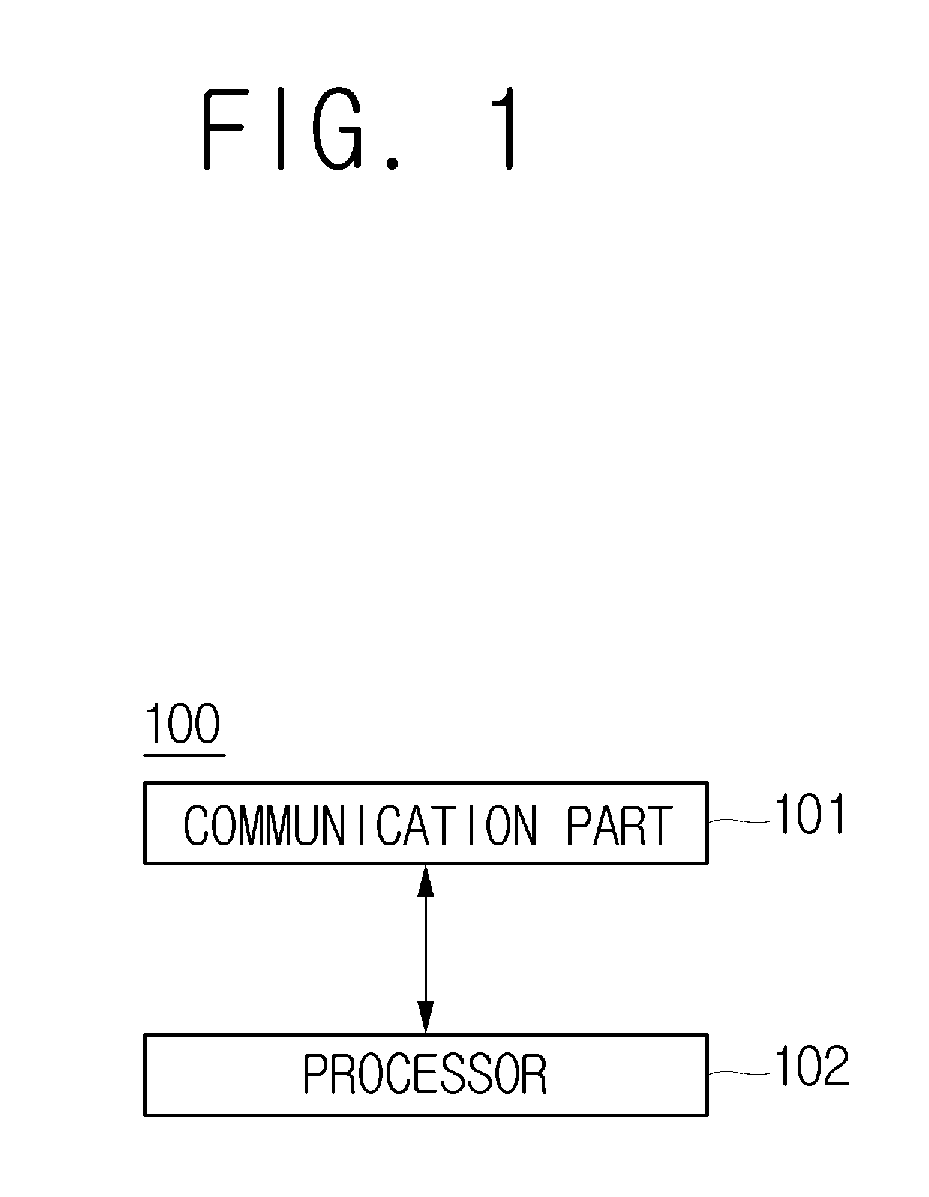
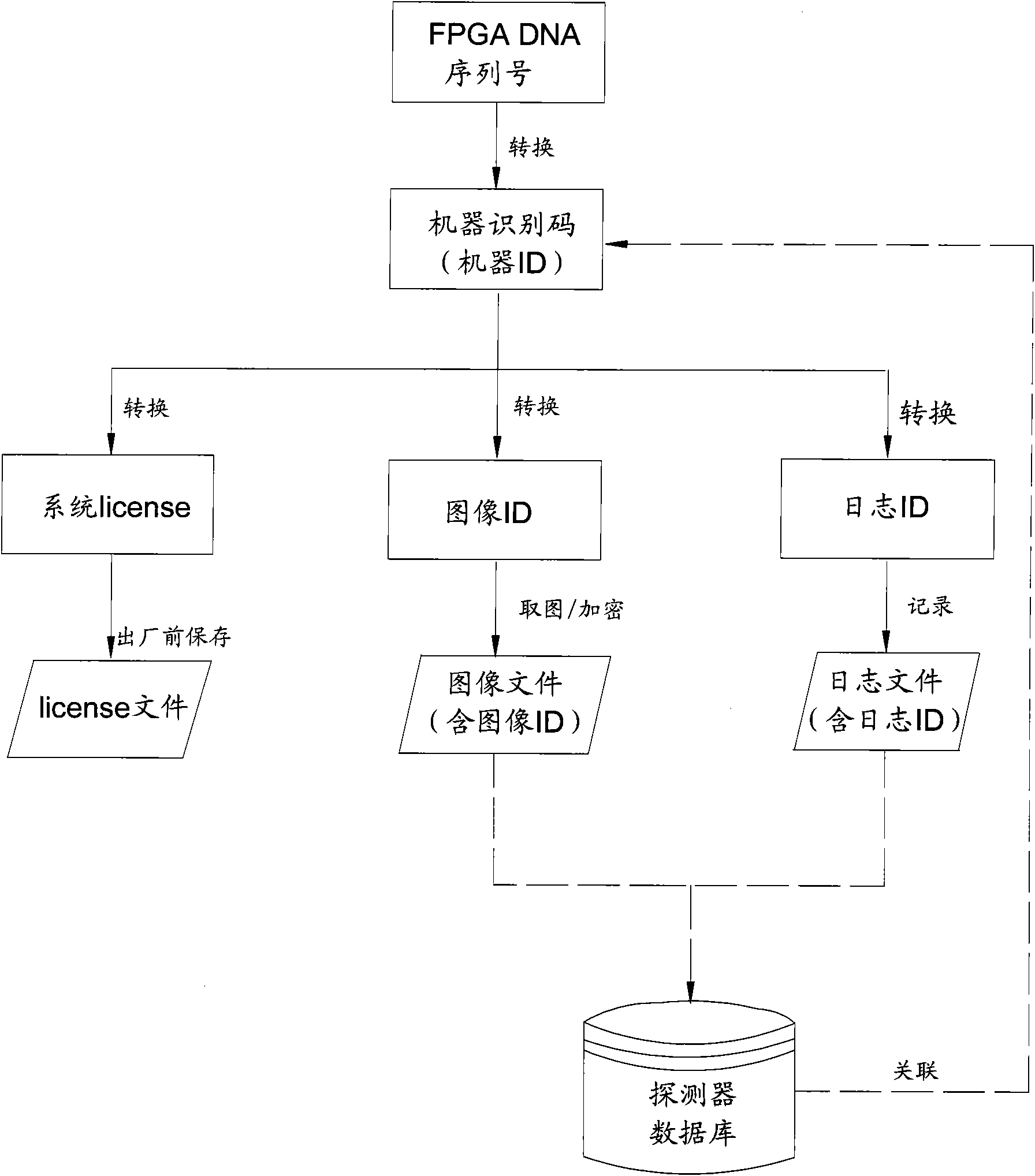Patents
Literature
129results about How to "Prevent illegal copying" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data-recording method, data-recording apparatus, and data-recording system
InactiveUS20070208916A1Prevent illegal copyingMemory loss protectionError detection/correctionMini discData recording
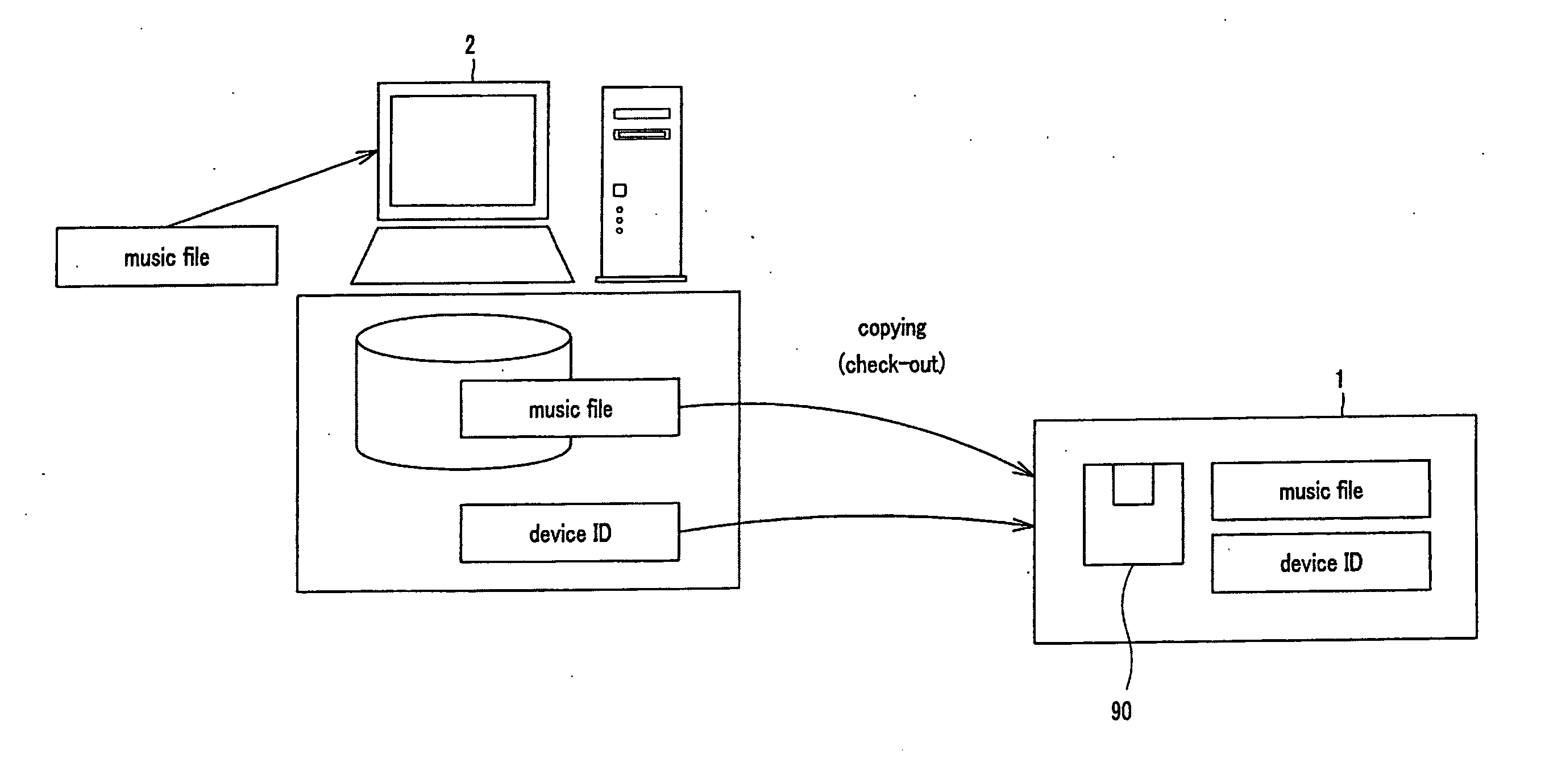
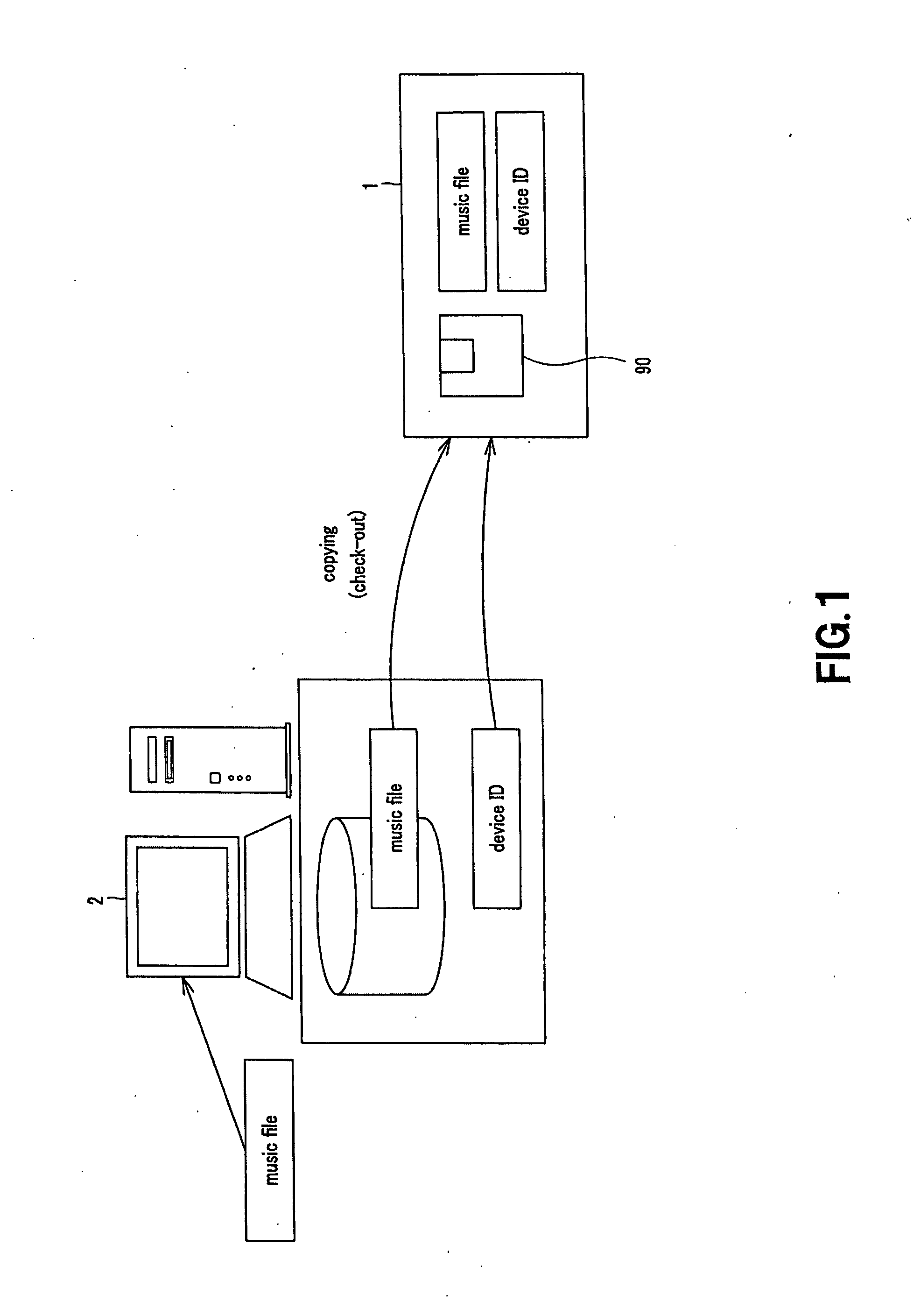
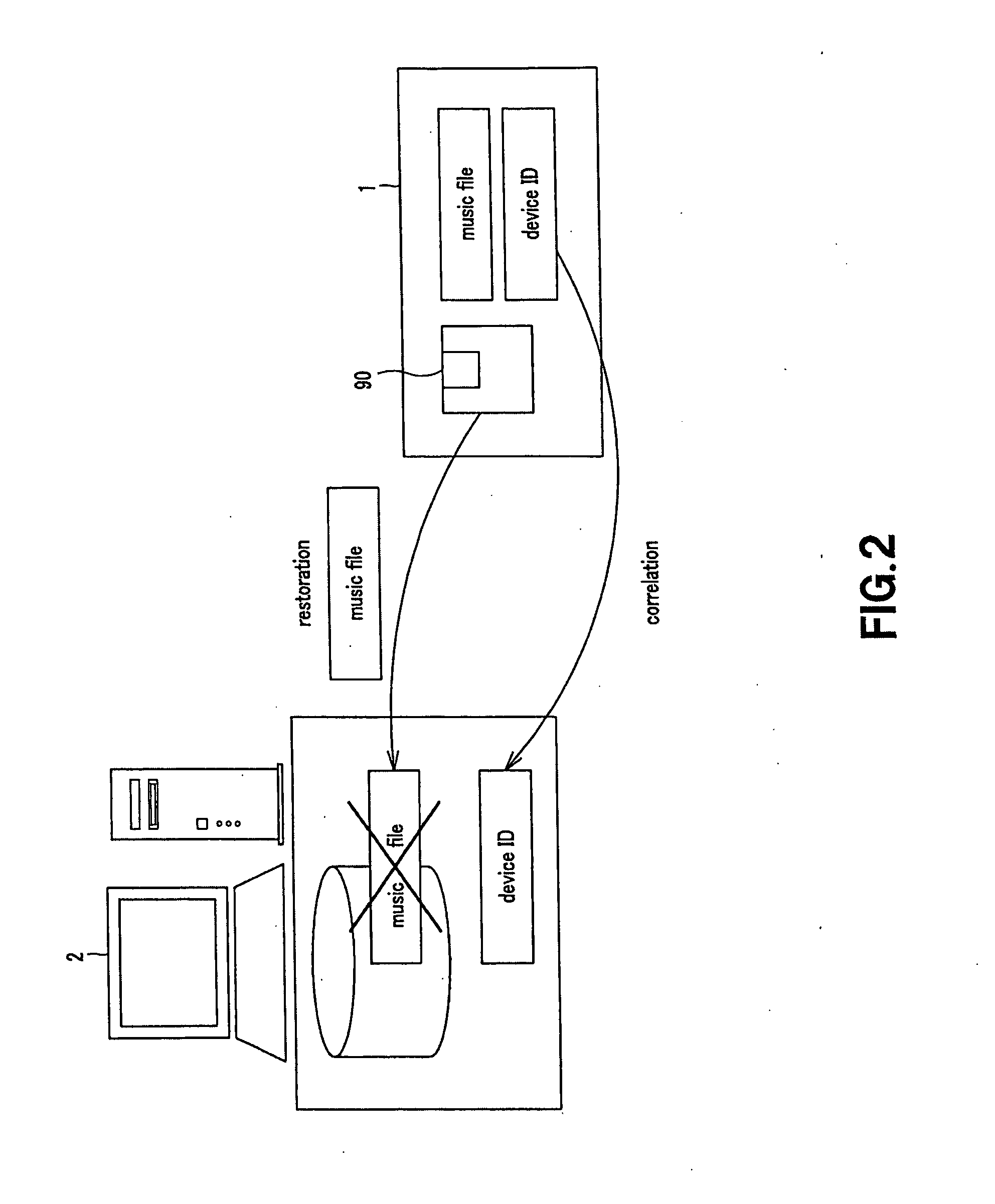
A PC, which is a data-processing apparatus copies a file in a mini disc via a data-recording apparatus. The file is composed of a copyrighted music content accumulated in the HDD of the PC, which have been reproduced from another recording medium such as a CD, a DVD or the like. The data-recording apparatus records the ID specific to the PC in the mini disc. Not only the music file, but also the content ID specific to the content is recorded in the next-generation mini disc used in an embodiment of this invention. The music file, thus backed up, is restored when the device in which the content is to be restored is identical to the PC that has been checked out, or when this device is collated to be identical to the PC.
Owner:SONY CORP
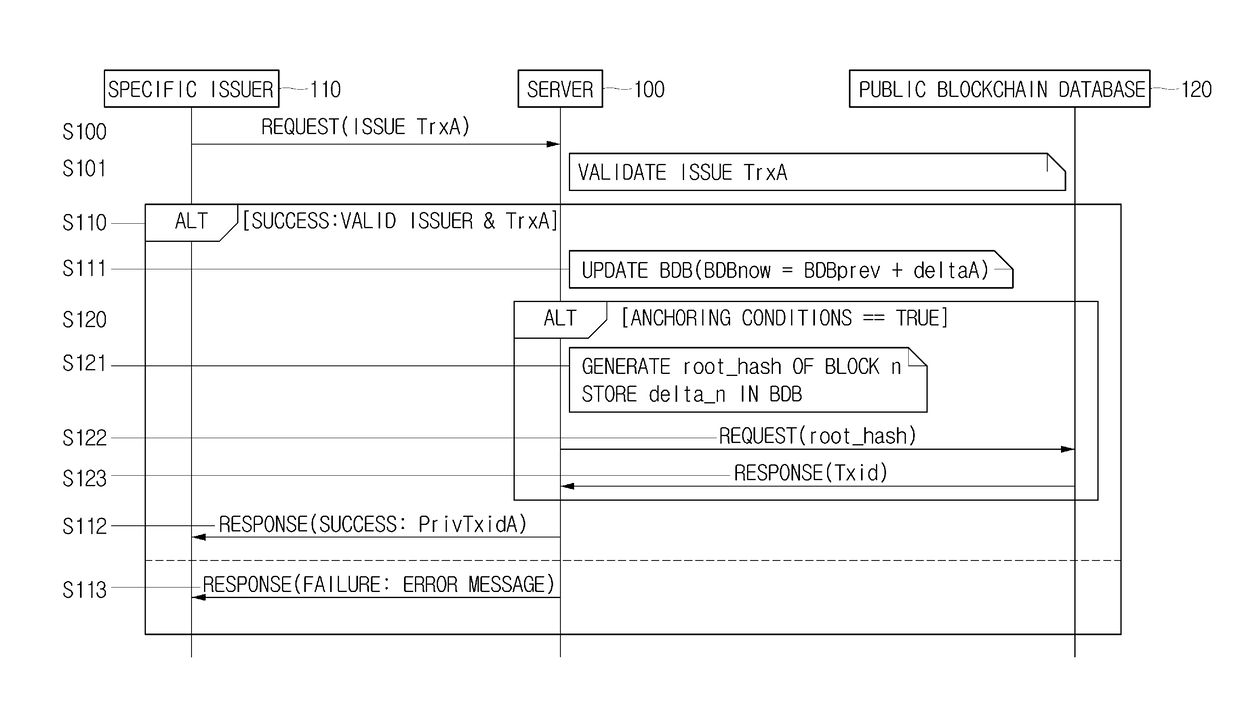
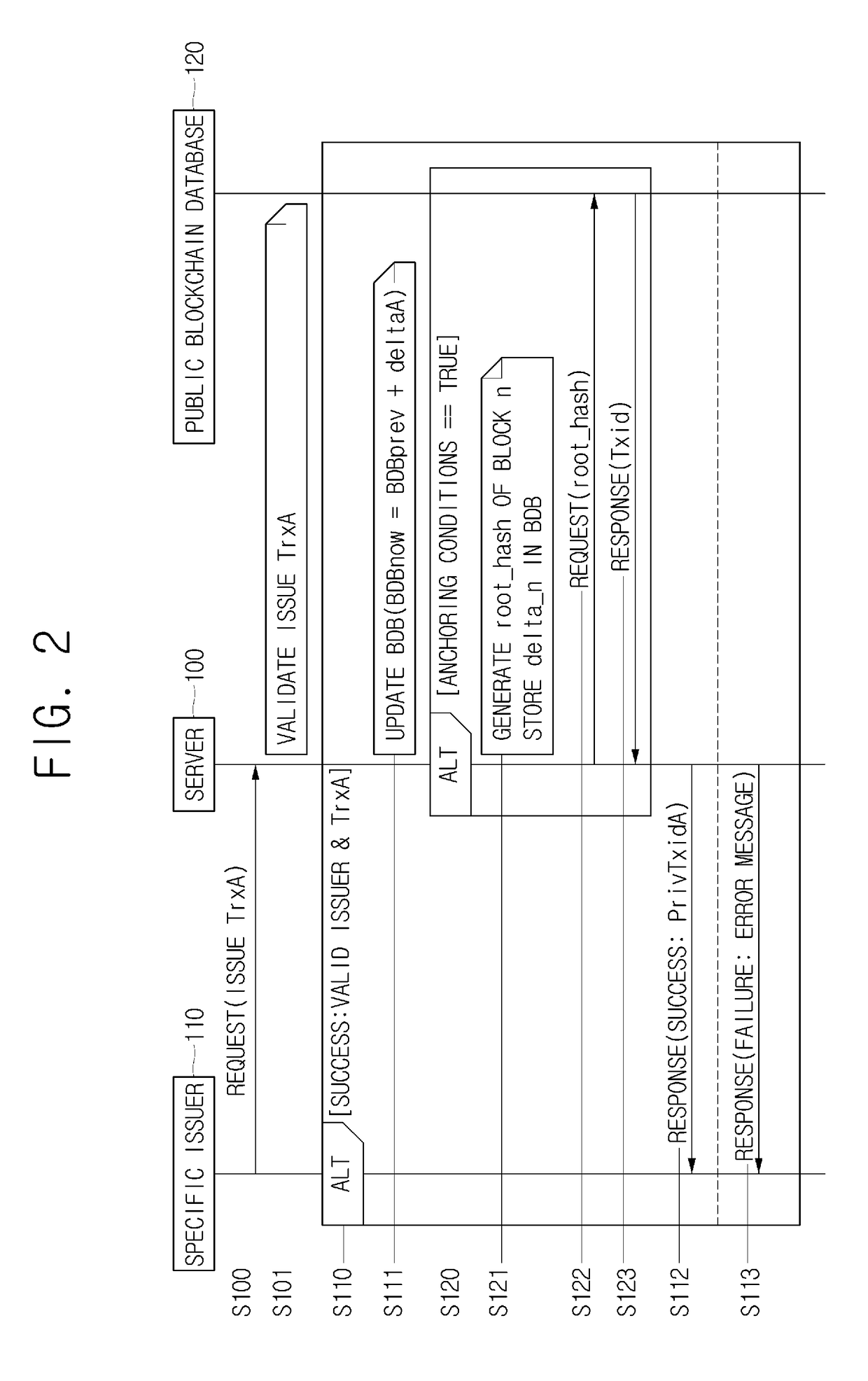
Method for issuing, using, refunding, settling and revocating electronic voucher using updated status of balance database by respective blocks in blockchain, and server using the same
ActiveUS20180101844A1Prevent forgeryPrevent illegal copyingKey distribution for secure communicationDigital data information retrievalVoucherData bank
A method of issuing an electronic voucher by an issuer is provided. The method includes steps of: (a) creating and registering a transaction including a voucher data, a public key and a signature value of the issuer, with a private blockchain database, providing the issuer with a PrivTxid locating the transaction in the private blockchain database, and updating and registering value information including a balance of the voucher data with a BDB; and (b) acquiring and registering a representative hash value calculated using a specific hash value, which is a hash value of the voucher data, the public key, and the signature value, and its corresponding hash values which include a hash value of a delta_n including all balances of all vouchers, identifiable by all PrivTxids locating their transactions, with a public blockchain database, and acquiring a Txid locating the representative hash value in the public blockchain database.
