Patents
Literature
214 results about "Partial match" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Partial match. A partial match is defined to be a prefix of some valid match. For example, 123 is a partial match for the regex \d+\.\d+, since appending, for example, .4 yields the match 123.4.
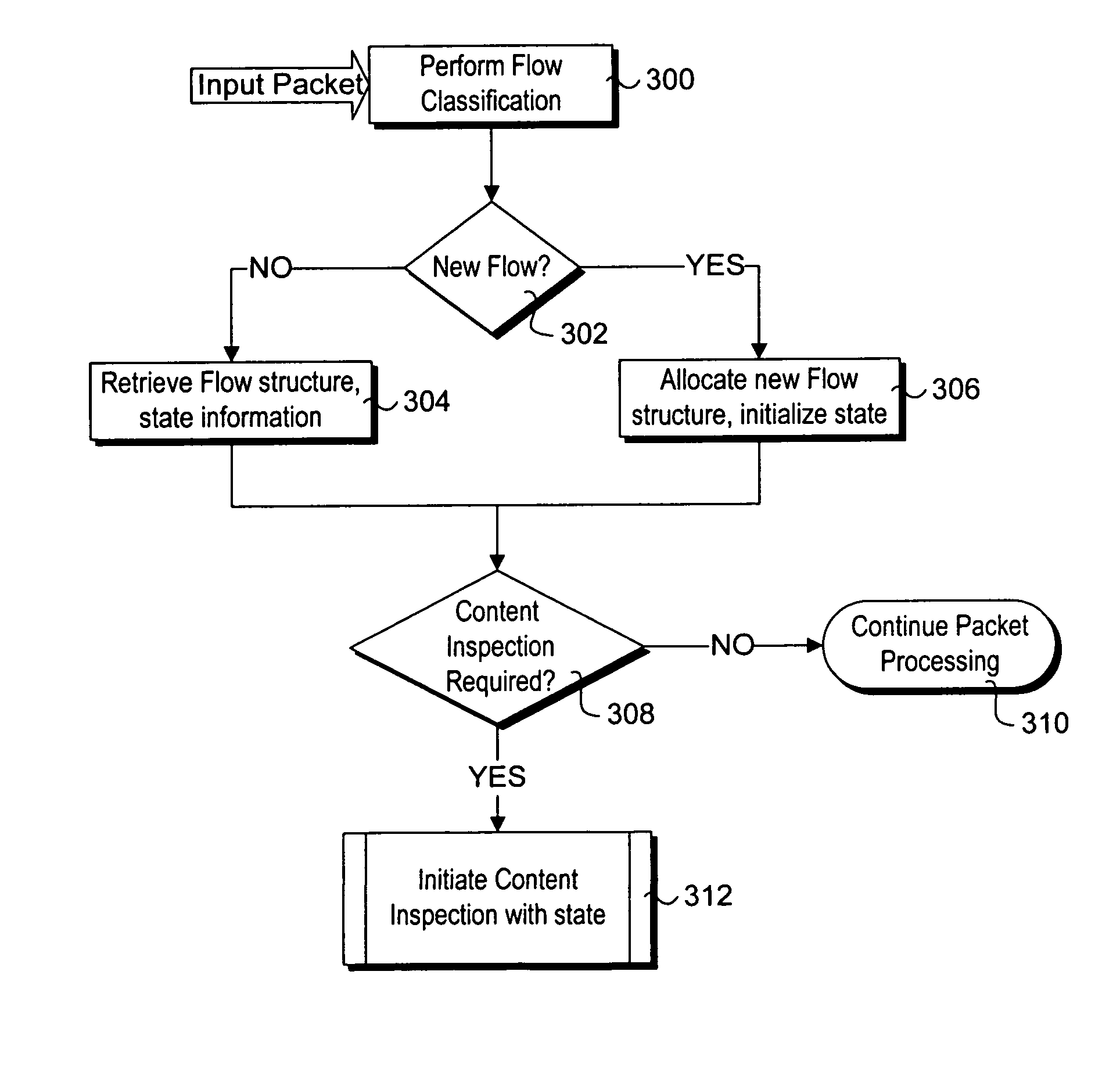
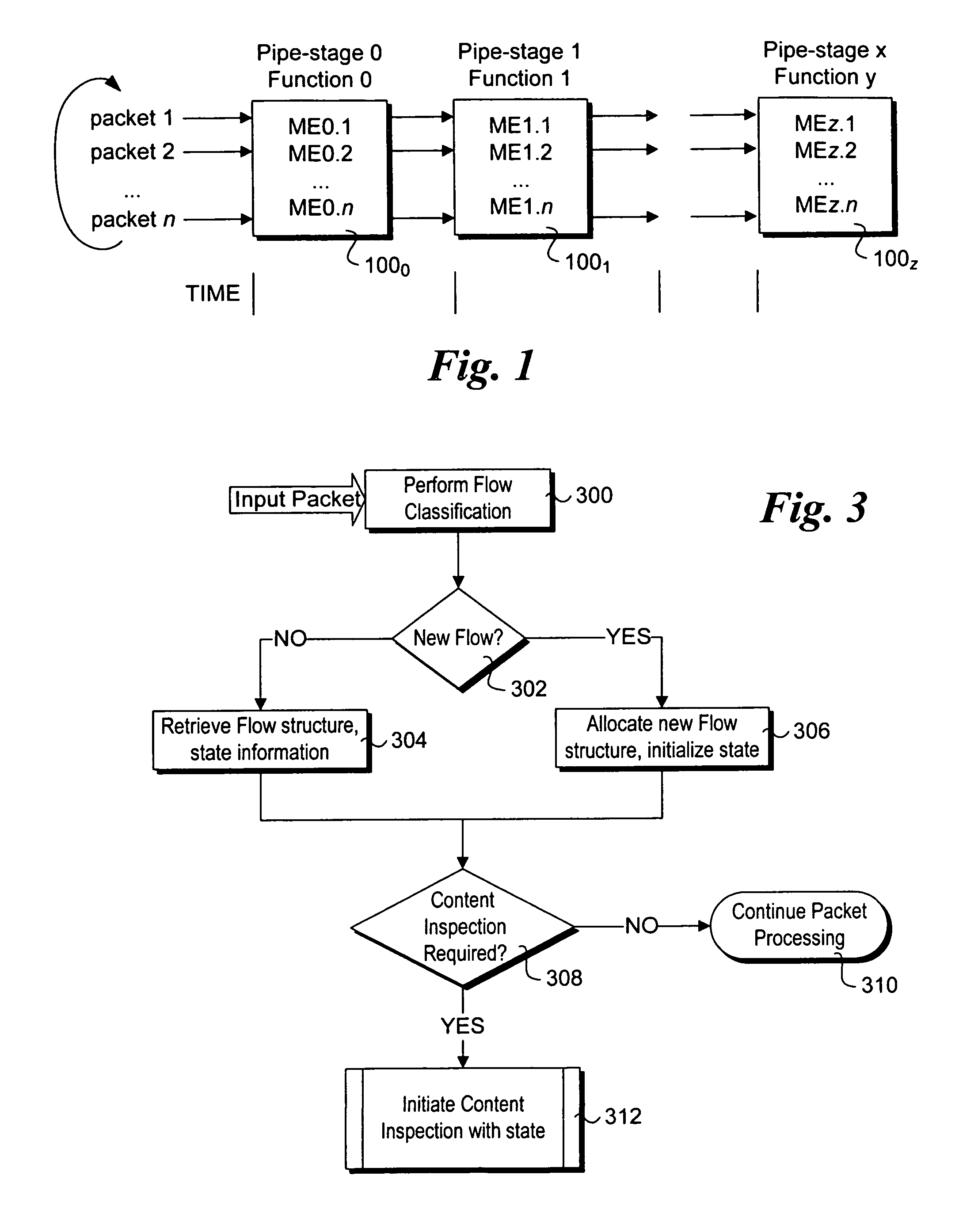
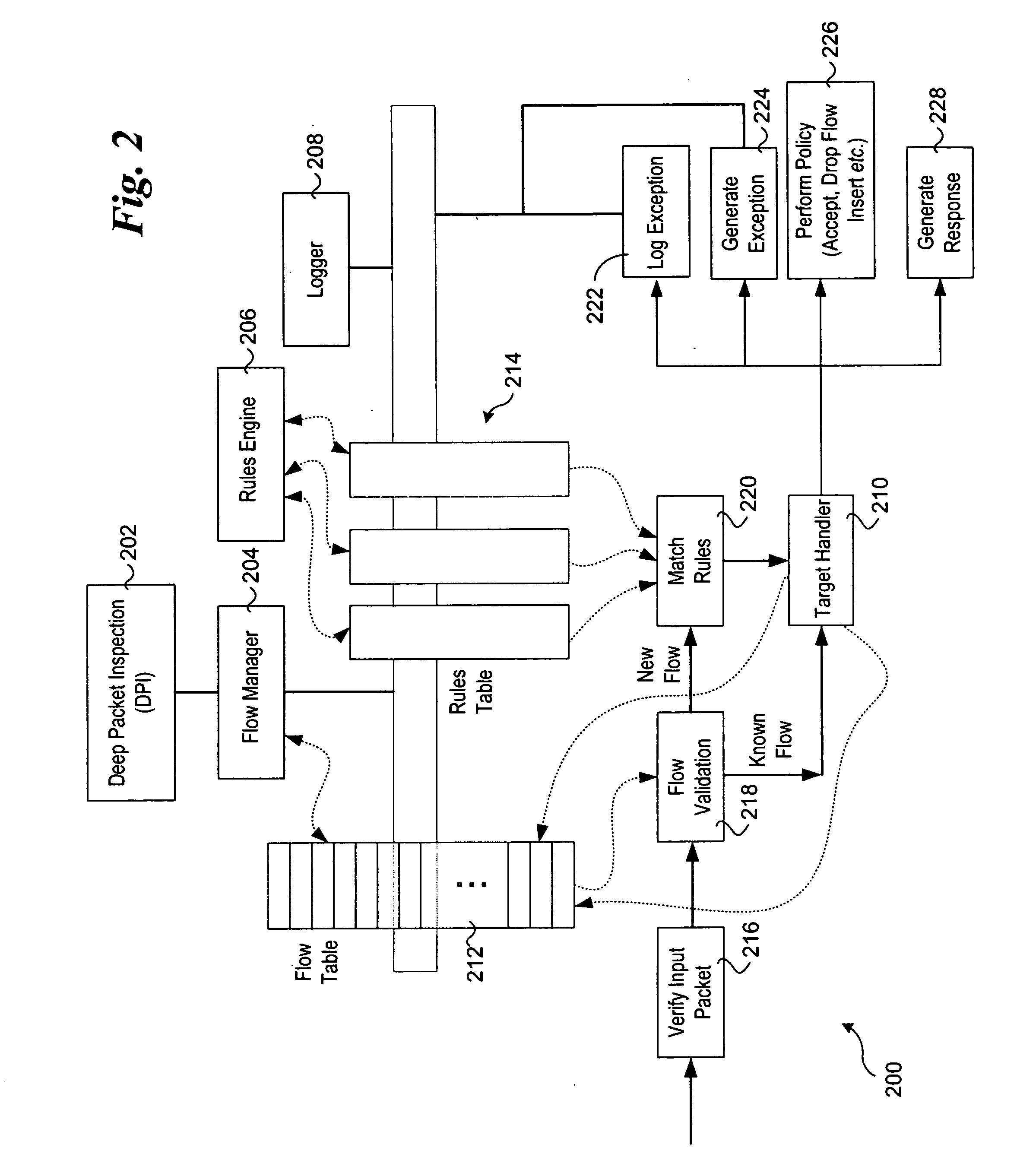
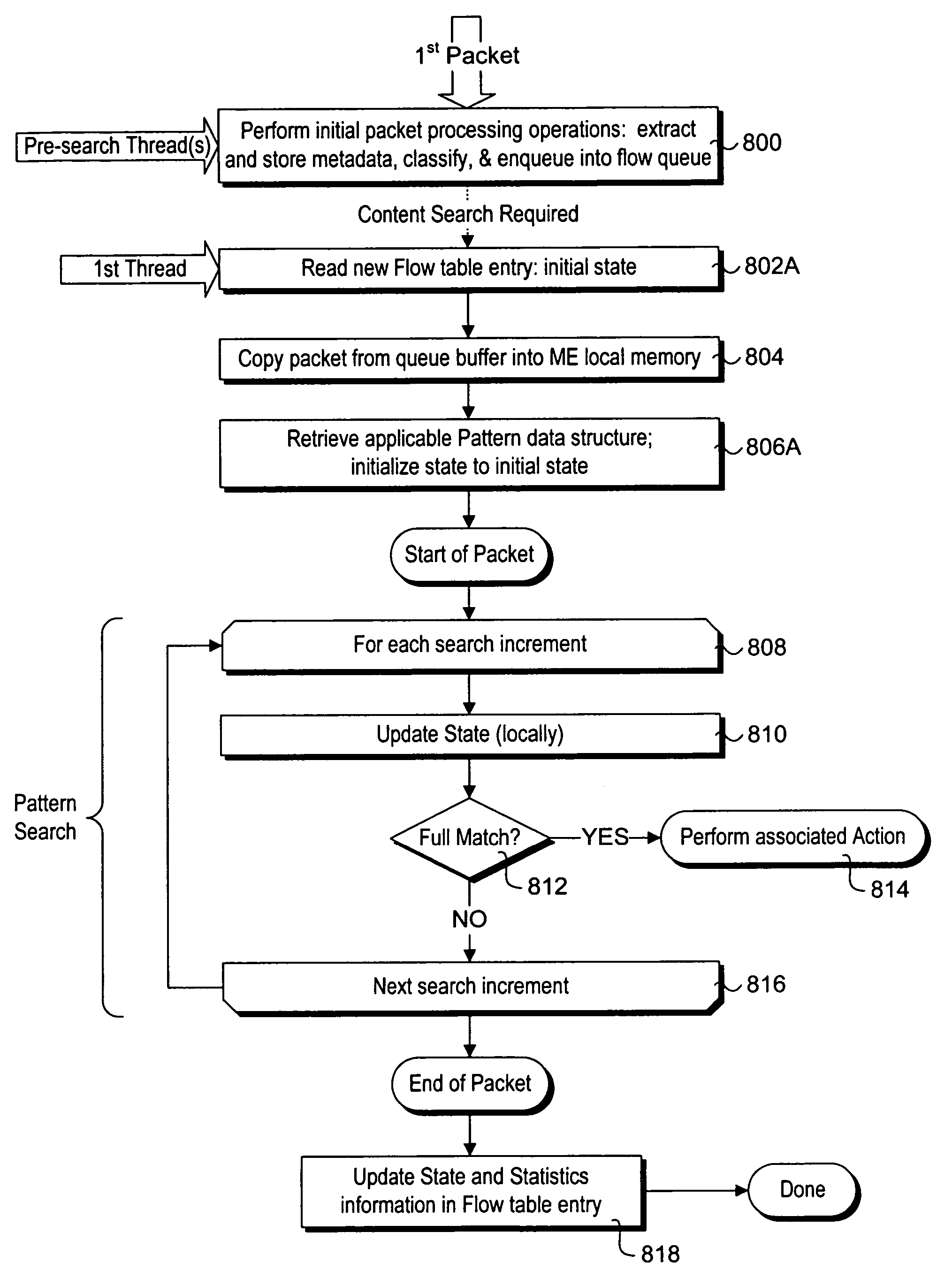
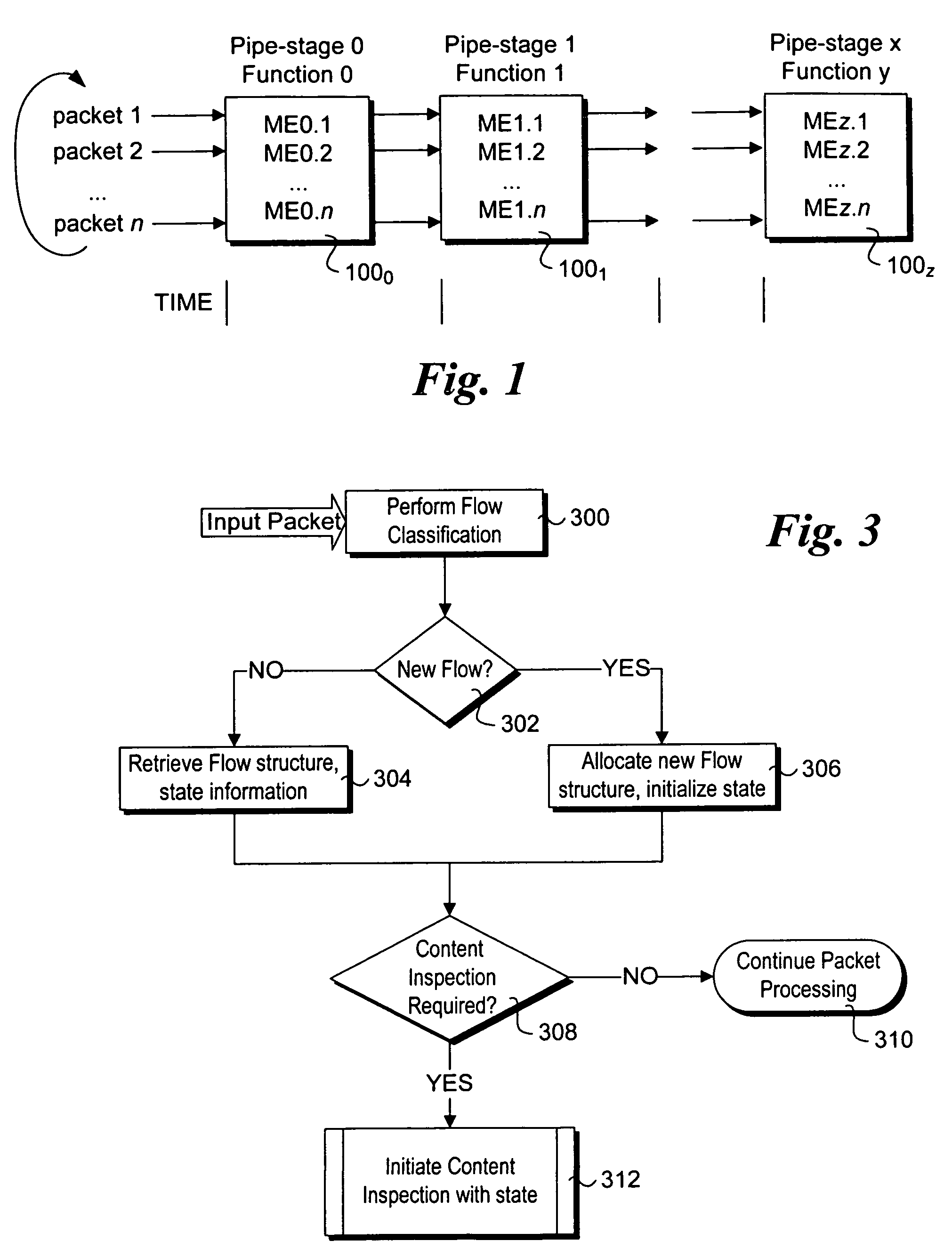
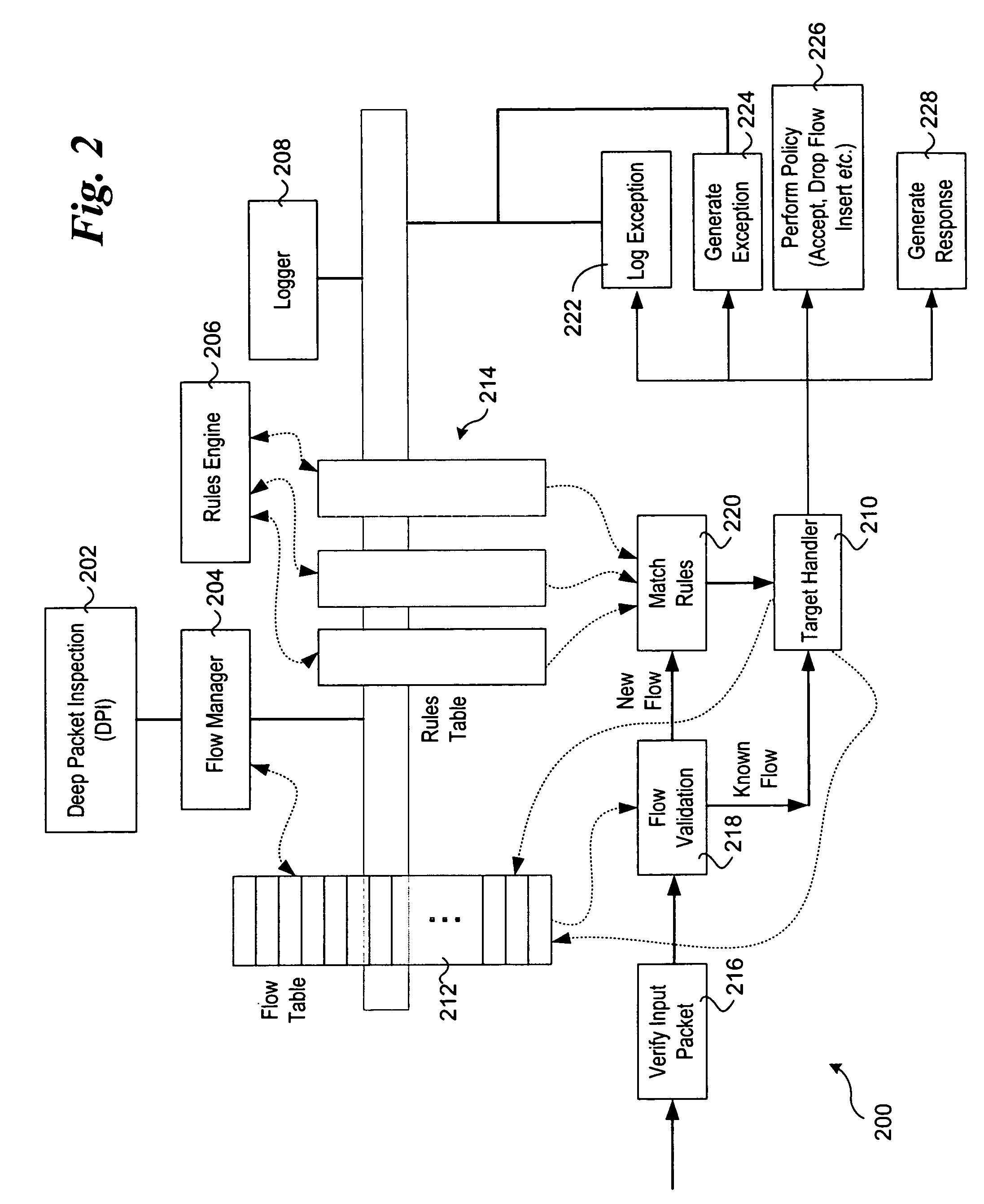
Stateful packet content matching mechanisms
ActiveUS20070011734A1Energy efficient ICTMultiprogramming arrangementsComputer hardwareString searching algorithm
Methods and apparatus for performing content inspection across packet boundaries using stateful packet content matching mechanisms. Pattern data structures are employed to facilitate string search algorithm machines. Incoming packets are classified to flows, and stored in corresponding flow queues. Flow table entries are used to identify the pattern data structure for a given flow. During content inspection, the algorithm machine updates state information to identify partial or full matches. When a partial match is detected towards the end of an earlier packet state information in the flow table is updated to reflect the state such that content inspection of a following packet begins at that state. As a result, content inspection across packet boundaries is supported. The techniques may further be employed in a packet processing context pipeline stage.
Owner:TAHOE RES LTD
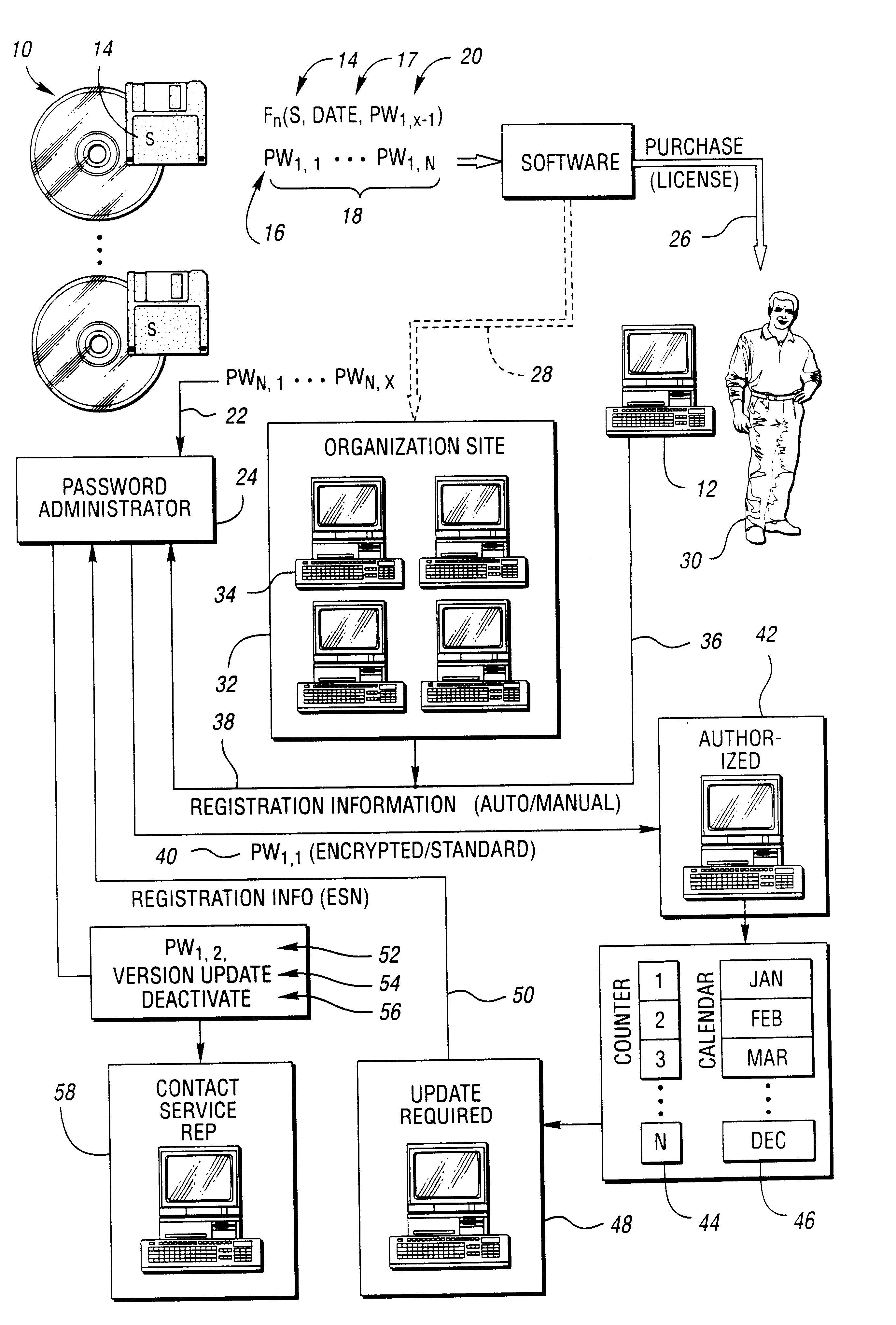
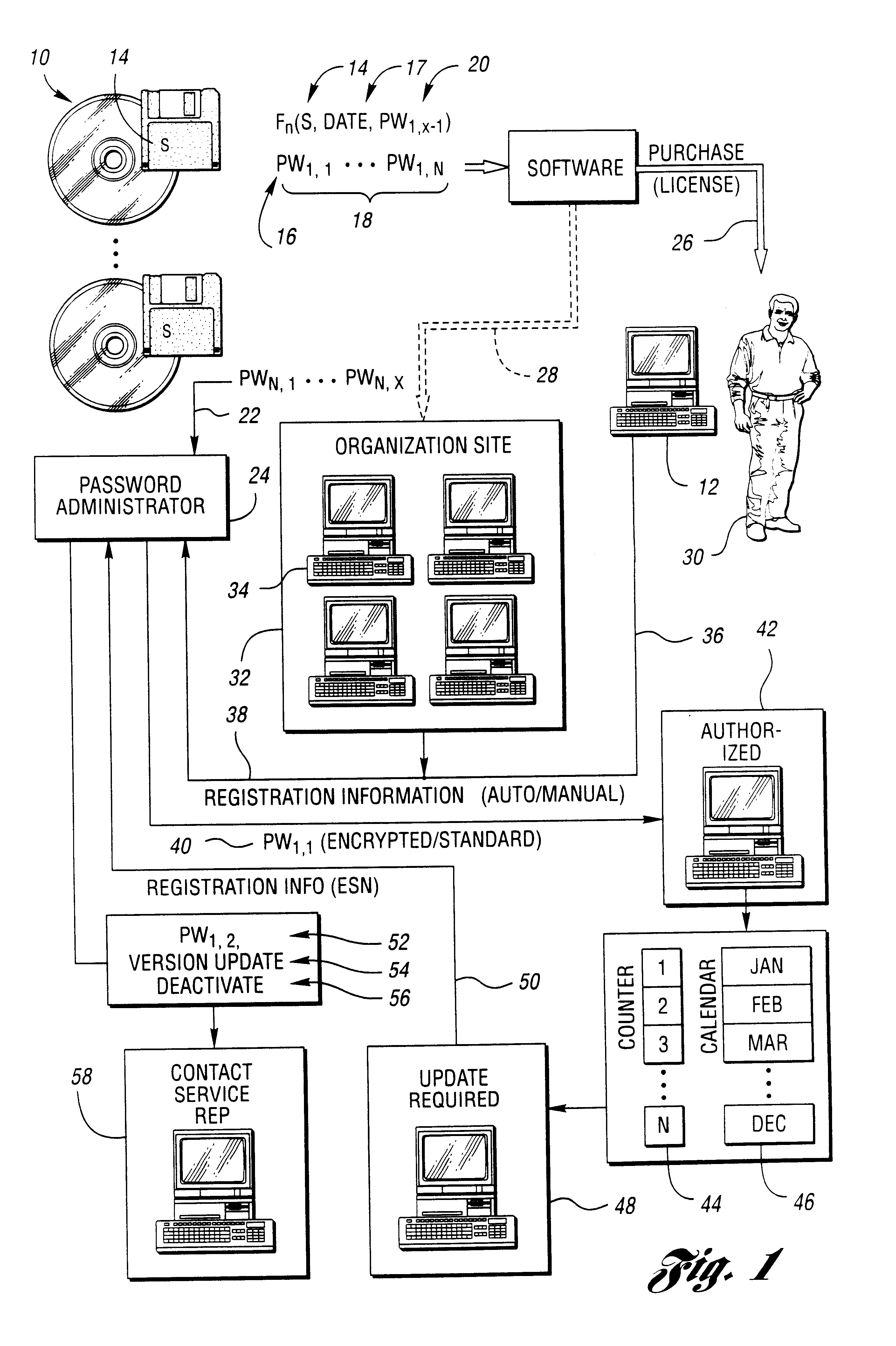
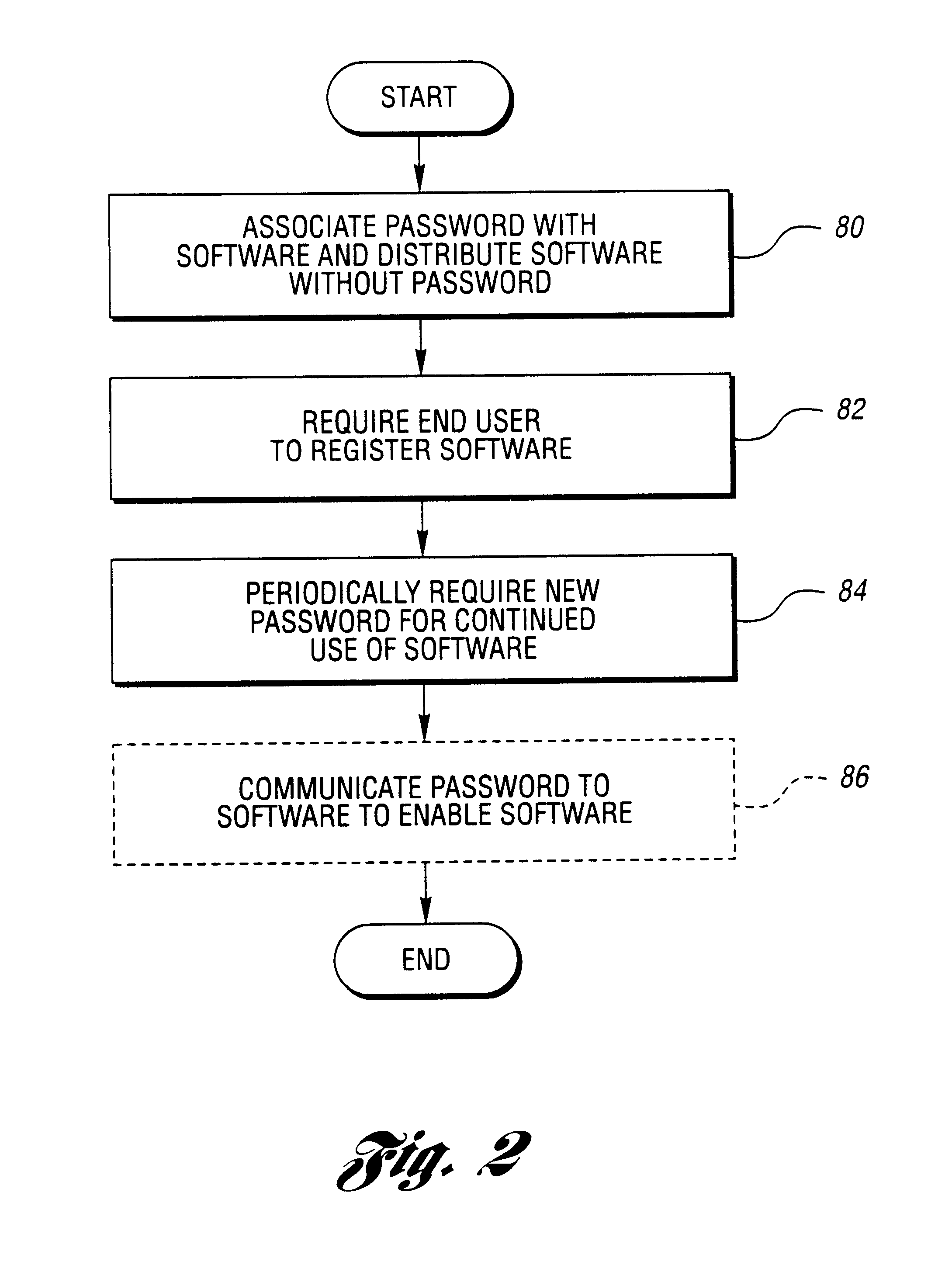
Method for securing software to increase license compliance
InactiveUS6857078B2Improve securityReduces unauthorized useDiscounts/incentivesMemory loss protectionSoftware engineeringAuthorization
A method for reducing unauthorized software use includes supplying a first authorization code with the software. The first authorization code enables the software on a computer for use by a user for an initial authorized period upon entry by the user. The user is required to contact the representative for retrieval of an additional authorization code. The software is operable during a subsequent authorization period beyond the initial authorization period without further or continual communication with the representative following entry of the additional authorization code. The user chooses manual or electronic registration and provides registration information to the representative prior to retrieval of the additional authorization code. The registration information includes computer specific information. The additional authorization code is communicated to the software upon the registration information indicating that the software has not been previously registered or upon the registration information matching a portion of previously provided registration information.
