Program executable image encryption
An image and program technology, applied in the field of program executable image encryption, can solve the problems of slow processor operation and consumption of processor cycles, etc., and achieve the effect of fast loading
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
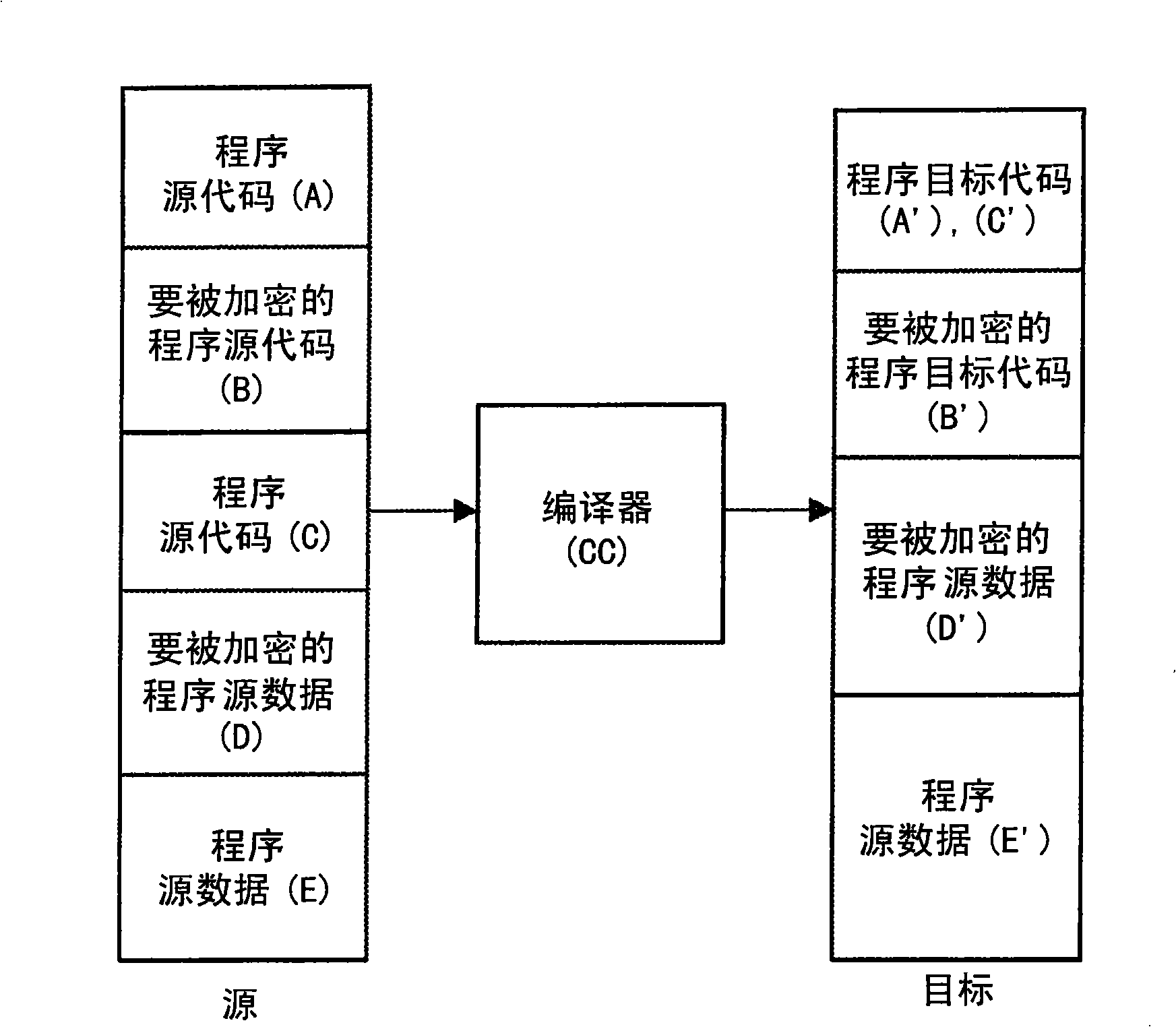
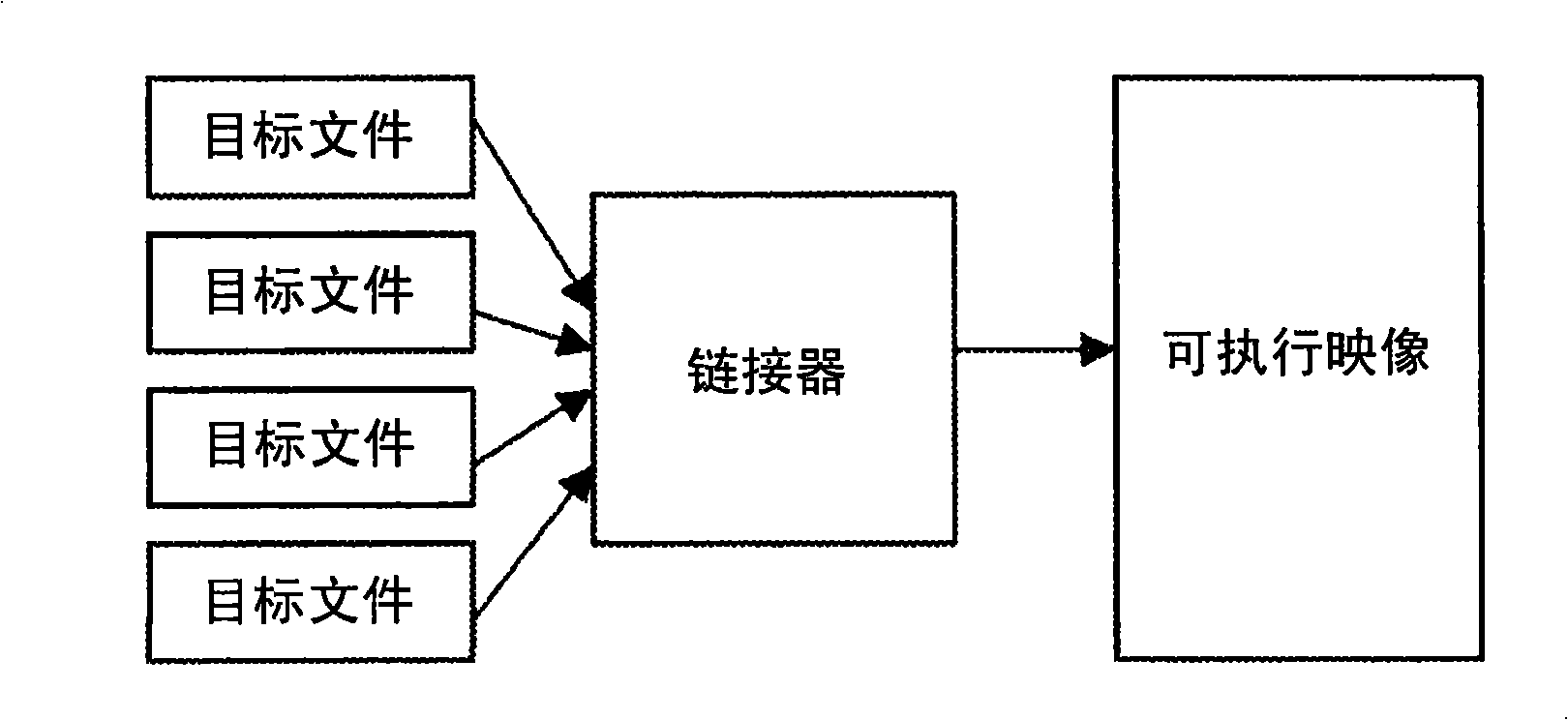
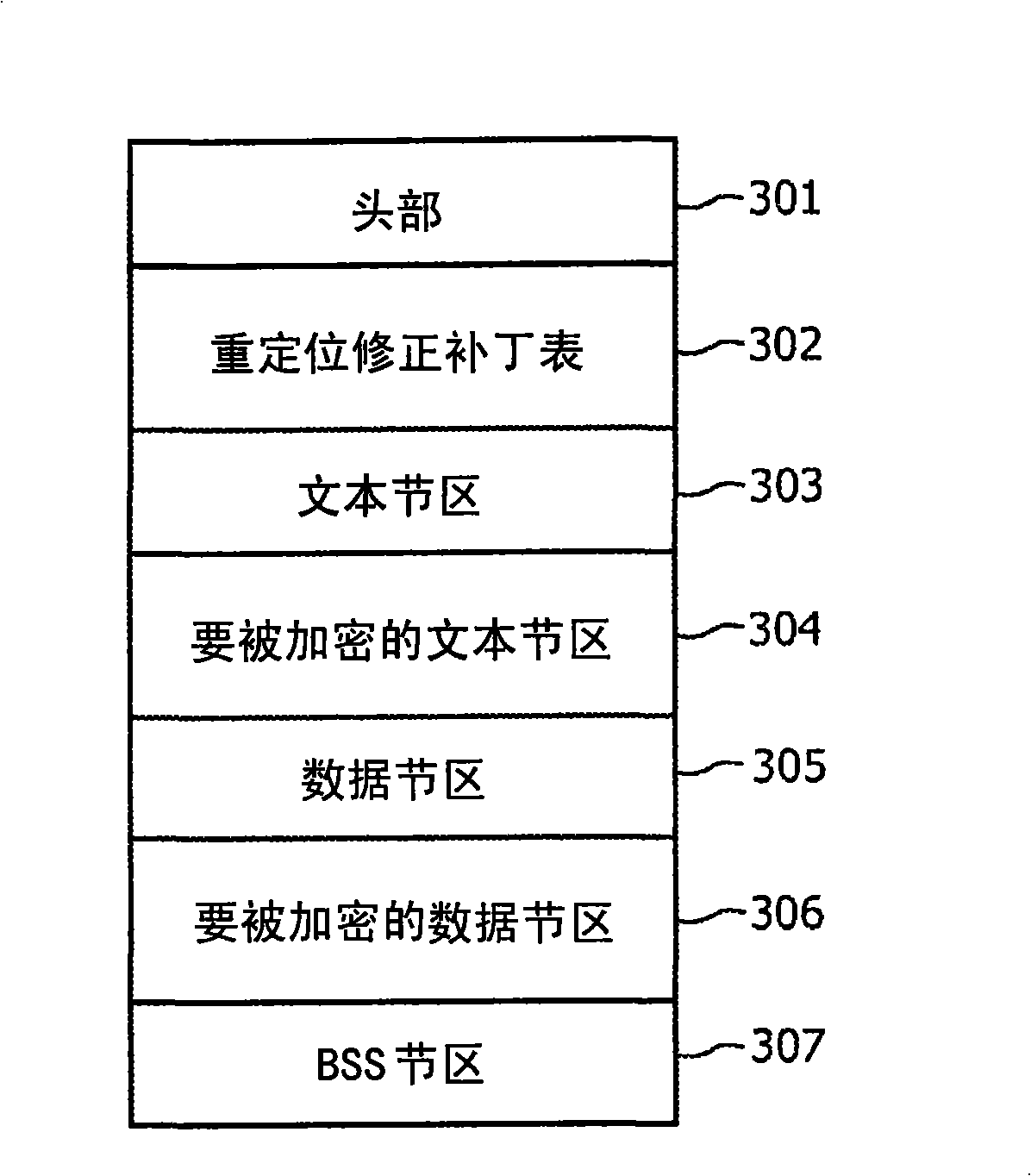
[0029] A program's executable image contains section information, and an executable image traditionally has multiple components or sections, such as text components forming the executable program code, data including space for initialized or uninitialized program static data component, and a Block Storage Segment (BSS) component that includes a region allocated by the loader that contains static data that is initialized to zero. The BSS is a memory-mapped component that contains data that is allocated as a binary image at execution time. The more components in a system, the more granular and flexible the system. Granularity indicates the degree to which a system consists of discrete components. For example, the Philips TriMedia Compiler allows renaming of sections or components in a generated object file after compile time and before linking the generated object file into the final executable image.
[0030]Compilers such as the GNU GCC C compiler allow sections to be annota...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com