Owner:COINPLUG LNC
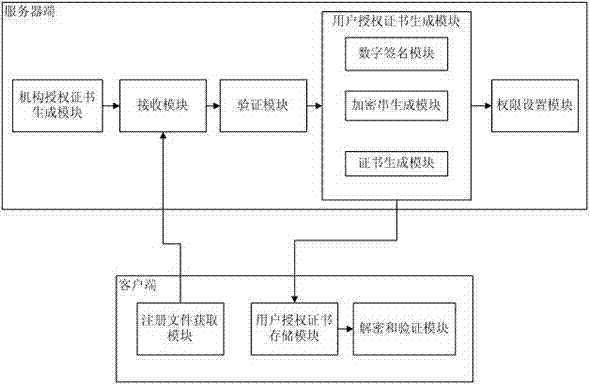
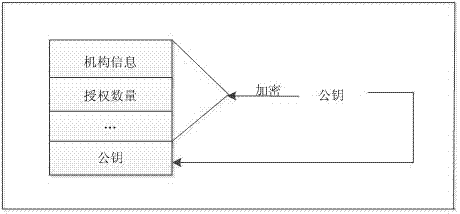
Software authorization system based on public key cryptosystem
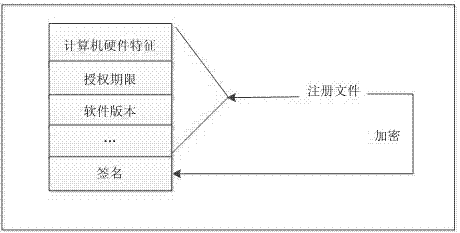
ActiveCN103491097APrevent illegal copyingEasy to upgradeVersion controlUser identity/authority verificationAuthorization certificateAuthorization Mode
The invention discloses a software authorization system based on public key cryptosystem. The software authorization system comprises a server end and a client end, wherein the server end comprises an institution authorization certification generation module, a receiving module, a verification module and a user authorization certificate generation module. The user authorization certificate generation module comprises a digital signing module used for carrying out digital signing on computer hardware characteristics h0 in a user registration file with an RSA private key to generate S0, an encryption string generation module used for carrying out preset hybrid operations on obtained software version information v, user information u, an authorization term ex, current time cur and s0 to generate an encryption string signB64 and a certificate generation module used for generating a user authorization certificate with the encryption string signB64 and the RSA public key. The method can prevent software from being illegally copied, meanwhile, the software can be managed by a software issuer in a concentrated mode, and upgrading and tracking of the software, pushing personalized services for users and other after-sale management are facilitated.
Owner:HUAZHONG NORMAL UNIV
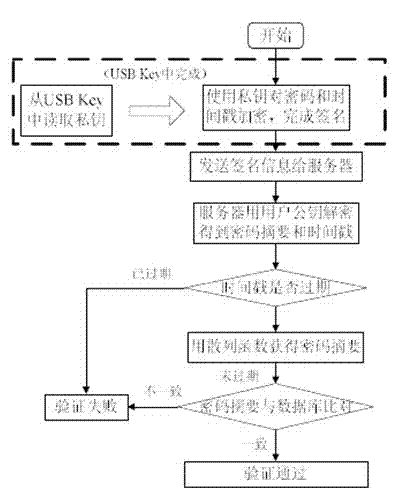
External data transmission method for cloud computing system
The invention relates to an external data transmission method for a cloud computing system. The method is based on identity authentication and data encryption of universal serial bus (USB) equipment. A method for checking the identity of a user logging into a server comprises the following steps of: encrypting a password and a time stamp by a private key, and finishing signature in a USBKey; sending signature information to a cloud server; decrypting the signature information by the cloud server through a user public key to obtain the password and the time stamp, and if the time stamp is overdue, indicating that checking fails; acquiring a password abstract by a hash function, and if the password abstract does not accord with user password information stored in a database, indicating that checking fails; and only when the time stamp is effective, and the password abstract is consistent, indicating that user checking succeeds, accepting the identity of the user by the system, and supplying service. By the technical scheme, the security of the cloud computing system can be effectively improved.
Owner:JIANGSU LEMAIDAO NETWORK TECH
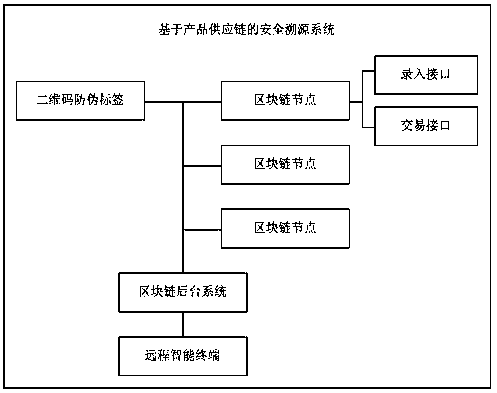
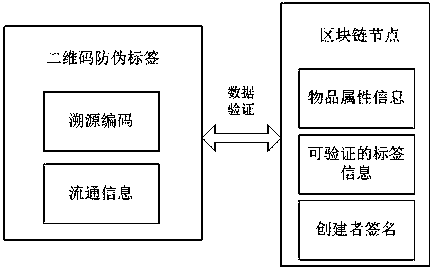
Safety traceability system based on product supply chain
InactiveCN108256875ANo illegal copyingPrevent data from being tampered withCommerceBlockchainTraceability
The invention belongs to the technical field of product supervision and tracing and particularly relates to a safety traceability system based on a product supply chain. The safety traceability systemsafely stores digital currency transaction or other data through a decentralization protocol and features that, for instance, information is faking resistant and tamper resistant; full-process safetysupervision and tracing where product origins and destinations are traceable is achieved. The a safety traceability system based on the product supply chain comprises: a QR (quick response) code anti-faking label firmed on a product, wherein the QR code anti-faking label is used for recording a traceability code of the product and circulation information of the product occurred during product circulation; blockchain nodes in one-to-one correspondence with product supply links and serially connected in sequence, wherein each blockchain link is provided with an entering interface and a transaction interface.
Owner:王先笨
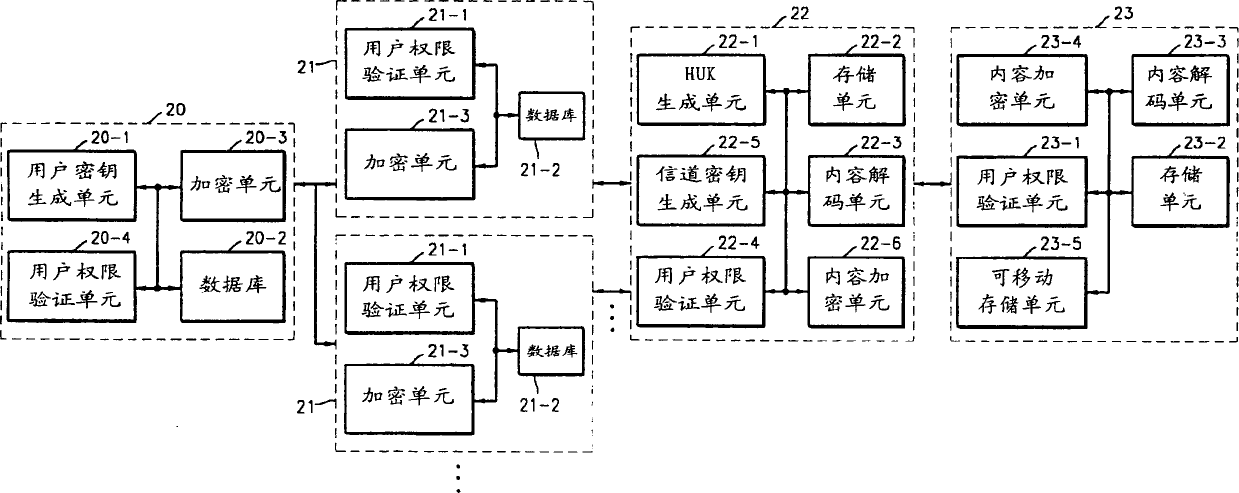
System and method for protecting content data
InactiveCN1392700APrevent illegal copyingMultiple keys/algorithms usageUser identity/authority verificationUser PrivilegeEncryption
A system and method for protecting content data are provided. In the system and method, by encrypting content data so that the content data is distributed with user privileges managed as the copyright holder wants, illegal copying is prevented and user privileges are managed according to predetermined regulations. The method for providing content data comprising the steps of (a) receiving user keys generated by a combination of unique information assigned uniquely to a user; and (b) encrypting the content data using the user keys and a predetermined encryption algorithm, and transmitting the encrypted content data to a user system. According to the system and method, by encrypting content data so that the content data is distributed with the user privileges managed as the copyright holder wants, illegal copying is prevented and user privileges are managed according to predetermined regulations. Also, because user keys are encrypted using the HUK, the possible exposure of user keys is prevented and content data can be distributed as the copyright holder wants using the DRM database.
Owner:SAMSUNG ELECTRONICS CO LTD
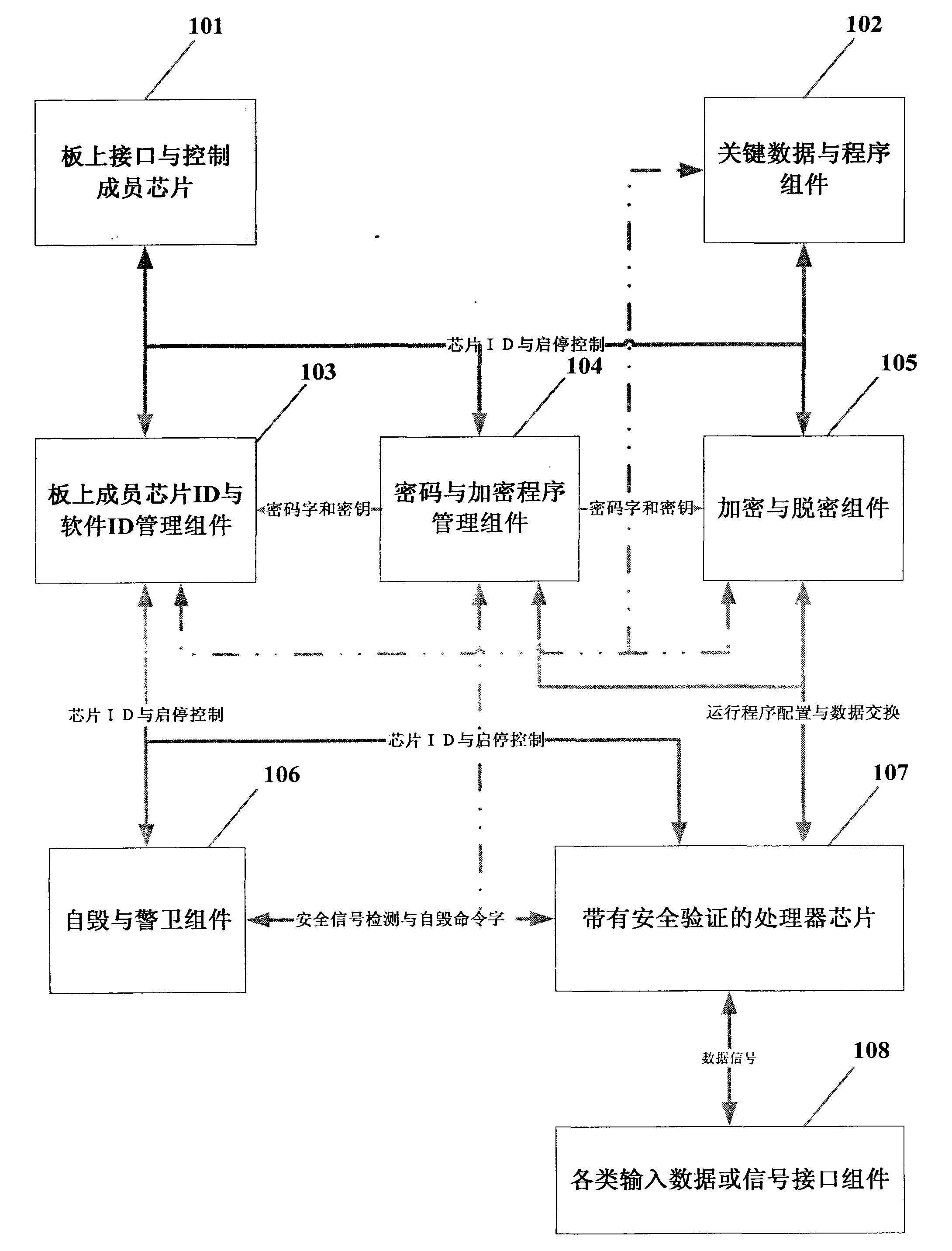
Dereplication encryption lock for software and hardware of embedded system
InactiveCN102915411APrevent copyingTightly boundProgram/content distribution protectionProgram managementOn board
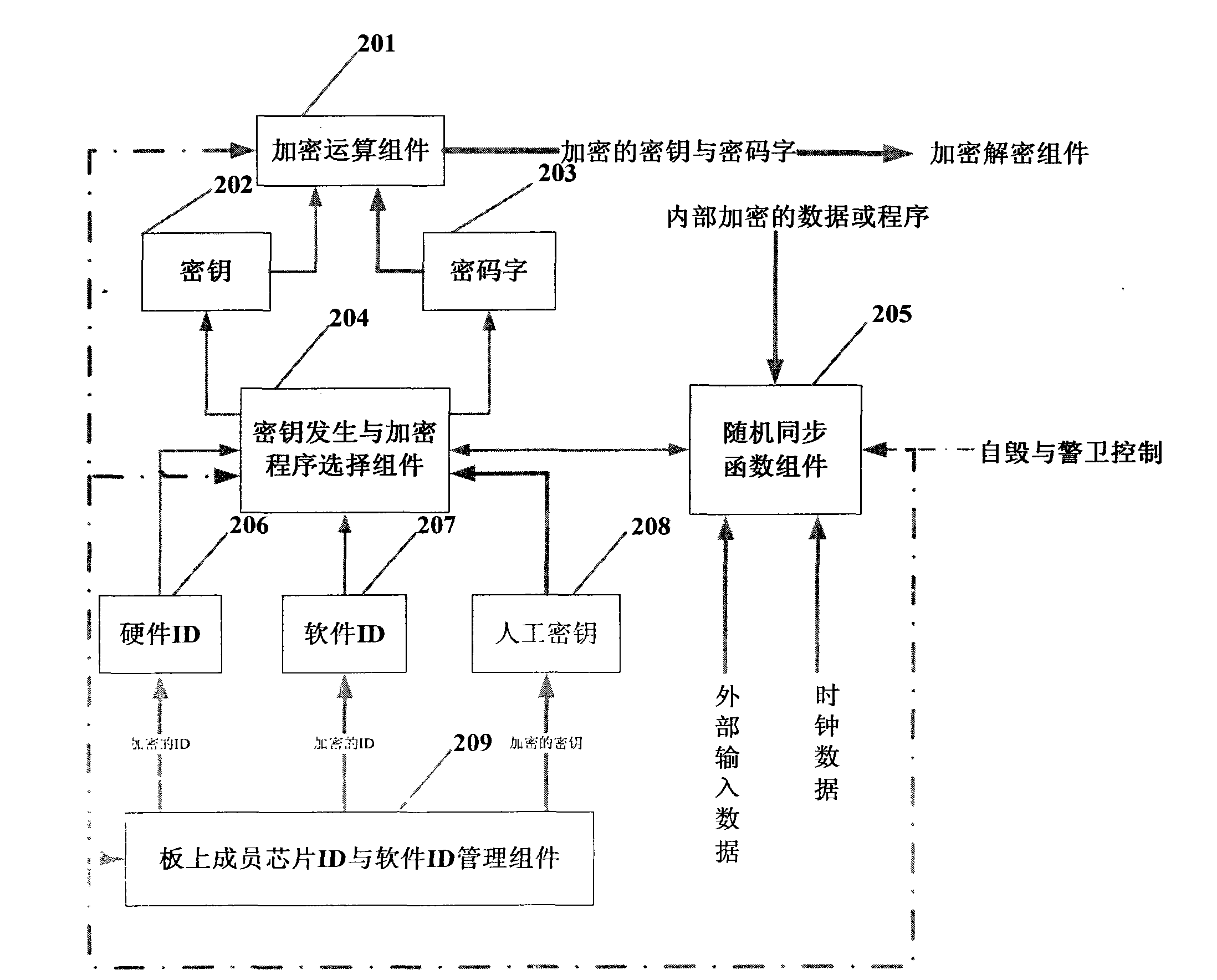
The invention discloses a dereplication encryption lock for software and hardware of an embedded system. The dereplication encryption lock comprises an on-board member chip ID (identification) and software ID management component, a password and encryption program management component, an encryption and decryption component, a self-destruction and guard component, a processor chip with security verification and on-board port and control member chip. The on-board member chip ID (identification) and software ID management component is used for managing and controlling software and hardware in the system. The password and encryption program management component is used for generating secret keys and password exclusive to the system according to ID number of software and hardware, part number and artificial secret keys in the system. The encryption and decryption component is used for decrypting programs or data ciphertexts according to selected secret keys and encryption program to generate executable programs or data plaintexts. The self-destruction and guard component is used for performing safety detection and protection to chips in the system and preventing illegal tamper and replacement. The processor chip guarantees safe operation of programs needed by the system and cannot store any other programs or data except for own necessary serial number, starting code and response programs after power failure. The on-board port and control member chip is a port chipset which is used for finishing all functions of the system.
Owner:张景彬 +1
Electronic bill system, apparatus and method
ActiveCN101430800APrevent illegal copyingTicket-issuing apparatusTelephonic communicationMemory chipComputer terminal
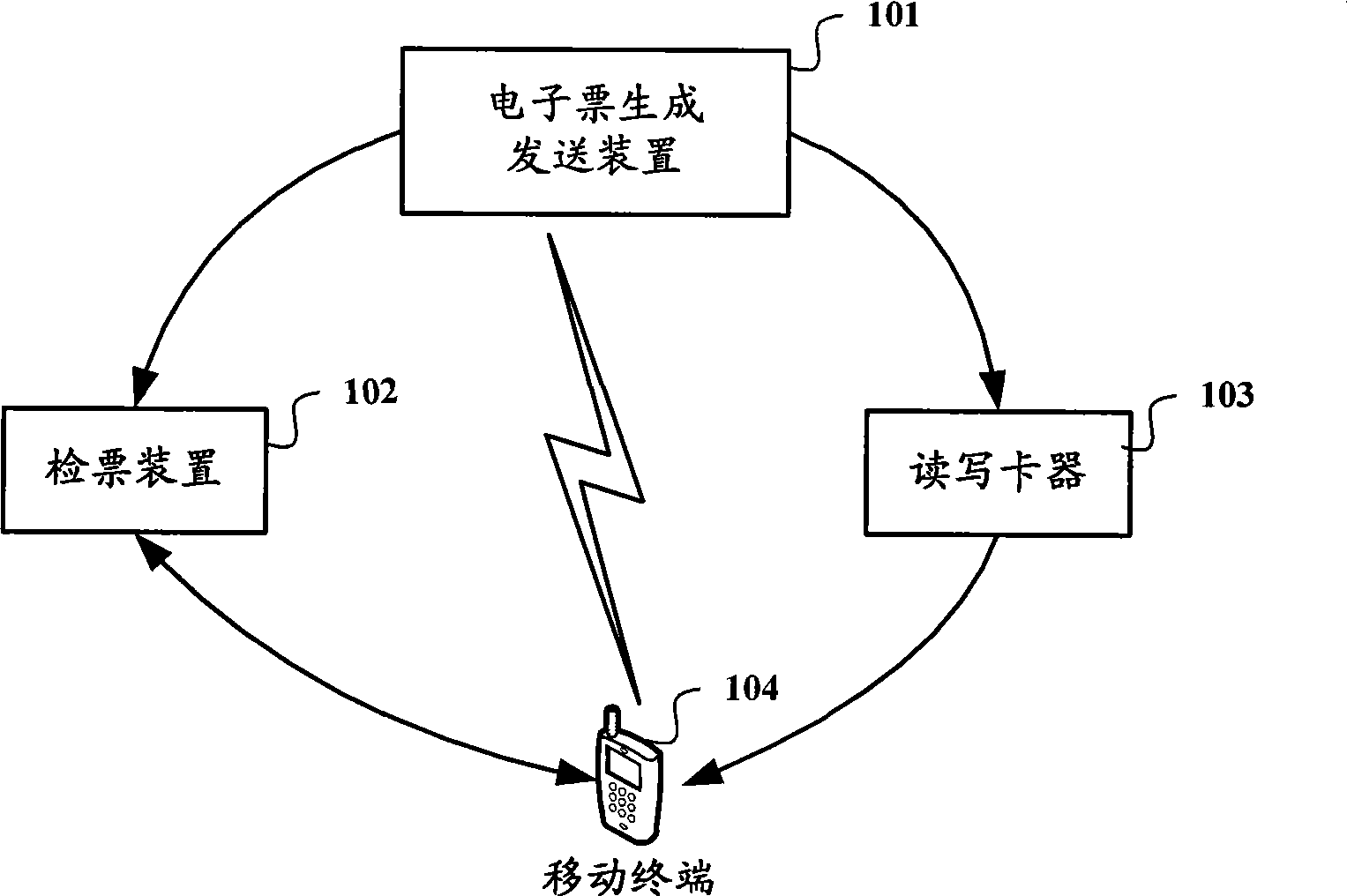
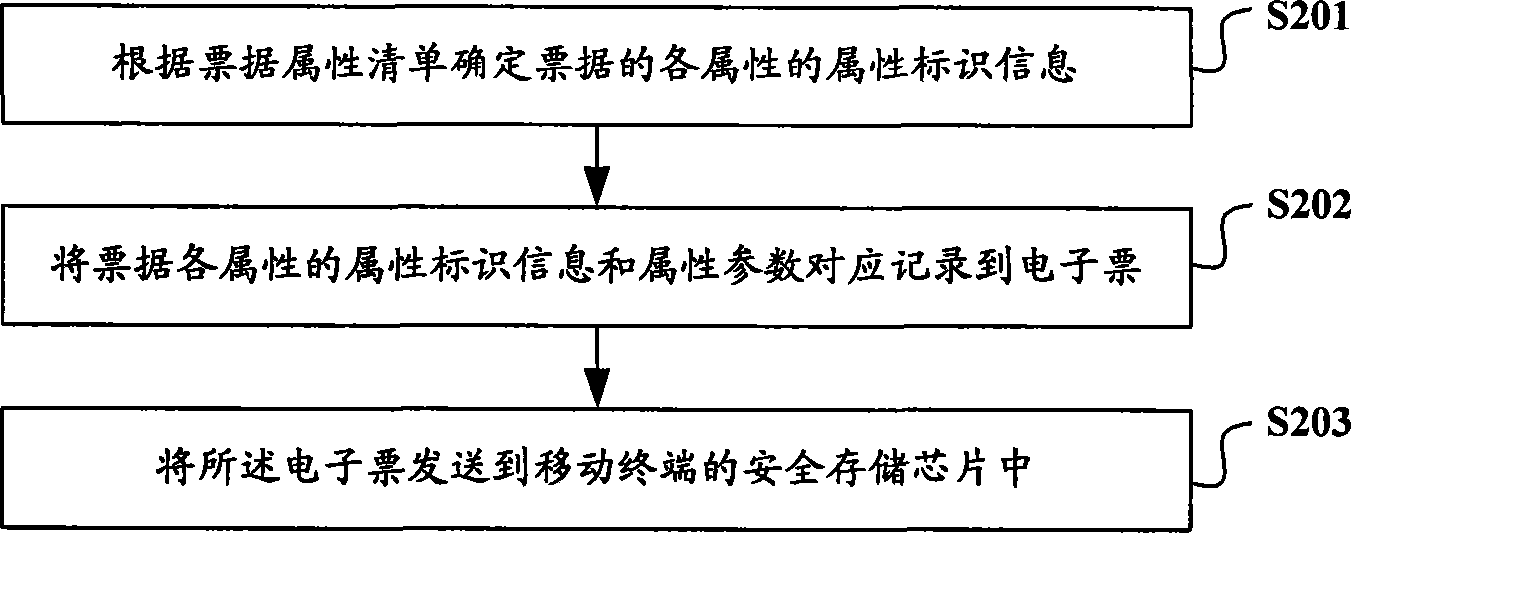
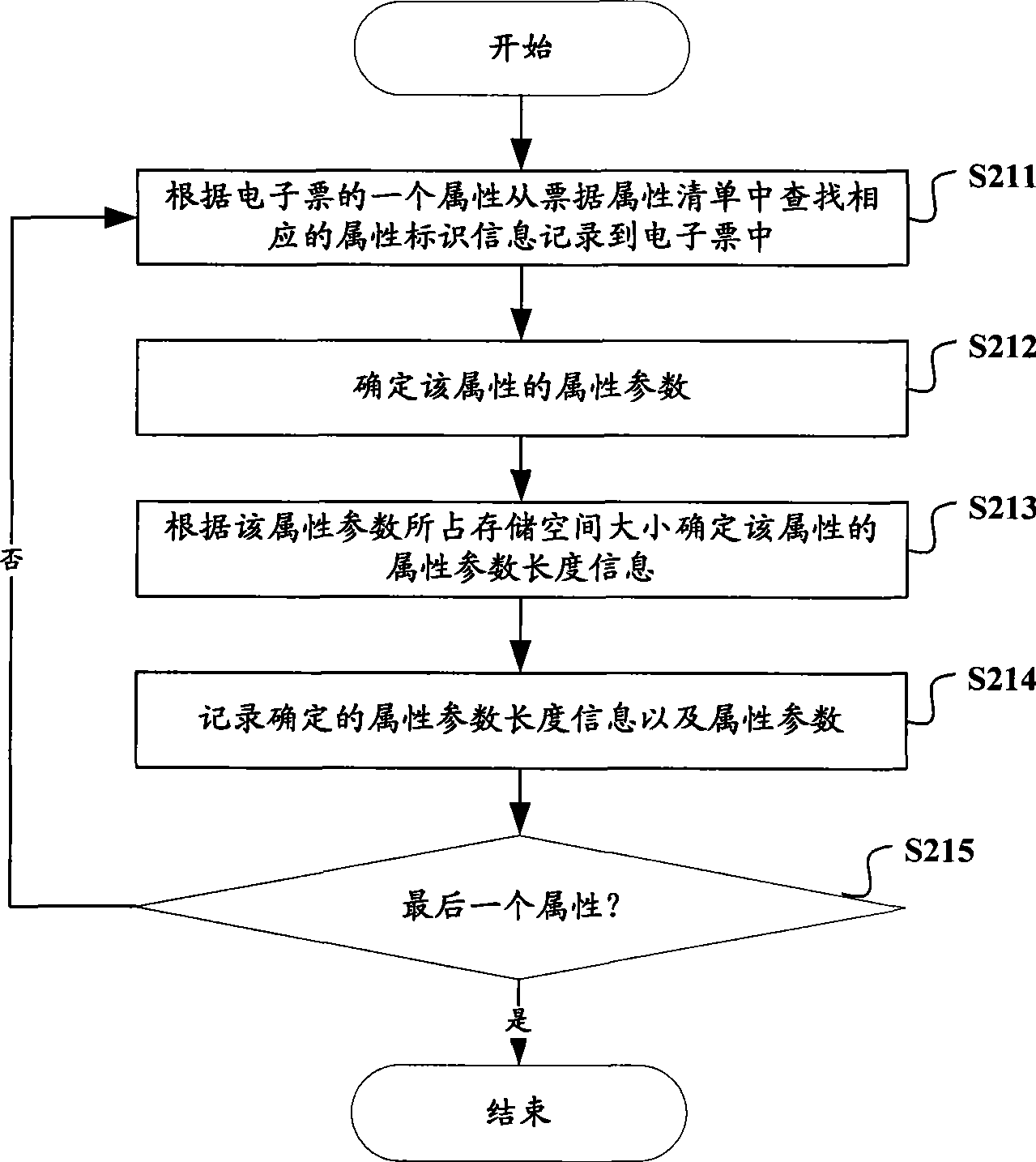
The invention relates to the field of electronic ticket, in particular to an electronic ticket system which has universality and can prevent non-buyers from illegally duplicating the electronic tickets. The invention provides an electronic ticket system, a device and a method thereof. The method comprises the following steps: firstly, the property identification information of each property of a ticket is determined according to the property list of the ticket secondly, the corresponding relation of the properties of various tickets and the identification information of the property is recorded in the property list of the ticket thirdly, the property identification information of each property and the property parameters of the ticket are correspondingly recorded in the electronic ticket and fourthly, the electronic ticket is transmitted to the secure memory chip of a mobile terminal. The property identification information of each property and the property parameters of various tickets can be recorded in the electronic ticket according to the property list of the ticket to form various electronic tickets, thereby ensuring the universality of the electronic ticket system; furthermore, the electronic ticket can be transmitted to the secure memory chip, so as to prevent the electronic ticket from being duplicated illegally.
