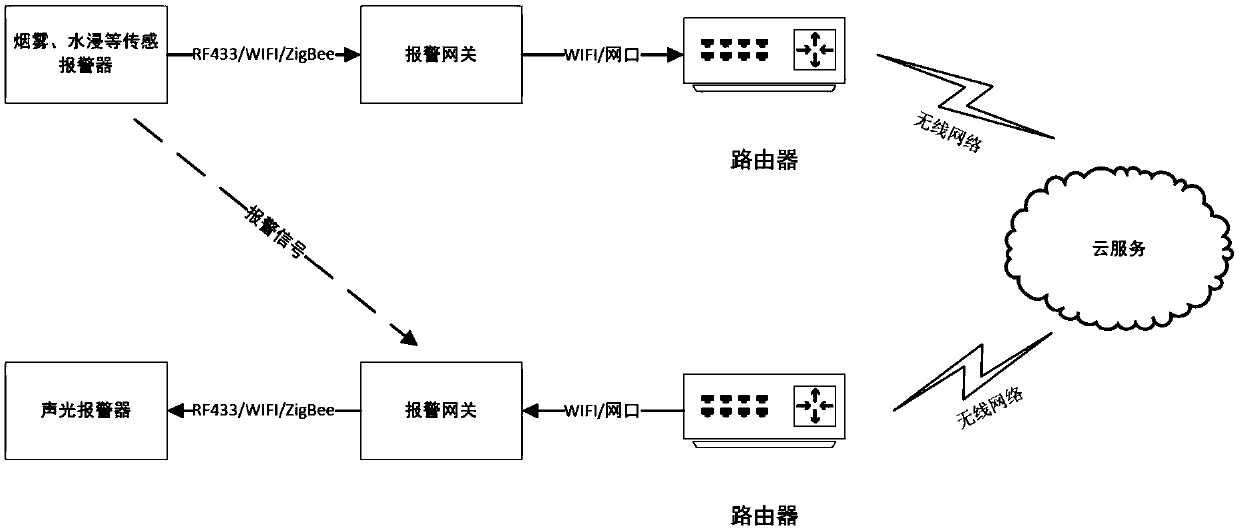
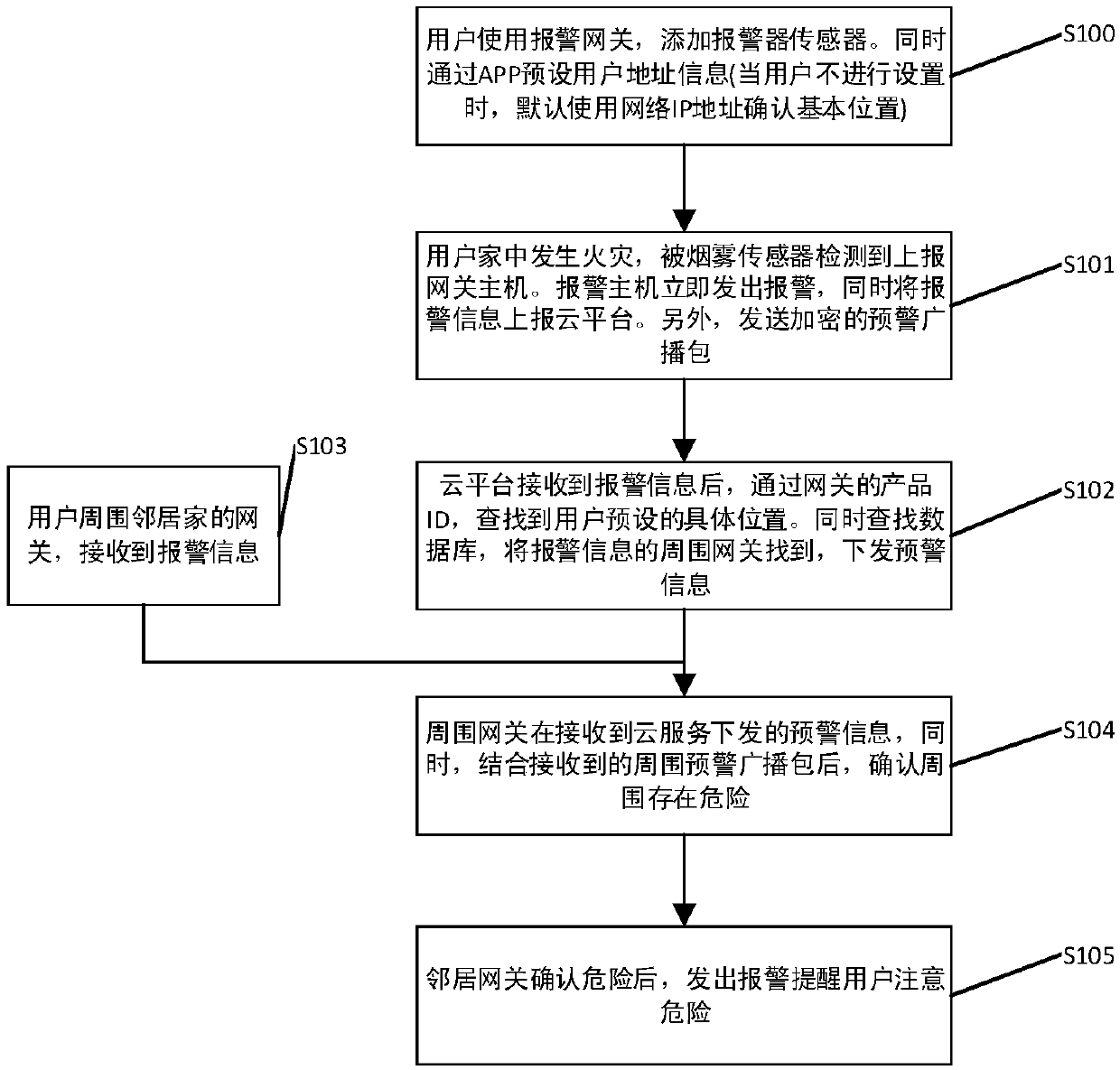
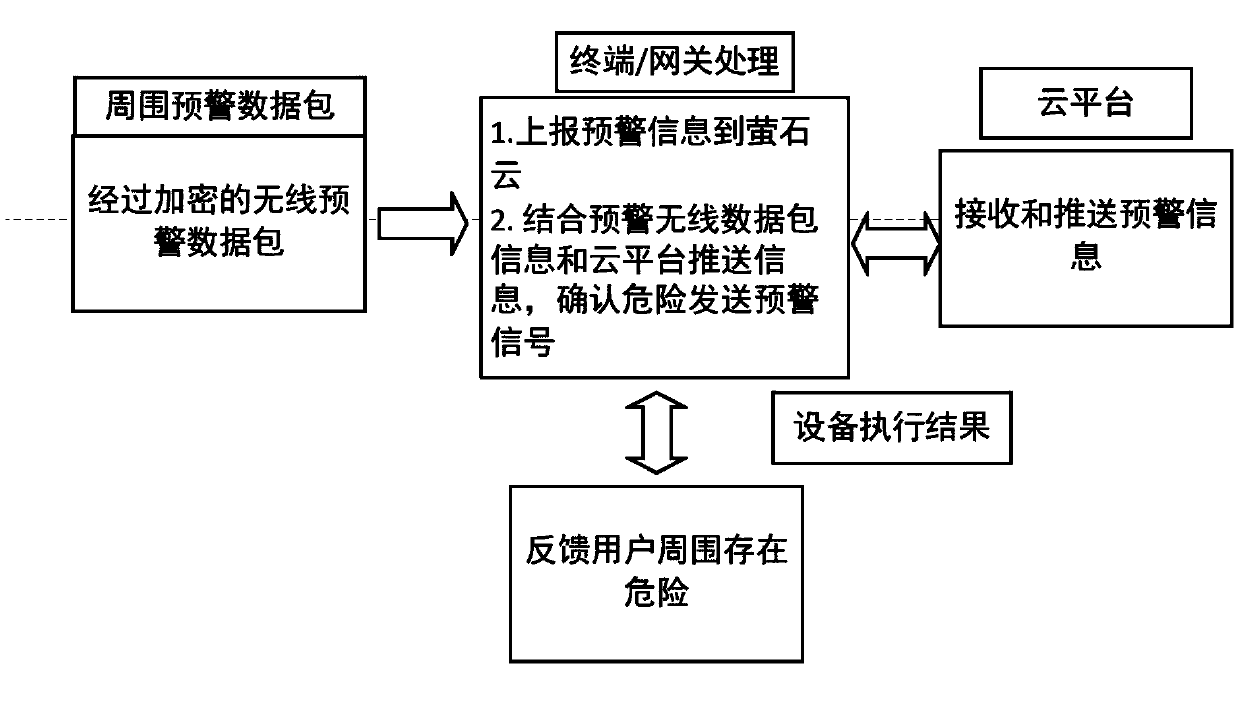
ActiveCN111415500AAvoid false positivesPrevent hackingAlarmsHome automation networksEarly warning systemAlarm message
The invention discloses a smart home early warning system, which comprises an alarm sensor, an alarm gateway and a cloud service platform, and is characterized in that the alarm sensor is an alarm node device and is used for sending a danger alarm to the alarm gateway when an alarm event is detected; the alarm gateway is used for receiving the alarm sent by the alarm sensor, uploading corresponding alarm information to the cloud service platform according to the alarm, and broadcasting an early warning data packet to other alarm gateways around in a wireless mode; and the cloud service platform is used for receiving the alarm information from the alarm gateway, generating early warning information according to the alarm information and pushing the early warning information to other alarm gateways around the alarm position. The invention further provides a corresponding smart home early warning method and device. By applying the technical scheme disclosed by the invention, the surrounding danger can be early warned to the user of the smart home, and the reliability of the early warning of the smart home is improved.
