Disk array and computer or storage medium authentication method and system
A disk array and storage medium technology, applied in the field of computer information storage technology and security, can solve problems such as hidden dangers of data security, untrustworthy certification of disk arrays, non-compliance of disk arrays, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
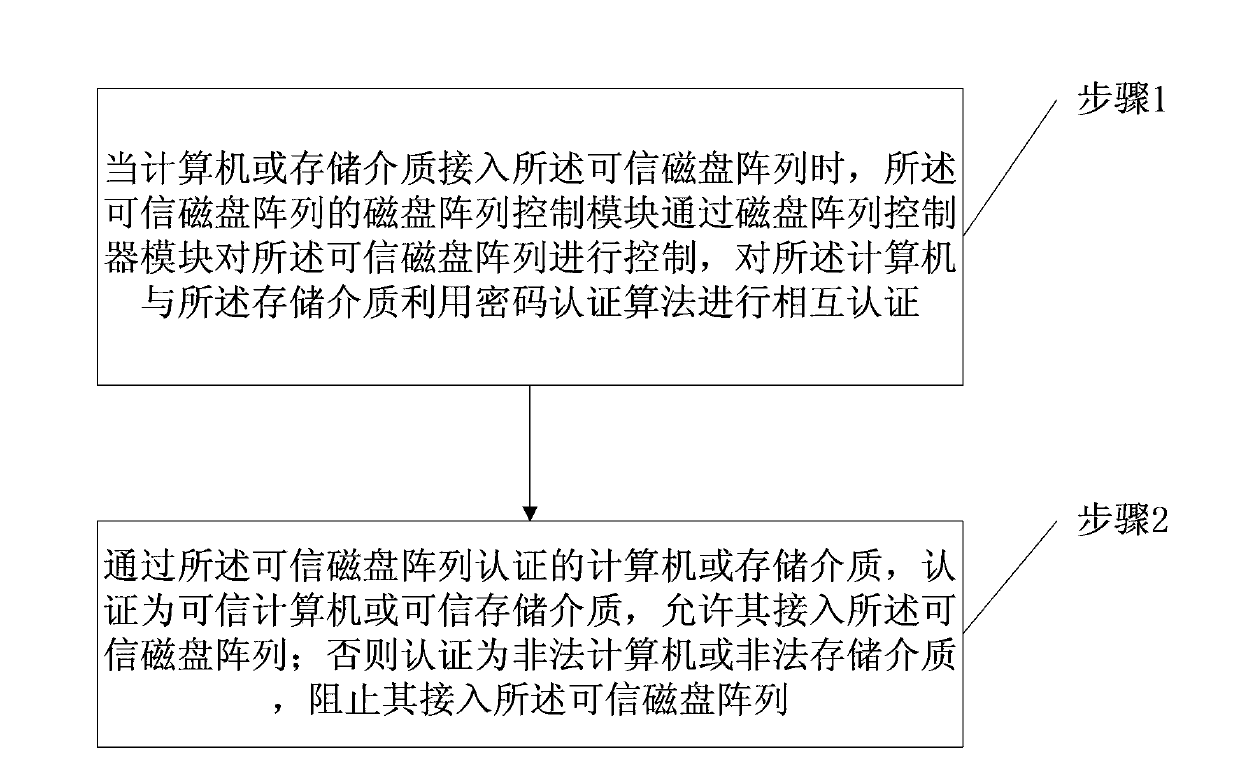
[0045] figure 1 It is a flowchart of the authentication method between the trusted disk array and the computer or the storage medium of the present invention. Such as figure 1 As shown, the method includes:
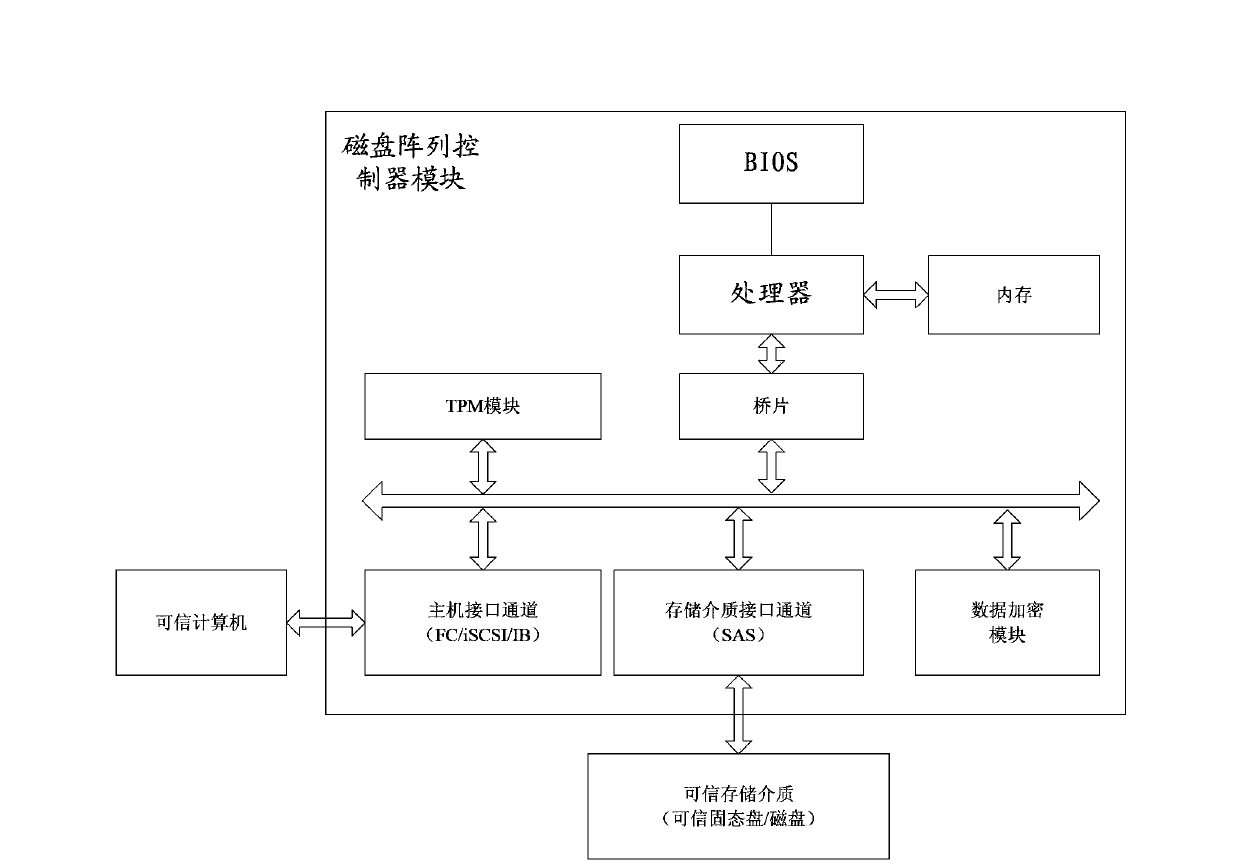