Owner:CHINA MOBILE COMM GRP CO LTD
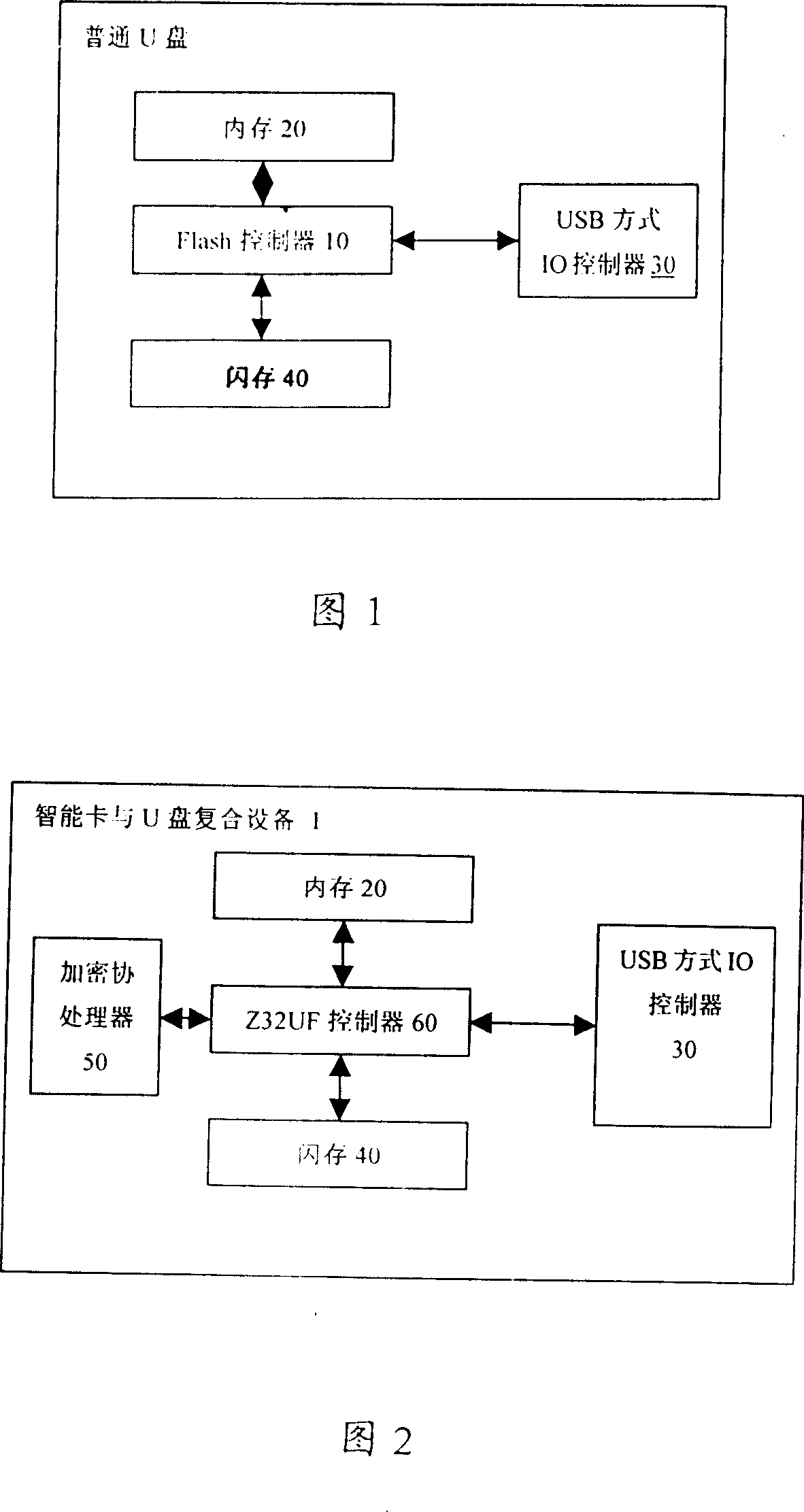
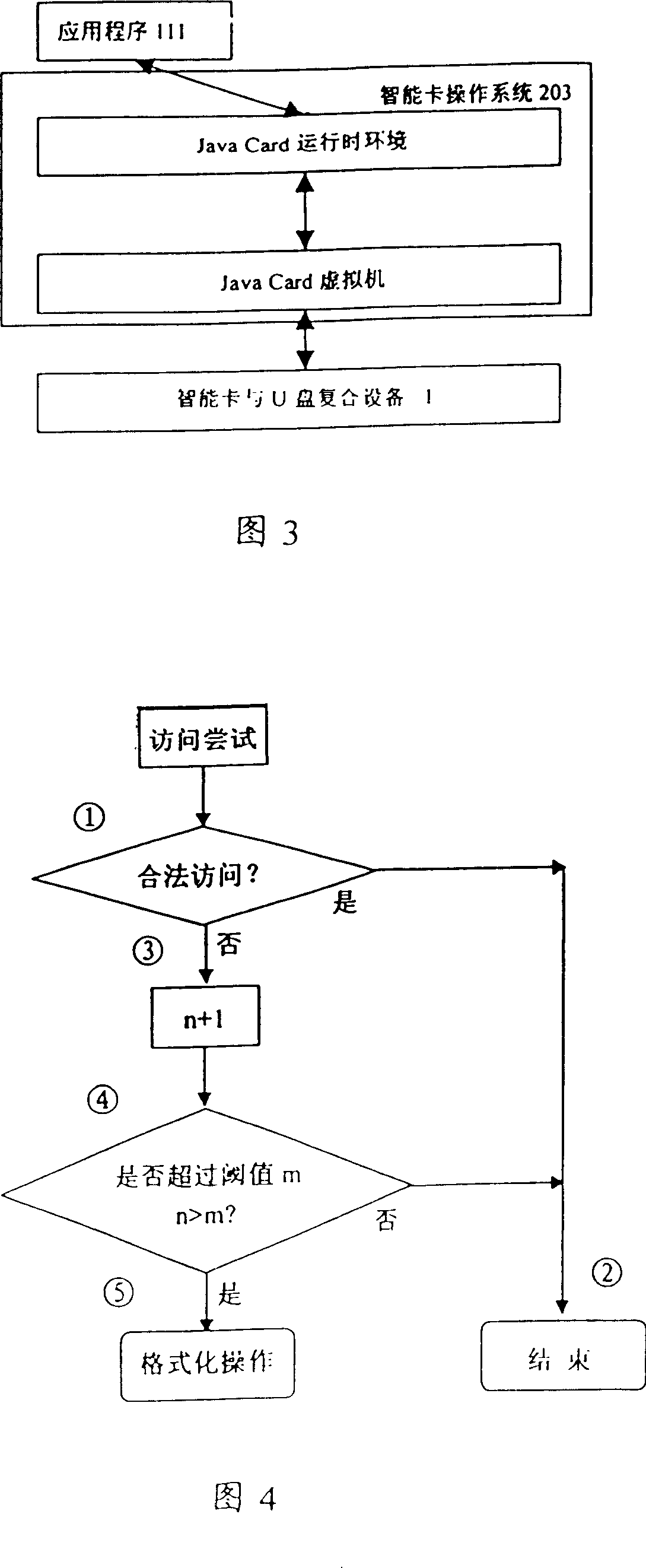
Smart card and USB combined equipment and method of self-destroy forillegal access and try to pass valve value
InactiveCN101000583ANo confidentialityImprove confidentialityUnauthorized memory use protectionInternal/peripheral component protectionOperational systemSmart card
A integrated device of intelligent card and USB is prepared as setting autonomous operation system based on Java virtual machine on integrated device of intelligent card and USB, erecting self-destroying program on said autonomous system, enabling to finalize logic judgment that non-authorized call frequency is over threshold by self-destroying program and realizing self-destroying function when non-authorized call frequency is over set top-limit threshold.
Owner:中国信息安全产品测评认证中心 +1
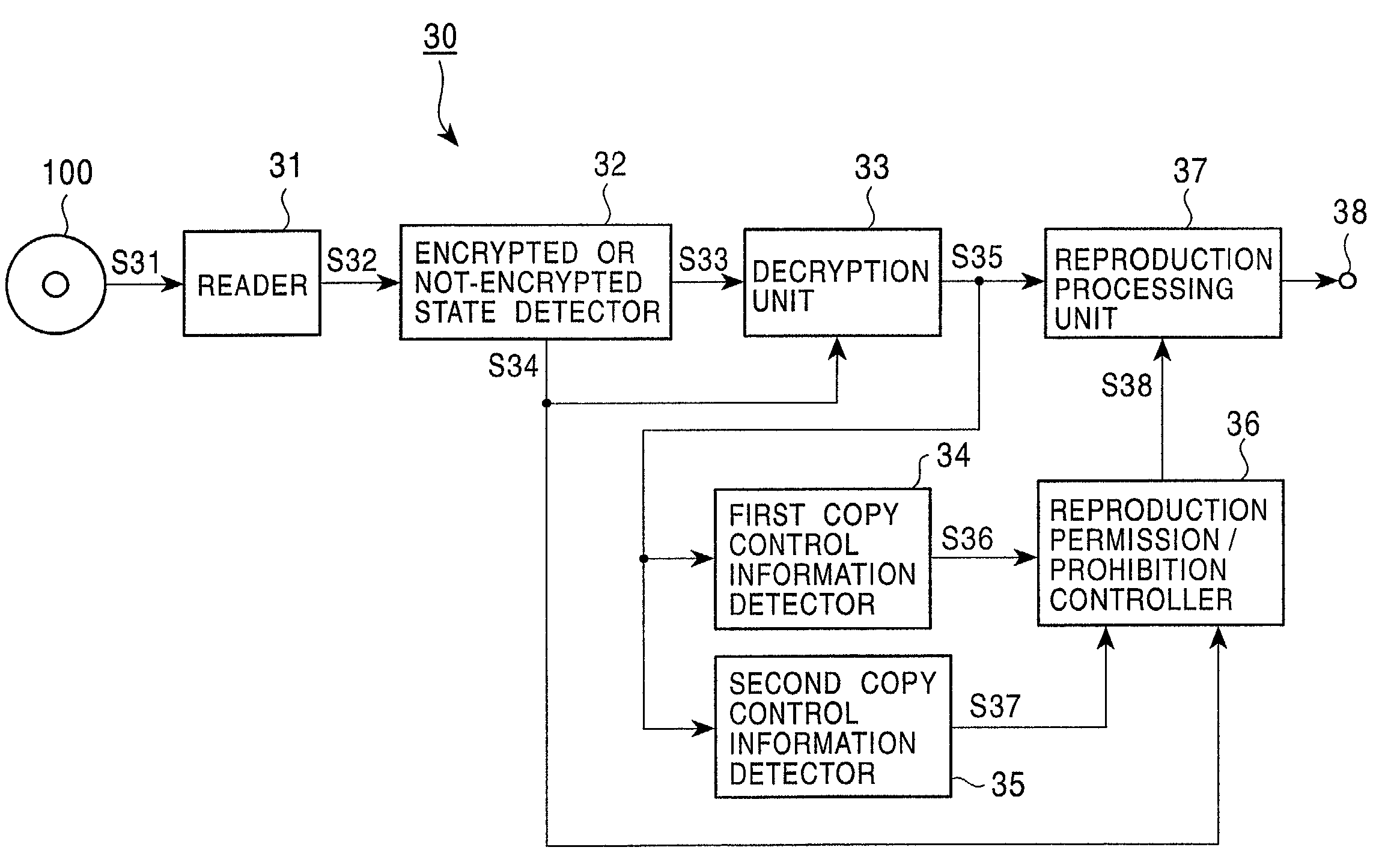
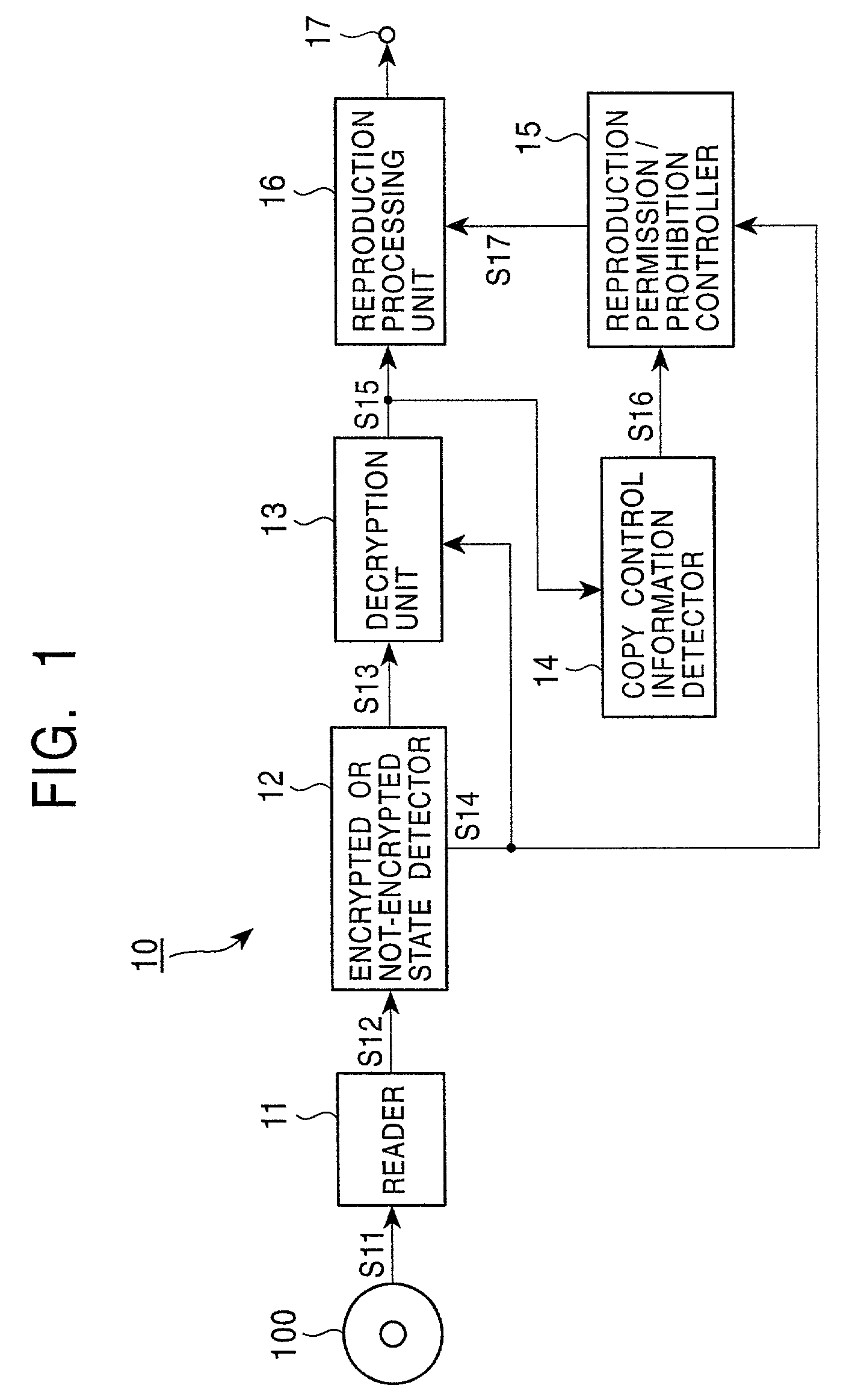
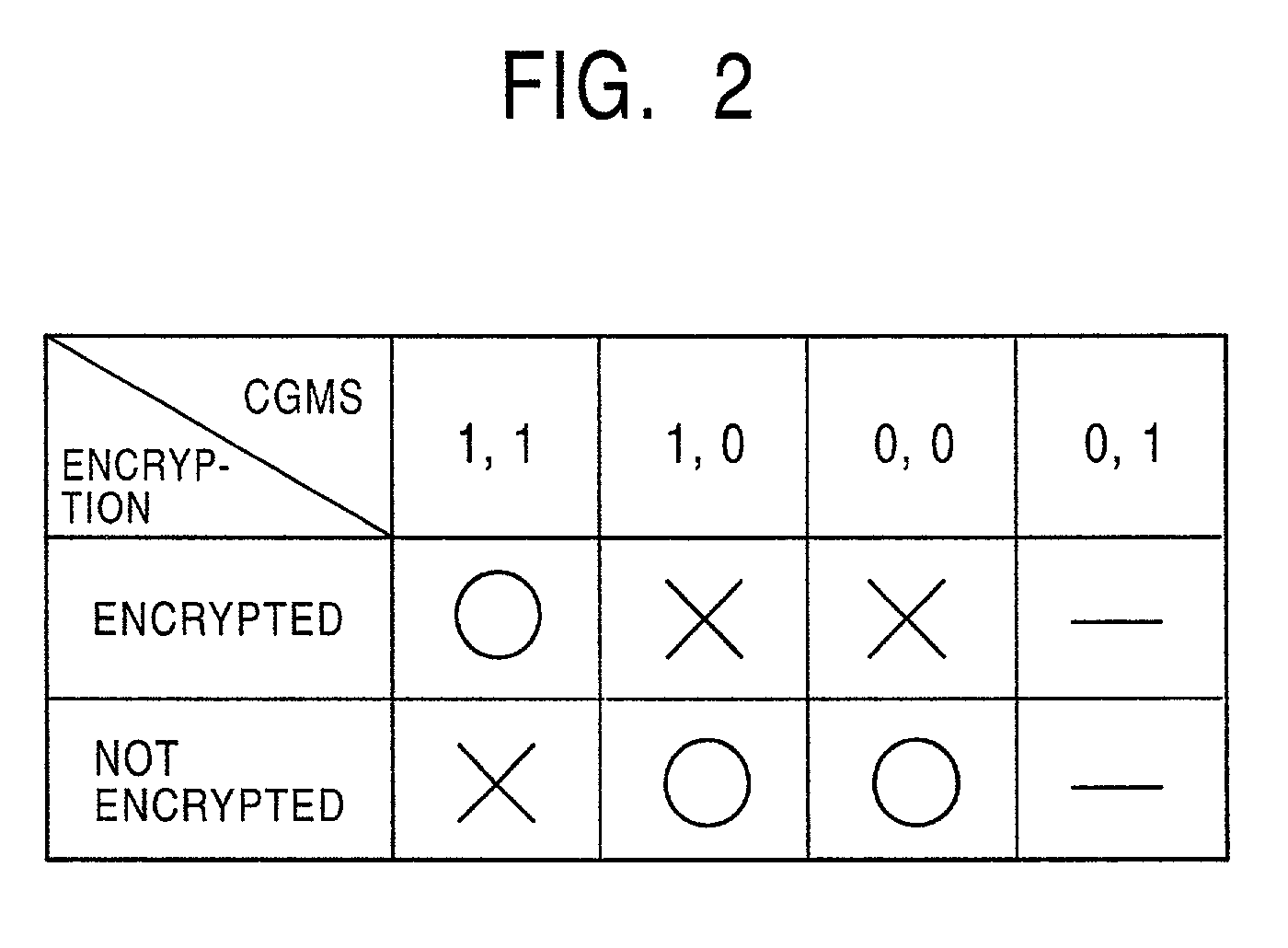
Information signal reproducing apparatus, information signal outputting apparatus, information signal reproducing method, and information signal outputting method
InactiveUS7031942B2Prevent illegal copyingAvoid loopsTelevision system detailsRecord information storageCopy controlReproduction
An information signal reproducing apparatus for reproducing an information signal from a recording medium on which the information signal, including added copy control information is recorded, comprising a first detector for detecting whether the information signal read out from said recording medium is encrypted or not-encrypted and for producing an output representative thereof; a second detector for detecting said copy control information from the information signal read out from the recording medium and for producing an output representative thereof; and a controller for selectively restricting reproduction of the information signal based on the outposts of the first detector and the second detector.
