Patents
Literature
208results about How to "Quick delete" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
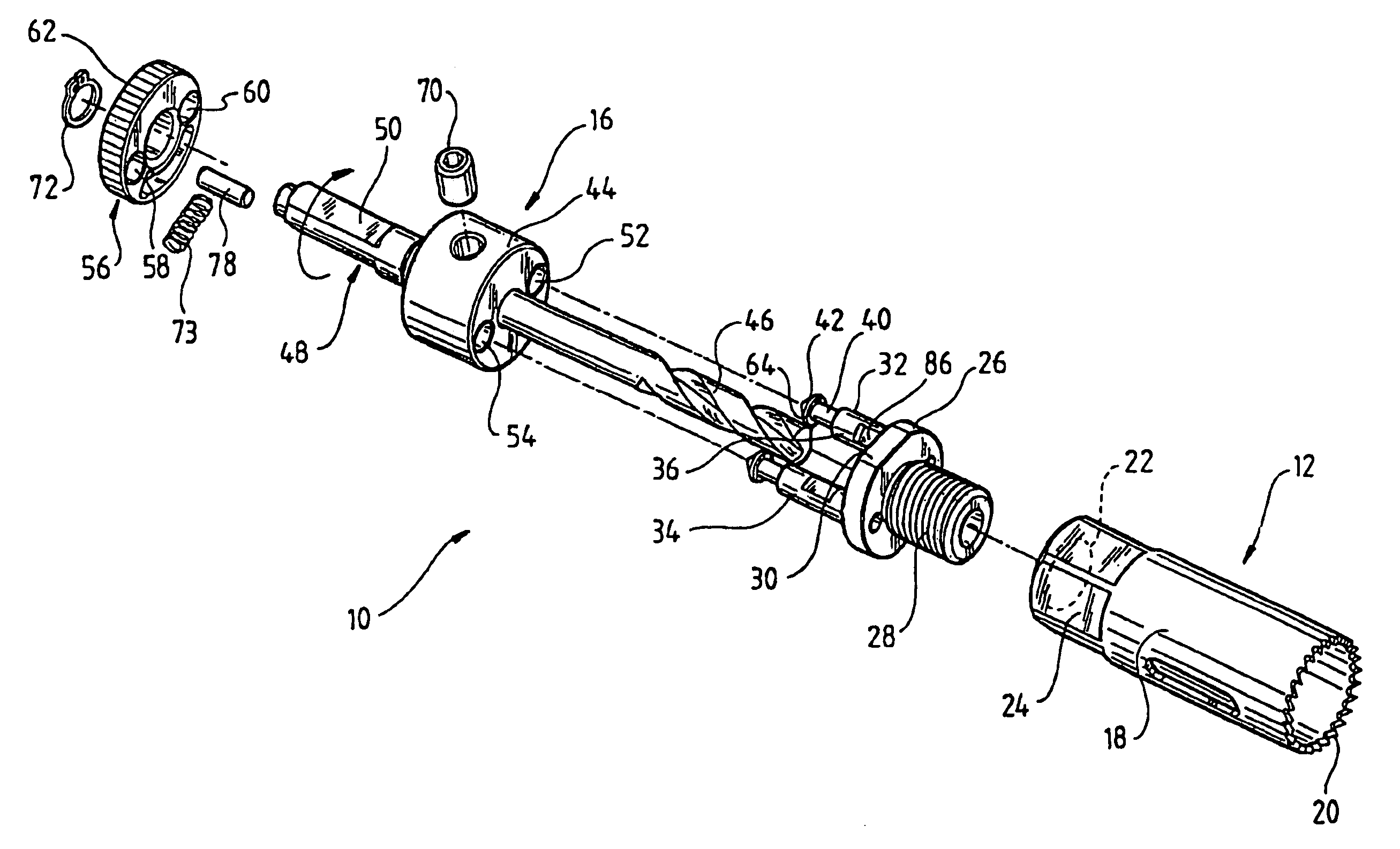
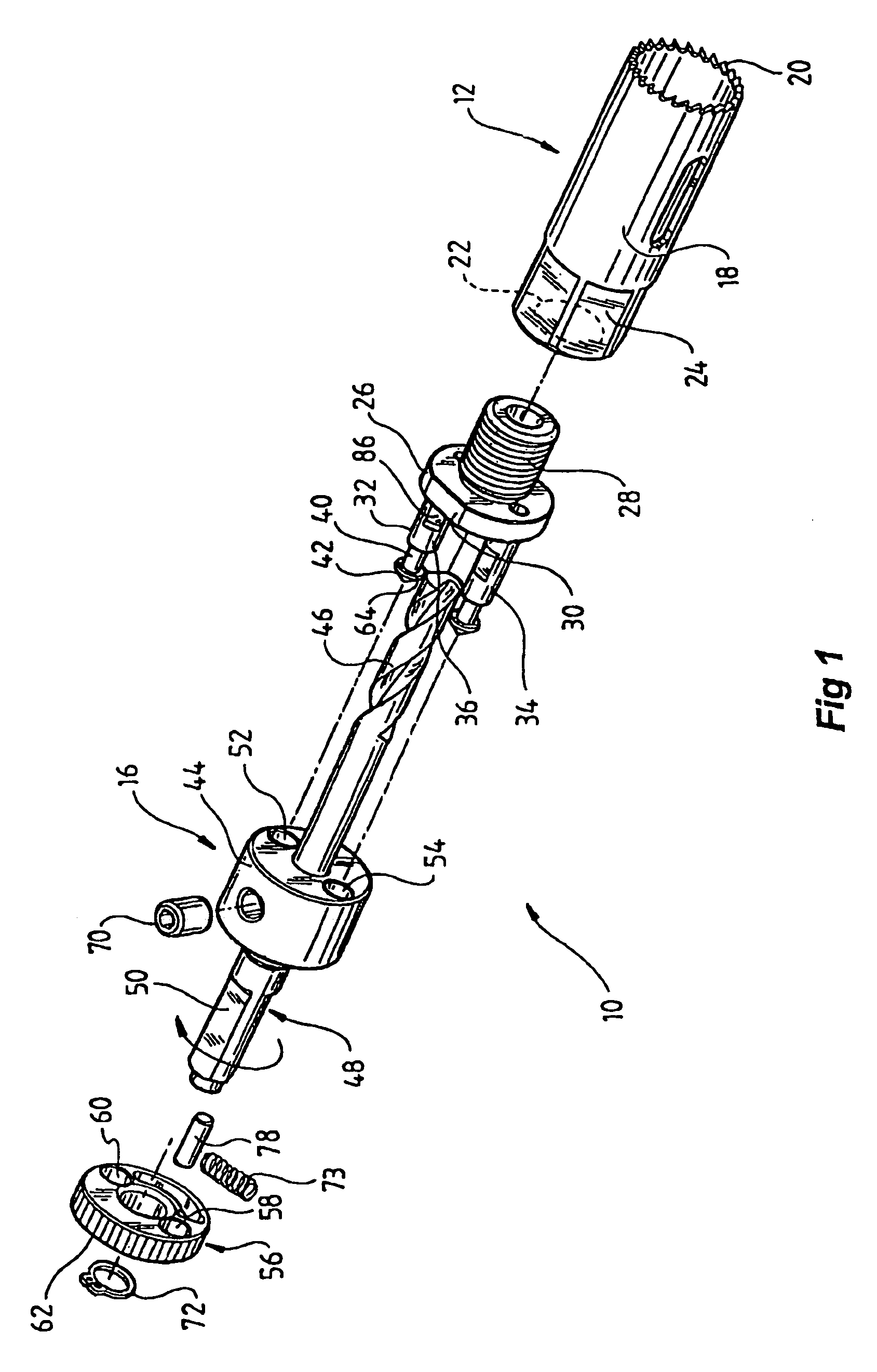
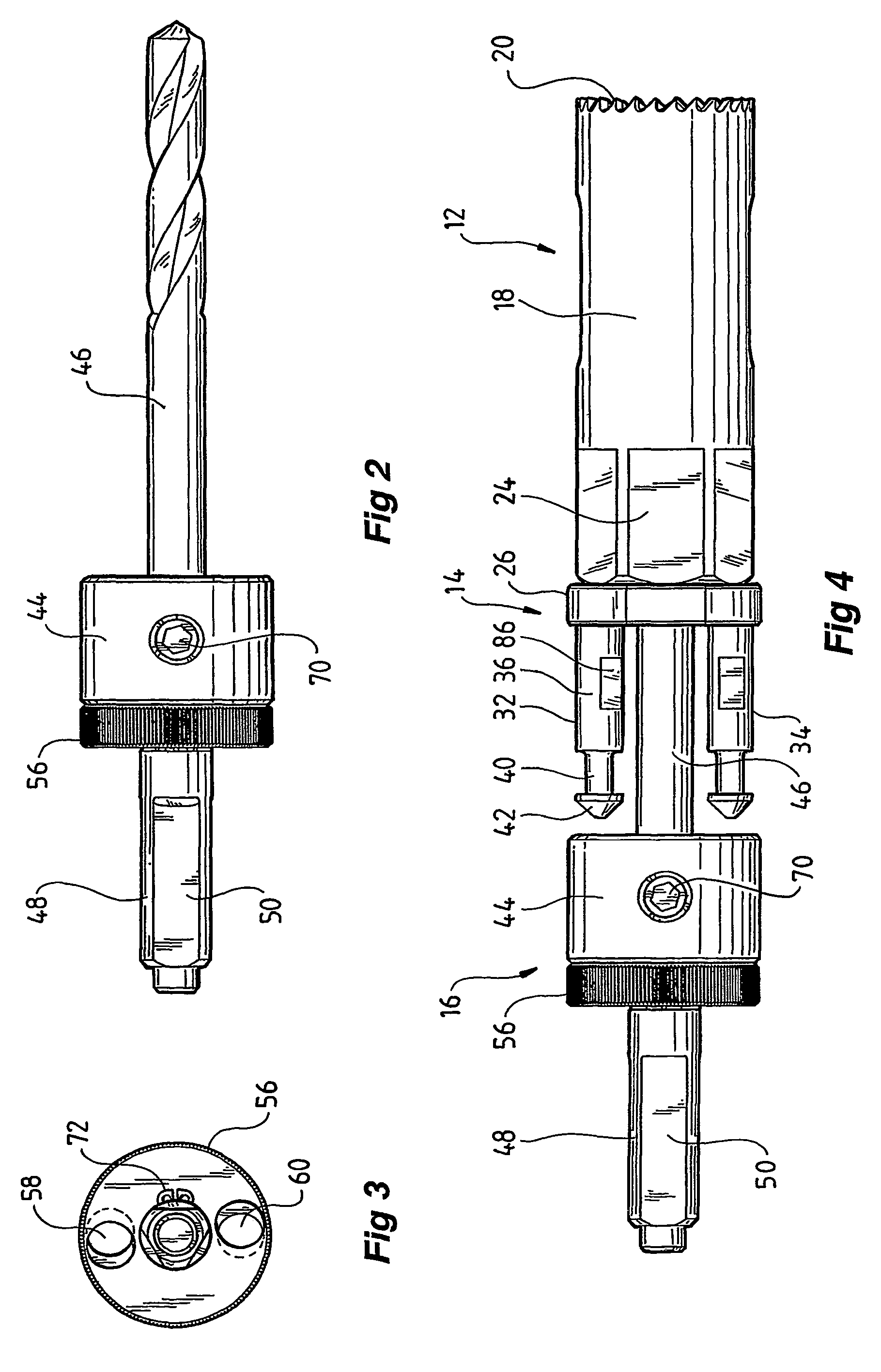
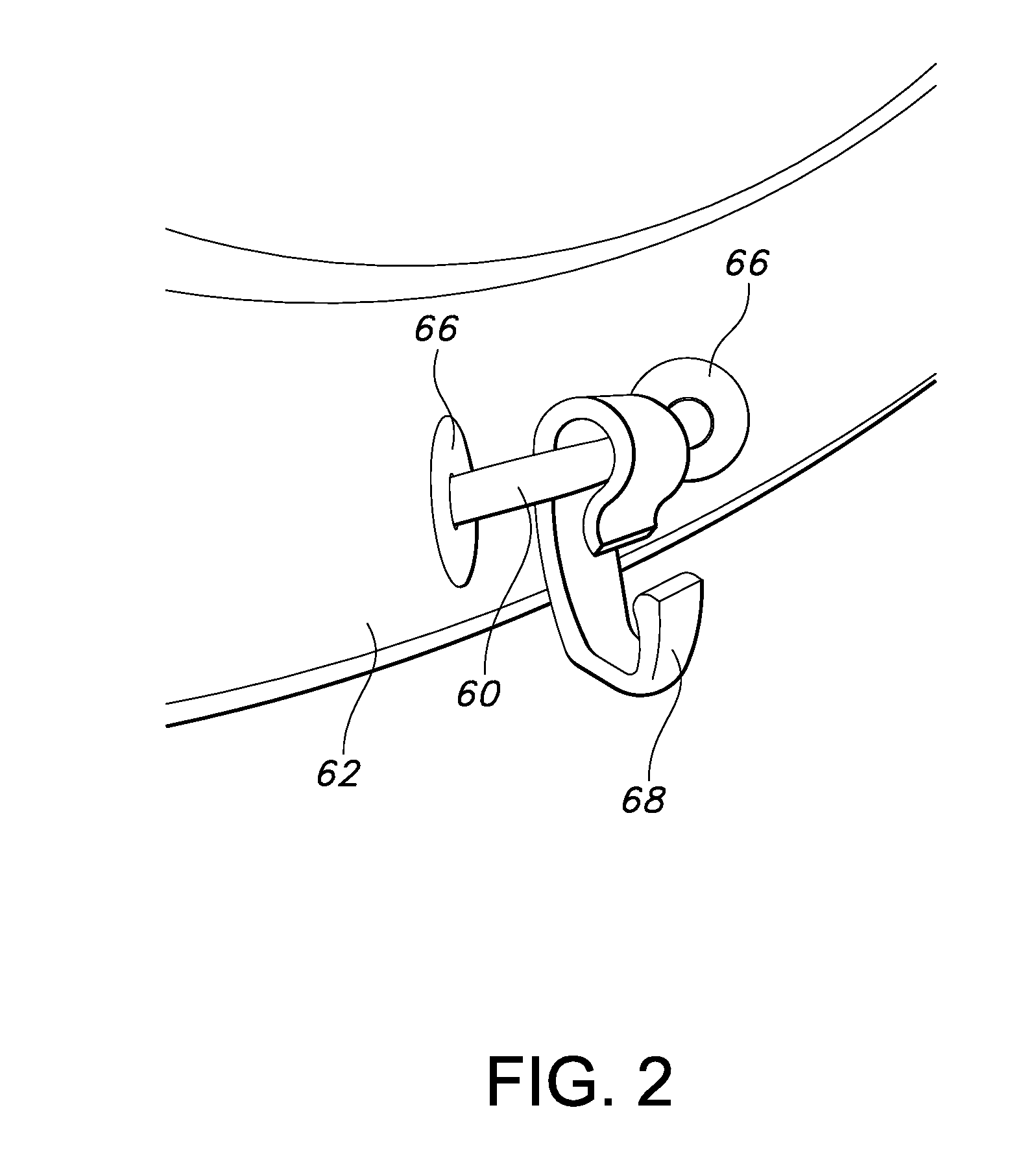
Hole saw assembly
InactiveUS7101124B2Quick deleteThread cutting machinesTransportation and packagingHole sawEngineering
A hole-saw assembly including a hole-saw having at one end a plurality of cutting teeth and at the other end two shafts. The assembly includes a mandrel coaxially aligned with said hole-saw and including a body having two bores therethrough coaxially aligned with said shafts. An annulus located on top of the body is coaxially aligned with said mandrel and hole saw and includes two holes, the annulus rotatable around its longitudinal axis from a first to a second position. In the first position the annulus holes are aligned with the bores and shafts allowing the shafts to be freely insertable and removable and in the second position the holes are misaligned to lock the shafts to the annulus. Such an arrangement allows the hole-saw and the mandrel to be easily and quickly mountable and demountable.
Owner:KEIGHTLEY KYM JOHN
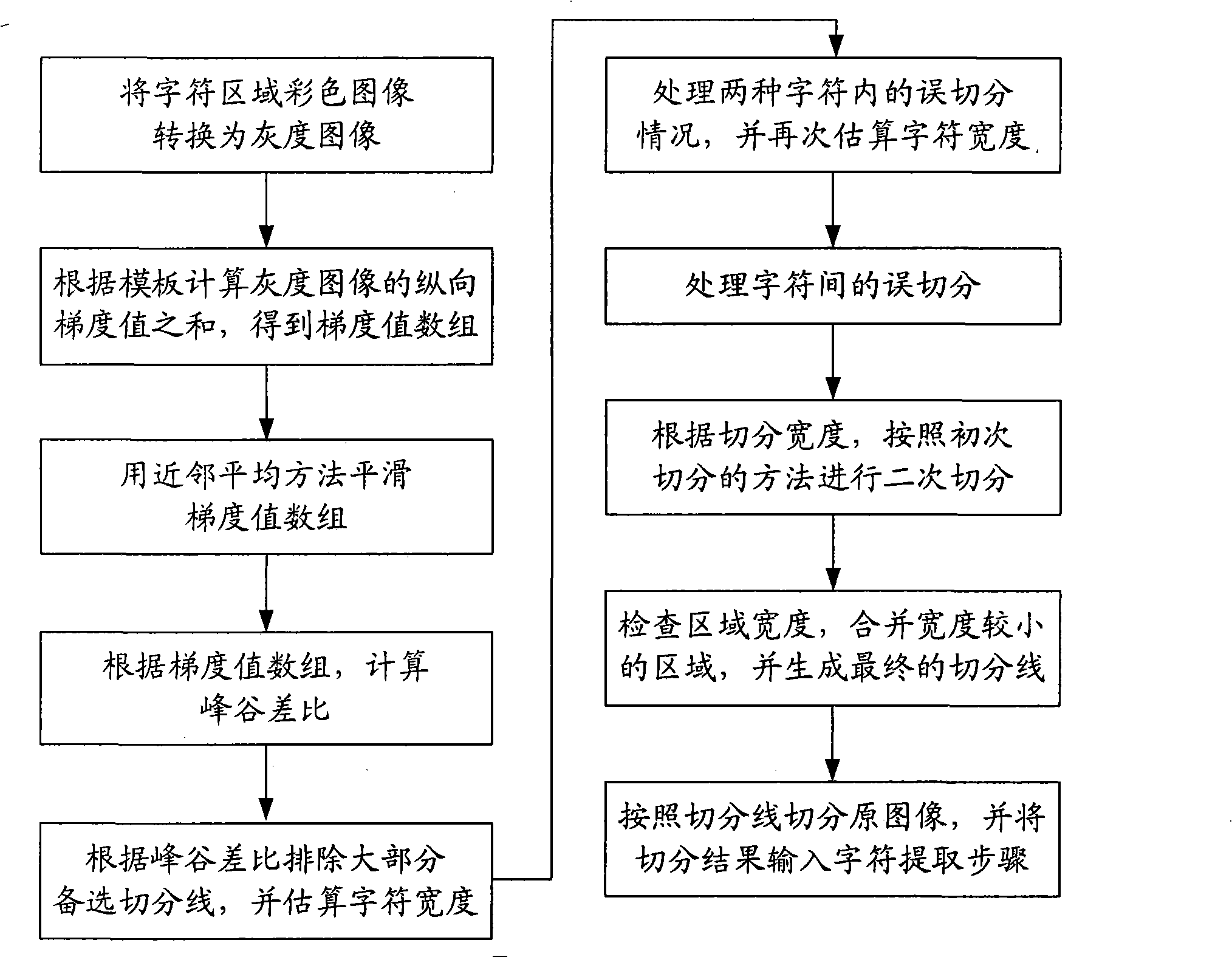
Character extracting method in digital video based on character segmentation and color cluster
InactiveCN101515325AImprove recognition rateReduce processing complexityCharacter and pattern recognitionVertical projectionDigital video
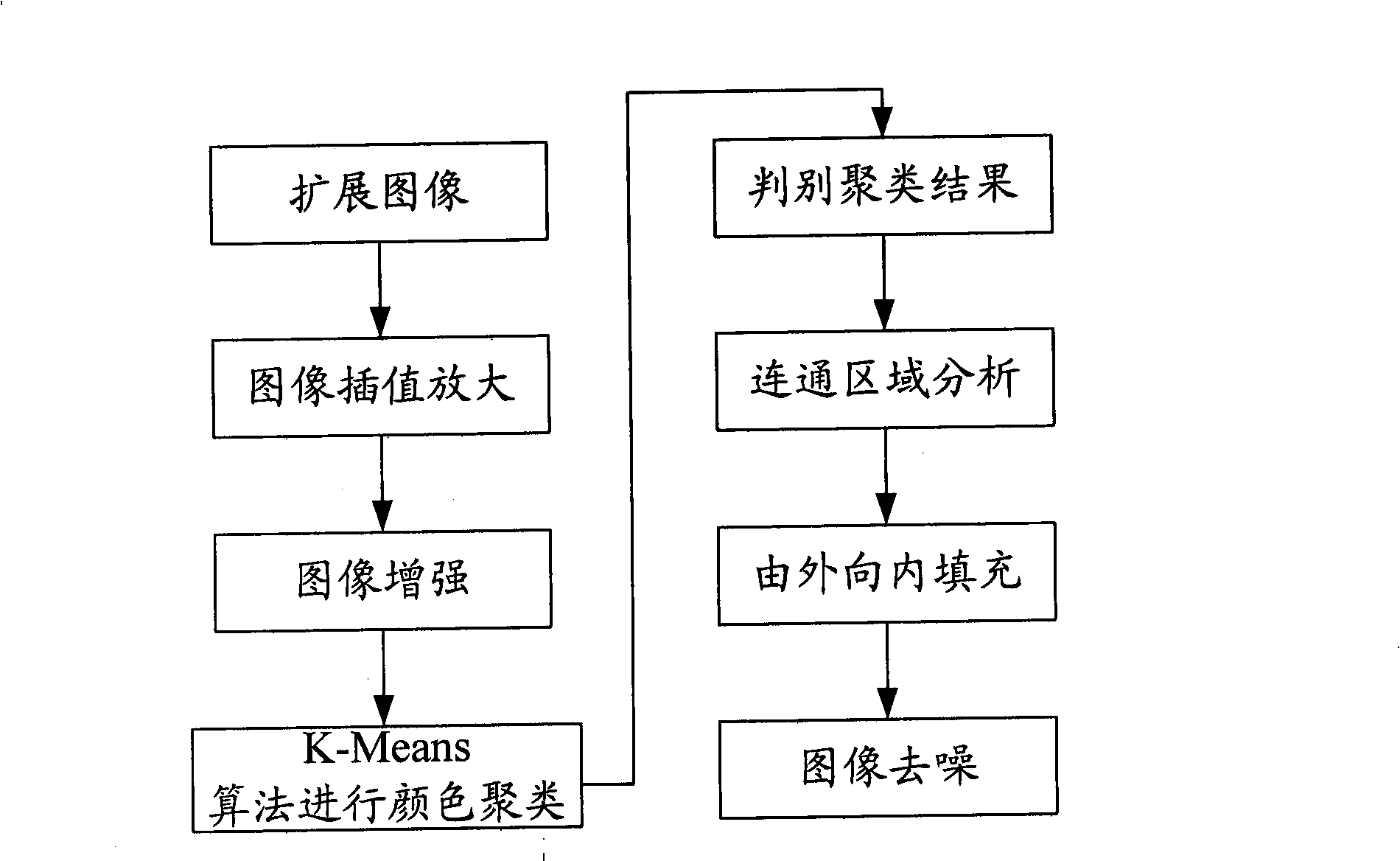
The invention relates to a character extracting method in a digital video based on character segmentation and color cluster, which comprises the following steps: (1) character segmentation: utilizing the characteristic differences of a character area and a character interval area to carry out vertical projection to segment images in the character area, namely, segmenting each row of area image containing a plurality of characters into a plurality of subarea images only containing a single character so as to reduce the post operating and treating difficulties and improve the identifying accuracy rate of OCR; and (2) character extraction: firstly, using the character color characteristic in the image to cluster colors, finding out an image layer containing maximum character information as a target image layer, and deleting the background area; and then, using the communicating characteristics of the characters to analyze a communicating area of the target image layer, and removing non-character areas to obtain such three results as single character images, an integral image of the character area and an integral image spliced by the single character images respectively, wherein all the three results are input to an OCR system to be identified, and the latter two results use the semantic processing function of the OCR and can accurately determine the characters with similar forms according to the context to improve the identifying effect.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Computer system for protecting software and method for protecting software
ActiveCN101178677AReduce consumptionSolve the problem of deletion efficiencySpecial data processing applicationsRedundant operation error correctionDistributed indexComputerized system
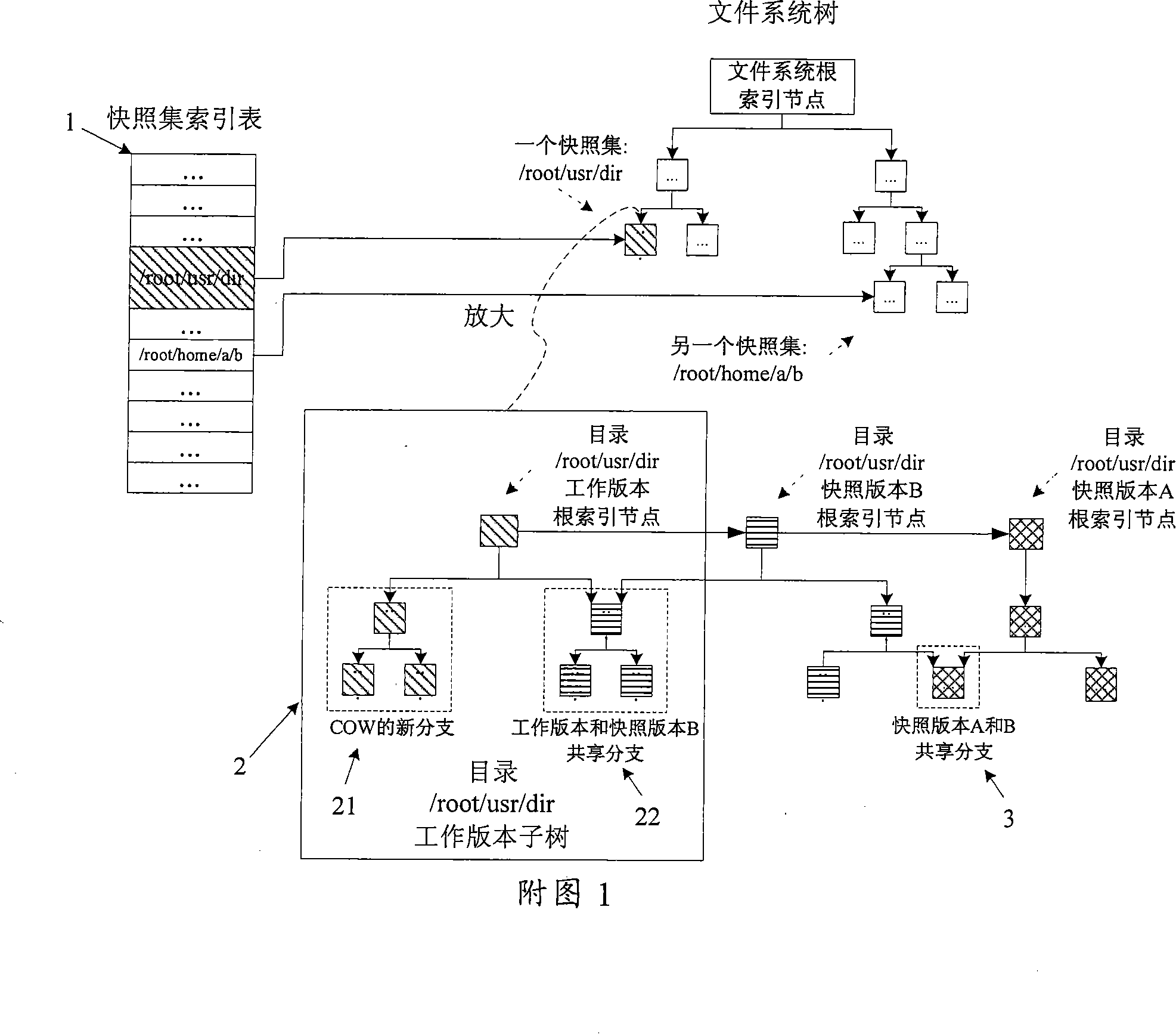
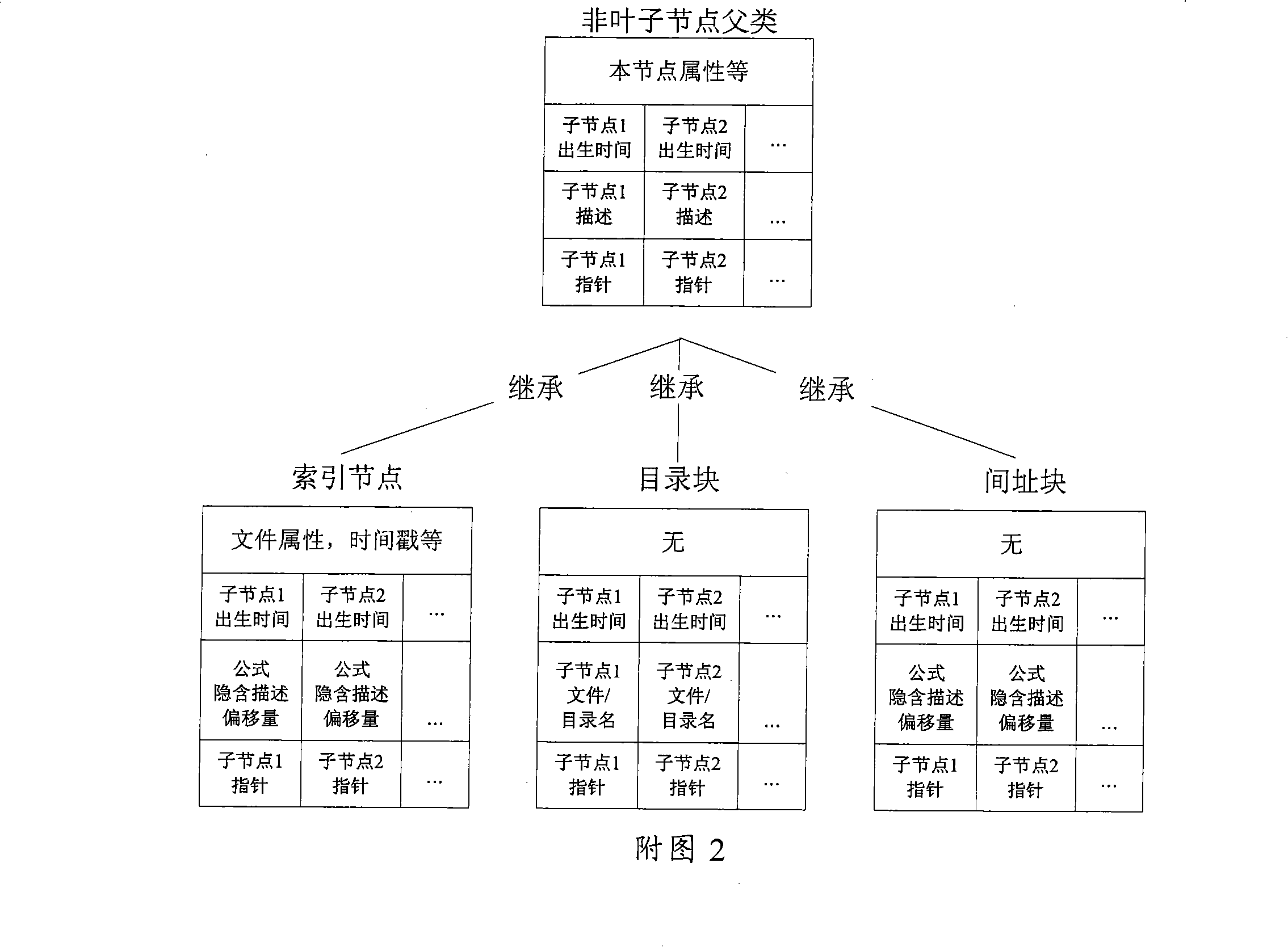
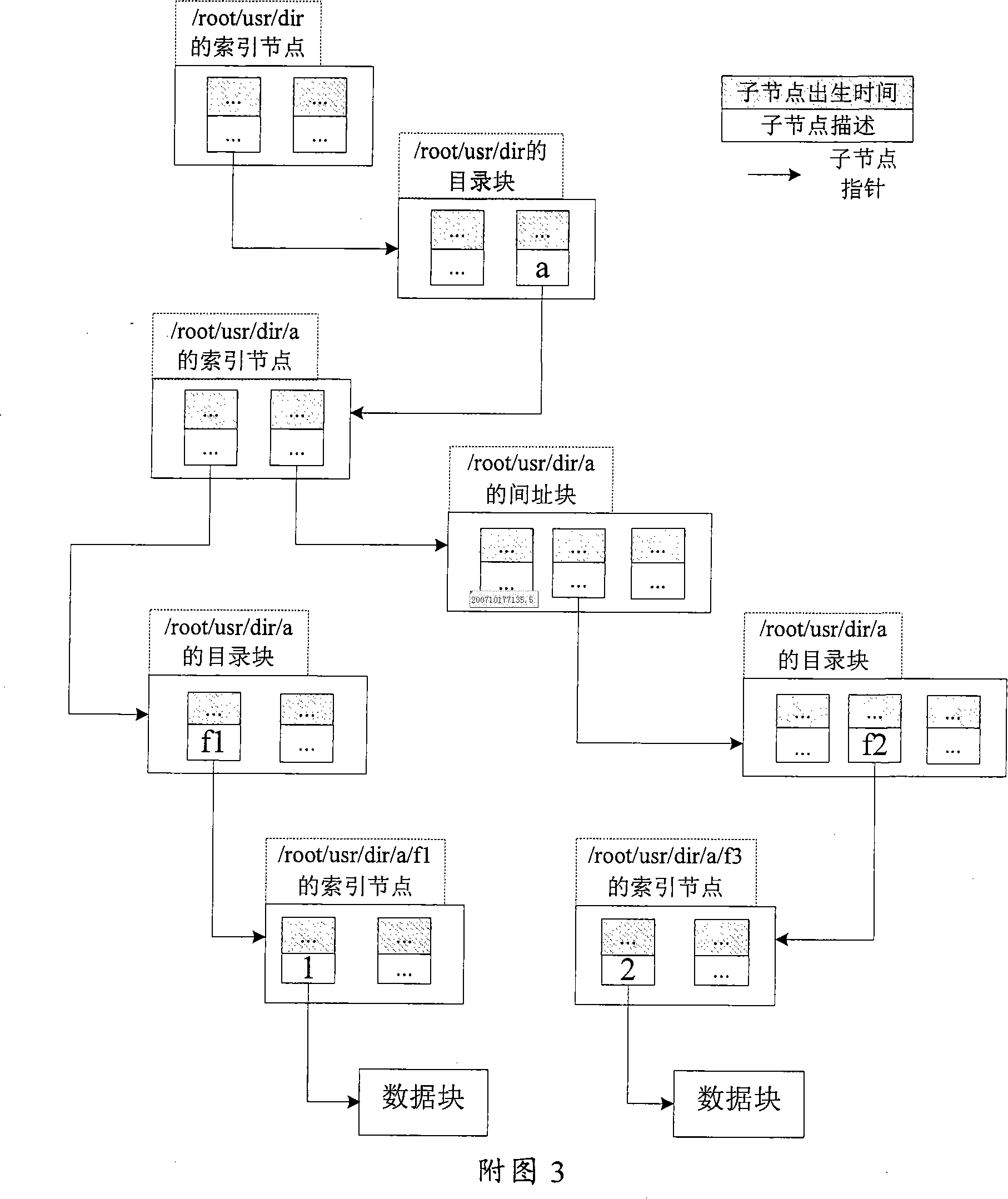
