Dereplication encryption lock for software and hardware of embedded system
An embedded system, software and hardware technology, applied in the field of embedded system software and hardware anti-copy encryption lock, can solve the problem of being unable to prevent a large number of wanton copying of hardware, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0007] In order to make the object, technical scheme and advantages of the present invention clearer, the present invention is further described in detail by giving examples below
[0008] The invention adopts the mode of chip family member management and encryption, which effectively prevents the software and hardware of the embedded system from being illegally used, copied and tampered with.
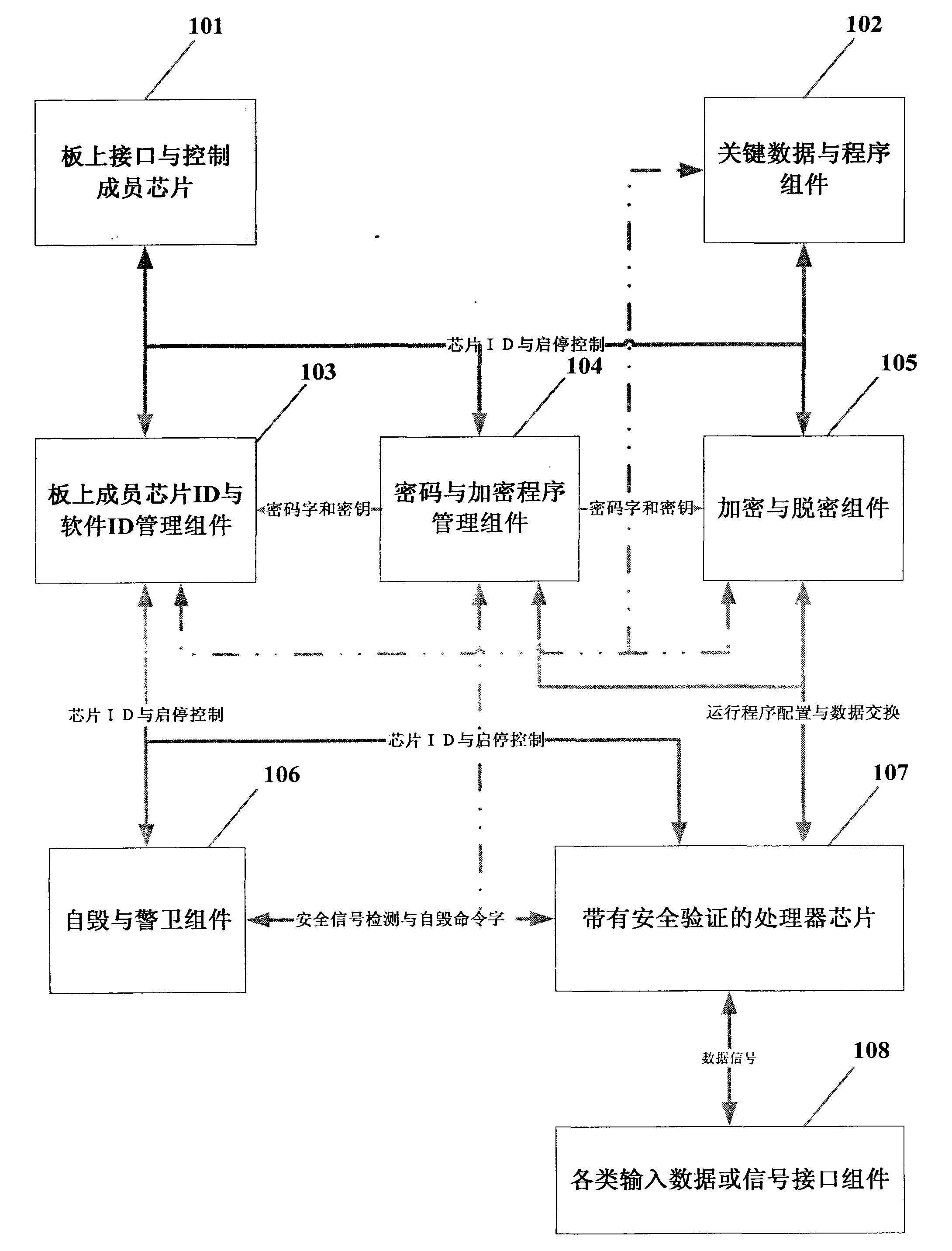
[0009] figure 1 It is the overall unit schematic diagram of the example of the present invention.