Owner:SONY CORP
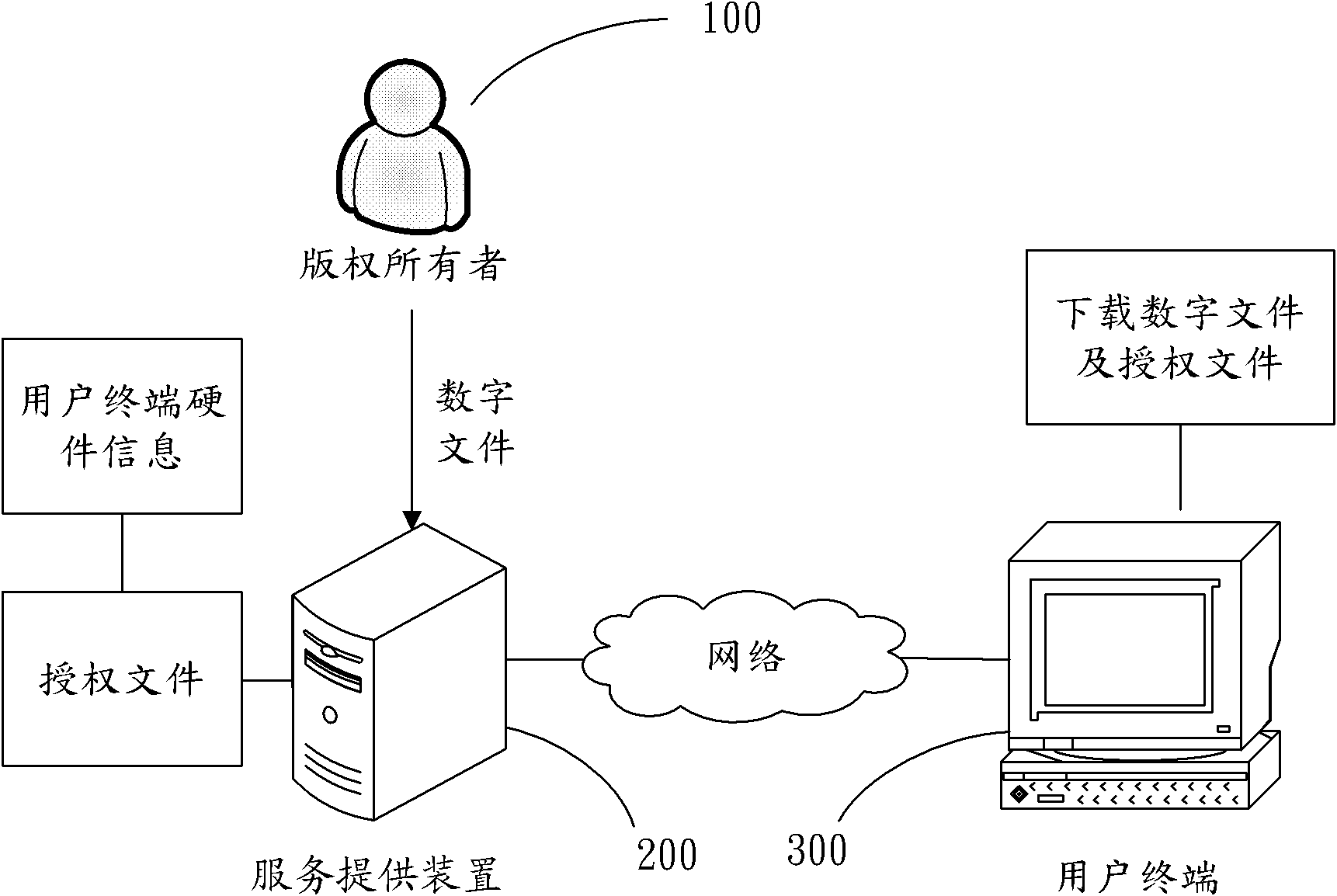
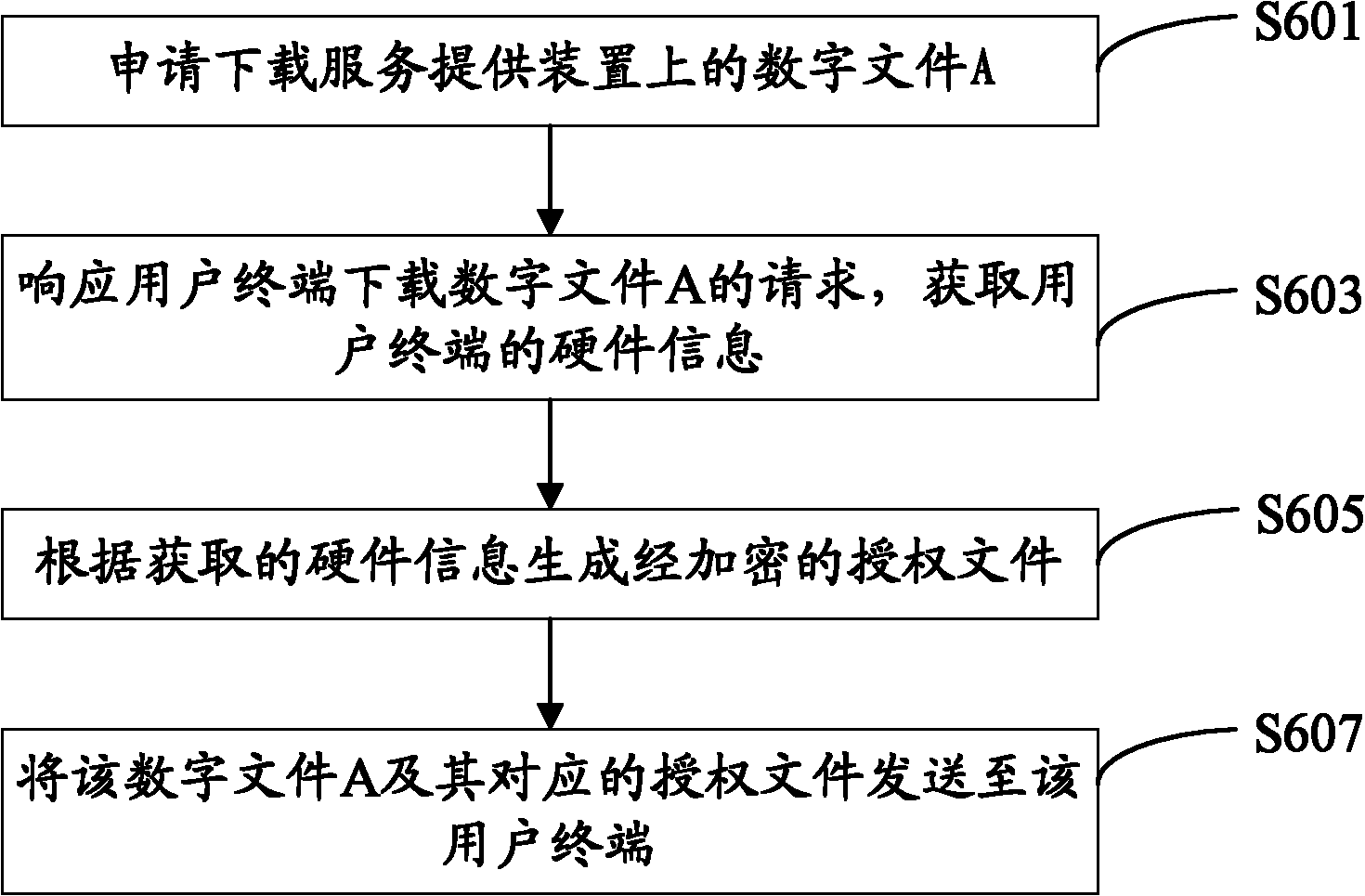
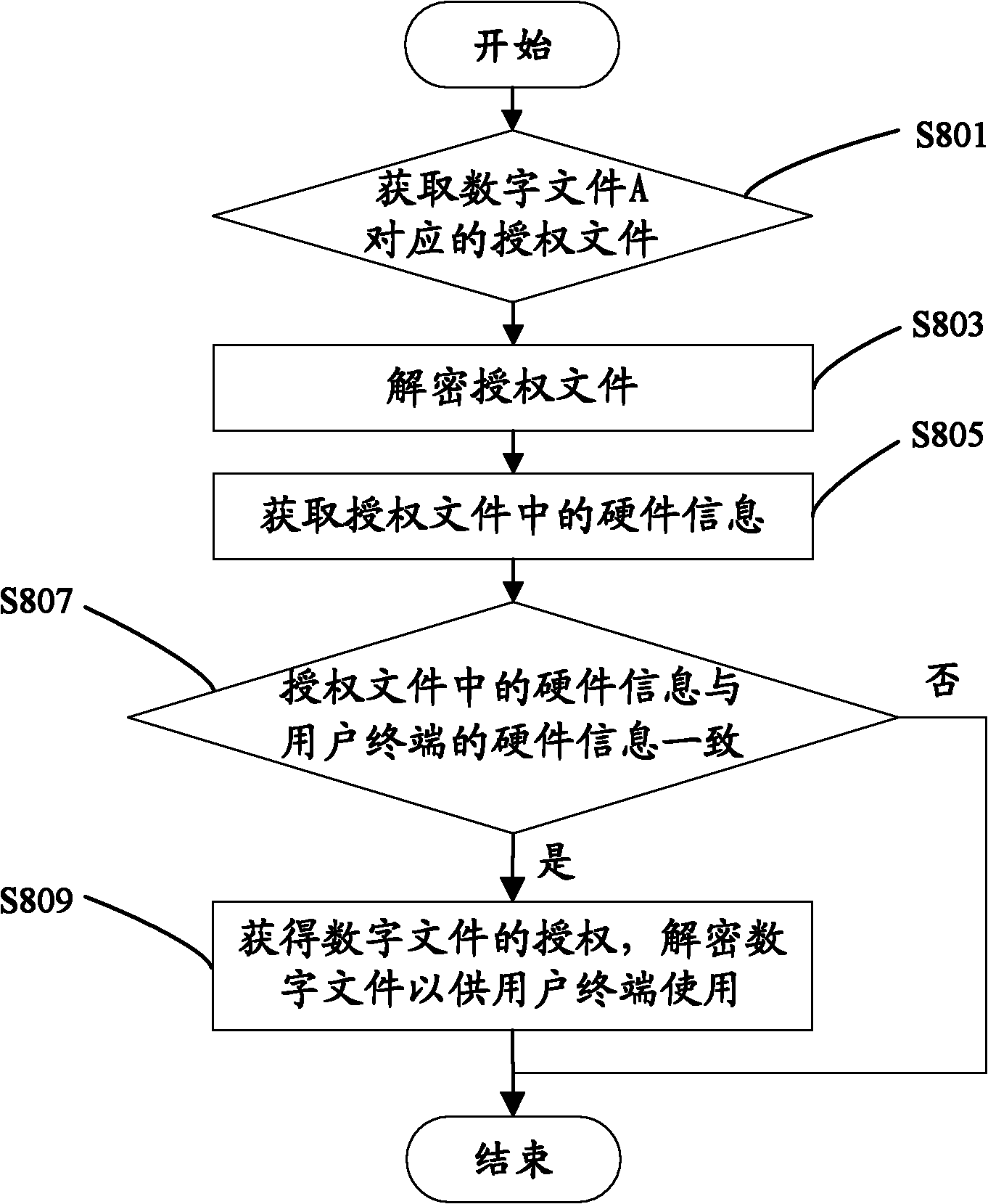
Service provision device in copyright protection, user terminal and copyright protection method
InactiveCN101923616APrevent illegal copyingProgram/content distribution protectionComputer hardwareService provision
The invention relates to a copyright protection method, which comprises the following steps of: sending a request for downloading an encrypted digital file to a service provision device by a user terminal; downloading the encrypted digital file and an authorization file corresponding to the digital file from the service provision device, and embedding hardware information of the user terminal into the authorization file; and judging whether hardware information in the authorization file is consistent with the hardware information of the user terminal or not, and when the hardware information in the authorization file is consistent with the hardware information of the user terminal, permitting the user terminal to obtain the authorization of the digital file. The hardware information of the user terminal is embedded into the authorization file, and the corresponding digital file can be used only when the hardware information in the authorization file is consistent with the hardware information of the terminal, therefore, the copyright protection method can prevent from illegally copying the digital file. The invention also provides the service provision device for preventing the user terminal from illegally copying the digital file and the user terminal capable of eligibly copying the digital file.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
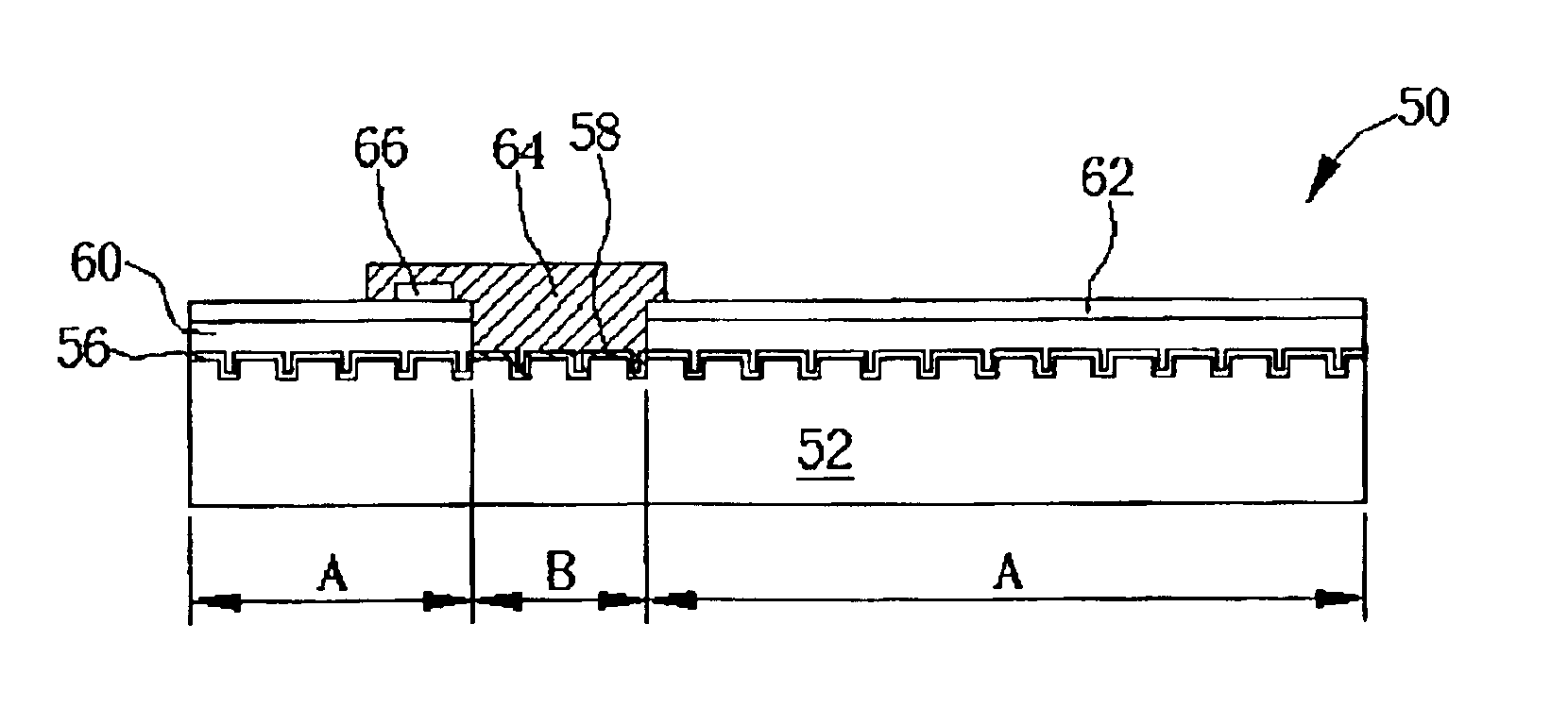
Scratch-off material layer applied on optical recording media
InactiveUS6901043B2Prevent illegal copyingOther printing matterLayered productsOptical recordingReflective layer
An optical recording medium having a scratch-off material layer includes a transparent substrate, a reflective layer formed on the transparent substrate, a protective layer formed on the reflective layer, information formed on a surface of the protective layer, and at least one opaque scratch-off material layer formed on the protective layer for disguising the information.
Owner:U TECH MEDIA
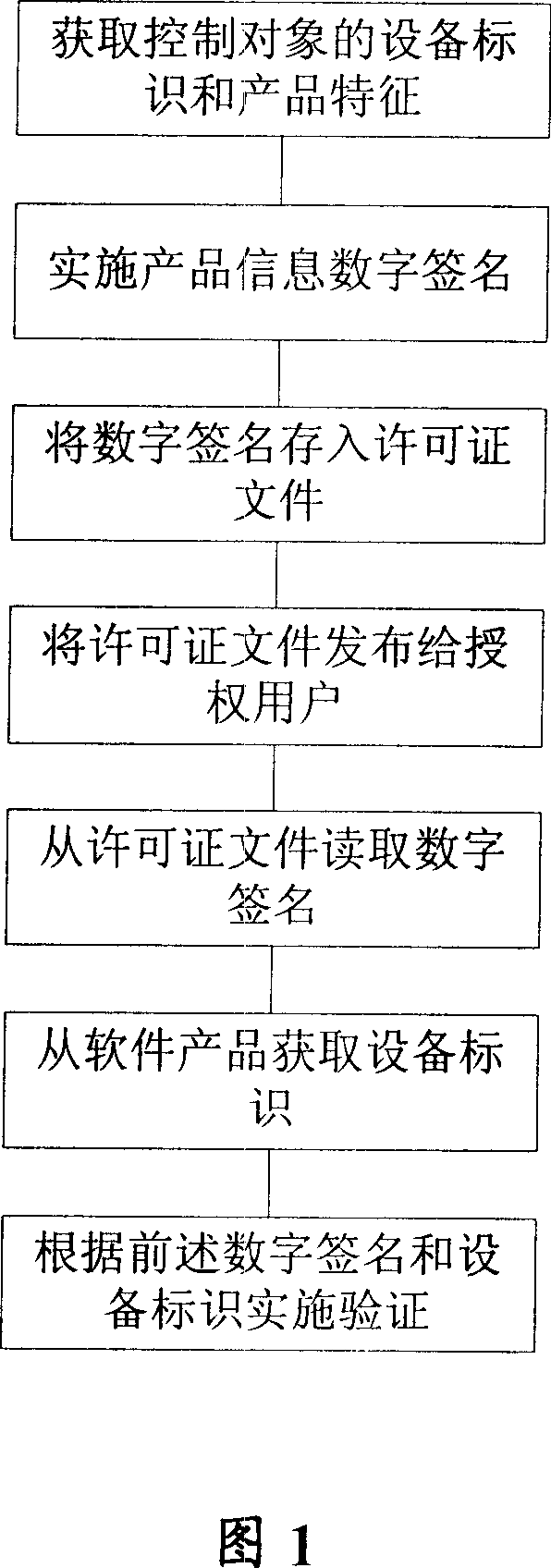
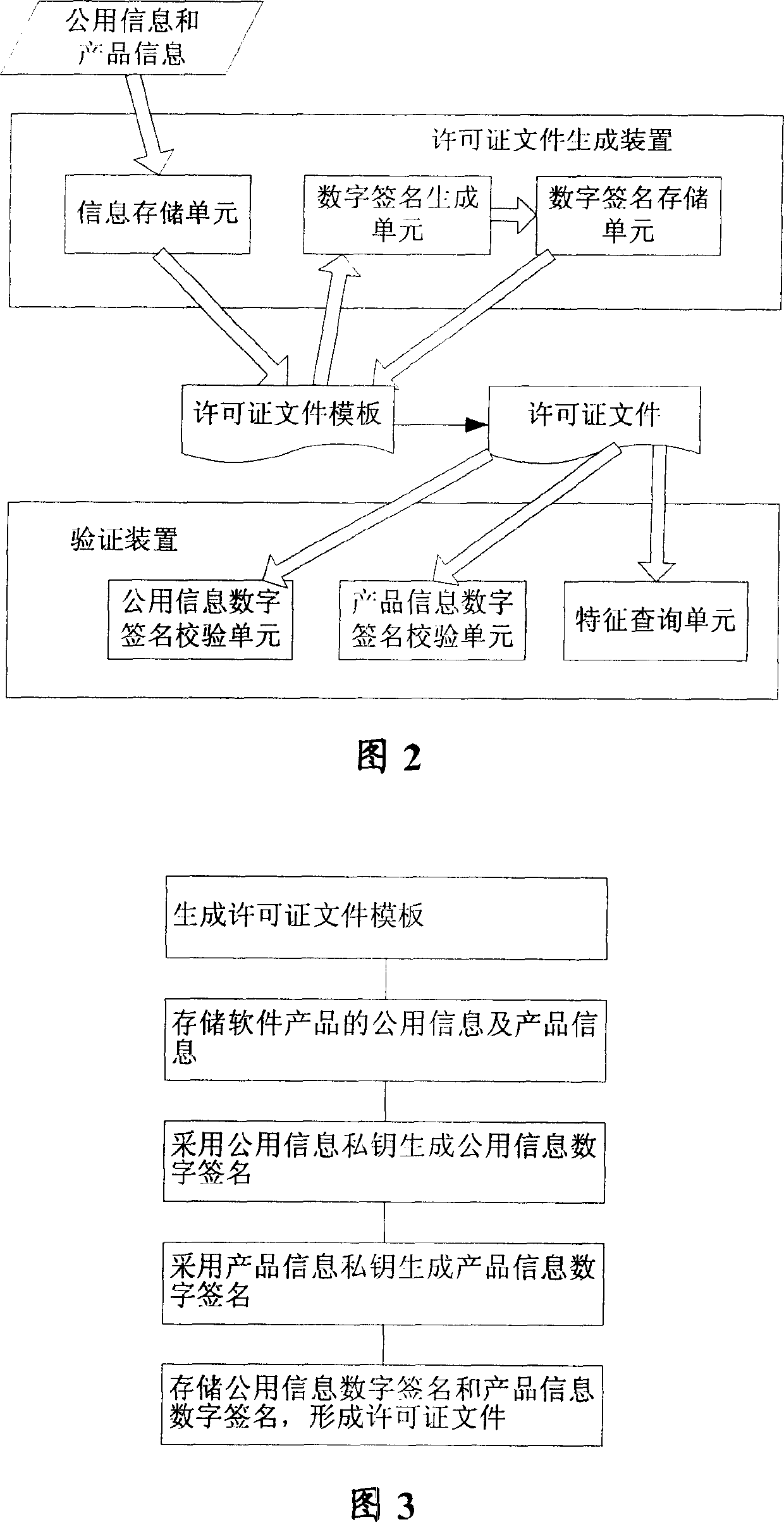
Licensing file generating method, software product protection method and system
InactiveCN1704863AIncrease the difficultyPrevent illegal copyingDigital data processing detailsComputer securitySoftware
This invention discloses a generation method for permit documents including the following steps: generating a permit document die plate, storing shared information and product information for a soft product, applying a shared information private key to generate a shared information digital signature, its cleartext data include at least the above mentioned shared information, applying a product information private key to generate its digital signature and storing the signature of the shared information and the product information in a permit document die plate to form a permit document. This invention also relates to a protection method and a system for software products.
Owner:HUAWEI TECH CO LTD
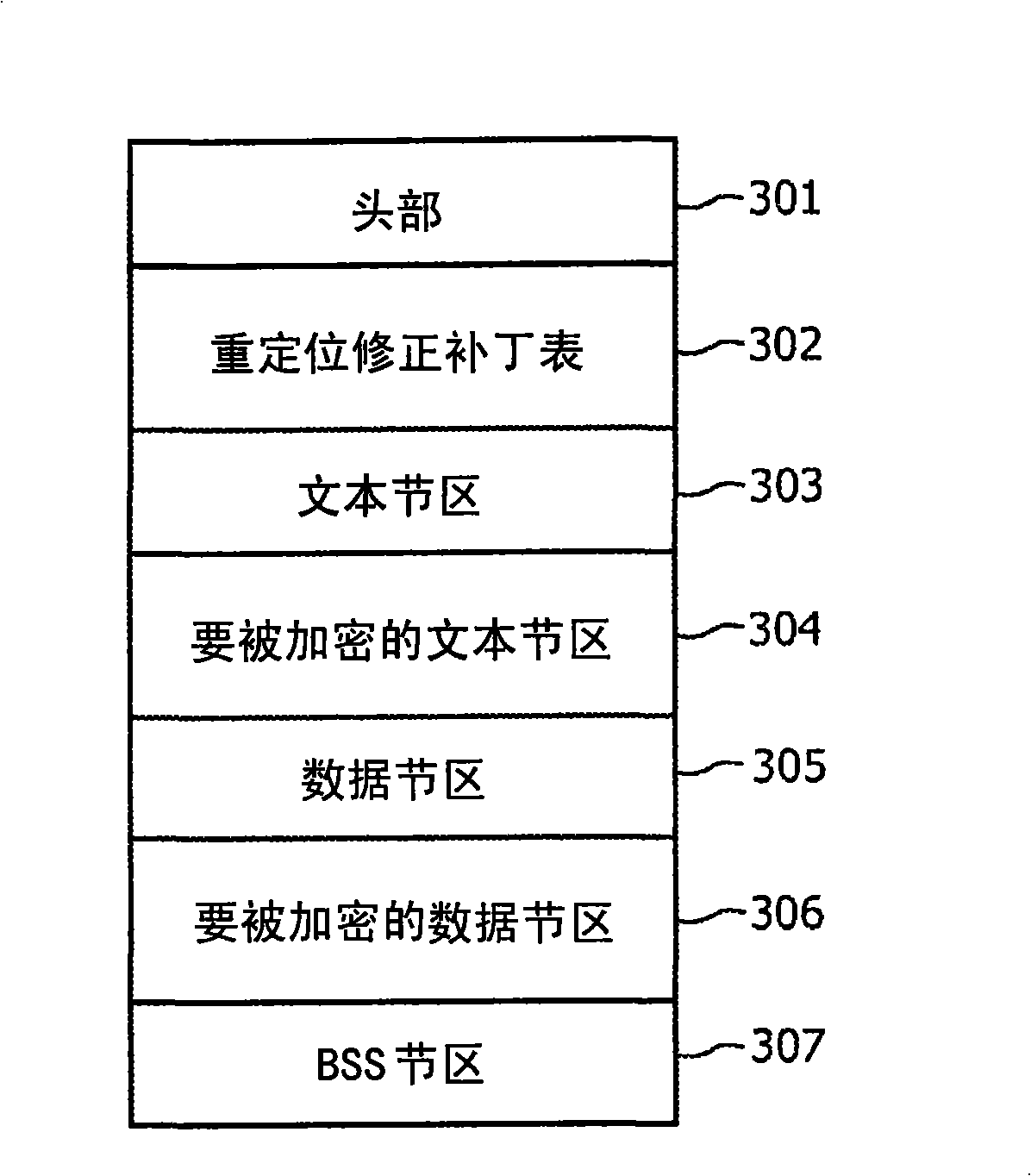
Program executable image encryption
InactiveCN101288083APrevent illegal usePrevent illegal copyingMemory adressing/allocation/relocationProgram/content distribution protectionLoad timeEncryption
The present invention provides for a method of encrypting and executing an executable image, comprising; flagging sections of the executable image to be encrypted using commands in source files and compiling said executable images so as to generate object files, linking one or more of said executable images using a linker to produce a final executable image, passing said linked executable images to a post-linker encryption engine to encrypt a relocation fix-up patch table and sections of executable images flagged for encryption, and at load time decrypting relocating and executing the executable images.
Owner:NXP BV
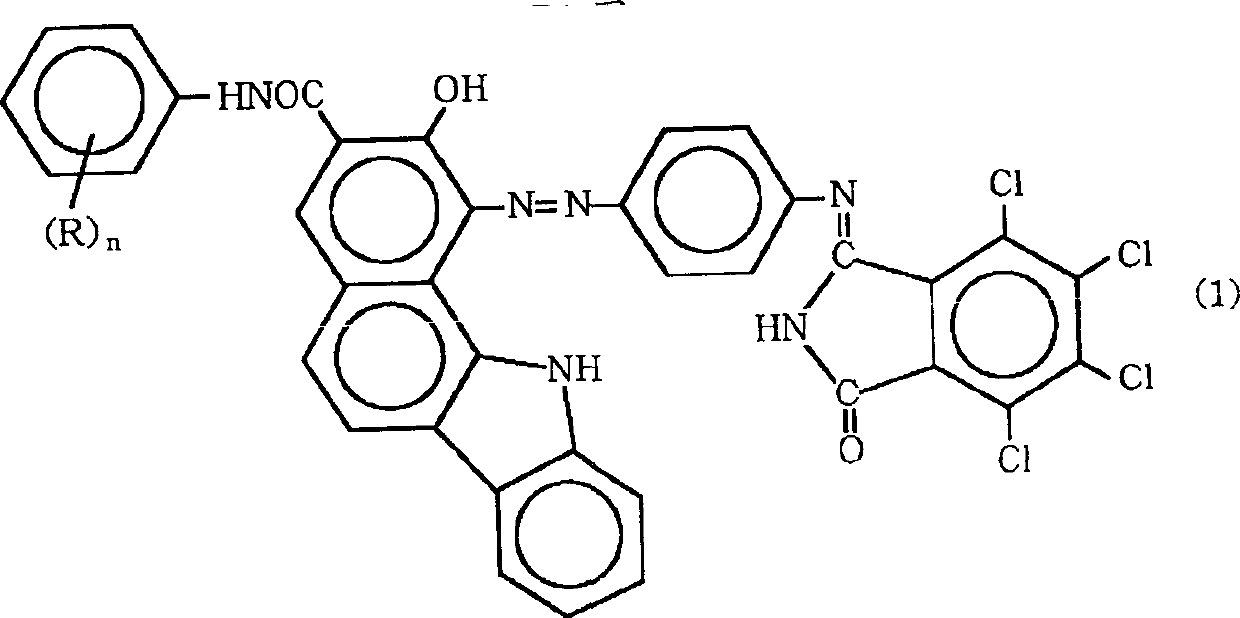
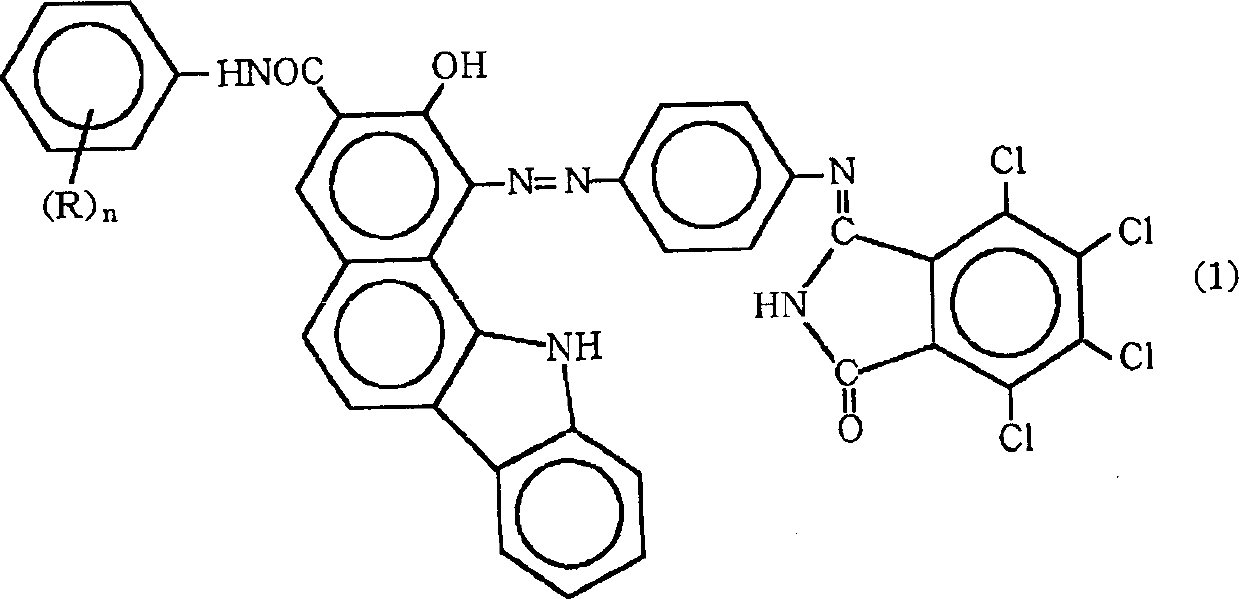
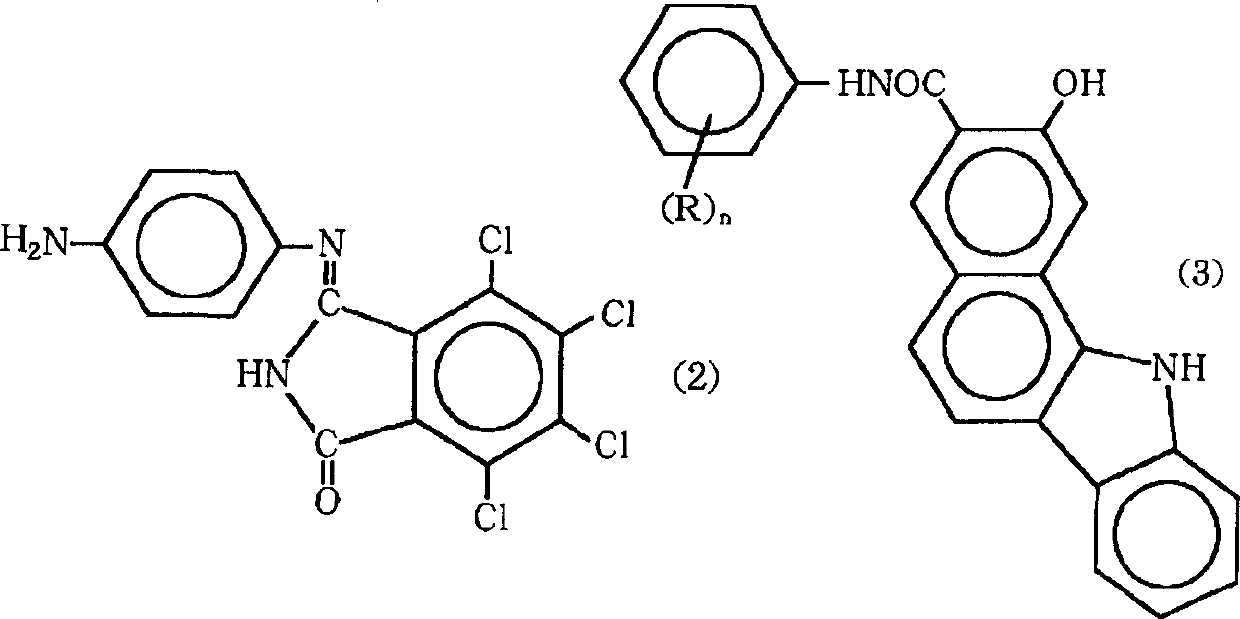
Near-infrared transmitting black azo-dye
Near-infrared transmitting black azo pigments are represented by the following formula (1) and have a crystalline form selected from the group consisting of a thin, long crystalline form and a leaf-shaped crystalline form, wherein R represents at least one group selected from the group consisting of lower alkyl groups having 1 to 3 carbon atoms and lower alkoxy groups having 1 to 3 carbon atoms, n stands for an integer of from 1 to 5, and, when n is other than 1, R may be the same or different. These near-infrared transmitting black azo pigments can be produced by treating the corresponding black azo pigments of the formula (1) with an alkali in an alcohol. Near-infrared transmitting black azo pigments compositions each comprises one or more of the near-infrared transmitting black azo pigments and a near-infrared transmitting material as a vehicle.