The invention provides a creating method of catalogue-grade computer file system snapshot, which comprises: the catalogue that needs to create snap is confirmed; when the catalogue creates the snap firstly, the root index node information of the catalogue work version is added to the snap index list and update the last time point of creating or deleting the snap; a new index node is distributed as the root index node of the creating snap version, and the content of the root index node of the work version is copied to the new distributed index node; the write copy chain list of the work version is copied to the root index node of the new creating snap, and then the write copy chain list content of the work version is deleted; the creating time of snap of the root index node of snap version is set as the present time of the computer system; the root index node of the snap version is linked to the snap chain list of the catalogue. The invention also provides the deleting method of the catalogue-grade computer file system snap and the modifying method of the catalogue work version.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
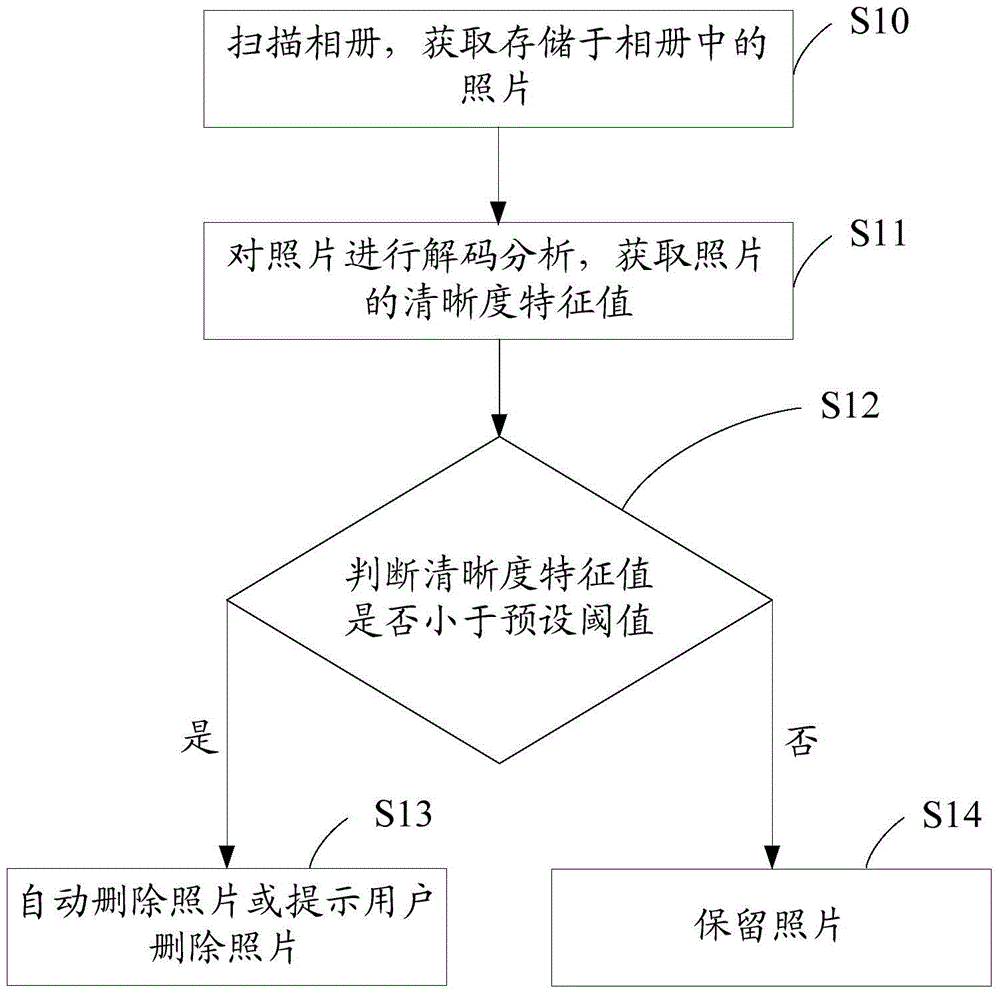
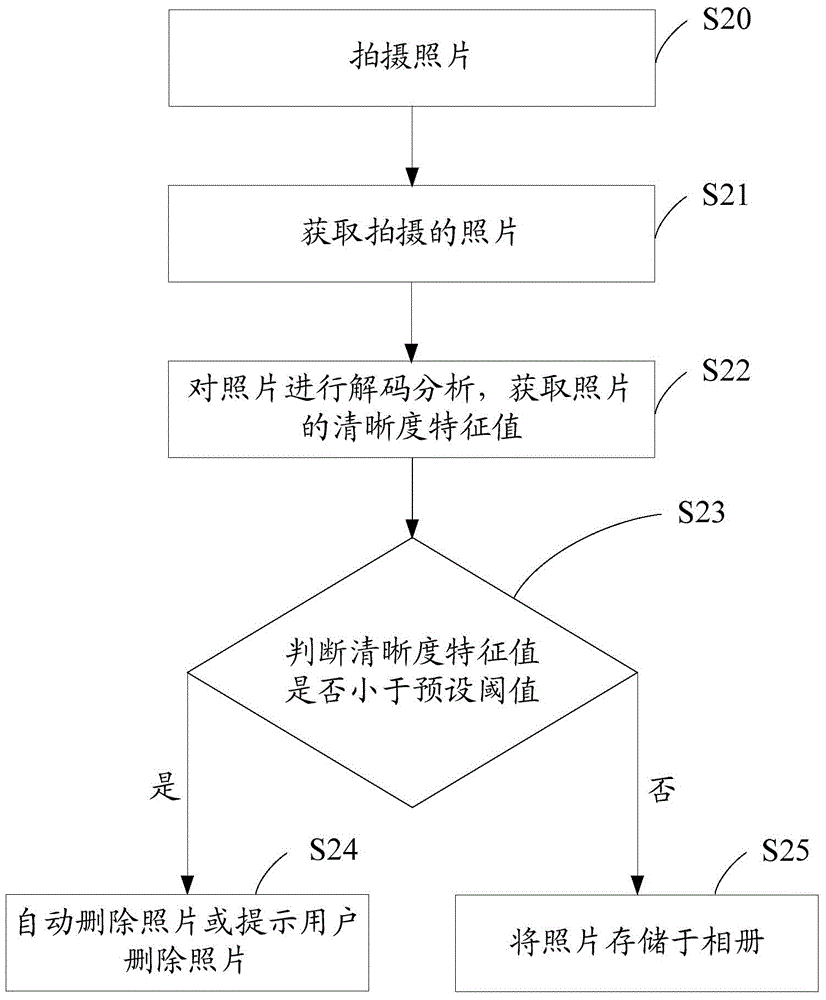
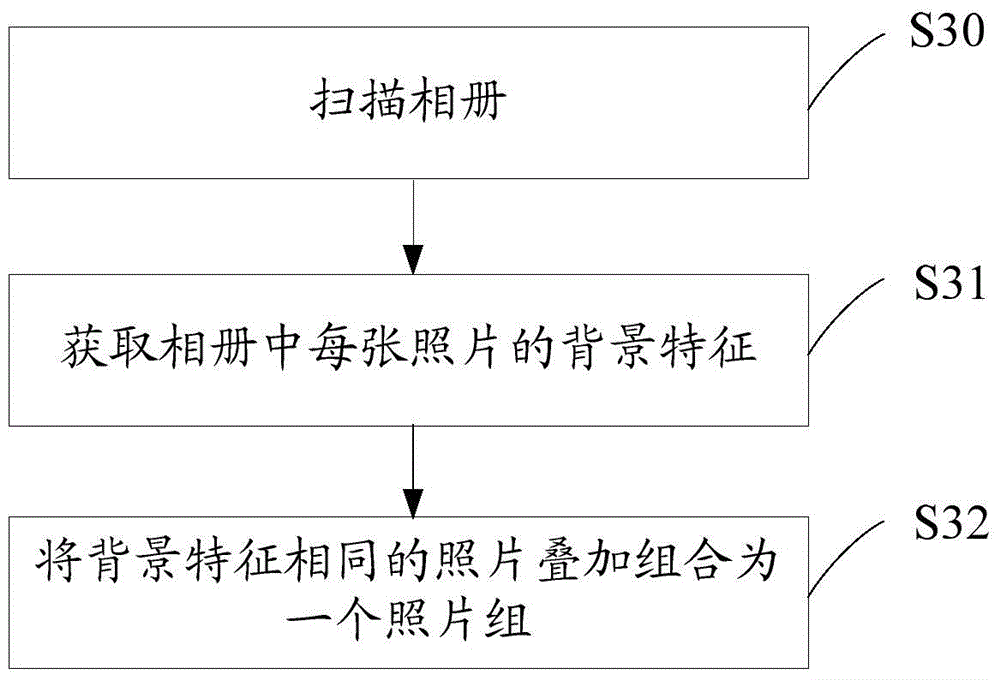
Photo album management method and device
ActiveCN104408061AQuick deleteQuick managementFile access structuresSpecial data processing applicationsComputer graphics (images)Management efficiency
The invention discloses a photo album management method and device. The photo album management method comprises the following steps: obtaining a currently-shot picture or a picture stored in a photo album; carrying out decoding analysis on the picture, and obtaining a definition characteristic value of the picture; when the definition characteristic value is smaller than a preset threshold value, automatically deleting the picture or prompting a user to delete the picture. Therefore, the pictures in the photo album can be automatically managed, and blurred pictures with poor quality in the photo album can be quickly cleared to improve management efficiency. Especially in a shooting process, the currently-shot picture can be analyzed and processed in time, so that the pictures stored in the photo album during shooting are all high-quality pictures, a phenomenon that a storage space is occupied by the condition that unqualified pictures are stored into the photo album is avoided, a user does not need to manually delete the pictures one by one from the photo album after the shooting is finished, efficiency is improved, and user experience is improved.
Owner:NUBIA TECHNOLOGY CO LTD
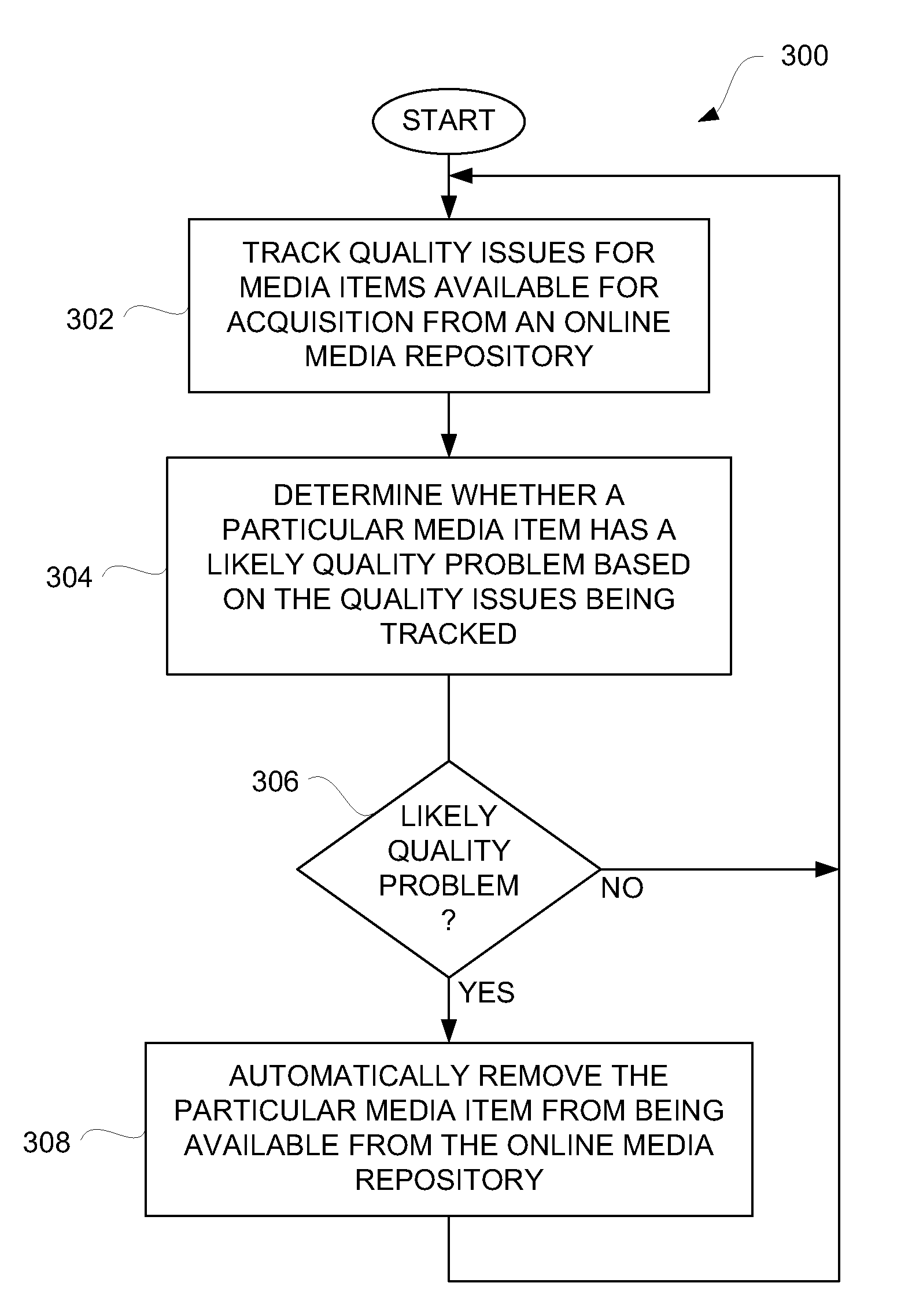
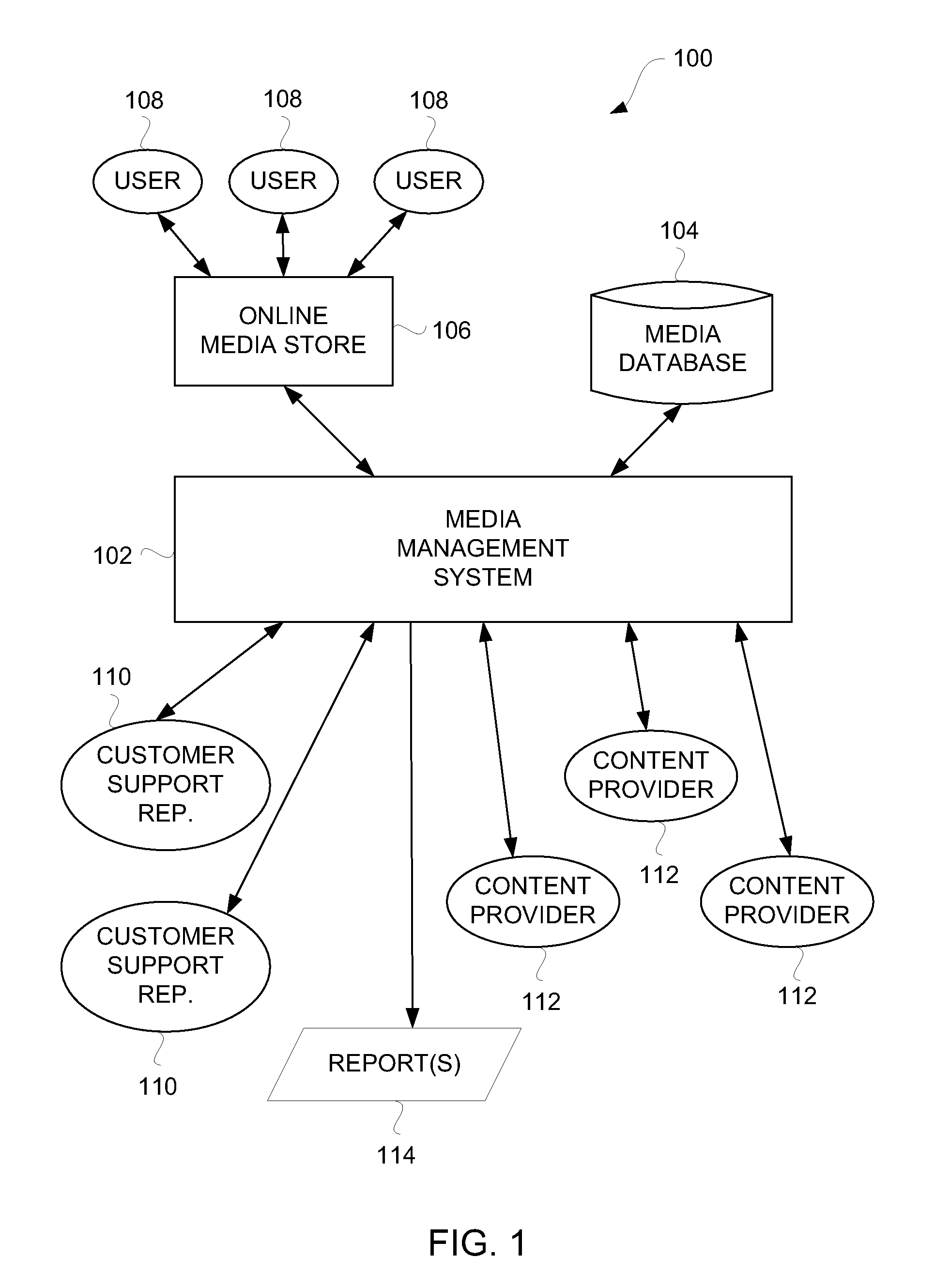
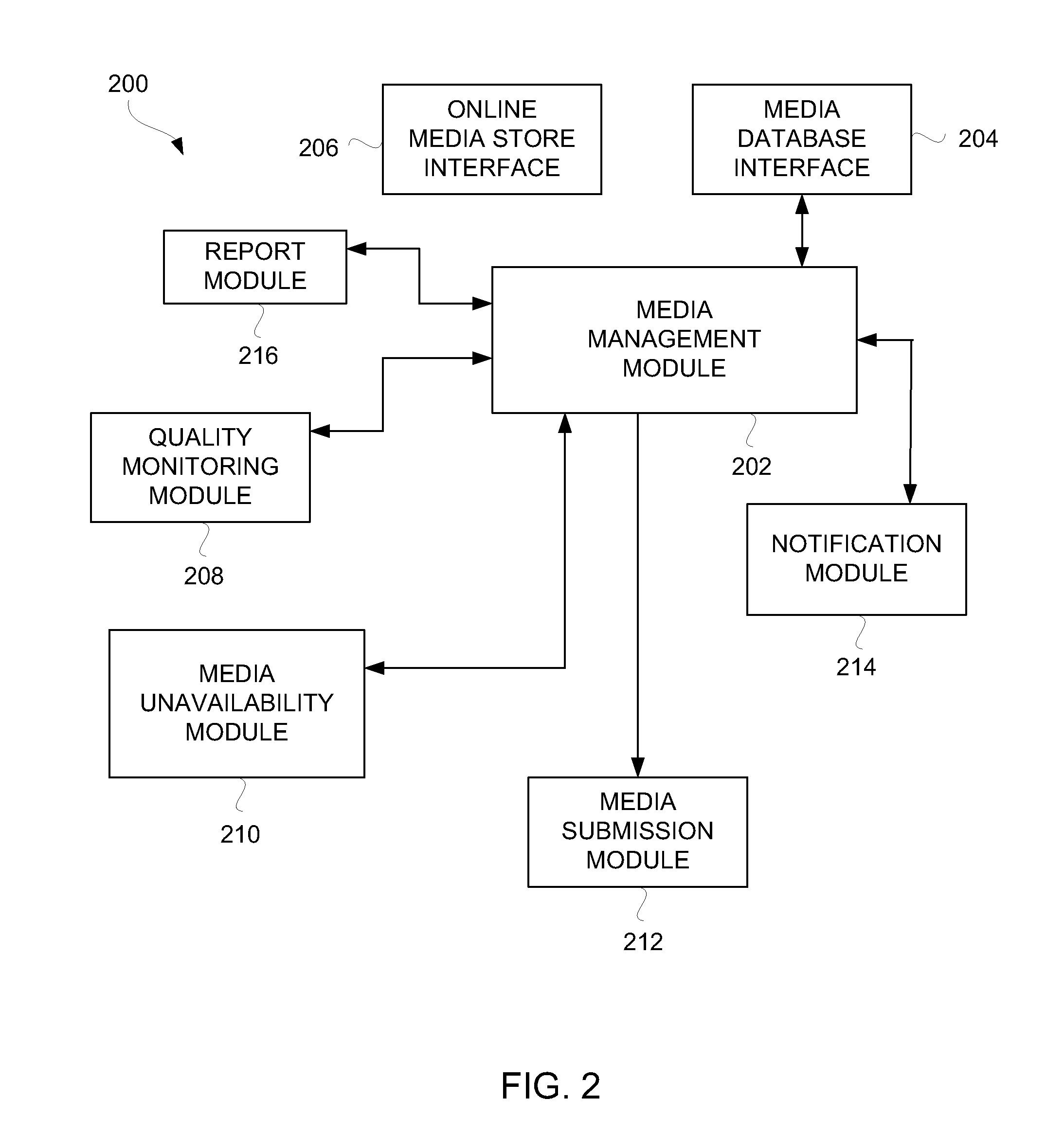
Quality-Based Media Management for Network-Based Media Distribution
Disclosed are techniques and configurations for monitoring quality of digital media assets available from a network-based media distribution system, and taking action to make those digital media assets that have quality deficiencies unavailable from the network-based media distribution system. The network-based media distribution system can provide an online media store from which users can acquire those of the digital media assets that are deemed available. In one embodiment, digital media assets that have quality deficiencies can be rapidly discovered and automatically removed from being available at an online media store.