Owner:COLVIN DAVID S
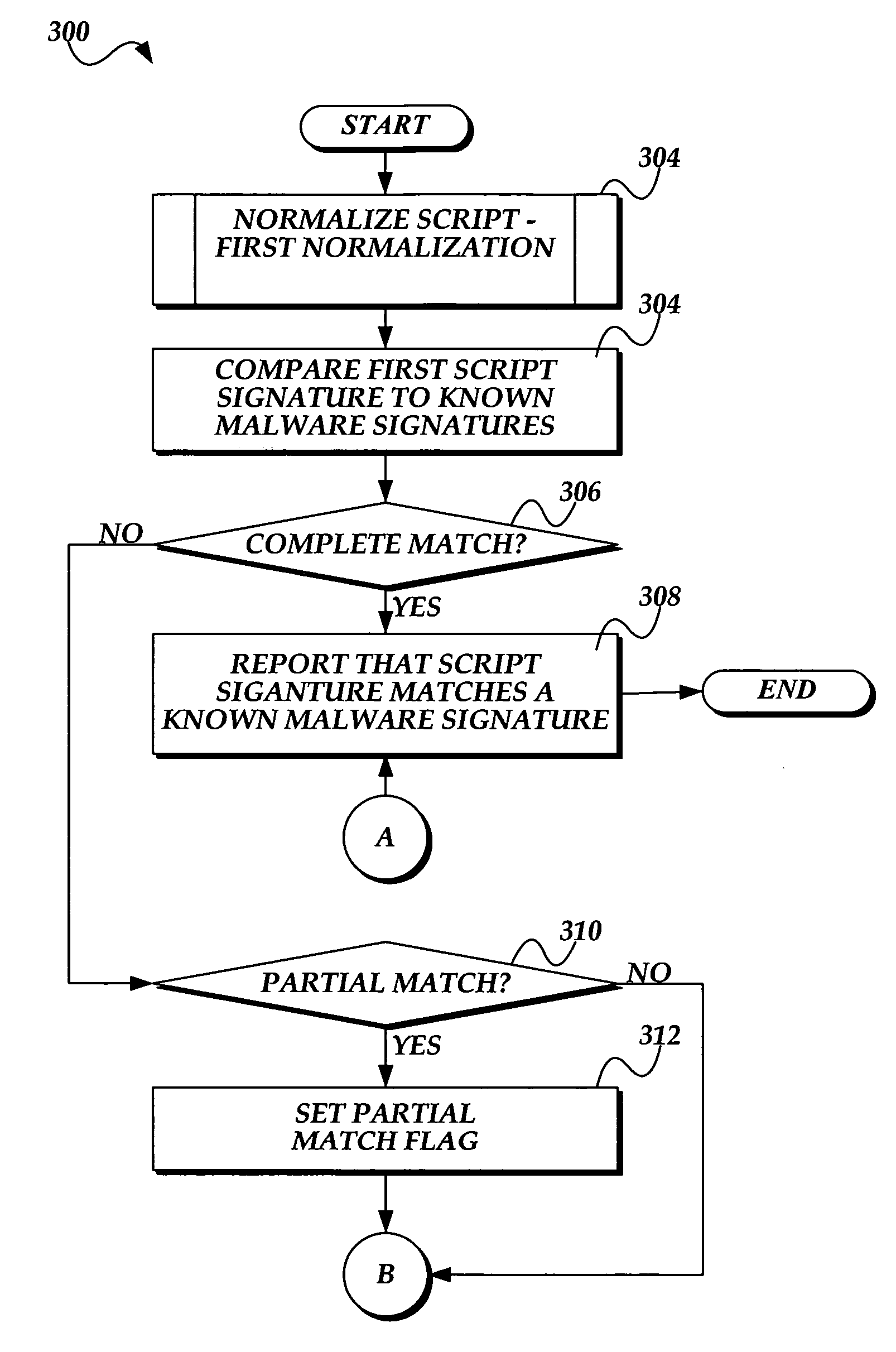
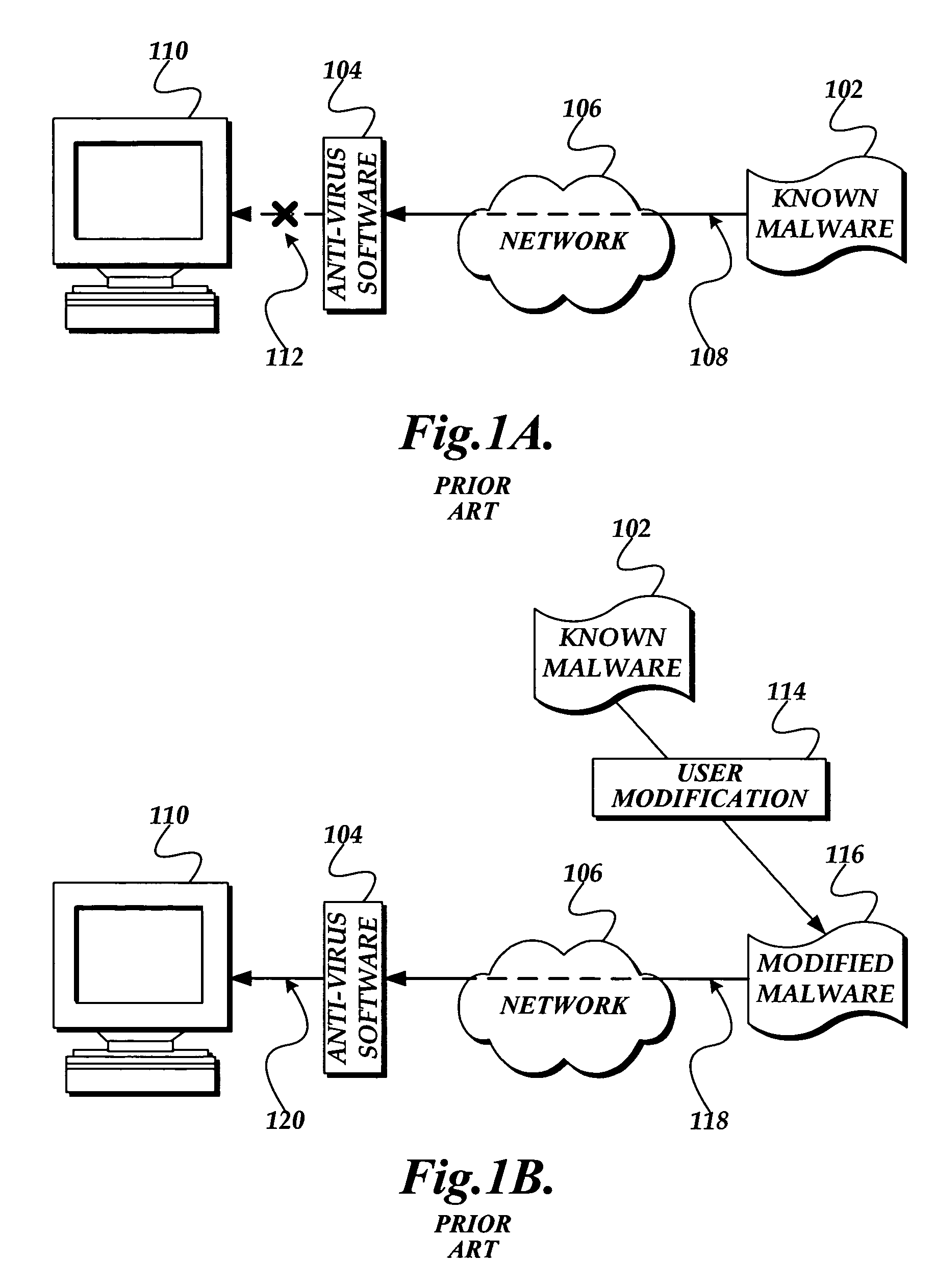
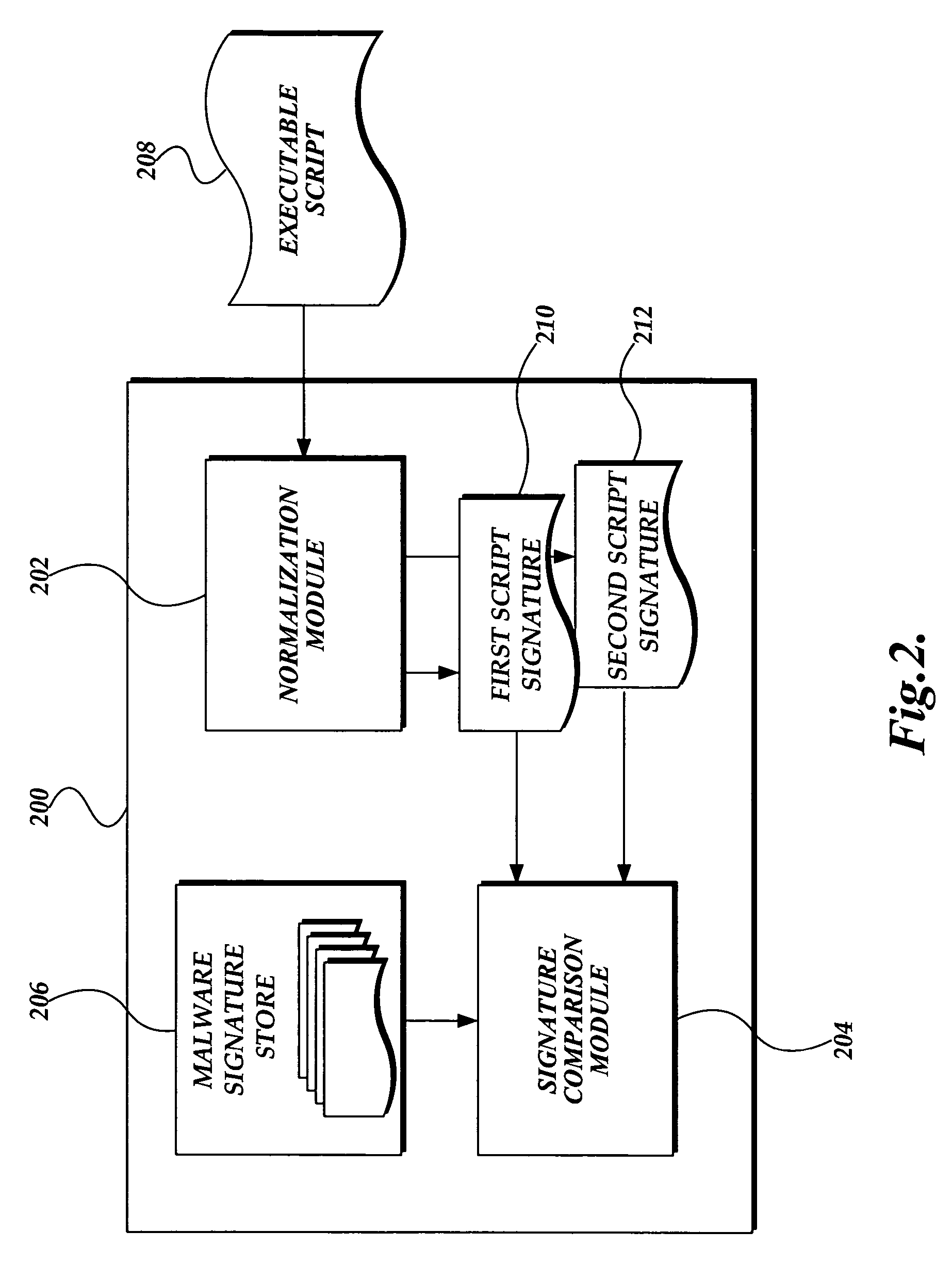
System and method for detecting malware in executable scripts according to its functionality
A malware detection system and method for determining whether an executable script is malware is presented. The malware detection system determines whether the executable script is malware by comparing the functional contents of the executable script to the functional contents of known malware. In practice, the executable script is obtained. The executable script is normalized, thereby generating a script signature corresponding to the functionality of the executable script. The script signature is compared to known malware script signatures in a malware signature store to determine whether the executable script is malware. If a complete match is made, the executable script is considered to be malware. If a partial match is made, the executable script is considered to likely be malware. The malware detection system may perform two normalizations, each normalization generating a script signature which is compared to similarly normalized known malware script signatures in the malware signature store.
Owner:MICROSOFT TECH LICENSING LLC
System and method for recognition in 2D images using 3D class models
ActiveUS20060285755A1Digital data information retrievalSpecial data processing applicationsPattern recognitionClass model
A system and method for recognizing instances of classes in a 2D image using 3D class models and for recognizing instances of objects in a 2D image using 3D class models. The invention provides a system and method for constructing a database of 3D class models comprising a collection of class parts, where each class part includes part appearance and part geometry. The invention also provides a system and method for matching portions of a 2D image to a 3D class model. The method comprises identifying image features in the 2D image; computing an aligning transformation between the class model and the image; and comparing, under the aligning transformation, class parts of the class model with the image features. The comparison uses both the part appearance and the part geometry.
Owner:STRIDER LABS
Method and apparatus for arranging social meetings
InactiveUS20060143214A1Convenient ArrangementFacilitates reservationDigital data information retrievalVideo gamesLibrary sciencePublic figure
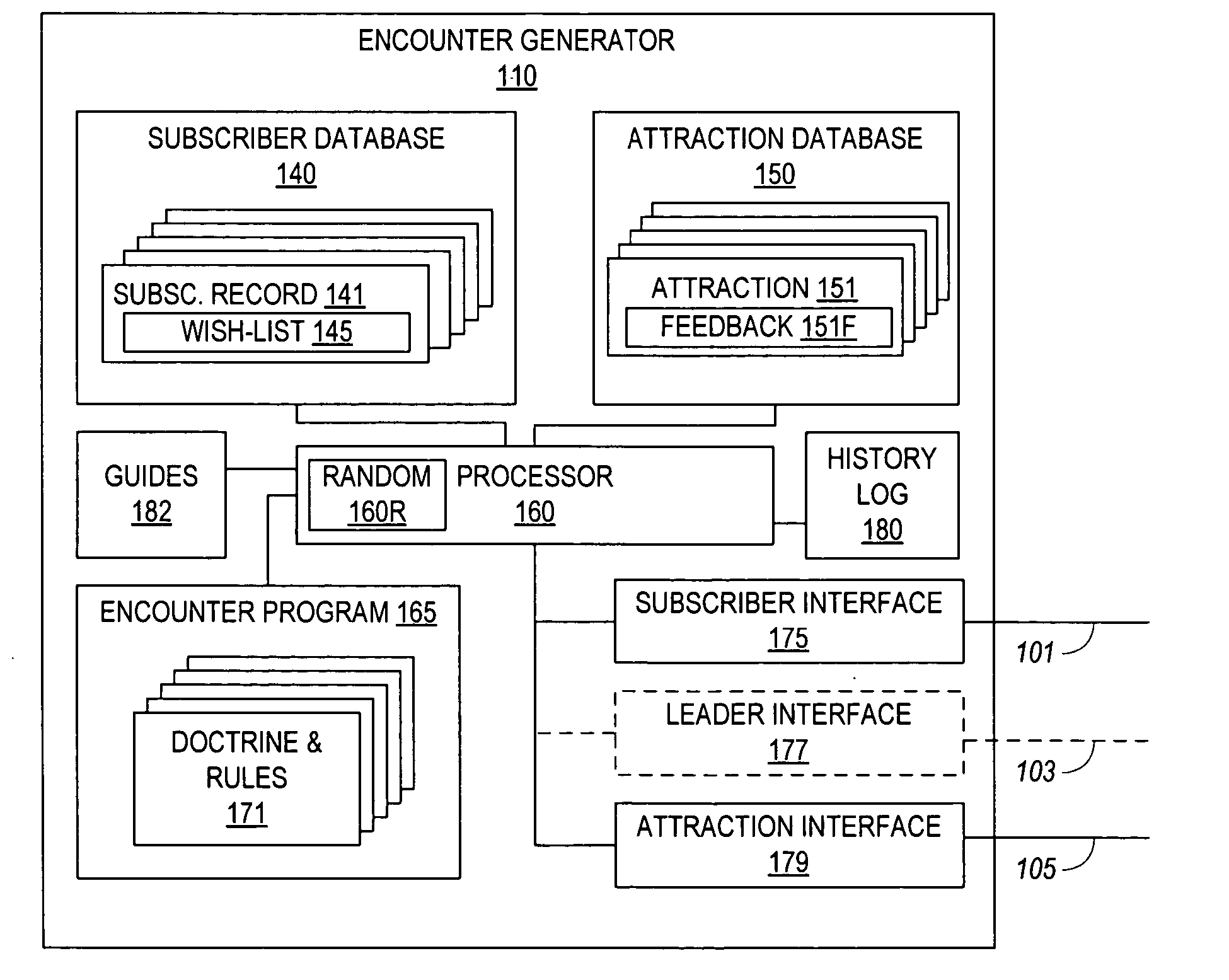
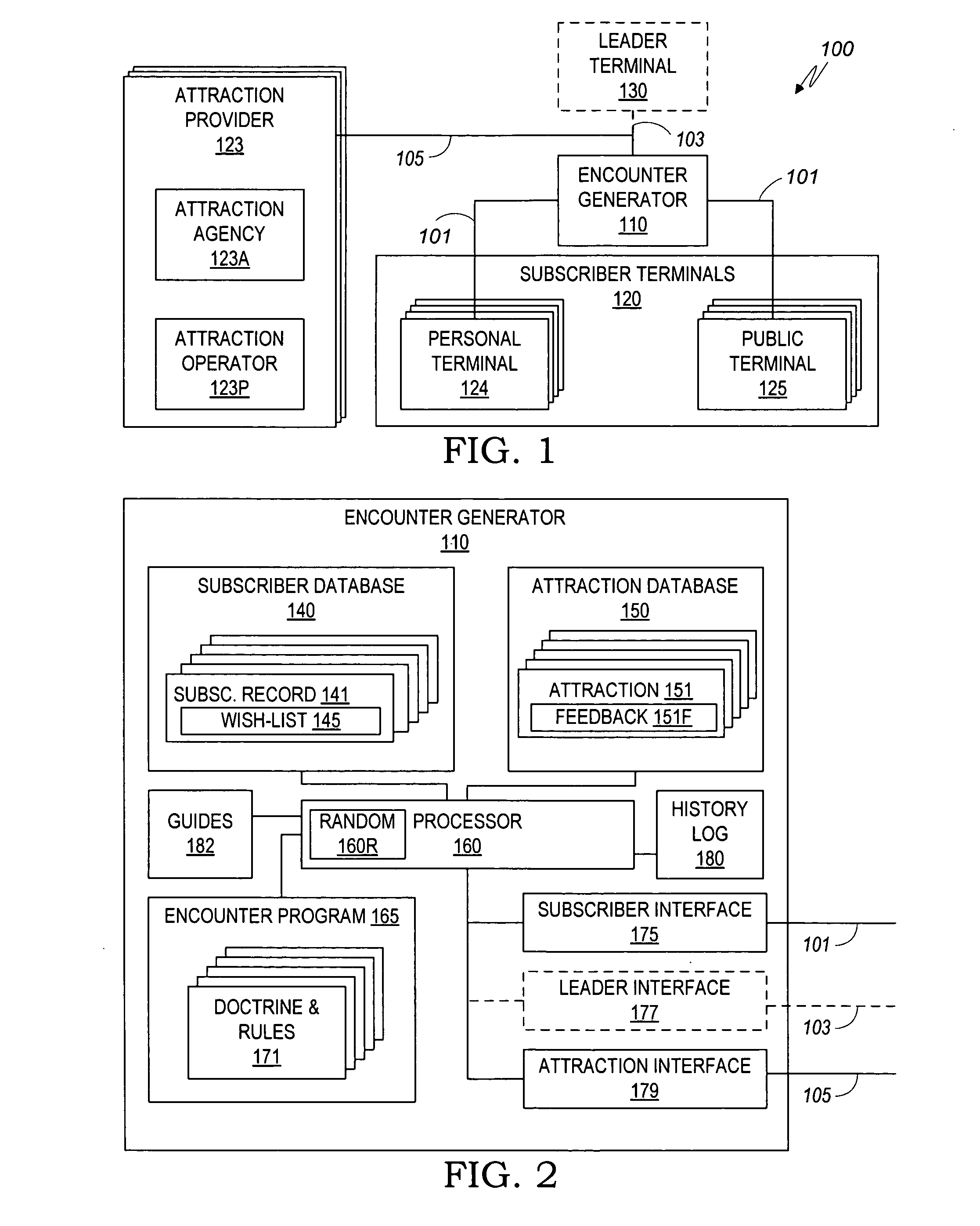
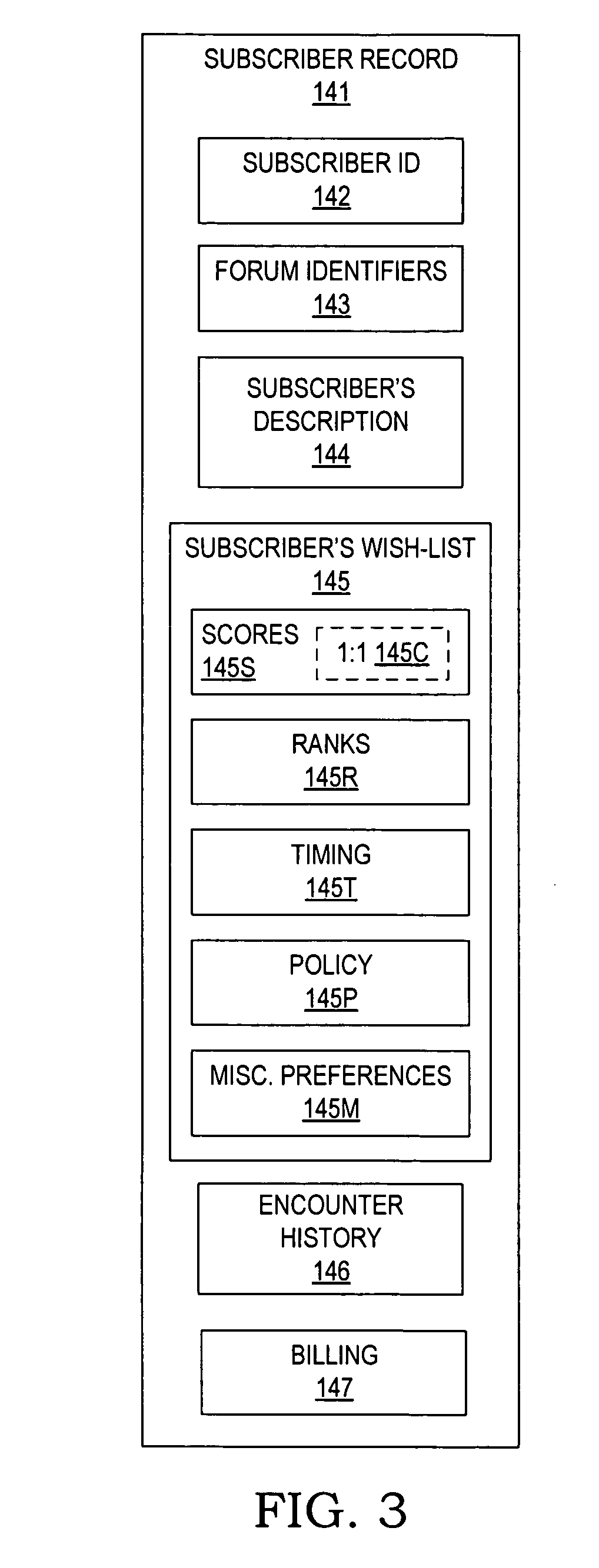
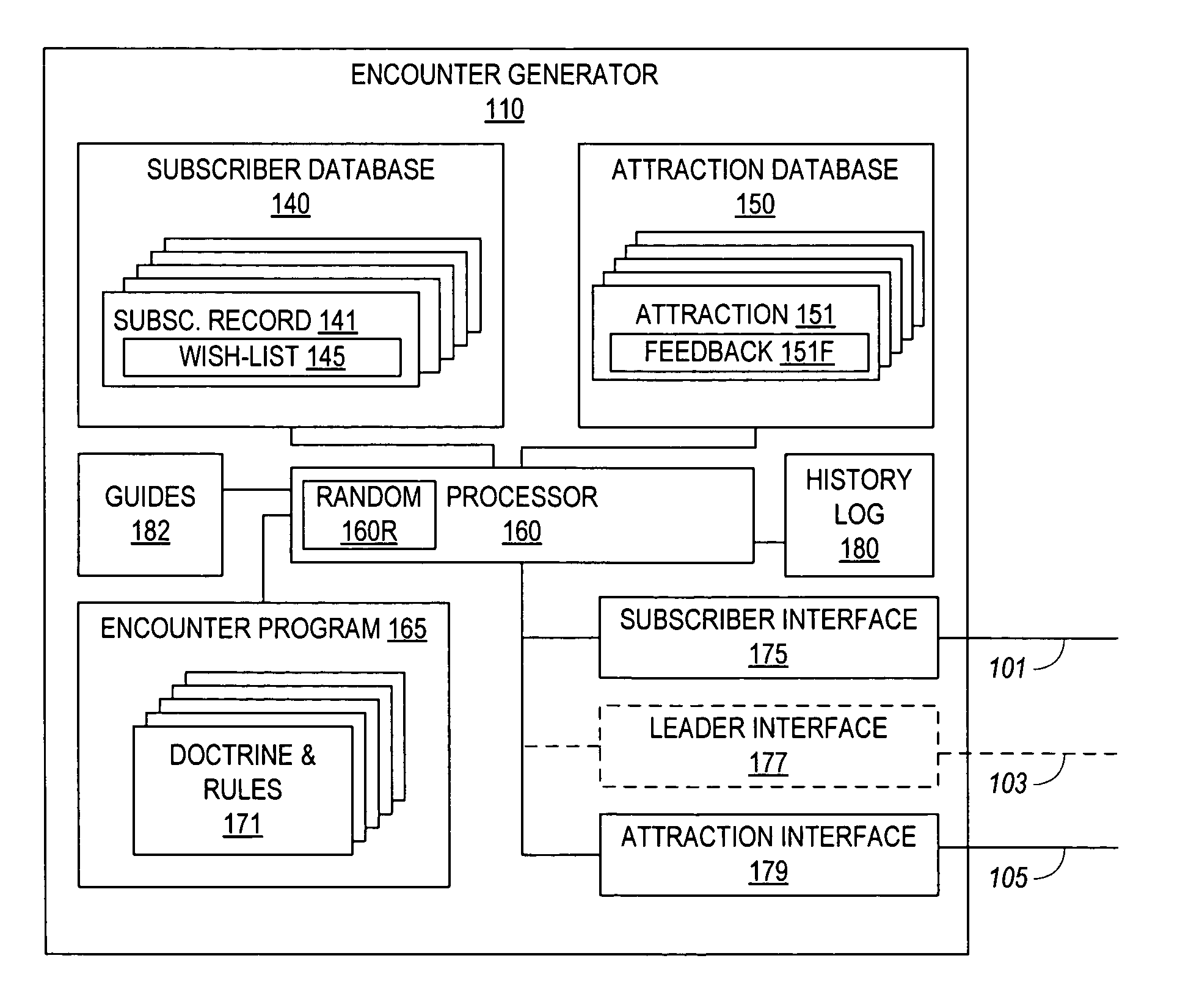
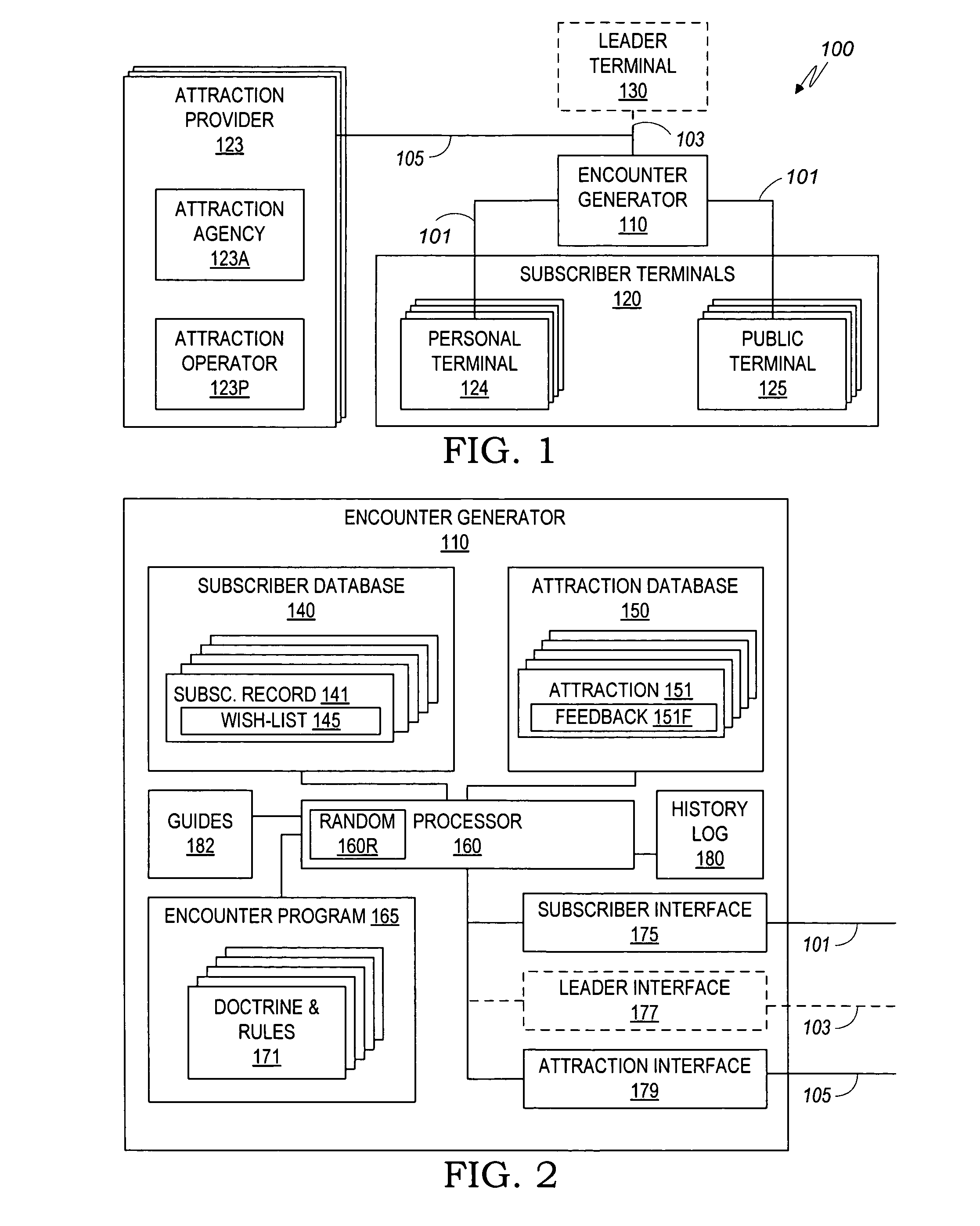
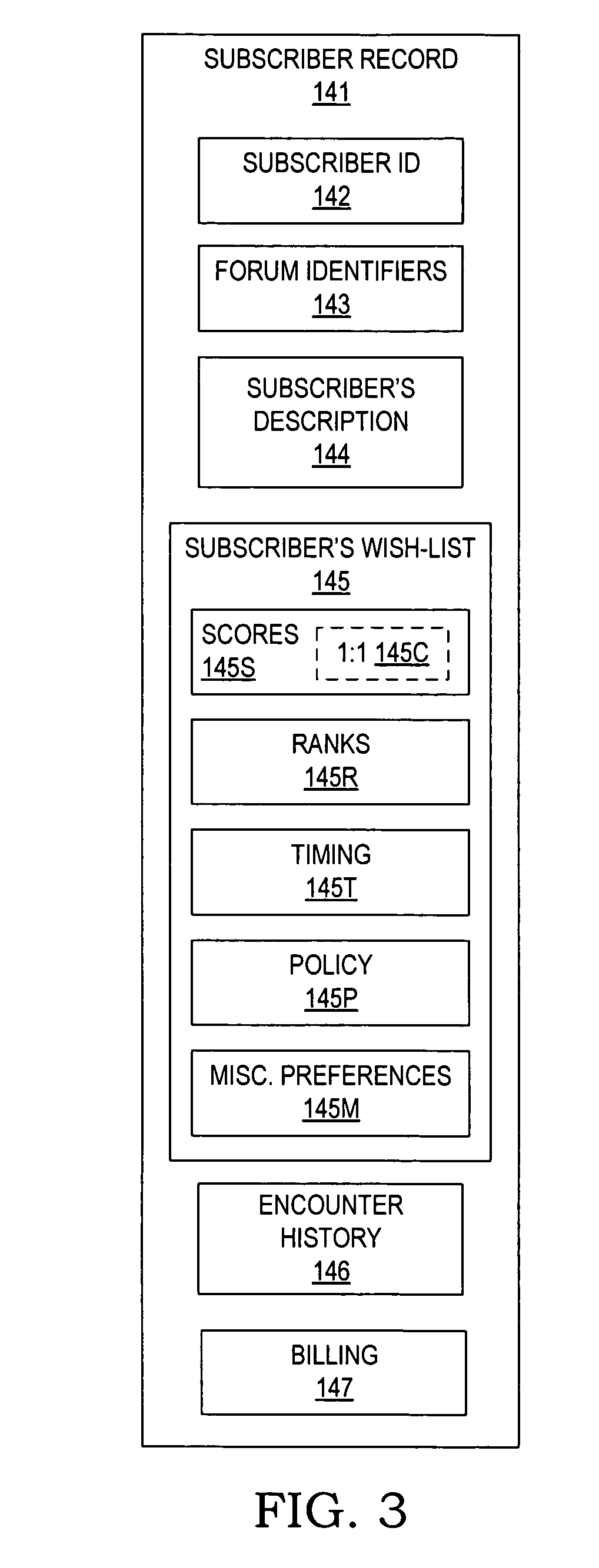
Individuals, couples, and families subscribe to a computerized service for facilitating the arrangement of their outings and social meetings. Subscribers fill in wish-lists to specify their level of interest in specific attractions, in getting together with specific other subscribers, and in arranging their preferred schedules for outings. An encounter generator processes the subscriber wish-lists to identify matches of subscribers who are interested in the same attraction, who favor each other's company, and who are free at the same time. The system notifies the matched subscribers, optionally offering ticketing and / or reservation assistance. Partial matches are optionally referred to the respective subscribers for negotiating the unmatched schedule or attraction. The system is adaptable to serve singles who wish to identify and get to know a prospective mate through mutual visits to attractions, as well as individuals, couples, and families who want to go out with their existing friends or make new friends.
