Patents
Literature
376 results about "Software usage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
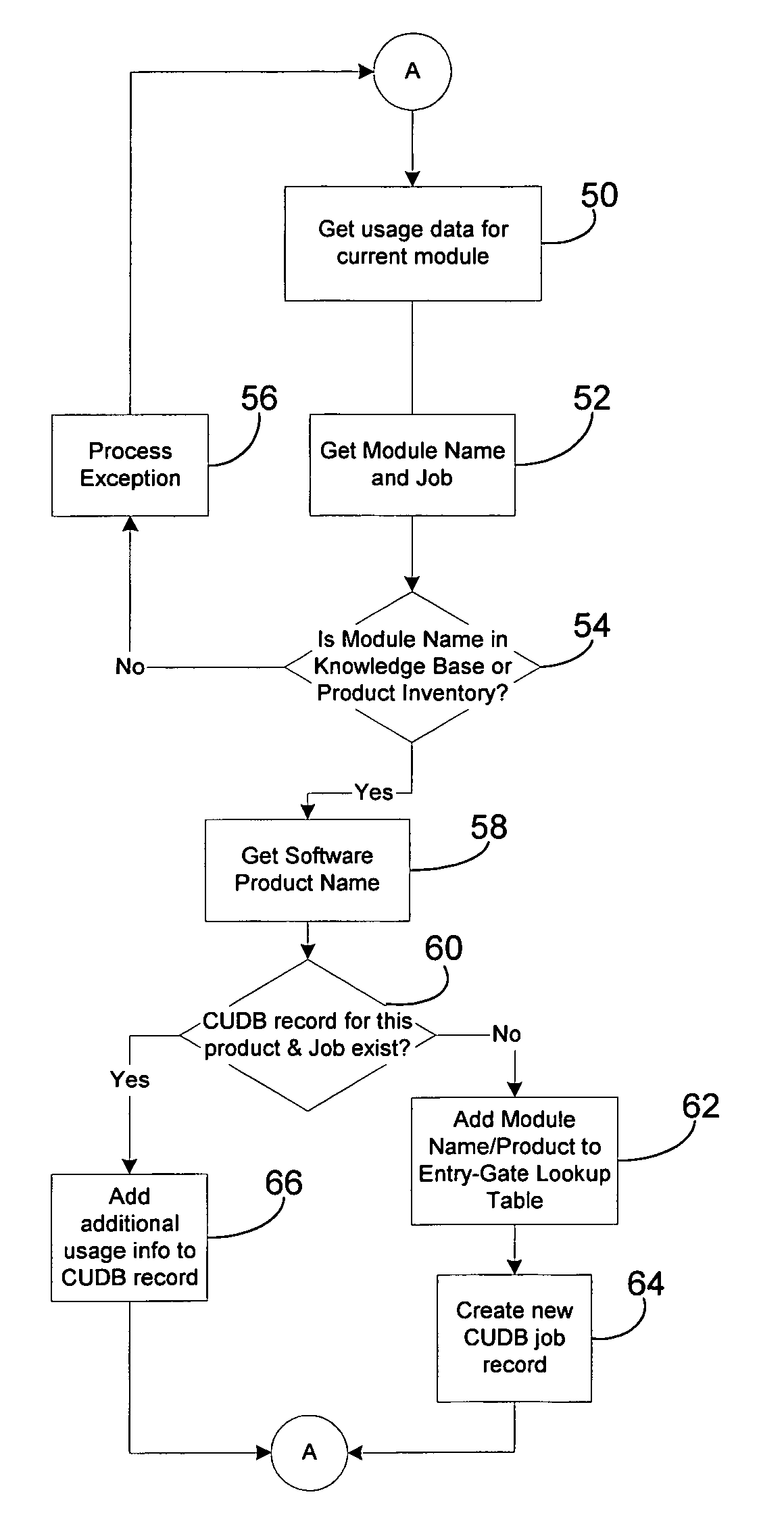
Consolidation and reduction of usage data
InactiveUS6996807B1Quantity minimizationHardware monitoringSpecific program execution arrangementsReducerComputer memory
A software monitoring and auditing system which determines the inventory of software products on a computer includes data reducer software which processes detailed software usage data gathered by a monitoring component of the software to create a condensed usage database. The reducer software contemporaneously converts the data records in a manner which reduces the amount of data records by at least a factor of 100, consuming less computer memory and allowing users of the software monitoring and auditing system to review usage data on a desktop PC or the like.
Owner:IBM CORP
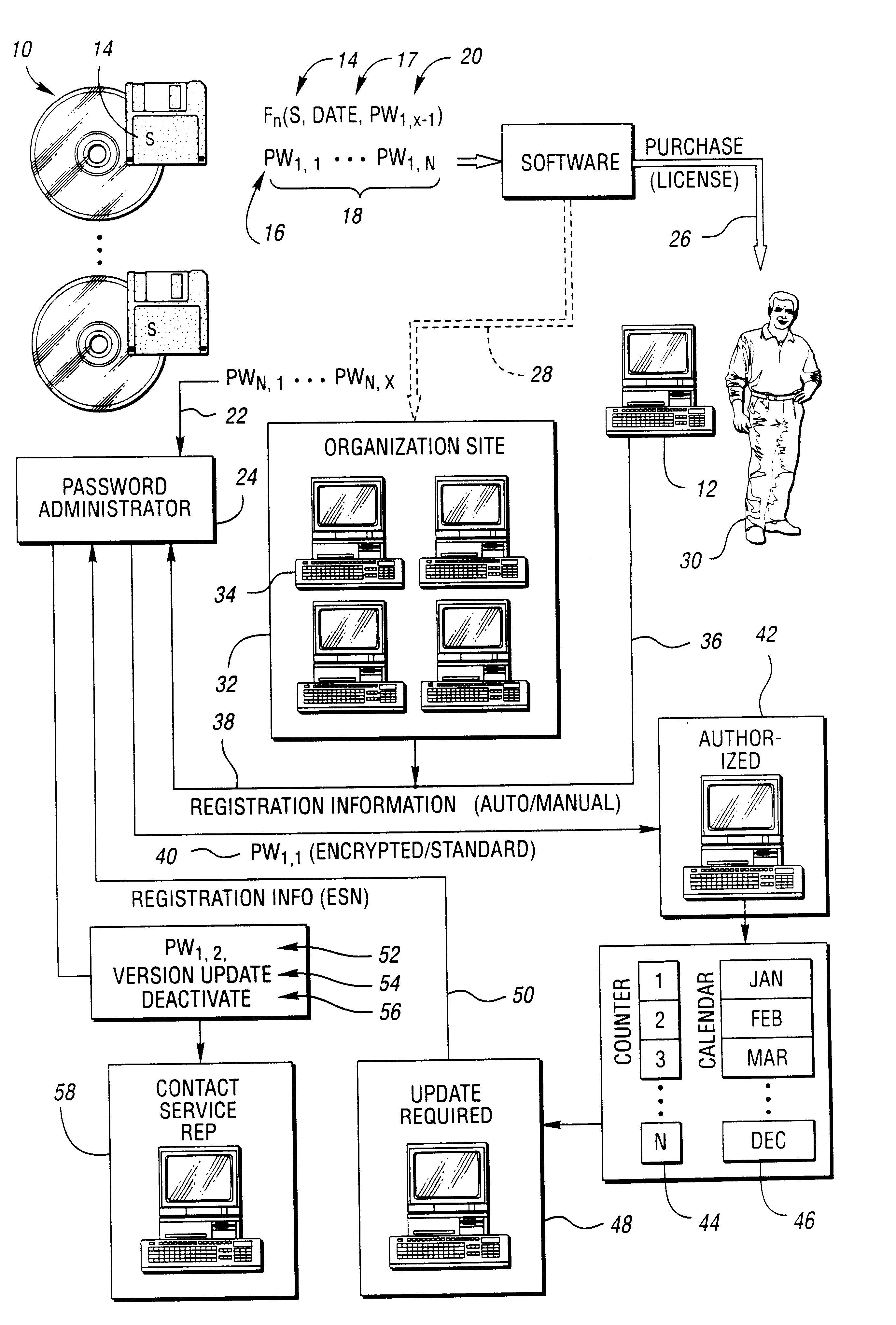
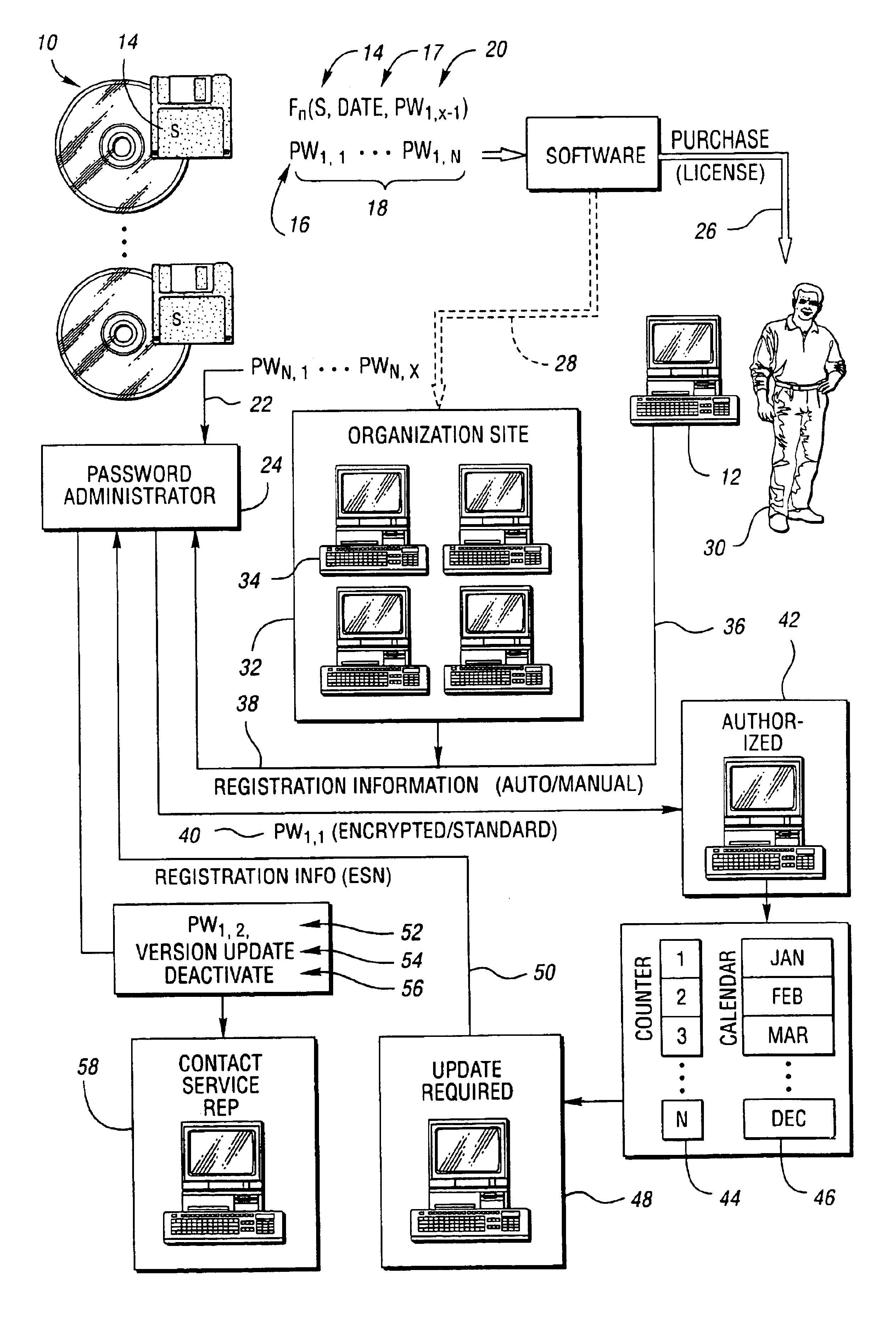
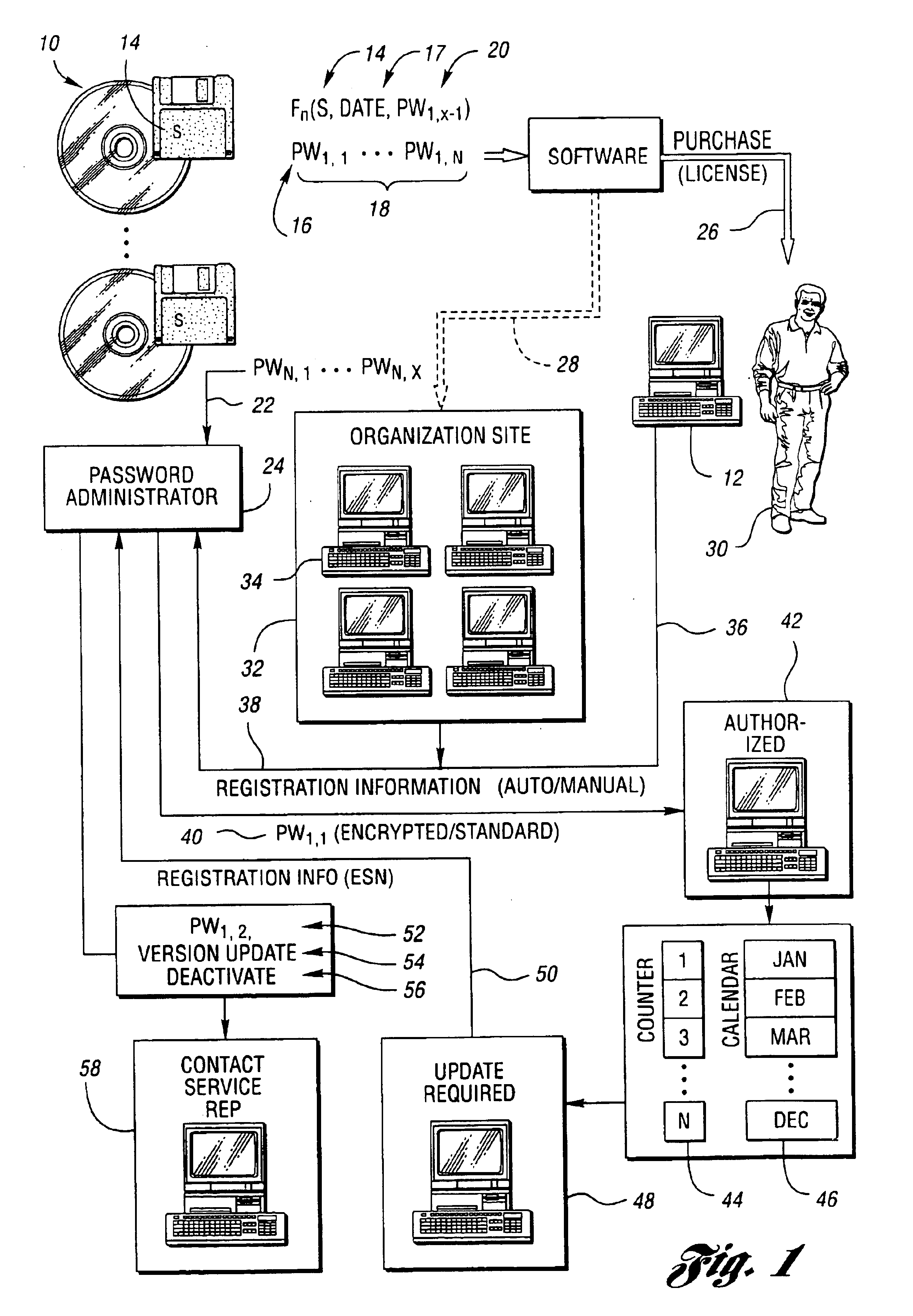
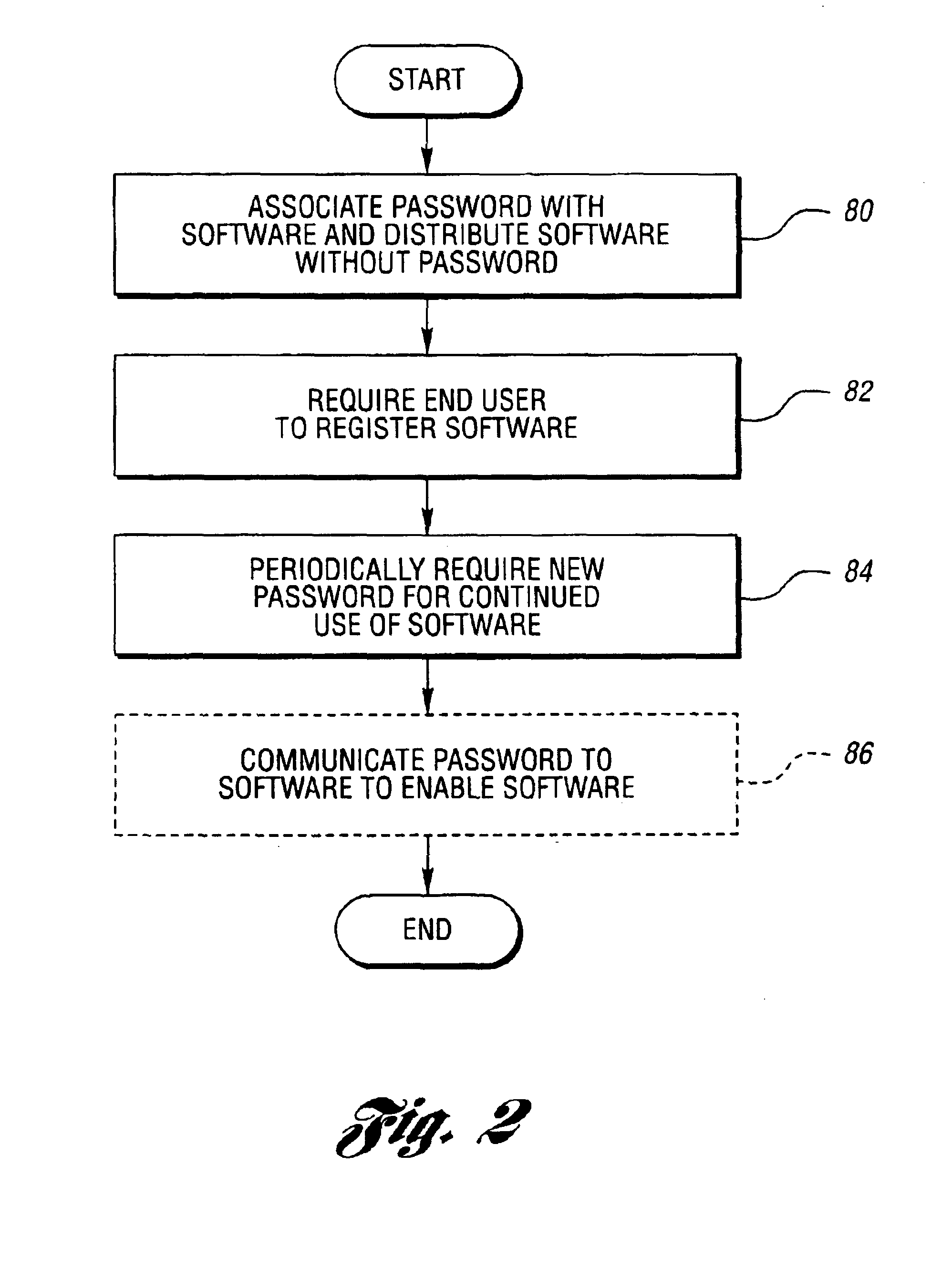
Method for securing software to increase license compliance
InactiveUS6857078B2Improve securityReduces unauthorized useDiscounts/incentivesMemory loss protectionSoftware engineeringAuthorization
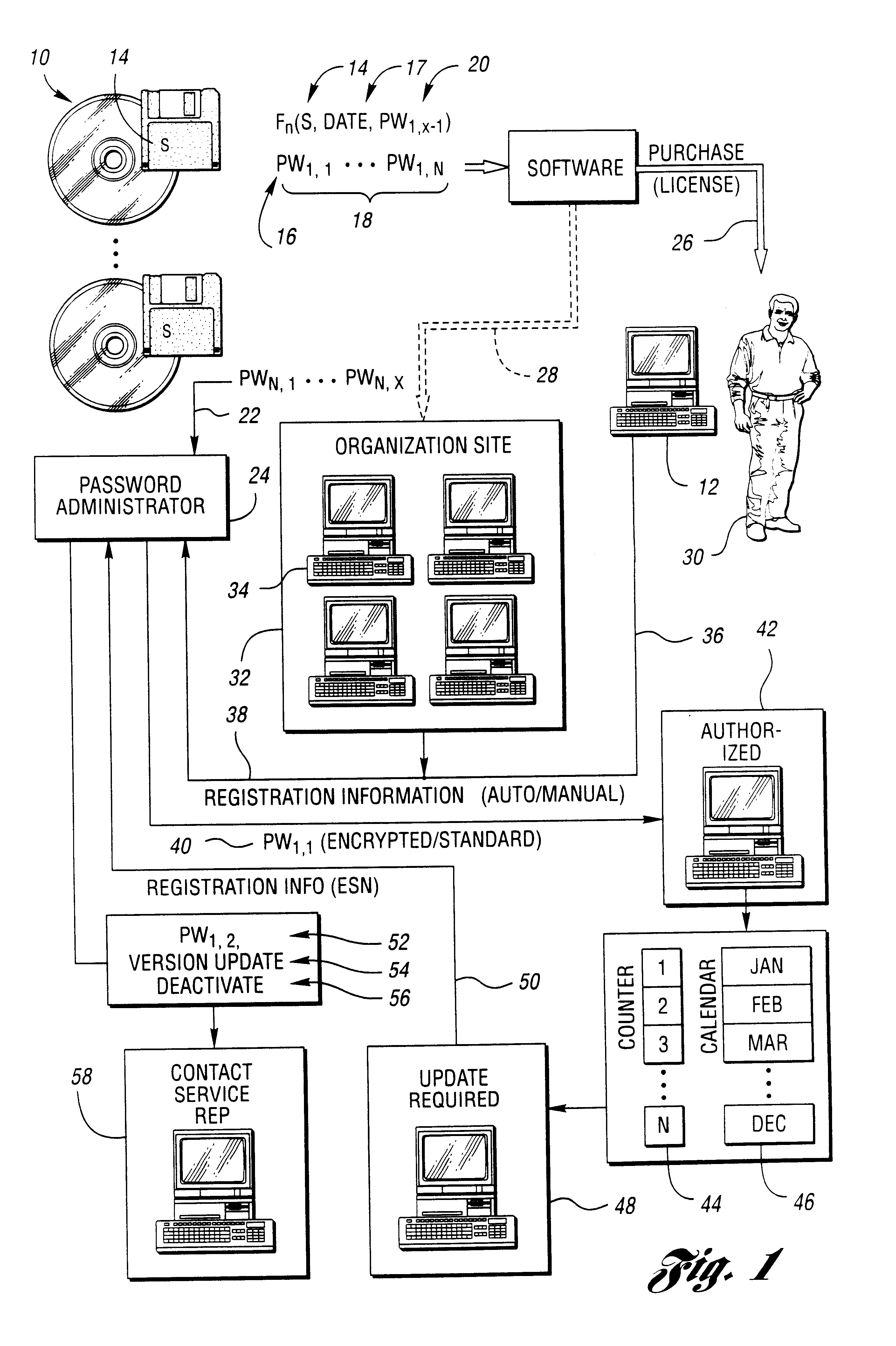
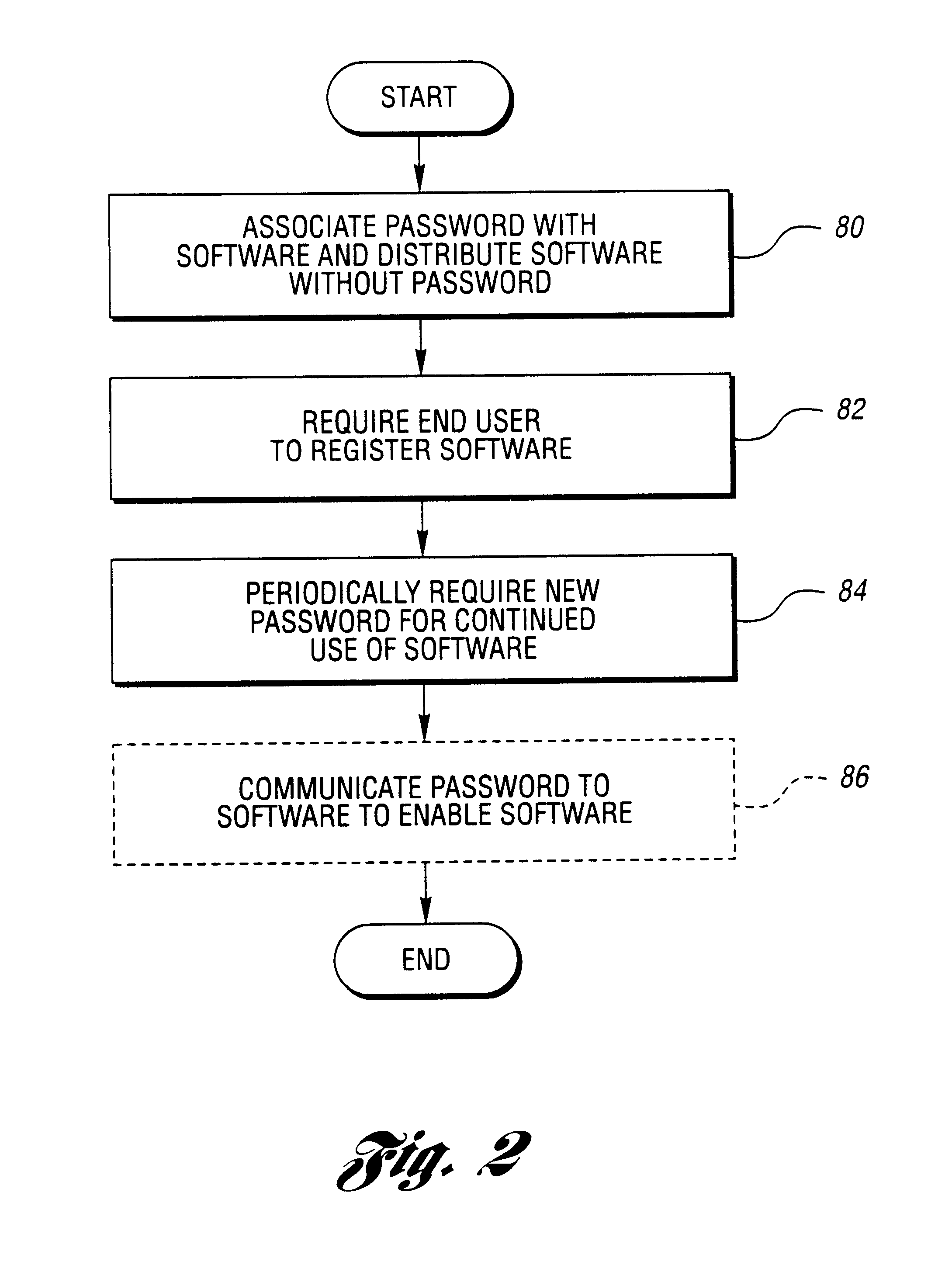
A method for reducing unauthorized software use includes supplying a first authorization code with the software. The first authorization code enables the software on a computer for use by a user for an initial authorized period upon entry by the user. The user is required to contact the representative for retrieval of an additional authorization code. The software is operable during a subsequent authorization period beyond the initial authorization period without further or continual communication with the representative following entry of the additional authorization code. The user chooses manual or electronic registration and provides registration information to the representative prior to retrieval of the additional authorization code. The registration information includes computer specific information. The additional authorization code is communicated to the software upon the registration information indicating that the software has not been previously registered or upon the registration information matching a portion of previously provided registration information.
