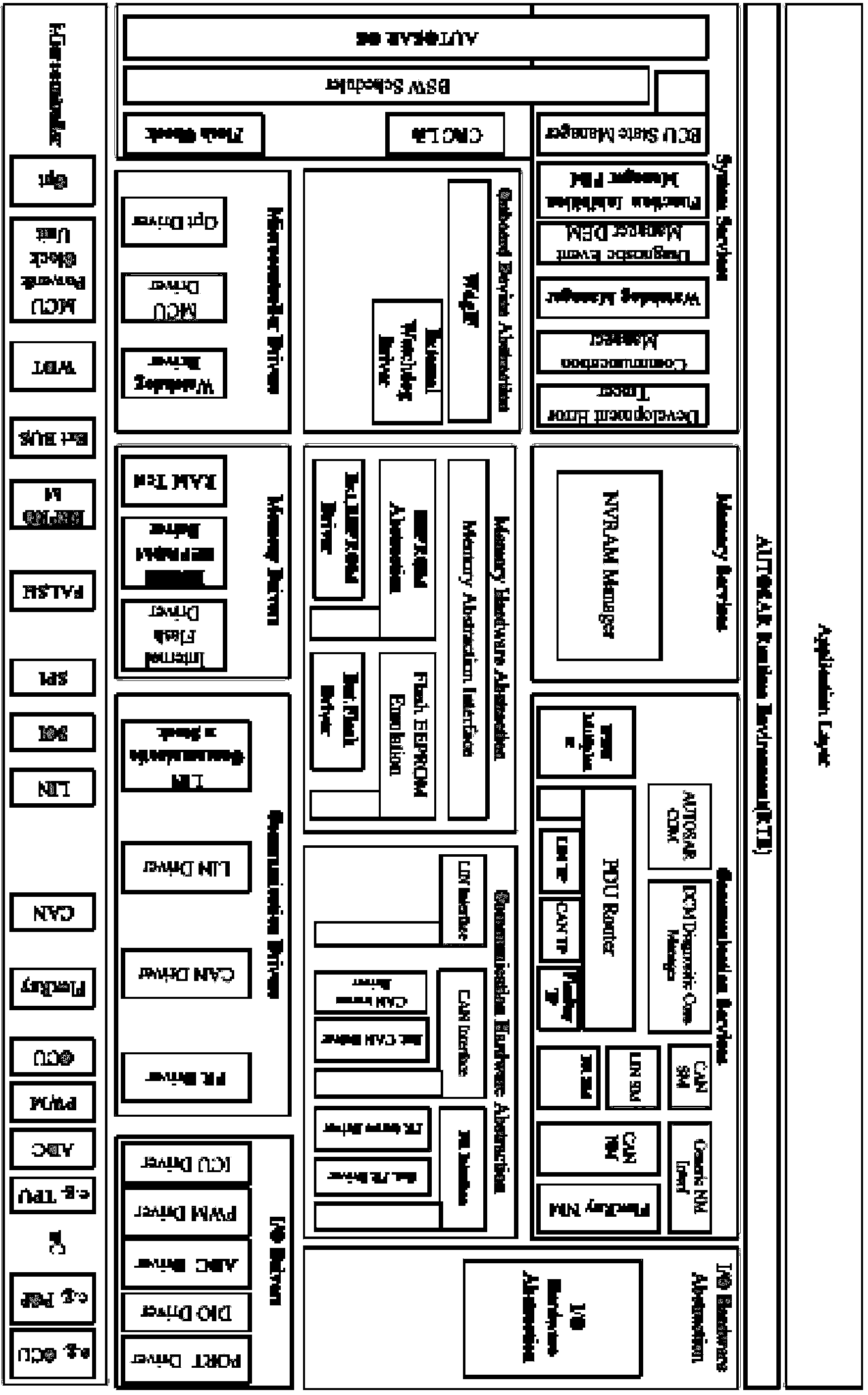
Patents
Literature
30results about How to "Prevent illegal reading" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
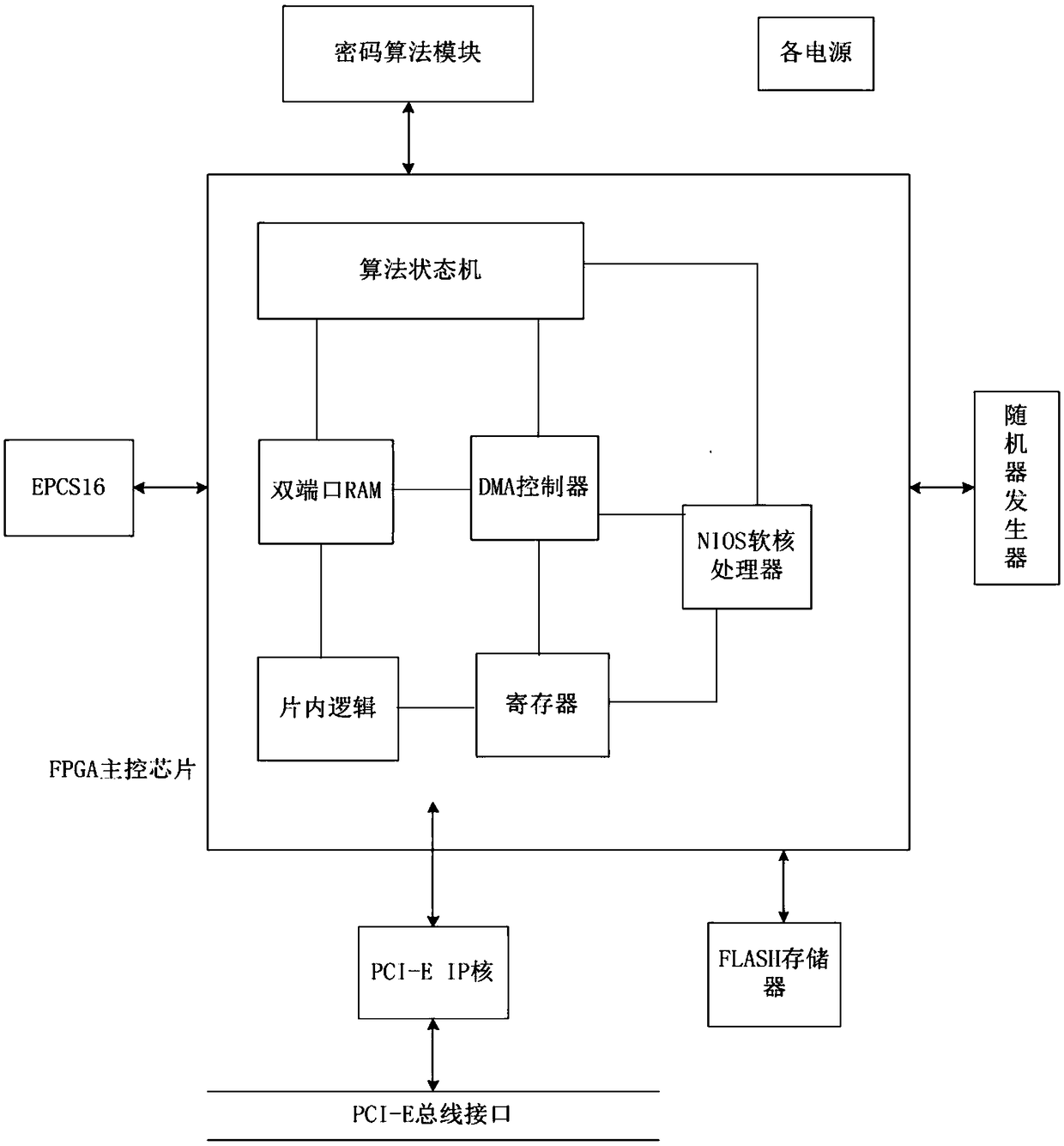
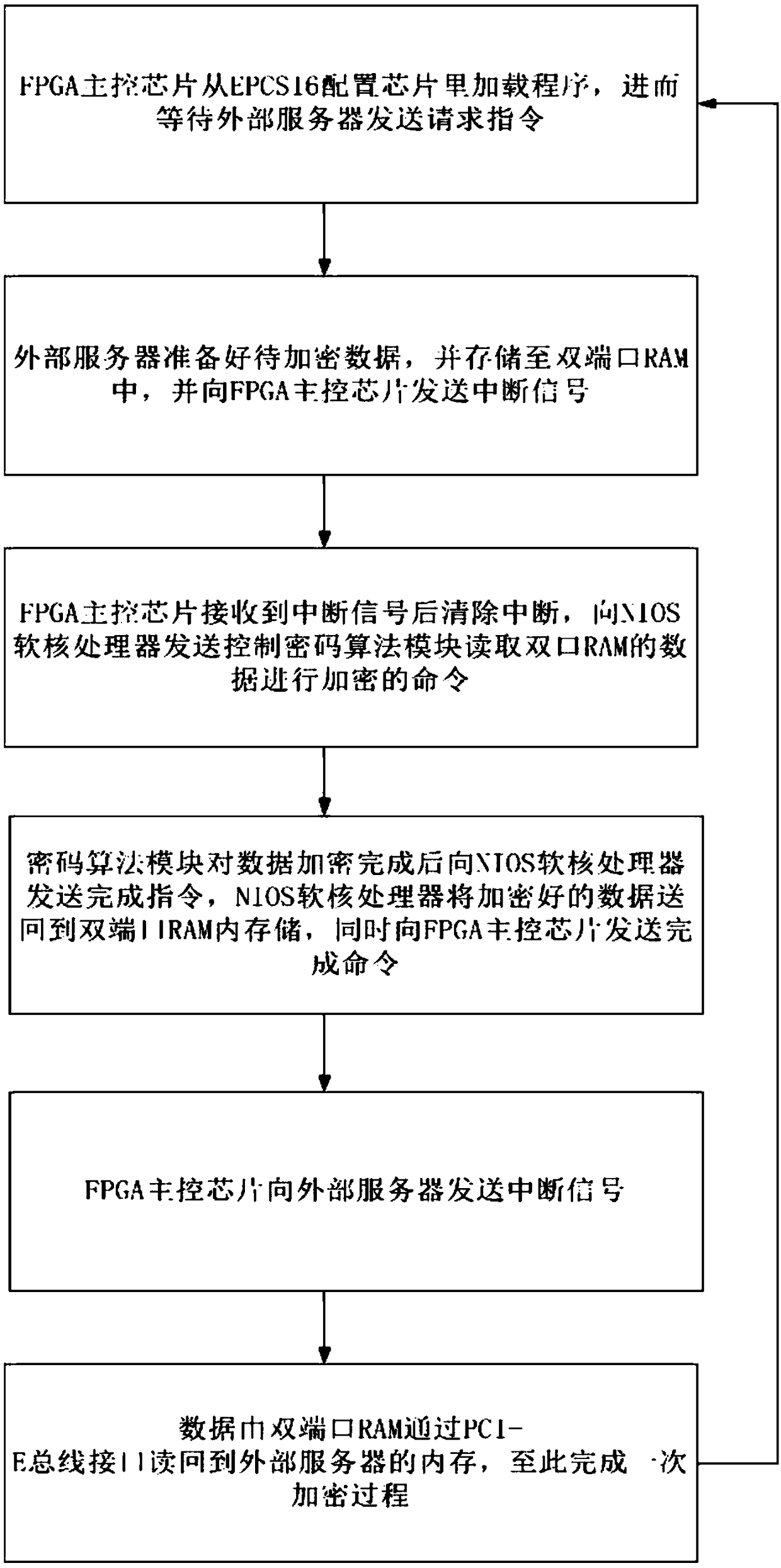
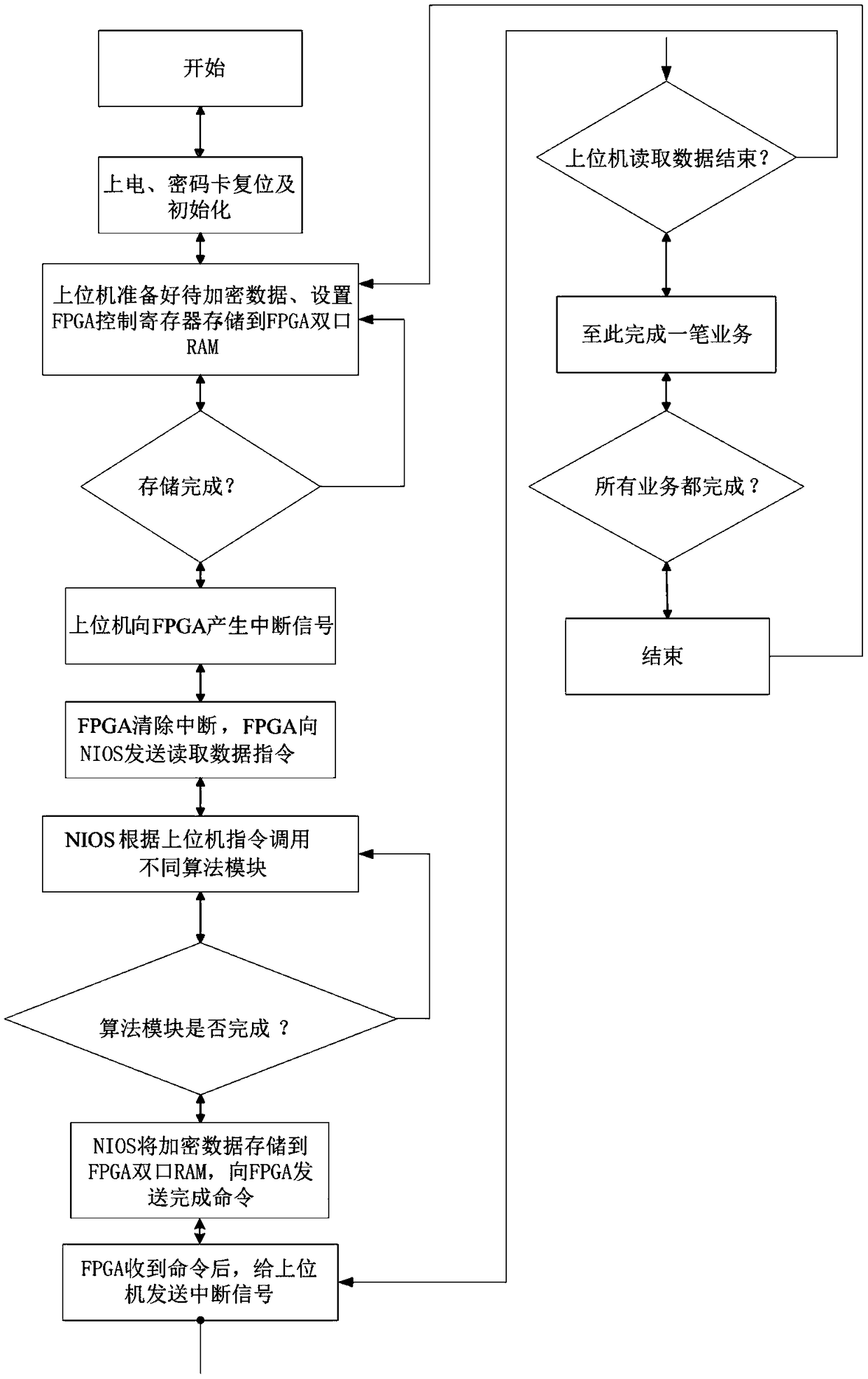
A full algorithm cryptographic card based on PCI-E interface and an encryption method thereof
InactiveCN109145568AImprove security strengthImprove securityDigital data authenticationEnergy efficient computingAlgorithmic State MachineSERCOS interface
The invention discloses a method based on PCI-E interface full algorithm cryptographic card, including: a cryptographic algorithm module, a FLASH memory, a PCI-E bus interface, a random numb generator, and an FPGA master control chip with NIOS soft core processor, wherein a PCI-E IP core and an algorithm state machine are integrated in the FPGA master control chip. The cryptographic algorithm module comprises a symmetric key encryption SM4 algorithm chip, a symmetric key encryption SM1 algorithm chip and an asymmetric key encryption SM2 algorithm chip. The invention also discloses an encryption method of the cipher card. The invention provides a high-performance full-algorithm cryptographic card, which simultaneously reduces the complexity of hardware circuit and energy consumption, improves the key operation speed, and the cryptographic card adopts a home-made cryptographic algorithm, so that the user's key is most securely protected.
Owner:西安得安信息技术有限公司
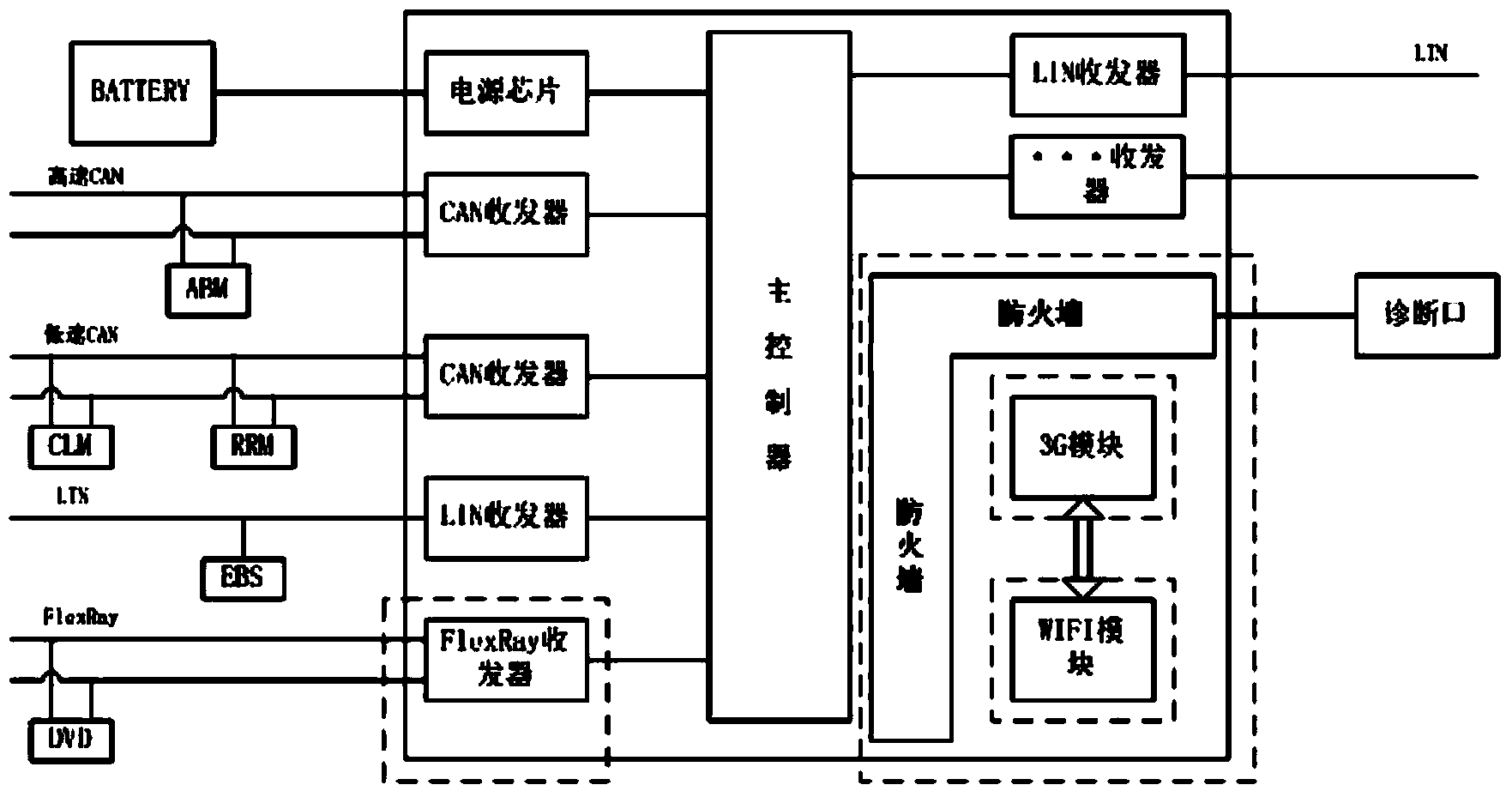
Multifunctional gateway used for vehicle and control method thereof
ActiveCN103873595AEnsure safetyIllegal control of ECU functionsNetwork connectionsTransceiverThe Internet
The invention relates to a multifunctional gateway used for a vehicle and a control method thereof. The multifunctional gateway comprises a main controller, transceivers, a 3G module and a WI-FI module, wherein the main controller is a processor of the multifunctional gateway and is in control connection with the transceivers, the 3G module and the WI-FI module, the transceivers are all in communication connection with the main controller and are used for receiving and transmitting network signals, the 3G module is used for providing 3G internet functions, and the WI-FI module is used for being used by a terminal electronic device with the gateway as a WI-FI hot spot. The multifunctional gateway is a gateway integrating an in-vehicle network, the Internet and an inter-vehicle network and extends and integrates firewall functions, remote diagnosis functions, 3G functions, WIFI functions, power supply security level management functions and the like; extension function hardware and software are designed in a modularized mode, meanwhile, the multifunctional gateway serves as a platform-type multifunctional gateway, the extension functions have transplantable performance, the multifunctional gateway is suitable for vehicle models with different configuration parameters and of different levels in a platform, and development cost and develop frequency can be effectively reduced.