Owner:TIES SOCIAL TECH
Method and system of providing a search tool
InactiveUS20110010367A1High response rateDigital data information retrievalDigital data processing detailsData miningRapid response
A system and method of providing information to improve efficiency of human searchers obtaining information on behalf of users is described. A first responder to a request is provided with specialized tools for responding to a request. An initial evaluation of a query may be used to determine the responder and the type of tools which will be provided initially. A toolset which allows rapid responses based on data resources, common queries, and contextual information of a user, a request, partially matching queries and previous responses to previous queries is used to improve the probability that a first responder may provide a suitable response to a query.
Owner:CHACHA SEARCH
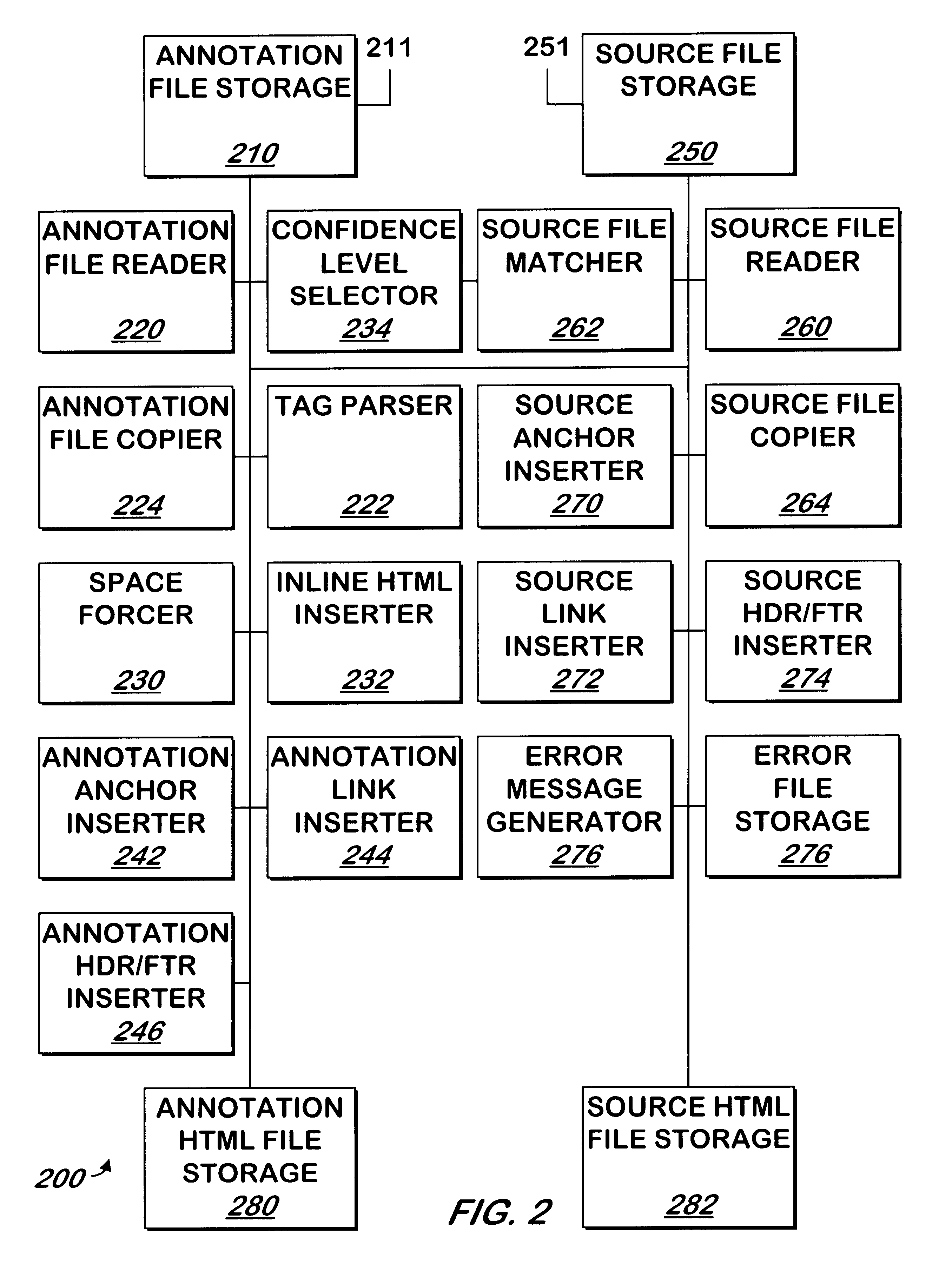
System and method for automated annotation of files
InactiveUS6572661B1Digital data information retrievalDigital computer detailsSoftware engineeringPartial match
Owner:CISCO TECH INC
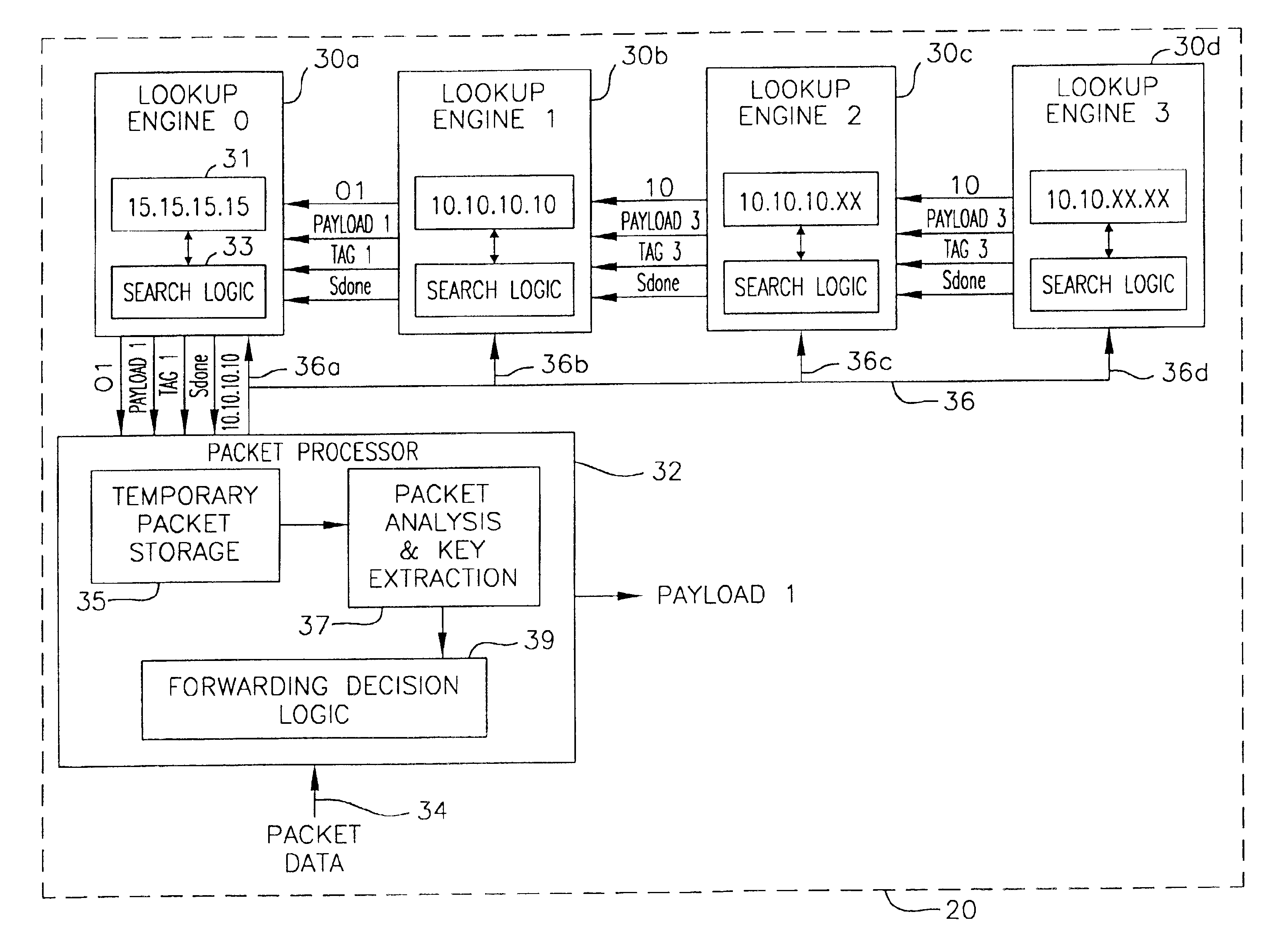
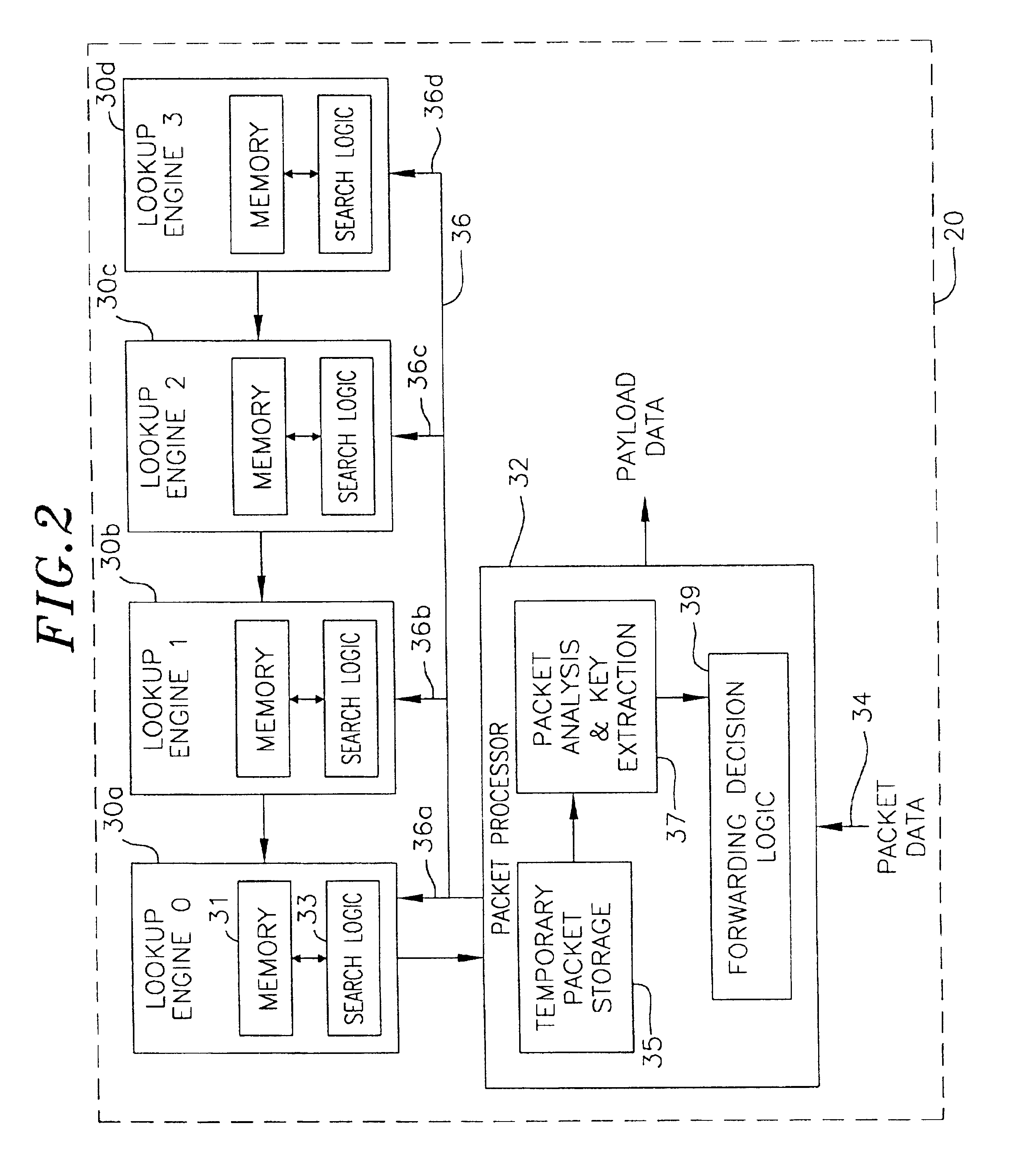
Stackable lookup engines
InactiveUS6957272B2Increase in sizeDigital computer detailsData switching by path configurationExact matchComputer science
Owner:ALCATEL INTERNETWORKING PE
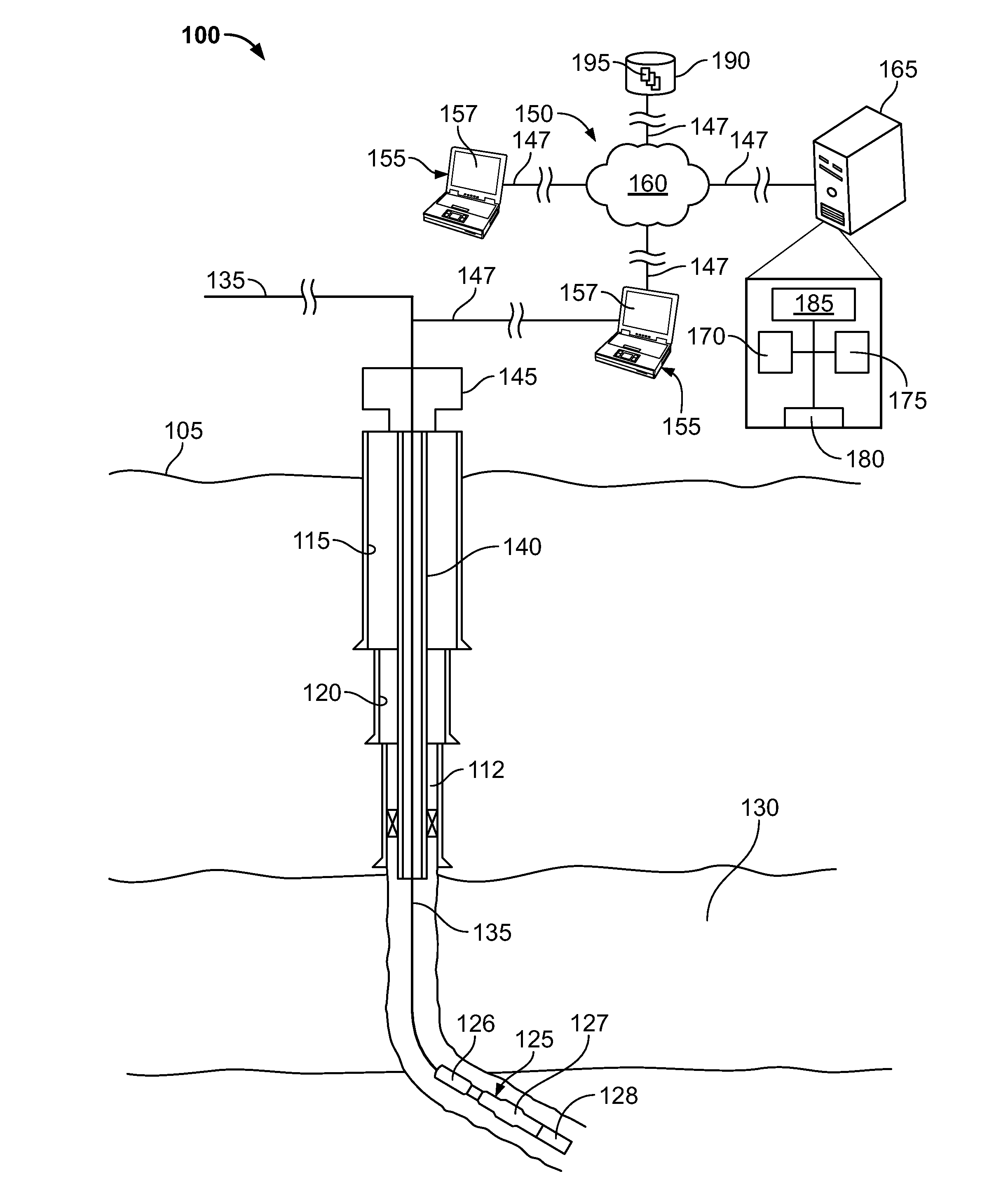
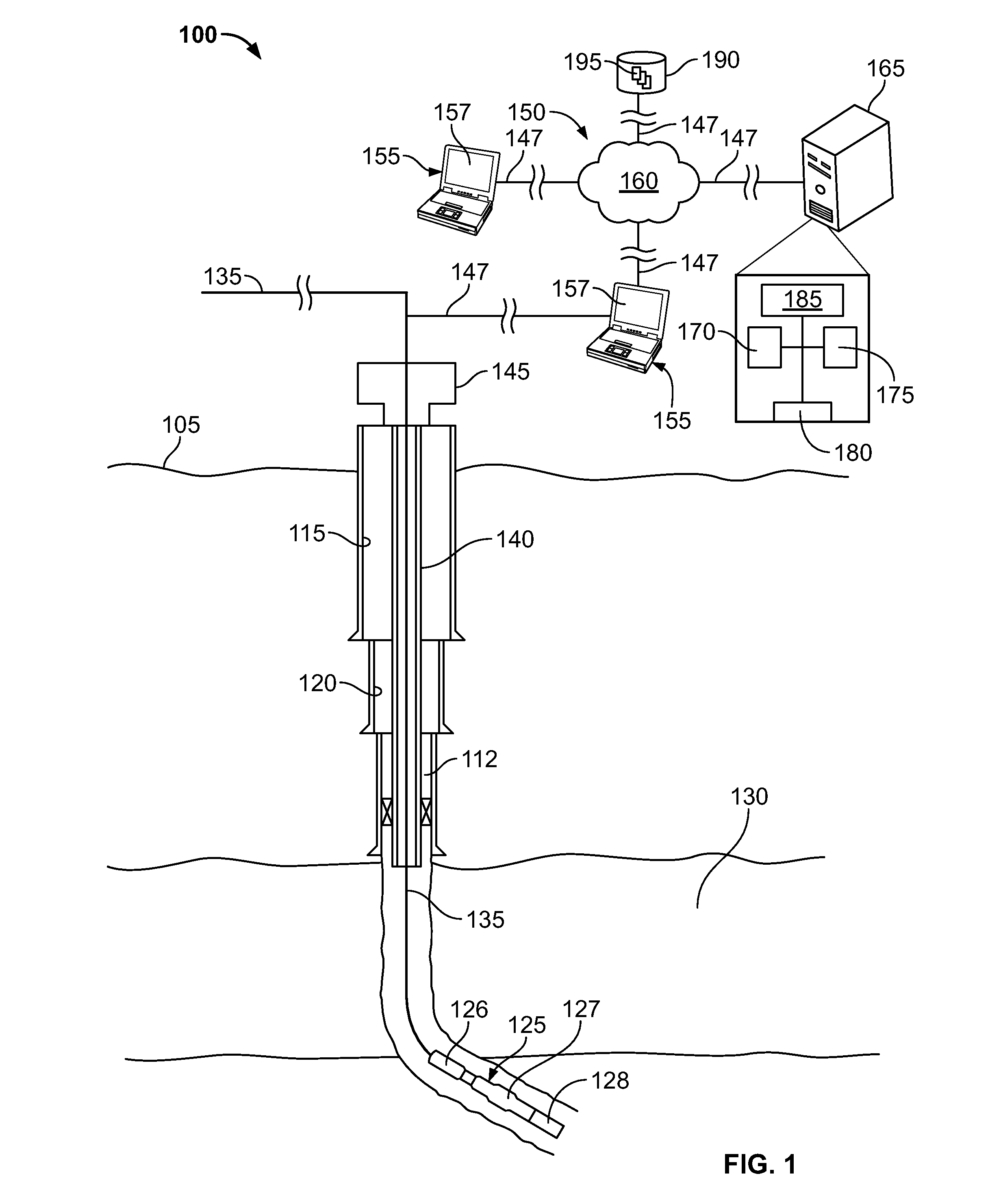
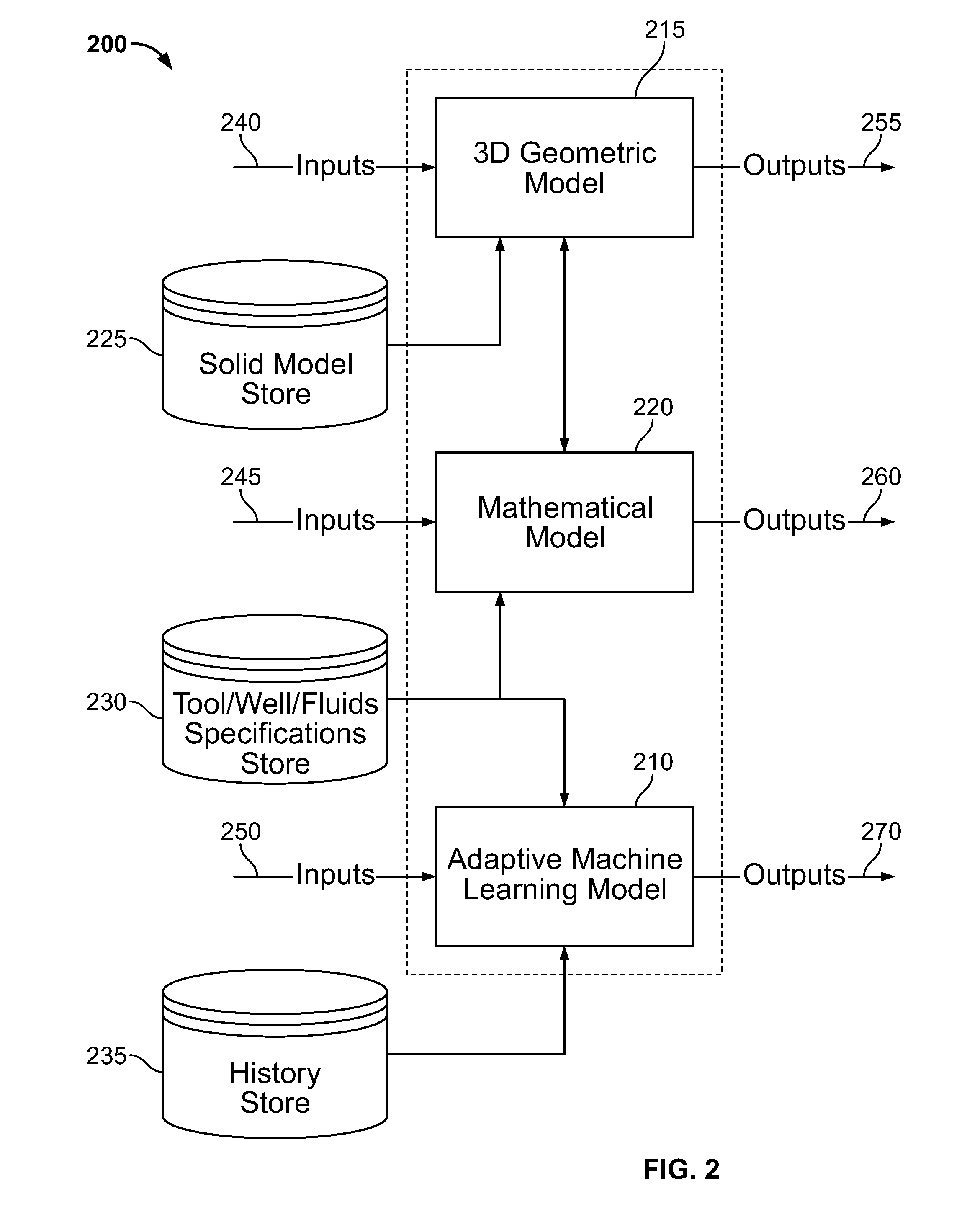
Modeling Passage of a Tool Through a Well
ActiveUS20130124176A1Special data processing applicationsMeasurement devices for drillingAlgorithmPartial match
In modeling passage of an elongate well tool through an interval of a well an adaptive machine learning model executed on a computing system receives a first set of inputs representing a plurality of characteristics of the well tool and a second set of inputs representing a plurality of characteristics of the well. The adaptive machine learning model also receives historical data representing a plurality of other well tools passed through a plurality of other wells and a plurality of characteristics of the other well tools and the other wells. The adaptive machine learning model matches the historical data with at least a portion of the first and second sets of inputs, and determines, based on the matching whether the well tool can pass through the interval of the well.