Owner:COLVIN DAVID S
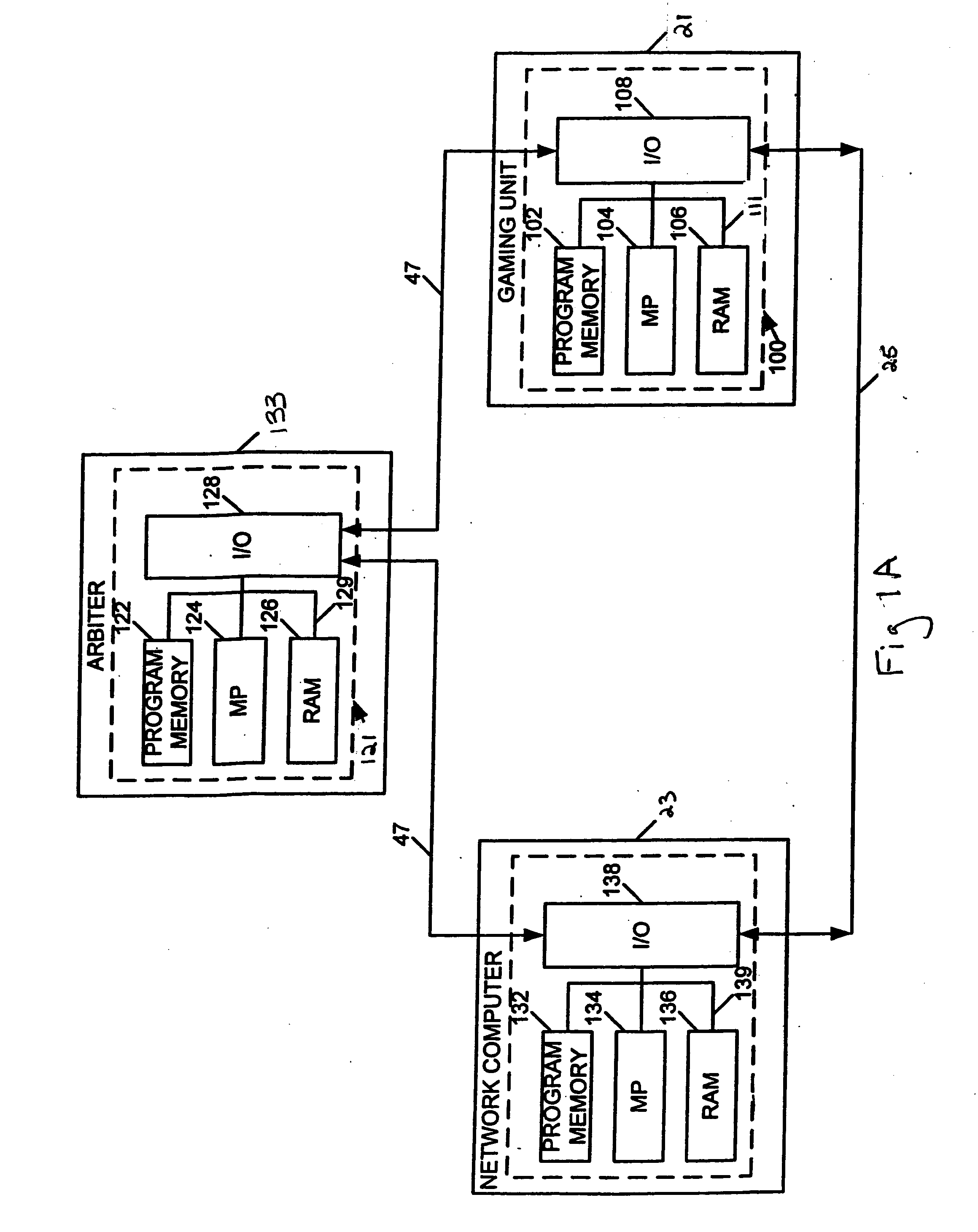
Methods and devices for authentication and licensing in a gaming network
ActiveUS20070026942A1Computer security arrangementsApparatus for meter-controlled dispensingHuman–computer interactionLicense
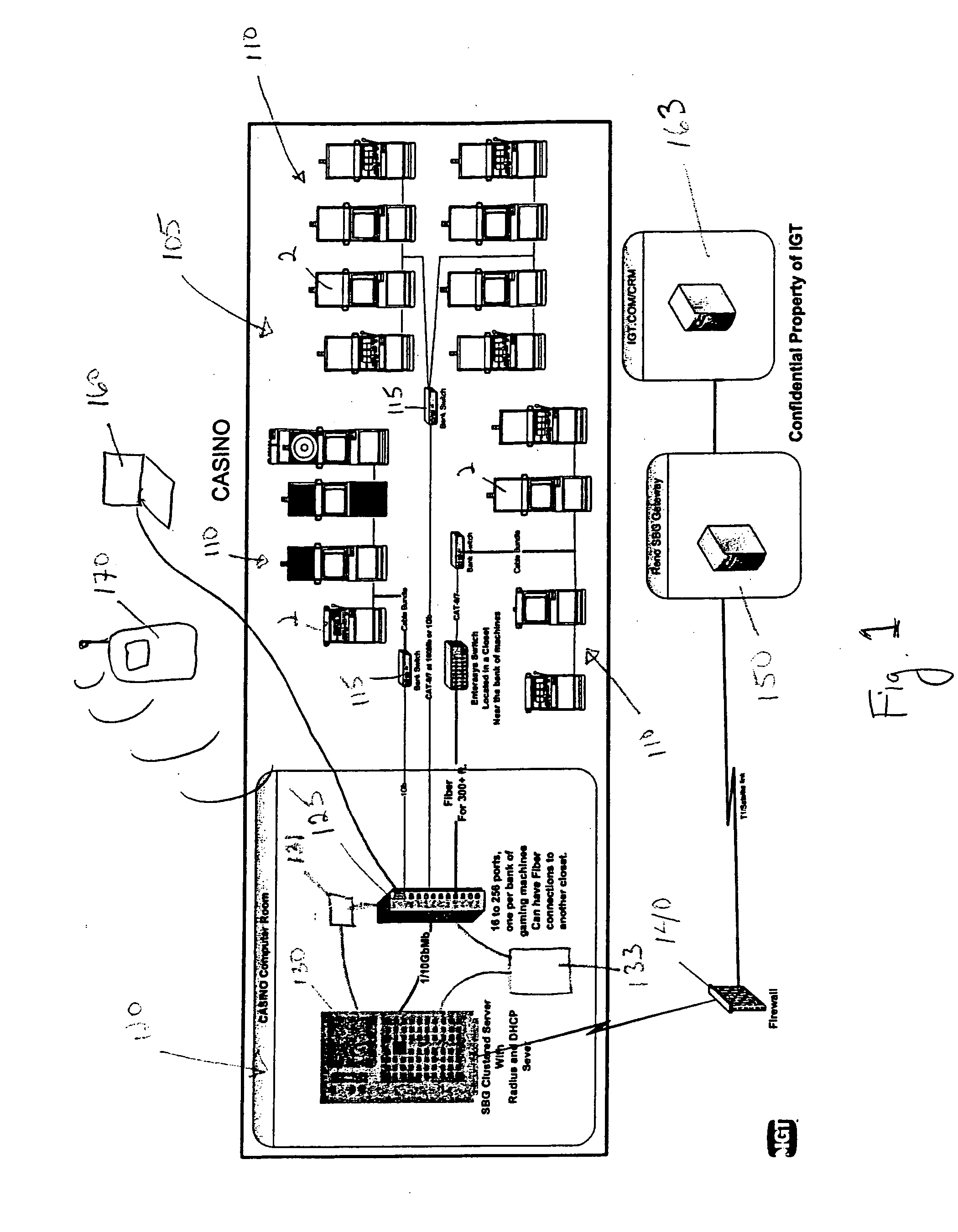
Methods and devices are provided for managing licenses in gaming networks. Some aspects of the invention are provided as a license manager module that operates as part of a server-based system for provisioning and configuring gaming machines. Security and authentication techniques are provided to prevent unauthorized gaming software usage. Such gaming software may be, for example, downloaded to gaming machines in the network under the control of a gaming establishment's game management server that is in communication with a license manager device. In preferred implementations, a gaming machine is prevented from executing software for a game of chance unless the license for that game is valid and has not expired.
Owner:IGT
Method for monitoring software using encryption including digital signatures/certificates
InactiveUS6986063B2Reducing unauthorized useDigital data processing detailsUser identity/authority verificationPasswordDigital signature
A method and system for reducing unauthorized software use include generating a key based on computer-specific information of a computer on which the software is installed and using the key to encrypt an authorization code which enables use of the software on the computer. A representative maintains contact with the software user as a new authorization code from the representative is required after some period of use of the software. The representative encrypts the new password using the key and transfers the encrypted key to authorize use of the software for a next period of use. The encrypted password is a form of digital signature or certificate which is unique to a particular computer and limits use of the software to the particular computer. The key may be generated using various computer-specific information such as the motherboard / processor identification, the number of bad sectors or hard disk identification, and / or the amount of installed memory.
Owner:Z4 TECH
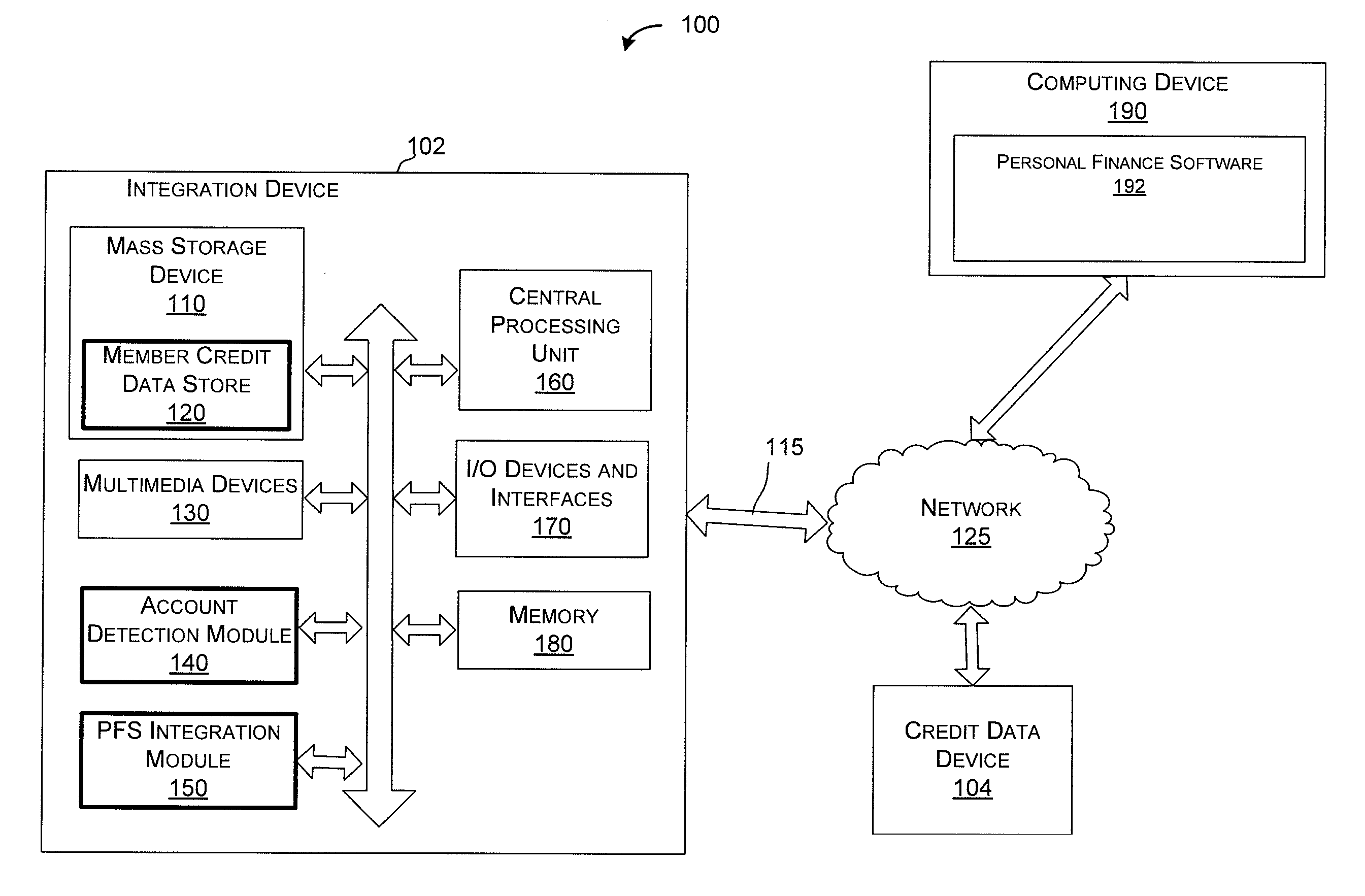
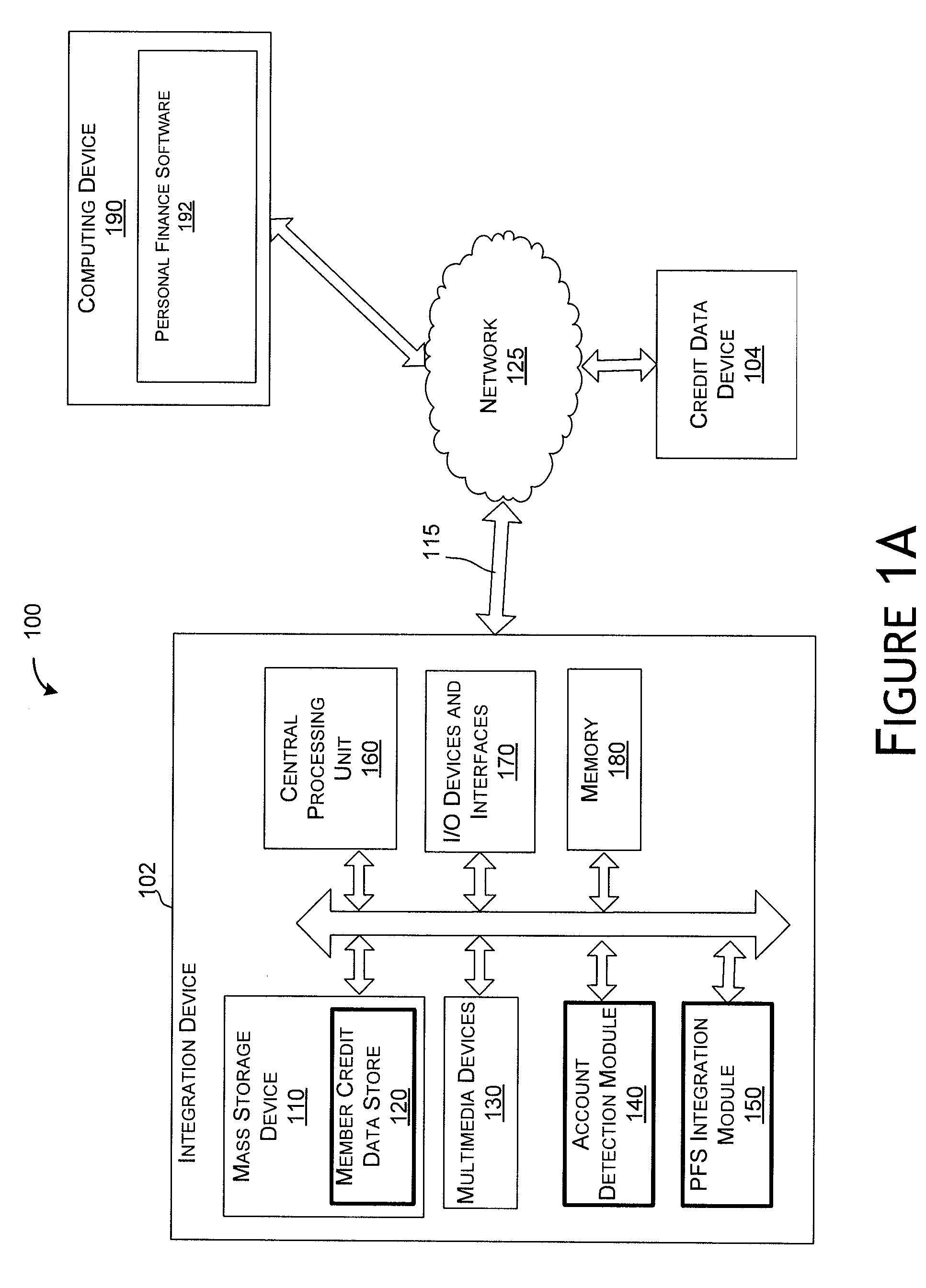
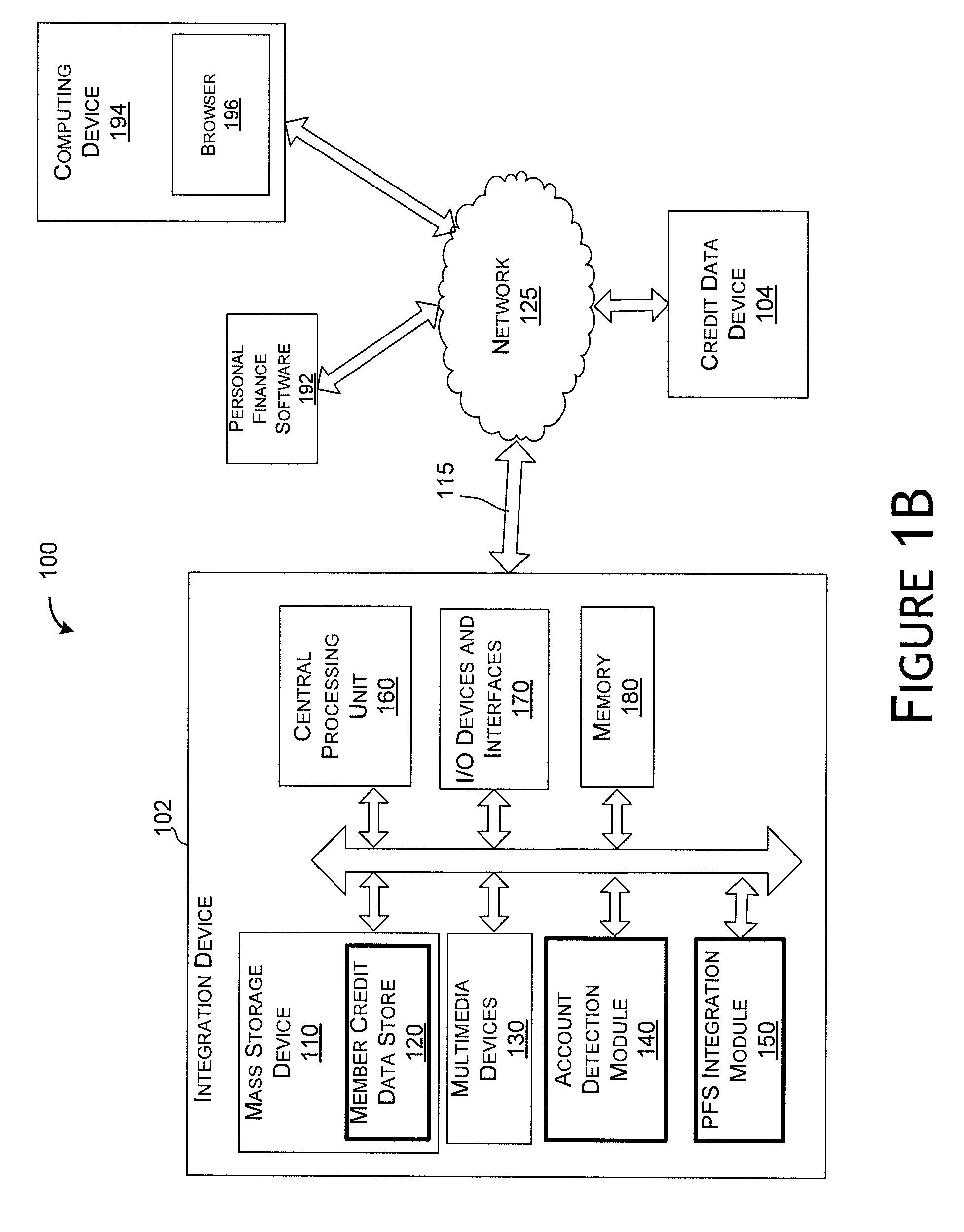
Personal finance integration system and method
Owner:CONSUMERINFO COM
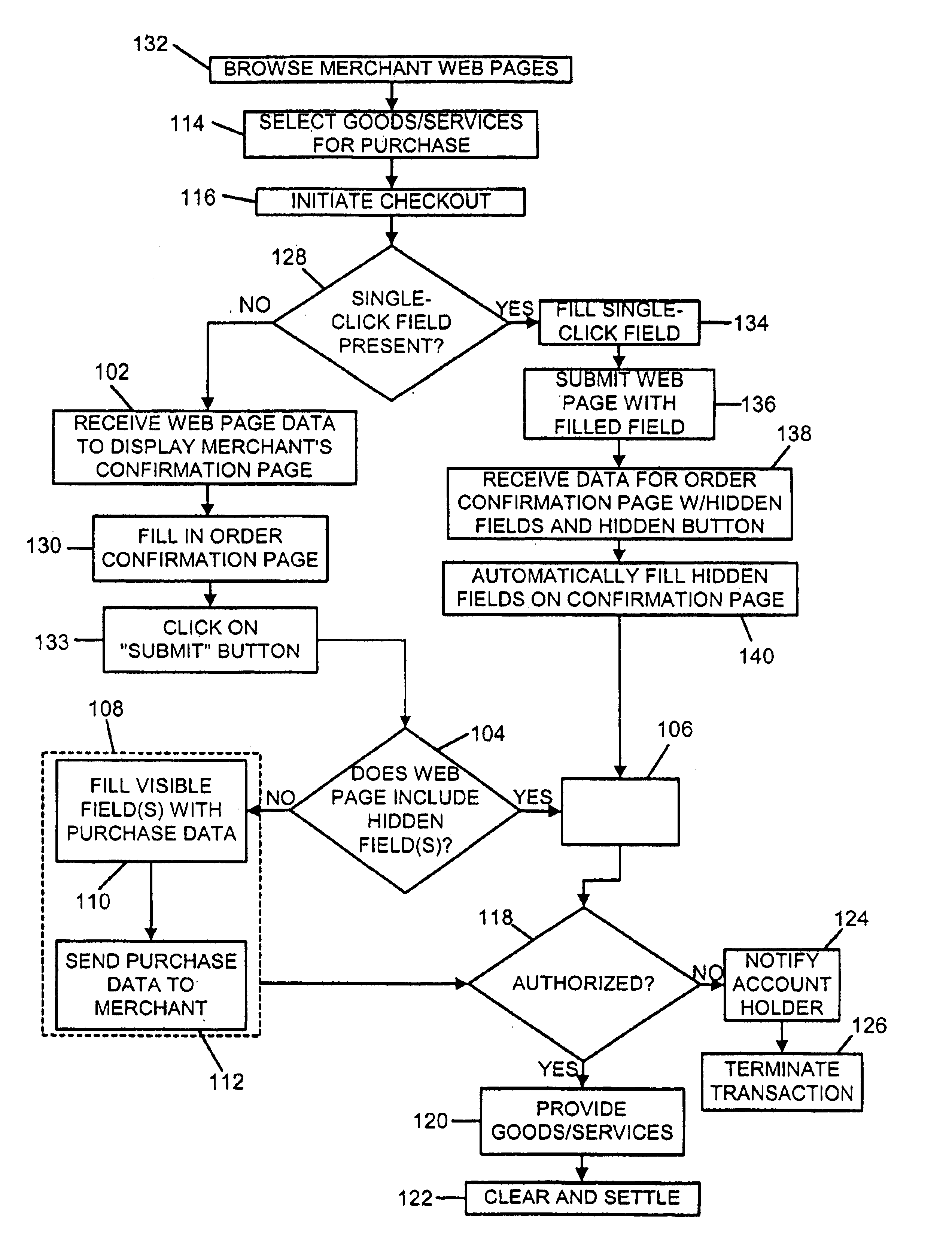
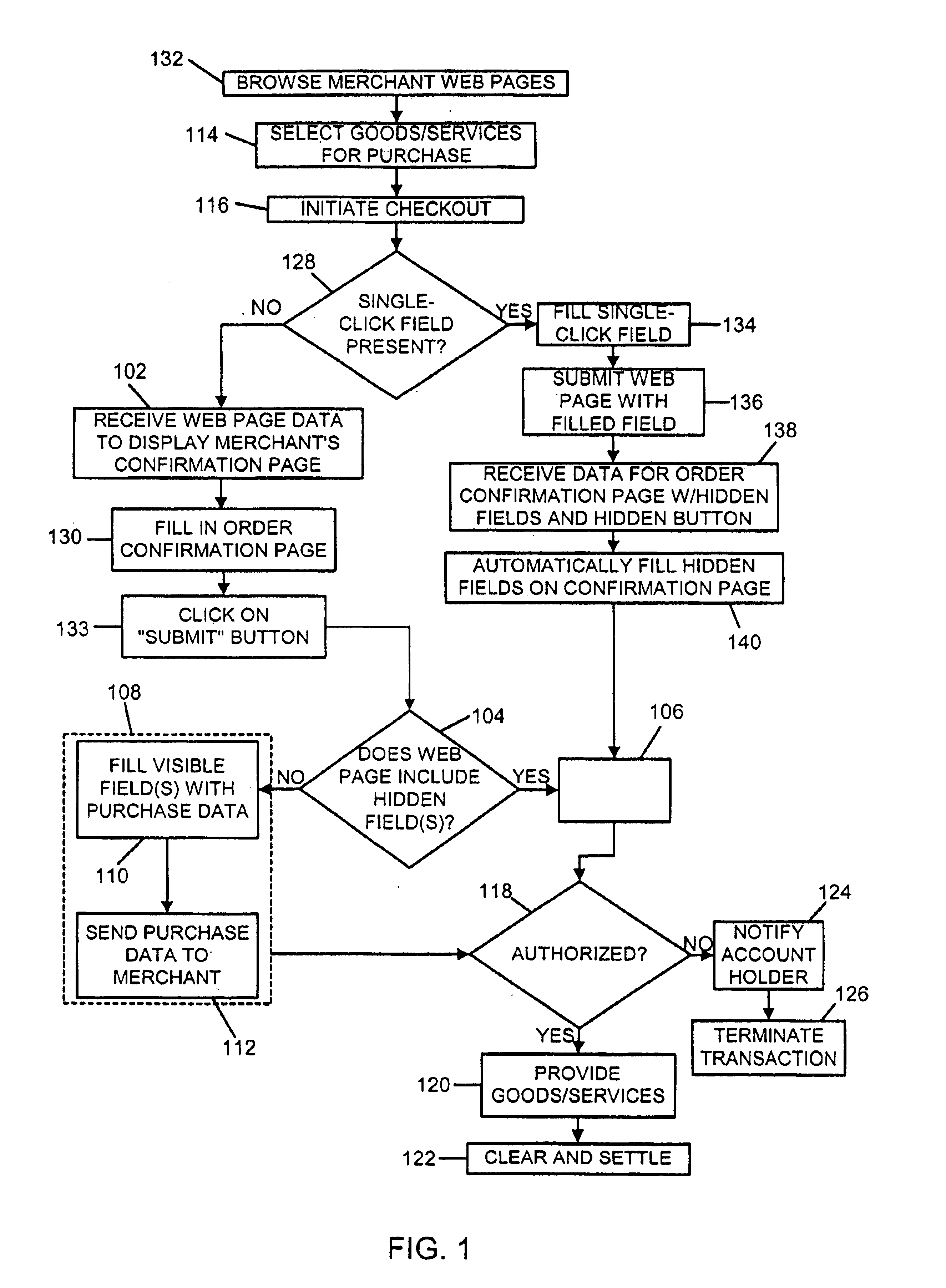
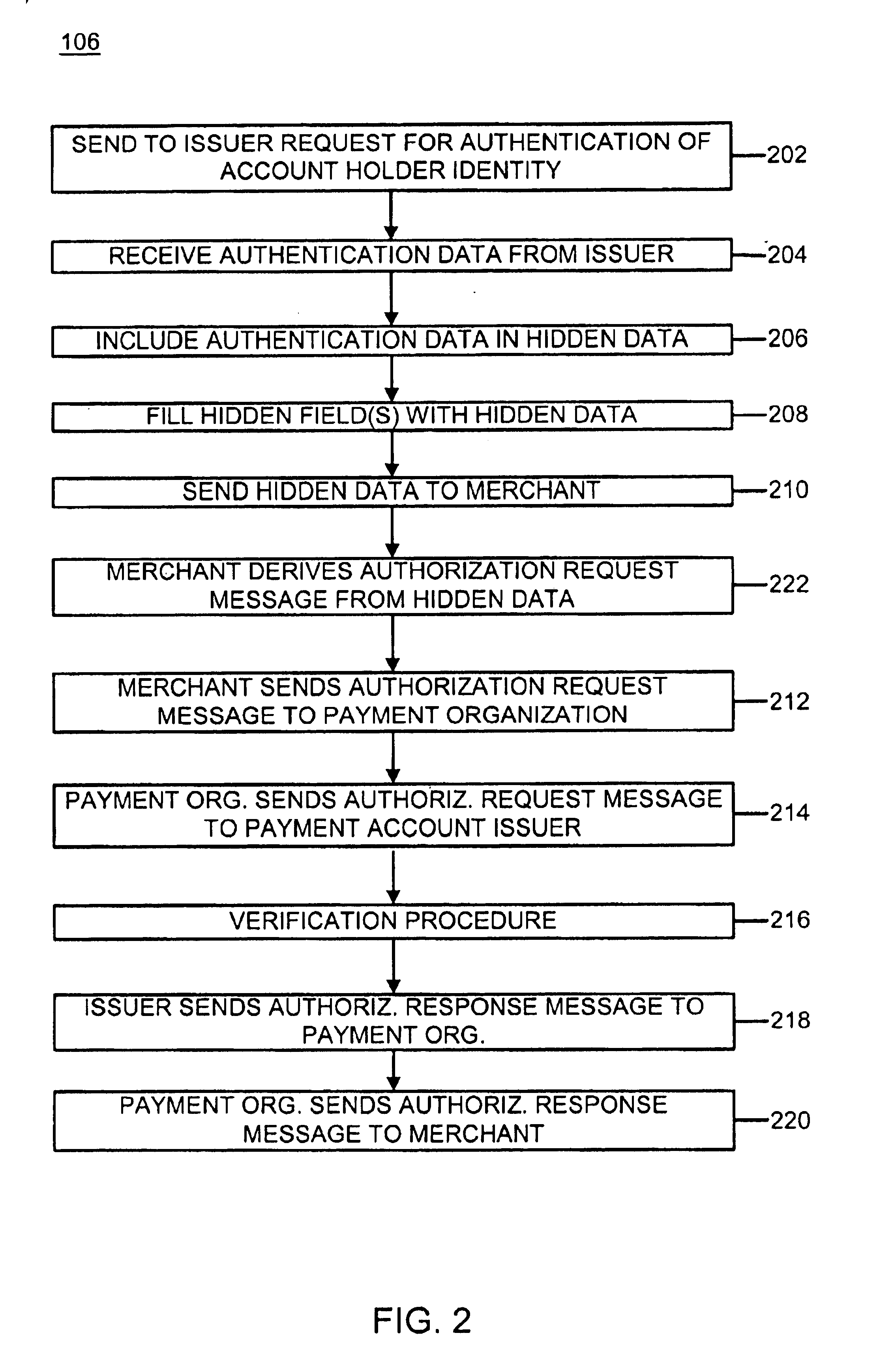
System and method for conducting secure payment transactions
In a secure electronic payment system, authentication data is sent from a payment account issuer to user software operated by a purchaser. The user software sends the authentication data to a merchant using hidden fields on the Web page of the merchant. The merchant generates an authorization request message based upon the authentication data. The authorization request message is sent to a payment organization either directly from the merchant or via the merchant's acquirer. The payment organization forwards the authorization request message to a payment account issuer which verifies the authorization request message, thereby generating an authorization response message which is sent to the payment organization. The payment organization forwards the authorization response message to the merchant, either directly or via the acquirer.