Owner:APPLE INC
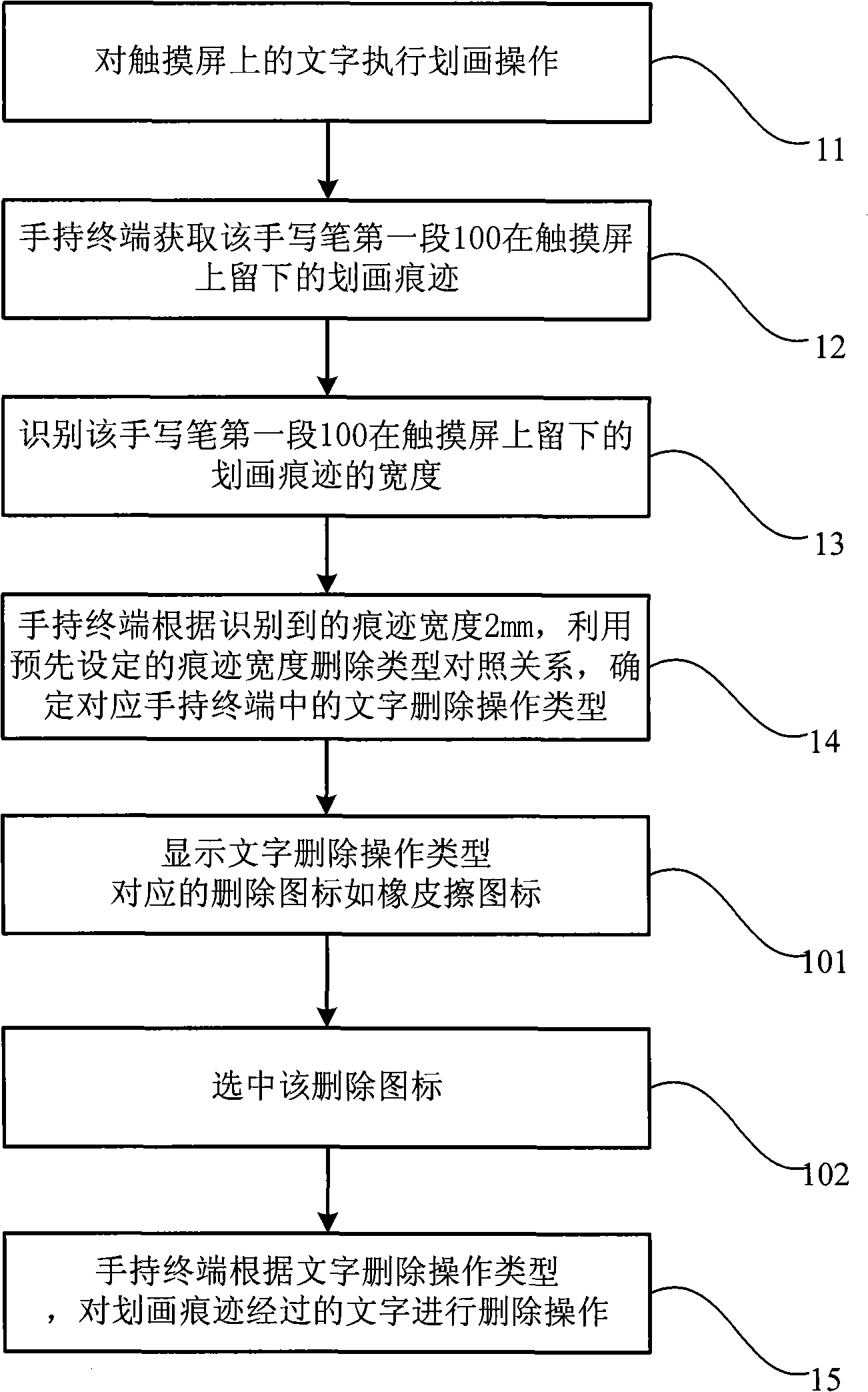
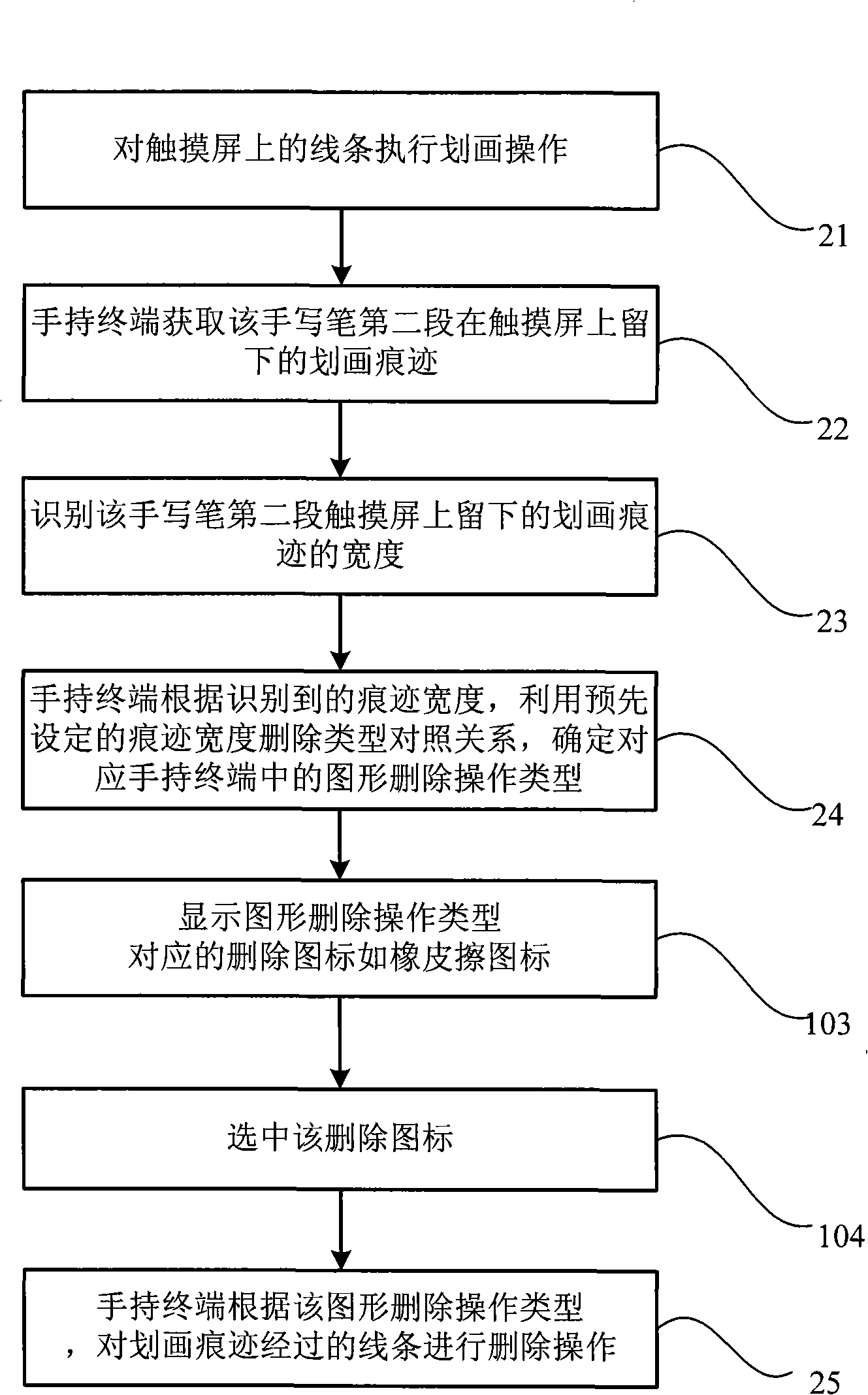
Handheld terminal deletion processing method and system thereof
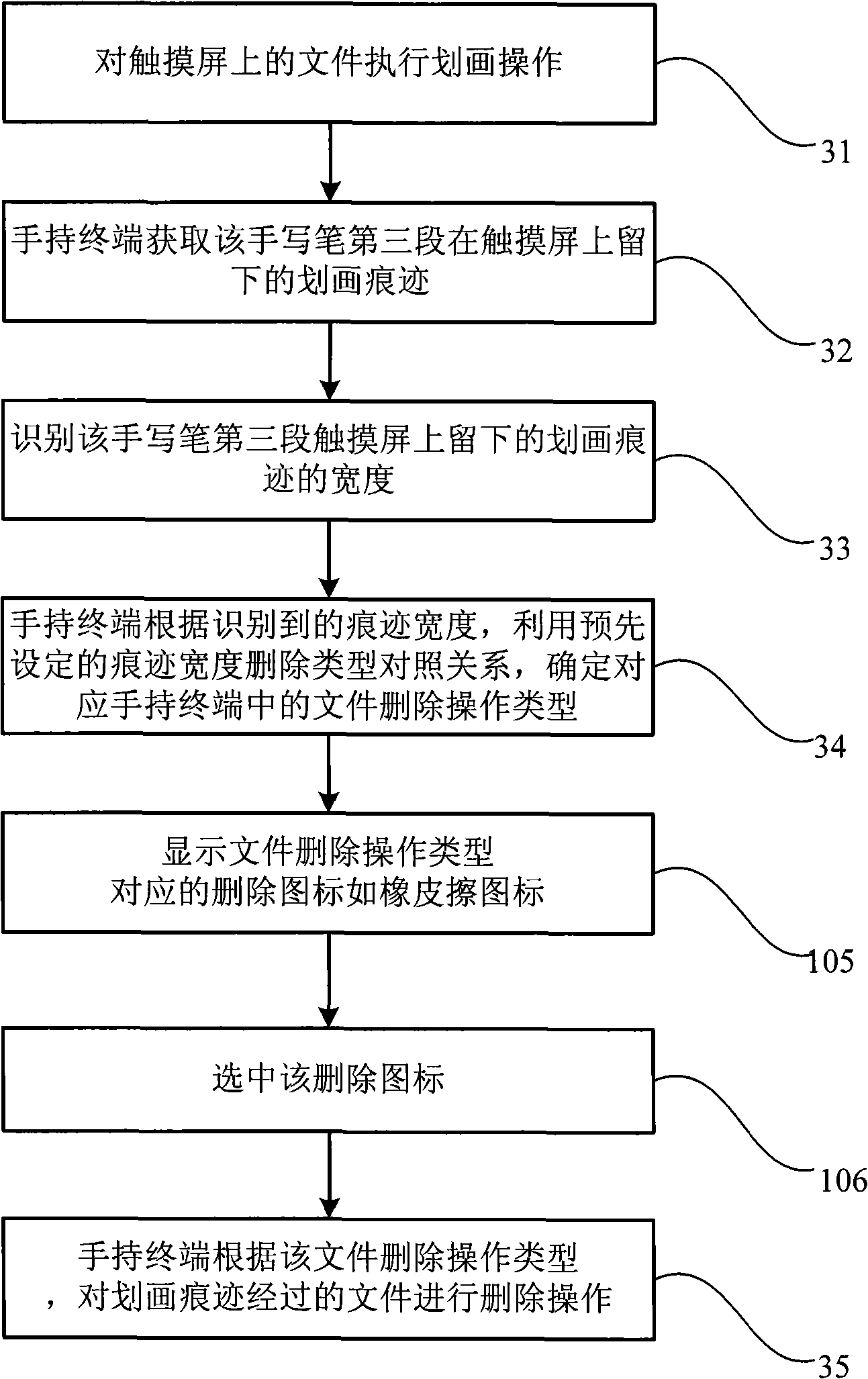
The invention discloses a handheld terminal deletion processing method, comprising the following steps of: marking an object to be deleted on a touch screen; obtaining the marking trace left on the object to be deleted after the marking operation; identifying the width of the marking trace; determining the corresponding deletion operation type of the width in a handheld terminal according to the width of the identified marking trace and by utilizing the preset contrast relationship of the trace width and the deletion type; and deleting the object to be deleted which is involved by the marking trace according to the deletion operation type. The invention further discloses a handheld terminal deletion processing system which is provided with a marking pen and a handheld terminal comprising a marking trace acquisition module, a marking width identification module and a module determining and implementing the deletion operation. Therefore, the invention provides the user a visual operation for rapidly deleting texts, images and document objects, thus causing the operation of the terminal to conform to the operation model in the real world.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Method and device for processing display information of mobile terminal and touch screen thereof
InactiveCN101943995AQuick deleteEasy to deleteSubstation equipmentInput/output processes for data processingComputer terminalTouchscreen
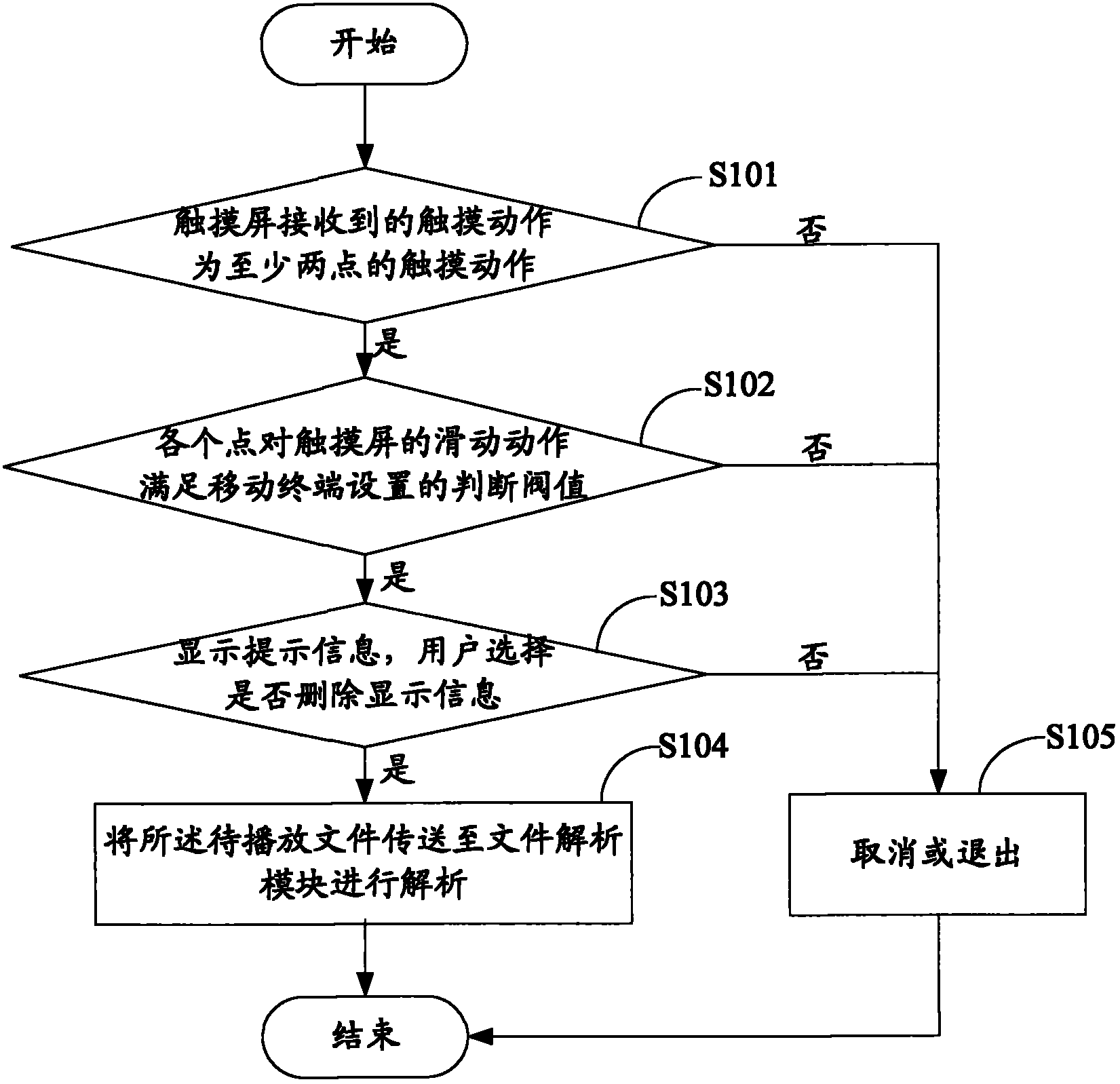
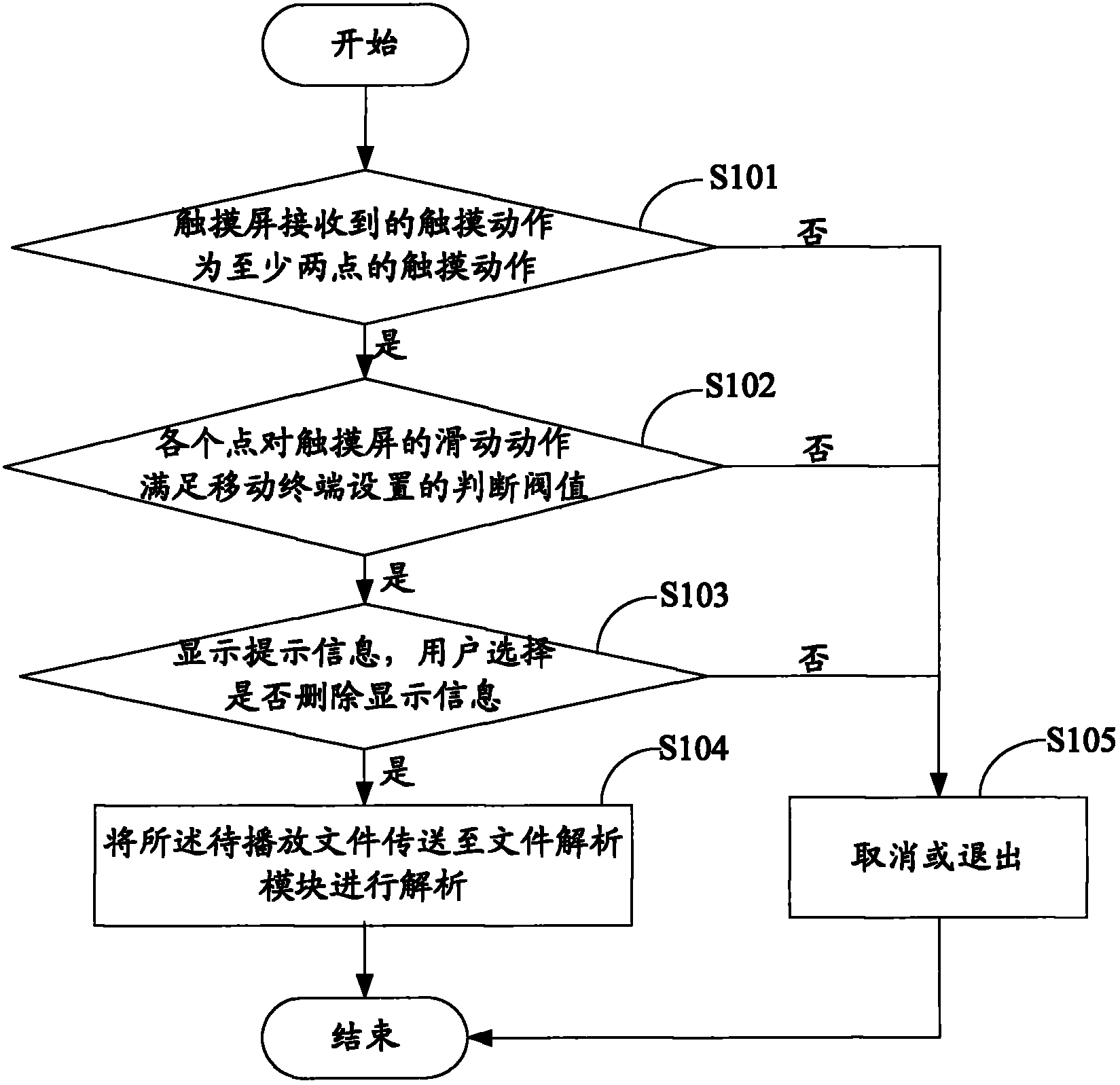
The invention belongs to the technical field of mobile terminals, and discloses a method and a device for processing display information of a mobile terminal and a touch screen thereof. The method comprises the following steps: judging whether the touch action received by the touch screen has at least two touch points; if so, judging whether the slide action of each point on the touch screen satisfies the judgment threshold set by the mobile terminal; and if so, deleting the display information on the current interface, wherein the judgment threshold is determined by the following steps: at least two points on the touch screen slide in parallel, the connected slide actions of the points are opposite in directions, and the angle between the connected slide actions is within the judgment angle set by the mobile terminal. The invention can be used for deleting the display information on the interface quickly and conveniently, thereby enhancing the interactions between the mobile terminal and a user and benefiting the popularization of the mobile terminal.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
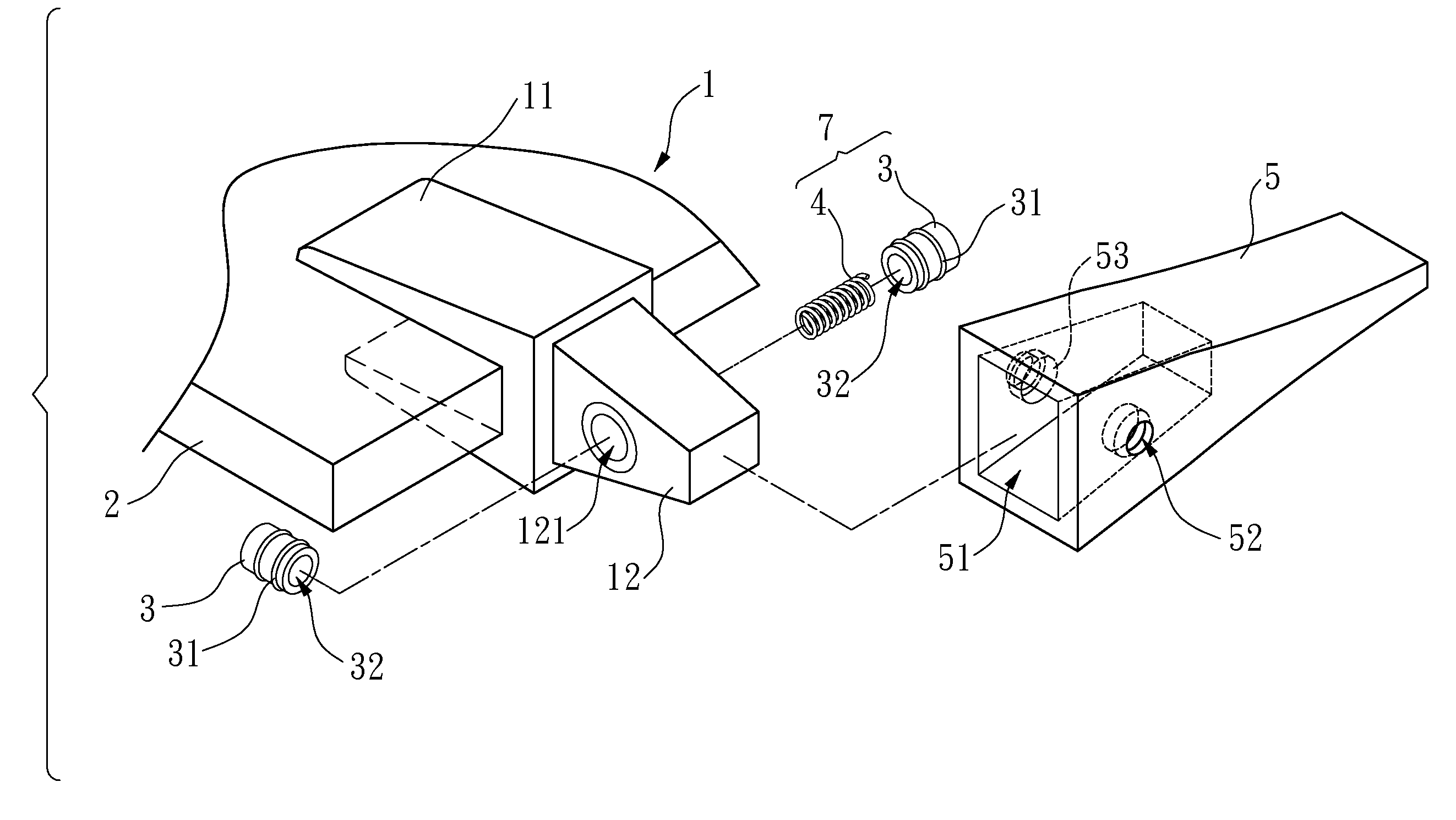
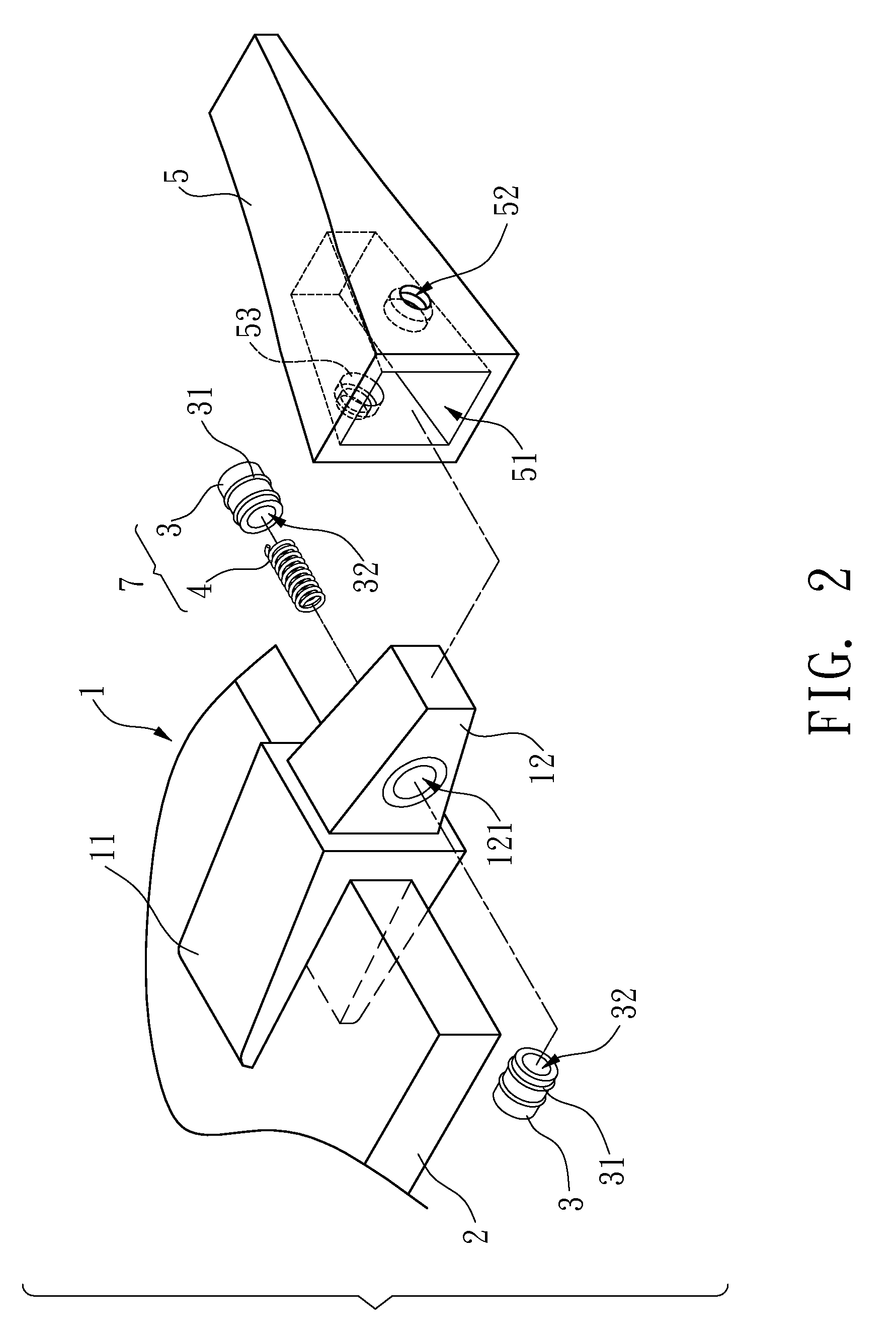
Replacement and urging device for the bucket teeth of an engineering construction machine
InactiveUS20100257759A1Quick removalQuick assemblySoil-shifting machines/dredgersEngineeringBuilding construction
A replacement and urging device for the bucket teeth of an engineering construction machine is disclosed. An adaptor is mounted with a bucket tooth. A first through hole holes horizontally through the adaptor. Both sides of the bucket tooth are formed with a second through hole, respectively. An engaging unit is interposed between the first through hole and the second through hole to slide between them. This enables the bucket tooth to be mounted and positioned on the adaptor. The invention thus prevents the bucket tooth from constantly hitting the adaptor.
Owner:KO JUNG CHING
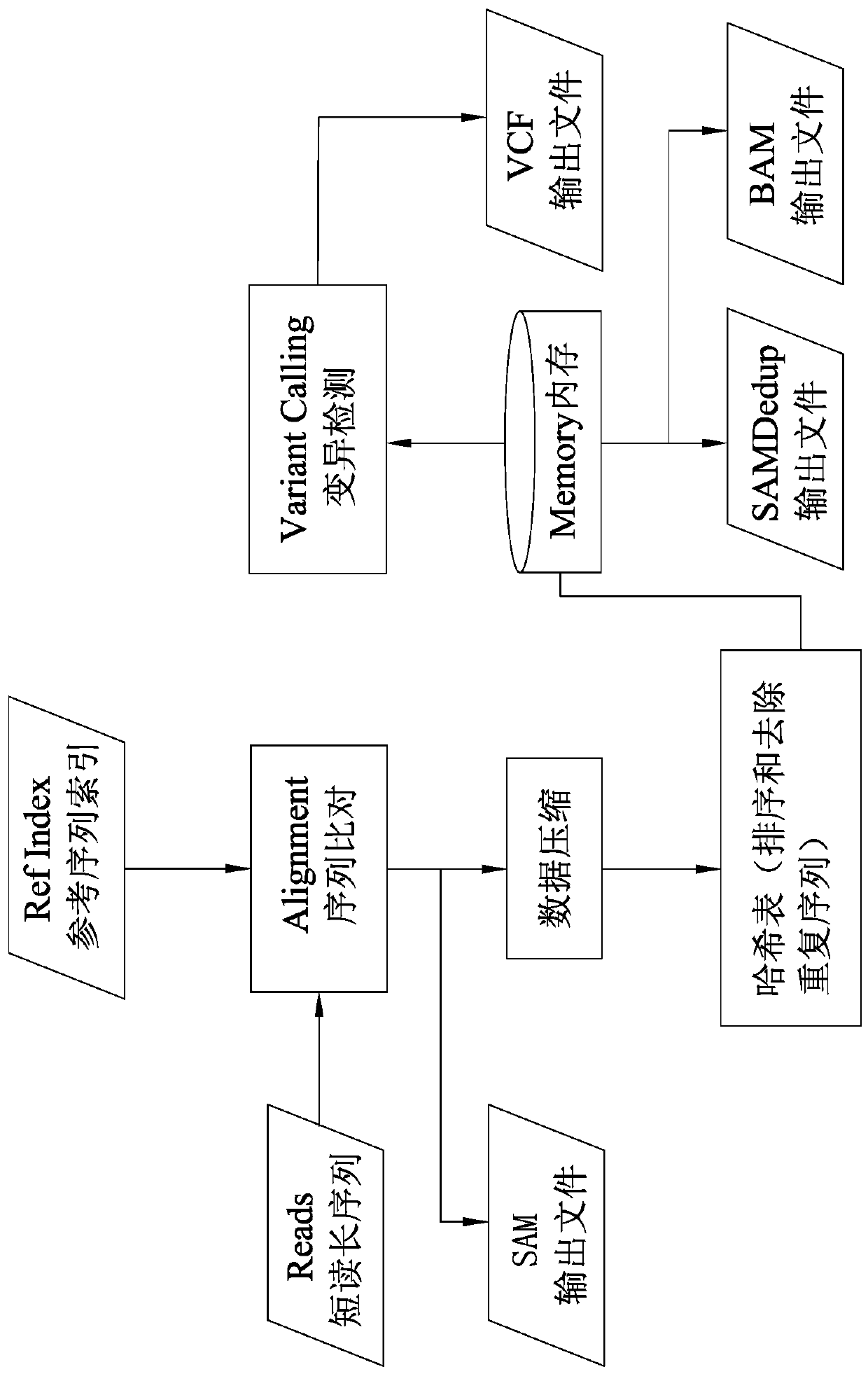
Data processing method of next-generation sequencing (NGS) data analysis platform (IMP)
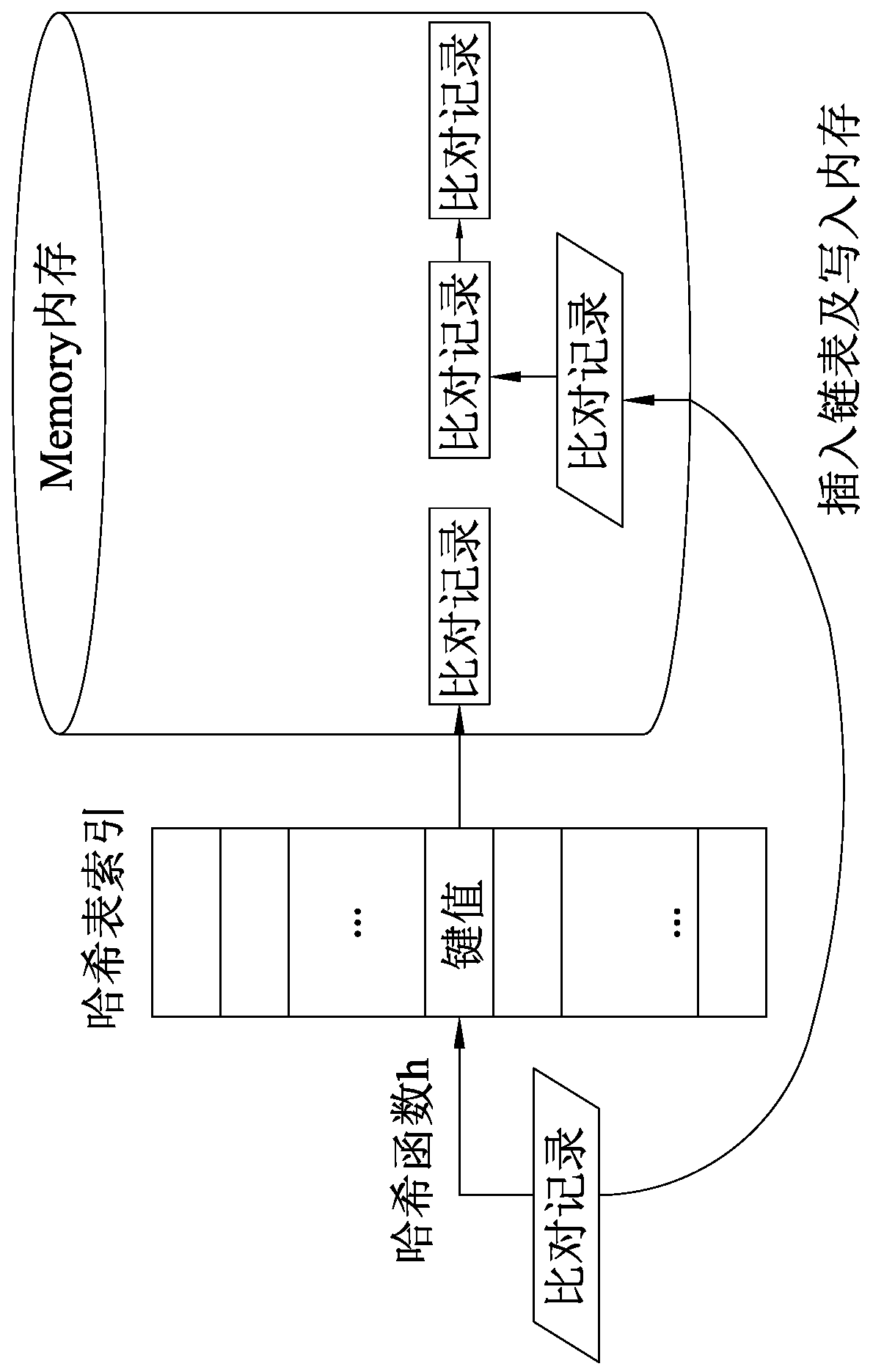
The invention discloses a data processing method of a next-generation sequencing (NGS) data analysis platform (IMP). The next-generation sequencing data analysis platform implements an entire next-generation sequencing processing process as a single step from inputting of short-reading long-sequences of an FASTQ file format to outputting of mutation detection of a standard VCF file format; at thesame time, the method also provides an option of outputting an intermediate result of sequence alignment in a standard SAM or BAM format; longer data searching and loading time required for I / O accessing of hard drives and SSDs can be avoided through massive memory accessing without using slow I / O to exchange data; hash table writing or reading, deletion of duplicated alignment records and mutation detection are all enabled to be faster; quick next-generation sequencing data analysis can be realized on the premise of not impacting analysis quality; and compared with speeds of existing schemes,a speed of the method is increased up to 20 times.
