Confidential method for set-top box software
A software security, set-top box technology, applied in electrical components, computer security devices, program/content distribution protection, etc., can solve problems such as high cost and easy cracking of single-chip encryption, achieve simple operation, protect software copyright, and prevent illegal copying. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
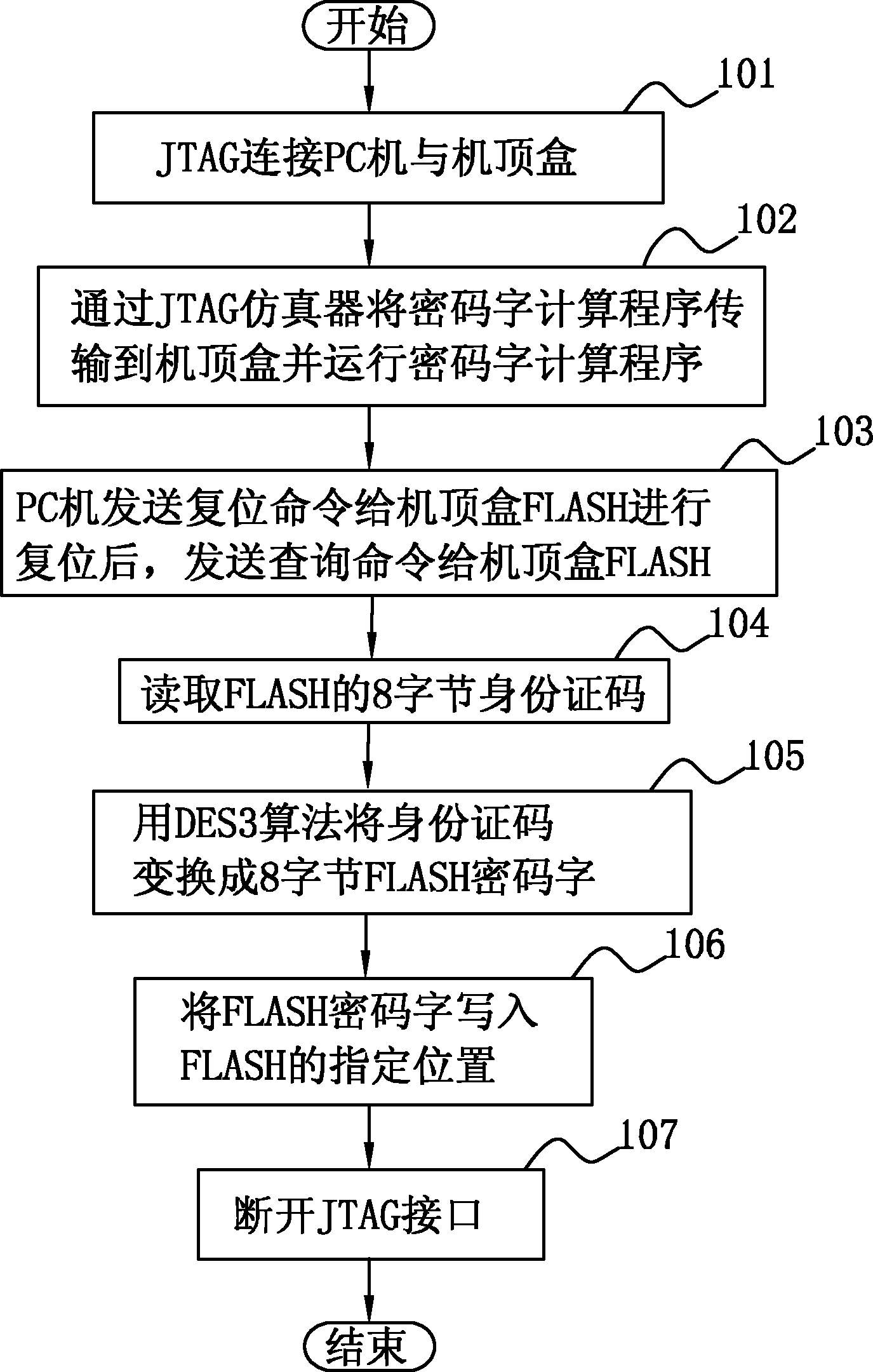
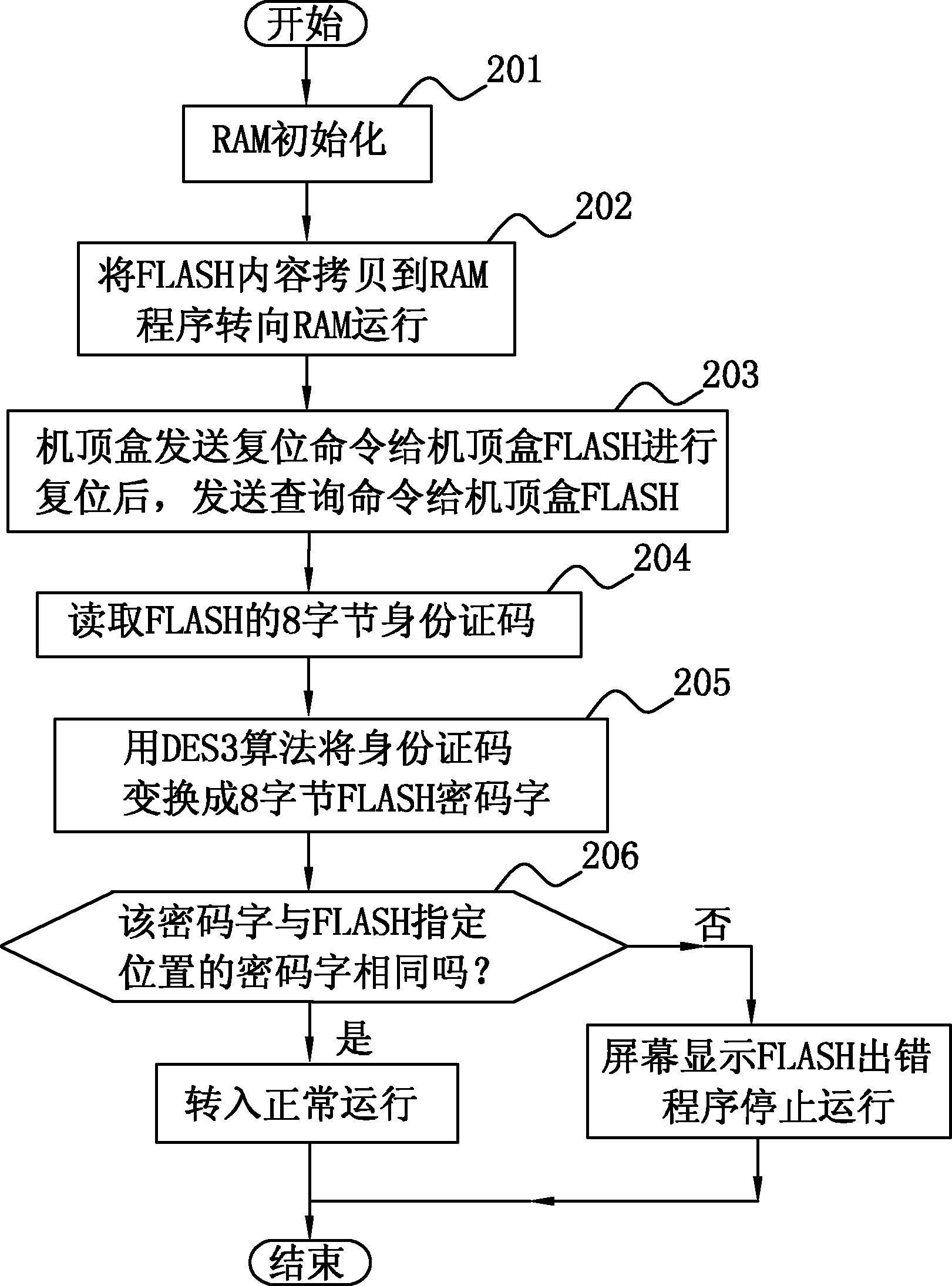
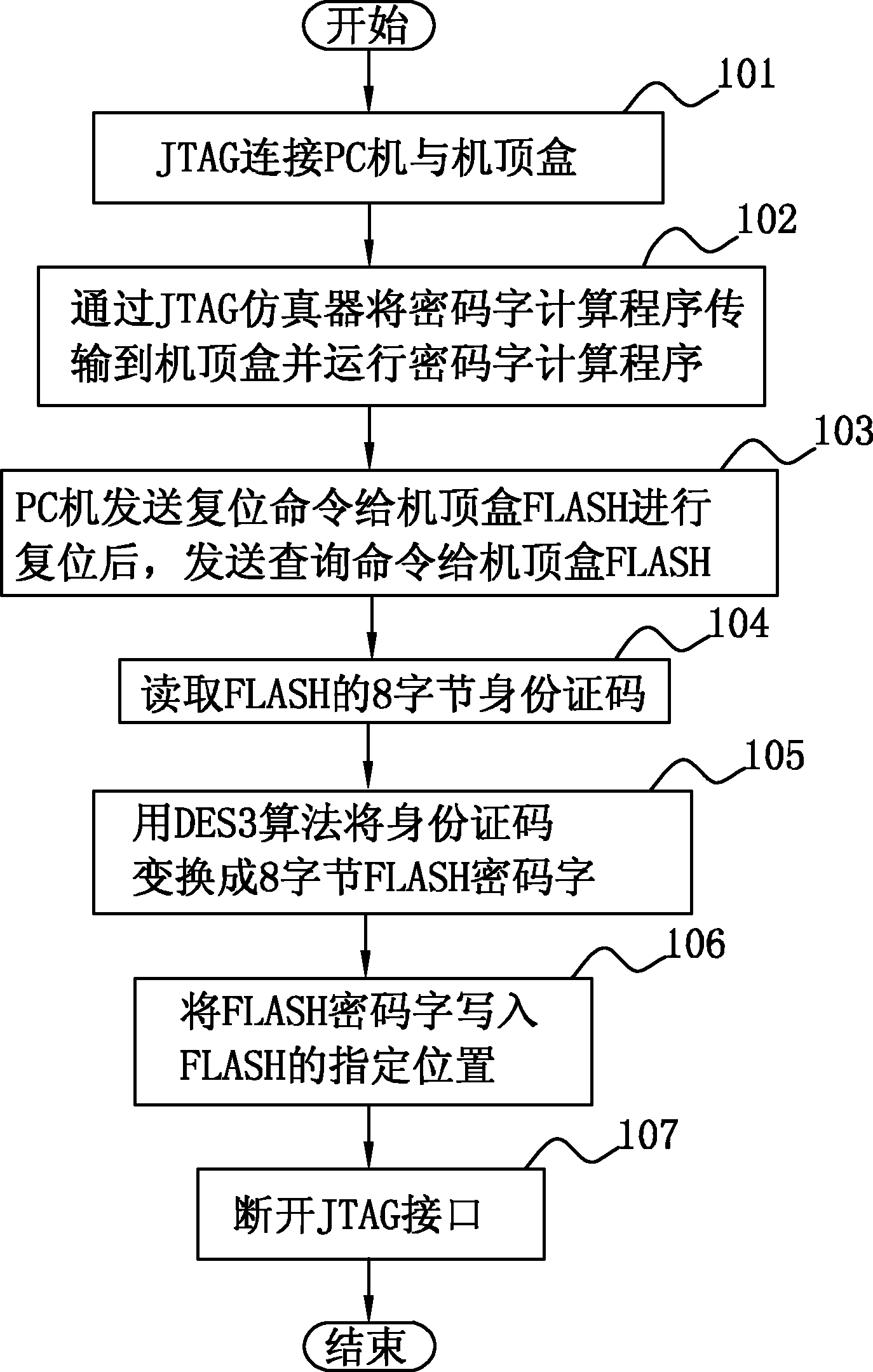
[0026] The program capacity of the set-top box FLASH is relatively large, and it is impossible to put the program in the single-chip microcomputer for encryption like ordinary single-chip microcomputers. However, the FLASH program can be read and written by an ordinary programmer, and the program can be copied. Some FLASH program chips have a globally unique ID code inside, such as ST’s M29W160ET, by sending a CFI query command to the FLASH, the 8-byte Security Code can be read, which is the only ID code. Using this group of 8-byte data and a group of 8-byte keys set by ourselves, we use the DES3 algorithm to obtain a group of 8-byte passwords. DES3 is an encryption algorithm commonly used in the world, and there are free source programs available for download on the Internet.
[0027] Since the ID codes of each piece of FLASH are different, the corresponding passwords are also different. When others copy FLASH, because they don't know our password, they can't write the corr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com