Owner:MASTERCARD INT INC
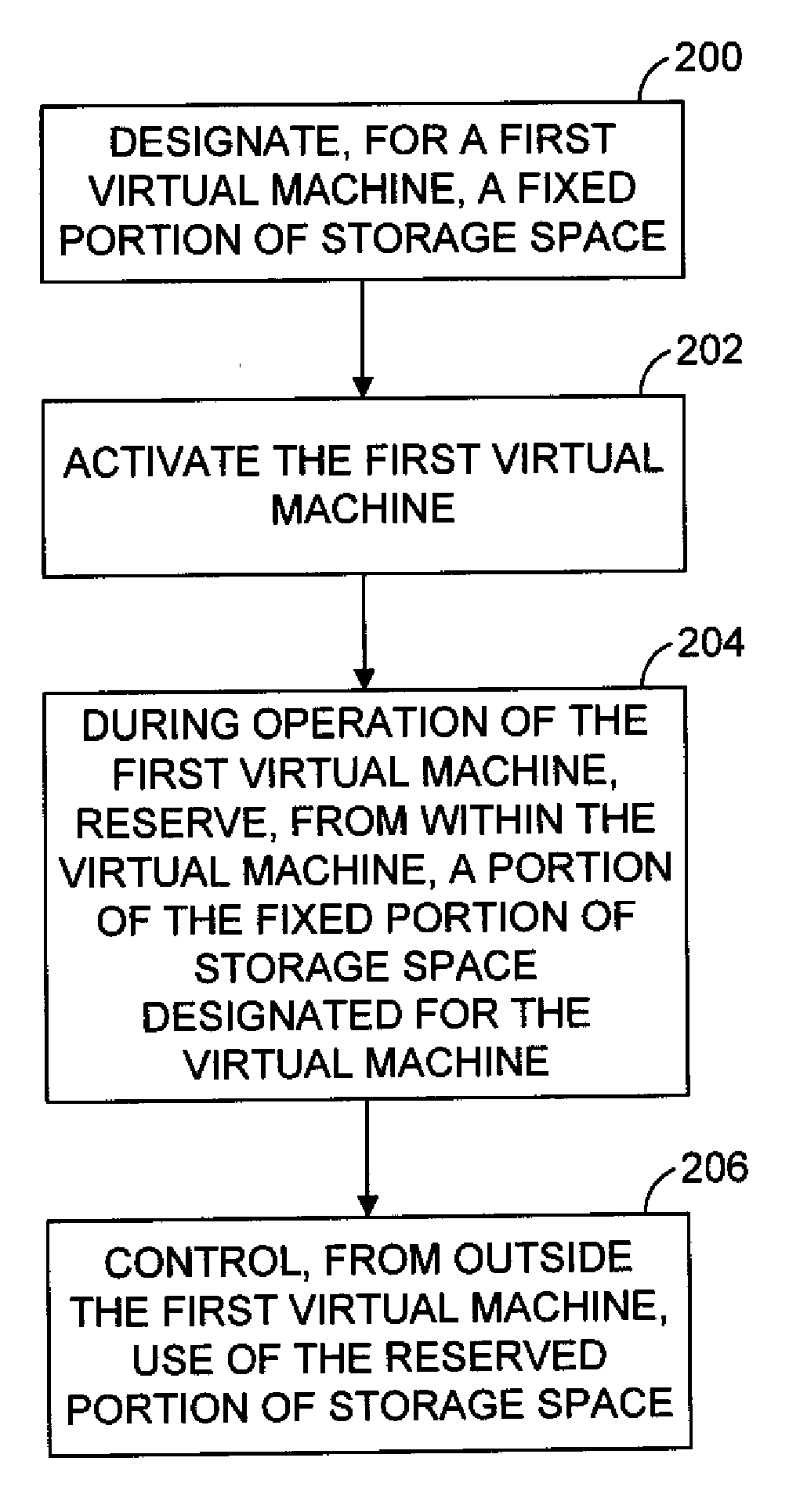
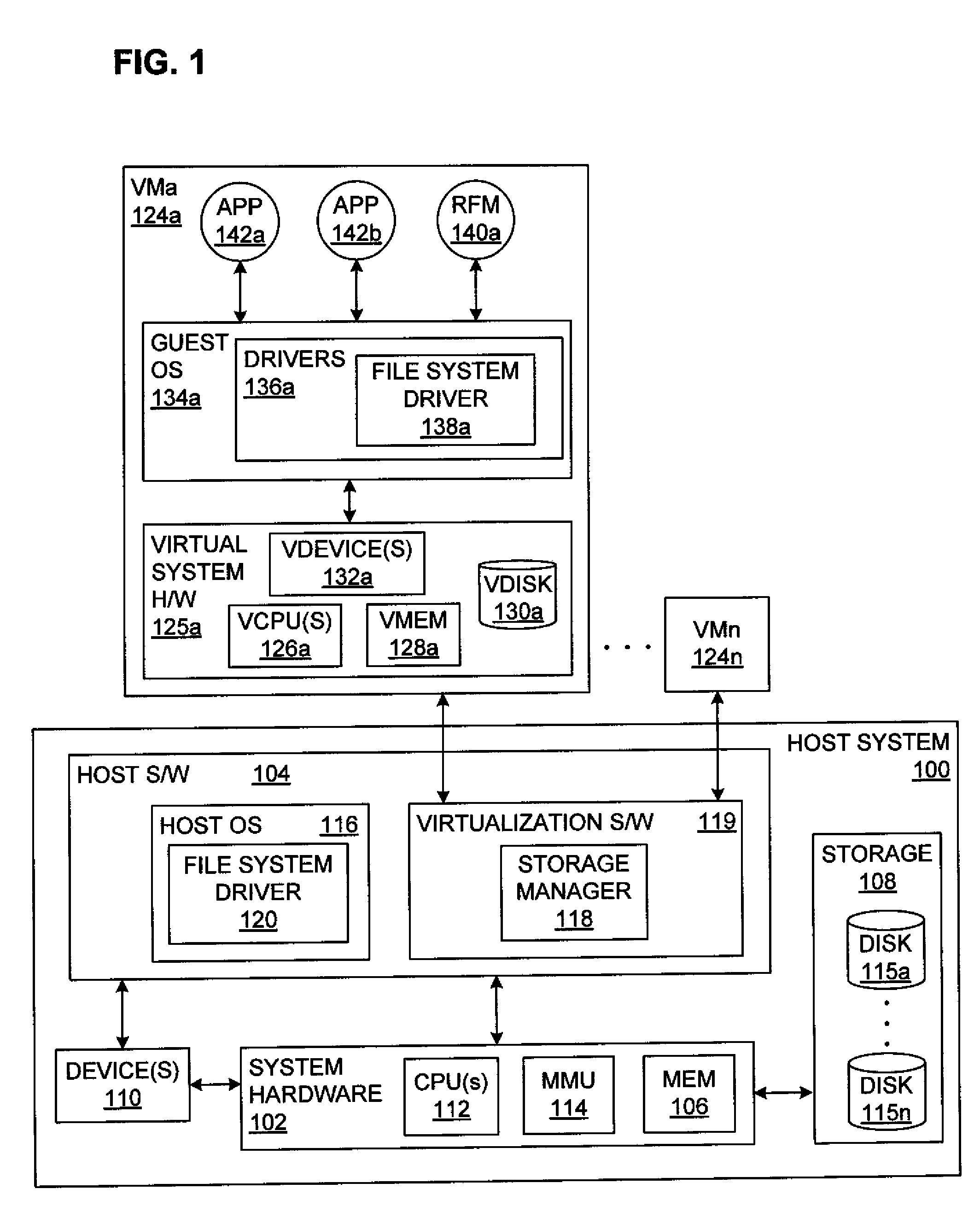
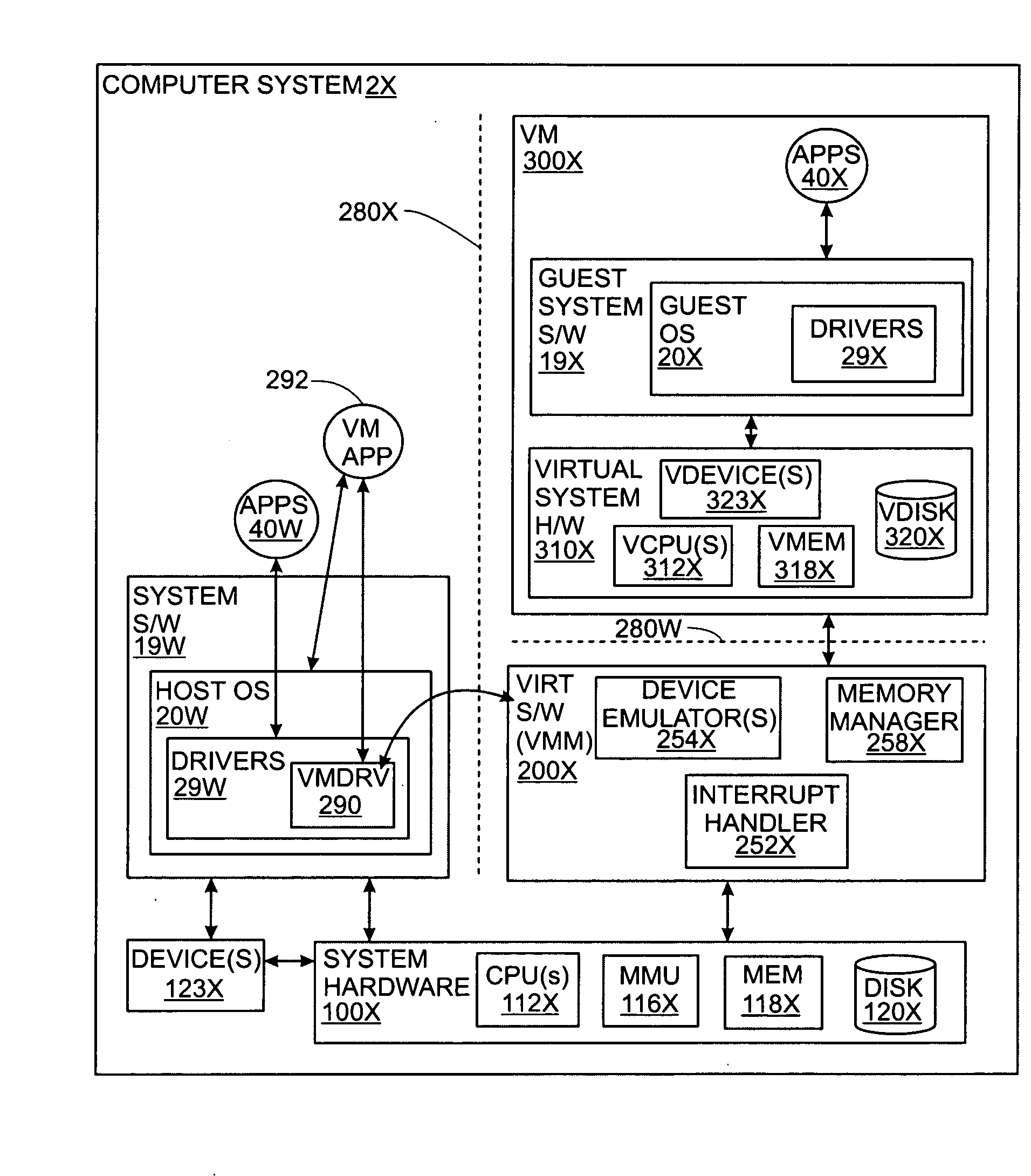
Adjusting Available Persistent Storage During Execution in a Virtual Computer System
ActiveUS20080270674A1Memory adressing/allocation/relocationComputer security arrangementsVirtual computingRunning time
The amount of virtual disk space that is available for use by software executing within a virtual machine may be dynamically adjusted while the virtual machine is running in a virtual computer system. According to one aspect, a method for flexible run-time reservation of disk space from a virtual machine is provided. The method includes designating for use by a first virtual machine, a fixed portion of disk space accessible by a computing system. The first virtual machine is activated. During operation of the first virtual machine, a portion of the fixed portion of the disk space designated for use by the first virtual machine is reserved from within the first virtual machine. Use of the reserved portion is controlled from outside of the first virtual machine.
Owner:VMWARE INC
Universal upgrade architecture
InactiveUS20060041881A1Universal flexibilityImprove transmission efficiencySoftware engineeringTransmissionSoftware modulesUpgrade
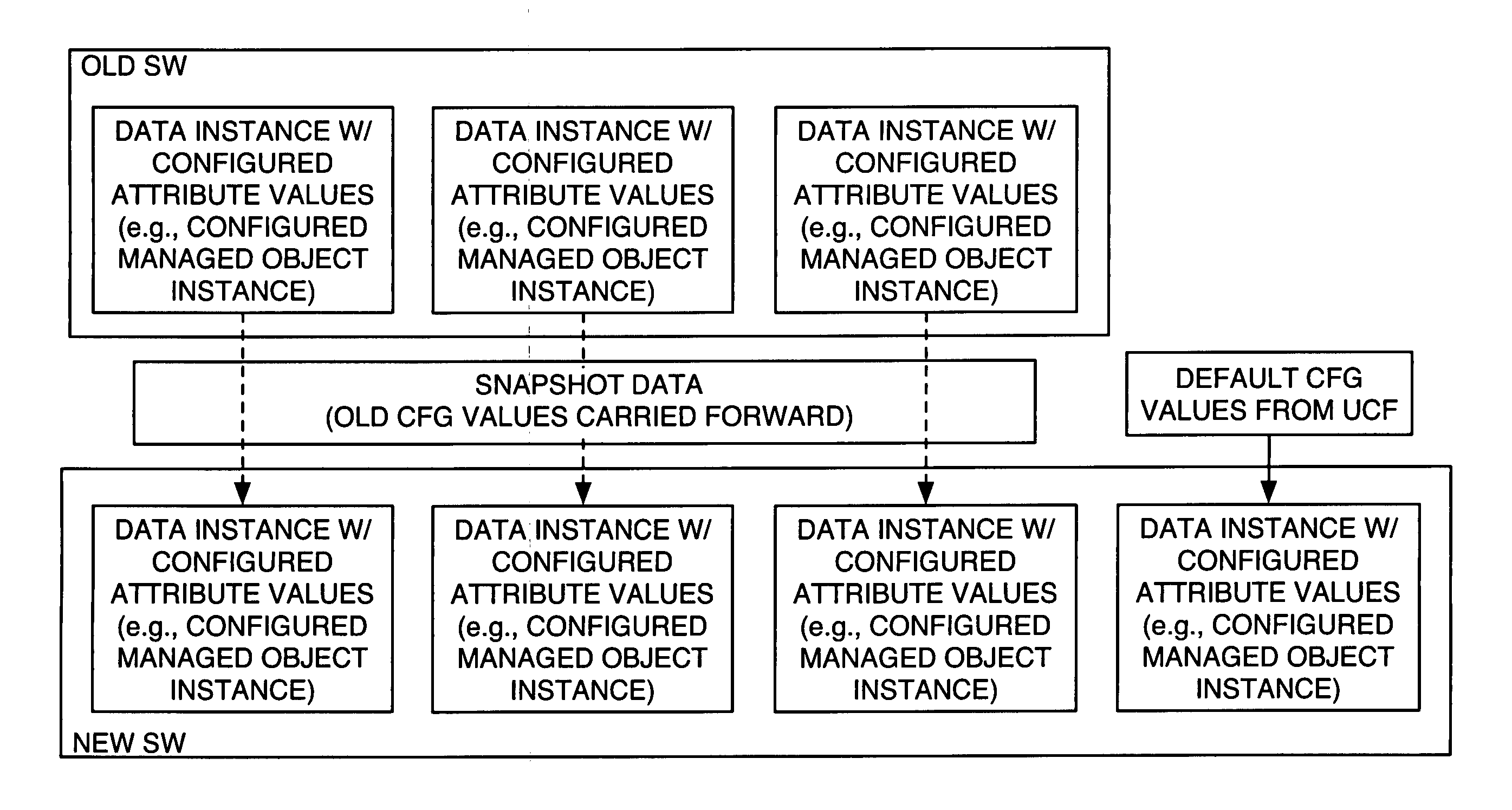
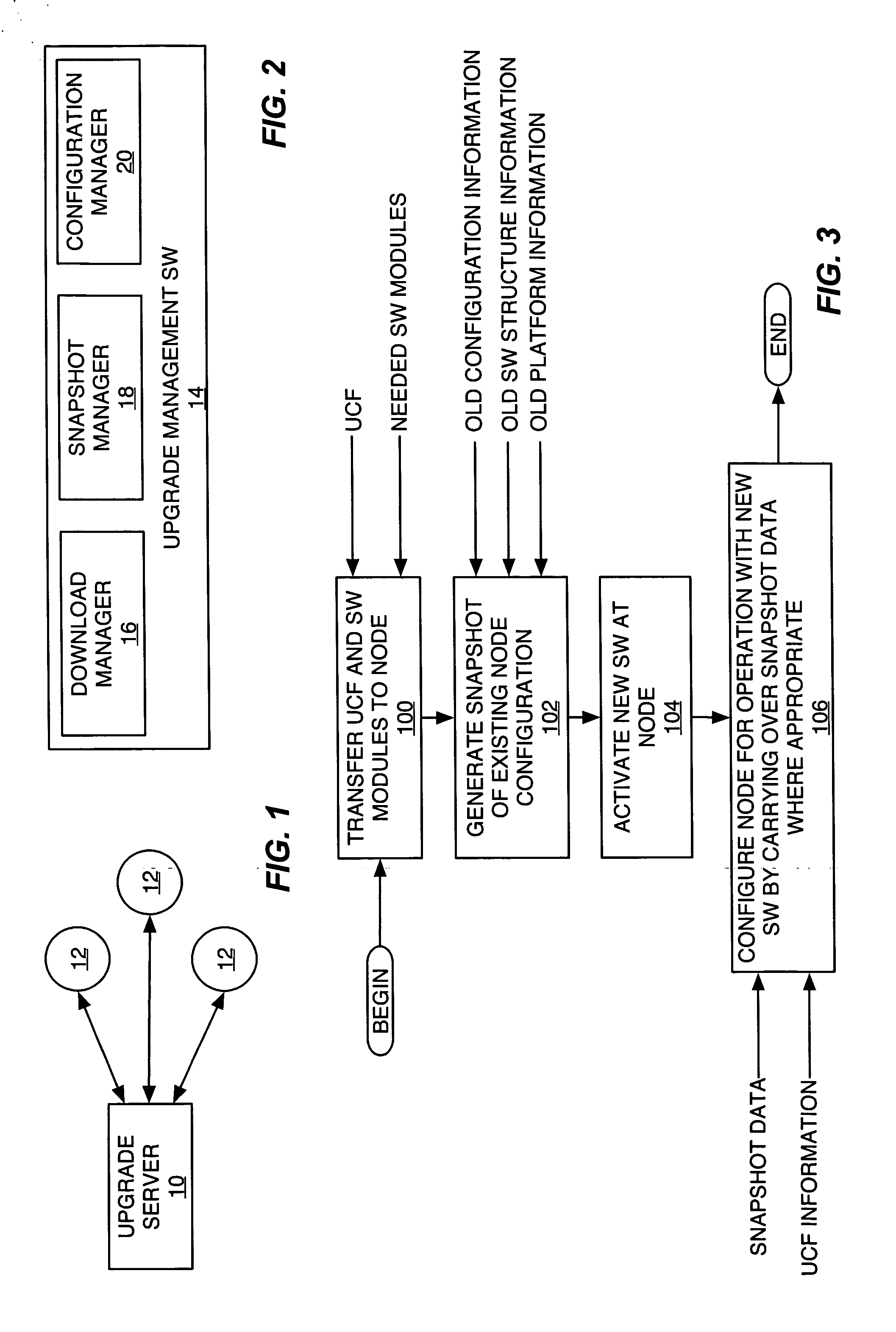
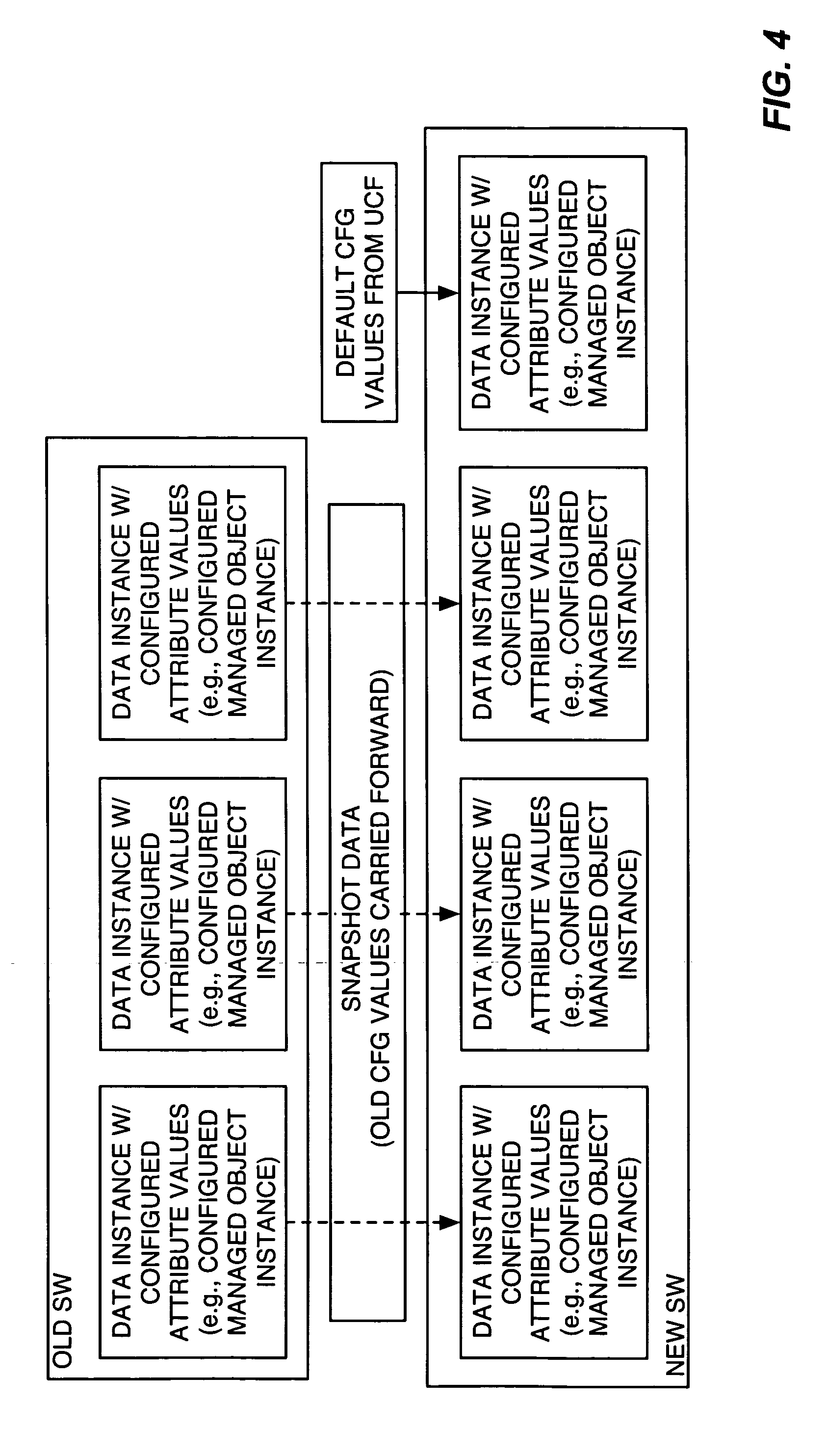
A method of upgrading a wireless communication network node comprises transferring new software modules to the node as needed, saving existing configuration information for the old version of software, and configuring the node for operation with the new version of software using the saved configuration information where appropriate. The upgrade method saves a listing of data instances used by the old software, and saves the actual configuration values for those data instances. Then, the upgrade method configures the node for operation with the software by determining which data instances used in the new version of software had corresponding data instances in the old software, and using the saved configuration information for those data instances. For data instances where reuse of prior configuration data is not possible, or is not desired, the method uses default configuration data, which may be supplied in the form of an upgrade configuration file.
Owner:TELEFON AB LM ERICSSON (PUBL)
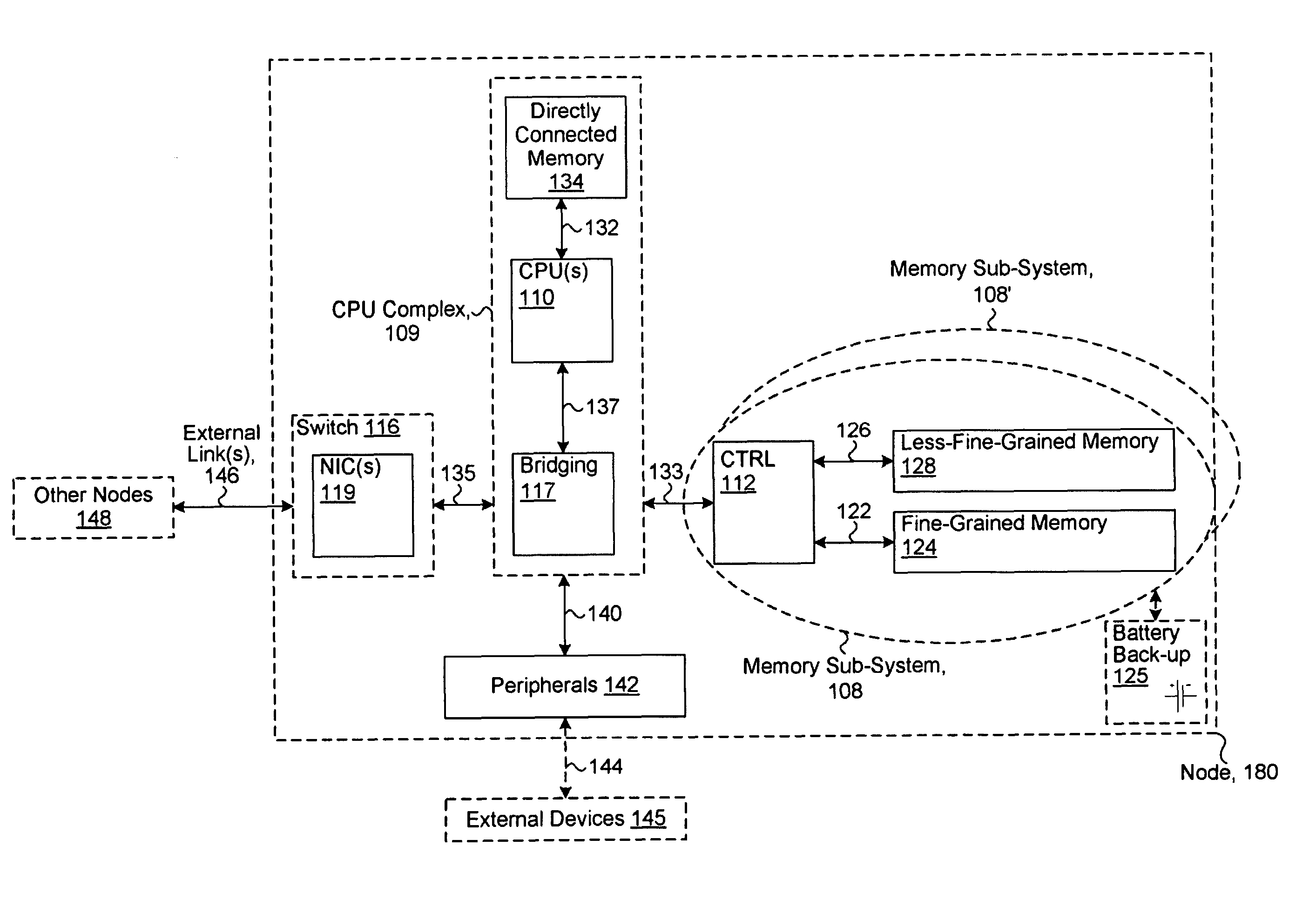
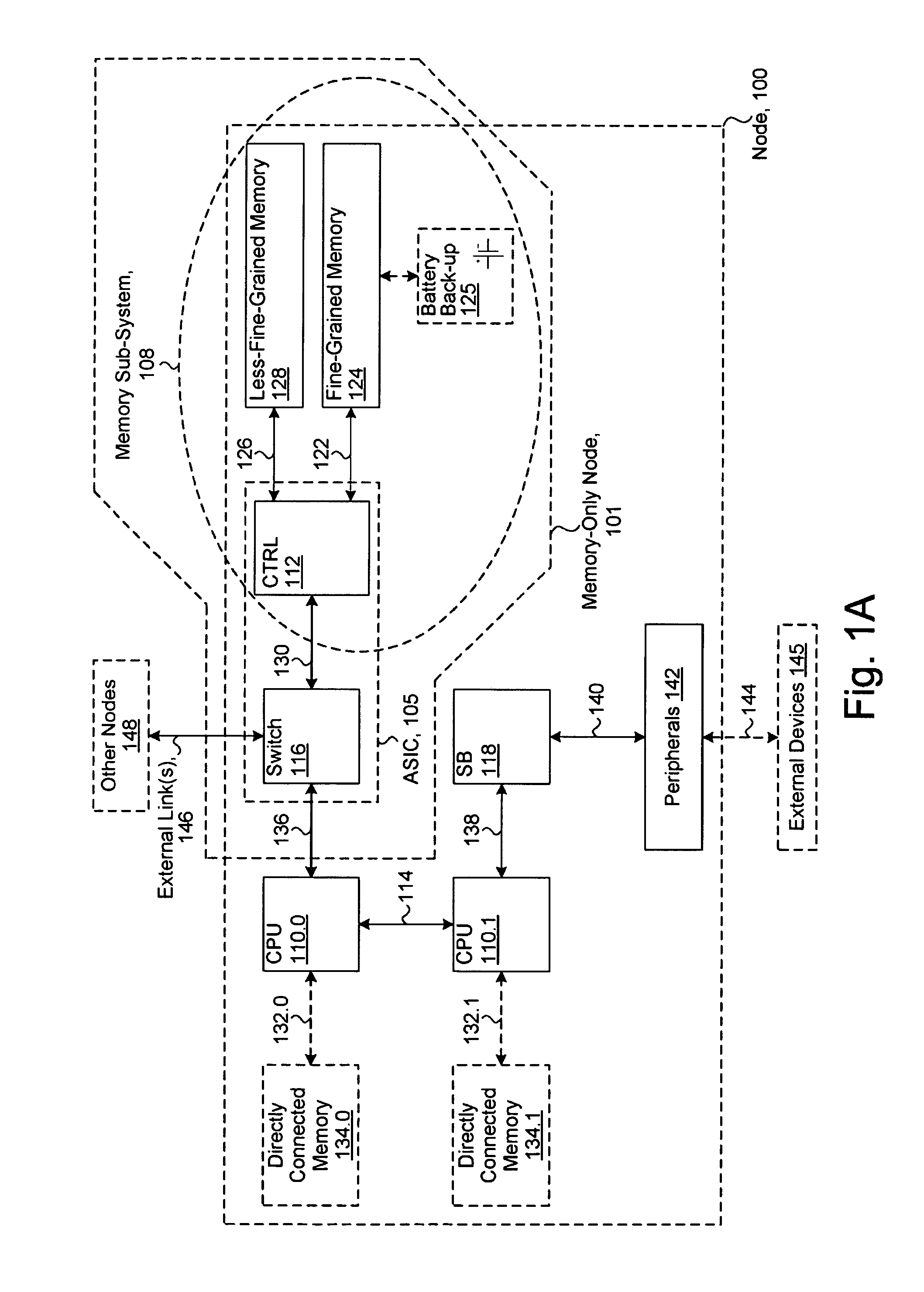
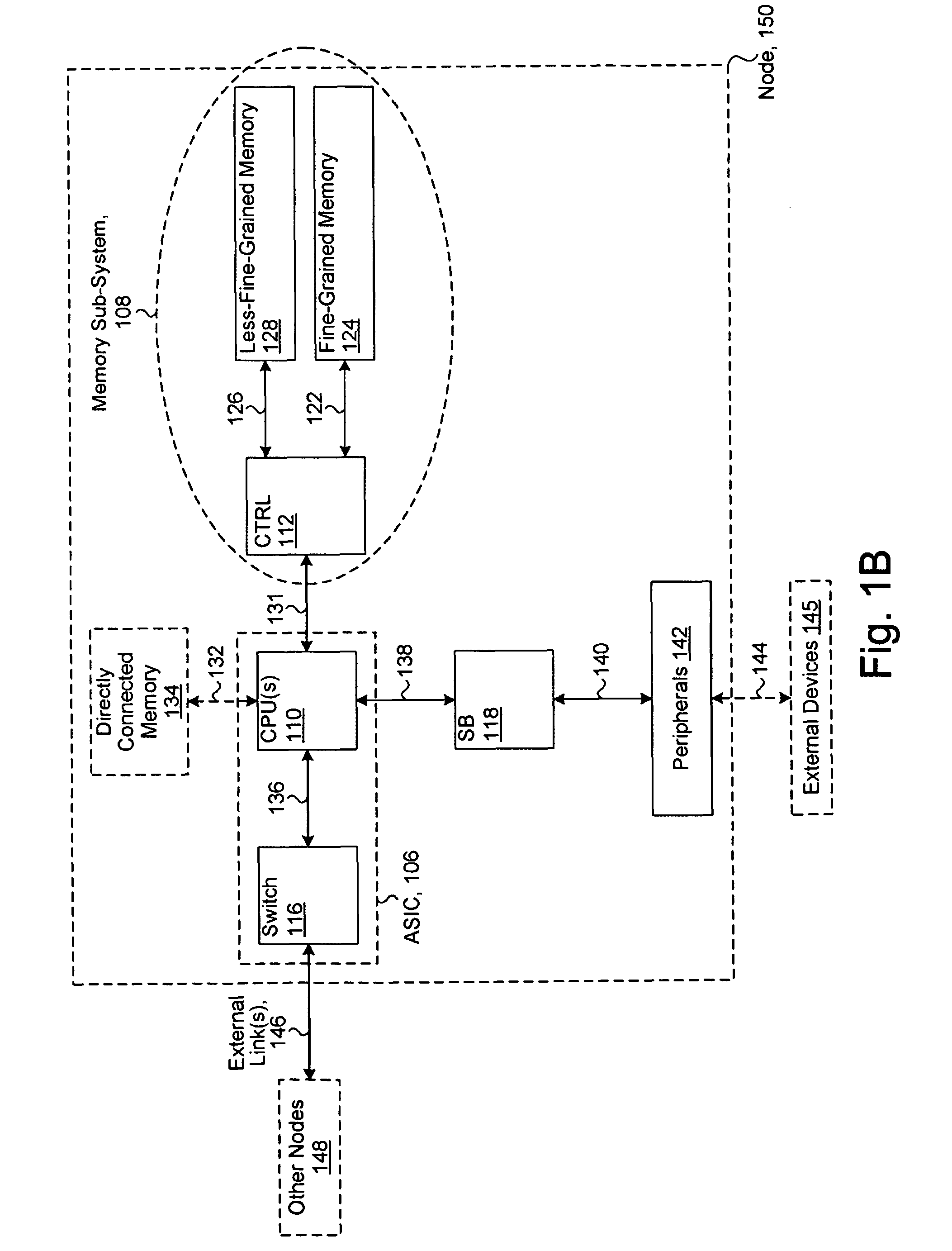
System including a fine-grained memory and a less-fine-grained memory
ActiveUS7975109B2Memory architecture accessing/allocationEnergy efficient ICTData processing systemWrite buffer
A data processing system includes one or more nodes, each node including a memory sub-system. The sub-system includes a fine-grained, memory, and a less-fine-grained (e.g., page-based) memory. The fine-grained memory optionally serves as a cache and / or as a write buffer for the page-based memory. Software executing on the system uses a node address space which enables access to the page-based memories of all nodes. Each node optionally provides ACID memory properties for at least a portion of the space. In at least a portion of the space, memory elements are mapped to locations in the page-based memory. In various embodiments, some of the elements are compressed, the compressed elements are packed into pages, the pages are written into available locations in the page-based memory, and a map maintains an association between the some of the elements and the locations.