Owner:HANGZHOU EZVIZ SOFTWARE CO LTD
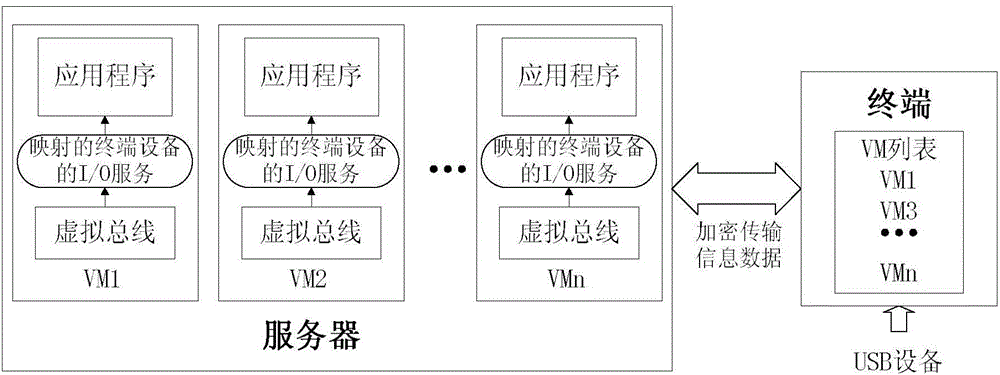
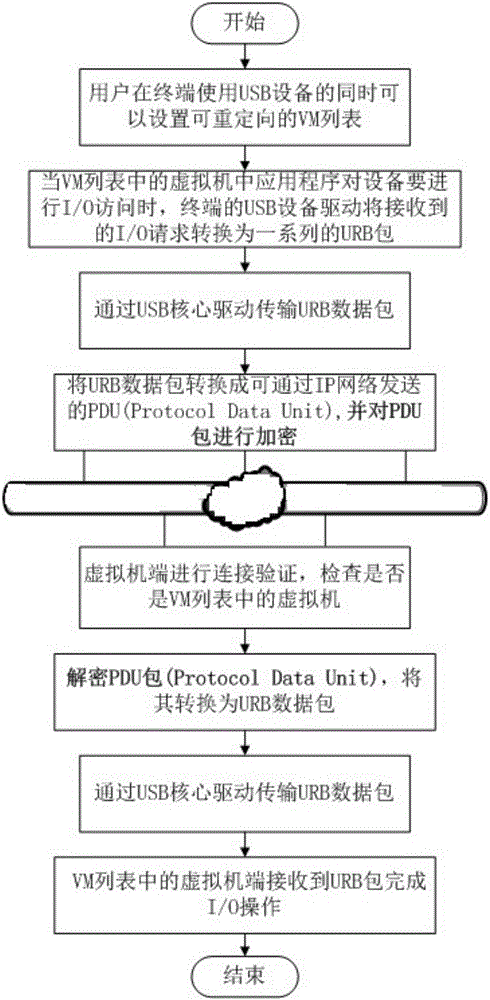
USB (universal serial bus) equipment security sharing method and system based on desktop virtualization
ActiveCN105871926APrevent hackingAvoid immeasurable lossesKey distribution for secure communicationData virtualizationVirtual machine
The invention relates to a USB (universal serial bus) equipment security sharing method and system based on desktop virtualization. USB equipment is used at a terminal, and meanwhile, a redirected VM (virtual machine) list (any one VM in the list can share the USB equipment); some VMs are designated to have the authority to access the USB equipment, so that the network security is improved. PDU (protocol data unit) data packets are sent by the modes of combining symmetrical encryption and asymmetric encryption; the PDU data packets are sent in the symmetrical encryption mode; a secret key used by the symmetrical encryption is sent in the asymmetric encryption mode; the secret key of the symmetrical encryption is encrypted by a public key using the asymmetric encryption; the transmission is performed through a network; a receiver uses a private key for decryption to obtain the symmetrical encryption secret key. The network transmission security can be ensured; the URB data packet transmission speed and the USB equipment reading speed can also be accelerated.