Owner:HALLIBURTON ENERGY SERVICES INC
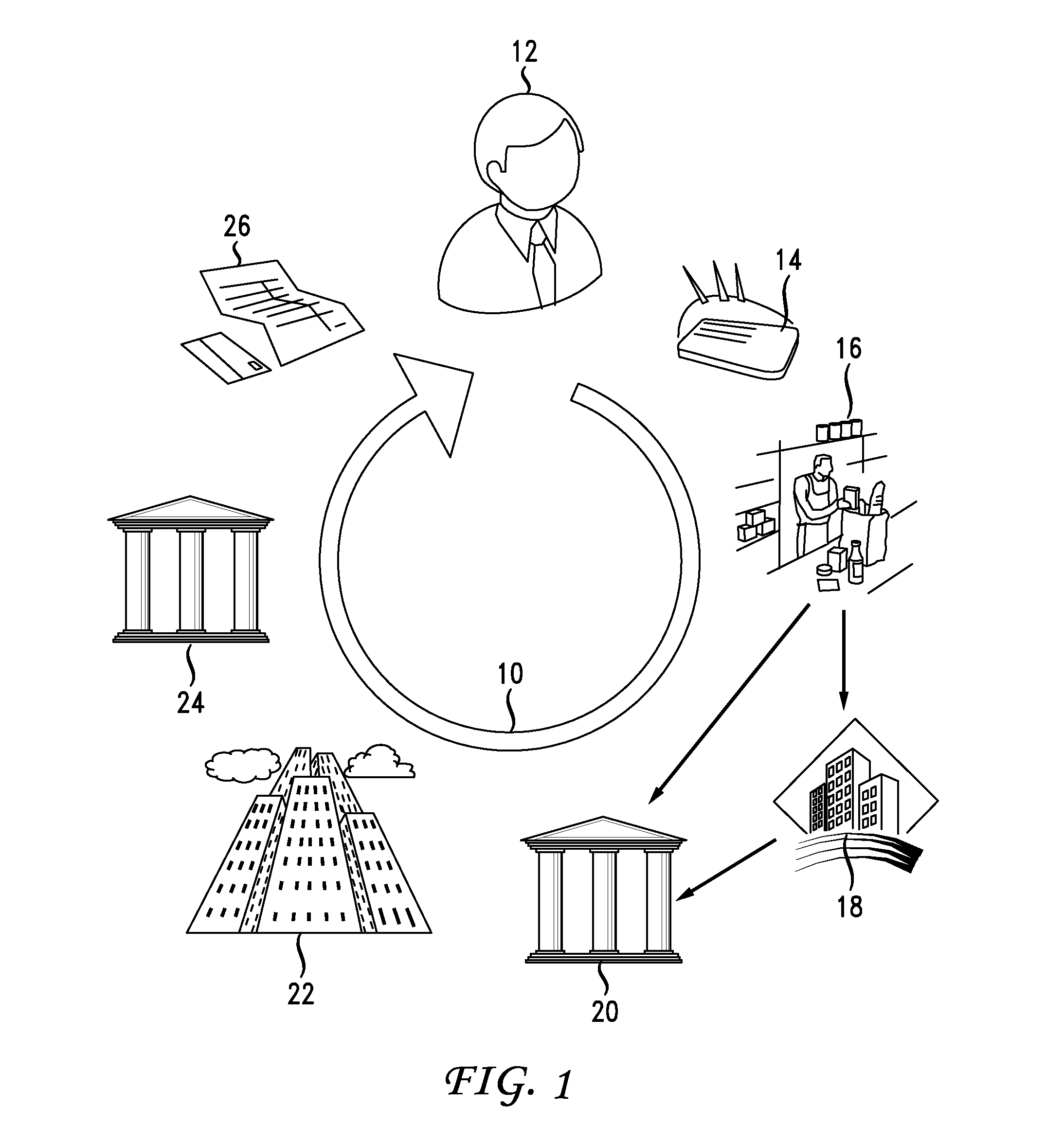
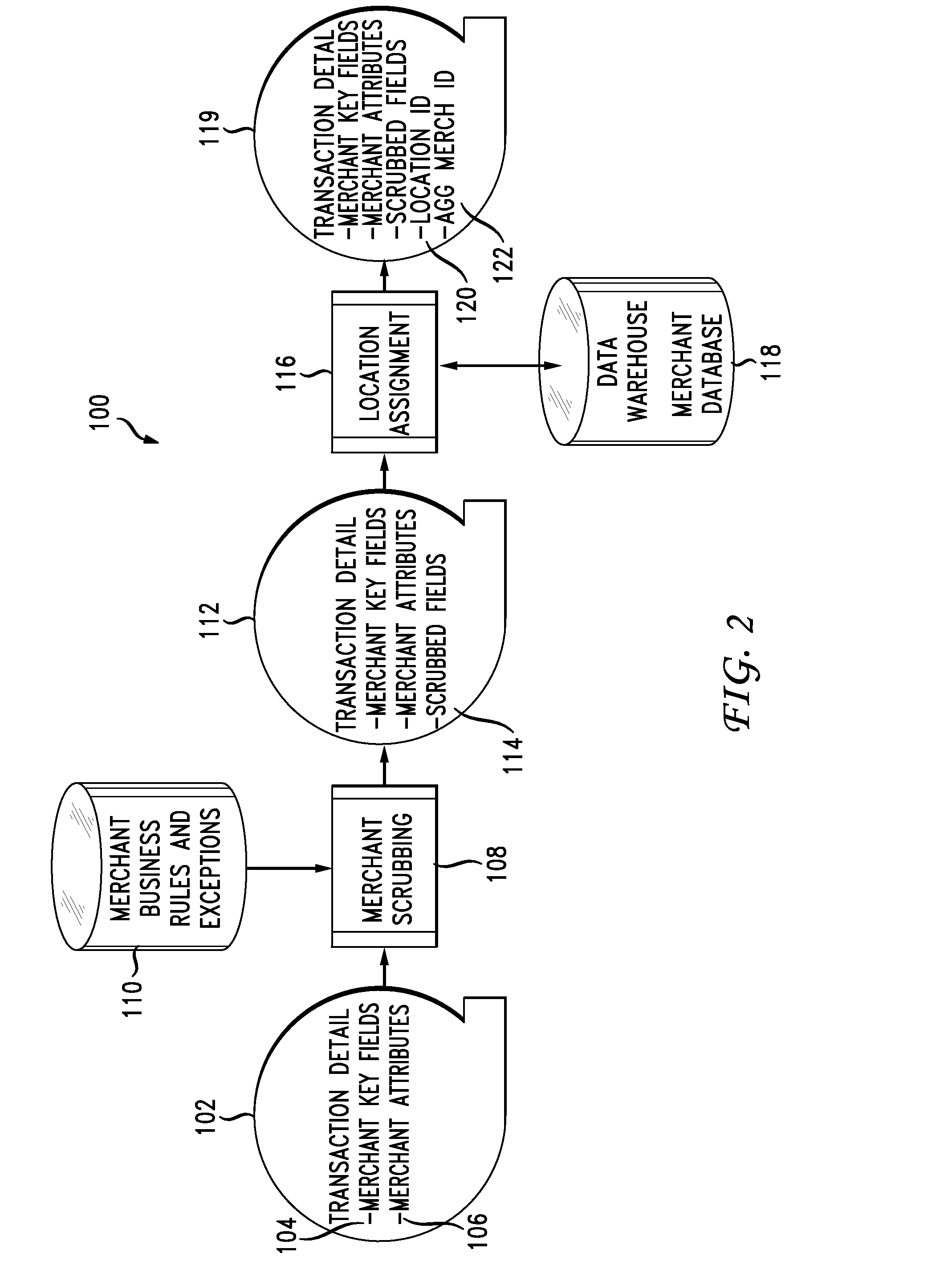
Instantaneous merchant information retrieval for financial transactions
A solution to disambiguate ambiguous merchant data in connection with processing a cashless transaction request in a real-time manner. Provided according to the present disclosure are a system and method including a binary-searchable non-transitory computer-readable medium is configure to store a first set of unambiguous merchant identification data having plural data entries therein, each entry corresponding to a merchant. A binary search of the first set of unambiguous merchant identification data is carried out using search keys based upon the ambiguous merchant identification data to determine whether one or more entries of the first set satisfies at least one of a hierarchical second set of partial match criteria for comparing the ambiguous merchant identification data with the first set of unambiguous merchant identification data. An entry of the first set of unambiguous merchant identification data is assigned to correspond with the ambiguous merchant identification data where at least a predetermined number of the second set of partial match criteria are met.
Owner:MASTERCARD INT INC
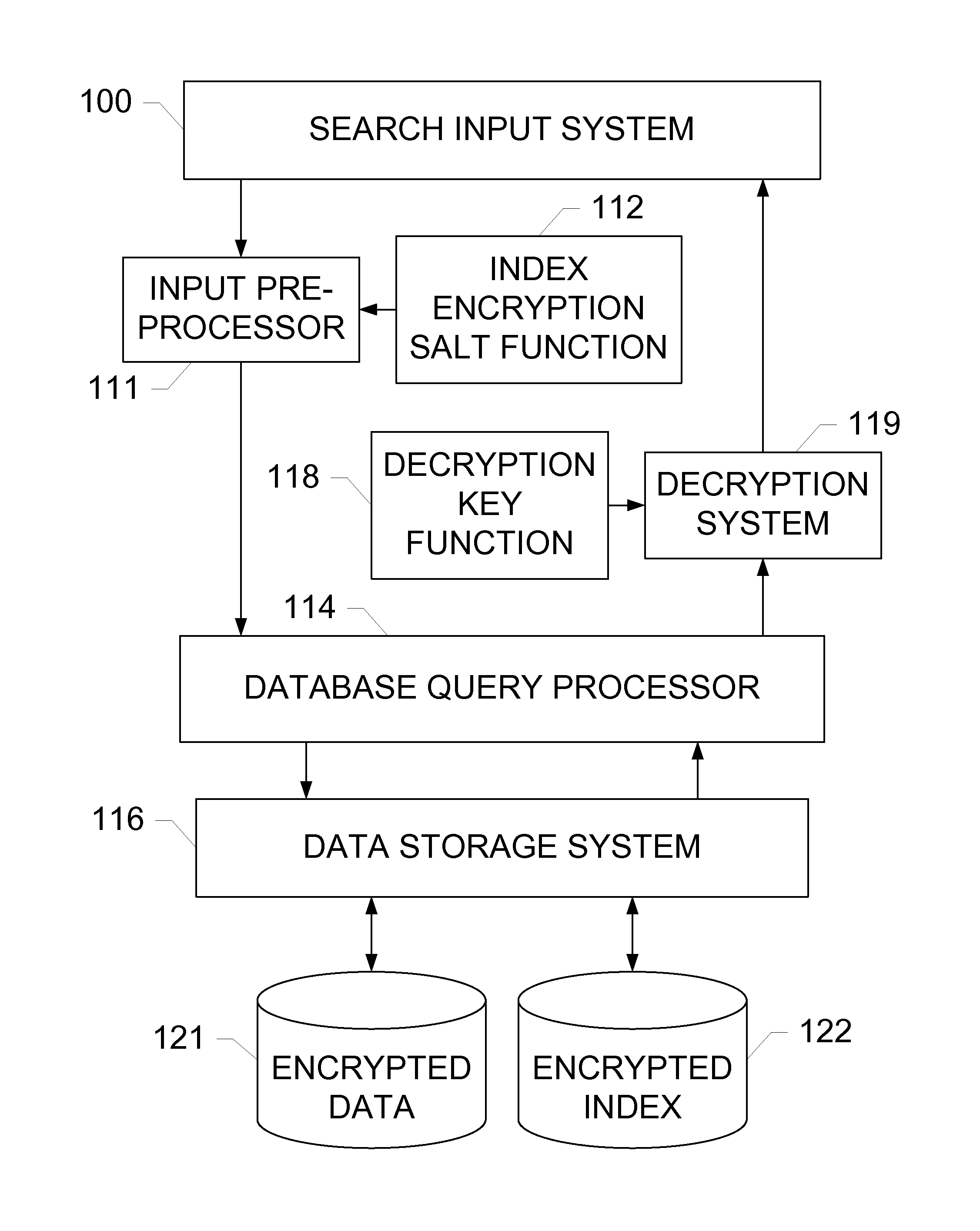
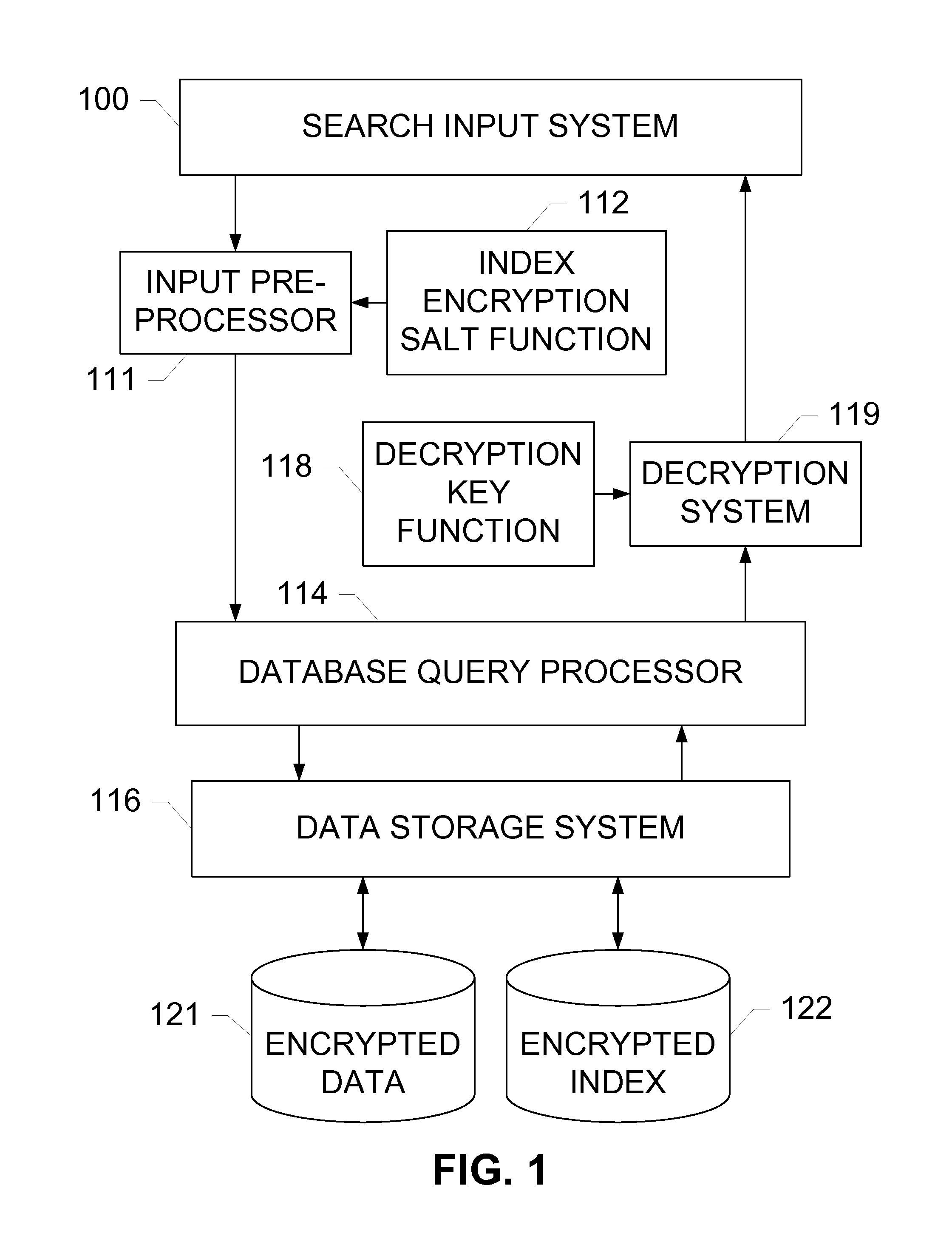
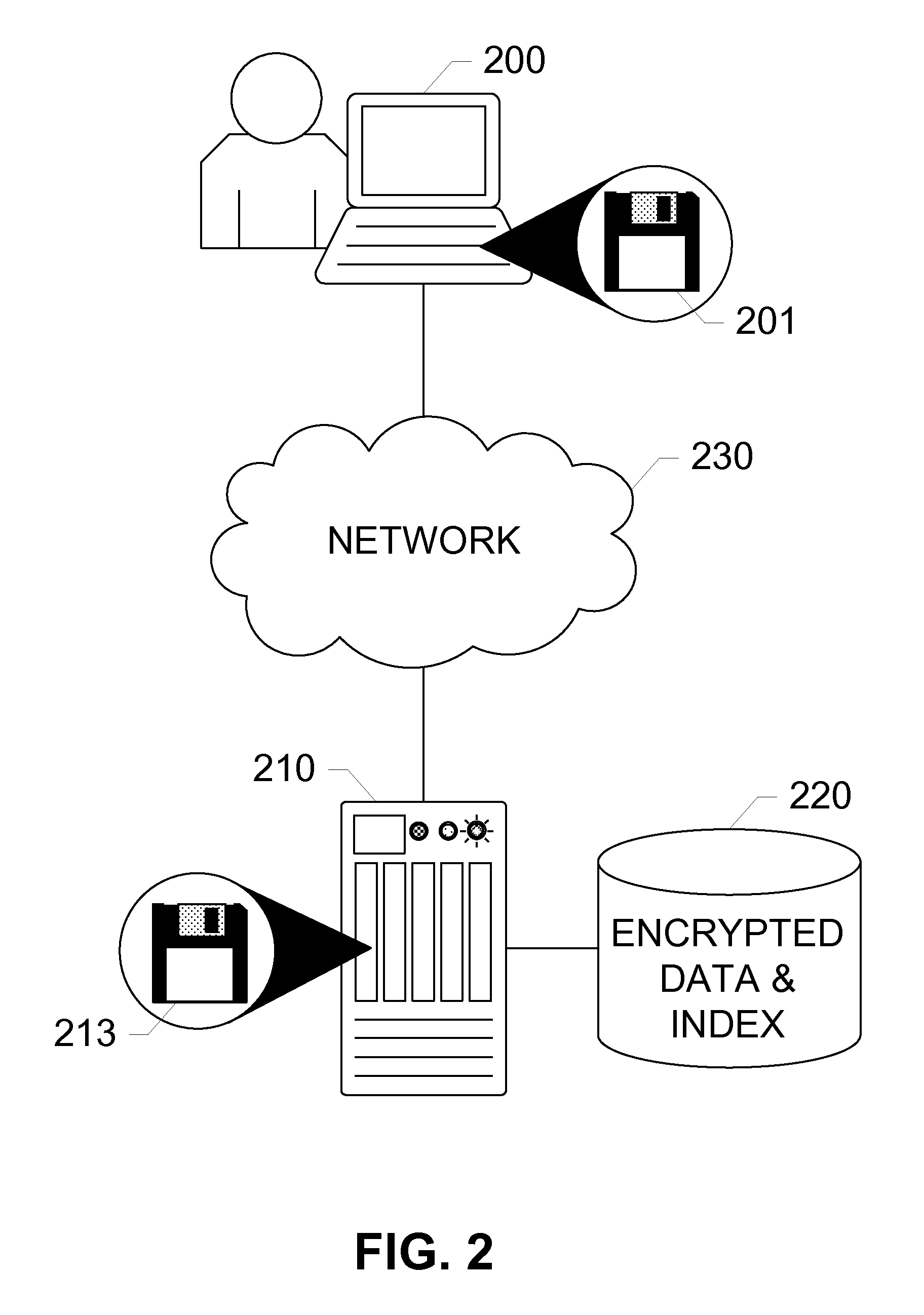
Partial-Match Searches of Encrypted Data Sets
InactiveUS20130238646A1Digital data processing detailsComputer security arrangementsData setHash table
Devices, systems, and methods are disclosed which relate to utilizing hash tables of chunks of index data created using a one-way hashing encryption algorithm. Hash tables of chunks of the index data are then stored within the database system, each hash stored along with a reference to a corresponding encrypted record. When searching the index, the input text is broken into chunks and hashed with the same one-way encryption algorithm as the index data, and the resulting chunk hash tables are searched for within the index.
Owner:EVRICHART
Prefix Domain Matching for Anti-Phishing Pattern Matching
Phishing uniform resource locators are detected and / or filtered. After a uniform resource locator is received, it is determined if at least a portion of a prefix of the uniform resource locator matches at least a portion of a blacklist entry and the uniform resource locator is filtered if at least a portion of the prefix of the uniform resource locator matches at least a portion of the blacklist entry. The prefix of the uniform resource locator is constrained to be a predetermined number of the highest level domain labels of the domain name in the received uniform resource locator.
Owner:AT&T INTPROP I L P
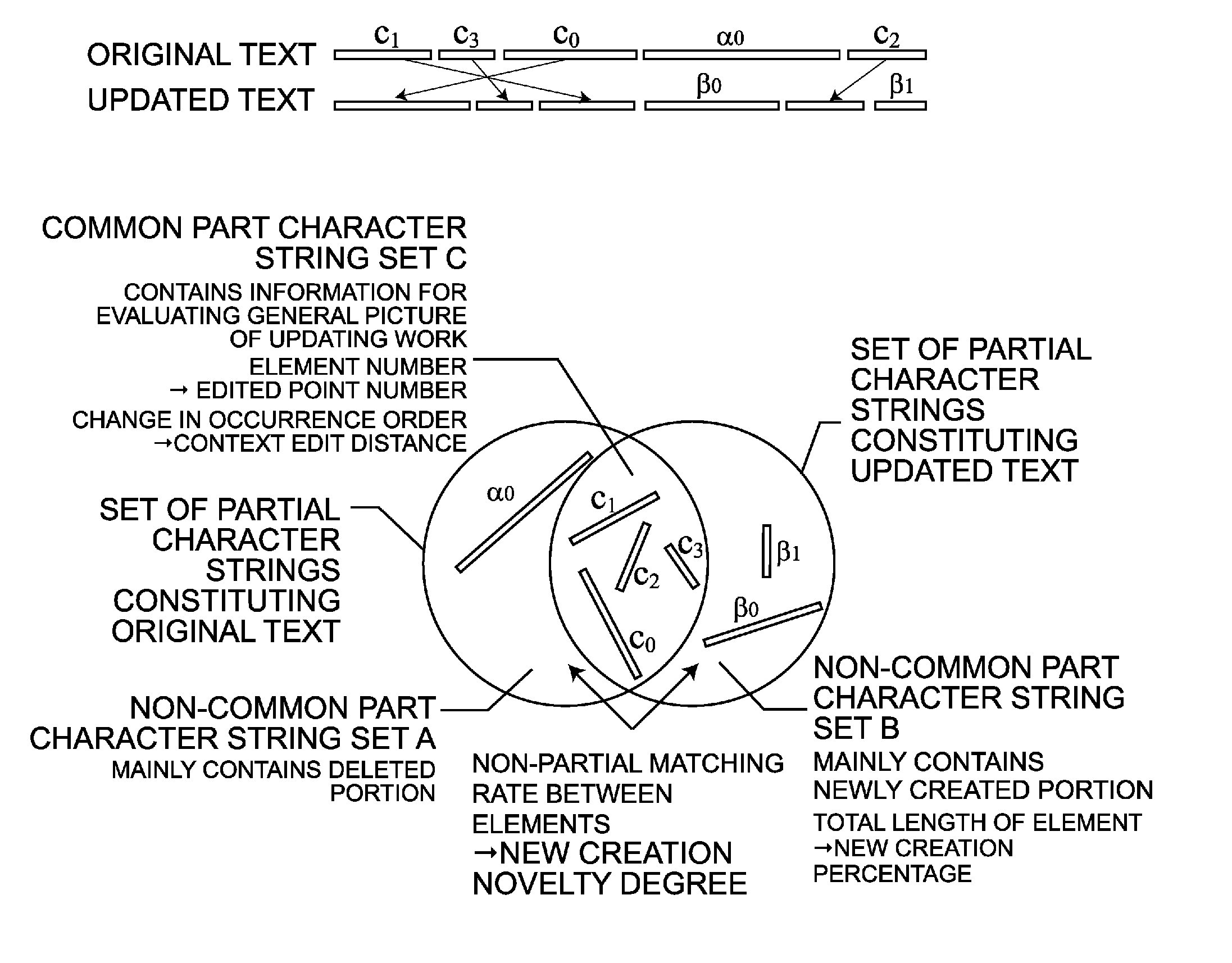
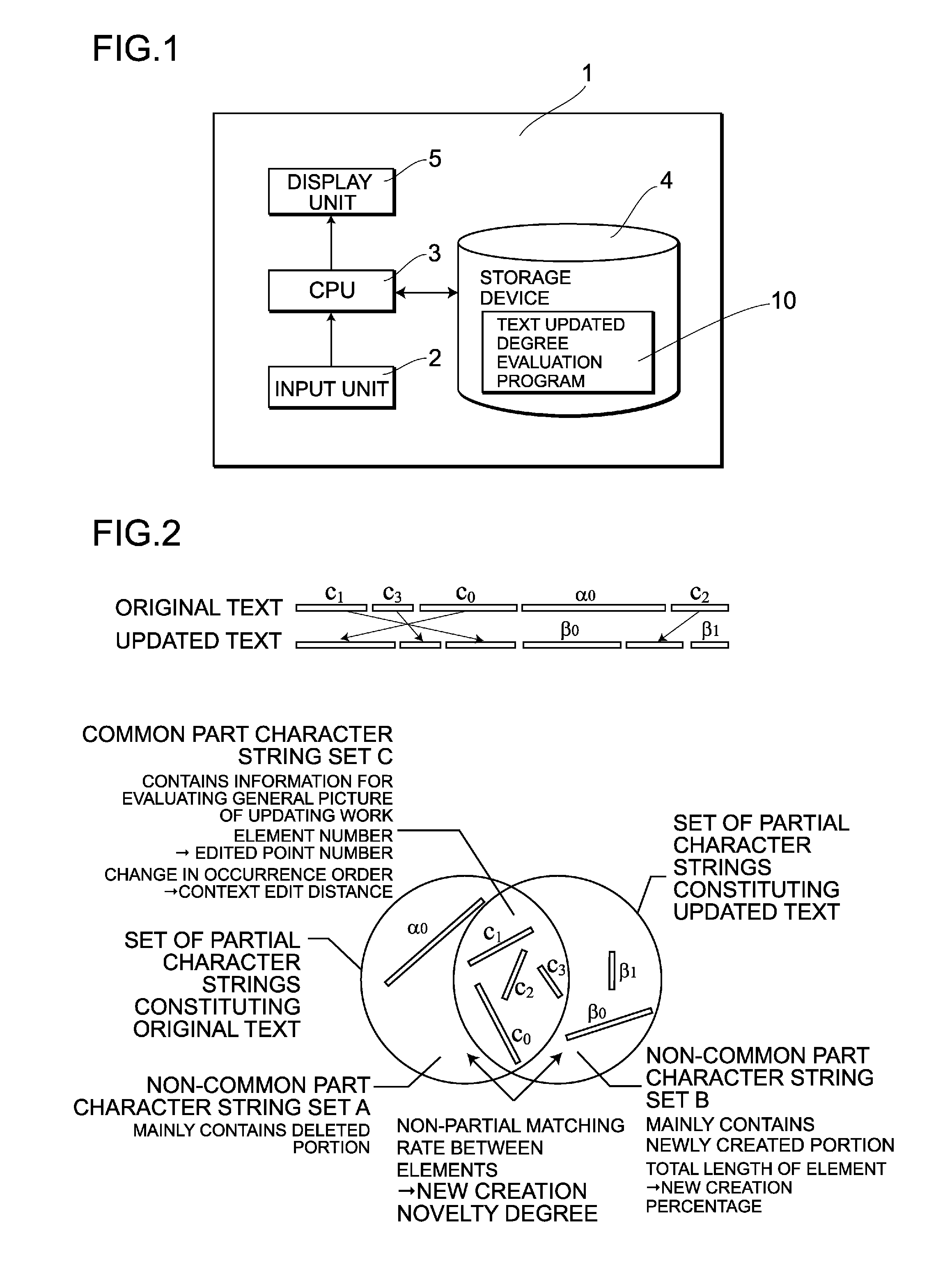
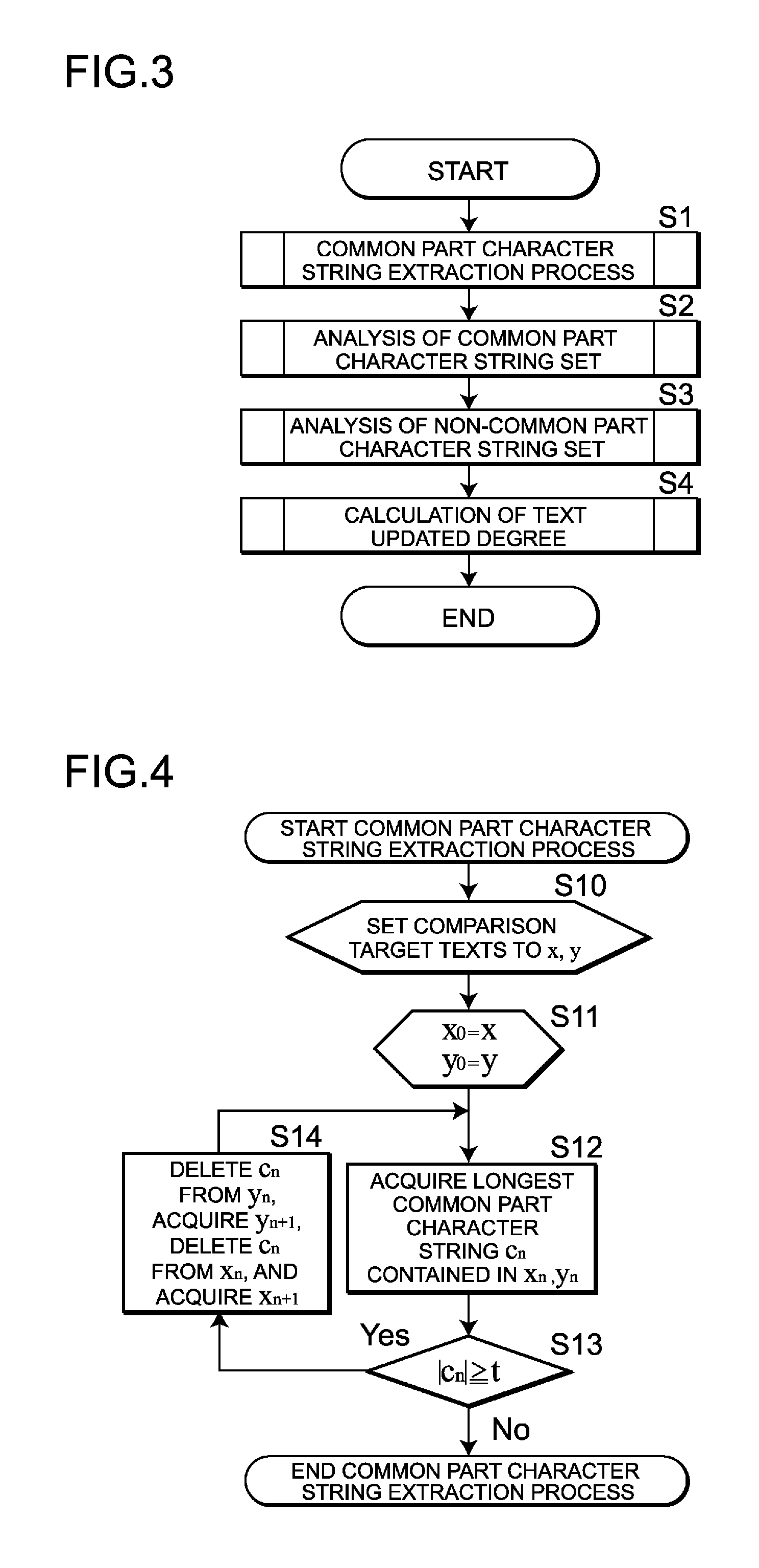
Character string updated degree evaluation program
InactiveUS20090226098A1Digital data information retrievalCharacter and pattern recognitionTheoretical computer scienceEdit distance
There is provided a character string updated degree evaluation program that enables quantitative grasping of an amount of intellectual work through editing and updating of character strings. A text subjected to comparison is divided into common part character strings each having a length greater than or equal to a threshold value, and non-common part character strings. A number of edited points from the original text and a context edit distance are calculated based on the rate of the common part character strings and the occurrence pattern thereof. A number of edited point is acquired from a number of elements contained in a common part character string set, and a context edit distance is acquired from a change in an order of occurrence of the common part character strings. Calculation of a new creation percentage and analysis by an N-gram are performed on the non-common part character string. The new creation percentage is acquired from the total length of the elements contained in a non-common part character string set, and a new creation novelty degree is acquired from a non-partial matching rate between a non-common part character string set and an element contained in the non-common part character string set. Calculations for the common part character string set and for the non-common part character string set are united, thereby calculating a text updated degree.