Owner:CHERY AUTOMOBILE CO LTD
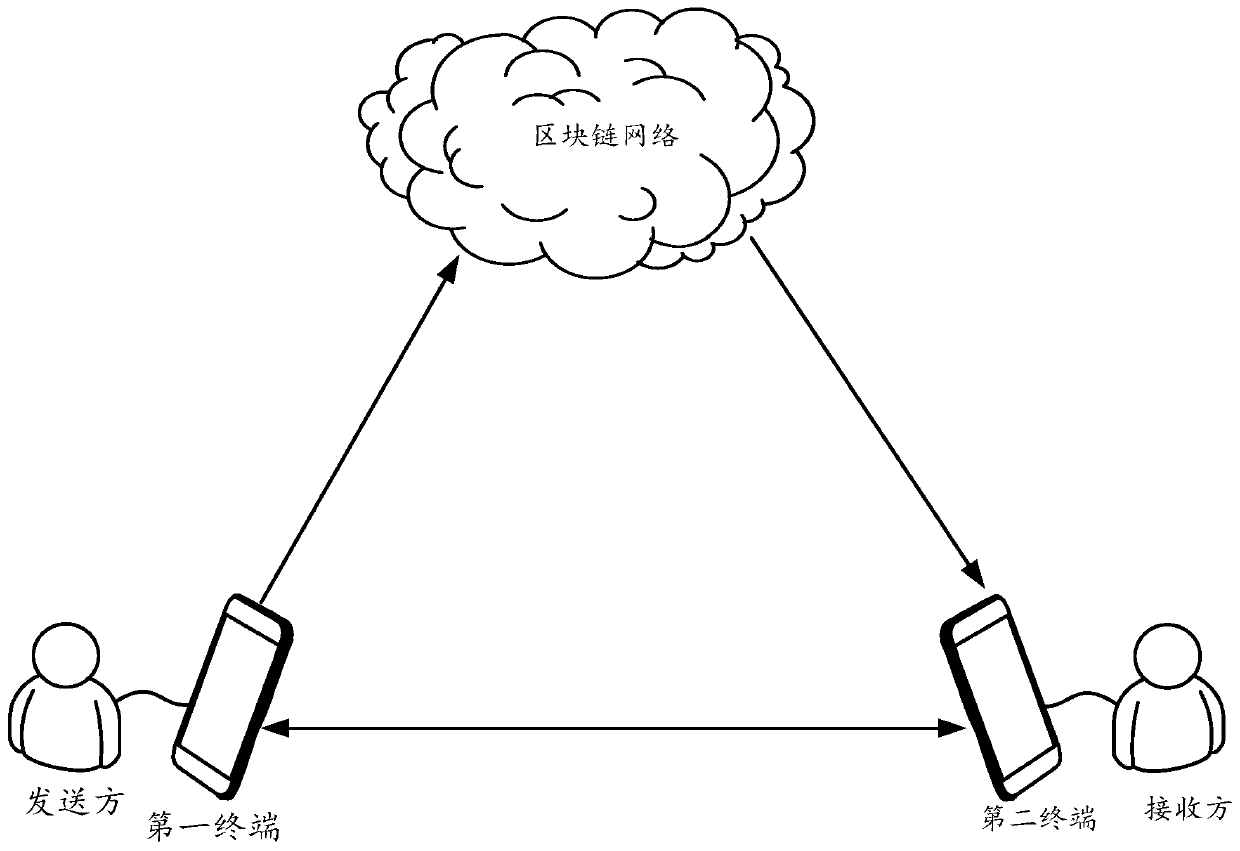
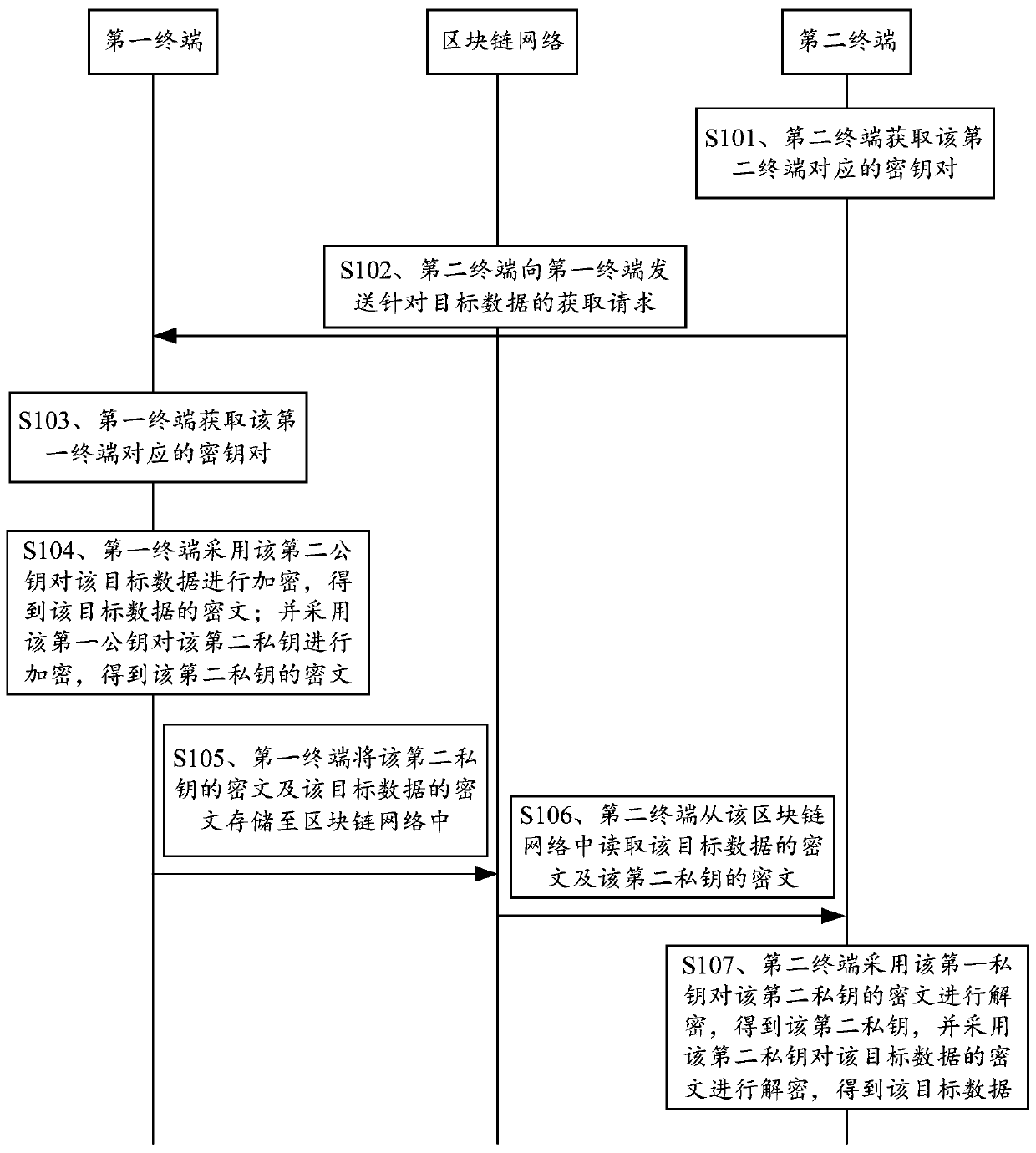
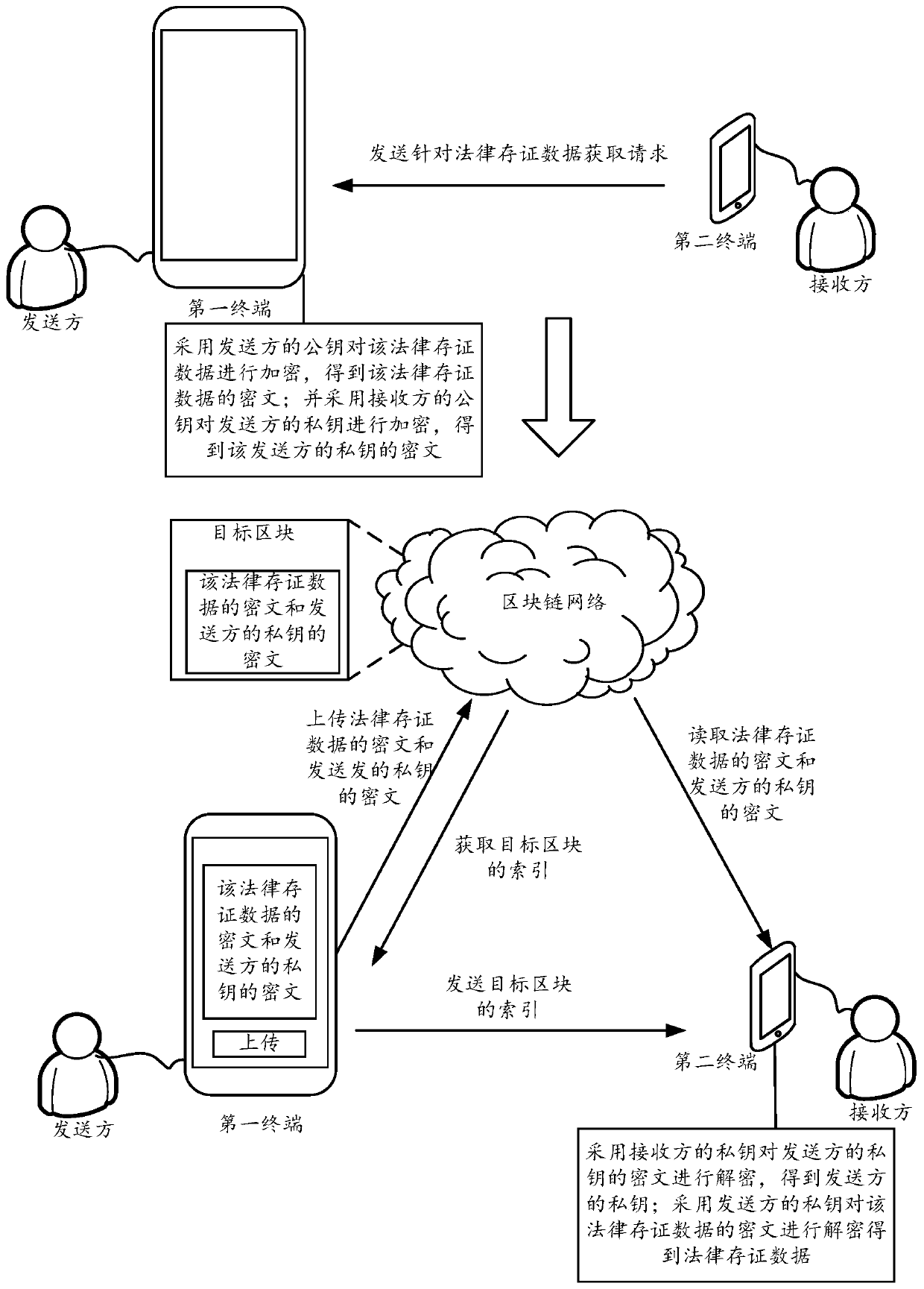
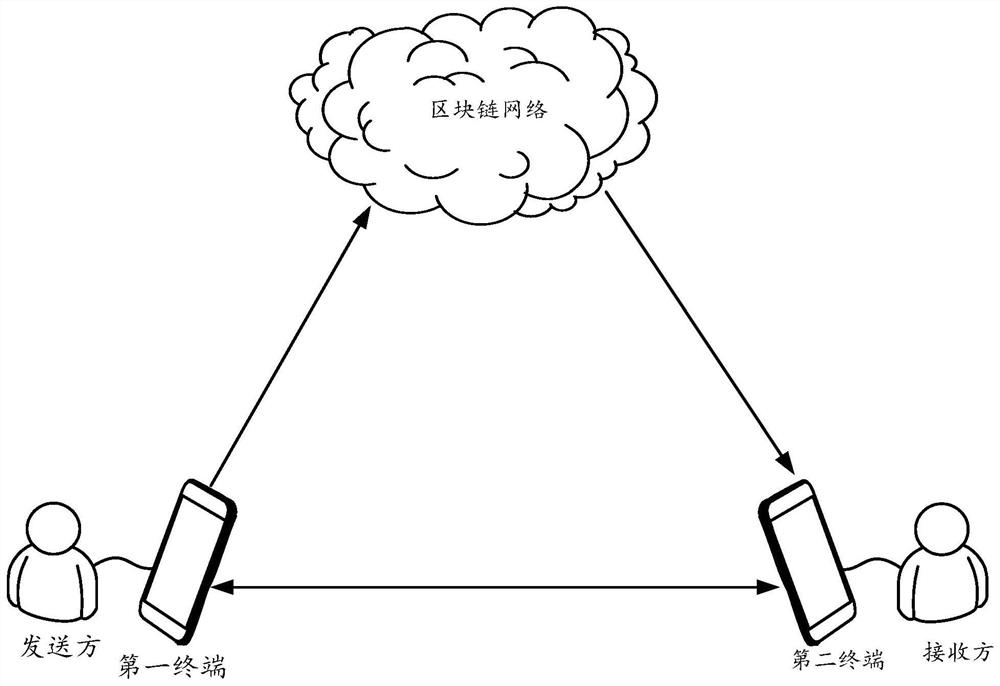
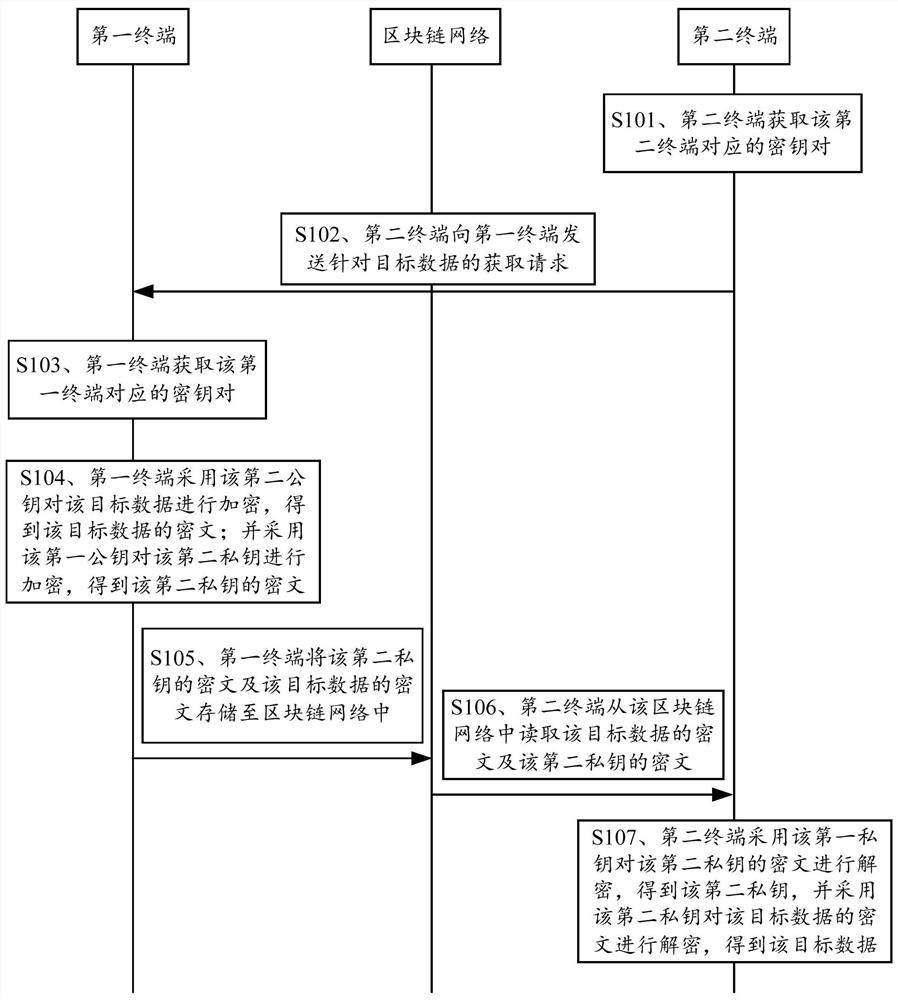
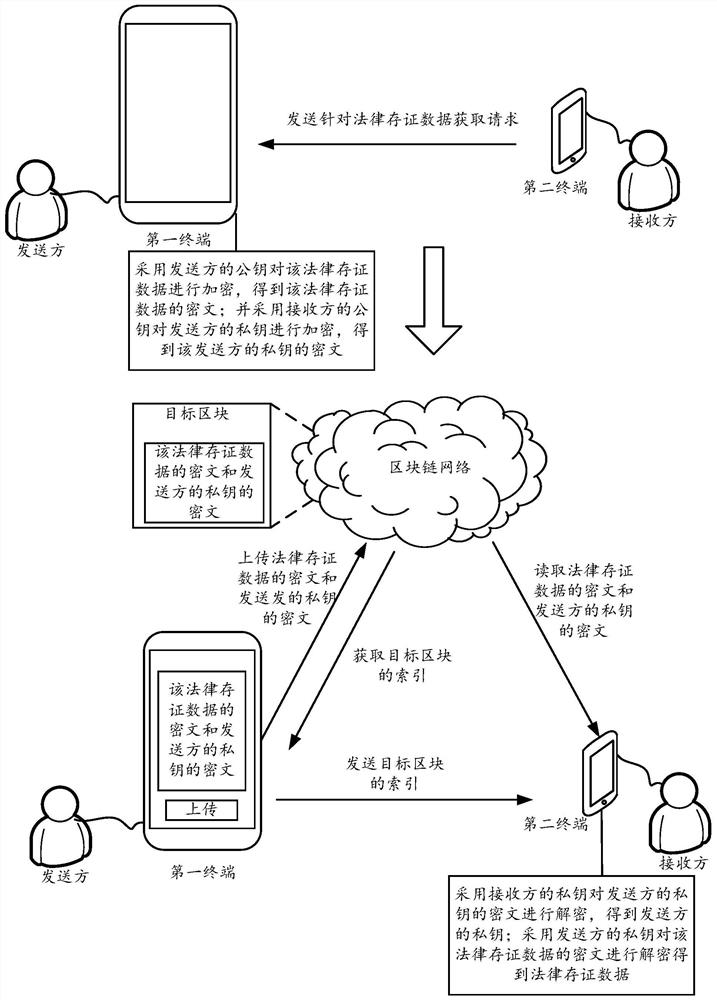
Data processing method and device based on block chain and terminal
ActiveCN110798315APrevent illegal readingPrevent leakageKey distribution for secure communicationComputer networkCiphertext
The embodiment of the invention discloses a data processing method and device based on a block chain and a terminal, and the method comprises the steps: receiving an obtaining request, sent by a second terminal, for target data, obtaining a secret key pair corresponding to a first terminal, and enabling the secret key pair corresponding to the first terminal to comprise a second private key and asecond public key; encrypting the target data by adopting the second public key to obtain a ciphertext of the target data; encrypting the second private key by adopting the first public key to obtaina ciphertext of the second private key; and storing the ciphertext of the second private key and the ciphertext of the target data in a blockchain network, so that the second terminal reads the ciphertext of the second private key and the ciphertext of the target data from the blockchain network, and decrypts the ciphertext of the target data according to the ciphertext of the second private key to obtain the target data. Through the embodiment of the invention, the security of the data in the blockchain can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Anti-counterfeiting recognition device provided with self-destructive protection assembly and self-destructive protection method
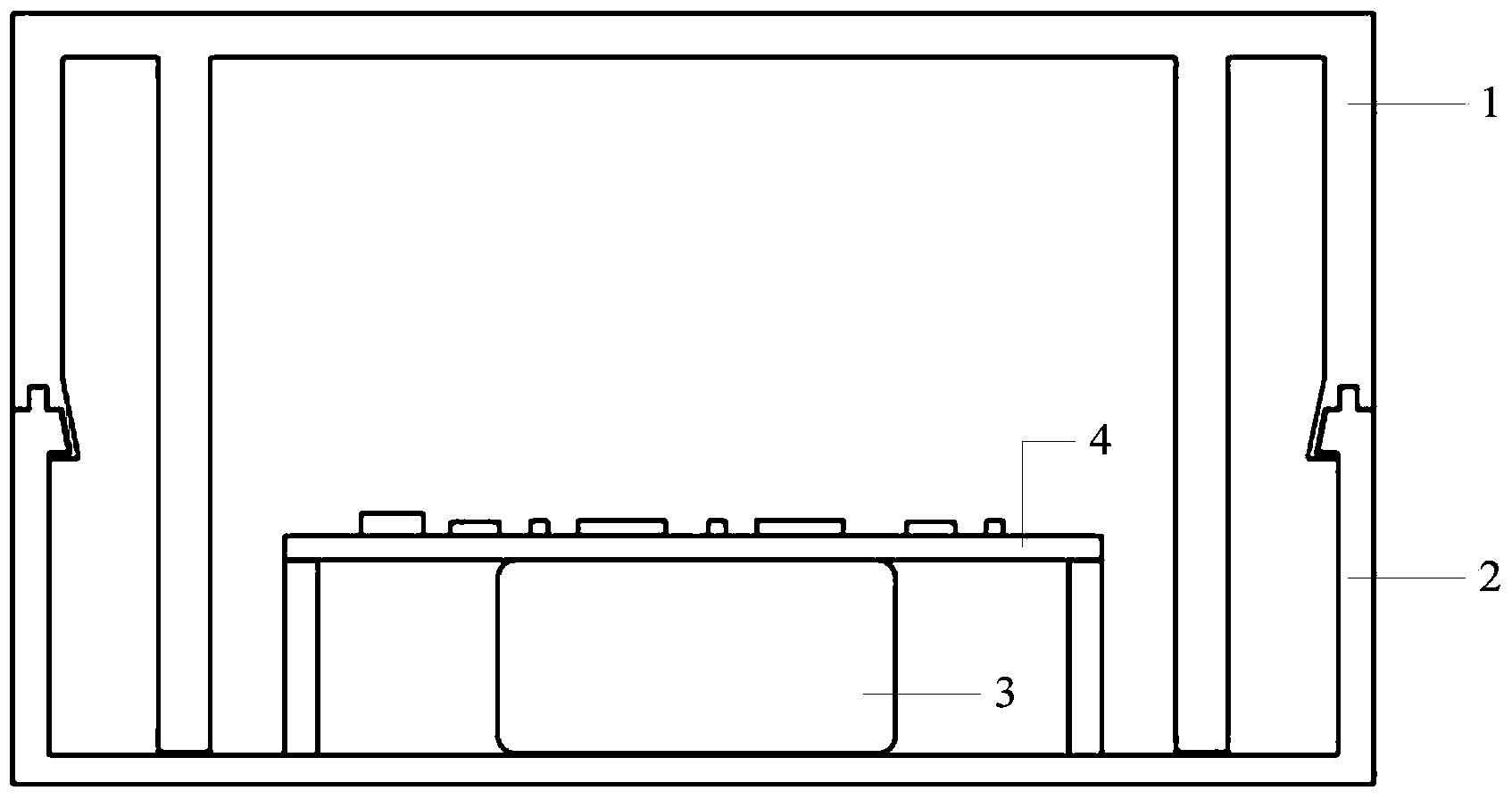
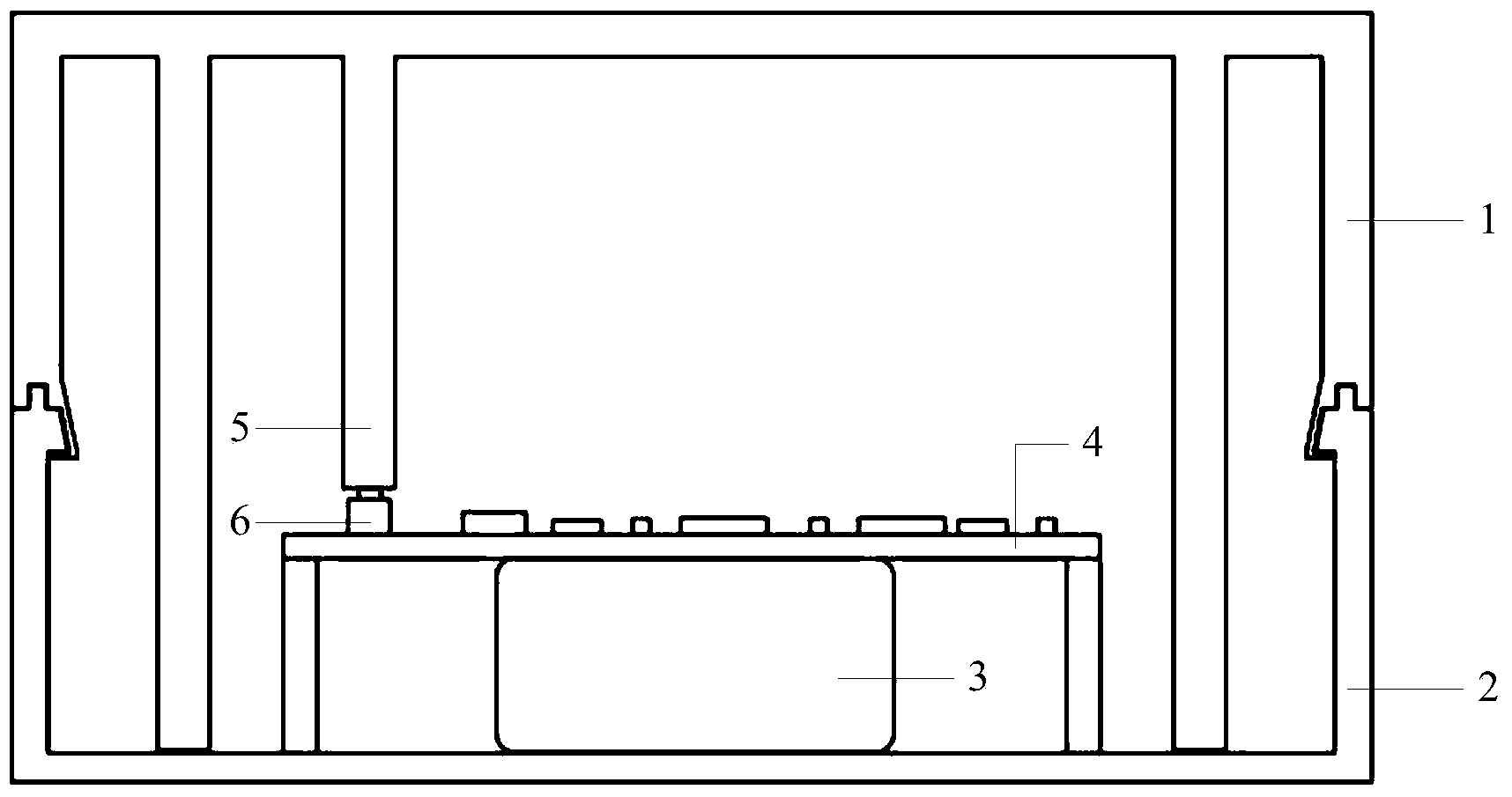
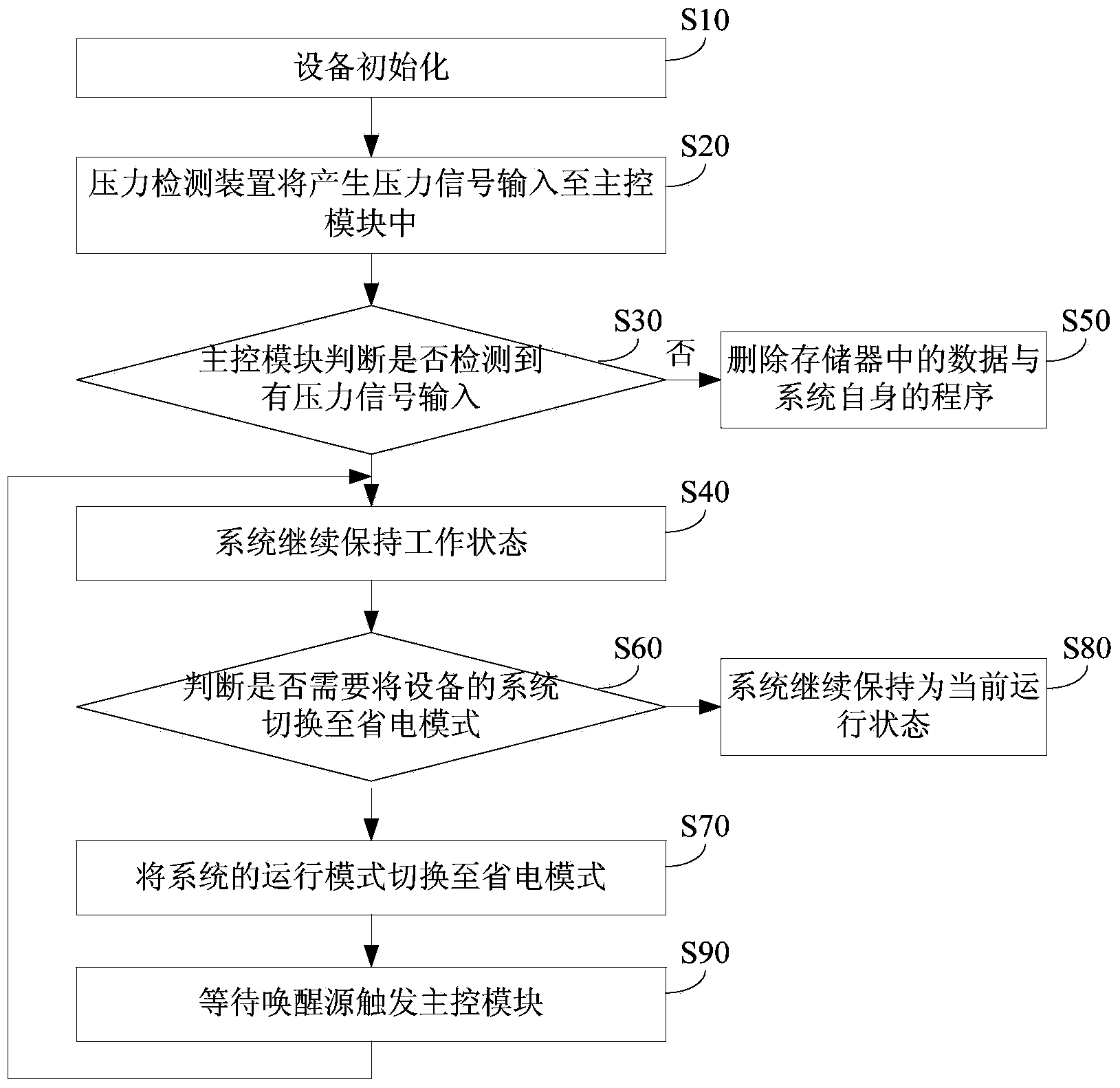
InactiveCN103942509APrevent illegal readingUnauthorized memory use protectionInternal/peripheral component protectionElectrical batteryData storing
The invention provides an anti-counterfeiting recognition device provided with a self-destructive protection assembly. The device comprises a top shell, a bottom shell, a battery fixed into the bottom shell and a circuit board connected with the battery, and further comprises at least one voltage detection device used for detecting voltage signals. The voltage detection device is connected with a main control module. The top shell is further provided with at least one convex column extending to the inside of the bottom shell, and the bottom of the convex column is in contact with the voltage detection device so as to generate the voltage signals. A method for using the device includes the steps that the main control module reads the voltage signals input by the voltage detection device in real time; when the main control module can not detect the voltage signals input by the voltage detection device in real time, the main control module starts a self-destructive program so as to delete data stored in a memory. When the device is detached illegally, the main control module can quickly delete all the data and programs in the memory at the moment that the top shell is separated from the bottom shell, so that the data and the programs in the memory are prevented from being read illegally.