Owner:厦门极元科技有限公司
Wooden horse monitoring and auditing method and system thereof
InactiveCN102045220APerformance is not affectedRealize real-time monitoringData switching networksWeb operationsNetwork behavior
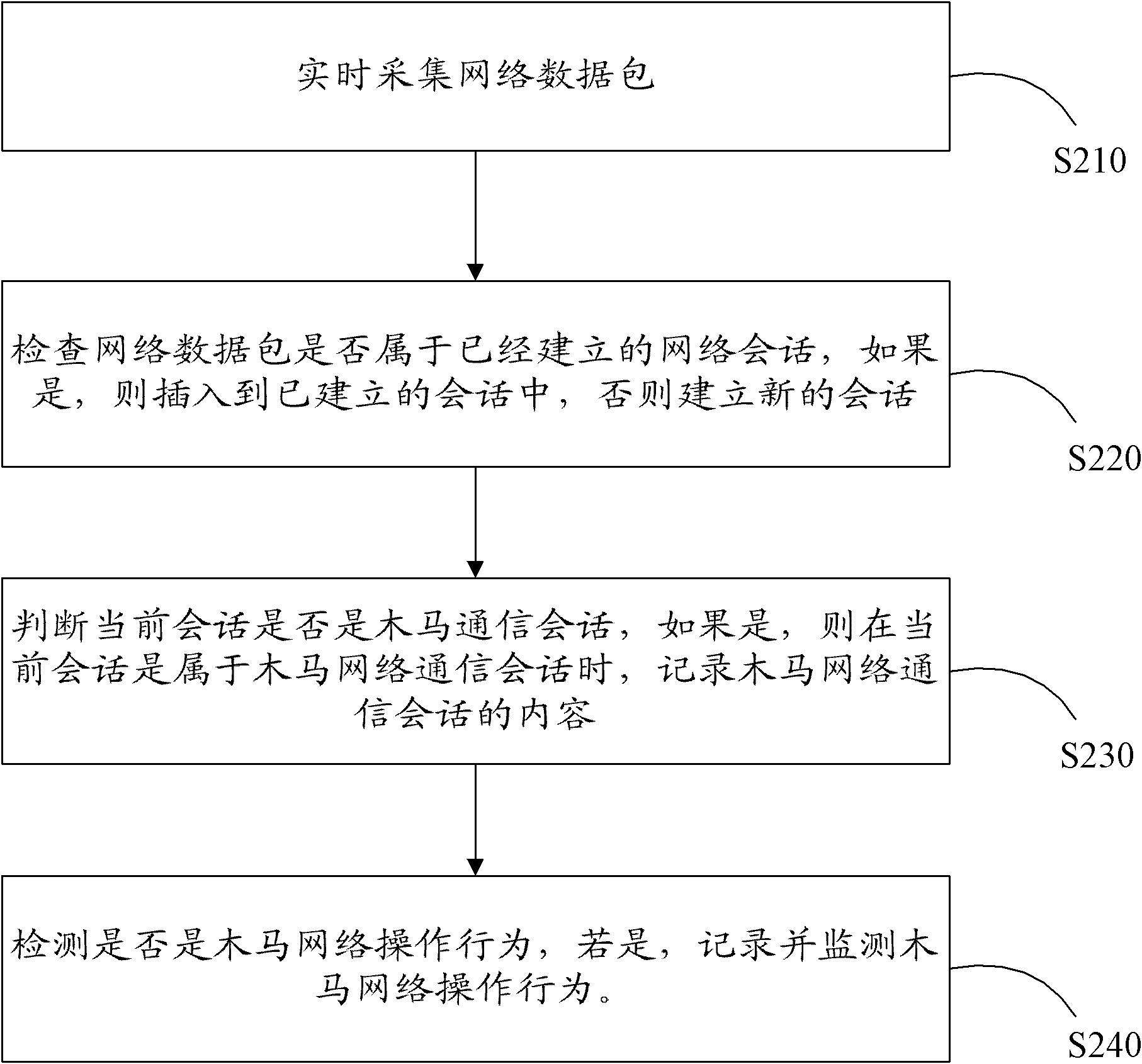
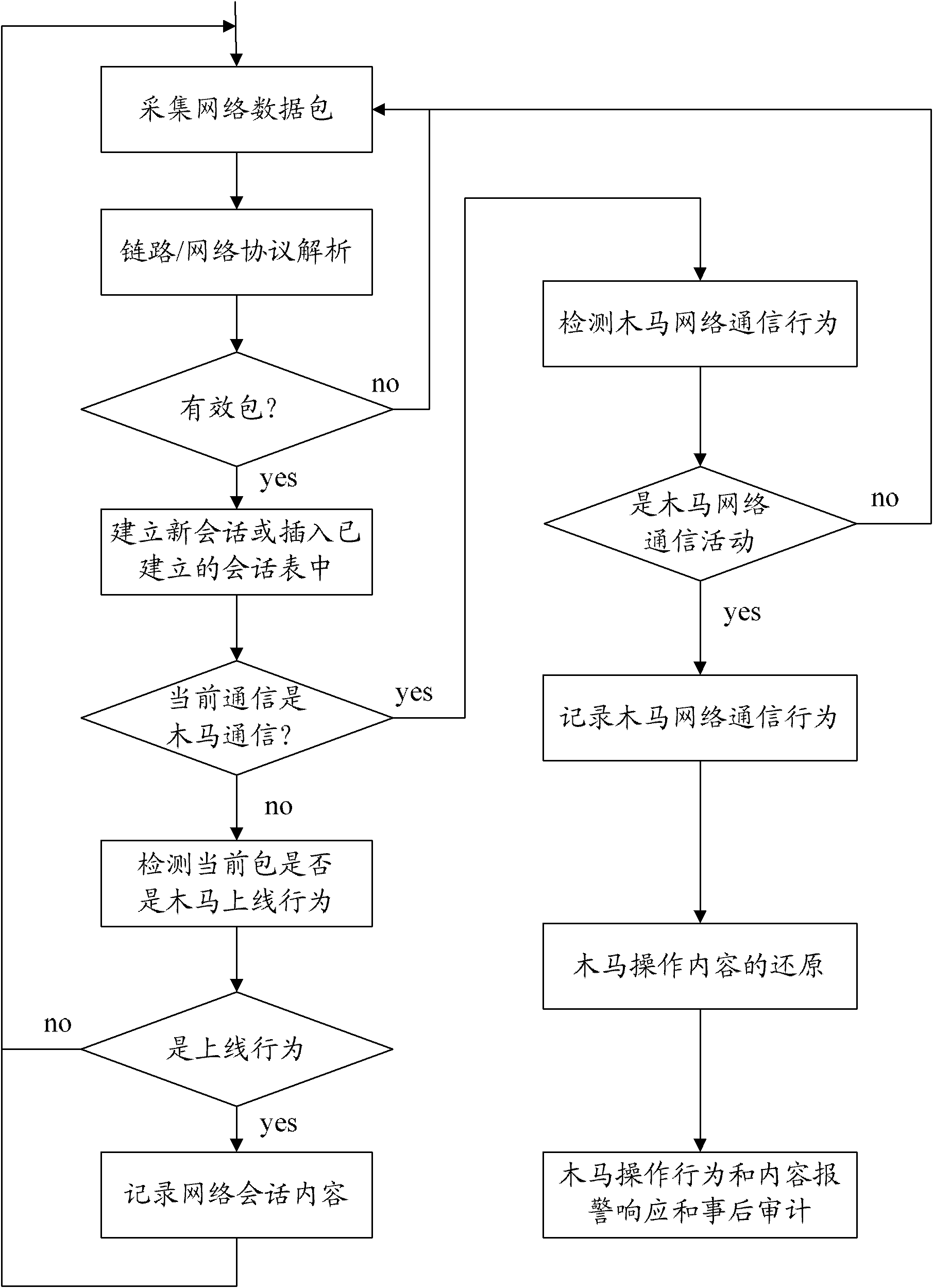
The invention discloses a wooden horse monitoring and auditing method and a system thereof, wherein the method comprises the following steps: acquiring a network data packet in real time; determining the current session, checking whether the network data packet belongs to the established network session, if so, inserting the network data packet into the established session, and otherwise, establishing new session; judging whether the current session is wooden horse communication session, if so, recording the content of wooden horse network communication session when the current session belongs to the wooden horse network communication session; according to the recorded content of the wooden horse network communication session, detecting whether the content is wooden horse network operation behavior, if so, recording and monitoring the wooden horse network operation behavior. According to the invention, not only the type of the wooden horse can be recognized, but also the network behavior of the wooden horse can be monitored.
Owner:国都兴业信息审计系统技术(北京)有限公司
Data anti-theft method in case of mobile phone loss
InactiveCN103391367AQuick deleteMuch timeUnauthorised/fraudulent call preventionInternal/peripheral component protectionExternal storageMobile phone
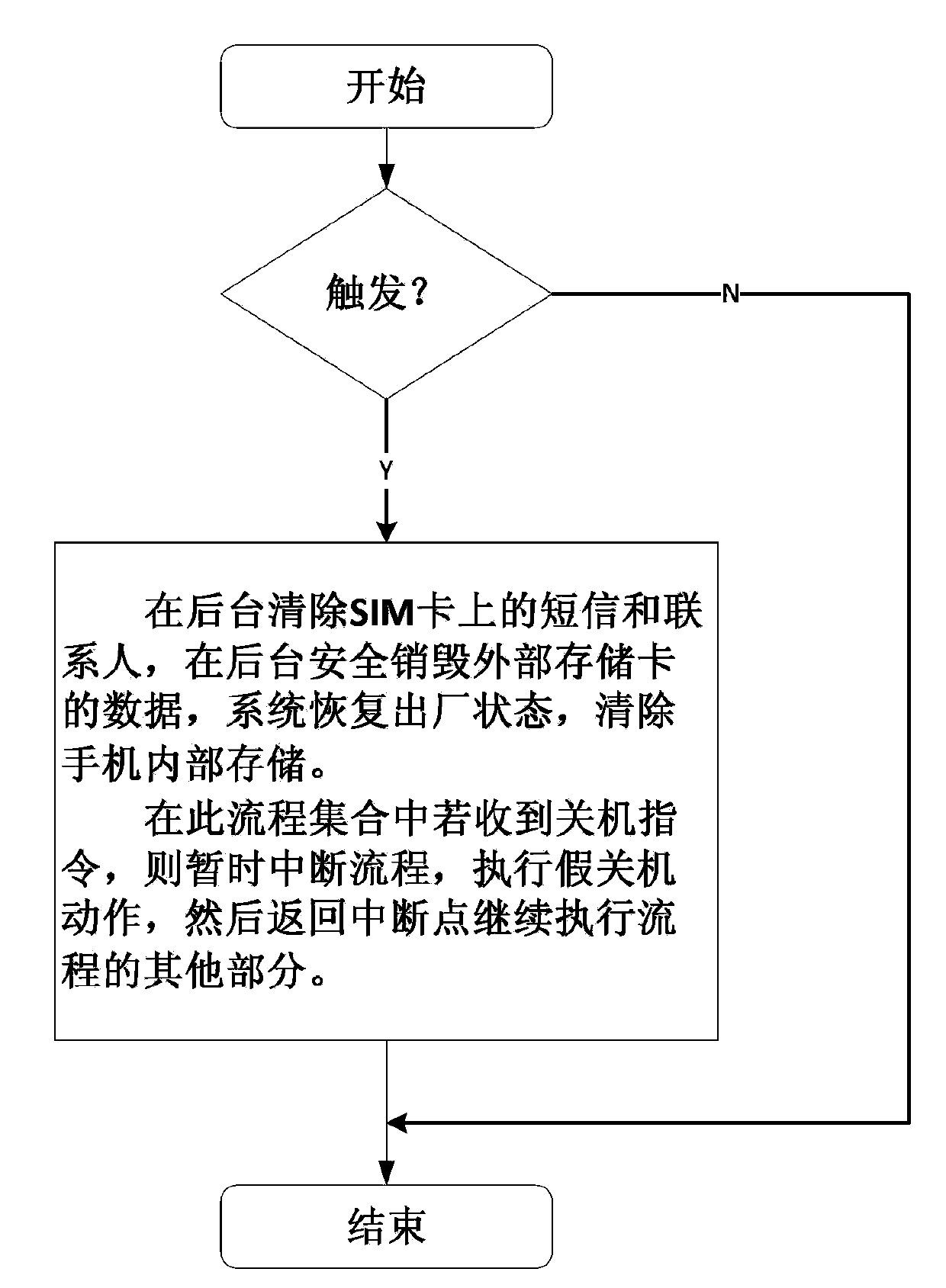
The invention discloses a data anti-theft method in case of mobile phone loss. The method comprises the following processes: first, an instruction for deleting the data on appointed equipment is triggered; then, a system enters a process set, wherein the process set comprises three processes of: eliminating messages and contacts on an SIM card from the backstage, safely destroying the data on an external storage card from the backstage, and allowing the system to be recovered to the state as delivered and erasing the internal storage in the phone; finally, when the three processes of the process set are performed, if an instruction showing that a phone picker turns off the phone is received, interrupting and saving the current status are performed, an operation of performing false shutdown is performed, and then the three processes are continuously performed from the interrupting point. Due to the adoption of the method, when the picker turns off the phone, an illusion that the phone is already turned off is created, so as to gain more time to perform the processing processes against loss, and accordingly, the mobile data on the phone can be completely and quickly erased in case the phone is lost.
Owner:BLUEDON INFORMATION SECURITY TECH CO LTD
Method and device for inserting or deleting cells or rows and lines in spreadsheet
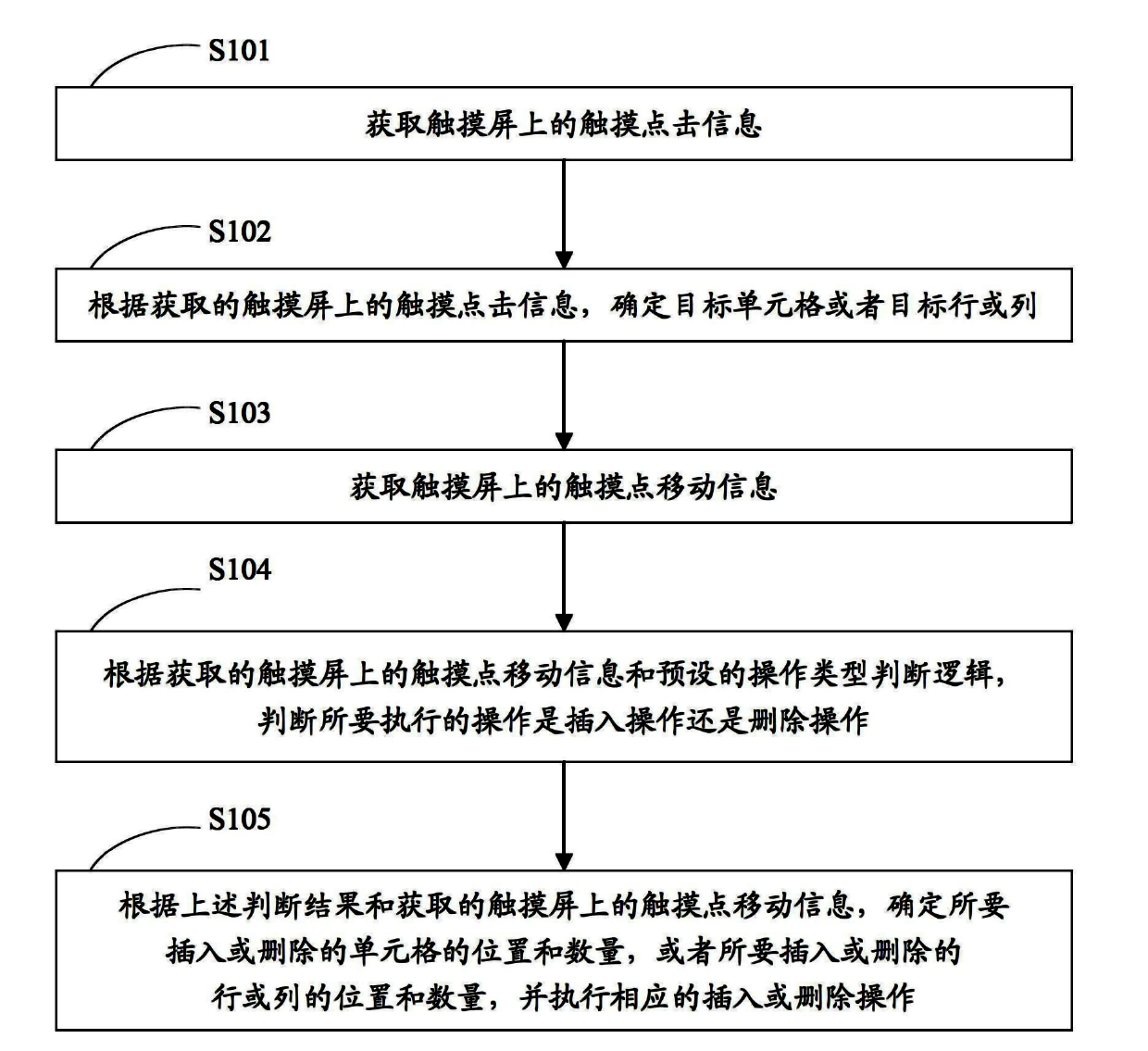
ActiveCN102637118AEasy to operateQuick insertText processingSpecial data processing applicationsElectronic formInterposition operation
Owner:ZHUHAI KINGSOFT OFFICE SOFTWARE +1
Android-based Handler memory leakage prevention device and method
InactiveCN106598725AEliminate memory leaksImprove efficiencyResource allocationInterprogram communicationTime sequenceComputer hardware
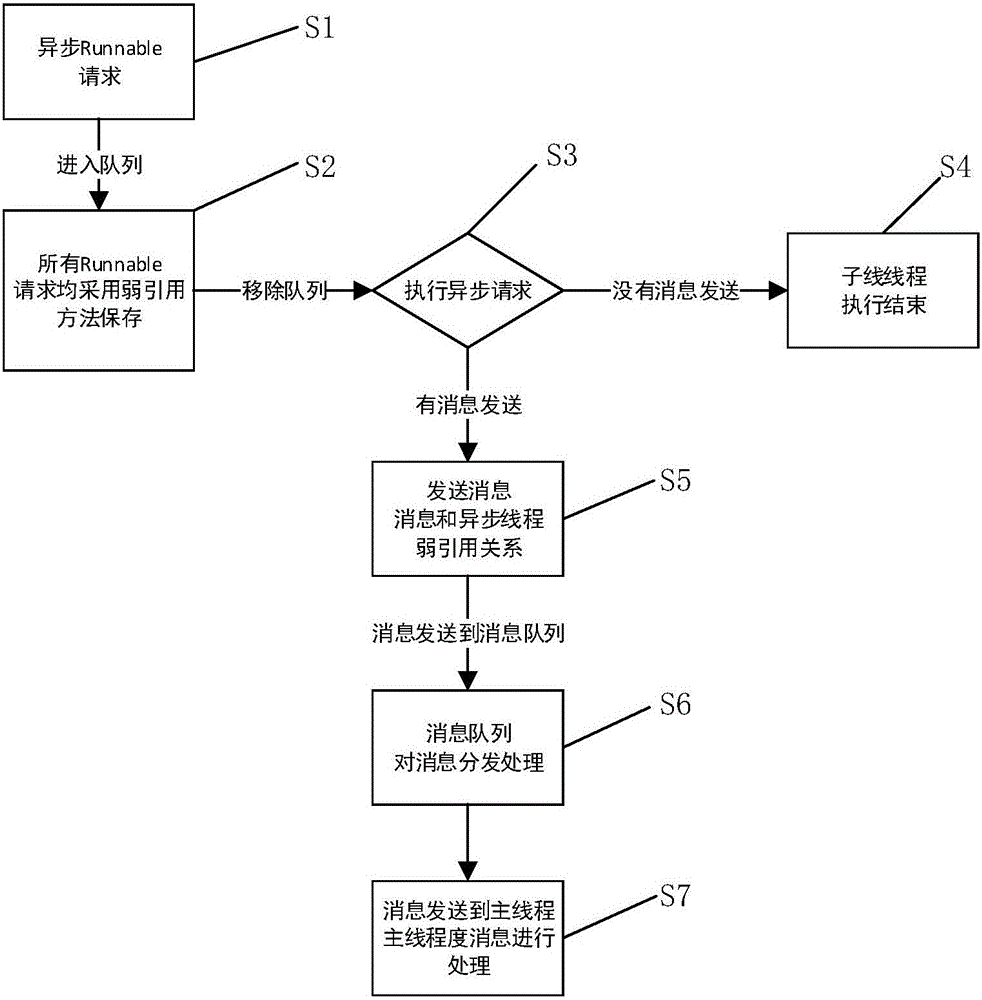
The invention provides an Android-based Handler memory leakage prevention device comprising: an asynchronous Runnable request receiving module used for receiving Runnable requests of asynchronous tasks; a synchronizing module used for synchronizing all received Runnable requests of the asynchronous tasks by adopting a weak quotation method; an asynchronous request execution module used for executing the Runnable requests of the asynchronous tasks and judging whether a message needs to be sent; a sub-line thread execution termination module used for terminating a sub-line thread if there is no message to be sent; a message sending module used for sending a message and a weak quotation relationship between the message and an asynchronous thread when the message needs to be sent; and a message distribution module used for storing the message and the weak quotation relationship between the message and the asynchronous thread and sending the same to a main thread for processing according to the time sequence of the message. According to the Android-based Handler memory leakage prevention device provided by the invention, the weak quotation relationship is introduced to ensure that resources can be smoothly recycled by a garbage collector, and no memory leakage is generated in the case of normal communication of the sub-thread and the main thread.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
A processing method for multi-node communication failure
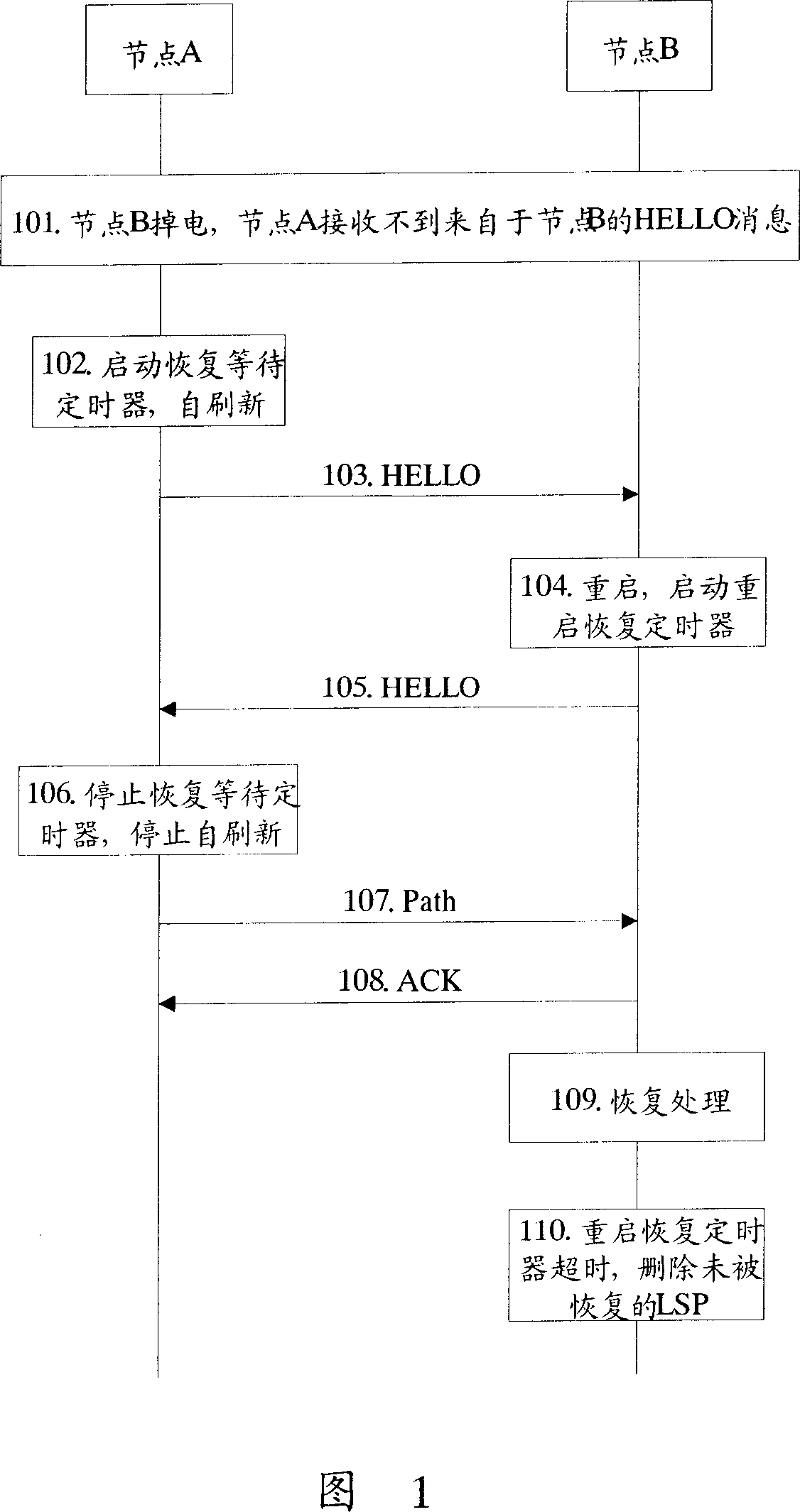
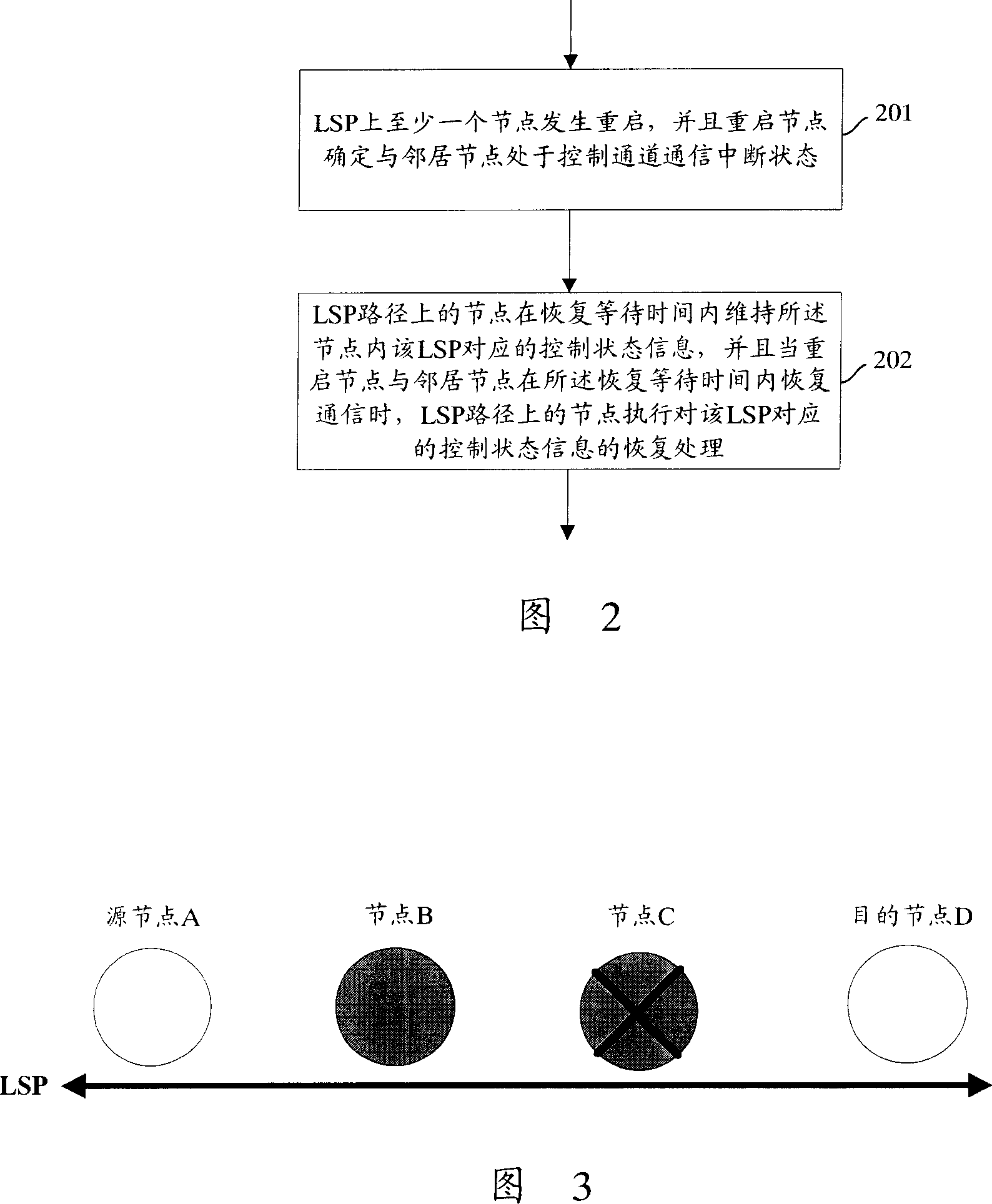
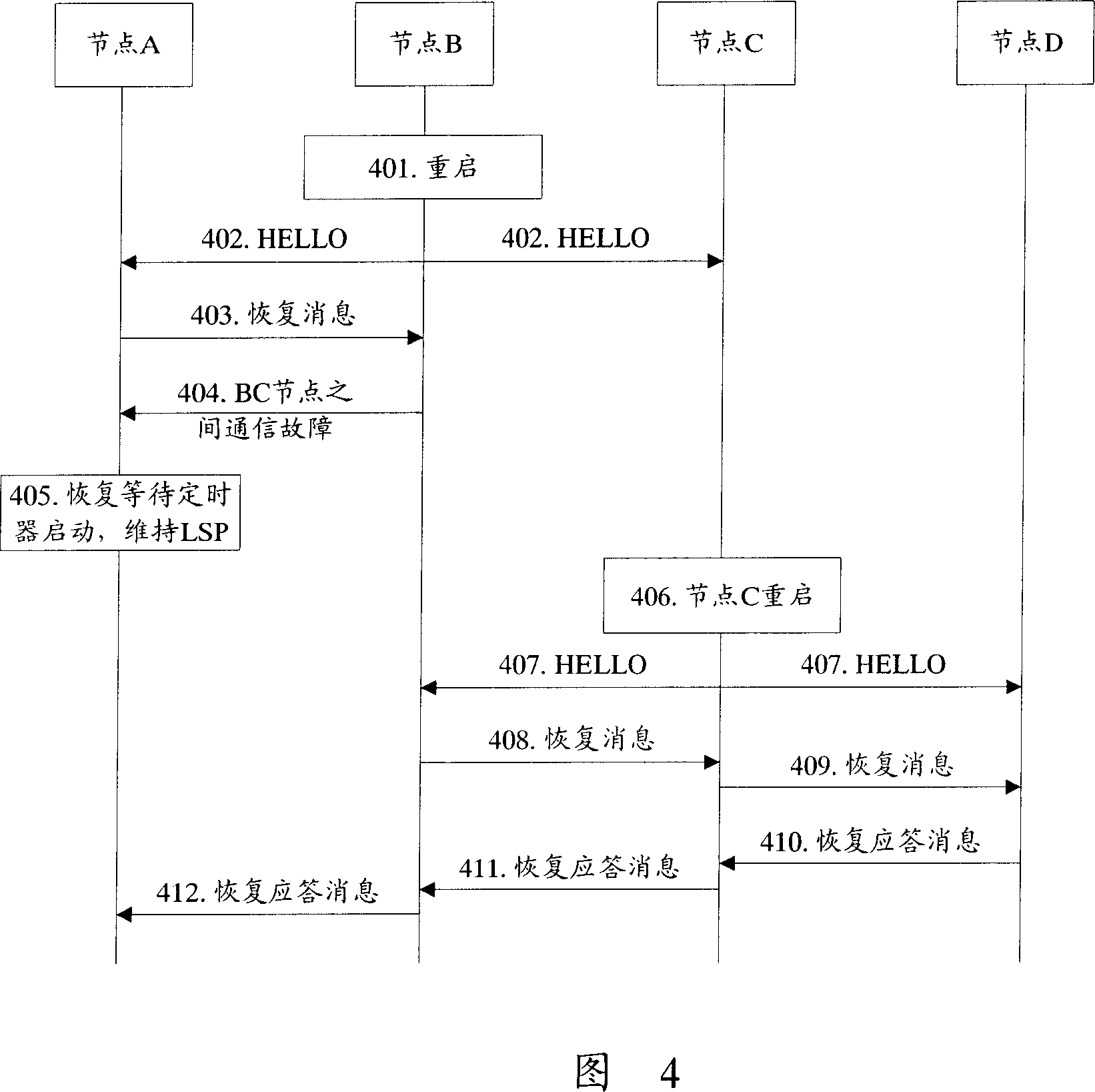
ActiveCN101087207APrevent abnormal deletionImprove reliabilityMultiplex system selection arrangementsStore-and-forward switching systemsLabel switchingControl channel
The invention discloses a processing method for multi-node communication failure, and the method includes: A. restarts at least one node on label switch path LSP, and the restarting node determines the control channel in interruptable state of adjacent nodes; B. the node on LSP in waiting time keeps the control state information corresponding with LSP, and when the restarting node and adjacent node recover the communication, the node on LSP path recovers the control state information corresponding with said LSP. Using the invention, it can recover the LSP when several nodes on LSP have communication failure.