Owner:DAINICHISEIKA COLOR & CHEM MFG CO LTD
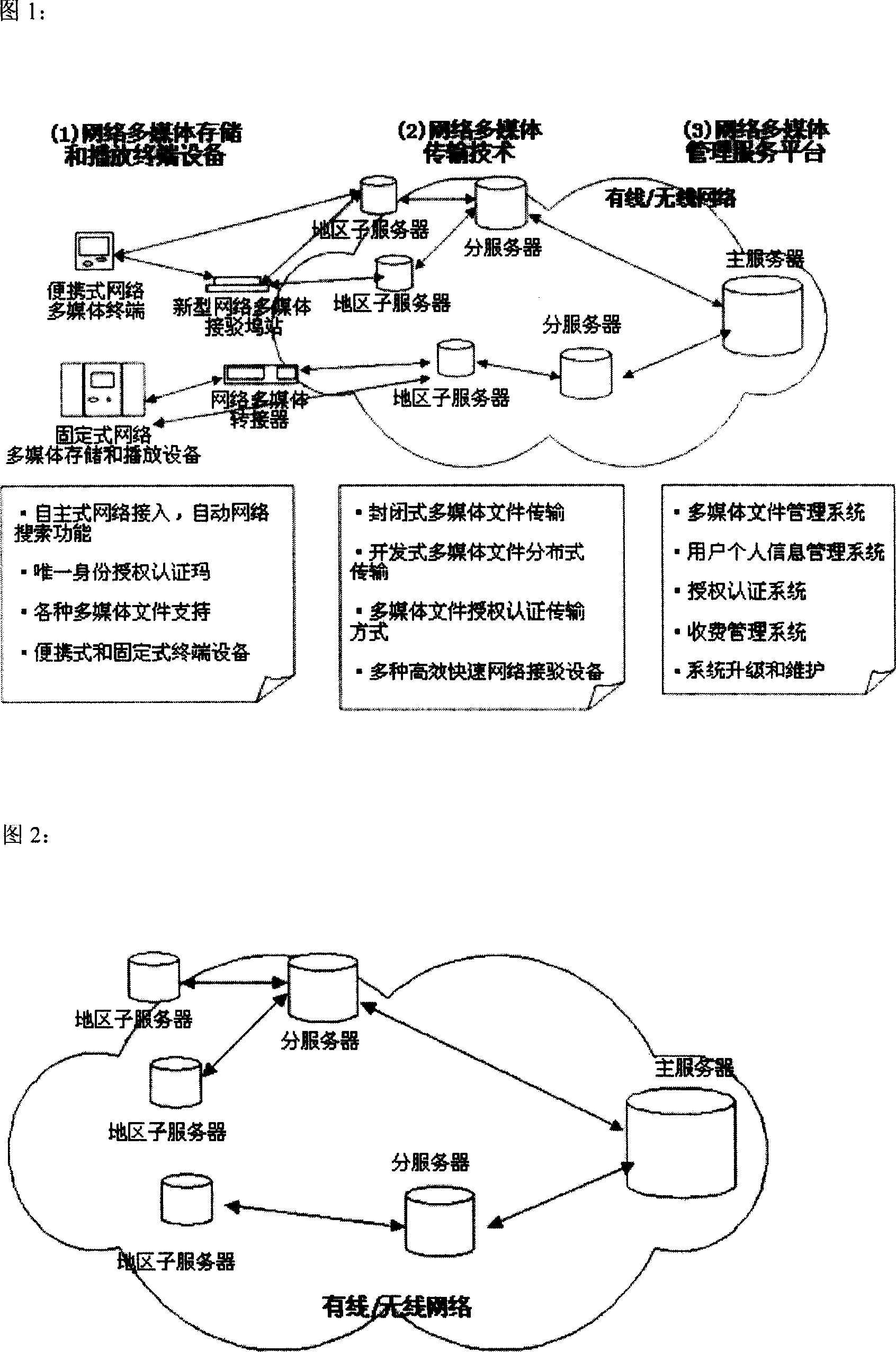
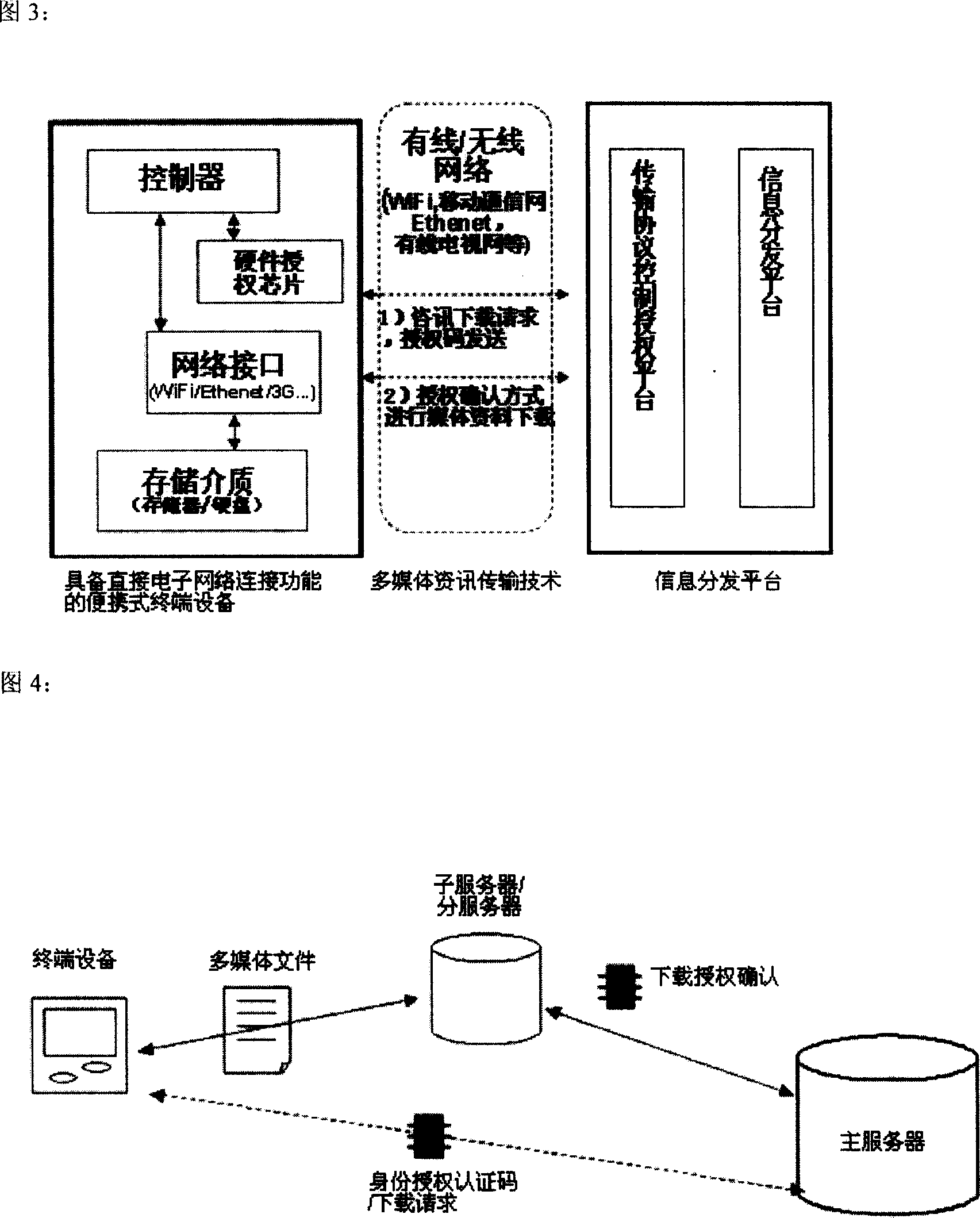
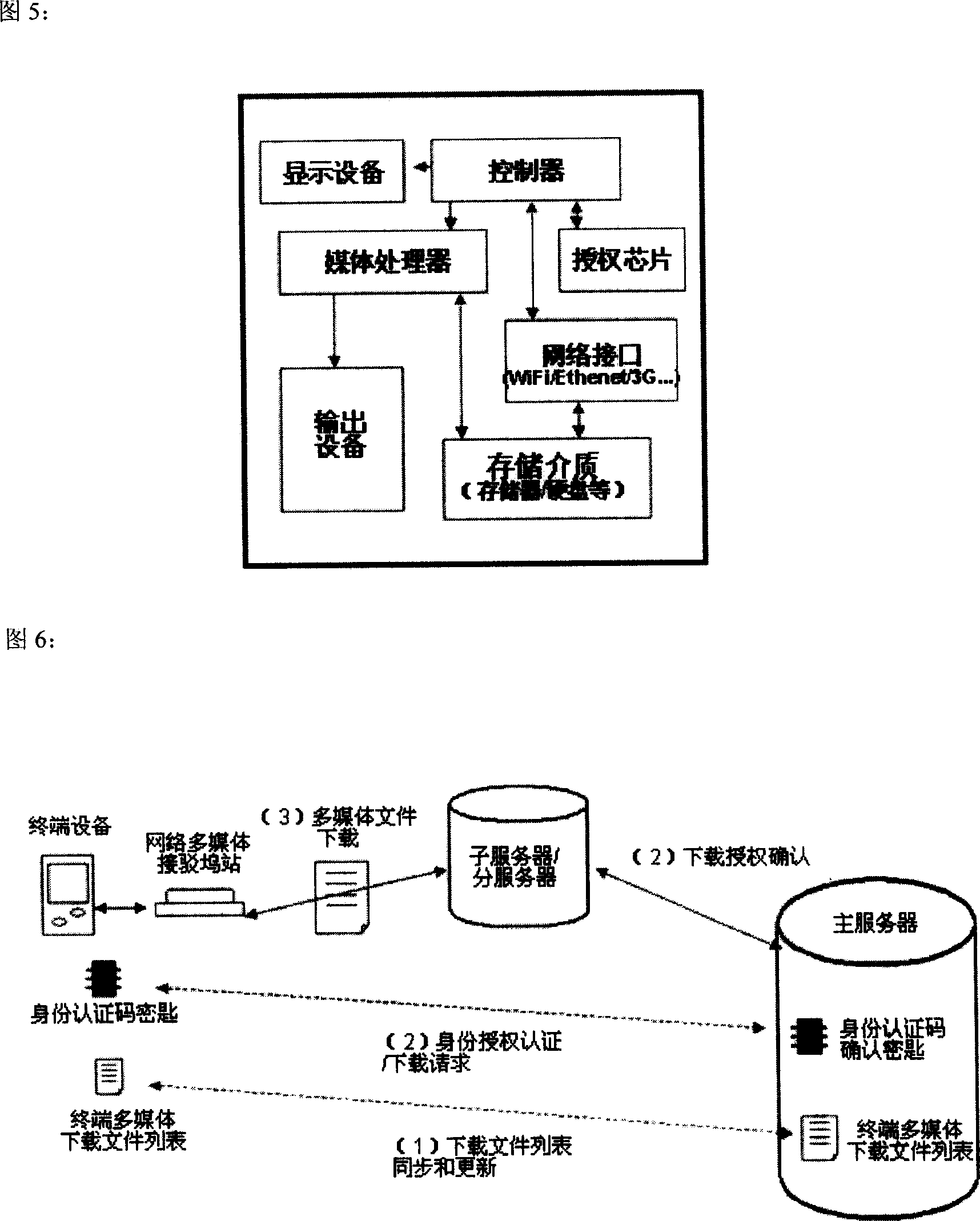
Information subscribing system for portable device with direct network connection function
ActiveCN1937611ACopyright protectionDownload guaranteeProgram/content distribution protectionData switching networksAuthorization ModeNetwork connection
The invention describes an information subscribing system in accordance with portable equipment with direct network connecting function, making data exchange with the portable equipment based on information issuing platform, by electronic network and by distributed transmission concept and ID authorization mode with uniqueness, thus implementing high-efficiency multimedia message transmission, so that terminal users can conveniently and in high efficiency obtain multimedia messages, preventing illegal copying and implementing copyright protection.
Owner:张闻麒
ISCSI disc array controller with internal path redundant function
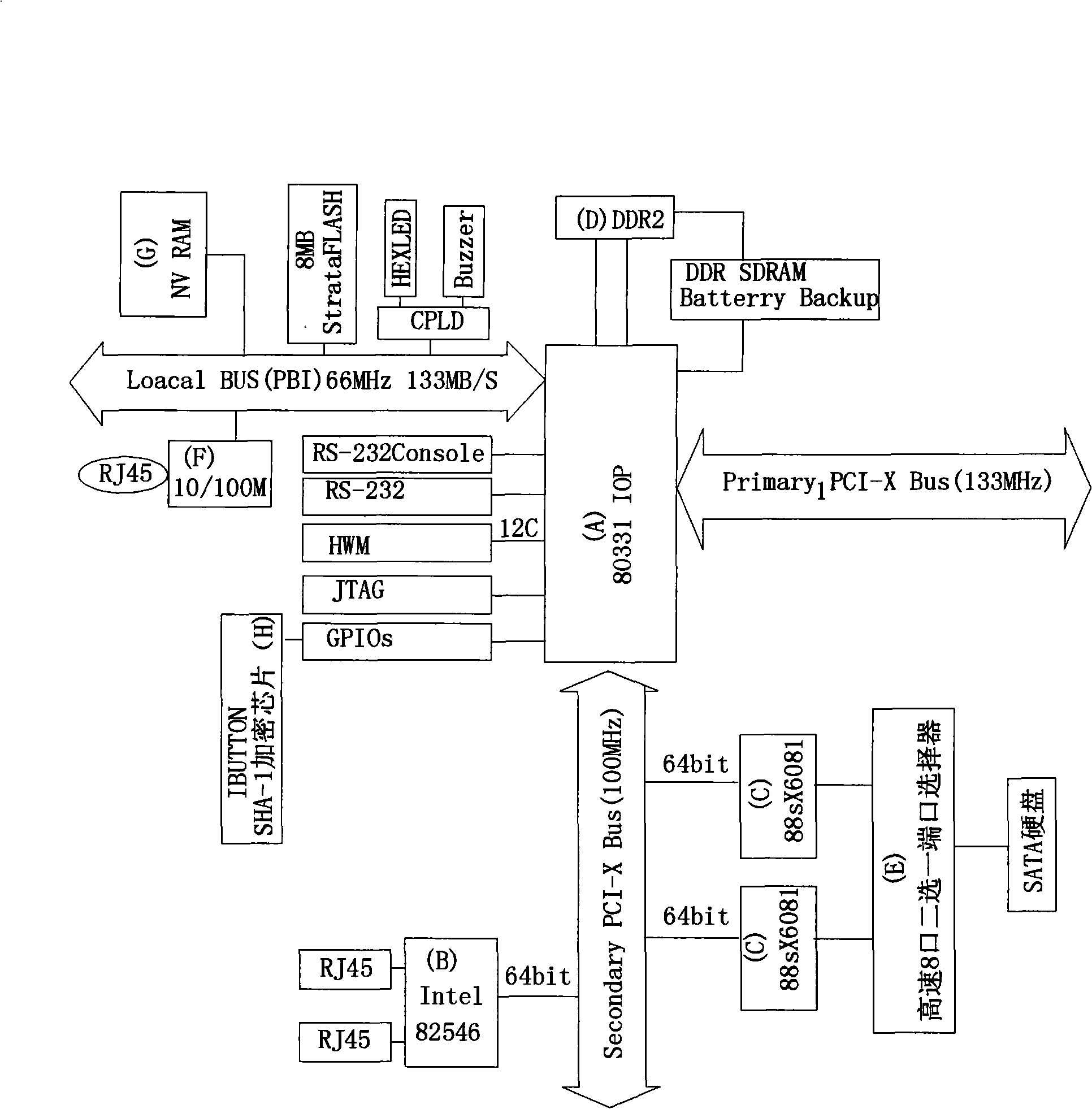
InactiveCN101359279AAchieving Path RedundancyImprove reliabilityInput/output to record carriersTransmissionCopyingGigabit Ethernet
The invention discloses an embedded IOP331 processor, which integrates a master CPU, a DDR2 memory, a dual-gigabit Ethernet, a dual-SATA disk controller and other major chips on a signal mainboard and can realize the single-path access and control of the maximum 16 SATA disks and also supports the dual-path redundancy control of 8 hard drives of a stand-alone. The host end can adopt the standard ISCSI agreement to realize the RAID creation, zoning and other disk operations of the SATA disks. The invention not only realizes the ISCSI disk array controller functions of a single mainboard, but also selectively provides the path redundancy of 8 disks and the path redundancy of the dual-gigabit Ethernet host in the controller based on the provision of 16-bit ISCSI access and RAID operations, so as to greatly improve the reliability of the disk array system under a single controller. The invention achieves high availability and high reliability, on the basis of low cost. At the same time, in order to prevent illegal copying of software products, the invention integrates a security chip with an SHA-1 encryption engine for the security encryption of the entire system.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Server side for providing digital content in encryption mode
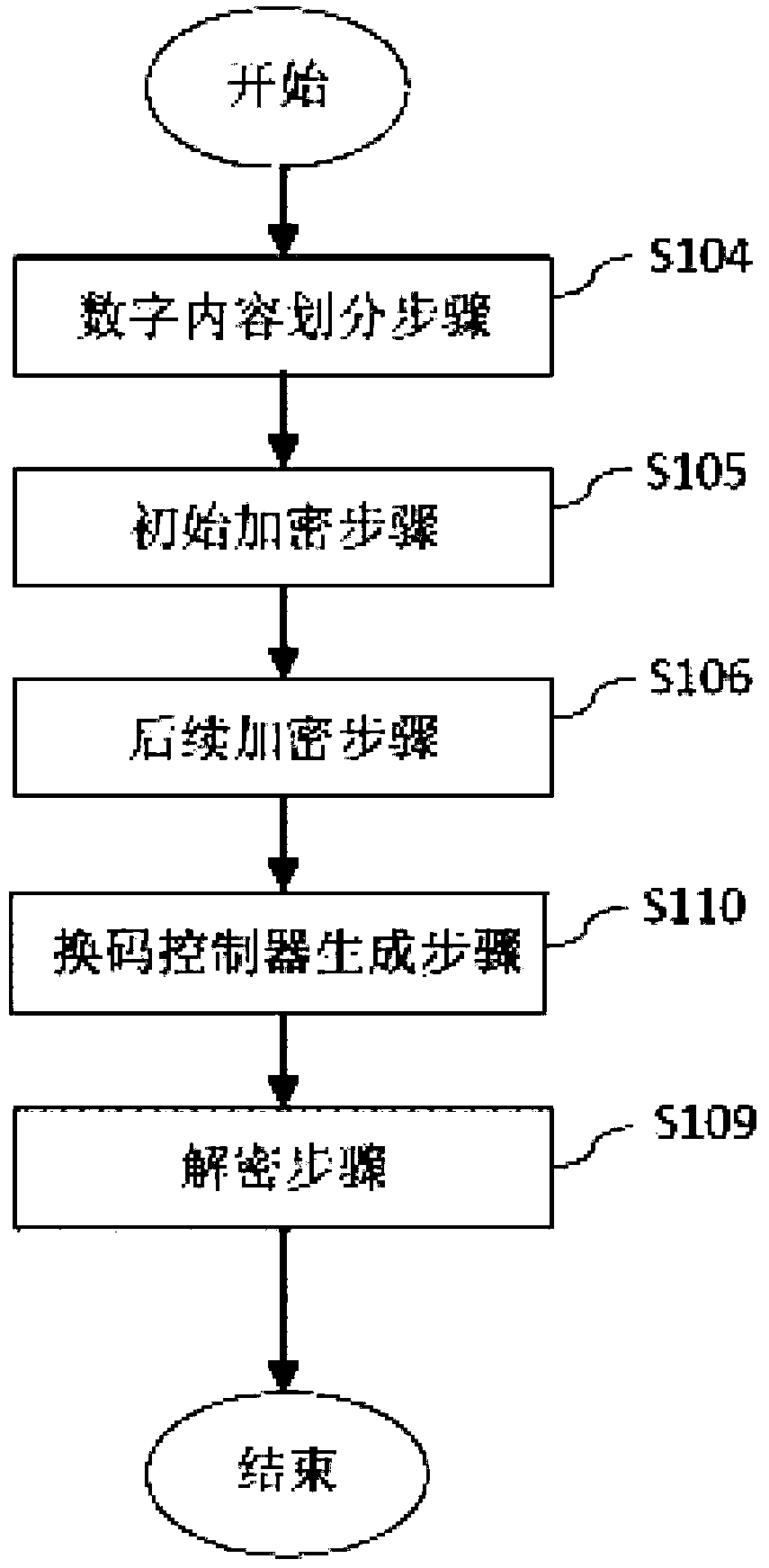
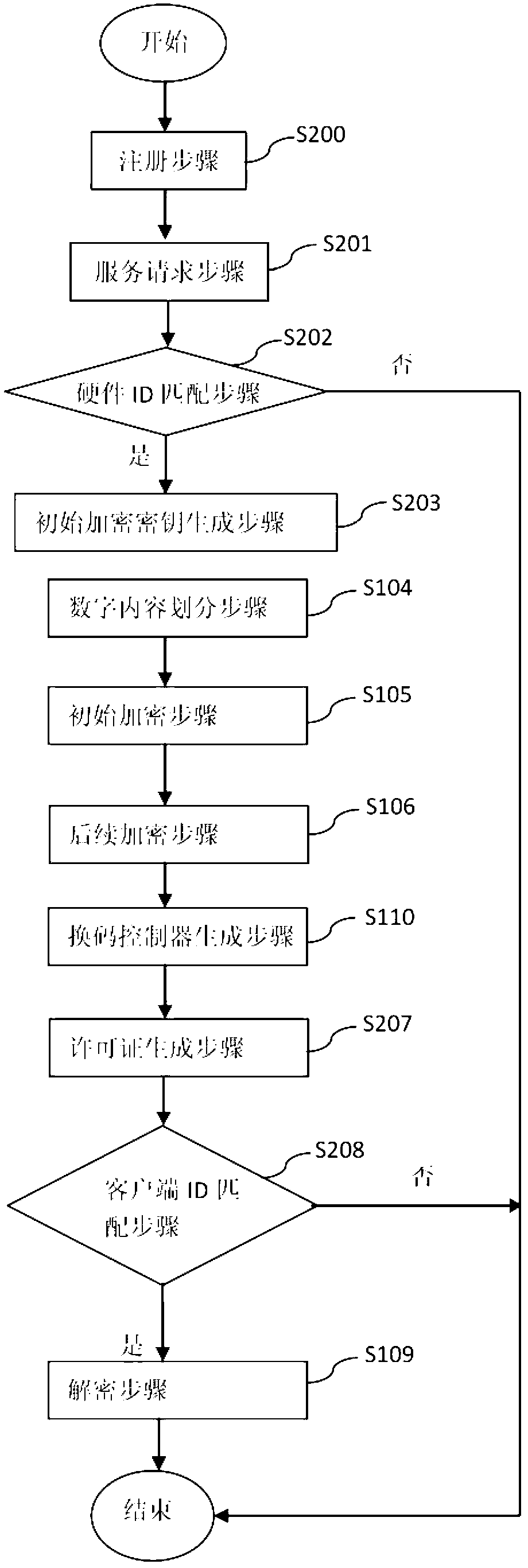
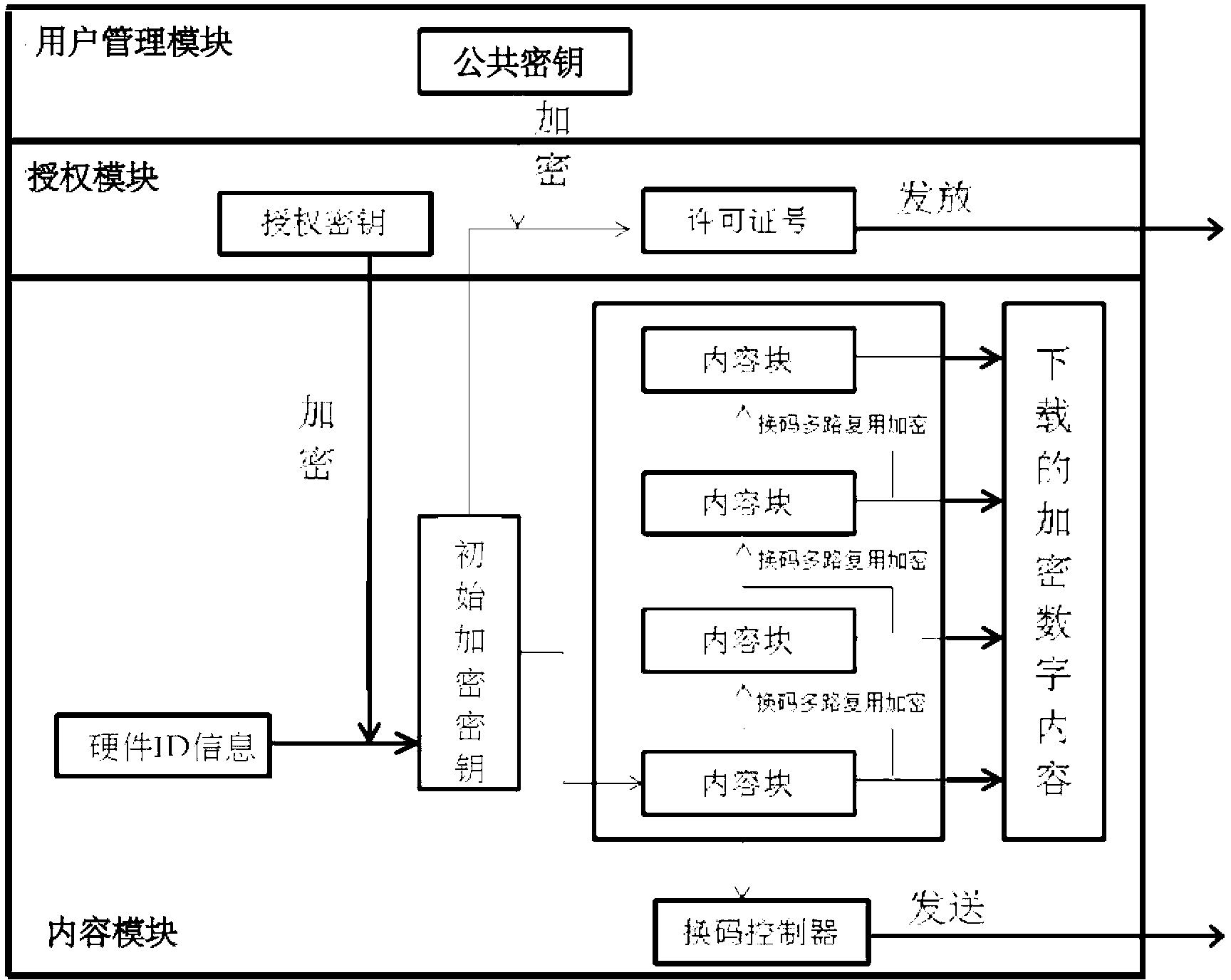
The invention provides a server side for providing digital contents in an encryption mode. The server side for providing the digital contents in the encryption mode comprises a user management module, an authorization module and a content module. The server side divides the digital contents into a plurality of blocks by the use of data segmentation technique, each content block is encrypted and decrypted in order by the use of the information related to client's hardware ID (identification), and the hardware ID information comprises CPUID (central processing unit identifier) information, hard disk volume number information, BIOS (basic input output system) information, network card MAC (media access control) addresses, IP (internet protocol) addresses and combination of above information. The server side has the advantages that with the client's hardware ID information used during the authentication process and the encryption process, security during the communication process is ensured, and encryption efficiency is improved.