Owner:SANDISK TECH LLC
Virtualization with Merged Guest Page Table and Shadow Page Directory
ActiveUS20090300263A1Memory architecture accessing/allocationTransformation of program codeVirtualizationPage table
In a computing system having virtualization software including a guest operating system (OS), a method for providing page tables that includes: providing a guest page table used by the guest OS and a shadow page table and a shadow page directory used by the virtualization software wherein: at least a portion of the guest page table and the shadow page directory are the same; and the portions that are the same are shared in computer memory by the guest page table and the shadow page directory.
Owner:VMWARE INC
Method for testing of software
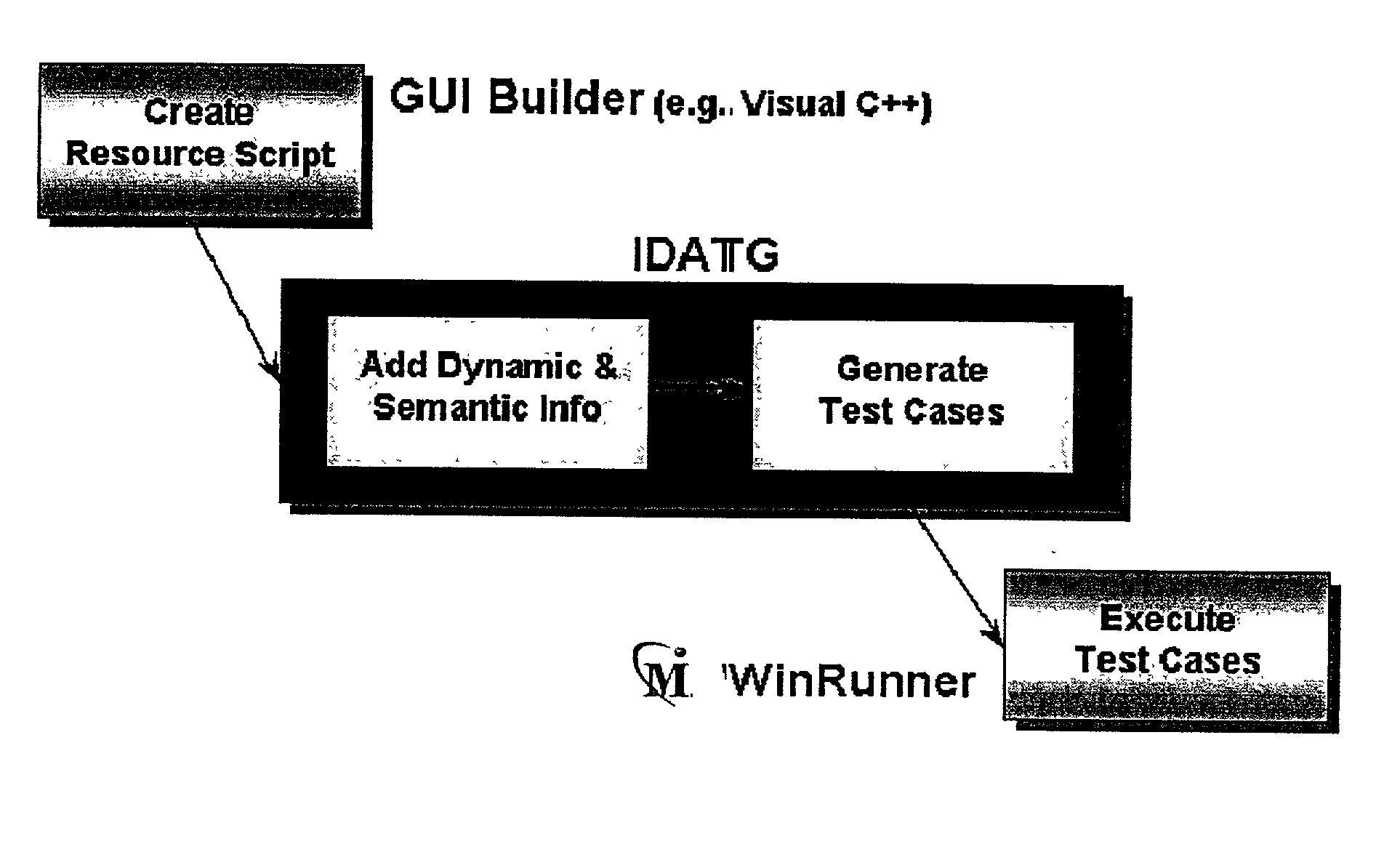
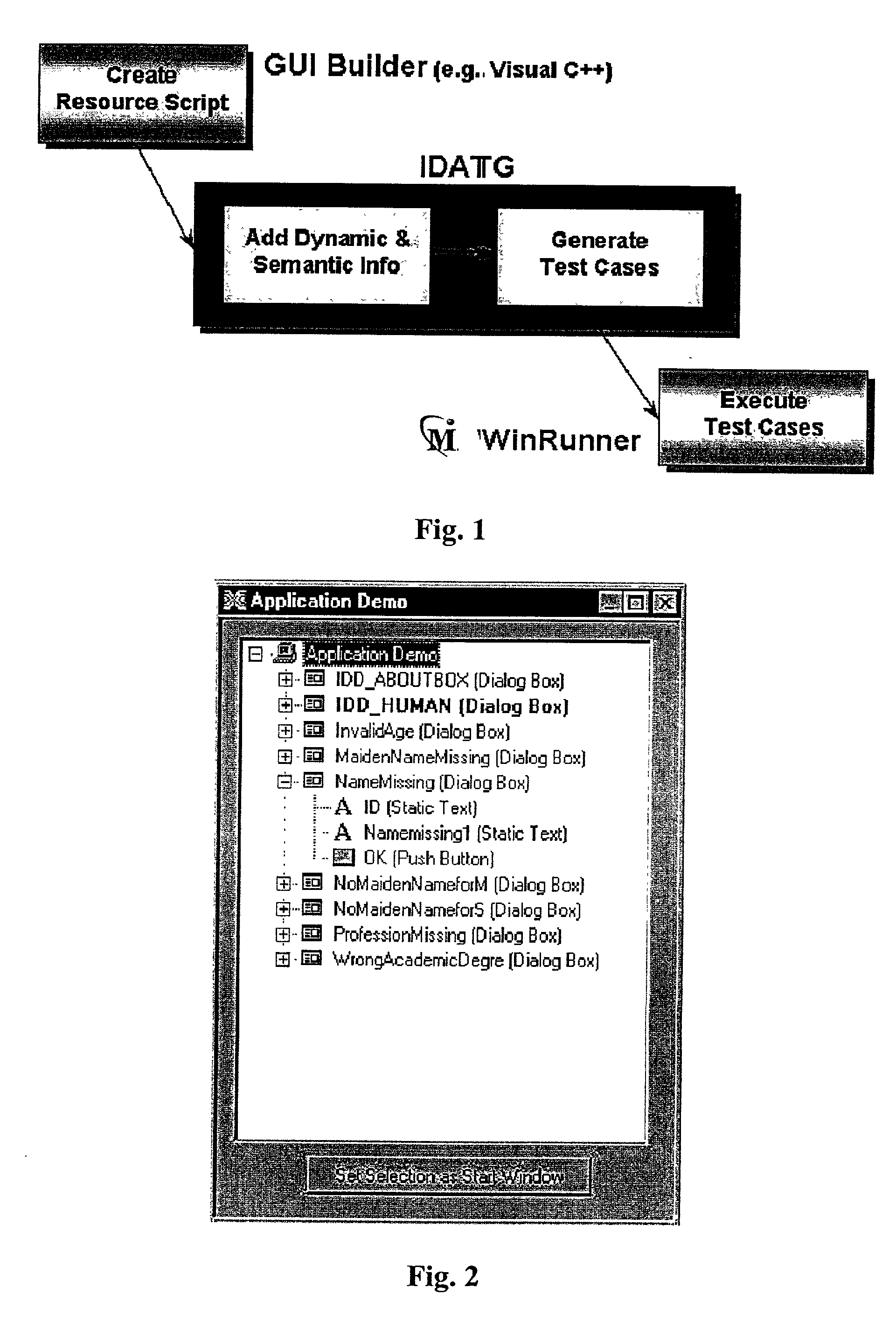
InactiveUS20030005413A1Enable designEnable processSoftware testing/debuggingSpecific program execution arrangementsComputer hardwareGraphics
There is provided a method for the automated testing of software, which has a graphic user interface. With at least one graphic editor, at least the dynamic and the semantic behavior of the user interface of the software is specified. Test cases are generated by a test case generator software using the thus specified behavior of the user interface, which are then executed by a software for automatic running test running either immediately or in a later step.
Owner:SIEMENS AG OESTERR
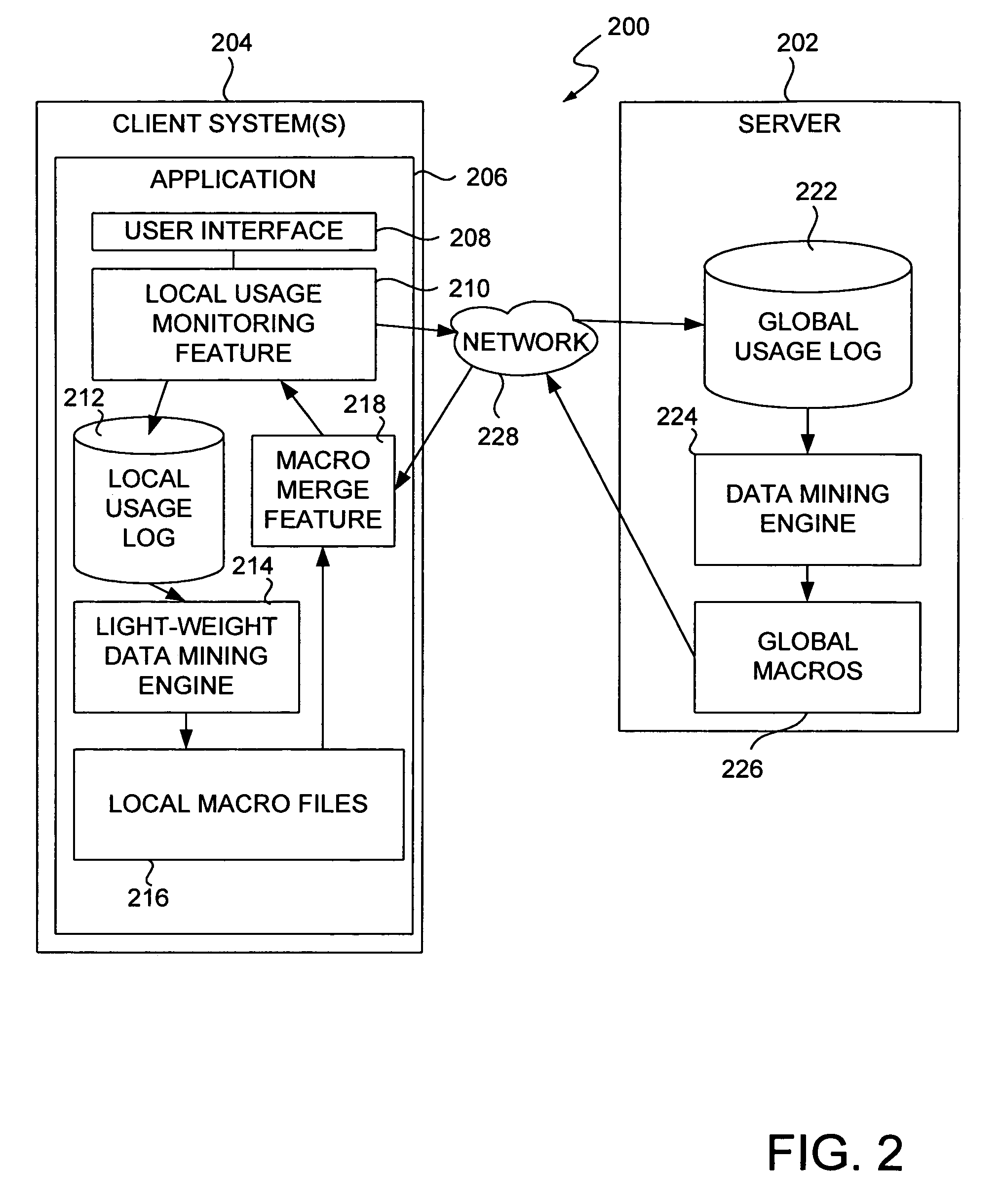
Method and system for tracking client software use
A method and system for tracking client software use is disclosed. User data, specifically user interaction with a client-installed software application, is collected in data files and the data files are dynamically uploaded over a global computer system, such as the Internet, to a remote analysis system. The data files are parsed for on-going analysis of feature usage. Typically, for any action that a user performs in the software application, several items are recorded in a data file, such as a user ID, an absolute time-stamp, the method invoked including application source (if the software application includes more than one application), and details such as the dialog invoked, button pressed, menu used, menu item selected, application launch, application termination, as well as environment variables, such as operating system, screen resolution, etc.
Owner:MICROSOFT TECH LICENSING LLC
Software and/or software information pushing method, system, acquisition device, software shop service system and mobile terminal
InactiveCN101937547AIncrease download rateImprove participationMarketingSpecial data processing applicationsSoftware engineeringComputer terminal
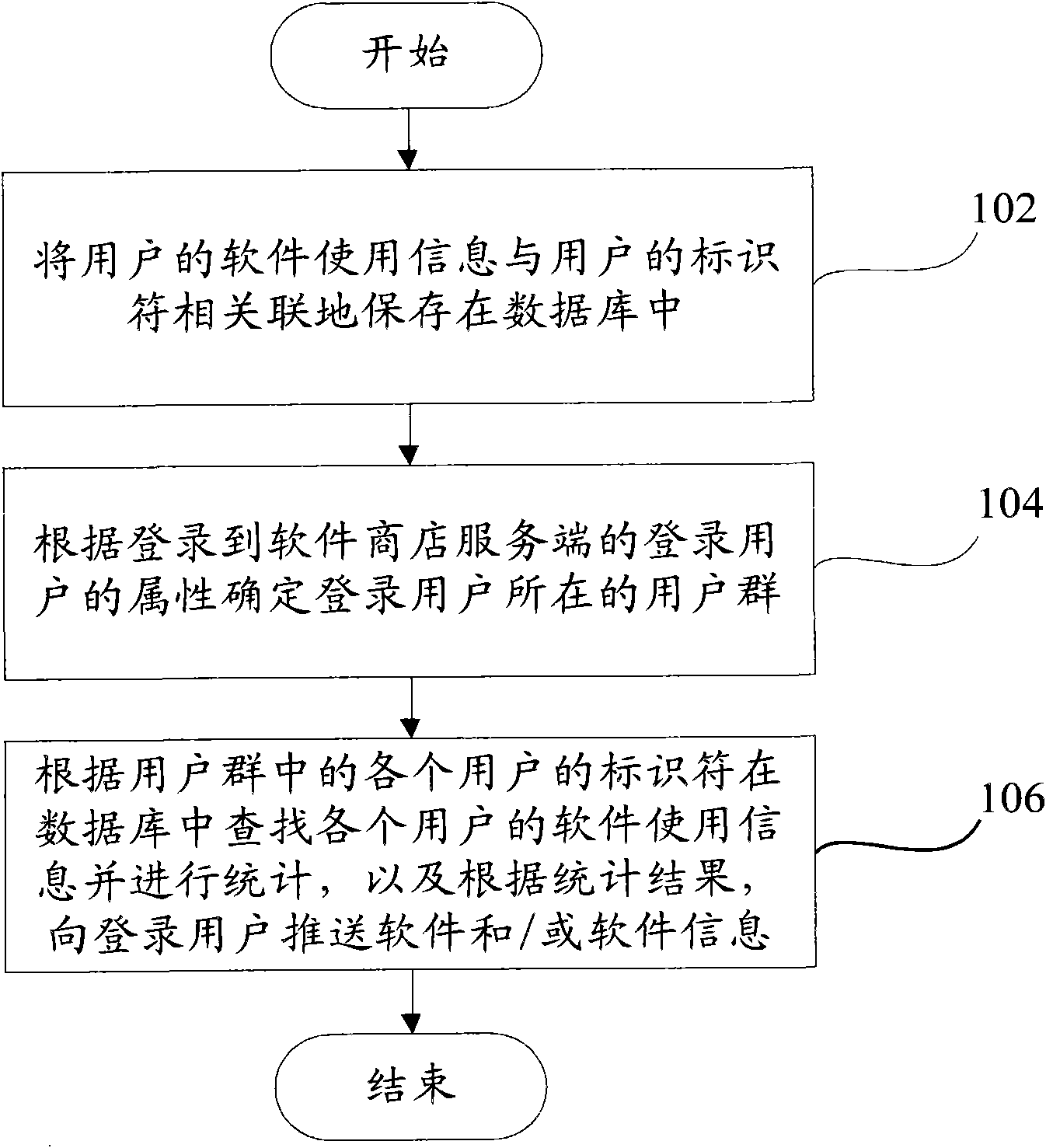
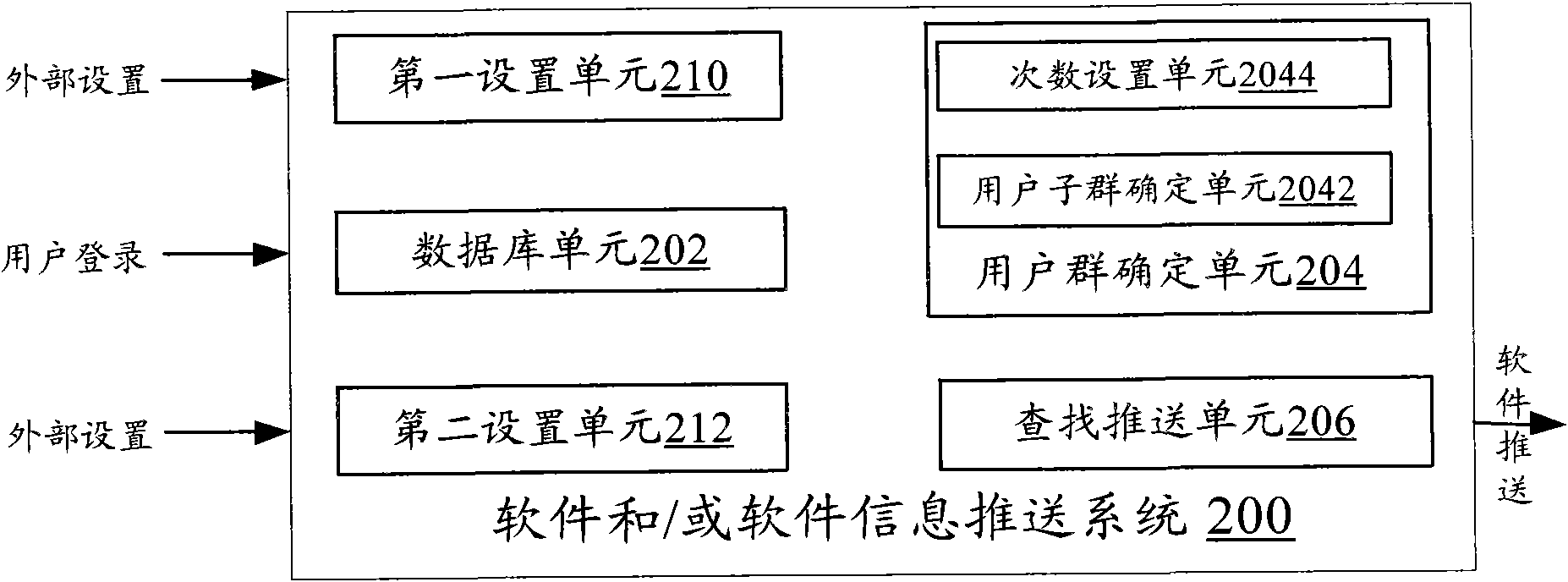
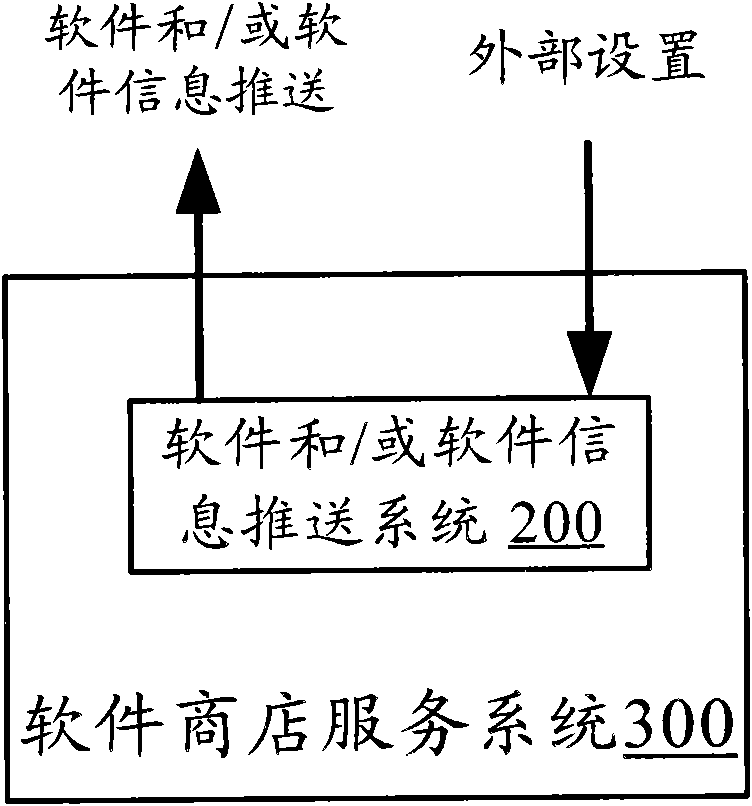
The invention provides a software and / or software information pushing method, comprising the following steps of: 102, associatively storing software use information of a user and an identifier of the user into a database; 104, determining a user group of the user according to the attribute of the user logging in a software shop service end; and 106, searching and counting the software use information of each user in the database according to the identifier of each user in the user group, and pushing the software and / or the software information to the logged user according to a statistical result. According to the provided software and / or software information pushing method, a recommendation principle according to a software category per se or a user category is discarded, the user group for the user is established according to the attribute of the user to form the pushing information to push the software and / or the software information to the user. The invention also provides a software and / or software information pushing system, a software shop service system comprising the system, a software and / or software information acquisition device and a mobile terminal with the device.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
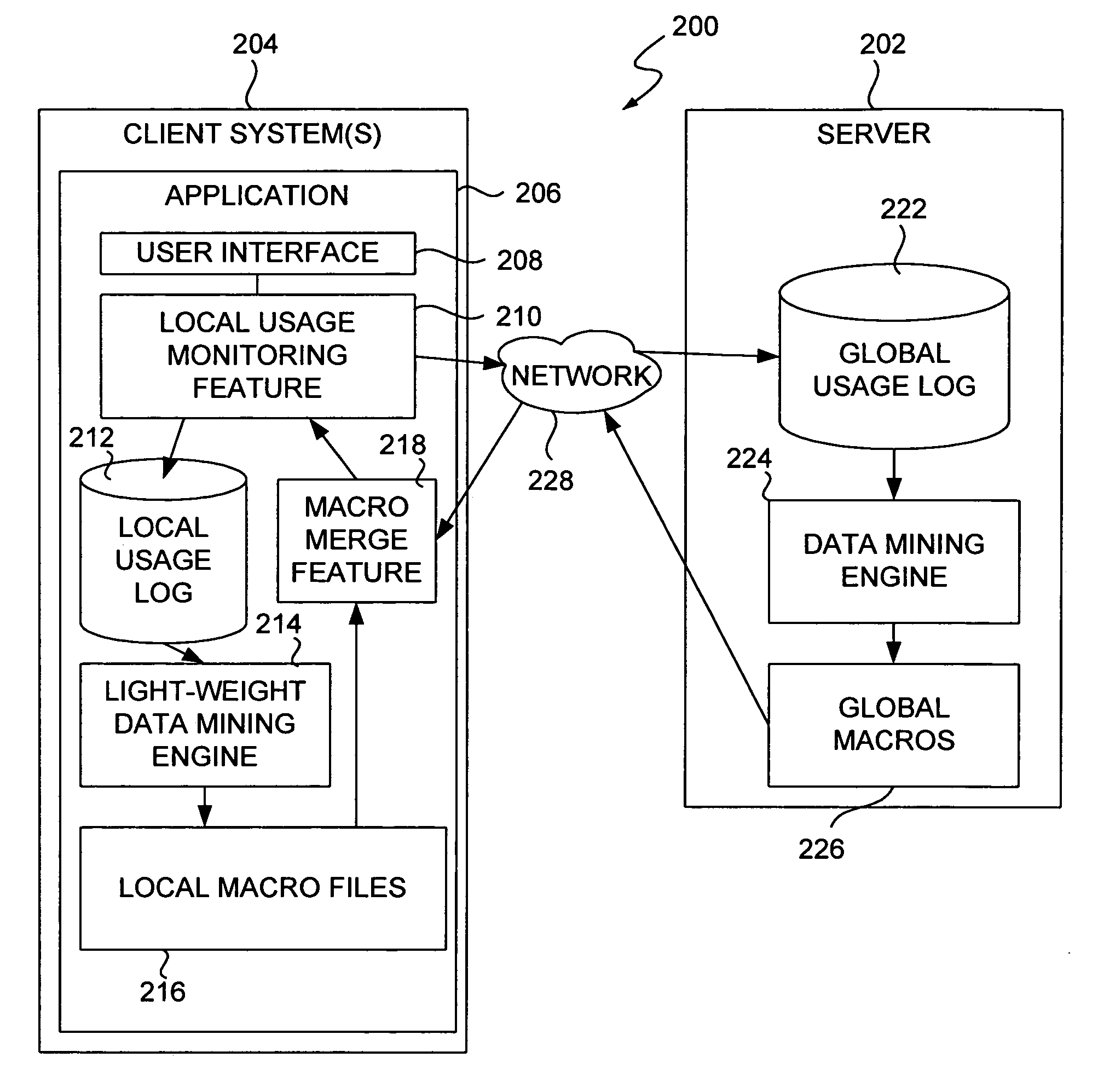
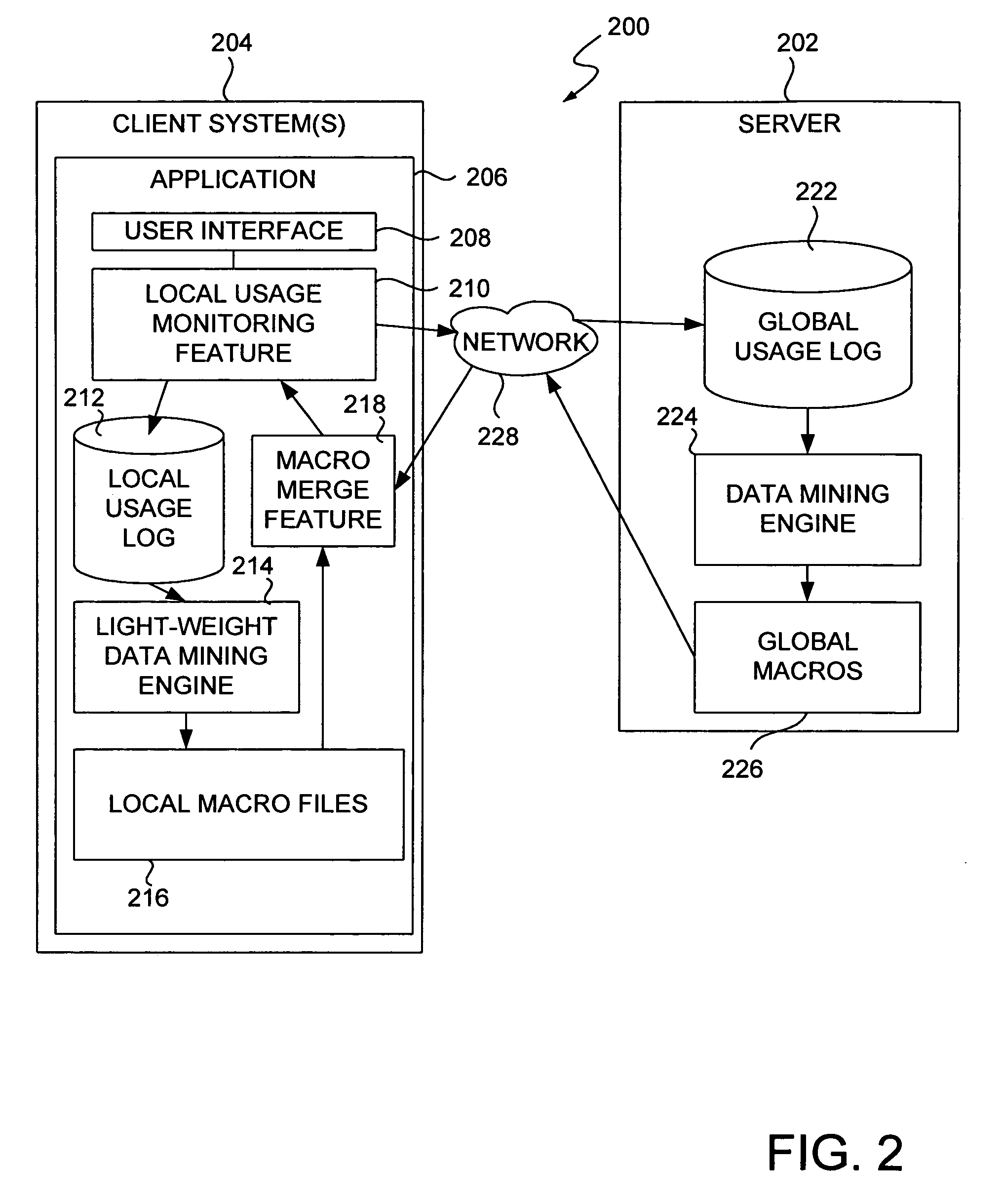
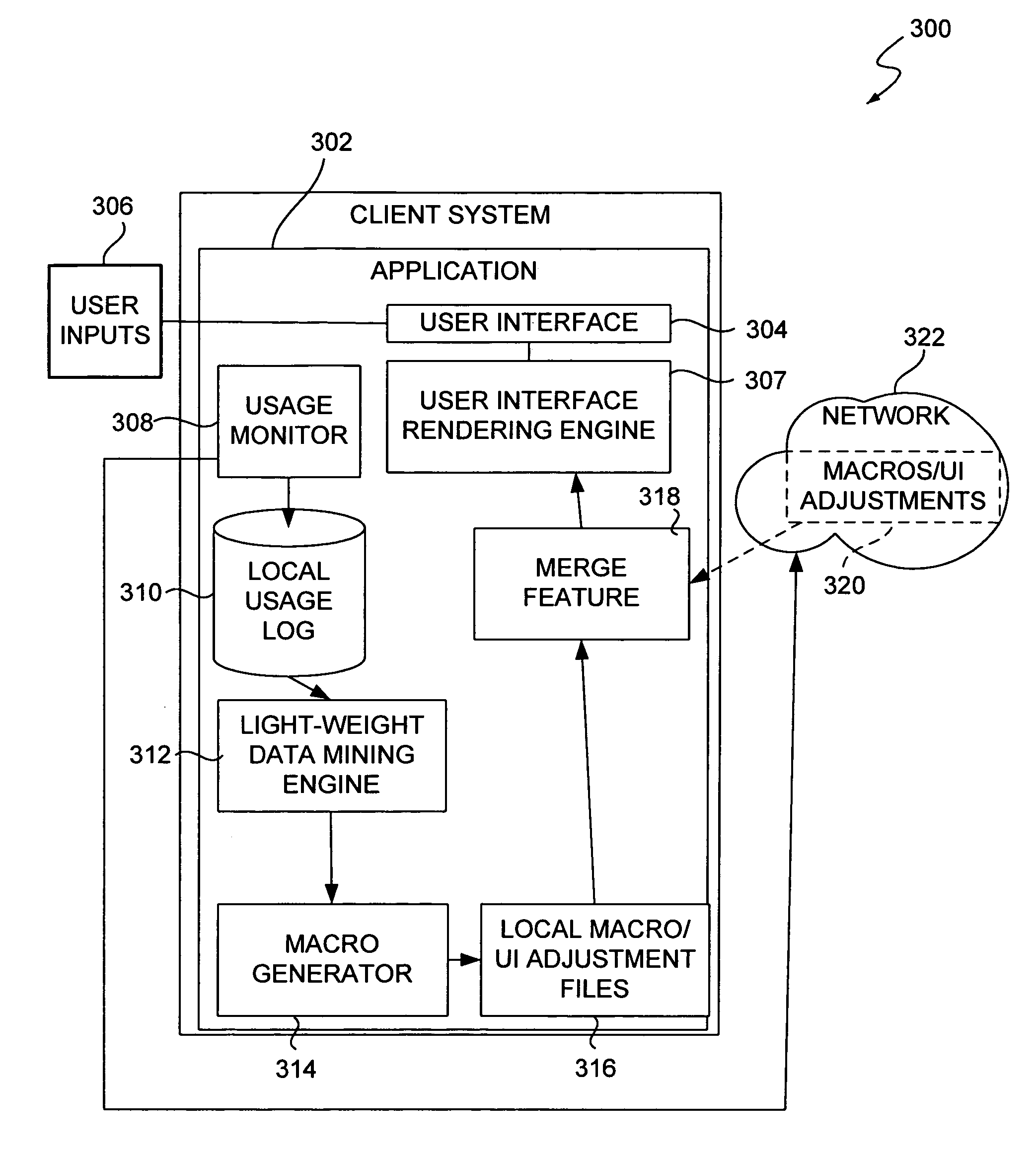
Adaptive systems and methods for making software easy to use via software usage mining
A system for dynamically updating user accessible features of a software application on a client computer has a user interface, a local usage data file, and a data mining engine. The user interface is adapted to receive operator inputs. The local usage data file is adapted to store usage information corresponding to the operator inputs. The data mining engine is adapted to process the stored usage information and to generate local adjustments to a user interface of the software application based on the operator inputs. In one embodiment, a server is adapted to receive usage data from a plurality of application instances on a plurality of client computers and to generate global adjustments based on the received usage data. In one embodiment, the system has a merge feature adapted to blend and resolve conflicts between local and global adjustments to generate an interface adjustment for the user interface.