Owner:NAT UNIV CORP NAGAOKA UNIV TECH
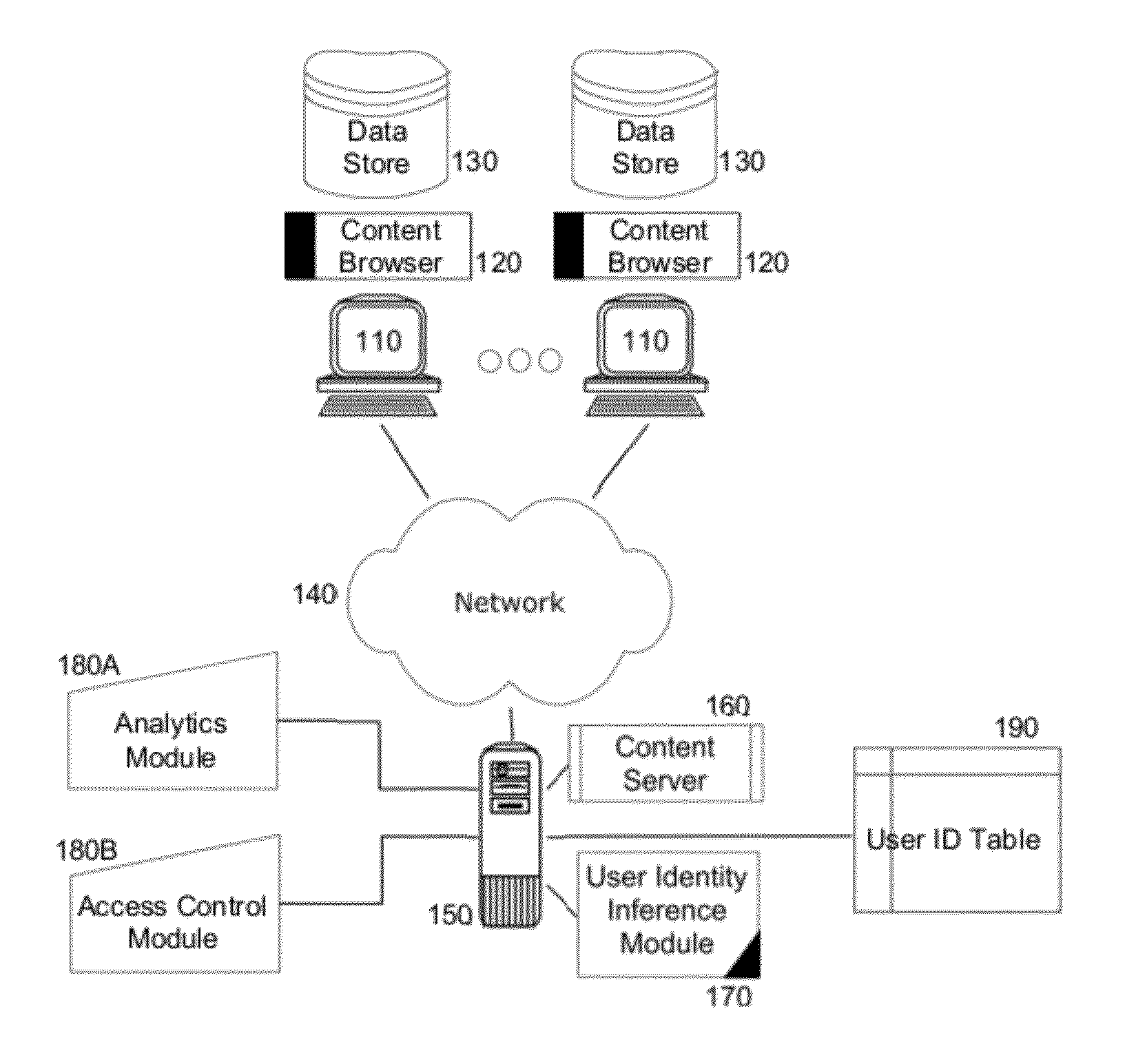
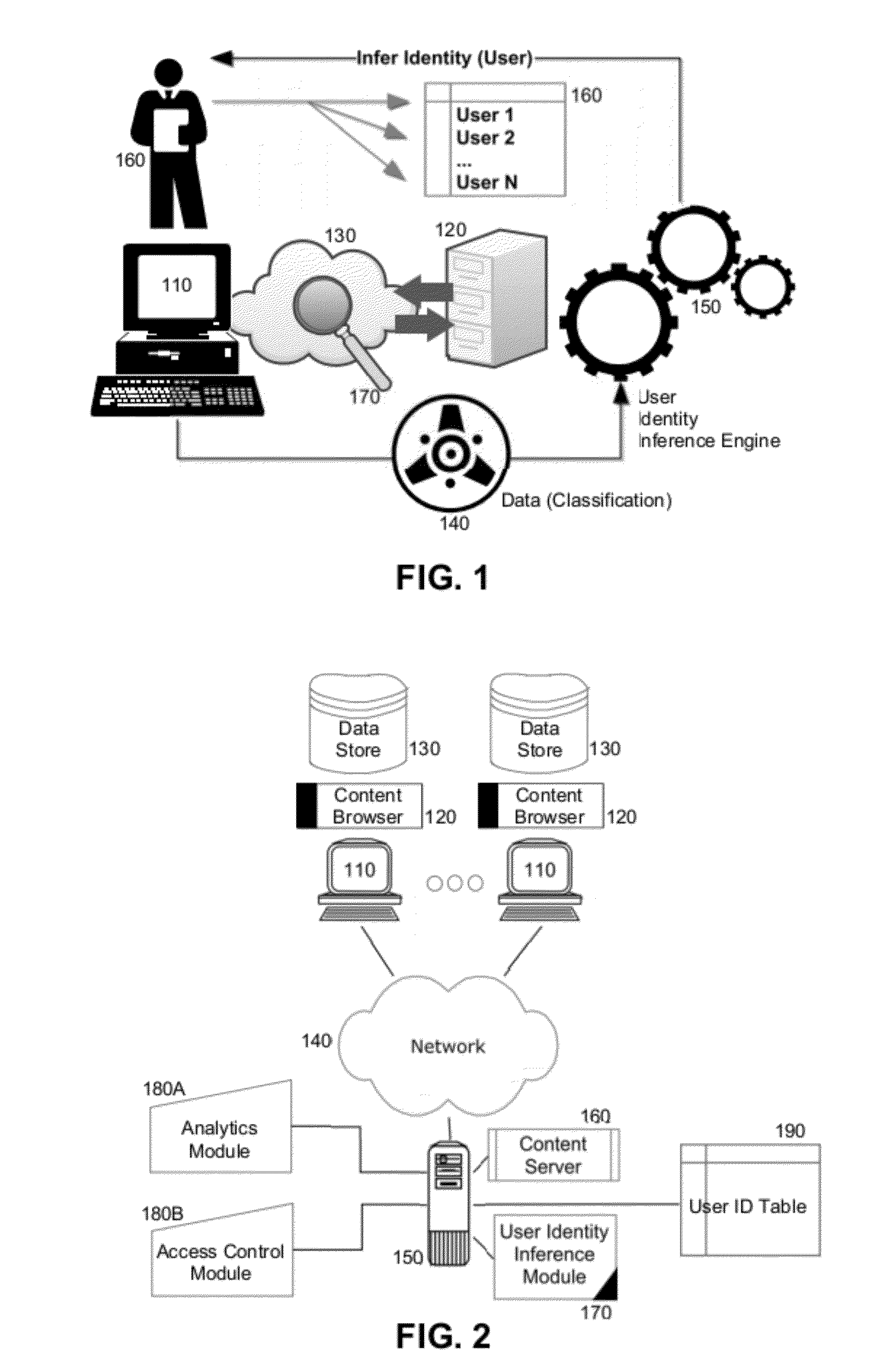
Inferred user identity in content distribution
ActiveUS20120310980A1Digital data processing detailsSpecial data processing applicationsContent distributionData set
Embodiments of the present invention provide a method, system and computer program product for inferred user identity in content distribution. In an embodiment of the invention, a method for inferred user identity in content distribution includes retrieving a set of data of a particular classification from a data store of a computing device of an unidentified user requesting access to content in a content distribution system. The method further includes comparing the set of data of the particular classification to known patterns of data of the particular classification corresponding to different known users. The method yet further includes inferring an identity of the unidentified user based upon at least a partial matching of the compared set of data of the particular classification and known patterns of data of the particular classification. Finally, the method includes managing user interactions of the unidentified user based upon the inferred identity.
Owner:IBM CORP
Method and apparatus for arranging social meetings
InactiveUS7761386B2Convenient ArrangementEasy to bookDigital data information retrievalVideo gamesLibrary sciencePartial match
Individuals, couples, and families subscribe to a computerized service for facilitating the arrangement of their outings and social meetings. Subscribers fill in wish-lists to specify their level of interest in specific attractions, in getting together with specific other subscribers, and in arranging their preferred schedules for outings. An encounter generator processes the subscriber wish-lists to identify matches of subscribers who are interested in the same attraction, who favor each other's company, and who are free at the same time. The system notifies the matched subscribers, optionally offering ticketing and / or reservation assistance. Partial matches are optionally referred to the respective subscribers for negotiating the unmatched schedule or attraction. The system is adaptable to serve singles who wish to identify and get to know a prospective mate through mutual visits to attractions, as well as individuals, couples, and families who want to go out with their existing friends or make new friends.
Owner:TIES SOCIAL TECH
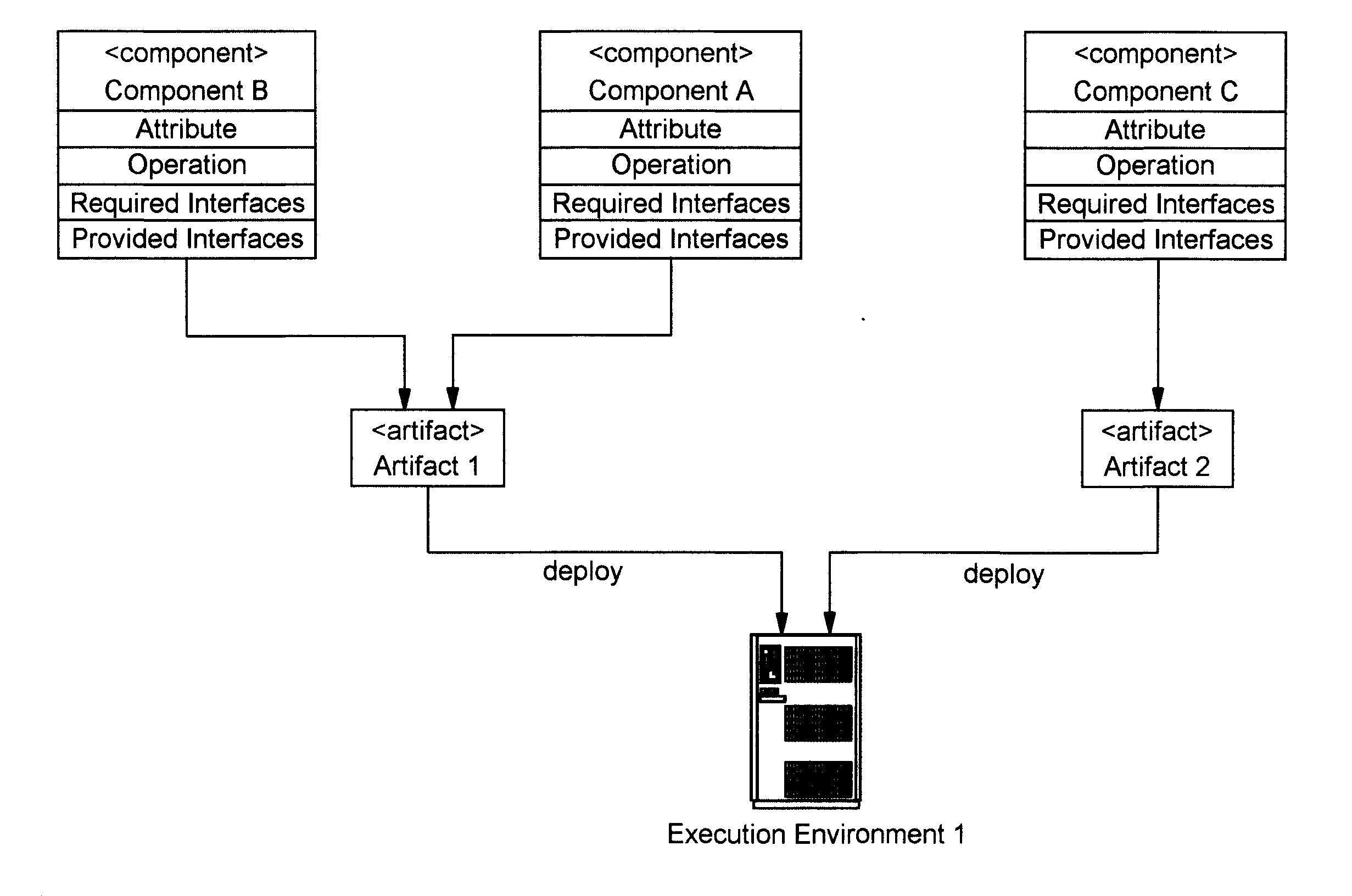
Model driven deployment of composite applications
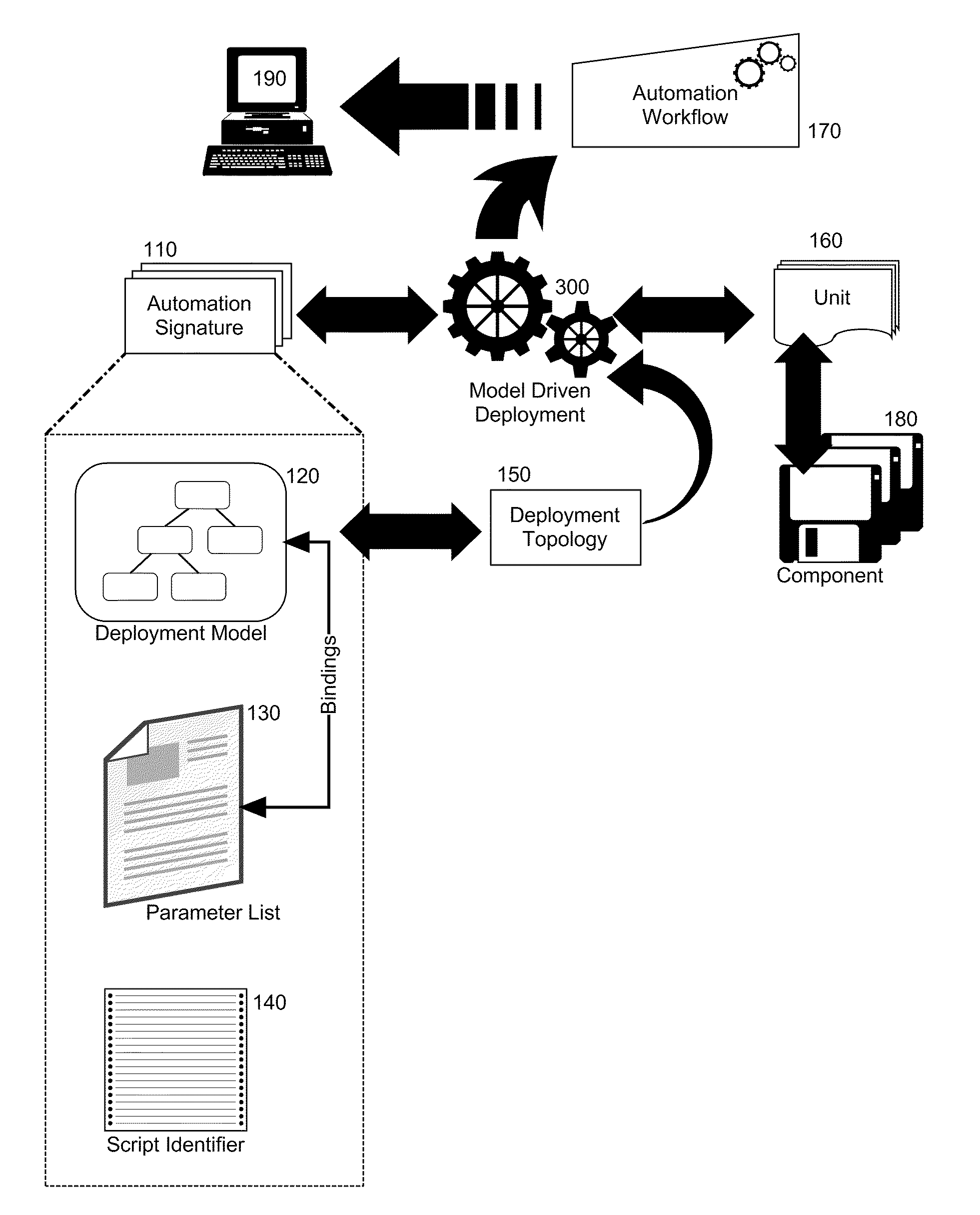
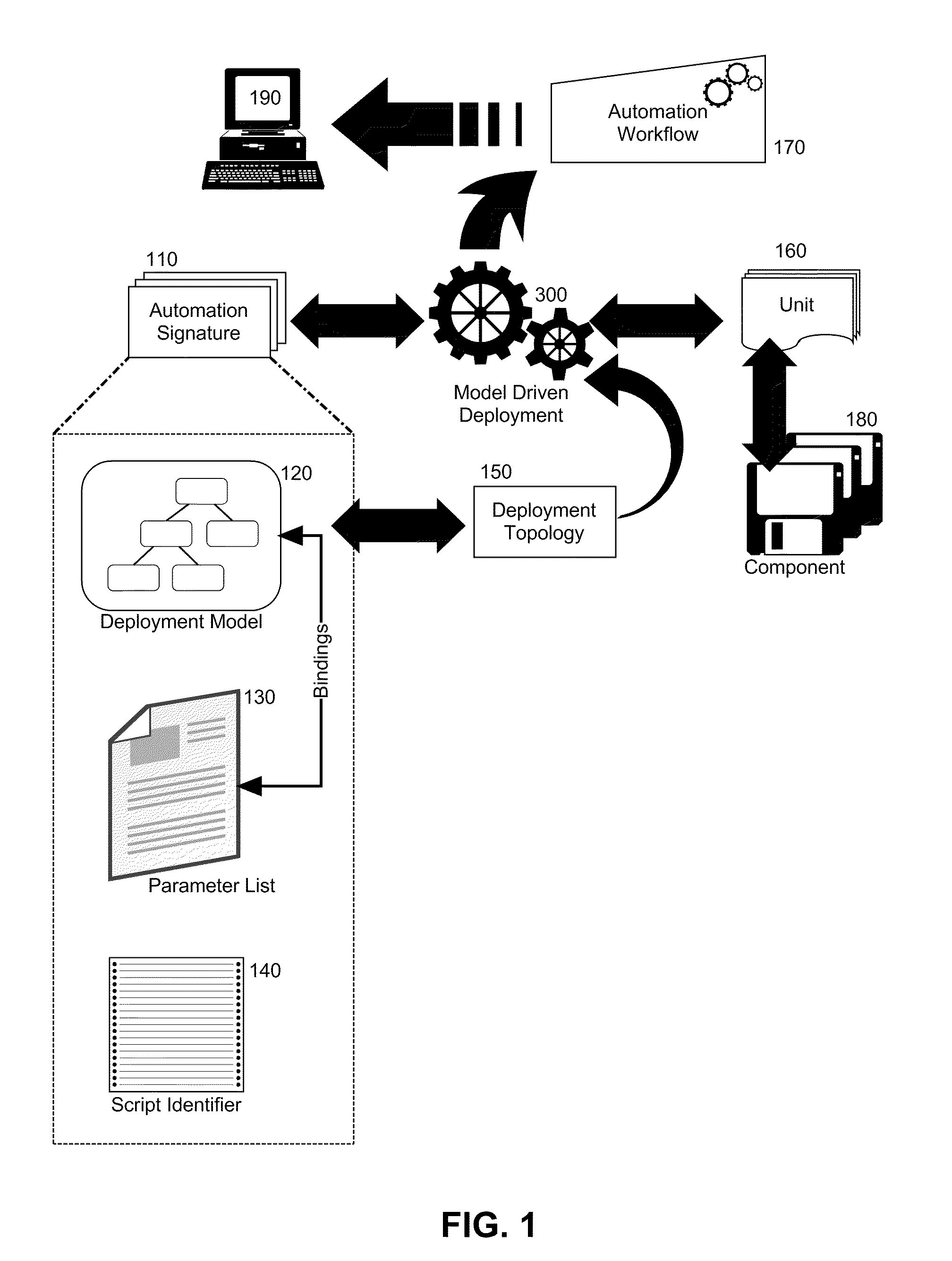
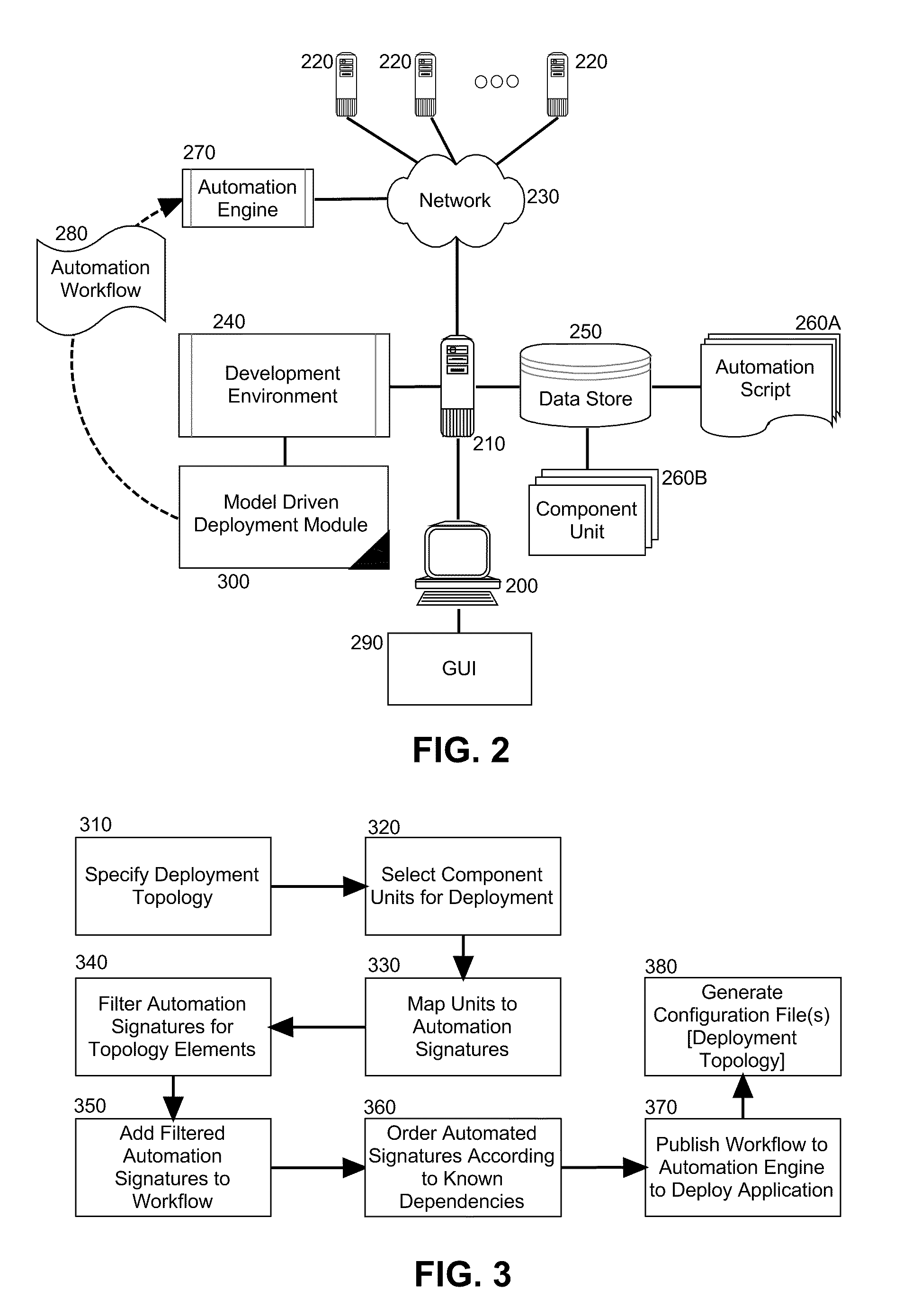
InactiveUS20110029967A1Program loading/initiatingMemory systemsComposite applicationApplication software
Embodiments of the present invention provide a method, system and computer program product for model driven deployment of component based applications. In an embodiment of the invention, a method for model driven deployment of component based applications can include selecting units representative of corresponding programmatic objects to be deployed into a target environment and specifying a deployment topology for the target environment. The method also can include matching portions of the units to different automation signatures and filtering the different automation signatures to a set of automation signatures based upon the deployment topology. The set of automation signatures can be ordered according to known dependencies of a corresponding deployment model and the ordered set of automation signatures can be bundled into an automation workflow and published to an automation engine for execution to deploy the programmatic objects into the target environment.
Owner:IBM CORP
Method and system for identifying potential adverse network conditions
A method and system for identifying potential adverse network conditions, the method including monitoring for events in the network, saving data indicative of the events, responding to an adverse network condition by electronically searching the events preceding the adverse network condition for patterns, and storing data indicative of the patterns associated with data indicative of the respective adverse network condition. The method may further include monitoring during run-time for matches or partial matches between the patterns and sequences of network events, and responding to a match or partial match by issuing a warning identifying the adverse network condition or conditions associated with a matched pattern or matched patterns.