Owner:HUAWEI TECH CO LTD
Route table space managing method, apparatus, switch and router
InactiveCN101335706AImprove space utilizationQuick insertData switching networksLongest prefix matchSpace management
The invention relates to a method, a device, a switch and a router for space management of a routing table. Distribution management to the space of the routing table is carried out by the space management unit in a space management link table so as to lead the entries of layer 3 switches or routers inserted in the routing table to be arranged by the mask (prefix) length in a long-to-short order, ensure that the routing entry with the longest prefix can be matched with the one with the longest mask from the start of the matching, avoid repetitive depositing of the same entry in the routing table and the problem that the routing entry with the largest mask length can not be obtained until all entries in the routing table are matched and greatly increase the search speed of the routing table; besides, arrangement of entries in the routing table by a certain order facilitates fast insertion and deletion of the entries, the space utilization rate of the routing table is significantly improved.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
Quickly detached cooling fan mounting bracket for computer
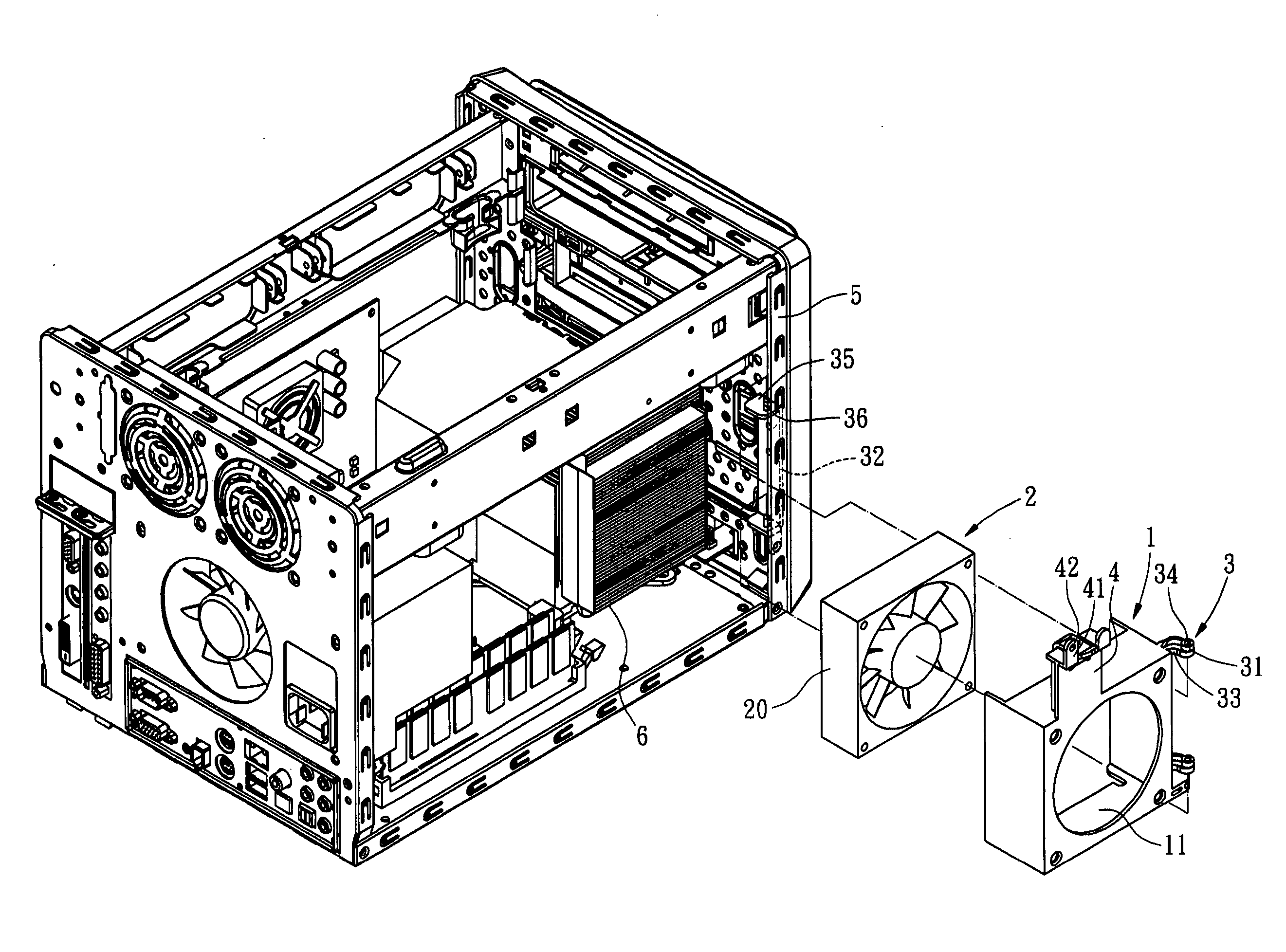
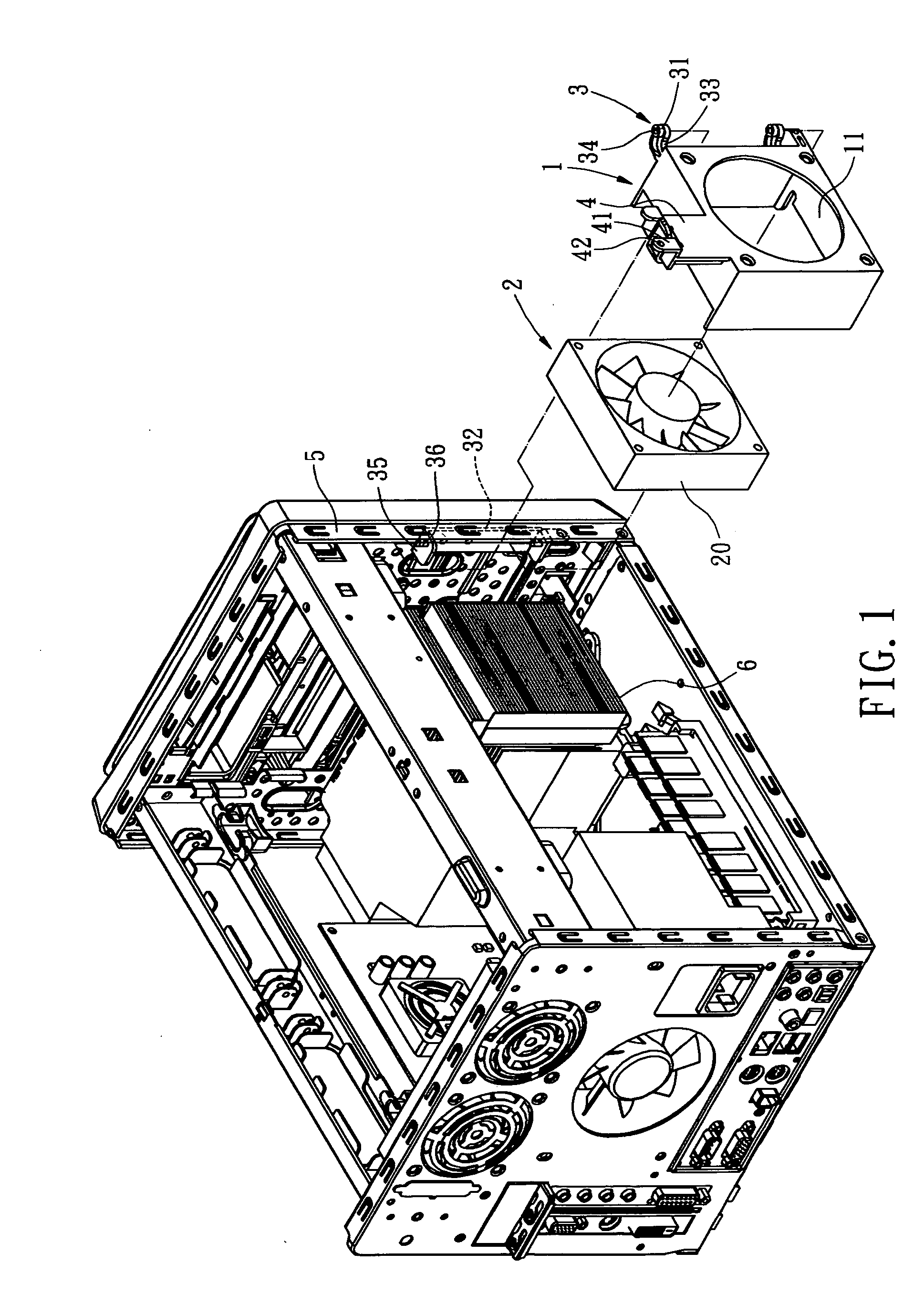
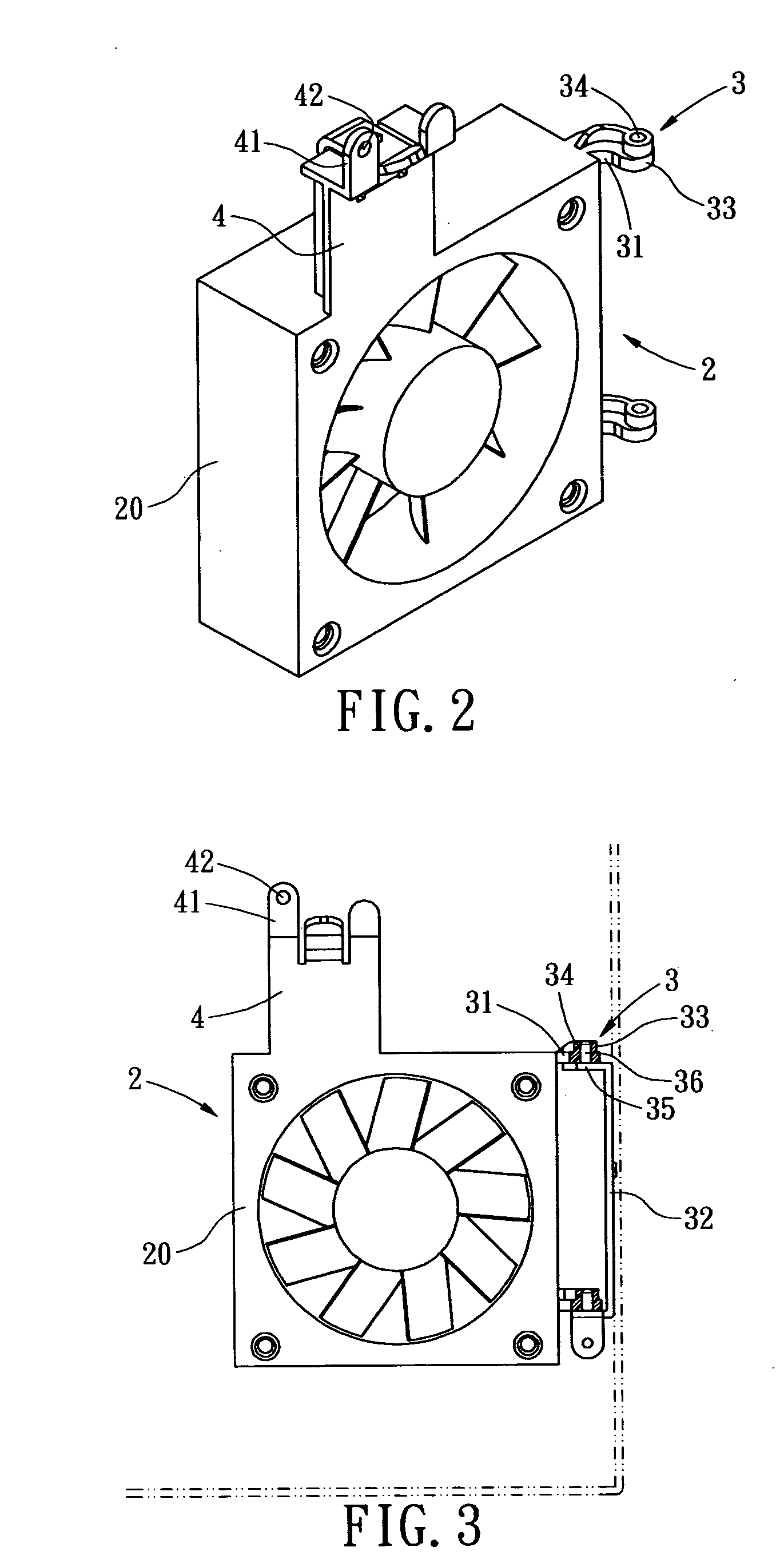
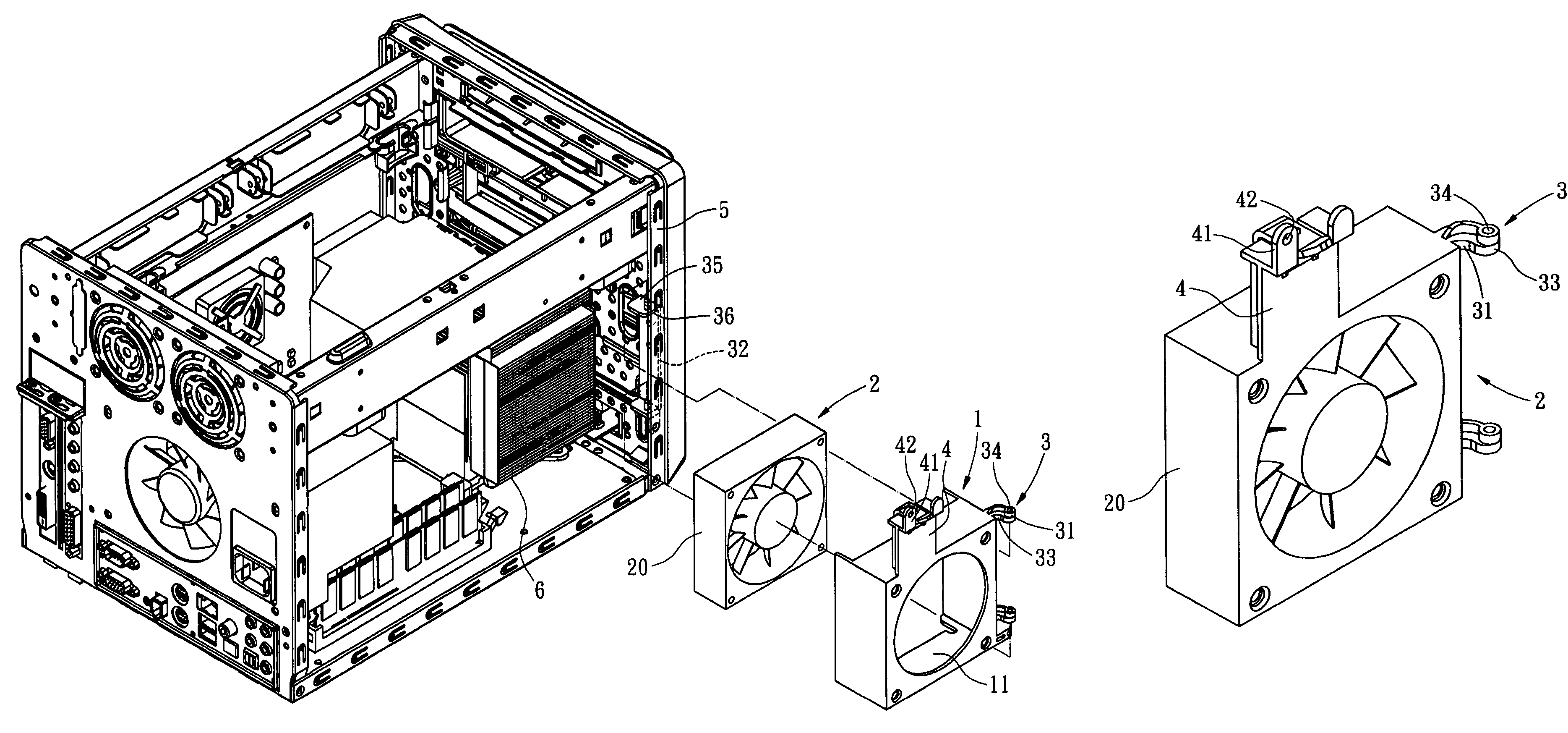
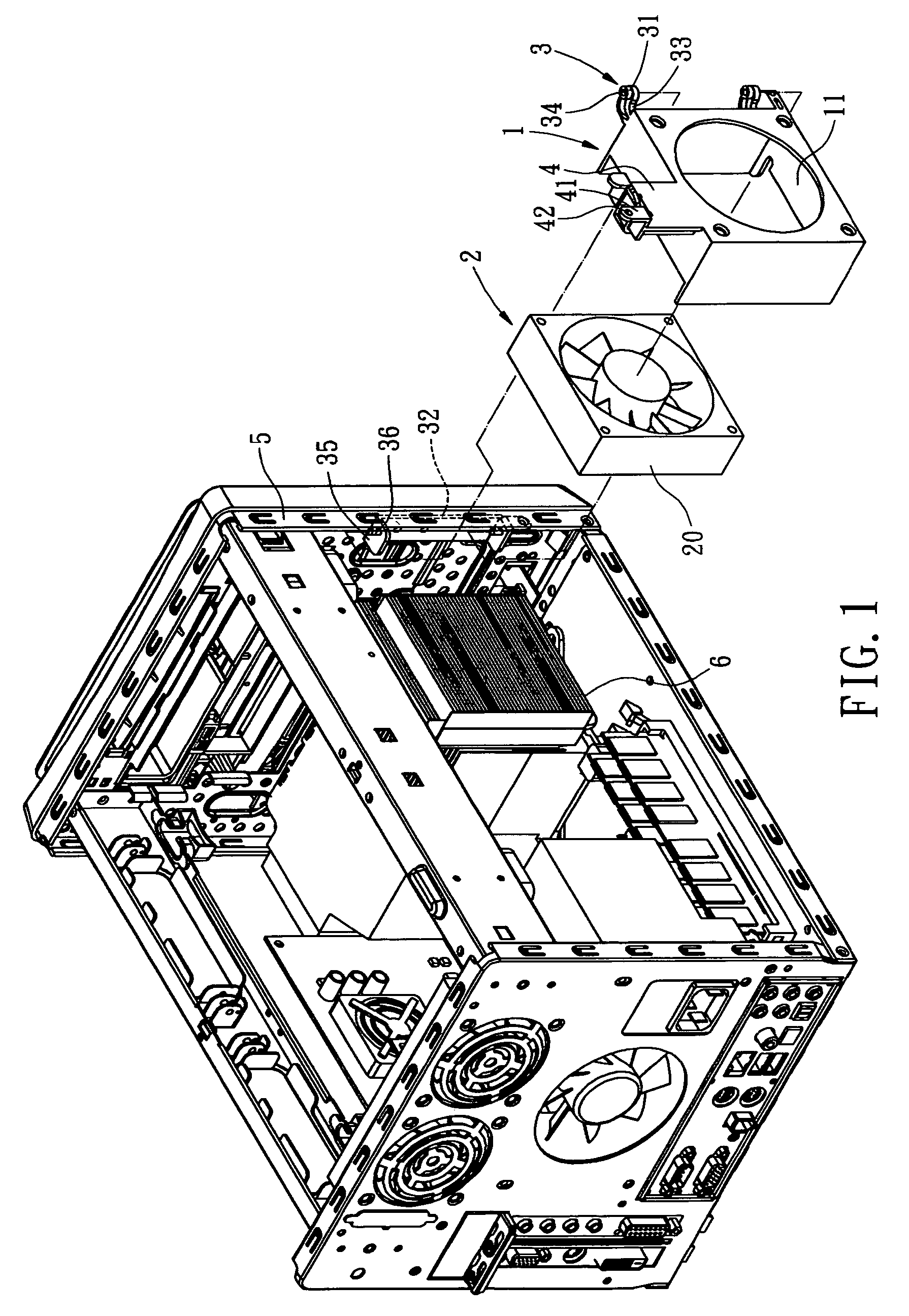
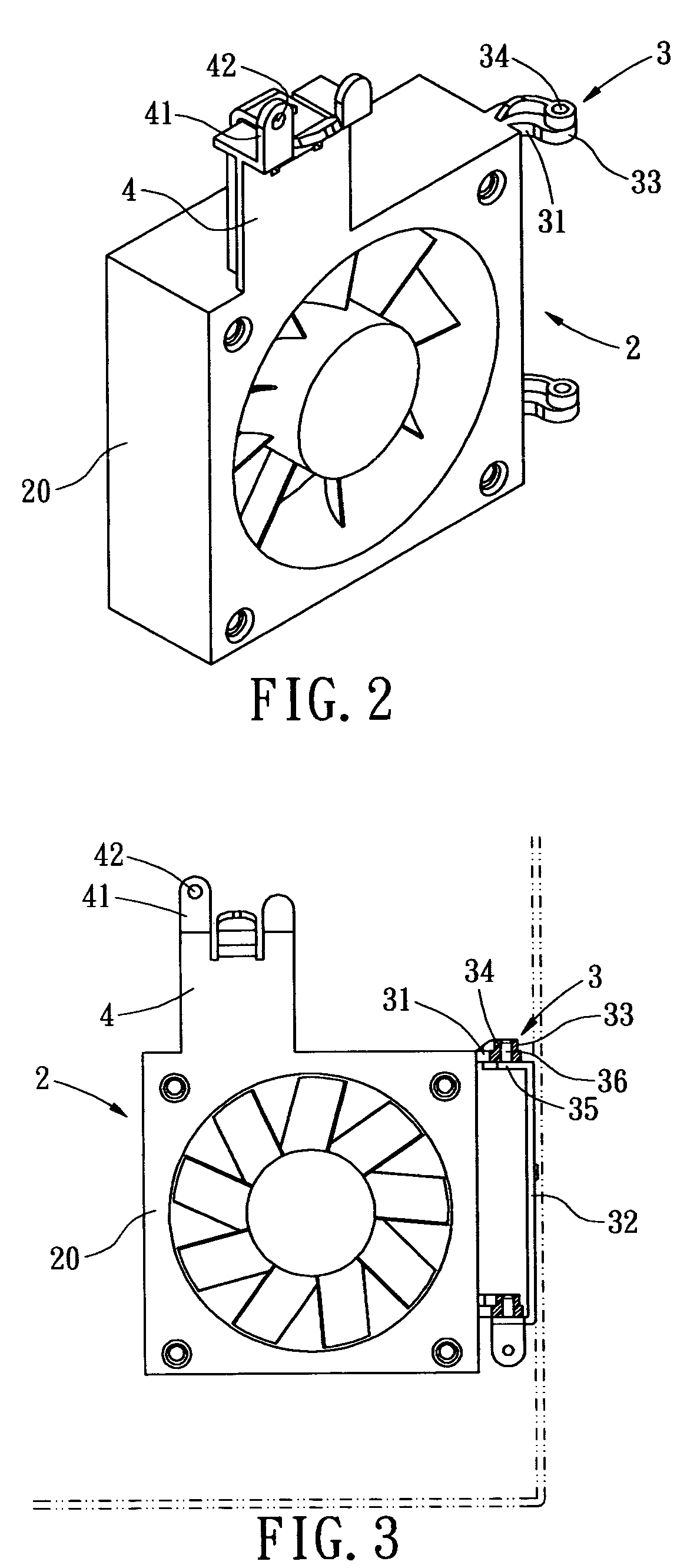
InactiveUS20060003683A1Quick deleteQuick changeCooling/ventilation/heating modificationsElectrical apparatus casings/cabinets/drawersInterior spaceComputer engineering
A quickly detached cooling fan mounting bracket for a computer, by which a cooling fan can be quickly removed away from a computer chassis without detaching any other peripheral devices, whereby a large enough computer inner space is exposed in order to facilitate rapid replacement of electrical components. The cooling fan mounting bracket includes a cooling fan receptive mount; a cooling fan; a connecting member, which allows the cooling fan receptive mount to be movably installed on the computer chassis; and a orienting member, which secures the cooling fan receptive mount and the cooling fan onto the computer chassis, and prevents the cooling fan from vibration during the normal operation. Compared with the conventional art, the present invention is easier to remove the cooling fan away from the chassis, thereby, facilitates rapid replacement or maintenance of the computer components.