Owner:MICROSOFT TECH LICENSING LLC
Software license brokering within a cloud computing environment
InactiveUS20110251937A1Complete banking machinesDigital data processing detailsPaymentSoftware license
Under embodiments of the present invention, a set (at least one) of Clouds, a set of software providers, and a set of Cloud consumers (hereinafter “consumers”) are registered with a Cloud software license broker (hereinafter “broker”). Consumer information will be matched with the set of software providers to determine applicable licenses as well as pricing and usage rates. Use of software within the set of Clouds by the set of Cloud consumers will be tracked, aggregated, and reported. Based on the use, a licensing arrangement (including a price) will be determined. Applicable amounts will then be billed, and payments will be collected and disbursed (e.g., to the set of software providers) in accordance with the licensing arrangements. Under the present invention, prices / amounts can be determined based on a per use / on-demand of software and / or based on use of the software over an interval of time (e.g., interval-based pricing).
Owner:IBM CORP
Adaptive systems and methods for making software easy to use via software usage mining
A system for dynamically updating user accessible features of a software application on a client computer has a user interface, a local usage data file, and a data mining engine. The user interface is adapted to receive operator inputs. The local usage data file is adapted to store usage information corresponding to the operator inputs. The data mining engine is adapted to process the stored usage information and to generate local adjustments to a user interface of the software application based on the operator inputs. In one embodiment, a server is adapted to receive usage data from a plurality of application instances on a plurality of client computers and to generate global adjustments based on the received usage data. In one embodiment, the system has a merge feature adapted to blend and resolve conflicts between local and global adjustments to generate an interface adjustment for the user interface.
Owner:MICROSOFT TECH LICENSING LLC
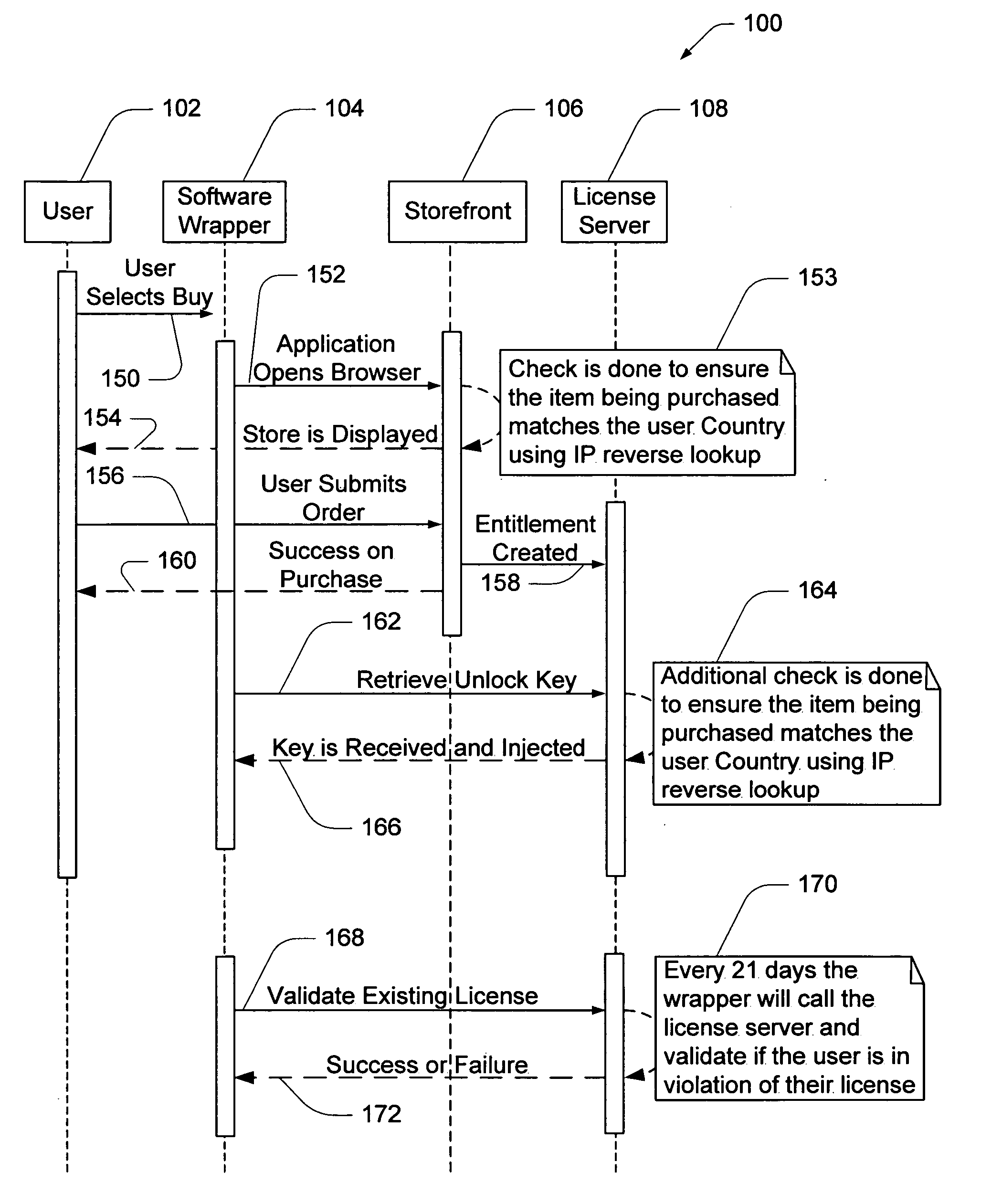
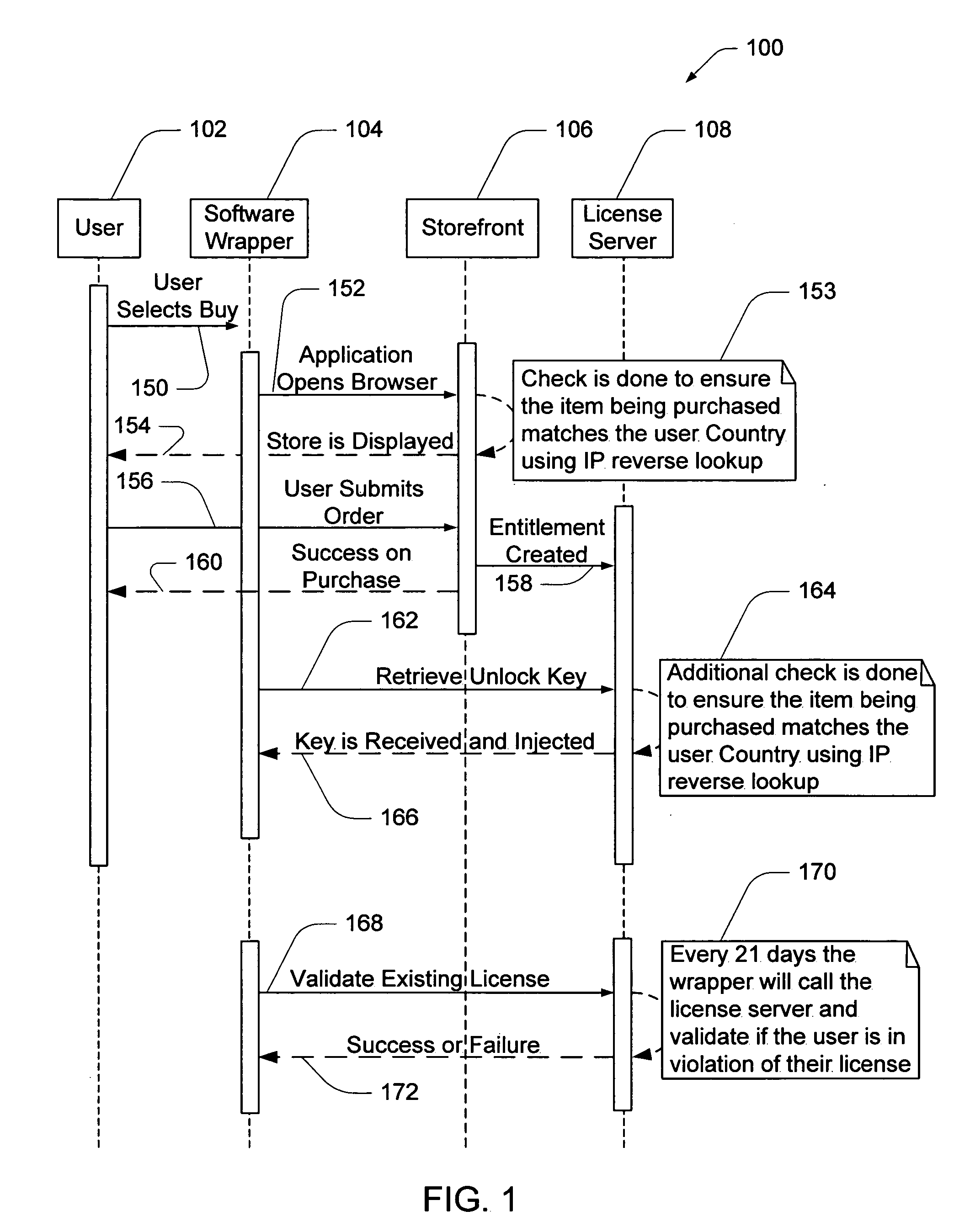
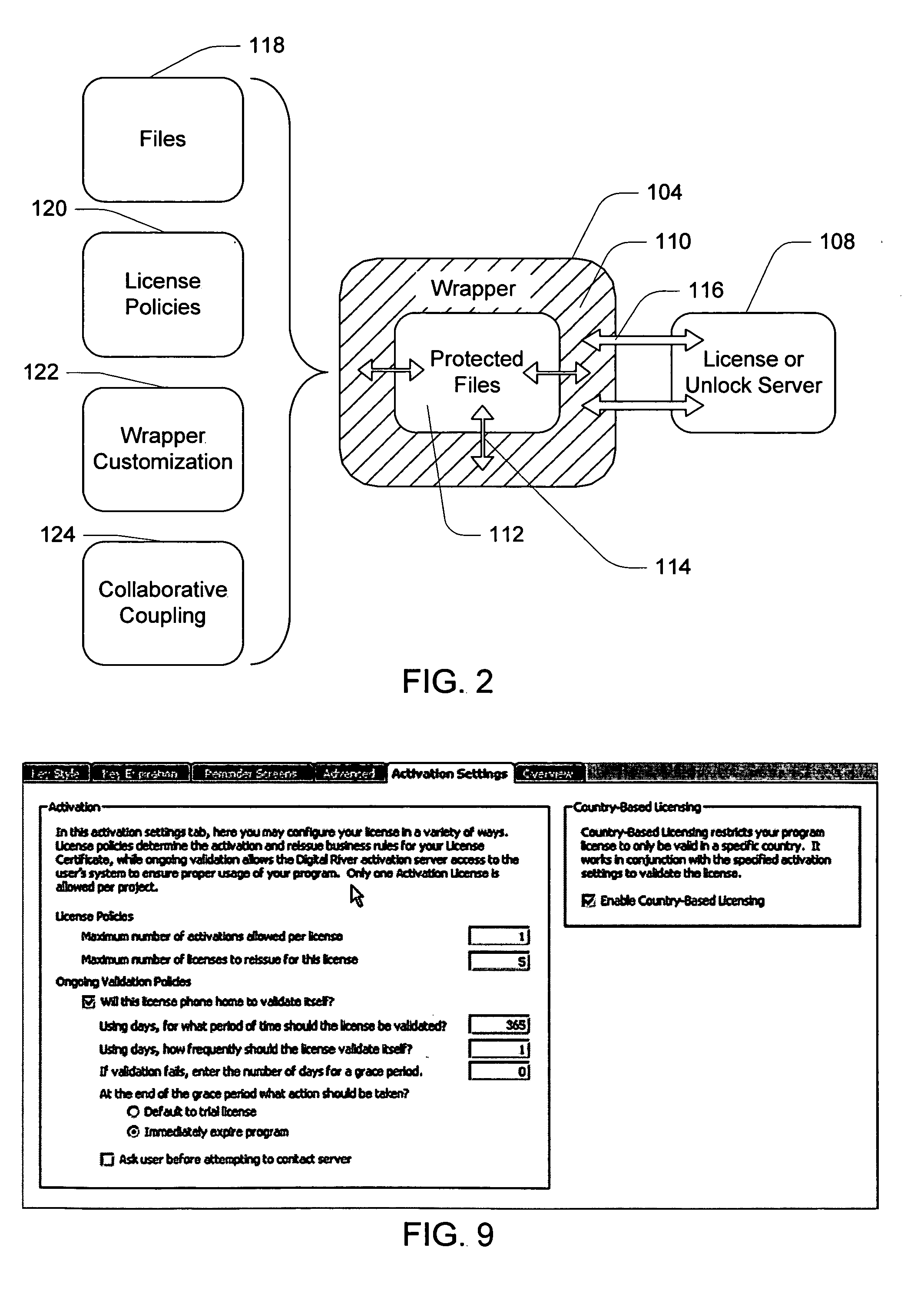
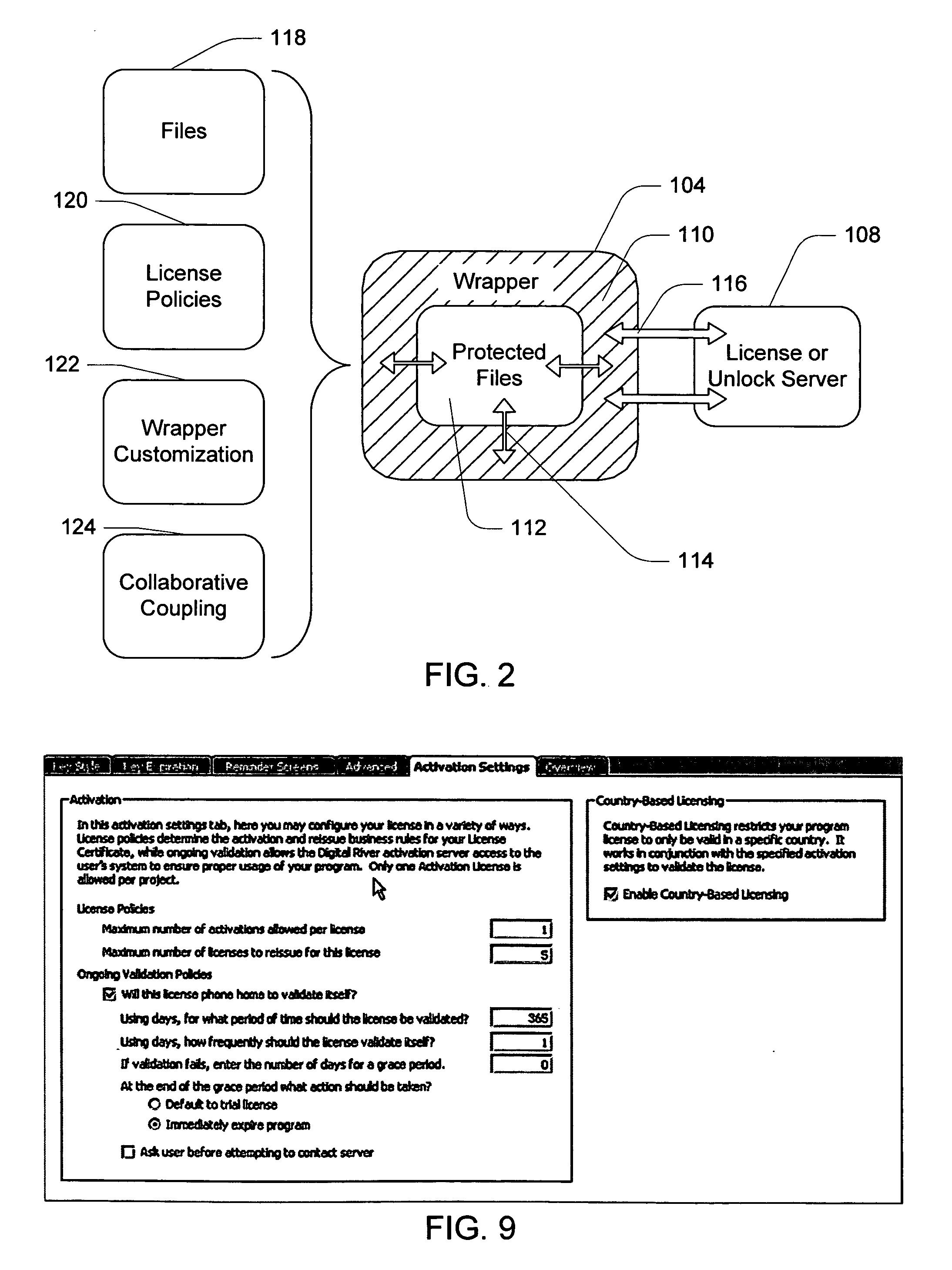
Software wrapper having use limitation within a geographic boundary
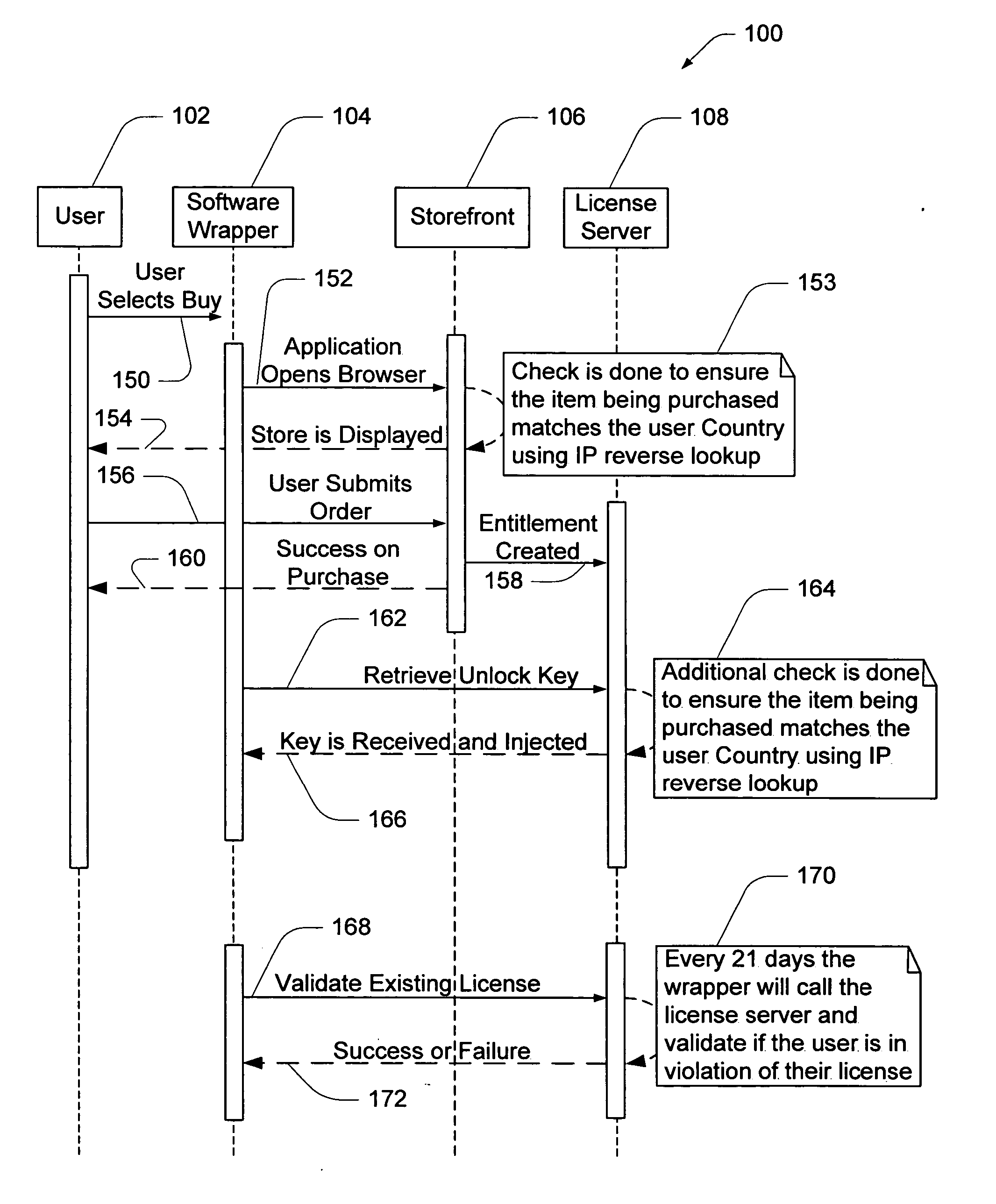
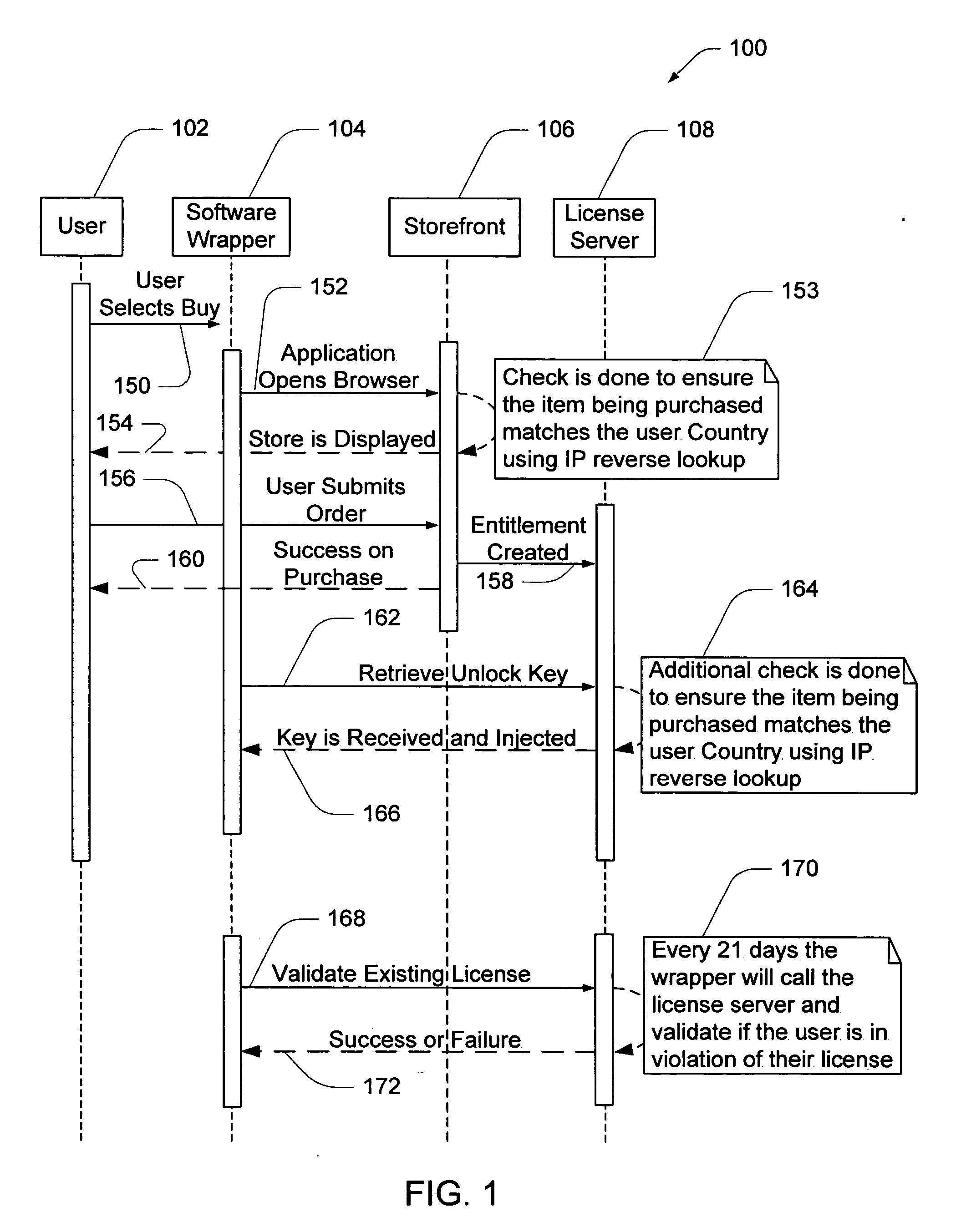
ActiveUS20060059099A1Payment architectureProgram/content distribution protectionSecurity softwareSoftware license
A computer software license management system wrapper for use in a local computer is described. The software wrapper includes a wrapper interface that provides controlled access to a computer software application file. The software application file is encapsulated by security software code to protect it from unauthorized access. The software wrapper also includes a software license key identifying a license policy specifying a use limitation within a geographic boundary. In addition, the software wrapper includes a license validation mechanism that periodically determines compliance with the license policy. The license validation mechanism permits access by another process operating on the local computer through the wrapper interface in response to a valid license confirmation signal received from the license server. A license server that utilizes and an electronic storefront that sells software license wrappers having software use limitations within a geographic boundary also are described.