Owner:LEADER TECH BEIJING DIGITAL TECH
Self-destroying protection method based on malicious invasion of file system and device thereof
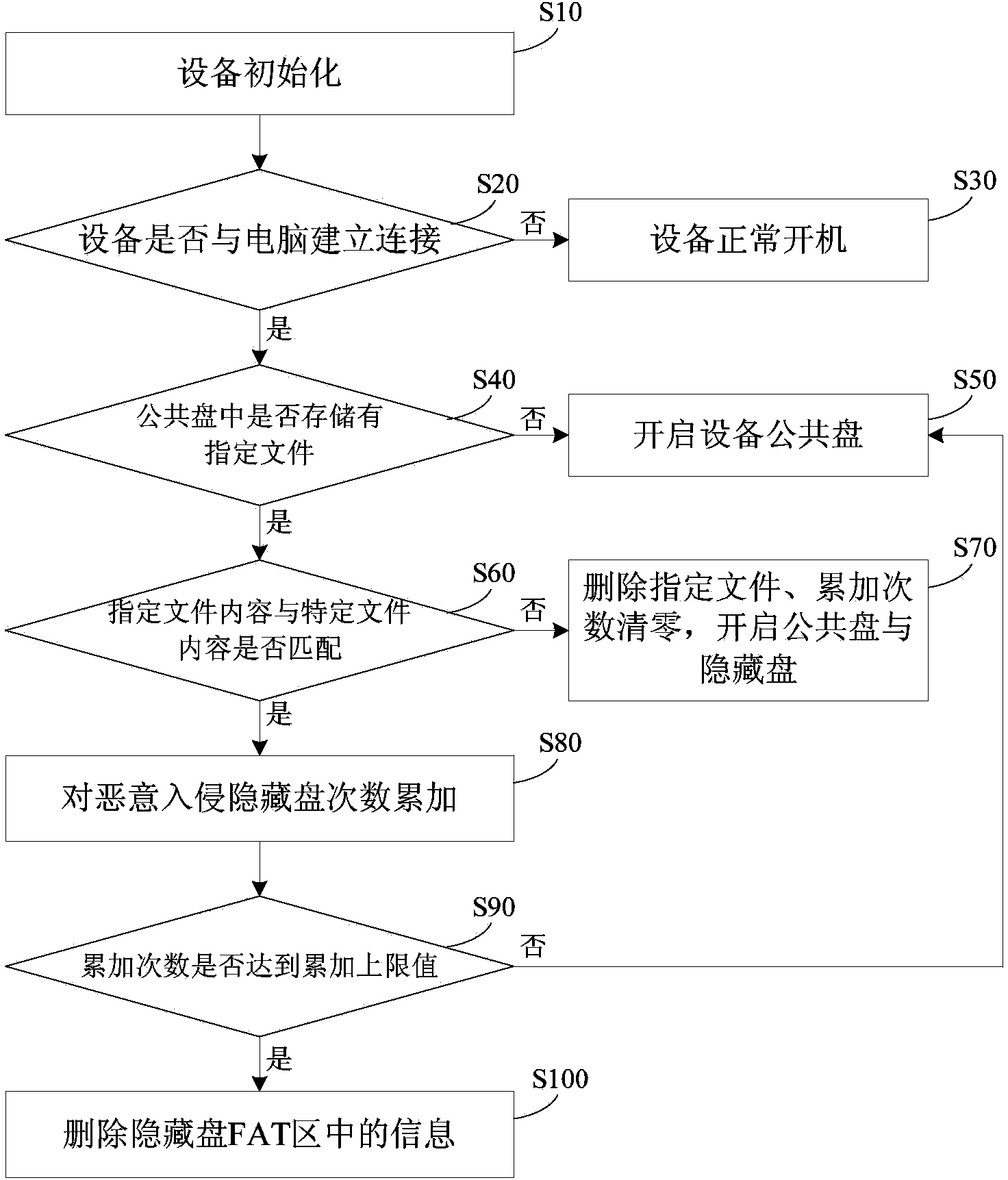
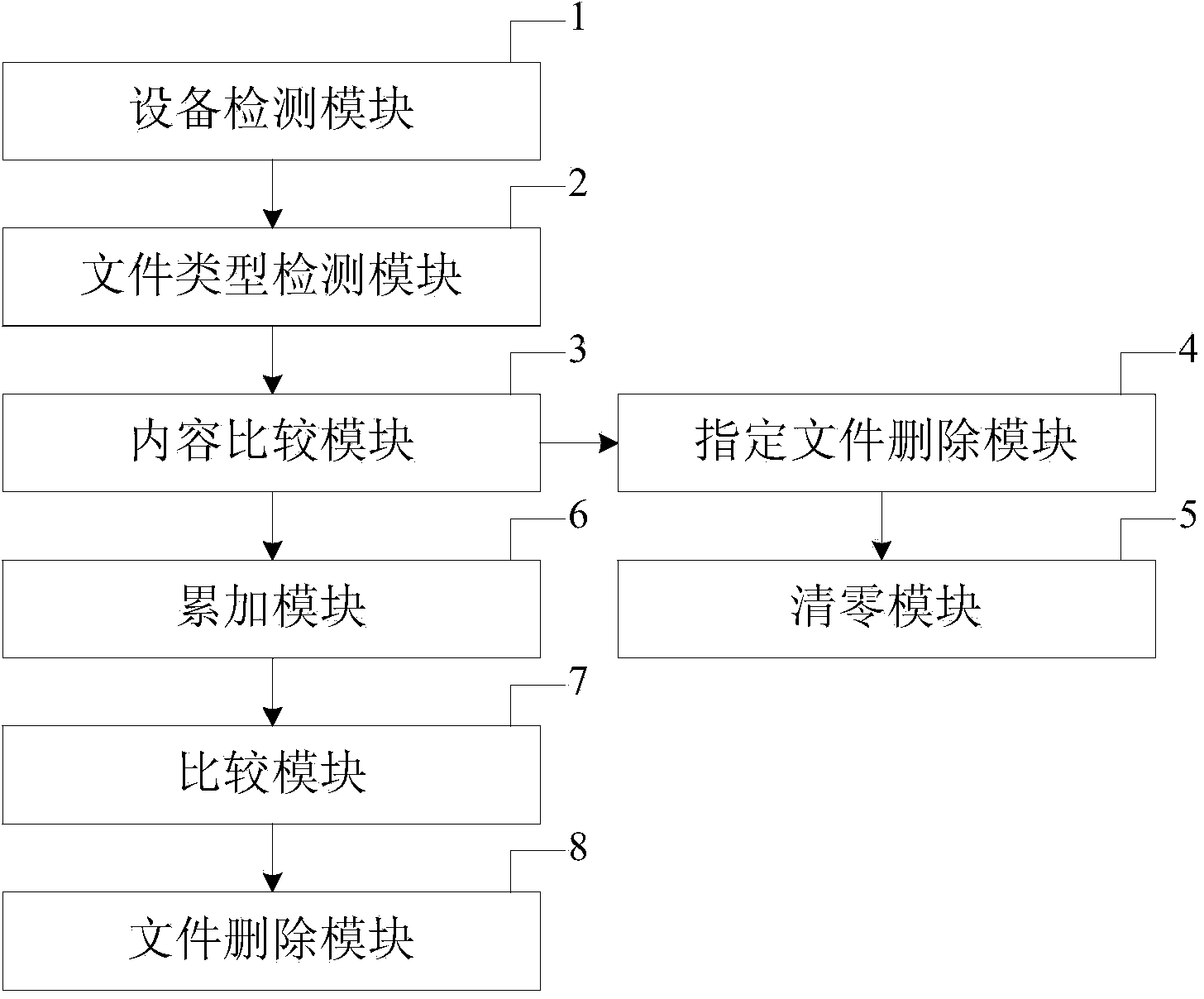
InactiveCN103942293AImprove securityPrevent illegal copyingUnauthorized memory use protectionDigital data protectionFile systemLimit value
The invention provides a self-destroying protection method based on a malicious invasion of a file system. The method comprises the steps that when the content of a specified file in a common disk is not matched with the content in a specific file, the number of times of the malicious invasion of a hidden disk is accumulated; when the number of times of the malicious invasion of the hidden disk reaches an upper limit, the file system of the hidden disk is deleted, and the content in the hidden disk cannot be read. A device executing the method comprises a file type detection module, a content comparison module, an accumulating module, a comparison module for the number of times and a file system deleting module. The file type detection module is used for detecting the type of the specified file stored in the common disk of equipment, the content comparison module is used for distinguishing whether the content of the specified file is matched with that of the specific file or not, the accumulating module is used for accumulating the number of times of the malicious invasion of the hidden disk, the comparison module for the number of times is used for comparing the accumulated number of times of the malicious invasion of the hidden disk and the upper limit value of the accumulated number of times, and the file system deleting module is used for deleting information in an FAT area of the hidden disk. According to the method and the device, the safety of data in the equipment can be improved, and the data are effectively prevented from being illegally copied.
Owner:LEADER TECH BEIJING DIGITAL TECH
Data storage method, data reading method and device
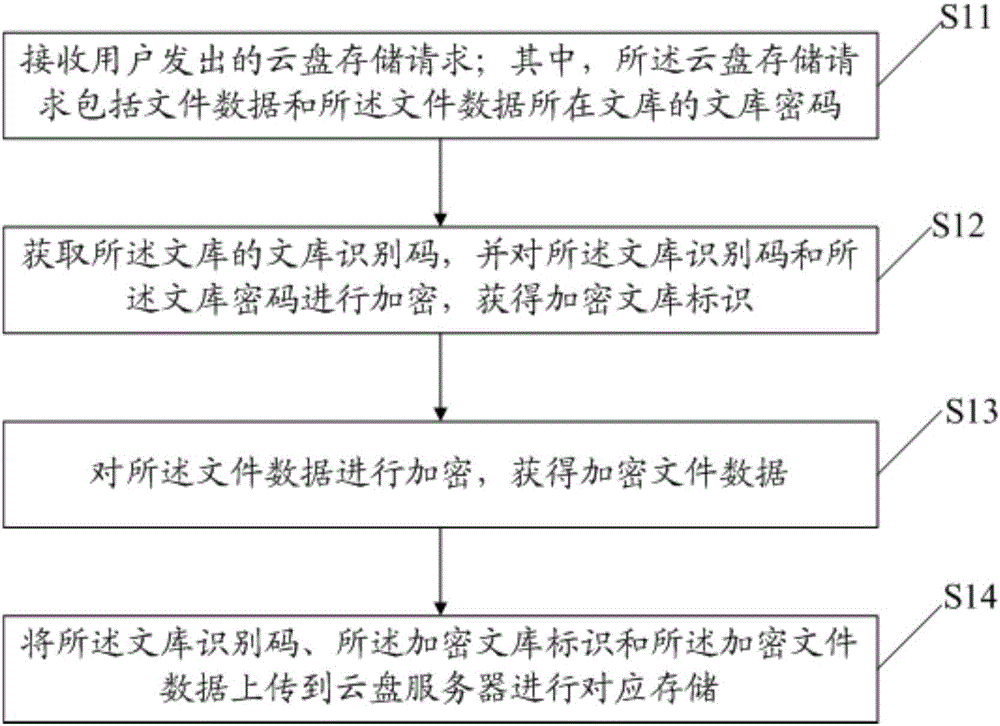
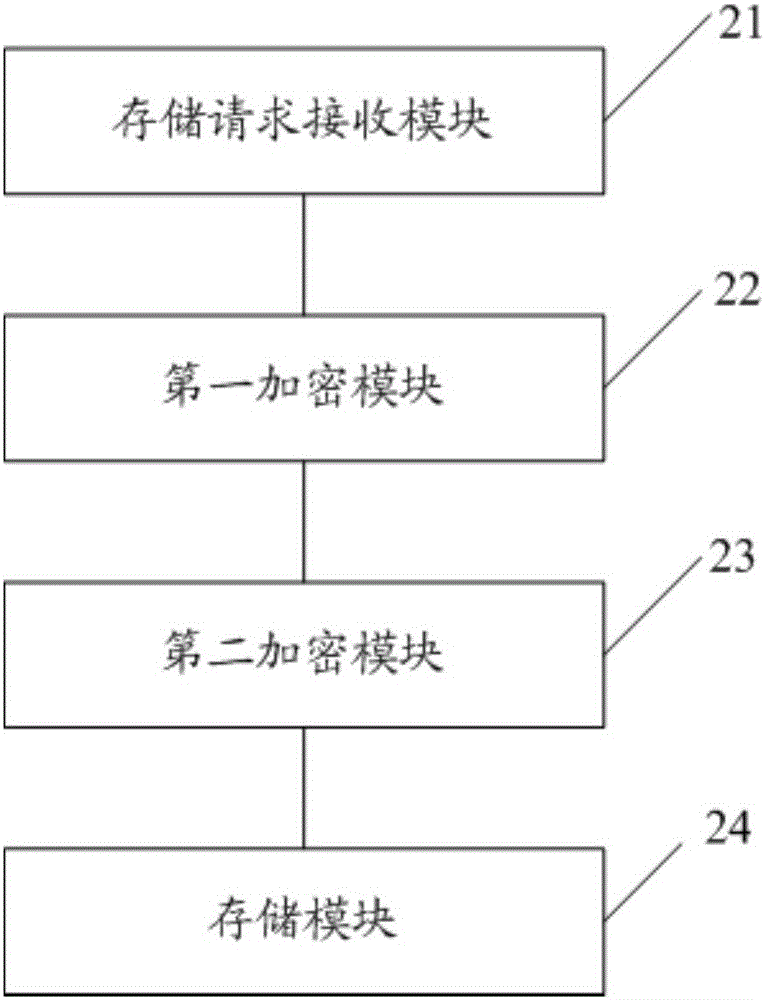
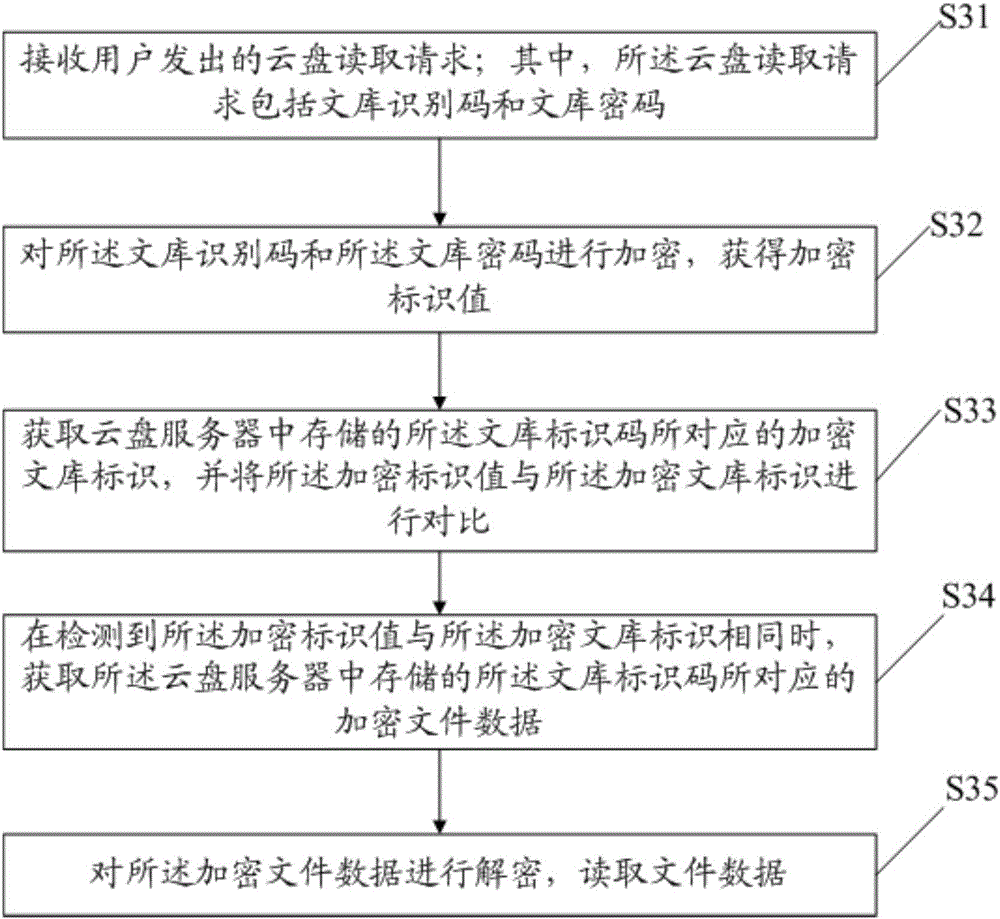
The invention discloses a data storage method which comprises the steps that a cloud disk storage request sent out by a user is received, wherein the cloud disk storage request comprises document data and a library password of a library in which the document data is located; a library identification code of the library is acquired, the library identification code and the library password are encrypted, and an encrypted library identifier is obtained; the document data is encrypted, and encrypted document data is obtained; and the library identification code, the encrypted library identification and the encrypted document data are uploaded to a cloud disk server for corresponding storage. Correspondingly, the invention also discloses a data reading method and a device. By the data storage method, the data reading method and the device disclosed by the embodiment of the invention, the data storage becomes safer; operations are simple; and user experience is improved.
Owner:GCI SCI & TECH
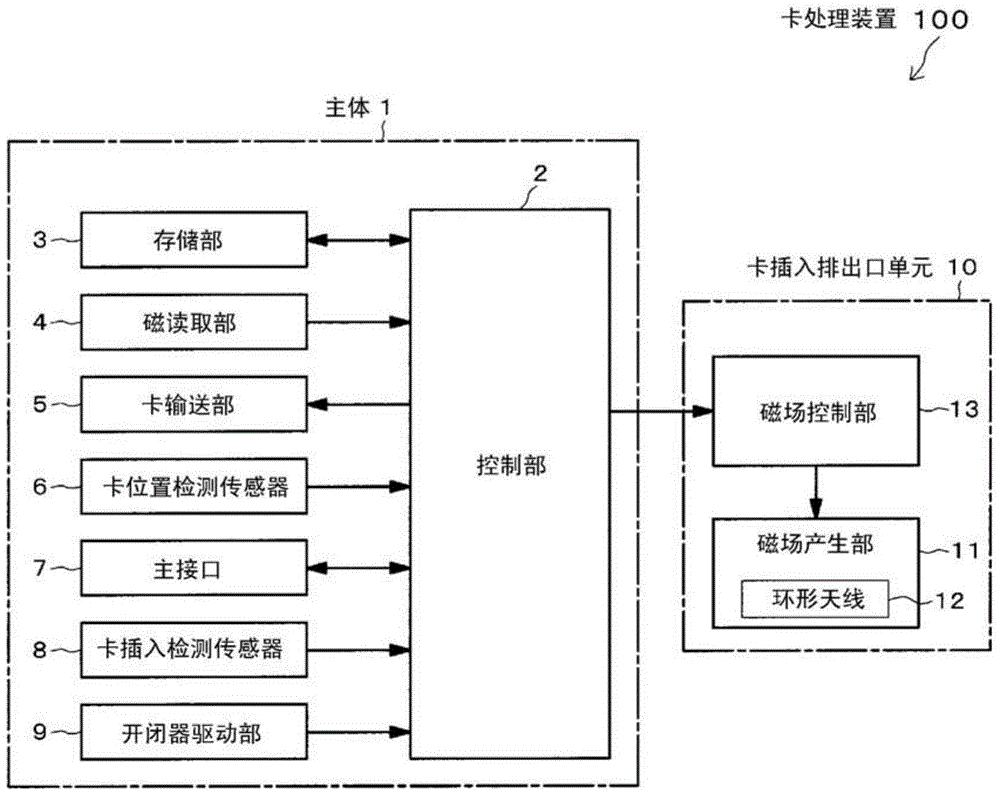
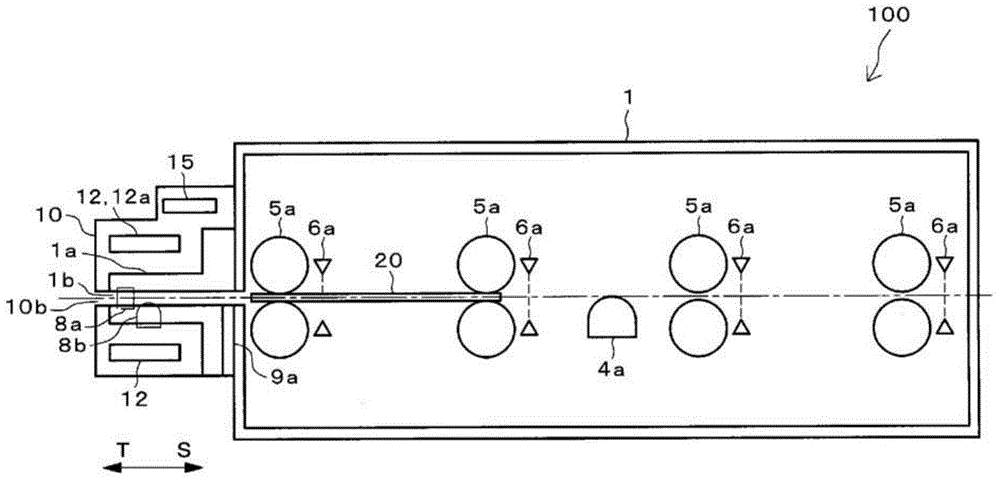
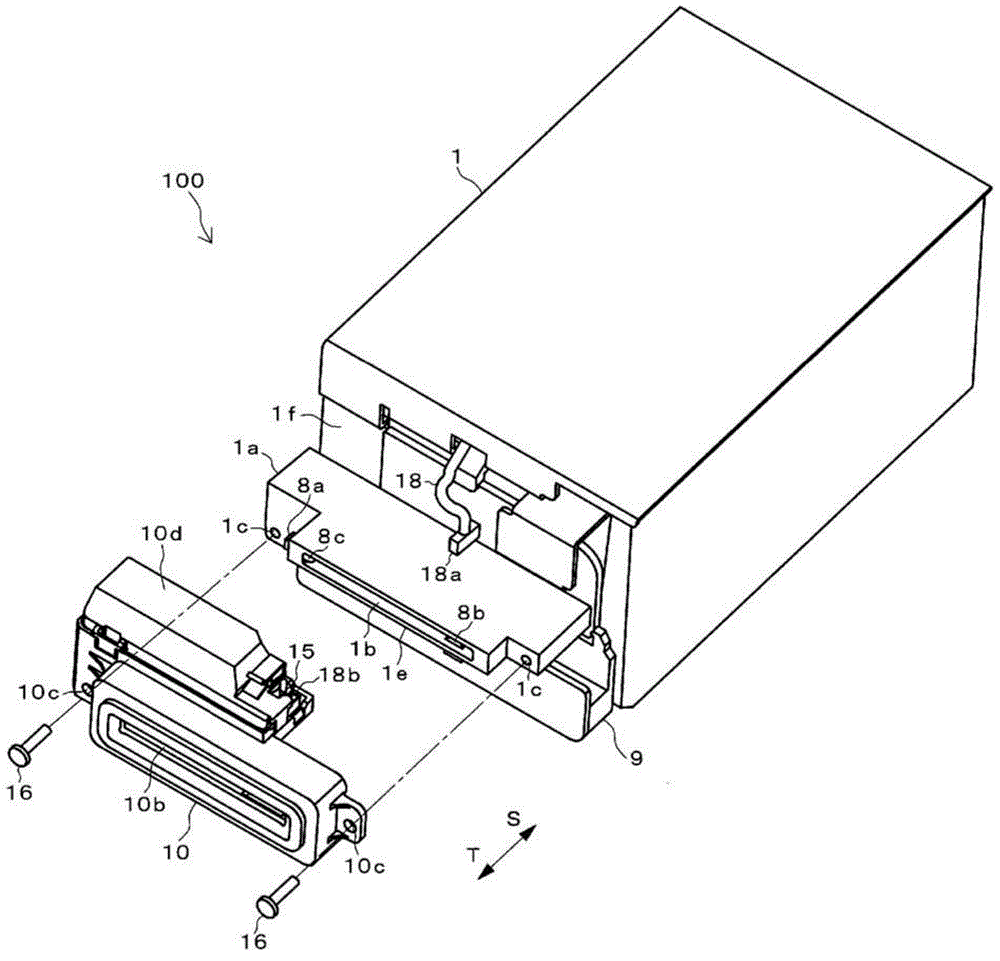
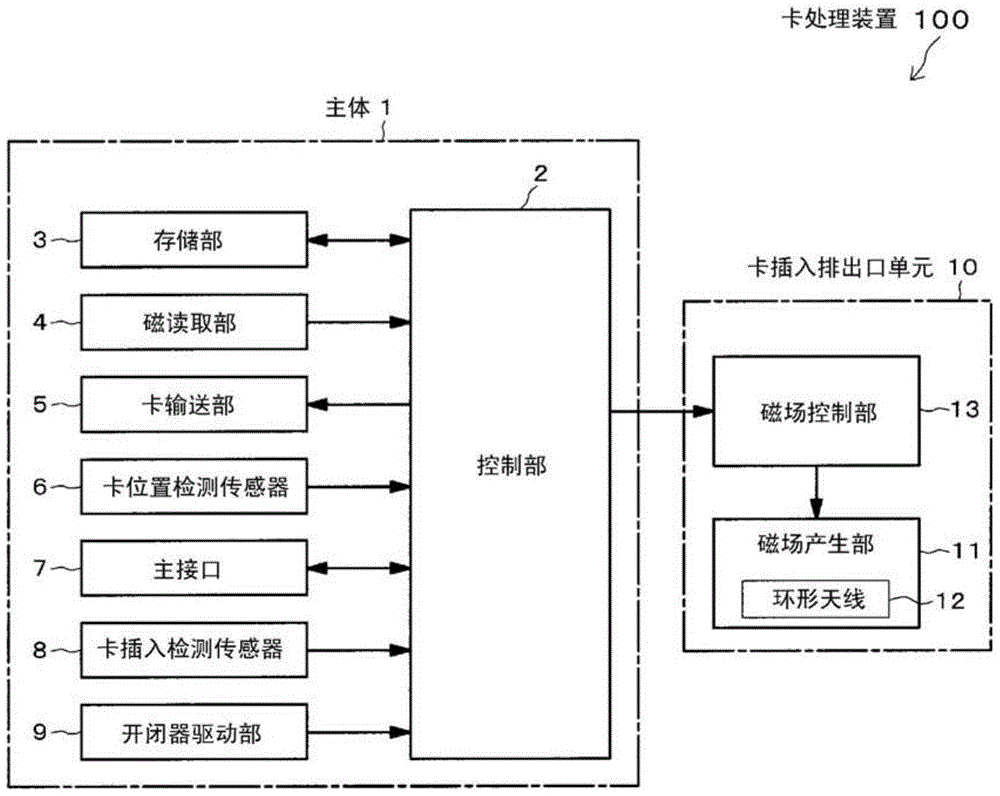
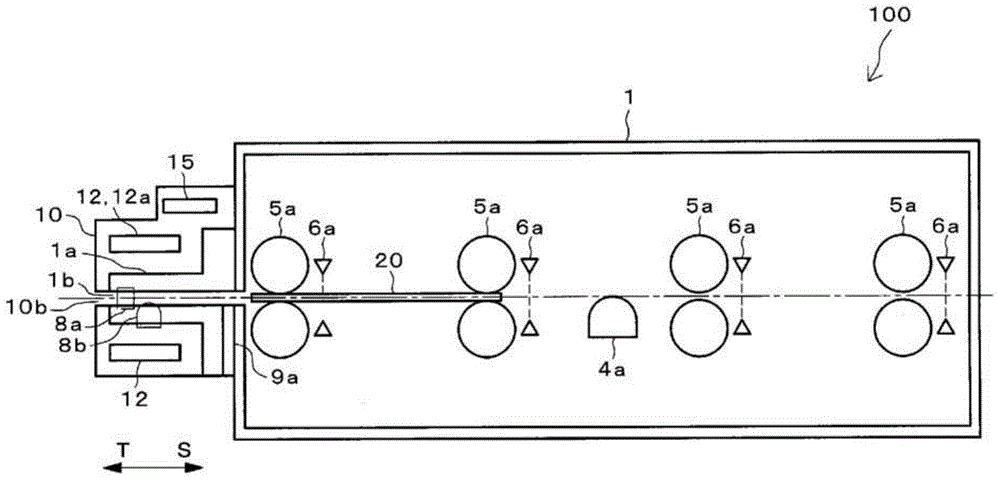
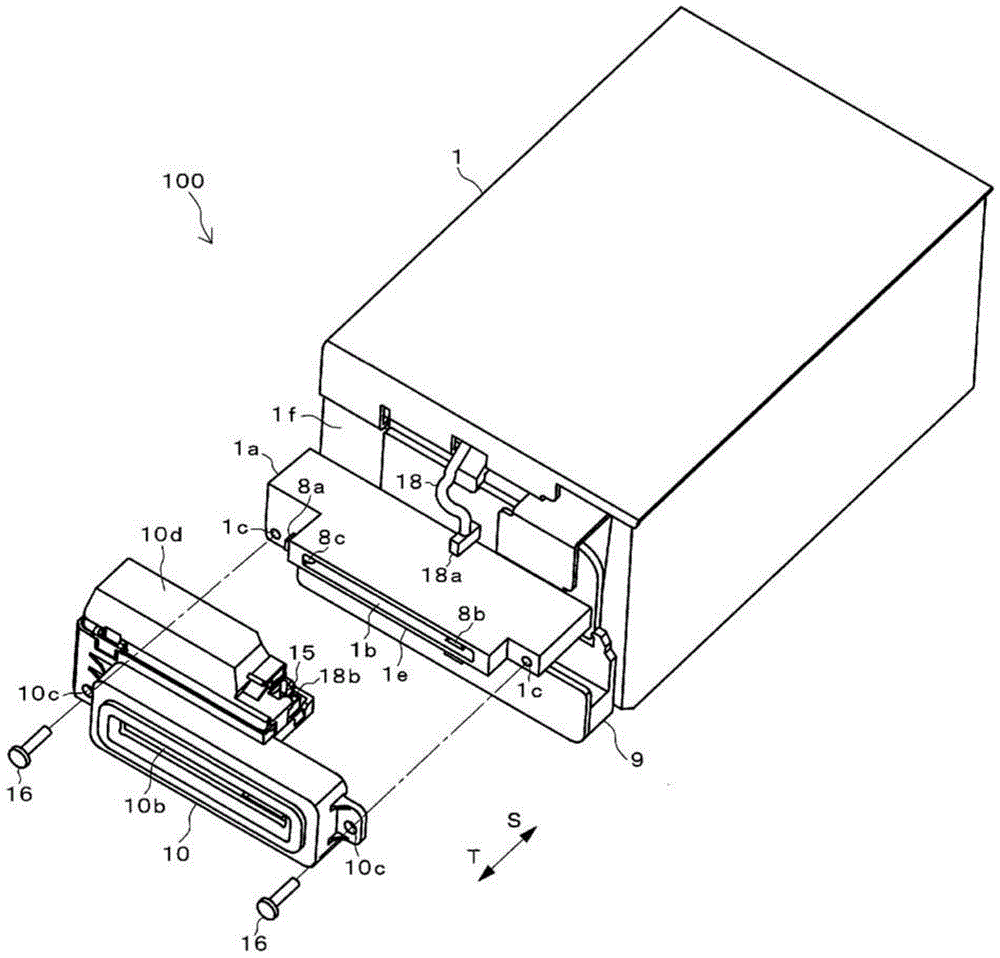
Card insertion and ejection opening unit and card processing device
InactiveCN104487983APrevent illegal readingImprove maintainabilityAcutation objectsConveying record carriersComputer hardwareMagnetic field
A card processing device (100) in which a card transfer unit (5) transfers a magnetic card (20) and a magnetic reading unit (4) reads magnetic information recorded in the magnetic card (20) in a body part (1) is provided with a card insertion and ejection opening unit (10). The card insertion and ejection opening unit (10) includes an opening (10b) into which and from which the magnetic card (20) is inserted and ejected, and a magnetic field generation unit (11) for generating an interference magnetic field, and is detachable from a card slot part (1a) of the body part (1) of the card processing device (100).