Owner:SHUTTLE
Doppelganger management method and system for application program
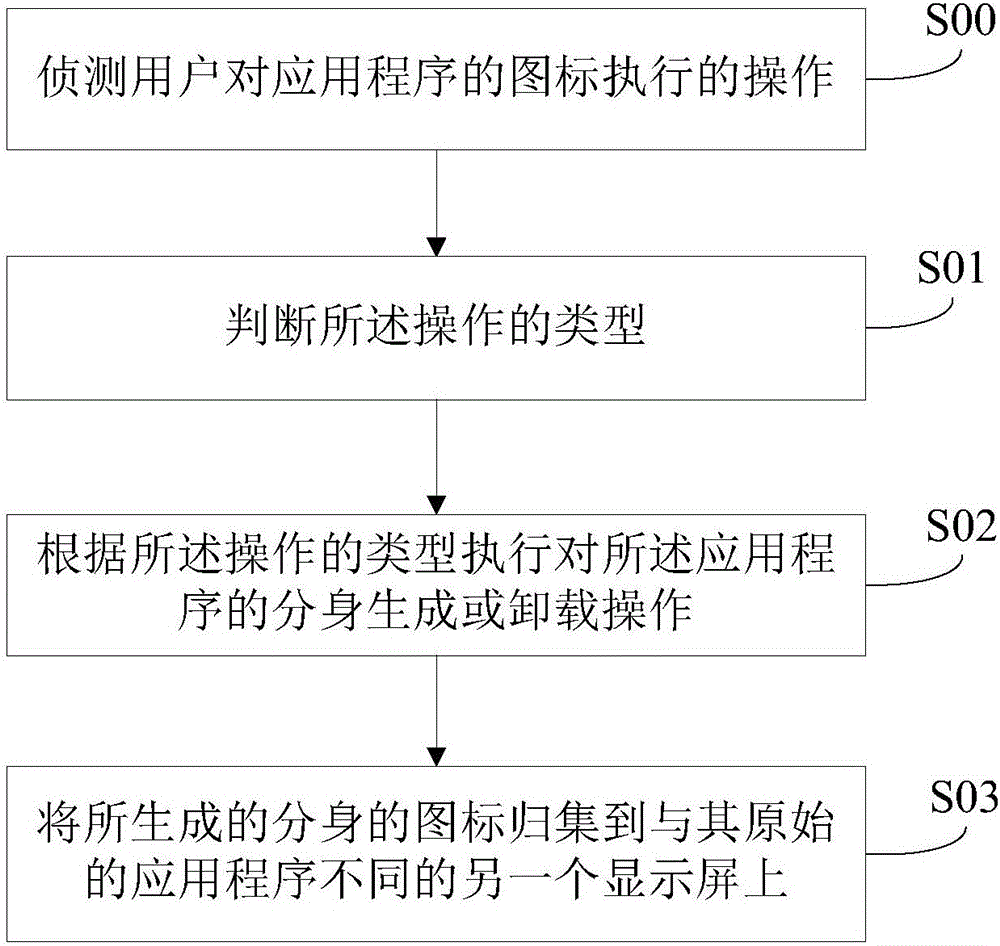
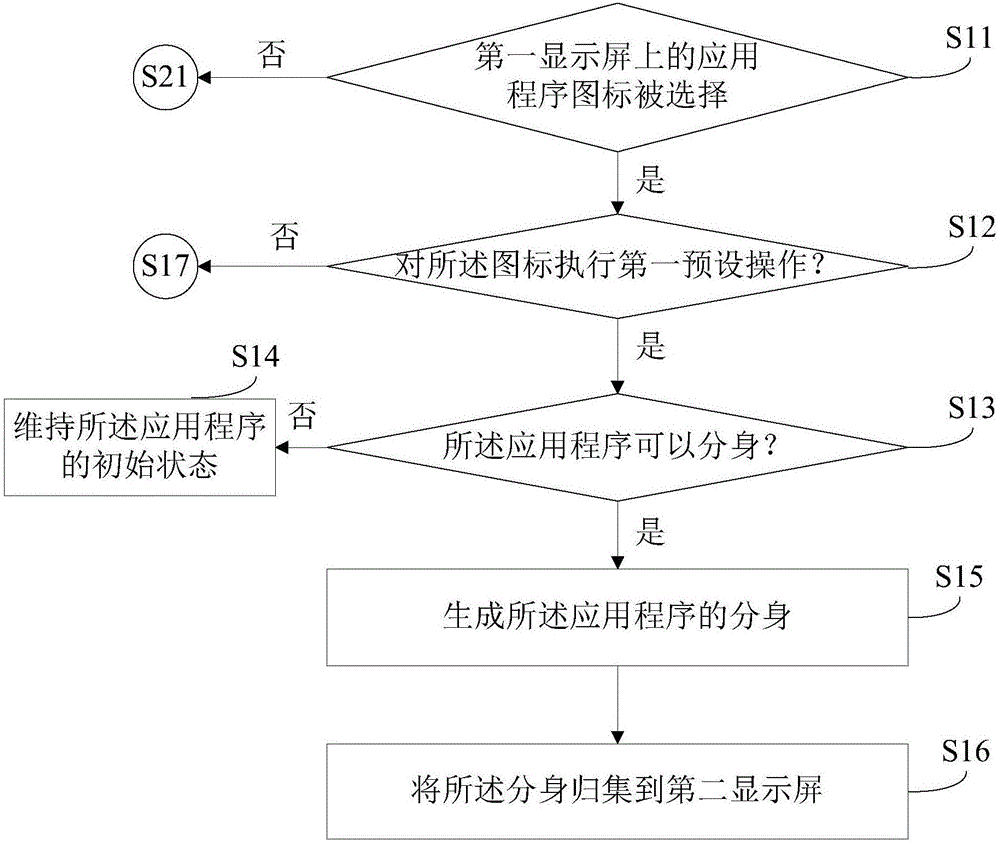
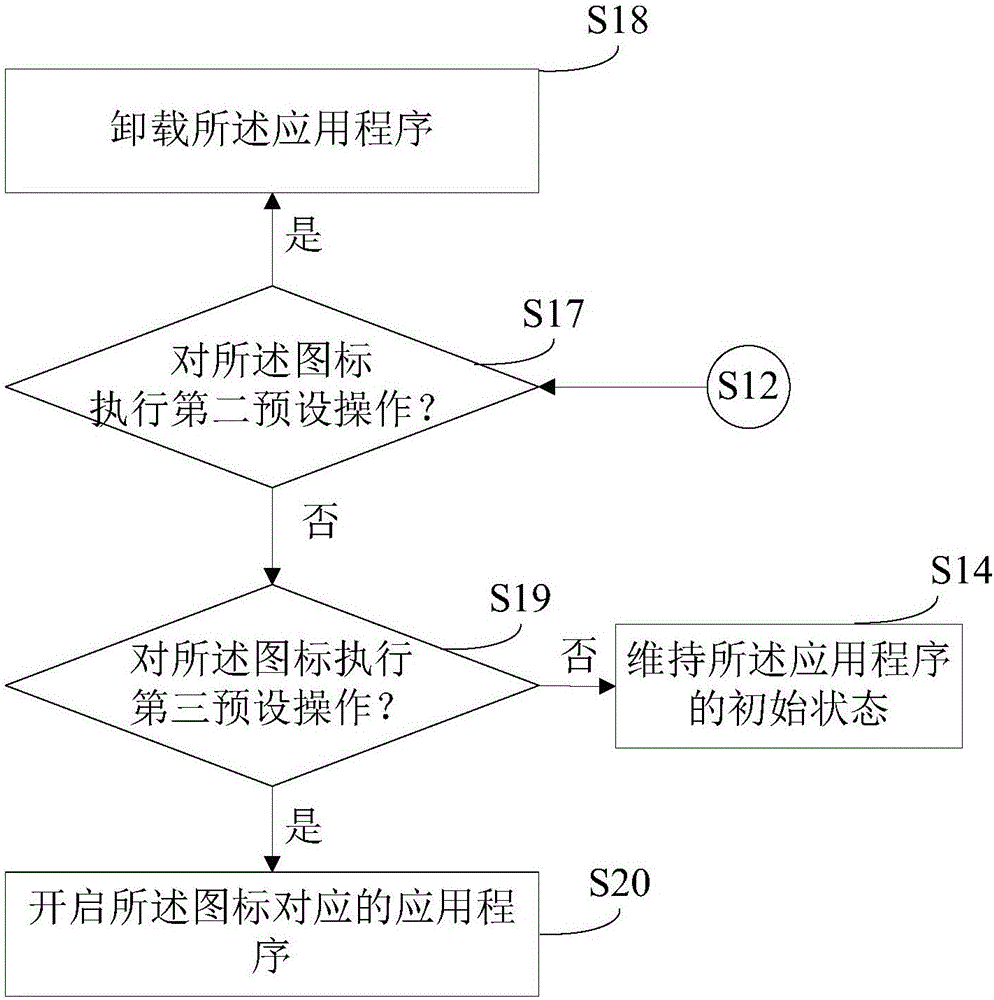
ActiveCN106445292AEfficient managementQuick buildInput/output processes for data processingTransaction processingComputer scienceManagement system
A doppelganger management method for an application program comprising following steps: detecting an operation from a user on an application program icon on an intelligent terminal display screen; determining the type of the operation; according to the type of the operation executed on the display screen, executing doppelganger generating or unloading operations on the application program; collecting the icon of the generated doppelganger of the application program to another display screen which is different from the corresponding original application program. The invention also provides a doppelganger management system for an application program. By means of the method and the system of the invention, doppelgangers of application programs can be rapidly generated and deleted; application programs and doppelgangers thereof can be effectively managed.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
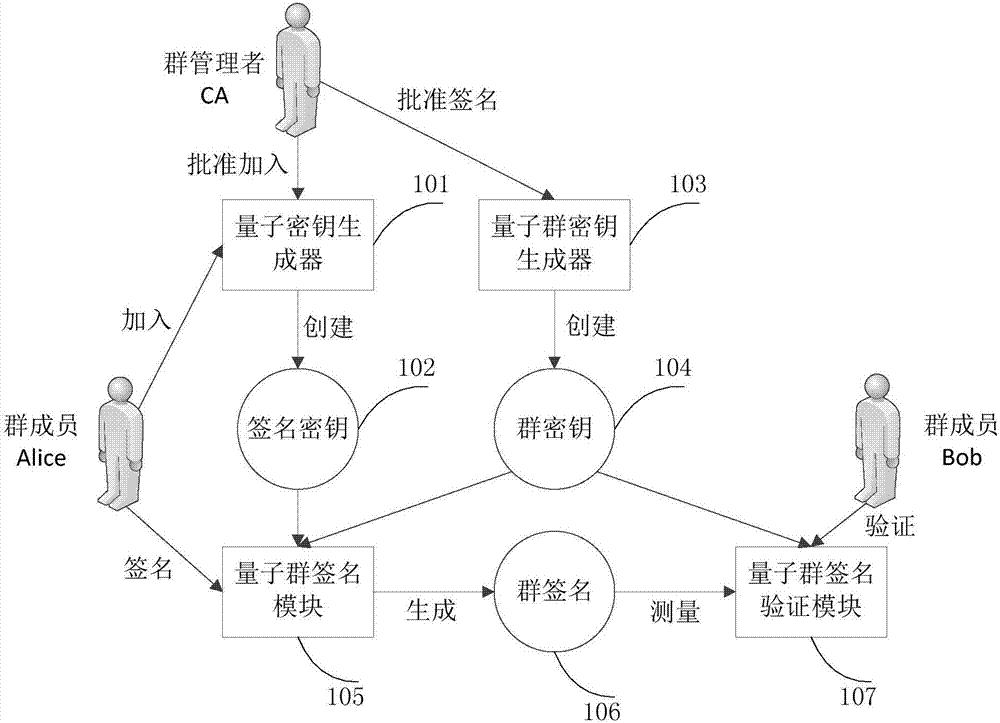
Group signature system based on quantum keys
ActiveCN107395367AGuaranteed absolute securityImprove securityKey distribution for secure communicationUser identity/authority verificationKey generatorLaser source
The invention discloses a group signature system based on quantum keys. The group signature system comprises a quantum key generator, a signature key, a quantum group key generator, a group key, a quantum group signature module, a group signature and a quantum group signature verification, wherein the quantum key generator is a quantum sequence device generated by a laser source, and is used for forming a shared key of a newly-added group member and a group administrator; the quantum group key is issued to group members by the group administrator and used for encryption in signing according to a quantum state sequence generated by means of the quantum group key generator, and different sequences are generated according to different business transactions; and the quantum group signature module is used for performing quantum encryption on messages and signatures by the group members. The group signature system based on the quantum keys has the significant advantages that: identities are determined through distribution and measurement of the quantum keys, the efficiency is higher while the security is improved, and group members can be added and deleted quickly; and the group signature system is more suitable for a complex group signature environment, has the features of unlinkability and coalition attack resistance, and can realize coalition signature of a plurality of the group members.
Owner:CHINA THREE GORGES UNIV
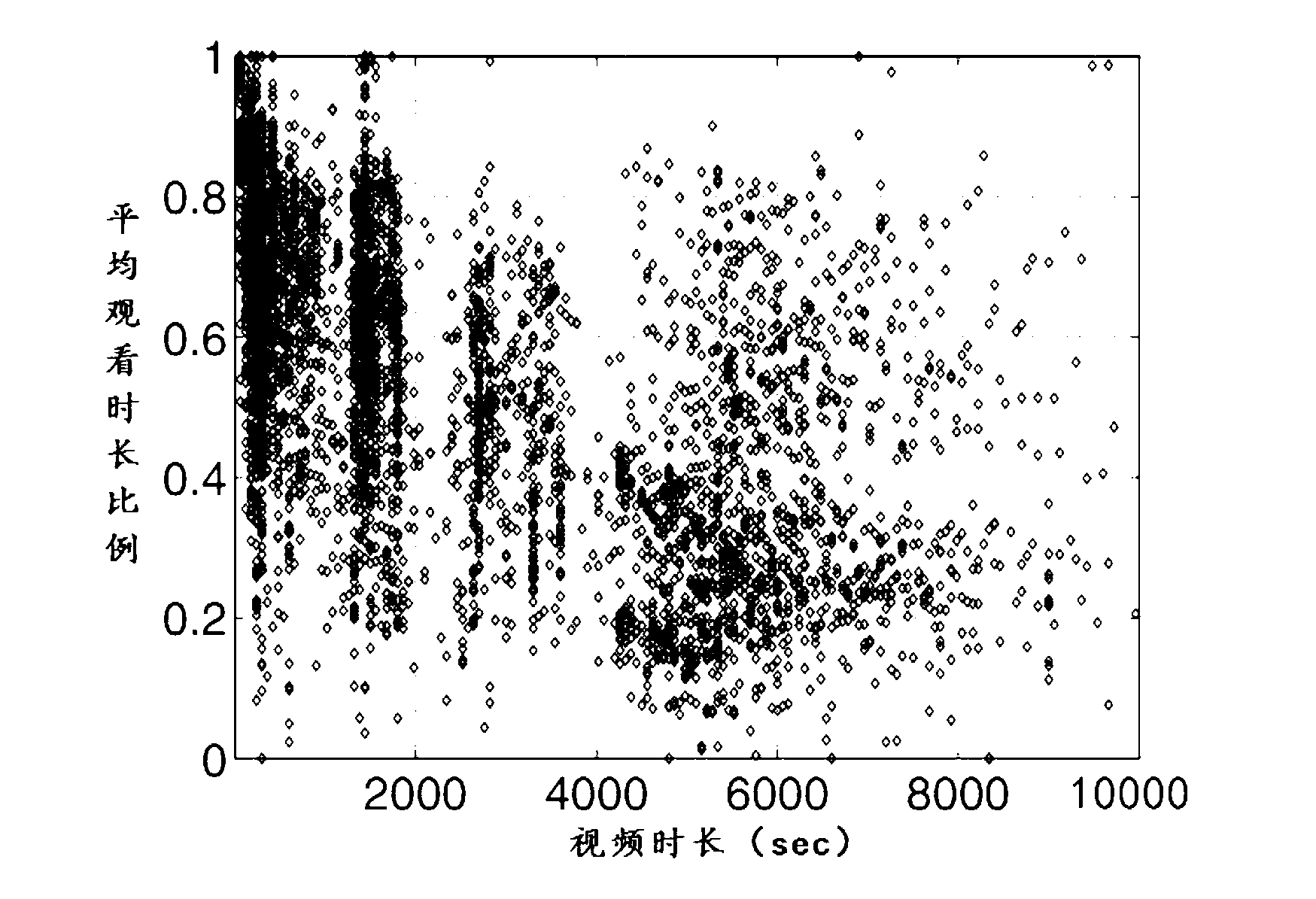
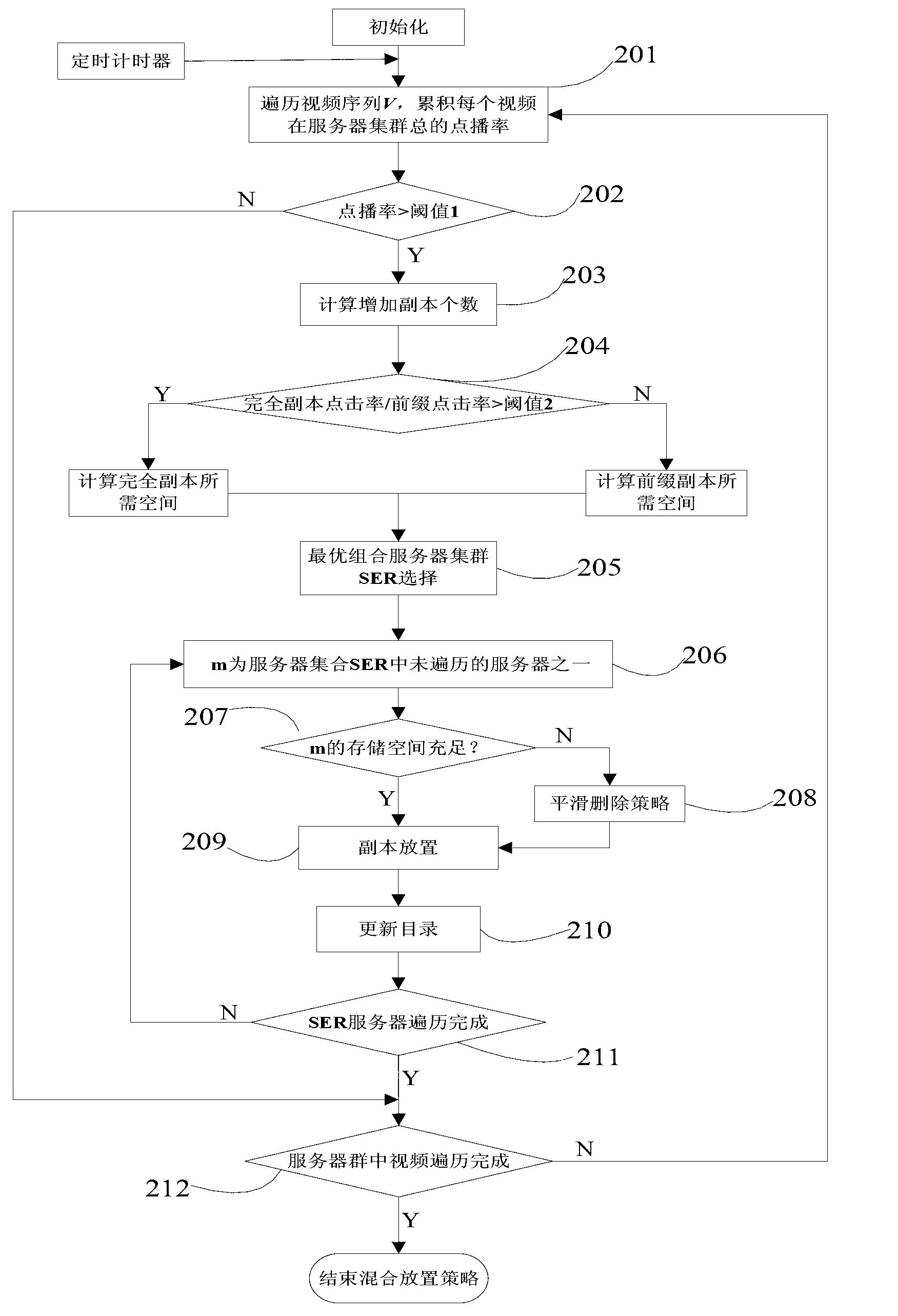
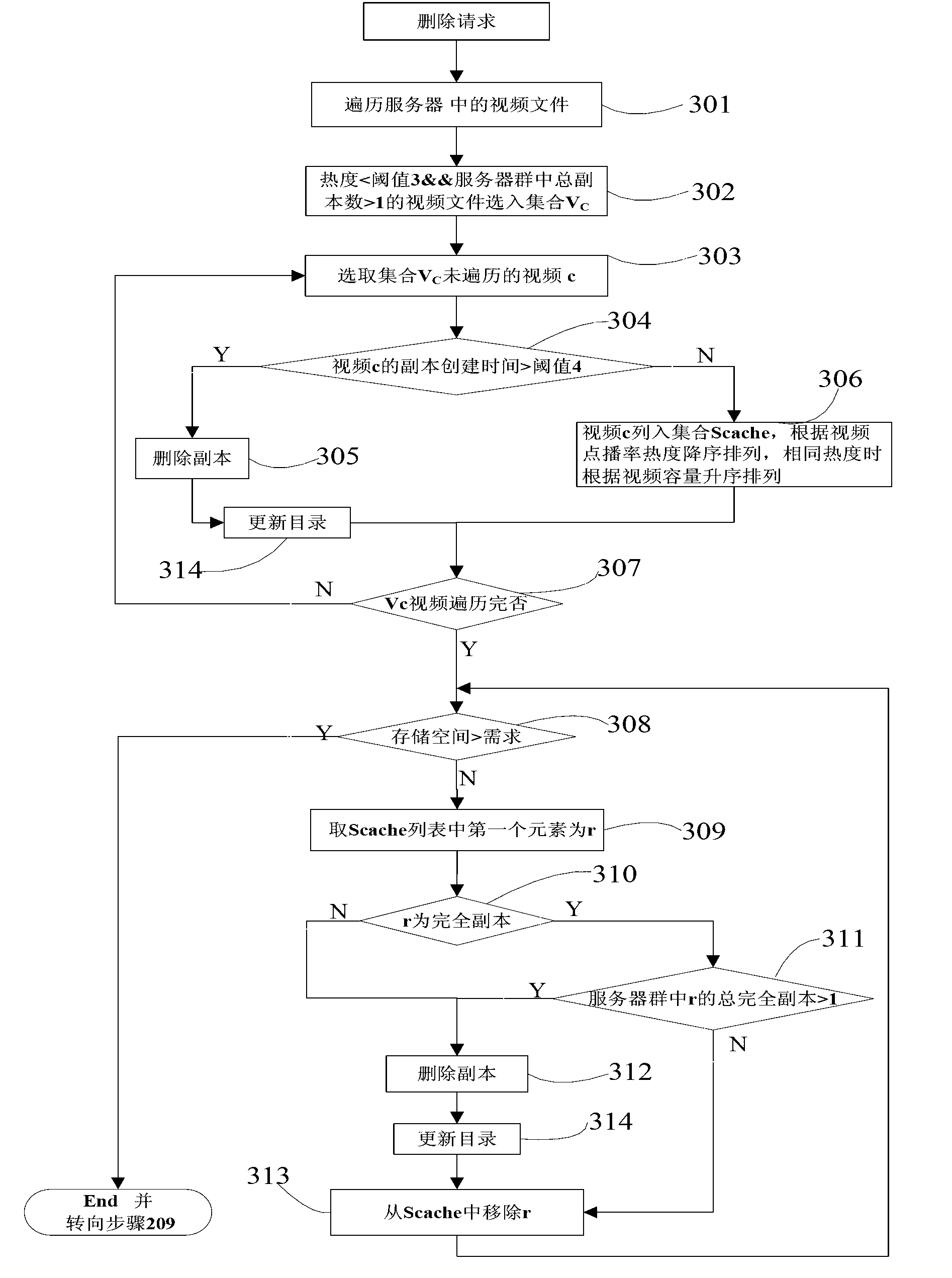
Streaming media video-on-demand duplicate hybrid buffer strategy based on cloud server cluster
InactiveCN103297431APrevent copyingAvoid deletionTransmissionSpecial data processing applicationsVideo on demandDemand rate
The invention discloses a method for effectively buffering streaming media video-on-demand duplicate hybrid buffer strategy based on a cloud server cluster. The method includes performing prefix dynamic blocking on the video duplicates based on video duration, and utilizing a dynamic prefix and complete duplicate hybrid storage strategy to improve system efficiency and experience quality of users; confirming number of needed duplicates according to factors such as video hot degree and confirming two types of the duplicates (complete duplicates and prefix duplicates) on the basis of demanding rate, and dynamically segmenting prefixes of the prefix duplicates on the basis of video duration so as to generate the prefix duplicates; and when storage space is enough, utilizing a hot balance and load balance combining method to store the duplicates, and when storage space is not enough, smoothly deleting hot-degree-decreasing video duplicates based on time window threshold values. By the method, users can obtain good video-on-demand experience.
Owner:NANJING UNIV OF POSTS & TELECOMM
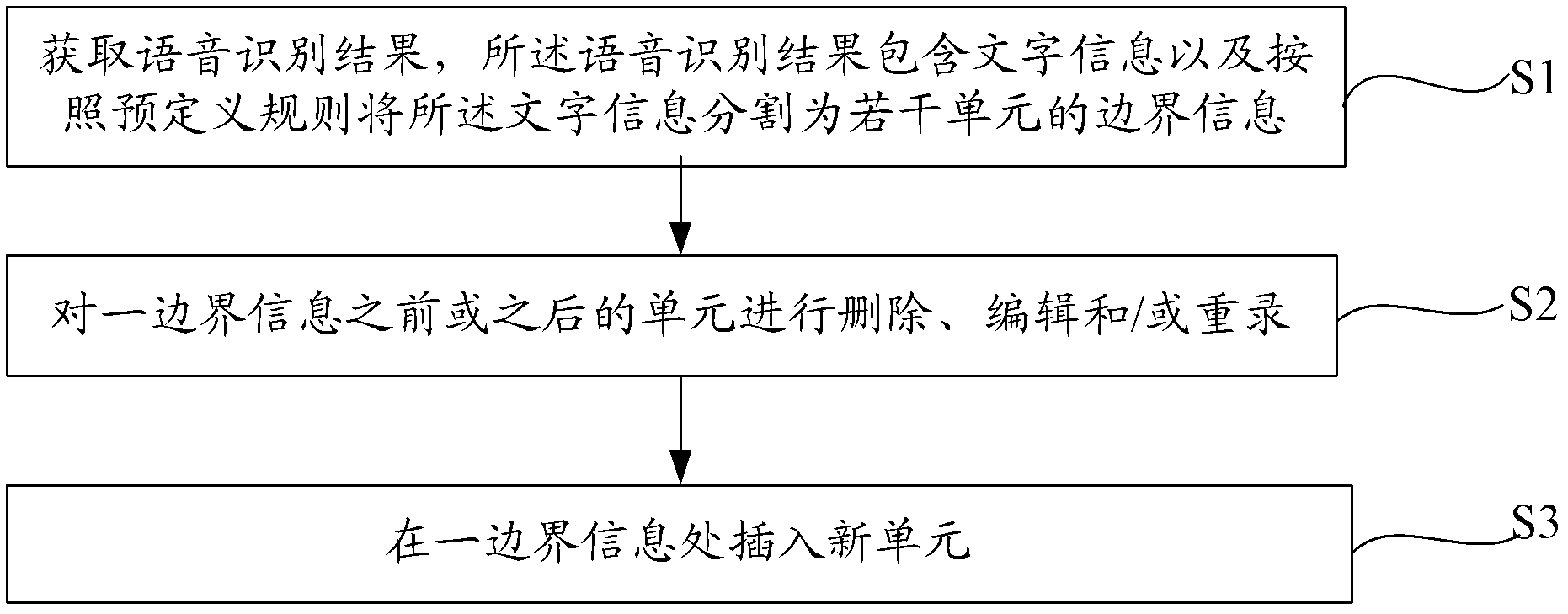
Method and system for correcting based on voice identification results
InactiveCN103150294AQuick editQuick modificationSpecial data processing applicationsHuman–computer interactionSpeech sound
The invention provides a method and a system for correcting based on voice identification results. The method comprises the following steps of on the premise that the accuracy of converting voice into a text cannot reach 100%, blocking the text of text information by combining boundary information with a predefined rule, using the boundary information as the basis, the quickly editing, modifying and deleting the text block before or after the boundary information in the voice identification results, and quickly inserting new text information in the boundary information. Compared with the traditional keyboard modifying method, the method for correcting the text based on the text-blocking voice identification results has the advantage that the number of operation times is reduced, and the interaction experience of a user and an intelligent terminal is greatly improved.