Owner:DIGITAL RIVER INC
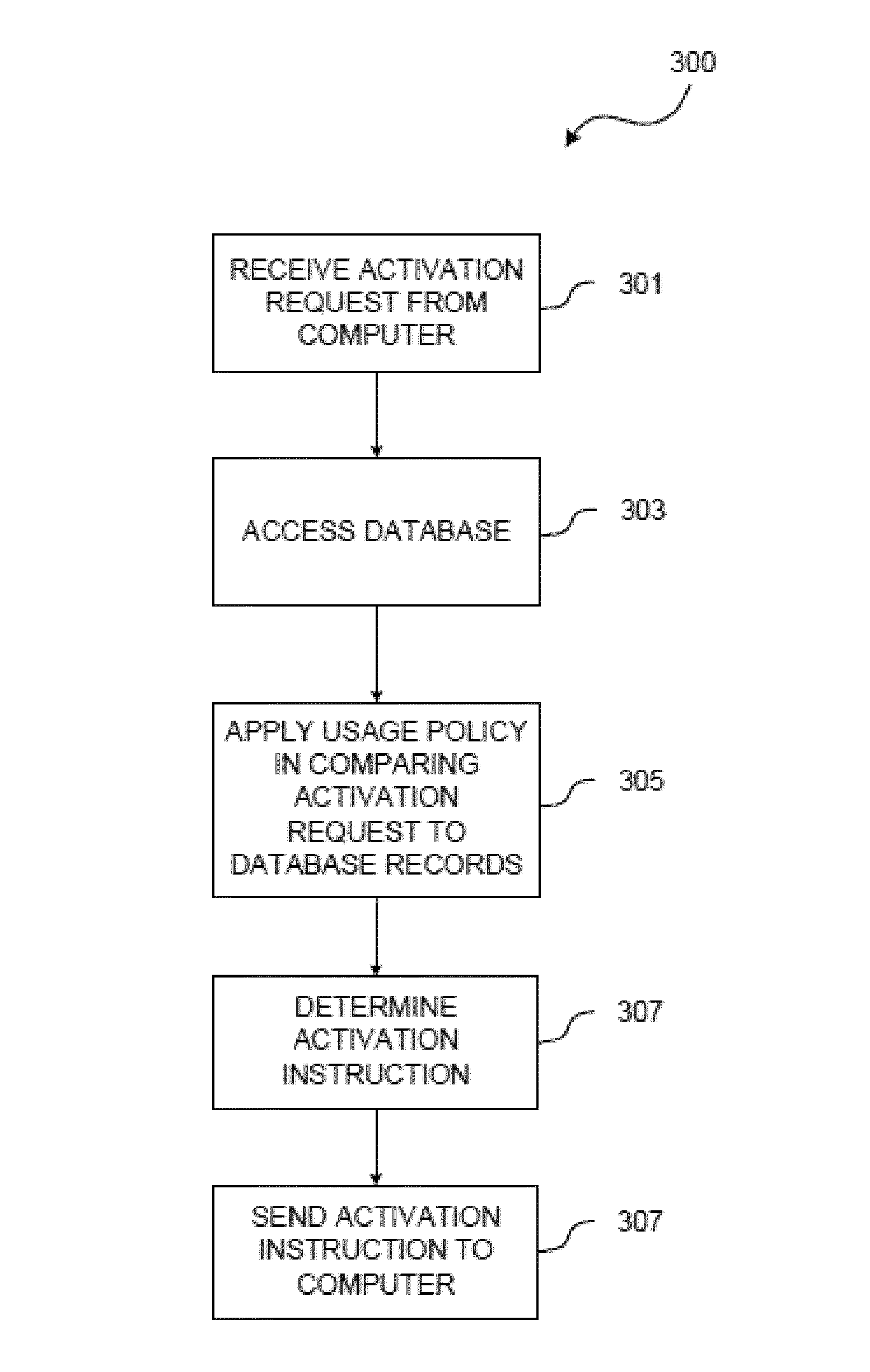
System and Method for Software Activation
InactiveUS20100325735A1Increase the number ofReduce in quantityDigital data processing detailsAnalogue secracy/subscription systemsTelecommunications linkCommunication link
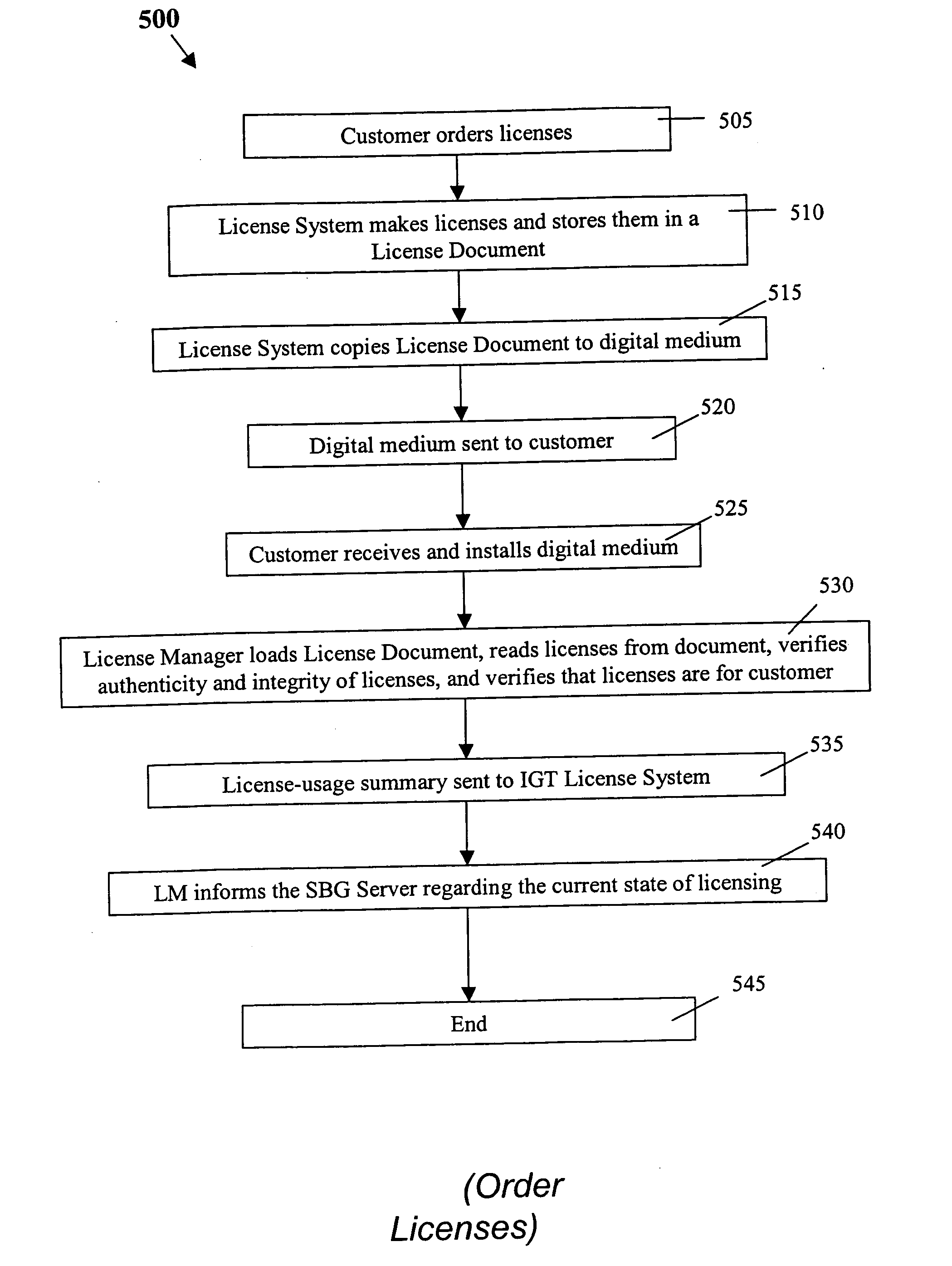
A system and related method for activating use of software on a computing device utilizes a license server configured so that, responsive to a communication link being available between the license server and the computing device, the license server receives from the computing device, via the communication link, an activation request including (a) a software identifier identifying the software, (b) a device identifier identifying the computer, and (c) a license key for the software, accesses a database storing previously received software identifiers, device identifiers, and license keys, determines an activation instruction through application of a usage policy that compares the activation request to records within the database, and sends the activation instruction to the computing device.
Owner:UNILOC LUXEMBOURG
Detection device and method for security vulnerability of software
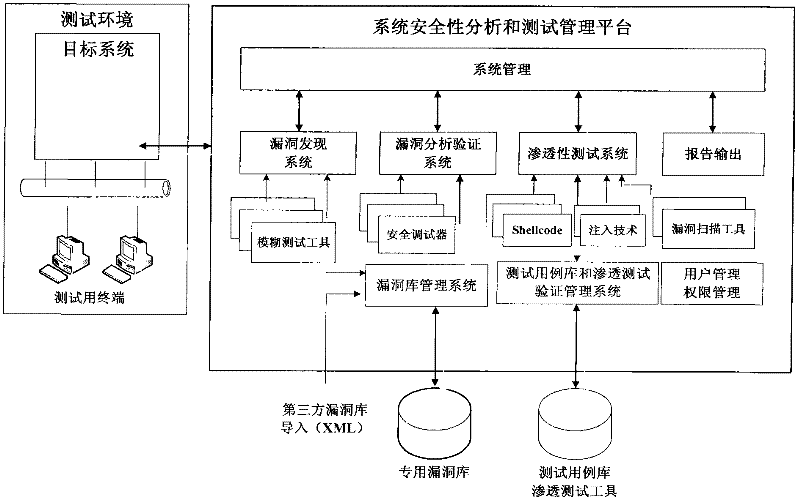
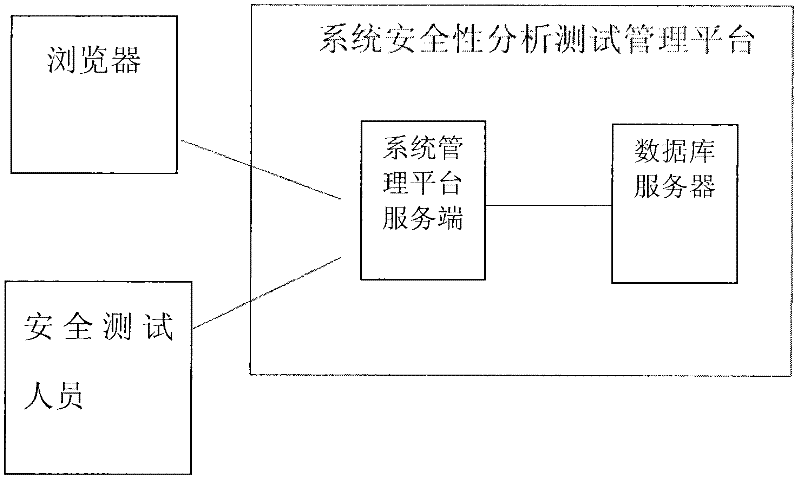
InactiveCN102541729ASatisfy attentionImprove use valueSoftware testing/debuggingSystems managementGoal system
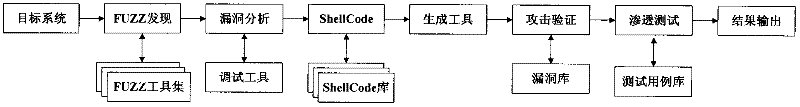
The invention relates to the field of computers, in particular to a detection device and method for a security vulnerability of a dedicated information system. According to the detection device and method disclosed by the invention, a tester can not only access a target system to a testing network but also access the detection device to a production system by connecting a test terminal with the target system, wherein the target system is located in the production system. As the core of the detection device, a system security analysis and test management platform comprises a vulnerability discovering system, a vulnerability authenticating and analyzing system, a permeability testing system, a vulnerability library, a test case library, a report outputting system, a user and permission management system, a system management platform and the like. When the detection device and method for the security vulnerability of the software, provided by the invention, are adopted, the vulnerability can be found before the application of the software, and corresponding strategies can be provided, so that the detection device and method meet the requirement on the emphasis on information security in the current society in a better manner; and moreover, the detection device and method have a higher application value.
Owner:AVIATION IND INFORMATION CENT
Process, system, method creating medical billing code letters, electronic superbill and communication
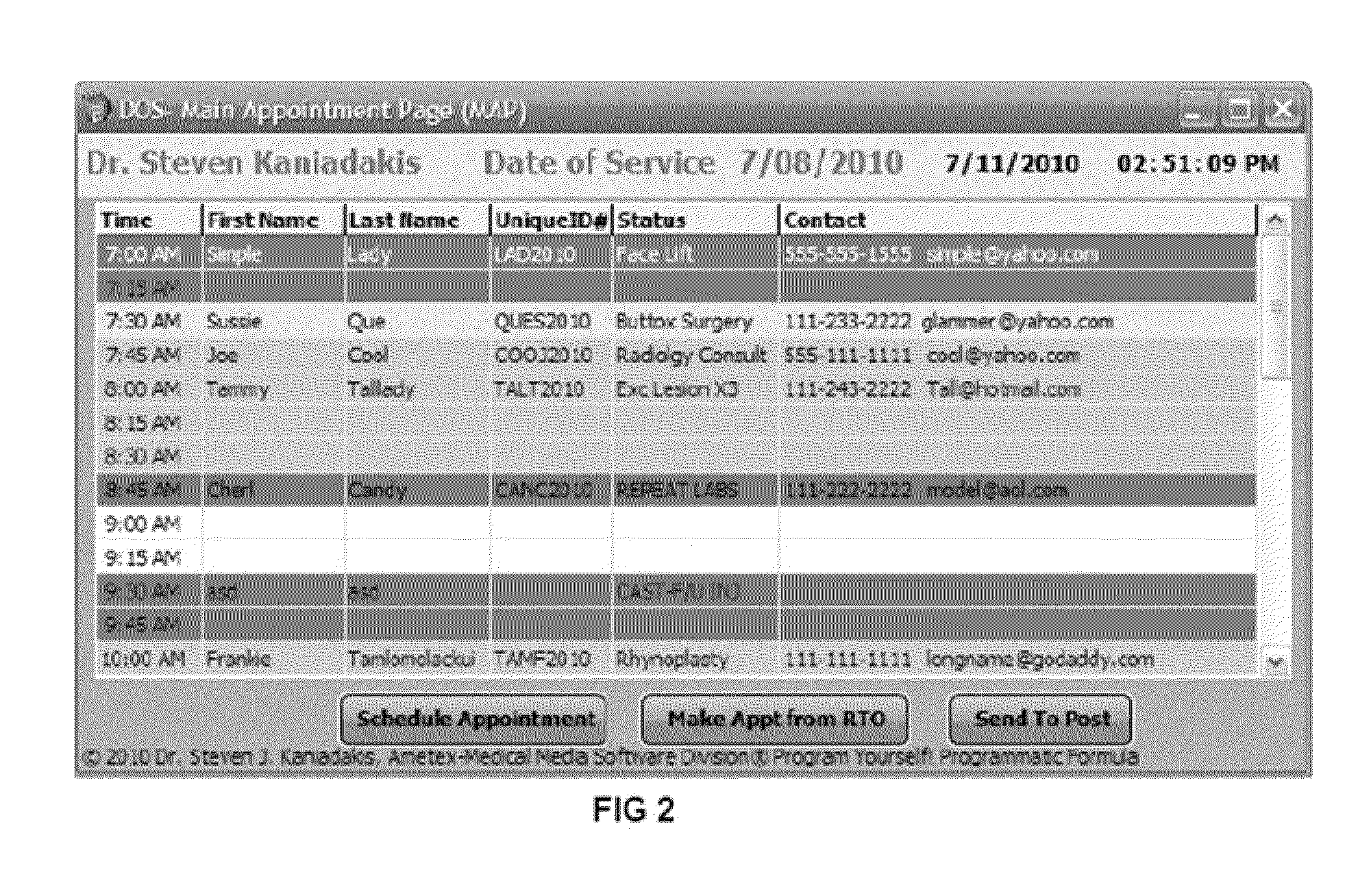
ActiveUS20120010900A1Easy to rememberImprove recallCharacter and pattern recognitionMultiple digital computer combinationsMedical recordApplication software
This invention is a method, system and process creating a machine readable language of medical billing codes from medical records by artificial intelligence and human intelligence both. The software related engine is achieved by converting difficult billing code numbers into and from easy code letters. Also, this software makes scheduling easier, with reappointments and sends letters by electronic means, messaging, voice over internet protocol and wireless connections using an unique implementation of other applications in combination with this novel medical software operation.
Owner:KANIADAKIS STEVEN J
Software license server with geographic location validation
ActiveUS20060059100A1Payment architectureProgram/content distribution protectionGeographic siteSecurity software
A computer software license management system wrapper for use in a local computer is described. The software wrapper includes a wrapper interface that provides controlled access to a computer software application file. The software application file is encapsulated by security software code to protect it from unauthorized access. The software wrapper also includes a software license key identifying a license policy specifying a use limitation within a geographic boundary. In addition, the software wrapper includes a license validation mechanism that periodically determines compliance with the license policy. The license validation mechanism permits access by another process operating on the local computer through the wrapper interface in response to a valid license confirmation signal received from the license server. A license server that utilizes and an electronic storefront that sells software license wrappers having software use limitations within a geographic boundary also are described.
Owner:DIGITAL RIVER INC
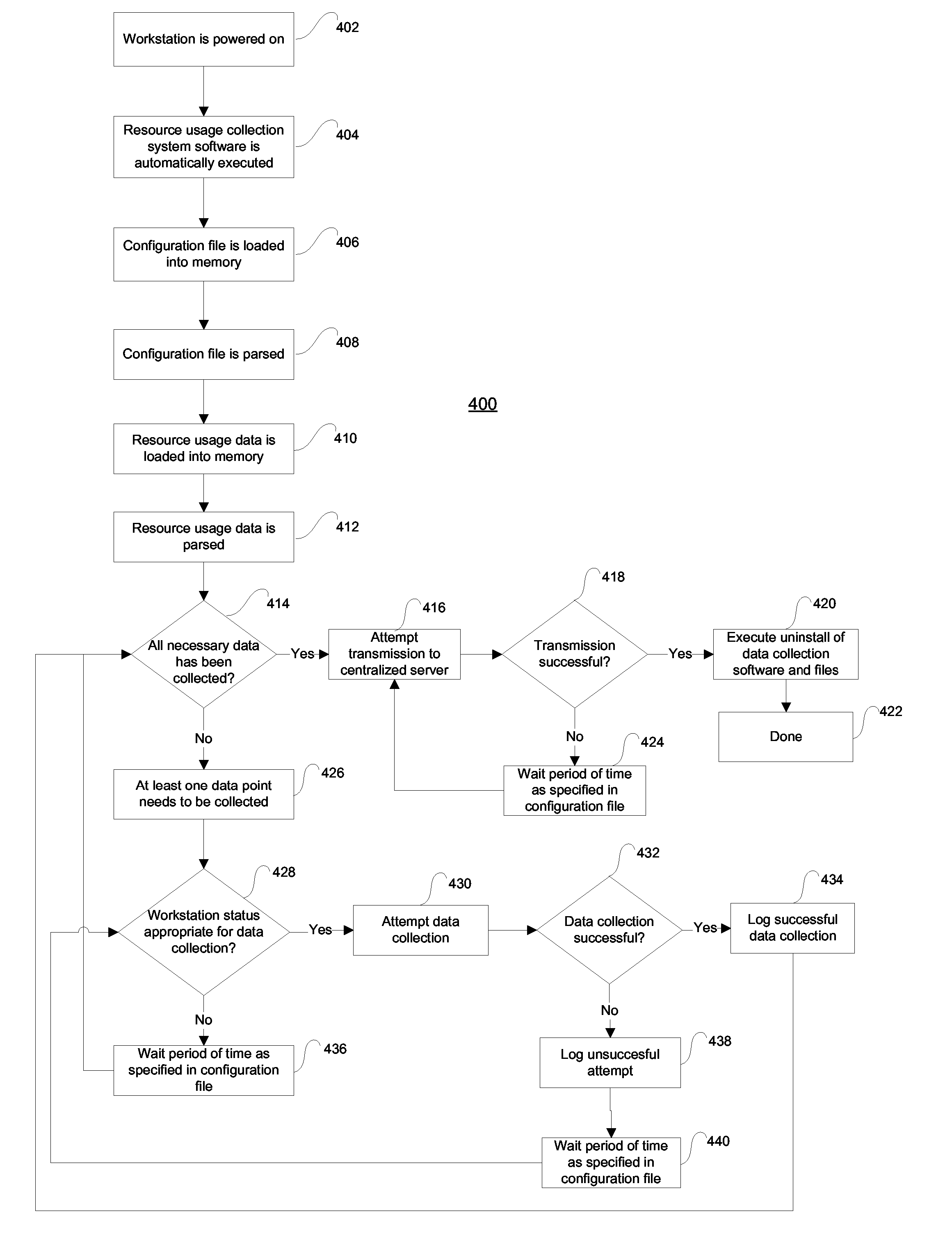
Computer workstation resource usage monitoring system
InactiveUS20060112375A1Error detection/correctionDigital computer detailsComputer resourcesOperational system
A configurable computer resource usage system for collecting hardware and software usage from computer systems with various operating systems, aggregating and filtering the data, transferring it to a centralized computer system, and performing analysis to determine if a hardware or software upgrade is needed. A computer software product that executes on a client computer workstation and collects performance data relevant to that specific machine and data indicating the versions of software and hardware components installed on that machine. A centralized computer that receives the performance and versioning data, stores it, aggregates it with other static data, and performs analysis to determine if the client computer is an upgrade candidate. A graphical user interface displaying the analysis and relevant summarized data is provided through one of several methods, including a web browser accessing the data over the Internet or LAN or WAN.