Owner:HITACHI OMRON TERMINAL SOLUTIONS CORP
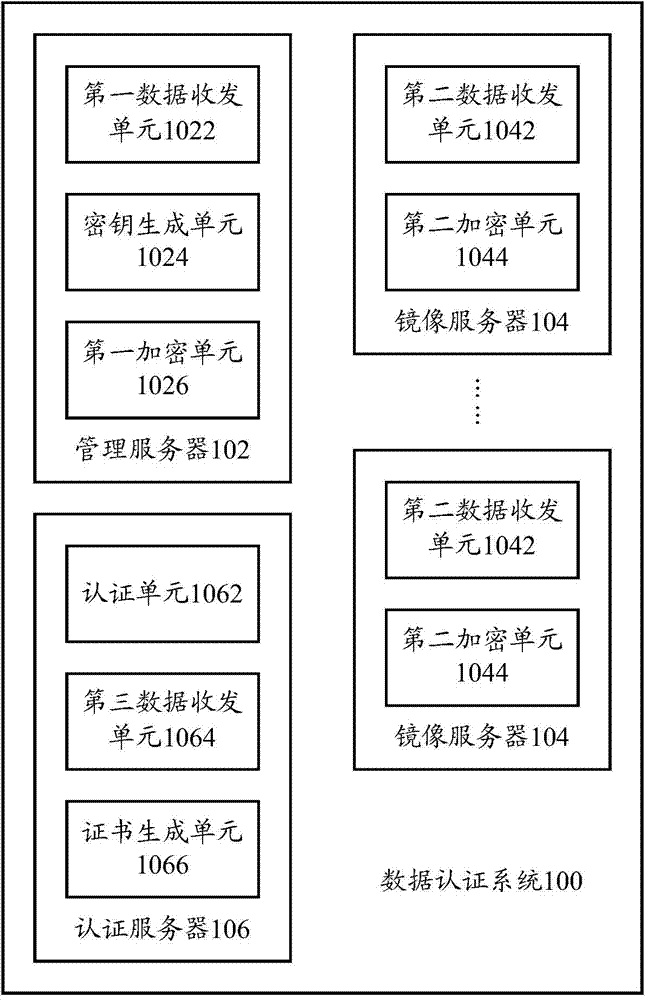
Data authentication system and data authentication method
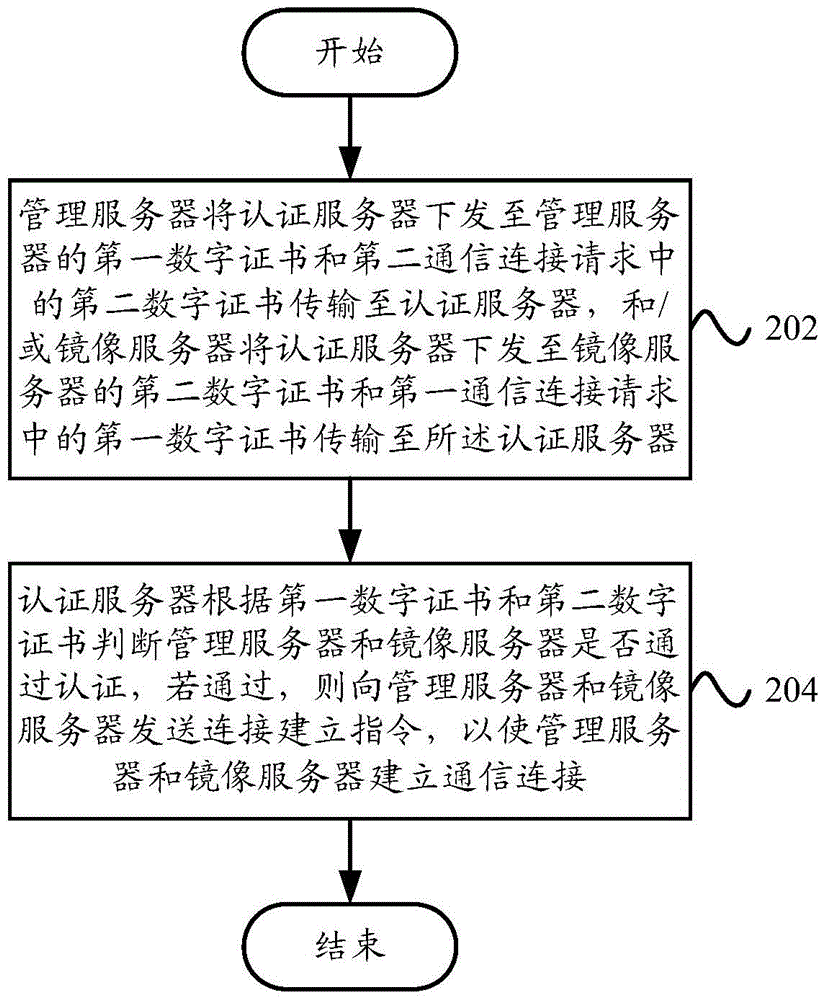
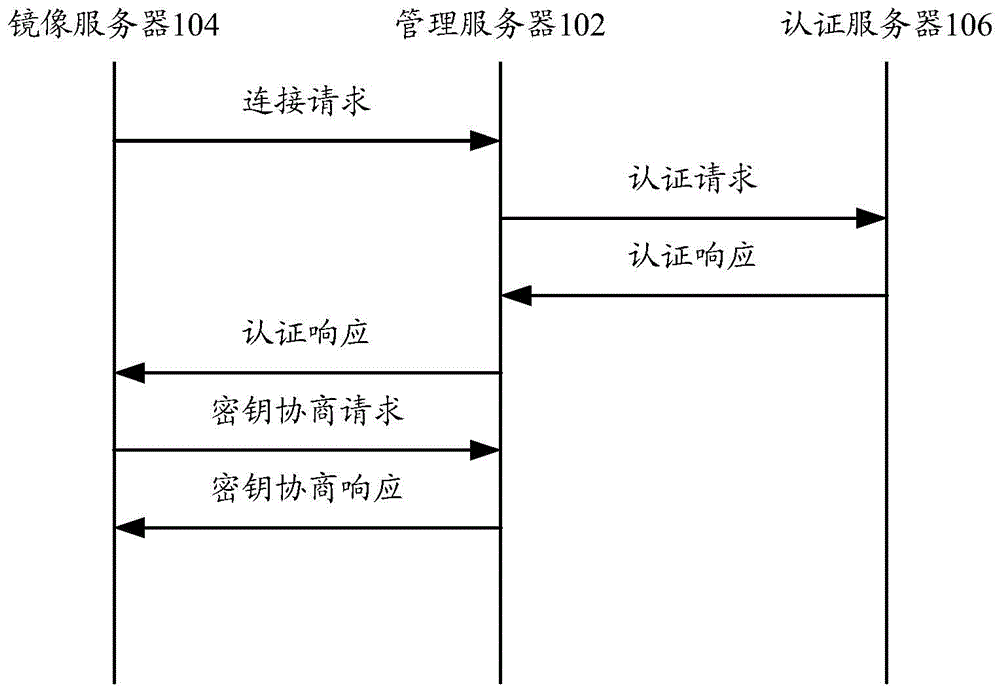
ActiveCN103501230AEnsure safetyPrevent illegal readingUser identity/authority verificationData Authentication AlgorithmAuthentication server
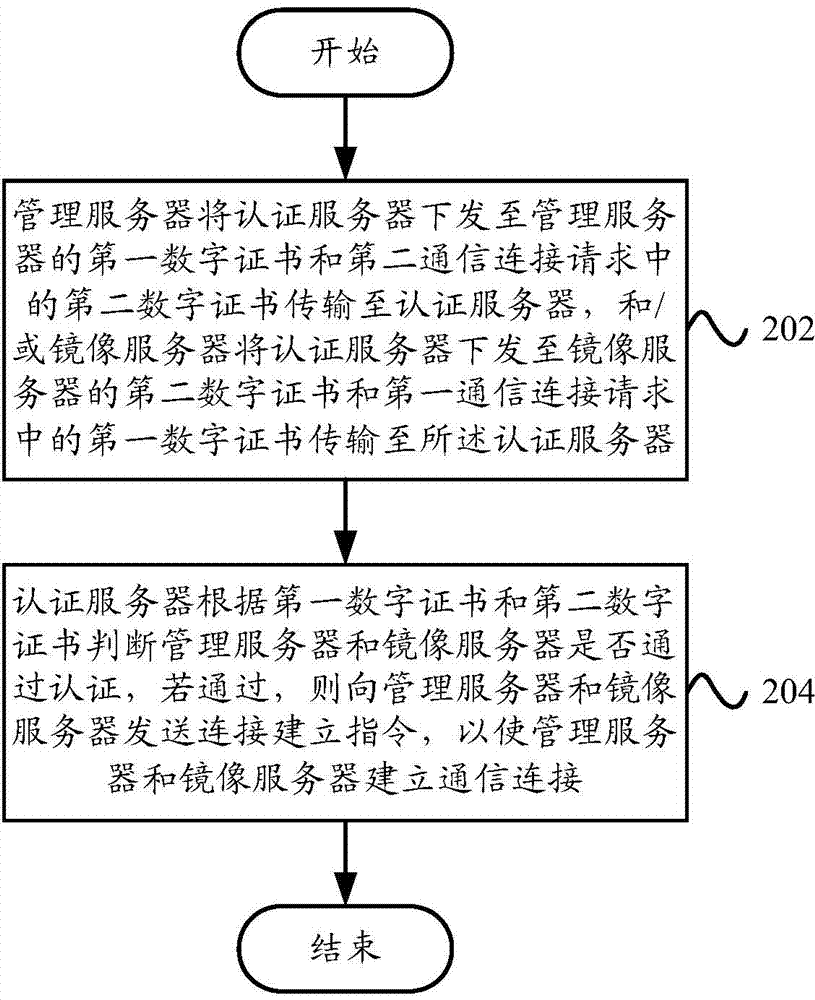
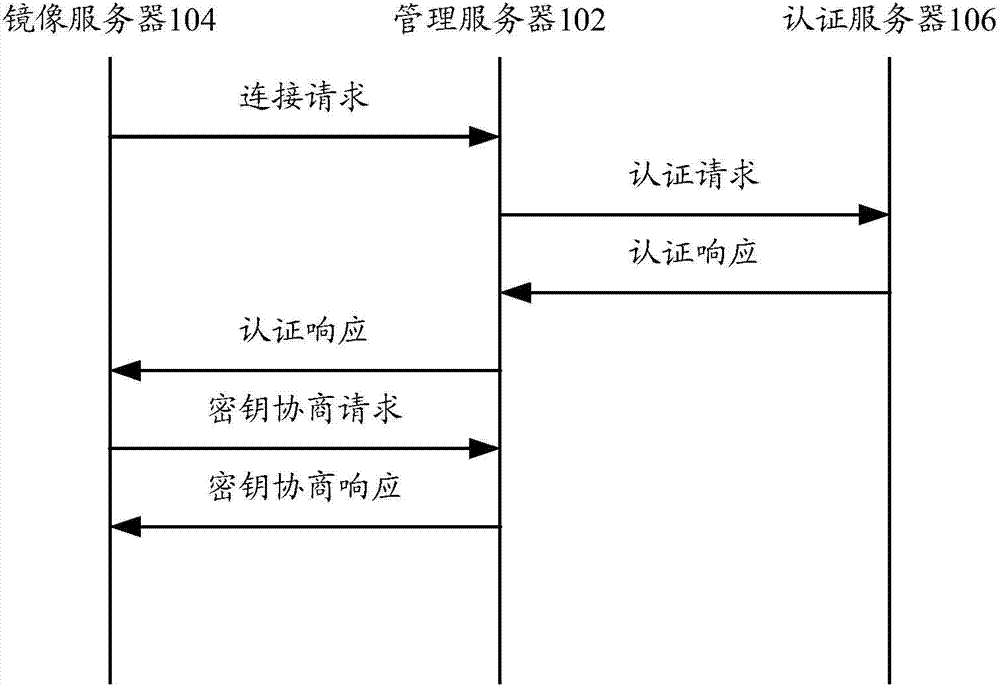
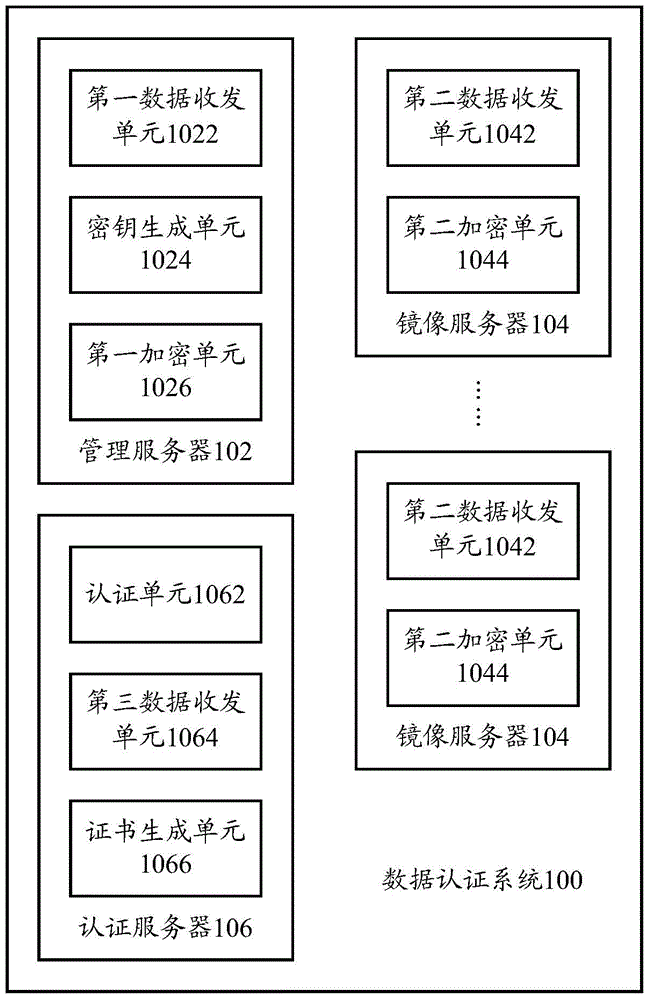
The invention provides a data authentication system, which comprises a management server, at least one mirror image server and an authentication server, wherein the management server is used for receiving a first communication connection request, and transmitting a first digital certificate and a second digital certificate in the first communication connection request to the authentication server; the at least one mirror image server is used for receiving a second communication connection request, and transmitting the second digital certificate and the first digital certificate in the second communication connection request to the authentication server; the authentication server is used for judging whether the management server and the at least one mirror image server pass authentication or not, and if the management server and the at least one mirror image server pass the authentication, a communication connection is allowed to be established between the management server and the at least one mirror image server. The invention also provides a data authentication method. According to the technical scheme provided by the invention, the safety of patient information in the management server and the at least one mirror image server can be ensured, and therefore, the patient information in the management server and the at least one mirror image server is prevented from being illegally read, and illegal information is prevented from being written in the management server or the at least one mirror image server.
Owner:PKU HEALTHCARE IT
Secure communication method and system of mobile terminal
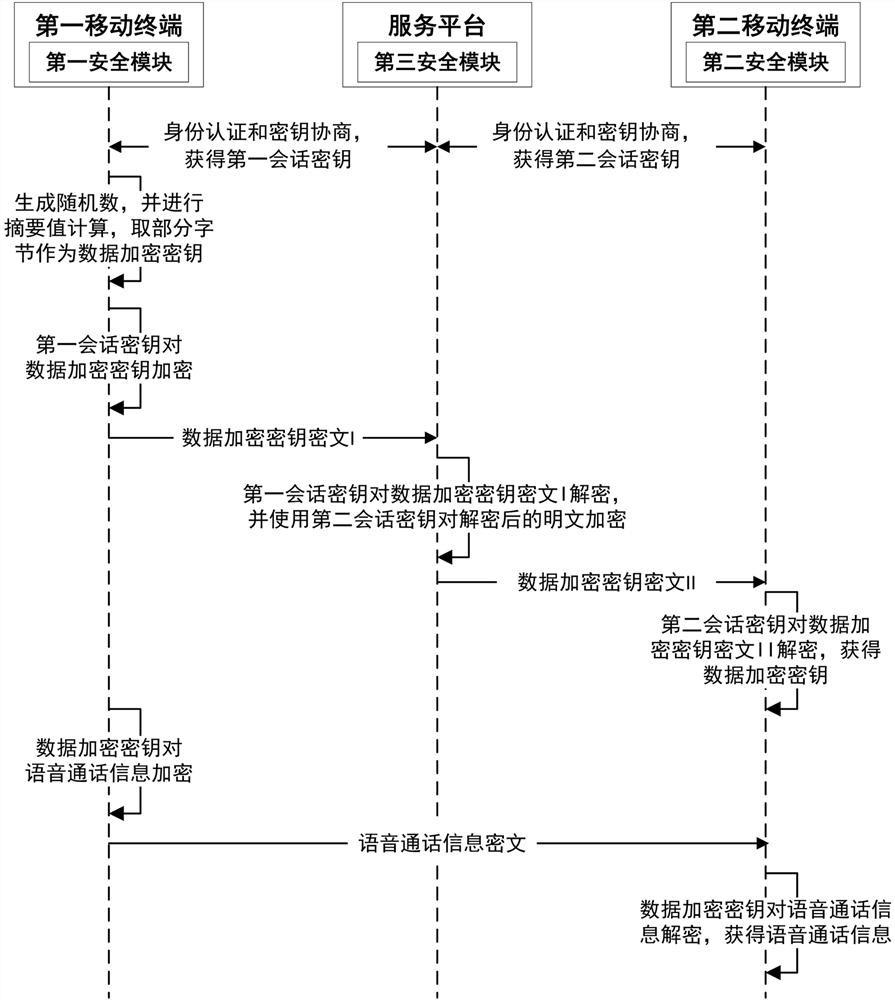
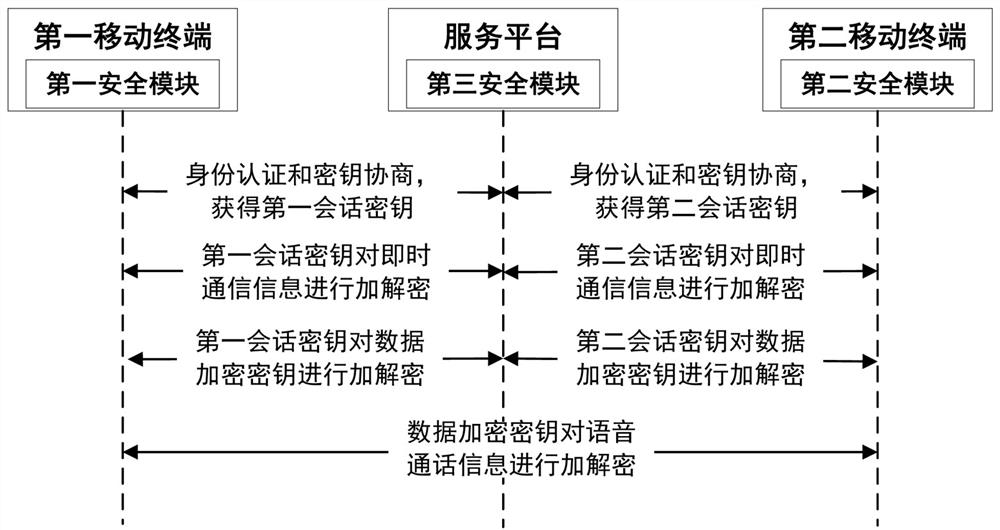
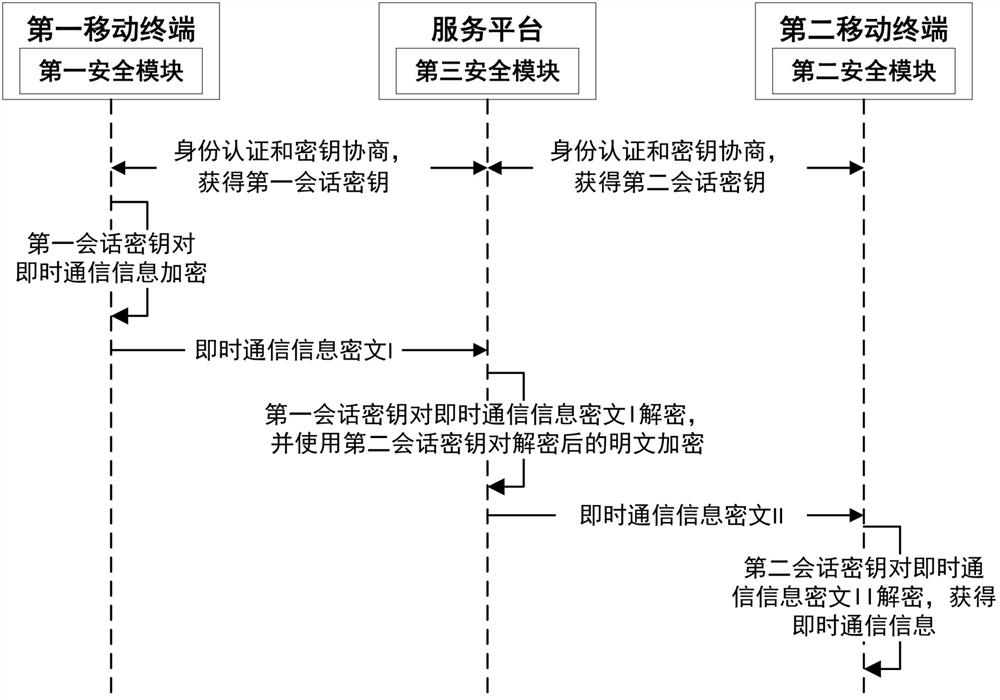
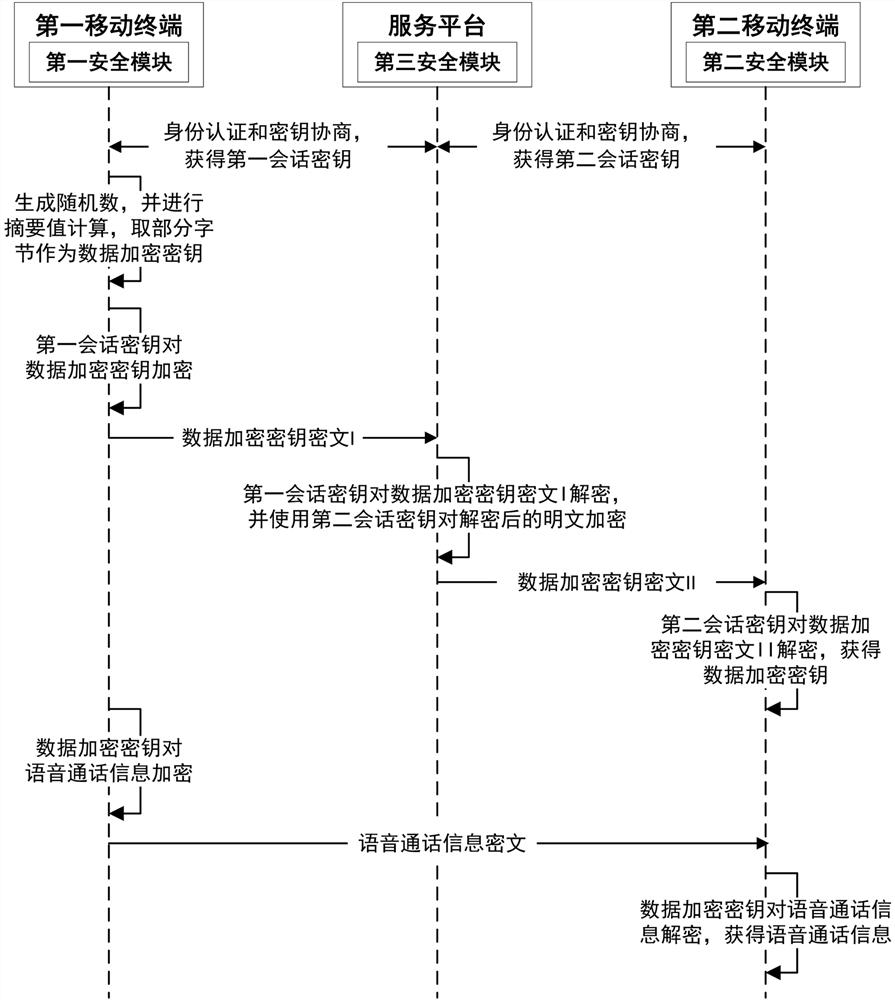
ActiveCN112054905AGuaranteed Interaction SecurityEnsure safetyKey distribution for secure communicationUser identity/authority verificationSecure communicationEngineering
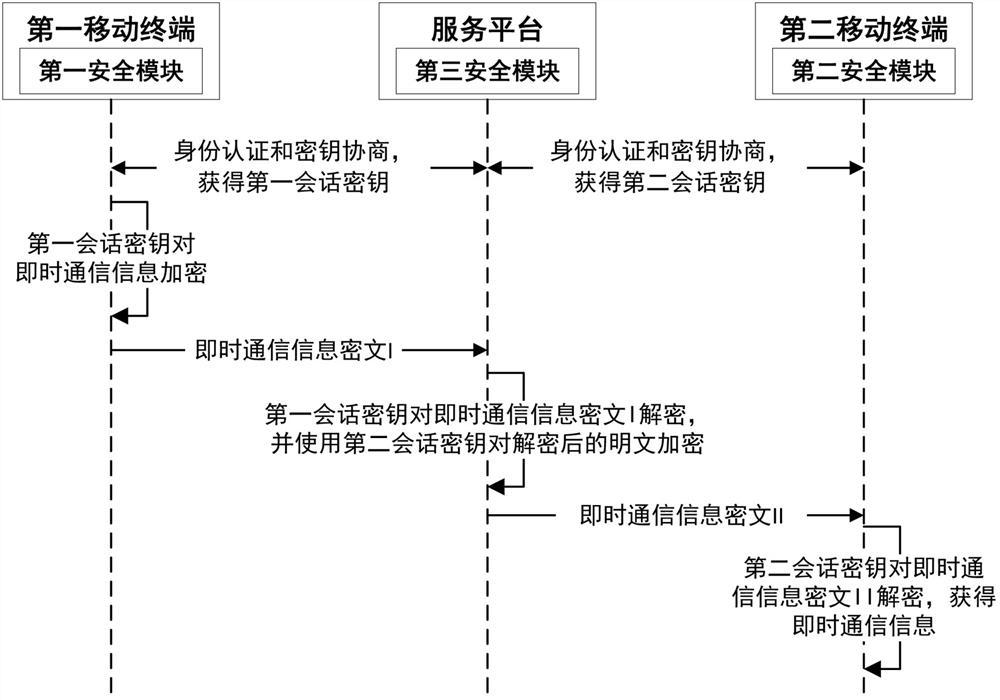
The invention provides a secure communication method and system of a mobile terminal. The method comprises a key negotiation process, a secure instant messaging process and a secure call process. Thekey negotiation process comprises the following steps: a first mobile terminal and a service platform obtain a first session key after identity authentication and key negotiation; a second mobile terminal performs identity authentication and key negotiation with the service platform to obtain a second session key; in the safe instant messaging process, the first mobile terminal encrypts and decrypts instant messaging information by adopting the first session key and the second session key between the service platform and the second mobile terminal; in the secure call process, the first mobileterminal uses the first session key, the second session key and the second mobile terminal to distribute a data encryption key through the service platform; and the first mobile terminal and the second mobile terminal encrypt and decrypt voice call information through the data encryption key.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
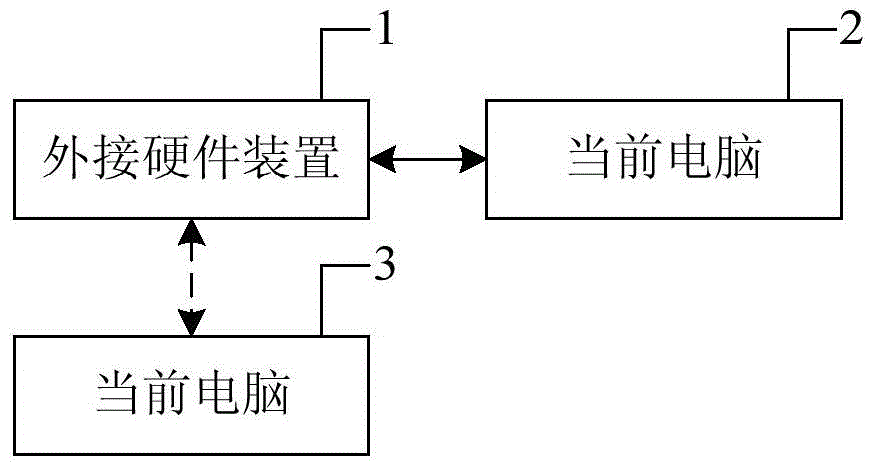
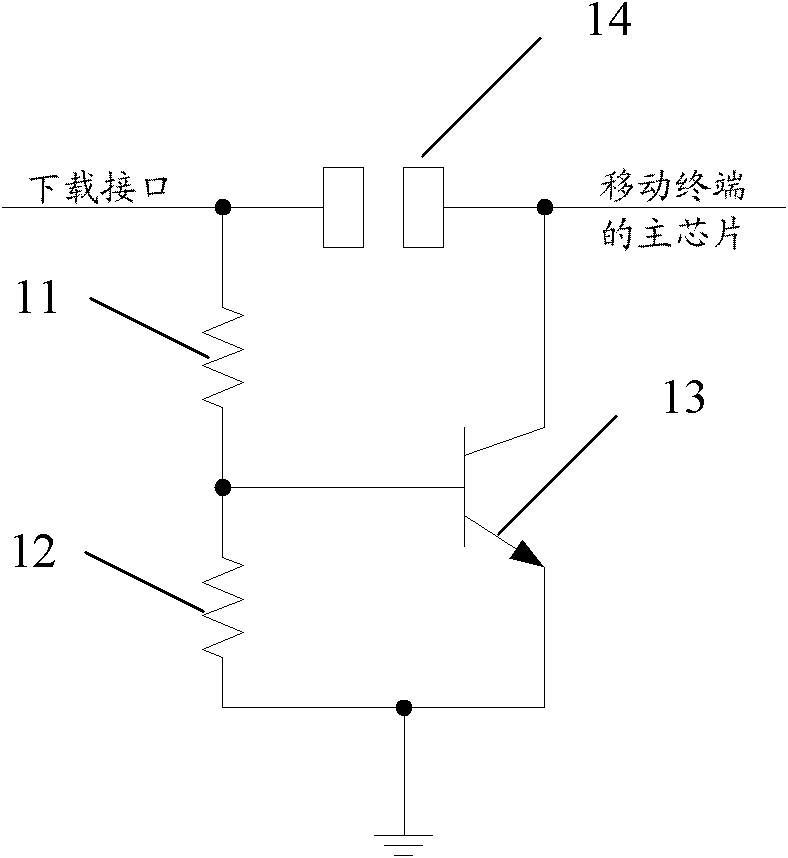
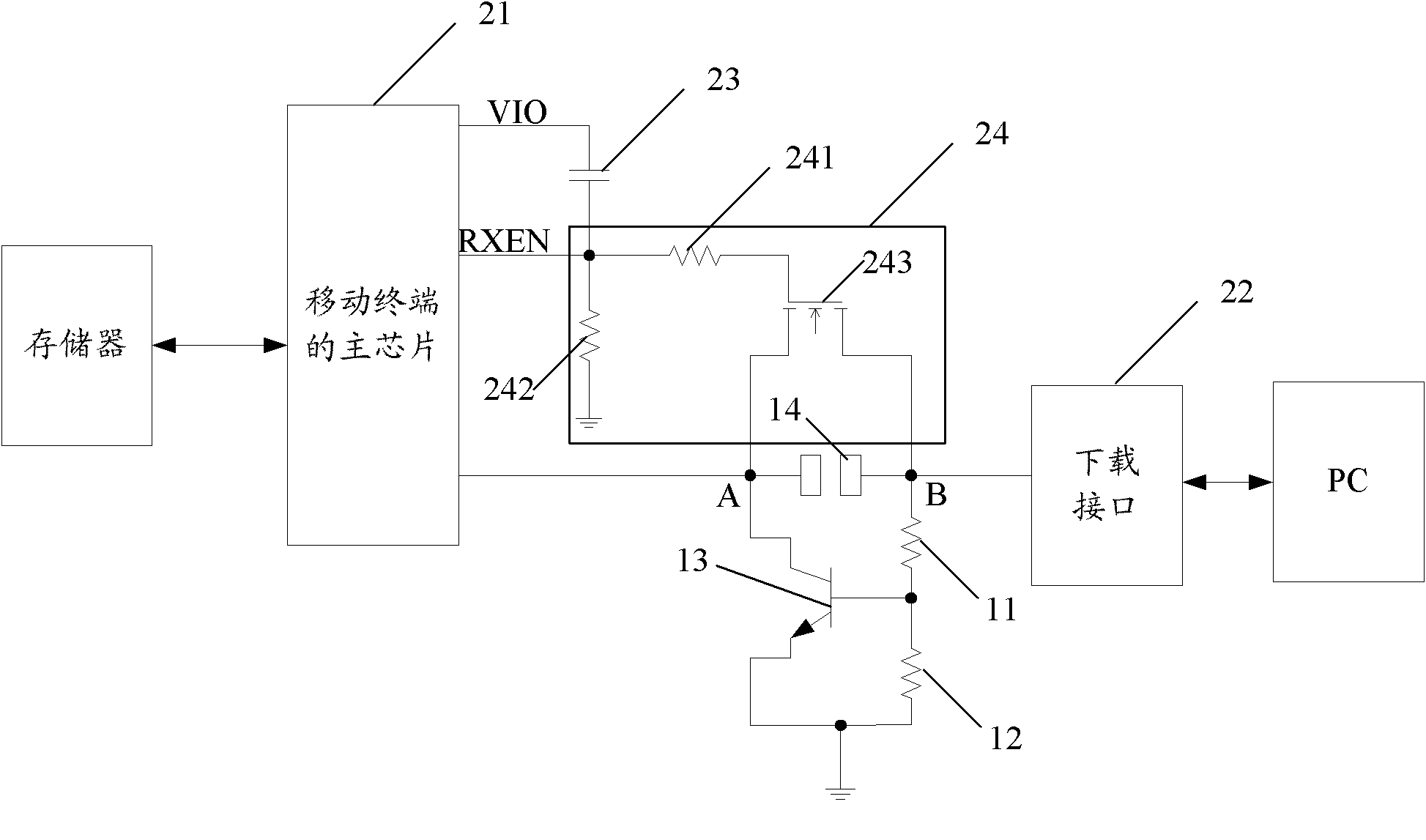
Device for recovering mobile terminal download access
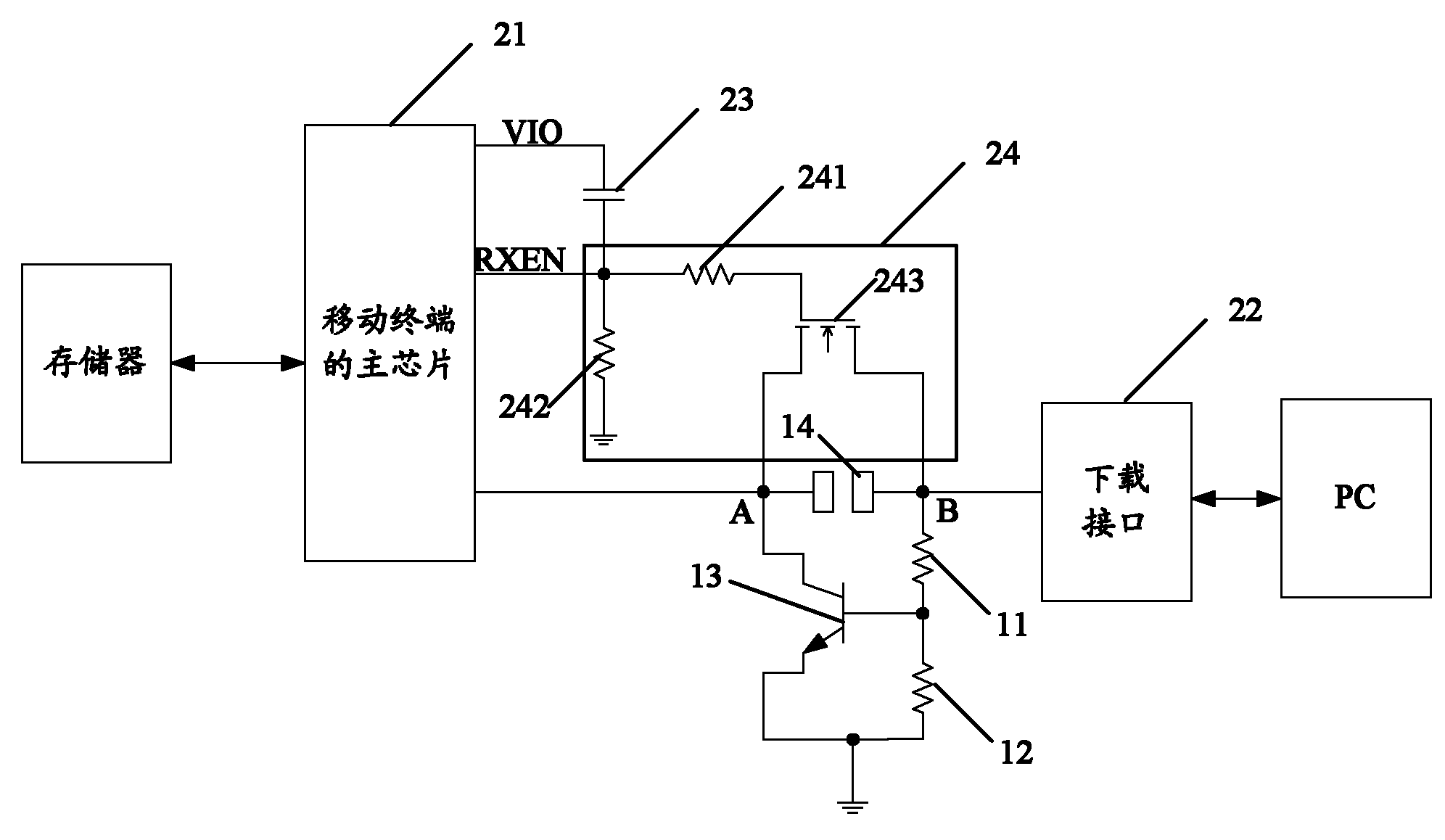
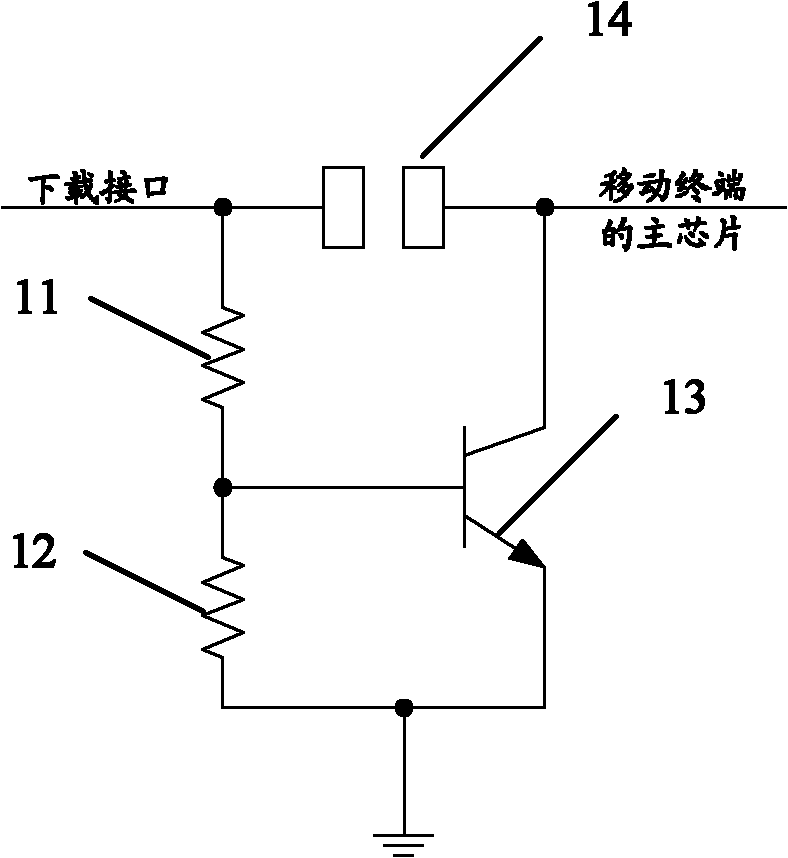
ActiveCN102111917APrevent illegal readingTo achieve the purpose of locking the networkSubstation equipmentWireless communicationComputer terminalCapacitor
The invention discloses a device for recovering a mobile terminal download access, which comprises a capacitor and a switch circuit. One end of the capacitor is connected with a pin of a master chip of a mobile terminal, and the other end of the capacitor is connected with the switch circuit. The switch circuit is connected in series between the master chip of the mobile terminal and a download interface. By the invention, the legal download of downloading updated software legally is realized, user experience is promoted, and a hacker is effectively prevented from illegally reading and downloading data of the mobile terminal, so the network locking is better realized.