Owner:GUPTA ANKUR
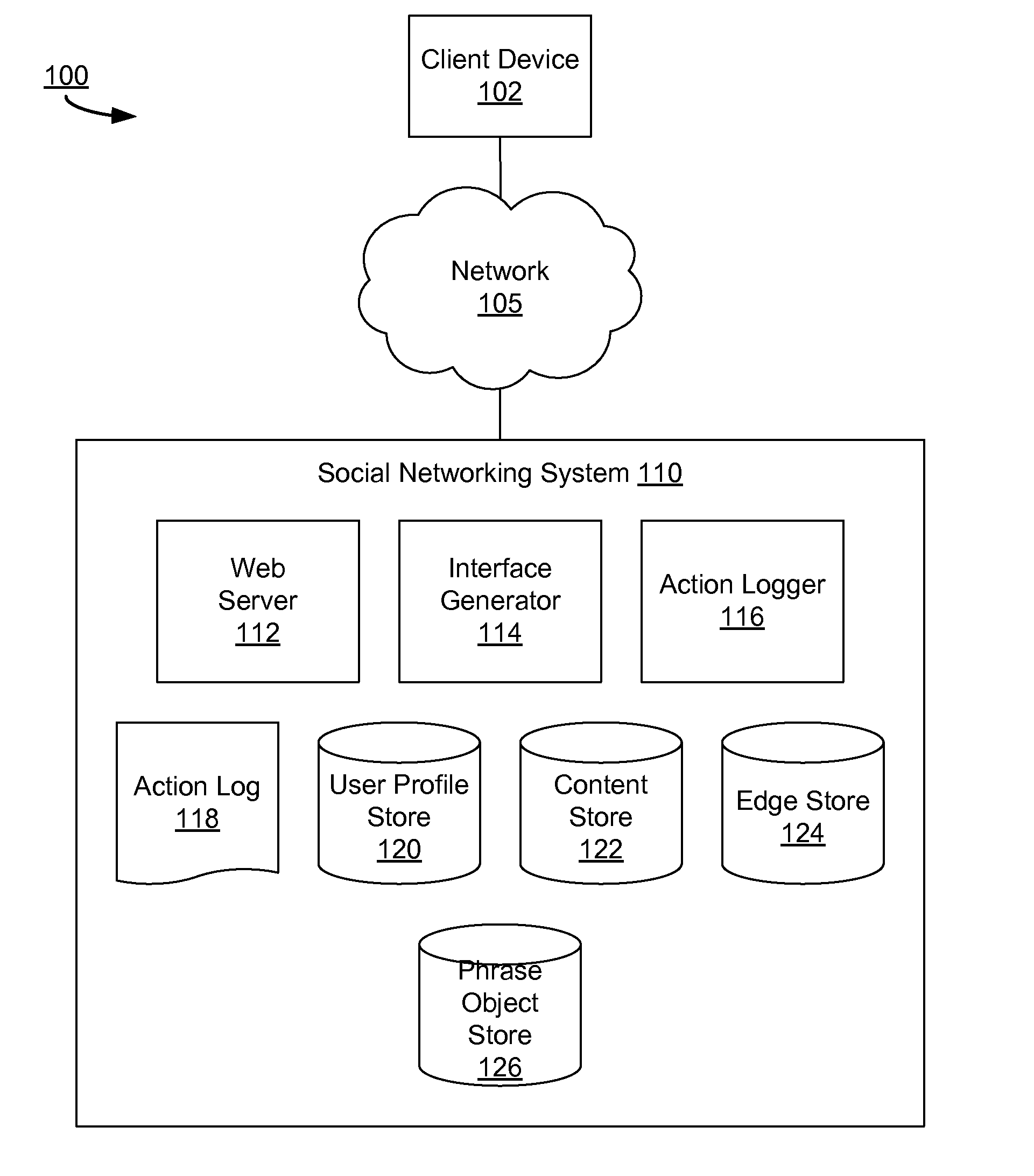
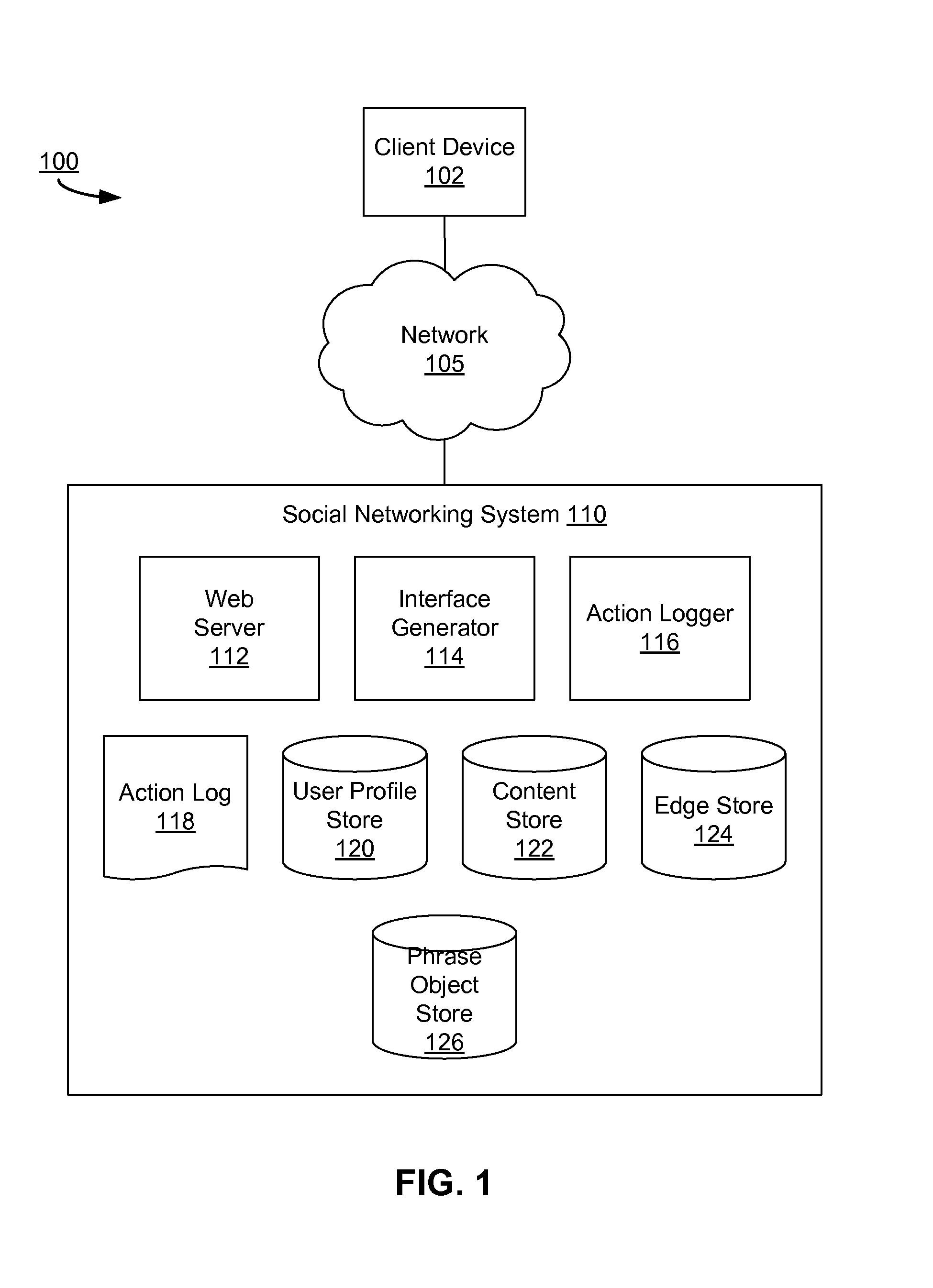
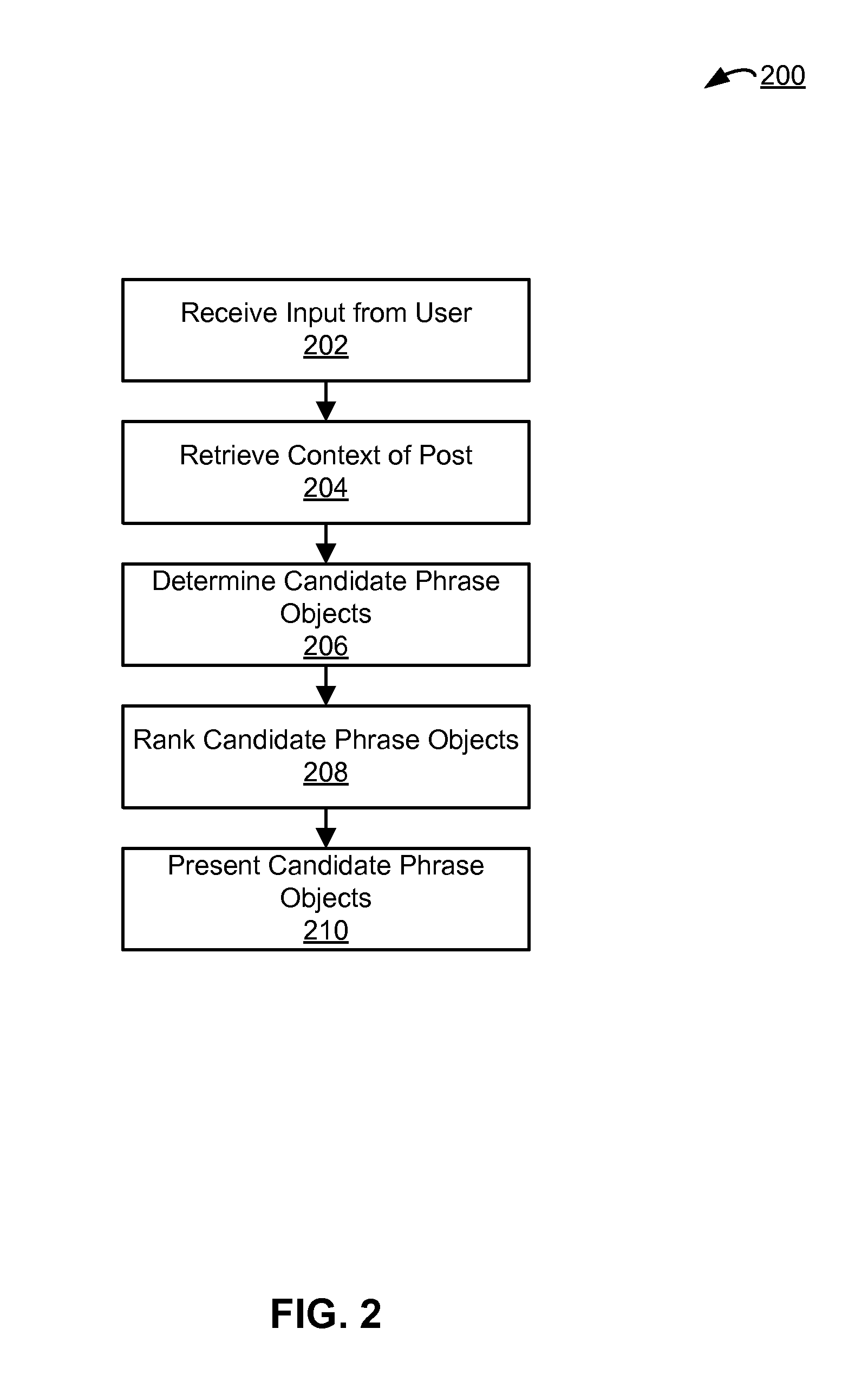
Determining phrase objects based on received user input context information
ActiveUS20140244622A1Quick distinctionSmall sizeDigital data information retrievalDigital data processing detailsObject basedUser input
A composer interface allows a user to provide input, such as text data, to the social networking system. To reduce the number of inputs for a user to provide to the social networking system, one or more phrase objects are presented to the user when providing input. A phrase object includes a group of objects that users have previously provided to the social networking system. The social networking system presents phrase objects to the user that match at least a portion of the received input. Context information associated with the input and associated with various phrase objects may be used to select the presented phrase objects. By selecting a presented phrase object, the user includes the selected phrase object in the input.
Owner:META PLATFORMS INC
Partial document content matching using sectional analysis
Owner:EMC IP HLDG CO LLC
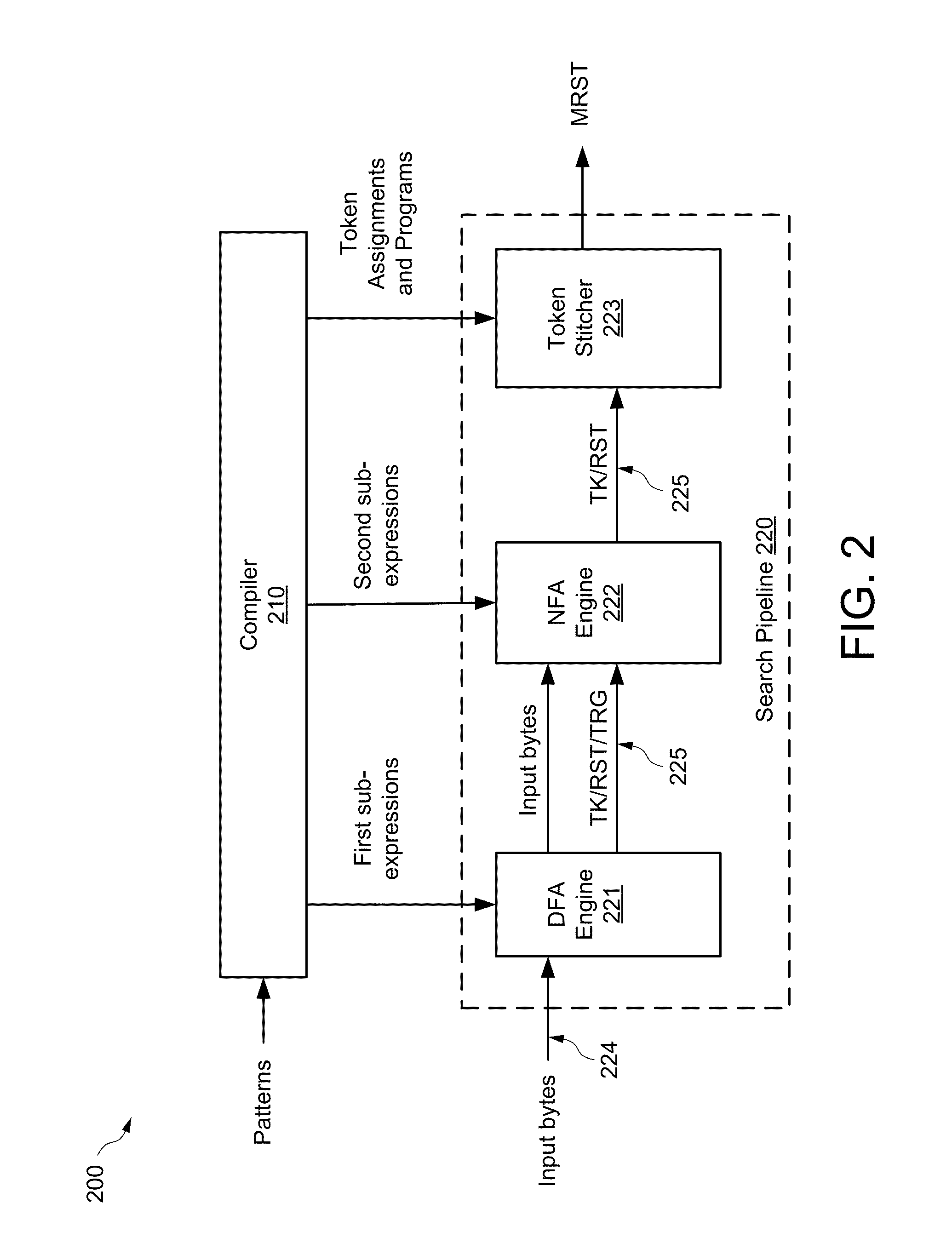
Pipeline sequential regular expression matching
ActiveUS20070055664A1Data processing applicationsDigital data information retrievalTheoretical computer scienceRegular expression
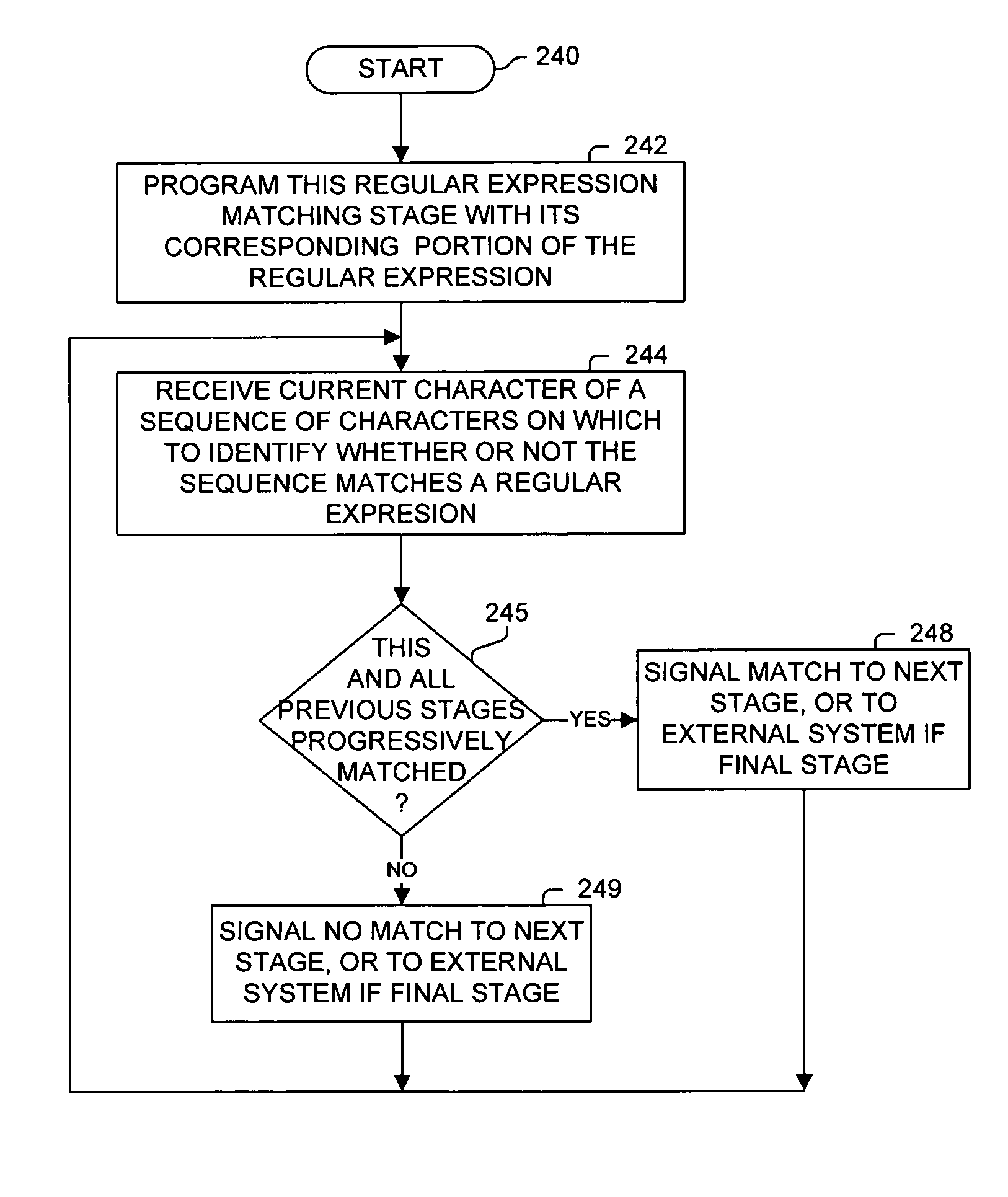
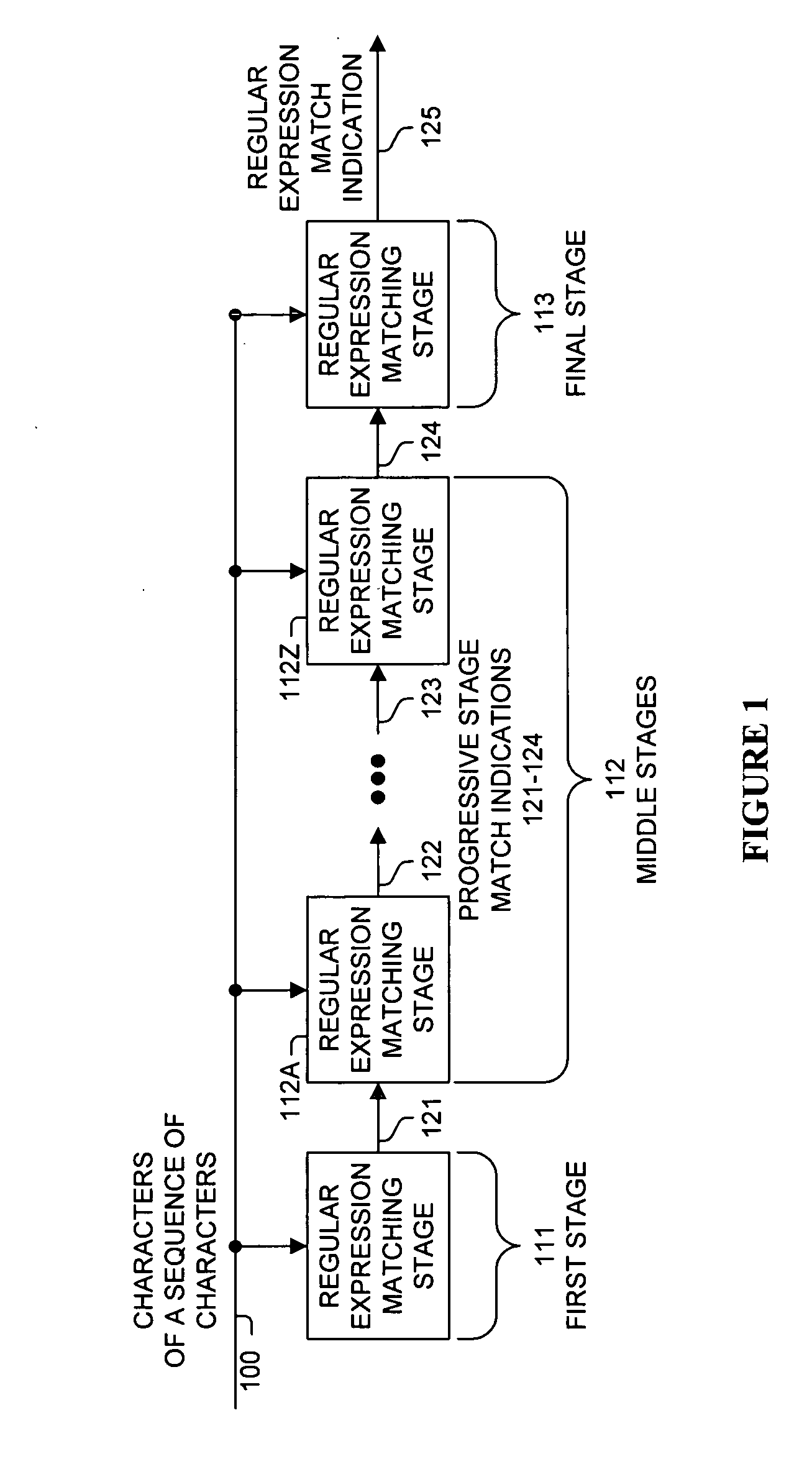
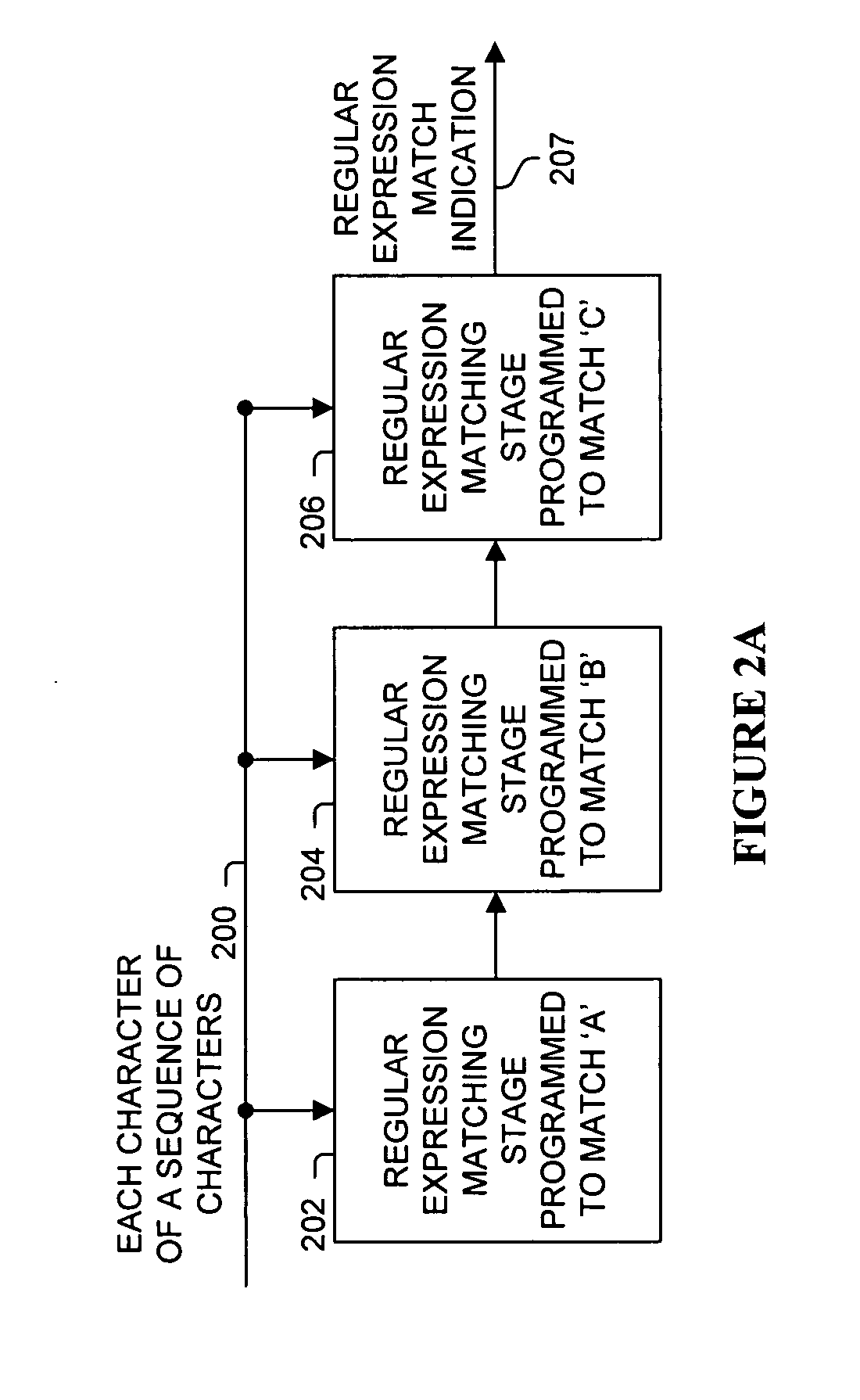
Regular expression matching is performed on a sequence of characters using a pipeline architecture of regular expression matching stages. Multiple regular expression matching stages are connected together in a pipeline manner, with each of these regular expression matching stages corresponding to a different portions of the regular expression. These stages are response to indications from their immediately preceding stages (if they have a preceding stage) of whether or not a progressive match was determined. If all preceding stages matched for corresponding characters of the sequence of characters, then a stage will identify whether or not the current character matches its programmed portion of the regular expression to a next stage or to another device (e.g., the final stage may indicate to a packet processor whether or not the regular expression is matched).
Owner:CISCO TECH INC
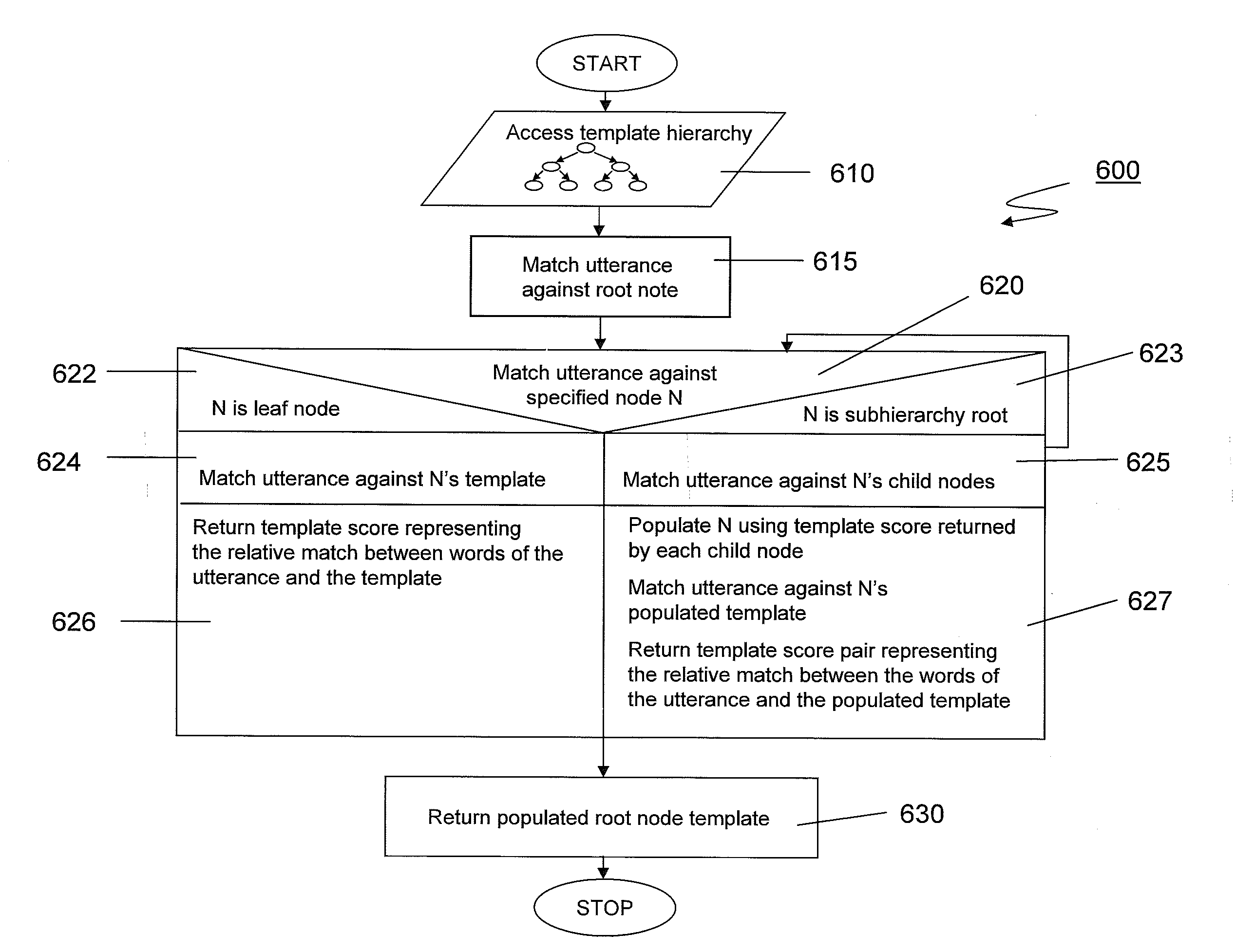
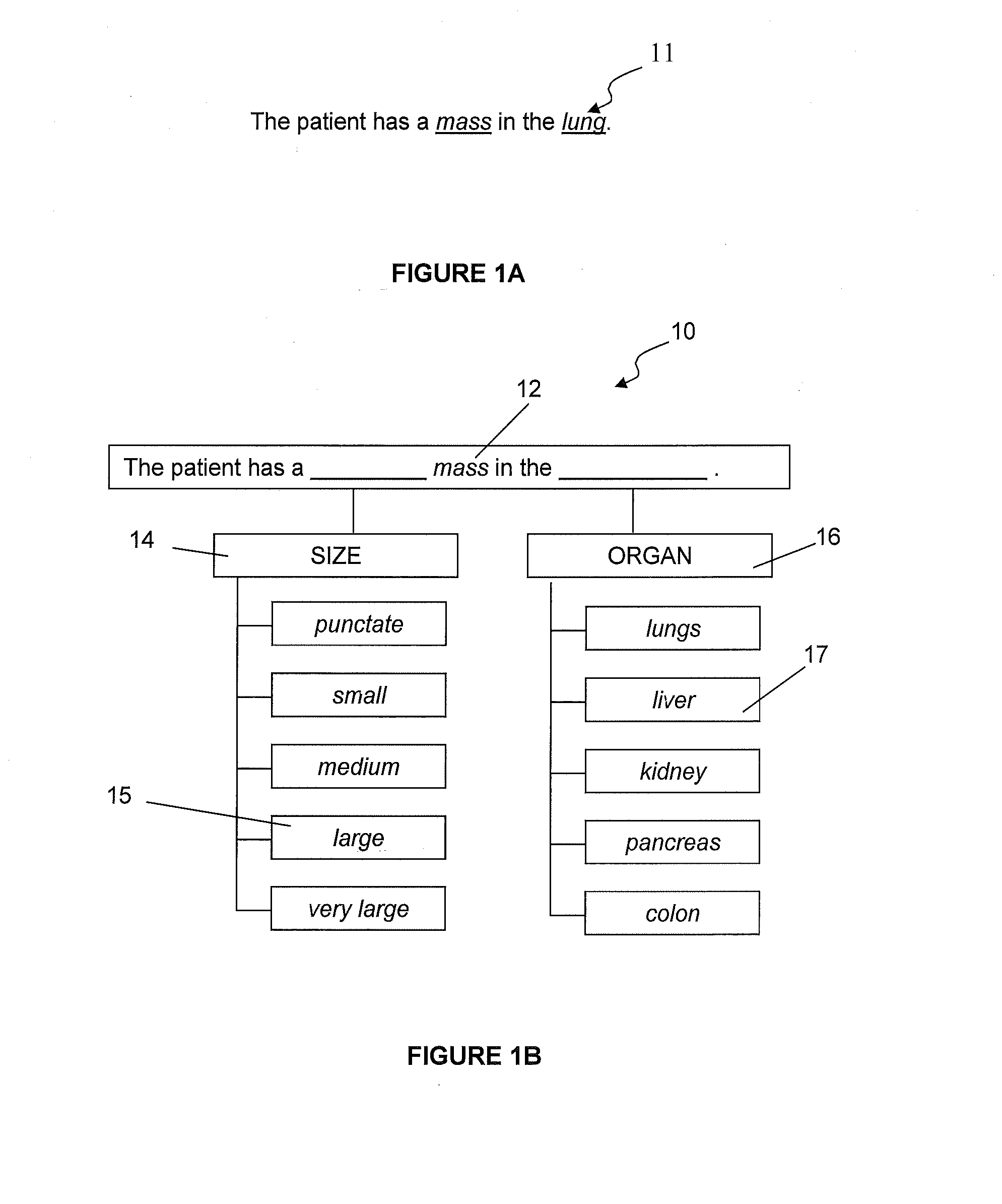
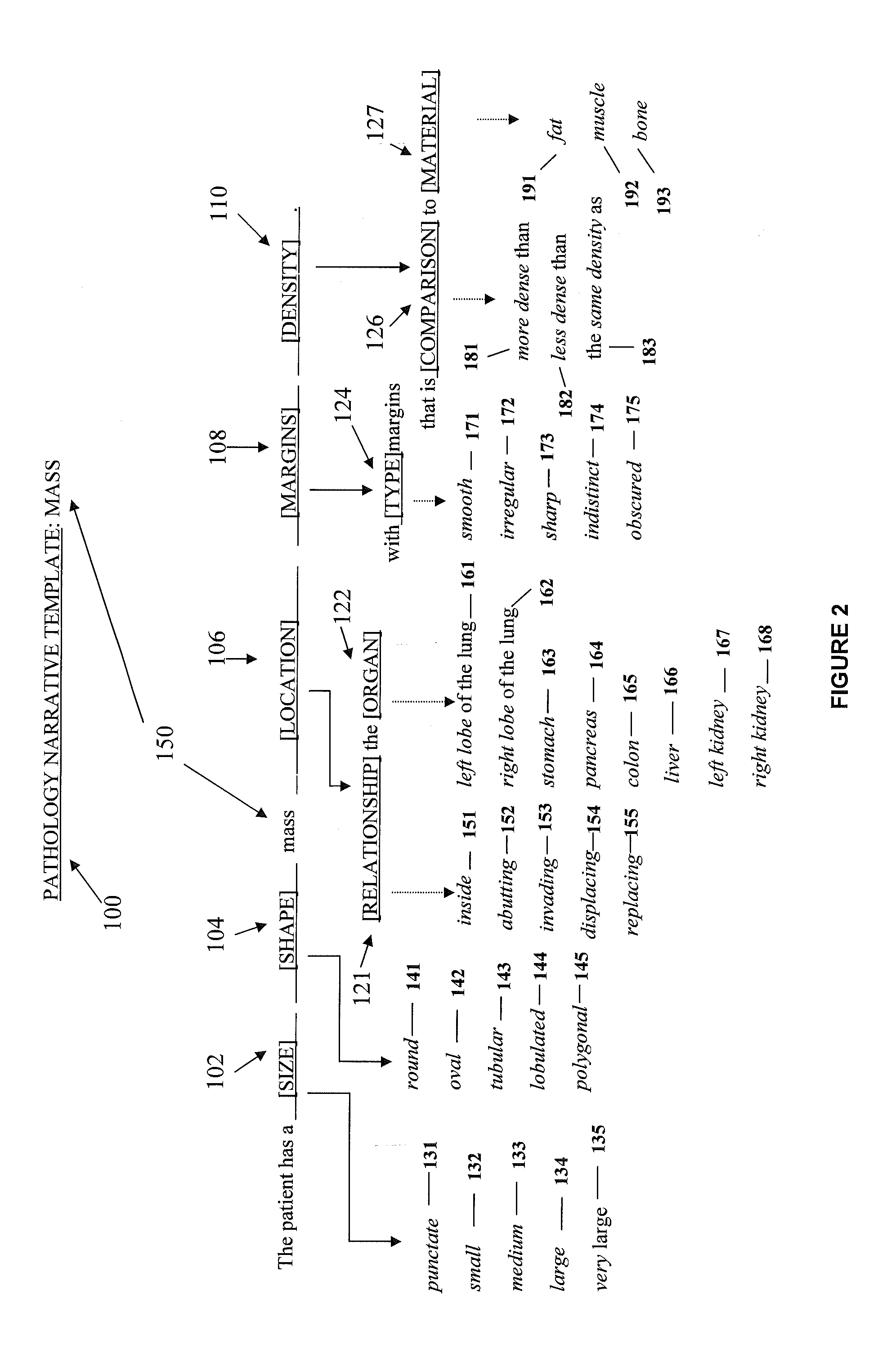
System and methods for matching an utterance to a template hierarchy
ActiveUS20140052444A1Easily verbalizeMaintaining visual focusSpeech recognitionPartial matchUtterance
A system and methods for matching at least one word of an utterance against a set of template hierarchies to select the best matching template or set of templates corresponding to the utterance. Certain embodiments of the system and methods determines at least one exact, inexact, and partial match between the at least one word of the utterance and at least one term within the template hierarchy to select and populate a template or set of templates corresponding to the utterance. The populated template or set of templates may then be used to generate a narrative template or a report template.