Owner:SHANDONG UNIV
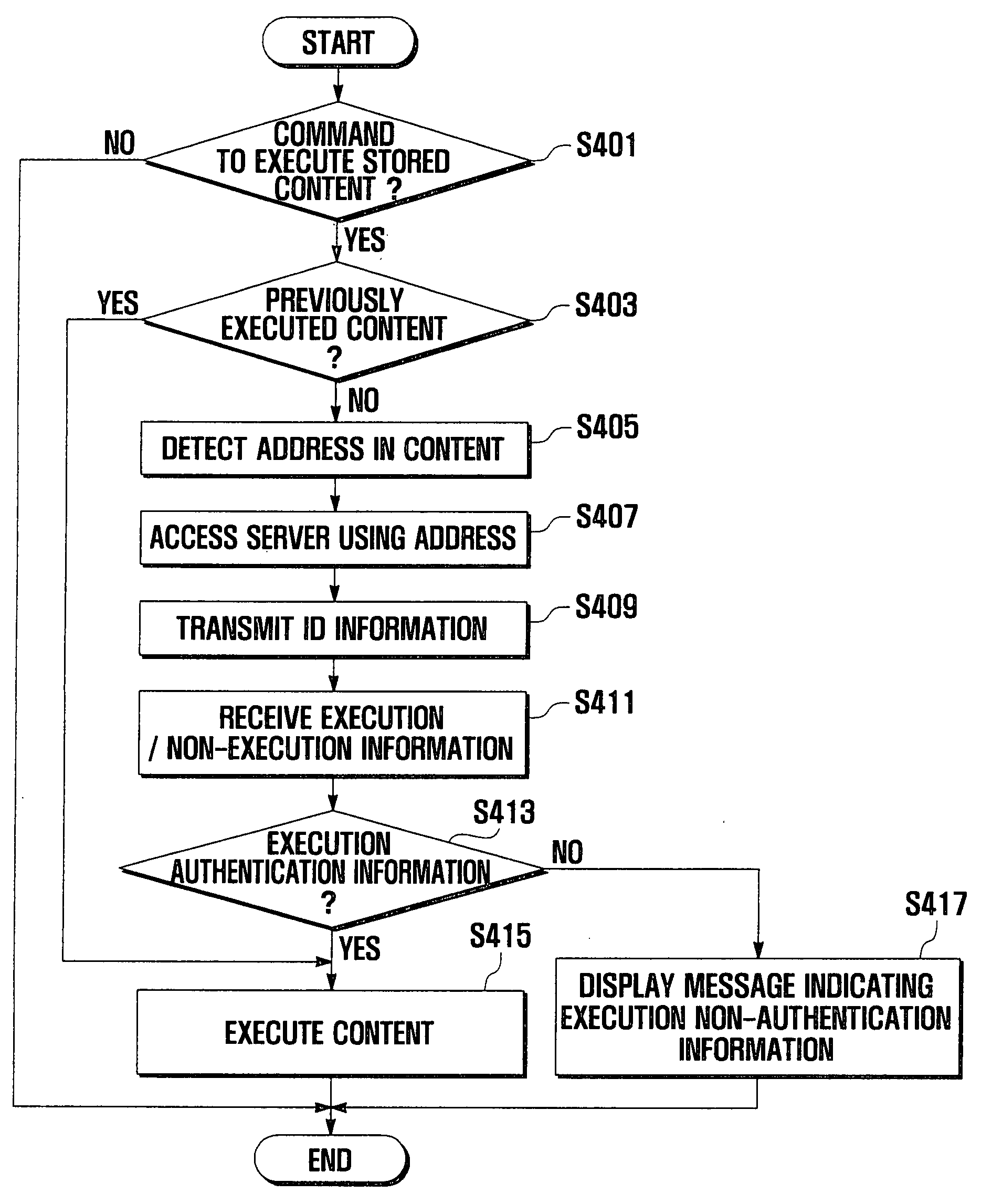
System and method for protecting copyrights of digital content
InactiveUS20080127315A1Prevent illegal copyingPrevent hackingDigital data processing detailsMultiple digital computer combinationsDigital contentAuthentication
A system for protecting copyrights of digital content includes a digital content server for providing digital content containing an address of a digital content server, performing authentication of the digital content, and generating execution / non-execution information representing an authentication result for the digital content. A mobile terminal receives the execution / non-execution information from the digital content server and executes the digital content according to the execution / non-execution information. A method may include the steps of detecting an address of a digital content server contained in the digital content; accessing the digital content server using the detected address and transmitting identification (ID) information necessary for executing the digital content to the digital content server; performing authentication of the digital content in the digital content server using the ID information, and generating execution / non-execution information representing an authentication result for the digital content, and transmitting the execution / non-execution information to the mobile terminal.