Owner:ZTE CORP
Security data storage method, computer device and computer readable storage medium
PendingCN114780981AImprove securityReduce manufacturing costInterprogram communicationDigital data protectionSoftware engineeringData store
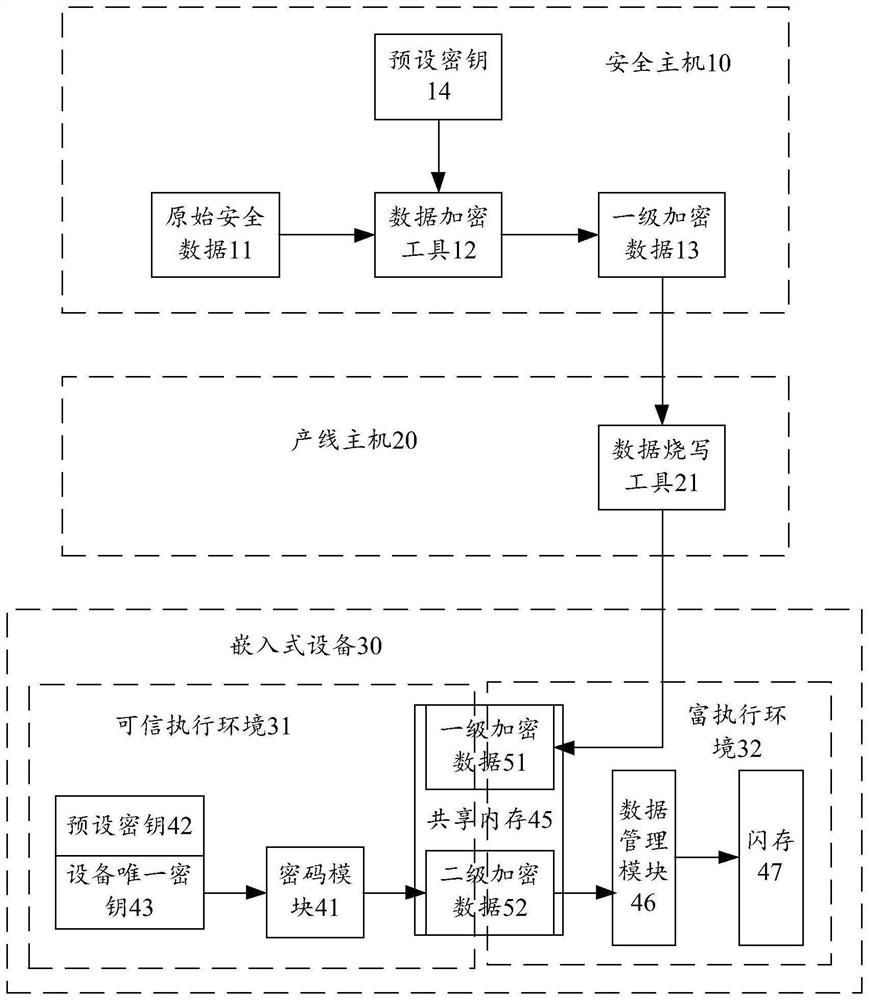
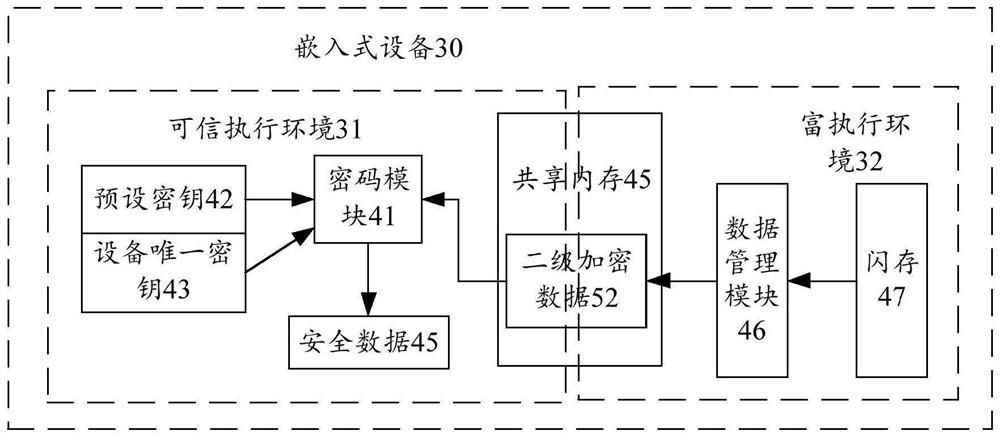
The invention provides a security data storage method, a computer device and a computer readable storage medium, and the method comprises the steps: obtaining first-level encrypted data, transmitting the first-level encrypted data to a trusted execution environment through a shared memory, encrypting the first-level encrypted data in the trusted execution environment by using a unique key of equipment, and storing the encrypted first-level encrypted data in the trusted execution environment; obtaining secondary encrypted data; and transmitting the second-level encrypted data to the rich execution environment through the shared memory, and storing the second-level encrypted data in a preset storage area of the rich execution environment. The invention further provides a computer device and a computer readable storage medium for implementing the method. According to the invention, the embedded device can store the security data with low cost, and the security of security data storage is ensured.
Owner:ALLWINNER TECH CO LTD
Multi-host shared storage system and data integrity protection method
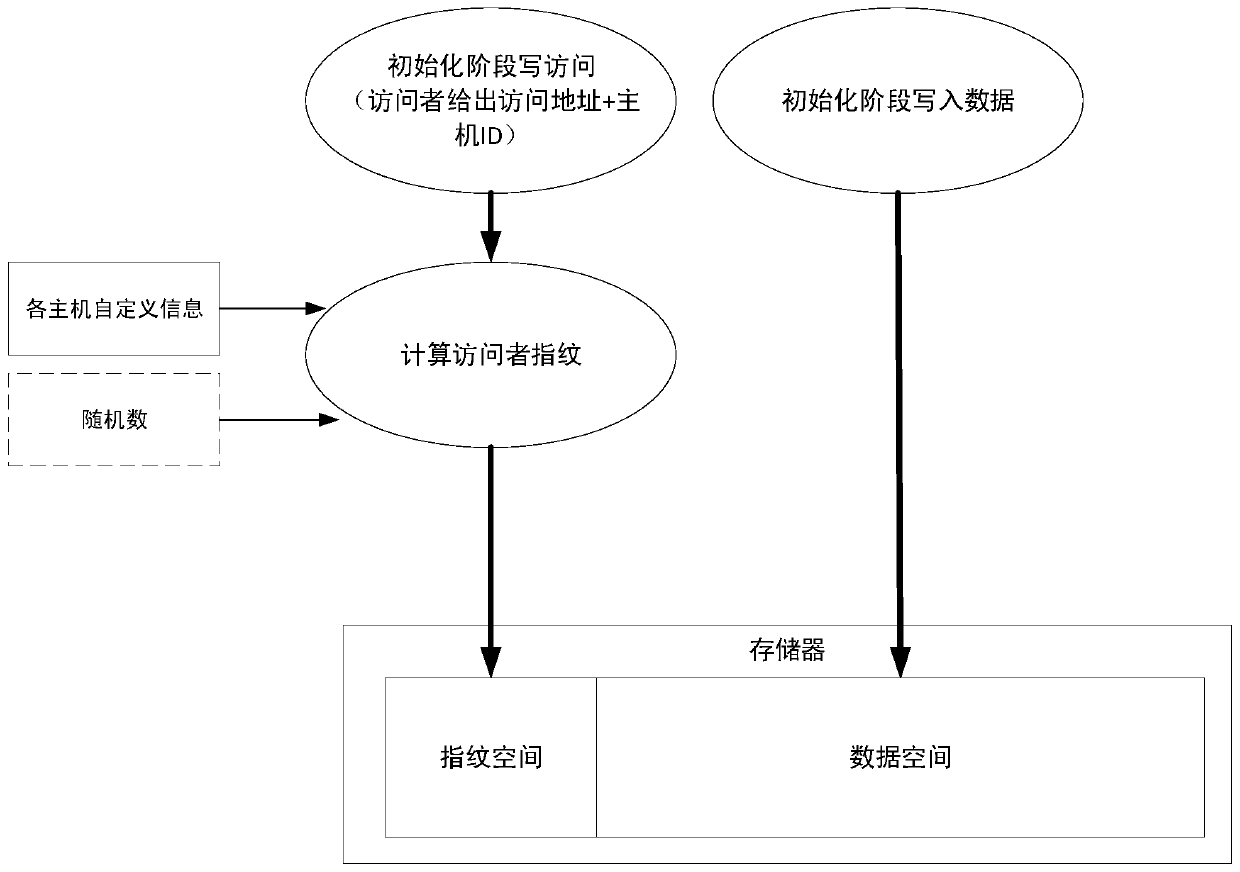
InactiveCN110443070AImprove integrityPrevent illegal readingDigital data protectionInternal/peripheral component protectionData integrityData access
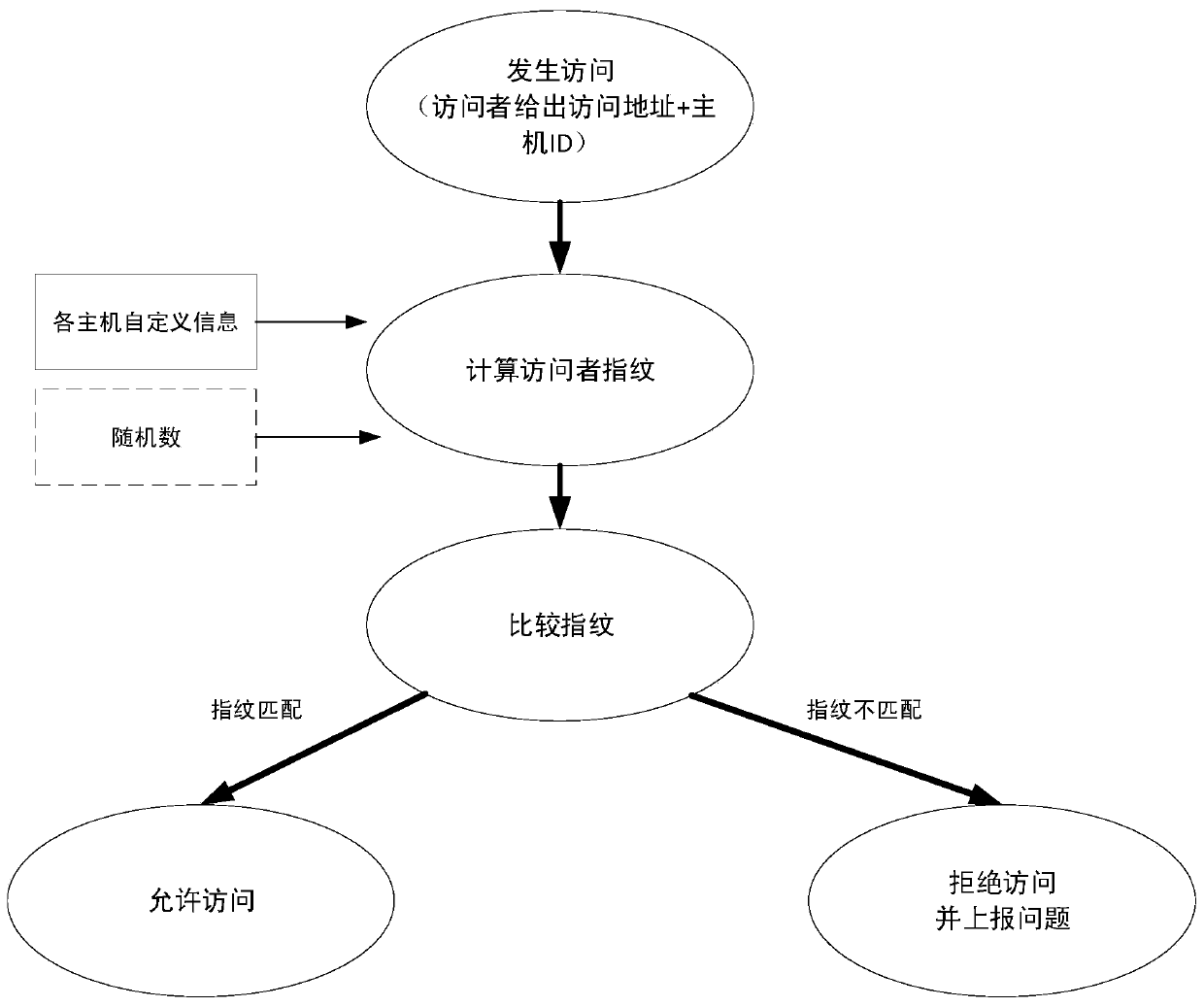
The invention discloses a multi-host shared storage system and a data integrity protection method. The fingerprint for the data is calculated according to the feature information of the data owner system, the address information needing to be stored and the like, and the fingerprint and the data are written into the storage medium together. Therefore, in the data access process, whether the fingerprint information corresponds to the original fingerprint information or not can be judged on the basis of the system identity of the system corresponding to the visitor, the provided address and other information, and therefore the integrity of data is protected between different systems. Particularly, since in the data access process, fingerprint matching needs to be carried out on the system requested to be accessed in advance, illegal access can be prevented and the system sending the abnormal data access request can be reported in time when fingerprint mismatching is judged, traceabilityis achieved, illegal reading and tampering of data can be detected and prevented, integrity of data between different systems is protected, and data safety is greatly enhanced.
Owner:NANJING SEMIDRIVE TECH CO LTD
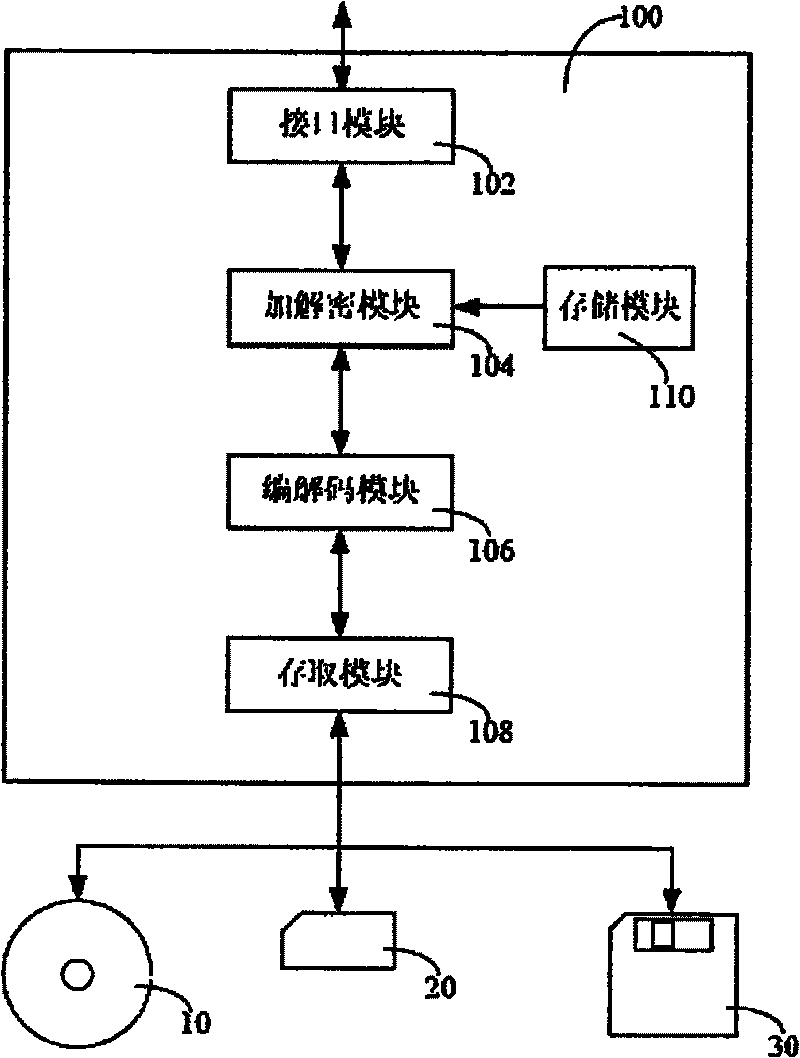
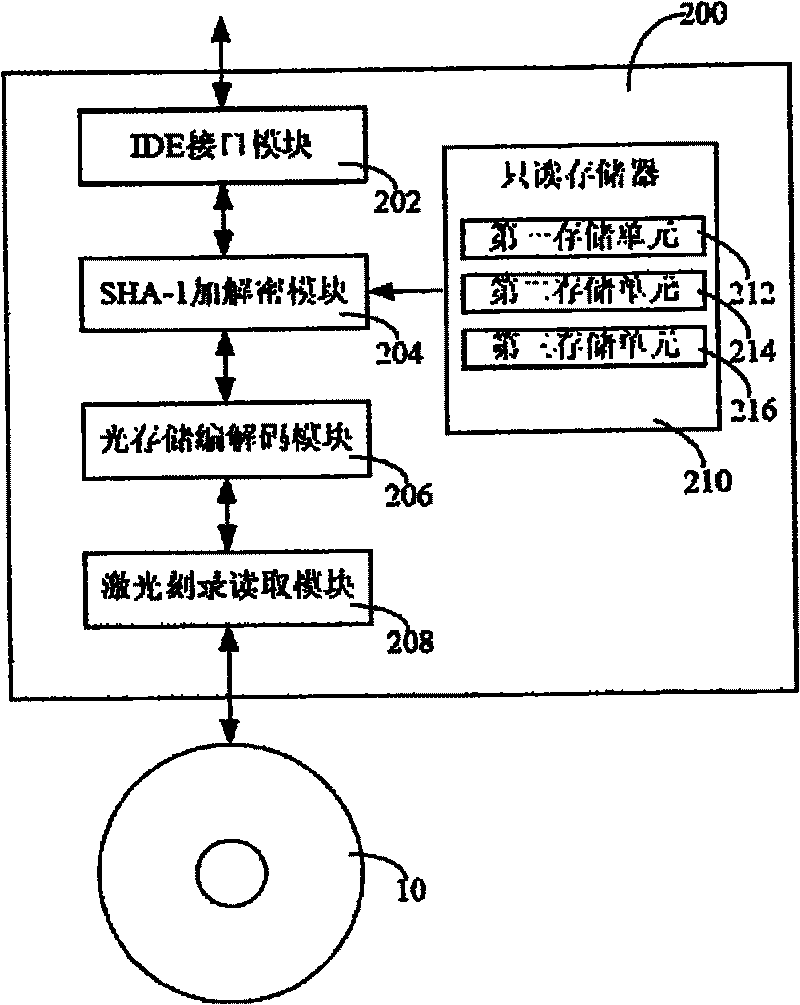
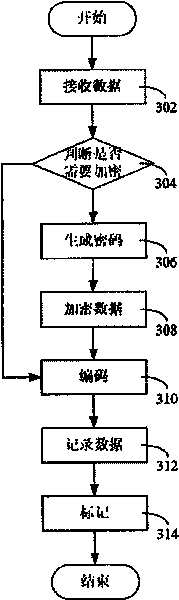
Electronic equipment and its data encryption method and data deciphering method
ActiveCN101286338BPrevent illegal readingOptical discsRecord information storageComputer hardwareData decryption
Owner:HANGZHOU HIKVISION DIGITAL TECH
Tungsten alloy shielding plate and electronic information card provided with tungsten alloy shielding plate
ActiveCN106756379BExcellent electromagnetic wave shieldingThe overall thickness is thinRecord carriers used with machinesRare earthCopper
The invention discloses an electronic information card provided with a tungsten alloy shield plate. The electronic information card comprises an electronic information card substrate and the tungsten alloy shield plate arranged in the electronic information card substrate; the electronic information card substrate comprises a chip and / or a magnetic strip; the tungsten alloy shield plate comprises the following components in mass percentage: 30%-98% of tungsten, 1.23%-40% of nickel, 0.53%-27% of copper, 0.24%-3% of cobalt and 0.1%-1.0% of rare earth. The invention further discloses the tungsten alloy shield plate. According to the tungsten alloy shield plate and the electronic information card provided with the same, the tungsten alloy shield plate with an excellent radiation-proof property is arranged in the electronic information card, so that information in the electronic information card can be prevented from being read or interfered.