Owner:北京中科联众科技股份有限公司
Video frequency data copying control system and method
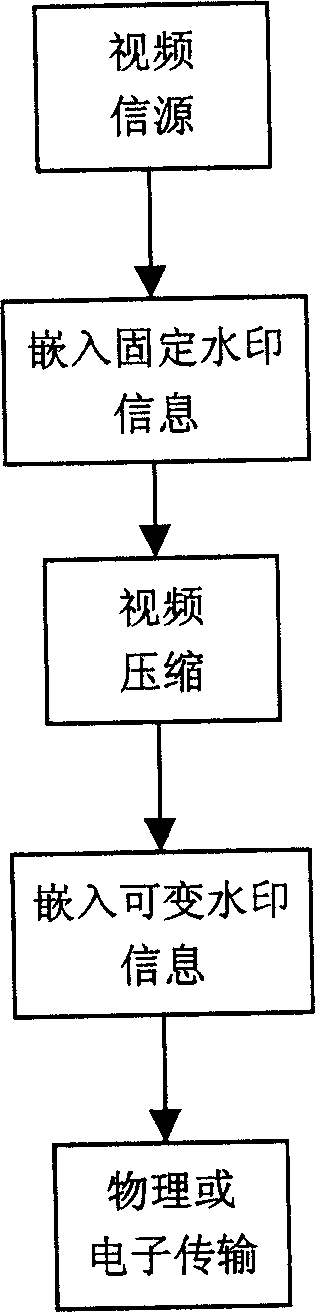
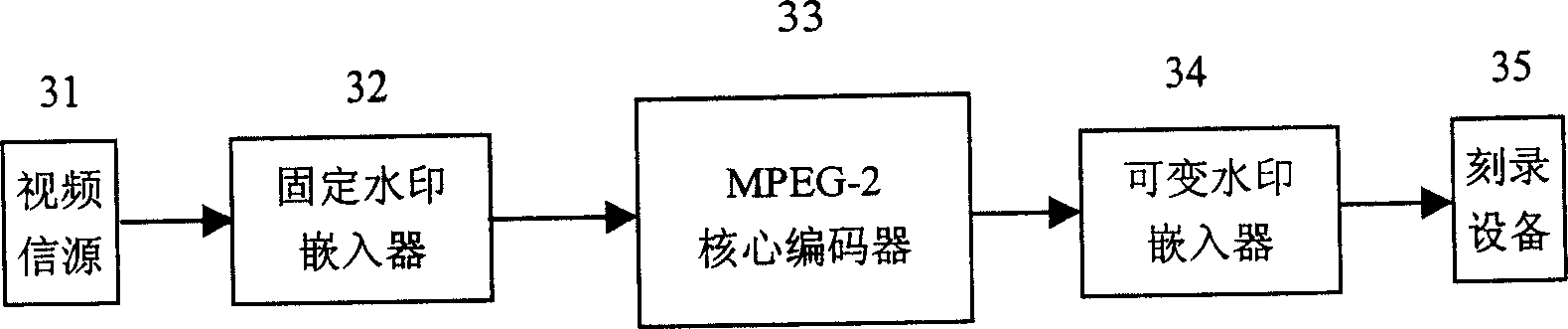
InactiveCN1512769APrevent illegal copyingTelevision system detailsColor television detailsControl systemArtificial intelligence
This invention relates to a video data duplication control system including a video compound water-mark inserting system for inserting a fixed and a variable water marks into a video signal source, a pick-up and detection system for detecting fixed and variable water-mark information inserted in video data to determine the source allowance duplication state, a modification system for modifying variable water-mark information. The method includes detecting variable water-mark information to determine its allowance duplication state and to modify variable water-mark information when it expresses it can duplicate the video data to register the data and modified information on media.
Owner:TIANJIN UNIV +1
Method and device for registration code generation, and method and device for software registration
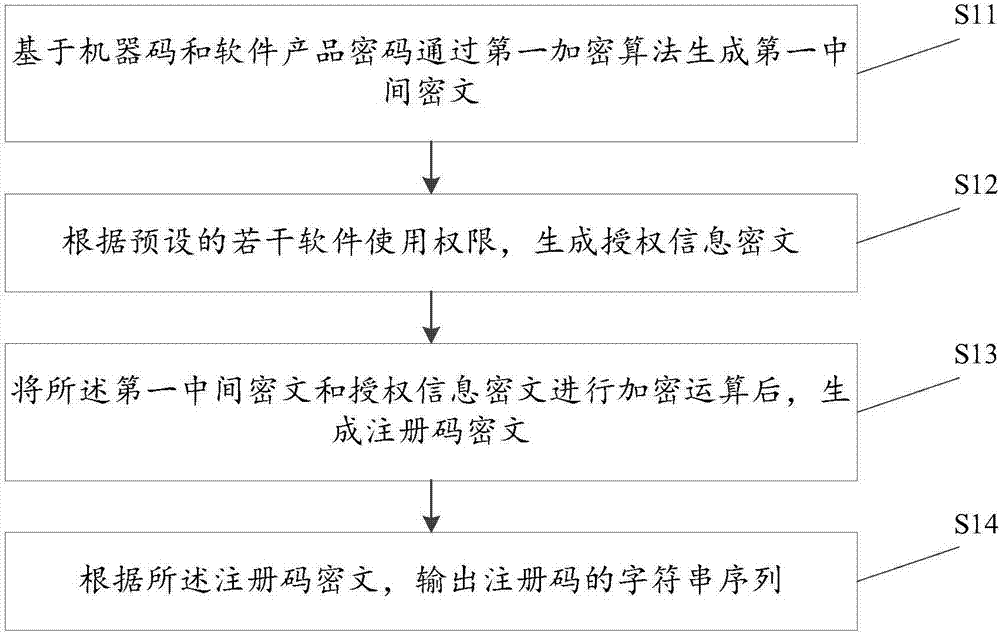
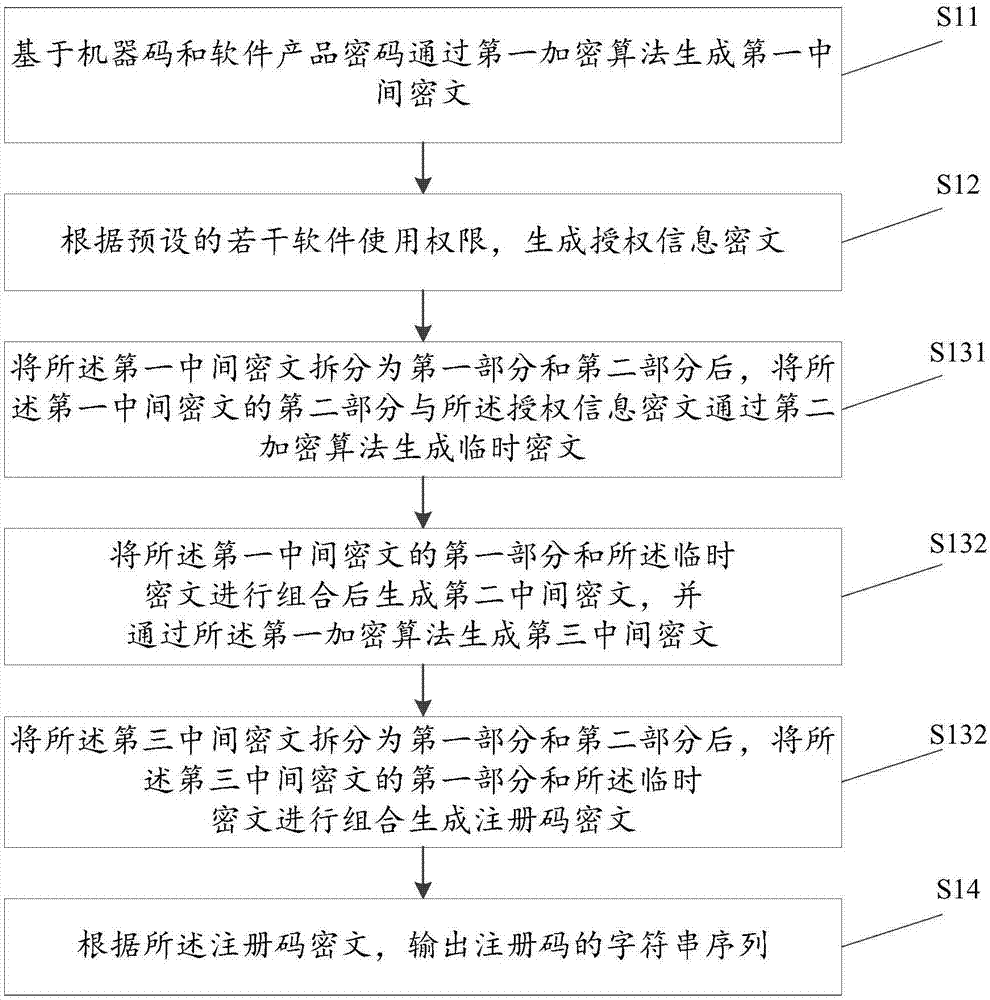
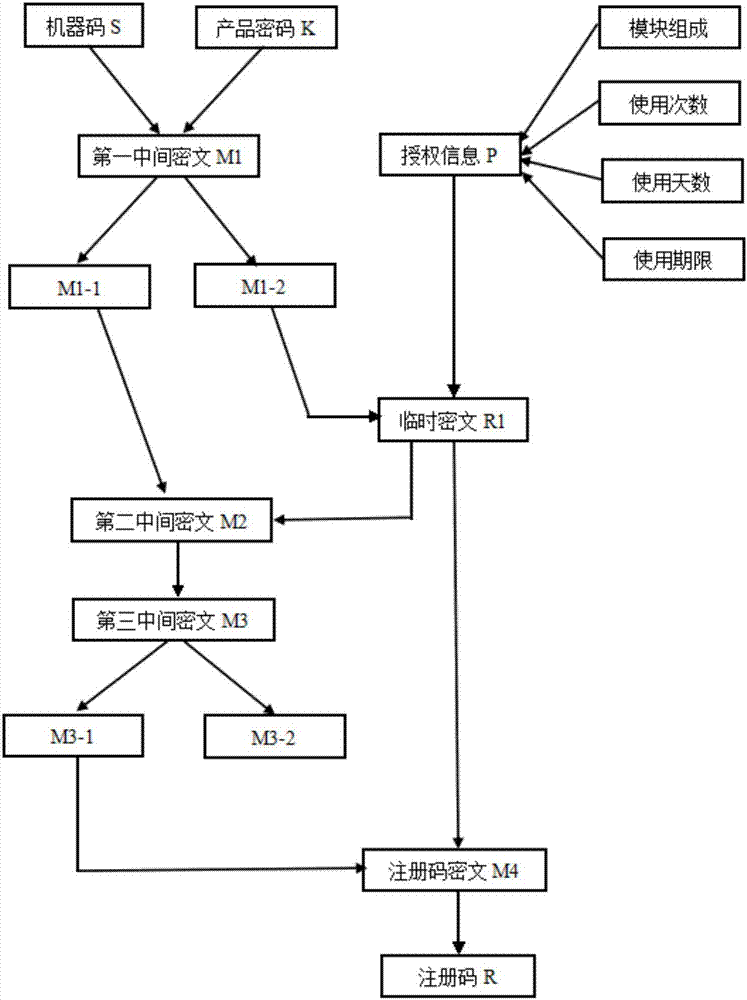
ActiveCN106919810AOvercoming the lack of informationOvercome functionProgram/content distribution protectionSoftware developmentAuthorization
The invention discloses a method for registration code generation. A registration code comprises three types of information including a machine code, software product passwords and several software permissions, wherein the machine code can prevent illegal software use situations such as illegal copying and installation of software, re-installation of a reinstalled system and reinstallation after expiration of agreed trial conditions; by the different software product passwords, software developers can use the same software registration protection method to protect various types of software products; and in addition, setting of different software permissions can satisfy diversified demands of different users, and control is flexible. Hence, the scheme can effectively overcome the detects that existing registration codes only contain a little of information and single functions and can avoid the problems that authorization courses with application of a license document are too complicated and parameters are fixed, so users' input becomes convenient; and only the registration codes need to be changed when a software trial stage is switched to a formal use stage, re-installation is not needed, and operations are convenient and rapid.
Owner:GRG BAKING EQUIP CO LTD
Confidential method for set-top box software
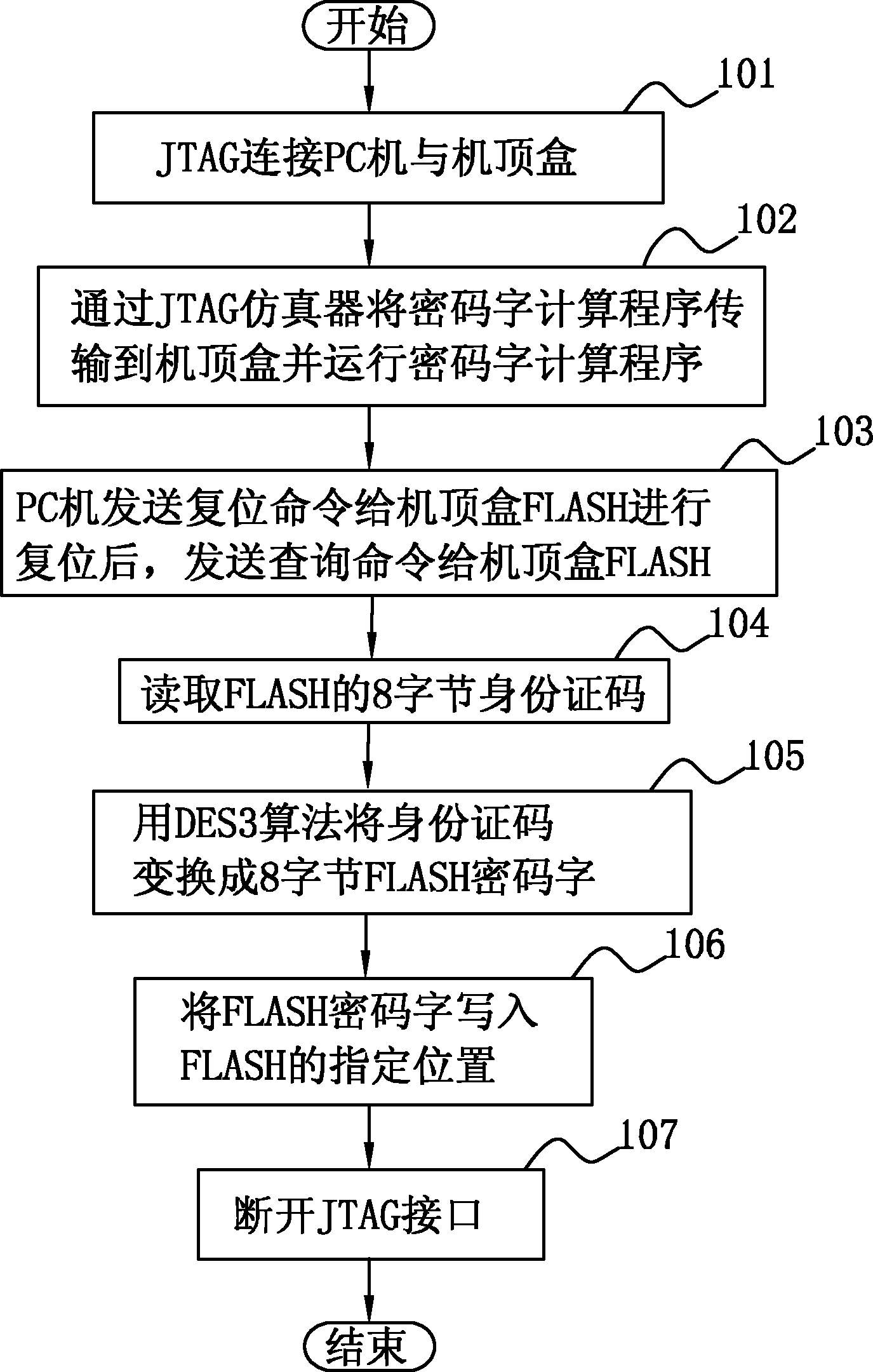
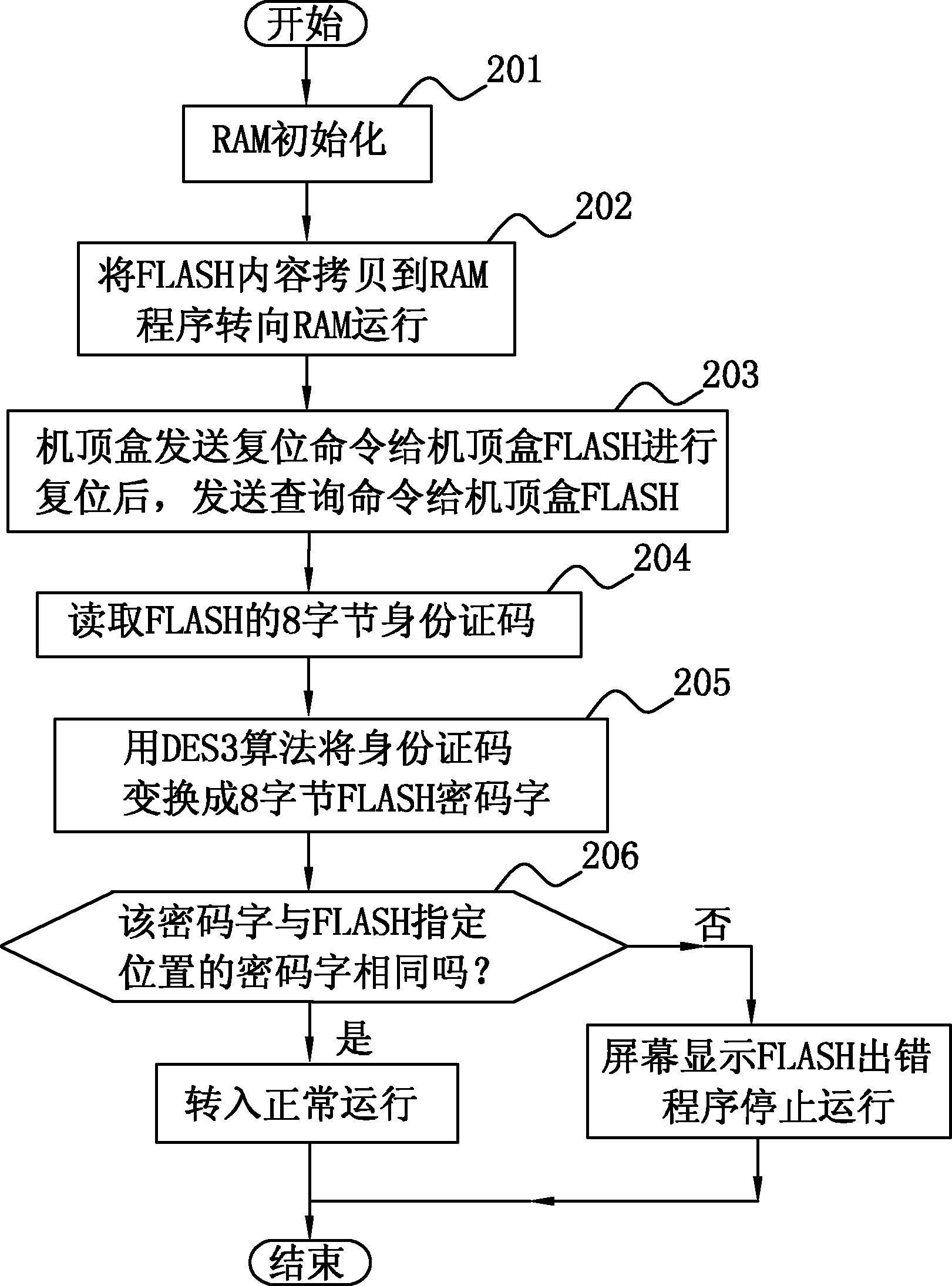
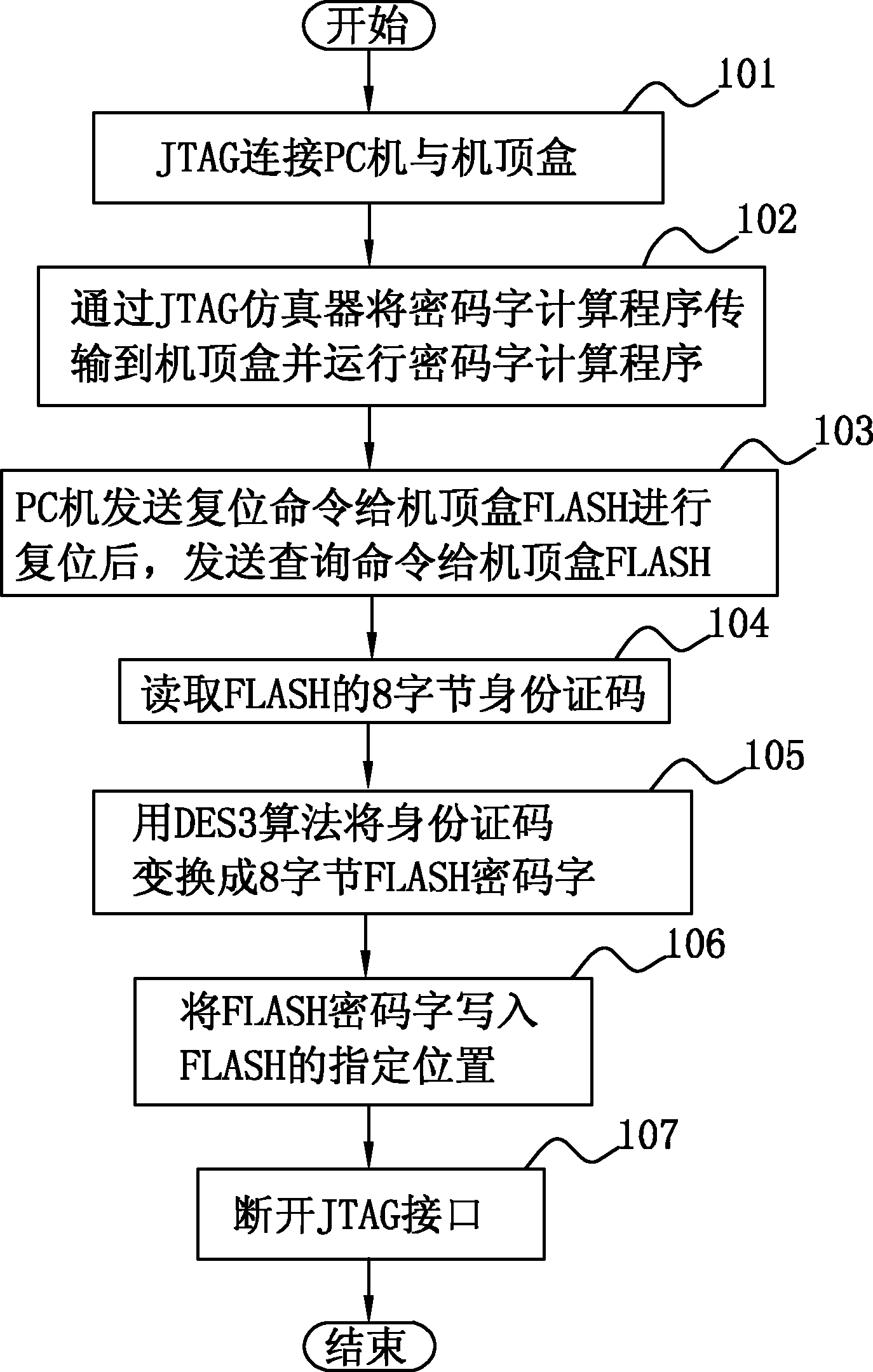
InactiveCN102104801ACopyright protectionPrevent illegal copyingSelective content distributionProgram/content distribution protectionElectricityPersonal computer
The invention discloses a confidential method for set-top box software, which comprises that: a personal computer (PC) is connected with a set-top box by a joint test action group (JTAG) simulator, a central processing unit (CPU) of the PC transmits a code word calculation program to a random access memory (RAM) of the set-top box by the JTAG simulator, and the code word calculation program automatically reads an identity code of a set-top box FLASH, calculates a code word by using a data encryption standard (DES) 3 algorithm and writes the code word into a given position in the set-top box FLASH; and the set-top box is initialized after being electrified, the CPU of the set-top box runs the code word calculation program to calculate the code word of the set-top box FLASH, and compares the calculated code word with the code word, obtained by the step A, at the given position in the set-top box FLASH, and the set-top box is normally run if the code words are consistent, otherwise displays a FLASH running error prompt in a display interface thereof and terminate the running of the program. Due to the adoption of the method, the software is effectively prevented from being illegally copied with simple operations on the basis of not increasing hardware cost.