Owner:SAMSUNG ELECTRONICS CO LTD
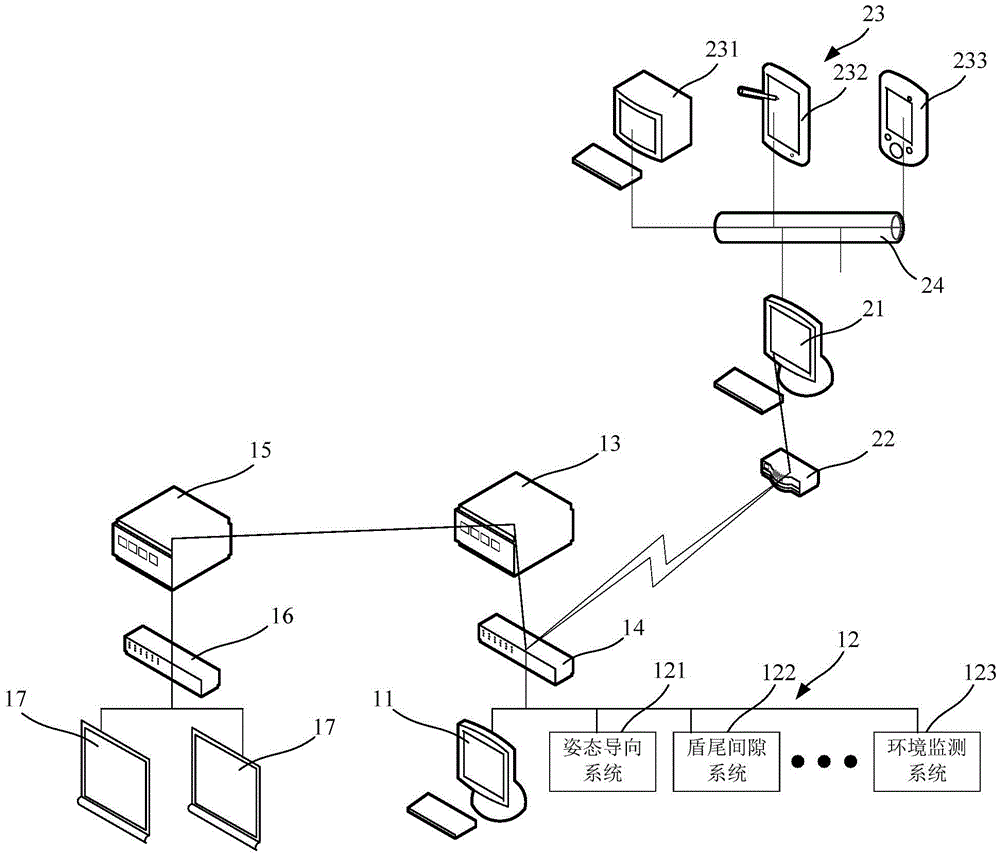
System and method of management and control of quasi-rectangular shield construction
ActiveCN105487476AEnsure safety and reliabilityPrevent hackingProgramme control in sequence/logic controllersData exchangeShield tunneling
The present invention relates to a system and method of management and control of quasi-rectangular shield construction. The system comprises: a shield data acquisition device arranged in a tunnel and configured to collect the construction data in the process of shield tunneling machine construction; a plug-in subsystem configured to monitor the shield construction date in the tunnel in real time; a data exchange processor arranged in the tunnel configured to connect the data acquisition device and the plug-in subsystem through an exchange and transmit the construction data monitored by the plug-in subsystem to the data acquisition device; a data management center arranged on the ground and configured to connect the data exchange processor through the exchange to receive and display the construction data transmitted by the data exchange processor; a shield control PLC arranged in the tunnel and configured to control the shield tunneling machine which is connected with the data exchange processor through a bus. According to the invention, the safety and the reliability of an original control system of a shield tunneling machine are effectively ensured.
Owner:SHANGHAI TUNNEL ENG CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com