Owner:GUANGDONG HUASITE ALLOY PROD CO LTD
Blockchain-based data processing method, device and terminal
ActiveCN110798315BPrevent illegal readingPrevent leakageKey distribution for secure communicationComputer networkCiphertext
The embodiment of the present application discloses a blockchain-based data processing method, device, and terminal, wherein the method includes: receiving an acquisition request for target data sent by a second terminal, acquiring a key pair corresponding to the first terminal, The key pair corresponding to the first terminal includes a second private key and a second public key; use the second public key to encrypt the target data to obtain the ciphertext of the target data; and use the first public key to encrypt the target data The second private key is encrypted to obtain the ciphertext of the second private key; the ciphertext of the second private key and the ciphertext of the target data are stored in the block chain network, so that the second terminal can obtain the ciphertext from the area The ciphertext of the second private key and the ciphertext of the target data are read in the block chain network, and the ciphertext of the target data is decrypted according to the ciphertext of the second private key to obtain the target data. Through the embodiments of the present application, the security of data in the blockchain can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
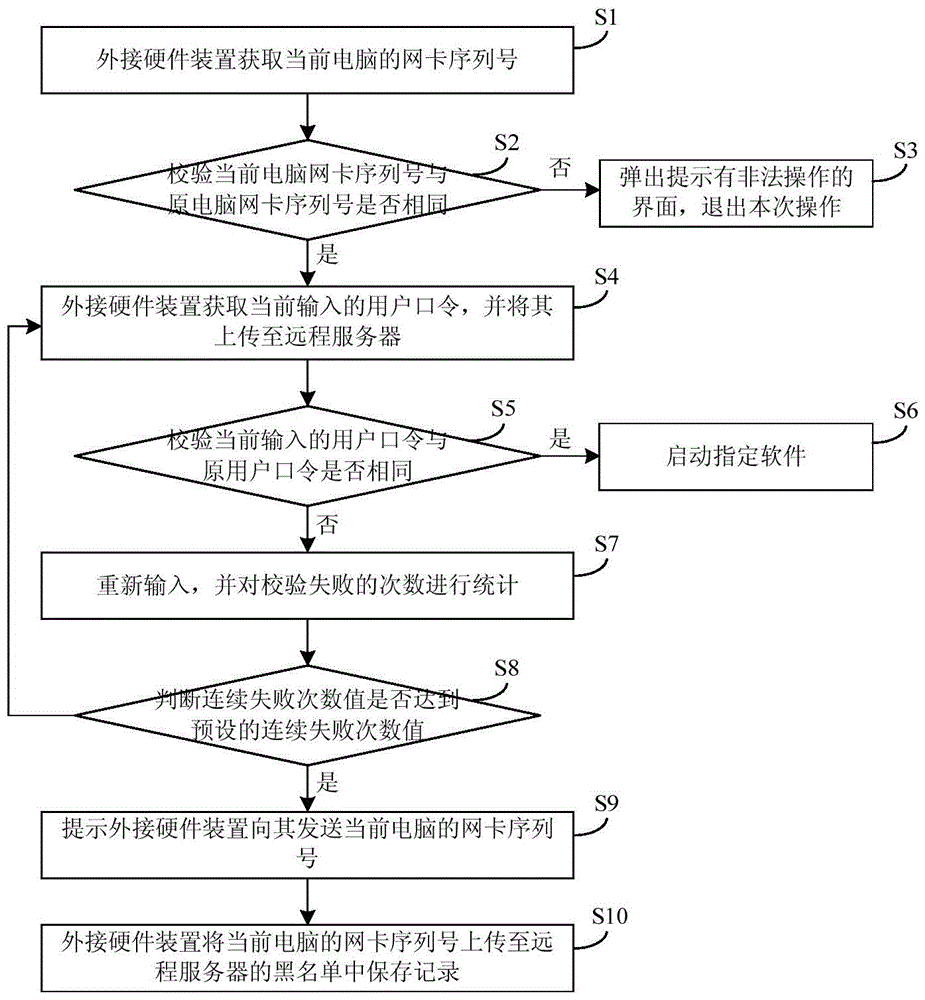
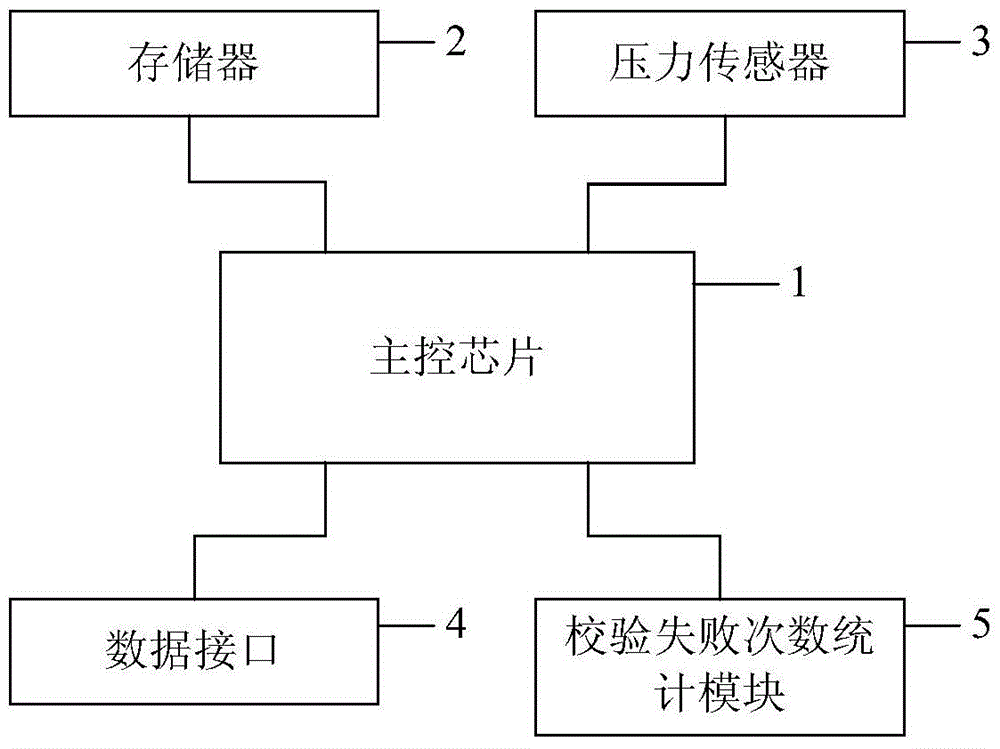
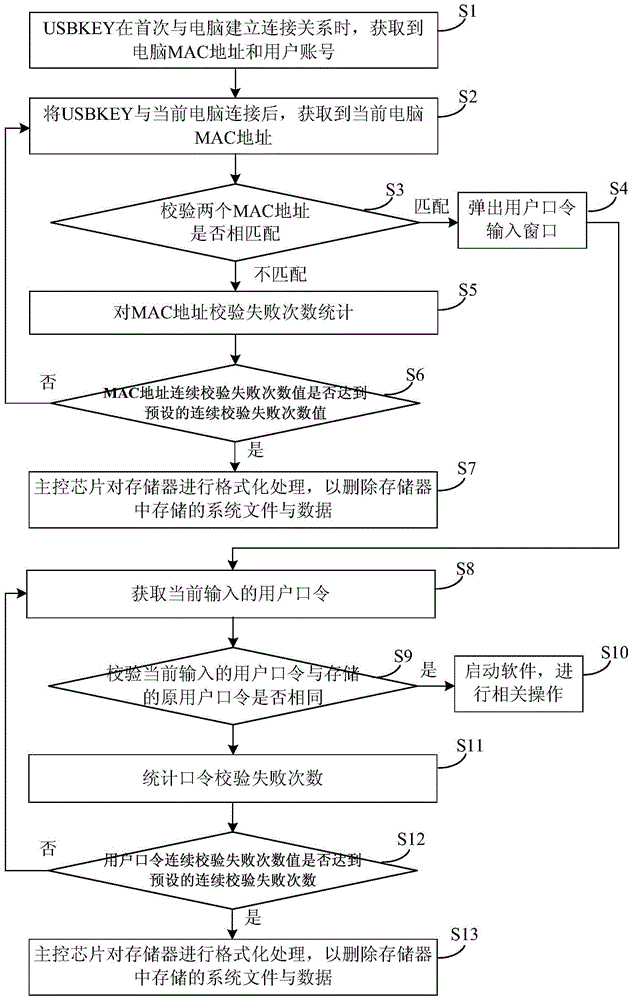
Method for shielding unauthorized users from starting software
InactiveCN103942473BEnsure safetyGuaranteed validityInternal/peripheral component protectionProgram/content distribution protectionPasswordUSB
The invention provides a method for preventing an unauthorized user from starting software. The method includes the following steps that when a network card serial number stored in an external hardware device and a network card serial number of a current computer are the same, a specified software logging interface is popped up, and otherwise, the operation is logged out; when a user password stored in a remote server and a user password input at present are the same, it is shown that a current user is an authorized user, and the specified software can be started, and otherwise, the verification failure frequencies are counted; when the continuous verification failure frequency value is equal to a preset continuous verification failure frequency value, the network card serial number of the current computer is uploaded to a blacklist of the remote server. A system for implementing the method comprises the external hardware device and the remote server. According to the method for preventing the unauthorized user from starting the software and the system for implementing the method, after it is determined that the current computer has no binding relation with a USB KEY, the specified software cannot be started, and therefore the safety and the effectiveness of the software are guaranteed.
Owner:南京颂歌网络科技有限公司
Device for recovering mobile terminal download access
ActiveCN102111917BPrevent illegal readingTo achieve the purpose of locking the networkSubstation equipmentWireless communicationCapacitanceCapacitor
The present invention discloses a device for restoring the download path of a mobile terminal, and the device includes a capacitor(23) and a switch circuit(24), wherein one end of the capacitor(23) is connected with a pin of the main chip(21) of the mobile terminal, and the other end is connected with the switch circuit(24); and the switch circuit(24) is serially connected between the main chip(24) of the mobile terminal and a download interface(22). The application of the present invention can realize the legal download purpose of legally downloading update software, thereby improving user experience, effectively preventing a hacker from illegally reading data from and downloading data to the mobile terminal, and better achieving the purpose of network locking.
Owner:ZTE CORP
A method for anti-cracking of two-dimensional barcode
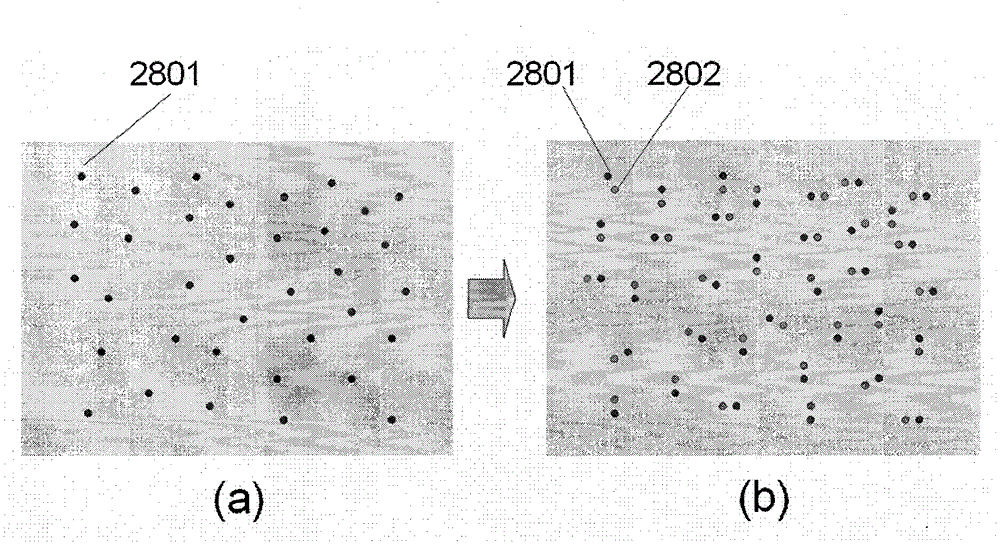
ActiveCN102890768BImprove securityAvoid crackingCo-operative working arrangementsSensing by electromagnetic radiationInformation processingBarcode
The invention relates to a novel anti-cracking method of a two-dimensional barcode in the field of information processing. Cracking the code content and illegally reading the code can improve the security of the code and the effectiveness of anti-counterfeiting. It is also suitable for low-precision printers. While printing the printed image, a large amount of information is embedded through various patterns and texts, so that The printed image is beautiful, and at the same time, the embedded information will not be copied, so as to realize the anti-counterfeiting effect of goods and tax stamps, thereby completely solving the problems of bill forgery, tampering, and commodity counterfeiting spreading in society, and promoting the harmonious development of society.
Owner:天津市阿波罗信息技术有限公司
Card insertion ejection unit, card handling unit
InactiveCN104487983BPrevent illegal readingImprove maintainabilityAcutation objectsConveying record carriersComputer hardwareMagnetic field
A card processing device (100) in which a card transfer unit (5) transfers a magnetic card (20) and a magnetic reading unit (4) reads magnetic information recorded in the magnetic card (20) in a body part (1) is provided with a card insertion and ejection opening unit (10). The card insertion and ejection opening unit (10) includes an opening (10b) into which and from which the magnetic card (20) is inserted and ejected, and a magnetic field generation unit (11) for generating an interference magnetic field, and is detachable from a card slot part (1a) of the body part (1) of the card processing device (100).
Owner:HITACHI OMRON TERMINAL SOLUTIONS CORP
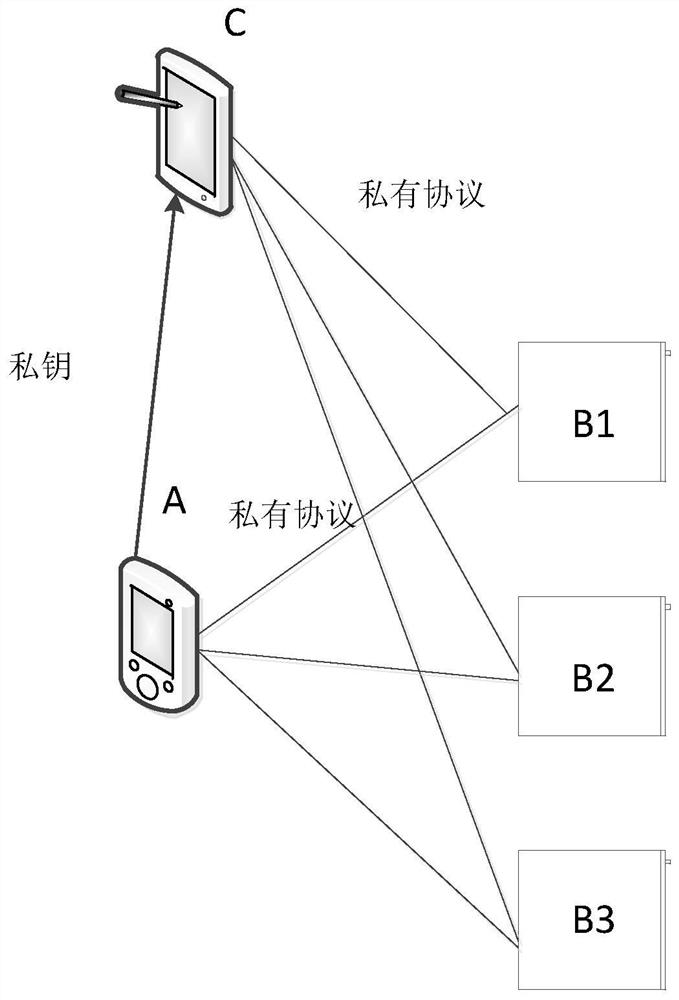
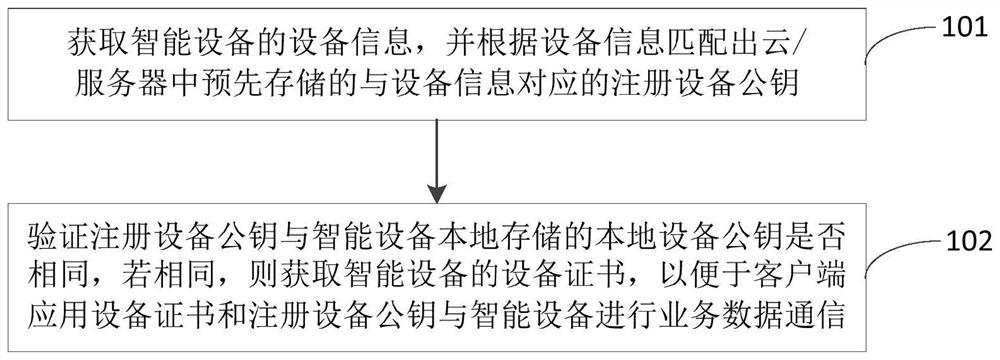
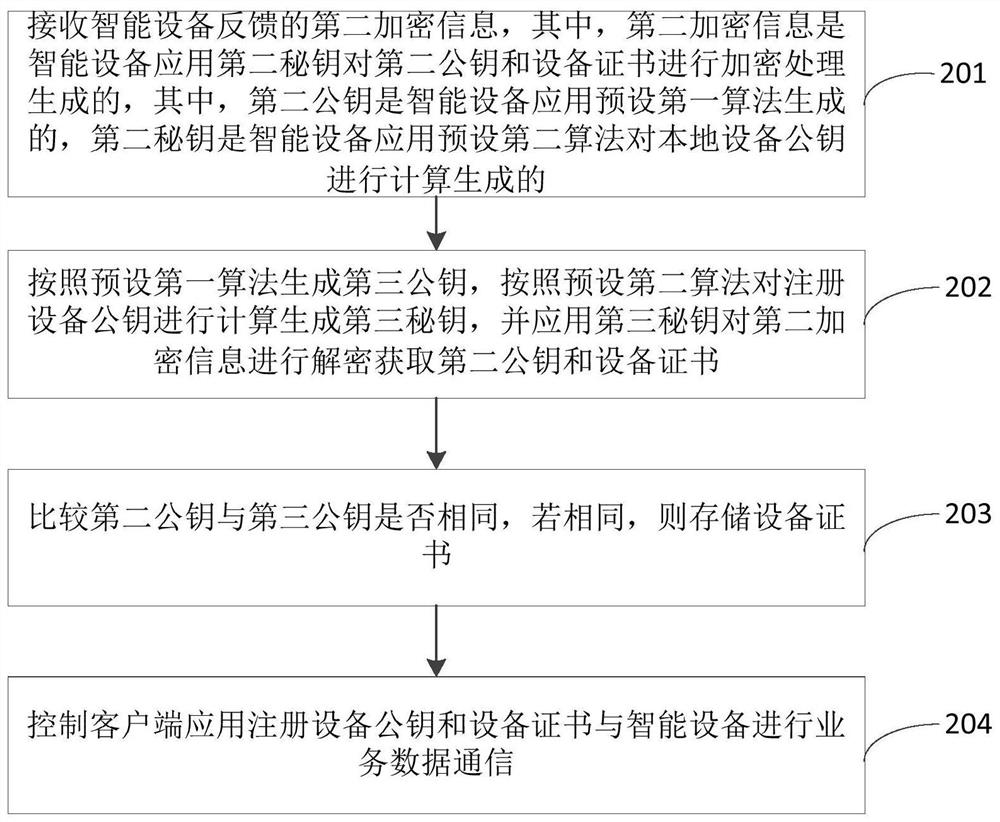
Data communication method, device and equipment of intelligent equipment
ActiveCN108366063BEnsure communication securityPrevent illegal readingKey distribution for secure communicationEngineeringBusiness data
The invention discloses a data communication method, device and equipment of an intelligent device, wherein the method includes: obtaining equipment information of an intelligent equipment, and matching the registered equipment corresponding to the equipment information pre-stored in the cloud / server according to the equipment information Public key; verify whether the registered device public key is the same as the local device public key stored locally on the smart device, and if they are the same, obtain the device certificate of the smart device so that the client can use the device certificate and registered device public key to exchange business data with the smart device communication. As a result, the reliability of security authentication when the smart device performs data communication is improved, and no cluster reaction is caused, the randomness is strong, and the security is higher.
Owner:GUANGDONG MIDEA KITCHEN APPLIANCES MFG CO LTD +1
Disk array and computer or storage medium authentication method and system
InactiveCN103870768APrevent unauthorized accessAvoid getting out of controlInternal/peripheral component protectionPasswordTrusted Computing
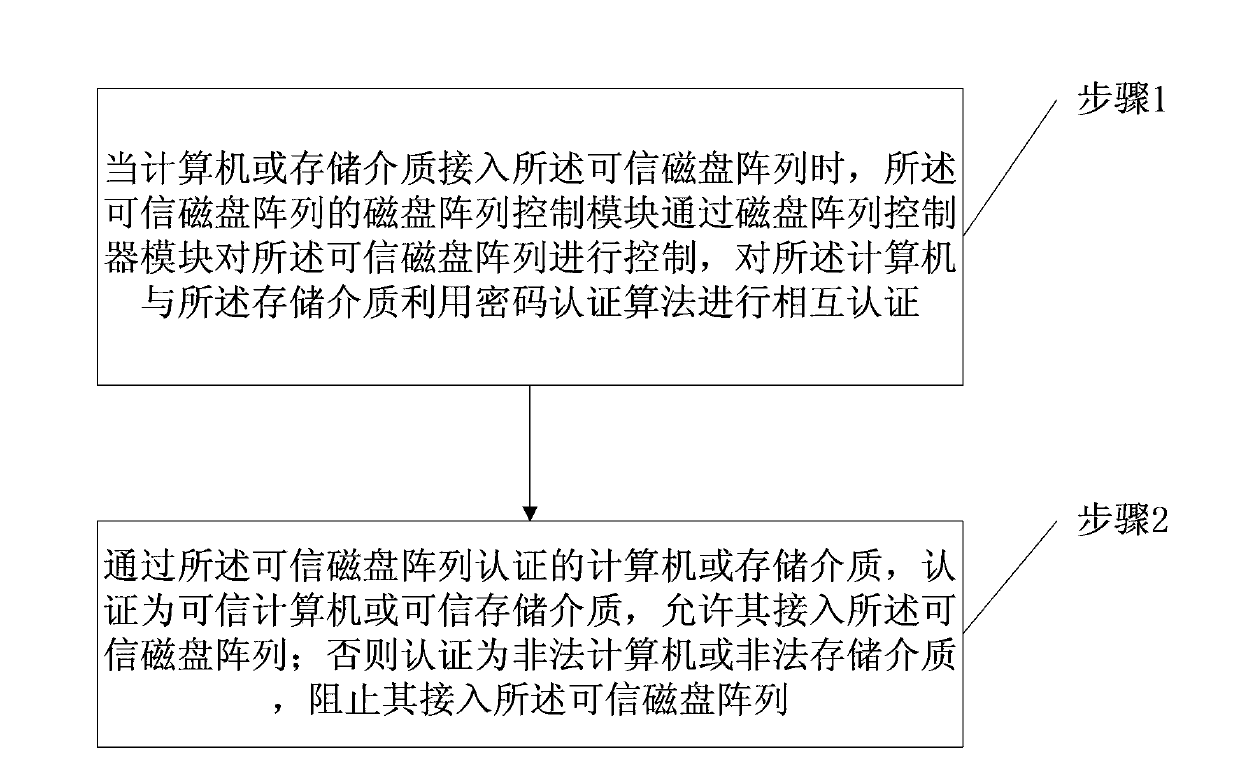
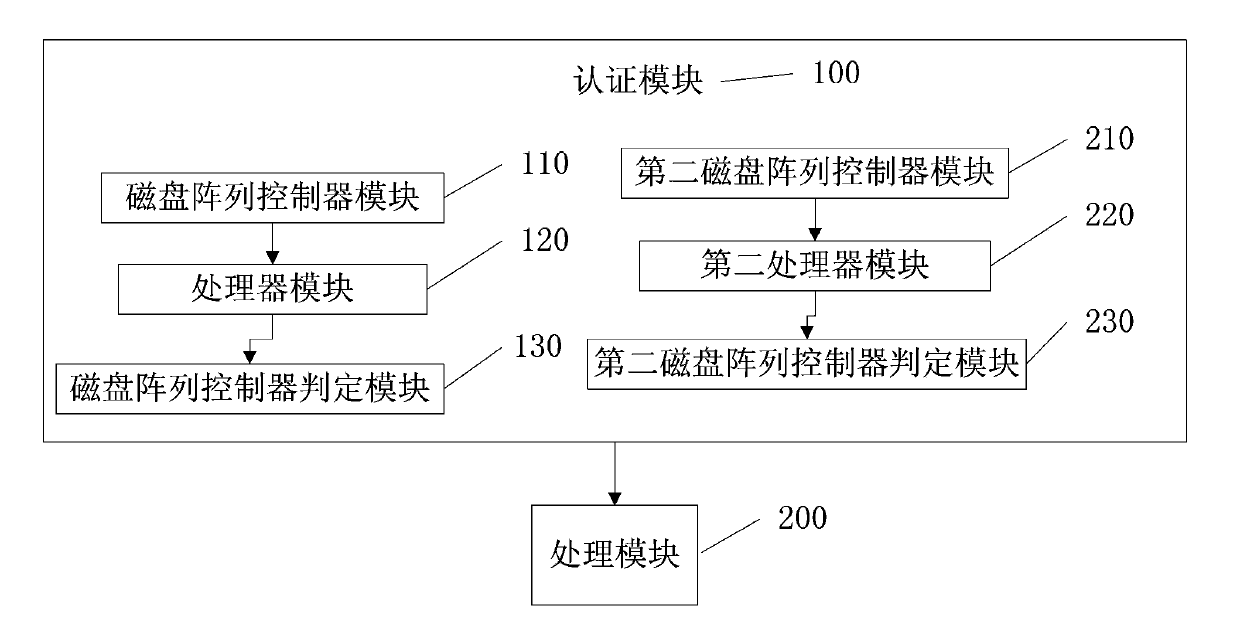
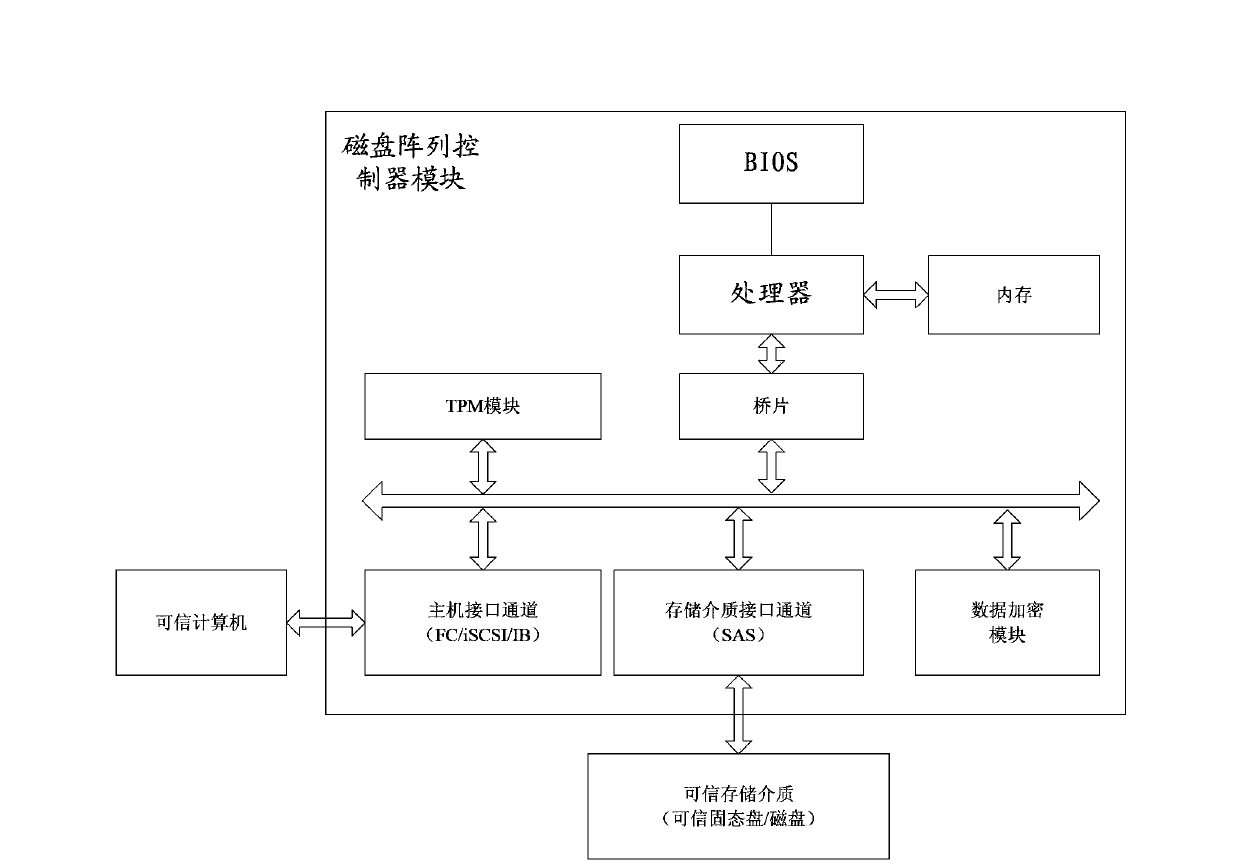
The invention provides a disk array and computer or storage medium authentication method and system. The method includes the following steps that 1 a disc array control module of a credible disk array controls the credible disk array through a disk array controller module and conducts mutual authentication on a computer and a storage medium by utilizing a password authentication algorithm; 2 the computer or the storage medium passing the credible disk array authentication is authenticated to be a credible computer or a credible storage medium and is permitted to enter the credible disk array; otherwise, the computer or the storage medium is authenticated to be an illegal computer or an illegal storage medium and is prevented from being connected into the credible disk array. By means of the method and system, credible authentication between the disk array and the credible computer and between the disk array and the internal storage medium is achieved, and data on the disk array and the storage medium cannot be accessed illegally.
