Method for shielding unauthorized users from starting software
A user and non-authorized technology, applied in the direction of internal/peripheral computer component protection, program/content distribution protection, instruments, etc., to avoid illegal reading, ensure security and effectiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
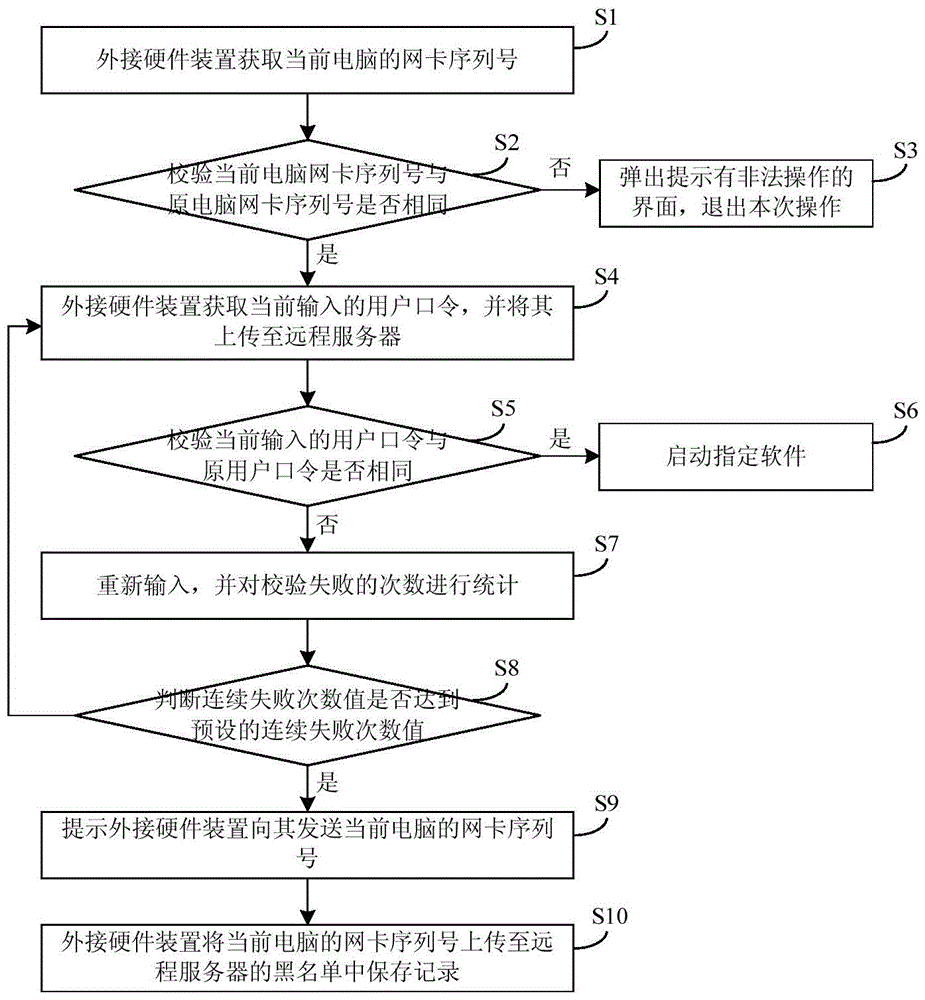
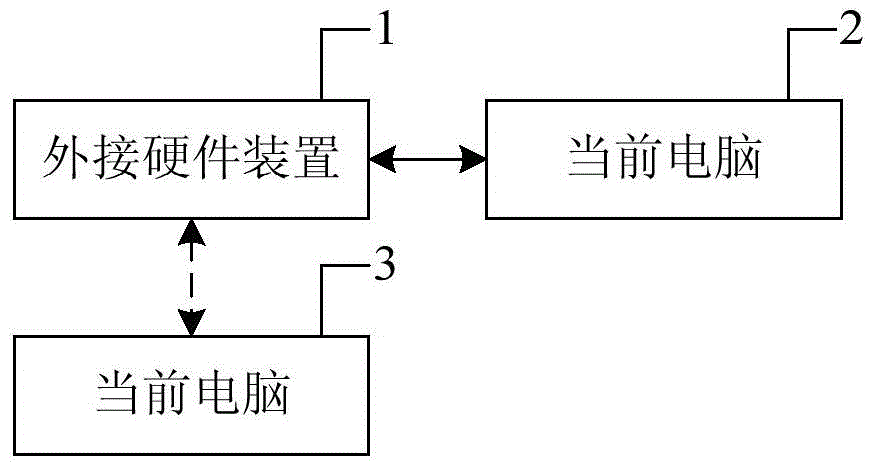
[0040] The present invention provides a method for shielding unauthorized users from starting software, which includes the following steps:
[0041] When the serial number of the network card stored in the external hardware device is the same as that of the current computer, the login interface of the specified software will pop up, otherwise, exit this operation;
[0042] When the user password stored in the remote server is the same as the currently entered user password, it indicates that the current user is an authorized user and can start the specified software; otherwise, count the number of verification failures;
[0043] When the number of consecutive verification failures reaches the preset number of consecutive verification failures, upload the serial number of the network card of the current computer to the blacklist of the remote server.
[0044] Such as figure 1 As shown, the specific steps of the above method are as follows:
[0045] S1. After establishing a co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com