Self-destroying protection method based on malicious invasion of file system and device thereof
A malicious intrusion and file system technology, applied in computer security devices, internal/peripheral computer component protection, digital data protection, etc., to avoid illegal reading, prevent illegal copying, and improve data security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
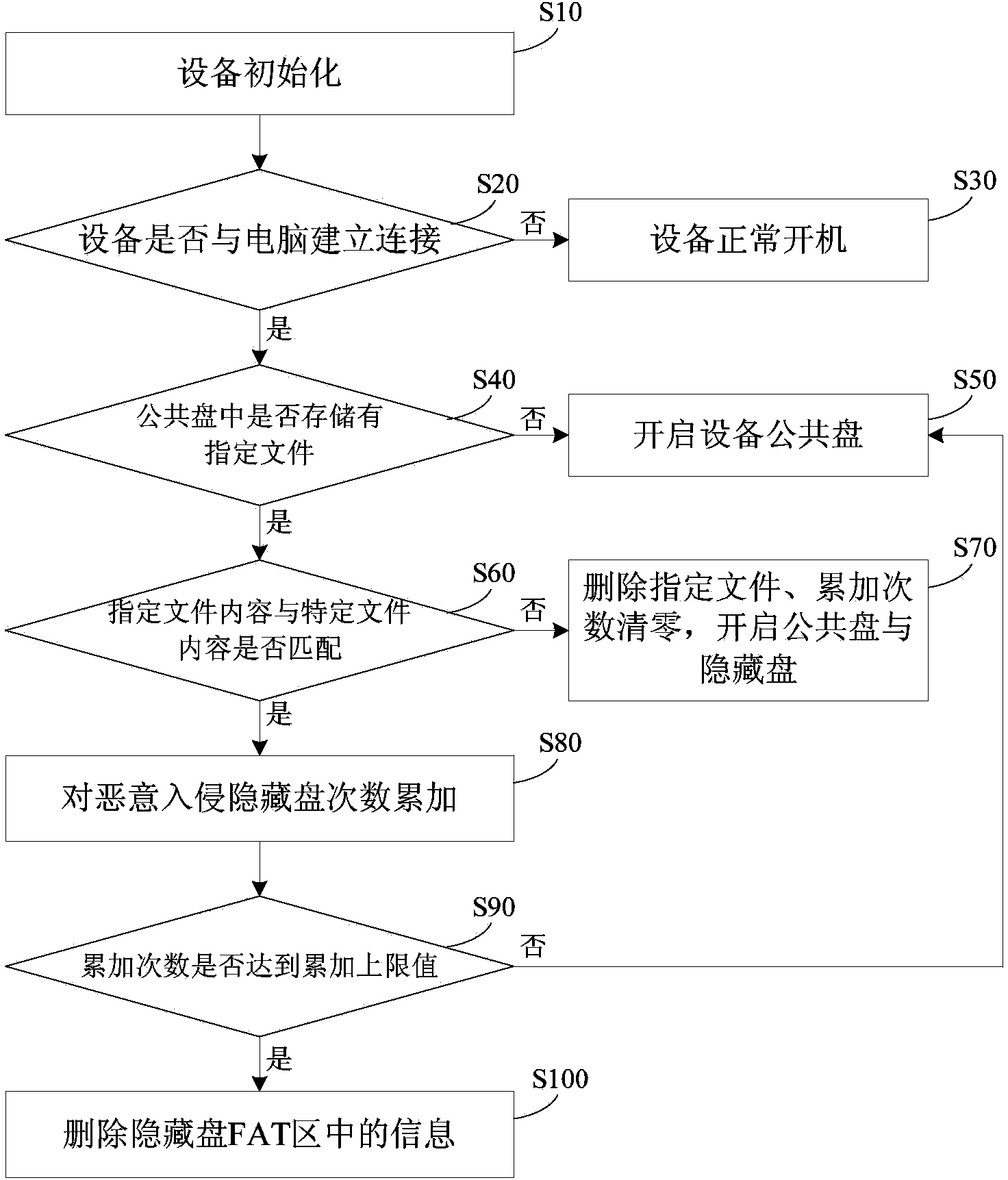
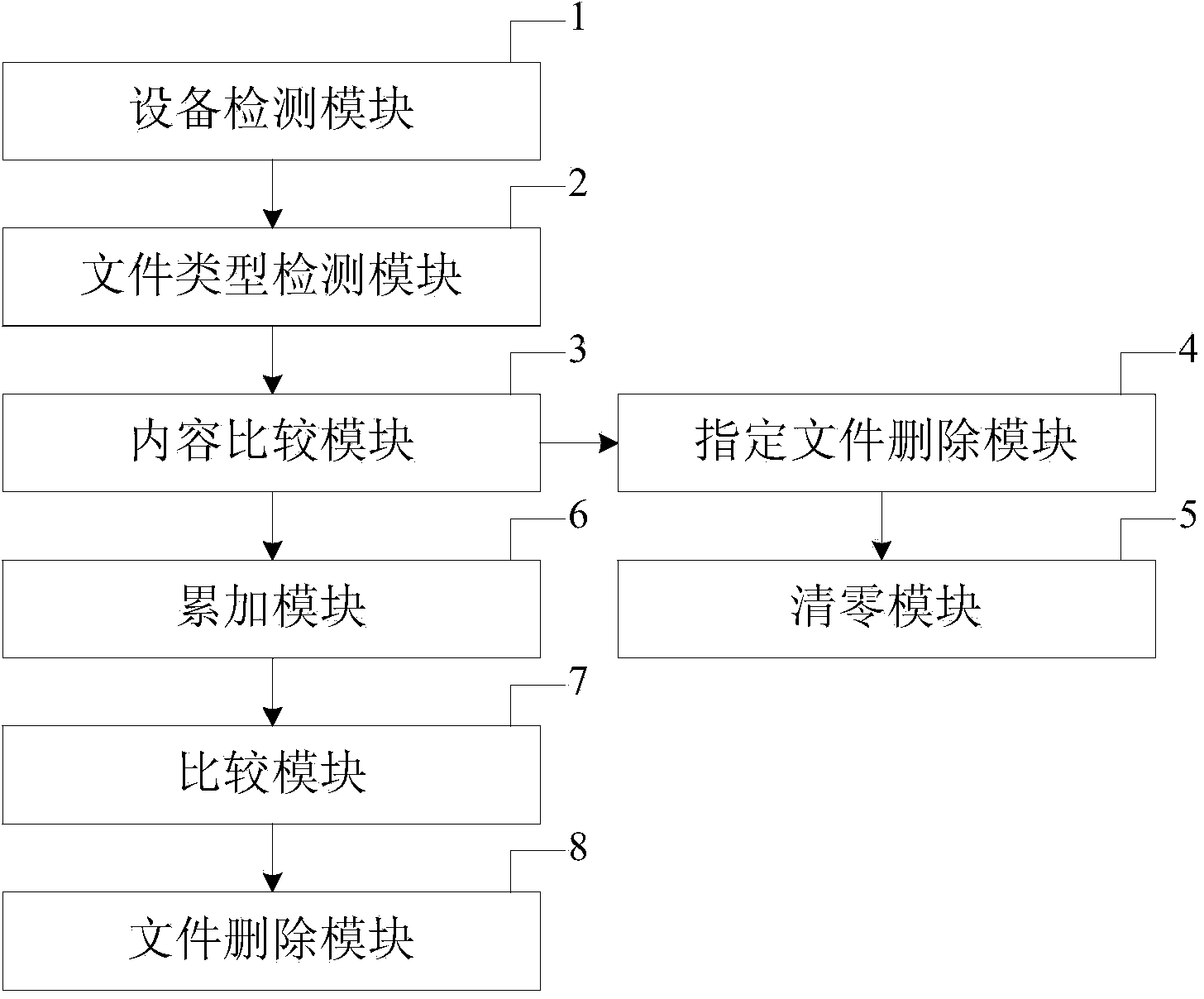
[0033] The invention provides a self-destruction protection method based on malicious intrusion of a file system, which includes the following steps:
[0034] When the content of the specified file in the public disk does not match the content of the specific file, the number of malicious intrusions into the hidden disk is accumulated, otherwise the hidden disk and the public disk are opened;
[0035] When the number of malicious intrusions into the hidden disk reaches the upper limit, the file system of the hidden disk is deleted, so that the hidden disk cannot be read.
[0036] Such as figure 1 As shown, the present invention provides a self-destruction protection method based on malicious intrusion of a file system, which specifically includes the following steps:
[0037] S10. The device is initialized.
[0038] S20. Connect the device and the computer, and determine whether a connection is established between the device and the computer.
[0039] If it is determined that the connect...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com