Owner:BEIJING INST OF COMP TECH & APPL +1
Data authentication system and data authentication method
ActiveCN103501230BEnsure safetyPrevent illegal readingUser identity/authority verificationData Authentication AlgorithmAuthentication server
Owner:PKU HEALTHCARE IT
Method and device for shielding unauthorized users from starting software
ActiveCN103942472BEnsure safetyGuaranteed validityInternal/peripheral component protectionProgram/content distribution protectionPasswordData interface
Owner:贵州灵劲科技有限公司
A secure communication method and system for a mobile terminal
ActiveCN112054905BGuaranteed Interaction SecurityEnsure safetyKey distribution for secure communicationUser identity/authority verificationSecure communicationTelecommunications
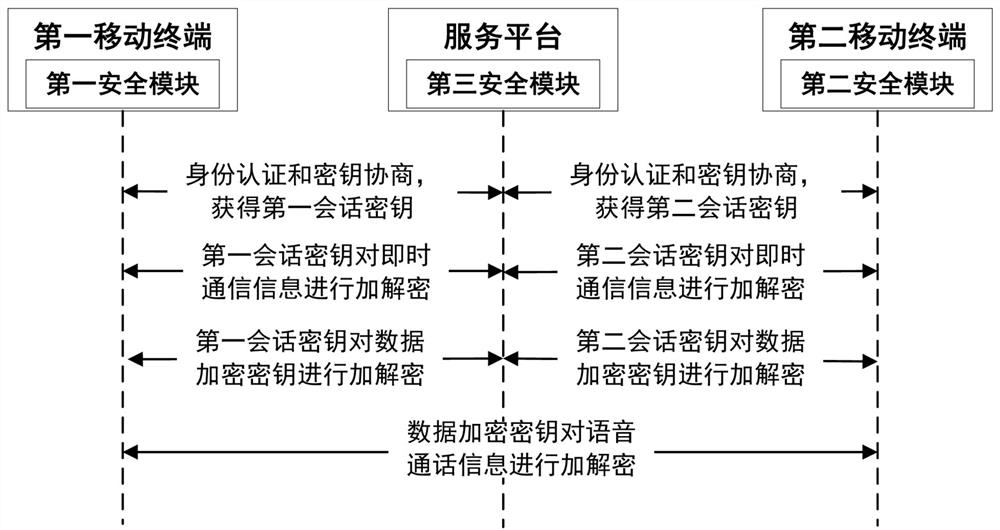
The present invention proposes a mobile terminal secure communication method and system, the method includes a key negotiation process, a secure instant communication process and a secure call process; the key negotiation process: the first mobile terminal and the service platform perform identity authentication and key The first session key is obtained after negotiation; the second mobile terminal obtains the second session key after identity authentication and key negotiation with the service platform; the secure instant messaging process: the first mobile terminal communicates with the service platform through the service platform The second mobile terminal uses the first session key and the second session key to perform encryption and decryption processing of instant messaging information; the secure call process: the first mobile terminal uses the service platform to The first session key, the second session key and the second mobile terminal distribute the data encryption key; the first mobile terminal and the second mobile terminal use the data encryption key to Encryption and decryption of voice call information.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Method, device and equipment for storing driving data
ActiveCN109215170BImprove securityPrevent illegal readingRegistering/indicating working of vehiclesMultiple keys/algorithms usageData storeEmbedded system
Owner:APOLLO INTELLIGENT DRIVING (BEIJING) TECHNOLOGY CO LTD
Method and system for protecting permission of volatile memory bank
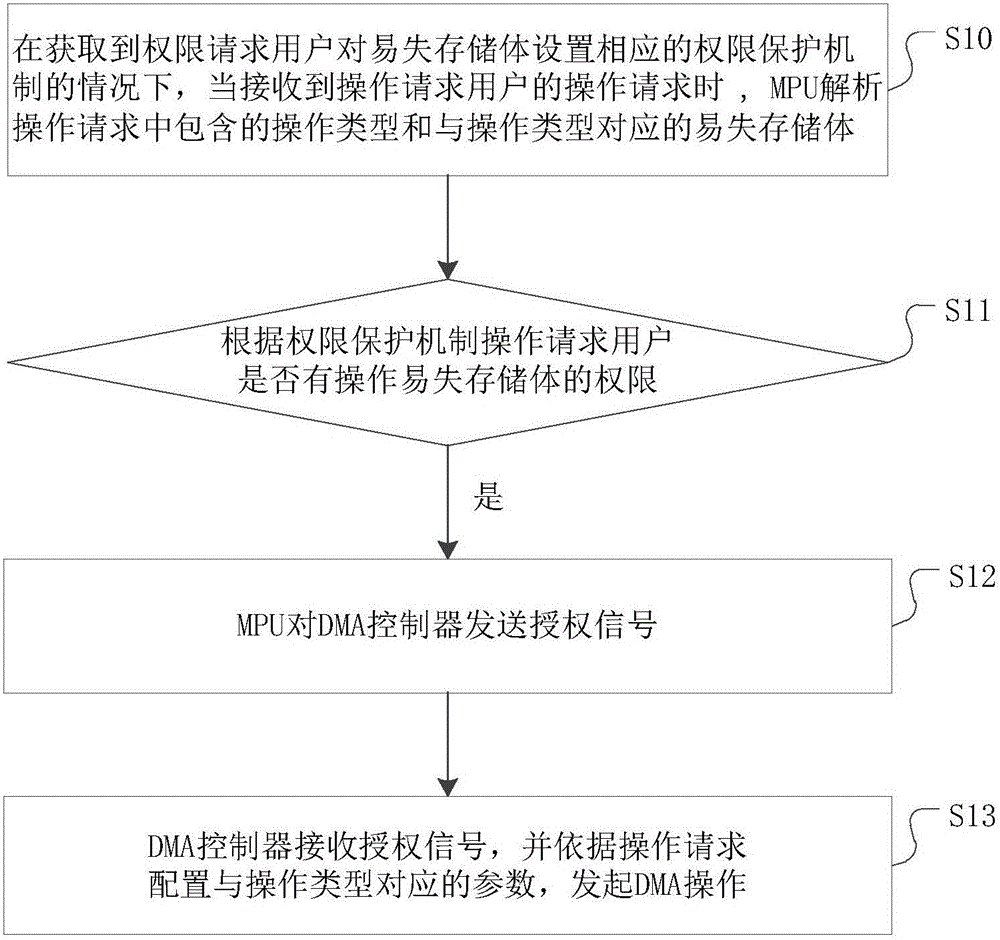
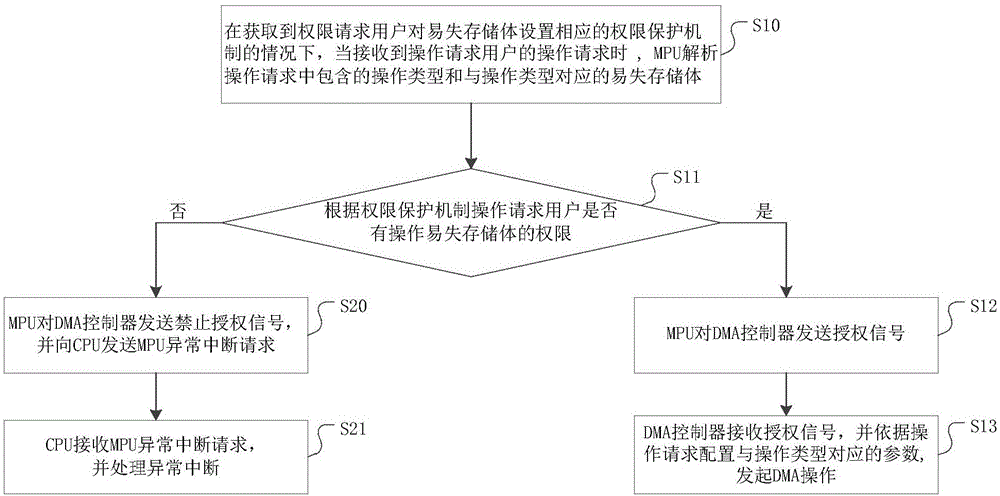
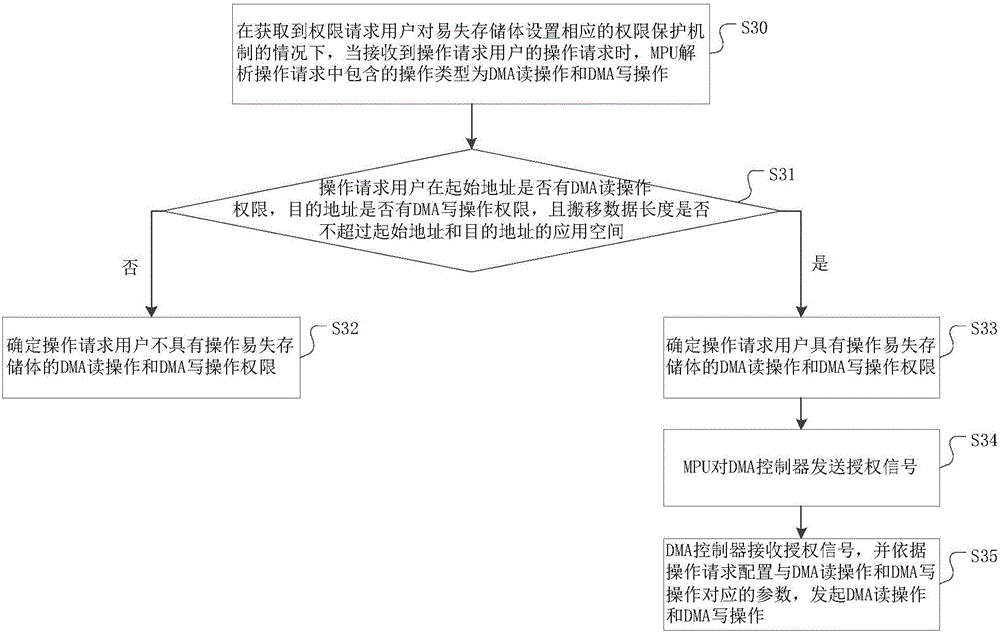
InactiveCN106339643AImprove the protection mechanismPrevent illegal readingInternal/peripheral component protectionAuthorizationProtection mechanism
The invention discloses a method for protecting permission of a volatile memory bank. The method comprises the following steps: when receiving an operation request of an operation request user, an MPU analyzes the operation type in the operation request and the volatile memory bank corresponding to the operation type, and judges whether the operation request user has a permission to operate the volatile memory bank according to a permission protection mechanism; if so, the MPU transmits an authorization signal to a DMA controller; the DMA controller receives the authorization signal, and configures parameters corresponding to the operation type according to the operation request. Therefore, the DMA controller executes the corresponding operation only after the authorization of the MPU is successful, so that the data in the volatile memory bank are prevented from being illegally changed or read by other users, and the security is enhanced. As the protection mechanism for the volatile memory bank is added, the user can change the operation permission of the DMA on the volatile memory bank, and the operation flexibility is improved. In addition, the invention further discloses a system for protecting permission of the volatile memory bank, and the effects are as mentioned above.
Owner:苏州国芯科技股份有限公司
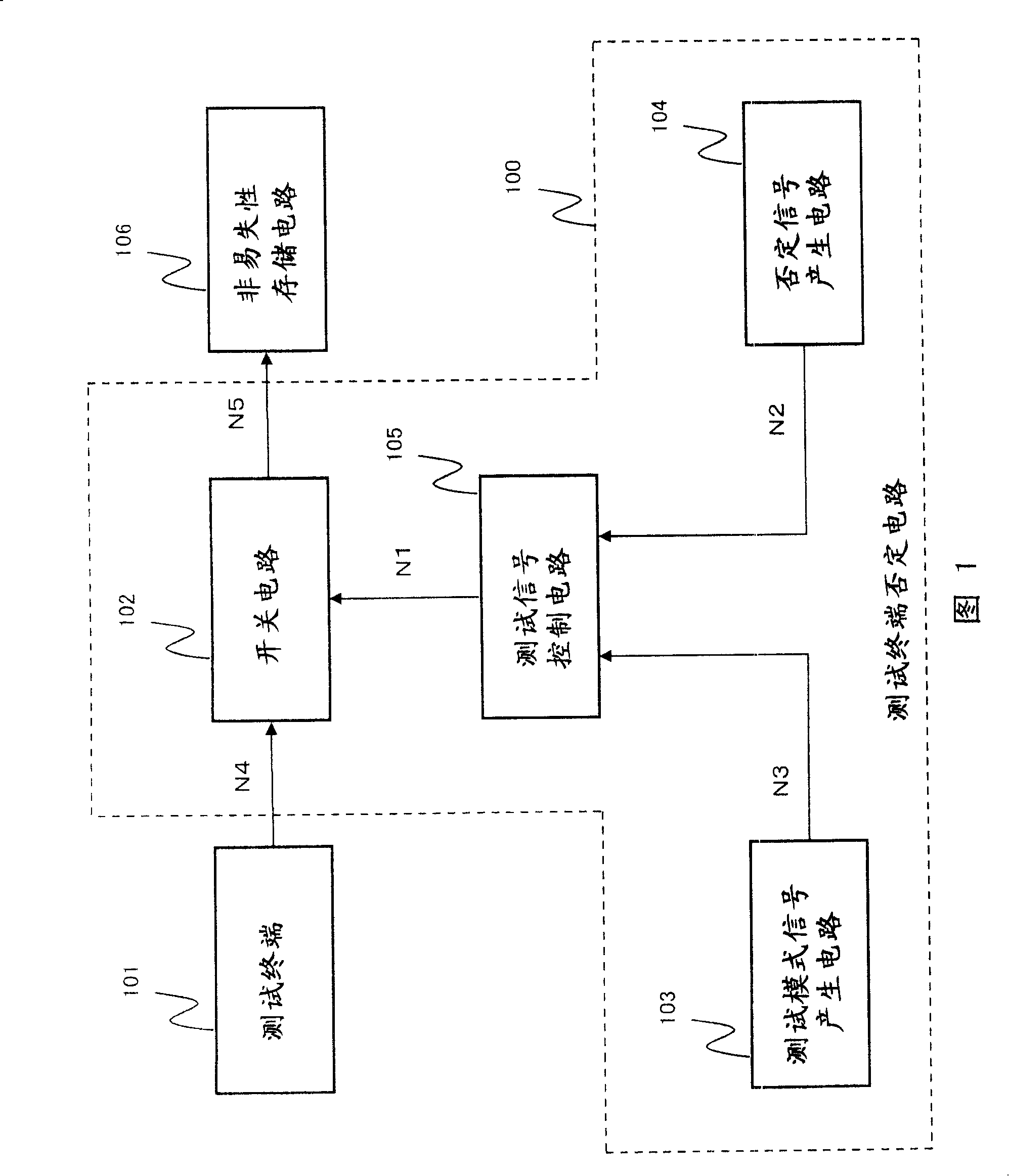
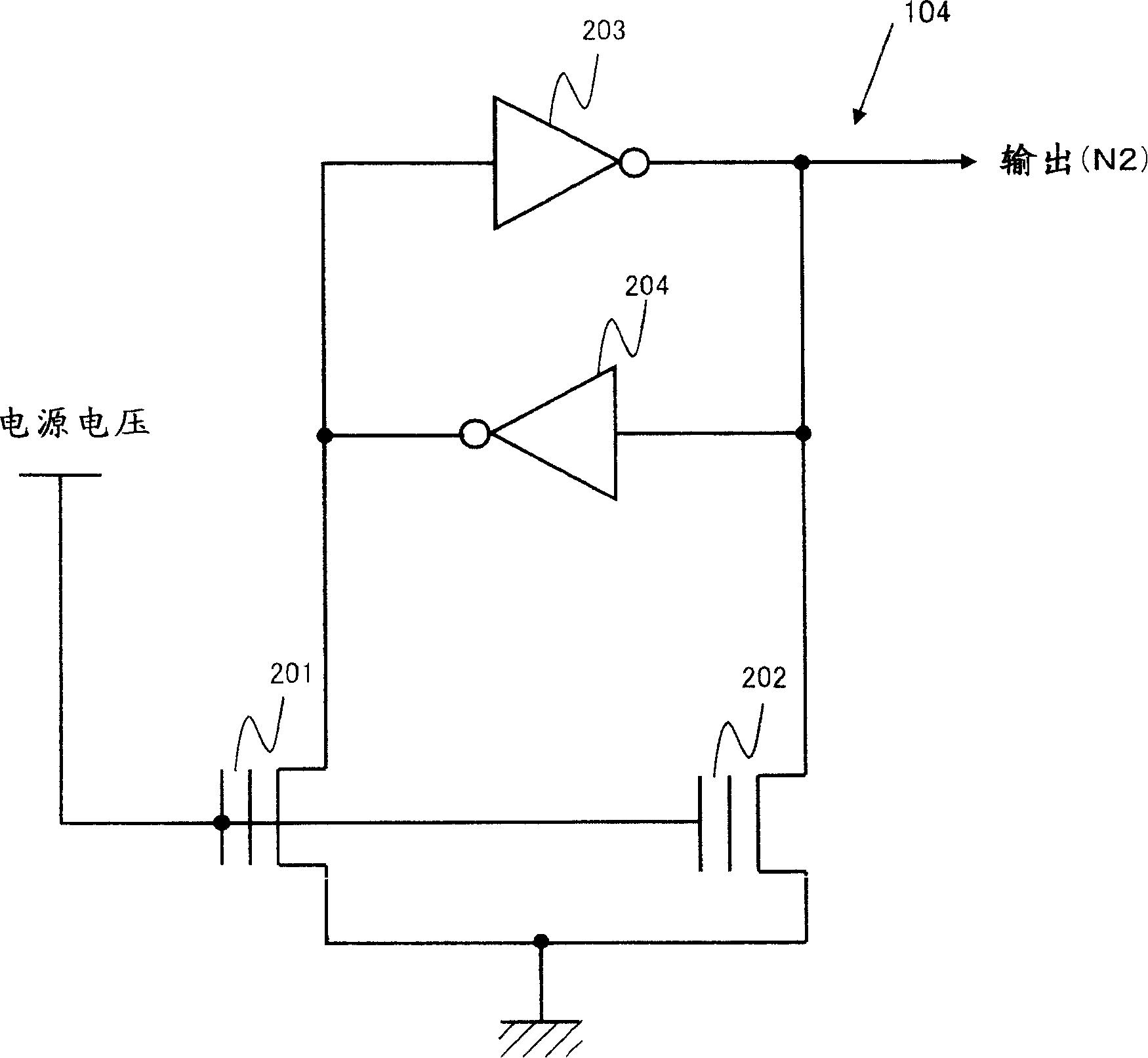
Test terminal negation circuit
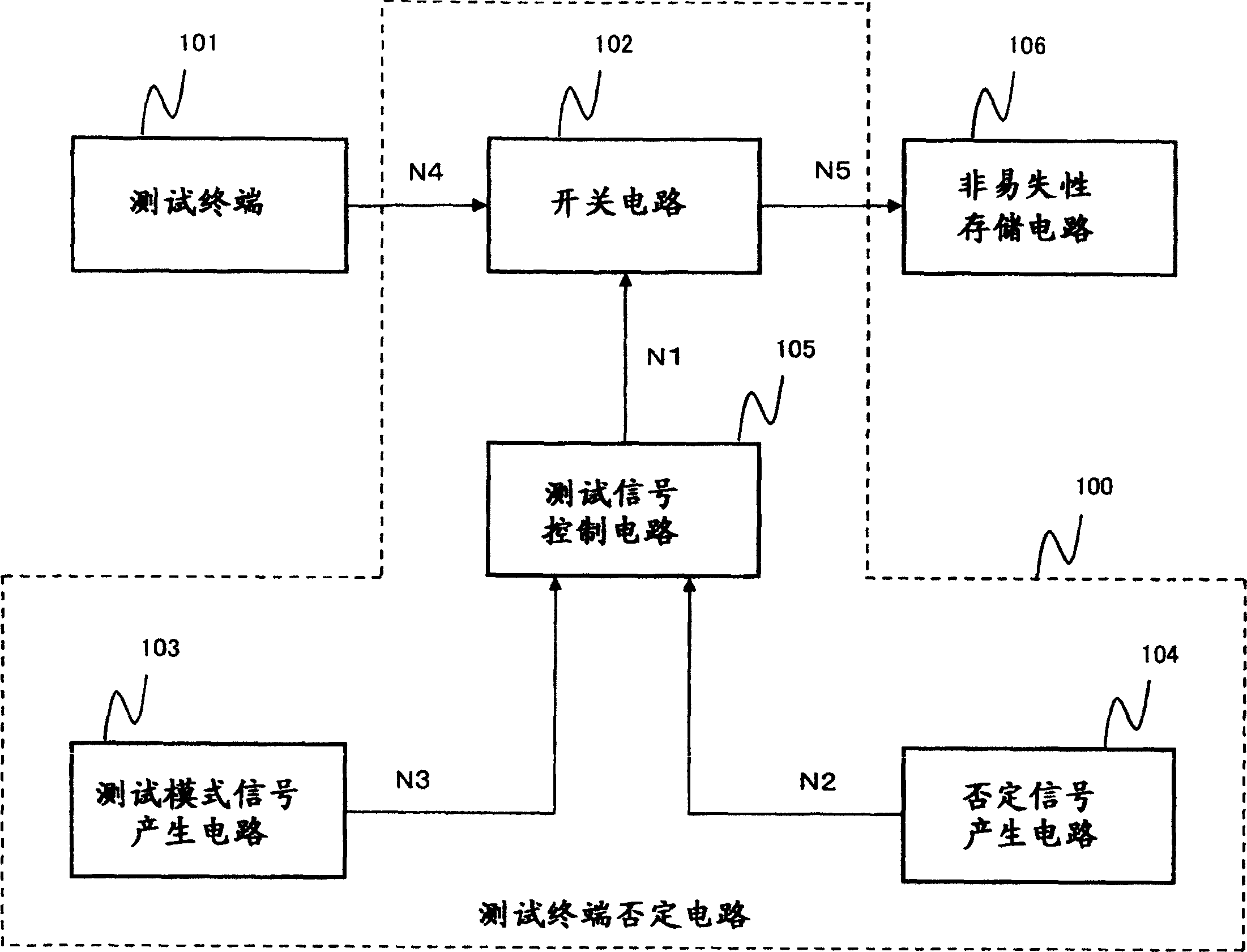
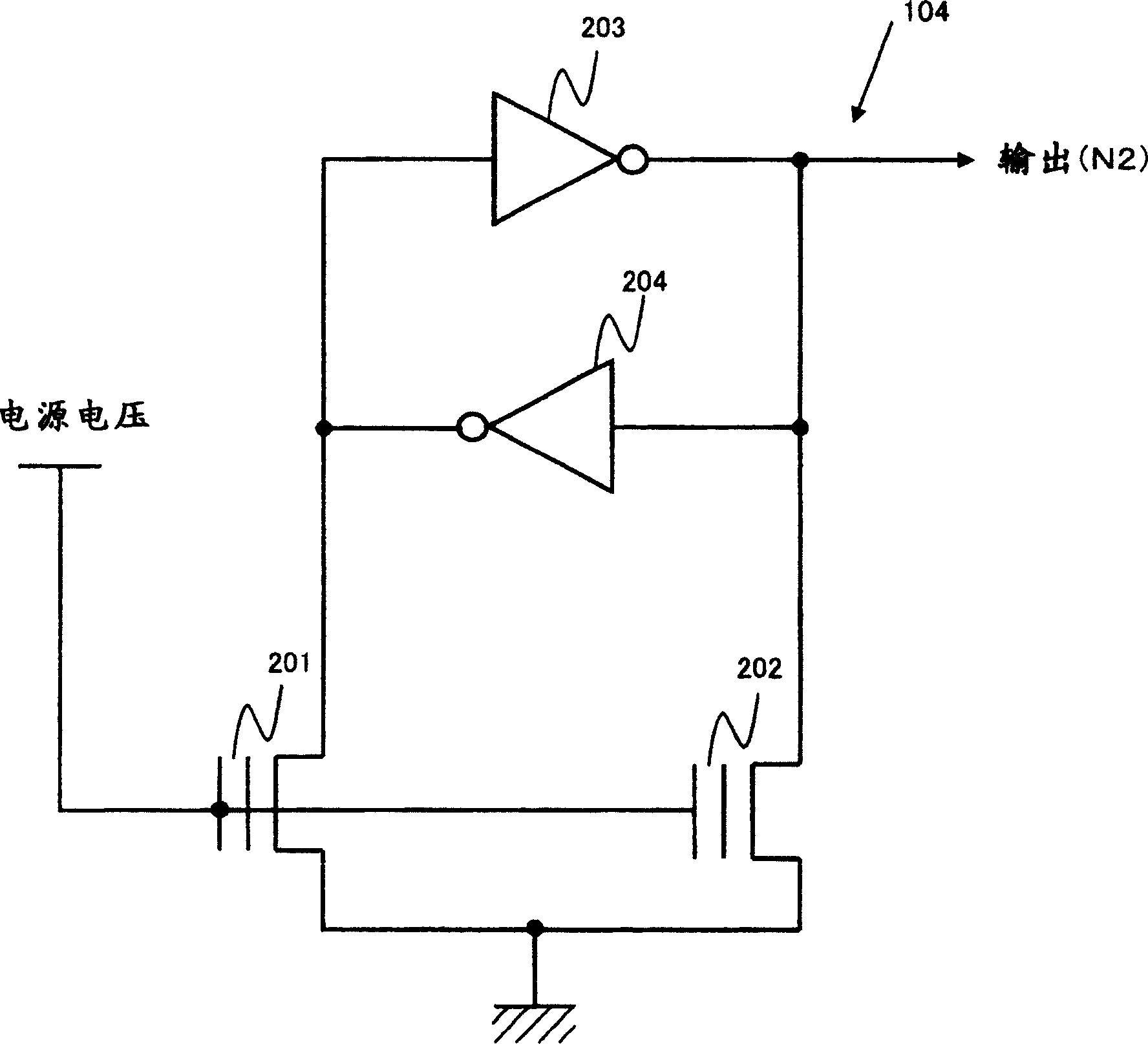
ActiveCN1677119APrevent illegal readingDigital circuit testingSemiconductor/solid-state device testing/measurementTest objectElectricity
A test terminal negation circuit (100) comprises a switch circuit (102) receiving a test signal from a test terminal (101) and outputs it in an asserted state as it is or in a predetermined negated state to a test object circuit (106), a test signal control circuit (105) which controls an output signal of the switch circuit (102) to be asserted or negated, a test mode signal generation circuit (103) which generates a test mode signal which asserts the output signal of the switch circuit (102), and a negating signal generation circuit (104) which can output a negating signal for forcing the output signal of the switch circuit (102) into negated state and comprises an electrically rewritable nonvolatile memory element. When the test signal control circuit (105) receives the negating signal, it does not assert the output signal of the switch circuit (102) even it receives the test mode signal.