[0010] refer to figure 1 The present invention includes on-board member ID and software ID management component 103, password and encryption program management component 104, encryption and decryption component 105, key data and program component 102, self-destruction and guard component 106, and a processor with security verification 107 and on-board interface and control chip 101.
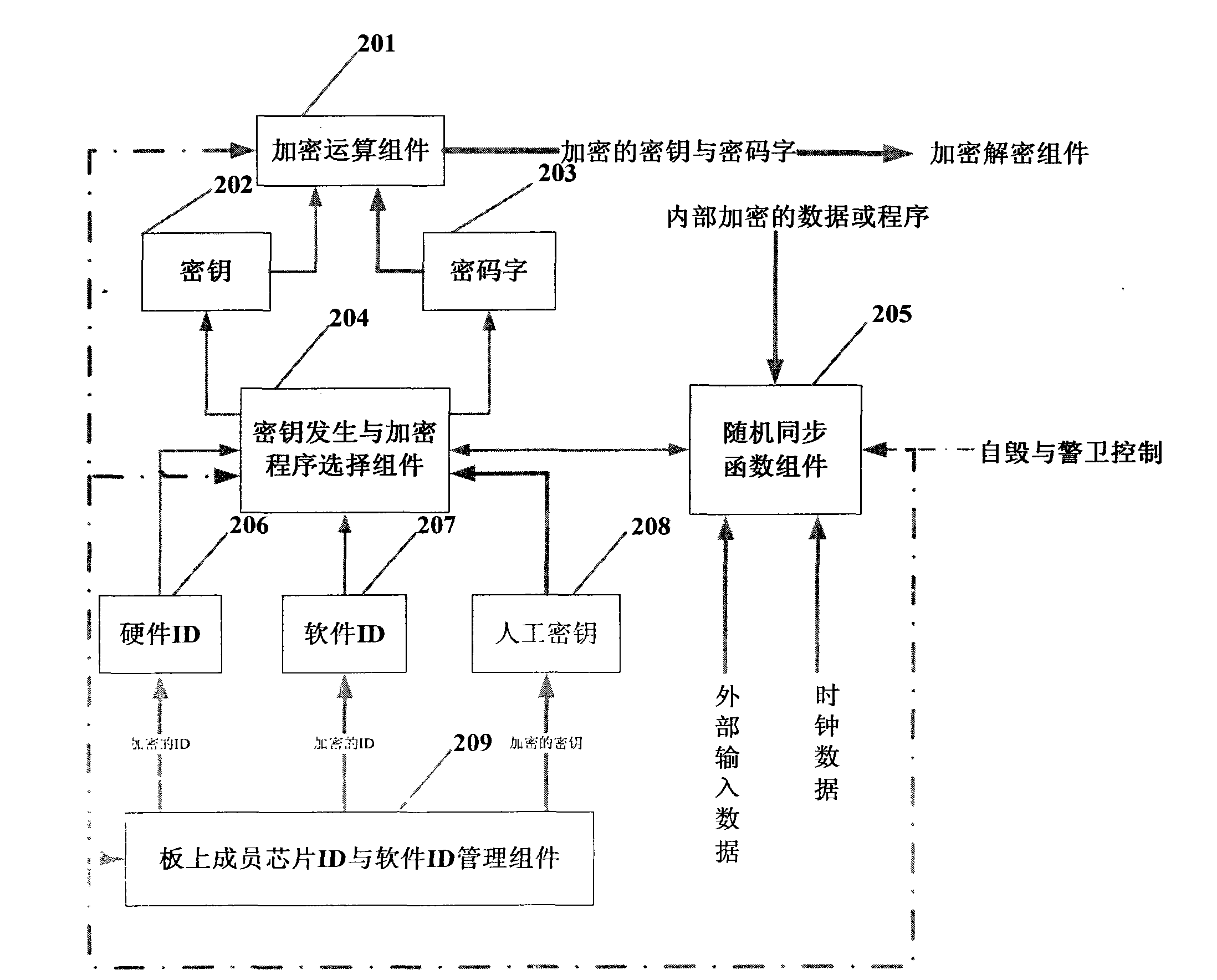
[0011] After the embedded system starts, the member ID and software ID management component 103 on th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com