Owner:SCHNEIDER JOHN ROGER
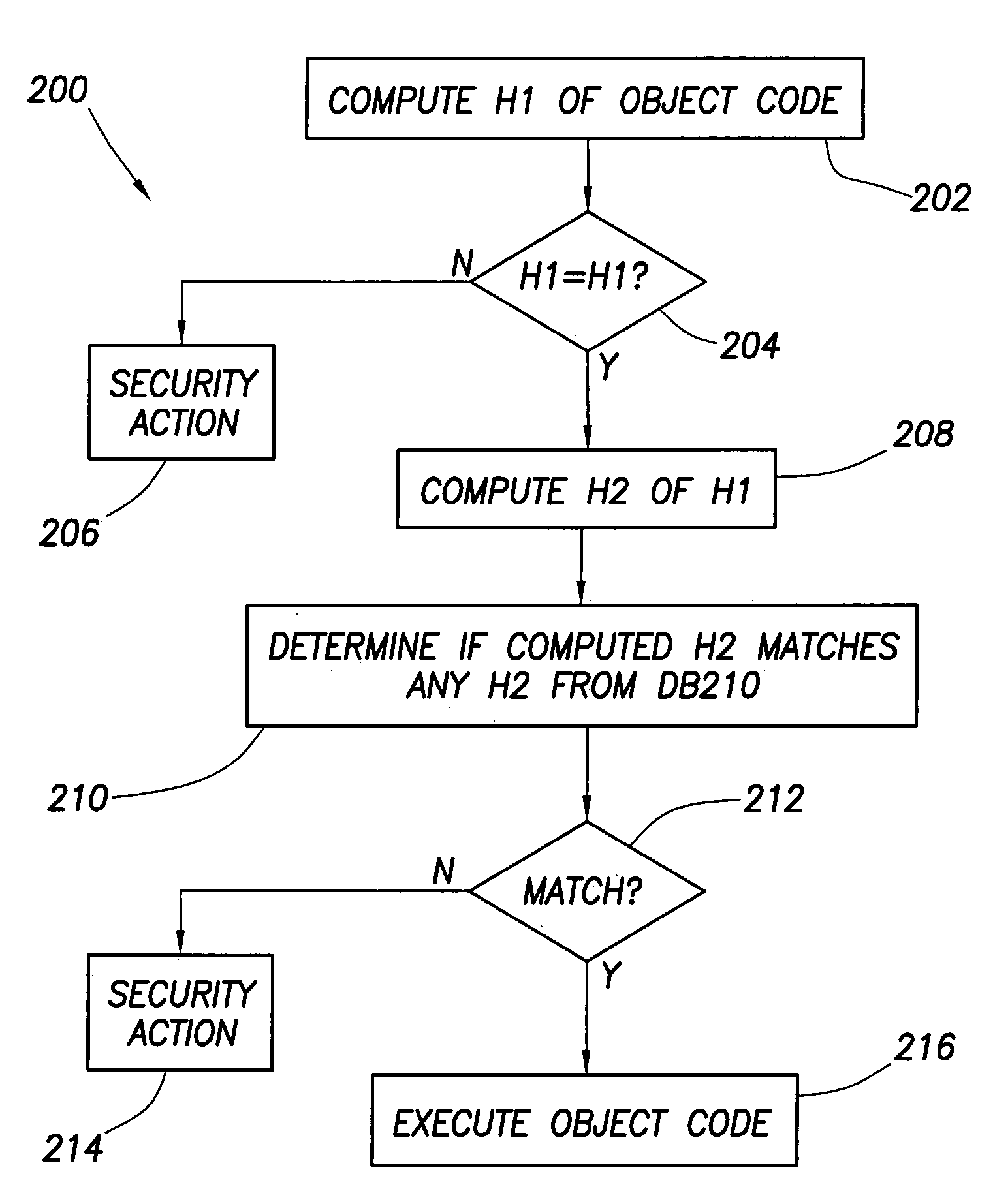
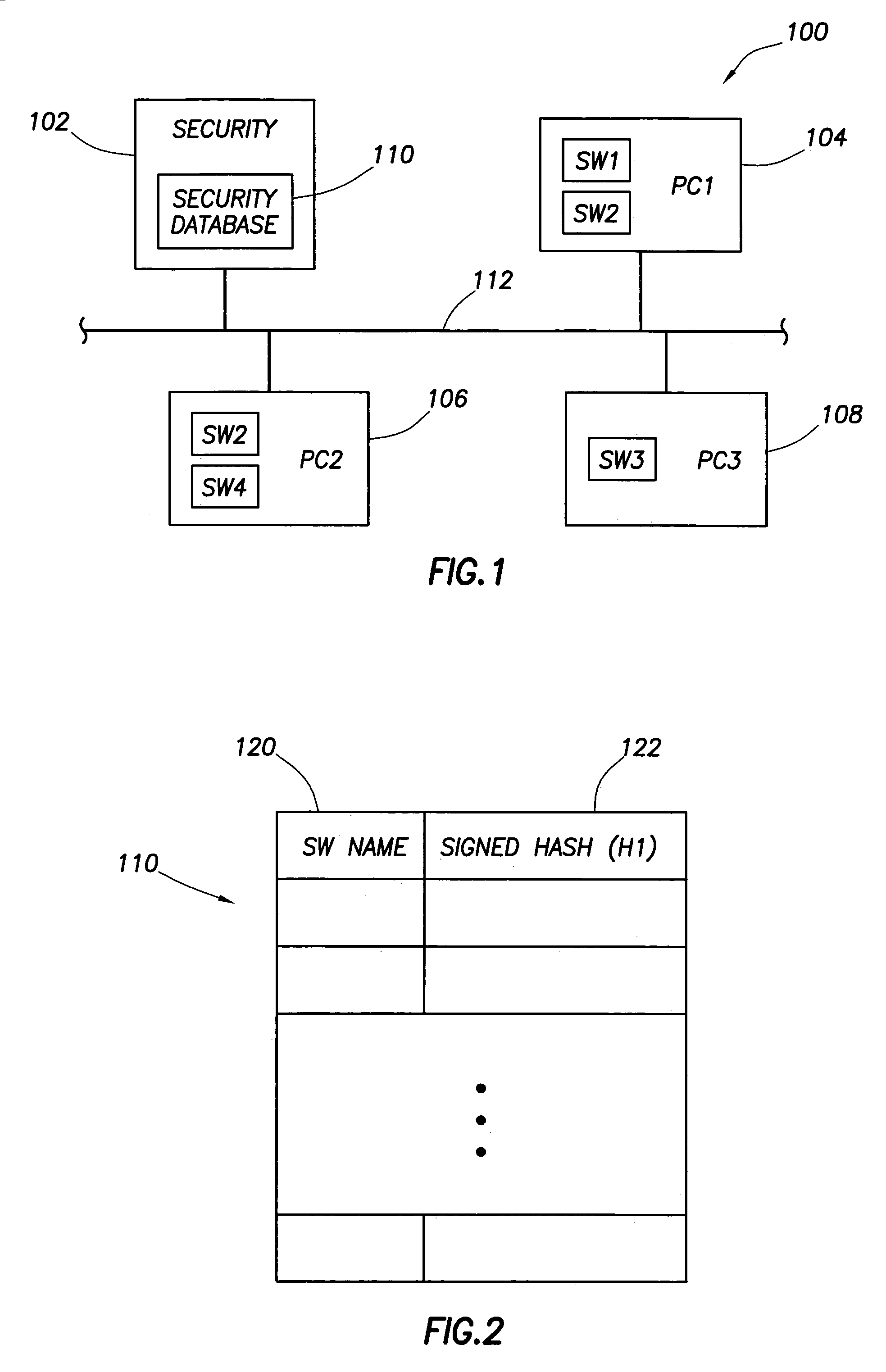
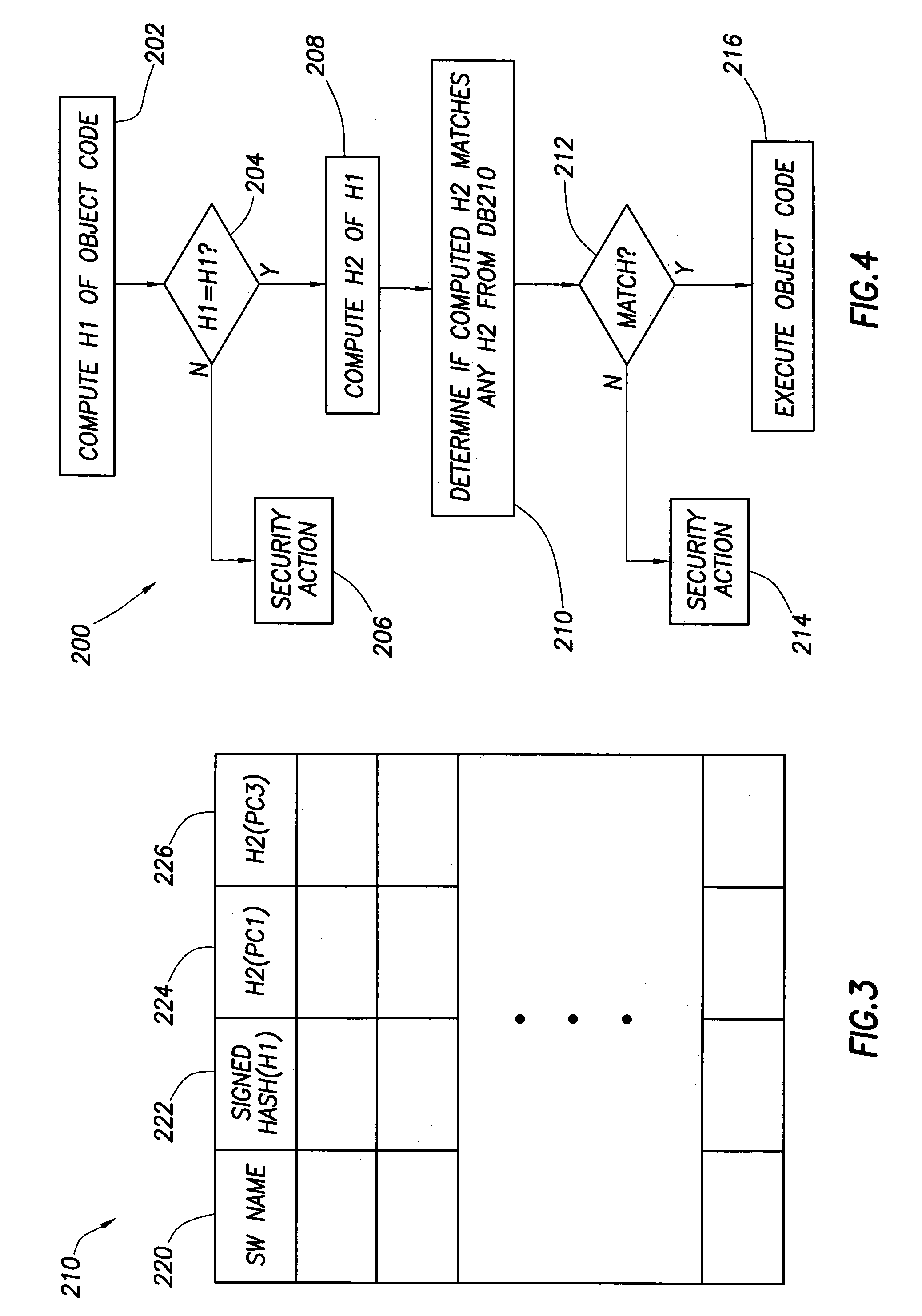
Authentication and verification for use of software
InactiveUS7003672B2Easy to modifyUser identity/authority verificationDigital computer detailsComputerized systemWorkstation
A computer system comprises a security computer having a security database and at least one workstation computer on which software is accessible for execution. The database includes security values that the workstation computers use to verify whether their copy of software is authentic (i.e., unmodified such as might occur from action of a virus). The database can also be used verify whether the software can be run on a particular workstation computer.
Owner:HEWLETT PACKARD DEV CO LP
System and method for transferring items having value
InactiveUS7778924B1Ensure protectionComputer security arrangementsFranking apparatusRelevant informationDigital signature
The present invention is directed to a system for providing secured access to a software rental or a postage metering system. The virtual postage meter software of this invention enables a user to print postage indicia on documents, envelopes or labels. To generate valid postage indicia the virtual meter software is executed on a first computer while it is in communication with the remotely located second computer. All communication between the first computer and the second computer utilize data encryption algorithms to preserve the security and integrity of the data transferred. In one embodiment, the second computer is a collection of one or more computers with virtual postage meter enabling software capable of communicating simultaneously to a number of user computers that are concurrently executing the virtual postage meter software. The second computer is connected to one or more US FIPS 140-1 security level 3 or better certified cryptographic devices identified as Postal Security Devices (PSD). The printed postage indicia appears as a two-dimensional barcode that includes digital signature, amount of postage, ZIP code and other relevant information.
Owner:STAMPS COM
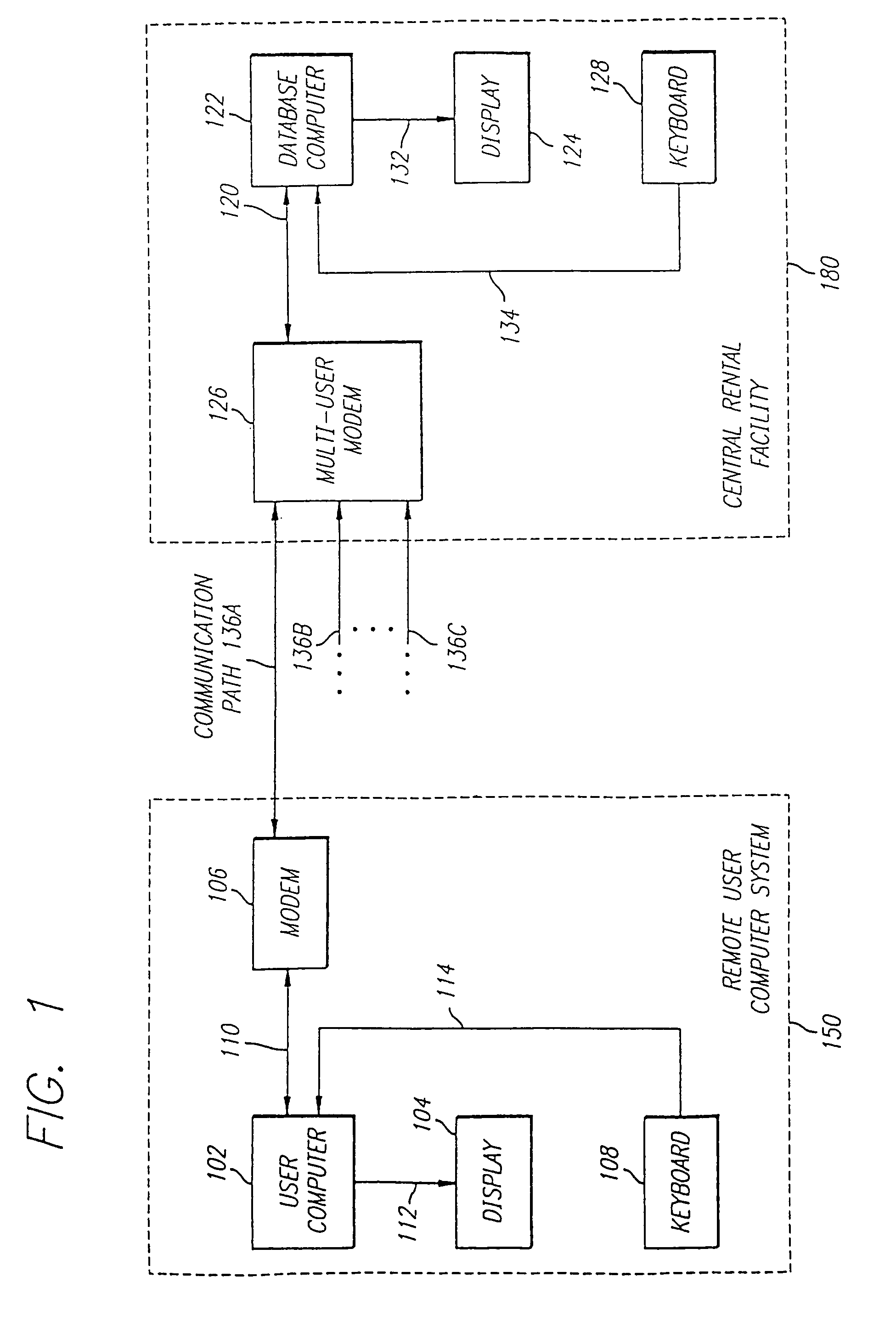
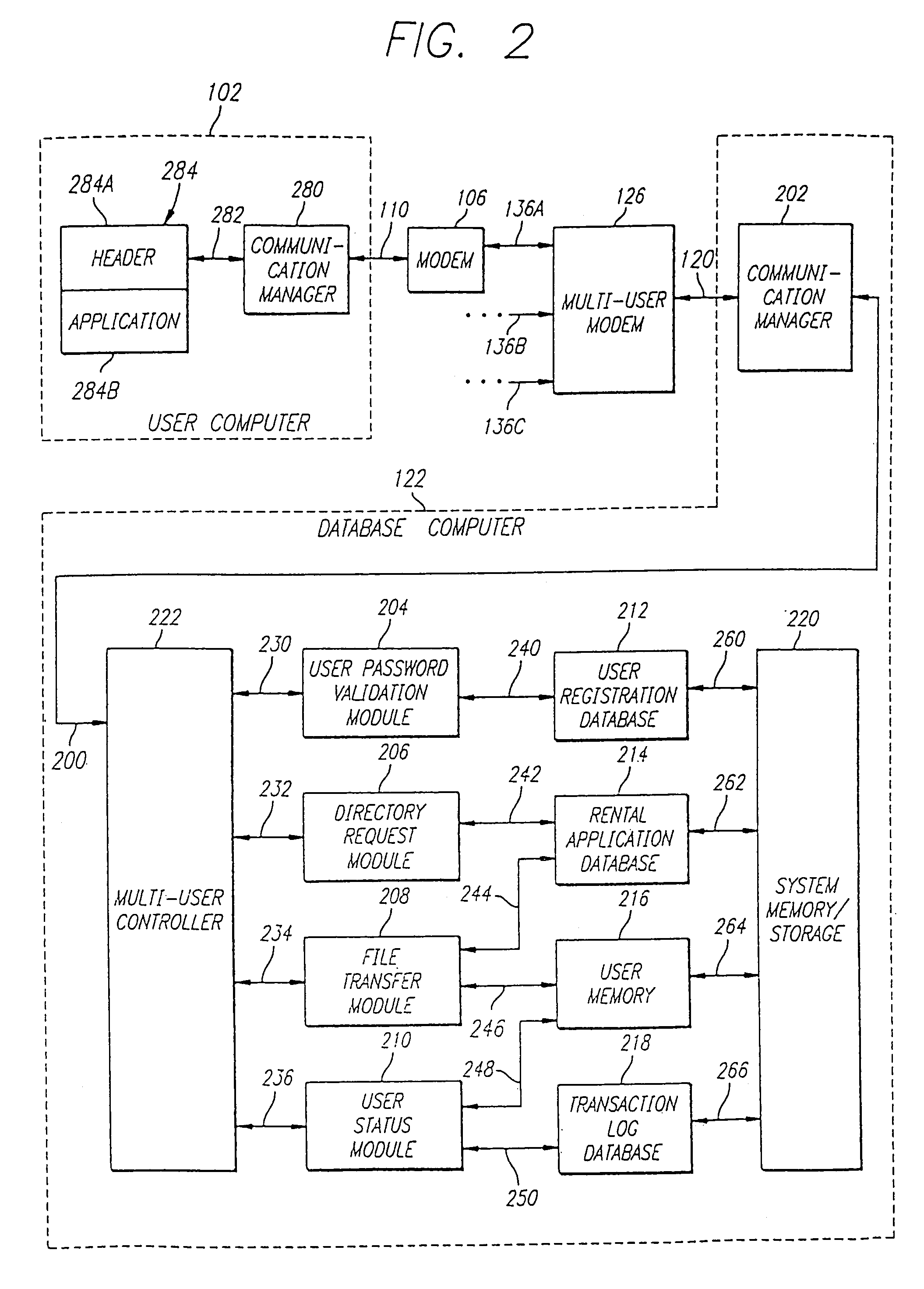
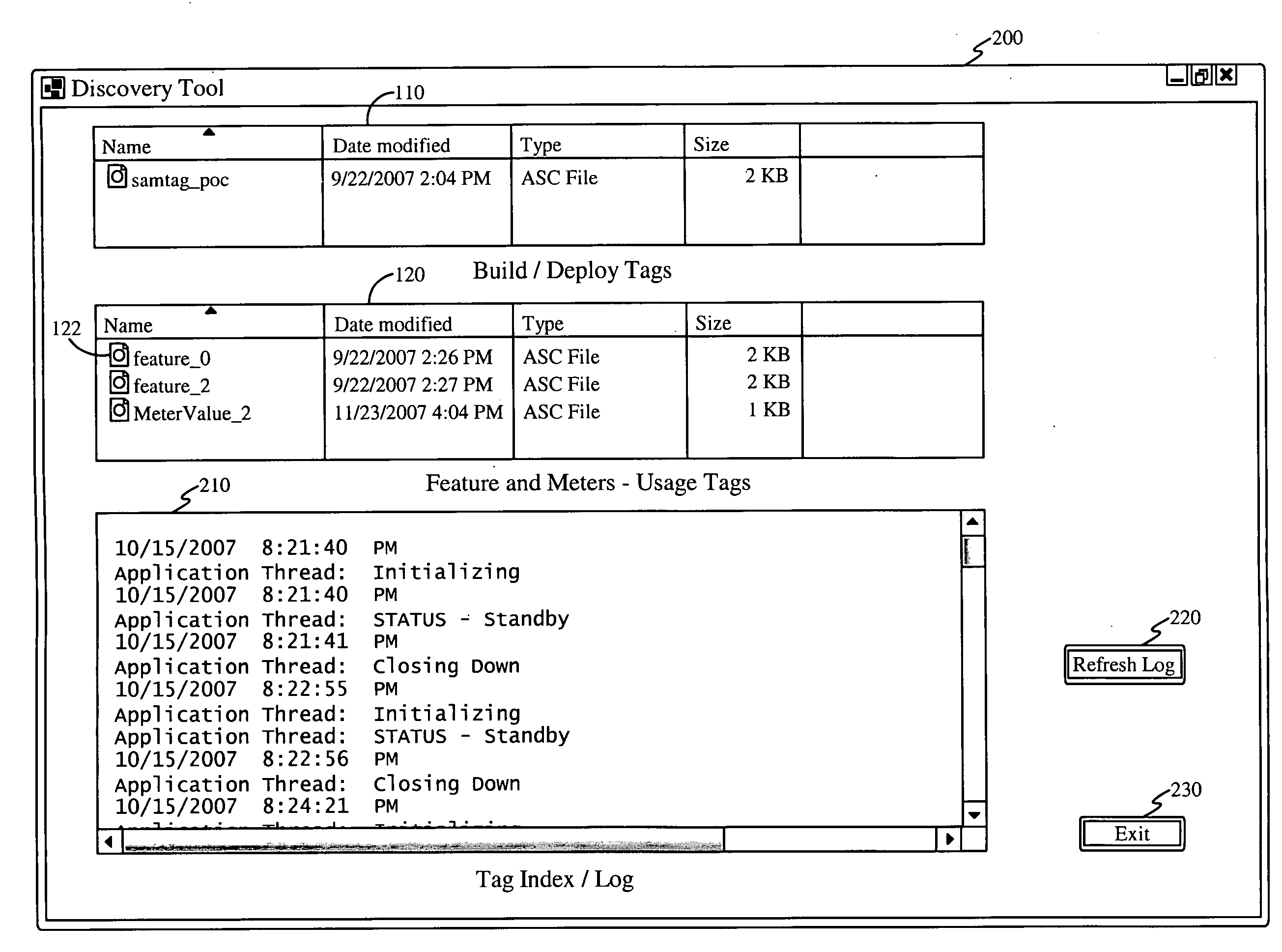
Dynamic, secure software tagging for software asset management with respect to deployment, configuration, and usage
InactiveUS20090113397A1Complete banking machinesTelephonic communicationSoftware asset managementStop time
A software tagging application is configured to measure software application usage within an enterprise deployment. The software tagging application using the concepts of tags, and extends the use of tags to convey monitored software usage. This usage data is written to the tag and secured with a signature calculated using public / private key cryptography. The signature ensures that the usage data collected is correct and has not been tampered with. Usage data refers to both the number of client versions of the software and specific software features installed, and any type of metric for monitoring real usage of the specific software features, for example the number of minutes used, and the start and stop times that the feature was executed. Monitoring usage in this manner provides a dynamic usage model that tracks current and historical software usage, from an enterprise-wide level down to a specific user and feature level.
Owner:WRIGHT DAVID D
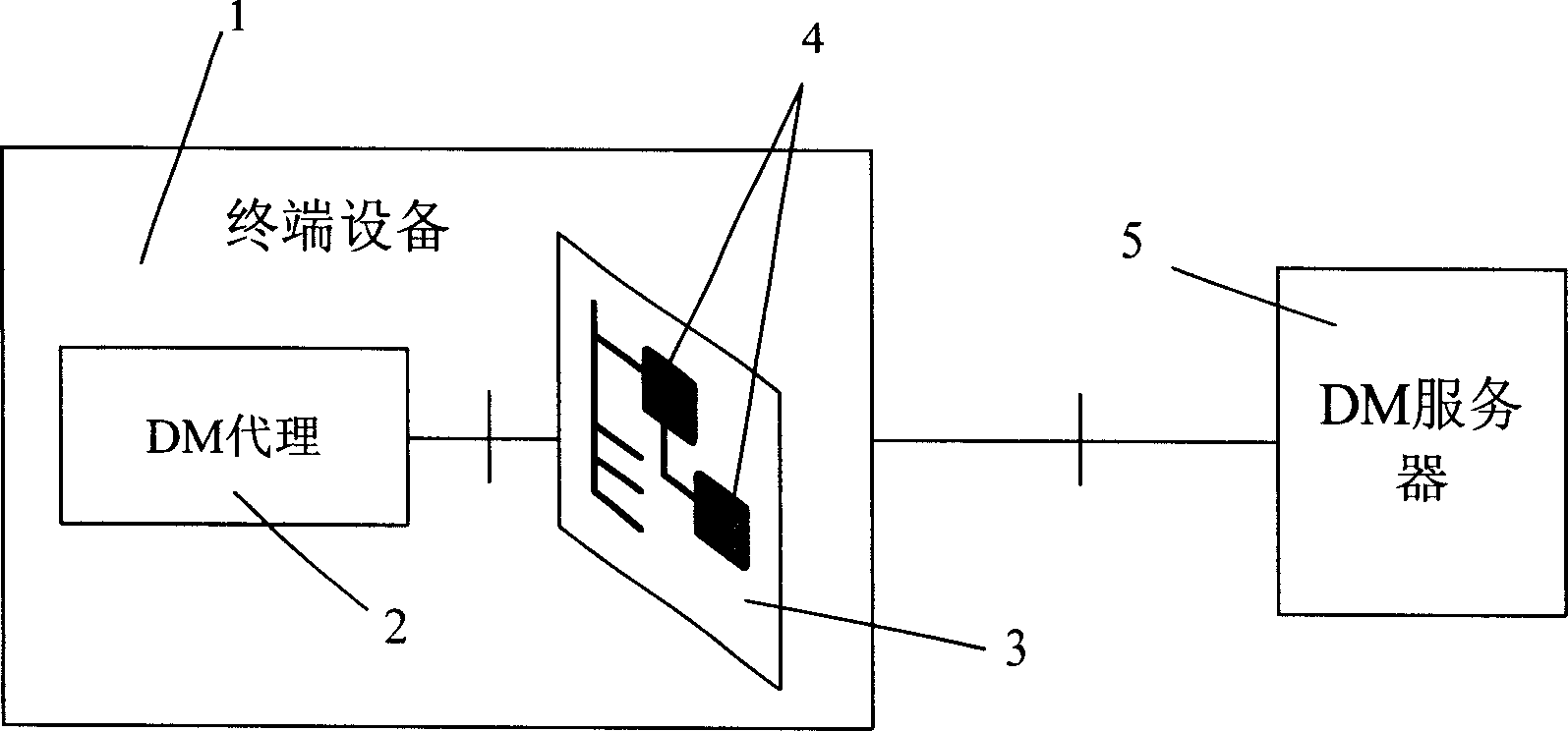
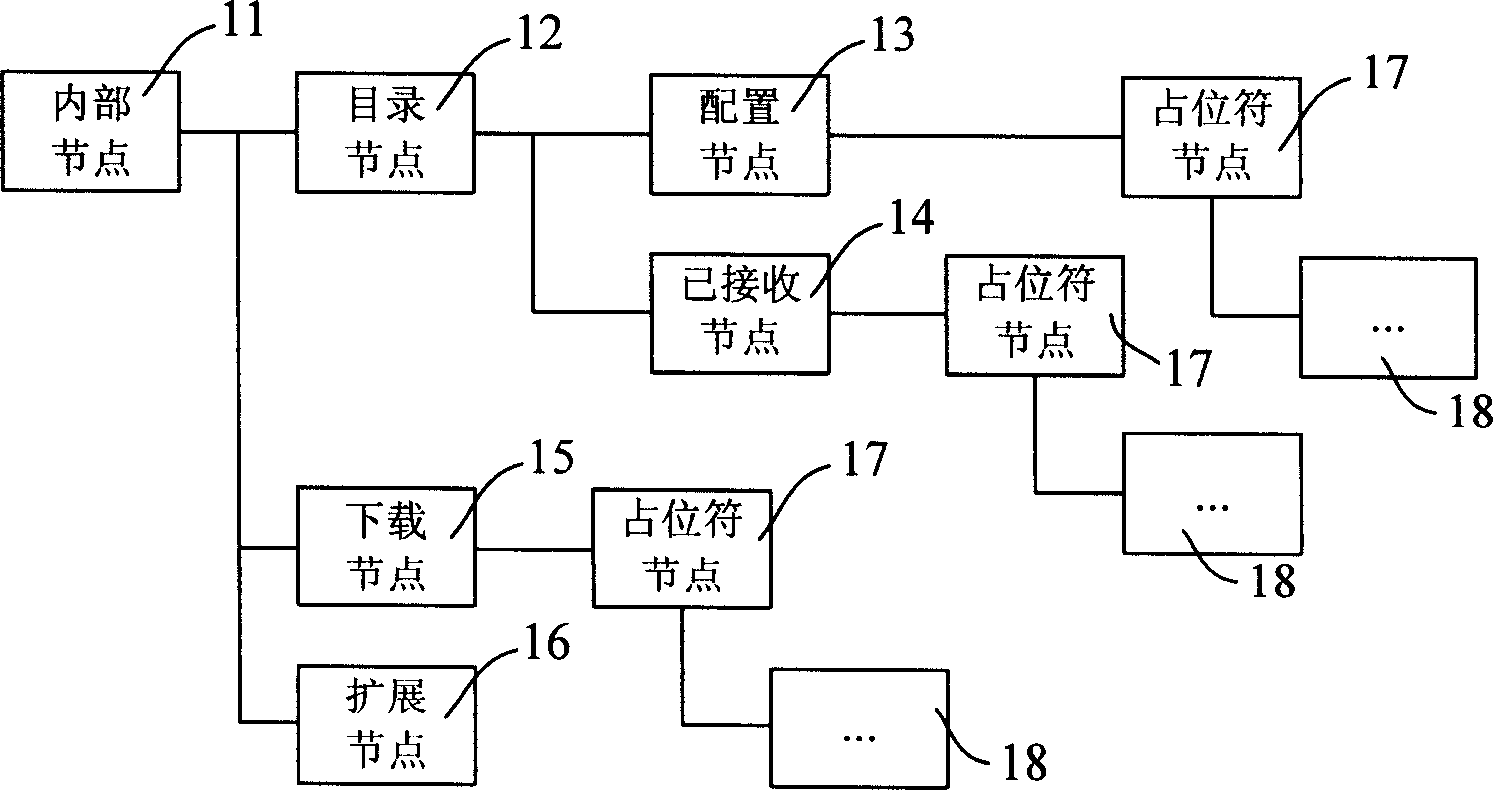
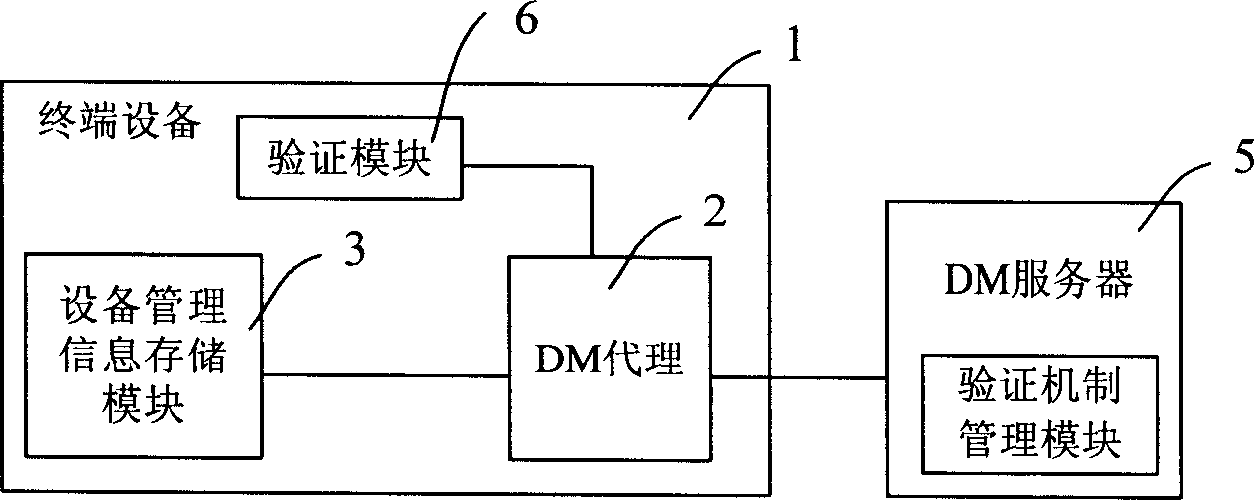
Software validity checking system and method based on device management protocol
InactiveCN1866870AImplementation licenseImprove experienceData switching networksValidation methodsControl system
The invention discloses a software legality checking system of device control system, which consists of device control server and terminal device, wherein terminal device includes device control proxy and device control information memory module for storing checking information and one checking modular. The invention also discloses a software legality checking method based on device control protocol with uniform encryption mode, registration code and digital copyright control mode. The invention is favorable for software provider controlling and managing, which guarantees the legality of software usage.