Owner:SHANGHAI GUOKE ELECTRONICS
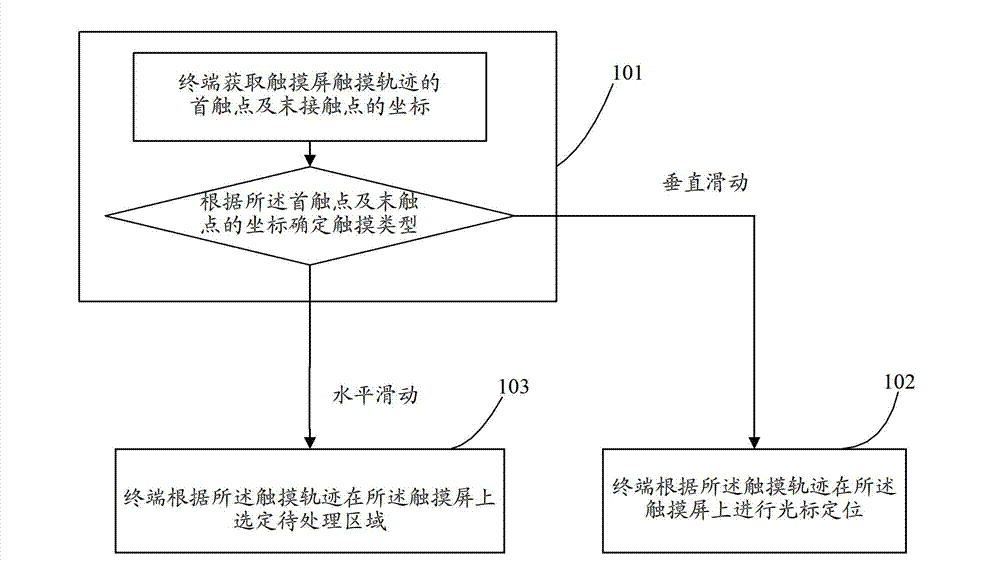
Character handling method and terminal based on touch screen
ActiveCN103116461AReplace shortcutAccurately determineInput/output processes for data processingComputer graphics (images)Computer vision
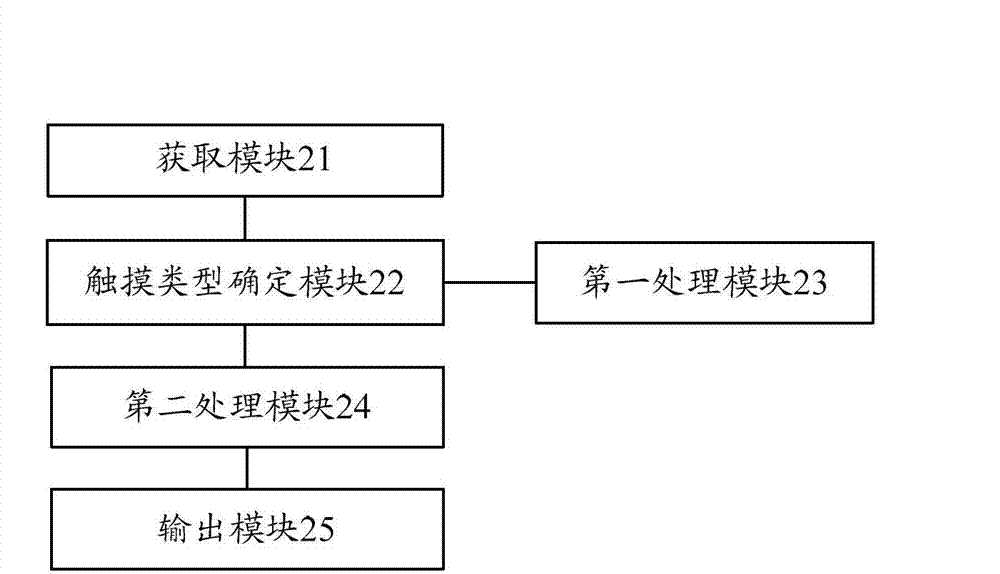
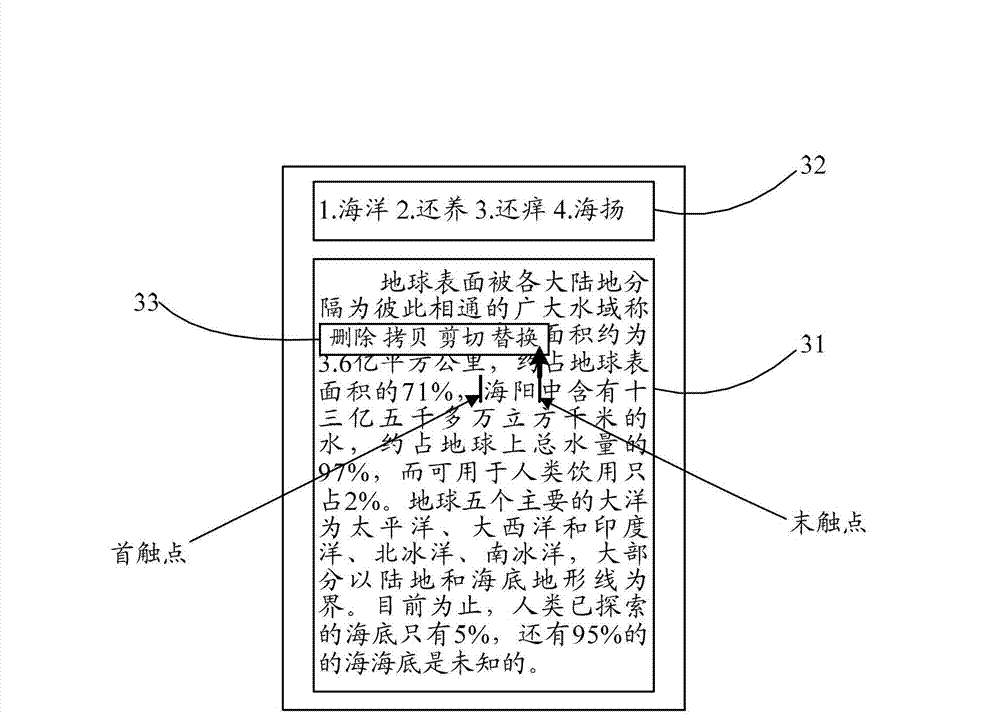
The invention discloses a character handling method based on a touch screen. The character handling method based on the touch screen comprises that coordinates of a head contacting point and a tail contacting point of a touching track of a touch screen can be obtained. When the touching types of the coordinates of the head contacting point and the tail contacting point are ensured to be slipped vertically, the touching track can be used as a base to implement a cursor location on the touch screen. When touching types are ensured to be slipped horizontally, the touching track can be used as a base to select a to-be-processed area on the touch screen. The invention further discloses a character handling terminal based on the touch screen. The character handling method and the terminal based on the touch screen can be used for locating a cursor precisely, deleting the characters swiftly and replacing the characters swiftly in a character handling process.
Owner:ZTE CORP
Method and device of sharing picture
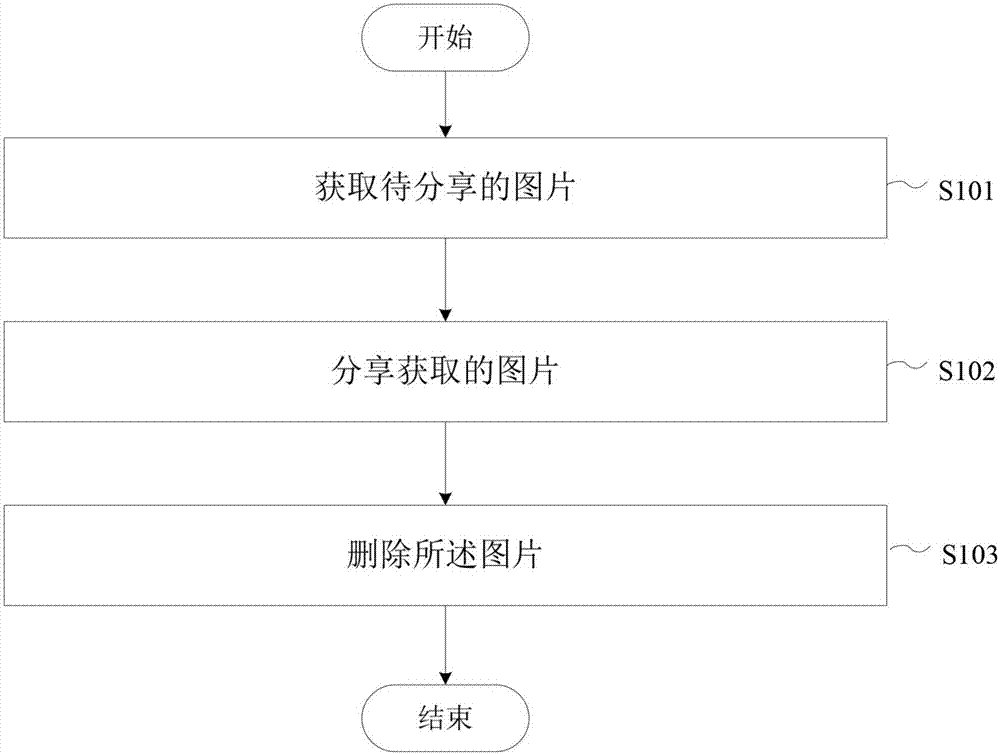
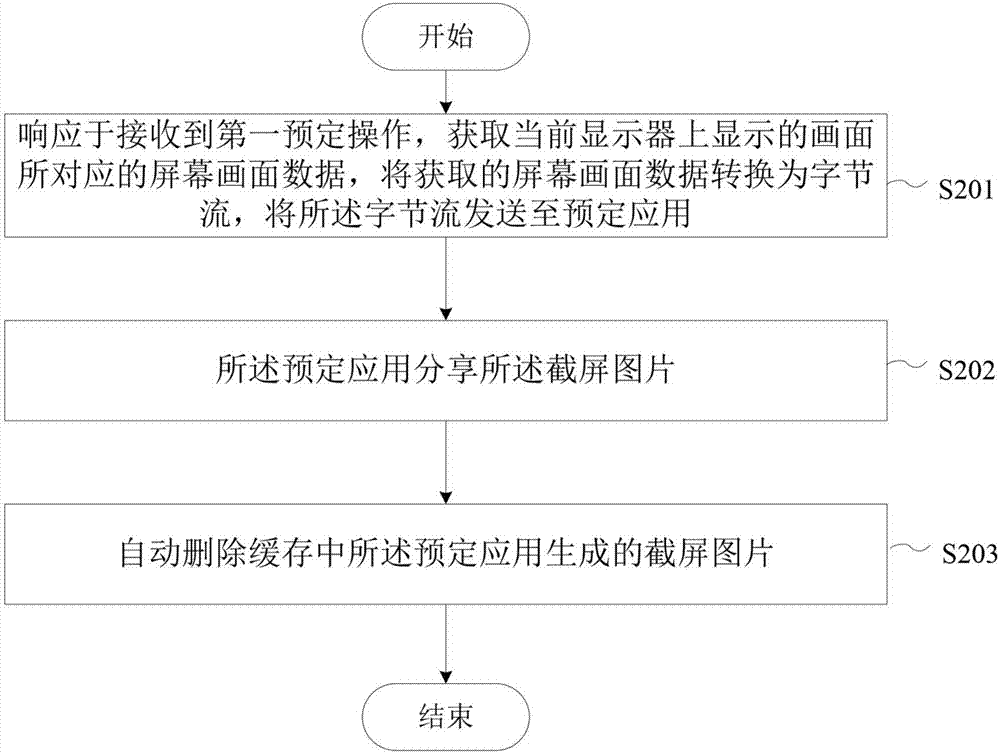
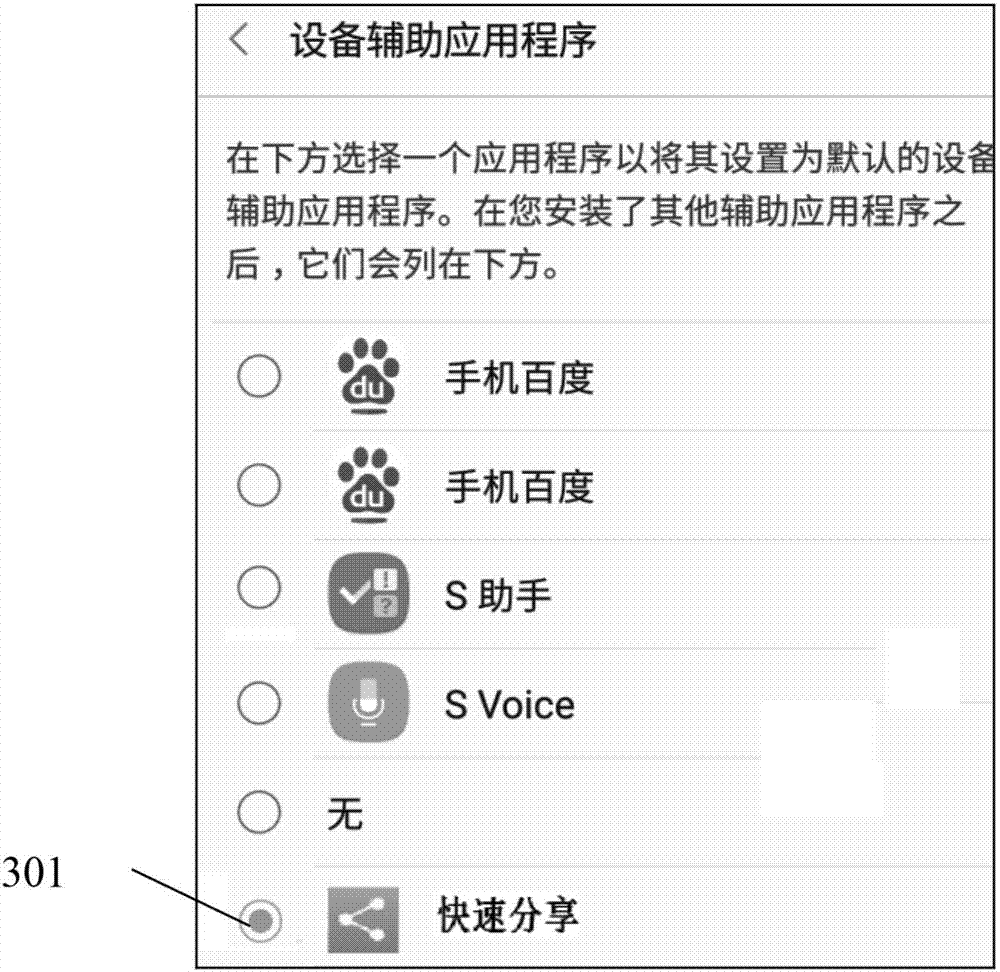
InactiveCN107291839AQuick deleteSimple and fast operationStill image data indexingSpecial data processing applicationsComputer science
Owner:SAMSUNG GUANGZHOU MOBILE R&D CENT +1
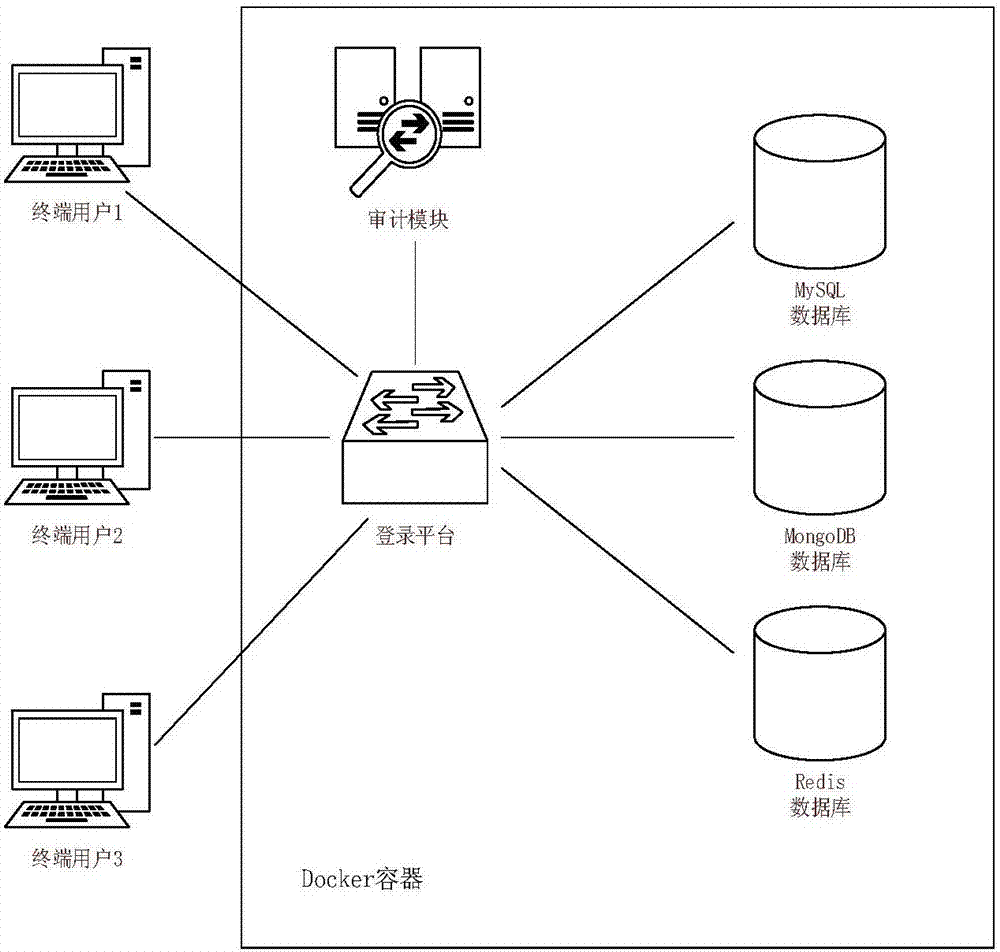
Cloud database security audit method based on Docker virtualization
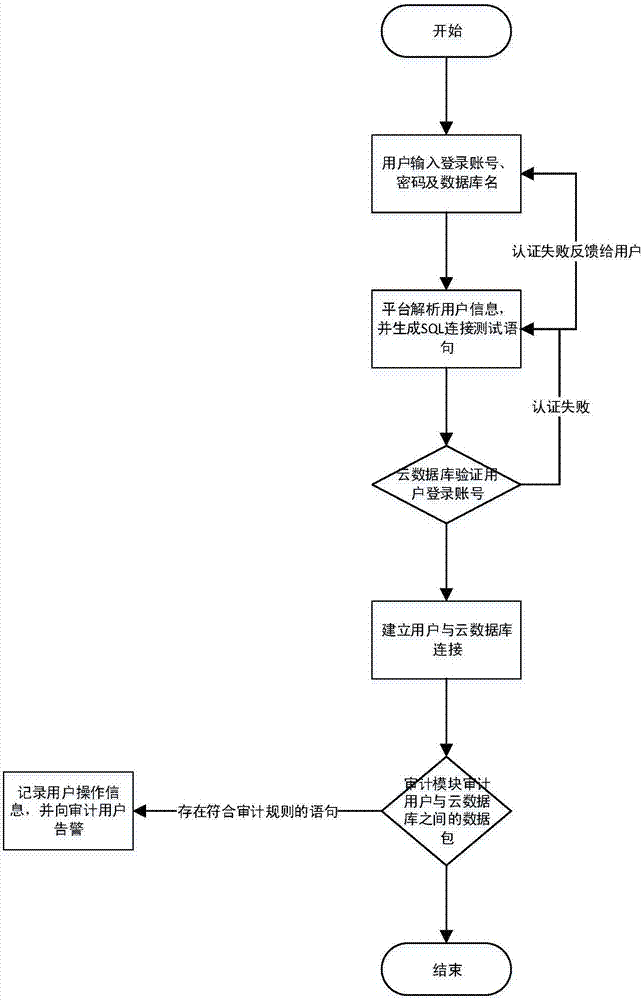
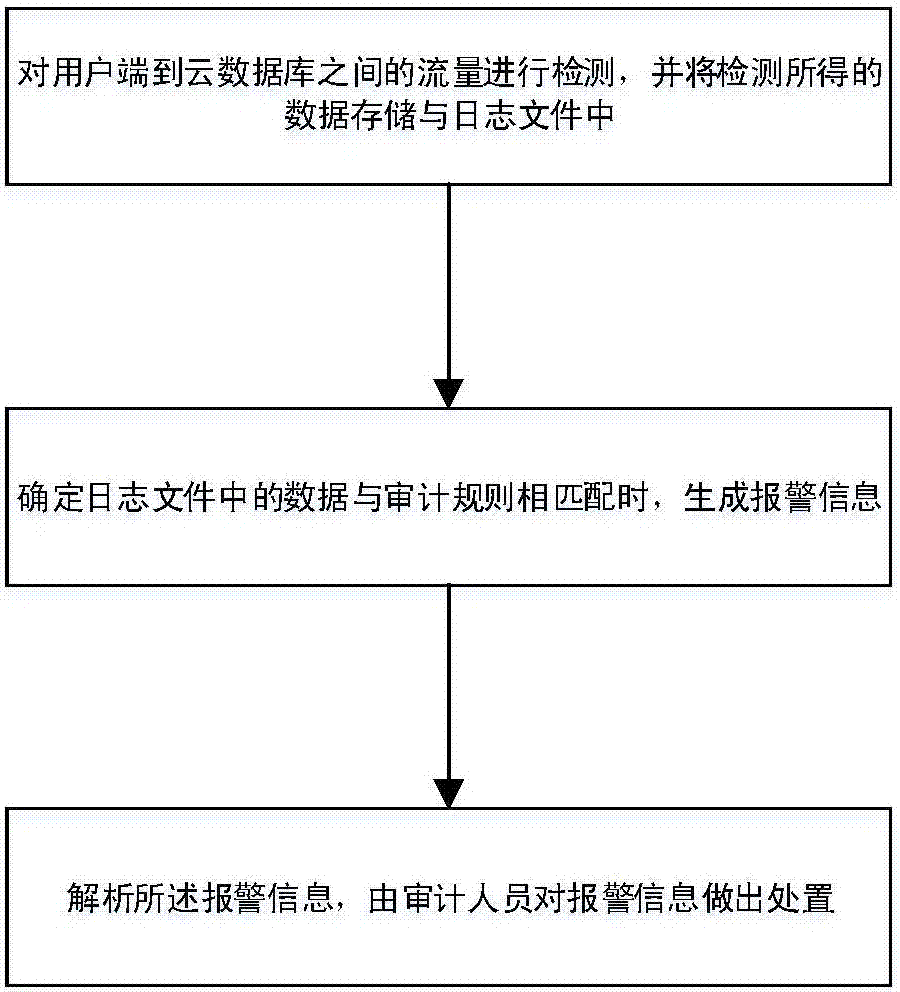
InactiveCN107465661AImprove securityRapid deploymentData switching networksVirtualizationData stream
The invention discloses a cloud database security audit method based on Docker virtualization. The method comprises the following steps: S1, receiving a database name to be accessed and user login information; S2, analyzing the received user input information to obtain a user login account password, a database address and the database name, and generating a database connection instruction according to the information; S3, invoking the database connection instruction, and verifying the user login information; S4, starting a security audit module, monitoring a data stream between a user and a database container between the user and a cloud database to obtain a data source, analyzing requests of the user, and distinguishing a normal request from a malicious request so as to realize secure audit of the cloud database; and S5, operating the database by the user, if user authentication is successful, establishing a stable connection with the security audit module, and operating the database through the security audit module. The method improves the security.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
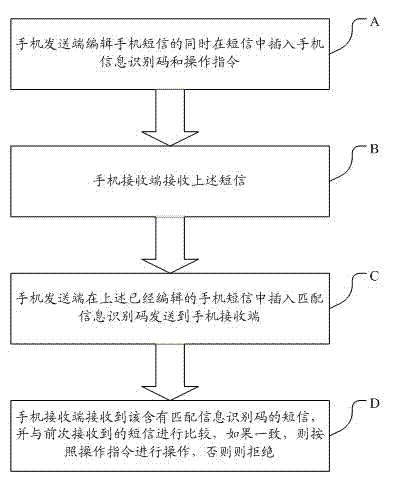
Short message revocation method in sending process of mobile phone short message
InactiveCN103167446AQuick deletePrevent leakageMessaging/mailboxes/announcementsMobile phoneOperations order
The invention discloses a short message revocation method in a sending process of a mobile phone short message. The short message revocation method comprises the following steps: step A, a mobile phone sending terminal edits the short message and inserts a mobile phone information identification code and an operation order at the same time; step B, a mobile phone receiving terminal receives the short message; step C, the mobile phone sending terminal inserts a matching information identification code into the edited short message and sends the edited short message to a mobile phone receiving terminal; and step D, the mobile phone receiving terminal receives the short message containing the matching information identification code, and compares the short message containing the matching information identification code with the short message which is received previously. If the short message containing the matching information identification code is identical to the short message which is received previously, operation is conducted according to the operation order; otherwise the operation order is refused. Compared with the prior art, on the condition that the short message is sent by mistake, the short message revocation method enables the sent short message to be deleted, revoked or covered rapidly, and the conditions that important information is leaked and misunderstandings occur can be avoided effectively.
Owner:SHENZHEN GIONEE COMM EQUIP
Quickly detached cooling fan mounting bracket for computer
InactiveUS7530890B2Quick deleteQuick changeCooling/ventilation/heating modificationsElectrical apparatus casings/cabinets/drawersInterior spaceComputer engineering
A quickly detached cooling fan mounting bracket for a computer, by which a cooling fan can be quickly removed away from a computer chassis without detaching any other peripheral devices, whereby a large enough computer inner space is exposed in order to facilitate rapid replacement of electrical components. The cooling fan mounting bracket includes a cooling fan receptive mount; a cooling fan; a connecting member, which allows the cooling fan receptive mount to be movably installed on the computer chassis; and a orienting member, which secures the cooling fan receptive mount and the cooling fan onto the computer chassis, and prevents the cooling fan from vibration during the normal operation. Compared with the conventional art, the present invention is easier to remove the cooling fan away from the chassis, thereby, facilitates rapid replacement or maintenance of the computer components.
Owner:SHUTTLE
Method for deleting chat messages and associated product
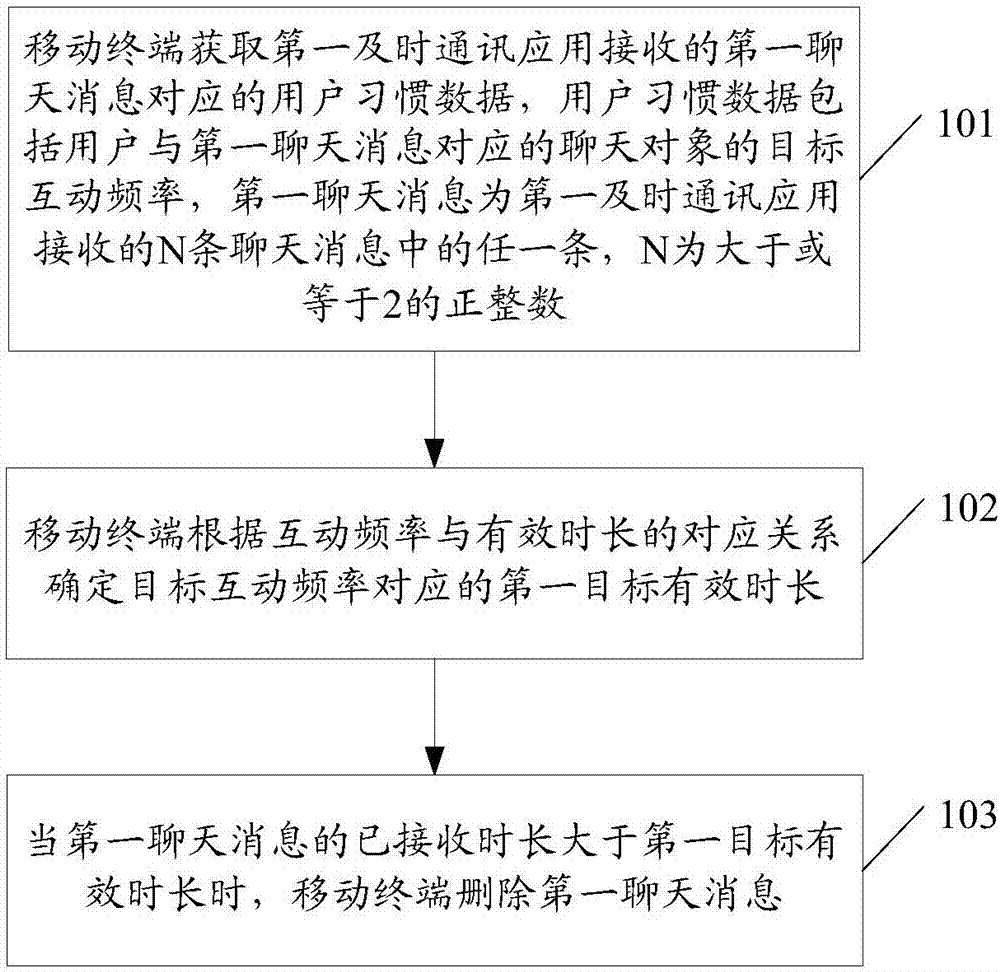
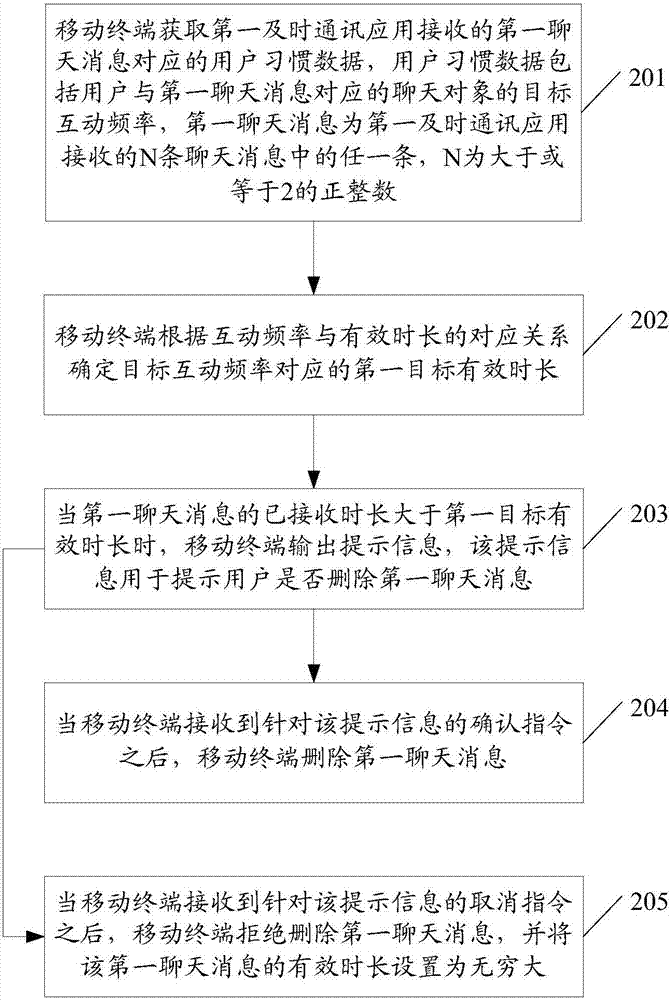
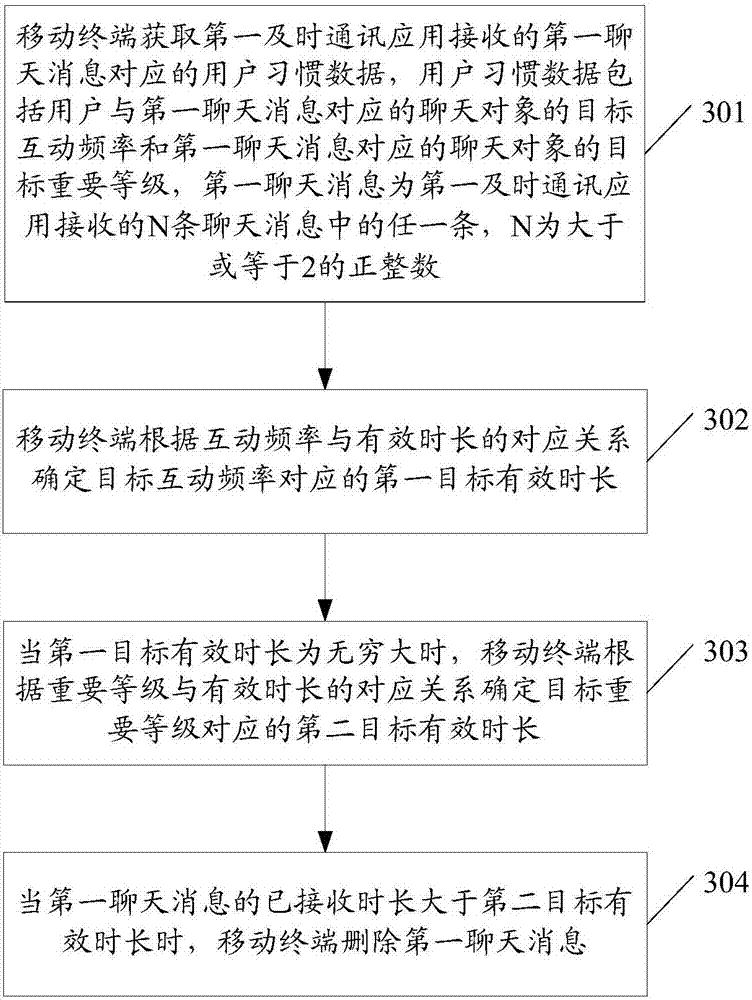
ActiveCN107295173AQuick deleteSave storage spaceSubstation equipmentData switching networksComputer terminalHabit
The embodiments of the invention disclose a method for deleting chat messages and an associated product, wherein the method comprises: obtaining by a mobile terminal the user habit data corresponding to a first chat message received by a first instant communication application, wherein the user habit data comprises the target interaction frequency of the user with the chat object corresponding to the first chat message and the first chat message can be any message of the N chat messages received by the first instant communication application with N being a positive integer equal to or greater than two; according to the corresponding relationship between the interaction frequency and the valid duration, determining the valid duration of the first target corresponding to the interaction frequency; and when the already received duration of the first chat message is longer than the valid duration of the first target, deleting the first chat message. According to the embodiments of the invention, the chat messages that a user is not interested in can be deleted, which saves the storing space of a mobile terminal.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Method and apparatus for binding domain name and specific service
InactiveCN101505305AFlexible topologyEffective Dynamic SettingsTransmissionDomain nameBinding domain
The invention discloses a method for binding a domain name and specific service, which comprises the following steps that: 1) a mapped domain name is generated for a user and specific service; 2) a service storage address corresponding to the domain name is set; 3) a service client requests the analysis of the domain name; 4) a domain name analysis server analyzes the domain name to the corresponding service storage address; and 5) the service client sends the request to the service storage address to acquire the specific service. The technical proposal maps each specific user and specific service to the specific domain name, and the subsequent access of the user is positioned to a preset server by analyzing the specific domain name, thereby achieving the aim of flexible network topology configuration and achieving complete and most effective load balance.