Owner:FUJIAN ERLING ELECTRONICS
Client system and method of digital rights management and digital rights management system
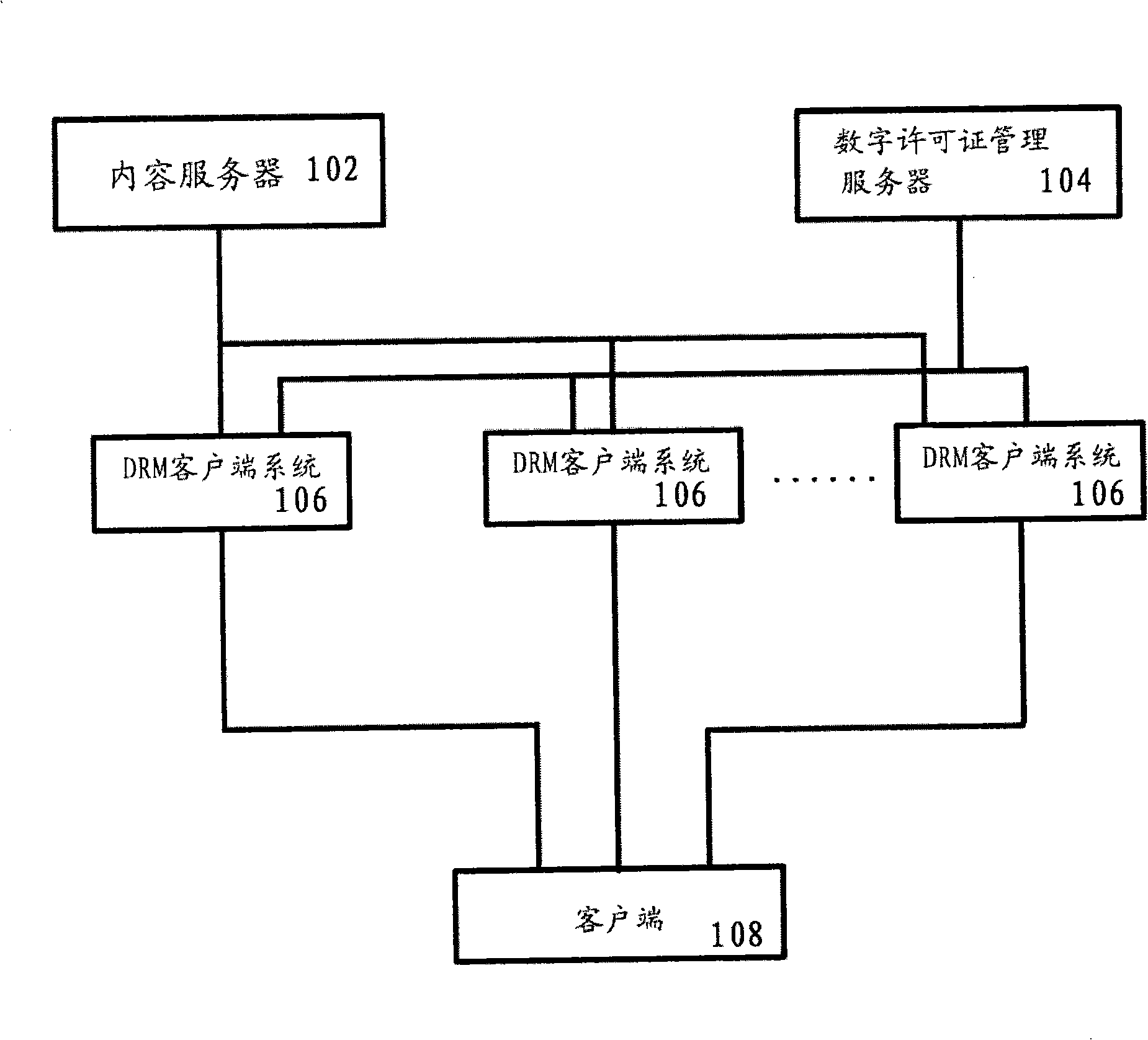
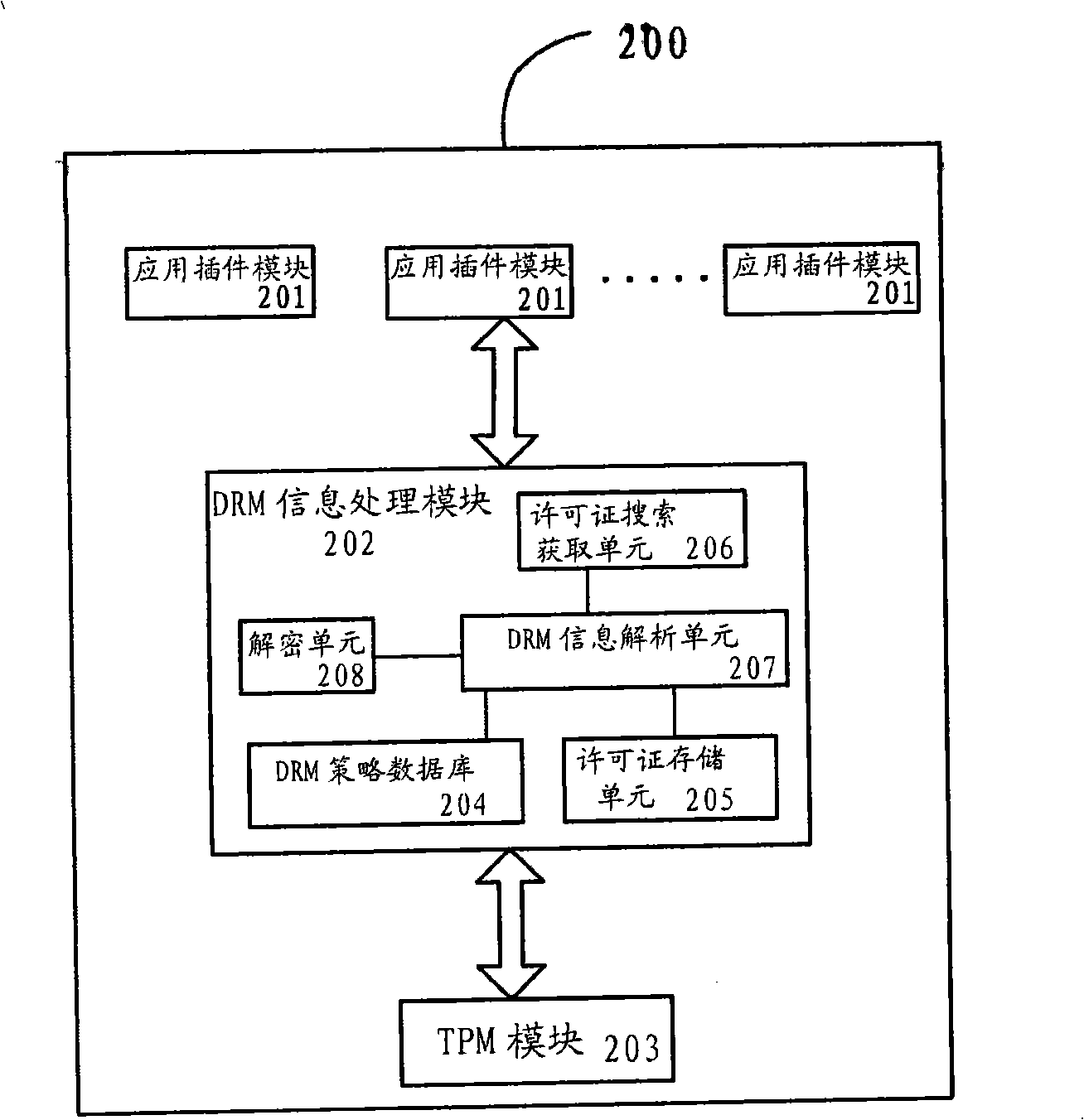
InactiveCN101526985AWith DRM functionLow costTransmissionProgram/content distribution protectionDigital dataInformation processing
Owner:SONY CHINA
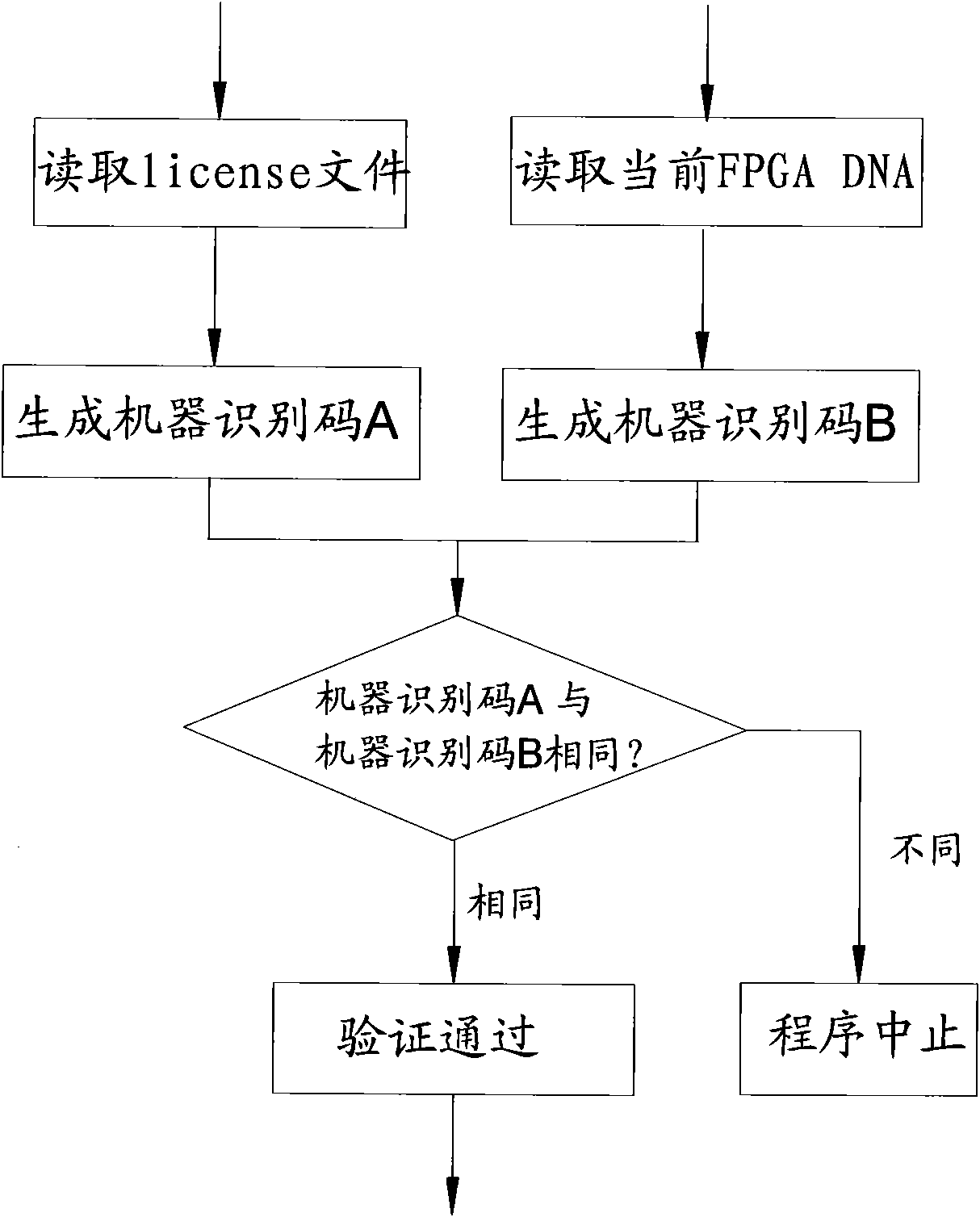
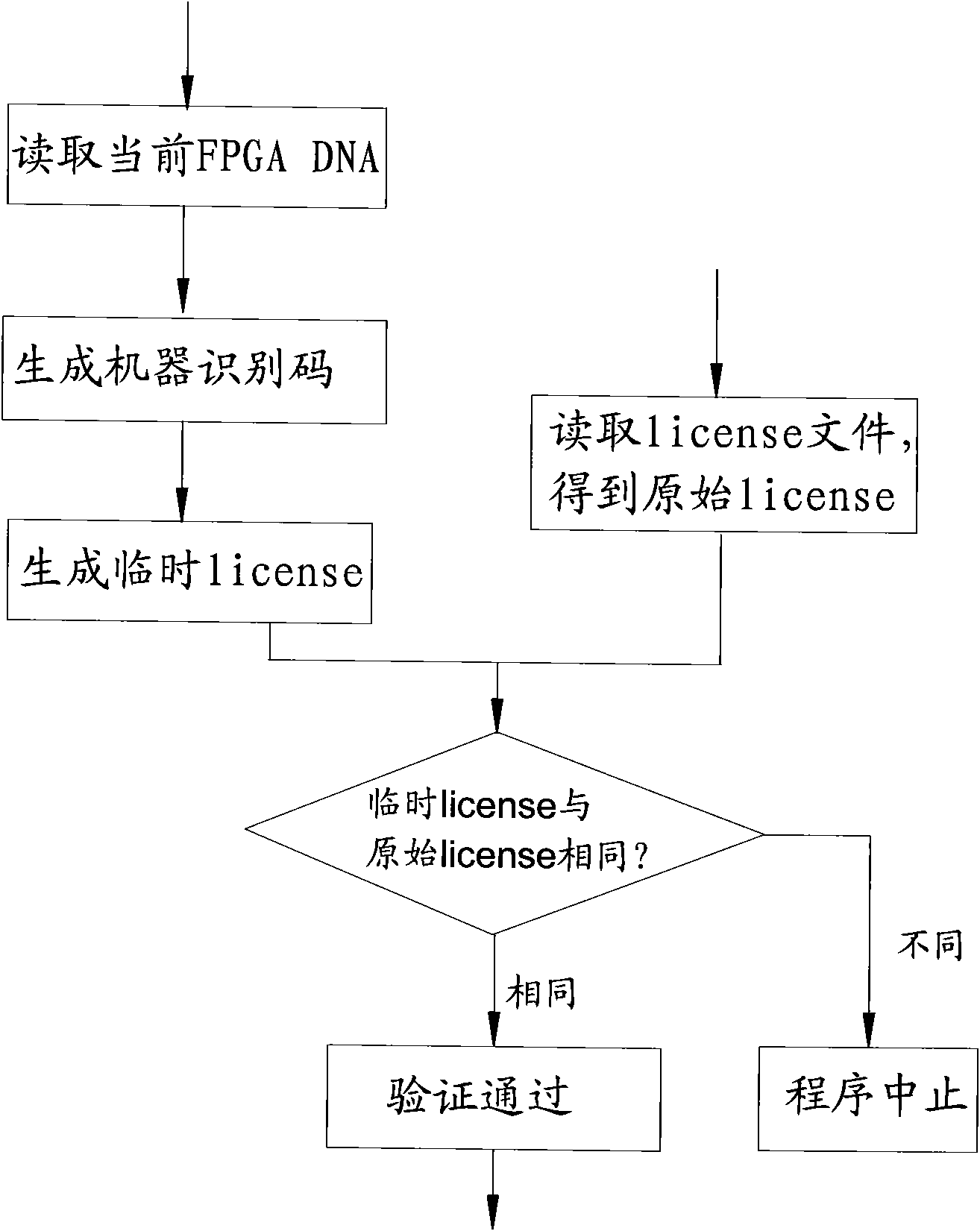
Method for generating machine identification code of flat panel detector and extended application method
ActiveCN101964033AGlobally uniquePrevent illegal copyingInternal/peripheral component protectionSensing record carriersFlat panel detectorIntegrated operations
The invention relates to a method for generating a machine identification code of a flat panel detector. The flat panel detector is provided with at least one FPGA (field programmable gate array) chip used for processing image acquisition affairs on hardware, and each FPGA chip has an only device DNA sequence number for differing from other FPGA chips. The method for generating the machine identification code comprises the following steps of: acquiring the device DNA sequence number of a corresponding FPGA chip; converting the device DNA sequence number into a sequence which differs from the device DNA sequence number; and deriving a system license, an image ID and a log ID by using the machine identification code as an identity proof of the detector, wherein the system license is used for preventing illegal copying of a system, the image ID is used for indexing an image management database of the detector, the log ID is used for indexing a log database of the detector, and the detector is integrated with a background database of the detector established by an operation in charge, and has higher extended utility.
Owner:CARERAY DIGITAL MEDICAL TECH CO LTD
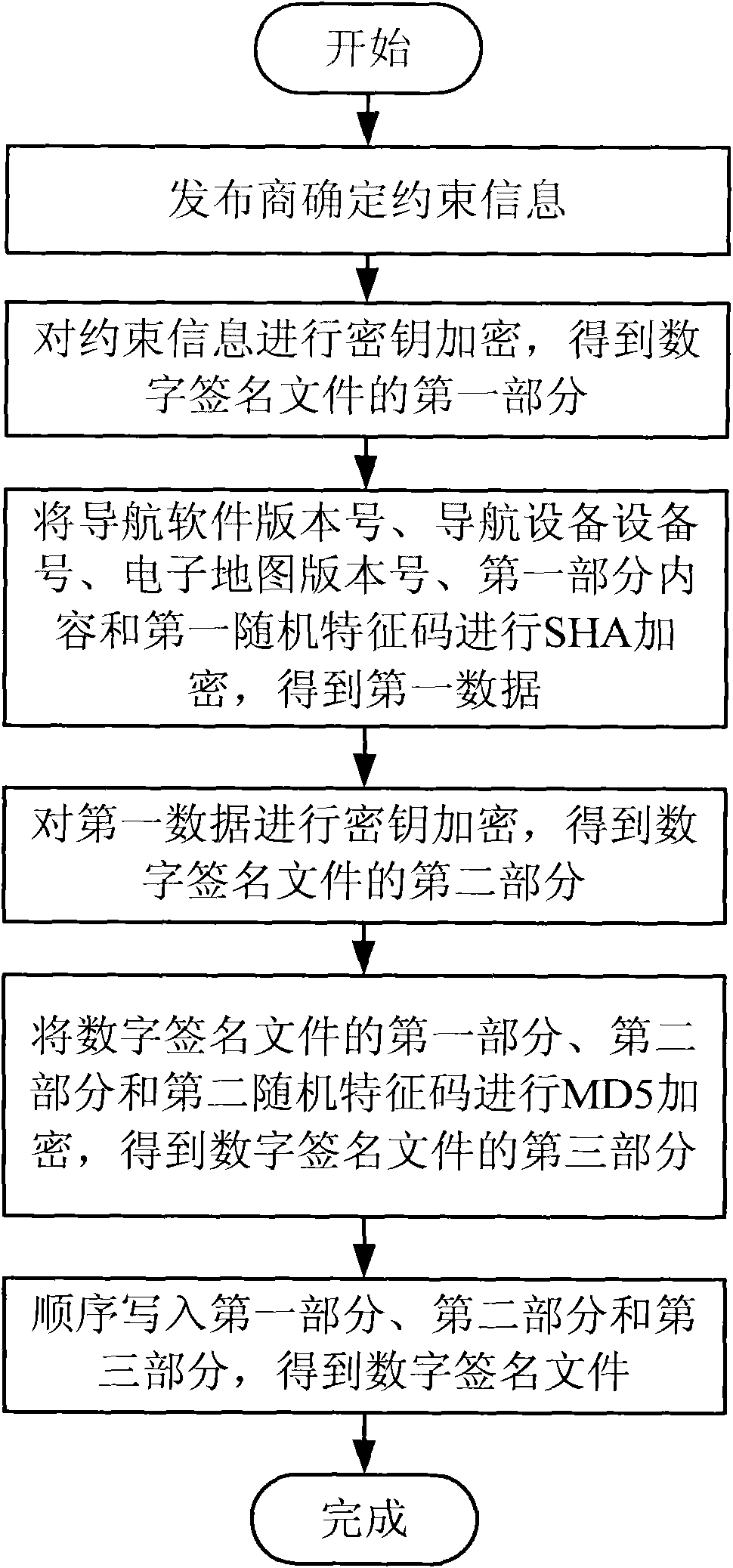
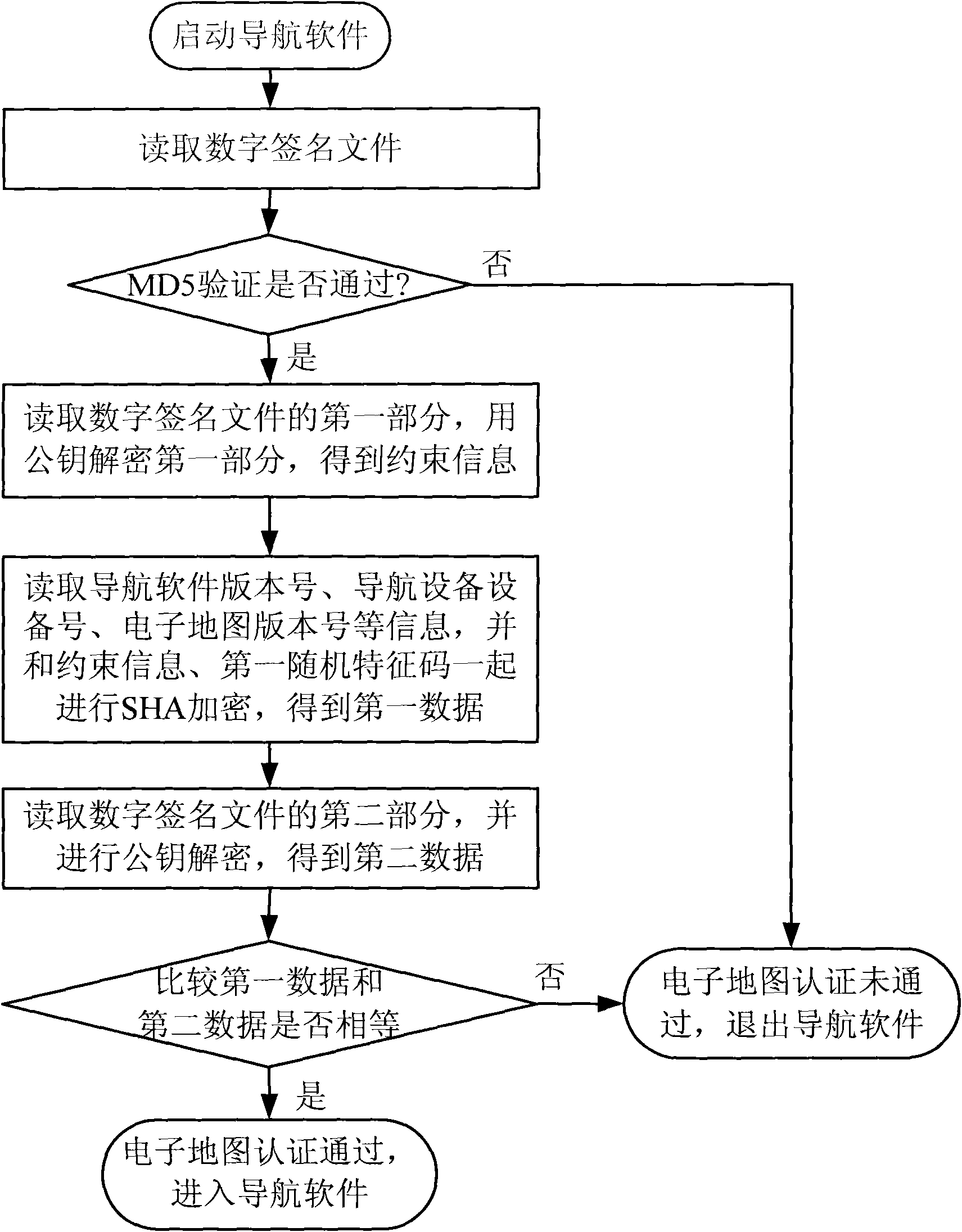
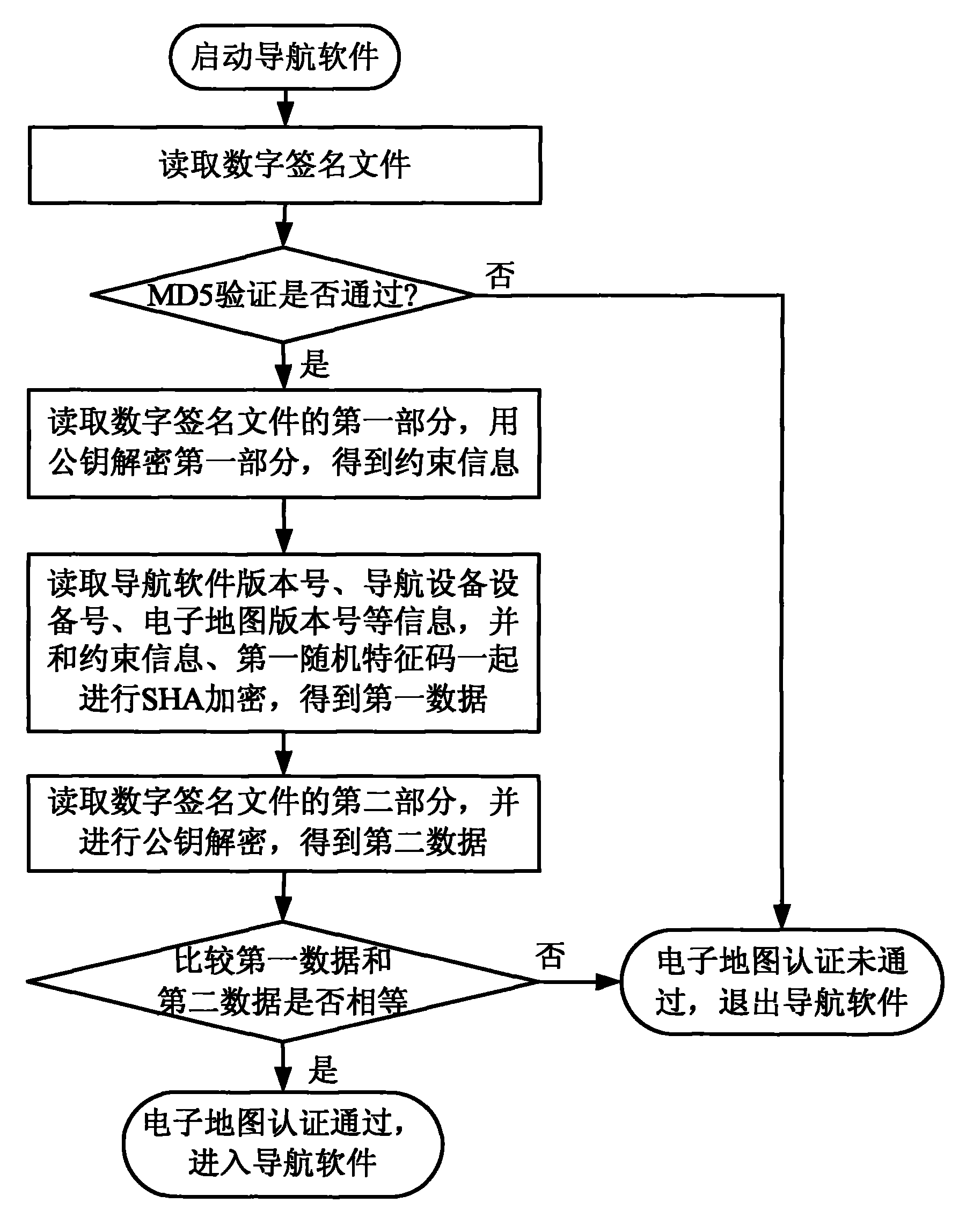
Method for restricting encrypted certificated electronic map with variable information
InactiveCN101795195APrevent illegal copyingCopyright protectionMultiple keys/algorithms usageUser identity/authority verificationDigital signatureComputer science
The invention discloses a method for restricting an encrypted certificated electronic map with variable information. Restriction information is set in a digital signature file by using a plurality of kinds of encryption algorithms. A user can use the electronic map only after the user passes the certification of the digital signature file. The publisher of the electronic map can randomly set a plurality of kinds of restriction information. When a novel electronic map is published, the user can upgrade the electronic map. The upgraded electronic map can only be used for restricting using time, specific user, specific software version or specific device specified in the information, thereby obtaining the goals of protecting the copyright of the electronic map and differently treating different users.