[0046] Step 1, when the computer or storage medium accesses the trusted disk array, the disk array control module of the trusted disk array controls the trusted disk array through the disk array controller module, and controls the computer and The storage medium uses a cryptographic authentication algorithm to perform mutual authentication;
[0047] Step 2, the computer or storage medium authenticated by the trusted disk array is certified as a trusted computer or trusted storage medium, allowing it to access the trusted disk array; otherwise it is certified as an illegal computer or illegal storage medium, preventing It accesses the trusted disk array.
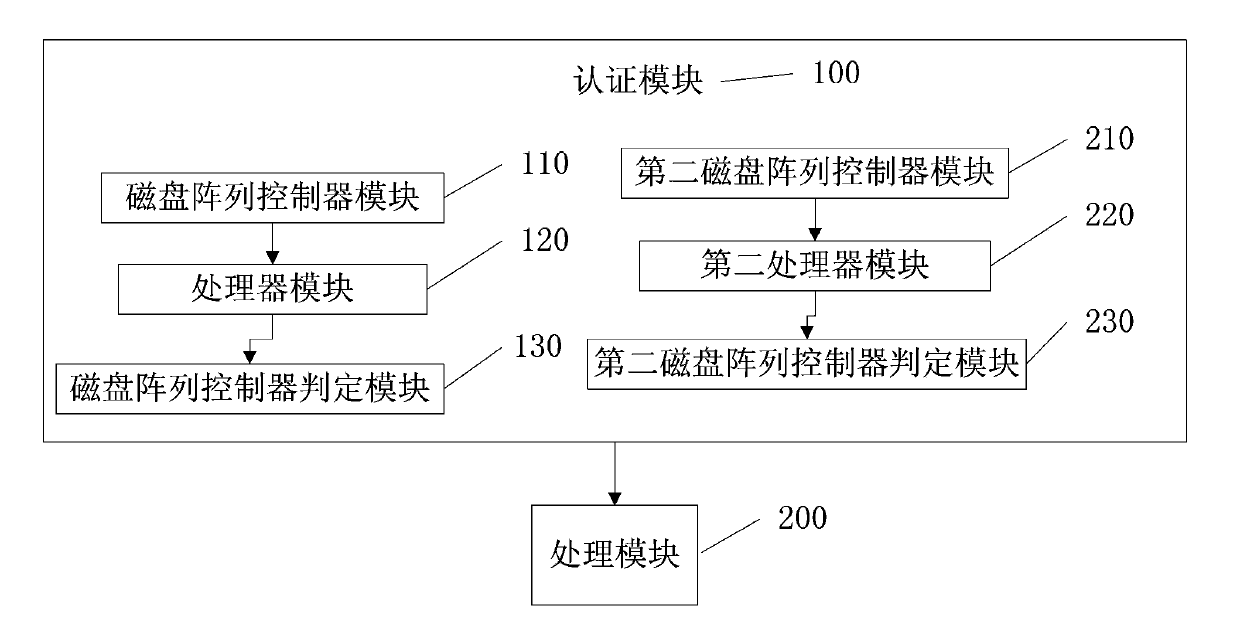
[0048]Further, the step 1 includes:
[0049] Step 11, the disk array controller module is connected to the comput...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com