Owner:杭州比比西网络科技有限公司
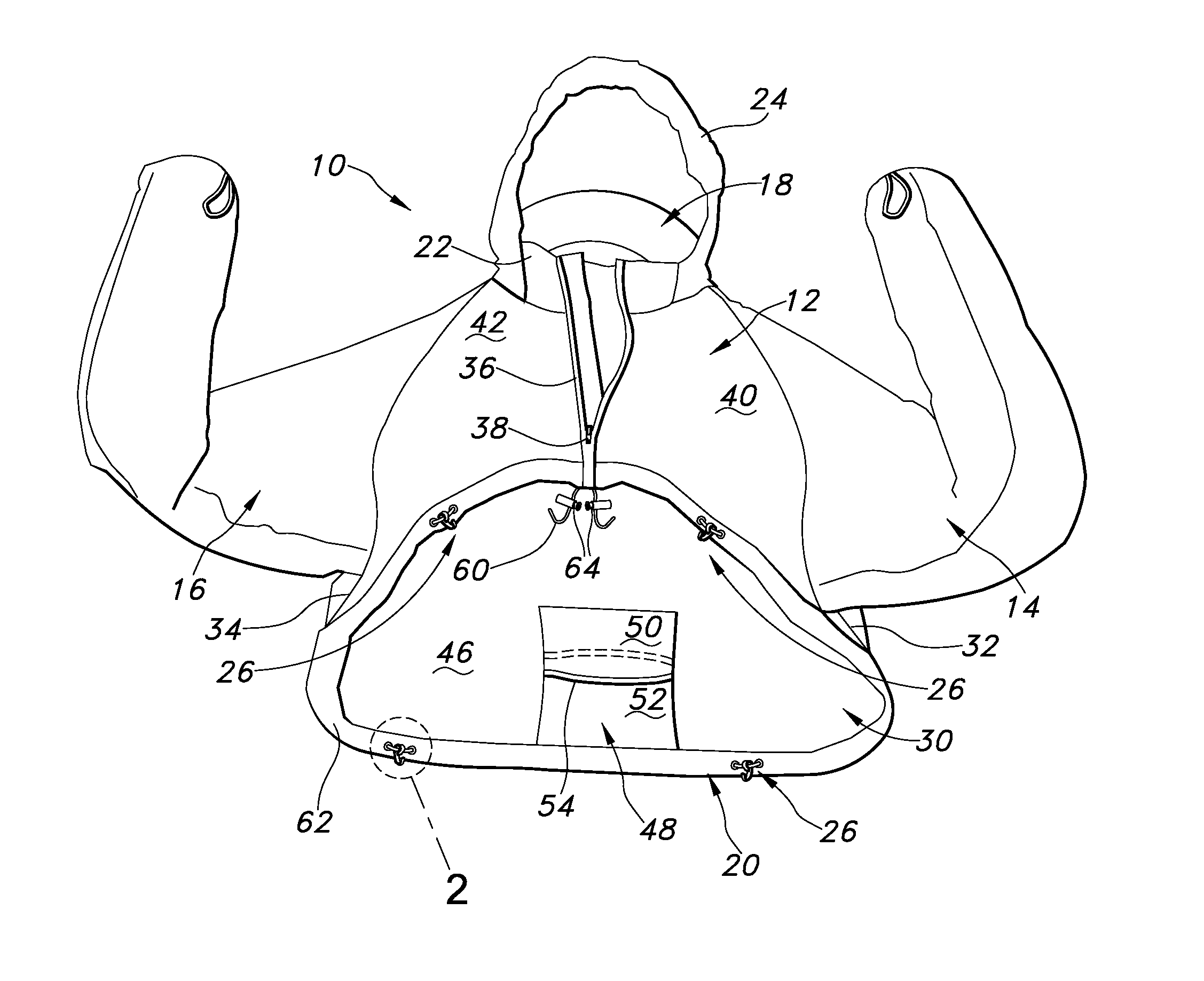
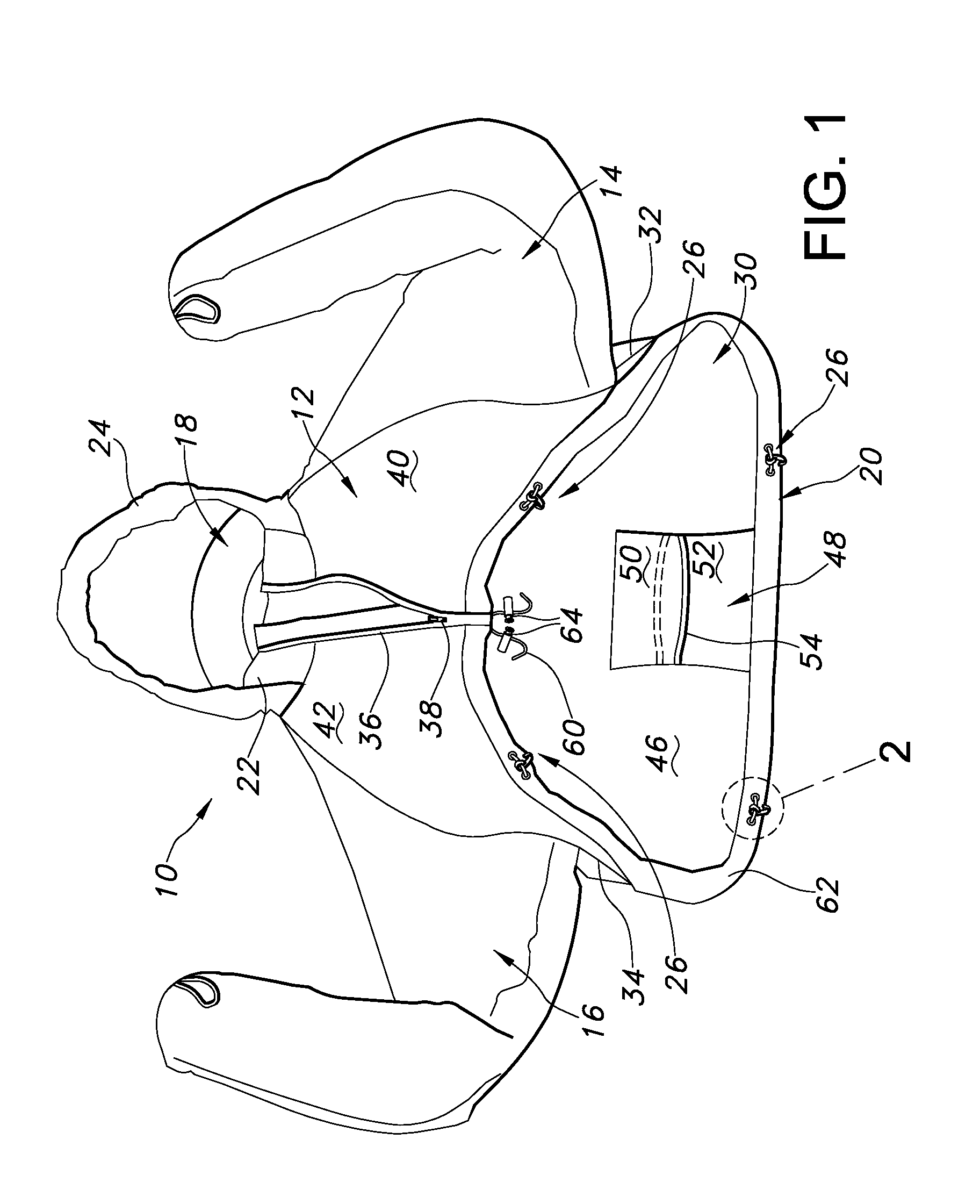
Stowable jacket
ActiveUS20130067631A1Quick removalQuick foldGarment special featuresConvertible garmentFastenerBiomedical engineering
A stowable outerwear garment is provided. The outerwear garment includes a shortened torso portion that deploys from an integral pouch to provide protection to a wearer's upper torso when worn in combination with a load-bearing vest. The shortened torso portion can include an elastic band extending about the wearer's torso and a plurality of fasteners supported by the elastic band to detachably secure the garment to the load-bearing vest. Sleeves can extend from the torso portion and can include an outer waterproof shell, an inner lining and an insulating material therebetween.
Owner:LINEWEIGHT
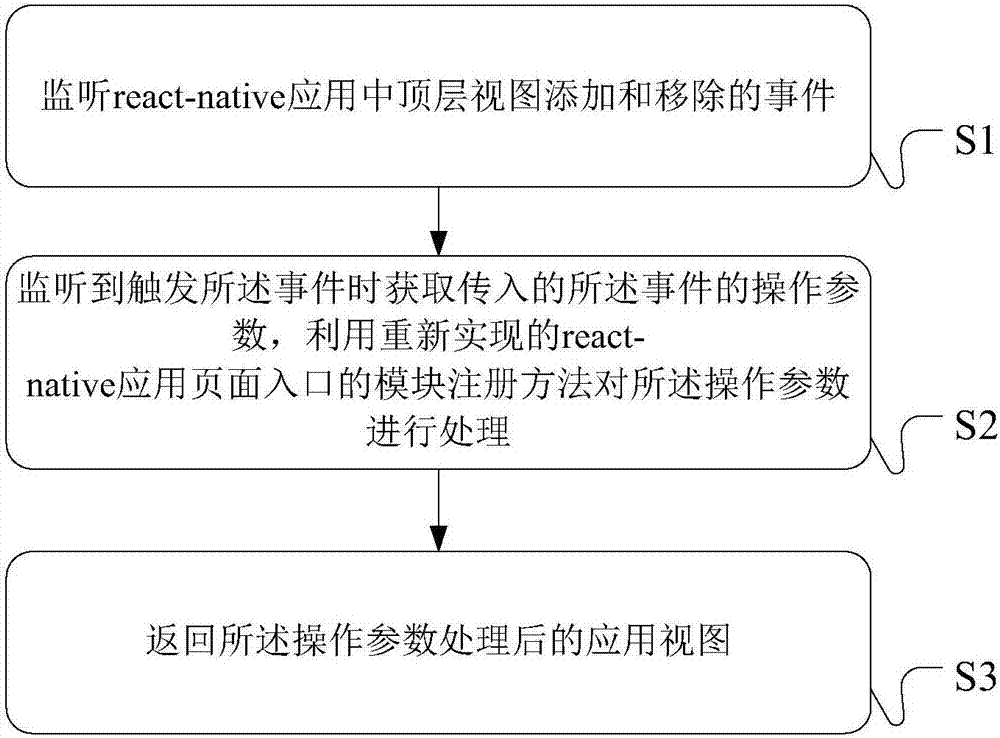
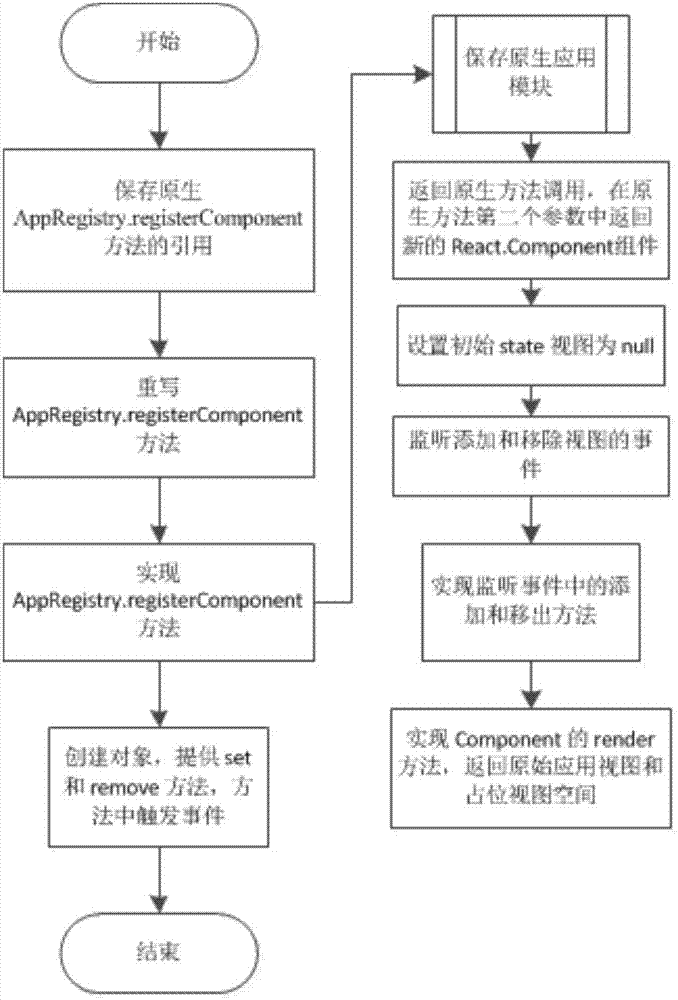
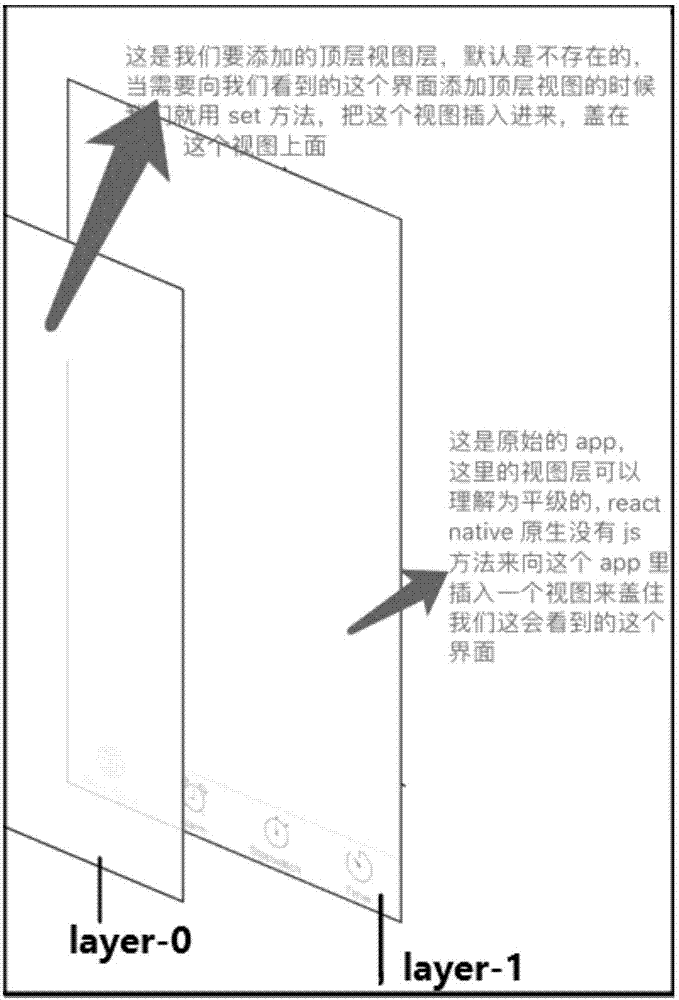
Application top view processing method, device and component
ActiveCN107045438AQuick addQuick deleteSoftware engineeringSpecific program execution arrangementsDevelopment staffComputer engineering
The embodiment of the invention discloses an application top view processing method, device and component. The method comprises the steps that an addition and deletion event of a top view in a react-native application is monitored; when it is monitored that the event is triggered, transmitted operation parameters of the triggered event are acquired, and a module registration method of a react-native application page entrance which is realized again is utilized to process the operation parameters; and an application view obtained after processing of the operation parameters is returned to. By use of all embodiments, the top view can be dynamically added across platforms through simple front-end javascript codes, a developer can add and delete the top view of the application quickly, efficiently and conveniently, learning cost is lowered, the development cycle is shortened, and application development efficiency and developer operation experience are improved.
Owner:ADVANCED NEW TECH CO LTD
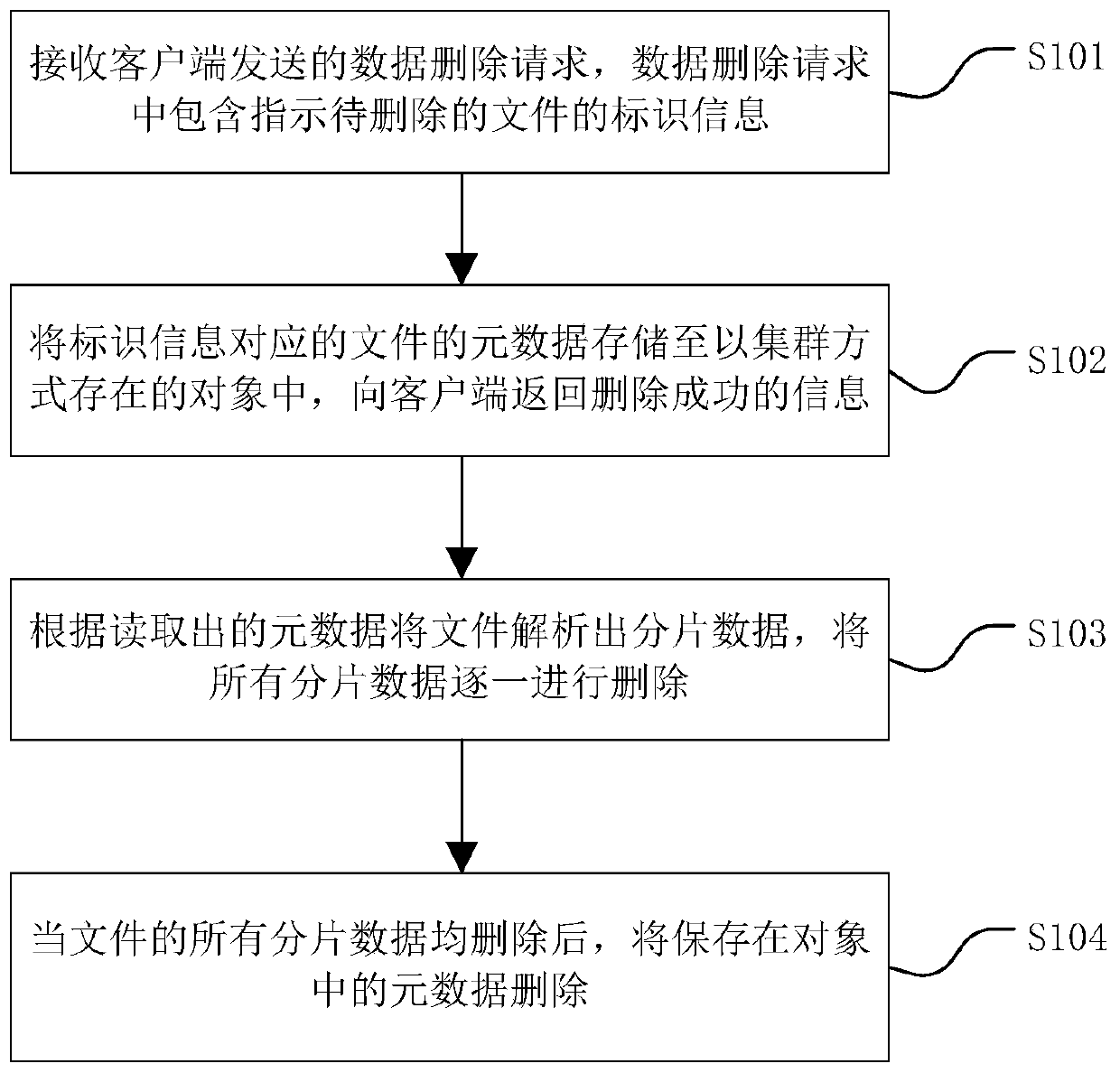
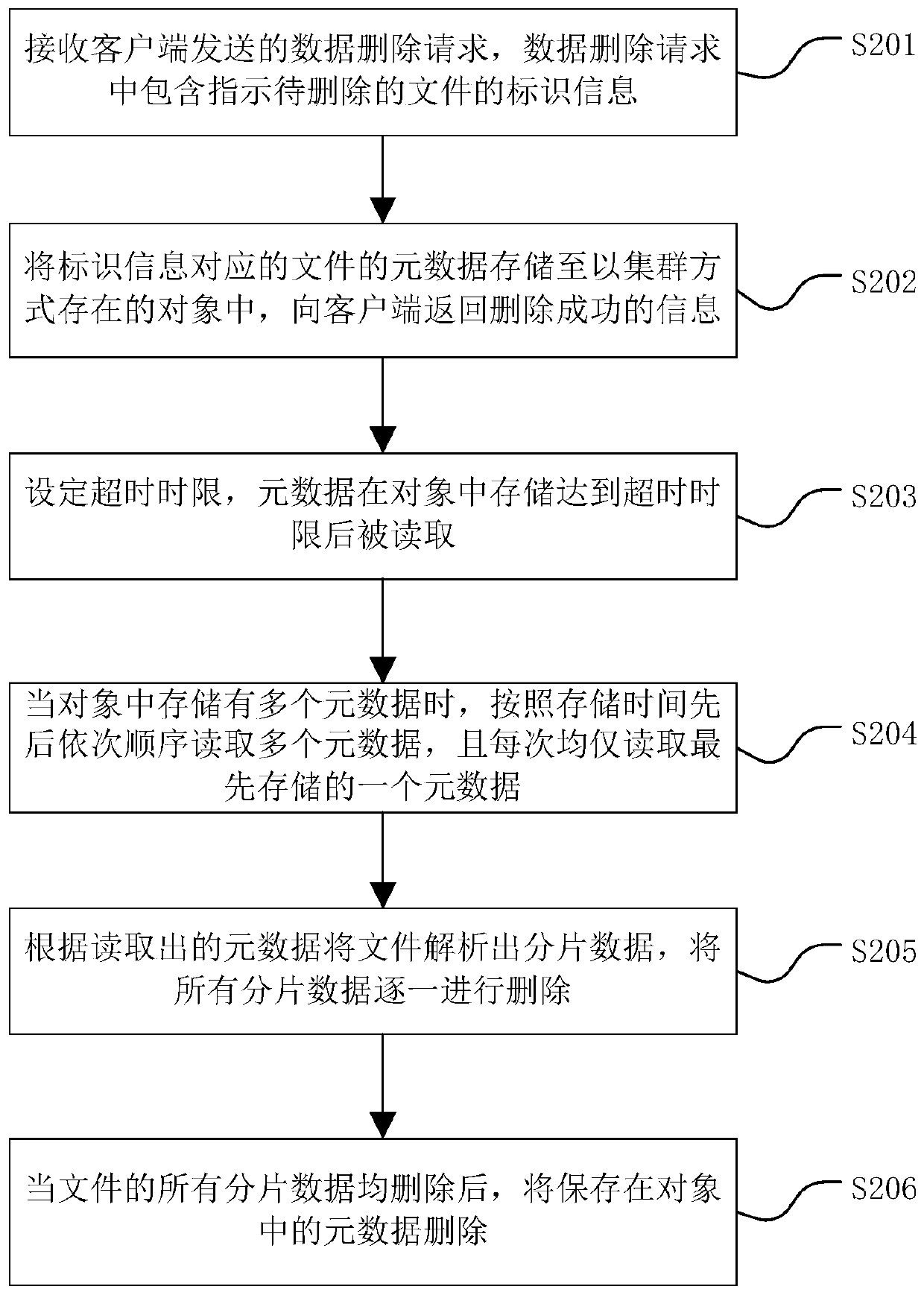
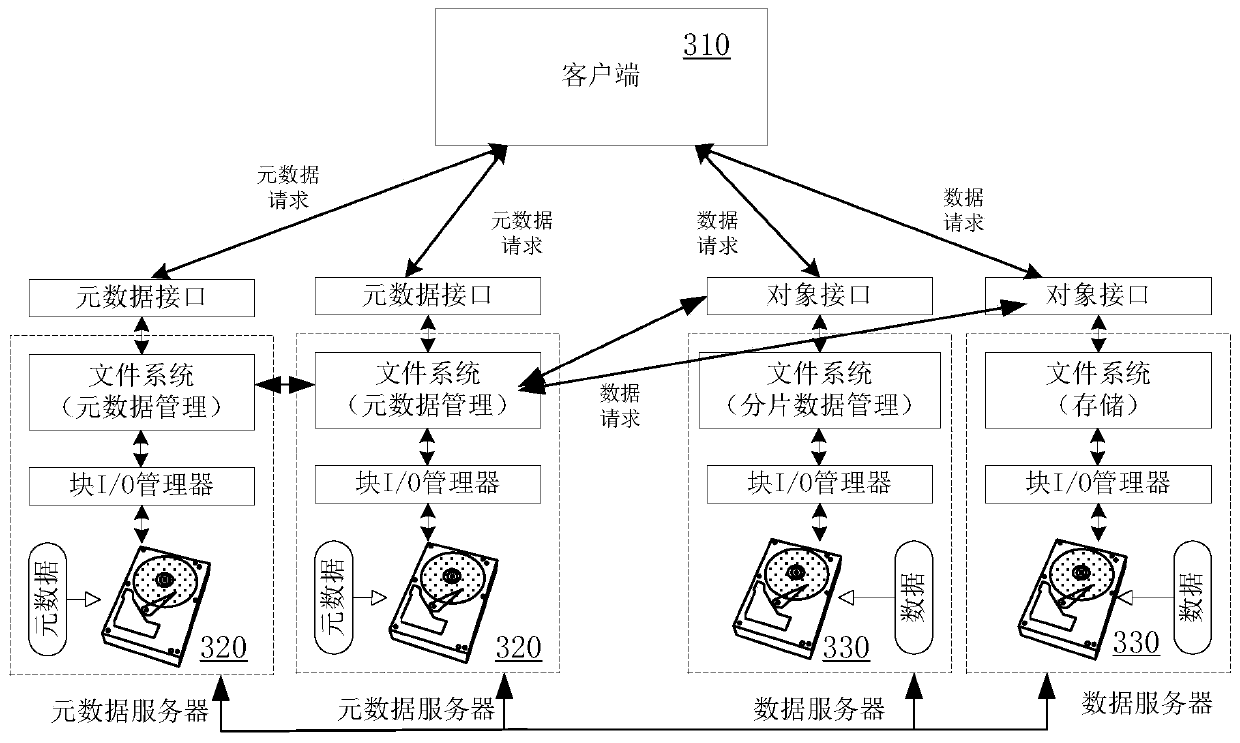
Data deleting method, data deleting device and computer readable storage medium
PendingCN109976668ATimely replacementDoes not take up storage spaceInput/output to record carriersClient-sideMetadata
The invention relates to a data deleting method, a data deleting device and a computer readable storage medium. The data deleting method is applied to the distributed storage system and comprises: receiving a data deleting request sent by a client side, and the data deleting request comprises identification information indicating a file to be deleted; storing the metadata of the file correspondingto the identification information into an object existing in a cluster mode, and returning deletion success information to the client; analyzing the file into fragmented data according to the read metadata, and deleting all the fragmented data one by one; and when all the fragmented data of the file are deleted, deleting the metadata stored in the object. According to the data deleting method, the metadata of the file to be deleted is stored in the cluster, the fragmented data are analyzed according to the metadata to be asynchronously deleted, finally, the metadata is deleted, the file can be safely and rapidly deleted, and meanwhile the deleting integrity and data consistency can be guaranteed.
Owner:BEIJING DAJIA INTERNET INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com