Owner:HUAWEI TECH CO LTD
Method, system, server and client for remotely storing locally executed software
InactiveCN102279748AImprove compatibilityFull processing capacityTransmissionSpecific program execution arrangementsVirtual file systemFile system
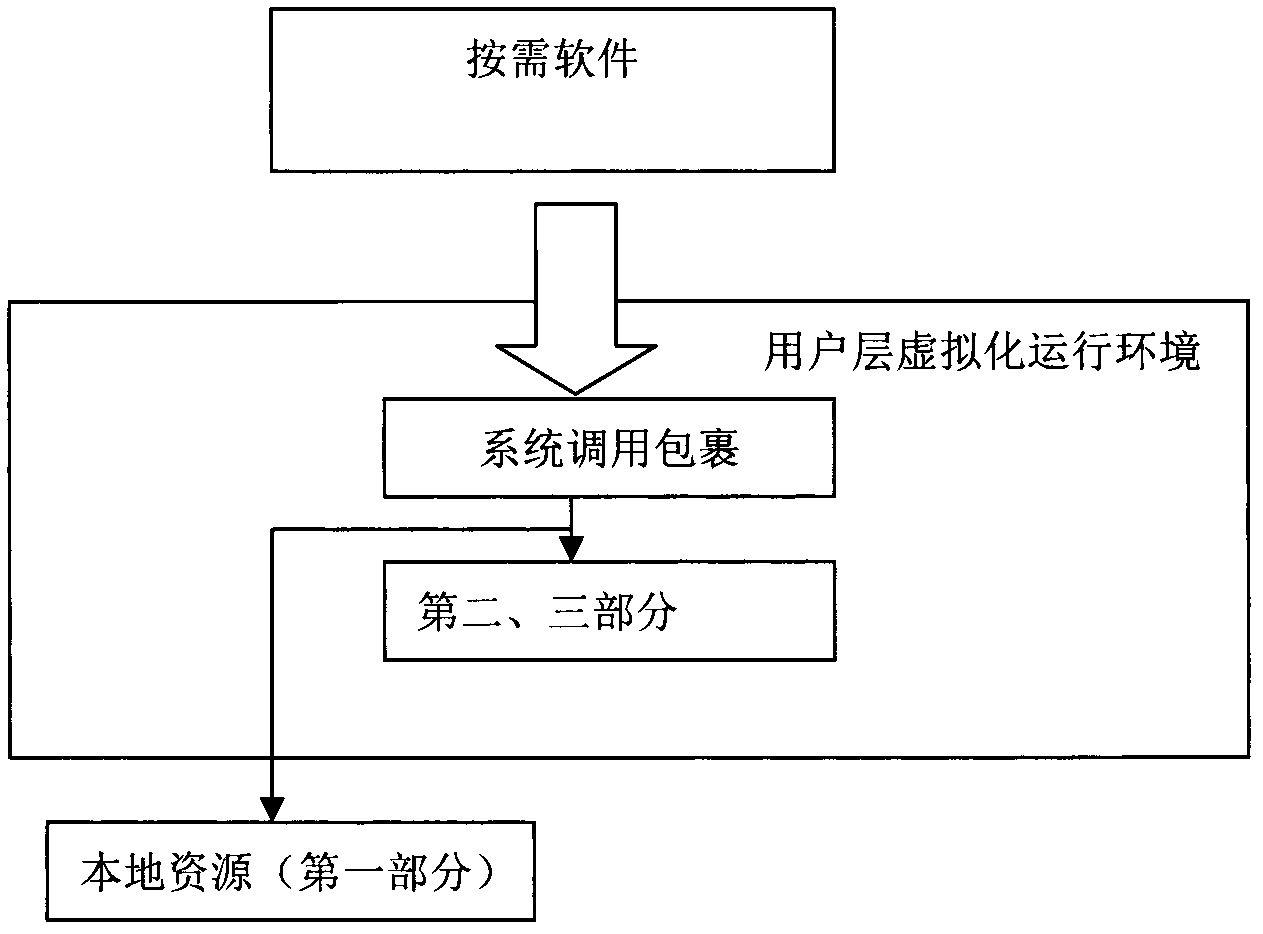
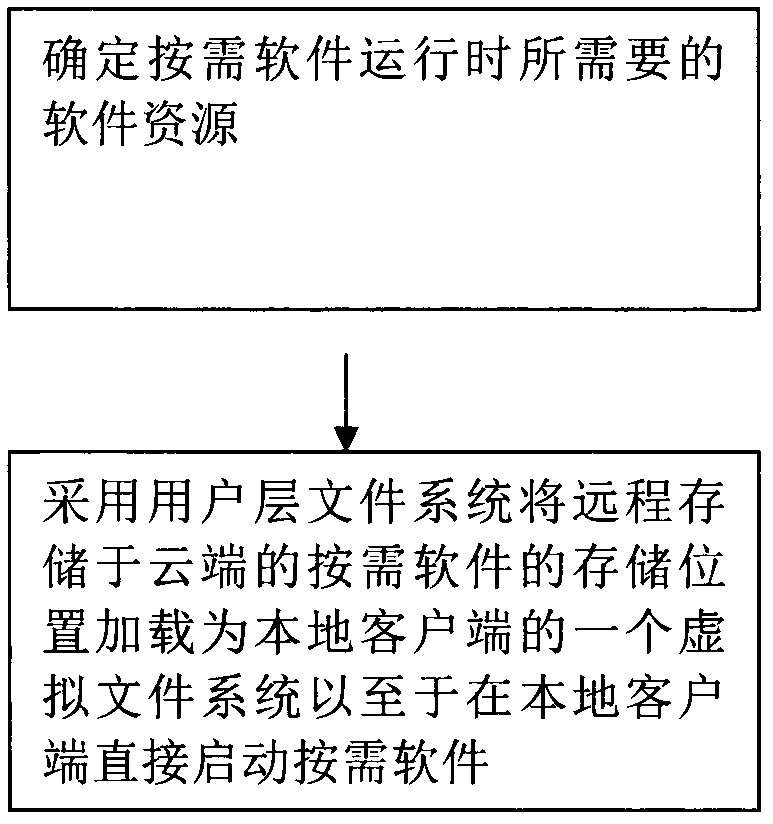
The invention provides a method, a system, a server and a client for remote storage and local execution of software. The software fortune is stored in the cloud and can be executed on the local client. The method includes: step 1: determining the software resources needed for the on-demand software to run, and step 2: using the user-level file system to remotely store the on-demand The storage location of the software is loaded as a virtual file system of the local client so that the on-demand software can be started directly on the local client. The existing software can be stored remotely and run locally (client) without modifying the source code, achieving both compatibility and high performance.
Owner:焦秀琴
Apparatus and Method for Displaying Telemetry Data
InactiveUS20130169644A1Improves graph interactionShorten the timeDrawing from basic elementsSub-station arrangementsGraphicsData set
Browser-based software uses image tiling techniques to display interactive charts of large scale, time-based datasets. Scalable Vector Graphics instantiated from code loaded in memory associated with a server dynamically generates image tiles at the server, which tiles are then selectively called up and downloaded to a client system for display. The server consolidates requested data into averaged data points and then renders an overall graphic representation by appropriately assembling the averaged data points into discrete tiles. Mapping-based tiling software at the client system assembles a composite image of a portion of a chart / graph for a user-selected region at a selected resolution within a viewport of predetermined size, considerably improving graph interaction and reducing rendering times over existing Flash-based solutions. The server is configured to pre-empt selection of any particular area by generating a sub-layer of tiles that would, upon request, be immediately downloadable to the client system.
Owner:DEXDYNE
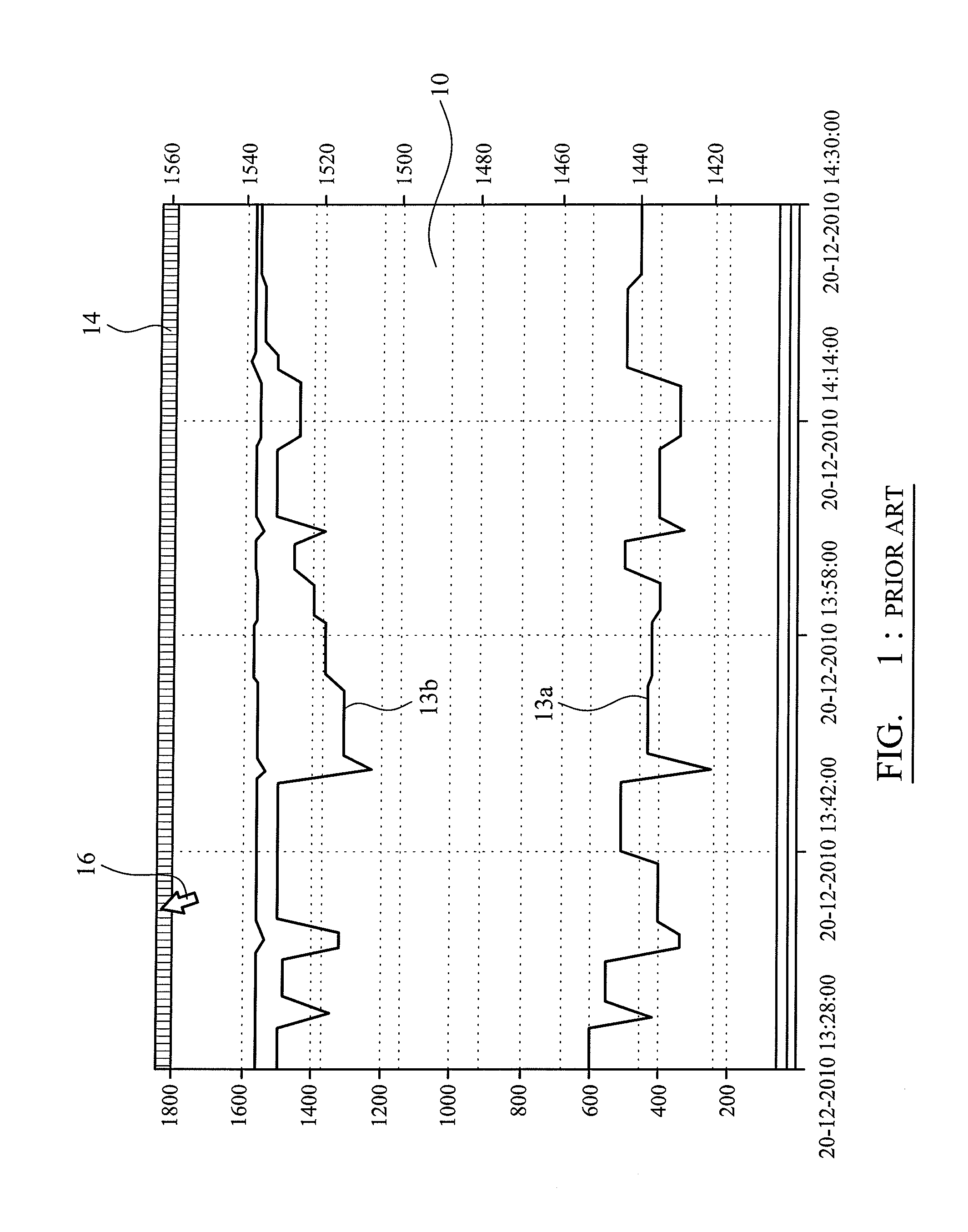
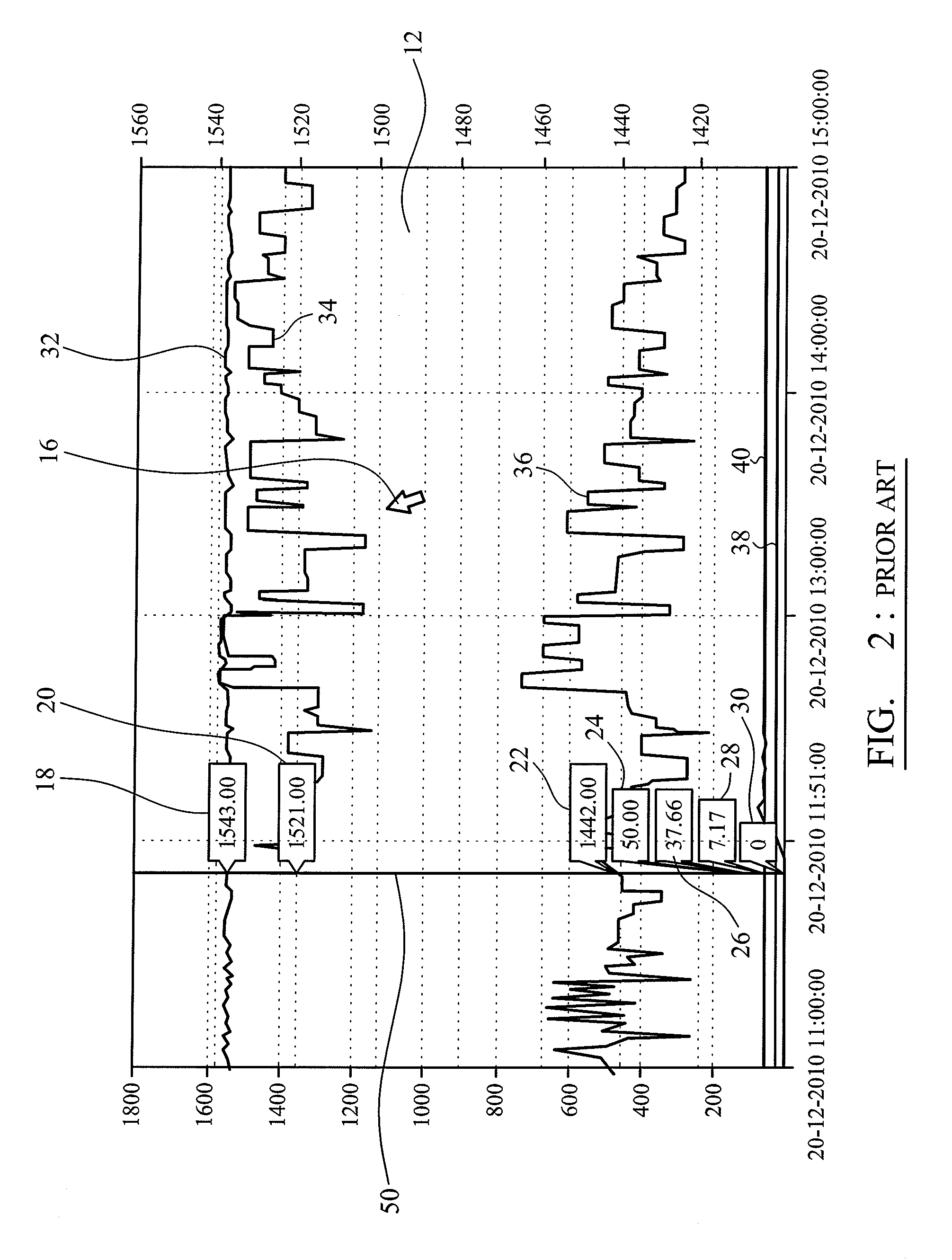
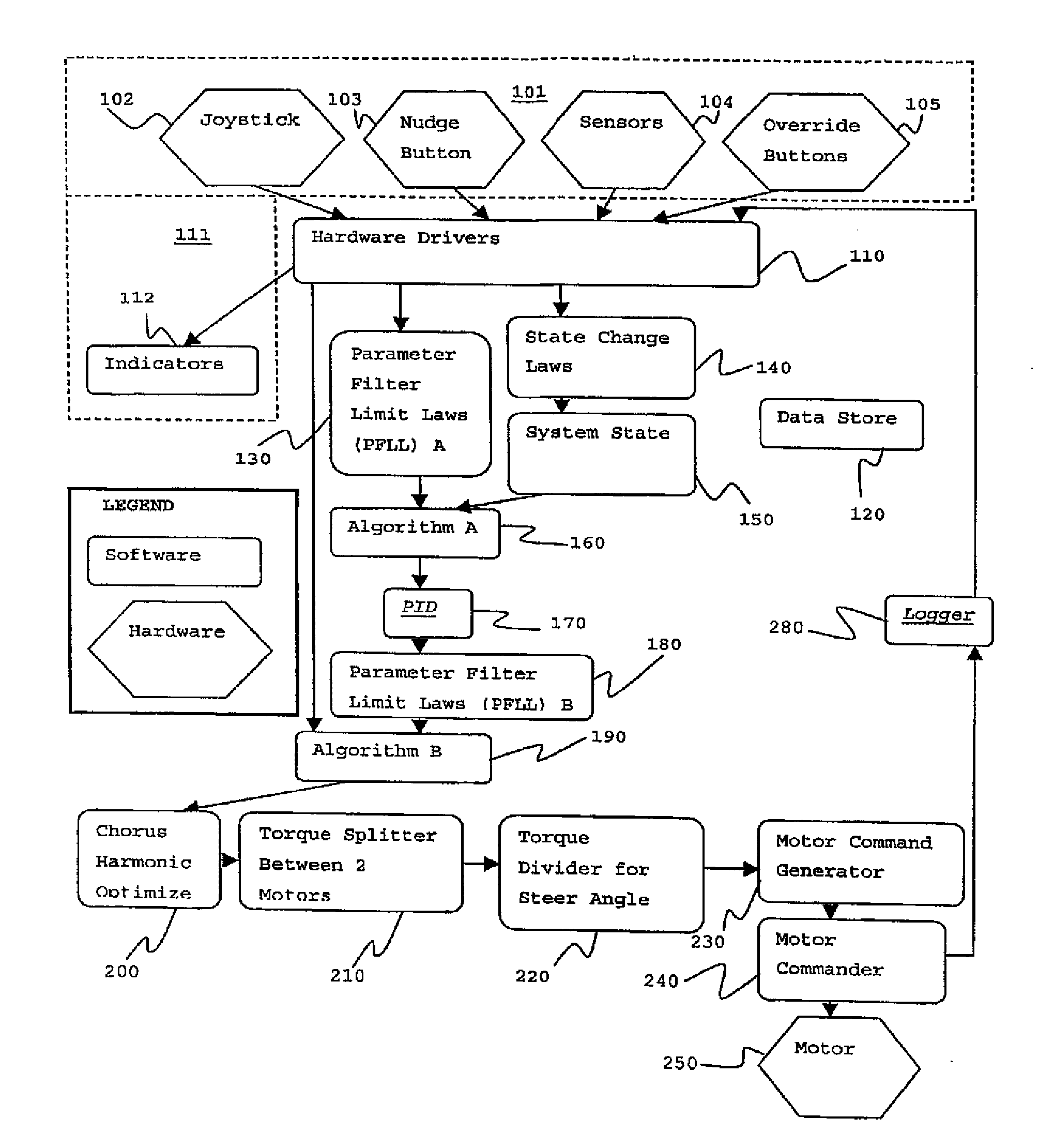
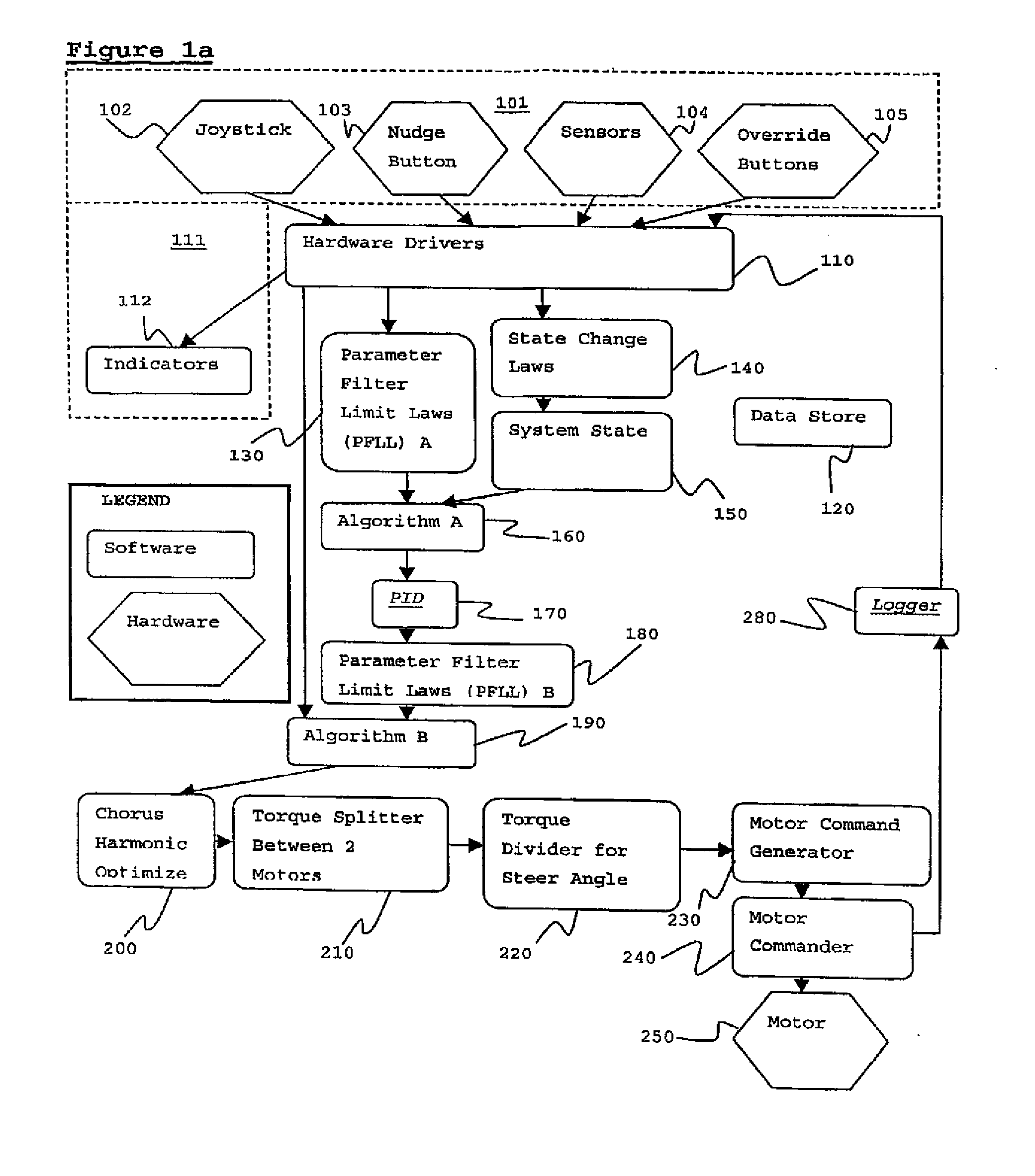
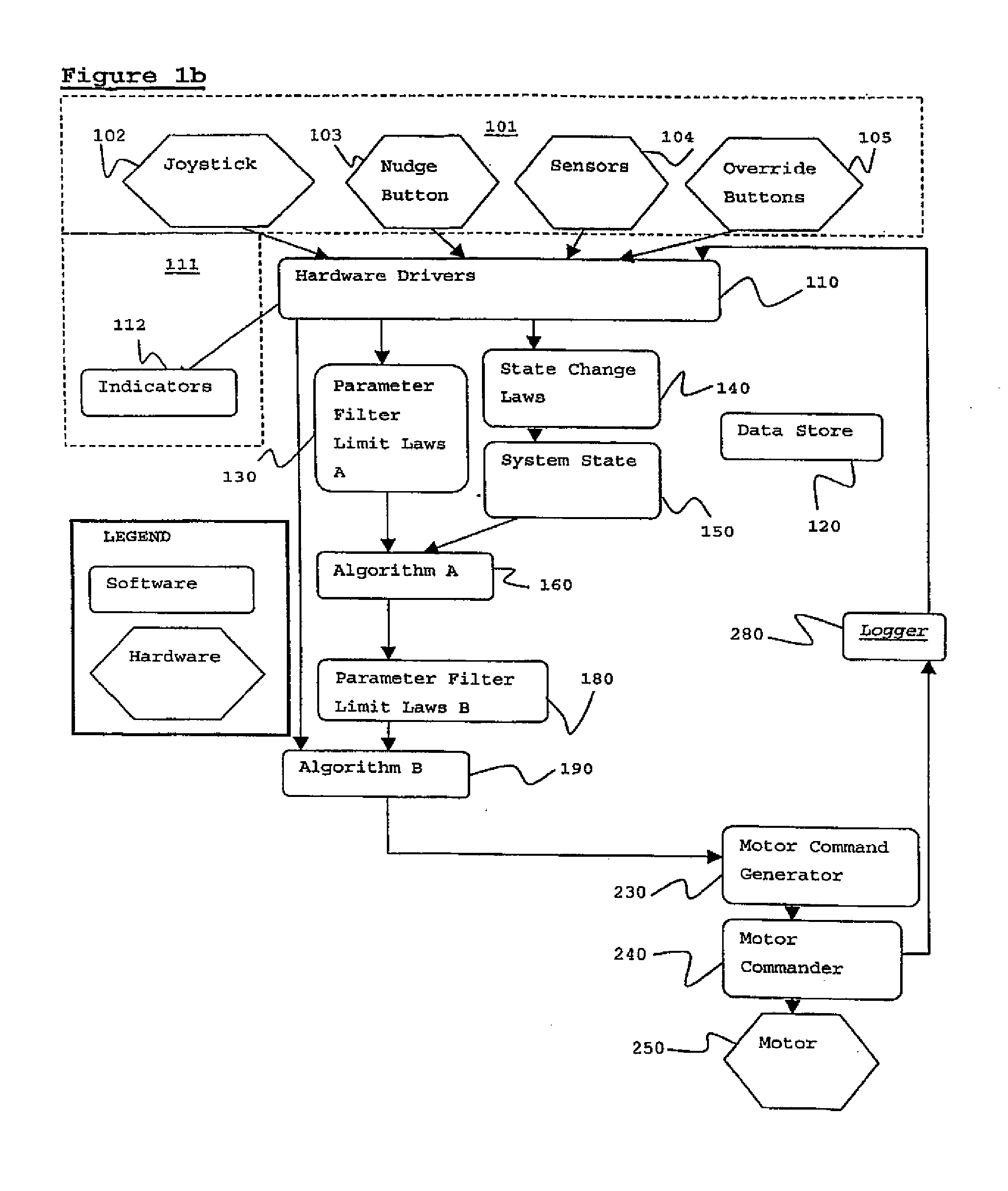
Motor controller
ActiveUS20120018574A1Low costLower Level RequirementsEnergy efficient operational measuresDigital data processing detailsCOLA (software architecture)Software architecture
This application describes the software invented to control an electric motor system. The electric motor system is mounted on one or more aircraft main wheels or nose wheels to drive an aircraft independently on the ground without aircraft engines or tow vehicles. The software uses closed-loop control together with several other control laws to operate the drive motor or motors. Knowledge of the current operating state of the drive motor, together with knowledge of the commands given to taxi forward, taxi in reverse, or brake in reverse, is used to configure the motors to optimal operating parameters. The software architecture is described along with the pilot interface and many details of software implementation.
Owner:BOREALIS TECH LTD
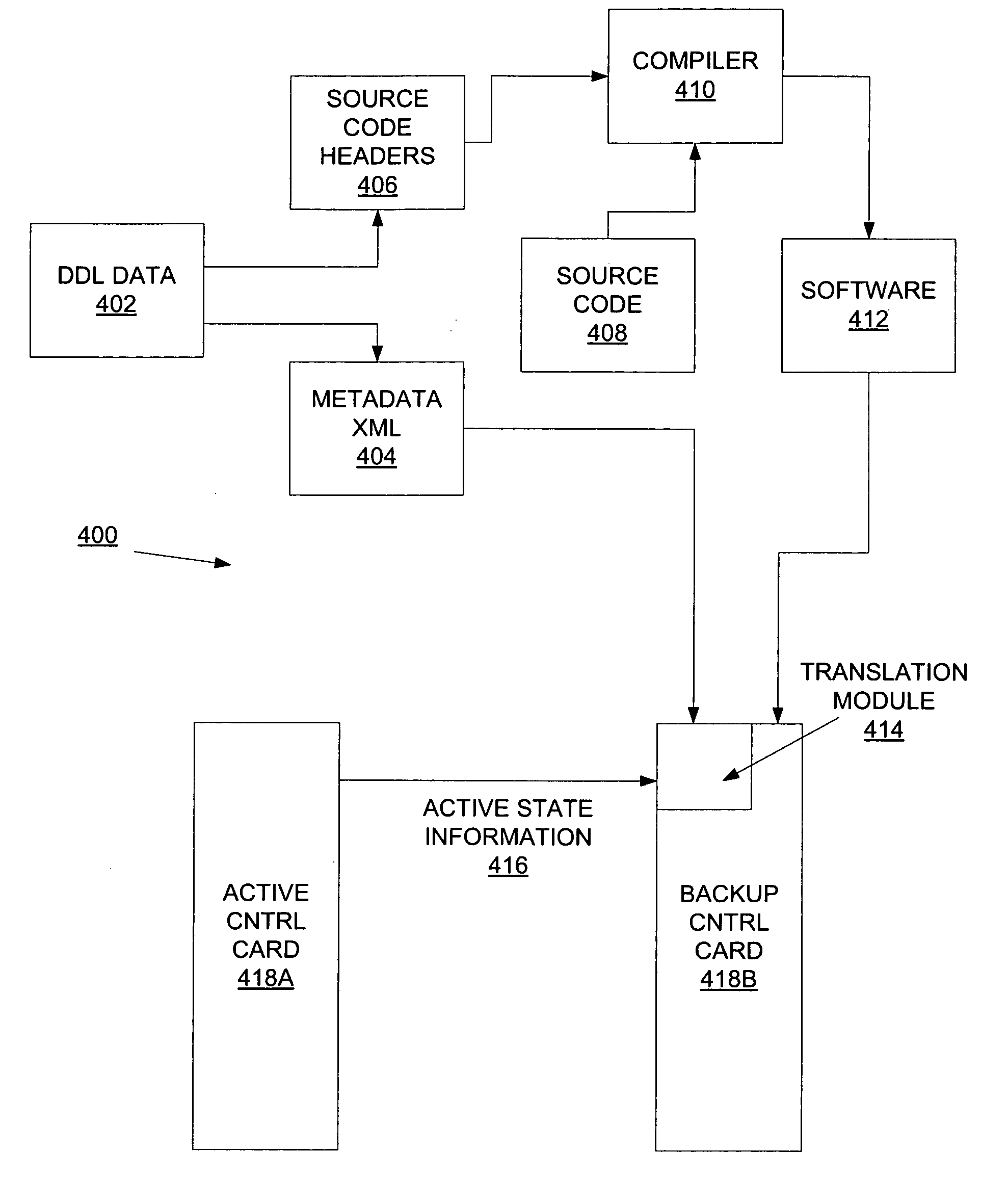
In-service software upgrade utilizing metadata-driven state translation
A method and apparatus for a metadata-driven upgrade of a network element is described. A network element comprises an active and backup controller card and receives new software to be installed on that network element. In addition, the network element installs the software on the backup controller card and synchronizes the active state of the network element to the backup controller card. Furthermore, the network element uses metadata to translate the active state to the format used by the new software.
Owner:TELEFON AB LM ERICSSON (PUBL)
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com