Owner:ASCEND HIT LLC
Stateful packet content matching mechanisms
ActiveUS7784094B2Energy efficient ICTMultiprogramming arrangementsComputer hardwareString searching algorithm
Methods and apparatus for performing content inspection across packet boundaries using stateful packet content matching mechanisms. Pattern data structures are employed to facilitate string search algorithm machines. Incoming packets are classified to flows, and stored in corresponding flow queues. Flow table entries are used to identify the pattern data structure for a given flow. During content inspection, the algorithm machine updates state information to identify partial or full matches. When a partial match is detected towards the end of an earlier packet state information in the flow table is updated to reflect the state such that content inspection of a following packet begins at that state. As a result, content inspection across packet boundaries is supported. The techniques may further be employed in a packet processing context pipeline stage.
Owner:TAHOE RES LTD
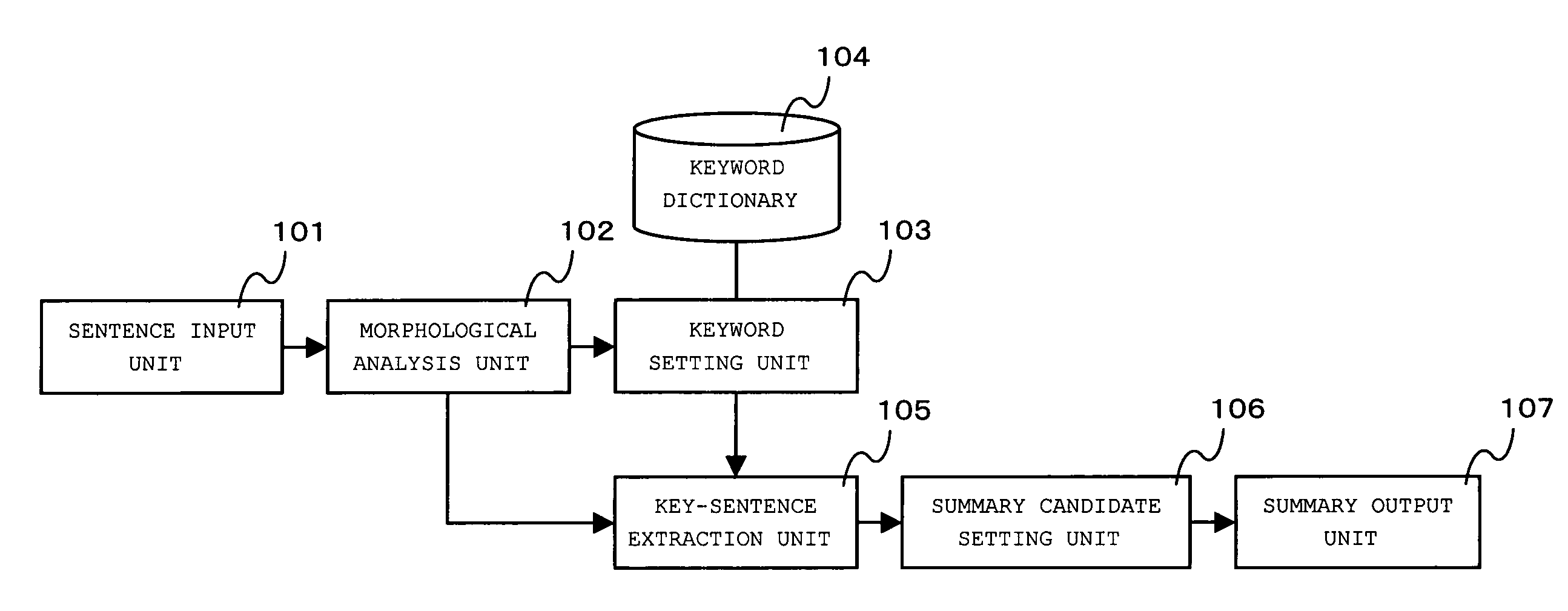
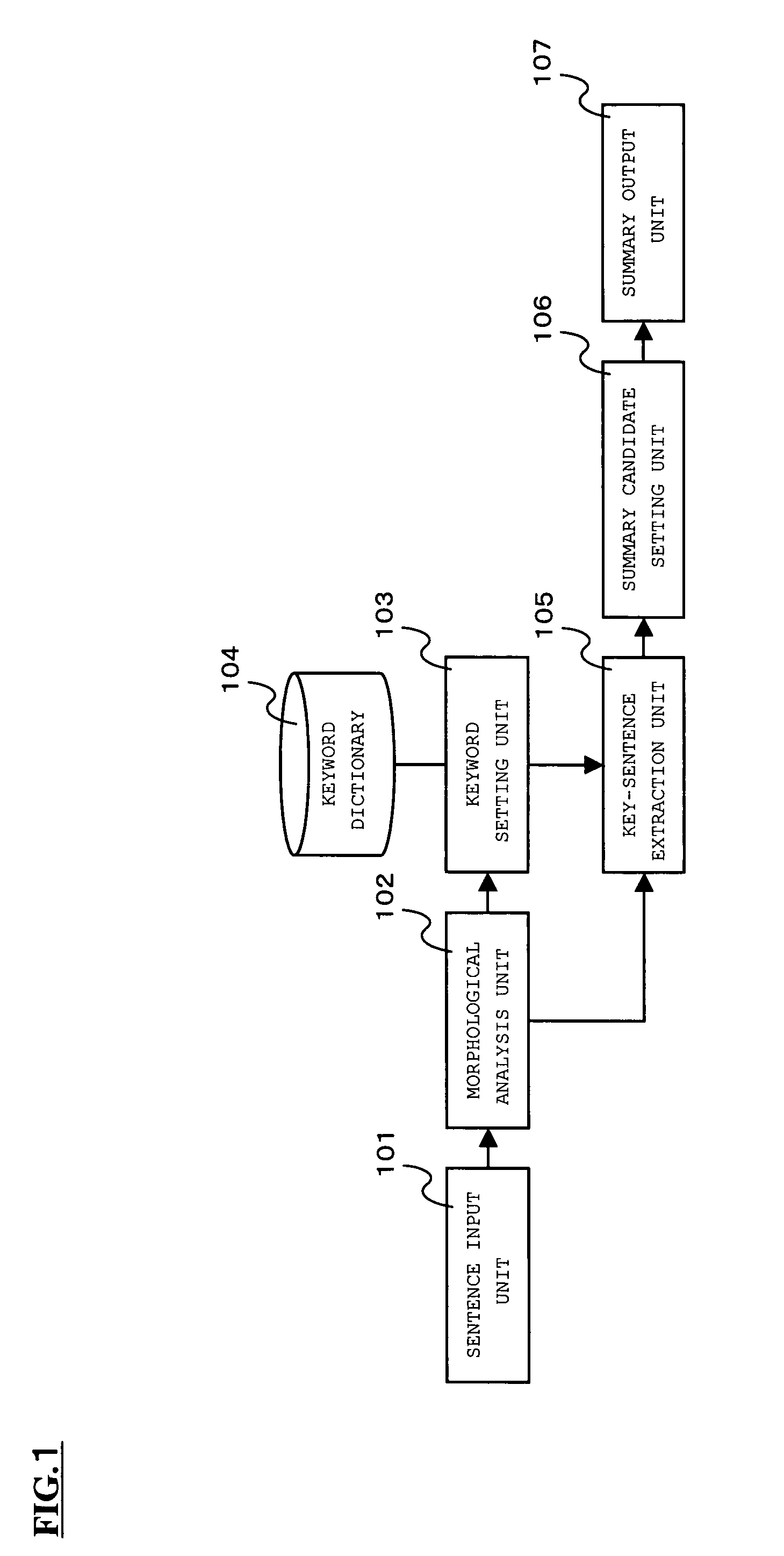
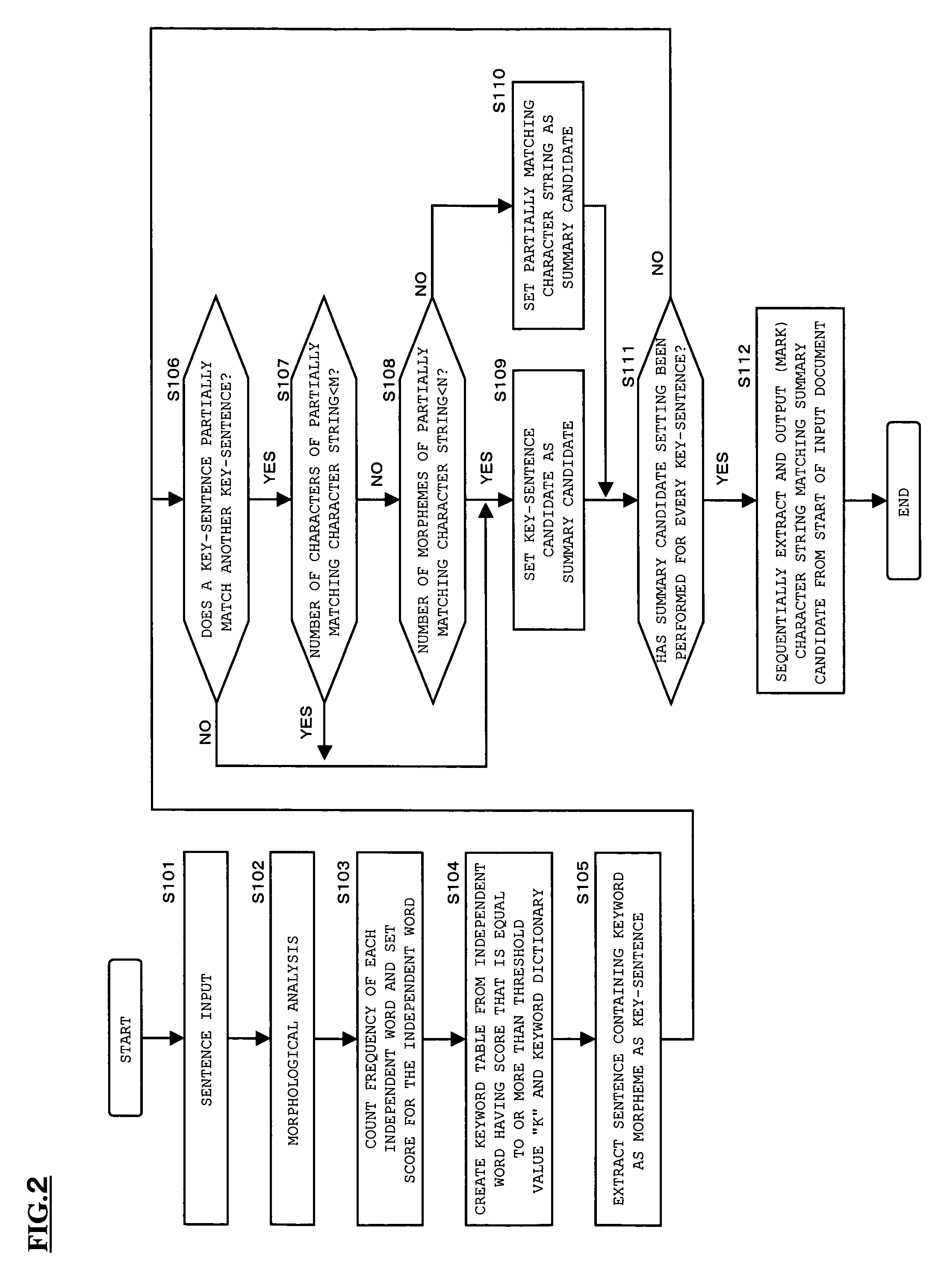
Abstract generation method and program product
InactiveUS20050131931A1Digital data information retrievalNatural language data processingMedical recordPaper document
The present invention relates to an abstract generation method of generating an abstract from document information, such as an electronic patient chart, and a program product that implements the abstract generation method, and has an object to make it possible to display only main parts of sentences concisely and effectively. When document information (electronic patient chart, for instance) is inputted into a system, morphological analysis is performed on the document information and it is judged whether a part of a sentence matches the whole of another sentence. When a matching result is obtained, a partially matching character string is set as a simplified sentence candidate. On the other hand, when a matching result is not obtained, the sentence is set as a simplification candidate as it is. Note that even when the partially matching result is obtained, when the number of characters of the matching character string is less than M or when the number of morphemes thereof is less than N, the partially matching character string is not set as the simplified sentence candidate but the sentence is set as the simplification candidate as it is. Next, each simplification candidate containing a keyword is extracted from among generated simplification candidates and is set as a summary candidate. Then, an abstract is generated by marking each part of the input document corresponding to the summary candidate.
Owner:SANYO ELECTRIC CO LTD
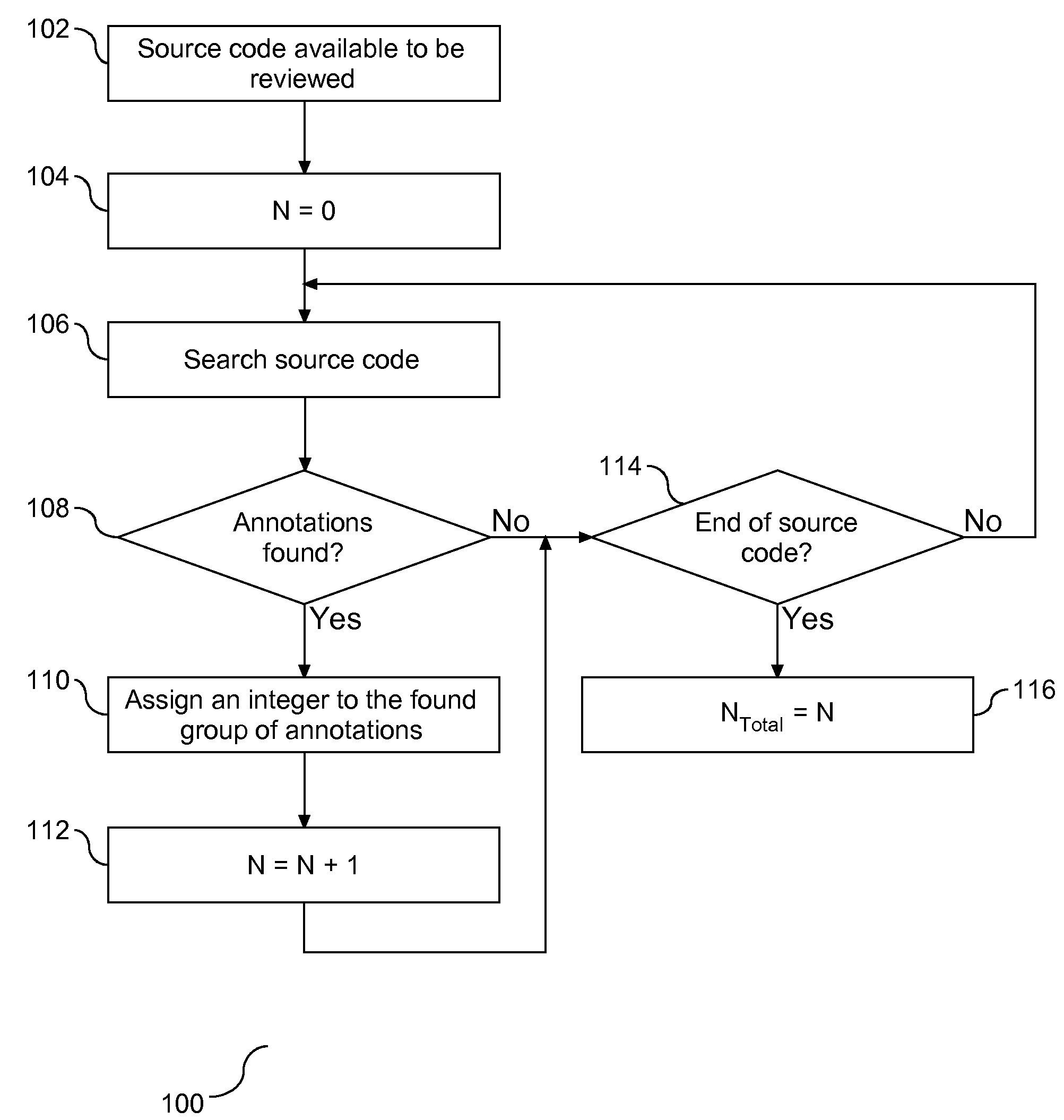
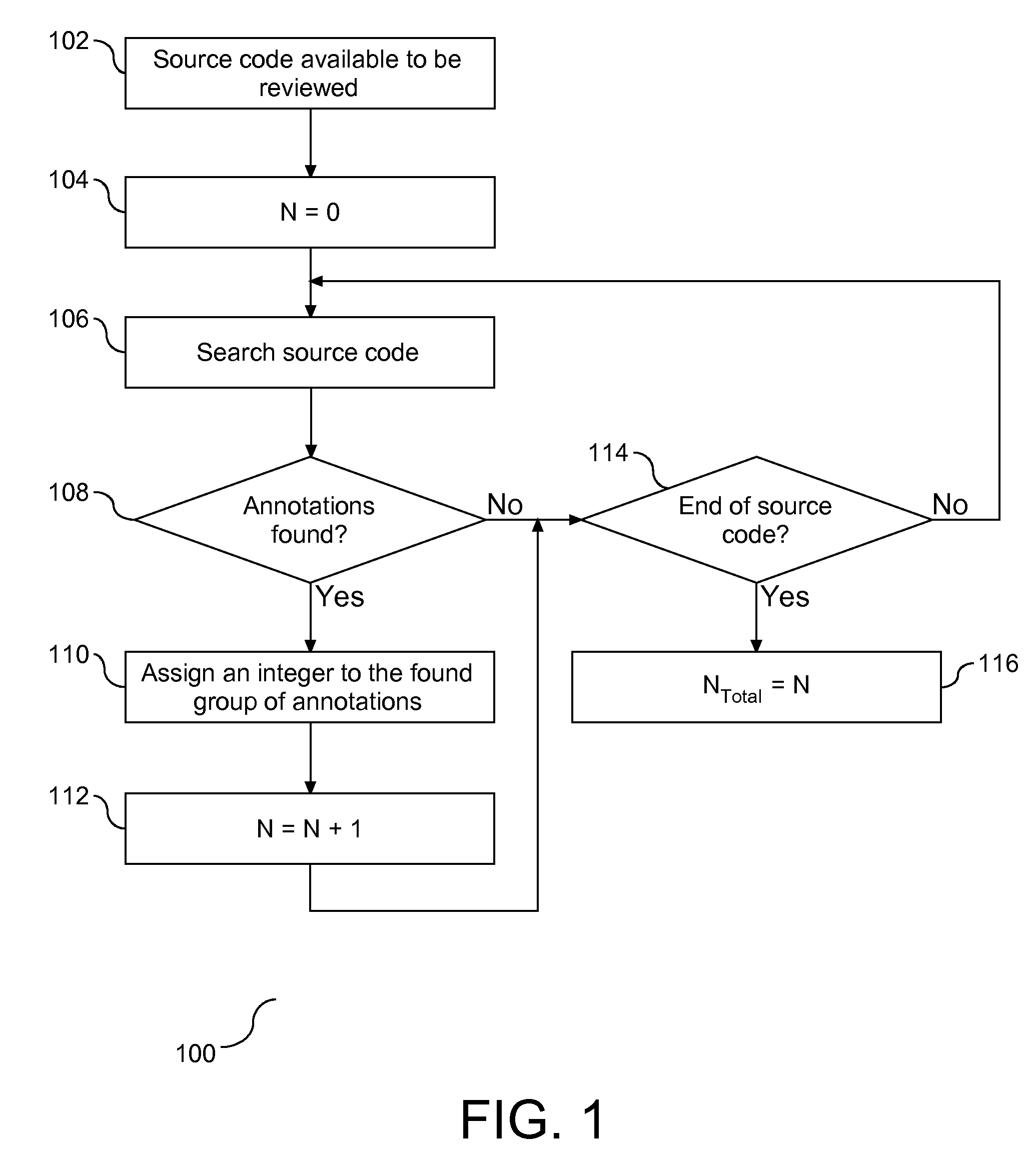
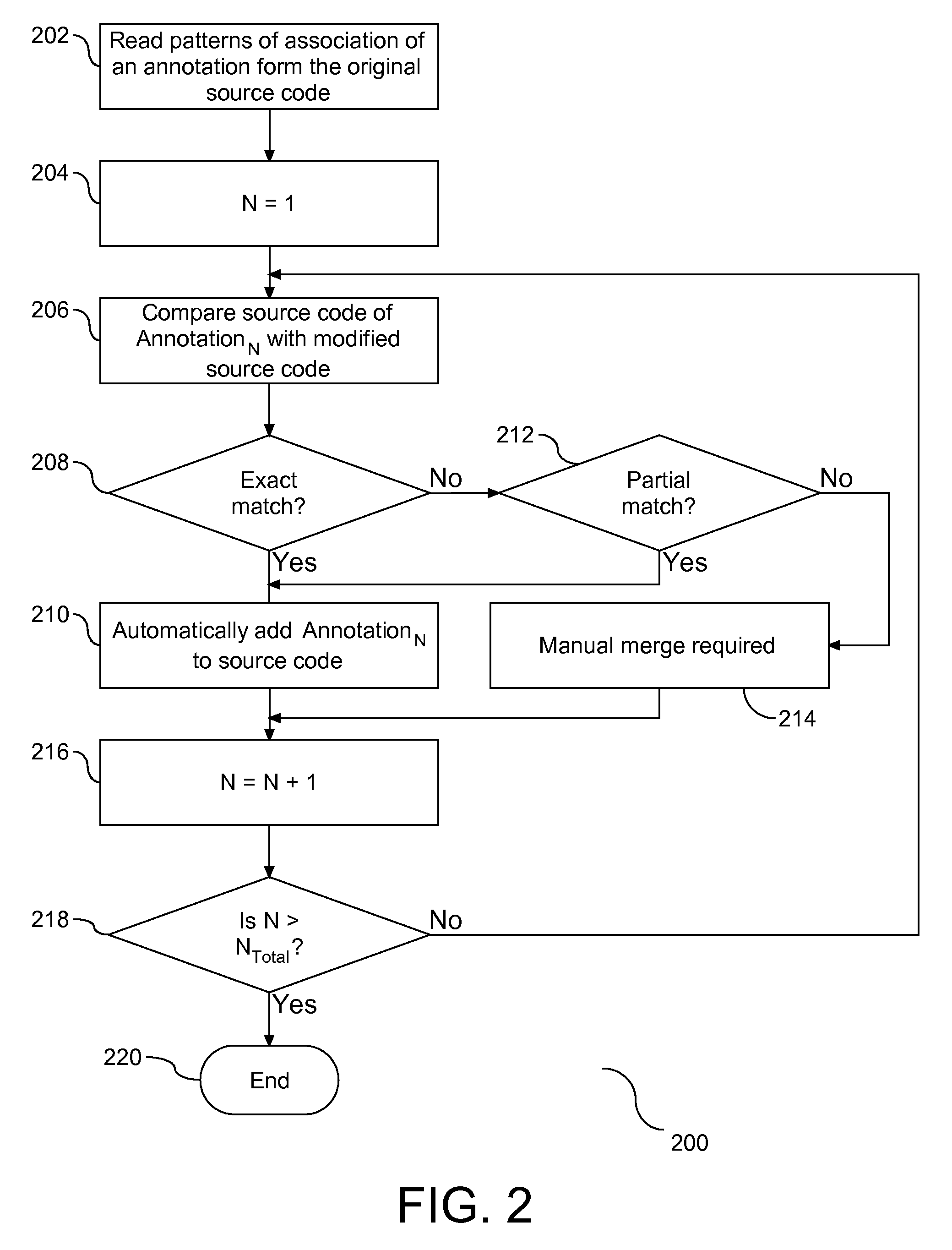
Method To Transfer Annotation Across Versions of the Data
InactiveUS20090249291A1Version controlSpecific program execution arrangementsExact matchParallel computing
A method, apparatus, and article are provided for managing migration of annotations between versions of source code. Annotations associated with patterns of source code are identified. A comparison of the modified source code is conducted in conjunction with the identified annotations in a prior version of the source code to determine if the annotations may be migrated to any portions of the modified source code. The comparison includes an exact match and a partial match. With respect to the partial match, a threshold value is employed to define the parameters of a partial match. All annotations that are determine to be an exact match or a partial match are automatically migrated to a location in the modified source code determine to match within the threshold value.