Owner:知识产权I公司
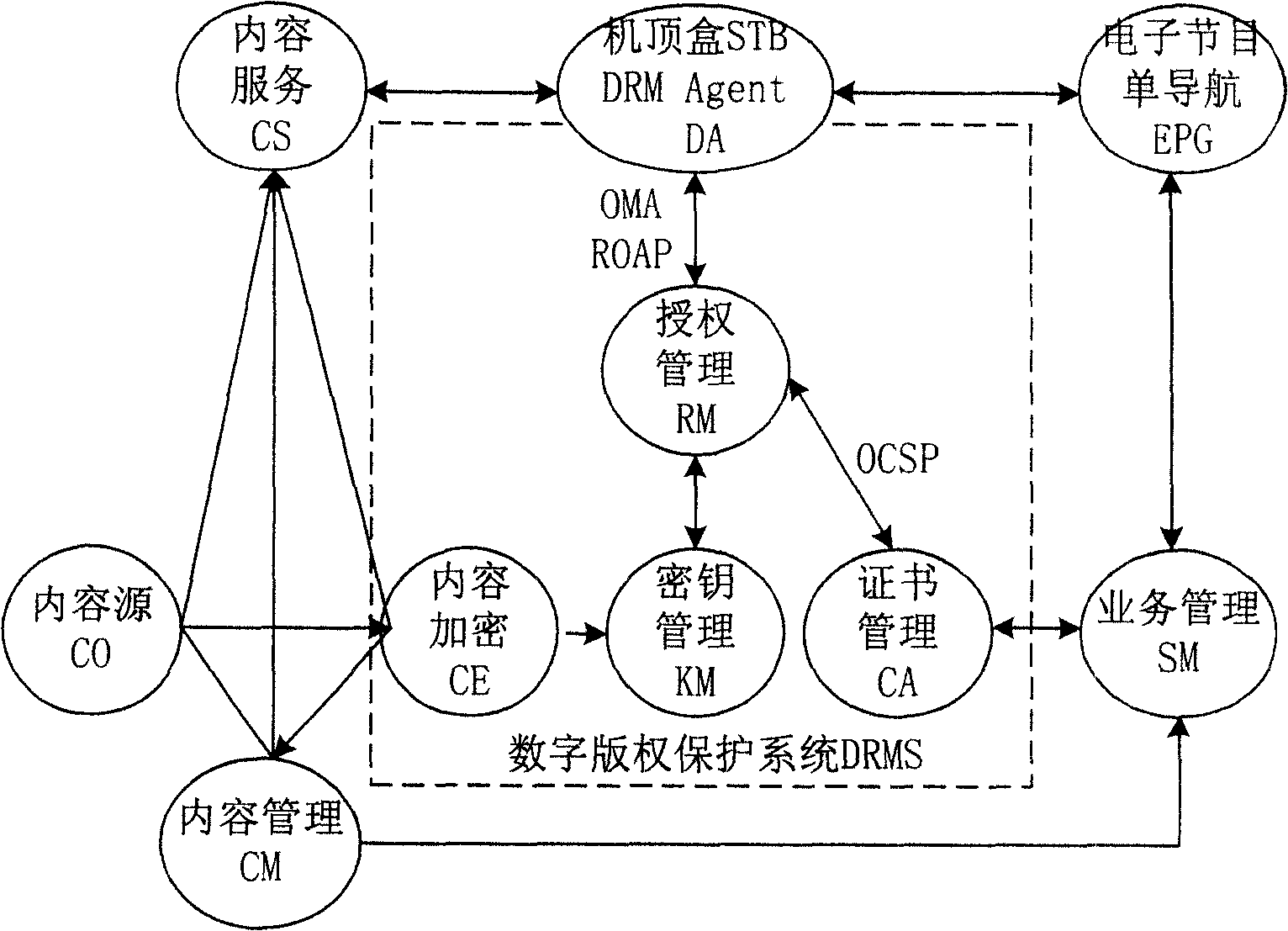
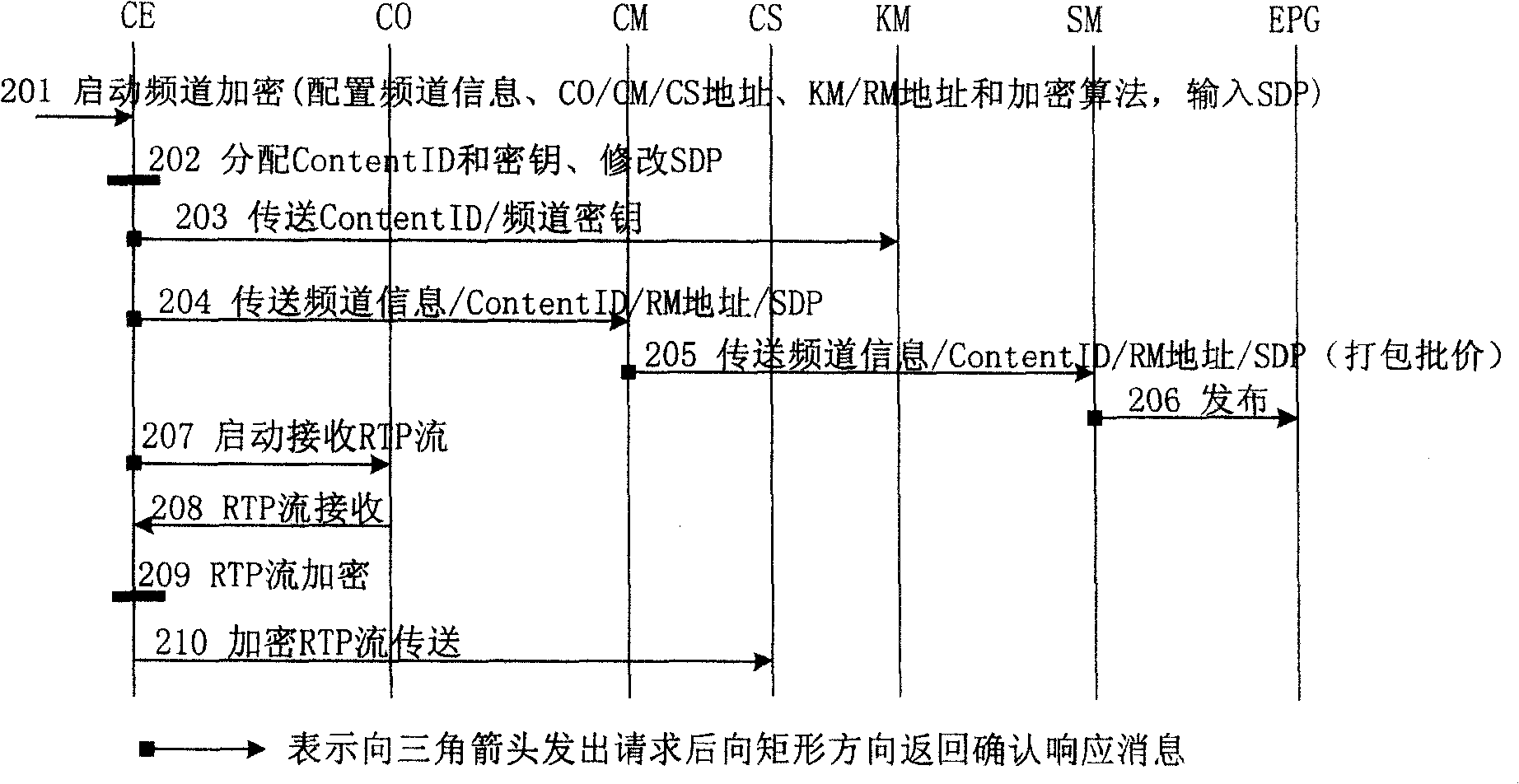
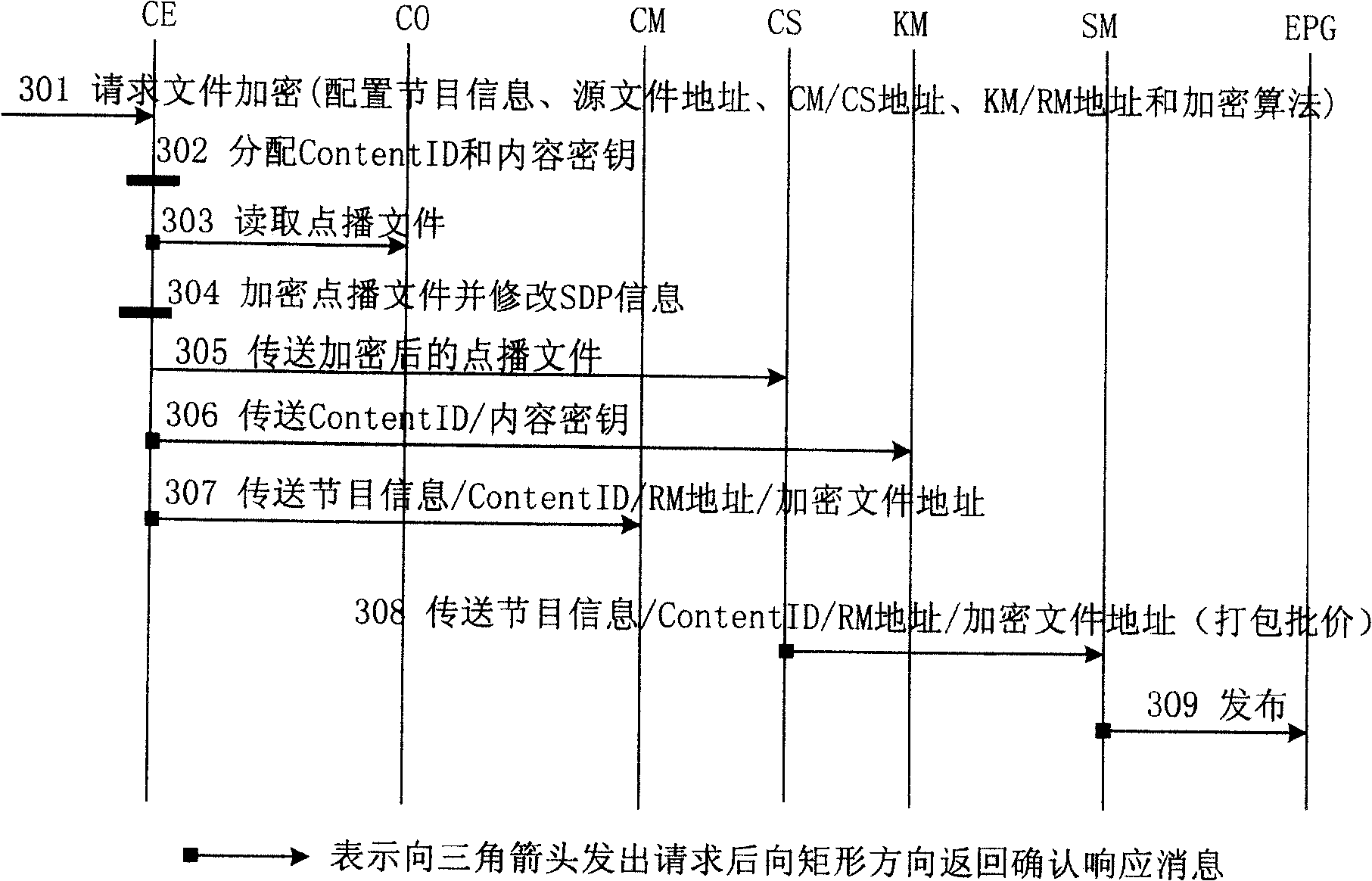
IPTV system, enciphered digital program issuing and watching method
ActiveCN100459697CImplement encrypted transmissionGuaranteed not to be illegally copied and disseminatedAnalogue secracy/subscription systemsTwo-way working systemsManagement unitSecure transmission
An IPTV system comprises content source CO, content service unit CS, content management unit CM, service management unit SM, single-way guide unit EPG of electronic program, top box STB, content enciphering unit CE, cipher key management unit KM and authorization management unit RM for providing enciphered program. The method of issuing and viewing enciphered program is also disclosed.
Owner:HUAWEI TECH CO LTD
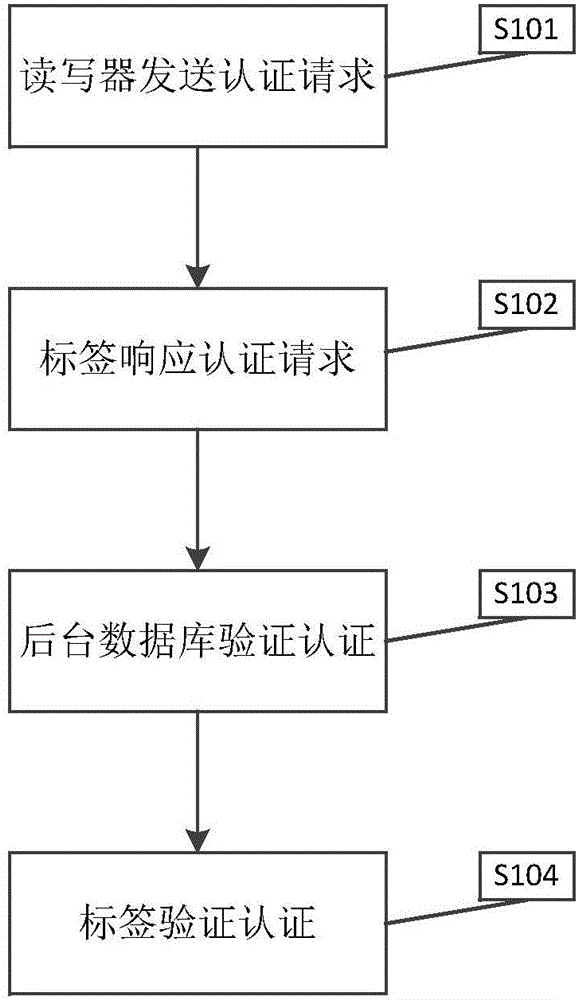
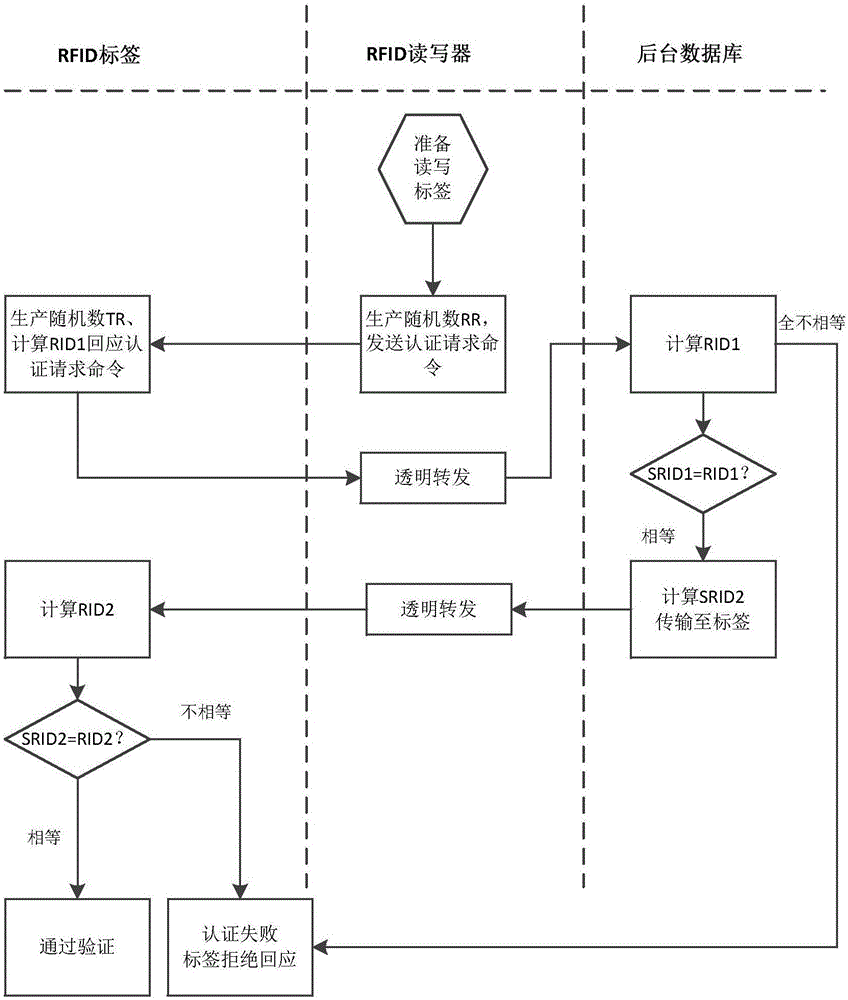
Dynamic ID based RFID verification method and system
InactiveCN106548102AGuaranteed Privacy ContentPrevent eavesdroppingMemory record carrier reading problemsTransmissionCard readerEncryption
The invention comprises a dynamic ID based RFID verification method. The method is characterized by comprising the realization steps that S1) a reader sends an authentication request, and the authentication request is completed; S2) a label makes response feedback in response to the authentication request; S3) a background database is used to verify authentication preliminarily; and S4) the label is used for verify authentication secondarily. The method and system have the advantages that use of formula encryption can ensure that private content is safe and eavesdropping and position tracking are prevented; use of double-randomized-number verification can prevent playback attack effectively; neither an invalid card reader nor an invalid label can pass validity authentication, invalid reading, counterfeiting attack and disguising can be prevented effectively; and due to a formula is simple, neither too high computing capability nor too much storage space is needed, and the manufacture cost is not increased.
Owner:珠海南方集成电路设计服务中心
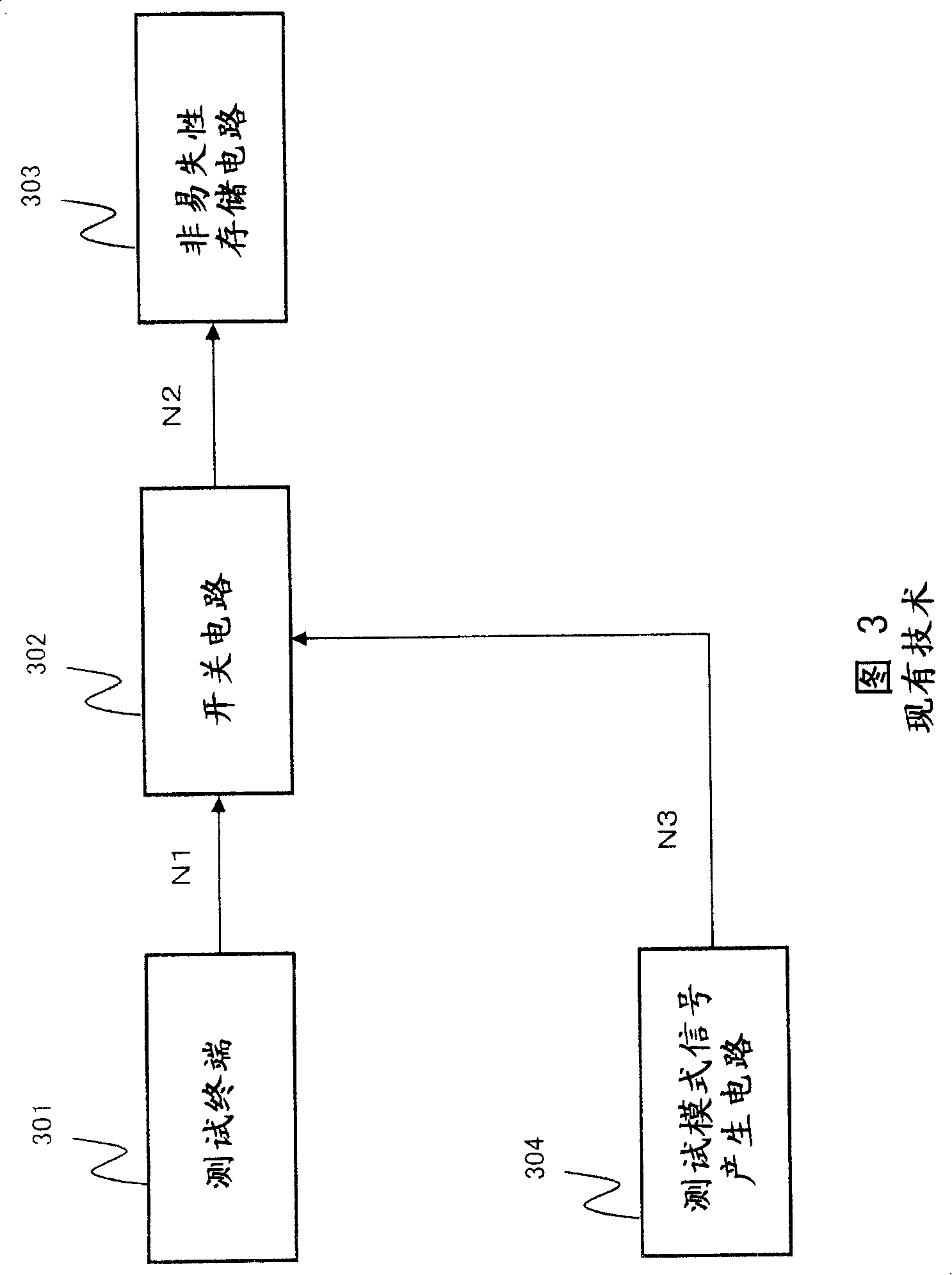
Test terminal negation circuit
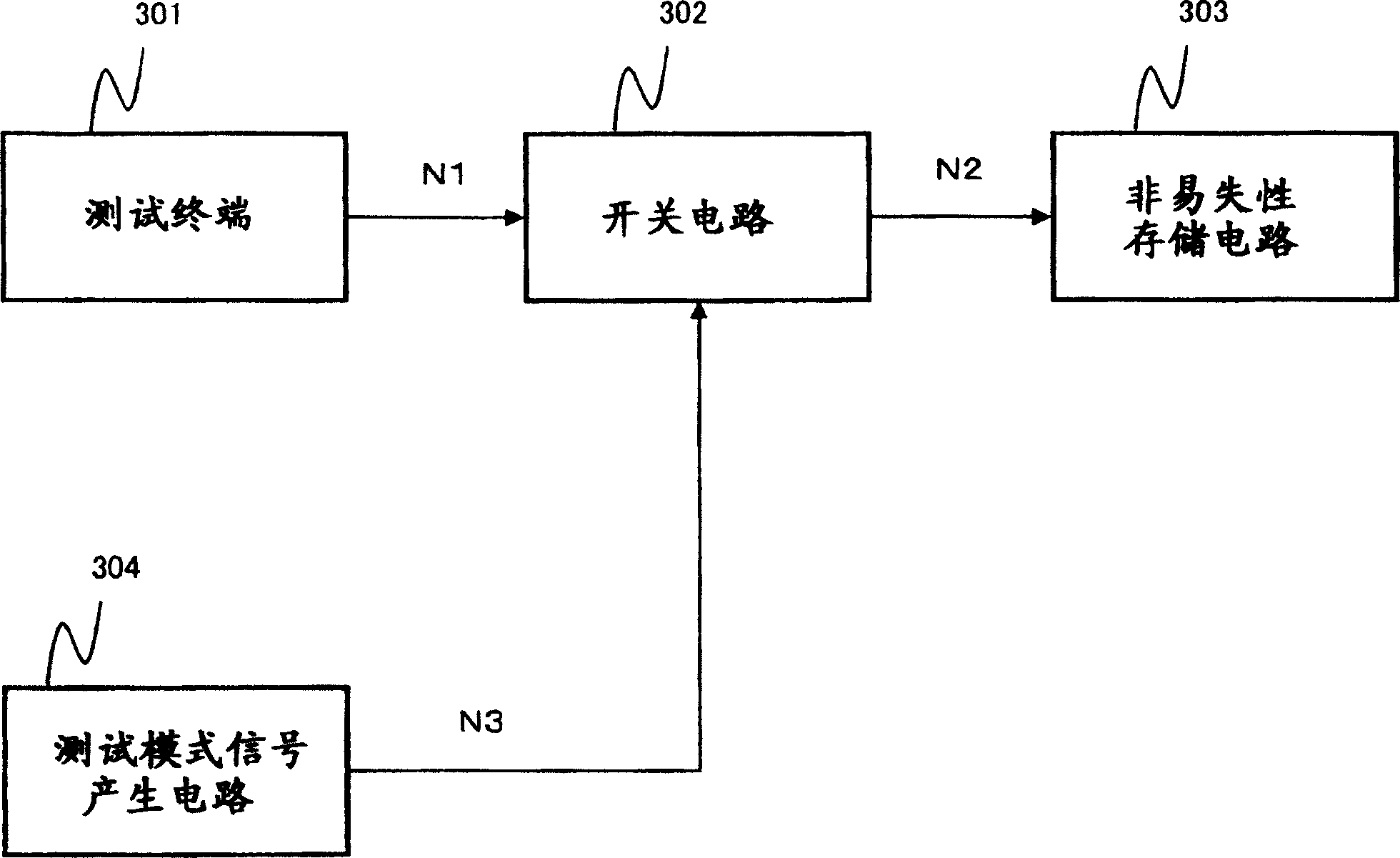
ActiveCN100405074CPrevent illegal readingDigital circuit testingSemiconductor/solid-state device testing/measurementElectricityNegation
A test terminal negation circuit (100) comprises a switch circuit (102) receiving a test signal from a test terminal (101) and outputs it in an asserted state as it is or in a predetermined negated state to a test object circuit (106), a test signal control circuit (105) which controls an output signal of the switch circuit (102) to be asserted or negated, a test mode signal generation circuit (103) which generates a test mode signal which asserts the output signal of the switch circuit (102), and a negating signal generation circuit (104) which can output a negating signal for forcing the output signal of the switch circuit (102) into negated state and comprises an electrically rewritable nonvolatile memory element. When the test signal control circuit (105) receives the negating signal, it does not assert the output signal of the switch circuit (102) even it receives the test mode signal.
Owner:知识产权I公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com