Owner:苏州位置科技有限公司
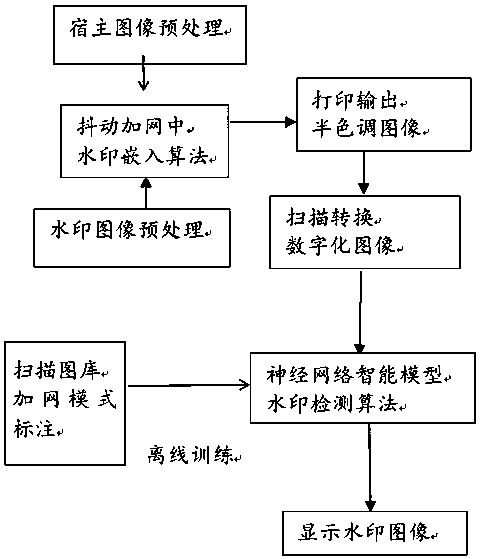
An anti-counterfeit halftone intelligent digital watermark making method of paper medium output
ActiveCN109102451AHiddenPrevent illegal copyingImage data processing detailsImage perceptionNetwork model
The invention discloses an anti-counterfeit halftone intelligent digital watermark making method of paper medium output. The specific steps are as follows: the host image is binarized, at the same time, the embedded watermark image is binarized, forming a binary digit string, and as the embeddable watermark coding information, a series of two-dimensional random number pairs are generated by usingthe random number seed as the key. The watermark coding information formed in S1 is embedded into the selected embedding position as the embedding position of the embeddable watermark coding information, and the host image embedding the watermark coding information is optimized by using the visual iterative algorithm. The trained neural network model is used to extract the watermark image. The invention can produce printing watermark with anti-counterfeiting function, has wide application prospect in copyright identification, anti-counterfeiting packaging and intelligent packaging, has high technical content, has large printing watermark embedding quantity, does not obviously affect image perception quality, and has hiding property and does not affect consumers to use printed matter.
Owner:QILU UNIV OF TECH
Method for preventing illegal copy and hardware storage device
InactiveCN101241530AAvoid accidental deletionPrevent illegal copyingUnauthorized memory use protectionRecord information storageData contentApplication software
The present invention provides a method of preventing piracy, including an application program for providing data content and playing data content, at least part of the application program being read by a player; storing data content by unrecognized data format of the player; providing data chaining in the application program. The invention is used for preventing duplication, data delete in the adding hardware storage device.
Owner:LEADCONN TECH
Disk array control device, storage system, and method of controlling disk array
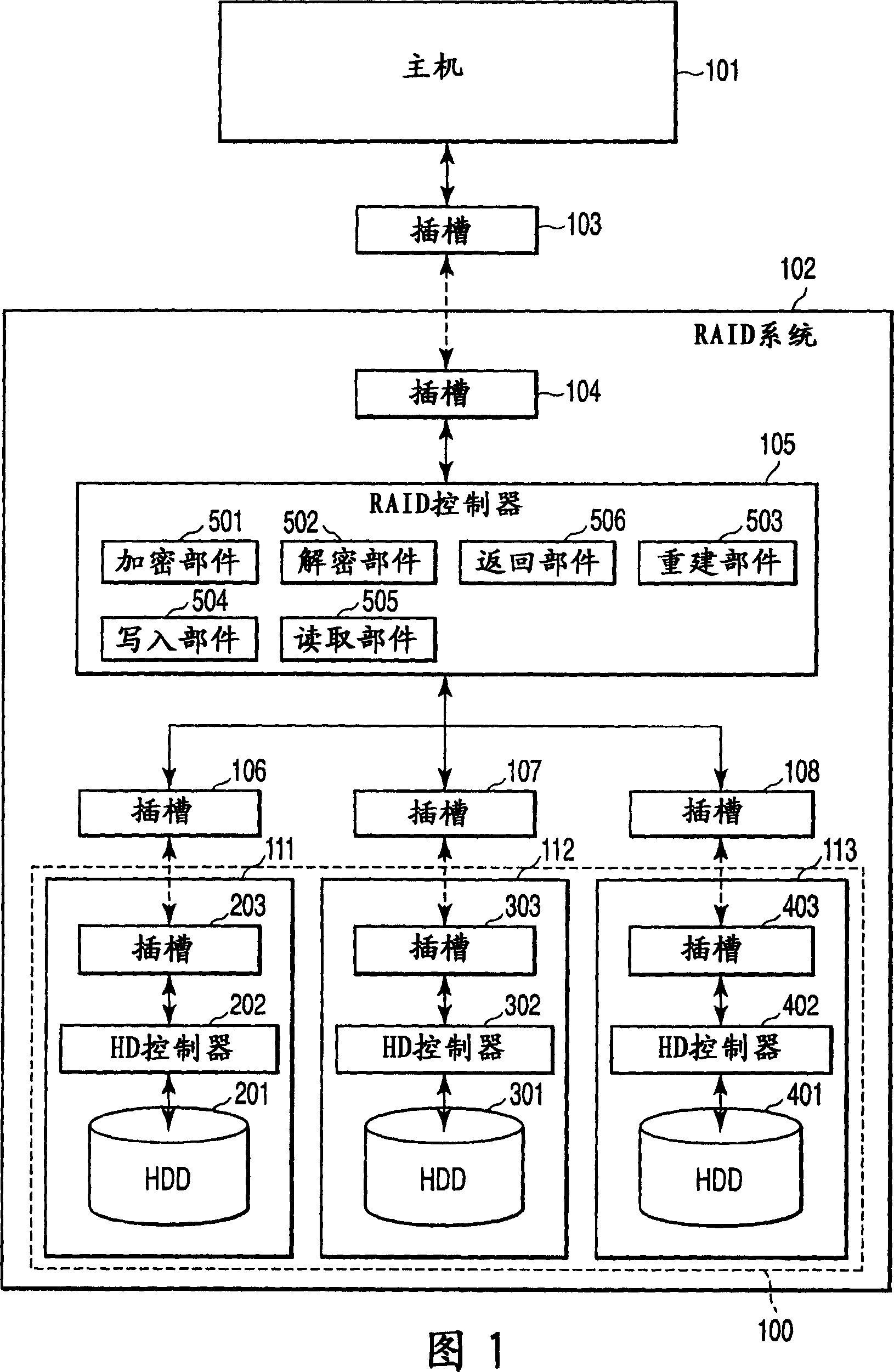
InactiveCN1831749APrevent illegal copyingSafe storageInput/output to record carriersError detection/correctionDisk arrayControl equipment
A disk array control device controls a disk array in accordance with a disk access request from a host device. The disk array control device includes a cipher unit which ciphers write data transmitted from the host device, using a key unique to the disk array control device, a write unit which writes the ciphered write data and redundant data for recovering a fault of the ciphered write data to the disk array, a read unit which reads ciphered data out of the disk array in accordance with a read request from the host device, a decipher unit which deciphers the ciphered data that is read out of the disk array, using the key, and a return unit which returns the deciphered data to the host device.
Owner:KK TOSHIBA
Method and device for software protection based on shell technology
InactiveCN104504310APrevent illegal copyingHigh-strength software protectionProgram/content distribution protectionFingerprintAuthorization
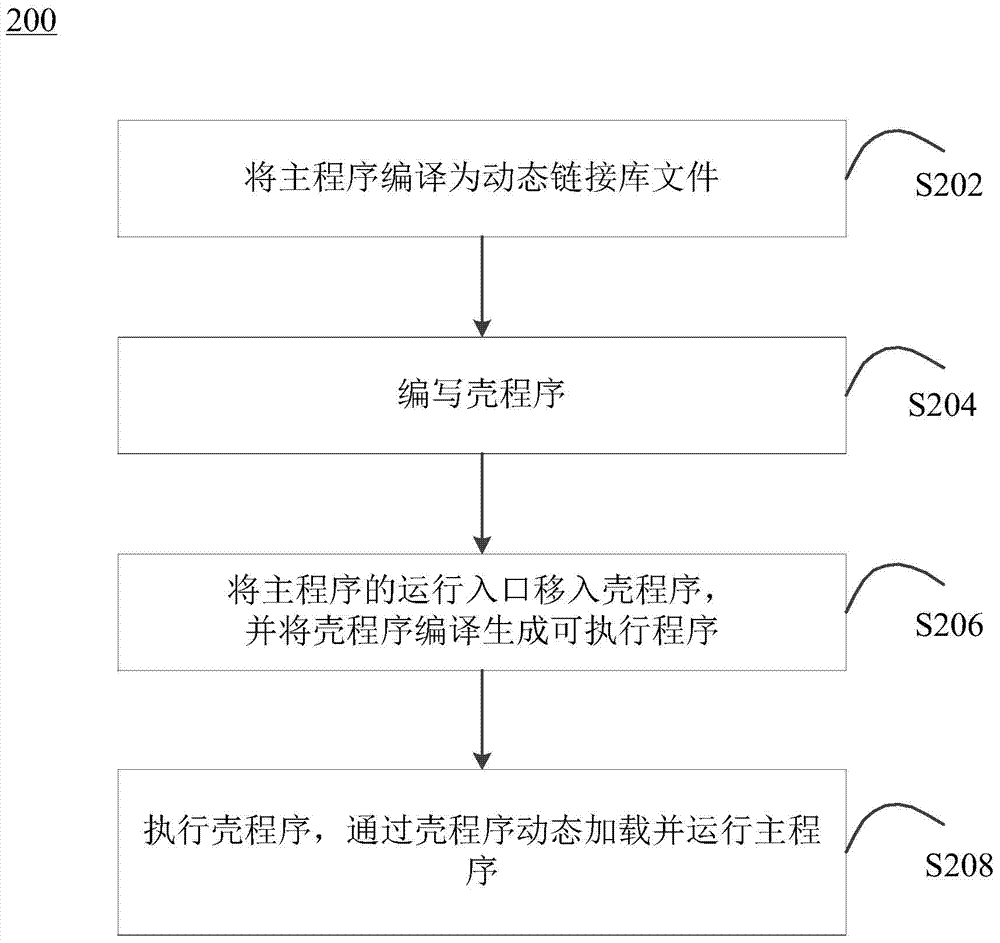
The invention provides a method for software protection based on a shell technology. The method is characterized by comprising the steps of compiling a main program into a dynamic link library file through a compiling module; writing a shell program through the compiling module; moving a running access of the main program into the shell program through an execution module, and compiling the shell program into an executable program through the compiling module; executing the shell program through the execution module, and dynamically loading and running the main program through the shell program. The method for software protection can prevent illegal copying of software, fingerprint authorization is performed for computer hardware, client access services of not a local server can be avoided for the network version, and high-strength software protection is achieved.
Owner:DONSON TIMES INFORMATION TECH CO LTD
System and method for protecting copyrights of digital content
InactiveUS20080127315A1Prevent illegal copyingPrevent hackingDigital data processing detailsMultiple digital computer combinationsDigital contentAuthentication
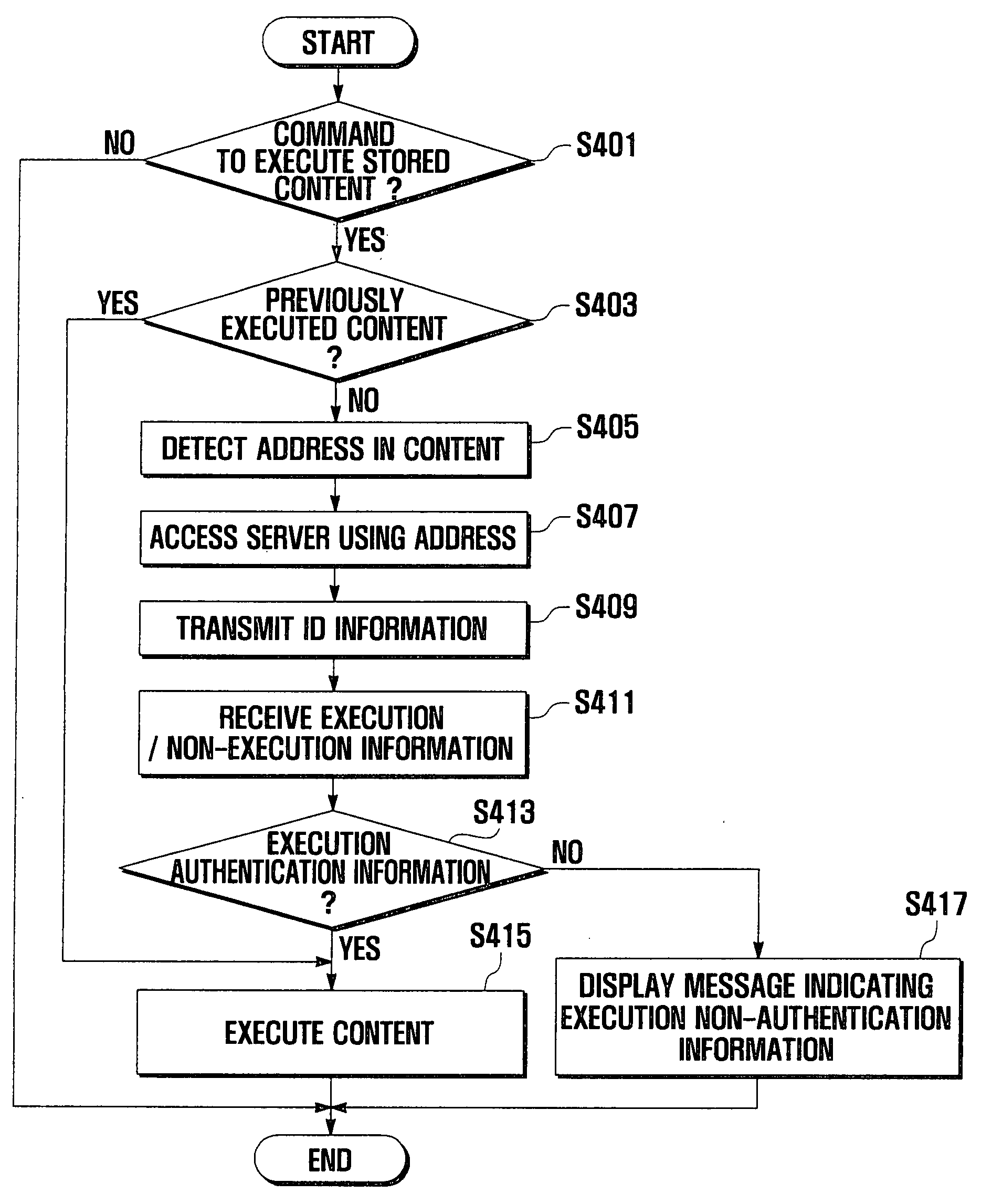
A system for protecting copyrights of digital content includes a digital content server for providing digital content containing an address of a digital content server, performing authentication of the digital content, and generating execution / non-execution information representing an authentication result for the digital content. A mobile terminal receives the execution / non-execution information from the digital content server and executes the digital content according to the execution / non-execution information. A method may include the steps of detecting an address of a digital content server contained in the digital content; accessing the digital content server using the detected address and transmitting identification (ID) information necessary for executing the digital content to the digital content server; performing authentication of the digital content in the digital content server using the ID information, and generating execution / non-execution information representing an authentication result for the digital content, and transmitting the execution / non-execution information to the mobile terminal.
Owner:SAMSUNG ELECTRONICS CO LTD
Self-destroying protection method based on malicious invasion of file system and device thereof
InactiveCN103942293AImprove securityPrevent illegal copyingUnauthorized memory use protectionDigital data protectionFile systemLimit value
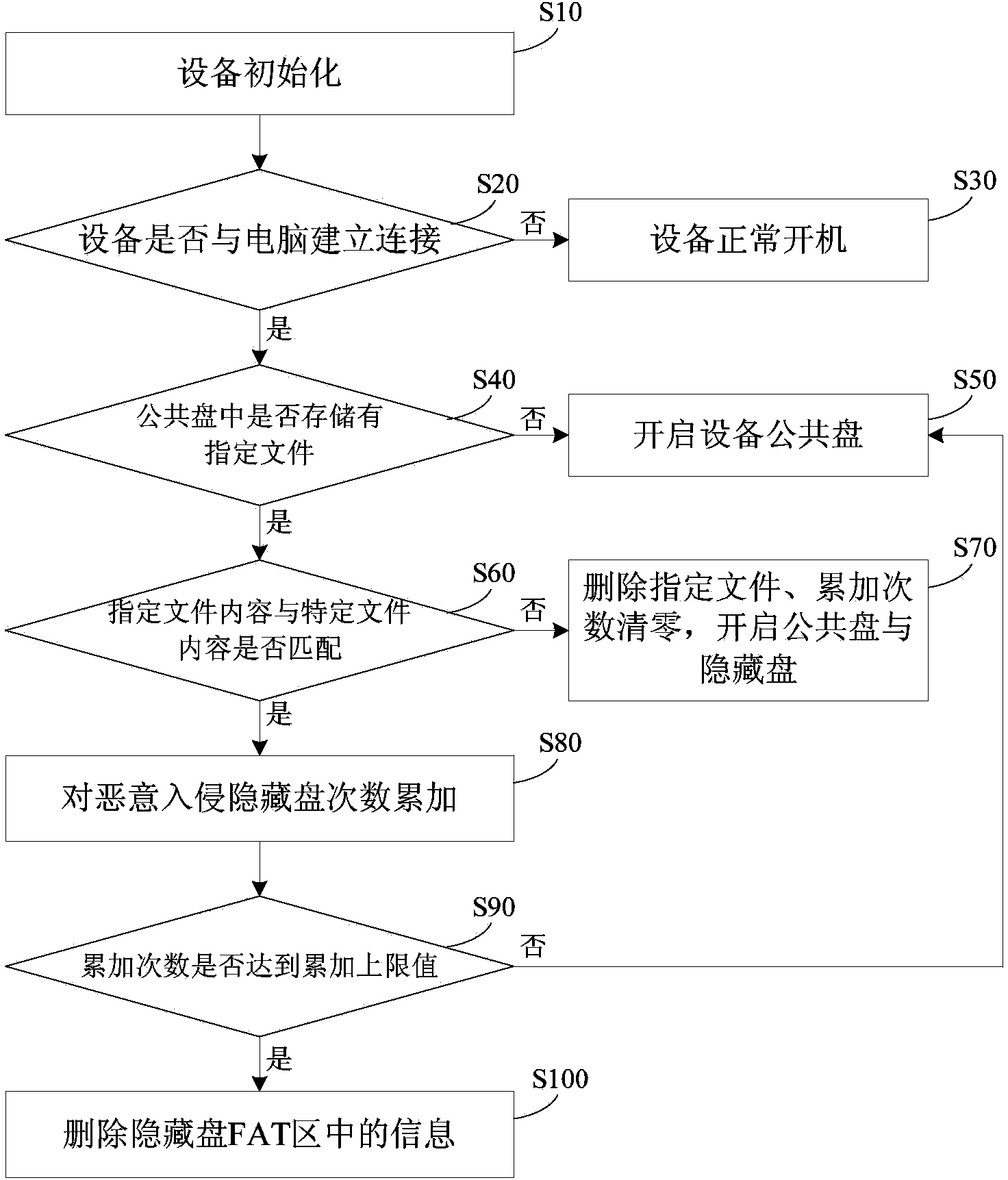
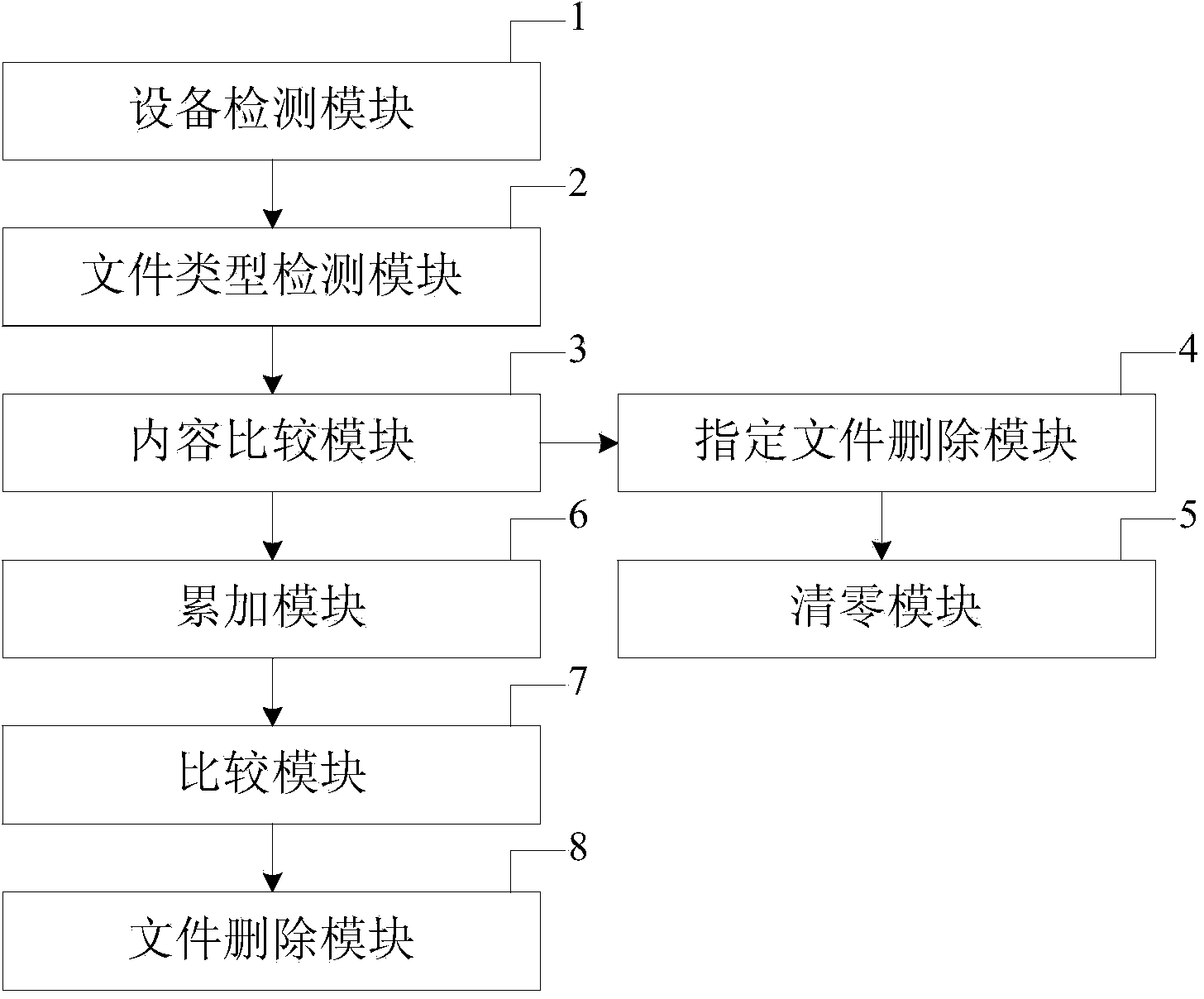
The invention provides a self-destroying protection method based on a malicious invasion of a file system. The method comprises the steps that when the content of a specified file in a common disk is not matched with the content in a specific file, the number of times of the malicious invasion of a hidden disk is accumulated; when the number of times of the malicious invasion of the hidden disk reaches an upper limit, the file system of the hidden disk is deleted, and the content in the hidden disk cannot be read. A device executing the method comprises a file type detection module, a content comparison module, an accumulating module, a comparison module for the number of times and a file system deleting module. The file type detection module is used for detecting the type of the specified file stored in the common disk of equipment, the content comparison module is used for distinguishing whether the content of the specified file is matched with that of the specific file or not, the accumulating module is used for accumulating the number of times of the malicious invasion of the hidden disk, the comparison module for the number of times is used for comparing the accumulated number of times of the malicious invasion of the hidden disk and the upper limit value of the accumulated number of times, and the file system deleting module is used for deleting information in an FAT area of the hidden disk. According to the method and the device, the safety of data in the equipment can be improved, and the data are effectively prevented from being illegally copied.
Owner:LEADER TECH BEIJING DIGITAL TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com