Owner:IBM CORP
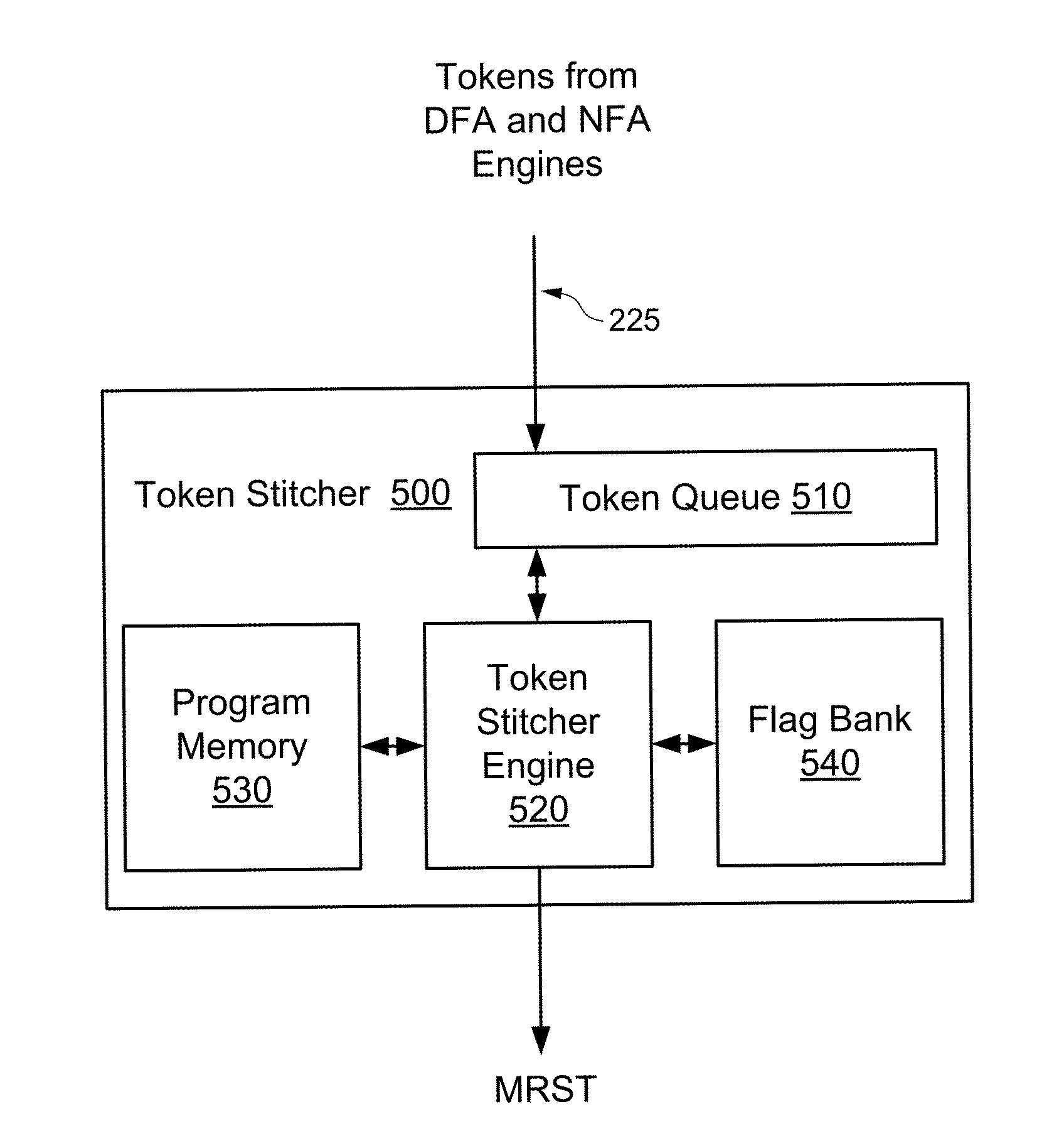
Token stitcher for a content search system having pipelined engines
InactiveUS8589405B1Digital data information retrievalDigital data processing detailsTheoretical computer scienceRegular expression
A content search system includes multiple pipelined search engines that implement different portions of a regular expression search operation. For some embodiments, the search pipeline includes a DFA engine, an NFA engine, and a token stitcher that combines partial match results generated by the DFA and NFA engines. The token stitcher can be configured to implement unbounded sub-expressions without utilizing resources of the DFA or NFA engines. A token stitcher may comprise an input line for receiving tokens that indicate a partial match between an input string and a regular expression, a flag bank that stores flags which, when activated, identify one or more of the sub-expressions that match the input string, a program memory that stores programs that each comprises instructions for processing tokens, and an engine configured to identify programs that are associated with a newly received token.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
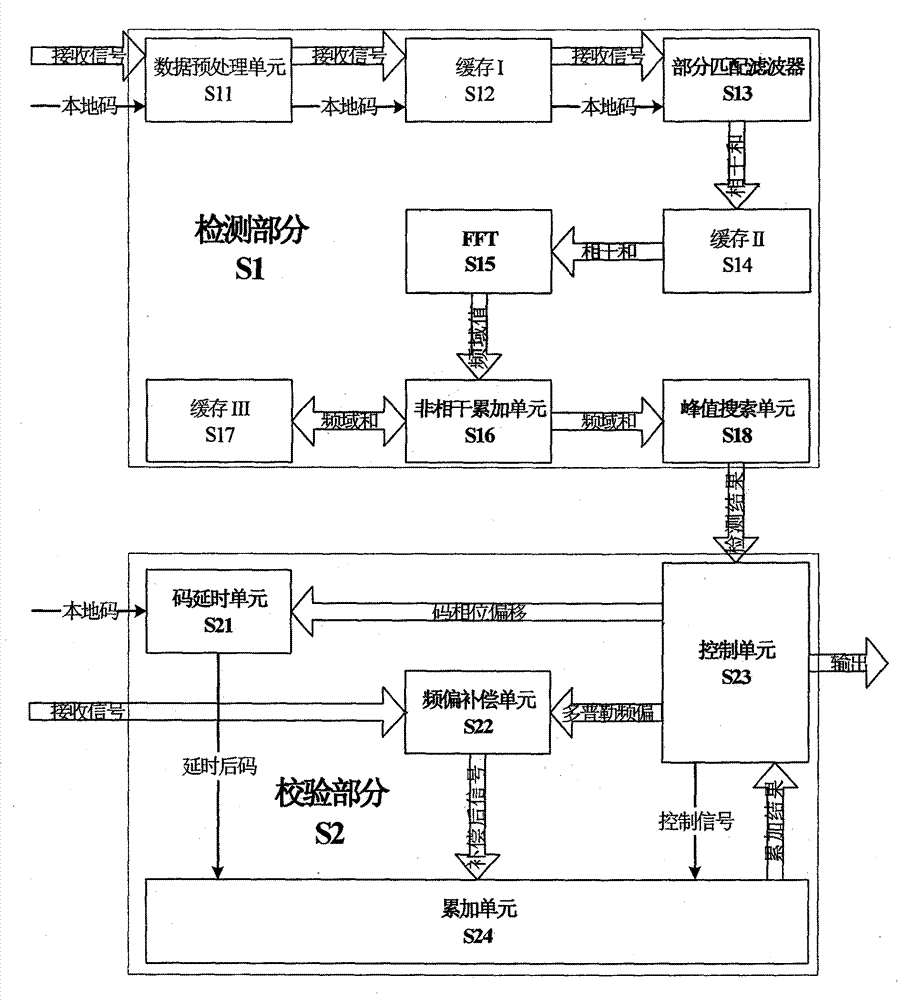
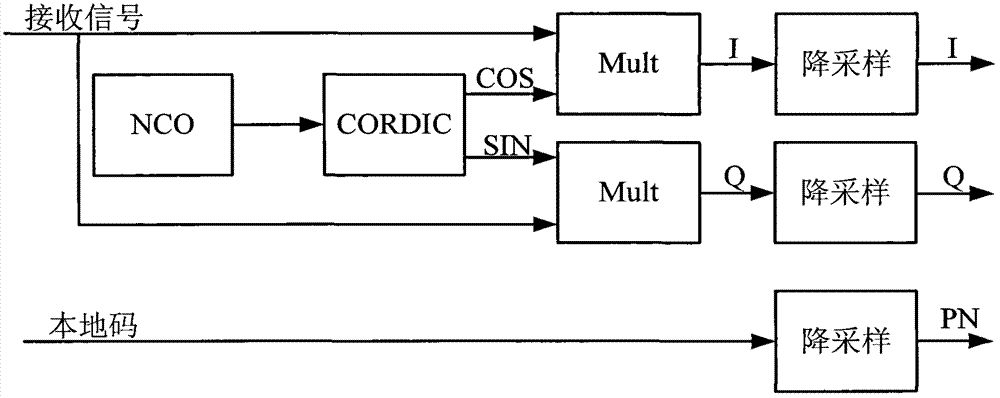
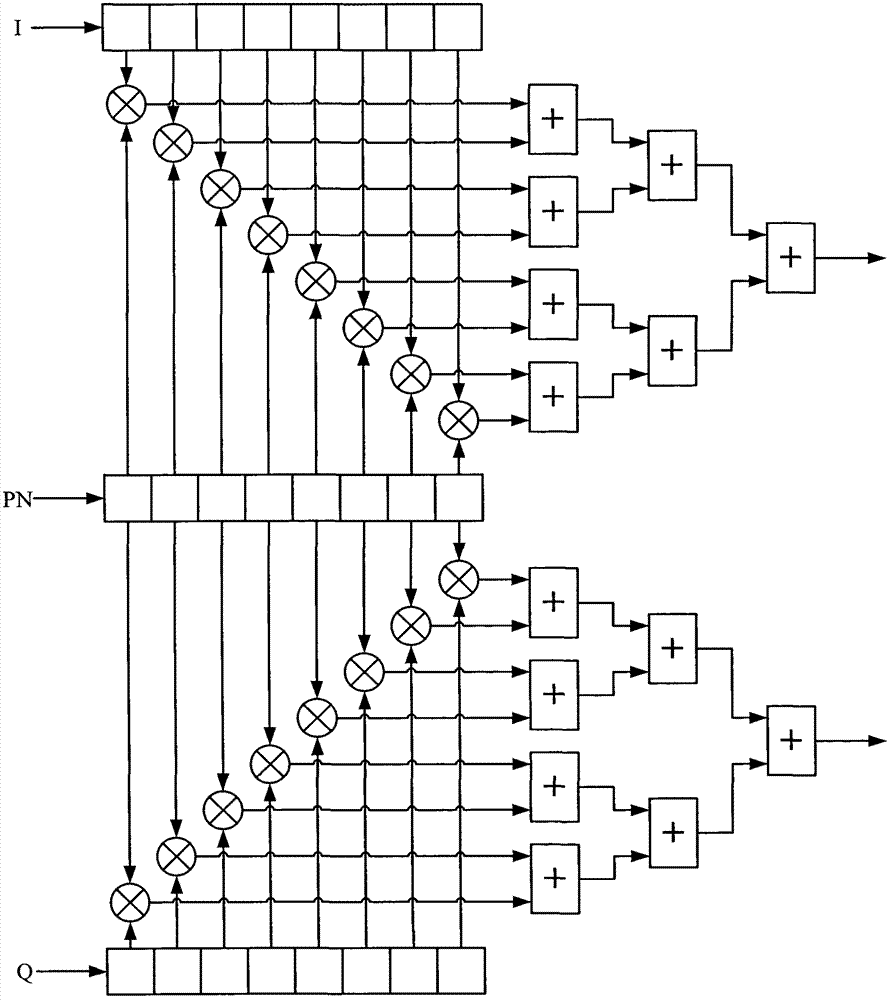
Two-dimensional parallel acquisition system in spread spectrum communication
The invention discloses a two-dimensional parallel acquisition system in spread spectrum communication, which comprises a detection part and a check part. A data preprocessing unit in the detection part performs down-conversion and down-sampling to signals and simultaneously performs down sampling to local codes, results are saved in a buffer memory I, then the results are transmitted to partial matching filters for computation, the results are saved in a buffer memory II, then the results are sequentially transmitted to an FFT (Fast Fourier Transform) and incoherent accumulation unit, the results are saved in a buffer memory III, finally the results are transmitted to peak searching unit for searching for a code phase a Doppler frequency offset corresponding to a maximum value, and the results are transmitted to the check part; a code time delay unit and a frequency offset compensation unit in the check part respectively perform code time delaying and signal frequency offset compensation to the detection results, the results are transmitted to an accumulation unit for coherent and incoherent accumulation, then the results are transmitted to a control unit for threshold judgment, the acquisition is successful if the results exceed a threshold, otherwise, the acquisition of a next section is performed and the acquisition is failed if all code phases are traversed. The two-dimensional parallel acquisition system in spread spectrum communication has the beneficial effects that the parallel acquisition of the code phase and the Doppler frequency offset is realized through a streamline method and the acquisition efficiency is greatly improved.
Owner:北京星地恒通信息科技有限公司
Method of automatically including parenthetical information from set databases while creating a document
InactiveUS20060020615A1Simple methodDigital data information retrievalSpecial data processing applicationsElectronic documentEmail address
A method of creating an electronic document by entering data into the electronic document, searching one or more information sets to identify a set entry which matches a portion of the entered data, and inserting a link to information from the set entry into the electronic document, wherein the link is associated with the matched portion of the entered data. Searching occurs automatically as the data is entered, and different information sets can be designated for searching from among a plurality of available information sets, such as database files, file folders, web browser bookmarks, or email address books. The link is inserted in response to selection of the set entry for inclusion in the electronic document, particularly when multiple matches to parenthetical information are found. In the example where the set entry is a separate file and the document is an email message, the link points to the separate file as an attachment to the email message.
Owner:IBM CORP
Navigation apparatus and navigation program
InactiveUS20080312817A1Simplify the search processInstruments for road network navigationRoad vehicles traffic controlSyllableCommon word
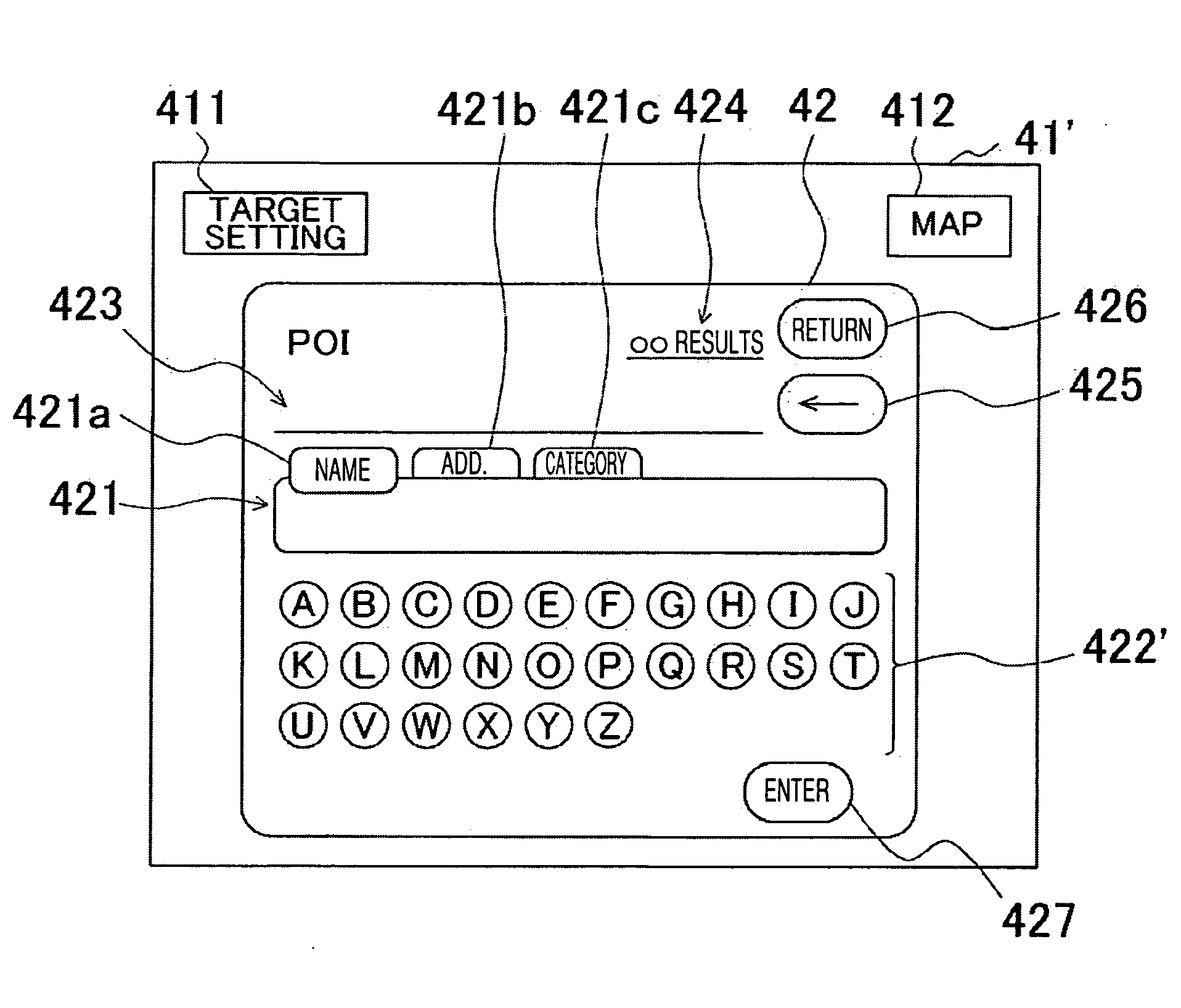
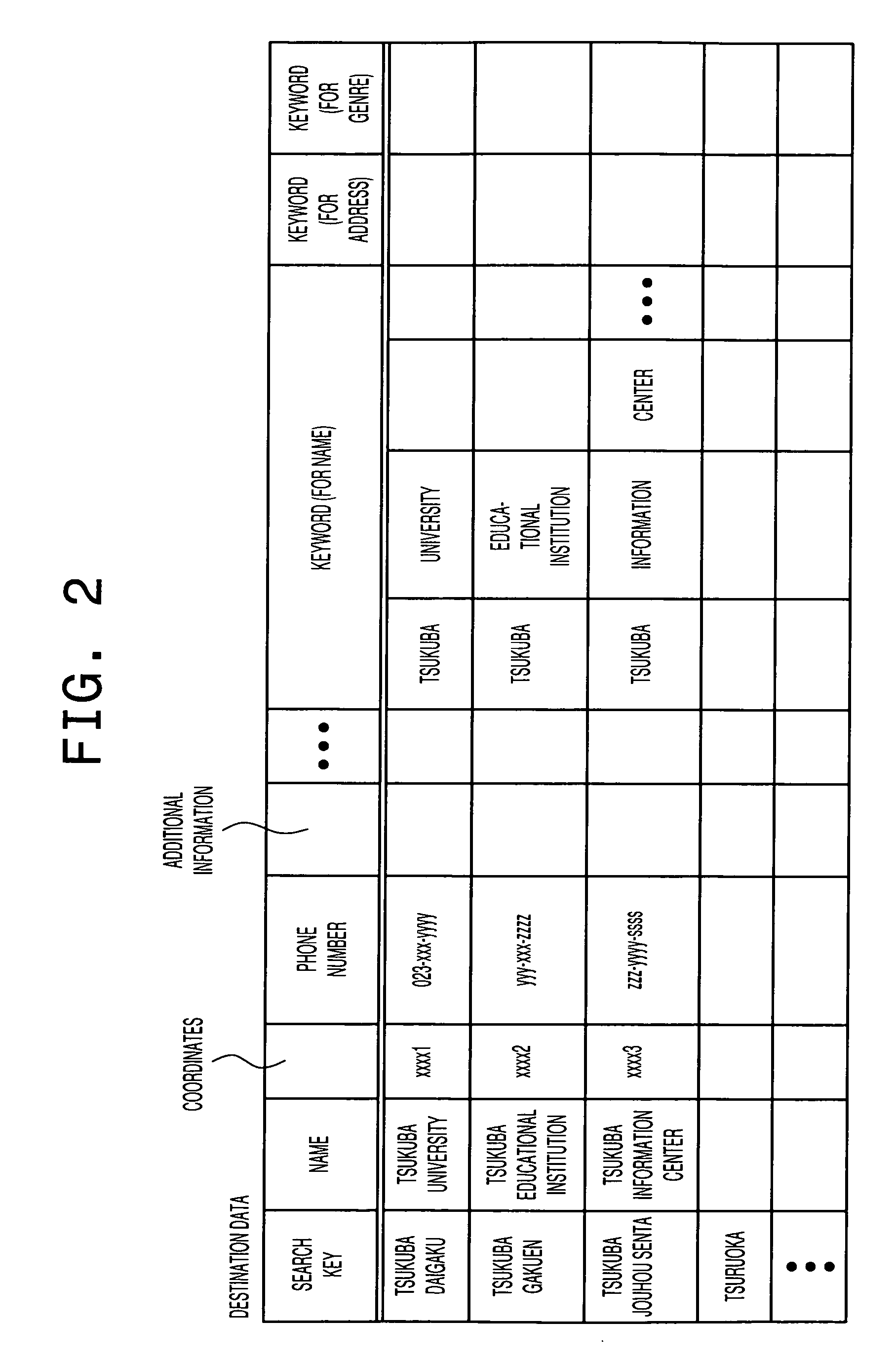
A common word in Japanese syllabary is extracted from multiple items of the destination data, and the common words thus extracted are stored as search keywords. Furthermore, the search keywords are assigned to each potential destination which may be a search target. When a search is made for a destination, those keywords which match the input characters, in whole or in part, are extracted, and the keywords thus extracted are displayed as selectable keys, thus allowing the location candidates to be narrowed down based upon the input characters and the selected keywords. The priority levels of the extracted location candidates are adjusted according to priority score adjustment rules set by operator input, and the location candidates are displayed in the form of a list in descending order of priority. This allows the extracted location candidates to be displayed in the form of a list in an order matching the user's preference.
Owner:AISIN AW CO LTD
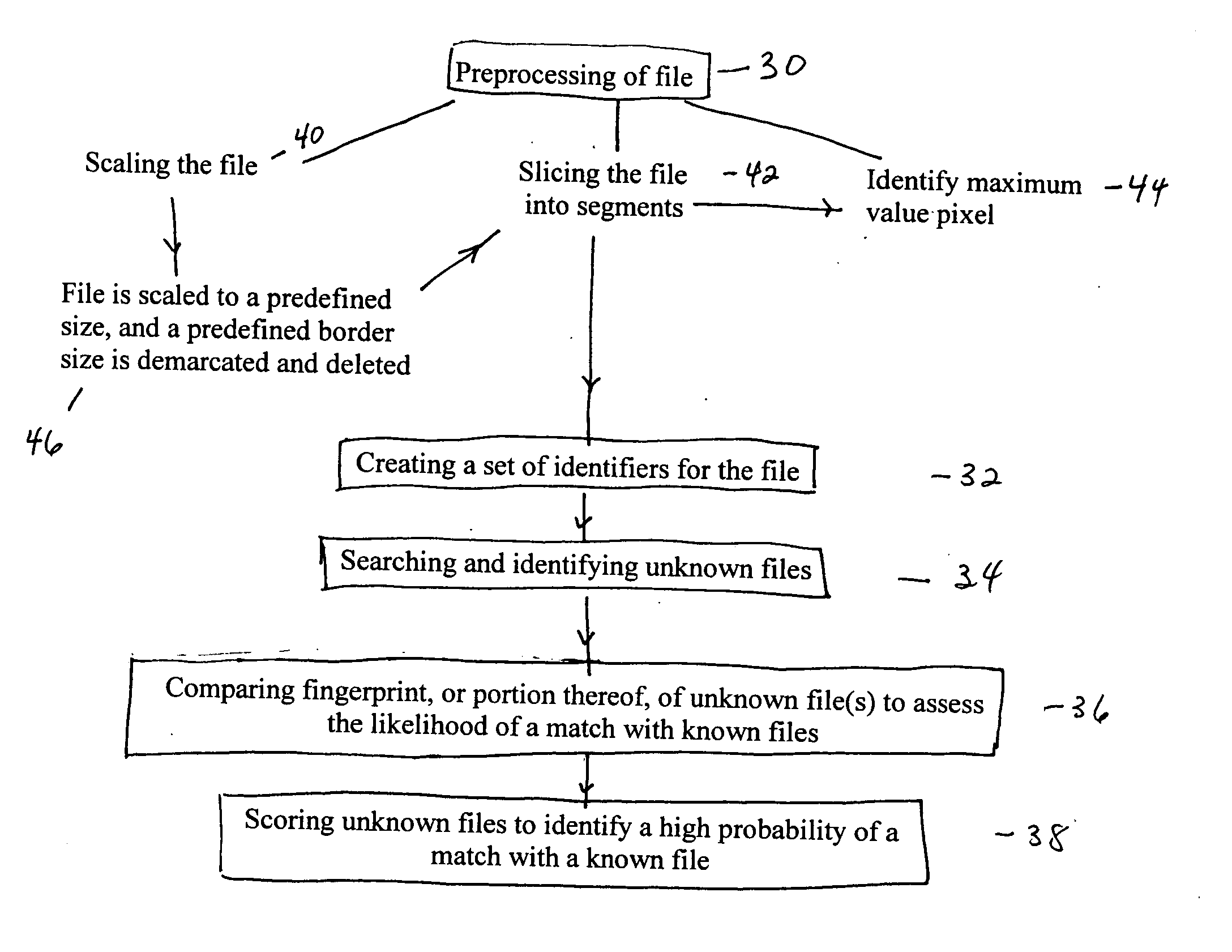
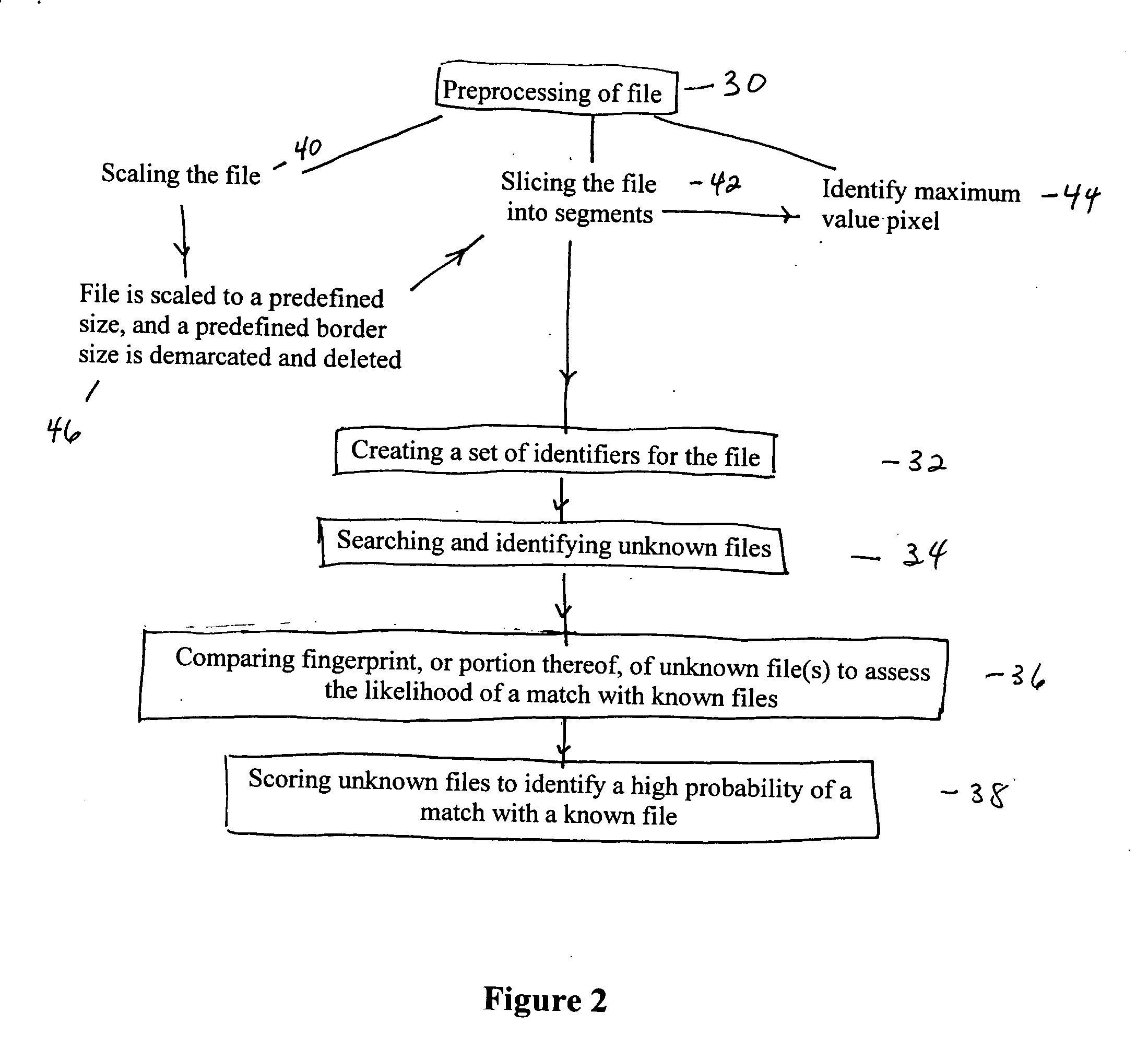
Image processing and identification system, method and apparatus
ActiveUS20060059116A1Compared quicklyElimination of falseData processing applicationsDigital data information retrievalImaging processingData file
Embodiments of the present invention are directed to a system and method for processing and identifying a first data file, the first data file having set of data points, wherein each data point is defined by an x,y coordinate and has a value corresponding to the lightness or darkness of the data resident at the data point, comprising: dividing the first data file into segments; identifying the coordinates of at least one contrast point for each segment; creating a first set of identifiers for the data file, creating a second set of identifiers for a second data file, comparing at least one identifier of the first data file to the corresponding identifier in the second data file; and assessing whether at least a portion of the second data file matches at least a portion of the first data file.
Owner:XWEB
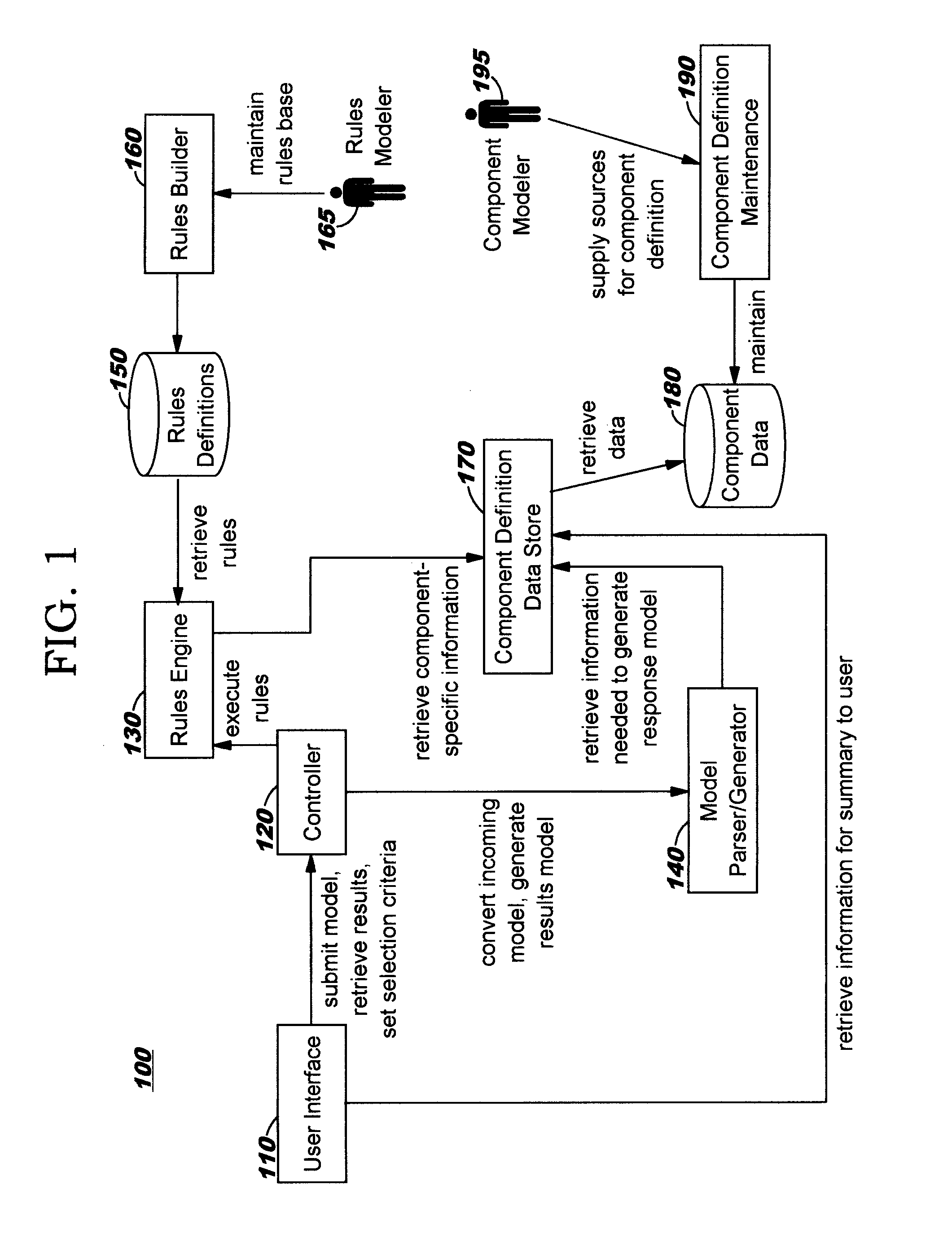
Configuring Assembly of a System using Supplied Architectural Artifacts
The configuration of a system is programmatically determined. More particularly, these determinations are made using architecture artifacts that describe requirements of the system (which may be comprised of software, hardware, services, or some combination thereof), where these requirements are iteratively compared to characteristics of available components. A percentage of match is preferably computed, thus allowing for complete matches as well as partial matches. A weighting factor may be applied to attributes, effectively prioritizing attributes in view of their relative importance in the assembled system. When more than one component is a candidate for meeting a particular requirement, user input may be obtained to select one of the candidates. One or more attributes (such as cost information) of each candidate, including how well that candidate matched requirements, may be included for each candidate presented for user selection. The model may be updated and re-evaluated iteratively.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com