Detection device and method for security vulnerability of software
A vulnerability detection and software security technology, applied in the computer field, can solve the problems of threats, personal privacy loss, Internet terminal attacks, etc., and achieve the effect of high use value
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
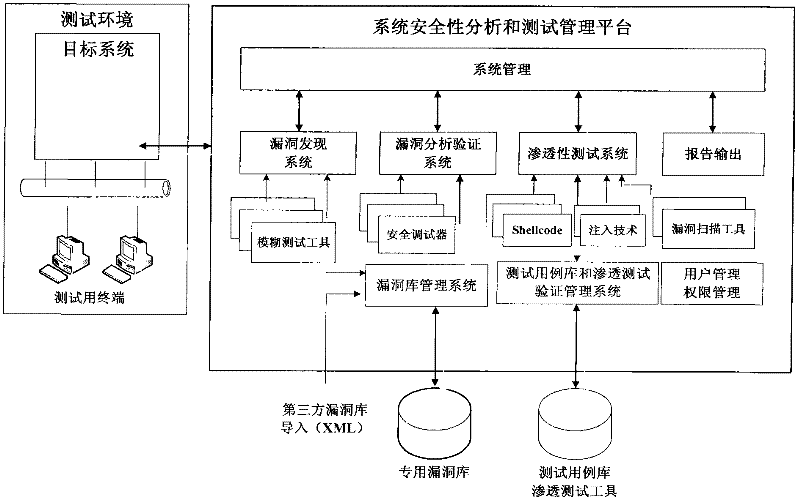
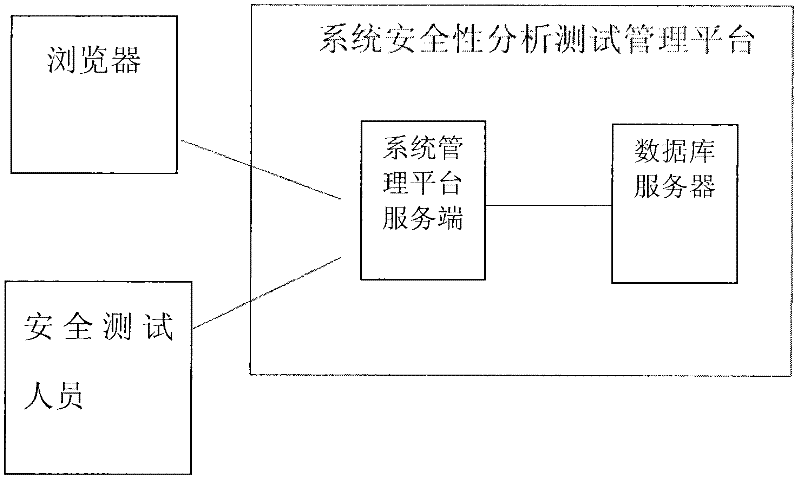
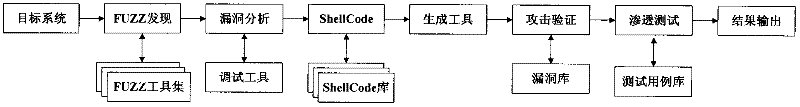
[0021] The present invention is specifically described below in conjunction with the accompanying drawings, as figure 1 As shown, a large-scale design software security vulnerability detection device, the tester connects the test terminal to the target system, can connect the target system to the test network, and can also connect this product to the production system where the target system is located. Security testing service personnel can select and schedule corresponding attack scripts in the test case library according to the environment and version of the target system to conduct penetration testing. The system security analysis and test management platform is the core of the present invention, including a vulnerability discovery system, a vulnerability verification and analysis system, a penetration testing system, a vulnerability library, a test case library, a report output system, a user and authority management system, and a system management platform Wait. The ded...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com